EVPN is an IETF technology per RFC7432, BGP MPLS-Based Ethernet VPN, that uses a new BGP address family and allows VPLS services to be operated as IP-VPNs, where the MAC addresses and the information to set up the flooding trees are distributed by BGP.
Figure 110 shows the use of EVPN for VXLAN overlay tunnels on the 7x50 SR/ESS/XRS when it is used as a Layer-2 DC GW.
Figure 111 shows the use of EVPN for VXLAN overlay tunnels on the 7x50 SR/ESS/XRS, when the DC provides LAYER-2 connectivity and the DC GW can route the traffic to the WAN through an R-VPLS and linked VPRN.
Figure 112 shows the use of EVPN for VXLAN tunnels on the 7x50 SR/ESS/XRS, when the DC provides distributed layer-3 connectivity to the DC tenants.
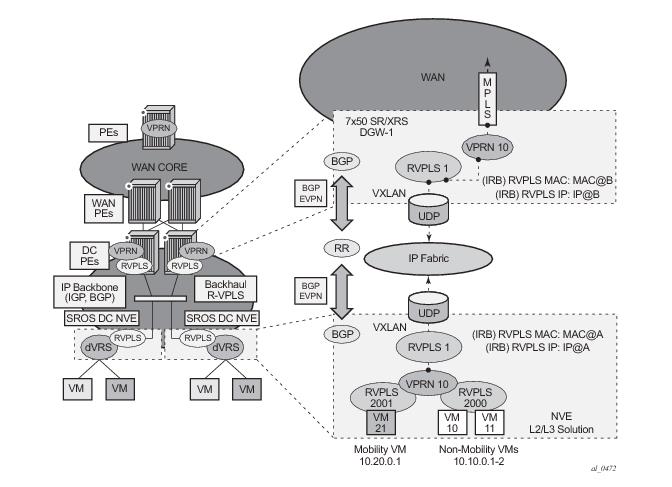
Each tenant will have several subnets for which each DC Network Virtualization Edge (NVE) provides intra-subnet forwarding. An NVE may be a Nuage VSG, VSC/VRS, or any other NVE in the market supporting the same constructs, and each subnet normally corresponds to an R-VPLS. For example, in Figure 112, subnet 10.20.0.0 corresponds to R-VPLS 2001 and subnet 10.10.0.0 corresponds to R-VPLS 2000. In this example, the NVE provides inter-subnet forwarding too, by connecting all the local subnets to a VPRN instance. When the tenant requires L3 connectivity to the IP-VPN in the WAN, a VPRN is defined in the DC GWs, which connects the tenant to the WAN. That VPRN instance will be connected to the VPRNs in the NVEs by means of an IRB (Integrated Routing and Bridging) backhaul R-VPLS. This IRB backhaul R-VPLS provides a scalable solution because it allows L3 connectivity to the WAN without the need for defining all of the subnets in the DC GW.
Figure 113 shows the use of EVPN for VXLAN tunnels on the 7x50 SR/ESS/XRS, when the DC provides distributed layer-3 connectivity to the DC tenants and the VPRN instances are connected through EVPN tunnels.
The solution described in section EVPN for VXLAN Tunnels in a Layer 3 DC with Integrated Routing Bridging Connectivity among VPRNs provides a scalable IRB backhaul R-VPLS service where all the VPRN instances for a specified tenant can be connected by using IRB interfaces. When this IRB backhaul R-VPLS is exclusively used as a backhaul and does not have any SAPs or SDP-bindings directly attached, the solution can be optimized by using EVPN tunnels.
EVPN tunnels are enabled using the evpn-tunnel command under the R-VPLS interface configured on the VPRN. EVPN tunnels provide the following benefits to EVPN-VXLAN IRB backhaul R-VPLS services:
Note — IPv6 interfaces do not require the provisioning of an IPv6 Global Address; a Link Local Address is automatically assigned to the IRB interface.
Figure 114 shows the use of EVPN for MPLS tunnels on the 7x50 SR/ESS/XRS. In this case, EVPN is used as the control plane for ELAN services in the WAN.
Figure 115 shows the use of EVPN for MPLS tunnels on the 7x50 SR/ESS/XRS. In this case, EVPN is used as the control plane for ELAN services in the WAN.
Figure 116 shows an example of the VXLAN encapsulation supported by the Alcatel-Lucent’s implementation.
As shown in Figure 116, VXLAN encapsulates the inner Ethernet frames into VXLAN + UDP/IP packets. The main pieces of information encoded in this encapsulation are:
Note—The 7x50 will never fragment or reassemble VXLAN packets. In addition, the 7x50 always sets the DF (Do not Fragment) flag in the VXLAN outer IP header.
This tool allows the operator to specify a wide range of variables to influence how the packet is forwarded from the VTEP source to VTEP termination. The ping function requires the operator to specify a different test-id (equates to originator handle) for each active and outstanding test. The required local
service identifier from which the test is launched will determine the source IP (the system IP address) to use in the outer IP header of the packet. This IP address is encoded into the VXLAN header Source IP TLV. The service identifier will also encode the local VNI. The
outer-ip-destination must equal the VTEP termination point on the remote node, and the
dest-vni must be a valid VNI within the associated service on the remote node. The remainder of the variables are optional.
oam vxlan-ping test-id 1 service 600 dest-vni 31 outer-ip-destination 1.1.1.31 interval 0.1 send-count 10
vxlan-ping destination vxlan-id 31 ip-address 1.1.1.31 reply-mode udp interval 0.1s count 10
! ! ! ! ! ! ! ! ! !
---- vxlan-id 31 ip-address 1.1.1.31 PING Statistics ----
10 packets transmitted, 10 packets received, 0.00% packet loss
10 non-errored responses(!), 0 out-of-order(*), 0 malformed echo responses(.)
0 send errors(.), 0 time outs(.)
0 overlay segment not found, 0 overlay segment not operational
forward-delay min = 0.912ms, avg = 1.355ms, max = 2.332ms, stddev = 0.425ms
round-trip-delay min = 0.679ms, avg = 0.949ms, max = 1.587ms, stddev = 0.264ms
oam vxlan-ping test-id 2 service 600 dest-vni 31 outer-ip-destination 1.1.1.31 outer-ip-source-udp 65000 outer-ip-ttl 64 inner-l2 d0:0d:1e:00:00:01 inner-ip-source 192.168.1.2 inner-ip-destination 127.0.0.8 reply-mode overlay send-count 20 interval 1 timeout 3 padding 2000 reflect-pad fc nc profile out
vxlan-ping destination vxlan-id 31 ip-address 1.1.1.31 reply-mode overlay interval 1s count 20
=======================================================================================================================
rc=1 Malformed Echo Request Received, rc=2 Overlay Segment Not Present, rc=3 Overlay Segment Not Operational, rc=4 Ok
=======================================================================================================================
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=1 ttl=255 rtt-time=0.722ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=2 ttl=255 rtt-time=0.750ms fwd-time=1.508ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=3 ttl=255 rtt-time=0.974ms fwd-time=0.588ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=4 ttl=255 rtt-time=1.714ms fwd-time=0.819ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=5 ttl=255 rtt-time=0.799ms fwd-time=1.776ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=6 ttl=255 rtt-time=0.892ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=7 ttl=255 rtt-time=0.843ms fwd-time=1.560ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=8 ttl=255 rtt-time=0.825ms fwd-time=1.253ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=9 ttl=255 rtt-time=0.958ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=10 ttl=255 rtt-time=0.963ms fwd-time=1.673ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=11 ttl=255 rtt-time=0.929ms fwd-time=1.697ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=12 ttl=255 rtt-time=0.973ms fwd-time=1.362ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=13 ttl=255 rtt-time=0.813ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=14 ttl=255 rtt-time=0.887ms fwd-time=1.676ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=15 ttl=255 rtt-time=1.119ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=16 ttl=255 rtt-time=1.017ms fwd-time=1.887ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=17 ttl=255 rtt-time=0.873ms fwd-time=1.746ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=18 ttl=255 rtt-time=1.105ms fwd-time=0.000ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=19 ttl=255 rtt-time=0.909ms fwd-time=1.484ms. rc=4
2132 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=20 ttl=255 rtt-time=0.906ms fwd-time=1.849ms. rc=4
---- vxlan-id 31 ip-address 1.1.1.31 PING Statistics ----
20 packets transmitted, 20 packets received, 0.00% packet loss
20 valid responses, 0 out-of-order, 0 malformed echo responses
0 send errors, 0 time outs
0 overlay segment not found, 0 overlay segment not operational
forward-delay min = 0.000ms, avg = 0.951ms, max = 1.887ms, stddev = 0.887ms
round-trip-delay min = 0.722ms, avg = 0.948ms, max = 1.714ms, stddev = 0.202ms
oam vxlan-ping test-id 1 service 600 dest-vni 31 outer-ip-destination 1.1.1.31 send-count 10 end-system 00:00:00:00:00:01 interval 0.1
vxlan-ping destination vxlan-id 31 ip-address 1.1.1.31 reply-mode udp end-system 00:00:00:00:00:01 interval 0.1s count 10
1 1 1 1 1 1 1 1 1 1
---- vxlan-id 31 ip-address 1.1.1.31 PING Statistics ----
10 packets transmitted, 10 packets received, 0.00% packet loss
10 non-errored responses(!), 0 out-of-order(*), 0 malformed echo responses(.)
0 send errors(.), 0 time outs(.)
0 overlay segment not found, 0 overlay segment not operational
10 end-system present(1), 0 end-system not present(2)
forward-delay min = 0.000ms, avg = 0.000ms, max = 0.316ms, stddev = 0.520ms
round-trip-delay min = 0.704ms, avg = 0.855ms, max = 1.151ms, stddev = 0.121ms
oam vxlan-ping test-id 1 service 600 dest-vni 31 outer-ip-destination 1.1.1.31 send-count 10 end-system 00:00:00:00:00:01
vxlan-ping destination vxlan-id 31 ip-address 1.1.1.31 reply-mode udp end-system 00:00:00:00:00:01 interval 1s count 10
=======================================================================================================================
rc=1 Malformed Echo Request Received, rc=2 Overlay Segment Not Present, rc=3 Overlay Segment Not Operational, rc=4 Ok
mac=1 End System Present, mac=2 End System Not Present
=======================================================================================================================
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=1 ttl=255 rtt-time=0.753ms fwd-time=1.240ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=2 ttl=255 rtt-time=0.785ms fwd-time=0.000ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=3 ttl=255 rtt-time=1.425ms fwd-time=2.759ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=4 ttl=255 rtt-time=1.657ms fwd-time=1.659ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=5 ttl=255 rtt-time=0.650ms fwd-time=0.982ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=6 ttl=255 rtt-time=0.894ms fwd-time=0.464ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=7 ttl=255 rtt-time=0.839ms fwd-time=0.581ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=8 ttl=255 rtt-time=0.714ms fwd-time=0.995ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=9 ttl=255 rtt-time=0.798ms fwd-time=0.881ms. rc=4 mac=1
92 bytes from vxlan-id 31 1.1.1.31: vxlan_seq=10 ttl=255 rtt-time=0.839ms fwd-time=1.068ms. rc=4 mac=1
---- vxlan-id 31 ip-address 1.1.1.31 PING Statistics ----
10 packets transmitted, 10 packets received, 0.00% packet loss
10 valid responses, 0 out-of-order, 0 malformed echo responses
0 send errors, 0 time outs
0 overlay segment not found, 0 overlay segment not operational
10 end-system present, 0 end-system not present
forward-delay min = 0.000ms, avg = 0.978ms, max = 2.759ms, stddev = 0.865ms
round-trip-delay min = 0.650ms, avg = 0.935ms, max = 1.657ms, stddev = 0.314ms
*A:PE1# show service id 1 igmp-snooping port-db vxlan vtep 192.0.2.72 vni 1 detail
===============================================================================
IGMP Snooping VXLAN 192.0.2.72/1 Port-DB for service 1
===============================================================================
-------------------------------------------------------------------------------
IGMP Group 232.0.0.1
-------------------------------------------------------------------------------
Mode : exclude Type : dynamic
Up Time : 0d 19:07:05 Expires : 137s
Compat Mode : IGMP Version 3
V1 Host Expires : 0s V2 Host Expires : 0s
-------------------------------------------------------
Source Address Up Time Expires Type Fwd/Blk
-------------------------------------------------------
No sources.
-------------------------------------------------------------------------------
IGMP Group 232.0.0.2
-------------------------------------------------------------------------------
Mode : include Type : dynamic
Up Time : 0d 19:06:39 Expires : 0s
Compat Mode : IGMP Version 3
V1 Host Expires : 0s V2 Host Expires : 0s
-------------------------------------------------------
Source Address Up Time Expires Type Fwd/Blk
-------------------------------------------------------
10.0.0.232 0d 19:06:39 137s dynamic Fwd
-------------------------------------------------------------------------------
Number of groups: 2
===============================================================================
*A:PE1# show service id 1 igmp-snooping statistics vxlan vtep 192.0.2.72 vni 1
===============================================================================
IGMP Snooping Statistics for VXLAN 192.0.2.72/1 (service 1)
===============================================================================
Message Type Received Transmitted Forwarded
-------------------------------------------------------------------------------
General Queries 0 0 556
Group Queries 0 0 0
Group-Source Queries 0 0 0
V1 Reports 0 0 0
V2 Reports 0 0 0
V3 Reports 553 0 0
V2 Leaves 0 0 0
Unknown Type 0 N/A 0
-------------------------------------------------------------------------------
Drop Statistics
-------------------------------------------------------------------------------
Bad Length : 0
Bad IP Checksum : 0
Bad IGMP Checksum : 0
Bad Encoding : 0
No Router Alert : 0
Zero Source IP : 0
Wrong Version : 0
Lcl-Scope Packets : 0
Rsvd-Scope Packets : 0
Send Query Cfg Drops : 0
Import Policy Drops : 0
Exceeded Max Num Groups : 0
Exceeded Max Num Sources : 0
Exceeded Max Num Grp Srcs: 0
MCAC Policy Drops : 0
===============================================================================
*A:PE1# show service id 1 mfib
===============================================================================
Multicast FIB, Service 1
===============================================================================
Source Address Group Address Sap/Sdp Id Svc Id Fwd/Blk
-------------------------------------------------------------------------------
* * sap:1/1/1:1 Local Fwd
* 232.0.0.1 sap:1/1/1:1 Local Fwd
vxlan:192.0.2.72/1 Local Fwd
10.0.0.232 232.0.0.2 sap:1/1/1:1 Local Fwd
vxlan:192.0.2.72/1 Local Fwd
-------------------------------------------------------------------------------
Number of entries: 3
===============================================================================
Figure 117 shows the EVPN MP-BGP NLRI, required attributes and extended communities, and two route types supported for the DC GW Layer 2 applications:
EVPN Route Type 2 – MAC/IP Advertisement Route
Figure 118 shows the IP prefix route or route-type 5.
Figure 110 shows a DC with a Layer-2 service that carries the traffic for a tenant who wants to extend a subnet beyond the DC. The DC PE function is carried out by the 7x50 where a VPLS instance exists for that particular tenant. Within the DC, the tenant will have VPLS instances in all the Network Virtualization Edge (NVE) devices where they require connectivity (such VPLS instances can be instantiated in TORs, Nuage VRS, VSG, and so on). The VPLS instances in the redundant DC GW and the DC NVEs will be connected by VXLAN bindings. BGP-EVPN will provide the required control plane for such VXLAN connectivity.
*A:DGW1>config>service>vpls# info
----------------------------------------------
description "vxlan-service"
vxlan vni 1 create
exit
bgp
route-distinguisher 65001:1
route-target export target:65000:1 import target:65000:1
exit
bgp-evpn
unknown-mac-route
mac-advertisement
vxlan
no shutdown
exit
sap 1/1/1:1 create
exit
no shutdown
----------------------------------------------
|
•
|
no unknown-mac-route and mac-advertisement (default option) — The 7x50 will advertise new learned MACs (on the SAPs or sdp-bindings) or new conditional static MACs.
|
|
•
|
unknown-mac-route and no mac-advertisement — The 7x50 will only advertise an unknown-mac-route as long as the service is operationally UP (if no BGP-MH site is configured in the service) or the 7x50 is the DF (if BGP-MH is configured in the service).
|
|
•
|
unknown-mac-route and mac-advertisement — The 7x50 will advertise new learned MACs, conditional static MACs, and the unknown-mac-route. The unknown-mac-route will only be advertised under the preceding described conditions.
|
*A:DGW# show service id 1 vxlan
===============================================================================
VPLS VXLAN, Ingress VXLAN Network Id: 1
===============================================================================
Egress VTEP, VNI
===============================================================================
VTEP Address Egress VNI Num. MACs Mcast Oper State L2 PBR
-------------------------------------------------------------------------------
192.0.2.71 1 1 Yes Up No
192.0.0.72 1 1 Yes Up No
-------------------------------------------------------------------------------
Number of Egress VTEP, VNI : 2
-------------------------------------------------------------------------------
===============================================================================
|
•
|
When unknown-mac-route is configured, it will be generated when no (BGP-MH) site is configured, or a site is configured AND the site is DF in the PE.
|
Note — The
unknown-mac-route will not be installed in the FDB (therefore, will not show up in the show service id x fdb detail command).
A:PE65# show service id 1000 fdb detail
===============================================================================
Forwarding Database, Service 1000
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1000 00:00:00:00:00:01 vxlan: Evpn 10/05/13 23:25:57
192.0.2.63:1063
1000 00:00:00:00:00:65 sap:1/1/1:1000 L/30 10/05/13 23:25:57
1000 00:ca:ca:ca:ca:00 vxlan: EvpnS 10/04/13 17:35:43
192.0.2.63:1063
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
Note—Although the 7x50 can be configured to generate and advertise the unknown-mac-route, the 7x50 will never honor the unknown-mac-route and will flood to the TLS-flood list when an unknown-unicast packet arrives at an ingress SAP/sdp-binding.
Figure 111 shows a DC with a Layer-2 service that carries the traffic for a tenant who extends a subnet within the DC, while the DC GW is the default gateway for all the hosts in the subnet. The DC GW function is carried out by the 7x50 where an R-VPLS instance exists for that particular tenant. Within the DC, the tenant will have VPLS instances in all the NVE devices where they require connectivity (such VPLS instances can be instantiated in TORs, Nuage VRS, VSG, and so on). The WAN connectivity will be based on existing IP-VPN features.
A:PE73# show router 2 arp
=======================================================================
ARP Table (Service: 2)
=======================================================================
IP Address MAC Address Expiry Type Interface
-----------------------------------------------------------------------
10.10.10.70 d8:46:ff:ff:ff:3e 00h00m00s Evp[I] local
10.10.10.71 d8:47:ff:ff:ff:3e 00h00m00s Evp[I] local
10.10.10.73 d8:49:ff:ff:ff:3e 00h00m00s Oth[I] local
-----------------------------------------------------------------------
No. of ARP Entries: 3
=======================================================================
Figure 112 shows a Layer 3 DC model, where a VPRN is defined in the DC GWs, connecting the tenant to the WAN. That VPRN instance will be connected to the VPRNs in the NVEs by means of an IRB backhaul R-VPLS. Since the IRB backhaul R-VPLS provides connectivity only to all the IRB interfaces and the DC GW VPRN is not directly connected to all the tenant subnets, the WAN ip-prefixes in the VPRN routing table must be advertised in EVPN. In the same way, the NVEs will send IP prefixes in EVPN that will be received by the DC GW and imported in the VPRN routing table.
Note — To generate or process IP prefixes sent or received in EVPN route type 5, the support for IP route advertisement must be enabled in BGP-EVPN. This is performed through the
bgp-evpn>ip-route-advertisement command. This command s disabled by default and must be explicitly enabled. The command is tied to the
allow-ip-int-bind command required for R-VPLS.
Note — Local router interface host addresses are not advertised in EVPN by default. To advertise them, the
ip-route-advertisement incl-host command must be enabled. For example:
===============================================================================
Route Table (Service: 2)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Active Metric
-------------------------------------------------------------------------------
10.1.1.0/24 Local Local 00h00m11s 0
if Y 0
10.1.1.100/32 Local Host 00h00m11s 0
if Y 0
==============================================================================
vprn 500 customer 1 create
ecmp 4
route-distinguisher 65072:500
auto-bind-tunnel
resolution-filter
resolution-filter gre ldp rsvp
vrf-target target:65000:500
interface "evi-502" create
address 20.20.20.72/24
vpls "evpn-vxlan-502"
exit
exit
interface "evi-501" create
address 10.10.10.72/24
vpls "evpn-vxlan-501"
exit
exit
no shutdown
vpls 501 customer 1 create
allow-ip-int-bind
vxlan vni 501 create
exit
bgp
route-distinguisher 65072:501
route-target export target:65000:501 import target:65000:501
exit
bgp-evpn
ip-route-advertisement incl-host
vxlan
no shutdown
exit
exit
service-name "evpn-vxlan-501"
no shutdown
exit
vpls 502 customer 1 create
allow-ip-int-bind
vxlan vni 502 create
exit
bgp
route-distinguisher 65072:502
route-target export target:65000:502 import target:65000:502
exit
bgp-evpn
ip-route-advertisement incl-host
vxlan
no shutdown
exit
exit
service-name "evpn-vxlan-502"
no shutdown
exit
*A:PE72# show router 500 route-table
===============================================================================
Route Table (Service: 500)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
20.20.20.0/24 Local Local 01d11h10m 0
evi-502 0
20.20.20.71/32 Remote BGP EVPN 00h02m26s 169
10.10.10.71 0
156.10.10.0/24 Remote Static 00h00m05s 5
10.10.10.71 1
172.16.0.1/32 Remote BGP EVPN 00h02m26s 169
10.10.10.71 0
-------------------------------------------------------------------------------
No. of Routes: 4
Figure 113 shows an L3 connectivity model that optimizes the solution described in
EVPN for VXLAN in IRB Backhaul R-VPLS Services and IP Prefixes . Instead of regular IRB backhaul R-VPLS services for the connectivity of all the VPRN IRB interfaces, EVPN tunnels can be configured. The main advantage of using EVPN tunnels is that they don't need the configuration of IP addresses, as regular IRB R-VPLS interfaces do.
In addition to the ip-route-advertisement command, this model requires the configuration of the
config>service>vprn>interface>vpls <name> evpn-tunnel.
Note — The evpn-tunnel can be enabled independently of
ip-route-advertisement, however, no route-type 5 advertisements will be sent or processed in that case.
vprn 500 customer 1 create
ecmp 4
route-distinguisher 65071:500
auto-bind-tunnel
resolution-filter
resolution-filter gre ldp rsvp
vrf-target target:65000:500
interface "evi-504" create
vpls "evpn-vxlan-504"
evpn-tunnel
exit
exit
no shutdown
exit
vpls 504 customer 1 create
allow-ip-int-bind
vxlan vni 504 create
exit
bgp
route-distinguisher 65071:504
route-target export target:65000:504 import target:65000:504
exit
bgp-evpn
ip-route-advertisement
vxlan
no shutdown
exit
exit
service-name "evpn-vxlan-504"
no shutdown
exit
Note — EVPN tunnel R-VPLS services do not support SAPs or SDP-binds.
*A:PE71# show router 500 route-table
===============================================================================
Route Table (Service: 500)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
20.20.20.72/32 Remote BGP EVPN 00h23m50s 169
10.10.10.72 0
30.30.30.0/24 Remote BGP EVPN 01d11h30m 169
evi-504 (ET-d8:45:ff:00:01:35) 0
156.10.10.0/24 Remote BGP VPN 00h20m52s 170
192.0.0.69 (tunneled) 0
200.1.0.0/16 Remote BGP EVPN 00h22m33s 169
evi-504 (ET-d8:45:ff:00:01:35) 0
-------------------------------------------------------------------------------
No. of Routes: 4
*A:Dut-A# show router bgp routes evpn ip-prefix prefix 3.0.1.6/32 detail
===============================================================================
BGP Router ID:10.20.1.1 AS:100 Local AS:100
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
Origin codes : i - IGP, e - EGP, ? - incomplete, > - best, b - backup
===============================================================================
BGP EVPN IP-Prefix Routes
===============================================================================
-------------------------------------------------------------------------------
Original Attributes
Network : N/A
Nexthop : 10.20.1.2
From : 10.20.1.2
Res. Nexthop : 192.168.19.1
Local Pref. : 100 Interface Name : NotAvailable
Aggregator AS : None Aggregator : None
Atomic Aggr. : Not Atomic MED : 0
AIGP Metric : None
Connector : None
Community : target:100:1 mac-nh:00:00:01:00:01:02
bgp-tunnel-encap:VXLAN
Cluster : No Cluster Members
Originator Id : None Peer Router Id : 10.20.1.2
Flags : Used Valid Best IGP
Route Source : Internal
AS-Path : No As-Path
EVPN type : IP-PREFIX
ESI : N/A Tag : 1
Gateway Address: 00:00:01:00:01:02
Prefix : 3.0.1.6/32 Route Dist. : 10.20.1.2:1
MPLS Label : 262140
Route Tag : 0xb
Neighbor-AS : N/A
Orig Validation: N/A
Source Class : 0 Dest Class : 0
Modified Attributes
Network : N/A
Nexthop : 10.20.1.2
From : 10.20.1.2
Res. Nexthop : 192.168.19.1
Local Pref. : 100 Interface Name : NotAvailable
Aggregator AS : None Aggregator : None
Atomic Aggr. : Not Atomic MED : 0
AIGP Metric : None
Connector : None
Community : target:100:1 mac-nh:00:00:01:00:01:02
bgp-tunnel-encap:VXLAN
Cluster : No Cluster Members
Originator Id : None Peer Router Id : 10.20.1.2
Flags : Used Valid Best IGP
Route Source : Internal
AS-Path : 111
EVPN type : IP-PREFIX
ESI : N/A Tag : 1
Gateway Address: 00:00:01:00:01:02
Prefix : 3.0.1.6/32 Route Dist. : 10.20.1.2:1
MPLS Label : 262140
Route Tag : 0xb
Neighbor-AS : 111
Orig Validation: N/A
Source Class : 0 Dest Class : 0
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
*A:PE71# show router 30 route-table ipv6
===============================================================================
IPv6 Route Table (Service: 30)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
300::/64 Local Local 00h01m19s 0
int-PE-71-CE-1 0
500::1/128 Remote BGP EVPN 00h01m20s 169
fe80::da45:ffff:fe00:6a-"int-evi-301" 0
-------------------------------------------------------------------------------
No. of Routes: 2
Flags: n = Number of times nexthop is repeated
B = BGP backup route available
L = LFA nexthop available
S = Sticky ECMP requested
===============================================================================
*A:PE71# show router bgp routes evpn ipv6-prefix prefix 500::1/128 hunt
===============================================================================
BGP Router ID:192.0.2.71 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked
Origin codes : i - IGP, e - EGP, ? - incomplete, > - best, b - backup
===============================================================================
BGP EVPN IP-Prefix Routes
===============================================================================
-------------------------------------------------------------------------------
RIB In Entries
-------------------------------------------------------------------------------
Network : N/A
Nexthop : 192.0.2.69
From : 192.0.2.69
Res. Nexthop : 192.168.19.2
Local Pref. : 100 Interface Name : int-71-69
Aggregator AS : None Aggregator : None
Atomic Aggr. : Not Atomic MED : 0
AIGP Metric : None
Connector : None
Community : target:64500:301 bgp-tunnel-encap:VXLAN
Cluster : No Cluster Members
Originator Id : None Peer Router Id : 192.0.2.69
Flags : Used Valid Best IGP
Route Source : Internal
AS-Path : No As-Path
EVPN type : IP-PREFIX
ESI : N/A Tag : 301
Gateway Address: fe80::da45:ffff:fe00:*
Prefix : 500::1/128 Route Dist. : 192.0.2.69:301
MPLS Label : 0
Route Tag : 0
Neighbor-AS : N/A
Orig Validation: N/A
Source Class : 0 Dest Class : 0
Add Paths Send : Default
Last Modified : 00h41m17s
-------------------------------------------------------------------------------
RIB Out Entries
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
Note — The service must be pre-provisioned in the 7x50 using the CLI, SNMP, or other supported interfaces. The VSD will only push a limited number of parameters into the configuration. This 7x50 – VSD integration model is known as a Static-Dynamic provisioning model, because only a few parameters are dynamically pushed by VSD, as opposed to a Fully Dynamic model, where the entire service can be created dynamically by VSD.
|
•
|
The configuration of vsd-domains on those services where VSD will dynamically provision parameters. As part of the static provisioning of a service, the user will configure a domain name (that will be used between VSD and 7750 SR) using a new CLI command vsd-domain name. Any parameters sent by the VSD for an existing service will contain the vsd-domain. Based on that tag, the 7x50 will add the required configuration changes to the correct service.
|
Figure 119 shows the basic XMPP architecture in the data center. While a single XMPP server is represented in the diagram, XMPP allows for easy server clustering and performs message replication to the cluster. It is similar to how BGP can scale and replicate the messages through the use of route reflectors.
A:Dut-C# configure system xmpp server
- no server <xmpp-server-name>
- server <xmpp-server-name> [domain-name <fqdn>] [username <user-name>]
[password <password>] [create]
<xmpp-server-name> : [32 chars max]
<fqdn> : [256 chars max]
<user-name> : [32 chars max]
<password> : [32 chars max]
<create> : keyword - mandatory while creating an entry.
[no] shutdown - Administratively enable or disable XMPP server
|
•
|
When the xmpp server is properly configured and no shutdown, the 7750 SR will try to establish a TCP session with the XMPP server through the management interface first. If it fails to establish communication, the 7750 SR will use an in-band communication and will use its system IP as source IP address. Shutdown will not remove the dynamic configs in all the services. No server will remove all the dynamic configs in all the services.
|
Note—The DNS must be configured on the 7x50 so that the XMPP server name can be resolved. XMPP relies on the Domain Name System (DNS) to provide the underlying structure for addressing, instead of using raw IP addresses. The DNS is configured using the following bof commands:
bof primary-dns,
bof secondary-dns,
bof dns-domain.
Dut# show system xmpp server "vsd1-hy"
===============================================================================
XMPP Server Table
===============================================================================
XMPP FQDN : vsd1-hy.alu.us
XMPP Admin User : csproot
XMPP Oper User : csproot
State Lst Chg Since: 0d 02:56:44 State : Functional
Admin State : Up Connection Mode : outOfBand
Auth Type : md5
IQ Tx. : 47 IQ Rx. : 47
IQ Error : 0 IQ Timed Out : 0
IQ Min. Rtt : 0 ms IQ Max. Rtt : 180 ms
IQ Ack Rcvd. : 47
Push Updates Rcvd : 1 VSD list Upd Rcvd : 12
Msg Tx. : 27 Msg Rx. : 27
Msg Ack. Rx. : 27 Msg Error : 0
Msg Min. Rtt : 0 ms Msg Max. Rtt : 180 ms
Sub Tx. : 1 UnSub Tx. : 0
Msg Timed Out : 0
===============================================================================
*B:Dut>config>system>vsd# info
----------------------------------------------
system-id "SR12U-46-PE"
----------------------------------------------
B:Dut#show system xmpp vsd
===============================================================================
Virtual Services Directory Table
===============================================================================
Id User Name Uptime Status
-------------------------------------------------------------------------------
1 cna@vsd1-hy.alu-srpm.us/nua* 0d 00:44:36 Available
-------------------------------------------------------------------------------
No. of VSD's: 1
===============================================================================
* indicates that the corresponding row element may have been truncated.
*B:Dut#show system xmpp vsd 1
===============================================================================
VSD Server Table
===============================================================================
VSD User Name : cna@vsd1-hy.alu-srpm.us/nuage
Uptime : 0d 00:44:39 Status : Available
Msg Tx. : 16 Msg Rx. : 10
Msg Ack. Rx. : 4 Msg Error : 6
Msg TimedOut : 0 Msg MinRtt : 80 ms
Msg MaxRtt : 240 ms
===============================================================================
Figure 120 shows the workflow for the attachment of the WAN services defined on the DC GW to the DC domains.
Note — The parameters between brackets “[..]” are not configured at this step. They will be pushed by the VSD through XMPP.
In the Static-Dynamic integration model, VSD can only provision certain parameters in VPLS and/or VPRN services. When VSD and the DC GW exchange XMPP messages for a specified service, they use vsd-domains to identify those services. A
vsd-domain is a tag that will be used by the 7x50 and the VSD to correlate a configuration to a service. When redundant DC GWs are available, the
vsd-domain for the same service can have the same or a different name in the two redundant DC GWs.
There are four different types of vsd-domains that can be configured in the 7x50:
The domains will be configured in the config>service# context and assigned to each service.
# configure service vsd domain
- domain <name> [type {l2-domain|vrf-gre|vrf-vxlan|l2-domain-irb}] [create]
- no domain <name>
<name> : [32 chars max]
<create> : keyword
[no] description - Set VSD Domain Description
[no] shutdown - Administratively enable/disable the domain
L2-DOMAIN VSD-domains will be associated with VPLS services configured without a route-target and
vxlan VNI. VSD will configure the route-target and VNI in the 7x50 VPLS service. Some considerations related to L2-DOMAINs are:
|
•
|
ip-route-advertisement and allow-ip-int-bind commands are not allowed in this type of domain. An example of configuration for an L2-DOMAIN association is shown below:
|
*B:Dut>config>service# info
...
vsd
domain nuage_501 type l2-domain create
description "nuage_501_l2_domain"
no shutdown
exit
*B:Dut>config>service# vpls 501
*B:Dut>config>service>vpls# info
----------------------------------------------
bgp
route-distinguisher 192.0.2.2:52
vsi-import “policy-1”
vsi-export “policy-1”
exit
bgp-evpn
exit
sap 1/1/1:501 create
exit
spoke-sdp 10:501 create
no shutdown
exit
vsd-domain "nuage_501"
no shutdown
----------------------------------------------
|
•
|
The VSD will push a dynamic vxlan vni and route-target that the 7x50 will add to the VPLS service. For the route-target, the system will check whether the VPLS service has a configured policy:
|
|
−
|
If there is no vsi-import/export policy, the received dynamic route-target will be added in the vpls>bgp> context, and will be used for all the BGP families in the service.
|
|
−
|
If there is a vsi-import/export policy, the dynamic route-target will be added to the policy, in an auto-created community that will be shown with the following format: “_ VSD_svc-id”. That community will be added to dynamically created entries 1000 and 2000 in the first policy configured in the service vsi-import and vsi-export commands. This allows the user to allocate entries before entries 1000 and 2000 in case other modifications have to be made (user entries would have an action next-entry). An example of the auto-generated entries is shown below:
|
*A:PE# show router policy "policy-1"
entry 900 # manual entry
from
as-path “null"
family evpn
exit
action next-entry
local-preference 500
exit
exit
entry 1000 # automatic VSD-generated entry
from
community "_VSD_1"
family evpn
exit
action accept
exit
exit
entry 2000 # automatic VSD-generated entry
from
family evpn
exit
action accept
community add "_VSD_1"
exit
exit
L2-DOMAIN-IRB VSD-domains will be associated with R-VPLS services configured without a static route-target and
vxlan VNI. VSD will configure the dynamic route-target and VNI in the 7x50 VPLS service. The same considerations described for L2-DOMAINs apply to L2-DOMAIN-IRB domains with one exception:
allow-ip-int-bind is now allowed.
|
•
|
If there is no vrf-import policy, the received dynamic route-target will be added in the vprn> context.
|
|
•
|
If there is a vrf-import policy, the dynamic route-target will be added to the policy, in an auto-created community that will be shown with the following format: “ VSD_svc-id” in a similar way as in L2-DOMAINs.
|
Note — In cases where a
vrf-import policy is used, the user will provision the WAN
route-target statically in a
vrf-export policy. This
route-target will also be used for the routes advertised to the DC.
*A:PE# show router policy "policy-1"
entry 1000 # automatic VSD-generated entry
from
community "_VSD_1"
family vpn-ipv4
exit
action accept
exit
exit
VRF-VXLAN VSD-domains will be associated with R-VPLS services configured without a static route-target and
vxlan VNI. VSD will configure the dynamic route-target and VNI in the 7x50 VPLS service. Some considerations related to VRF-VXLAN domains are:
|
•
|
ip-route-advertisement, allow-ip-int-bind, as well as the VPRN evpn-tunnel commands are now required for this type of VSD-domain. An example of configuration for a VRF-VXLAN association is shown below:
|
*A:Dut>config>service# info
<snip>
vsd
domain L3Domain-1 type vrf-vxlan create
description "L3Domain-example"
no shutdown
exit
*A:Dut>config>service# vpls 20003
*A:Dut>config>service>vpls# info
----------------------------------------------
allow-ip-int-bind
bgp
route-distinguisher 65000:20003
exit
bgp-evpn
ip-route-advertisement
exit
stp
shutdown
exit
service-name "vpls-20003"
vsd-domain "L3Domain-1"
no shutdown
----------------------------------------------
*A:sr7L2-47-PE4# configure service vprn 20002
*A:sr7L2-47-PE4>config>service>vprn# info
----------------------------------------------
route-distinguisher 65000:20002
auto-bind-tunnel
resolution-filter
resolution-filter gre ldp rsvp
vrf-target target:10:10
interface "toDC" create
vpls "vpls-20003"
evpn-tunnel
exit
exit
no shutdown
|
•
|
The VSD will push a dynamic vxlan VNI and route-target that the 7x50 will add to the VPLS service. For the route-target, the system will check whether the VPLS service has a configured policy and will push the route-target either in the service context or the vsi-import/export policies, as described in the section for L2-DOMAINs.
|
*A:Dut# show service service-using vsd
===========================================
Services-using VSD Domain
===========================================
Svc Id Domain
-------------------------------------------
501 nuage_501
200001 MyL2Domain
20003 MyL3Domain
-------------------------------------------
Number of services using VSD Domain: 3
===========================================
*A:Dut# show service vsd domain "MyL3Domain"
===============================================================================
VSD Information
===============================================================================
Name : MyL3Domain
Description : MyL3Domain-example
Type : vrfVxlan Admin State : inService
Last Error To Vsd : (Not Specified)
Last Error From Vsd: (Not Specified)
Statistics
-------------------------------------------------------------------------------
Last Cfg Chg Evt : 02/06/2015 01:28:30 Cfg Chg Evts : 671
Last Cfg Update : 02/06/2015 02:58:41 Cfg Upd Rcvd : 3
Last Cfg Done : 02/06/2015 02:58:41
Cfg Success : 667 Cfg Failed : 0
===============================================================================
*A:Dut# show service vsd domain "MyL3Domain" association
============================================================
Service VSD Domain
============================================================
Svc Id Svc Type Domain Type Domain Admin Origin
------------------------------------------------------------
20003 vpls vrfVxlan inService manual
------------------------------------------------------------
Number of entries: 1
============================================================
The 7x50 administrator only needs to provision parameters required for connectivity to the VSD, a service-range, and configure the python script/policy in the system. Provisioning of service parameters is not required.
The service-range defines the service identifiers to include for VSD provisioned services and, once configured, they are protected from CLI changes. The vsd-policy defines the script to be used:
*A:PE1>config>python# info
----------------------------------------------
python-script "l2-domain_services" create
primary-url "ftp://1.1.1.1/cf2/l2domain_service.py"
no shutdown
exit
python-policy "py-l2" create
description "Python script to create L2 domains"
vsd script "l2-domain_services"
exit
----------------------------------------------
*A:PE1>config>service>vsd# info
----------------------------------------------
service-range 64000 to 65000
----------------------------------------------
|
•
|
Configuration type— Static (for Static-Dynamic model) or Dynamic (for Fully-Dynamic model).
|
|
•
|
External route-target (RT-e) — Used to export/import the BGP routes sent/received from/to the WAN route-reflector. The value can be the same as the RT-i.
|
|
•
|
VNI (VXLAN Network Identifier) — Used to configure the EVPN-VXLAN VPLS service on the 7x50 (if the domain type is L2-DOMAIN, L2-DOMAIN-IRB, or VRF-VXLAN).
|
|
•
|
Metadata — A collection of 'opaque' <key=value> pairs including the rest of the service parameters required for the service configuration at the 7x50.
|
Note — The keys or values do not need to follow any specific format. The python script interprets and translates them into the 7x50 data model.
|
•
|
Python-policy— Used by the 7x50 to find the Python script that will translate the VSD parameters into configuration.
|
Note — The python-script cannot access all the CLI commands and nodes in the system. A white-list of nodes and commands is built and Python will only have access to those nodes/commands. The list can be displayed using the following command:
tools dump service vsd-services command-list.
In addition to the white-list, the user can further restrict the allowed CLI nodes to the VSD by using a separate CLI user for the XMPP interface, and associating that user to a profile where the commands are limited. The CLI user for the XMPP interface is configurable:
config>system>security>cli-script>authorization>
vsd
[no] cli-user <username>
When the system executes a python-script for VSD commands, the vsd cli-user profile is checked to allow the resulting commands. A single CLI user is supported for VSD, therefore, the operator can configure a single 'profile' to restrict (even further than the
whitelist) the CLI commands that can be executed by the VSD Python scripts.
No cli-user means that the system will not perform any authorization checks and the VSD scripts can access any commands that are supported in the
white-list.
Note — The CLI generated by the python-script is not saved in the configuration file and it is not displayed by the info commands when executed on the service contexts. Also the configuration generated by the python-script is protected and cannot be changed by a CLI user.
*A:PE1>config>python# info
----------------------------------------------
python-script "l2-domain_services" create
primary-url "ftp://1.1.1.1/cf2/l2domain_service.py"
no shutdown
exit
python-policy "py-l2" create
description "Python script to create L2 domains"
vsd script "l2-domain_services"
exit
----------------------------------------------
*A:PE1>config>service>vsd# info
----------------------------------------------
service-range 64000 to 65000
----------------------------------------------
{'rt': 'target:64000:64000', 'rte': 'target:64000:64000', 'domain': 'L2-DOMAIN-1', 'servicetype': 'L2DOMAIN', 'vni': '64000', 'metadata': 'rd=1:1, sap=1/1/10:3000'}
|
→
|
If a specified setup_script() fails, the teardown_script() is invoked.
|
|
→
|
If the modify_script() fails, the revert_script() is invoked. The teardown_script() is invoked if the revert_script() fails or does not exist.
|
|
•
|
The python-policy is always present in the attributes received from VSD; if the VSD user does not include a policy name, VSD will include 'default' as the python-policy. Hence, care must be taken to ensure that the 'default' policy is always configured in the 7750.
|
Note — The CLI configured services cannot be modified when the user is in
enable-vsd-config mode.
|
•
|
Unless the CLI user enters the enable-vsd-config mode, changes of the dynamic created services are not allowed in the CLI. However, changes through SNMP are allowed.
|
|
•
|
The command tools perform service vsd evaluate-script is introduced to allow the user to test their setup and to modify and tear down python scripts in a lab environment without the need to be connected to a VSD. The successful execution of the command for action setup will create a vsd domain and the corresponding configuration, just as the system would do when the parameters are received from VSD.
|
The following example shows the use of the tools perform service vsd evaluate-script command:
*A:PE1# tools perform service vsd evaluate-script domain-name "L2-DOMAIN-5" type l2-domain action setup policy "py-l2" vni 64000 rt-i target:64000:64000 rt-e target:64000:64000 metadata "rd=1:1, sap=1/1/10:3000"
Success
*A:PE1# show python python-script "l2-domain_services" source-in-use
===============================================================================
Python script "l2-domain_services"
===============================================================================
Admin state : inService
Oper state : inService
Primary URL : ftp://1.1.1.1/timos86/cses-V71/cf2/l2domain_service.py
Secondary URL : (Not Specified)
Tertiary URL : (Not Specified)
Active URL : primary
-------------------------------------------------------------------------------
Source (dumped from memory)
-------------------------------------------------------------------------------
1 from alc import dyn
2
3 def setup_script(vsdParams):
4
5 print ("These are the VSD params: " + str(vsdParams))
6 servicetype = vsdParams.get('servicetype')
7 vni = vsdParams.get('vni')
8 metadata = vsdParams['metadata']
9 print ("VSD metadata: " + str(metadata))
10 metadata = dict(e.split('=') for e in metadata.split(','))
11 print ("Modified metadata: " + str(metadata))
12 vplsSvc_id = dyn.select_free_id("service-id")
13 print ("this is the free svc id picked up by the system: " + vplsSvc_id)
14
15 if servicetype == "L2DOMAIN":
16 rd = metadata['rd']
17 sap_id = metadata[' sap']
18 print ('servicetype, VPLS id, rd, sap:', servicetype, vplsSvc_id, rd, sap_id)
19 dyn.add_cli("""
20 configure service
21 vpls %(vplsSvc_id)s customer 1 create
22 description vpls%(vplsSvc_id)s
23 bgp
24 route-distinguisher %(rd)s
25 route-target %(rt)s
26 exit
27 vxlan vni %(vni)s create
28 exit
29 bgp-evpn
30 evi %(vplsSvc_id)s
31 vxlan
32 no shutdown
33 exit
34 exit
35 service-name evi%(vplsSvc_id)s
36 sap %(sap_id)s create
37 exit
38 no shutdown
39 exit
40 exit
41 exit
42 """ % {'vplsSvc_id' : vplsSvc_id, 'vni' : vsdParams['vni'], 'rt' : vsdParams['rt'], 'rd' : metadata['rd'], 'sap_id' : sap_id})
43 # L2DOMAIN returns setupParams: vplsSvc_id, servicetype, vni, sap
44 return {'vplsSvc_id' : vplsSvc_id, 'servicetype' : servicetype, 'vni' : vni, 'sap_id' : sap_id}
45
46
47 #---------------------------------------------------------------------------------
48
49 def teardown_script(setupParams):
50 print ("These are the teardown_script setupParams: " + str(setupParams))
51 servicetype = setupParams.get('servicetype')
52 if servicetype == "L2DOMAIN":
53 dyn.add_cli("""
54 configure service
55 vpls %(vplsSvc_id)s
56 no description
57 bgp-evpn
58 vxlan
59 shutdown
60 exit
61 no evi
62 exit
63 no vxlan vni %(vni)s
64 bgp
65 no route-distinguisher
66 no route-target
67 exit
68 no bgp
69 no bgp-evpn
70 sap %(sap_id)s
71 shutdown
72 exit
73 no sap %(sap_id)s
74 shutdown
75 exit
76 no vpls %(vplsSvc_id)s
77 exit
78 exit
79 """ % {'vplsSvc_id' : setupParams['vplsSvc_id'], 'vni' : setupParams['vni'], 'sap_id' : setupParams['sap_id']})
80 return setupParams
81
82
83 d = { "script" : (setup_script, None, None, teardown_script) }
84
85 dyn.action(d)
===============================================================================
{'rt': 'target:64000:64000', 'rte': 'target:64000:64000', 'domain': 'L2-DOMAIN-5', 'servicetype': 'L2DOMAIN', 'vni': '64000', 'metadata': 'rd=1:1, sap=1/1/10:3000 '}
123 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base dyn-script req=setup
"dyn-script req=setup: L2-DOMAIN-5
state=init->waiting-for-setup
"
124 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base dyn-script req=setup
"dyn-script req=setup: L2-DOMAIN-5
state=waiting-for-setup->generating-setup
"
125 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base Python Output
"Python Output: l2-domain_services
These are the VSD params: {'rt': 'target:64000:64000', 'rte': 'target:64000:6400
0', 'domain': '', 'servicetype': 'L2DOMAIN', 'vni': '64000', 'metadata': 'rd=1:1
, sap=1/1/10:3000 '}
VSD metadata: rd=1:1, sap=1/1/10:3000
Modified metadata: {'rd': '1:1', ' sap': '1/1/10:3000 '}
this is the free svc id picked up by the system: 64000
('servicetype, VPLS id, rd, sap:', 'L2DOMAIN', '64000', '1:1', '1/1/10:3000 ')
"
Success
126 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base Python Result
"Python Result: l2-domain_services
"
127 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base dyn-script req=setup
"dyn-script req=setup: L2-DOMAIN-5
state=generating-setup->executing-setup
"
128 2015/06/16 23:35:40.22 UTC MINOR: DEBUG #2001 Base dyn-script cli 1/1
"dyn-script cli 1/1: script:L2-DOMAIN-5(cli 698 dict 0->126)
configure service
vpls 64000 customer 1 create
description vpls64000
bgp
route-distinguisher 1:1
route-target target:64000:64000
exit
vxlan vni 64000 create
exit
bgp-evpn
evi 64000
vxlan
no shutdown
exit
exit
service-name evi64000
sap 1/1/10:3000 create
exit
no shutdown
exit
exit
exit
"
143 2015/06/16 23:35:40.23 UTC MINOR: DEBUG #2001 Base dyn-script req=setup
"dyn-script req=setup: L2-DOMAIN-5
state=executing-setup->established"
Table 18 lists all the EVPN routes supported in 7x50 SROS and their usage in EVPN-VXLAN, EVPN-MPLS, and PBB-EVPN.
Note — Route type 1 is not required in PBB-EVPN as per draft-ietf-l2vpn-pbb-evpn.
Note — The unknown-mac-route is not supported for EVPN-MPLS services.
Note — The AD per-EVI route is not sent with the ESI label Extended Community.
*A:PE-1>config>service>vpls# info
----------------------------------------------
description "evpn-mpls-service"
bgp
bgp-evpn
evi 10
vxlan
shutdown
mpls
no shutdown
auto-bind-tunnel resolution any
sap 1/1/1:1 create
exit
spoke-sdp 1:1 create
The user will configure a bgp-evpn context where
vxlan must be shutdown and
mpls no shutdown. In addition to the
mpls no shutdown command, the minimum set of commands to be configured to set up the EVPN-MPLS instance are the
evi and the
auto-bind-tunnel resolution commands. However, the user can configure some other options. The most relevant configuration options are described below.
evi {1..65535} — This EVPN identifier is unique in the system and will be used for the service-carving algorithm used for multi-homing (if configured) and auto-deriving route-target and route-distinguishers in the service. It can be used for EVPN-MPLS and EVPN-VXLAN services.
Note — When the vsi-import/export polices are configured, the route-target must be configured in the policies and those values take preference over the auto-derived route-targets. The operational route-target for a service will be displayed by the
show service id x bgp command.
When the evi is configured, a
config>service>vpls>bgp node (even empty) is required to allow the user to see the correct information on the
show service id 1 bgp and
show service system bgp-route-distinguisher commands.
Although not mandatory, if no multi-homing is configured, the configuration of an evi is enforced for EVPN services with SAPs/SDP-bindings in an
ethernet-segment. See the 'EVPN multi-homing' section for more information about
ethernet-segments.
|
•
|
control-word: Required as per RFC7432 to avoid frame disordering. The user can enable/disable it so that interoperability to other vendors can be guaranteed.
|
|
•
|
auto-bind-tunnel: Allows the user to decide what type of MPLS transport tunnels will be used for a particular instance. The command will be used in the same way as it is used in VPRN services.
|
Note — For bgp-evpn mpls, ‘
bgp’ is explicitly added to the
resolution-filter in EVPN (‘
bgp’ is implicit in VPRNs).
|
•
|
force-vlan-vc-forwarding: This command will allow the system to preserve the vlan-id and pbits of the service-delimiting qtag in a new tag added in the customer frame before sending it to the EVPN core.
|
Note — This command may be used in conjunction with the
sap ingress vlan-translation command. If so, the configured translated vlan-id will be the vlan-id sent to the EVPN binds as opposed to the service-delimiting tag vlan-id. If the ingress SAP/binding is ‘null’-encapsulated, the output vlan-id and pbits will be zero.
|
•
|
split-horizon-group: This command allows the association of a user-created split-horizon-group to all the EVPN-MPLS destinations. See the EVPN and VPLS integration section for more information.
|
|
•
|
ecmp: When this command is set to a value greater than 1, aliasing is activated to the remote PEs that are defined in the same all-active multi-homing ethernet-segment. See the EVPN multi-homing section for more information.
|
|
•
|
ingress-replication-bum-label: This command is only enabled when the user wants the PE to advertise a label for BUM traffic (Inclusive Multicast routes) that is different from the label advertised for unicast traffic (with the MAC/IP routes). This is useful to avoid potential transient packet duplication in all-active multi-homing.
|
Those bindings, as well as the MACs learned on them, can be checked through the following show commands. In the following example, the remote PE(192.0.2.69) is configured with no ingress-replication-bum-label and PE(192.0.2.70) is configured with
ingress-replication-bum-label. Hence, Dut has a single EVPN-MPLS destination binding to PE(192.0.2.69) and two bindings (unicast and multicast) to PE(192.0.2.70).
*A:Dut# show service id 1 evpn-mpls
===============================================================================
BGP EVPN-MPLS Dest
===============================================================================
TEP Address Egr Label Num. MACs Mcast Last Change
Transport
-------------------------------------------------------------------------------
192.0.2.69 262118 1 Yes 06/11/2015 19:59:03
ldp
192.0.2.70 262139 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.70 262140 1 No 06/11/2015 19:59:03
ldp
192.0.2.72 262140 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.72 262141 1 No 06/11/2015 19:59:03
ldp
192.0.2.73 262139 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.254 262142 0 Yes 06/11/2015 19:59:03
bgp
-------------------------------------------------------------------------------
Number of entries : 7
-------------------------------------------------------------------------------
===============================================================================
*A:Dut# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:ca:fe:ca:fe:69 eMpls: EvpnS 06/11/15 21:53:48
192.0.2.69:262118
1 00:ca:fe:ca:fe:70 eMpls: EvpnS 06/11/15 19:59:57
192.0.2.70:262140
1 00:ca:fe:ca:fe:72 eMpls: EvpnS 06/11/15 19:59:57
192.0.2.72:262141
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
|
•
|
The bgp-evpn mpls split-horizon-group must reference a user-configured split-horizon-group. User-configured split-horizon-groups can be configured within the service context. The same group-name can be associated with saps, spoke-sdps, pw-templates, pw-template-bindings, and EVPN-MPLS endpoints.
|
|
•
|
If the split-horizon-group command in bgp-evpn>mpls> is not used, the default split-horizon-group (in which all the EVPN endpoints are) is still used, but it will not be possible to refer to it on saps/spoke-sdps.
|
|
•
|
The SAPs and/or spoke-SDPs added to an EVPN split-horizon-group should not be part of any EVPN multi-homed ES. If that happened, the PE would still advertise the AD per-EVI route for the SAP and/or spoke-SDP, attracting EVPN traffic that could not possibly be forwarded to that SAP and/or sdp-binding.
|
|
•
|
Similar to the preceding statement, a split-horizon-group composed of SAPs/sdp-bindings used in a BGP-MH site should not be configured under bgp-evpn>mpls>split-horizon-group. This misconfiguration would prevent traffic being forwarded from the EVPN to the BGP-MH site, regardless of the DF/NDF state.
|
Figure 123 shows an example of EVPN-VPLS integration.
*A:PE1>config>service# info
----------------------------------------------
pw-template 1 create
vpls 1 customer 1 create
split-horizon-group "SHG-1" create
bgp
route-target target:65000:1
pw-template-binding 1 split-horizon-group SHG-1
bgp-ad
no shutdown
vpls-id 65000:1
bgp-evpn
evi 1
mpls
no shutdown
split-horizon-group SHG-1
spoke-sdp 12:1 create
exit
sap 1/1/1:1 create
exit
*A:PE5>config>service# info
----------------------------------------------
pw-template 1 create
vpls 1 customer 1 create
bgp
route-target target:65000:1
pw-template-binding 1 split-horizon-group SHG-1 # auto-created SHG
bgp-ad
no shutdown
vpls-id 65000:1
spoke-sdp 52:1 create
exit
*A:PE2>config>service# info
----------------------------------------------
vpls 1 customer 1 create
end-point CORE create
no suppress-standby-signaling
spoke-sdp 21:1 end-point CORE
precedence primary
spoke-sdp 25:1 end-point CORE
In a VPLS service, multiple BGP families and protocols can be enabled at the same time. When bgp-evpn is enabled,
bgp-ad and
bgp-mh are supported as well (not bgp-vpls in 13.0.R4). Note that a single RD is used per service and not per BGP family/protocol.
Note — This reconfiguration will fail if the new RD already exists in a different VPLS/epipe.
|
•
|
Because the vpls-id takes precedence over the evi when deriving the RD automatically, adding evpn to an existing bgp-ad service will not impact the existing RD - this is important to support bgp-ad to evpn migration.
|
EVPN multi-homing implementation is based on the concept of the ethernet-segment. An
ethernet-segment is a logical structure that can be defined in one or more PEs and identifies the CE (or access network) multi-homed to the EVPN PEs. An
ethernet-segment is associated with port, LAG, or SDP objects and is shared by all the services defined on those objects.
Each ethernet-segment has a unique identifier called
esi (Ethernet Segment Identifier) that is 10 bytes long and is manually configured in the 7x50.
NOTE: The
esi is advertised in the control plane to all the PEs in an EVPN network; therefore, it is very important to ensure that the 10-byte
esi value is unique throughout the entire network. Single-homed CEs are assumed to be connected to an ethernet-segment with esi = 0 (single-homed ethernet-segments are not explicitly configured).
Figure 124 shows the need for DF election in all-active multi-homing.
Note — BUM traffic from the CE to the network and known unicast traffic in any direction is allowed on both the DF and non-DF PEs.
Figure 125 shows the EVPN split-horizon concept for all-active multi-homing.
Figure 126 shows the EVPN aliasing concept for all-active multi-homing.
*A:PE1>config>lag(1)# info
----------------------------------------------
mode access
encap-type dot1q
port 1/1/2
lacp active administrative-key 1 system-id 00:00:00:00:00:22
no shutdown
*A:PE1>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 1.1.1.1:0
ethernet-segment "ESI2" create
esi 01:12:12:12:12:12:12:12:12:12
multi-homing all-active
service-carving
lag 1
no shutdown
*A:PE1>config>redundancy>evpn-multi-homing# info
----------------------------------------------
boot-timer 120
es-activation-timer 10
*A:PE1>config>service>vpls# info
----------------------------------------------
description "evpn-mpls-service with all-active multihoming"
bgp
bgp-evpn
evi 10
mpls
no shutdown
auto-bind-tunnel resolution any
sap lag-1:1 create
exit
*A:PE1>config>lag(1)# info
----------------------------------------------
mode access
encap-type dot1q
port 1/1/1
lacp active administrative-key 1 system-id 00:00:00:00:00:22
no shutdown
*A:PE1>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 1.1.1.1:0
ethernet-segment "ESI12" create
esi 01:12:12:12:12:12:12:12:12:12
multi-homing all-active
service-carving
lag 1
no shutdown
*A:PE1>config>redundancy>evpn-multi-homing# info
----------------------------------------------
boot-timer 120
es-activation-timer 10
*A:PE1>config>service>vpls# info
----------------------------------------------
description "evpn-mpls-service with all-active multihoming"
bgp
route-distinguisher 65001:60
route-target target:65000:60
bgp-evpn
evi 10
mpls
no shutdown
auto-bind-tunnel resolution any
sap lag-1:1 create
exit
|
•
|
The ethernet-segment must be configured with a name and a 10-byte esi:
|
|
→
|
config> service> system> bgp-evpn#ethernet-segment < es_name> create
|
|
→
|
config> service> system> bgp-evpn> ethernet-segment# esi < value>
|
|
•
|
Only a LAG can be associated with the ethernet-segment. This LAG will be exclusively used for EVPN multi-homing. Other LAG ports in the system can be still used for MC-LAG and other services.
|
|
•
|
The same ethernet-segment may be used for EVPN-MPLS and PBB-EVPN services. Note — The source-bmac-lsb attribute must be defined for PBB-EVPN (so that it will only be used in PBB-EVPN, and ignored by EVPN). Other than EVPN-MPLS and PBB-EVPN I-VPLS/Epipe services, no other Layer-2 services are allowed in the same ethernet-segment (regular VPLS or EVPN-VXLAN SAPs defined on the ethernet-segment will be kept operationally down).
|
Ethernet-segment ESI-1 is configured as per the previous section, with all the required parameters. When
ethernet-segment no shutdown is executed, PE1 and PE2 will advertise an ES route for ESI-1. They will both include the route-target auto-derived from the MAC portion of the configured ESI. If the route-target address family is configured in the network, this will allow the RR to keep the dissemination of the ES routes under control.
Note — the remote PE IPs must be present in the local PE's RTM so that they can participate in the DF election.
|
•
|
An es-activation-timer can be configured at the redundancy>bgp-evpn-multi-homing>es-activation-timer level or at the service>system>bgp-evpn>eth-seg>es-activation-timer level. This timer, which is 3 seconds by default, delays the transition from non-DF to DF for a specified service, after the DF election has run.
|
|
→
|
This use of the es-activation-timer is different from zero and minimizes the risks of loops and packet duplication due to "transient" multiple DFs.
|
|
→
|
The same es-activation-timer should be configured in all the PEs that are part of the same ESI. It is up to the user to configure either a long timer to minimize the risks of loops/duplication or even es-activation-timer=0 to speed up the convergence for non-DF to DF transitions. When the user configures a specific value, the value configured at ES level supersedes the configured global value.
|
A:PE1# show redundancy bgp-evpn-multi-homing
===============================================================================
Redundancy BGP EVPN Multi-homing Information
===============================================================================
Boot-Timer : 10 secs
Boot-Timer Remaining : 0 secs
ES Activation Timer : 3 secs
===============================================================================
|
•
|
When service-carving mode auto is configured (default mode), the DF election algorithm will run the function [V(evi) mod N(peers) = i(ordinal)] to identify the DF for a specified service and ESI, as described in the following example:
|
|
→
|
As shown in Figure 127, PE1 and PE2 are configured with ESI-1. Given that V(10) mod N(2) = 0, PE1 will be elected DF for VPLS-10 (because its IP address is lower than PE2's and it is the first PE in the candidate list). Note — The algorithm takes the configured evi in the service as opposed to the service-id itself. The evi for a service must match in all the PEs that are part of the ESI. This guarantees that the election algorithm is consistent across all the PEs of the ESI. The evi must be always configured in a service with saps/sdp-bindings that are created in an ES.
|
|
•
|
A manual service-carving option is allowed so that the user can manually configure for which evi identifiers the PE is primary: service-carving mode manual / manual service <evi> to <evi> primary.
|
|
→
|
For example, as shown in Figure 127: if PE1 is configured with service-carving manual evi 1 to 100 primary and PE2 with service-carving manual evi 101 to 200 primary, then PE1 will be the primary PE for service VPLS 10 and PE2 the secondary PE.
|
config>service>system>bgp-evpn>ethernet-segment> mode off
The following show command displays the ethernet-segment configuration and DF status for all the EVIs and ISIDs (if PBB-EVPN is enabled) configured in the
ethernet-segment.
*A:PE1# show service system bgp-evpn ethernet-segment name "ESI-1" all
===============================================================================
Service Ethernet Segment
===============================================================================
Name : ESI-1
Admin State : Up Oper State : Up
ESI : 01:00:00:00:00:71:00:00:00:01
Multi-homing : allActive Oper Multi-homing : allActive
Source BMAC LSB : 71-71
ES BMac Tbl Size : 8 ES BMac Entries : 1
Lag Id : 1
ES Activation Timer : 0 secs
Exp/Imp Route-Target : target:00:00:00:00:71:00
Svc Carving : auto
ES SHG Label : 262142
===============================================================================
===============================================================================
EVI Information
===============================================================================
EVI SvcId Actv Timer Rem DF
-------------------------------------------------------------------------------
1 1 0 no
-------------------------------------------------------------------------------
Number of entries: 1
===============================================================================
-------------------------------------------------------------------------------
DF Candidate list
-------------------------------------------------------------------------------
EVI DF Address
-------------------------------------------------------------------------------
1 192.0.2.69
1 192.0.2.72
-------------------------------------------------------------------------------
Number of entries: 2
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
===============================================================================
ISID Information
===============================================================================
ISID SvcId Actv Timer Rem DF
-------------------------------------------------------------------------------
20001 20001 0 no
-------------------------------------------------------------------------------
Number of entries: 1
===============================================================================
-------------------------------------------------------------------------------
DF Candidate list
-------------------------------------------------------------------------------
ISID DF Address
-------------------------------------------------------------------------------
20001 192.0.2.69
20001 192.0.2.72
-------------------------------------------------------------------------------
Number of entries: 2
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
===============================================================================
BMAC Information
===============================================================================
SvcId BMacAddress
-------------------------------------------------------------------------------
20000 00:00:00:00:71:71
-------------------------------------------------------------------------------
Number of entries: 1
===============================================================================
*A:PE1# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:ca:ca:ba:ce:03 sap:lag-1:1 L/0 06/11/15 00:14:47
1 00:ca:fe:ca:fe:70 eMpls: EvpnS 06/11/15 00:09:06
192.0.2.70:262140
1 00:ca:fe:ca:fe:72 eMpls: EvpnS 06/11/15 00:09:39
192.0.2.72:262141
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
*A:PE2# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:ca:ca:ba:ce:03 sap:lag-1:1 Evpn 06/11/15 00:14:47
1 00:ca:fe:ca:fe:69 eMpls: EvpnS 06/11/15 00:09:40
192.0.2.69:262141
1 00:ca:fe:ca:fe:70 eMpls: EvpnS 06/11/15 00:09:40
192.0.2.70:262140
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
Note — When PE1 (non-DF) and PE2 (DF) exchange BUM packets for
evi 1, all those packets will be sent including the ESI label at the bottom of the stack (in both directions). The ESI label being used by each PE for ESI-1 can be displayed by the following command:
*A:PE1# show service system bgp-evpn ethernet-segment name "ESI-1"
===============================================================================
Service Ethernet Segment
===============================================================================
Name : ESI-1
Admin State : Up Oper State : Up
ESI : 01:00:00:00:00:71:00:00:00:01
Multi-homing : allActive Oper Multi-homing : allActive
Source BMAC LSB : 71-71
ES BMac Tbl Size : 8 ES BMac Entries : 1
Lag Id : 1
ES Activation Timer : 0 secs
Exp/Imp Route-Target : target:00:00:00:00:71:00
Svc Carving : auto
ES SHG Label : 262142
===============================================================================
*A:PE2# show service system bgp-evpn ethernet-segment name "ESI-1"
===============================================================================
Service Ethernet Segment
===============================================================================
Name : ESI-1
Admin State : Up Oper State : Up
ESI : 01:00:00:00:00:71:00:00:00:01
Multi-homing : allActive Oper Multi-homing : allActive
Source BMAC LSB : 71-71
ES BMac Tbl Size : 8 ES BMac Entries : 0
Lag Id : 1
ES Activation Timer : 20 secs
Exp/Imp Route-Target : target:00:00:00:00:71:00
Svc Carving : auto
ES SHG Label : 262142
===============================================================================
Following the example in Figure 127, if the service configuration on PE3 has ECMP > 1, PE3 will add PE1 and PE2 to the list of next-hops for ESI-1. As soon as PE3 receives a MAC for ESI-1, it will start load-balancing between PE1 and PE2 the flows to the remote ESI CE. The following command shows the FDB in PE3.
Note — mac 00:ca:ca:ba:ce:03 is associated with the ethernet-segment eES:01:00:00:00:00:71:00:00:00:01 (esi configured on PE1 and PE2 for ESI-1).
*A:PE3# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:ca:ca:ba:ce:03 eES: Evpn 06/11/15 00:14:47
01:00:00:00:00:71:00:00:00:01
1 00:ca:fe:ca:fe:69 eMpls: EvpnS 06/11/15 00:09:18
192.0.2.69:262141
1 00:ca:fe:ca:fe:70 eMpls: EvpnS 06/11/15 00:09:18
192.0.2.70:262140
1 00:ca:fe:ca:fe:72 eMpls: EvpnS 06/11/15 00:09:39
192.0.2.72:262141
-------------------------------------------------------------------------------
No. of MAC Entries: 4
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
Note — The ethernet-segment eES:01:00:00:00:00:71:00:00:00:01 is resolved to PE1 and PE2 addresses:
*A:PE3# show service id 1 evpn-mpls
===============================================================================
BGP EVPN-MPLS Dest
===============================================================================
TEP Address Egr Label Num. MACs Mcast Last Change
Transport
-------------------------------------------------------------------------------
192.0.2.69 262140 0 Yes 06/10/2015 14:33:30
ldp
192.0.2.69 262141 1 No 06/10/2015 14:33:30
ldp
192.0.2.70 262139 0 Yes 06/10/2015 14:33:30
ldp
192.0.2.70 262140 1 No 06/10/2015 14:33:30
ldp
192.0.2.72 262140 0 Yes 06/10/2015 14:33:30
ldp
192.0.2.72 262141 1 No 06/10/2015 14:33:30
ldp
192.0.2.73 262139 0 Yes 06/10/2015 14:33:30
ldp
192.0.2.254 262142 0 Yes 06/10/2015 14:33:30
bgp
-------------------------------------------------------------------------------
Number of entries : 8
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
BGP EVPN-MPLS Ethernet Segment Dest
===============================================================================
Eth SegId TEP Address Egr Label Last Change
Transport
-------------------------------------------------------------------------------
01:00:00:00:00:71:00:00:00:01 192.0.2.69 262141 06/10/2015 14:33:30
ldp
01:00:00:00:00:71:00:00:00:01 192.0.2.72 262141 06/10/2015 14:33:30
ldp
01:74:13:00:74:13:00:00:74:13 192.0.2.73 262140 06/10/2015 14:33:30
ldp
-------------------------------------------------------------------------------
Number of entries : 3
-------------------------------------------------------------------------------
===============================================================================
*A:PE3>config>service>vpls# info
----------------------------------------------
bgp
exit
bgp-evpn
evi 1
vxlan
shutdown
exit
mpls
ecmp 4
auto-bind-tunnel
resolution any
exit
no shutdown
exit
exit
proxy-arp
shutdown
exit
stp
shutdown
exit
sap 1/1/1:2 create
exit
no shutdown
Figure 128 shows the behavior on the remote PEs (PE3) when there is an
ethernet-segment failure.
1. PE3 can only forward MAC DA = CE2 to both PE1 and PE2 when the MAC advertisement route from PE1 (or PE2) and the set of Ethernet AD per-ES routes and Ethernet AD per-EVI routes from PE1 and PE2 are active at PE3.
2. If there was a failure between CE2 and PE2, PE2 would withdraw its set of Ethernet AD and ES routes, then PE3 would forward traffic destined to CE2 to PE1 only. PE3 does not need to wait for the withdrawal of the individual MAC.
3. The same behavior would be followed if the failure had been at PE1.
4. If after (2), PE2 withdraws its MAC advertisement route, then PE3 treats traffic to MAC DA = CE2 as unknown unicast, unless the MAC had been previously advertised by PE1.
1. Reception of ES route update (local ES shutdown/no shutdown or remote route)
2. New AD-ES route update/withdraw
4. Local ES port/SAP/service shutdown
5. Service carving range change (affecting the evi)
6. Multi-homing mode change (single/all active to all/single-active)
If an individual VPLS service is shutdown in PE1 (the example is also valid for PE2), the corresponding LAG SAP will go
oper-down. This event will trigger the withdrawal of the AD per-EVI route for that particular SAP. PE3 will remove PE1 of its list of aliased next-hops and PE2 will take over as DF (if it was not the DF already). However, this will not prevent the network from black-holing the traffic that CE2 'hashes' to the link to PE1. Traffic sent from CE2 to PE2 or traffic from the rest of the CEs to CE2 will be unaffected, so this situation is not easily detected on the CE.
Note — When
bgp-evpn mpls shutdown is executed, the sap associated with the ES will be brought operationally down (
StandbyforMHprotocol) and so will the entire service if there are no other saps or sdp-bindings in the service. However, if there are other saps/sdp-bindings, the service will remain operationally up.
This scenario is illustrated by the diagram on the left in Figure 130. In an all-active multi-homing scenario, if a specified MAC address is not yet learned in a remote PE, but is known in the two PEs of the ES, for example, PE1 and PE2, the latter PEs might send duplicated packets to the CE.
This issue is solved by the use of ingress-replication-bum-label in PE1 and PE2. If configured, PE1/PE2 will know that the received packet is an unknown unicast packet, therefore, the NDF (PE1) will not send the packets to the CE and there will not be duplication.
Note — Even without the
ingress-replication-bum-label, this is only a transient situation that would be solved as soon as MAC1 is learned in PE3.
This case is illustrated by the diagram on the right in Figure 130. In an all-active multi-homing scenario, MAC1 is known in PE3 and aliasing is applied to MAC1. However, MAC1 is not known yet in PE1, the NDF for the ES. If PE3 hashing picks up PE1 as the destination of the aliased MAC1, the packets will be black-holed.
*A:PE1>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 1.1.1.1:0
ethernet-segment "ESI2" create
esi 01:12:12:12:12:12:12:12:12:12
multi-homing single-active
service-carving
sdp 1
no shutdown
*A:PE1>config>redundancy>evpn-multi-homing# info
----------------------------------------------
boot-timer 120
es-activation-timer 10
*A:PE1>config>service>vpls# info
----------------------------------------------
description "evpn-mpls-service with single-active multihoming"
bgp
bgp-evpn
evi 10
mpls
no shutdown
auto-bind-tunnel resolution any
spoke-sdp 1:1 create
exit
*A:PE1>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 1.1.1.1:0
ethernet-segment "ESI2" create
esi 01:12:12:12:12:12:12:12:12:12
multi-homing single-active
service-carving
sdp 2
no shutdown
*A:PE1>config>redundancy>evpn-multi-homing# info
----------------------------------------------
boot-timer 120
es-activation-timer 10
*A:PE1>config>service>vpls# info
----------------------------------------------
description "evpn-mpls-service with single-active multihoming"
bgp
bgp-evpn
evi 10
mpls
no shutdown
auto-bind-tunnel resolution any
spoke-sdp 2:1 create
exit
|
•
|
The ethernet-segment will be configured for single-active: service>system>bgp-evpn>ethernet-segment>multi-homing single-active.
|
|
→
|
port would be used for single-active sap redundancy without the need for lag.
|
|
→
|
sdp would be used for single-active spoke-sdp redundancy.
|
|
→
|
lag would be used for single-active LAG redundancy Note — In this case, key, system-id, and system-priority must be different on the PEs that are part of the ethernet-segment).
|
|
−
|
LAG with or without LACP
In this case, the multi-homed ports on the CE will be part of the different LAGs (a LAG per multi-homed PE will be used in the CE). The non-DF PE for each service can signal that the sap is oper-down if eth-cfm fault-propagation-enable {use-if-tlv|suspend-ccm} is configured.
|
|
−
|
Regular Ethernet 802.1q/ad ports
In this case, the multi-homed ports on the CE/network will not be part of any LAG. Eth-cfm can also be used for non-DF indication to the multi-homed device/network.
|
|
−
|
Active-standby PWs
In this case, the multi-homed CE/network is connected to the PEs through an MPLS network and an active/standby spoke-sdp per service. The non-DF PE for each service will make use of the LDP PW status bits to signal that the spoke-sdp is oper-down on the PE side.
|
The following show commands display the status of the single-active ESI-7413 in the non-DF.
Note — The associated spoke-SDP is operationally down and it signals PW Status standby to the multi-homed CE:
*A:PE1# show service system bgp-evpn ethernet-segment name "ESI-7413"
===============================================================================
Service Ethernet Segment
===============================================================================
Name : ESI-7413
Admin State : Up Oper State : Up
ESI : 01:74:13:00:74:13:00:00:74:13
Multi-homing : singleActive Oper Multi-homing : singleActive
Source BMAC LSB : <none>
Sdp Id : 4
ES Activation Timer : 0 secs
Exp/Imp Route-Target : target:74:13:00:74:13:00
Svc Carving : auto
ES SHG Label : 262141
===============================================================================
*A:PE1# show service system bgp-evpn ethernet-segment name "ESI-7413" evi 1
===============================================================================
EVI DF and Candidate List
===============================================================================
EVI SvcId Actv Timer Rem DF DF Last Change
-------------------------------------------------------------------------------
1 1 0 no 06/11/2015 20:05:32
===============================================================================
===============================================================================
DF Candidates Time Added
-------------------------------------------------------------------------------
192.0.2.70 06/11/2015 20:05:20
192.0.2.73 06/11/2015 20:05:32
-------------------------------------------------------------------------------
Number of entries: 2
===============================================================================
*A:PE1# show service id 1 base
===============================================================================
Service Basic Information
===============================================================================
Service Id : 1 Vpn Id : 0
Service Type : VPLS
Name : (Not Specified)
Description : (Not Specified)
<snip>
-------------------------------------------------------------------------------
Service Access & Destination Points
-------------------------------------------------------------------------------
Identifier Type AdmMTU OprMTU Adm Opr
-------------------------------------------------------------------------------
sap:1/1/1:1 q-tag 9000 9000 Up Up
sdp:4:13 S(192.0.2.74) Spok 0 8978 Up Down
===============================================================================
* indicates that the corresponding row element may have been truncated.
*A:PE1# show service id 1 all | match Pw
Local Pw Bits : pwFwdingStandby
Peer Pw Bits : None
*A:PE1# show service id 1 all | match Flag
Flags : StandbyForMHProtocol
Flags : None
A remote PE (PE3 in Figure 131) will import the AD routes per ESI, where the single-active flag is set. PE3 will interpret that the ethernet-segment is single-active if at least one PE sends an AD route per-ESI with the single-active flag set. MACs for a specified service and ESI will be learned from a single PE, that is, the DF for that <ESI, EVI>.
*A:PE3# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:ca:ca:ba:ca:02 sap:1/1/1:2 L/0 06/12/15 00:33:39
1 00:ca:ca:ba:ca:06 eES: Evpn 06/12/15 00:33:39
01:74:13:00:74:13:00:00:74:13
1 00:ca:fe:ca:fe:69 eMpls: EvpnS 06/11/15 21:53:47
192.0.2.69:262118
1 00:ca:fe:ca:fe:70 eMpls: EvpnS 06/11/15 19:59:57
192.0.2.70:262140
1 00:ca:fe:ca:fe:72 eMpls: EvpnS 06/11/15 19:59:57
192.0.2.72:262141
-------------------------------------------------------------------------------
No. of MAC Entries: 5
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
*A:PE3# show service id 1 evpn-mpls
===============================================================================
BGP EVPN-MPLS Dest
===============================================================================
TEP Address Egr Label Num. MACs Mcast Last Change
Transport
-------------------------------------------------------------------------------
192.0.2.69 262118 1 Yes 06/11/2015 19:59:03
ldp
192.0.2.70 262139 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.70 262140 1 No 06/11/2015 19:59:03
ldp
192.0.2.72 262140 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.72 262141 1 No 06/11/2015 19:59:03
ldp
192.0.2.73 262139 0 Yes 06/11/2015 19:59:03
ldp
192.0.2.254 262142 0 Yes 06/11/2015 19:59:03
bgp
-------------------------------------------------------------------------------
Number of entries : 7
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
BGP EVPN-MPLS Ethernet Segment Dest
===============================================================================
Eth SegId TEP Address Egr Label Last Change
Transport
-------------------------------------------------------------------------------
01:74:13:00:74:13:00:00:74:13 192.0.2.73 262140 06/11/2015 19:59:03
ldp
-------------------------------------------------------------------------------
Number of entries : 1
-------------------------------------------------------------------------------
===============================================================================
Figure 132 shows the remote PE (PE3) behavior when there is an ethernet-segment failure.
|
•
|
If an individual VPLS service is administrative shutdown in PE1, the corresponding SAP/SDP-binding will go oper-down. This event will trigger the withdrawal of the AD per-EVI route for that particular SAP/SDP-binding. PE3 will apply its backup mechanisms and PE2 will take over as DF (if it was not the DF already). To signal the fault to CE2:
|
|
•
|
Route Distinguisher: Taken from the RD of the B-VPLS service within the BGP context. Note —The RD can be configured or derived from the bgp-evpn evi value.
|
|
→
|
MPLS label: Carries the MPLS label allocated for the service in the high-order 20 bits of the label field. Note — This label will be the same label used in the BMAC routes for the same B-VPLS service unless bgp-evpn mpls ingress-replication-bum-label is configured in the B-VPLS service.
|
|
•
|
Route Distinguisher—Taken from the RD of the VPLS service within the BGP context. Note — The RD can be configured or derived from the bgp-evpn evi value.
|
Note — The EVPN route type 1
—Ethernet Auto Discovery route is not used in PBB-EVPN.
Each PE in the B-VPLS domain will advertise its source-bmac as either configured in
(b)vpls>pbb>source-bmac or auto-derived from the chassis mac. The remote PEs will install the advertised BMACs in the B-VPLS FDB. If a specified PE is configured with an
ethernet-segment associated with an I-VPLS or PBB Epipe, it may also advertise an
es-bmac for the ethernet-segment.
In the example shown in Figure 134, when a frame with MAC DA = AA gets to PE1, a mac lookup is performed on the I-VPLS FDB and BMAC-34 is found. A BMAC lookup on the B-VPLS FDB will yield the next-hop (or next-hops if the destination is in an all-active ethernet-segment) to which the frame is sent. As in PBB-VPLS, the frame will be encapsulated with the corresponding PBB header. A label specified by EVPN for the B-VPLS and the MPLS transport label are also added.
*A:PE-1>config#
service vpls 1 b-vpls create
description "pbb-evpn-service"
service-mtu 2000
pbb
source-bmac 00:00:00:00:00:03
bgp
bgp-evpn
evi 1
vxlan
shutdown
mpls
no shutdown
auto-bind-tunnel resolution any
sap 1/1/1:1 create
exit
spoke-sdp 1:1 create
*A:PE-1>config#
service vpls 101 i-vpls create
pbb
backbone-vpls 1
sap 1/2/1:101 create
spoke-sdp 1:102 create
*A:PE-1>config#
service epipe 102 create
pbb
tunnel 1 backbone-dest-mac 00:00:00:00:00:01 isid 102
sap 1/2/1:102 create
When bgp-evpn>mpls no shutdown is added to a specified B-VPLS instance, the following considerations apply:
|
→
|
bgp-evpn>mac-advertisement - this command will only have affect on the 'learned' BMACs on saps or sdp-bindings and not on the system BMAC or sap/es-bmacs being advertised.
|
The example in Figure 135 shows how the MFIBs are populated in PBB-EVPN.
isid-policy
entry 10 create
no advertise-local
range 1 to 2000
use-def-mcast
|
•
|
no advertise-local instructs the system to not advertise the local active ISIDs contained in the 1 to 2001 range.
|
|
•
|
use-def-mcast instructs the system to use the default flooding list as opposed to the MFIB.
|
|
•
|
When an isid-policy is configured and a range of ISIDs use the default multicast list, the remote PBB-EVPN PEs will be added to the default multicast list as long as they advertise an IMET route with an ISID included in the policy's ISID range. PEs advertising IMET routes with Ethernet-tag = 0 are also added to the default multicast list (7x50 SROS behavior).
|
sap 1/1/1:1 create
exit
spoke-sdp 1:1 create
static-mac
mac 00:fe:ca:fe:ca:fe create sap 1/1/1:1 monitor fwd-status
static-isid
range 1 isid 3000 to 5000 create
Note — The configuration of PBB-Epipes does not trigger any IMET advertisement.
All the concepts described in section PBB-EVPN and PBB-VPLS Integration are also supported in B-VPLS services so that B-VPLS SAP/SDP-bindings can be integrated with PBB-EVPN destination bindings. The features described in that section also facilitate a smooth migration from B-VPLS SDP-bindings to PBB-EVPN destination bindings.
PBB-EVPN multi-homing reuses the ethernet-segment concept described in section '
EVPN Multi-Homing in VPLS Services '. However, unlike EVPN-MPLS, PBB-EVPN does not use AD routes; it uses BMACs for split-horizon checks and aliasing.
|
•
|
A shared-bmac (in IETF) is a source-bmac as configured in service>(b)vpls>pbb>source-bmac
|
|
•
|
A dedicated-bmac per ES (in IETF) is an es-bmac as configured in service>pbb>use-es-bmac
|
|
→
|
The use of source-bmacs minimizes the number of BMACs being advertised but has a larger impact on CMAC flush upon ES failures.
|
|
→
|
The use of es-bmacs optimizes the CMAC flush upon ES failures at the expense of advertising more BMACs.
|
Figure 136 shows the use of all-active multi-homing in the 7x50 SROS PBB-EVPN implementation.
In Figure 136 and the following configuration, the
es-bmac used by PE3 and PE4 will be BMAC-34, i.e. 00:00:00:00:00:34. The
es-bmac for a specified
ethernet-segment is configured by the
source-bmac-lsb along with the
(b-)vpls>pbb>use-es-bmac command.
*A:PE3>config>lag(1)# info
----------------------------------------------
mode access
encap-type dot1q
port 1/1/1
lacp active administrative-key 32768
no shutdown
*A:PE3>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 3.3.3.3:0
ethernet-segment ESI-1 create
esi 00:34:34:34:34:34:34:34:34:34
multi-homing all-active
service-carving auto
lag 1
source-bmac-lsb 00:34 es-bmac-table-size 8
no shutdown
*A:PE3>config>service>vpls 1(b-vpls)# info
----------------------------------------------
bgp
bgp-evpn
evi 1
mpls
no shutdown
ecmp 2
auto-bind-tunnel resolution any
pbb
source-bmac 00:00:00:00:00:03
use-es-bmac
*A:PE3>config>service>vpls (i-vpls)# info
----------------------------------------------
pbb
backbone-vpls 1
sap lag-1:101 create
*A:PE1>config>service>epipe (pbb)# info
----------------------------------------------
pbb
tunnel 1 backbone-dest-mac 00:00:00:00:00:01 isid 102
sap lag-1:102 create
*A:PE4>config>lag(1)# info
----------------------------------------------
mode access
encap-type dot1q
port 1/1/1
lacp active administrative-key 32768
no shutdown
*A:PE4>config>service>system>bgp-evpn# info
----------------------------------------------
route-distinguisher 4.4.4.4:0
ethernet-segment ESI-1 create
esi 00:34:34:34:34:34:34:34:34:34
multi-homing all-active
service-carving auto
lag 1
source-bmac-lsb 00:34 es-bmac-table-size 8
no shutdown
*A:PE4>config>service>vpls 1(b-vpls)# info
----------------------------------------------
bgp
bgp-evpn
evi 1
mpls
no shutdown
ecmp 2
auto-bind-tunnel resolution any
pbb
source-bmac 00:00:00:00:00:04
use-es-bmac
*A:PE4>config>service>vpls (i-vpls)# info
----------------------------------------------
pbb
backbone-vpls 1
sap lag-1:101 create
*A:PE4>config>service>epipe (pbb)# info
----------------------------------------------
pbb
tunnel 1 backbone-dest-mac 00:00:00:00:00:01 isid 102
sap lag-1:102 create
Note — The ethernet-segment ESI-1 can also be used for regular VPLS services.
|
•
|
ESI association: Only LAG is supported for all-active multi-homing. The following commands are used for the LAG to ESI association:
|
|
−
|
The source-bmac-lsb attribute must be set to a specific 2-byte value. The value must match on all the PEs part of the same ESI, for example, PE3 and PE4 for ESI-1. This means that the configured pbb>source-bmac on the two PEs for B-VPLS 1 must have the same 4 most significant bytes.
|
|
−
|
The es-bmac-table-size parameter modifies the default value (8) for the maximum number of virtual BMACs that can be associated with the ethernet-segment, i.e. es-bmacs. When the source-bmac-lsb is configured, the associated es-bmac-table-size is reserved out of the total FDB space.
|
|
−
|
When multi-homing all-active is configured within the ethernet-segment, only a LAG can be associated with it. The association of a port or an sdp will be restricted by the CLI.
|
|
•
|
If service-carving is configured in the ESI, the DF election algorithm will be a modulo function of the ISID and the number of PEs part of the ESI, as opposed to a modulo function of evi and number of PEs (used for EVPN-MPLS).
|
|
•
|
A service-carving mode manual option is added so that the user can control what PE is DF for a specified ISID. The PE will be DF for the configured ISIDs and non-DF for the non-configured ISIDs.
|
|
•
|
DF election: An all-active Designated Forwarder (DF) election is also carried out for PBB-EVPN. In this case, the DF election defines which of the PEs of the ESI for a specified I-VPLS is the one able to send the downstream BUM traffic to the CE. Only one DF per ESI is allowed in the I-VPLS service, and the non-DF will only block BUM traffic and in the downstream direction.
|
|
•
|
Split-horizon function: In PBB-EVPN, the split-horizon function to avoid echoed packets on the CE is based on an ingress lookup of the ES BMAC (as opposed to the ESI label in EVPN-MPLS). In Figure 136 PE3 sends packets using BMAC SA = BMAC-34. PE4 does not send those packets back to the CE because BMAC-34 is identified as the es-bmac for ESI-1.
|
|
•
|
Aliasing: In PBB-EVPN, aliasing is based on the ES BMAC sent by all the PEs part of the same ESI. See the following section for more information. In Figure 136 PE1 performs load balancing between PE3 and PE4 when sending unicast flows to BMAC-34 (es-bmac for ESI-1).
|
In the configuration above, a PBB-Epipe is configured in PE3 and PE4, both pointing at the same remote pbb tunnel backbone-dest-mac. On the remote PE, i.e. PE1, the configuration of the PBB-Epipe will point at the
es-bmac:
*A:PE1>config>service>epipe (pbb)# info
----------------------------------------------
pbb
tunnel 1 backbone-dest-mac 00:00:00:00:00:34 isid 102
sap 1/1/1:102 create
When PBB-Epipes are used in combination with all-active multi-homing, Alcatel-Lucent recommends using bgp-evpn mpls ingress-replication-bum-label in the PEs where the
ethernet-segment is created, that is in PE3 and PE4. This guarantees that in case of flooding in the B-VPLS service for the PBB Epipe, only the DF will forward the traffic to the CE.
Note — PBB-Epipe traffic always uses BMAC DA = unicast; therefore, the DF cannot check whether the inner frame is unknown unicast or not based on the group BMAC. Therefore, the use of an EVPN BUM label is highly recommended.
All-active multi-homed es-bmacs are treated by the remote PEs as
eES:MAX-ESI BMACs. The following example shows the FDB in B-VPLS 1 in PE1 as shown in
Figure 136:
*A:PE1# show service id 1 fdb detail
===============================================================================
Forwarding Database, Service 1
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:00:00:00:00:03 eMpls: EvpnS 06/12/15 15:35:39
192.0.2.3:262138
1 00:00:00:00:00:04 eMpls: EvpnS 06/12/15 15:42:52
192.0.2.4:262130
1 00:00:00:00:00:34 eES: EvpnS 06/12/15 15:35:57
MAX-ESI
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
The show service id evpn-mpls on PE1 shows that the remote
es-bmac, i.e. 00:00:00:00:00:34, has two associated next-hops, i.e. PE3 and PE4:
*A:PE1# show service id 1 evpn-mpls
===============================================================================
BGP EVPN-MPLS Dest
===============================================================================
TEP Address Egr Label Num. MACs Mcast Last Change
Transport
-------------------------------------------------------------------------------
192.0.2.3 262138 1 Yes 06/12/2015 15:34:48
ldp
192.0.2.4 262130 1 Yes 06/12/2015 15:34:48
ldp
-------------------------------------------------------------------------------
Number of entries : 2
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
BGP EVPN-MPLS Ethernet Segment Dest
===============================================================================
Eth SegId TEP Address Egr Label Last Change
Transport
-------------------------------------------------------------------------------
No Matching Entries
===============================================================================
===============================================================================
BGP EVPN-MPLS ES BMAC Dest
===============================================================================
VBMacAddr TEP Address Egr Label Last Change
Transport
-------------------------------------------------------------------------------
00:00:00:00:00:34 192.0.2.3 262138 06/12/2015 15:34:48
ldp
00:00:00:00:00:34 192.0.2.4 262130 06/12/2015 15:34:48
ldp
-------------------------------------------------------------------------------
Number of entries : 2
-------------------------------------------------------------------------------
===============================================================================
ES failures are resolved by the PEs withdrawing the es-bmac. The remote PEs will withdraw the route and update their list of next-hops for a specified
es-bmac.
When the route corresponding to the last next-hop for a specified es-bmac is withdrawn, the es-bmac will be flushed from the B-VPLS FDB and all the CMACs associated with it will be flushed too.
The following events will trigger a withdrawal of the es-bmac and the corresponding next-hop update in the remote PEs:
|
•
|
Change of es-bmac (or removal of pbb use-es-bmac).
|
Note — Individual saps going oper-down in an ES will not generate any BGP withdrawal or indication so that the remote nodes can flush their CMACs. This is solved in EVPN-MPLS by the use of AD routes per EVI; however, there is nothing similar in PBB-EVPN for indicating a partial failure in an ESI.
|
•
|
The ethernet-segment will be configured for single-active: service>system>bgp-evpn>ethernet-segment>multi-homing single-active.
|
|
•
|
While all-active multi-homing only uses es-bmac assignment to the ES, single-active multi-homing can use source-bmac or es-bmac assignment. The system allows the following user choices per B-VPLS and ES:
|
|
→
|
A dedicated es-bmac per ES can be used. In that case, the pbb>use-es-bmac command will be configured in the B-VPLS and the same procedures explained in PBB-EVPN all-active multi-homing service model will follow with one difference. While in all-active multi-homing all the PEs part of the ESI will source the PBB packets with the same source es-bmac, single-active multi-homing requires the use of a different es-bmac per PE.
|
|
→
|
A non-dedicated source-bmac can be used. In this case, the user will not configure pbb>use-es-bmac and the regular source-bmac will be used for the traffic. A different source-bmac has to be advertised per PE.
|
|
→
|
The use of source-bmacs or es-bmacs for single-active multi-homed ESIs has a different impact on CMAC flushing, as shown in Figure 137.
|
|
−
|
If es-bmacs are used as shown in the representation on the right in Figure 137, a less-impacting CMAC flush is achieved, therefore, minimizing the flooding after ESI failures. In case of ESI failure, PE1 will withdraw the es-bmac 00:12 and the remote PE3 will only flush the CMACs associated with that es-bmac (only the CMACs behind the CE are flushed).
|
|
−
|
If source-bmacs are used, as shown on the left-hand side of Figure Figure 137, in case of ES failure, a BGP update with higher sequence number will be issued by PE1 and the remote PE3 will flush all the CMACs associated with the source-bmac. Therefore, all the CMACs behind the PE's B-VPLS will be flushed, as opposed to only the CMACs behind the ESI's CE.
|
|
•
|
If the BMAC address assignment is based on the use of es-bmacs, DF and non-DFs will send the es-bmac/ESI=0 for a specified ESI. Each PE will have a different es-bmac for the same ESI (as opposed to the same es-bmac on all the PEs for all-active). In case of an ESI failure on a PE:
|
|
→
|
The far-end PEs will interpret a source-bmac advertisement with a different sequence number as a flush-all-from-me message from the PE detecting the failure. They will flush all the CMACs associated with that BMAC in all the ISID services.
|
|
•
|
Change of pbb>source-bmac. This will trigger the withdrawal and re-advertisement of the source-bmac, causing the corresponding CMAC flush in the remote PEs.
|
|
•
|
Change of es-bmac (removal of pbb use-es-bmac). This will trigger the withdrawal of the es-bmac and re-advertisement of the new es-bmac.
|
Figure 138 shows the EVPN MH support in a three-node scenario.
Figure 139 shows the EVPN MH support in a two-node scenario.
Figure 140 shows an example of how proxy-ARP is used in an EVPN network. Proxy-ND would work in a similar way. Note that the MAC address notation in the diagram is shortened for readability.
*A:PE1>config>service>vpls# info
----------------------------------------------
vxlan vni 600 create
exit
bgp
route-distinguisher 192.0.2.71:600
route-target export target:64500:600 import target:64500:600
exit
bgp-evpn
vxlan
no shutdown
exit
exit
proxy-arp
age-time 600
send-refresh 200
dup-detect window 3 num-moves 3 hold-down max anti-spoof-mac 00:ca:ca:ca:ca:ca
dynamic-arp-populate
no shutdown
exit
sap 1/1/1:600 create
exit
no shutdown
----------------------------------------------
Figure 140 shows the following steps, assuming proxy-ARP is no shutdown on PE1 and PE2, and the tables are empty:
4. Assuming PE1 was configured with unknown-arp-request-flood-evpn, the ARP-request is flooded to PE2 and delivered to ISP-B. ISP-B replies with its MAC in the ARP-reply. The ARP-reply is finally delivered to ISP-A.
Note — A static IP->MACentry requires the addition of the MAC address to the FDB as either learned or CStatic (conditional static mac) in order to become active (
Status —> active).
|
→
|
If the anti-spoof-mac is configured, the proxy-ARP/ND offending entry's MAC is replaced by this <mac-address> and advertised in an unsolicited GARP/NA for local SAP/SDP-bindings and in EVPN to remote PEs.
|
|
→
|
This mechanism assumes that the same anti-spoof-mac is configured in all the PEs for the same service and that traffic with destination anti-spoof-mac received on SAPs/SDP-bindings will be dropped. An ingress mac-filter has to be configured in order to drop traffic to the anti-spoof-mac.
|
Table 19 shows the combinations that will produce a
Status = Active proxy-arp entry in the table. The system will only reply to proxy-ARP requests for active entries. Any other combination will result in a
Status = inActv entry. If the service is not active, the proxy-arp entries will not be active either, irrespective of the FDB entries
NOTE—A static entry is active in the FDB even when the service is down.
These messages are activated by the send-refresh command and their objective is to keep the existing FDB and Proxy-ARP/ND entries alive, in order to minimize EVPN withdrawals and re-advertisements.
—A node capable of routing IPv6 packets must reply to NS messages with NA messages where the R flag is set (R=1).
—Hosts must reply with NA messages where R=0.
a. Either provide the appropriate R flag information in proxy-ND NA replies
b. Flood the received NA messages if it cannot provide the appropriate R flag when replying
|
•
|
In addition, the evpn-nd-advertise {host | router} command will indicate what static and dynamic IP->MAC entries the system will advertise in EVPN. If evpn-nd-advertise router is configured, the system should flood the received unsolicited NA messages for hosts. This is controlled by the [no] host-unsolicited-na-flood-evpn command. The opposite is also recommended so that the evpn-nd-advertise host is configured with the router-unsolicited-na-flood-evpn.
|
Note — When EVPN multi-homing is used in EVPN-MPLS, the ESI is compared to determine whether a MAC received from two different PEs has to be processed within the context of MAC mobility or multi-homing. Two MAC routes that are associated with the same remote or local ESI but different PEs are considered reachable through all those PEs. Mobility procedures are not triggered as long as the MAC route still belongs to the same ESI.
To remedy such situation, a 7x50 that detects a MAC mobility event by way of local learning starts a window <in-minutes> timer (default value of window = 3) and if it detects
num-moves <num> before the timer expires (default value of num-moves = 5), it concludes that a duplicate MAC situation has occurred. The 7x50 then alerts the operator with a trap message. The offending MAC address can be shown using the show service id x bgp-evpn command:
10 2014/01/14 01:00:22.91 UTC MINOR: SVCMGR #2331 Base
"VPLS Service 1 has MAC(s) detected as duplicates by EVPN mac-duplication detection."
# show service id 1 bgp-evpn
===============================================================================
BGP EVPN Table
===============================================================================
MAC Advertisement : Enabled Unknown MAC Route : Disabled
VXLAN Admin Status : Enabled Creation Origin : manual
MAC Dup Detn Moves : 5 MAC Dup Detn Window: 3
MAC Dup Detn Retry : 9 Number of Dup MACs : 1
-------------------------------------------------------------------------------
Detected Duplicate MAC Addresses Time Detected
-------------------------------------------------------------------------------
00:00:00:00:00:12 01/14/2014 01:00:23
-------------------------------------------------------------------------------
===============================================================================
a. The MAC is flushed due to a local event (sap/sdp-binding associated with the MAC fails) or the reception of a remote update with better SEQ number (due to a mac flush at the remote 7x50).
b. The retry <in-minutes> timer expires, which will flush the MAC and restart the process.
Note—The other 7x50s in the VPLS instance will forward the traffic for the duplicate MAC address to the 7x50 advertising the best route for the MAC.
The values of num-moves and window are configurable to allow for the required flexibility in different environments. In scenarios where BGP rapid-update evpn is configured, the operator might want to configure a shorter window timer than in scenarios where BGP updates are sent every (default) min-route-advertisement interval.
*A:DGW1>config>service>vpls>bgp-evpn# info
----------------------------------------------
mac-advertisement
unknown-mac-route
mac-duplication
detect num-moves num window in_mins
[no] retry in_mins
vxlan
no shutdown
exit
*A:PE63>config>service>vpls# info
----------------------------------------------
description "vxlan-service"
...
sap 1/1/1:1000 create
exit
static-mac
mac 00:ca:ca:ca:ca:00 create sap 1/1/1:1000 monitor fwd-status
exit
no shutdown
*A:PE64# show router bgp routes evpn mac hunt mac-address 00:ca:ca:ca:ca:00
...
===============================================================================
BGP EVPN Mac Routes
===============================================================================
Network : 0.0.0.0/0
Nexthop : 192.0.2.63
From : 192.0.2.63
Res. Nexthop : 192.168.19.1
Local Pref. : 100 Interface Name : NotAvailable
Aggregator AS : None Aggregator : None
Atomic Aggr. : Not Atomic MED : 0
AIGP Metric : None
Connector : None
Community : target:65000:1000 mac-mobility:Seq: 0/Static
Cluster : No Cluster Members
Originator Id : None Peer Router Id : 192.0.2.63
Flags : Used Valid Best IGP
Route Source : Internal
AS-Path : No As-Path
EVPN type : MAC
ESI : 0:0:0:0:0:0:0:0:0:0 Tag : 1063
IP Address : :: RD : 65063:1000
Mac Address : 00:ca:ca:ca:ca:00 Mac Mobility : Seq:0
Neighbor-AS : N/A
Source Class : 0 Dest Class : 0
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
Figure 141 shows the 7x50 Service Chaining integration with the Nuage VSP on VPLS services. In this example, the DC GW, PE1, is connected to an L2-DOMAIN that exists in the DC and must redirect the traffic to the Service Function SF-1. The regular Layer-2 forwarding procedures would have taken the packets to PE2, as opposed to SF-1.
In the example shown in Figure 141, the PBF filter will redirect the matching packets to ESI 0x01 in VPLS-1
Note — Figure 141 represents ESI as ‘0x01’ for simplicity; in reality, the ESI is a 10-byte number.
Note— When packets get to PE3, VNI-1 (the VNI advertised in the AD route) will indicate that a 'cut-through' switching operation is needed to deliver the packets straight to the SF-1 vport, without the need for a regular MAC lookup.
A:PE1>config>filter>mac-filter# info
----------------------------------------------
default-action forward
entry 10 create
action
forward esi ff:00:00:00:00:00:00:00:00:01 service-id 301
exit
exit
A:PE1# show filter mac 1
===============================================================================
Mac Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Forward
Entries : 1 Type : normal
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : Mac
-------------------------------------------------------------------------------
Entry : 10 FrameType : Ethernet
Description : (Not Specified)
Log Id : n/a
Src Mac : Undefined
Dest Mac : Undefined
Dot1p : Undefined Ethertype : Undefined
DSAP : Undefined SSAP : Undefined
Snap-pid : Undefined ESnap-oui-zero : Undefined
Match action: Forward (ESI) Active
ESI : ff:00:00:00:00:00:00:00:00:01
Svc Id : 301
PBR Down Act: Forward (entry-default)
Ing. Matches: 3 pkts
Egr. Matches: 0 pkts
===============================================================================
A:PE1# show service id 301 es-pbr
===============================================================================
L2 ES PBR
===============================================================================
ESI Users Status
VTEP:VNI
-------------------------------------------------------------------------------
ff:00:00:00:00:00:00:00:00:01 1 Active
192.0.2.72:7272
-------------------------------------------------------------------------------
Number of entries : 1
-------------------------------------------------------------------------------
===============================================================================
A:PE1# show router bgp routes evpn auto-disc esi ff:00:00:00:00:00:00:00:00:01
===============================================================================
BGP Router ID:192.0.2.71 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP EVPN Auto-Disc Routes
===============================================================================
Flag Route Dist. ESI NextHop
Tag Label
-------------------------------------------------------------------------------
u*>i 192.0.2.72:100 ff:00:00:00:00:00:00:00:00:01 192.0.2.72
0 VNI 7272
-------------------------------------------------------------------------------
Routes : 1
=============================================================
A:PE1# show service id 301 vxlan
===============================================================================
VPLS VXLAN, Ingress VXLAN Network Id: 301
===============================================================================
Egress VTEP, VNI
===============================================================================
VTEP Address Egress VNI Num. MACs Mcast Oper State L2 PBR
-------------------------------------------------------------------------------
192.0.2.69 301 1 Yes Up No
192.0.2.72 301 1 Yes Up No
192.0.2.72 7272 0 No Up Yes
-------------------------------------------------------------------------------
Number of Egress VTEP, VNI : 3
-------------------------------------------------------------------------------
===============================================================================
Figure 142 shows the 7x50 Service Chaining integration with the Nuage VSP on L2-DOMAIN-IRB domains. In this example, the DC GW, PE1, is connected to an L2-DOMAIN-IRB that exists in the DC and must redirect the traffic to the Service Function SF-1 with IP address 10.10.10.1. The regular layer-3 forwarding procedures would have taken the packets to PE2, as opposed to SF-1.
In this case, an operator must configure a PBR match/action filter policy entry in an IPv4 ingress access or network filter deployed on IES/VPRN interface using CLI/SNMP/NETCONF management interfaces. The PBR target identifies first service function in the chain (ESI 0x01 in Figure 142, identifying where the Service Function is connected and the IPv4 address of the SF) and EVPN VXLAN egress interface on the PE (VPRN routing instance and R-VPLS interface name). The BGP control plane together with ESI PBR configuration are used to forward the matching packets to the next-hop in the EVPN-VXLAN data center chain (through resolution to a VNI and VTEP). If the BGP control plane information is not available, the packets matching the ESI PBR entry will be, by default, forwarded using regular routing. Optionally, an operator can select to drop the packets when the ESI PBR target is not reachable.
*A:PE1>config>filter>ip-filter# info
----------------------------------------------
default-action forward
entry 10 create
match
dst-ip 10.10.10.253/32
exit
action
forward esi ff:00:00:00:00:21:5f:00:df:e5 sf-ip 10.10.10.1 vas-interface "evi-301" router 300
exit
pbr-down-action-override filter-default-action
exit
----------------------------------------------
Note — In this use case, the following are required in addition to the ESI: the
sf-ip (10.10.10.1 in the example above),
router instance (300), and
vas-interface.
The sf-ip is used by the system to know which inner MAC DA it has to use when sending the redirected packets to the SF. The SF-IP will be resolved to the SF MAC following regular ARP procedures in EVPN-VXLAN.
The router instance may be the same as the one where the ingress filter is configured or may be different: for instance, the ingress PBR filter can be applied on an IES interface pointing at a VPRN router instances that is connected to the DC fabric.
The vas-interface refers to the R-VPLS interface name through which the SF can be found. The VPRN instance may have more than one R-VPLS interface, therefore, it is required to specify which R-VPLS interface to use.
*A:PE1# show filter ip 1
===============================================================================
IP Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Forward
System filter: Unchained
Radius Ins Pt: n/a
CrCtl. Ins Pt: n/a
RadSh. Ins Pt: n/a
PccRl. Ins Pt: n/a
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10
Description : (Not Specified)
Log Id : n/a
Src. IP : 0.0.0.0/0
Src. Port : n/a
Dest. IP : 172.16.0.253/32
Dest. Port : n/a
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Src Route Opt : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Egress PBR : Undefined
Match action : Forward (ESI) Active
ESI : ff:00:00:00:00:21:5f:00:df:e5
SF IP : 10.10.10.1
VAS If name: evi-301
Router : 300
PBR Down Act : Forward (filter-default-action) Ing. Matches : 3 pkts (318 bytes)
Egr. Matches : 0 pkts
===============================================================================
*A:PE1# show service id 300 es-pbr
===============================================================================
L3 ES PBR
===============================================================================
SF IP ESI Users Status
Interface MAC
VTEP:VNI
-------------------------------------------------------------------------------
10.10.10.1 ff:00:00:00:00:21:5f:00:df:e5 1 Active
evi-301 d8:47:01:01:00:0a
192.0.2.71:7171
-------------------------------------------------------------------------------
Number of entries : 1
-------------------------------------------------------------------------------
=================================================================================
*A:PE1# show service id 301 vxlan
===============================================================================
VPLS VXLAN, Ingress VXLAN Network Id: 301
===============================================================================
Egress VTEP, VNI
===============================================================================
VTEP Address Egress VNI Num. MACs Mcast Oper State L2 PBR
-------------------------------------------------------------------------------
192.0.2.69 301 1 Yes Up No
192.0.2.71 301 0 Yes Up No
192.0.2.71 7171 1 No Up No
-------------------------------------------------------------------------------
Number of Egress VTEP, VNI : 3
-------------------------------------------------------------------------------
===============================================================================
*A:PE1# show service id 301 fdb detail
===============================================================================
Forwarding Database, Service 301
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
301 d8:45:ff:00:00:6a vxlan: EvpnS 06/15/15 21:55:27
192.0.2.69:301
301 d8:47:01:01:00:0a vxlan: EvpnS 06/15/15 22:32:56
192.0.2.71:7171
301 d8:48:ff:00:00:6a cpm Intf 06/15/15 21:54:12
-------------------------------------------------------------------------------
No. of MAC Entries: 3
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static
===============================================================================
Note — In case BGP has to run an actual selection and a given (otherwise valid) EVPN route 'loses' to another EVPN route, the non-selected route will be displayed by the
show router BGP routes evpn x detail command with a 'tie-breaker' reason.
|
•
|
eth-cfm (meps, vmeps, mips): This command can be configured and used in EVPN VPLS service objects (service, saps and sdp-bindings). Although vmeps can be configured and used to local saps and sdp-bindings, eth-cfm tests will not work through EVPN destination bindings.
|
|
→
|
bgp-evpn is blocked in m-vpls services; however, a different m-vpls service can manage a SAP or spoke-sdp in a bgp-evpn enabled service.
|
|
•
|
mac-move—in bgp-evpn enabled VPLS services, mac-move can be used in saps/sdp-bindings; however, the MACs being learned through BGP-EVPN will not be considered.
|
Note—The mac duplication already provides a protection against mac-moves between EVPN and saps/sdp-bindings.
|
•
|
disable-learning and other fdb-related tools —these will only work for data plane learned mac addresses.
|
|
•
|
mac-protect —mac-protect cannot be used in conjunction with EVPN.
|
Note—EVPN provides its own protection mechanism for static mac addresses.
|
•
|
provider-tunnel—p2mp RSVP/mLDP LSPs are not supported in the bgp-evpn service. The configuration of the provider-tunnel is blocked.
|
|
•
|
MAC OAM—any MAC OAM tool is not supported for bgp-evpn services, that is: mac-ping, mac-trace, mac-populate, mac-purge, and cpe-ping.
|
Note —The number of BGP-MH sites per EVPN-VXLAN service is limited to 1.
|
•
|
Note—SAPs/SDP-bindings that belong to a specified ES but are configured on non-bgp-evpn-mpls-enabled VPLS or Epipe services will be kept down with the StandByForMHProtocol flag.
|
|
•
|
When bgp-evpn mpls is enabled in a b-vpls service, an i-vpls service linked to that b-vpls cannot be an R-VPLS (the allow-ip-int-bind command is not supported).
|
|
•
|
ethernet-segments can be associated with b-vpls SAPs/SDP-bindings and i-vpls/epipe SAPs/SDP-bindings,; however, the same ES cannot be associated with b-vpls and i-vpls/epipe SAP/SDP-bindings at the same time.
|
Figure 143 shows an example of how VPN-IPv4 routes are imported into the RTM (Routing Table Manager), and then passed to EVPN for its own process.
Note — VPN-IPv4 routes can be tagged at ingress and that tag is preserved throughout the RTM and EVPN processing, so that the tag can be
matched at the egress BGP routing policy.
Note — Policy tags can be used to match EVPN IP prefixes that were learned not only from BGP VPN-IPv4 but also from other routing protocols. The tag range supported for each protocol is different:
<tag> : accepts in decimal or hex
[0x1..0xFFFFFFFF]H (for OSPF and IS-IS)
[0x1..0xFFFF]H (for RIP)
[0x1..0xFF]H (for BGP)
Figure 144 shows an example of the reverse workflow: routes imported from EVPN and exported from RTM to BGP VPN-IPv4.
Note — The preceding described behavior and the use of tags is also valid for vsi-import and vsi-export policies in the R-VPLS.









