The 7750 SR supports all three methods following the best-practice RFC for TCP (RFC 5382, NAT Behavioral Requirements for TCP) and UDP (RFC 4787,
Network Address Translation (NAT) Behavioral Requirements for Unicast UDP). Port Forwarding is supported on the 7750 SR to allow servers which operate on well-known ports <1024 (such as HTTP and SMTP) to request the appropriate outside port for permanent allocation.
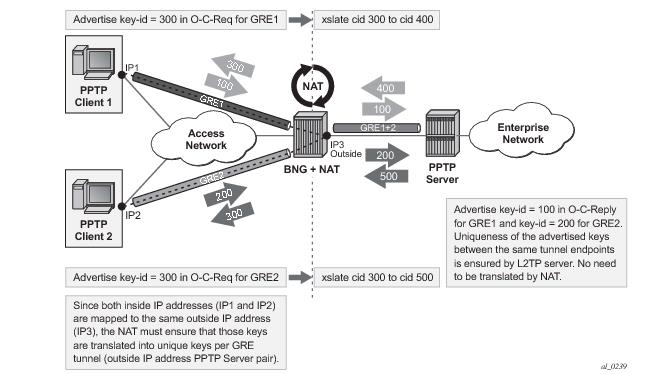
PPTP is defined in RFC 2637, Point-to-Point Tunneling Protocol (PPTP), and is used to provide VPN connection for home/mobile users to gain secure access to the enterprise network. Encrypted payload is transported over GRE tunnel that is negotiated over TCP control channel. In order for PPTP traffic to pass through NAT, the NAT device must correlate the TCP control channel with the corresponding GRE tunnel. This mechanism is referred to as PPTP ALG.
+--------------------------------+
| Media Header | Ethernet header, for example
+--------------------------------+
| IP Header | Tunnel endpoints
+--------------------------------+
| GRE Header | See following example
+--------------------------------+
| PPP Packet | Packet payload including PPP header
+--------------------------------+
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|C|R|K|S|s|Recur|A| Flags | Ver | Protocol Type |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Key (HW) Payload Length | Key (LW) Call ID |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Sequence Number (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Acknowledgment Number (Optional) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
The scenario where multiple clients behind the NAT are terminated to the same PPTP server is shown in Figure 53. In this case, it is possible that the source IP addresses of the two PPTP clients are mapped to the same outside address of the NAT. Since the endpoints of the GRE tunnel from the NAT to the PPTP server will be the same for both PPTP clients (although their real source IP addresses are different), the NAT must ensure the uniqueness of the Call-IDs in the outbound data connection. This is where Call-ID translation in the NAT becomes crucial.
|
•
|
This feature is enabled with the configuration command port-forwarding-dyn-block-reservation under the configure>service>vprn>nat>outside>pool and the configure>router>nat>outside>pool CLI hierarchy. This command can be enabled only if the maximum number of configured port blocks per outside IP is greater or equal then the maximum configured number of subscribers per outside IP address. This will guarantee that all subscribers (up the maximum number per outside IP address) configured with port forwards will be able to reserve a dynamic port block.
|
|
•
|
Nat-group: Watermarks can be placed to monitor the total number of sessions on an MDA.
|
|
•
|
Pool: Watermarks can be placed to monitor the total number of blocks in use in a pool.
|
|
•
|
Policy: In the policy it is possible to define watermarks on session and port usage. In both cases, it is the usage per subscriber (for l2-aware nat) or per host (for large-scale nat) that will be monitored.
|
config
router
nat
inside
deterministic
prefix 10.0.0.0/24 subscriber-type classic-lsn-sub nat-policy ‘one-to-one’
map start 10.0.0.10 end 10.0.0.10 to 1.2.3.4
map start 10.0.0.15 end 10.0.0.15 to 1.2.3.20
map start 10.0.0.100 end 10.0.0.100 to 1.2.3.30
Static mappings
10.0.0.0 — 1.2.3.0
10.0.0.1 — 1.2.3.1
10.0.0.2 — 1.2.3.2
10.0.0.3 — 1.2.3.3
10.0.0.4 — 1.2.3.5
10.0.0.5 — 1.2.3.6
:
10.0.0.9 — 1.2.3.10
10.0.0.10 — 1.2.3.4
10.0.0.11 — 1.2.3.11
10.0.0.12 — 1.2.3.12
:
10.0.0.14 — 1.2.3.14
10.0.0.15 — 1.2.3.20
10.0.0.16 — 1.2.3.15
:
10.0.0.19 — 1.2.3.18
10.0.0.20 — 1.2.3.19
10.0.0.21 — 1.2.3.21
:
10.0.0.28 — 1.2.3.28
10.0.0.29 — 1.2.3.29
10.0.0.30 — 1.2.3.31
:
10.0.0.99 — 1.2.3.100
10.0.0.100 — 1.2.3.30
10.0.0.101 — 1.2.3.101
:
10.0.0.255 — 1.2.3.255
config
router / service vprn
nat
outside
pool “one-to-one” nat-group 1 large-scale application agnostic
mode one-to-one
no port-forward-range
no port-reservation
subscriber-limit 1
deterministic port-reservation 65536
address-range 192.168.0.0 192.168.255.255
mode one-to-one
no port-forward-range
no port-reservation
subscriber-limit 1
deterministic port-reservation 65536.
config
router / service vprn X
nat
inside
deterministic
classic-lsn-max-subscriber-limit <num>
service vprn 10
nat
inside
destination-prefix 192.168.0.0/16 nat-policy pol-2
determinisitic
prefix 10.10.10.0/24 subscriber-type classic-lsn-sub nat-policy pol-1
service vprn 10
nat
inside
destination-prefix 192.168.0.0/16 nat-policy pol-2
determinisitic
prefix 10.10.10.0/30 subscriber-type classic-lsn-sub nat-policy pol-1
service vprn 10
nat
inside
destination-prefix 192.168.0.0/16
nat-policy pol-2
determinisitic
prefix 10.10.10.0/30 subscriber-type classic-lsn-sub nat-policy pol-1
In an effort to address issues of conflicting address space raised in draft-shirasaki-nat444-isp-shared-addr-02 Alcatel-Lucent co-developed an enhancement to Large Scale NAT to give every broadband subscriber their own NAT mapping table, yet still share a common outside pool of IPs.
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Version = 1 |R| OpCode | Reserved (16 bits) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Requested Lifetime |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
: :
: (optional) opcode-specific information :
: :
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
: :
: (optional) PCP Options :
: :
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Version = 1 |R| OpCode | Reserved | Result Code |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Lifetime |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Epoch |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
: :
: (optional) OpCode-specific response data :
: :
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
: (optional) Options :
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Protocol | Reserved (24 bits) |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Internal port | Suggested external port |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
: :
: Suggested External IP Address (32 or 128, depending on OpCode):
: :
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
configure
[router] | [service vprn]
nat
inside
dual-stack-lite
address <IPv6 Addr>
tunnel-mtu bytes
ip-fragmentation {disabled|fragment-ipv6|fragment-ipv6-unless-ipv4-df-set}
configure
[router] | [service vprn]
nat
inside
nat64
ipv6-mtu bytes
ip-fragmentation {disabled|fragment-ipv6|fragment-ipv6-unless-ipv4-df-set}
2012 tmnxNatPlBlockAllocationLsn
2013 tmnxNatPlBlockAllocationL2Aw
2 2012/07/12 16:40:58.23 WEST MINOR: NAT #2012 Base NAT
"{2} Free 80.0.0.1 [1884-1888] -- vprn10 5.5.5.5 at 2012/07/12 16:40:58"
1 2012/07/12 16:39:55.15 WEST MINOR: NAT #2012 Base NAT
"{1} Map 80.0.0.1 [1884-1888] -- vprn10 5.5.5.5 at 2012/07/12 16:39:55"
*A:left-a20>config>log# info
----------------------------------------------
filter 1
default-action drop
entry 1
action forward
match
application eq "nat"
numbr eq 2012
exit
exit
exit
event-control "nat" 2001 suppress
event-control "nat" 2002 suppress
event-control "nat" 2003 suppress
event-control "nat" 2004 suppress
event-control "nat" 2005 suppress
event-control "nat" 2006 suppress
event-control "nat" 2007 suppress
event-control "nat" 2008 suppress
event-control "nat" 2009 suppress
event-control "nat" 2010 suppress
event-control "nat" 2011 suppress
event-control "nat" 2012 generate
event-control "nat" 2014 suppress
event-control "nat" 2015 suppress
event-control "nat" 2017 suppress
syslog 10
exit
log-id 5
filter 1
from main
to memory
exit
----------------------------------------------
*A:left-a20# show log event-control "nat"
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2001 tmnxNatPlL2AwBlockUsageHigh WA gen 0 0
2002 tmnxNatIsaMemberSessionUsageHigh WA gen 0 0
2003 tmnxNatPlLsnMemberBlockUsageHigh WA gen 0 0
2004 tmnxNatLsnSubIcmpPortUsageHigh WA gen 0 0
2005 tmnxNatLsnSubUdpPortUsageHigh WA gen 0 0
2006 tmnxNatLsnSubTcpPortUsageHigh WA gen 0 0
2007 tmnxNatL2AwSubIcmpPortUsageHigh WA gen 0 0
2008 tmnxNatL2AwSubUdpPortUsageHigh WA gen 0 0
2009 tmnxNatL2AwSubTcpPortUsageHigh WA gen 0 0
2010 tmnxNatL2AwSubSessionUsageHigh WA gen 0 0
2011 tmnxNatLsnSubSessionUsageHigh WA gen 0 0
2012 tmnxNatPlBlockAllocationLsn MI gen 2 0
2013 tmnxNatPlBlockAllocationL2Aw MI gen 0 0
2014 tmnxNatResourceProblemDetected MI gen 0 0
2015 tmnxNatResourceProblemCause MI gen 0 0
2016 tmnxNatPlAddrFree MI gen 0 0
2017 tmnxNatPlLsnRedActiveChanged WA gen 0 2
2018 tmnxNatPcpSrvStateChanged MI gen 0 0
2019 tmnxNatFwdEntryAdded MI gen 0 0
=======================================================================
tmnxNatPlL2AwBlockUsageHigh
The tmnxNatPlL2AwBlockUsageHigh notification is sent when
the block usage of a Layer-2-Aware NAT address pool
reaches its high watermark ('true')
or when it reaches its low watermark again ('false').
tmnxNatIsaMemberSessionUsageHigh
The tmnxNatIsaMemberSessionUsageHigh notification is sent when
the session usage of a NAT ISA group member reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatPlLsnMemberBlockUsageHigh
The tmnxNatPlLsnMemberBlockUsageHigh notification is sent when
the block usage of a Large Scale NAT address pool
reaches its high watermark ('true')
or when it reaches its low watermark again ('false')
on a particular member MDA of its ISA group.
tmnxNatLsnSubIcmpPortUsageHigh
The tmnxNatLsnSubIcmpPortUsageHigh notification is sent when
the ICMP port usage of a Large Scale NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatLsnSubUdpPortUsageHigh
The tmnxNatLsnSubUdpPortUsageHigh notification is sent when
the UDP port usage of a Large Scale NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatLsnSubTcpPortUsageHigh
The tmnxNatLsnSubTcpPortUsageHigh notification is sent when
the TCP port usage of a Large Scale NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatL2AwSubIcmpPortUsageHigh
The tmnxNatL2AwSubIcmpPortUsageHigh notification is sent when
the ICMP port usage of a Layer-2-Aware NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatL2AwSubUdpPortUsageHigh
The tmnxNatL2AwSubUdpPortUsageHigh notification is sent when
the UDP port usage of a Layer-2-Aware NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatL2AwSubTcpPortUsageHigh
The tmnxNatL2AwSubTcpPortUsageHigh notification is sent when
the TCP port usage of a Layer-2-Aware NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatL2AwSubSessionUsageHigh
The tmnxNatL2AwSubSessionUsageHigh notification is sent when
the session usage of a Layer-2-Aware NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatLsnSubSessionUsageHigh
The tmnxNatLsnSubSessionUsageHigh notification is sent when
the session usage of a Large Scale NAT subscriber reaches its high
watermark ('true') or when it reaches its low watermark
again ('false').
tmnxNatPlBlockAllocationLsn
The tmnxNatPlBlockAllocationLsn notification is sent when
an outside IP address and a range of ports is allocated to
a NAT subscriber associated with a Large Scale NAT (LSN) pool,
and when this allocation expires.
tmnxNatPlBlockAllocationL2Aw
The tmnxNatPlBlockAllocationL2Aw notification is sent when
an outside IP address and a range of ports is allocated to
a NAT subscriber associated with a Layer-2-Aware NAT pool,
and when this allocation expires.
tmnxNatResourceProblemDetected
The tmnxNatResourceProblemDetected notification is sent when
the value of the object tmnxNatResourceProblem changes.
tmnxNatResourceProblemCause
The tmnxNatResourceProblemCause notification is to describe the cause
of a NAT resource problem.
tmnxNatPlAddrFree
The tmnxNatPlAddrFree notification is sent when
a range of outside IP addresses becomes free at once.
tmnxNatPlLsnRedActiveChanged
The tmnxNatPlLsnRedActiveChanged notification is related to NAT Redundancy sent when the value of the object tmnxNatPlLsnRedActive changes. The cause is
explained in the tmnxNatNotifyDescription which is a printable character string.
*A:left-a20>config>log# info
----------------------------------------------
file-id 5
description "nat logging"
location cf3:
rollover 15 retention 12
exit
log-id 5
filter 1
from main
to file 5
exit
*A:left-a20>config>log# info
----------------------------------------------
filter 1
default-action drop
entry 1
action forward
match
application eq "nat"
number eq 2012
exit
exit
exit
snmp-trap-group 6
trap-target "nat" address 114.0.1.10 port 9001 snmpv2c notify-community "private"
exit
log-id 6
filter 1
from main
to snmp
exit
----------------------------------------------
*A:left-a20>config>log#info
----------------------------------------------
...
filter 1
default-action drop
entry 1
action forward
match
application eq "nat"
number eq 2012
exit
exit
exit
syslog 7
address 114.0.1.10
exit
log-id 7
filter 1
from main
to syslog 7
exit
----------------------------------------------
*A:left-a20# configure log event-control "nat" 2012 generate
<severity-level>
cleared indeterminate critical major minor warning
*A:left-a20>config>aaa>nat-acct-plcy# info detail
description "nat-acct-basic policy"
include-radius-attribute
framed-ip-addr
nas-identifier
no nat-subscriber-string =>only relevant when subscriber aware NAT is enabled
user-name
inside-service-id
outside-service-id
outside-ip
port-range-block
hardware-timestamp
release-reason
multi-session-id
frame-counters
octet-counters
session-time
called-station-id
no subscriber-data =>only relevant when subscriber aware NAT is enabled
exit
radius-accounting-server
access-algorithm direct
retry 3
router "Base"
source-address-range 114.0.1.20 114.0.1.20
timeout sec 5
server 1 address 114.0.1.10 secret "KlWIBi08CxTyM/YXaU2gQitOu8GgfSD7Oj5hjese27A" hash2 port 1813
exit
*A:left-a20# show router route-table
==================================================================================================
Route Table (Router: Base)
==================================================================================================
Dest Prefix[Flags] Type Proto Age Pref Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
80.0.0.1/32 Remote NAT 02d18h24m 0 NAT outside: group 1 member 1 0
114.0.1.0/28 Local Local 02d20h25m 0 radius 0
114.0.1.20/32 Remote NAT 00h38m29s 0 NAT outside: group 1 member 1 0
*A:left-a20>config>isa>nat-group# info
----------------------------------------------
active-mda-limit 1
radius-accounting-policy "nat-acct-basic"
mda 1/2
no shutdown
Fri Jul 13 09:55:15 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Start
Acct-Multi-Session-Id = "500052cd2edcaeb97c2dad3d7c2dad3d"
Acct-Session-Id = "500052cd2edcaeb96206475d7c2dad3d"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "LSN44@26.0.0.58"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.58
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 2024-2028 router base"
Acct-Input-Packets = 0
Acct-Output-Packets = 0
Acct-Input-Octets = 0
Acct-Output-Octets = 0
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 0
Event-Timestamp = "Jul 13 2012 09:54:37 PDT"
Acct-Unique-Session-Id = "21c45a8b92709fb8"
Timestamp = 1342198515
Request-Authenticator = Verified
Fri Jul 13 09:55:16 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Start
Acct-Multi-Session-Id = "500052cd2edcaeb97c2dad3d7c2dad3d"
Acct-Session-Id = "500052cd2edcaeb9620647297c2dad3d"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "LSN44@26.0.0.58"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.58
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 2029-2033 router base"
Acct-Input-Packets = 0
Acct-Output-Packets = 5
Acct-Input-Octets = 0
Acct-Output-Octets = 370
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 1
Event-Timestamp = "Jul 13 2012 09:54:38 PDT"
Acct-Unique-Session-Id = "baf26e8a35e31020"
Timestamp = 1342198516
Request-Authenticator = Verified
Fri Jul 13 09:56:18 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Stop
Acct-Multi-Session-Id = "500052cd2edcaeb97c2dad3d7c2dad3d"
Acct-Session-Id = "500052cd2edcaeb96206475d7c2dad3d"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "LSN44@26.0.0.58"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.58
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 2024-2028 router base"
Acct-Terminate-Cause = Port-Unneeded
Acct-Input-Packets = 0
Acct-Output-Packets = 25
Acct-Input-Octets = 0
Acct-Output-Octets = 1850
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 64
Event-Timestamp = "Jul 13 2012 09:55:41 PDT"
Acct-Unique-Session-Id = "21c45a8b92709fb8"
Timestamp = 1342198578
Request-Authenticator = Verified
Fri Jul 13 09:56:20 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Stop
Acct-Multi-Session-Id = "500052cd2edcaeb97c2dad3d7c2dad3d"
Acct-Session-Id = "500052cd2edcaeb9620647297c2dad3d"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "LSN44@26.0.0.58"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.58
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 2029-2033 router base"
Acct-Terminate-Cause = Host-Request
Acct-Input-Packets = 0
Acct-Output-Packets = 25
Acct-Input-Octets = 0
Acct-Output-Octets = 1850
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 65
Event-Timestamp = "Jul 13 2012 09:55:42 PDT"
Acct-Unique-Session-Id = "baf26e8a35e31020"
Timestamp = 1342198580
Request-Authenticator = Verified
Fri Jul 13 11:57:38 2012
Acct-Status-Type = Start
NAS-IP-Address = 1.1.1.1
User-Name = "l2-aware-nat"
Framed-IP-Address = 25.0.1.100
Framed-IP-Netmask = 255.255.255.0
Class = 0x6c322d61776172652d636c737373
Calling-Station-Id = "remote-l2-aware0"
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000001150006F7C"
Event-Timestamp = "Jul 13 2012 11:57:00 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.13"
ADSL-Agent-Circuit-Id = "l2-aware-nat"
ADSL-Agent-Remote-Id = "remote-l2-aware0"
Alc-Subsc-ID-Str = "l2-aware-1"
Alc-Subsc-Prof-Str = "l2-aware-nat"
Alc-SLA-Prof-Str = "tp_sla_prem"
Alc-Nat-Port-Range = "83.0.0.1 1024-1079 router base"
Alc-Client-Hardware-Addr = "00:00:65:05:13:01"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Acct-Unique-Session-Id = "6bbbd5a110313b47"
Timestamp = 1342205858
Request-Authenticator = Verified
------------------------------------------------------------------------
Owner : LSN-Host@10.0.0.15
Router : 10
FlowType : UDP Timeout (sec) : 11
Inside IP Addr : 10.0.0.15 Inside Port : 100
Outside IP Addr : 80.0.0.1 Outside Port : 1164
Foreign IP Addr : 10.0.3.2 Foreign Port : 5000
Dest IP Addr : 10.0.3.2 Dest Port : 5000
-------------------------------------------------------------------------------
Flows are formatted according to IETF IPFIX RFC 5101, Specification of the IP Flow Information Export (IPFIX) Protocol, for the Exchange of IP Traffic Flow Information. Data structures are contained in RFC5102,
Information Model for IP Flow Information Export. NAT flow logging is sent to up to two different IP addresses both of which must be unicast IPv4 destinations. These UDP streams are stateless due to the significant volume of transactions. However they do contain sequence numbers such that packet loss can be identified. They egress the chassis at FC NC.
*A:left-a20>config>service>ipfix# info detail
----------------------------------------------
ipfix-export-policy "ipxif-policy" create
description "external IPFIX collector"
collector router "Base" ip 114.0.1.10 create
mtu 1500
source-address 114.0.1.20
template-refresh-timeout min 10
no shutdown
exit
exit
*A:left-a20>config>service>nat>nat-policy# info
----------------------------------------------
pool "base" router Base
ipfix-export-policy "ipxif-policy"
Table 16 lists the values and descriptions of the fields in the example flow creation and deletion templates.
However, in cases where the inside traffic is mapped to multiple pools
1, the basic per pool multi-chassis redundancy mode can cause the inside traffic within the same routing instance to fail since some pools referenced from the routing instance might be active on one node while other pools might be active on the other node.
configure
router/service vprn
nat
outside
pool <name>
redundancy
export <ip-prefix/length>
monitor <ip-prefix/length>[no] shutdown
follow router <rtr-id> pool <master-pool>
router/service vprn
nat
outside
pool "nat0-pool" nat-group 1 type large-scale create
port-reservation ports 252
redundancy
follow router 500 pool "nat500-pool"
exit
address-range 128.251.12.0 128.251.12.10 create
exit
no shutdown
exit
exit
exit
*A:Dut-B# show router 500 nat pool "nat500-pool"
===============================================================================
NAT Pool nat500-pool
===============================================================================
Description : (Not Specified)
ISA NAT Group : 1
Pool type : largeScale
Admin state : inService
Mode : auto (napt)
Port forwarding dyn blocks reserved : 0
Port forwarding range : 1 - 1023
Port reservation : 2300 blocks
Block usage High Watermark (%) : (Not Specified)
Block usage Low Watermark (%) : (Not Specified)
Subscriber limit per IP address : 65535
Active : true
Deterministic port reservation : (Not Specified)
Last Mgmt Change : 02/17/2014 09:41:43
===============================================================================
===============================================================================
NAT address ranges of pool nat500-pool
===============================================================================
Range Drain Num-blk
-------------------------------------------------------------------------------
81.81.1.0 - 81.81.1.255 0
-------------------------------------------------------------------------------
No. of ranges: 1
===============================================================================
===============================================================================
NAT members of pool nat500-pool ISA NAT group 1
===============================================================================
Member Block-Usage-% Hi
-------------------------------------------------------------------------------
1 < 1 N
2 < 1 N
3 < 1 N
4 < 1 N
5 < 1 N
6 < 1 N
-------------------------------------------------------------------------------
No. of members: 6
===============================================================================
===============================================================================
Dual-Homing
===============================================================================
Type : Leader
Export route : 170.0.0.3/32
Monitor route : 170.0.0.2/32
Admin state : inService
Dual-Homing State : Active
===============================================================================
===============================================================================
Dual-Homing fate-share-group
===============================================================================
Router Pool Type
-------------------------------------------------------------------------------
Base nat0-pool Follower
vprn500 nat500-pool Leader
vprn501 nat501-pool Follower
vprn502 nat502-pool Follower
-------------------------------------------------------------------------------
No. of pools: 4
===============================================================================
*A:Dut-B# show router 501 nat pool "nat501-pool"
===============================================================================
NAT Pool nat501-pool
===============================================================================
Description : (Not Specified)
ISA NAT Group : 1
Pool type : largeScale
Admin state : inService
Mode : auto (napt)
Port forwarding dyn blocks reserved : 0
Port forwarding range : 1 - 1023
Port reservation : 2300 blocks
Block usage High Watermark (%) : (Not Specified)
Block usage Low Watermark (%) : (Not Specified)
Subscriber limit per IP address : 65535
Active : true
Deterministic port reservation : (Not Specified)
Last Mgmt Change : 02/17/2014 09:41:43
===============================================================================
===============================================================================
NAT address ranges of pool nat501-pool
===============================================================================
Range Drain Num-blk
-------------------------------------------------------------------------------
81.81.2.0 - 81.81.2.255 0
81.81.3.0 - 81.81.3.255 0
-------------------------------------------------------------------------------
No. of ranges: 2
===============================================================================
===============================================================================
NAT members of pool nat501-pool ISA NAT group 1
===============================================================================
Member Block-Usage-% Hi
-------------------------------------------------------------------------------
1 < 1 N
2 < 1 N
3 < 1 N
4 < 1 N
5 < 1 N
6 < 1 N
-------------------------------------------------------------------------------
No. of members: 6
===============================================================================
===============================================================================
Dual-Homing
===============================================================================
Type : Follower
Follow-pool : "nat500-pool" router 500
Dual-Homing State : Active
===============================================================================
===============================================================================
Dual-Homing fate-share-group
===============================================================================
Router Pool Type
-------------------------------------------------------------------------------
Base nat0-pool Follower
vprn500 nat500-pool Leader
vprn501 nat501-pool Follower
vprn502 nat502-pool Follower
-------------------------------------------------------------------------------
No. of pools: 4
===============================================================================
*A:Dut-B# show service nat overview
===============================================================================
NAT overview
===============================================================================
Inside/ Policy/ Type
Outside Pool
-------------------------------------------------------------------------------
vprn550 lsn-policy_unused default
Base nat0-pool
vprn550 lsn-policy_nat1 destination prefix
vprn500 nat500-pool
vprn550 lsn-policy-nat2 destination prefix
vprn501 nat501-pool
vprn551 lsn-policy_unused default
Base nat0-pool
vprn551 lsn-policy-nat3 destination prefix
vprn501 nat501-pool
vprn551 lsn-policy-nat4 destination prefix
vprn502 nat502-pool
vprn552 lsn-policy_unused default
Base nat0-pool
vprn552 lsn-policy-nat5 destination prefix
vprn502 nat502-pool
===============================================================================
The maximum number of NAT subscribers that can be mapped to a single outside IP address is configurable using a subscriber-limit command under the pool hierarchy. For Deterministic NAT, this number is restricted to the power of 2 (2^n). The consequence of this is that the number of NAT subscribers must be configuration-wise organized in ranges with the boundary that must be power of 2.
The number of subscribers per outside IP (the subscriber-limit command [2^n]) multiplied by the number of IP addresses over all address-range in an outside pool will determine the maximum number of subscribers that a deterministic pool can support.
The determinisitic>port-reservation command enables deterministic mode of operation for the pool.
The example in Table 17 shows how port ranges would be carved out in ideal scenario.
* — Signifies the fixed parameters (requirements).
Note that port-block-limit includes the deterministic port block plus all dynamic port-blocks.
* — Signifies the fixed parameters (requirements).
The final example is similar as Table 18 with the difference that the number of deterministic port blocks fixed are kept, as in the original example (300, 500 and 700).
configure
service
vprn
nat
outside
pool mypool
port-reservation ports 180
deterministic
port-reservation 300
subscriber-limit 128
port-forwarding-range 4023
configure
service
nat
nat-policy mypolicy
block-limit 5 1 deterministic port block + 4 dynamic port blocks
pool ‘mypool’ nat-group 1 type large-scale
port-reservation {blocks <dynBlocks>} | {ports <ports>}
deterministic
port-reservation <ports>
subscriber-limit <sub-limit>
port-forwarding-range <pfRange>
address-range <start-ip-address> <end-ip-address>
address-range <start-ip-address> <end-ip-address>
The mapping itself is represented by the map command under the prefix hierarchy:
router/service vprn
nat
inside
deterministic
prefix <ip-prefix/length> subscriber-type <nat-sub-type> nat-policy <nat-policy-name>
map start <inside-ip-address> end <inside-ip-address> to <outside-ip-address>
3.
The outside-ip-address in the map statements must be unique amongst all map statements referencing the same pool. In other words, two map statements cannot reference the same
outside-ip-address in the pool.
In case that the number of subscribers (IP addresses in LSN44) in the map statement is larger than the subscriber-limit per outside IP, then the subscribers must be split over a block of consecutive outside IP addresses where the
outside-ip-address in the map statement represent only the first outside IP address in that block.
router
nat
outside
pool ‘my-det-pool’ nat-group 1 type large-scale
subscriber-limit 128
deterministic
port-reservation 400
address-range 128.251.0.0 128.251.0.10
service vprn 10
nat
inside
deterministic
prefix 10.0.0.0/24 subscriber-type classic-lsn-sub nat-policy det
map start 10.0.0.0 end 10.0.0.255 to 128.251.0.1
Alternatively, the map statement can be configured as:
service vprn 10
nat
inside
deterministic
prefix 10.0.0.0/24 subscriber-type classic-lsn-sub nat-policy det
map start 10.0.0.0 end 10.0.0.127 to 128.251.0.1
map start 10.0.0.128 end 10.0.0.255 to 128.251.0.5
service vprn 10
nat
inside
deterministic
prefix 10.0.0.0/24 subscriber-type classic-lsn-sub nat-policy det
map start 10.0.0.0 end 10.0.0.63 to 128.251.0.1
map start 10.0.0.64 end 10.0.0.127 to 128.251.0.3
map start 10.0.0.128 end 10.0.0.255 to 128.251.0.5
service vprn 10
nat
inside
deterministic
prefix 10.0.0.0/26 subscriber-type classic-lsn-sub nat-policy det
map start 10.0.0.0 end 10.0.0.63 to 128.251.0.1
prefix 10.0.1.0/26 subscriber-type classic-lsn-sub nat-policy det
map start 10.0.1.0 end 10.0.1.63 to 128.251.0.1
Note that each configured prefix can evaluate into multiple map commands. The number of map commands will depend on the length of the configured prefix, the
subscriber-limit command and fragmentation of outside address-range within the pool with which the prefix is associated.
The configuration example shown Figure 61 depicts a case in which prefixes from multiple routing instances are mapped to the same outside pool and at the same time the prefixes from a single inside routing instance are mapped to different pools (we do not support the latter with non-deterministic NAT).
tools dump nat deterministic-mapping outside-ip <ipv4-address> router <router-instance> outside-port <[1..65535]>
<ipv4-address> : a.b.c.d
<router-instance> : <router-name>|<service-id>
router-name - "Base"
service-id - [1..2147483647]
config service nat deterministic-script location <remote-url>
<remote-url> - [{ftp://|tftp://}<login>:<pswd>@<remote-locn>/][<file-path>]
180 chars max
show service nat deterministic-script
========================================================================
Deterministic NAT script data
========================================================================
Location : ftp://10.10.10.10/pub/det-nat-script/det-nat.py
Save needed : yes
Last save result : none
Last save time : N/A
========================================================================
admin nat save-deterministic-script
Once the script is exported (saved), the status of the script is changed as well:
show service nat deterministic-script
========================================================================
Deterministic NAT script data
========================================================================
Location : ftp://10.10.10.10/pub/det-nat-script/det-nat.py
Save needed : no
Last save result : sucess
Last save time : 2013/01/07 10:33:43
========================================================================
user@external-server:/home/ftp/pub/det-nat-script$ ./det-nat.py
Usage: det-nat-.py {{DIRECTION PARAMS} | -h[elp] }
where DIRECTION := { -f[orward] | -b[ackward] }
where PARAMS := { -s[ervice] -a[ddress] -p[ort] }
Router 10, Source-ip: 20.0.5.0-20.0.5.127 to router base, outside-ip 85.0.0.1
Router 10 Source-ip: 20.0.5.128-20.0.5.255 to router base outside-ip 85.0.0.2
subscriber has public ip address 85.0.0.1 from service 0 and is using ports [1324 - 1353]
user@external-server:/home/ftp/pub/det-nat-script$ ./det-nat.py -b -s 0 -a 85.0.0.1 -p 3020
subscriber has private ip address 20.0.5.66 from service 10
config>service>vprn>nat>inside>dslite#
subscriber-prefix-length [32..64 | 128] (default is 128)
config>service>vprn>nat>inside>deterministic#
prefix <v6-prefix/length> subscriber-type dslite-lsn-sub nat-policy <policy-name>
config>service>vprn>nat>inside>deterministic#
prefix ABCD:FF::/56 subscriber-type dslite-lsn-sub nat-policy det-policy
config>service>vprn>nat>inside>dslite#
subscriber-prefix-length 60
ABCD:FF::/60 to ABCD:FF:00:70::/60 to 128.151.1.1
ABCD:FF:00:80::/60 to ABCD:FF:00:F0::/60 to 128.151.1.2
configure
router/service vprn
nat
inside
deterministic
dslite-max-subscriber-limit <1,2,4,8…32768>
subscriber-prefix-length – n = [32..64,128]
where n = log2(dslite-max-subscriber-limit)
[or dslite-max-subscriber-limit = 2^n]
|
•
|
To modify nat pool parameters, the nat pool must be in a shutdown state.
|
|
•
|
Shutting down the nat pool by configuration ( shutdown command) is not allowed in case that any nat-policy referencing this pool is active. In other words, all configured prefixes referencing the pool via the nat-policy must be deleted system-wide before the pool can be shut down. Once the pool is enabled again, all prefixes referencing this pool (with the nat-policy) will have to be recreated. For a large number of prefixes, this can be performed with an offline configuration file executed using the exec command.
|
config>service>vprn>nat>inside>deterministic# info
----------------------------------------------
classic-lsn-max-subscriber-limit 128
prefix 10.0.5.0/24 subscriber-type classic-lsn-sub nat-policy "det"
map start 10.0.5.0 end 10.0.5.127 to 128.251.0.7
map start 10.0.5.128 end 10.0.5.255 to 128.251.0.2
shutdown
config>service>vprn>nat>inside>deterministic# info
----------------------------------------------
dslite-max-subscriber-limit 128
prefix 2001:db8:0:1/64 subscriber-type dslite-lsn-sub nat-policy "det"
map start 2001:BD8::/64 end 2001:BD8::FF:0:0:0:0/64 to 85.0.0.5
shutdown
config>service>vprn>nat>inside>ds-lite#
subscriber-prefix-length 64
no shutdown
The outside-ip-address in the map statements must be unique amongst all map statements referencing the same pool. In other words, two map statements cannot reference the same <outside-ip-address> in a pool.
The NAT command histogram displays compartmentalized port distribution per protocol for an aggregated number of subscribers. This allows operators to trend port usage over time and consequently adjust the configuration as the port demand per subscriber increase/decrease. For example, an operator may find that the port usage in a pools has increased over a period of time. Accordingly, the operator may plan to increase the number of ports per port block.
# tools dump nat histogram
- histogram router <router-instance> pool <pool-name> bucket-size <[1..65536]> num-buckets <[2..50]>
<router-instance> : <router-name>|<service-id>
router-name - "Base"
service-id - [1..2147483647]
<pool-name> : [32 chars max]
tools dump nat histogram router "Base" pool "det" bucket-size 20 num-buckets 20
========================================================================Usage histogram NAT pool "det" router "Base"
========================================================================
Num-ports Sub-TCP Sub-UDP Sub-ICMP
------------------------------------------------------------------------
0-19 0 0 0
20-39 0 0 0
40-59 0 0 0
60-79 0 0 0
80-99 0 0 0
100-119 0 0 0
120-139 0 0 0
140-159 0 0 0
160-179 0 0 0
180-199 0 0 0
200-219 0 0 0
220-239 0 0 0
240-259 0 0 0
260-279 0 0 0
280-299 0 0 0
300-319 0 0 0
320-339 0 0 0
340-359 0 0 0
360-379 0 0 0
380- 0 0 0
---------------------------------------------------
The output of the histogram command can be periodically exported to en external destination via cron. The following is an example:
*A:CPM>config>cron# info
----------------------------------------------
script "nat_histogram"
location "ftp://*:*@138.203.8.62/nat-histogram.txt"
no shutdown
exit
action "dump_nat_histogram"
results "ftp://*:*@138.203.8.62/nat_histogram_results.txt"
script "nat_histogram"
no shutdown
exit
schedule "nat_histogram_schedule"
interval 600
action "dump_nat_histogram"
no shutdown
exit
----------------------------------------------
*A:CPM>config>cron#
tools dump nat histogram router 4 pool "deterministic" bucket-size
10 num-buckets 10
[root@ftp]# ls nat_histogram_results.txt*
nat_histogram_results.txt_20130117-153548.out
nat_histogram_results.txt_20130117-153648.out
nat_histogram_results.txt_20130117-153748.out
nat_histogram_results.txt_20130117-153848.out
nat_histogram_results.txt_20130117-153948.out
nat_histogram_results.txt_20130117-154048.out
[root@ftp]#
tools dump nat histogram router <router-instance> pool <pool-name> bucket-size <[1..65536]> num-buckets <[2..50]>
tools dump nat histogram router "Base" pool "det" bucket-size 20 num-buckets 40
===============================================================================
Usage histogram NAT pool "det" router "Base"
===============================================================================
Num-ports Sub-TCP Sub-UDP Sub-ICMP
-------------------------------------------------------------------------------
0-19 0 0 0
20-39 0 1 0
40-59 0 0 0
60-79 0 0 0
80-99 0 0 0
100-119 0 0 0
120-139 0 0 0
140-159 0 0 0
160-179 0 0 0
180-199 0 0 0
200-219 0 0 0
220-239 0 0 0
240-259 0 0 0
260-279 0 0 0
280-299 0 0 0
300-319 0 0 0
320-339 0 0 0
340-359 0 0 0
360-379 0 0 0
380-399 0 0 0
400-419 0 0 0
420-439 0 0 0
440-459 0 0 0
460-479 0 0 0
480-499 0 0 0
500-519 0 0 0
520-539 0 0 0
540-559 0 0 0
560-579 0 0 0
580-599 0 0 0
600-619 0 0 0
620-639 0 0 0
640-659 0 0 0
660-679 0 0 0
680-699 0 0 0
700-719 0 0 0
720-739 0 0 0
740-759 0 0 0
760-779 0 0 0
780- 0 0 0
-------------------------------------------------------------------------------
No. of entries: 40
===============================================================================
The selection of the NAT pool and the outside routing context is performed through the NAT policy. Multiple NAT policies can be used within an inside routing context. This feature effectively allows selective mapping of the incoming traffic within an inside routing context to different NAT pools (with different mapping properties
2) and to different outside routing contexts. NAT policies can be configured:
The concept of the NAT pool selection mechanism based on the destination of the traffic via routing is shown in Figure 62.
The routing approach relies on upstream traffic being directed (or diverted) to the NAT function based on the destination-prefix command in the
configure>service>vprn/router>nat>inside CLI context. In other words, the upstream traffic will be NATed only if it matches a preconfigured destination IP prefix. The
destination-prefix command creates a static route in the routing table of the inside routing context. This static route will divert all traffic with the destination IP address that matches the created entry, towards the MS-ISA. The NAT function itself will be performed once the traffic is in the proper context in the MS-ISA.
service vprn/router
nat
inside
destination-prefix <ip-prefix/length> nat-policy <policy-name>]
:
:
service vprn/router
nat
inside
destination-prefix 20.20.10.0/24 nat-policy policy-1
destination-prefix 30.30.30.0/24 nat-policy policy-1
destination-prefix 40.40.40.0/24 nat-policy policy-2
*A:right-a21>config>filter>ip-filter>entry# match
- match [protocol <protocol-id>]
- no match
<protocol-id> : protocol numbers - [0..255] (Decimal,
Hexadecimal, or Binary representation).
Supported IANA IP protocol names -
none|crtp|crudp|egp|eigrp|encap|ether-ip|
gre|icmp|idrp|igmp|igp|ip|ipv6|ipv6-frag|ipv6-icmp|
ipv6-no-nxt|ipv6-opts|ipv6-route|isis|iso-ip|l2tp|
ospf-igp|pim|pnni|ptp|rdp|rsvp|sctp|stp|tcp|udp|vrrp
* - udp/tcp wildcard
[no] dst-ip - Configure dest. ip match condition
[no] dst-port - Configure destination port match condition
[no] port - Configure port match condition
[no] src-ip - Configure source ip match condition
[no] src-port - Configure source port match condition
filter
entry
action nat [nat-policy <nat-policy-name>]
configure
filter
ipv6-filter
entry <entry-id> [time-range <time-range-name>] [create]
action nat nat-type <nat-type> [nat-policy <nat-policy-name>]
exit
exit
exit
exit
Where the nat-type parameter can be either
dslite or
nat64.
The DS-Lite AFTR address and NAT64 destination prefix configuration under the corresponding (DS-Lite or NAT64) router/vprn>nat>inside context is mandatory. Note that this is even in the case when only filters are desired for traffic diversion to NAT.
The default nat-policy is always mandatory and must be configured under the
router/vprn>nat>inside context. This default NAT policy can reference any configured pool in the desired ISA group. The pool referenced in the default
nat-policy can be then overridden by the
nat-policy associated with the destination-prefix in LSN44 or by the
nat-policy referenced in the ipv4/ipv6-filter used for NAT diversion in LSN44/DS-Lite/NAT64.
Each subscriber using multiple policies is counted as 1 subscriber for the inside resources scaling limits (such as the number of subscribers per MS-ISA), and counted as 1 subscriber per (subscriber + policy combination) for the
outside limits (
subscriber-limitsubscribers per IP;
port-reservation port/block reservations per subscriber).
tools perform nat port-forwarding-action lsn
- lsn create router <router-instance> [b4 <ipv6-address>] [aftr <ipv6-address>] ip <ip-
address> protocol {tcp|udp} [port <port>] lifetime <lifetime> [outside-ip <ipv4-
address>] [outside-port <port>] [nat-policy <policy-name>]
In the absence of the nat-policy referenced in the SPF creation request, the default
nat-policy under the
vprn/router>nat>inside context will be used.
The consequence of this is that the operator must know the nat-policy in which the SPF is to be created. The SPF cannot be created via PCP outside of the pool referenced by the default
nat-policy, since PCP does not provide means to communicate nat-policy name in the SPF creation request.
Figure 64 and
Figure 65 describe certain scenarios that are more theoretical and are less likely to occur in reality. However, they are described here for the purpose of completeness.
Figure 64 represents the case where traffic from the WEB server 1.1.1.1 is initiated toward the destined network 11.0.0.0/8. Such traffic will end up translated in the Pool B and forwarded to the 11.0.0.0/8 network even though the static port forward has been created in Pool A. In this case the nat-policy rule (dest 11.0.0.0/8
pool B) will determine the pool selection in the upstream direction (even though the SPF for the WEB server already exists in the Pool A).
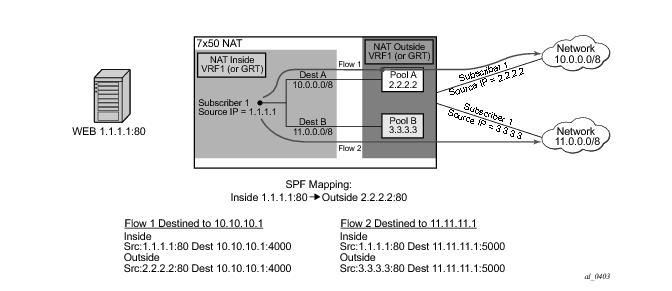
The next example in Figure 65 shows a case where the Flow 1 is initiated from the outside. Since the partial mapping matching this flow already exist (created by SPF) and there is no more specific match (FQF)
3 present, the downstream traffic will be mapped according to the SPF (through Pool A to the Web server). At the same time, a more specific entry (FQF) will be created (initiated by the very same outside traffic). This FQF will now determine the forwarding path for all traffic originating from the inside that is matching this flow. This means that the Flow 2 (reverse of the Flow 1) will not be mapped to an IP address from the pool B (as the policy dictates) but instead to the Pool A which has a more specific match.
When multiple NAT policies per inside routing context are deployed, a new policy-id parameter is added to certain syslog messages. The format of the policy-id is:
plcy-id XX
Introduction of the policy-id in logs is necessary due to the bulk-operations associated with multiple NAT policies per inside routing context. A bulk operation, for example, represents the removal of the
nat-policy from the configuration, shutting down the NAT pool, or removing an IP address range from the pool. Note that removing a NAT accounting policy in case of RADIUS NAT logging will not trigger a summarization log since an acct-off message is sent. Such operations have a tendency to be heavy on NAT logging since they affect a large number of NAT subscribers at once. Summarization logs are introduced to prevent excessive logging during bulk operations. For example, the nat-policy deletion can be logged with a single (summarized) entry containing the policy-id of the nat-policy that was removed and the inside srvc-id. Since all logs contain the policy-id, a single summarization
free4 log can be compared to all
map2 logs containing the same policy-id to determine for which subscribers the NAT mappings have ceased.
|
•
|
When the nat-policy is removed — With a single nat-policy per inside routing context, a summarization log is generated with only one field: inside srvc-id ( vprn or base). This is sufficient since there is only one nat-policy per inside routing context. To determine subscribers for which NAT mappings are terminated, the operator should search all most recent map logs matching the service-id from the summarization log.
|
A log search based on the policy-id and inside
srvc-id should reveal all subscribers whose mappings were affected by the
nat-policy removal.
An open log sequence in RADIUS, for example a map for the <inside IP 1, outside IP 1,port-block 1> followed at some later time with a map for <inside IP 2, outside IP 1, port-block 1>, is an indication that the free log for <inside IP 1, outside IP 1,port-block 1> is missing. This means that either the free log for <inside IP 1, outside IP 1,port-block 1> was lost or that a policy/pool/address-range was removed from the configuration. In the latter case, the operator should look in the CPM log for the summarization message.
*A:left-a20>config>service>vprn#
radius-proxy
server "proxy-acct" purpose accounting create
default-accounting-server-policy "lsn-policy"
description "two side server -interface:client ; default-plcy:real server"
interface "rad-proxy-loopback"
secret "TEg1UEZzemRMyZXD1HvvQGkeGfoQ58MF" hash2
no shutdown
exit
exit
The lsn-policy is defined as:
*A:left-a20>config>aaa#
radius-server-policy "lsn-policy" create
servers
router "Base"
source-address 114.0.1.12
server 1 name "114"
exit
exit
*A:left-a20>config>router>radius-server# info
----------------------------------------------
server "114" address 114.0.1.10 secret "KRr7H.K3i0z9O/hj2BUSmdJUdl.zWrkE" hash2 port 1813 create
description "real radius or acct server"
exit
*A:left-a20>config>subscr-mgmt>sub-prof# info
----------------------------------------------
radius-accounting-policy "real-acct-srvr" duplicate “lsn”
egress
agg-rate-limit 10000
exit
----------------------------------------------
*A:left-a20>config>subscr-mgmt>acct-plcy# info
description “lsn radius-acct-policy”
update-interval 5
include-radius-attribute
acct-authentic
acct-delay-time
called-station-id
calling-station-id remote-id
circuit-id
framed-interface-id
framed-ip-addr
framed-ip-netmask
mac-address
nas-identifier
nas-port-id
nas-port-type
nat-port-range
remote-id
sla-profile
sub-profile
subscriber-id
user-name
alc-acct-triggered-reason
exit
session-id-format number
radius-accounting-server
router 10 (service id where proxy radius is configured)
server 1 address 5.5.5.5 secret "cVi1sidvgH28Pd9QoN1flE" hash2
(radius proxy IP address is 5.5.5.5 on interface “rad-proxy-loopback”; the ‘secret’ is the same as configured on RADIUS accounting proxy)
exit
*A:left-a20>config>service>vprn>nat>inside# info
----------------------------------------------
nat-policy "nat-base"
destination-prefix 10.0.0.0/16
subscriber-identification
attribute vendor "standard" attribute-type "station-id"
description "sub-aware CGN"
radius-proxy-server router 10 name "proxy-acct"
no shutdown
exit
----------------------------------------------
*A:left-a20>config>isa>nat-group# info
----------------------------------------------
active-mda-limit 1
radius-accounting-policy "nat-acct-basic"
mda 1/2
no shutdown
*A:left-a20>config>aaa>nat-acct-plcy# info detail
----------------------------------------------
description "nat-acct-basic policy"
include-radius-attribute
framed-ip-addr
nas-identifier
nat-subscriber-string
user-name
inside-service-id
outside-service-id
outside-ip
port-range-block
hardware-timestamp
release-reason
multi-session-id
frame-counters
octet-counters
session-time
called-station-id
subscriber-data
exit
radius-accounting-server
access-algorithm direct
retry 3
router "Base"
source-address-range 114.0.1.20 114.0.1.20
timeout sec 5
server 1 address 114.0.1.10 secret "KlWIBi08CxTyM/YXaU2gQitOu8GgfSD7Oj5hjese27A" hash2 port 1813
exit
----------------------------------
Mon Jul 16 10:59:27 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Start
Acct-Multi-Session-Id = "500456500365a4de7c29a9a07c29a9a0"
Acct-Session-Id = "500456500365a4de6201d7b87c29a9a0"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "remote0"
Calling-Station-Id = "remote0"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.7
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 1054-1058 router base"
Acct-Input-Packets = 0
Acct-Output-Packets = 0
Acct-Input-Octets = 0
Acct-Output-Octets = 0
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 0
Event-Timestamp = "Jul 16 2012 10:58:40 PDT"
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Event-Timestamp = "Jul 16 2012 10:58:24 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Acct-Unique-Session-Id = "10f8bce6e5e7eb41"
Timestamp = 1342461567
Request-Authenticator = Verified
Mon Jul 16 11:03:56 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Interim-Update
Acct-Multi-Session-Id = "500456500365a4de7c29a9a07c29a9a0"
Acct-Session-Id = "500456500365a4de6201d7b87c29a9a0"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "remote0"
Calling-Station-Id = "remote0"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.7
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 1054-1058 router base"
Acct-Input-Packets = 0
Acct-Output-Packets = 1168
Acct-Input-Octets = 0
Acct-Output-Octets = 86432
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 264
Event-Timestamp = "Jul 16 2012 11:03:04 PDT"
Acct-Delay-Time = 5
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Acct-Session-Time = 279
Event-Timestamp = "Jul 16 2012 11:03:04 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Acct-Unique-Session-Id = "10f8bce6e5e7eb41"
Timestamp = 1342461836
Request-Authenticator = Verified
Mon Jul 16 11:04:34 2012
NAS-IP-Address = 1.1.1.1
NAS-Identifier = "left-a20"
NAS-Port = 37814272
Acct-Status-Type = Stop
Acct-Multi-Session-Id = "500456500365a4de7c29a9a07c29a9a0"
Acct-Session-Id = "500456500365a4de6201d7b87c29a9a0"
Called-Station-Id = "00-00-00-00-01-01"
User-Name = "remote0"
Calling-Station-Id = "remote0"
Alc-Serv-Id = 10
Framed-IP-Address = 26.0.0.7
Alc-Nat-Outside-Ip-Addr = 80.0.0.1
Alc-Nat-Port-Range = "80.0.0.1 1054-1058 router base"
Acct-Terminate-Cause = Host-Request
Acct-Input-Packets = 0
Acct-Output-Packets = 1321
Acct-Input-Octets = 0
Acct-Output-Octets = 97754
Acct-Input-Gigawords = 0
Acct-Output-Gigawords = 0
Acct-Session-Time = 307
Event-Timestamp = "Jul 16 2012 11:03:47 PDT"
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Acct-Session-Time = 279
Event-Timestamp = "Jul 16 2012 11:03:04 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Acct-Unique-Session-Id = "10f8bce6e5e7eb41"
Timestamp = 1342461874
Request-Authenticator = Verified
Mon Jul 16 10:59:11 2012
Acct-Status-Type = Start
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Address = 26.0.0.7
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
Calling-Station-Id = "remote0"
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Event-Timestamp = "Jul 16 2012 10:58:24 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
ADSL-Agent-Circuit-Id = "cgn_1_ipoe"
ADSL-Agent-Remote-Id = "remote0"
Alc-Subsc-ID-Str = "CGN1"
Alc-Subsc-Prof-Str = "nat"
Alc-SLA-Prof-Str = "tp_sla_prem"
Alc-Client-Hardware-Addr = "00:00:65:05:10:01"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Acct-Unique-Session-Id = "9c1723d05e87c043"
Timestamp = 1342461551
Request-Authenticator = Verified
Mon Jul 16 11:03:51 2012
Acct-Status-Type = Interim-Update
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Address = 26.0.0.7
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
Calling-Station-Id = "remote0"
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Acct-Session-Time = 279
Event-Timestamp = "Jul 16 2012 11:03:04 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
ADSL-Agent-Circuit-Id = "cgn_1_ipoe"
ADSL-Agent-Remote-Id = "remote0"
Alc-Subsc-ID-Str = "CGN1"
Alc-Subsc-Prof-Str = "nat"
Alc-SLA-Prof-Str = "tp_sla_prem"
Alc-Client-Hardware-Addr = "00:00:65:05:10:01"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Alcatel-IPD-Attr-163 = 0x00000001
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00010000000000020468
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x0001000000000000052a
Alc-Acct-I-Inprof-Octets-64 = 0x00030000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00030000000000000000
Alc-Acct-I-Inprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-I-Inprof-Octets-64 = 0x00050000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00050000000000000000
Alc-Acct-I-Inprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000003154
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x0001000000000000009a
Alc-Acct-O-Inprof-Octets-64 = 0x00030000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00030000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-O-Inprof-Octets-64 = 0x00050000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00050000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00050000000000000000
Acct-Unique-Session-Id = "9c1723d05e87c043"
Timestamp = 1342461831
Request-Authenticator = Verified
Mon Jul 16 11:04:34 2012
Acct-Status-Type = Stop
NAS-IP-Address = 1.1.1.1
User-Name = "cgn_1_ipoe"
Framed-IP-Address = 26.0.0.7
Framed-IP-Netmask = 255.255.255.0
Class = 0x63676e2d636c6173732d7375622d6177617265
Calling-Station-Id = "remote0"
NAS-Identifier = "left-a20"
Acct-Session-Id = "D896FF0000000550045640"
Acct-Session-Time = 322
Acct-Terminate-Cause = User-Request
Event-Timestamp = "Jul 16 2012 11:03:47 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:5.10"
ADSL-Agent-Circuit-Id = "cgn_1_ipoe"
ADSL-Agent-Remote-Id = "remote0"
Alc-Subsc-ID-Str = "CGN1"
Alc-Subsc-Prof-Str = "nat"
Alc-SLA-Prof-Str = "tp_sla_prem"
Alc-Client-Hardware-Addr = "00:00:65:05:10:01"
Acct-Delay-Time = 0
Acct-Authentic = RADIUS
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x000100000000000248c4
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000005d9
Alc-Acct-I-Inprof-Octets-64 = 0x00030000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00030000000000000000
Alc-Acct-I-Inprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-I-Inprof-Octets-64 = 0x00050000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00050000000000000000
Alc-Acct-I-Inprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000003860
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x000100000000000000b0
Alc-Acct-O-Inprof-Octets-64 = 0x00030000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00030000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00030000000000000000
Alc-Acct-O-Inprof-Octets-64 = 0x00050000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00050000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00050000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00050000000000000000
Acct-Unique-Session-Id = "9c1723d05e87c043"
Timestamp = 1342461874
Request-Authenticator = Verified
Map and
Free logs are generated when the port-block for the subscribers are allocated and de-allocated.







