Securing the NFM-P
Overview
Nokia recognizes the importance of deploying important software such as the NFM-P in secure environments and, as such, supports the use of security techniques to enhance the security of the NFM-P.
NFM-P communications is secured using TLS 1.2 by default, SNMPv3 and HTTPS. See the NSP Installation and Upgrade Guide for configuration information.
NFM-P implements a number of safeguards to ensure protection of private data. Additional information can be found in the Security section of the NSP Installation and Upgrade Guide.
Nokia recommends performing the following steps to achieving NFM-P station security:
-
Install a clean operating system environment with the minimum required packages documented in the NSP Installation and Upgrade Guide.
-
Install the latest recommended patch cluster for RHEL. For customers using the Nokia provided RHEL OS image, these must be obtained directly from Nokia only. For customer sourced and manually deployed RHEL OS instances, the patches must be obtained from Red Hat.
-
Harden the RHEL operating system installation based upon the CIS Benchmarks best practices. Reference the NSP System Architecture Guide for the Recommendations and Compliance statements. The supported CIS Benchmark best practices are already implemented on the NSP RHEL OS images.
-
Implement firewall rules for NFM-P to control access to ports on NFM-P platforms as described in Deploying NFM-P with firewalls . NFM-P systems have no ingress or egress requirements to access the public internet and should be isolated with properly configured firewalls.
-
If installing RHEL, enable the RHEL firewall filter rules lists. See NFM-P firewall and NAT rules for more details
-
Installation of NFM-P with a secure configuration described in Installing the NFM-P components
-
Network element connection configuration as described in NFM-P network element communication
-
Configure NFM-P to run at runlevel 3 as opposed to the default runlevel 5
-
Update the supported TLS versions and ciphers to remove older versions, if not required
-
Consider using a Certificate Authority signed certificate instead of self-signed certificates
-
Use TLS certificates signed with stronger hashing algorithms
-
Enable SELinux in permissive/enforcing mode for the components that support it
-
Enable Federal Information Processing Standards (FIPS) security. Note that using FIPS and SNMPv3 algorithms larger than SHA1/AES128 will add CPU load and NE response times may be diminished.
Operating system installation for NFM-P stations
For customer sourced and manually deployed RHEL OS instances, Nokia supports customers applying RHEL patches provided by Red Hat which include security fixes as well as functional fixes. Nokia also supports customers applying Windows patches provided by Micorsoft. If a patch is found to be incompatible with the NSP, the patch may need to be removed until a solution to the incompatibility is provided by Red Hat or Nokia. See the NSP Release Notice for up-to-date information about the recommended RHEL maintenance update and patch levels.
For customers using the Nokia provided RHEL OS images, only the RHEL OS patch bundles provided by Nokia can be applied.
NFM-P is supported on RHEL installed with the list of required RHEL Packages documented in the NSP Installation and Upgrade Guide. SELinux is supported in both permissive and enforcing mode for most NSP components. Auxiliary databases support SELinux in permissive mode only.
Additional efforts to secure the system could impact NFM-P's operation or future upgrades of the product. Customers should perform some level of basic testing to validate additional platform hardening does not impact NFM-P's operation. The NFM-P Product Group makes no commitment to make NFM-P compatible with a customer's hardening requirements.
Installing the NFM-P components
Nokia recommends performing the following steps when installing the NFM-P components:
-
Configure the NFM-P server IP validation during the NFM-P database installation to ensure that only the specified IP address can communicate with the NFM-P database. This is documented in the NSP Installation and Upgrade Guide.
-
Maintain secure communication between the NFM-P server and NFM-P clients (XML-API and UI) as documented in the NSP Installation and Upgrade Guide. This is enabled by default.
Nokia also recommends the configuration (as documented in the NSP NFM-P User Guide) of the following options to secure communication with the NFM-P client UI and the NFM-P client XML API interfaces:
NFM-P network element communication
The following configurations are documented in the NSP NFM-P User Guide, and help secure communication between the network elements and NFM-P server installations:
Deploying NFM-P with firewalls
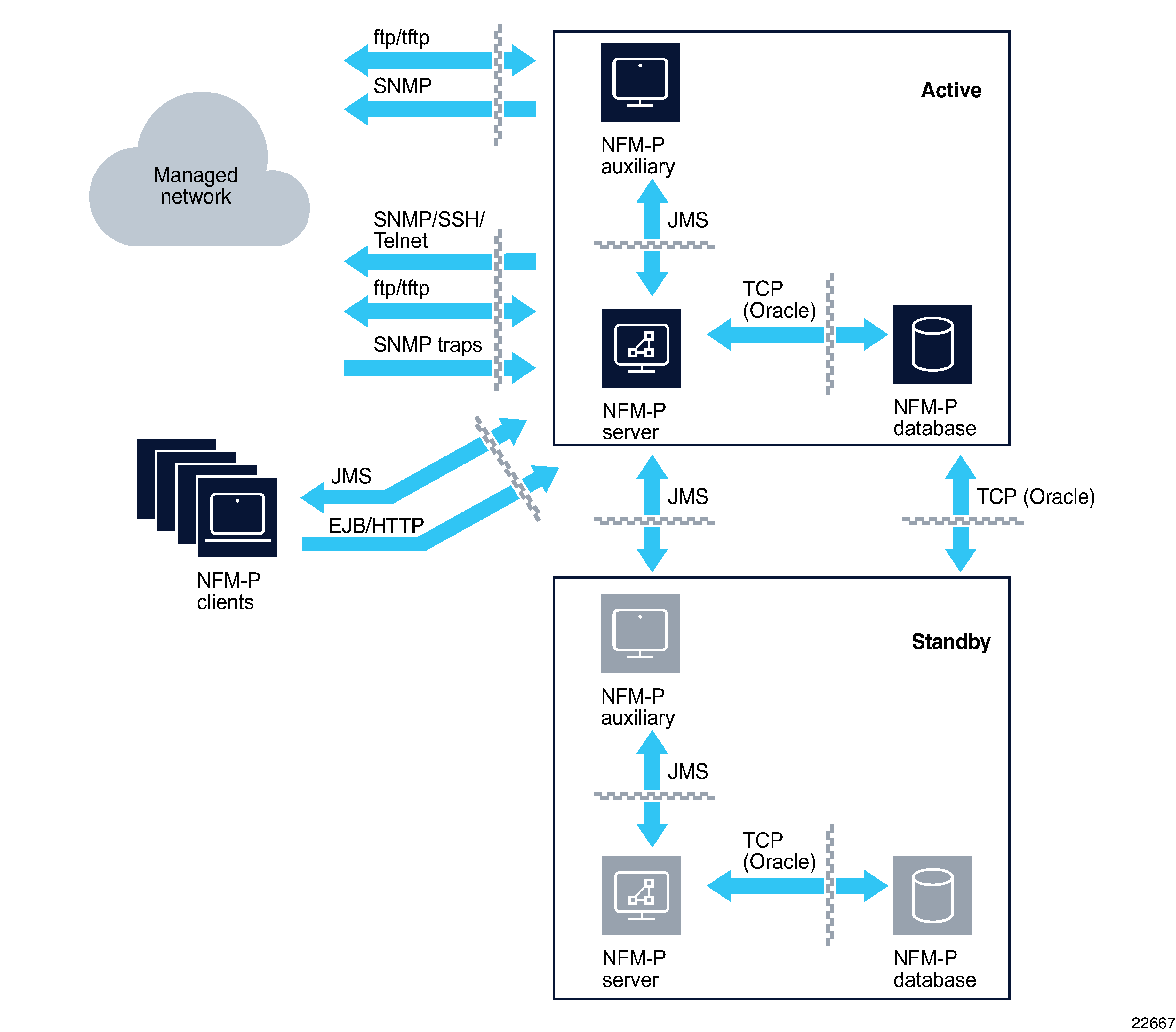
A firewall can be deployed to protect the NFM-P server from the managed network and to protect the server from the network hosting the NFM-P clients. The diagrams below illustrate this and show the communications services that are required through the firewalls. Installations of NFM-P can make use of the RHEL built in firewall using firewalld. Standalone Firewall products must not be collocated on servers hosting NFM-P components. Only the built-in RHEL firewall used to enable filter rules lists can be collocated with NFM-P components. See NFM-P firewall and NAT rules for more details.
Some NFM-P operations require idle TCP ports to remain open for longer periods of time. Therefore, customers using a firewall that closes idle TCP connections should adjust Operating System TCP keepalives to a value that ensures that the firewall will not close sockets in use by NFM-P.
For some of the network elements described in Network element specific requirements there is a requirement for the NFM-P GUI client to communicate directly with the network element using specialized configuration tools.
Figure 6-2: Firewalls and NFM-P standalone deployments
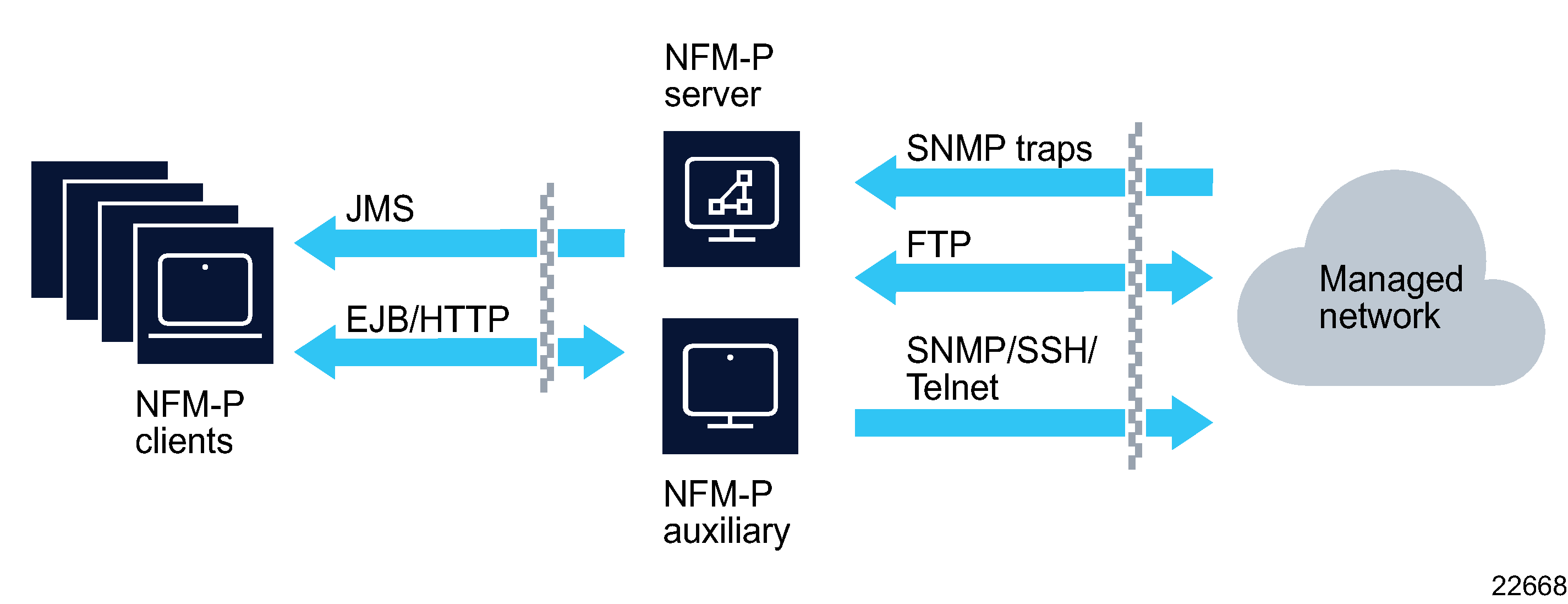
Figure 6-3: Firewalls and NFM-P redundant deployments