NFM-P authentication with embedded nspOS
Brute-force password protection
A brute-force password attack consists of submitting passwords over-and-over for the purpose of eventually guessing the correct one. NFM-P with embedded nspOS implements a login throttling mechanism to help mitigate brute-force password attacks. User login throttling limits the number of failed login attempts. Login throttling is enabled in NFM-P with embedded nspOS deployments, however, the throttling parameters are fixed (not configurable).
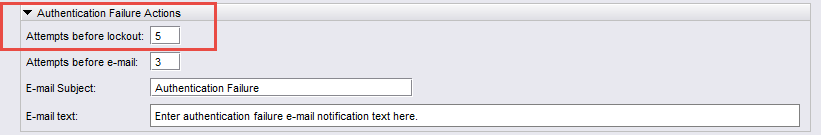
In NFM-P with embedded nspOS, a user account may be locked-out after a configurable number of consecutive failed login attempts is exceeded. The default number of attempts before lockout is five. This means that a user account is suspended on the sixth failed login attempt. The number of attempts before lockout can be configured in the Java GUI. When lockout occurs, the user account is suspended and the NFM-P administrator must reactivate. Additional details can be found in the NSP System Administrator Guide.
Figure 4-1: Authentication Failure Actions
Note: It is strongly recommended that an administrator configure the number of attempts before lockout threshold according to the company security policy. Setting the attempts before lockout parameter to 0 disables the lockout function, and is not recommended.
Local user authentication
NFM-P with embedded nspOS supports local authentication. When NFM-P local authentication is enabled, NSP authentication information is stored in the Oracle database. If local authentication is disabled in NFM-P, then NSP authentication is managed by the remote authentication server and NSP user authentication data is not stored locally.
Password storage (local users)
A one-way cryptographic hash is applied to all NSP user passwords stored in the NFM-P local database. This adds protection in the event of an accidental or intentional database disclosure since the original plaintext password cannot be recovered. To further mitigate against certain password attacks, a randomized salt is added to the user passwords before the one-way cryptographic hash is applied.
Password complexity
In an NSP system where local authentication is managed by NFM-P, user passwords must conform to the following rules:
-
It must contain at least 3 of the following 4:
-
Must not contain more than 3 consecutive instances of the same character.
-
Number of password changes before a password can be reused: 5
Note: NFM-P minimum password length is 8 characters which meets the current NIST 800-63 recommendations. However, length has been found to be a primary factor in characterizing password strength. Administrators with stricter password policies are encouraged to create passwords longer than 8 characters.
Remote user authentication
NFM-P user authentication and authorization can be accomplished via remote servers. NFM-P with embedded nspOS supports the following remote user access protocols:
If you intend to use LDAP for remote access, it is strongly recommended that you use only a server that uses secure LDAP, or LDAPS.
Administrators can use NFM-P Remote Authentication Manager to configure the protocols and define the authentication order for users. For example, if you specify an order of RADIUS, LDAP, local, the NFM-P tries to authenticate each remote user via RADIUS; if the RADIUS servers are unavailable, the NFM-P tries LDAP, and upon failure tries to match the user credentials to a local NFM-P account.
Configuration for remote authentication is available through the NFM-P Java GUI under Administration→Security→NFM-P Remote User Authentication from the NFM-P main menu. Details can be found in the NSP System Administrator Guide.
Session controls
For NFM-P with embedded nspOS, the maximum number of concurrent sessions can be configured for admin users and clients in the nms-server.xml configuration file:
max5620SAMAdminSessions: maximum number of concurrent admin operator positions (Default: 5)
See the NSP System Administrator Guide for more information.
© 2023 Nokia. Nokia Confidential Information
Use subject to agreed restrictions on disclosure and use.