The triple play service delivery architecture
Overview
The triple play service delivery architecture (TPSDA) is based on three major components, as shown in the figure below:
Figure 70-13: TPSDA components
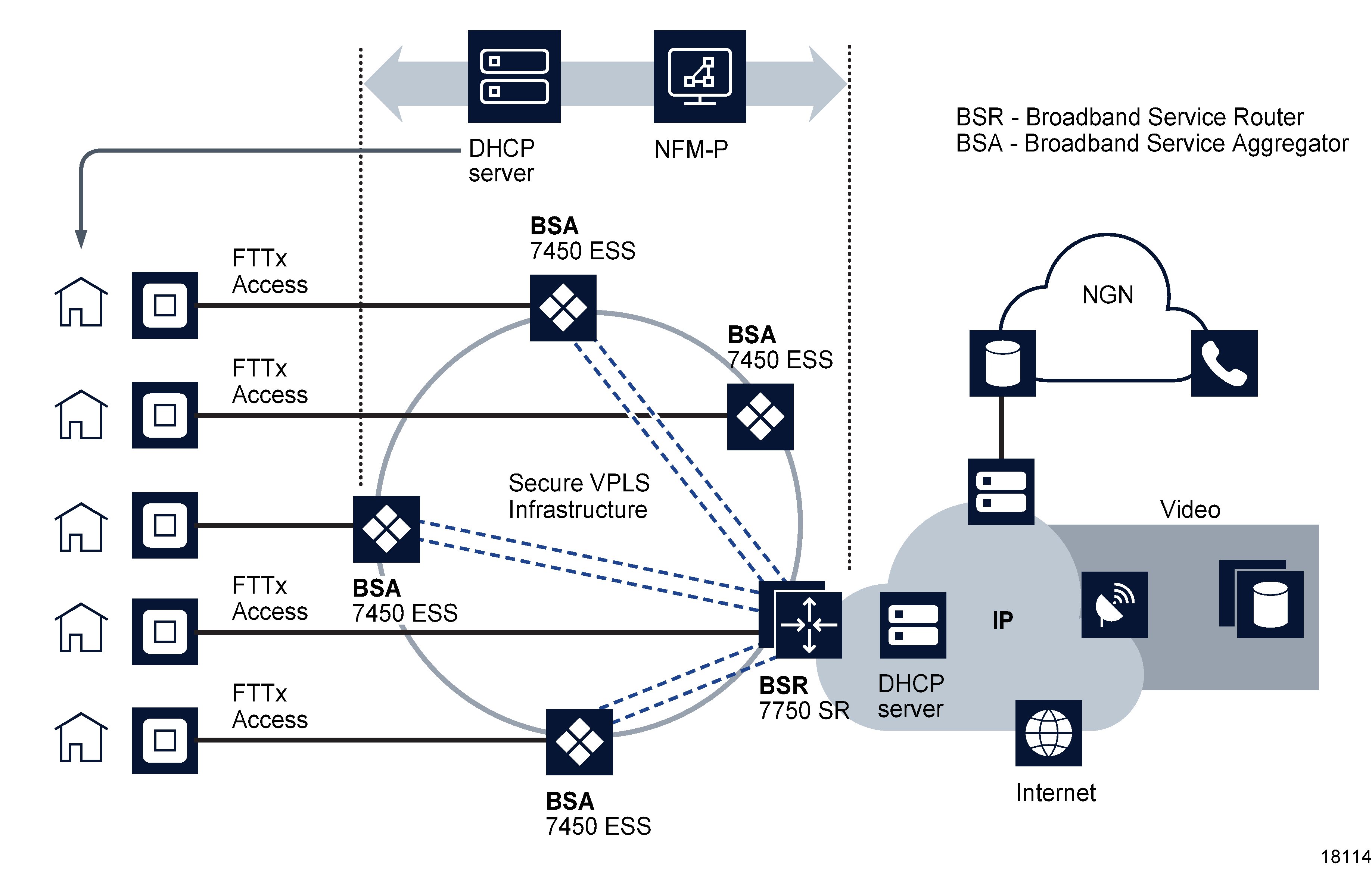
The table below lists the Nokia TPSDA product components.
Table 70-3: Product components of the TPSDA
|
Product |
Role |
Notes |
|---|---|---|
|
NFM-P |
Provides network, service, and policy management across the TPSDA architecture, including a unified interface for element management and simple service activation and monitoring. |
— |
|
7750 SR |
BSR |
Support per-service and per-content type differentiation of QoS levels and supports distribution of multicast traffic. |
|
7450 ESS |
BSA |
Aggregate traffic from DSLAMs and other FTTx access devices that are connected to end-user residential gateways. |
DSLAMs or other access NEs are connected to Ethernet access ports on the broadband service aggregator. Typically, a single VLAN for each customer is set up between the access NE and the BSA. This a configuration enables the application of consistent per-customer policies, such as QoS, filtering, and accounting, to be applied on the BSA.
Scaling of traffic and services is done by dividing L2 and L3 functions between the BSA and the BSR. The BSA aggregates traffic over Gigabit Ethernet ports and performs per-customer service queuing, scheduling, accounting and filtering, as described later in this chapter. The BSR terminates L2 access and routes over IP/MPLS with support for all protocols, including multicasting. Time of day QoS policies can be applied using NFM-P policy management.
Interconnectivity between BSAs and BSRs is provided by VPLS. VPLS instances can be automatically established using hub-and-spoke or ring topologies. Both can be configured and sites added to the VPLS using the NFM-P. Regardless of the fiber plant layout, VPLS enables a full mesh between all sites that are receiving and distributing customer traffic in the TPSDA, ensuring efficient transport and protection from NE or fiber failures.
VPLS also provides mechanisms for traffic security, including residential split horizon groups in which direct user bridging is prohibited; ARP and broadcast suppression; DHCP-populated MAC and IP address filtering to prevent denial or service and theft of service using DHCP snooping, and RADIUS or TACACS+ authentication.