RCA audit policies overview
Introduction
The CPAM allows you to perform on-demand verifications of the IP/MPLS configuration of ISIS and OSPF routing protocols on NFM-P-managed NEs. RCA audit policies identify problems or errors in protocol-related and control plane configurations. These configuration problems, if not discovered in a timely manner, can have significant effects on higher layers, such as MPLS and VPN.
Note: An NFM-P user that is assigned the Administrator or RCA Verification scope of command role can create, modify, and execute all of the RCA audit policies. The results of an RCA audit are associated with the object, not the user.
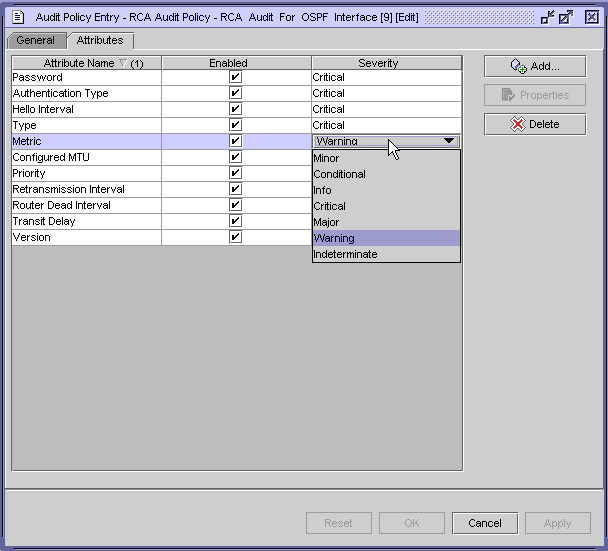
You can create RCA audit policies for IGP administrative domains to verify the configuration of network objects on NFM-P-managed routers. For each audit policy that you create, you can specify one or more policy entries that define the scope of configuration that is verified by the audit and the severity of the related problem, as displayed in the figure below. For example, an RCA audit policy on an OSPF interface verifies the configuration of several default attributes, such as the configured MTU and Hello interval. A problem with the specified severity is raised against the IGP administration domain for ISIS misconfigurations, the OSPF area for OSPF misconfigurations, and the ISIS or OSPF interface for interface misconfigurations, and so on, depending on the policy entry.
Figure 15-1: Audit policy entry form—Attribute and problem severity
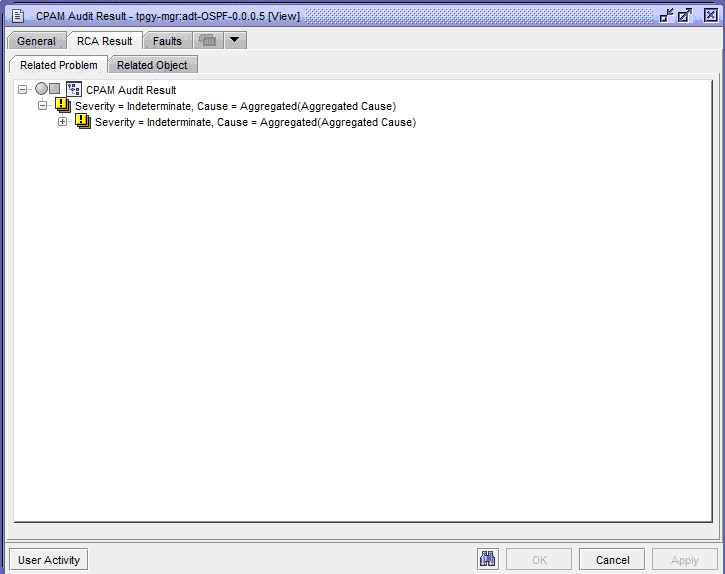
The results of the verification are displayed in two components trees: the problem tree and the object tree. You can expand the problem tree to view the problem type and other objects affected by the same problem, as displayed in the following figure:
Figure 15-2: RCA audit—problem tree
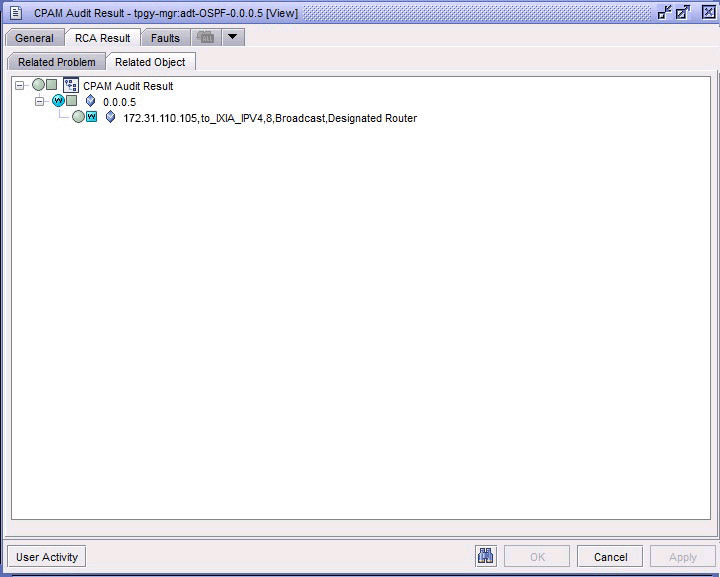
You can expand the object tree to view all of the problems that are associated with the selected object, as displayed in the figure below. You can also view RCA audit results on the properties form of an OSPF or ISIS interface or routing instance.
Figure 15-3: RCA audit—object tree
In addition to the attributes that you specify in an RCA audit policy, the CPAM verifies the following for each protocol:
-
-
the administrative state of the corresponding ISIS router interface
-
whether the ISIS instance is L1 and the ISIS interface is L2
-
whether the ISIS instance is L2 and the ISIS interface is L1
-
whether the ISIS instance is L1 (L1/L2) and the ISIS interface is L2 (l1/L2) and missing an ISIS area
-
whether the ISIS interface is L1 and (L1/L2) and the far-end ISIS interface is L1 (L1/L2) and missing a common area
-
whether the ISIS instance is L1 and the far-end ISIS interface is L2
-
whether the ISIS instance is L2 and the far-end ISIS interface is L1
-
© 2024 Nokia. Nokia Confidential Information
Use subject to agreed restrictions on disclosure and use.