Communication between the NSP and external systems
Overview
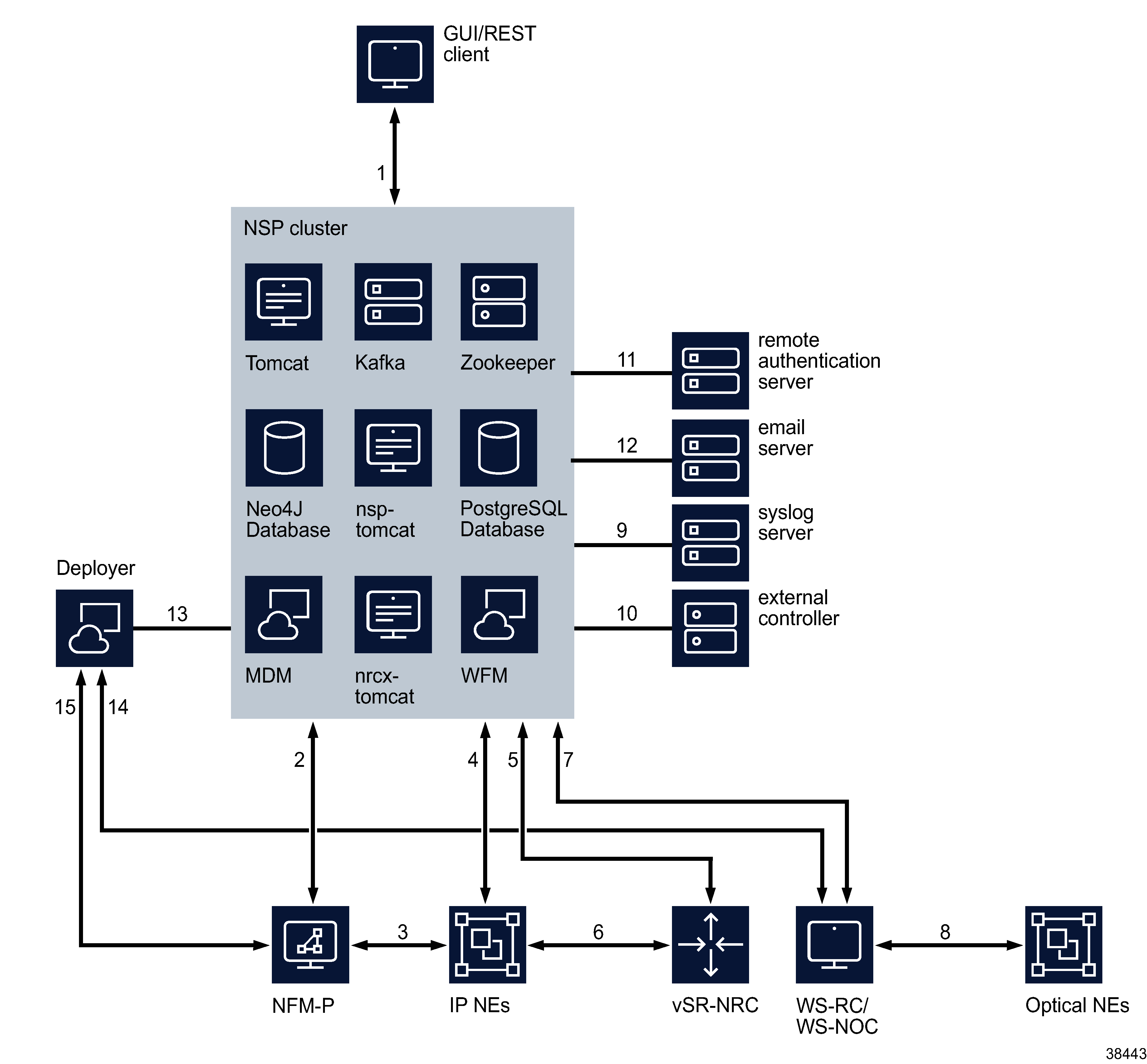
The following diagrams illustrate the various components of the NSP and its internal communications, as well as communications with external systems.
The following figure shows a standalone NSP deployment and its communications with external systems.
Figure 6-1: Standalone NSP deployment
|
Connection |
Usage |
|---|---|
|
1 |
Web Client/REST API client connections. REST over HTTPS secured with TLS |
|
2 |
SSO authentication (secure), zookeeper registration (secure), neo4j database (non-secure), kafka (secure), NFM-P API (secure), Data connection – CPROTO protocol secured with TLS |
|
3 |
NE mediation using SNMP and FTP/SCP |
|
4 |
NE mediation using gRPC/gNMI, SNMP, NETCONF, SSH, ICMP |
|
5 |
Data connection – CPROTO (non-secure) |
|
6 |
BGP-LS (supports GTSM), PCEP (secured by TLS), OpenFlow communications (secured by TLS) * Note |
|
7 |
SSO authentication (secure), zookeeper registration (secure), REST over HTTPS secured with TLS, proprietary HTTP with WS-NOC |
|
8 |
NE mediation with SNMP and TL-1 |
|
9 |
syslog notifications secured with TLS |
|
10 |
Mediator communications with external controller, REST/RESTCONF secured with TLS |
|
11 |
LDAP, RADIUS, TACACS communications with remote authentication servers |
|
12 |
SMTP, SMTPS, STARTTLS communication with email server |
|
13 |
Kubernetes and NSP software installation and upgrade |
|
14,15 |
NFM-P and WS-NOC communications with deployer PKI server |
Note: VSR-NRC supports secure PCEP and OpenFlow communications in specific releases. See the SR OS documentation for details.