SecGW Drop Dashboard
SecGW Drop Dashboard overview
The SecGW Drop Dashboard shows the AA firewall packet-drop activity on selected AA partitions.
Use cases
Network security monitoring—Use the report to monitor network threats and identify potential attacks.
Policy verification—Use the report to ensure that policies are not dropping legitimate traffic.
Dashboard characteristics
The following table lists the principal dashboard characteristics.
Table 5-2: SecGW Drop Dashboard characteristics
Example
The following figures show the dashlets that the dashboard contains.
Figure 5-9: Top GTP Filter Drop dashlet
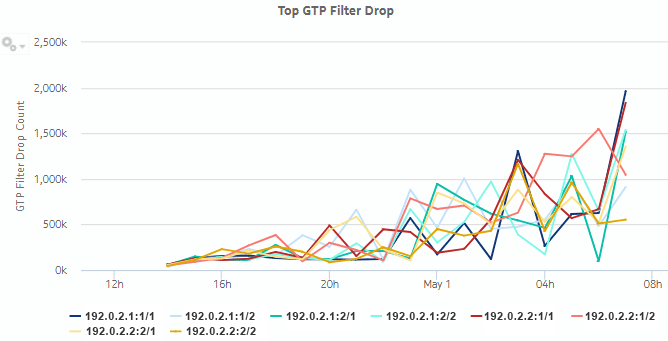
Figure 5-10: Top GTP Filter Drop drill-down
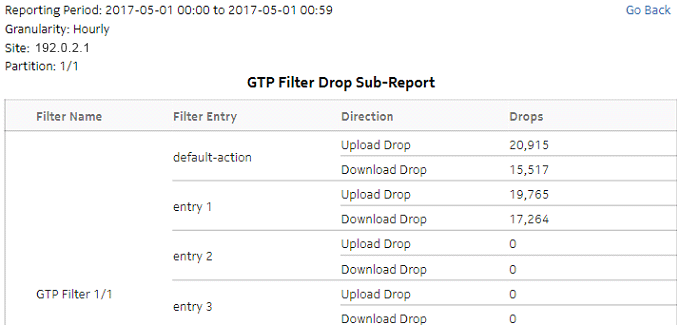
Figure 5-11: Top SCTP Filter Drop dashlet
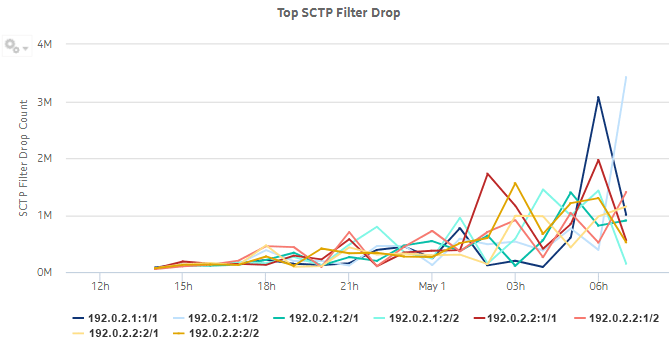
Figure 5-12: Top SCTP Filter Drop drill-down
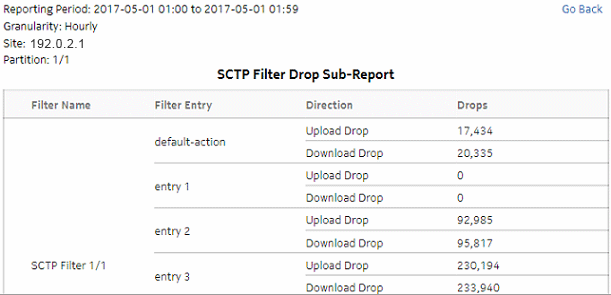
Figure 5-13: Top Session Filter Drop dashlet
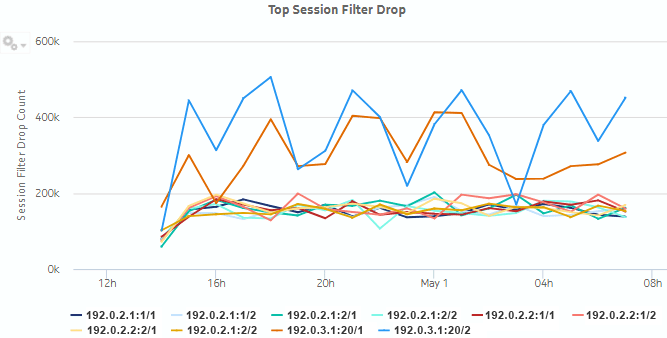
Figure 5-14: Top Session Filter Drop drill-down
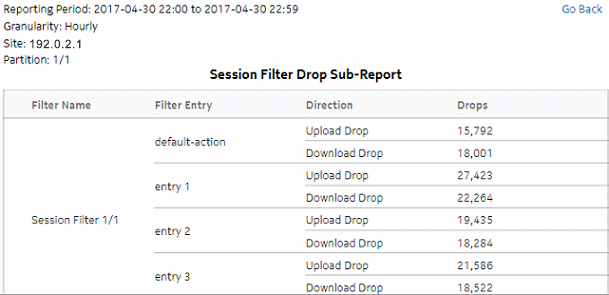
Figure 5-15: Top Policer Drop dashlet
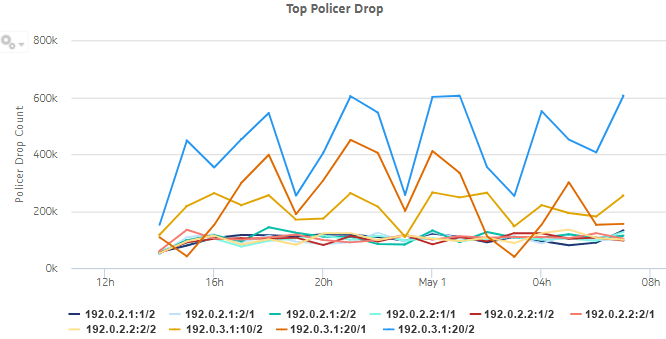
Figure 5-16: Top Policer Drop drill-down
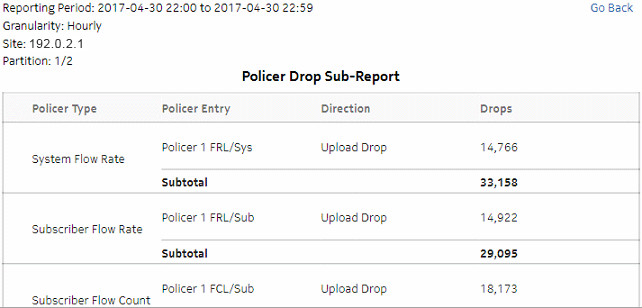
Figure 5-17: Top Anomaly Drop dashlet
Figure 5-18: Top Anomaly Drop drill-down
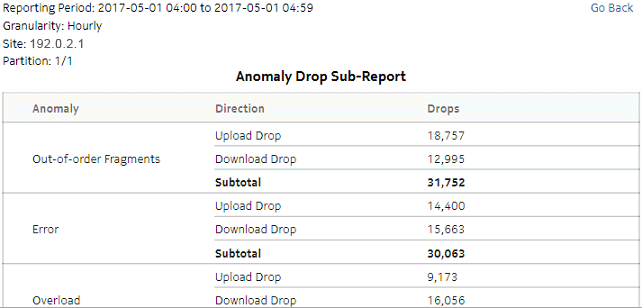
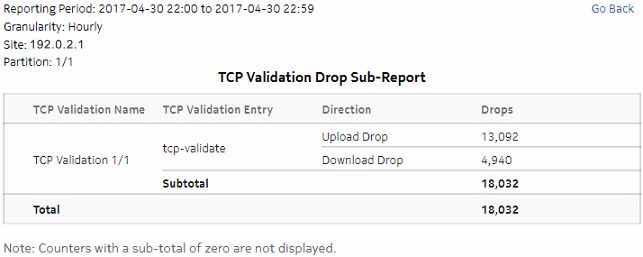
Figure 5-19: Top TCP Validation Drop dashlet
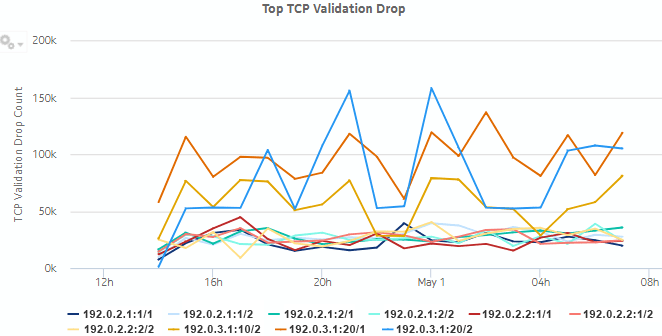
Figure 5-20: Top TCP Validation Drop drill-down