What is User Access Control?
Overview
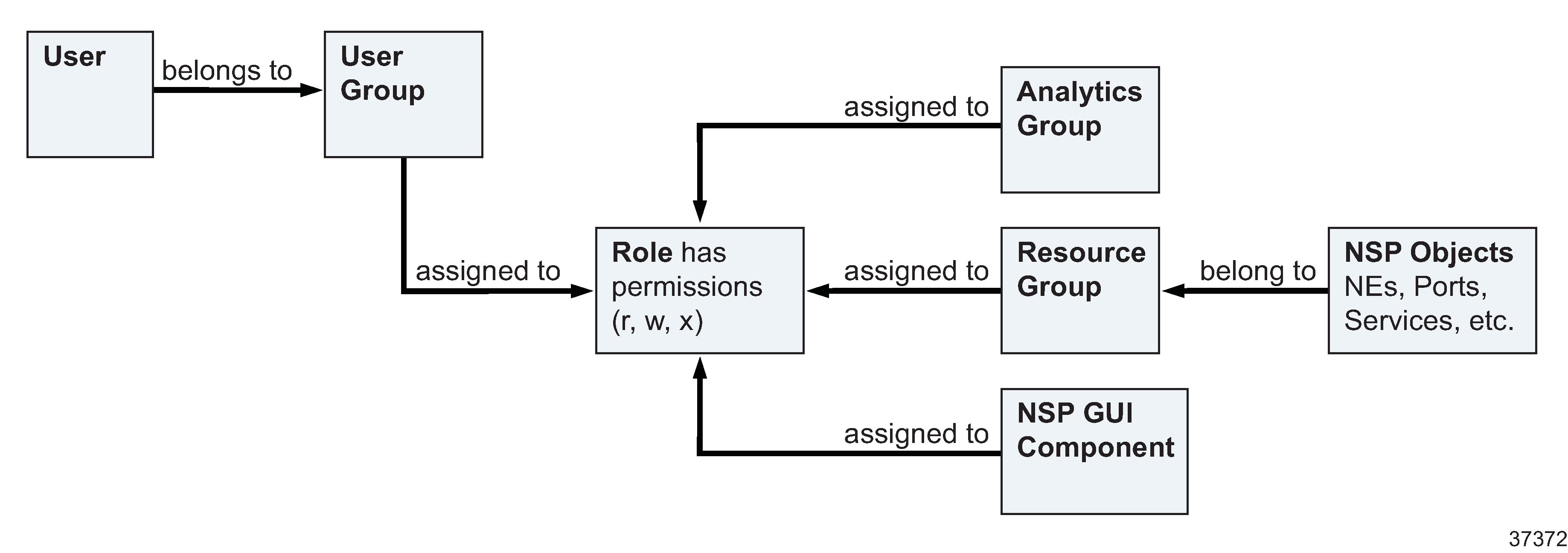
User Access Control (UAC) defines what commands a user can perform in an NSP system and what objects those commands can be performed on. NSP UAC is defined through role definitions that are assigned to user groups, and each user is associated with one user group.
In an NSP deployment, UAC applies to a user when accessing NSP function. NSP users that access NFM-P or WSNOC will have access determined by what is configured for that user group in NFM-P or WSNOC applications. (eg. An NSP user accessing NFM-P will have access to the NFM-P scope and span profiles that belong to the user’s NFM-P user group).
NSP User Access Control is disabled by default, meaning that users can access any NSP function that is not restricted by a specific user group requirement. Users that belong to the admin user group can access all function, including admin-only functions. Users that do not belong to the admin user group can access all non-admin applications. A user that does not belong to the admin user group but has a system administrator role privilege will not be able to access admin-only functions.
When NSP UAC is enabled, the role definitions belonging to an NSP user group determine the NSP functions and commands a user can access, and which network objects the user can access.
In CLM deployments, UAC applies to CLM users.
When UAC is enabled, access is assigned at the NSP level and applies across the NSP GUI. Users will see their specified NSP access permissions enforced when they login to NSP. The user access configuration specified in NSP is enforced in place of any pre-existing access control setup (from NFM-P or WS-NOC). Local NSP user access to NSP resources is always controlled through NSP, regardless of whether UAC is enabled or not.
As a network evolves, an NSP administrator must create or modify user groups, roles, and resource groups to provide the required user access to NSP functions. Be aware of functional cross-dependencies.
When UAC is enabled, it controls user access to NSP functions independently of the user management systems in NFM-P or WS-NOC.
UAC does not apply to WS-NOC or NFM-P GUI or OSS client sessions if pre-existing user access control mechanisms are in use. If you maintain your NSP user accounts in an NFM-P user database, all NFM-P functions related to user lifecycle management, such as password expiry time or failed-login lockout, also affect NSP user access. Local NSP user accounts are configured for UAC and lifecycle management entirely within the NSP.
Figure 8-1: User Access Control architecture
Roles
A role object specifies which resources and NSP functions its associated user groups can access. Network resource access is assigned to a role through resource groups, while functional access and Analytics resource access are specified directly on a role object.
NSP administrator role
A predefined NSP administrator role, user group, and admin user account are automatically created during NSP system installation and cannot be modified. The admin user has full access to all NSP functions and resources, and can define the roles and resource groups that are assigned to user groups. The admin user can create additional roles with the Administrator designation, which carries the same unlimited functional and resource access.
User groups
A user group associates a group of NSP users with one or more roles, thereby enabling user access to functional areas and resources. Administrators create user groups and assign roles to them, according to the type of network activities the user group is meant to perform. When a role is assigned to a user group, all users within the group have the same access to resources and functions, as specified on the role. A user group can be assigned multiple roles to allow broader access rights for its users.
Individual NSP users can be created by external authentication sources (NFM-P, LDAP, RADIUS, TACACS) where users are assigned to corresponding user groups. In order for the members of a user group to have access to NSP resources and functions, the user group name returned by the authentication source must exactly match a corresponding user group name in NSP.
Local NSP users and user groups can also be created in the NSP.
Users requiring WS-NOC access require a user group assignment that maps to a predefined WS-NOC role; for information, see To map external user groups to predefined WS-NOC roles in the NSP Installation and Upgrade Guide.
Resource groups
A resource group is a collection of network equipment or services which can be assigned to a role. The role is assigned to a user group, thereby granting the user group access to the network resources in the resource group. Resource groups are defined in Map Layouts and Groups.