L2TP for Subscriber Access — LAC
This chapter provides information about L2TP for subscriber access.
Topics in this chapter include:
Applicability
This chapter describes L2TP Access Concentrator (LAC) support for the L2TP Access Aggregation (LAA) architecture model and was initially written for SR OS Release 11.0.R4. The CLI in the current edition is based on Release 16.0.R7. PPP hosts are supported in a Routed CO model (with IES or VPRN services) using ATM, Ethernet or Ethernet over Pseudowire SAPs. A description of the L2TP Tunnel Switch (LTS) and L2TP Network Server (LNS) functions are out of the scope of this chapter.
Overview
PPP access architectures
The Broadband Forum proposes two architectures for point-to-point protocol (PPP) access.
The PPP terminated aggregation architecture (PTA)
The L2TP access aggregation architecture (LAA)
The PTA architecture (local-access model) uses the Broadband Network Gateway (BNG) to terminate user PPP sessions (see scenario PPPoE-5 in PPP access architectures).
The LAA architecture (which is a tunneled access model) uses a LAC and an LNS to transport PPP sessions from the LAC to the LNS which performs tunnel termination (see scenario PPPoE-1 and PPPoE -2 in PPP access architectures).
Optionally, an LTS can be used in the transport network to perform the grooming of traffic between tunnels (see scenarios PPPoE-3 and PPPoE-4 in PPP access architectures).
The LNS is the logical termination point of the PPP sessions originated by the remote clients and tunneled by the LAC/LTS.
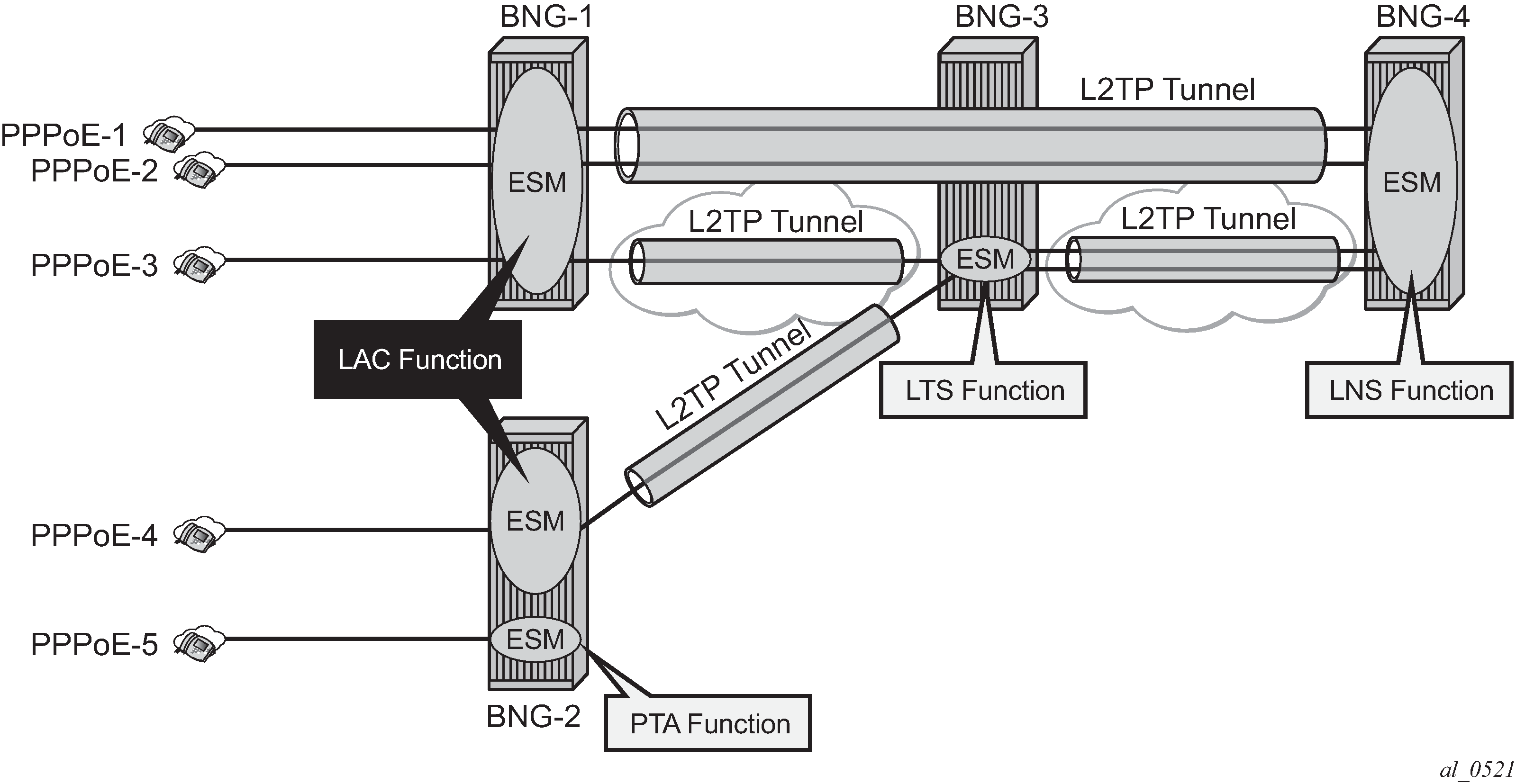
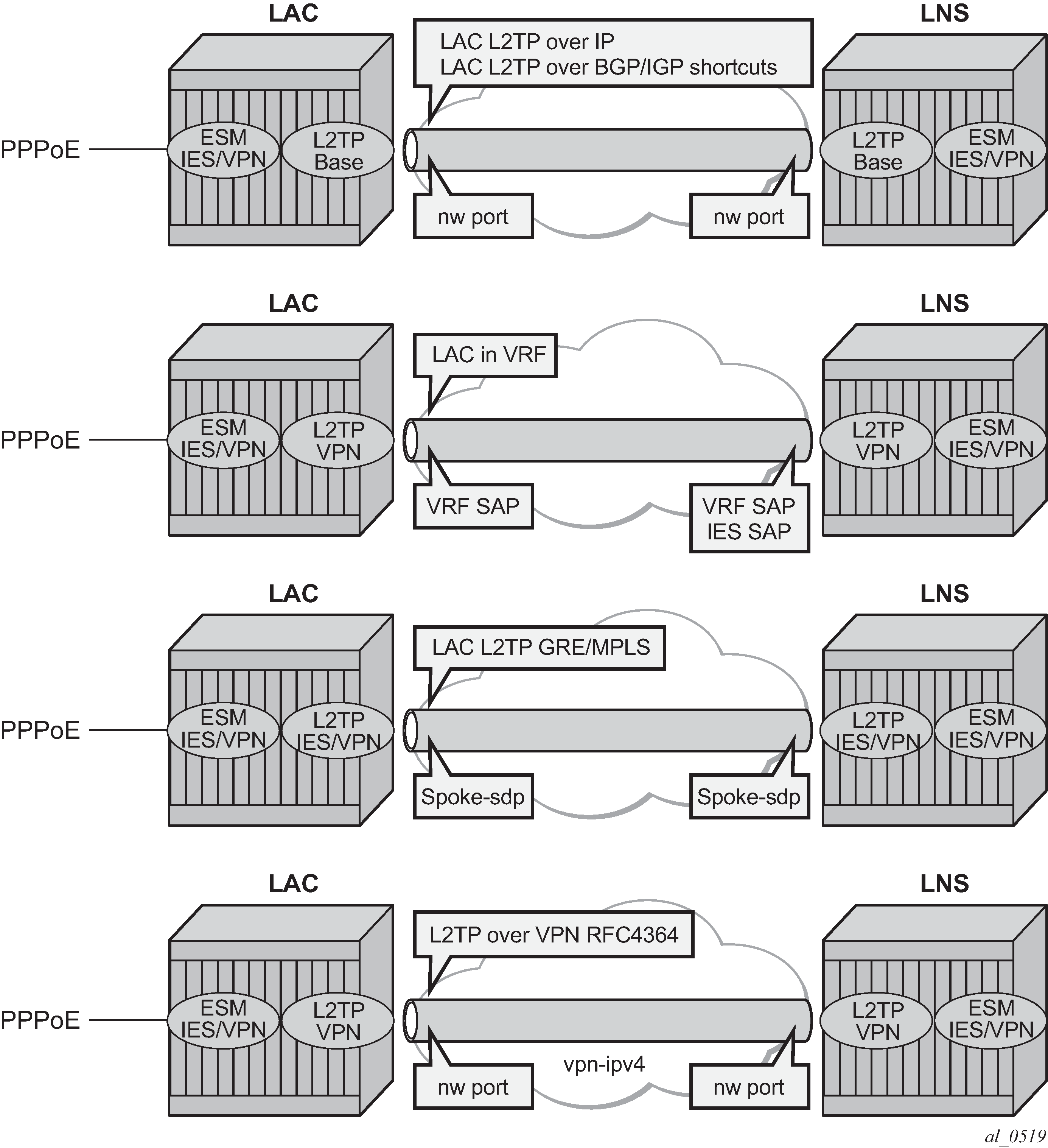
L2TP tunnels - LAC and LNS reachability options
The router instance where the L2TP tunnel starts and where ESM is handled can be one and the same, but does not need to be the same. The LNS peer address can be reachable via IP, BGP/IGP shortcuts, over a spoke SDP (GRE/MPLS), RFC 4364 VPRNs, but cannot be an address belonging to a directly connected interface. See Supported LT2P reachability options.
Recapitulation of the L2TPv2 protocol
L2TPv2 is a client-server protocol relying on UDP and encapsulates Layer 2 packets such as PPP for transmission across a network. L2TPv2 passes control and data messages over separate control and data channels, thus defines following message types:
Control messages—The in-band control channel passes sequenced control messages, supporting connection management, call management, error reporting, and session control. Optionally, a shared-secret challenge authentication method can be used between the tunnel endpoints.
The following messages are used for L2TP tunnel management:
Tunnel setup (control connection management)
Start-control-connection-request (SCCRQ)
Start-control-connection-reply (SCCRP)
Start-control-connection-connected (SCCCN)
Stop-control-connection-notification (StopCCN)
Tunnel keepalive
Hello
The following messages are used for L2TP session (call) management:
Session setup over an existing tunnel
Incoming-call-request (ICRQ)
Incoming-call-reply (ICRP)
Incoming-call-connected (ICCN)
Call-disconnect-notify (CDN)
Zero-length body (ZLB) messages are control packets with an L2TP header only and are used to explicitly acknowledge packets, making the control channel reliable.
L2TP message encoding is done through attribute value pairs (AVP).
Data messages — Data messages encapsulate the PPP frames that are sent into the L2TP tunnel.
L2TPv2 sessions run over an L2TP tunnel and are referenced by an L2TP session-id. An L2TP tunnel can carry none, one, or multiple L2TP sessions. An L2TP session corresponds to a PPPoE session. L2TPv3 for LAC-LNS dynamic tunnel setup is not supported.
L2TP header and AVP layout
The L2TPv2 header consists of following fields (RFC 2611):
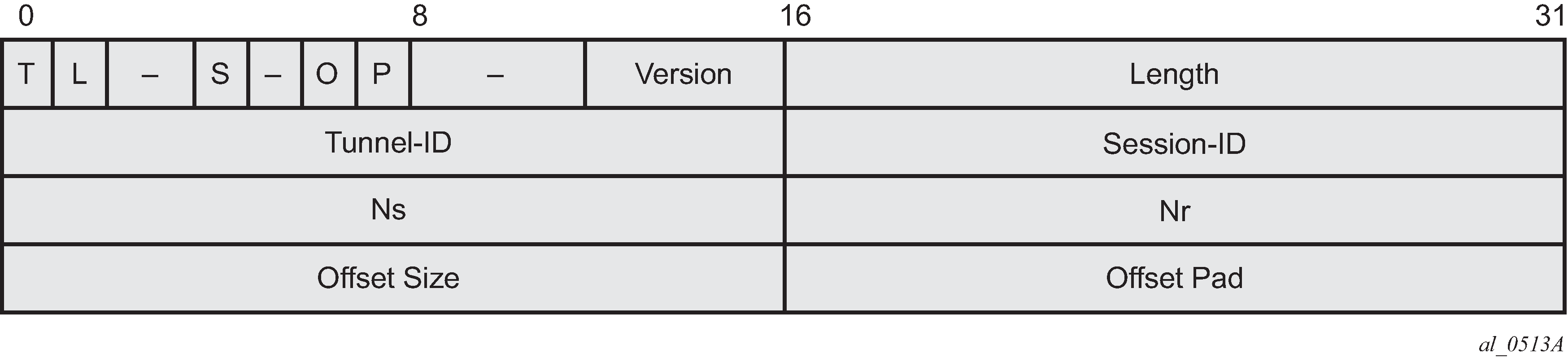
Field |
Description |
|---|---|
T |
Type of L2TP message (1 bit): 0—data message 1—control message |
L |
Indicates if the optional Length field is present in the message (1 bit): 0—the field is left out of the message entirely 1—the field is included (must be included in control messages) |
- |
Reserved for future use, must be set to zero. |
S |
Indicates if the Ns and Nr fields are present (1 bit): 0 — the fields are left out of the message; entirely 1 — the fields are included (must be included in control messages) |
O |
Indicates if the Offset field is present (1 bit): 0 — the field is left out of the message entirely (must be left out of control messages); 1 — the field is included |
P |
Used with data messages only. Indicates priority of the data message (1 bit): 0 — no (this value is used for all control messages); 1 — yes |
Version |
The version of the message (4 bits): 2 — this is the latest version of the L2TP data message header; 1 — indicates an L2F packet as described in RFC 2341. Packets with an unknown version number are discarded. |
Length |
The total length (in bytes) of the L2TP message (16 bits). |
Tunnel-ID |
Identifies the L2TP tunnel (that is, the control connection).This number has local significance — each end gives the same tunnel different tunnel IDs. The ID refers to the receiver, not the sender, and is assigned during tunnel creation (16 bits). |
Session-ID |
Identifies the PPP session within a tunnel. This number has local significance — each end gives the same session different session IDs. The ID refers to the receiver, not the sender, and is assigned during session creation (16 bits). |
Ns |
The sequence number of the message. This is mandatory for control messages (to enable re-transmission of lost messages) but optional for data messages (to re-order data messages that were mis-sequenced during forwarding). The number, which starts at 0 and increments by 1, is assigned by an L2TP peer for each session in a tunnel (16 bits). |
Nr |
The sequence number of the next control message expected to be received. This is equal to the sequence number of last received control message plus 1. Used by the receiving peer to ensure that control messages are sent in order without duplication. In data messages, the field (if present as indicated by the S bit) is ignored (16 bits). |
Offset Size |
The location of the L2TP payload, expressed as the number of octets from the start of the message header (16 bits). |
Offset pad |
User-defined bytes used to pad the message header so that the payload starts at the location indicated by the Offset Size field (16 bits). |
The AVP header consists of following fields (RFC 2611):
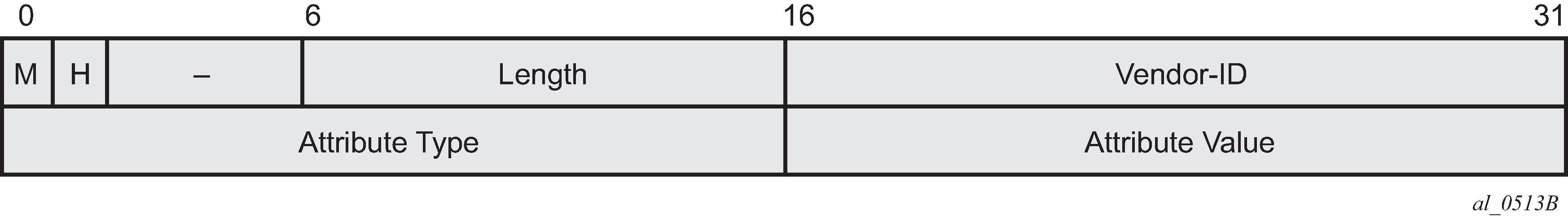
Field |
Description |
|---|---|
M |
Mandatory bit — If the M bit is set on an unrecognized AVP within a message associated with a particular session, the session associated with this message MUST be terminated (1 bit). |
H |
Hidden bit — Identifies the hiding of data in the Attribute-Value field of an AVP. This capability can be used to avoid the passing of sensitive data, such as user passwords, as clear text in an AVP. The H-bit MUST only be set if a shared secret exists between the LAC and LNS. The shared secret is the same secret that is used for tunnel authentication. If the H-bit is set in any AVP(s) in a given control message, a Random Vector AVP must also be present in the message and MUST precede the first AVP having an H bit of 1 (1 bit). |
- |
Reserved for future use, must be set to zero (4 bits). |
Length |
Indicates the total number of bytes (including the overall length and bitmask fields) contained in this AVP (10 bits). |
Vendor-id |
Any vendor wishing to implement their own L2TP extensions can use their own Vendor ID along with private Attribute values. Vendor-ID=0 means that the standard AVPs are used (2 bytes). |
Attribute type |
A value with a unique interpretation across all AVPs defined under a given Vendor (2 bytes). |
Attribute value |
This is the actual value as indicated by the Vendor ID and Attribute Type (2 bytes). |
RADIUS-triggered tunnel/session setup without LNS renegotiation
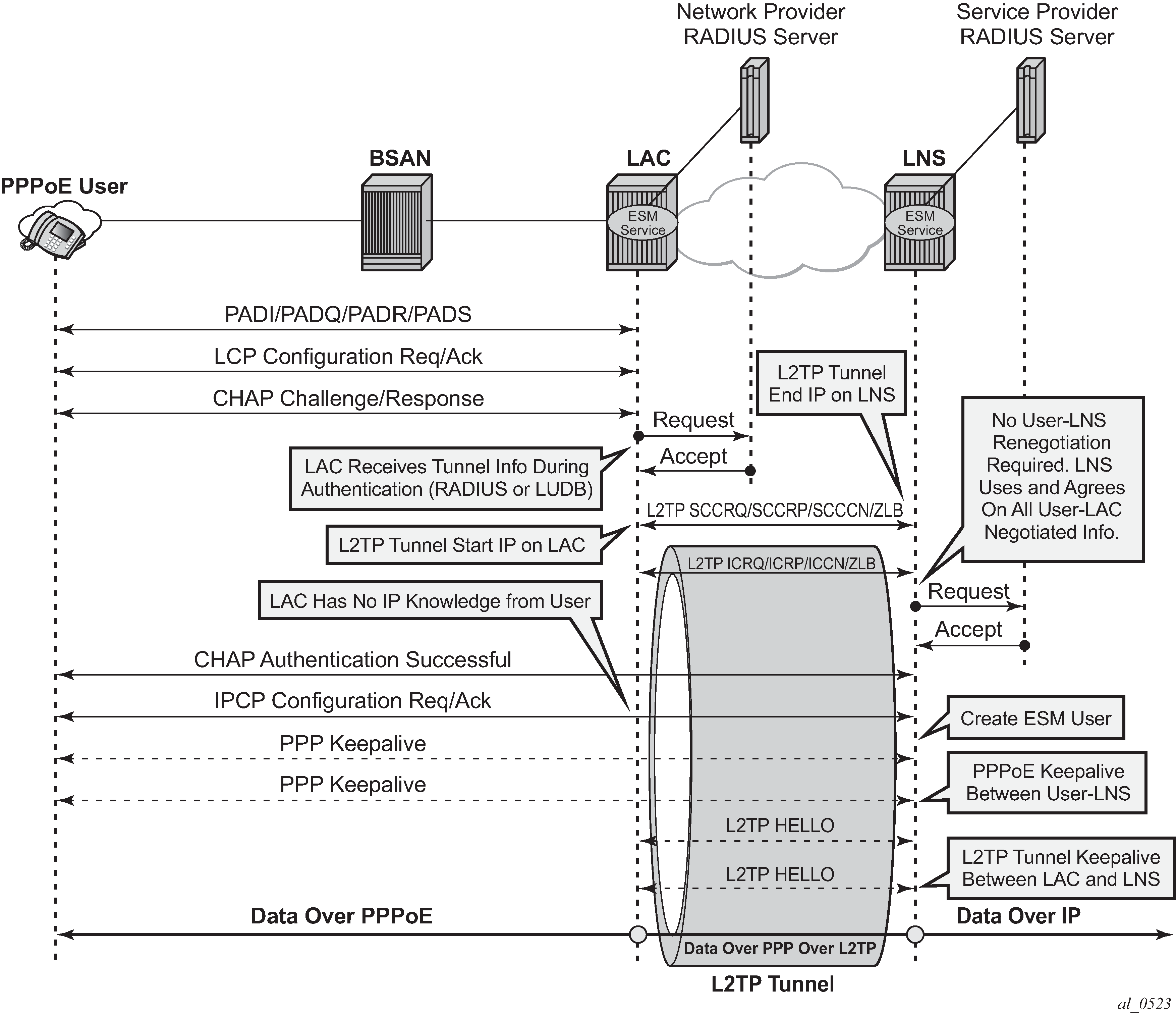
RADIUS-triggered tunnel/session setup without LNS renegotiation depicts the complete PPP session setup, using RADIUS authentication on both LAC and LNS. After the discovery phase (PADI/PADO/PADR/PADS) and LCP negotiation phase (LCP config_request/ack), the LAC initiates the L2TP tunnel setup based on RADIUS authentication information (RADIUS request/accept) and includes the negotiated PPP user-LAC information (called LCP proxy information). The LNS replies directly with a successful CHAP authentication if it agrees with the received proxy information. IP negotiation (IPCP config_request/ack) is handled between the user and the LNS, and the LAC has no IP knowledge of this PPP session.
RADIUS-triggered tunnel/session setup with LNS renegotiation
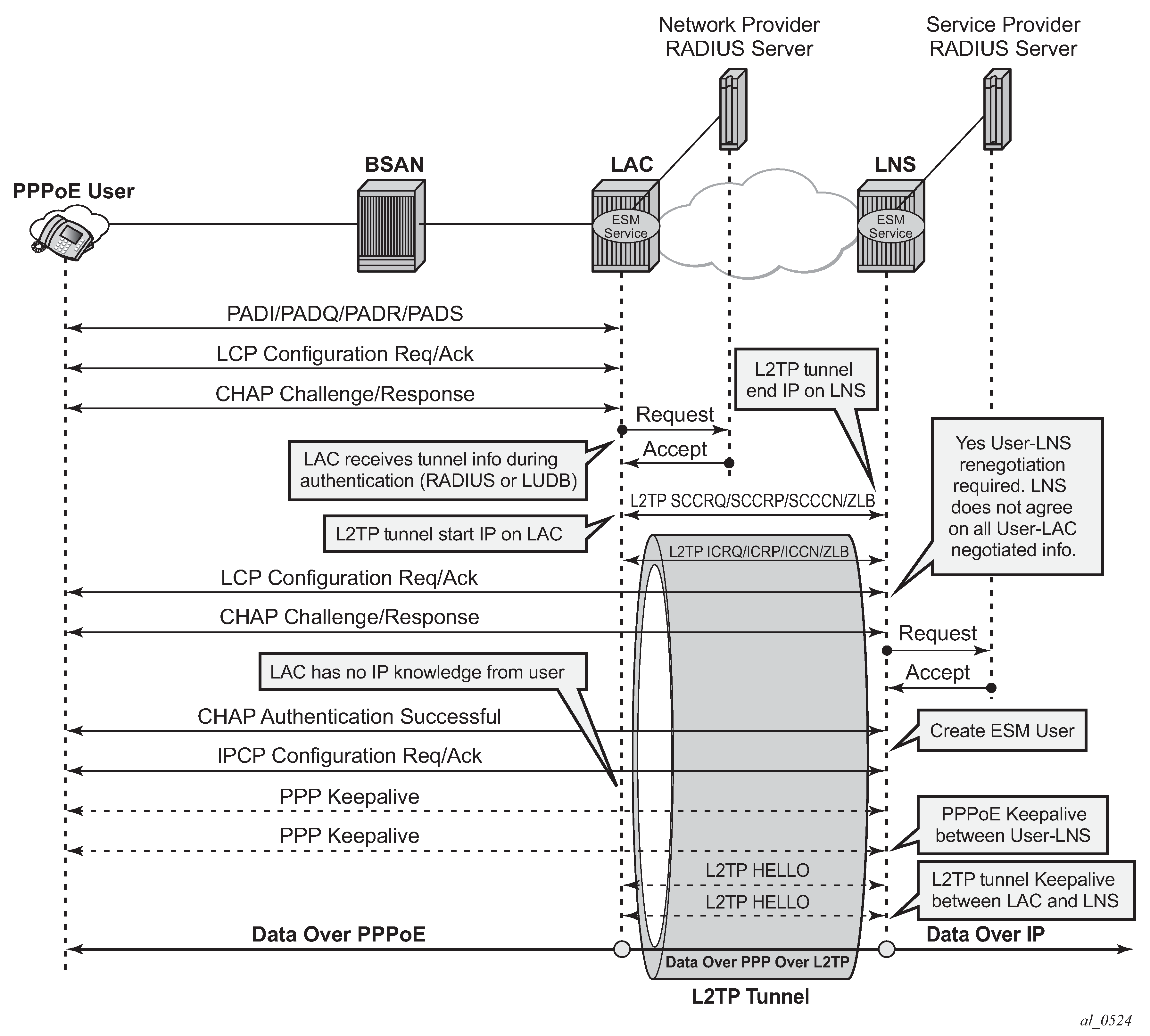
RADIUS-triggered tunnel/session setup with LNS renegotiation shows the scenario where the LNS does not agree with the received LCP proxy information and (re)starts the LCP phase (LCP config_request/ack) directly with the PPP user. The rest of this scenario is the same as shown in RADIUS-triggered tunnel/session setup without LNS renegotiation.
Running multiple PPP sessions over a single L2TP tunnel
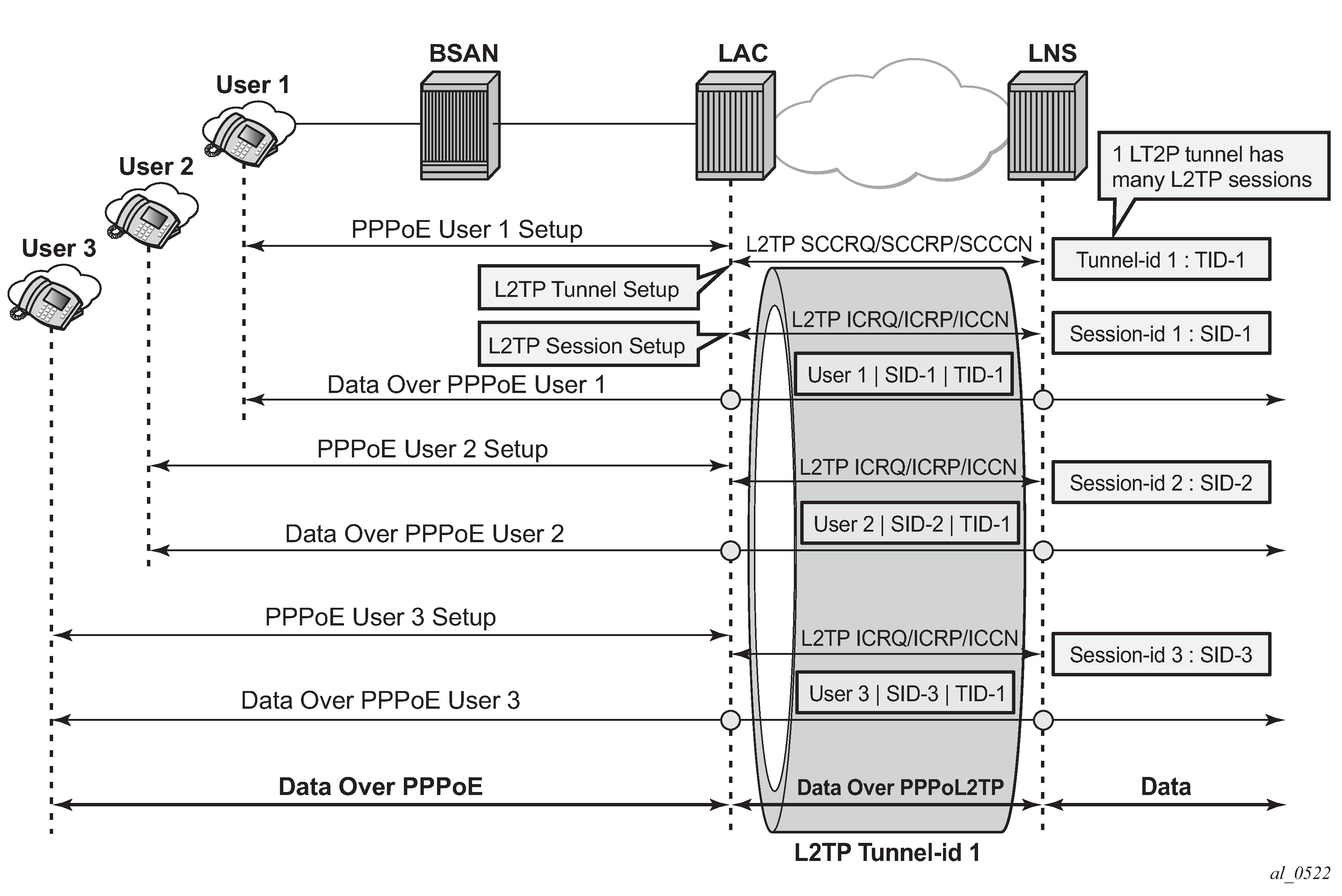
Running multiple PPP sessions over a single L2TP tunnel shows multiple PPP sessions tunneled over a single L2TP Tunnel. The LAC encapsulates each PPP session with a different L2TP session-id (SID) but with the same L2TP Tunnel-id (TID).
PPP user-initiated release/terminate
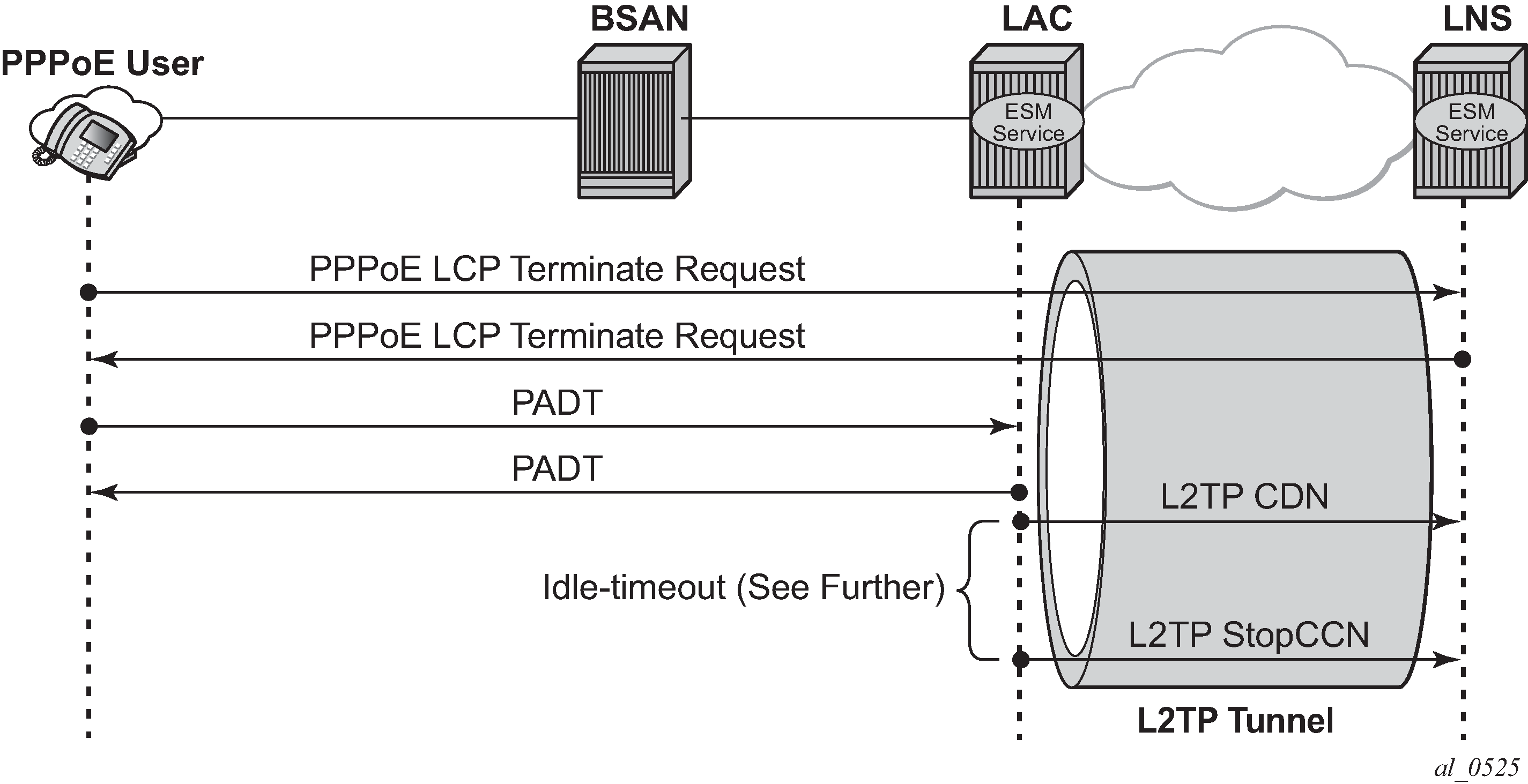
PPP user-initiated release/terminate shows the user initiated terminate_request tunneled by the LAC followed by the user initiated PADT terminated on the LAC. The LAC informs the LNS about the termination of the session via the L2TP CDN message. The L2TP tunnel can be optionally (idle-timeout) terminated via the L2TP StopCCN message.
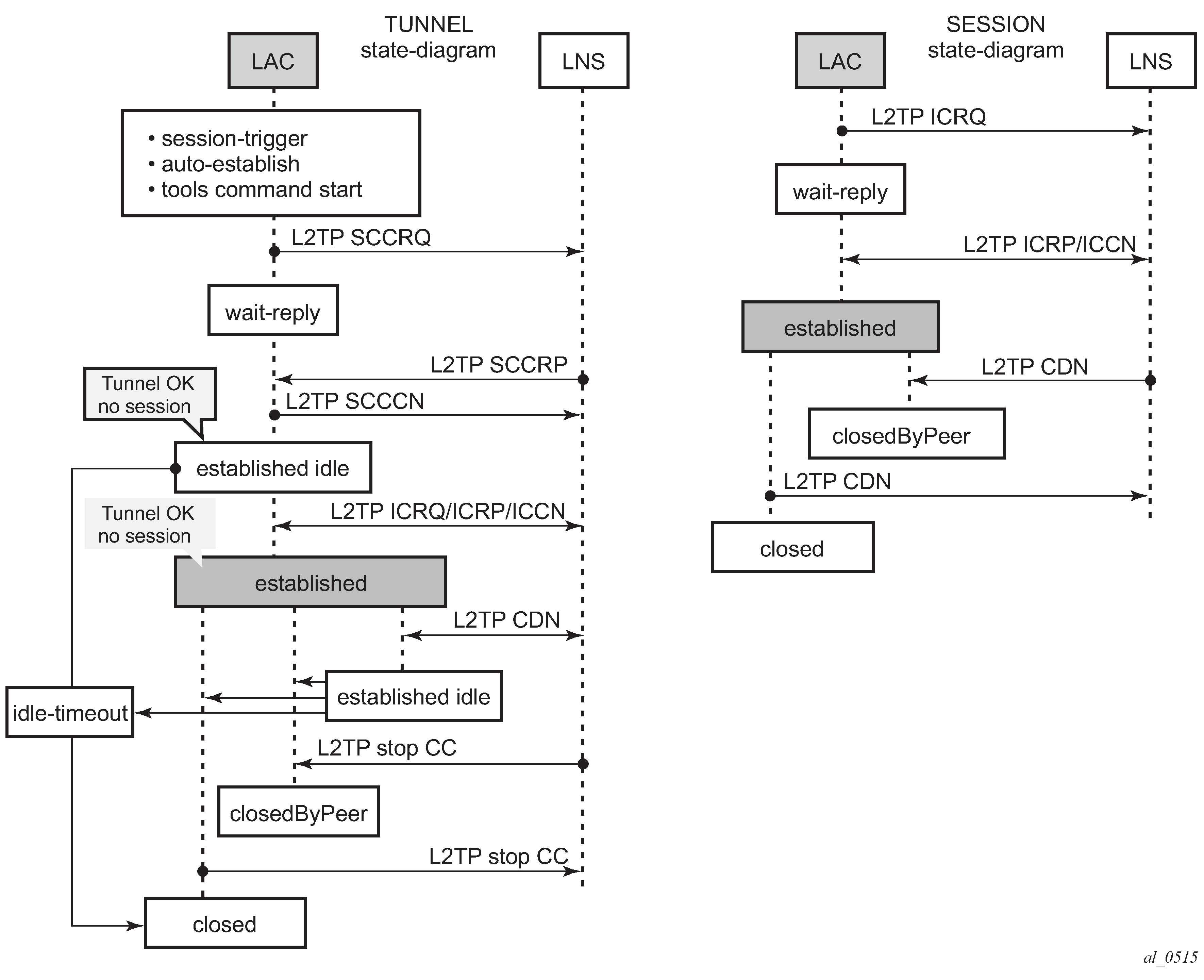
L2TP tunnel/session state diagram
L2TP tunnel and session state diagram gives an overview of the main L2TP tunnel and session states. An L2TP tunnel in the establishedIdle state is a tunnel without sessions. A tools command (see Advanced topics) can put an L2TP tunnel in a draining state (this prevents adding new sessions on tunnel but leaves the current sessions intact) or in a drained state (moved from draining to drained when all sessions terminated). The draining and drained state are not shown in the state diagram.
The L2TP tunnel setup occurs first with the triggers being: session activation, auto-establish, and a tools start command (see the Advanced topics section). An L2TP session setup trigger is always session based.
Configuration
Scenario 1: RADIUS-derived L2TP parameters
In the first scenario, the LAC receives an incoming connection and contacts the LAC RADIUS server. The RADIUS server retrieves the attributes for the user's domain (for example @wholesale.com) and passes the tunnel attributes to the LAC. Based on these RADIUS provided tunnel attributes, the LAC selects or initiates a new tunnel to the LTS or directly to the LNS. Once the tunnel is established, the LNS authenticates the end user using its own RADIUS server. Configuring the LNS and the LTS are out of the scope of this example.
In a RADIUS driven L2TP setup, either all or some of the required L2TP attributes are returned via RADIUS. If the RADIUS server only returns the L2TP [67] Tunnel-Server-Endpoint attributes, then the L2TP tunnel/session is established using the ‛l2tp node parameter values’ for the other required L2TP parameters. The ‛l2tp node parameters’ are defined under the configure router/service l2tp hierarchy. If the RADIUS server does not return all of the L2TP attributes and the node values are not configured, then the system falls back to default settings for these L2TP parameters.
The standard and vendor specific [26-6572] L2TP RADIUS attributes are listed in the tables below, together with the corresponding l2tp node parameters and defaults.
Attribute ID |
Attribute Name |
Mandatory |
CLI Node Parameter |
Corresponding Defaults |
|
|---|---|---|---|---|---|
64 |
Tunnel-Type |
Y |
- |
- |
- |
65 |
Tunnel-Medium-Type |
Y |
- |
- |
- |
66 |
Tunnel-Client-Endpoint:[0-31] |
N |
local-address |
no local-address |
system-ip |
67 |
Tunnel-Server-Endpoint |
N |
- |
- |
- |
69 |
Tunnel-Password |
N |
password |
no password |
- |
82 |
Tunnel-Assignment-ID:0 |
N |
- |
- |
default_radius_group |
82 |
Tunnel-Assignment-ID:[1..31] |
N |
- |
- |
Unnamed |
83 |
Tunnel-Preference |
N |
preference |
no preference |
50 |
90 |
Tunnel-Client-Auth-ID |
N |
local-name |
no local-name |
system-name |
91 |
Tunnel-Server-Auth-ID |
N |
- |
- |
- |
26-6527 |
Attribute Name |
Mandatory |
CLI Node Parameter |
Corresponding Defaults |
|
|---|---|---|---|---|---|
-46 |
Alc-Tunnel-Group |
N |
- |
- |
- |
-47 |
Alc-Tunnel-Algorithm |
N |
session-assign-method |
no session-assign-method |
existingFirst |
-48 |
Alc-Tunnel-Max-Sessions:0 |
N |
- |
group-session-limit |
131071 |
-48 |
Alc-Tunnel-Max-Sessions:[1..31] |
N |
- |
tunnel-session-limit |
32767 |
-49 |
Alc-Tunnel-Idle-Timeout |
N |
idle-timeout |
no idle-timeout |
Infinite |
-50 |
Alc-Tunnel-Hello-Interval |
N |
hello-interval |
no hello-interval |
300 sec |
-51 |
Alc-Tunnel-Destruct-Timeout |
N |
destruct-timeout |
no destruct-timeout |
60 sec |
-52 |
Alc-Tunnel-Max-Retries-Estab |
N |
max-retries-estab |
no max-retries-estab |
5 |
-53 |
Alc-Tunnel-Max-Retries-Not-Estab |
N |
max-retries-not-estab |
no max-retries-not-estab |
5 |
-54 |
Alc-Tunnel-AVP-Hiding |
N |
avp-hiding |
no avp-hiding |
Never |
-97 |
Alc-Tunnel-Challenge |
N |
challenge |
no challenge |
Never |
-104 |
Alc-Tunnel-Serv-Id |
N |
- |
- |
Base |
-120 |
Alc-Tunnel-Rx-Window-Size |
N |
receive-window-size |
no receive-window-size |
64 |
-144 |
Alc-Tunnel-Acct-Policy |
N |
radius-accounting-policy |
no radius-accounting-policy |
- |
Base router hosted LAC with single endpoint/single tunnel
Using the mandatory L2TP RADIUS attributes (see the following RADIUS user file) the LAC initiates an L2TP tunnel. The source address for the tunnel is the IPv4 address of a loopback interface in the base router system (LAC tunnel endpoint).The destination for the tunnel is defined by the Tunnel-Server-Endpoint RADIUS attribute [67], and is also known as the peer tunnel LNS endpoint address.
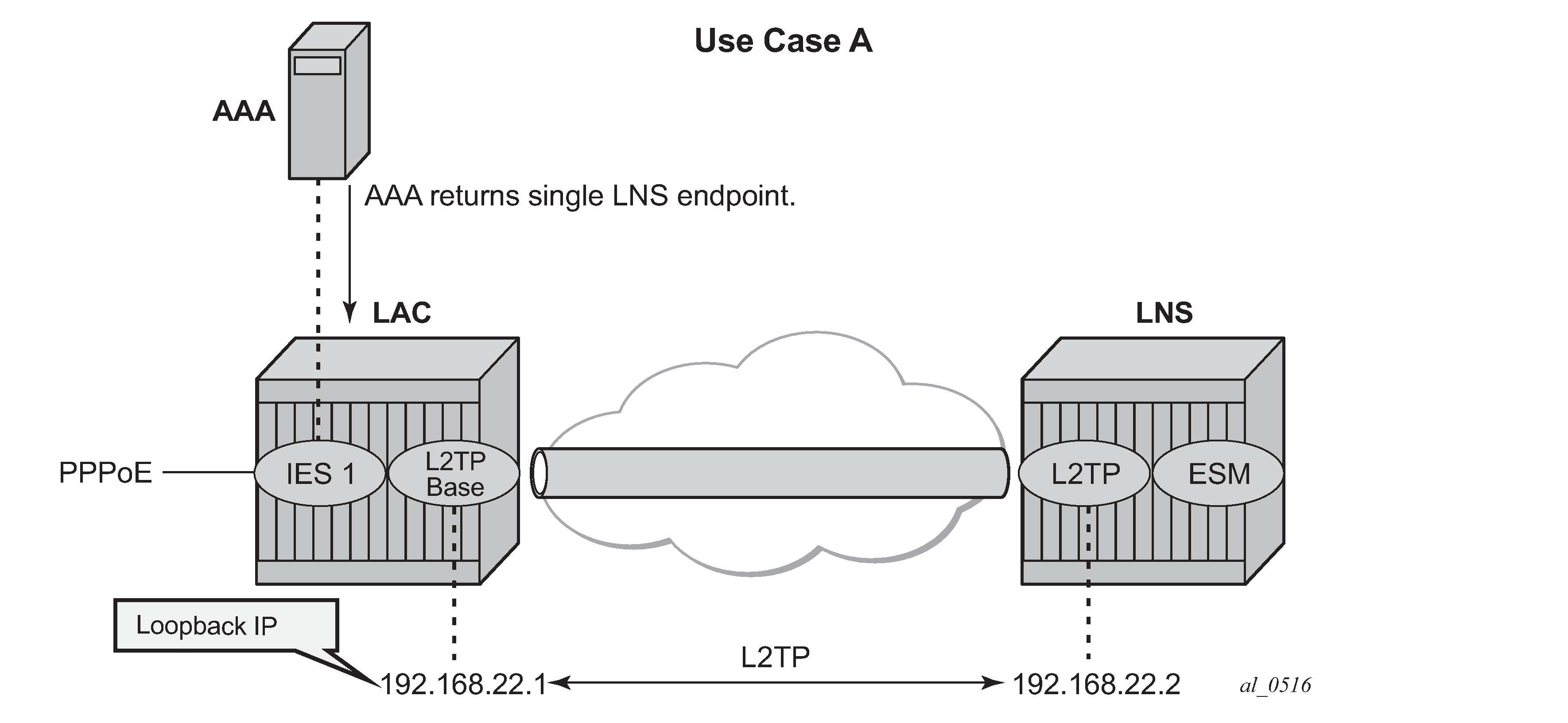
The PPPoE user terminates on IES service 1, sap 1/1/3:100, and is authenticated via RADIUS authentication-policy authentication-1 which provides wholesale/retail (L2TP) information.
configure
service
ies 1 customer 1 create
subscriber-interface "sub-l2tp" create
unnumbered "system"
group-interface "grp-l2tp" create
authentication-policy "radius-1"
sap 1/1/3:100 create
sub-sla-mgmt
sub-ident-policy "all-subscribers"
multi-sub-sap 1000
no shutdown
exit
exit
pppoe
sap-session-limit 10
no shutdown
exit
exit
exit
no shutdown
exit
exit
exit
The excerpt from the FreeRADIUS users file below shows the attributes to be returned.
user1@wholesale.com Cleartext-Password := "letmein", NAS-Identifier == "LAC"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1",
Tunnel-Type:1 += L2TP,
Tunnel-Medium-Type:1 +=IP,
Tunnel-Server-Endpoint:1 += 192.168.22.2,
L2TP is enabled (no shutdown) in the related service instance.
The L2TP tunnel is set up in the base instance and not in a VRF because the attribute Alc-Tunnel-Serv-Id is not returned from RADIUS.
Missing L2TP parameters are taken from defaults defined in the router l2tp context.
configure router l2tp
calling-number-format "%S %s" # L2TP AVP 22 format
# Default format ‛system-name sap-id’
---snip---
no local-name # default name equals system-name
no max-retries-estab # default value equals 5
---snip---
no shutdown # enable L2TP
This scenario shows the PPPoE session termination (base IES service 1) and the L2TP tunnel setup in the base router instance.
Base router hosted LAC with multiple endpoints
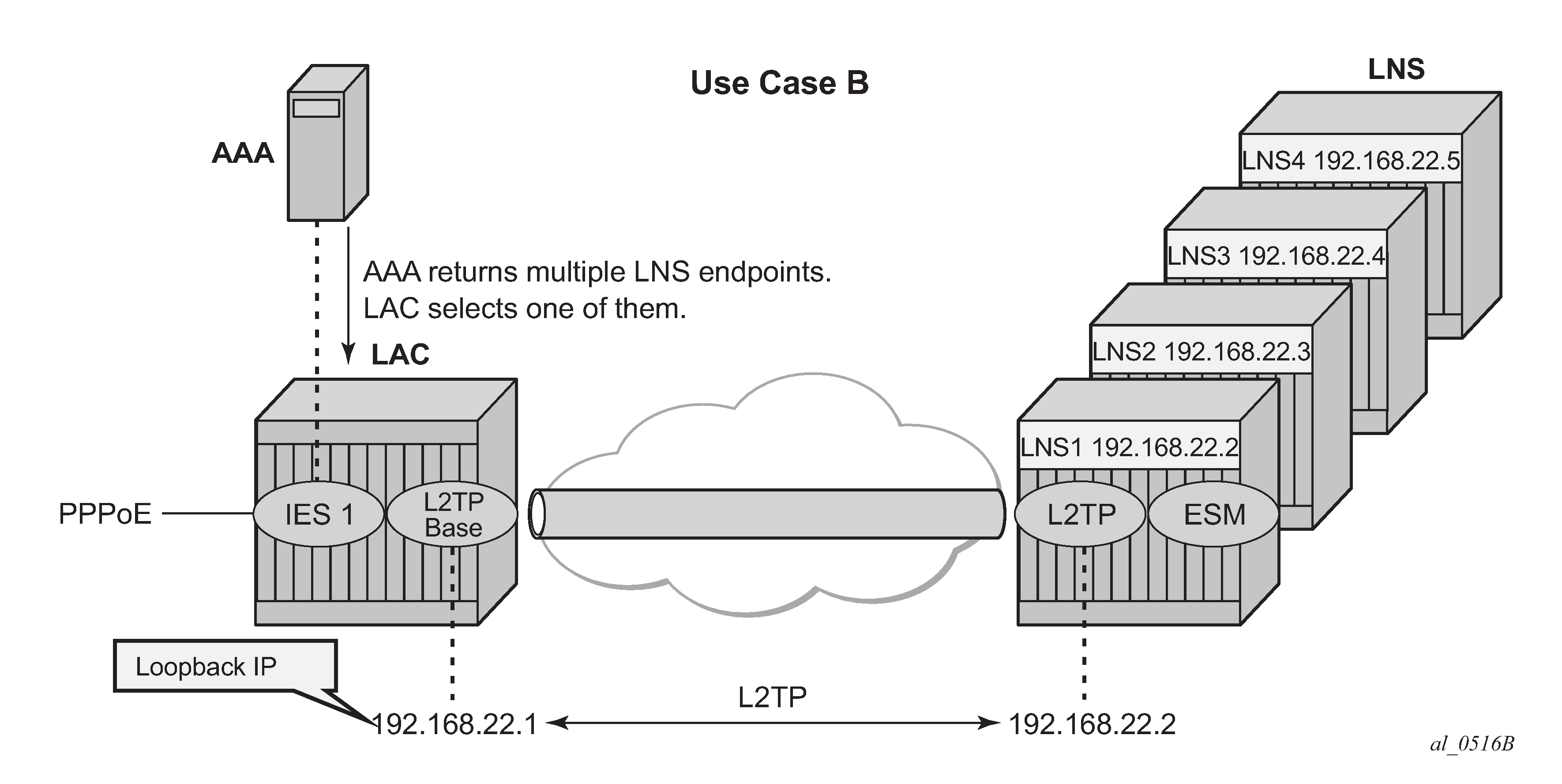
The following excerpt from the FreeRADIUS users file shows that user user1@wholesale.com has four possible endpoints (LNS), each with its own tunnel preference. The LAC selects one L2TP endpoint out of these four tunnel specifications according to the configured L2TP selection process. This use case uses weighted load balancing between RADIUS-tunnel-1 and RADIUS-tunnel-2. The L2TP tunnel selection process is out of the scope of this chapter.
user1@wholesale.com Cleartext-Password := "letmein", NAS-Identifier == "LAC"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1",
# group related info
Tunnel-Client-Endpoint:0 = 192.168.22.1,
Alc-Tunnel-Algorithm:0 = weighted-access,
Tunnel-Client-Auth-Id:0 = "lac-pe1",
Tunnel-Assignment-Id:0 = "RADIUS-group",
Alc-Tunnel-Max-Retries-Estab:0 = 2,
# tunnel-1 related info
Tunnel-Type:1 += L2TP,
Tunnel-Medium-Type:1 +=IP,
Tunnel-Server-Endpoint:1 += 192.168.22.2,
Tunnel-Assignment-Id:1 += "RADIUS-tunnel-1",
Tunnel-Preference:1 += 100,
# tunnel-2 related info
Tunnel-Type:2 += L2TP,
Tunnel-Medium-Type:2 +=IP,
Tunnel-Server-Endpoint:2 += 192.168.22.3,
Tunnel-Assignment-Id:2 += "RADIUS-tunnel-2",
Tunnel-Preference:2 += 80,
# tunnel-3 related info
Tunnel-Type:3 += L2TP,
Tunnel-Medium-Type:3 +=IP,
Tunnel-Server-Endpoint:3 += 192.168.22.4,
Tunnel-Assignment-Id:3 += "RADIUS-tunnel-3",
---snip---
This scenario shows the PPPoE session termination (base IES service 1) and the L2TP tunnel setup in the base router instance.
VRF hosted LAC
VRF hosted LAC shows the PPPoE session termination (base IES service 1) and the L2TP tunnel setup in a different router instance (VPRN 65536).
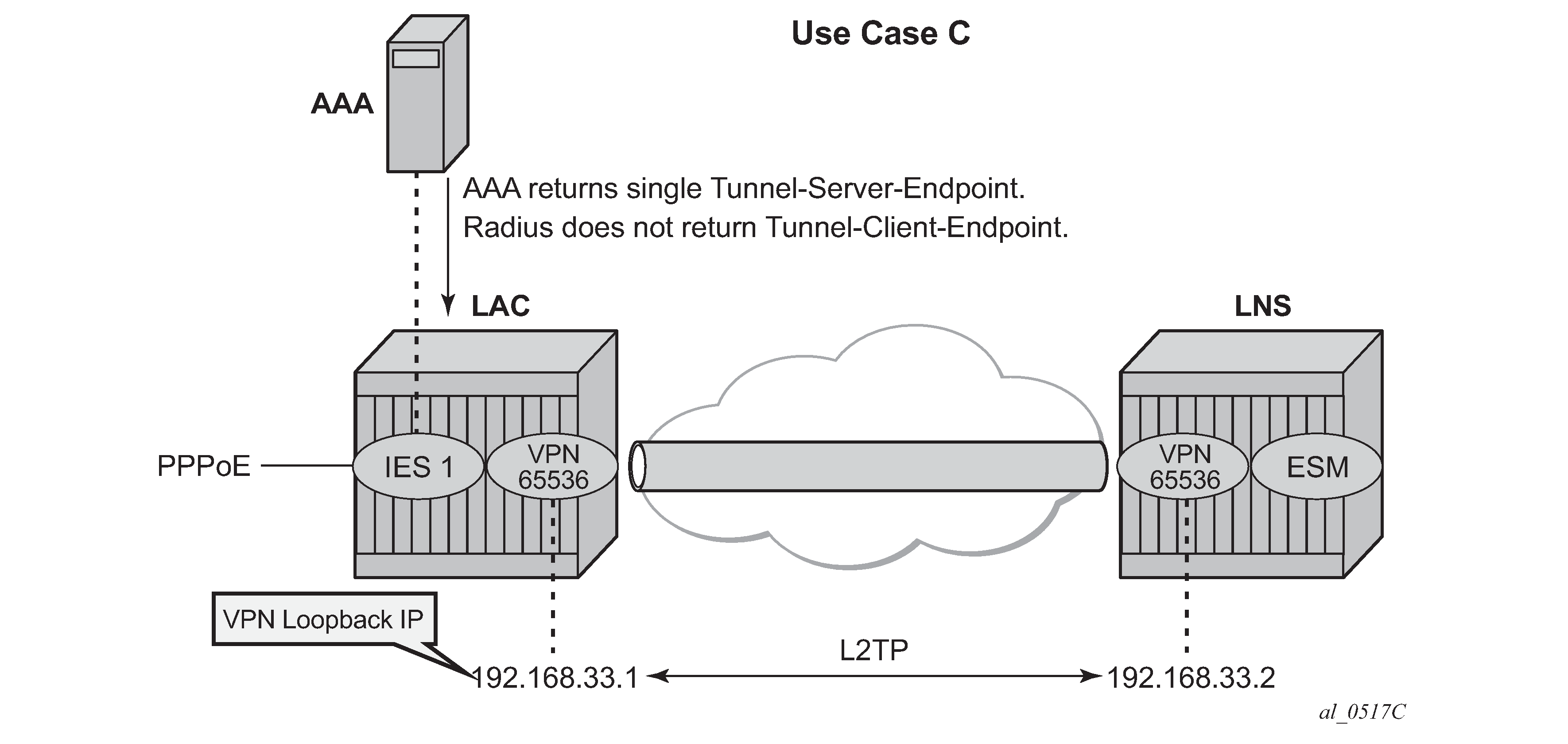
Using the following L2TP RADIUS attributes, the LAC initiates an L2TP tunnel in VPRN 65536. The PPPoE session is still handled by IES service 1, which proves that both router instances can be different. (See use-case A for configuration details of IES service 1).
user1@wholesale.com Cleartext-Password := "letmein", NAS-Identifier == "LAC"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1",
Alc-Tunnel-Serv-Id = 65536,
Tunnel-Client-Auth-Id:0 = "lac-pe1",
Tunnel-Assignment-Id:0 = "RADIUS-returned-TG",
Tunnel-Type:1 += L2TP,
Tunnel-Medium-Type:1 +=IP,
Tunnel-Server-Endpoint:1 += 192.168.33.2,
Tunnel-Assignment-Id:1 += "RADIUS-returned-TN",
If RADIUS does not return the L2TP source IP address (Tunnel-Client-Endpoint), then the IP address from the VPRN 65536 interface named ‛system’ is used as the L2TP source address. The tunnel setup fails if this system interface does not exist.
configure
service
vprn 65536
interface "system" create
address 192.168.33.1/32
loopback
exit
l2tp
no shutdown
exit
Scenario 2: node-derived L2TP parameters
In the second scenario, the LAC receives the incoming connection and an L2TP tunnel-group-name is assigned during LUDB or RADIUS authentication. This tunnel-group-name refers to the CLI preconfigured tunnel-group name context (configure router <router-name> l2tp group <tunnel-group-name>), which provides the context for all relevant tunnel attributes.
Based on these attributes, the LAC selects and initiates a tunnel to the LTS or directly to the LNS as in Scenario 1: RADIUS-derived L2TP parameters.
RADIUS returns L2TP tunnel group
In use case D, the L2TP tunnel-group-name is assigned during RADIUS authentication.
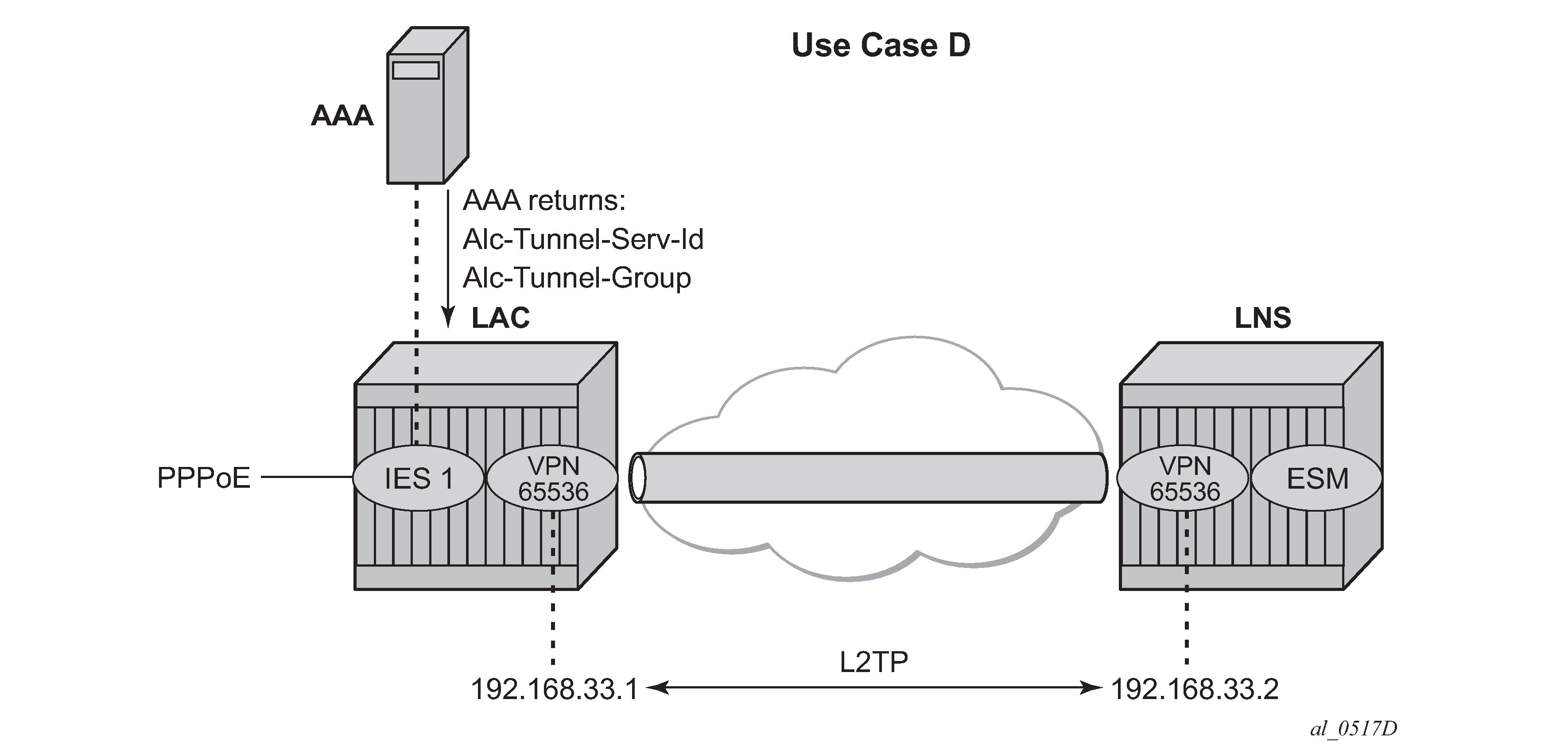
user1@wholesale.com Cleartext-Password := "letmein", NAS-Identifier == "LAC"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1",
Alc-Tunnel-Serv-Id = 65536,
Alc-Tunnel-Group = "wholesale.com",
The L2TP tunnel is initiated from VPRN 65536 (Alc-Tunnel-Serv-Id) and all L2TP tunnel information is taken from the l2tp group wholesale.com hierarchy (Alc-Tunnel-Group) as defined on the node.
configure
service
vprn 65536
---snip---
interface "system" create
address 192.168.33.1/32
loopback
exit
l2tp
group "wholesale.com" create
tunnel "wholesale.com" create
local-address 192.168.33.1
local-name "lac-pe1"
peer 192.168.33.2
no auto-establish
no shutdown
exit
no shutdown
exit
no shutdown
exit
no shutdown
exit
exit
exit
An L2TP tunnel is set up by either a PPP session-trigger, a tools command or by the l2tp group tunnel auto-establish parameter configuration. See the Advanced topics section for the non-session-triggered tunnel setup.
LUDB returns L2TP tunnel group
In use case E, the L2TP tunnel-group-name is assigned during LUDB authentication, so this essentially is a RADIUS-less scenario.
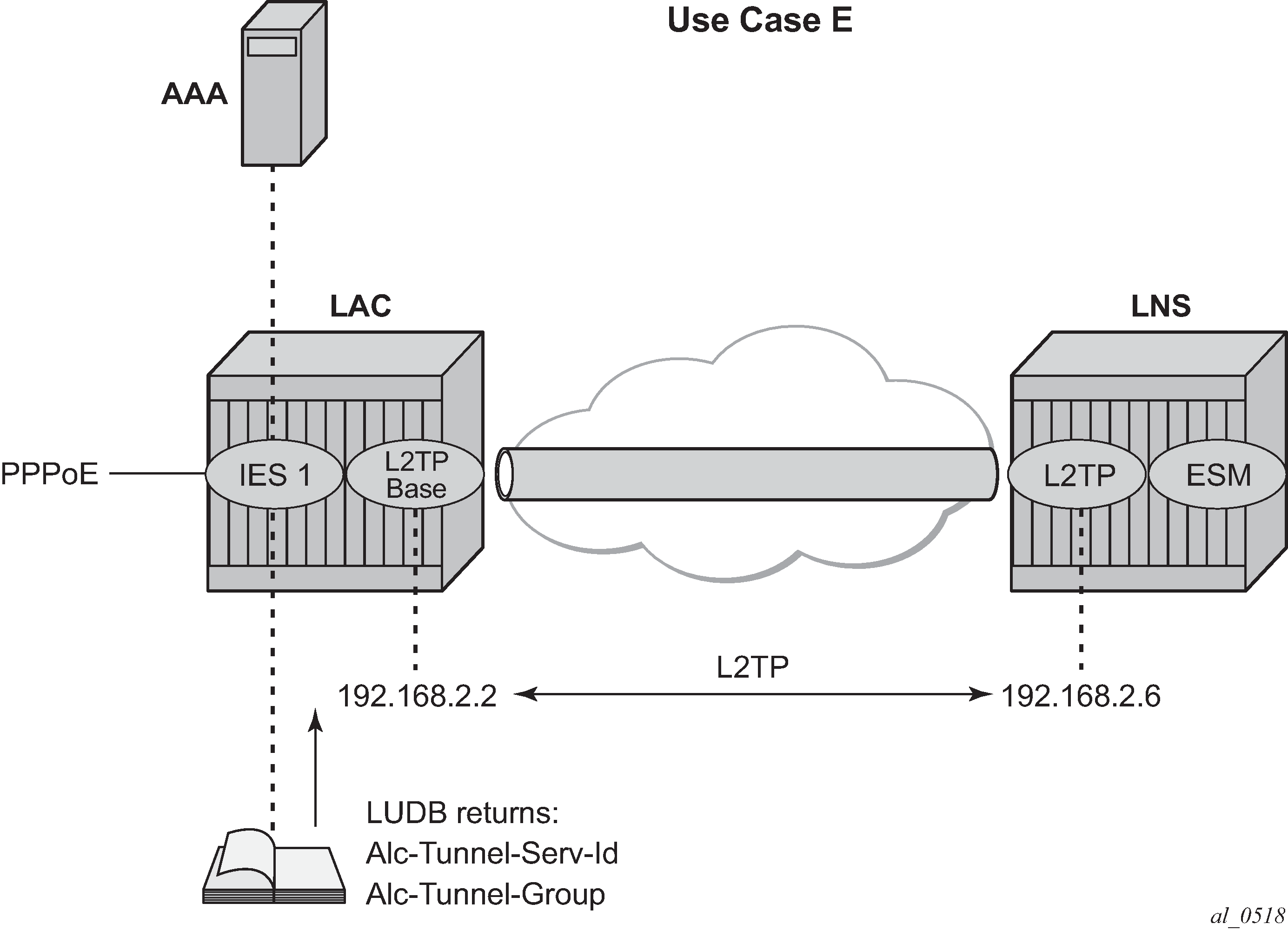
The PPPoE user enters on an IES service 1, sap 1/1/3:100, and is authenticated via the LUDB which provides L2TP wholesale/retail and ESM information. The PPPoE context refers to a local-user database l2tp to provide the subscriber authentication and the tunnel setup parameters, so no RADIUS is needed.
configure
service
ies 1 customer 1 create
subscriber-interface "sub-l2tp" create
unnumbered "system"
group-interface "grp-l2tp" create
sap 1/1/3:100 create
sub-sla-mgmt
sub-ident-policy "all-subscribers"
multi-sub-sap 1000
no shutdown
exit
exit
pppoe
sap-session-limit 10
user-db "l2tp"
no shutdown
exit
exit
exit
no shutdown
exit
exit
exit
The referenced local user database l2tp configuration provides all of the required L2TP and ESM information.
configure
subscriber-mgmt
local-user-db "l2tp" create
ppp
match-list username
host "wholesale.com" create
host-identification
username "wholesale.com" domain-only
exit
password ignore
identification-strings 254 create
subscriber-id "user@wholesale.com"
sla-profile-string "sla-profile-1"
sub-profile-string "sub-profile-1"
exit
l2tp
group "wholesale.com" service-id 65536
exit
no shutdown
exit
exit
no shutdown
exit
exit
exit
Operation and troubleshooting
The subsequent sections explain how the use cases A to E described in the configuration section are verified using show, debug, and tools commands.
The standard router debugging tools can be used to monitor and troubleshoot the L2TP tunnel and session setup.
Useful show commands are:
show service id <service-id> ppp session [detail]
show router l2tp tunnel [detail]
show router l2tp session [detail]
show router l2tp peer [ip-address]
To debug and show PPPoE packets:
debug service id <service-id> ppp packet mode egr-ingr-and-dropped
debug service id <service-id> ppp packet detail-level medium
To debug and show RADIUS authentication:
debug router radius packet-type authentication
To debug and show LUDB authentication:
debug subscriber-mgmt local-user-db <local-user-db-name> detail all
To debug and show the LAC tunnel selection process and L2TP state machine:
debug router l2tp event lac-session-setup
debug router l2tp event finite-state-machine
To debug and show the L2TP tunnel and session setup:
debug router l2tp packet direction both
debug router l2tp packet detail-level high
Understanding the L2TP debug output
The following L2TP ICRQ message (debug router l2tp packet) is used to explain how the displayed debug output should be interpreted. See Recapitulation of the L2TPv2 protocol -L2TP header and AVP layout for more details.
19 2019/05/21 14:02:10.811 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 13008 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
26540
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
25216
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"LAC 1/1/3:100"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000"
L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
version: v2
type field (T-bit): control message (ctrl)
192.0.2.1:1701 -> 192.168.22.2:1701
192.0.2.1:1701 - source tunnel-end-point:source udp port
192.168.22.2:1701 - destination tunnel-end-point:destination udp port
tunnel 13008 session 0, ns 2 nr 1, flags:, reserved=0
tunnel-id: 13008
session-id: 0
ns:2
nr:1
flags: 0 (refers to T/L/S/O/P bits L2TP header)
reserved field:0
AVP CallingNumber(0,22), flags: mandatory, reserved=0
AVP MessageType(0,22): "LAC 1/1/3:100"
Vendor-id: 0 - Standard Attribute
Attribute Type: 22 – Calling Number AVP
Attribute Value: "LAC 1/1/3:100"
Scenario 1: RADIUS-derived L2TP parameters
Base router hosted LAC with single endpoint/single tunnel
The debug service id <service-id> ppp packet mode egr-ingr-and-dropped command shows the PPPoE packet exchange. The following PADI packet shows the service, SAP, and received PPPoE tags. The received PPPoE DSL forum tags are by default copied during the LAC L2TP tunnel setup into the Incoming Call Request (ICRQ) DSL Forum AVPs (RFC 5515).
1 2019/05/21 14:02:10.779 CEST MINOR: DEBUG #2001 Base PPPoE
"PPPoE: RX Packet
IES 1, SAP 1/1/3:100
DMAC: ff:ff:ff:ff:ff:ff
SMAC: 00:00:00:00:01:01
Ether Type: 0x8863 (Discovery)
PPPoE Header:
Version: 1 Type : 1
Code : 0x09 (PADI) Session-Id: 0x0000 (0)
Length : 48
PPPoE Tags:
[0x0101] Service-Name: ""
[0x0103] Host-Uniq: len = 1, value = 31
[0x0105] Vendor-Specific: vendor-id = 0x0de9 (ADSL Forum)
[0x01] Agent-Circuit-Id: "circuit0"
[0x02] Agent-Remote-Id: "remote0"
[0x81] Actual-Upstream: 2000
[0x82] Actual-Downstream: 4000
"
The debug router radius packet-type authentication command shows the actual authentication parameters returned by RADIUS. This example returns the minimum set of L2TP related RADIUS attributes.
12 2019/05/21 14:02:10.806 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 16 len 89 from 172.16.1.11:1812 vrid 1 pol rsp-radius-1
VSA [26] 15 Nokia(6527)
SUBSC PROF STR [12] 13 sub-profile-1
VSA [26] 15 Nokia(6527)
SLA PROF STR [13] 13 sla-profile-1
TUNNEL TYPE [64] 4 1 L2TP(3)
TUNNEL MEDIUM TYPE [65] 4 1 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 13 1 192.168.22.2
"
The debug router l2tp event lac-session-setup command shows the LAC tunnel selection for this example. An L2TP group-name default_radius_group with tunnel-name unnamed is created in this case, because RADIUS did not return an explicit group and tunnel name.
13 2019/05/21 14:02:10.808 CEST MINOR: DEBUG #2001 Base PPPoE 13->L2TP
"PPPoE 13->L2TP: UDP 192.0.2.1:1701 -> 192.168.22.2:1701
preference 50 tunnel default_radius_group:unnamed
request to open new tunnel 1640"
14 2019/05/21 14:02:10.808 CEST MINOR: DEBUG #2001 Base PPPoE 13->L2TP
"PPPoE 13->L2TP: UDP 192.0.2.1:1701 -> 192.168.22.2:1701
preference 50 tunnel default_radius_group:unnamed
create session 107505580"
The debug router l2tp packet detail-level command shows the L2TP tunnel and session setup for this example.
For the tunnel setup, the LAC sends a start-control-connection-request (SCCRQ) containing the assigned tunnel ID (no tunnel authentication in the example). The tunnel is now in a wait-reply state.
15 2019/05/21 14:02:10.808 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 0 session 0, ns 0 nr 0, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionRequest(1)
AVP ProtocolVersion(0,2), flags: mandatory, reserved=0
version=1, revision=0
AVP HostName(0,7), flags: mandatory, reserved=0
"lac-pe1"
AVP WindowSize(0,10), flags: mandatory, reserved=0
64
AVP FramingCapabilities(0,3), flags: mandatory, reserved=0
sync=no, async=no
AVP BearerCapabilities(0,4), flags: mandatory, reserved=0
digital=yes, analogue=no
AVP FirmwareRevision(0,6), flags:, reserved=0
4869
AVP VendorName(0,8), flags:, reserved=0
"Nokia"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0
1640"
The LNS can bring up the tunnel, so the LNS replies with a start-control-connection-reply (SCCRP) including the assigned tunnel-id.
16 2019/05/21 14:02:10.809 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, ingress)
"L2TP(v2, ctrl, ingress): UDP 192.168.22.2:1701 -> 192.0.2.1:1701
tunnel 1640 session 0, ns 0 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionReply(2)
AVP ProtocolVersion(0,2), flags: mandatory, reserved=0
version=1, revision=0
AVP HostName(0,7), flags: mandatory, reserved=0
"lns-pe2"
AVP WindowSize(0,10), flags: mandatory, reserved=0
64
AVP FramingCapabilities(0,3), flags: mandatory, reserved=0
sync=no, async=no
AVP BearerCapabilities(0,4), flags: mandatory, reserved=0
digital=yes, analogue=no
AVP FirmwareRevision(0,6), flags:, reserved=0
4869
AVP VendorName(0,8), flags:, reserved=0
"Nokia"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0
13008"
As the last step in the tunnel setup phase, the LAC responds with a start-control-connection-connected (SCCCN) message. After an LNS ZLB acknowledgment, the tunnel is in the establishedIdle state.
17 2019/05/21 14:02:10.810 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 13008 session 0, ns 1 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionConnected(3)"
Once the tunnel exists the session setup starts, a three-way exchange for session establishment within the tunnel is performed. The LAC sends an incoming-call-request (ICRQ) with the parameter information for the session. The session is now in the wait-reply state.
19 2019/05/21 14:02:10.811 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 13008 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
26540
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
25216
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"LAC 1/1/3:100"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000"
The LNS then sends an incoming-call-reply (ICRP) that contains the assigned session ID. The session is now in the connect state.
21 2019/05/21 14:02:10.813 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, ingress)
"L2TP(v2, ctrl, ingress): UDP 192.168.22.2:1701 -> 192.0.2.1:1701
tunnel 1640 session 26540, ns 1 nr 3, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallReply(11)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
2466"
Finally, the LAC sends an incoming call connected (ICCN) and provides the LNS with additional information from the user initiated session. This information includes the LCP information from the negotiation that the LAC and remote user performed. This information is used by the LNS to decide whether to start LCP re-negotiation and/or authentication re-negotiation with the PPP user or not. After an LNS ZLB acknowledgment, the session is in the established state.
24 2019/05/21 14:02:10.814 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 13008 session 2466, ns 3 nr 2, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallConnected(12)
AVP FramingType(0,19), flags: mandatory, reserved=0
sync=no, async=no
AVP TxConnectSpeed(0,24), flags: mandatory, reserved=0
4294967295
AVP InitialRxLcpConfReq(0,26), flags:, reserved=0
01 04 05 d4
[1] MRU: 1492
AVP LastTxLcpConfReq(0,27), flags:, reserved=0
01 04 05 d4 03 05 c2 23 05 05 06 75 25 ad d3
[1] MRU: 1492
[3] Authentication-Protocol: 0xc223 (CHAP), Algorithm = 5 (MD5)
[5] Magic-Number: 0x7525add3
AVP LastRxLcpConfReq(0,28), flags:, reserved=0
01 04 05 d4
[1] MRU: 1492
AVP ProxyAuthenType(0,29), flags:, reserved=0
chap(2)
AVP ProxyAuthenName(0,30), flags:, reserved=0
"user1@wholesale.com"
AVP ProxyAuthenChallenge(0,31), flags:, reserved=0
13 ba fc db 18 15 b5 21 03 c9 61 8d 8a 1b 43 00
c3 4a 80 51 df 52 f4 06 26 c8 16 db ce 2b 7d 62
e5 7a bd 7d 0f
AVP ProxyAuthenId(0,32), flags:, reserved=0
id=1, reserved=0
AVP ProxyAuthenResponse(0,33), flags:, reserved=0
da c4 40 35 e4 4b 3f 72 3f eb 84 7b 09 99 5d f7
AVP RxConnectSpeed(0,38), flags:, reserved=0
4294967295"
The operational PPPoE session information for the IES 1 (base router) instance is as follows.
*A:LAC# show service id 1 ppp session
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id MC-Stdby
-------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/3:100 mac:00:00:00:00:01:01 sid:1
0d 00:10:01 oE lac 107505580
-------------------------------------------------------------------------------
No. of PPP sessions: 1
===============================================================================
*A:LAC#
The operational tunnel information in the base instance shows that the tunnel is established.
*A:LAC# show router l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
107479040 1640 13008 established not-blacklisted 1
default_radius_group 1
unnamed
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
Detailed operational tunnel information is obtained using following command.
*A:LAC# show router l2tp tunnel tunnel-id 1640 detail
===============================================================================
L2TP Tunnel 107479040
===============================================================================
Connection ID: 107479040
Protocol : v2
State : established
IP : 192.0.2.1
UDP : 1701
Peer IP : 192.168.22.2
Peer UDP : 1701
Tx dst-IP : 192.168.22.2
Tx dst-UDP : 1701
Rx src-IP : 192.168.22.2
Rx src-UDP : 1701
Name : lac-pe1
Remote Name : lns-pe2
Assignment ID: unnamed
Group Name : default_radius_group
Acct. Policy : N/A
Error Message: N/A
Remote Conn ID : 852492288
Tunnel ID : 1640 Remote Tunnel ID : 13008
Preference : 50 Receive Window : 64
Hello Interval (s): 300 AVP Hiding : never
Idle TO (s) : infinite Destruct TO (s) : 60
Max Retr Estab : 5 Max Retr Not Estab: 5
Cfg'd Sess Limit : unlimited Oper Session Limit: 32767 '
Transport Type : udpIp Challenge : never
Time Started : 05/21/2019 14:02:11 Time Idle : N/A
Time Established : 05/21/2019 14:02:11 Time Closed : N/A
Stop CCN Result : noError General Error : noError
Blacklist-state : not-blacklisted
Set Dont Fragment : true
Failover
State : not-recoverable
Recovery Conn ID : N/A
Recovery state : not-applicable
Recovered Conn ID : N/A
Recovery method : mcs
Track SRRP : (Not specified)
Ctrl msg behavior : handle
Recovery time (ms)
Requested : N/A
Peer : N/A
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The operational L2TP session information shows the L2TP session is established.
*A:LAC# show router l2tp session
===============================================================================
L2TP Session Summary
===============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
-------------------------------------------------------------------------------
107505580 107479040 1640 26540 established
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
For detailed operational L2TP session information use the following command.
*A:LAC# show router l2tp session session-id 26540 detail
===============================================================================
L2TP Session 107505580
===============================================================================
Connection ID: 107505580
State : established
Tunnel Group : default_radius_group
Assignment ID: unnamed
Error Message: N/A
Control Conn ID : 107479040 Rem Cntrl Conn ID : 852492288
Tunnel ID : 1640 Remote Tunnel ID : 13008
Session ID : 26540 Remote Session ID : 2466
PW Type : ppp Remote Conn ID : 852494754
Time Started : 05/21/2019 14:02:11
Time Established : 05/21/2019 14:02:11 Time Closed : N/A
CDN Result : noError General Error : noError
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
Base router hosted LAC with multiple endpoints
The debug router radius packet-type authentication command shows the actual RADIUS authentication parameters returned. This example returns multiple tunnel endpoints from which the LAC selects one. This example uses weighted load balancing. (The L2TP tunnel selection process is out of the scope of this example).
12 2019/05/22 10:57:38.331 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 83 len 225 from 172.16.1.11:1812 vrid 1 pol rsp-radius-1
VSA [26] 15 Nokia(6527)
SUBSC PROF STR [12] 13 sub-profile-1
VSA [26] 15 Nokia(6527)
SLA PROF STR [13] 13 sla-profile-1
TUNNEL CLIENT ENDPOINT [66] 12 192.168.22.1
VSA [26] 6 Nokia(6527)
TUNNEL ALGORITHM [47] 4 weighted access(1)
TUNNEL CLIENT AUTH ID [90] 7 lac-pe1
TUNNEL ASSIGNMENT ID [82] 12 RADIUS-group
VSA [26] 6 Nokia(6527)
TUNNEL MAX RETRIES ESTAB [52] 4 0 2
TUNNEL TYPE [64] 4 1 L2TP(3)
TUNNEL MEDIUM TYPE [65] 4 1 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 13 1 192.168.22.2
TUNNEL ASSIGNMENT ID [82] 16 1 RADIUS-tunnel-1
TUNNEL PREFERENCE [83] 4 1 100
TUNNEL TYPE [64] 4 2 L2TP(3)
TUNNEL MEDIUM TYPE [65] 4 2 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 13 2 192.168.22.3
TUNNEL ASSIGNMENT ID [82] 16 2 RADIUS-tunnel-2
TUNNEL PREFERENCE [83] 4 2 80
"
The debug router l2tp event lac-session-setup command shows the LAC tunnel LNS2-T2 is selected for this example.
13 2019/05/22 10:57:38.332 CEST MINOR: DEBUG #2001 Base PPPoE 38->L2TP
"PPPoE 38->L2TP: UDP 192.168.22.1:1701 -> 192.168.22.3:1701
preference 80 tunnel RADIUS-group:RADIUS-tunnel-2
request to open new tunnel 8880"
14 2019/05/22 10:57:38.332 CEST MINOR: DEBUG #2001 Base PPPoE 38->L2TP
"PPPoE 38->L2TP: UDP 192.168.22.1:1701 -> 192.168.22.3:1701
preference 80 tunnel RADIUS-group:RADIUS-tunnel-2
create session 581989428"
The operational PPPoE session information in IES 1/base instance is shown as follows.
*A:LAC# show service id 1 ppp session
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id MC-Stdby
-------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/3:100 mac:00:00:00:00:01:01 sid:1
0d 00:01:19 oE lac 1066935934
-------------------------------------------------------------------------------
No. of PPP sessions: 1
===============================================================================
*A:LAC#
The operational L2TP tunnel information (base instance) is shown below.
*A:LAC# show router l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
581959680 8880 11367 established not-blacklisted 1
RADIUS-group 1
RADIUS-tunnel-2
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
Operational session information (base instance) shows the session is in the established state.
*A:LAC# show router l2tp session
===============================================================================
L2TP Session Summary
===============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
-------------------------------------------------------------------------------
581989428 581959680 8880 29748 established
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
The L2TP endpoint/peer information shows there are two tunnels for tunnel endpoint 192.168.22.2.
*A:LAC# show router l2tp peer
===============================================================================
L2TP Peers
===============================================================================
Peer IP Port Tun Active Ses Active
Drain Reachability Tun Total Ses Total
-------------------------------------------------------------------------------
192.168.22.2 1701 0 0
0 0
192.168.22.3 1701 1 1
1 1
-------------------------------------------------------------------------------
No. of peers: 2
===============================================================================
*A:LAC#
The following command gives a system overview of subscriber session related data. This system overview shows the current and peak values per session type (local PTA, LAC, LTS, LNS) and an overview of the number of originated or terminated L2TP tunnels. Peak values can be cleared via the clear subscriber-mgmt peakvalue-stats command.
*A:LAC# show subscriber-mgmt statistics session system
===============================================================================
Subscriber Management Statistics for System
===============================================================================
Type Current Peak Peak Timestamp
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
PPP Session Statistics
-------------------------------------------------------------------------------
Local PPP Sessions - PPPoE 0 0
PPP Sessions - PPPoEoA 0 0
PPP Sessions - PPPoA 0 0
PPP Sessions - L2TP (LNS) 0 0
-------------------------------------------------------------------------------
LAC PPP Sessions - PPPoE 1 2 05/22/2019 10:13:30
PPP Sessions - PPPoEoA 0 0
PPP Sessions - PPPoA 0 0
PPP Sessions - L2TP (LTS) 0 0
-------------------------------------------------------------------------------
Total PPP Sessions - established 1 2 05/22/2019 10:13:30
PPP Sessions - in setup 0 1 05/22/2019 10:57:38
PPP Sessions - local 0 0
PPP Sessions - LAC 1 2 05/22/2019 10:13:30
-------------------------------------------------------------------------------
L2TP L2TP Tunnels - originator 1 3 05/21/2019 14:49:38
L2TP Tunnels - receiver 0 0
Total L2TP Tunnels 1 3 05/21/2019 14:49:38
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
IPOE Session Statistics
-------------------------------------------------------------------------------
Total IPOE Sessions - established 0 0
IPOE Sessions - in setup 0 0
-------------------------------------------------------------------------------
===============================================================================
Peak values last reset at : n/a
*A:LAC#
VRF hosted LAC
This example returns VPRN 65536 as the L2TP service instance [26-6527-104 Alc-Tunnel-Serv-Id]. The VPRN 65536 interface system address is used as the L2TP source address because the attribute Tunnel-Client-Endpoint is not returned.
The IP address 192.168.33.1 (Tunnel-Server-Endpoint) needs to be routable in VRF 65536 over a SAP or to a remote PE. This example uses BGP/MPLS IP virtual private networks (VPNs) (RFC 4364) to access the remote PE.
*A:LAC# show router 65536 route-table
===============================================================================
Route Table (Service: 65536)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
---snip---
192.168.33.1/32 Local Local 01d21h26m 0
system 0
192.168.33.2/32 Remote BGP VPN 20h03m54s 170
192.0.2.2 (tunneled) 10
---snip---
===============================================================================
*A:LAC#
Operational PPPoE session information for IES 1 (base instance) is shown using following command.
*A:LAC# show service id 1 ppp session
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id MC-Stdby
-------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/3:100 mac:00:00:00:00:01:01 sid:1
0d 00:07:40 oE lac 893192647
-------------------------------------------------------------------------------
No. of PPP sessions: 1
===============================================================================
*A:LAC#
Operational tunnel information for VPRN 65536 is displayed as follows.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
893190144 13629 14251 established not-blacklisted 1
RADIUS-returned-TG 1
RADIUS-returned-TN
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
Operational session information for VPRN 65536 is displayed using following command, and shows that the session is established.
*A:LAC# show router 65536 l2tp session
===============================================================================
L2TP Session Summary
===============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
-------------------------------------------------------------------------------
893192647 893190144 13629 2503 established
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
Scenario 2: Node-derived L2TP parameters
RADIUS returns L2TP group
This example returns VPRN 65536 as the L2TP service instance [26-6527-104 ] Alc-Tunnel-Serv-Id and an L2TP group name wholesale.com [26-6527-46 ] Alc-Tunnel-Group.
12 2019/05/22 11:15:46.604 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 85 len 95 from 172.16.1.11:1812 vrid 1 pol rsp-radius-1
VSA [26] 15 Nokia(6527)
SUBSC PROF STR [12] 13 sub-profile-1
VSA [26] 15 Nokia(6527)
SLA PROF STR [13] 13 sla-profile-1
VSA [26] 6 Nokia(6527)
TUNNEL SERVICE ID [104] 4 65536
VSA [26] 15 Nokia(6527)
TUNNEL GROUP [46] 13 wholesale.com
"
For operational PPPoE session information in IES 1/base instance, use following command.
A:LAC# show service id 1 ppp session
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id MC-Stdby
-------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/3:100 mac:00:00:00:00:01:01 sid:1
0d 00:02:35 oE lac 217909462
-------------------------------------------------------------------------------
No. of PPP sessions: 1
===============================================================================
*A:LAC#
Operational tunnel information for VPRN 65536 shows the tunnel is in the established state.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
217907200 3325 374 established not-blacklisted 1
wholesale.com 1
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The operational session information for VPRN 65536 shows the session is in the established state.
*A:LAC# show router 65536 l2tp session
===============================================================================
L2TP Session Summary
===============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
-------------------------------------------------------------------------------
217909462 217907200 3325 2262 established
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
LUDB returns L2TP group
This example returns VPRN 65536 as the L2TP service instance and L2TP group name wholesale.com (LUDB L2TP group "wholesale.com" service-id 65536).
The debug subscriber-mgmt local-user-db l2tp detail all command shows the LUDB authentication access (The returned parameter details are not shown).
11 2019/05/22 11:26:21.277 CEST MINOR: DEBUG #2001 Base LUDB
"LUDB: User lookup success - host found
user-name:
original: user1@wholesale.com
masked: user1@wholesale.com
Host wholesale.com found in user data base l2tp"
To show the operational data from LUDB l2tp, use the following command.
*A:LAC# show subscriber-mgmt local-user-db "l2tp" ppp-host "wholesale.com"
| match N/A invert-match
| match none invert-match
===============================================================================
PPP Host "wholesale.com"
===============================================================================
Admin State : Up
Last Mgmt Change : 05/20/2019 13:45:52
Host Identification
User Name : wholesale.com (domain only)
Matched Objects : userName
Password Type : ignore
PADO Delay : 0msec
Diameter app policy : (Not Specified)
Diameter auth policy : (Not Specified)
Force IPv6CP : Disabled
Ignore DF Bit : Disabled
DHCPv6 lease times
Renew timer : > 9999 days
Rebind timer : > 9999 days
Preferred lifetime : 0d 00:00:00
Valid lifetime : 0d 00:00:00
Identification Strings (option 254)
Subscriber Id : user@wholesale.com
SLA Profile String : sla-profile-1
Sub Profile String : sub-profile-1
L2TP
Service : 65536
Tunnel Group : wholesale.com
MSAP defaults
Filter Overrules
Access loop info
===============================================================================
*A:LAC#
The debug router l2tp event lac-session-setup command shows the LAC tunnel selected for this example.
12 2019/05/22 11:26:21.278 CEST MINOR: DEBUG #2001 vprn65536 PPPoE 41->L2TP
"PPPoE 41->L2TP: UDP 192.168.33.1:1701 -> 192.168.33.2:1701
preference 50 tunnel wholesale.com:wholesale.com
request to open new tunnel 11734"
13 2019/05/22 11:26:21.278 CEST MINOR: DEBUG #2001 vprn65536 PPPoE 41->L2TP
"PPPoE 41->L2TP: UDP 192.168.33.1:1701 -> 192.168.33.2:1701
preference 50 tunnel wholesale.com:wholesale.com
create session 769017741"
For the operational PPPoE session information in IES 1/base instance, use the following command.
*A:LAC# show service id 1 ppp session
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id MC-Stdby
-------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/3:100 mac:00:00:00:00:01:01 sid:1
0d 00:03:12 oE lac 769017741
-------------------------------------------------------------------------------
No. of PPP sessions: 1
===============================================================================
*A:LAC#
Operational tunnel information for VPRN 65536 can be obtained using following command.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
768999424 11734 4184 established not-blacklisted 1
wholesale.com 1
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The operational session information for VPRN 65536 shows the session is in the established state.
*A:LAC# show router 65536 l2tp session
===============================================================================
L2TP Session Summary
===============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
-------------------------------------------------------------------------------
769017741 768999424 11734 18317 established
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
Advanced topics
Non-session-triggered L2TP tunnel setup
In addition to the PPP-session-triggered setup, an L2TP tunnel can also be set up via a tools command or an auto-establish command.
These non-session triggers are useful, for example, during the initial configuration phase where the LAC-LNS tunnel setup can be tested without the need for a user to attempt and establish a PPPoE connection.
The PPPoE user still triggers the L2TP session-setup over this L2TP tunnel and RADIUS needs to return an L2TP group name with the relevant name during authentication.
Auto-establish
Every minute, a check is performed to determine if tunnels need to be established (a process referred to as scan auto-establish). The tunnel state is establishedIdle when the tunnel is setup, and becomes established when user triggered sessions are set up over this tunnel.
configure
service
vprn 65536 customer 1 create
l2tp
group "wholesale.com" create
tunnel "wholesale.com" create
local-address 192.168.33.1
local-name "lac-pe1"
peer 192.168.33.2
auto-establish
no shutdown
exit
no shutdown
exit
no shutdown
exit
no shutdown
exit
exit
exit
There is no difference in operational behavior for a tunnel set up via a session-trigger or an auto-establish command. Removing the auto-establish parameter has no impact on active tunnels (establishedIdle or established).
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
475136000 7250 6770 establishedIdle not-blacklisted 0
wholesale.com 0
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
Tools tunnel start
First revert to the original situation, without auto-establish, as follows:
*A:LAC# configure service vprn 65536 l2tp group "wholesale.com"
tunnel "wholesale.com" no auto-establish
*A:LAC#
Verify the tunnel does not exist anymore, as follows:
*A:LAC# show router 65536 l2tp tunnel
No entries found.
*A:LAC#
Issue the tools command to manually establish the L2TP tunnel, as follows:
*A:LAC# tools perform router 65536 l2tp group "wholesale.com"
tunnel "wholesale.com" start
*A:LAC#
Verify a new tunnel has been created, as follows:
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
282394624 4309 4437 establishedIdle not-blacklisted 0
wholesale.com 0
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
How long remains a tunnel idle before being torn down?
An L2TP tunnel can be torn down automatically, after the expiration of an idle timer, or manually through a tools command.
Idle timeout
A persistent tunnel is a tunnel that remains available after the last session over that tunnel is closed. To create a persistent tunnel, the idle-timeout parameter must be set to infinite.
A non-persistent tunnel is torn down immediately (idle-timeout zero) after the last session over that tunnel is closed or after a configurable delay. The idle-timeout parameter is set via the RADIUS [26-6527-49] Alc-Tunnel-Idle-Timeout attribute or the corresponding node parameter. The default value for this parameter is infinite (persistent).
configure router l2tp | configure service vprn l2tp
idle-timeout [0..3600] s
---snip---
group <tunnel-group-name>
idle-timeout [0..3600] s | infinite
---snip---
tunnel <tunnel-name>
idle-timeout [0..3600] s | infinite
---snip---
The following shows an example of a non-persistent tunnel (idle-timeout 30 seconds). The tunnel changes state from established to establishedIdle when the last session is terminated. Idle-timeout seconds later, the session changes to the closed state. For the purpose of troubleshooting, the operational data stays available for destruct-timeout seconds (see later).
*A:LAC# show router l2tp tunnel detail
===============================================================================
L2TP Tunnel 921436160
===============================================================================
Connection ID: 921436160
Protocol : v2
State : closed
IP : 192.0.2.1
---snip---
Name : lac-pe1
Remote Name : lns-pe2
Assignment ID: unnamed
Group Name : default_radius_group
Acct. Policy : N/A
Error Message: idle timeout (30 seconds) expired
Remote Conn ID : 280231936
Tunnel ID : 14060 Remote Tunnel ID : 4276
Preference : 50 Receive Window : 64
Hello Interval (s): 300 AVP Hiding : never
Idle TO (s) : 30 Destruct TO (s) : 60
Max Retr Estab : 5 Max Retr Not Estab: 5
Cfg'd Sess Limit : unlimited Oper Session Limit: 32767 '
Transport Type : udpIp Challenge : never
---snip---
No. of tunnels: 1
===============================================================================
*A:LAC#
The following shows an example of a persistent tunnel (idle-timeout infinite).
*A:LAC# show router l2tp tunnel detail
===============================================================================
L2TP Tunnel 235405312
===============================================================================
Connection ID: 235405312
Protocol : v2
State : establishedIdle
IP : 192.0.2.1
---snip---
Name : lac-pe1
Remote Name : lns-pe2
Assignment ID: unnamed
Group Name : default_radius_group
Acct. Policy : N/A
Error Message: N/A
Remote Conn ID : 154861568
Tunnel ID : 3592 Remote Tunnel ID : 2363
Preference : 50 Receive Window : 64
Hello Interval (s): 300 AVP Hiding : never
Idle TO (s) : infinite Destruct TO (s) : 60
Max Retr Estab : 5 Max Retr Not Estab: 5
Cfg'd Sess Limit : unlimited Oper Session Limit: 32767
Transport Type : udpIp Challenge : never
---snip---
No. of tunnels: 1
===============================================================================
*A:LAC#
Tools tunnel stop
In addition to the idle timeout used for tunnel termination, a tools stop command is also available that can be used to terminate persistent and non-persistent tunnels at any moment in time. Be aware that this command is very destructive and destroys all sessions carried over the closed tunnel.
Following command shows the tunnel is in the establishedIdle state.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
60293120 920 7499 establishedIdle not-blacklisted 0
wholesale.com 0
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The following command terminates the L2TP tunnel. The tunnel is aborted (the LAC sends StopCCN) using the <connection-id> or <tunnel-group-name>+<tunnel-name> as input. This StopCCN indicates "operator request" as the error reason.
*A:LAC# tools perform router 65536 l2tp group "wholesale.com"
tunnel "wholesale.com" stop
INFO: CLI stopped 1 tunnels, destructed 0 tunnels.
*A:LAC#
The following debug output shows the tunnel being aborted.
13 2019/05/22 12:12:28.377 CEST MINOR: DEBUG #2001 vprn65536 L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.168.33.1:1701 -> 192.168.33.2:1701
tunnel 12828 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StopControlConnectionNotification(4)
AVP ResultCode(0,1), flags: mandatory, reserved=0
result-code: "generalRequestToClearControlConnection"(1),
error-code: "noGeneralError"(0)
error-msg: "operator request"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0
3695"
Alternatively, the tunnel can also be stopped with the following command. The effect would be the same.
*A:LAC# tools perform router 65536 l2tp tunnel 964886528 stop
Keepalive - L2TP hello
A keepalive mechanism is employed by L2TP in order to differentiate between tunnel outages and no control or data activity on a tunnel for an extended period. This is accomplished by injecting hello control messages after a specified period of time has elapsed since the last data or control message (ZLB not included) was received on a tunnel. As for any other L2TP control message, if the hello message is not reliably delivered, then the tunnel is declared down and reset, as defined in RFC 2661. This means that SR OS does not send hello packets if session control traffic is handled over this tunnel. The hello timer is reset if the system transmits any control packet over this tunnel (ZLB packets and data traffic are not taken into account).
The keepalive function is disabled (not recommended) using RADIUS [26-6527-50] Alc-Tunnel-Hello-Interval -1 or hello-interval infinite (default 300). The number of retries for unsuccessful hello packet delivery equals RADIUS [26-6527-52] Alc-Tunnel-Max-Retries-Estab or node parameter max-retries-estab (default 5). The retry interval is initially set to 1 second and doubles on each retry with a maximum interval of 8 seconds. Using a max-retries-estab 7 results in a retry of [1,2,4,8,8,8,8 seconds].
configure router l2tp | configure service vprn l2tp]
hello-interval [60..3600] s | infinite # default 300 s
max-retries-estab [2..7] # default 5
---snip---
group <tunnel-group-name>
hello-interval [60..3600] s | infinite
max-retries-estab [2..7]
---snip---
tunnel <tunnel-name>
hello-interval [60..3600] s | infinite
max-retries-estab [2..7]
---snip---
For example, the LAC can be configured with an hello timer of 1 minute and the LNS with an hello timer of 2 minutes. The hello timer interval for LAC and LNS do not have to be same because the keepalive mechanism works asynchronous. See L2TP keepalive mechanism.
*A:LAC# show router l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
794361856 11364 5391 established not-blacklisted 1
default_radius_group 1
unnamed
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
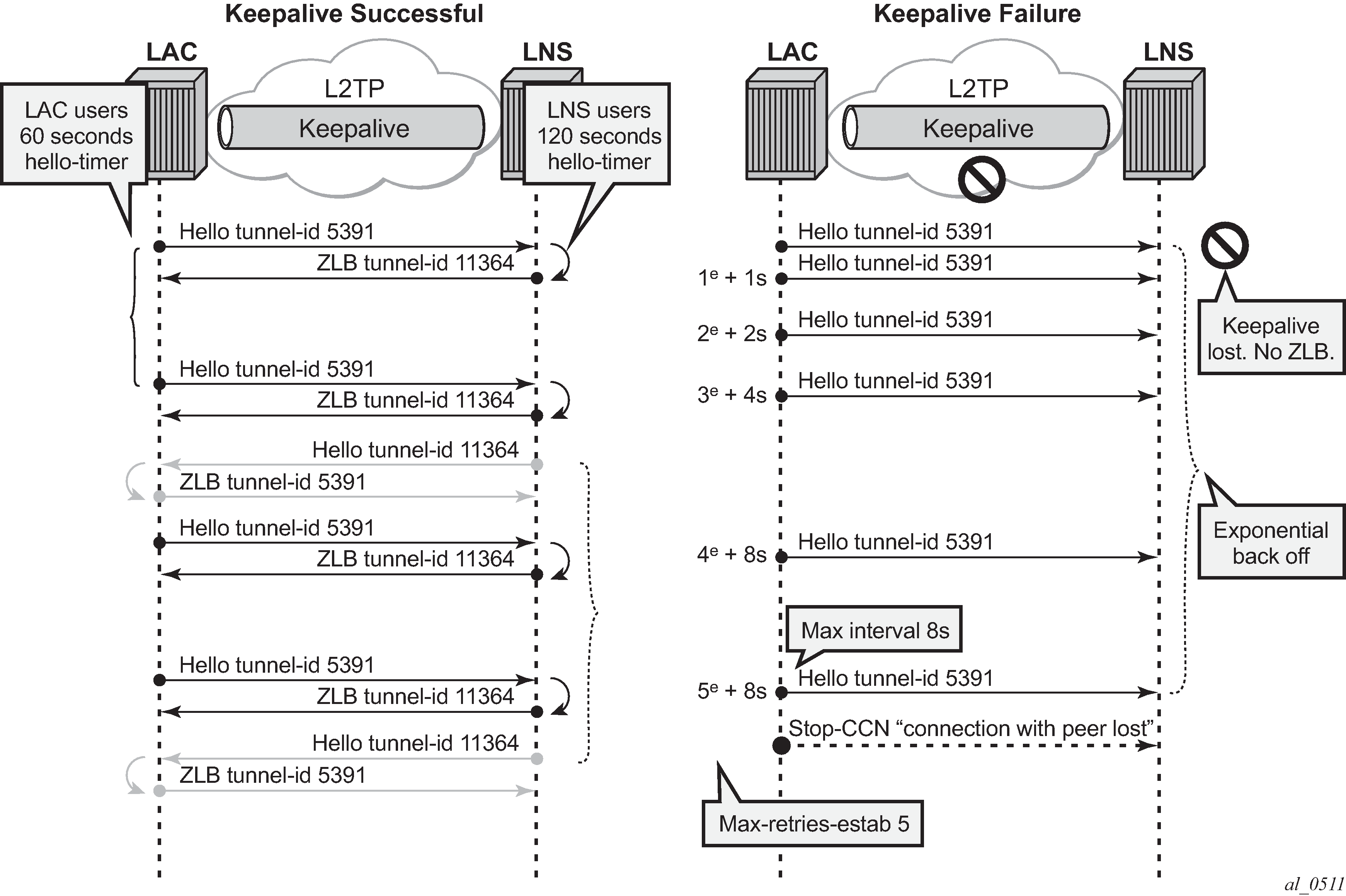
L2TP keepalive mechanism shows the tunnel being closed after 5 unsuccessful Hello deliveries with error-message connection with peer lost.
*A:LAC# show router 65536 l2tp tunnel detail
===============================================================================
L2TP Tunnel 479985664
===============================================================================
Connection ID: 479985664
---snip---
Acct. Policy : N/A
Error Message: connection with peer lost
Remote Conn ID : 201195520
Tunnel ID : 7324 Remote Tunnel ID : 3070
Preference : 50 Receive Window : 64
Hello Interval (s): 60 AVP Hiding : never
---snip---
No. of tunnels: 1
===============================================================================
*A:LAC#
Keeping closed tunnel and session information
The destruct-timeout parameter (expressed in seconds) controls the period of time that the tunnel, or session data related to a closed (disconnected) tunnel, or session persists before being removed. The destruct timeout is a debugging aid by keeping underlying memory structures after the tunnel or session is terminated. It is configured via the RADIUS [26-6527-51] Alc-Tunnel-Destruct-Timeout attribute or the corresponding node parameter. Default value for this parameter is 60 seconds.
configure router l2tp | configure service vprn l2tp
destruct-timeout [60..86400]
---snip---
group <tunnel-group-name>
destruct-timeout [60..86400]
---snip---
tunnel <tunnel-name>
destruct-timeout [60..86400]
The following output shows a session that is closed and the reason for it being terminated.
*A:LAC# show router l2tp session detail
===============================================================================
L2TP Session 900466242
===============================================================================
Connection ID: 900466242
State : closed
Tunnel Group : default_radius_group
Assignment ID: unnamed
Error Message: Terminated by PPPoE: Received PPPoE PADT
Control Conn ID : 900464640 Rem Cntrl Conn ID : 899416064
Tunnel ID : 13740 Remote Tunnel ID : 13724
Session ID : 1602 Remote Session ID : 23489
PW Type : ppp Remote Conn ID : 899439553
Time Started : 05/22/2019 13:54:44
Time Established : 05/22/2019 13:54:44 Time Closed : 05/22/2019 13:54:50
CDN Result : generalError General Error : vendorSpecific
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:LAC#
The following output shows a tunnel that is closed and the reason for it being closed.
*A:LAC# show router l2tp tunnel detail
===============================================================================
L2TP Tunnel 900464640
===============================================================================
Connection ID: 900464640
Protocol : v2
State : closed
IP : 192.0.2.1
UDP : 1701
Peer IP : 192.168.22.2
Peer UDP : 1701
Tx dst-IP : 192.168.22.2
Tx dst-UDP : 1701
Rx src-IP : 192.168.22.2
Rx src-UDP : 1701
Name : lac-pe1
Remote Name : lns-pe2
Assignment ID: unnamed
Group Name : default_radius_group
Acct. Policy : N/A
Error Message: idle timeout (60 seconds) expired
---snip---
No. of tunnels: 1
===============================================================================
*A:LAC#
When the destruct timeout expires the tunnel and session is deleted, as follows:
*A:LAC# show router l2tp session detail
No entries found.
*A:LAC# show router l2tp tunnel detail
No entries found.
*A:LAC#
Floating peers
A floating peer exists if the peer LNS address indicated in the source address of the SCCRP is different from the peer address known on the LAC. Floating peer allowance is configuration driven and is rejected by default.
The parameter peer-address-change-policy specifies whether the LAC accepts, ignores or rejects requests from a peer to change the destination IP address or UDP port.
configure router l2tp | configure service vprn l2tp
peer-address-change-policy accept | ignore | reject
accept — Specifies that this system accepts any source IP address change for received L2TP control messages related to a locally originated tunnel in the state wait-reply and rejects any peer address change for other tunnels. In case the new peer IP address is accepted, it is learned and used as destination address in subsequent L2TP messages.
Figure 14. Floating peers accept 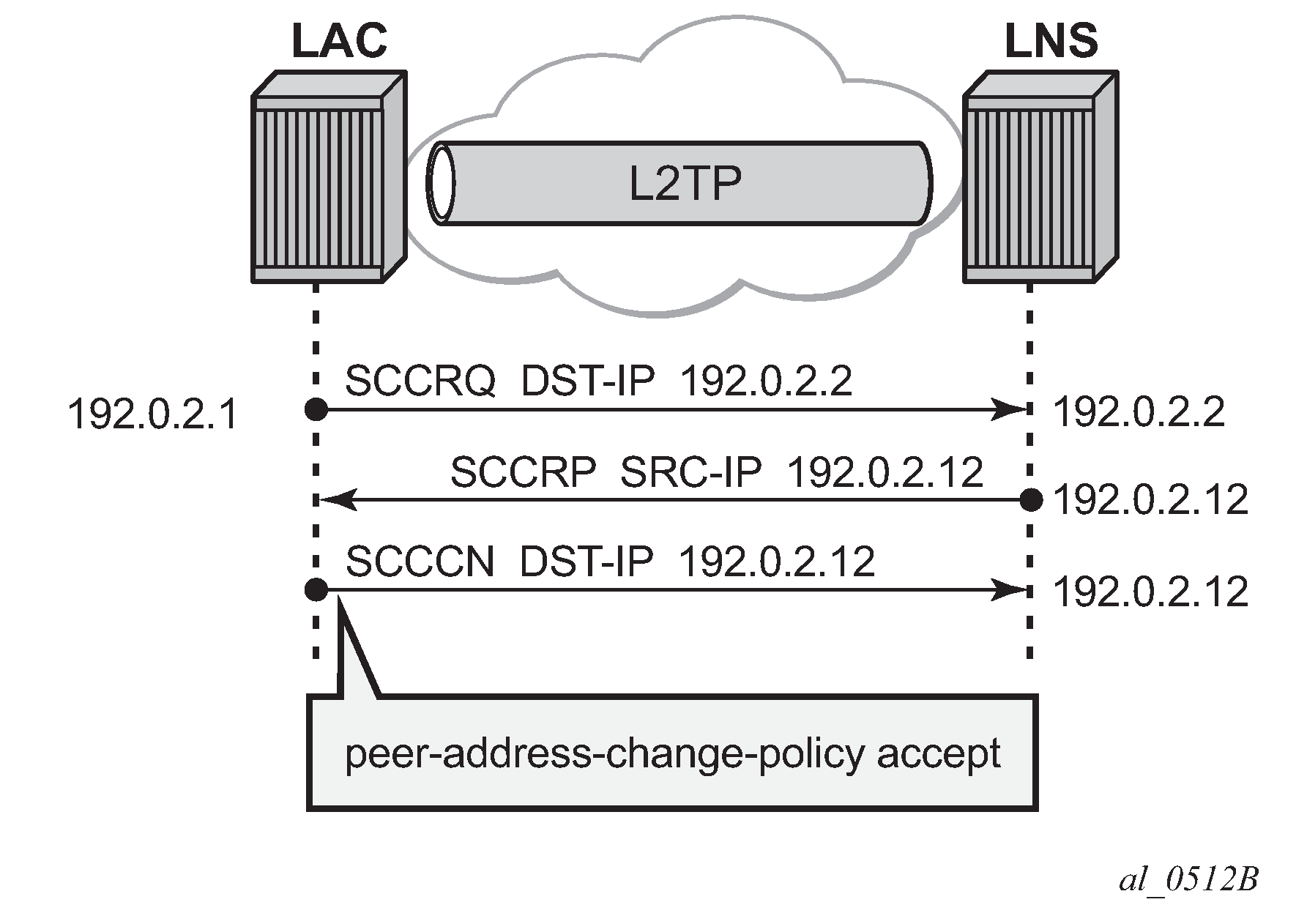
Ignore — Specifies that this system ignores any source IP address change for received L2TP control messages, does not learn any new peer IP address and does not change the destination address in subsequent L2TP messages.
Figure 15. Floating peers ignore 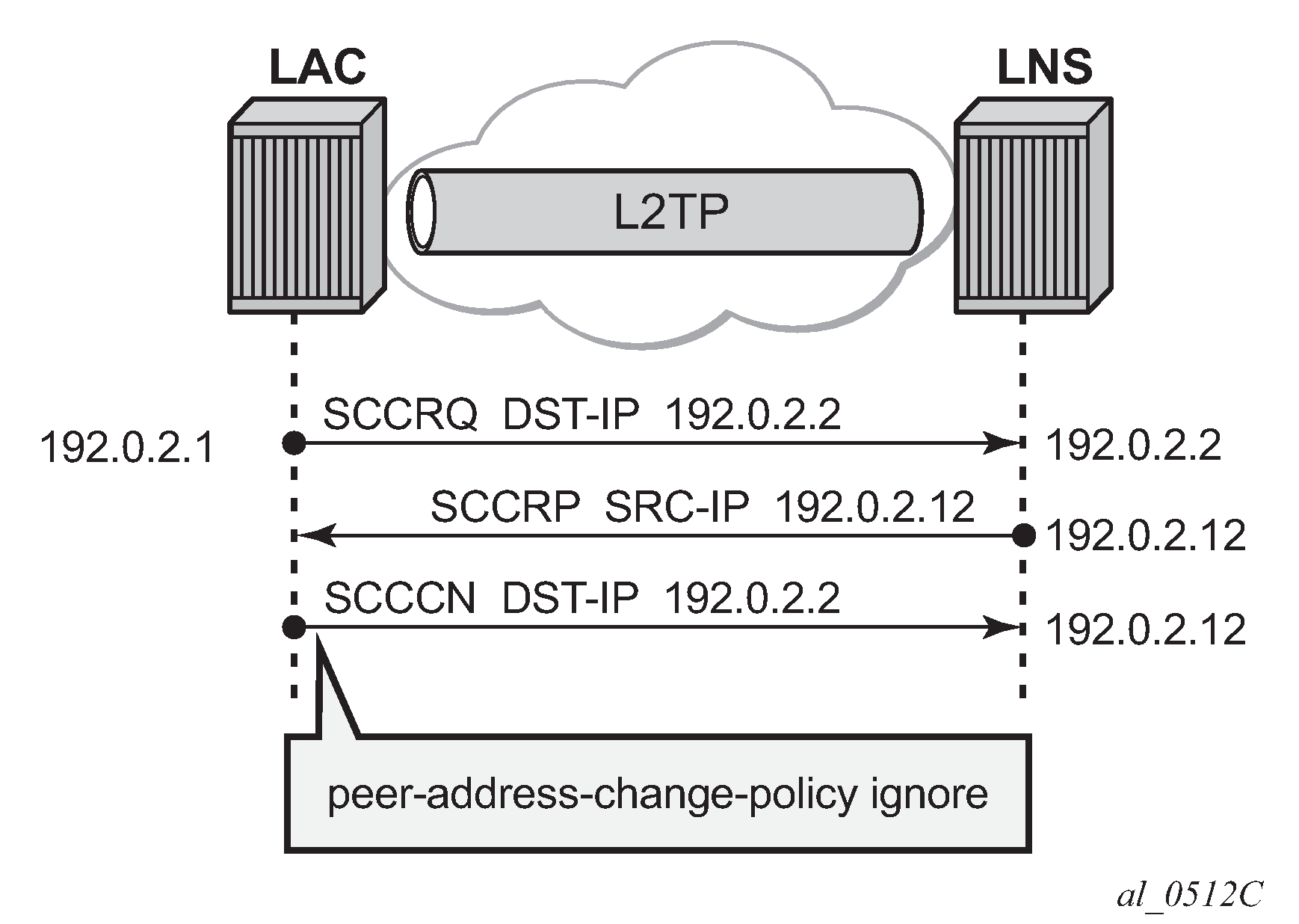
Reject — Specifies that this system rejects any source IP address change for received L2TP control messages and drops those messages.
Figure 16. Floating peers reject 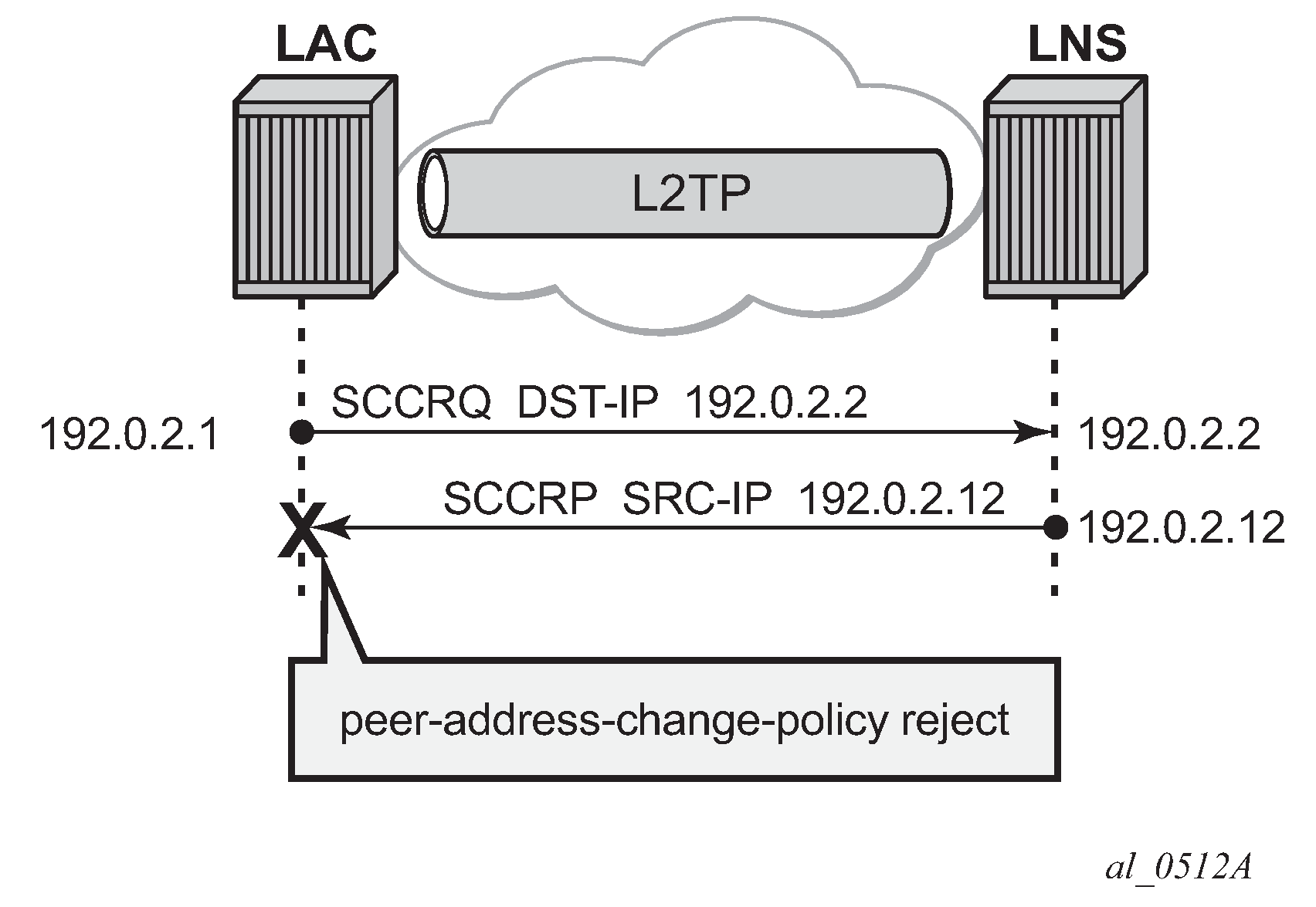
The values Peer IP, Tx dst-IP and Rx src-IP in the show router l2tp tunnel detail command indicates if floating peers are used or not.
An example of a floating peer (peer-address-change-policy accept) is as follows.
*A:LAC# show router l2tp tunnel detail
=======================================
L2TP Tunnel Status
=======================================
Connection ID: 897122304
State : established
IP : 192.0.2.1
UDP : 1701
Peer IP : 192.0.2.2 # (1) peer address used in SCCRQ
Peer UDP : 1701
Tx dst-IP : 192.0.2.12 # (3) peer address used in SCCCN
Tx dst-UDP : 1701
Rx src-IP : 192.0.2.12 # (2) SCCRP different IP received
Rx src-UDP : 1701
---snip---
Tx/Rx connect speed - AVP 24/38
The connect speed (TX AVP 24 and RX AVP 38) is passed in the ICCN messages sent from the LAC to the LNS. The L2TP AVP 24 defines the (Tx) connect speed in bps from the perspective of traffic flowing from the LAC towards the subscriber (BNG downstream rate).The L2TP AVP 38 defines the (Rx) connect speed in bps from the perspective of traffic flowing from the subscriber toward the LAC (BNG upstream rate).
The report-rate configuration option indicates what rate is reported to the LNS when creating an L2TP session.
configure subscriber-mgmt sla-profile <sla-profile-name> ingress | egress
report-rate agg-rate-limit|scheduler|pppoe-actual-rate|policer|rfc5515-actual-rate
agg-rate-limit — Take the aggregate rate as received from the RADIUS Access-Accept message in VSA Alc-Subscriber-QoS-Override. When this RADIUS VSA is not present in the Access-Accept, or when RADIUS is not used, then take the configured aggregate rate limit. In the case where this is not configured, then take the port rate.
scheduler <scheduler-name> — Take the rate of the specified scheduler. In case the scheduler is not linked with the scheduler-policy from the subscriber-profile, then take the port rate.
pppoe-actual-rate — Take the rate from the DSL-Forum Vendor-Specific PPPoE Tag when available, otherwise take the port rate.
rfc5515-actual-rate — Put the same value as the transmitted Actual-Data-Rate-Upstream AVP in the Rx-Connect-Speed AVP, and the same value as the transmitted Actual-Data-Rate-Downstream AVP in the Tx-Connect-Speed AVP.
Calling number AVP 22 format
The format of AVP 22 calling number in the ICRQ message is configurable via the parameter calling-number-format. The default format is "%S<space>%s" and corresponds to the concatenation of system-name<space>sap-id. Available parameters are %S (system-name), %c (Agent Circuit Id), %r Agent Remote Id, %s (sap-id), %l (Logical Line ID) and fixed strings. A combination can be configured from any of these parameters, but the total configured format cannot exceed 255 characters.
Example 1: Default configuration.
configure router l2tp calling-number-format "%S %s"
19 2019/05/22 14:01:04.885 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 5593 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
15342
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
84781
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"LAC 1/1/3:100"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000"
Example 2: Customized configuration and all parameters (%S %s %c) are available to construct the requested AVP 22.
configure router l2tp calling-number-format "start-%S###%s###%c-end"
19 2019/05/22 14:05:28.116 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 832 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
24748
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
84782
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"start-LAC###1/1/3:100###circuit0-end"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000"
Example 3: Customized configuration and not all parameters are available to construct the requested AVP 22. Option-82 circuit-id (%c),remote-id (%r), and LLID (%l) information are lacking and therefore missing (skipped) in the formatted attribute.
configure router l2tp calling-number-format "%S#%c#%r#%l#%s"
19 2019/05/22 14:07:26.302 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 255 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
20814
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
84783
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"LAC#circuit0#remote0##1/1/3:100"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
Prevent LAC from transmitting calling number AVP 22 to LNS
By default, the LAC includes the calling number AVP 22 in the L2TP incoming-call-request (ICRQ) packets transmitted to LNS. This AVP identifies the interface that is connected to the customer in the access network. Network access interface information can be hidden by configuring the LAC not to send the calling number AVP to the LNS.
Use the following command to disable the sending of L2TP calling number AVP 22.
configure router l2tp
exclude-avps calling-number
AVP 100 - Cisco-Nas-Port
Interoperation with a Cisco LNS requires that the LAC communicates a NAS port type to the LNS via the L2TP ICRQ ‛Cisco Nas Port Info AVP (100)’. This AVP (100) includes information that identifies the NAS port and indicates whether the port type is Ethernet or ATM and is configured via the cisco-nas-port parameter.
The Cisco AVP 100 format is as follows:
First 5 bytes are NAS-Port-Type:
0f10090203 (Ethernet)
0f10090201 (ATM)
Remaining four bytes correspond with the configured cisco-nas-port value
Example:
Ethernet 12b s-vlan-id; 10b c-vlan-id; 3b slot number; 2b MDA nbr; 5b port
ATM 12b VPI; 10b VCI; 3b slot number; 2b MDA nbr; 5b port
configure router l2tp
cisco-nas-port ethernet "*12o*10i*3s*2m*5p" atm "*12v*10c*3s*2m*5p"
nas-port 1/1/3:100 corresponds to 102563 (000000000000 0001100100 001 01 00011).
19 2019/05/22 14:11:49.431 CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.1:1701 -> 192.168.22.2:1701
tunnel 13002 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP CiscoNasPort(9,100), flags:, reserved=0
102563 type=ethernet(0f:10:09:02:03)
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
2461
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
84784
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"LAC 1/1/3:100"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0"
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000"
L2TP group/peer/tunnel draining
When the LAC has established sessions, the LAC can avoid the creation of new sessions for a specific group, peer, or tunnel, via the drain command.
No new sessions are created for a group, peer or tunnel that is being drained (draining state) but the current sessions are left intact.
After the drain command is issued, the group, peer, or tunnel moves from a draining to drained state when the last session is closed. A drained group, peer, or tunnel can then be managed (reconfigured, deleted) without any user impact.
Be aware that a group, peer, or tunnel in a draining or drained state is skipped in the tunnel selection process. The next example shows a tunnel draining; group and peer draining works according in the same way.
A tunnel has 1 session and is in established state.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
1023868928 15623 9957 established not-blacklisted 1
wholesale.com 1
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The following tools drain command puts the tunnel in a draining state and leaves the sessions intact.
*A:LAC# tools perform router 65536 l2tp tunnel 1023868928 drain
*A:LAC#
Initially the tunnel is in the draining state.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
1023868928 15623 9957 draining not-blacklisted 1
wholesale.com 1
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The tunnel moves to the drained state at the moment the last session is closed. Debugging shows that a drained tunnel is also not used as last resort and is skipped during the tunnel selection process.
*A:LAC# show router 65536 l2tp tunnel
===============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
-------------------------------------------------------------------------------
1023868928 15623 9957 drained not-blacklisted 0
wholesale.com 1
wholesale.com
-------------------------------------------------------------------------------
No. of tunnels: 1
===============================================================================
*A:LAC#
The following output shows new sessions cannot select a drained tunnel.
82289 2019/05/22 14:43:56.549 CEST MINOR: DEBUG #2001 vprn65536 PPPoE 19644->L2TP
"PPPoE 19644->L2TP: UDP 192.168.33.1:1701 -> 192.168.33.2:1701
preference 50 tunnel wholesale.com:wholesale.com
no additional session can be created in tunnel 15623"
82290 2019/05/22 14:43:56.549 CEST MINOR: DEBUG #2001 vprn65536 PPPoE 19644->L2TP
"PPPoE 19644->L2TP:
stop: no more tunnels can be tried"
The drained tunnel can then be closed without user impact.
*A:LAC# tools perform router 65536 l2tp tunnel 1023868928 stop
*A:LAC#
207376 2019/05/22 14:45:01.981 CEST MINOR: DEBUG #2001 vprn65536 L2TP(v2, ctrl,
ingress)
"L2TP(v2, ctrl, ingress): UDP 192.168.33.2:1701 -> 192.168.33.1:1701
tunnel 15623 session 0, ns 2 nr 8, flags:, reserved=0"
207377 2019/05/22 14:46:01.853 CEST MINOR: DEBUG #2001 vprn65536 L2TP(v2, ctrl,
ingress)
"L2TP(v2, ctrl, ingress): UDP 192.168.33.2:1701 -> 192.168.33.1:1701
tunnel 15623 session 0, ns 2 nr 8, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StopControlConnectionNotification(4)
AVP ResultCode(0,1), flags: mandatory, reserved=0
result-code: "generalRequestToClearControlConnection"(1),
error-code: "noGeneralError"(0)
error-msg: "idle timeout (60 seconds) expired"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0
9957"
For draining and undraining for example a group, following commands can be used.
tools perform router 65536 l2tp group "wholesale.com" drain
tools perform router 65536 l2tp group "wholesale.com" no drain
Conclusion
This example provides the LAC L2TP access server configuration and troubleshooting commands for the LAA architecture (tunneled-access) model.