BGP FlowSpec for IPv4 and IPv6
This chapter provides information about BGP FlowSpec for IPv4 and IPv6.
Topics in this chapter include:
Applicability
The configuration and information in this chapter are based on SR OS Release 22.7.R1.
Overview
The base BGP Flow Specification (FlowSpec) is defined in RFC 5575 (Flow Specification) and describes a method of encoding IPv4 flow specification information into Network Layer Reachability Information (NLRI). RFC 8955 updates RFC 5575 and RFC 8956 includes the IPv6 address family. The flow specification is an n-tuple consisting of one or more matching criteria, which can be applied to IP traffic. The FlowSpec NLRI is encoded into Multiprotocol BGP using MP_REACH_NLRI and MP_UNREACH_NLRI attributes.
As well as the flow specification defining match criteria, extended community attributes are defined to provide traffic filtering actions for the specified flow specification. Therefore, a FlowSpec route (MP_REACH_NLRI) contains a description of the traffic to be matched (using FlowSpec NLRI), and the filtering action to be taken with that traffic (using traffic filtering action extended communities). RFC 7674 provided an update to the original RFC 5575 specification to clarify the formatting of some of these traffic actions, notably redirect to VRF.
The use of FlowSpec is to dynamically distribute traffic filtering rules for mitigating distributed denial of service (DDoS) attacks. A router receiving a FlowSpec update can dynamically create IP filters to mitigate both intra-AS and inter-AS DDoS attacks. Mitigation is implemented by dropping traffic at the ingress point of the network (or nearest possible point toward the source of the DDoS attack) or by redirecting traffic to a separate routing context for forwarding (off-ramping) to a traffic-cleansing device. The ability to redirect traffic led to FlowSpec being considered for software defined networking (SDN)-driven applications or network re-optimization tools. In those cases, a subset of traffic needs to be forced (redirected) into a specific routing context or tunnel/label switched path (LSP) for network capacity optimization or to meet a service level agreement (SLA).
BGP FlowSpec uses AFI 1 (IPv4) or AFI 2 (IPv6) with SAFI 133 (IPv4 dissemination of flow specification rules) or SAFI 134 (VPNv4 dissemination of flow specification rules). SR OS supports IPv4 and IPv6. In SR OS Release 22.7.R1 and later, VPN-IPv4 and VPN-IPv6 are also supported.
The FlowSpec NLRI may consist of several components that form the flow specification. A packet only matches the flow specification when it matches all of the components in the NLRI. In the BGP FlowSpec section of the 7450 ESS, 7750 SR, 7950 XRS, and VSR Unicast Routing Protocols Guide, tables Subcomponents of FlowSpec IPv4 and FlowSpec-VPN IPv4 NLRI and Subcomponents of FlowSpec IPv6 and FlowSpec-VPN IPv6 NLRI list the component types that are currently defined, their type values, and their support in SR OS. Flow specification components must follow strict ordering. If present in the specification, a component must precede any other component of higher type value.
The traffic filtering action for a flow specification uses a number of extended community attributes. The attributes standardized in RFC 5575 are listed in the tables IPv4 FlowSpec actions and IPv6 FlowSpec actions in the BGP FlowSpec section of the 7450 ESS, 7750 SR, 7950 XRS, and VSR Unicast Routing Protocols Guide. The traffic rate extended community specifies the rate in bytes per second, where a rate of zero specifies a drop action. The traffic action extended community consists of six bytes; only the two least significant bits of the last byte are currently defined. The terminal action (T-bit), when set to 1, indicates that subsequent filtering rules should be applied (like a next-entry action). When this bit is set to zero, and this action is applied, the evaluation of the traffic filter stops. The sample bit (S-bit), when set to 1, enables traffic sampling and logging for this flow specification. The redirect-to-vrf and mark traffic class extended communities are self-explanatory, with a route-target value being used to define the target redirect VRF.
FlowSpec routes are typically originated and contained within the administrative domain of an operator; particularly when used for DDoS mitigation purposes. This approach means applying ingress filters at the point where traffic enters the autonomous system (AS), such as an external peering point.
These filters should be instantiated as close as possible to the source of the attack traffic, even if that means applying filters within another operator's domain. This means that FlowSpec routes must be exchanged between ASs, requiring a trust relationship between the ASs, and a method for validating FlowSpec routes exchanged across AS boundaries. This is covered in the BGP FlowSpec Route Validation chapter.
Example topology
The example topology used in this chapter is shown in Example topology. PE-1 through PE-6 and RR-7 participate in IS-IS Level-2 and LDP. All these devices are part of network AS 64496, with all PE routers peering in IBGP with the Route Reflector RR-7 for address families IPv4, IPv6, VPN-IPv4, VPN-IPv6, Label-IPv4, Label-IPv6, Flow-IPv4, and Flow-IPv6.
By including the Label-IPv4 and Label-IPv6 address families, generating labeled routes, and resolving these labeled routes to LDP tunnels on all PEs in the topology, IPv4 and IPv6 traffic is tunneled in MPLS.
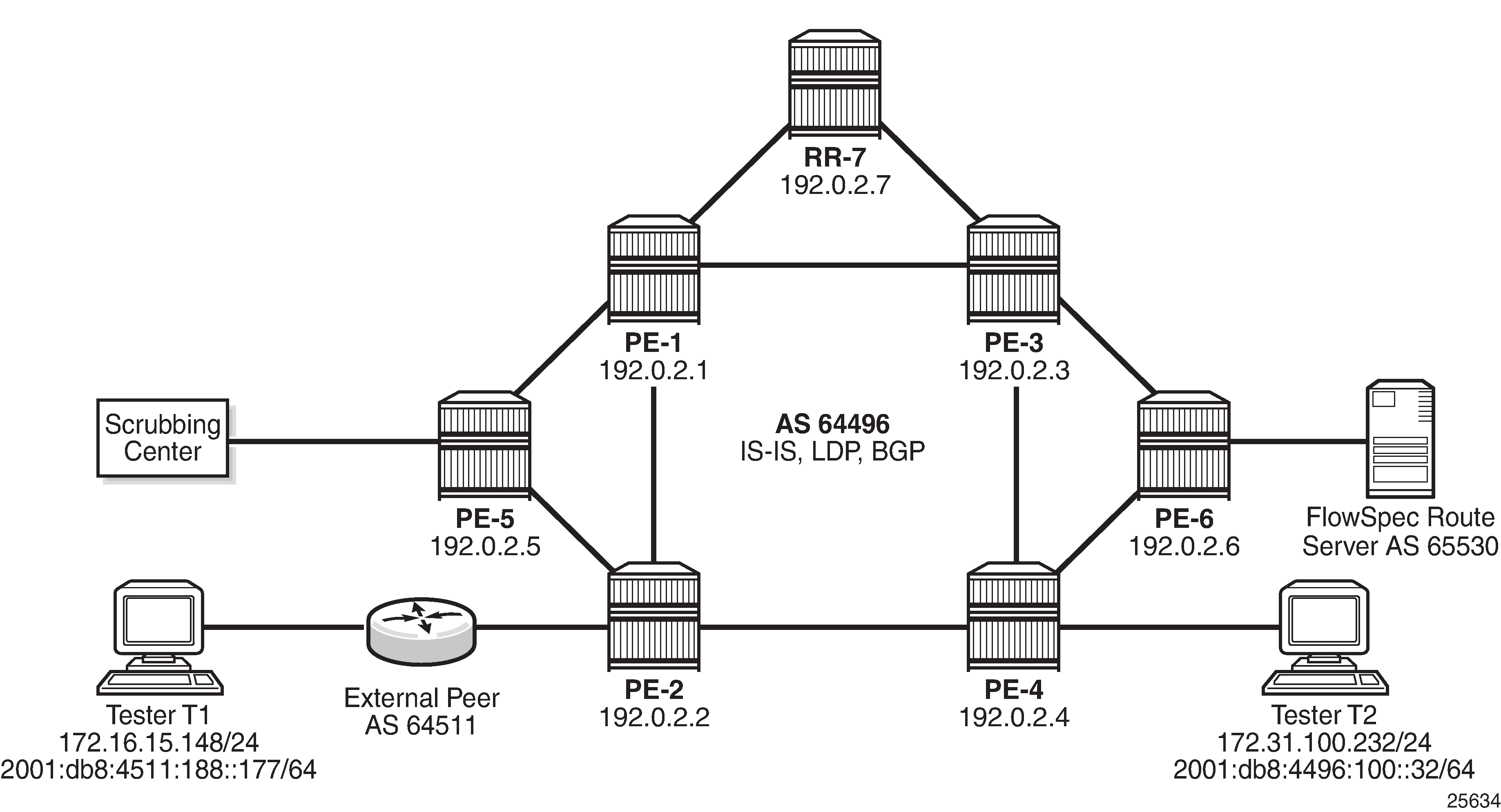
To demonstrate FlowSpec, the following items are connected to AS 64496:
PE-2 is connected to an external peer in AS 64511, which advertises the IPv4 prefix 172.16.0.0/20 and the IPv6 prefix 2001:db8:4511::/48 in EBGP. Both prefixes are advertised within AS 64496 by PE-2 as labeled routes.
PE-4 advertises IPv4 prefix 172.31.100.0/24 and IPv6 prefix 2001:db8:4496::/48 into IBGP, which PE-2 subsequently advertises in EBGP to AS 64511.
Tester T1 is connected to the external peer in AS 64511 and sources and sinks traffic from IPv4 address 172.16.15.148 and IPv6 address 2001:db8:4511:188::177. Tester T2 is connected to PE-4 and sources and sinks traffic from IPv4 address 172.31.100.232 and IPv6 address 2001:db8:4496:100:32.
PE-6 externally peers with a FlowSpec route server belonging to AS 65530.
PE-5 connects to a DDoS scrubbing center with two interfaces:
A "dirty" interface for forwarding of mitigated traffic toward the scrubbing center for cleansing. This interface is connected to an off-ramp VPRN configured on PE-5 and PE-2. PE-5 has static IPv4/IPv6 default routes toward the scrubbing center, which are subsequently advertised into the off-ramp VPRN. This provides sufficient routing information to attract redirected traffic from PE-2 toward the scrubbing center for cleansing.
A "clean" interface for traffic received from the scrubbing center after it has been cleansed. This interface is connected to an IES service and is therefore routed toward its destination using the Global Routing Table (GRT).
Configuration
As an example of FlowSpec configuration, the following output shows the BGP configuration on PE-1. Similar configurations are applied to all other PE routers. All PE routers within AS 64496 peer as clients with RR-7 for the address families IPv4, IPv6, VPN-IPv4, VPN-IPv6, Label-IPv4, Label-IPv6, Flow-IPv4, and Flow-IPv6. The Label-IPv4 and Label-IPv6 address families are required for labeled routes, and the resolution filter enables IPv4 and IPv6 traffic to pass through the MPLS/LDP transport tunnels. The Flow-IPv4 and Flow-IPv6 address families are required for propagating the FlowSpec routes, and represent the only part of the BGP configuration required by FlowSpec.
A:admin@PE-1# admin show configuration /configure router bgp
admin-state enable
path-mtu-discovery false
split-horizon true
group "IBGP" {
type internal
family {
ipv4 true
vpn-ipv4 true
ipv6 true
vpn-ipv6 true
flow-ipv4 true
flow-ipv6 true
label-ipv4 true
label-ipv6 true
}
}
neighbor "192.0.2.7" {
admin-state enable
group "IBGP"
}
PE-2 peers with AS 64511 through an IES service interface using the IPv4 and IPv6 address families, with a dedicated BGP session for each family. This external peering point is the point where the IPv4 and IPv6 filters embedding the flowspec filters are applied. In the following output, these filters are applied in the SAP ingress context, to enable FlowSpec for IPv4 and IPv6, respectively. Such filters can also be enabled on spoke-SDPs within routed interfaces, and is supported within the base and VPRN routing instances.
A:admin@PE-2# admin show configuration /configure service ies 10
admin-state enable
description "Flowspec-test"
customer "1"
interface "to-AS64511" {
sap 1/1/c4/1:10 {
ingress {
filter {
ip "104"
ipv6 "106"
}
}
}
ipv4 {
primary {
address 192.168.2.1
prefix-length 30
}
}
ipv6 {
address 2001:db8:1b0c:2121::2 {
prefix-length 127
}
}
}
FlowSpec operation
With FlowSpec enabled and configured as in previous section, FlowSpec routes can be advertised to dynamically trigger the instantiation of embedded filters. When valid FlowSpec routes are received, the FlowSpec filters are created. These FlowSpec filters must be referenced from the operator-defined IPv4 or IPv6 filters, for example as follows. These operator-defined filters must be applied to the interfaces in the ingress context for FlowSpec to work.
A:admin@PE-2# admin show configuration /configure filter
ip-filter "104" {
default-action accept
embed {
flowspec offset 10000 {
router-instance "Base"
}
}
}
ipv6-filter "106" {
default-action accept
embed {
flowspec offset 10000 {
router-instance "Base"
}
}
}
This section demonstrates the use of FlowSpec for traffic black-holing and traffic redirection for both IPv4 and IPv6.
IPv4 FlowSpec
To validate the instantiation of ingress filters based on IPv4 FlowSpec routes, a bidirectional traffic stream is started between T1 (172.16.15.148) in AS 64511 and T2 (172.31.100.232) in AS 64496. In the T1 to T2 direction, the destination port is TCP port 4191.
An IPv4 FlowSpec route is generated to black-hole/drop traffic with a source address of 172.16.15.148 (T1) and a destination address of 172.31.100.232 (T2), for any destination ports in the range 4191-4198. The following output shows the route as received at PE-2.
<timestamp> MINOR: DEBUG #2001 Base Peer 1: 192.0.2.7
"Peer 1: 192.0.2.7: UPDATE
Peer 1: 192.0.2.7 - Received BGP UPDATE:
Withdrawn Length = 0
Total Path Attr Length = 77
Flag: 0x90 Type: 14 Len: 28 Multiprotocol Reachable NLRI:
Address Family FLOW_IPV4
NLRI len: 22
dest_pref 172.31.100.232/32
src_pref 172.16.15.148/32
ip_proto [ == 6 ]
dest_port [ >4190 ] and [ <4199 ]
Flag: 0x40 Type: 1 Len: 1 Origin: 0
Flag: 0x40 Type: 2 Len: 6 AS Path:
Type: 2 Len: 1 < 65530 >
Flag: 0x40 Type: 5 Len: 4 Local Preference: 100
Flag: 0x80 Type: 9 Len: 4 Originator ID: 192.0.2.6
Flag: 0x80 Type: 10 Len: 4 Cluster ID:
192.0.2.7
Flag: 0xc0 Type: 16 Len: 8 Extended Community:
rate-limit: 0 kbps
"
The route is shown as an MP_REACH_NLRI for address family Flow-IPv4 (AFI 1 SAFI 133). The NLRI uses the source and destination prefixes, the IP protocol, and the destination-port components to describe the flow and create the filter match criteria. The traffic rate extended community is then used to define a rate of 0, which is the filter drop action.
Unlike other address families, there is no strict requirement for the Next-Hop attribute to be present in the MP_REACH_NLRI. The Length of Next-Hop in the Address field can optionally be set to zero and should be ignored on receipt.
The received FlowSpec route can also be verified in the RIB, which provides a concise output of the flow attributes and traffic filtering function, as follows:
A:admin@PE-2# /show router bgp routes flow-ipv4
===============================================================================
BGP Router ID:192.0.2.2 AS:64496 Local AS:64496
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP FLOW IPV4 Routes
===============================================================================
Flag Network Nexthop LocalPref MED
As-Path IGP Cost
-------------------------------------------------------------------------------
u*>? -- 0.0.0.0 100 None
65530
Community Action: redirect-to-vrf:64496:2
Flowspec Components:
Dest Pref : 172.31.100.232/32
Src Pref : 172.16.15.148/32
Ip Proto : [ == 6 ]
Port : [ >4190 ] or [ <4199 ]
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
The dynamically created FlowSpec IPv4 ingress filter is identified as fSpec-0, as follows. The origin indicates entry 256 has been added by BGP Flowspec.
A:admin@PE-2# /show filter ip "fSpec-0" detail
===============================================================================
IP Filter
===============================================================================
Filter Id : fSpec-0
Scope : Embedded
Type : Normal
Shared Policer : Off
Entries : 1 (insert By Bgp)
Sub-Entries : 4 (insert By Bgp)
Description : IPv4 BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 256
Origin : Inserted by BGP FlowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 172.16.15.148/32
Dest. IP : 172.31.100.232/32
Port : port-list "_tmnx_fSpec_ipv4_14_both"
Protocol : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Src Route Opt : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
Tcp-flag : (Not Specified)
Option-pres : Off
Egress PBR : Disabled
Primary Action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IP Prefix Lists
-------------------------------------------------------------------------------
No IP Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv4_14_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IP-filter 104 entry 10256 (Both)
IP-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
The configuration of filter 104 (embedding the fSpec-0 filter) is as follows, and shows a count of ingress matches, which are dropped. This is verified with the loss of traffic in the direction from T1 to T2, but not in the reverse direction.
A:admin@PE-2# /show filter ip 104 detail
===============================================================================
IP Filter
===============================================================================
Filter Id : 104 Applied : Yes
Scope : Template Def. Action : Forward
Type : Normal
Shared Policer : Off
System filter : Unchained
Radius Ins Pt : n/a
CrCtl. Ins Pt : n/a
RadSh. Ins Pt : n/a
PccRl. Ins Pt : n/a
Entries : 0/0/0/1 (Fixed/Radius/Cc/Embedded)
Sub-Entries : 0/0/0/4
Description : (Not Specified)
Filter Name : 104
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10256
Origin : Inserted by embedded filter fSpec-0 entry 256
Description : (Not Specified)
Log Id : n/a
Src. IP : 172.16.15.148/32
Dest. IP : 172.31.100.232/32
Port : port-list "_tmnx_fSpec_ipv4_14_both"
Protocol : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Src Route Opt : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
Tcp-flag : (Not Specified)
Option-pres : Off
Egress PBR : Disabled
Primary Action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IP Prefix Lists
-------------------------------------------------------------------------------
No IP Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv4_14_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IP-filter 104 entry 10256 (Both)
IP-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
When the route is withdrawn and PE-2 receives an MP_UNREACH_NLRI for the same FlowSpec NLRI, the dynamically created filter entries are removed and all associated hardware resources (TCAM entries) are released.
Instead of dropping traffic at the ingress point to the network, an alternative option is to redirect the mitigated traffic to a traffic-cleansing device, if this infrastructure exists. FlowSpec has the redirect-to-vrf extended community for this purpose, with the process of forwarding traffic toward a scrubbing center frequently referred to as off-ramping. At PE-2, a VPRN is configured to off-ramp traffic toward the scrubbing center connected to PE-5, as shown in the following output.
In the case of FlowSpec, traffic redirection is half-duplex. That is, traffic is forwarded from PE-2 toward PE-5, but not from PE-5 toward PE-2. This is because when the traffic has been cleansed, it re-enters the network at PE-5 within an IES, and is therefore routed toward its destination using the GRT. This process is frequently referred to as on-ramping. As a result of this half-duplex traffic flow, only a vrf-target import statement is required. There is no requirement to export any routes from PE-2.
A:admin@PE-2# admin show configuration /configure service vprn "2"
admin-state enable
description "FlowSpec-OffRamp-VRF"
customer "1"
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64496:2"
vrf-target {
import-community "target:64496:2"
}
auto-bind-tunnel {
resolution any
}
}
}
Off-ramping traffic also requires a VPRN service instance in PE-5 with a single SAP toward the scrubbing center, as shown in the following output. Static IPv4 and IPv4 default routes are configured with next hops of the scrubbing center and these are advertised into VPN-IPv4/VPN-IPv6 using route-policy. There is no requirement for PE-5 to import any BGP-VPN routes.
A:admin@PE-5# admin show configuration /configure service vprn "2"
admin-state enable
description "FlowSpec-OffRamp-VRF"
customer "1"
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64496:2"
vrf-export {
policy ["vrf2-export"]
}
}
}
interface "OffRamp-to-Scrubbing-Center" {
ipv4 {
primary {
address 192.168.2.5
prefix-length 30
}
}
sap 1/1/c3/1:10 {
}
ipv6 {
address 2001:db8:1b0c:2121::4 {
prefix-length 127
}
}
}
static-routes {
route 0.0.0.0/0 route-type unicast {
next-hop "192.168.2.6" {
admin-state enable
}
}
route ::/0 route-type unicast {
next-hop "2001:db8:1b0c:2121::5" {
admin-state enable
}
}
}
On-ramping the traffic back onto the network after cleansing the traffic is via IES 3, which is configured as follows. This way the cleansed traffic re-enters the network and is forwarded toward its destination using the GRT.
A:admin@PE-5# admin show configuration /configure service ies "3"
admin-state enable
description "FlowSpec-OnRamp-IES"
customer "1"
interface "OnRamp-from-Scrubbing-Center" {
sap 1/1/c3/1:11 {
}
ipv4 {
primary {
address 192.168.2.6
prefix-length 30
}
}
ipv6 {
address 2001:db8:1b0c:2121::5 {
prefix-length 127
}
}
}
To validate the instantiation of the redirection filter, the same bidirectional traffic stream is started between T1 (172.16.15.148) in AS 64511 and T2 (172.31.100.232) in AS 64496. In the T1 to T2 direction, the destination port is TCP port 4191. When the IPv4 FlowSpec route is received at PE-2, the NLRI shows the same traffic match criteria previously used for the black-hole/drop scenario. The extended community has changed to redirect-to-vrf with a route-target value of 64496:2, as shown in the following output.
<timestamp> MINOR: DEBUG #2001 Base Peer 1: 192.0.2.7
"Peer 1: 192.0.2.7: UPDATE
Peer 1: 192.0.2.7 - Received BGP UPDATE:
Withdrawn Length = 0
Total Path Attr Length = 77
Flag: 0x90 Type: 14 Len: 28 Multiprotocol Reachable NLRI:
Address Family FLOW_IPV4
NLRI len: 22
dest_pref 172.31.100.232/32
src_pref 172.16.15.148/32
ip_proto [ == 6 ]
dest_port [ >4190 ] and [ <4199 ]
Flag: 0x40 Type: 1 Len: 1 Origin: 0
Flag: 0x40 Type: 2 Len: 6 AS Path:
Type: 2 Len: 1 < 65530 >
Flag: 0x40 Type: 5 Len: 4 Local Preference: 100
Flag: 0x80 Type: 9 Len: 4 Originator ID: 192.0.2.6
Flag: 0x80 Type: 10 Len: 4 Cluster ID:
192.0.2.7
Flag: 0xc0 Type: 16 Len: 8 Extended Community:
redirect-to-vrf:64496:2
"
The dynamically created FlowSpec IPv4 ingress filter is identified as fSpec-0, as follows. The filter match criteria for entry 256 indicate the primary action is forward (VRF), and the forwarding router/service ID is service ID 2 (the off-ramp VPRN).
A:admin@PE-2# /show filter ip "fSpec-0" detail
===============================================================================
IP Filter
===============================================================================
Filter Id : fSpec-0
Scope : Embedded
Type : Normal
Shared Policer : Off
Entries : 1 (insert By Bgp)
Sub-Entries : 4 (insert By Bgp)
Description : IPv4 BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 256
Origin : Inserted by BGP FlowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 172.16.15.148/32
Dest. IP : 172.31.100.232/32
Port : port-list "_tmnx_fSpec_ipv4_11_both"
Protocol : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Src Route Opt : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
Tcp-flag : (Not Specified)
Option-pres : Off
Egress PBR : Disabled
Primary Action : Forward (VRF)
Router : 2
Extended Action : None
PBR Down Action : Drop (entry-default)
Ing. Matches : 4 pkts (328 bytes)
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IP Prefix Lists
-------------------------------------------------------------------------------
No IP Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv4_11_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IP-filter 104 entry 10256 (Both)
IP-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
The configuration of filter 1 (embedding the fSpec-0 filter) shows a count of ingress matches, and is as follows:
A:admin@PE-2# /show filter ip 104
===============================================================================
IP Filter
===============================================================================
Filter Id : 104 Applied : Yes
Scope : Template Def. Action : Forward
Type : Normal
Shared Policer : Off
System filter : Unchained
Radius Ins Pt : n/a
CrCtl. Ins Pt : n/a
RadSh. Ins Pt : n/a
PccRl. Ins Pt : n/a
Entries : 0/0/0/1 (Fixed/Radius/Cc/Embedded)
Sub-Entries : 0/0/0/4
Description : (Not Specified)
Filter Name : 104
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10256
Origin : Inserted by embedded filter fSpec-0 entry 256
Description : (Not Specified)
Log Id : n/a
Src. IP : 172.16.15.148/32
Dest. IP : 172.31.100.232/32
Port : port-list "_tmnx_fSpec_ipv4_12_both"
Protocol : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Src Route Opt : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
Tcp-flag : (Not Specified)
Option-pres : Off
Egress PBR : Disabled
Primary Action : Forward (VRF)
Router : 2
Extended Action : None
PBR Down Action : Drop (entry-default)
Ing. Matches : 4 pkts (328 bytes)
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IP Prefix Lists
-------------------------------------------------------------------------------
No IP Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv4_13_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IP-filter 104 entry 10256 (Both)
IP-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
Traffic is correctly received in the T1 to T2 direction, and also in the reverse direction. However, traffic in the T1 to T2 direction is redirected by PE-2 toward the scrubbing center attached to PE-5, before being forwarded to its destination at PE-4.
IPv6 FlowSpec
To validate the instantiation of ingress filters based on IPv6 FlowSpec routes, a bidirectional traffic stream is commenced between T1 (2001:db8:4511:188::177) in AS 64511 and T2 (2001:db8:4496:100::32) in AS 64496. In the T1 to T2 direction, the destination port is TCP port 4191.
An IPv6 FlowSpec route is generated to black-hole/drop traffic with a source address of 2001:db8:4511:188::177 (T1) and a destination address of 2001:db8:4496:100::32 (T2), for any destination ports in the range 4191-4198. The following output shows the route as received at PE-2.
<timestamp> MINOR: DEBUG #2001 Base Peer 1: 192.0.2.7
"Peer 1: 192.0.2.7: UPDATE
Peer 1: 192.0.2.7 - Received BGP UPDATE:
Withdrawn Length = 0
Total Path Attr Length = 103
Flag: 0x90 Type: 14 Len: 54 Multiprotocol Reachable NLRI:
Address Family FLOW_IPV6
NLRI len: 48
dest_pref 2001:db8:4496:100::32/128 offset 0
src_pref 2001:db8:4511:188::177/128 offset 0
ip_proto [ == 6 ]
dest_port [ >4190 ] and [ <4199 ]
Flag: 0x40 Type: 1 Len: 1 Origin: 0
Flag: 0x40 Type: 2 Len: 6 AS Path:
Type: 2 Len: 1 < 65530 >
Flag: 0x40 Type: 5 Len: 4 Local Preference: 100
Flag: 0x80 Type: 9 Len: 4 Originator ID: 192.0.2.6
Flag: 0x80 Type: 10 Len: 4 Cluster ID:
192.0.2.7
Flag: 0xc0 Type: 16 Len: 8 Extended Community:
rate-limit: 0 kbps
"
The route is shown as an MP_REACH_NLRI for address family Flow-IPv6 (AFI 2 SAFI 133). As with the FlowSpec IPv4 example, the NLRI uses the source and destination prefixes, the IP protocol, and the destination-port components to describe the flow and create the filter match criteria. The traffic rate extended community is then used to define a rate of 0, which is equivalent to a filter drop action.
The dynamically created FlowSpec IPv6 ingress filter is identified as fSpec-0, as follows. The description indicates entry 256 has been added through BGP Flowspec.
A:admin@PE-2# show filter ipv6 "fSpec-0" detail
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : fSpec-0
Scope : Embedded
Type : Normal
Shared Policer : Off
Entries : 1 (insert By Bgp)
Sub-Entries : 4 (insert By Bgp)
Description : IPv6 BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 256
Origin : Inserted by BGP FlowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 2001:db8:4511:188::177/128
Dest. IP : 2001:db8:4496:100::32/128
Port : port-list "_tmnx_fSpec_ipv6_14_both"
Next Header : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
Tcp-flag : (Not Specified)
Fragment : Off
HopByHop Opt : Off Routing Type0 : Off
Auth Hdr : Off ESP header : Off
Flow-label : n/a Flow-label Mask: n/a
Egress PBR : Disabled
Primary Action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IPv6 Prefix Lists
-------------------------------------------------------------------------------
No IPv6 Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv6_14_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IPv6-filter 106 entry 10256 (Both)
IPv6-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
The configuration of filter 106 (embedding the fSpec-0 filter) is as follows, and shows a count of ingress matches, which are dropped (primary action is drop). This is observed with the loss of traffic in the direction from T1 to T2, but not in the reverse direction.
A:admin@PE-2# /show filter ipv6 106 detail
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 106 Applied : Yes
Scope : Template Def. Action : Forward
Type : Normal
Shared Policer : Off
System filter : Unchained
Radius Ins Pt : n/a
CrCtl. Ins Pt : n/a
RadSh. Ins Pt : n/a
PccRl. Ins Pt : n/a
Entries : 0/0/0/1 (Fixed/Radius/Cc/Embedded)
Sub-Entries : 0/0/0/4
Description : (Not Specified)
Filter Name : 106
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 10256
Origin : Inserted by embedded filter fSpec-0 entry 256
Description : (Not Specified)
Log Id : n/a
Src. IP : 2001:db8:4511:188::177/128
Dest. IP : 2001:db8:4496:100::32/128
Port : port-list "_tmnx_fSpec_ipv6_14_both"
Next Header : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
Tcp-flag : (Not Specified)
Fragment : Off
HopByHop Opt : Off Routing Type0 : Off
Auth Hdr : Off ESP header : Off
Flow-label : n/a Flow-label Mask: n/a
Egress PBR : Disabled
Primary Action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IPv6 Prefix Lists
-------------------------------------------------------------------------------
No IPv6 Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv6_14_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IPv6-filter 106 entry 10256 (Both)
IPv6-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
The FlowSpec IPv6 route with the drop action is subsequently withdrawn, restoring the traffic flow between T1 and T2.
To off-ramp IPv6 traffic toward the scrubbing center, the same redirect infrastructure is used as in the IPv4 example:
PE-2 and PE-5 use the same off-ramp VPRN (VPRN 2), which transports both VPN-IPv4 and VPN-IPv6 traffic.
PE-5 uses the same on-ramp (IES). When traffic is returned from the scrubbing center, PE-5 routes packets toward their destination using the GRT.
An IPv6 FlowSpec route with a redirect-to-vrf extended community is then sourced by the FlowSpec route generator. When the route is received at PE-2, the NLRI shows the same traffic match criteria previously used for the IPv6 black-hole/drop scenario. The extended community has changed to redirect-to-vrf with a route-target value of 64496:2, as shown in the following output.
<timestamp> CEST MINOR: DEBUG #2001 Base Peer 1: 192.0.2.7
"Peer 1: 192.0.2.7: UPDATE
Peer 1: 192.0.2.7 - Received BGP UPDATE:
Withdrawn Length = 0
Total Path Attr Length = 103
Flag: 0x90 Type: 14 Len: 54 Multiprotocol Reachable NLRI:
Address Family FLOW_IPV6
NLRI len: 48
dest_pref 2001:db8:4496:100::32/128 offset 0
src_pref 2001:db8:4511:188::177/128 offset 0
ip_proto [ == 6 ]
dest_port [ >4190 ] and [ <4199 ]
Flag: 0x40 Type: 1 Len: 1 Origin: 0
Flag: 0x40 Type: 2 Len: 6 AS Path:
Type: 2 Len: 1 < 65530 >
Flag: 0x40 Type: 5 Len: 4 Local Preference: 100
Flag: 0x80 Type: 9 Len: 4 Originator ID: 192.0.2.6
Flag: 0x80 Type: 10 Len: 4 Cluster ID:
192.0.2.7
Flag: 0xc0 Type: 16 Len: 8 Extended Community:
redirect-to-vrf:64496:2
"
The dynamically created FlowSpec IPv4 ingress filter is identified as fSpec-0, as follows. The filter match criteria for entry 256 indicate the primary action is forward (VRF), and the forwarding router/service ID is service ID 2 (the off-ramp VPRN).
A:admin@PE-2# /show filter ipv6 "fSpec-0" detail
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : fSpec-0
Scope : Embedded
Type : Normal
Shared Policer : Off
Entries : 1 (insert By Bgp)
Sub-Entries : 4 (insert By Bgp)
Description : IPv6 BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 256
Origin : Inserted by BGP FlowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 2001:db8:4511:188::177/128
Dest. IP : 2001:db8:4496:100::32/128
Port : port-list "_tmnx_fSpec_ipv6_15_both"
Next Header : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
Tcp-flag : (Not Specified)
Fragment : Off
HopByHop Opt : Off Routing Type0 : Off
Auth Hdr : Off ESP header : Off
Flow-label : n/a Flow-label Mask: n/a
Egress PBR : Disabled
Primary Action : Forward (VRF)
Router : 2
Extended Action : None
PBR Down Action : Drop (entry-default)
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IPv6 Prefix Lists
-------------------------------------------------------------------------------
No IPv6 Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv6_15_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IPv6-filter 106 entry 10256 (Both)
IPv6-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
The configuration of IPv6 filter 106 (embedding the fSpec-0 filter) shows a count of ingress matches, and is as follows:
A:admin@PE-2# /show filter ipv6 106 detail
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 106 Applied : Yes
Scope : Template Def. Action : Forward
Type : Normal
Shared Policer : Off
System filter : Unchained
Radius Ins Pt : n/a
CrCtl. Ins Pt : n/a
RadSh. Ins Pt : n/a
PccRl. Ins Pt : n/a
Entries : 0/0/0/1 (Fixed/Radius/Cc/Embedded)
Sub-Entries : 0/0/0/4
Description : (Not Specified)
Filter Name : 106
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 10256
Origin : Inserted by embedded filter fSpec-0 entry 256
Description : (Not Specified)
Log Id : n/a
Src. IP : 2001:db8:4511:188::177/128
Dest. IP : 2001:db8:4496:100::32/128
Port : port-list "_tmnx_fSpec_ipv6_15_both"
Next Header : 6
Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
Tcp-flag : (Not Specified)
Fragment : Off
HopByHop Opt : Off Routing Type0 : Off
Auth Hdr : Off ESP header : Off
Flow-label : n/a Flow-label Mask: n/a
Egress PBR : Disabled
Primary Action : Forward (VRF)
Router : 2
Extended Action : None
PBR Down Action : Drop (entry-default)
Ing. Matches : 799 pkts (102272 bytes)
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IPv6 Prefix Lists
-------------------------------------------------------------------------------
No IPv6 Prefix Lists
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
Port list "_tmnx_fSpec_ipv6_15_both"
0-4198 4191-65535
NUM ports/ranges: 2
References:
IPv6-filter 106 entry 10256 (Both)
IPv6-filter fSpec-0 entry 256 (Both)
NUM references: 2
NUM Port Lists: 1
-------------------------------------------------------------------------------
Filter Match Protocol Lists
-------------------------------------------------------------------------------
No Protocol Lists
===============================================================================
Traffic is correctly received in the T1 to T2 direction, and also in the reverse direction. However, traffic in the T1 to T2 direction is redirected by PE-2 toward the scrubbing center attached to PE-5, before being forwarded to its destination at PE-4.
Resource consumption
Similar to static filters consuming hardware resources, dynamically instantiated FlowSpec filters consume hardware resources (TCAM entries) on the associated line cards. Therefore, resources must be checked and monitored to ensure that the system operates within its scaling boundaries.
Before the activation of any FlowSpec routes, there are two ingress ACL/QoS entries consumed for IPv4 and another two entries for IPv6, as shown in the following output.
A:admin@PE-2# /tools dump resource-usage system all | match 'Usage|Free|ACL Entries'
Resource Usage Information for System
Total Allocated Free
Resource Usage Information for Card Slot #1
Total Allocated Free
Resource Usage Information for Card Slot #1 FP #1
Total Allocated Free
Ingress ACL Entries (IPv4/v6) | 98304 2 98302
Egress ACL Entries (IPv4/v6) | 49152 2 49150
Resource Usage Information for Card Slot #1 MDA #1
Total Allocated Free
Resource Usage Information for Card Slot #1 MDA #2
Total Allocated Free
When a FlowSpec IPv4 rule matching on a source/destination IP address is dynamically instantiated, one additional ACL entry is consumed in hardware, as shown in the following output.
A:admin@PE-2# /tools dump resource-usage system all | match 'Usage|Free|ACL Entries'
Resource Usage Information for System
Total Allocated Free
Resource Usage Information for Card Slot #1
Total Allocated Free
Resource Usage Information for Card Slot #1 FP #1
Total Allocated Free
Ingress ACL Entries (IPv4/v6) | 98304 3 98301
Egress ACL Entries (IPv4/v6) | 49152 2 49150
Resource Usage Information for Card Slot #1 MDA #1
Total Allocated Free
Resource Usage Information for Card Slot #1 MDA #2
Total Allocated Free
TCAM entries are not consumed on a per-interface basis. When TCAM entries are consumed on a line card for a FlowSpec NLRI match criteria, the same criteria can be used for filtering across multiple IP interfaces on the same line card without consuming additional TCAM entries.
Conclusion
FlowSpec IPv4 and IPv6 provide a dynamic way to activate (and tear down) ingress filters to mitigate against DDoS attacks. SR OS supports a wide range of match criteria (FlowSpec NLRI) coupled with the ability to either drop or redirect mitigated traffic. This offers flexibility not only in what traffic is matched, but also in traffic treatment, depending on the availability of a traffic-cleansing infrastructure.
The ability of FlowSpec to dynamically create and remove filters has some immediate benefits:
Reduces the likelihood of configuration errors on one or more devices
Allows for temporary use of hardware resources, which are released when the threat has passed
Allows for a push configuration from a single point to a potentially large number of network devices, without having to visit each one to configure filters manually.