L2-aware NAT (with dNAT and MNPs)
This chapter provides information about Network Address Translation (NAT) in combination with Enhanced Subscriber Management (ESM).
Topics in this chapter include:
Applicability
The information and configuration in this chapter are applicable to all SR OS nodes that support Broadband (BB) MS-ISAs, including the virtual version of MS-ISA in VSR, and was tested on SR OS 15.0.R4.
Overview
L2-aware network address translation (NAT) is an enhanced NAT functionality that offers better IPv4 address conservation ratios than traditional NAT44. L2-aware NAT relies on tight integration between enhanced subscriber management (ESM) and NAT, and in the context of ESM, it maps (or binds) an ESM subscriber to an outside IP address and a single port block (PB). In this fashion, the private (inside) IPv4 address in L2-aware NAT is abstracted from the binding.
Binding is distinct from the flow/session concept. Flow or session state is maintained for each specific conversation between the two end nodes (this includes IP addresses, ports, and protocol), whereas binding is mapping between an inside entity (the subscriber ID in L2-aware NAT or the IPv4 source IP address in large scale NAT44 (LSN44)) and the outside IP address and the PB. Flows/session can then consume ports within the PB.
On the public side (outside), L2-aware NAT allows multiple hosts (inside IPv4 addresses) under the same subscriber to share the same outside IPv4 address and a PB. This contrasts with traditional NAT44 where each inside IPv4 address (host) is mapped to a unique IPv4 address and PB combination.
On the private side (inside), the abstraction of the host IPv4 address from the binding allows assignment of the same inside IPv4 address to multiple hosts that belong to different subscribers. This sharing of an inside IPv4 address between hosts that belong to different subscribers means that each host still has its own instance of the shared IPv4 address. For example, host 1 of subscriber 1 and host 2 of subscriber 2 can be both assigned the same inside IP address (for instance 10.10.1.1).
A binding in L2-aware NAT is defined as the following:
<subId, nat-policy> → <outside routing context, outside srcIP address, outside PB>
Where:
Inside |
|
|
Subscriber ID in the ESM context. |
|
NAT policy associated with the ESM subscriber. This association is performed within the sub-profile. A subscriber can have multiple NAT policies (MNPs), in which case each subscriber will have one binding per NAT policy. |
Outside |
|
|
Outside routing context that contains an L2-aware pool. NAT traffic is sent out of the node via this routing context. |
|
A subscriber in conjunction with the NAT policy is assigned this outside IP address. The source IP address of the subscriber traffic will be replaced by this IP address. |
|
A subscriber in conjunction with the NAT policy is assigned this outside PB. A source (TCP/UDP) port of the subscriber traffic will be replaced by one of the source ports from this PB. In the ICMP case, the query ID is selected from this PB. |
A simplified example of an L2-aware NAT binding is shown in NAT Binding. Subscriber 1 is mapped to the outside IP address 172.16.1.1 and PB 1. This means that the source IP addresses (10.10.1.1 and 10.10.1.2) for all hosts under Subscriber 1 will be translated to 172.16.1.1 and the source port will be translated to one of the ports from PB 1. Similar logic can be applied to Subscriber 2 mappings, where Subscriber 2 hosts will use PB 2 from the same outside IP address.
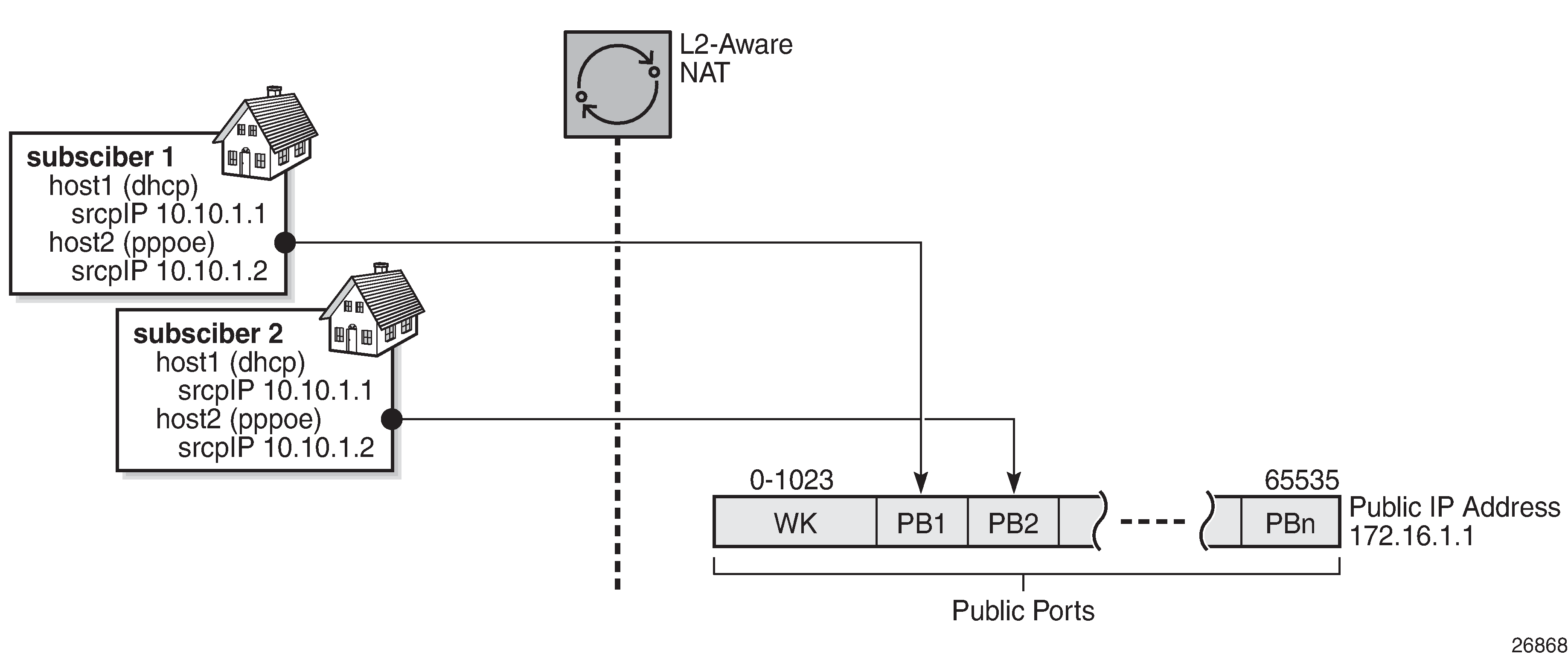
NAT binding in MS-ISA will be used to translate traffic arriving from the subscriber. When the first packet of the flow from the subscriber is received, the translation is performed and a flow state is created. This flow state is maintained for the duration of the flow. All consecutive packets of the flow will rely on the flow state lookup for translation.
The flow mapping in L2-aware NAT is characterized as:
<subId, inside srcIP address, inside srcPort, foreign ip address, foreign port, protocol> → <outside routing context, outside IP address, outside port, destination ip address, foreign port, protocol>
Flow mapping is more specific than a binding (which is a partial mapping), and the fields in flow mapping are self-explanatory. The flow mapping contains the original source IP address, which is needed to determine where to send the return (downstream) traffic.
The subId field needs to be unique in the mappings at the subscriber level, allowing all the other fields (including the source IP address) to overlap between the subscribers. This is the basis for sharing of the source IP addresses between the subscribers.
In flow mapping, there is a naming distinction between the foreign IP address and the destination IP address. A foreign IP address is the original destination IP address in the packet sourced by the host. This foreign IP address can be translated by destination-based NAT (dNAT), just like source IP is translated by NAT. In this case, the translated foreign IP address on the outside in the SR OS CLI syntax becomes a destination IP address. This naming distinction helps to differentiate two IP addresses of the same field in the IP header, one before dNAT is performed and the other after dNAT is performed.
The reason why there is only a foreign port (and no destination port) is that in SR OS the original destination port is not translated by dNAT, while the original destination IP is.
L2-aware NAT requires that ESM and NAT are collocated in the same SR OS node. Because of the tight integration between ESM and NAT, logging of L2-aware NAT resources can be integrated into ESM accounting via AAA.
This chapter does not discuss L2-aware NAT intra-chassis redundancy. Intra-chassis redundancy for L2-aware NAT offers protection against MS-ISA failure. The supported modes are:
Active/Standby MS-ISA
Active/Active MS-ISA
L2-aware Bypass
Each L2-aware NAT intra-chassis redundancy mode is described in the 7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Guide.
Configuration
The test setup in this configuration example will accommodate:
Two L2-aware subscribers.
Two hosts per L2-aware subscriber – one DHCPv4 host and one PPPoEv4 host per L2-aware subscriber.
IP addresses overlap between the subscribers.
Traffic split from a single host to three different NAT pools and outside routing contexts. This is achieved by selecting a NAT policy based on the destination IP address of the traffic.
Destination-based NAT (dNAT) – some of the traffic is subjected to dNAT, where the destination IP address in the outgoing packet is translated (in addition to the source IP address and source port).
The test setup is shown in Test Setup.
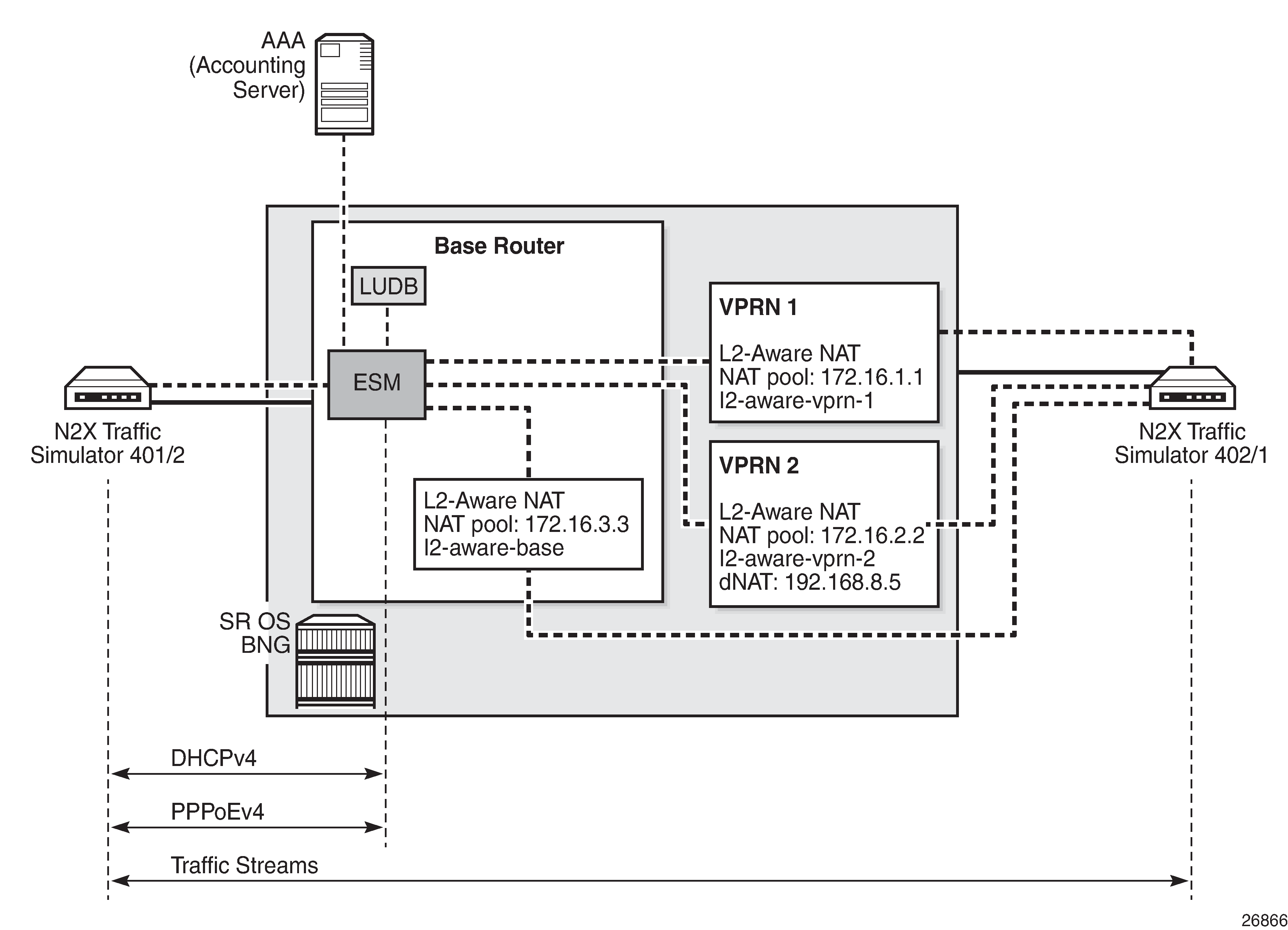
The N2X traffic simulator on the left is used to simulate two homes (subscribers) with DHCPv4 and PPPoE hosts. Those hosts are terminated on an IES interface in a Base router in the BNG and they are further associated with the L2-aware NAT pools in VPRN1, VPRN2, and the Base router. ESM host authentication and IP address assignment is performed via local user database (LUDB). Accounting for the subscribers is sent to an AAA server and the accounting records contain NAT logging information.
Once the subscriber hosts are instantiated, traffic is sent through L2-aware NAT. This traffic is then used to further examine operation of L2-aware NAT in SR OS BNG.
The L2-aware NAT configuration in SR OS is split into two major parts:
NAT-specific configuration – this is the subject of this document.
ESM-specific configuration focuses on ESM subscribers and is described in other chapters in this volume. There are some key parts of ESM configuration that are essential for understanding L2-aware NAT operation and those parts will be described in this section.
For the sake of completeness, the remaining, more generic part of ESM configuration is described in Appendix A – Generic ESM Configuration.
NAT-specific Configuration
L2-aware NAT requires the system IP address to be configured in the node. Without the system IP address, L2-aware NAT will not be operational. Lack of the system IP address within the L2-aware node is a common problem in most troubleshooting scenarios. The system IP is used within the system to pass traffic between the carrier IOM (where MS-ISA is attached) and the MS-ISA itself. The following is the command to configure the system IP address:
configure
router
interface "system"
address 192.0.2.2/32
no shutdown
exit
The inside NAT context in the following code identifies the private (inside) side of NAT, which in this example is configured in the Base routing context.
The address in the l2-aware context (in this example, address 10.10.1.254/24) represents the default gateway and an L2-aware subnet. All ESM hosts with IP addresses within the configured L2-aware subnet (in this example, 10.10.2.0/24) are subjected to L2-aware NAT.
ESM hosts with IP addresses out of the L2-aware subnet can be instantiated as regular (not L2-aware) hosts, effectively bypassing L2-aware NAT within the L2-aware enabled subscriber.
The outside NAT context contains the NAT pool configuration that is used for address translation. In this example, traffic is mapped to three outside contexts: Base, VPRN 1, and VPRN 2. IP address 172.16.3.3 is used for translation in the Base outside routing context, IP address 172.16.1.1 in the VPRN 1 outside routing context, and IP address 172.16.2.2 in the VPRN 2 outside routing context.
VPRN 1 and VPRN 2 also contain NAT pools with their own IP addresses.
configure
router
nat
inside
l2-aware
address 10.10.1.254/24
exit
exit
outside
pool "l2-aware-base" nat-group 1 type l2-aware create
port-reservation ports 2000
address-range 172.16.3.3 172.16.3.3 create
exit
no shutdown
exit
exit
exit
configure
service
vprn 1 name "1" customer 1 create
nat
outside
pool "l2-aware-vprn-1" nat-group 1 type l2-aware create
port-reservation ports 2000
address-range 172.16.1.1 172.16.1.1 create
exit
no shutdown
exit
exit
exit
exit
vprn 2 name "2" customer 1 create
nat
outside
port-reservation ports 2000
pool "l2-aware-vprn-2" nat-group 1 type l2-aware create
address-range 172.16.2.2 172.16.2.2 create
exit
no shutdown
exit
exit
exit
exit
NAT pool selection (and with this, the outside routing context) is performed based on the foreign IP address (traffic destination) in the packet. This is configured in the nat-prefix-list, which is then applied to the L2-aware subscriber via sub-profile.
Packets arriving from the inside and destined to networks 192.168.7.0/24 and 192.168.8.0/24 will be respectively routed to the VPRN 1 and VPRN 2 routing context, which are implied through NAT policies ‟l2-aware-vrf1” and ‟l2-aware-vrf2” referenced in the nat-prefix-list.
All other traffic will use the default NAT policy ‟l2-aware-base”, which is directly referenced in the sub-profile. This NAT policy is pointing to the Base outside routing context. Also, traffic identified by NAT classifier ‟vrf2” will be subject to dNAT.
In the example, NAT classifier ‟vrf2” identifies UDP traffic destined to port 5001. This implies that destination IP address for traffic that is mapped to VPRN 2 with UDP destination port 5001 will be translated. The new destination IP address (192.168.8.5) is configured in the NAT classifier ‟vrf2”, which is then applied via NAT policy ‟l2-aware-vrf2”.
All other traffic (destined to a destination UDP port other than 5001) will pass transparently through the classifier without the destination IP address being modified. Traffic that is subject to dNAT can be identified (or classified) based on destination-port only.
The block-limit command in L2-aware pool is automatically set to ‟1”. That is, each L2-aware subscriber is assigned exactly one PB. Additional PB allocation is not supported. That is why it is important that this single PB allocated to each L2-aware subscriber is initially configured with a large enough number of ports – this is performed via pool configuration (in this example, port-block size is set to 2000 ports). Once all the ports in this PB are exhausted, no new ports can be allocated.
configure
subscriber-mgmt
sub-profile "sub-prof-1" create
nat-policy "l2-aware-base"
nat-prefix-list "l2aware-mnp"
exit
configure
service
nat
nat-classifier "vrf2" create
entry 1 create
action dnat ip-address 192.168.8.5
match protocol udp
dst-port-range start 5001 end 5001
exit
exit
exit
nat-policy "l2-aware-base" create
block-limit 1
pool "l2-aware-base" router Base
exit
nat-policy "l2-aware-vrf1" create
block-limit 1
pool "l2-aware-vprn-1" router 1
exit
nat-policy "l2-aware-vrf2" create
dnat
nat-classifier "vrf2"
exit
exit
nat-prefix-list "l2aware-mnp" application l2-aware-dest-to-policy create
prefix 192.168.7.0/24 nat-policy "l2-aware-vrf1"
prefix 192.168.8.0/24 nat-policy "l2-aware-vrf2"
exit
exit
On the ESM side, anti-spoof configuration is of particular importance in L2-aware NAT.
L2-aware deployments with bridged homes (multiple ESM hosts within a subscriber) must have the anti-spoofing option set to ip-mac. This will allow each host within the home to be distinctly identified in ESM and consequently receive proper ESM treatment (filters, QoS, accounting, and so on).
L2-aware deployments with routed CPEs must have the anti-spoofing option set to nh-mac. In this case, only one host per ESM subscriber is allowed and this single host is the routed CPE. There can be multiple hosts behind this routed CPE and they will be all seen and properly treated (using NAT) by the MS-ISA. However, ESM will not be aware of them and all downstream traffic will be sent to the routed CPE (ESM host), which will then further route traffic to the proper destination.
From an ESM perspective, this approach is different from that for non-L2-aware ESM deployments. Non-L2-aware ESM deployments allow multiple ESM hosts per subscriber with the nh-mac anti-spoofing option enabled, where the ESM hosts have different MACs.
configure
subscriber-mgmt
msap-policy "msaps" create
sub-sla-mgmt
sub-ident-policy "sub_ident_pol"
multi-sub-sap limit 10
exit
ies-vprn-only-sap-parameters
anti-spoof ip-mac
exit
exit
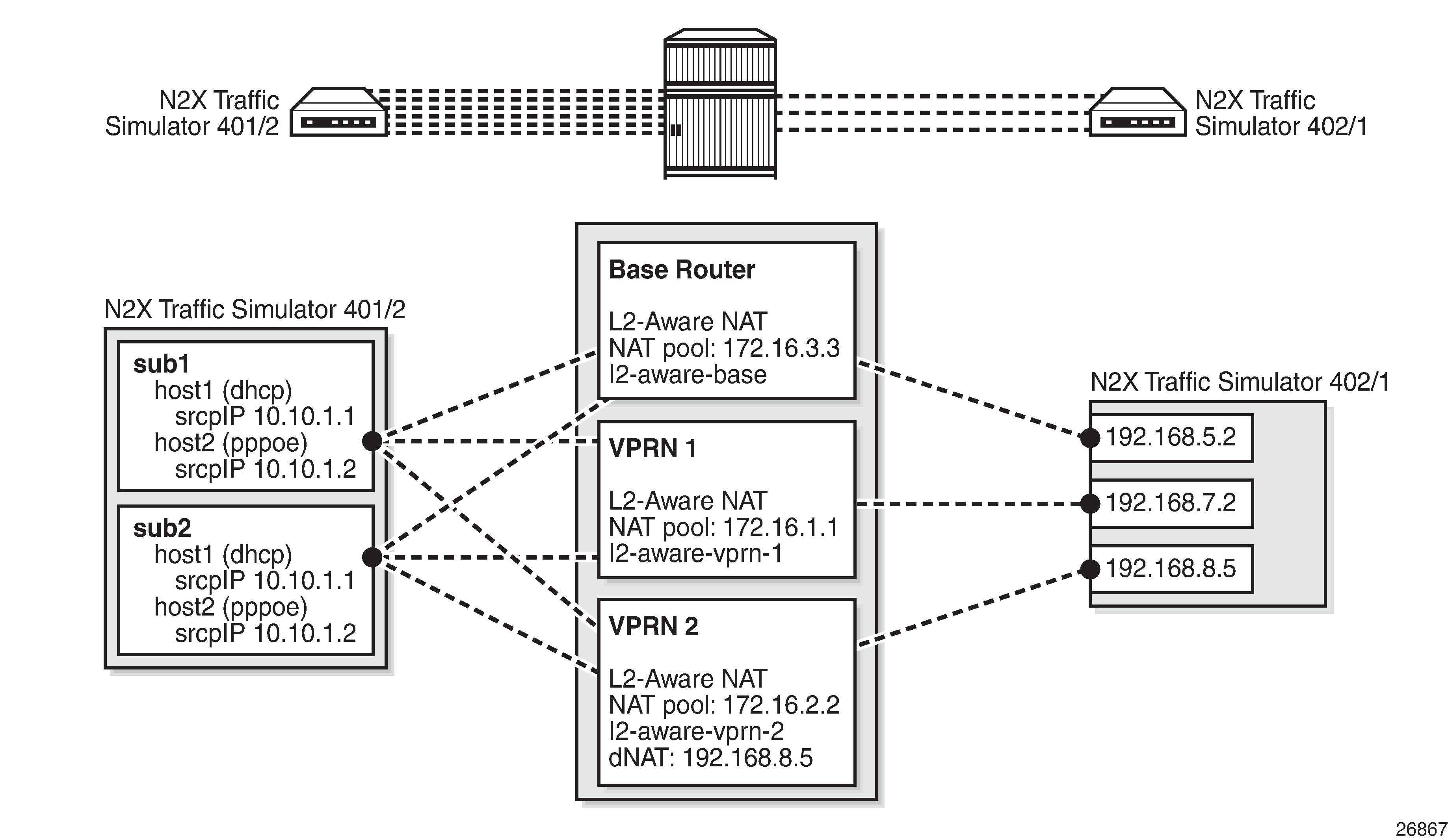
This preceding described configuration is shown in Logical Mapping of Subscribers to L2-aware Pool.
Logging
In this example, NAT logging is integrated with ESM accounting. This is configuration dependent and L2-aware NAT also supports syslog to convey information, about a subscriber that is hidden behind NAT, to the operator.
With RADIUS logging, NAT-specific information is carried in the Alc-Nat-Port-Range VSA, which must be explicitly enabled in accounting-policy. The ESM accounting model used in this example is per host-accounting with interim updates. For brevity, only the accounting records for host 1 of the subscriber 1 are shown following:
Acct Start is generated when the ESM host is created. The first host for the subscriber will allocate NAT resources in the MS-ISA.
Acct Interim-Update message is generated periodically (configuration dependent) and additionally carries information about consumed bytes flowing through queues/policers associated with the subscriber host.
Acct Stop is generated when the ESM host is terminated. NAT resources are then released. The significance of this is that freeing the NAT resources coincides with the termination of the subscriber, without having to wait for NAT flows in the MS-ISA to time out, long after the user has ceased.
Appendix B – Logging lists a more comprehensive stream of logs for all four hosts that are established in this exercise.
root@linux:/var/log/freeradius/radacct/192.168.114.2# more detail-20170814
Mon Aug 14 09:14:45 2017
Acct-Status-Type = Start
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:29:02 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502727285
Request-Authenticator = Verified
Mon Aug 14 09:20:11 2017
Acct-Status-Type = Interim-Update
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Session-Time = 326
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:34:28 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Alc-Acct-Triggered-Reason = regular
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x0001000000000000b220
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000001c8
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502727611
Request-Authenticator = Verified
Mon Aug 14 09:30:34 2017
Acct-Status-Type = Stop
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Session-Time = 949
Acct-Terminate-Cause = User-Request
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:44:51 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00010000000000037974
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000008e5
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502728234
Request-Authenticator = Verified
root@linux:/var/log/freeradius/radacct/192.168.114.2#
Operational Commands
In this example, three streams of traffic are run from host 1 of each subscriber (six streams in total). Traffic flows in the upstream direction (from the inside routing context to the outside routing context) and it will cause L2-aware NAT to allocate resources and create mappings that can be observed with the show and debug commands.
Host 1 of each subscriber is initiating three streams to three different destinations. Accordingly, traffic from the same host will be (based on the destination) routed to three different L2-aware NAT pools and outside routing contexts. One of the streams (stream 3) will, in addition to its source IP address/port, have its destination IP address translated as well.
The six traffic stream definitions are shown in Traffic Streams:
All six streams have the same source IP address, 10.10.1.1. The significance of this is that both subscribers have hosts that are assigned the same inside (private) IP address.
All streams carry UDP protocol.
The source UDP port is 5000 for all streams.
The UDP foreign port is 5000 except for the stream 3, which is assigned UDP foreign port 5001. Traffic with the foreign port 5001 is identified through the NAT classifier and is selected for dNAT (foreign IP address will be translated).
Each host sends traffic to three different destinations and this is signified by three different foreign IP addresses:
The stream with the foreign IP address 192.168.5.2 is sent to the Base routing context (
pool l2-aware-base).The stream with the foreign IP address 192.168.7.2 is sent to the VPRN 1 routing context (
pool l2-aware-vprn-1).The stream with the foreign IP address 192.168.8.2 is sent to the VPRN 2 routing context (
pool l2-aware-vprn-2).
The column labelled Out IP (Outside IP address) represents a newly translated source (private) IP address by L2-aware NAT. Each of the three pools (one per routing context in Base, VPRN 1, and VPRN 2) has its own single outside IP address configured. In this example, each pool has a single outside IP address configured but, usually, multiple address ranges per NAT pool are supported.
Each subscriber is allocated a single PB per pool with 2000 ports (configuration dependent) in each pool – this is reflected in the PB column. Subscriber 1 is allocated the same PB range in all three pools (one per routing context). A similar setup is shown for subscriber 2.
In this example, the PBs allocated per subscriber in three pools coincidentally match due to a low number of subscribers in the system (only two subscribers in our example). Usually, with an increased number of subscribers in the system, the probability for matching PB allocations per subscriber across pools would decrease. That is, each pool allocates PB independently of any other pool.
The Out Port column indicates a new (translated) source UDP source port, after L2-aware NAT is performed.
The Dest IP column indicates that the foreign IP address is modified only for stream 3, which is subject to dNAT (identified by UDP foreign port 5001 via a NAT classifier). The remaining streams do not have foreign IP addresses translated.
The Destination ports on the outside in all three streams remain unchanged. This applies even for stream 3, which is subject to dNAT (only the foreign IP address is translated by dNAT functionality).
Dynamically allocated parameters by L2-aware NAT are in the following traffic streams table (fields in bold typeface - Out IP, PB, Out Port, Dest IP) populated based on the observation in the system once the traffic is run. The values are collected based on the output provided by debug commands and a tools dump nat sessions command (both of them are shown further in the text).
|
Host |
Strm |
Packet Fields Before NAT (inside routing context – Base) |
Packet Fields After NAT (outside routing context) |
|||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Src IP |
Prot |
Src Port |
Forgn Port |
Forgn IP |
Outside Rtr |
Out IP |
PB |
Out Port |
Dest IP |
Dest Port |
||
|
Sub1 Host1 |
1 |
10.10.1.1 |
UDP |
5000 |
5000 |
192.168.5.2 |
Base |
172.16.3.3 |
1024-3023 |
2186 |
192.168.5.2 |
5000 |
|
2 |
192.168.7.2 |
VRF1 |
172.16.1.1 |
1024-3023 |
1124 |
192.168.7.2 |
||||||
|
3 |
5001 |
192.168.8.2 |
VRF2 |
172.16.2.2 |
1024-3023 |
3690 |
192.168.8.5 |
5001 |
||||
|
Sub2 Host1 |
4 |
10.10.1.1 |
UDP |
5000 |
5000 |
192.168.5.2 |
Base |
172.16.3.3 |
3024-5023 |
4470 |
192.168.5.2 |
5000 |
|
5 |
192.168.7.2 |
VRF1 |
172.16.1.1 |
3024-5023 |
4666 |
192.168.7.2 |
||||||
|
6 |
192.168.8.2 |
VRF2 |
172.16.2.2 |
3024-5023 |
4698 |
192.168.8.2 |
||||||
Show Commands
A good starting point for troubleshooting is a generic NAT command, show service nat overview, with the output that would normally point to misconfiguration:
*A:BNG1# show service nat overview
===============================================================================
NAT overview
===============================================================================
Inside/ Policy/ Type
Outside Pool
-------------------------------------------------------------------------------
* l2-aware-base l2aware
Base l2-aware-base
* l2-aware-vrf1 l2aware
vprn1 l2-aware-vprn-1
* l2-aware-vrf2 l2aware
vprn2 l2-aware-vprn-2
===============================================================================
No firewall policies found.
*A:BNG1#
The output of the show port statistics command provides information relevant to packet flow between the carrier IOM (to which the MS-ISA is attached) and the MS-ISA itself.
In the following output, ‟1/2/nat-in-l2” is the port on the carrier IOM that represents the private (inside) side of NAT and ‟1/2/nat-out-ip” is the port on the carrier IOM that represents the public (outside) side of NAT. In this example, traffic is sent only in one direction, from private side to public side, and therefore:
Traffic is egressing port ‟1/2/nat-in-l2” on the IOM and entering MS-ISA on the private side (11789 packets).
Traffic is leaving MS-ISA on the public side and ingressing port ‟1/2/nat-out-ip” on the IOM (11789 packets).
*A:BNG1# show port statistics
===============================================================================
Port Statistics on Slot 1
===============================================================================
Port Ingress Ingress Egress Egress
Id Packets Octets Packets Octets
-------------------------------------------------------------------------------
1/1/2 223162 25147835 0 0
1/1/3 815114 78685140 614895 60630323
1/1/4 15484 1531339 230226 25728265
1/1/5 84116 8375228 1054 69854
1/1/10 5115 835288 345 110442
1/2/nat-out-ip 11789 1131744 0 0
1/2/nat-in-l2 0 0 11789 1532570
===============================================================================
Port Statistics on Slot A
===============================================================================
Port Ingress Ingress Egress Egress
Id Packets Octets Packets Octets
-------------------------------------------------------------------------------
A/1 81952168 0 28663 2721059
===============================================================================
NAT resources are allocated during the subscriber instantiation phase (when the first host for an L2-aware subscriber is created), before any data traffic from the subscriber side is even initiated.
The following command is run to verify that the two subscribers, each with two hosts (one DHCP and one PPPoE) are online. In addition, this command lists limited input related to L2-aware NAT:
NAT policies associated with the subscriber
Outside IP address allocated to the subscriber
Port range in a PB
As shown in the output of this command, both L2-aware subscribers have hosts with overlapping IP addresses, which is a unique characteristic in L2-aware NAT functionality.
*A:BNG1# show service active-subscribers
===============================================================================
Active Subscribers
===============================================================================
-------------------------------------------------------------------------------
Subscriber sub-1 (sub-prof-1)
-------------------------------------------------------------------------------
NAT Policy: l2-aware-base
Outside IP: 172.16.3.3
Ports : 1024-3023
NAT Policy: l2-aware-vrf1
Outside IP: 172.16.1.1 (vprn1)
Ports : 1024-3023
NAT Policy: l2-aware-vrf2
Outside IP: 172.16.2.2 (vprn2)
Ports : 1024-3023
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[1/1/5:1.1] - sla:sla-1
-------------------------------------------------------------------------------
IP Address
MAC Address Session Origin Svc Fwd
-------------------------------------------------------------------------------
10.10.1.2
00:00:65:01:01:02 PPP 1 IPCP 3 Y
10.10.1.1
00:00:65:01:01:01 N/A DHCP 3 Y
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Subscriber sub-2 (sub-prof-1)
-------------------------------------------------------------------------------
NAT Policy: l2-aware-base
Outside IP: 172.16.3.3
Ports : 3024-5023
NAT Policy: l2-aware-vrf1
Outside IP: 172.16.1.1 (vprn1)
Ports : 3024-5023
NAT Policy: l2-aware-vrf2
Outside IP: 172.16.2.2 (vprn2)
Ports : 3024-5023
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[1/1/5:1.2] - sla:sla-1
-------------------------------------------------------------------------------
IP Address
MAC Address Session Origin Svc Fwd
-------------------------------------------------------------------------------
10.10.1.2
00:00:65:01:02:02 PPP 1 IPCP 3 Y
10.10.1.1
00:00:65:01:02:01 N/A DHCP 3 Y
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Number of active subscribers : 2
===============================================================================
*A:BNG1#
NAT-specific show commands can provide more information about the L2-aware subscribers. One such command is show service nat l2-aware-subscribers. In this example, this command is run in a simplest form, but it can be expanded with additional filtering capabilities:
show service nat l2-aware-subscribers [nat-policy <policy-name>] [nat-group <nat-group-id>] [member <[1..255]>] [outside-router <router-instance>] [outside-ip <outside-ip-address>] [firewall-policy <policy-name>]
*A:BNG1# show service nat l2-aware-subscribers
===============================================================================
Layer-2-Aware NAT subscribers
===============================================================================
Subscriber : sub-1
-------------------------------------------------------------------------------
ISA NAT group : 1
ISA NAT group member : 1
UPnP policy : (None)
Default NAT policy : l2-aware-base
Per-host port block size : N/A
Firewall policy : (None)
Policy : l2-aware-base
Purpose : nat
Outside router : Base
Outside IP : 172.16.3.3
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 1024-3023
Policy : l2-aware-vrf1
Purpose : nat
Outside router : vprn1
Outside IP : 172.16.1.1
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 1024-3023
Policy : l2-aware-vrf2
Purpose : nat
Outside router : vprn2
Outside IP : 172.16.2.2
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 1024-3023
Subscriber : sub-2
-------------------------------------------------------------------------------
ISA NAT group : 1
ISA NAT group member : 1
UPnP policy : (None)
Default NAT policy : l2-aware-base
Per-host port block size : N/A
Firewall policy : (None)
Policy : l2-aware-base
Purpose : nat
Outside router : Base
Outside IP : 172.16.3.3
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 3024-5023
Policy : l2-aware-vrf1
Purpose : nat
Outside router : vprn1
Outside IP : 172.16.1.1
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 3024-5023
Policy : l2-aware-vrf2
Purpose : nat
Outside router : vprn2
Outside IP : 172.16.2.2
DNAT default IP address override : (Not Specified)
DNAT disabled by override : false
Ports : 3024-5023
-------------------------------------------------------------------------------
No. of subscribers: 2
===============================================================================
Host-level L2-aware NAT information can be obtained via the show service nat l2-aware-hosts command. This command also provides additional filters for more targeted results:
show service nat l2-aware-hosts [outside-router <router-instance>] [outside-ip <outside-ip-address>] [inside-ip-prefix <ip-prefix/mask>]
In this case, the most generic version of this command is run where all four hosts and their L2-aware NAT specific information is shown:
*A:BNG1# show service nat l2-aware-hosts
===============================================================================
Layer-2-Aware NAT hosts
===============================================================================
Subscriber : sub-1
Inside IP address : 10.10.1.1
-------------------------------------------------------------------------------
Policy : l2-aware-base
Bypassing : false
Outside router : "Base"
Outside IP address : 172.16.3.3
Port block : N/A
Policy : l2-aware-vrf1
Bypassing : false
Outside router : 1
Outside IP address : 172.16.1.1
Port block : N/A
Policy : l2-aware-vrf2
Bypassing : false
Outside router : 2
Outside IP address : 172.16.2.2
Port block : N/A
Subscriber : sub-1
Inside IP address : 10.10.1.2
-------------------------------------------------------------------------------
Policy : l2-aware-base
Bypassing : false
Outside router : "Base"
Outside IP address : 172.16.3.3
Port block : N/A
Policy : l2-aware-vrf1
Bypassing : false
Outside router : 1
Outside IP address : 172.16.1.1
Port block : N/A
Policy : l2-aware-vrf2
Bypassing : false
Outside router : 2
Outside IP address : 172.16.2.2
Port block : N/A
Subscriber : sub-2
Inside IP address : 10.10.1.1
-------------------------------------------------------------------------------
Policy : l2-aware-base
Bypassing : false
Outside router : "Base"
Outside IP address : 172.16.3.3
Port block : N/A
Policy : l2-aware-vrf1
Bypassing : false
Outside router : 1
Outside IP address : 172.16.1.1
Port block : N/A
Policy : l2-aware-vrf2
Bypassing : false
Outside router : 2
Outside IP address : 172.16.2.2
Port block : N/A
Subscriber : sub-2
Inside IP address : 10.10.1.2
-------------------------------------------------------------------------------
Policy : l2-aware-base
Bypassing : false
Outside router : "Base"
Outside IP address : 172.16.3.3
Port block : N/A
Policy : l2-aware-vrf1
Bypassing : false
Outside router : 1
Outside IP address : 172.16.1.1
Port block : N/A
Policy : l2-aware-vrf2
Bypassing : false
Outside router : 2
Outside IP address : 172.16.2.2
Port block : N/A
-------------------------------------------------------------------------------
No. of hosts: 4
===============================================================================
The following two commands are more generic and their output displays packet and event statistics related to NAT operation in two contexts:
Per MS-ISA
Per member within the ISA
A member within an MS-ISA is a concept related to intra-chassis redundancy. CPM maintains a copy of the member configuration so that it can download it to a rescuing MS-ISA during the switchover (when an MS-ISA fails). An MS-ISA can contain one or more (in A/A redundancy model) members.
show isa nat-group 1 mda 1/2 statistics
show isa nat-group 1 member 1 statistics
The output is the following:
*A:BNG1# show isa nat-group 1 mda 1/2 statistics
===============================================================================
ISA NAT Group 1 MDA 1/1
===============================================================================
no resource : 0
pkt rx on wrong port : 0
unsupported protocol : 0
no host or host group : 0
no ip or port : 0
no matching flow : 0
max flow exceeded : 0
TCP no flow for RST : 0
TCP no flow for FIN : 0
TCP no flow : 0
addr. dep. filtering : 0
ICMP type unsupported : 0
ICMP local unsupported : 0
ICMP/ICMPv6 checksum error : 0
ICMP embedded checksum error : 0
ICMP/ICMPv6 unsupported embedded L4 : 0
ICMP/ICMPv6 too short : 0
ICMP/ICMPv6 length error : 0
Pkt not IPv4 or IPv6 : 0
Pkt rcv error : 0
Pkt error : 0
IPv4 header checksum violation : 0
IP header malformed : 0
IP malformed packet : 0
IP ttl zero : 0
IPv4 opt /IPv6 ext headers : 0
IP undefined error : 0
IPv6 fragments unsupported : 0
TCP/UDP malformed : 0
TCP/UDP checksum failure : 0
Pkt send error : 0
no buf to copy pkt : 0
no policy : 0
policy not in use by subscriber : 0
locked by mgmt core : 0
port range log failed : 0
MTU exceeded : 0
DS Lite unrecognized next hdr : 0
DS Lite unknown AFTR : 0
too many fragments for IP packet : 0
too many fragmented packets : 0
too many fragment holes : 0
too many frags buffered : 0
fragment list expired : 0
fragment rate too high : 0
flow log failed : 0
no multiple host or subscr. IPs allowed : 0
NAT64 disabled : 0
NAT64 invalid src addr : 0
NAT64 frag has zero checksum : 0
NAT64 v4 has zero checksum : 0
NAT64 ICMP frag unsupported : 0
Reassembly Failures : 0
subscriber-id unknown : 0
packet hashed to wrong MDA : 0
Nptv6 map failed : 0
Nptv6 IID all 1's : 0
UPnP rate too high : 0
Dest. IP is unroutable : 0
no TCP/UDP checksum : 0
to local : 0
to local ignored : 0
new flow : 0
TCP closed : 0
TCP expired : 0
UDP expired : 0
ICMP/ICMPv6 expired : 0
GRE expired : 0
ICMP local : 0
found flow : 0
ARPs ignored : 10
Fragments RX L2A : 0
Fragments RX LSN : 0
Fragments RX DSL : 0
Fragments RX DORMANT : 0
Fragments RX OUT : 0
Fragments TX L2A : 0
Fragments TX LSN : 0
Fragments TX DSL : 0
Fragments TX DORMANT : 0
Fragments TX NAT64 : 0
Fragments TX OUT : 0
flow create logged : 0
flow delete logged : 0
flow log pkt tx : 0
Reassembled Pkts : 0
subscriber-id cached : 0
subscriber-id delayed : 0
subscriber-id timeout : 0
forwarded DS-Lite V6 pkts : 0
V6 pkts fragmented : 0
dropped multicast : 0
SSDP rx : 0
SSDP tx : 0
SSDP dropped : 0
UPnP rx : 0
UPnP tx : 0
UPnP dropped : 0
no radius resources : 0
no radius connection resources : 0
Dest. NAT dest. IP mismatch : 0
Dest. NAT foreign IP mismatch : 0
temp. no policy : 0
no SNat enabled : 0
no default policy : 0
flow create failed, key ambiguous : 0
flow create failed, conflicting policies : 0
NAT64 unrecognized next hdr : 0
ICMP/ICMPv6 unsupported embedded L3 : 0
TCP reset waiting : 0
IPv6 downstream prohibited : 0
IPv6 ext. hdr parse error : 0
any V6 L4 expired : 0
ICMP embedded IPv6 ext. hdr parse error : 0
ICMPv6 type unsupported : 0
ICMP/ICMPv6 fragmented error : 0
Service-chaining rx : 0
Service-chaining tx : 0
Service-chaining encapsulation error : 0
Service-chaining decapsulation error : 0
Service-chaining filter drop : 0
PPPoE uplink down : 0
ICMP6 PTB dropped (mtu < 1280) : 0
firewall addr. dep. filtering : 0
unresolved L2-aware V6 host : 0
===============================================================================
*A:BNG1#
Resources monitoring is performed via the following commands:
tools dump nat isa resources nat-group <id> member <id>
tools dump nat isa resources mda <card-id/mds-id>
show isa nat-system-resources nat-group <id> member <id>
The NAT scale depends on the hardware (vSIMs, MS-ISA1, MS-ISA2, VSR-NAT).
Tools Commands
To display the complete session state, the following command can be used:
tools dump nat sessions [nat-group <nat-group-id>] [mda <mda-id>] [protocol {gre|icmp|icmp6|tcp|udp|unknown}] [inside-ip <ip-prefix[/ip-prefix- length]>] [inside-router <router-instance>] [inside-port <port-number>] [outside-ip <ipv4-address>] [outside-port <port-number>] [foreign-ip
<ip-address>] [foreign-port <port-number>] [dslite-address
<ipv6-address>] [wlan-gw-ue <ieee-address>] [next index <index>] [upnp] [member <member-id>] [nat-policy <policy-name>] [dest-ip <ip-address>] [firewall-policy <policy-name>] [address-type <addr-type>] [vas-filter
<filter-name>] [vas-filter-entry <vas-filter-entry-id>]
[l2-aware-subscriber <sub-ident>]
The output of this command is used to populate dynamically allocated fields (in bold) in Traffic Streams. The command, in its basic form, is run as:
*A:BNG1# tools dump nat sessions
===============================================================================
Matched 6 sessions on Slot #1 MDA #2
===============================================================================
Owner : L2-aware Subscr sub-1
Policy : l2-aware-vrf1
FlowType : UDP Timeout (sec) : 299
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.1.1
Outside Port : 1124
Foreign IP Addr : 192.168.7.2
Foreign Port : 5000
Dest IP Addr : 192.168.7.2
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Owner : L2-aware Subscr sub-2
Policy : l2-aware-vrf1
FlowType : UDP Timeout (sec) : 300
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.1.1
Outside Port : 4666
Foreign IP Addr : 192.168.7.2
Foreign Port : 5000
Dest IP Addr : 192.168.7.2
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Owner : L2-aware Subscr sub-2
Policy : l2-aware-base
FlowType : UDP Timeout (sec) : 300
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.3.3
Outside Port : 4470
Foreign IP Addr : 192.168.5.2
Foreign Port : 5000
Dest IP Addr : 192.168.5.2
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Owner : L2-aware Subscr sub-1
Policy : l2-aware-vrf2
FlowType : UDP Timeout (sec) : 300
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.2.2
Outside Port : 2068
Foreign IP Addr : 192.168.8.2
Foreign Port : 5001
Dest IP Addr : 192.168.8.5
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Owner : L2-aware Subscr sub-1
Policy : l2-aware-base
FlowType : UDP Timeout (sec) : 299
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.3.3
Outside Port : 2186
Foreign IP Addr : 192.168.5.2
Foreign Port : 5000
Dest IP Addr : 192.168.5.2
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Owner : L2-aware Subscr sub-2
Policy : l2-aware-vrf2
FlowType : UDP Timeout (sec) : 299
Inside IP Addr : 10.10.1.1
Inside Port : 5000
Outside IP Addr : 172.16.2.2
Outside Port : 3690
Foreign IP Addr : 192.168.8.2
Foreign Port : 5000
Dest IP Addr : 192.168.8.2
Nat Group : 1
Nat Group Member : 1
-------------------------------------------------------------------------------
Clear Commands
The following command clears L2-aware subscribers:
clear nat isa nat-group 1 member 1 l2-aware-
ESM subscribers are also deleted with this command. Therefore, this command should be used with caution because DHCP hosts in ESM do not send termination messages back to the client. This leaves the DHCP client in a state where it is not aware that its DHCP state in the L2-aware node has been deleted.
Debug Commands
Troubleshooting ESM subscribers is described in other configuration guides focusing on ESM. This chapter focuses only on the NAT aspect of ESM in L2-aware NAT.
L2-aware NAT debug output shows session (or flow) initiation information. As traffic is run, translations of the source IP address/port are performed and this information is displayed for debugging purposes. Traffic from both subscribers in this example is debugged with these two commands:
*A:BNG1# show debug
debug
nat
l2-aware-sub id 1 subscriber "sub-1"
l2-aware-sub id 2 subscriber "sub-2"
exit
exit
The following configuration sends debug output to the Telnet/SSH sessions screen:
A:BNG1>config>log# info
----------------------------------------------
log-id 50
from debug-trace
to session
no shutdown
exit
Debug output shows translations that are being performed on the incoming traffic, which consists of six streams in this example:
1 2017/08/31 08:37:39.223 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-1
Initiated flow from 172.16.3.3(port 2186) to 192.168.5.2(port 5000) protocol UDP"
2 2017/08/31 08:37:39.223 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-1
Initiated flow from 172.16.1.1(port 1124) to 192.168.7.2(port 5000) protocol UDP"
3 2017/08/31 08:37:39.483 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-1
Initiated flow from 172.16.2.2(port 3690) to 192.168.8.2(port 5001) protocol UDP"
4 2017/08/31 08:37:39.743 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-2
Initiated flow from 172.16.3.3(port 4470) to 192.168.5.2(port 5000) protocol UDP"
5 2017/08/31 08:37:39.743 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-2
Initiated flow from 172.16.1.1(port 4666) to 192.168.7.2(port 5000) protocol UDP"
6 2017/08/31 08:37:40.003 WEST MINOR: DEBUG #2001 Base NAT "NAT: L2-Aware@sub-2
Initiated flow from 172.16.2.2(port 4698) to 192.168.8.2(port 5000) protocol UDP”
Note that dNAT information is not displayed in the debug output.
Conclusion
L2-aware NAT integrates NAT functionality into ESM. NAT resources (outside IP address and a PB) are allocated per ESM subscriber and, consequently, all the hosts within the subscriber share those NAT resources. Each subscriber is initially assigned a single PB that will be used during the lifetime of the subscriber. The number of ports in this PB must be large enough to accommodate the needs of the subscriber during its lifetime.
The integration between ESM and NAT in L2-aware NAT introduces the following:
Using the subscriber-id field (instead of source IPv4 address) to identify the NAT binding allows the source IPv4 address to be abstracted from the binding. This allows hosts of different subscribers to have overlapping IP addresses .
IPv4 addresses cannot overlap between the hosts of the same subscriber, but they can overlap between the hosts of different subscribers.
NAT logging can be integrated into ESM RADIUS accounting, simplifying operations and removing the need for a separate network resource dedicated to the collection of NAT logs.
NAT resources are released when the ESM subscriber is disconnected. This prevents lingering of NAT resources in the system waiting for the timer of the last session to expire long after the entity that initially requested those resources ceased to exist. This improves resource utilization in a system with a high number of subscribers.
L2-aware NAT should be considered for deployment because it allows coupling between ESM and NAT.
Appendix A – Generic ESM Configuration
Appendix A describes the generic part of the ESM configuration.
ESM configuration starts with a subscriber-interface configured in an inside routing context. In this example, subscriber hosts are instantiated in the IES 3 service, under the group-interface ‟group-int-1”, which is created under the subscriber-interface ‟sub-int-1”. Authentication and address assignment of the subscriber hosts is performed via local user database (LUDB) user-db ‟user-db-1”. The IP addresses that are assigned to the hosts are statically configured in LUDB (no DHCP server is used in this setup).
configure
service
ies 3 customer 1 create
subscriber-interface "sub-int-1" create
address 10.10.1.254/24
group-interface "group-int-1" create
dhcp
proxy-server
emulated-server 10.10.1.254
no shutdown
exit
option
action keep
circuit-id
remote-id
exit
trusted
lease-populate 100
gi-address 10.10.1.254
user-db "user-db-1"
no shutdown
exit
pppoe
anti-spoof mac-sid-ip
policy "pppoe_pol"
session-limit 100
sap-session-limit 100
user-db "user-db-1"
no shutdown
exit
no shutdown
exit
exit
exit
service-name "ies-3"
no shutdown
exit
exit
Subscriber SAPs are automatically created based on the VLAN tags carried in the initial control packets of the subscriber hosts. This VLAN auto-detection and SAP auto-creation is configured under the capture SAP hierarchy. The capture SAP is configured to support LUDB authentication for dynamic DHCPv4/PPPoEv4 host instantiation, as follows:
configure
service
vpls 10 name "10" customer 1 create
sap 1/1/5:1.* capture-sap create
trigger-packet dhcp pppoe
dhcp-user-db "user-db-1"
pppoe-policy "pppoe_pol"
pppoe-user-db "user-db-1"
exit
exit
The first interaction between ESM and L2-aware NAT is performed through a sub-profile. Specifically, a nat-policy within the sub-profile is used to associate the ESM subscriber with NAT.
A nat-prefix-list within the sub-profile provides the place to configure multiple nat-policies per subscriber. Selection of nat-policy (and with this, the NAT pool and outside routing context) is based on the destination IP address in the packet sent by the subscriber.
RADIUS accounting records passed to the accounting server will contain subscriber-host specific information, including NAT logs. This is configured via a RADIUS accounting policy, which is referenced in the sub-profile.
configure
subscriber-mgmt
sub-profile "sub-prof-1" create
nat-policy "l2-aware-base"
nat-prefix-list "l2aware-mnp"
radius-accounting
policy "acct"
exit
exit
Although an sla-profile is a mandatory configuration for a subscriber, the sla-profile content is not relevant for understanding L2-aware NAT concepts. A basic sla-profile is chosen with default settings: a default qos-policy 1 and no ip-filters.
The sub-profile and sla-profile are associated with the subscriber(-host) during the authentication phase and, in this case, this is achieved through LUDB.
configure
subscriber-mgmt
sla-profile "sla-1" create
exit
The MSAP policy is a mandatory configuration for dynamically created SAPs (Managed SAP or MSAPs). It is used to determine SAP parameters during the MSAP creation process based on control traffic (DHCP or PPPoE) of the first host (MSAP trigger traffic). Parameters defined in msap-policy that are of relevance to our example are:
Sub-ident-policy → this is a mandatory parameter in ESM that governs mapping of subscriber-related profiles (
sub-profile,SLA-profile) to the subscriber host during the authentication phase.Anti-spoof filter → this is of particular importance in L2-aware NAT and is already described in more detail in the Configuration section.
configure
subscriber-mgmt
msap-policy "msaps" create
sub-sla-mgmt
sub-ident-policy "sub_ident_pol"
multi-sub-sap limit 10
exit
ies-vprn-only-sap-parameters
anti-spoof ip-mac
exit
exit
Sub-ident-policy is a mandatory configuration in ESM. It determines the mapping method between the sub/SLA profiles and the corresponding strings obtained during the authentication phase for the subscriber. Subscriber strings obtained during the authentication phase point, in some form (determined by sub-ident-policy), to the configured sub/SLA profiles (in the SR OS node) that will be associated with the subscriber.
configure
subscriber-mgmt
sub-ident-policy "sub_ident_pol" create
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
exit
In this example, authentication of the subscriber hosts and IP address assignment is performed through LUDB. The hosts are identified based on circuit-id and remote-id fields in DHCP and PPPoE control packets. Sla-sub-profile strings in the LUDB are directly mapped to the configured sub/sla-profiles in SR OS node. This direct mapping is implied by the preceding use-direct-map-as-default command within sub-ident-policy. The LUDB carries only ESM specific configuration. There is no NAT relevant configuration present in the LUDB.
configure
subscriber-mgmt
local-user-db "user-db-1" create
ipoe
match-list circuit-id remote-id
host "sub-1-host-1" create
host-identification
circuit-id string "sub-1"
remote-id string "host-1"
exit
address 10.10.1.1
identification-strings 254 create
subscriber-id "sub-1"
sla-profile-string "sla-1"
sub-profile-string "sub-prof-1"
exit
msap-defaults
group-interface "group-int-1"
policy "msaps"
service 3
exit
options
subnet-mask 255.255.255.0
exit
no shutdown
exit
host "sub-2-host-1" create
host-identification
circuit-id string "sub-2"
remote-id string "host-1"
exit
address 10.10.1.1
identification-strings 254 create
subscriber-id "sub-2"
sla-profile-string "sla-1"
sub-profile-string "sub-prof-1"
exit
msap-defaults
group-interface "group-int-1"
policy "msaps"
service 3
exit
options
subnet-mask 255.255.255.0
exit
no shutdown
exit
exit
ppp
match-list circuit-id remote-id
host "sub-1-host-2" create
host-identification
circuit-id string "sub-1"
remote-id string "host-2"
exit
address 10.10.1.2/24
identification-strings 254 create
subscriber-id "sub-1"
sla-profile-string "sla-1"
sub-profile-string "sub-prof-1"
exit
msap-defaults
group-interface "group-int-1"
policy "msaps"
service 3
exit
no shutdown
exit
host "sub-2-host-2" create
host-identification
circuit-id string "sub-2"
remote-id string "host-2"
exit
address 10.10.1.2/24
identification-strings 254 create
subscriber-id "sub-2"
sla-profile-string "sla-1"
sub-profile-string "sub-prof-1"
exit
msap-defaults
group-interface "group-int-1"
policy "msaps"
service 3
exit
no shutdown
exit
exit
no shutdown
exit
The accounting policy identifies the type of accounting and the attributes that will be carried in an accounting message. Among the ESM-specific attributes, nat-port-range is the only NAT-related attribute that will carry NAT logging information for the subscriber.
configure
subscriber-mgmt
radius-accounting-policy "acct" create
no queue-instance-accounting
host-accounting interim-update
update-interval 5
include-radius-attribute
circuit-id
framed-ip-addr
mac-address
nas-identifier
nas-port-id
nat-port-range
remote-id
sla-profile
sub-profile
subscriber-id
user-name
alc-acct-triggered-reason
exit
session-id-format number
radius-server-policy "aaa"
exit
Appendix B – Logging
Appendix B shows the RADIUS logging stream for all four hosts used in this chapter:
root@ linux:/var/log/freeradius/radacct/192.168.114.2# more detail-20170814
Mon Aug 14 09:14:45 2017
Acct-Status-Type = Start
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:29:02 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502727285
Request-Authenticator = Verified
Mon Aug 14 09:14:53 2017
Acct-Status-Type = Start
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003159916D66"
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:29:10 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:02"
Acct-Unique-Session-Id = "cc1701cf565fcdf5"
Timestamp = 1502727293
Request-Authenticator = Verified
Mon Aug 14 09:15:02 2017
Acct-Status-Type = Start
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003259916D70"
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:29:20 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:01"
Acct-Unique-Session-Id = "57659d99038f7c0d"
Timestamp = 1502727302
Request-Authenticator = Verified
Mon Aug 14 09:15:09 2017
Acct-Status-Type = Start
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003559916D76"
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:29:26 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:02"
Acct-Unique-Session-Id = "433924b3304e2d9e"
Timestamp = 1502727309
Request-Authenticator = Verified
Mon Aug 14 09:19:42 2017
Acct-Status-Type = Interim-Update
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003159916D66"
Acct-Session-Time = 289
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:33:59 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:02"
Alc-Acct-Triggered-Reason = regular
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00010000000000009024
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x00010000000000000171
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "cc1701cf565fcdf5"
Timestamp = 1502727582
Request-Authenticator = Verified
Mon Aug 14 09:20:01 2017
Acct-Status-Type = Interim-Update
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003559916D76"
Acct-Session-Time = 292
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:34:18 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:02"
Alc-Acct-Triggered-Reason = regular
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x0001000000000000a5a0
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000001a8
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "433924b3304e2d9e"
Timestamp = 1502727601
Request-Authenticator = Verified
Mon Aug 14 09:20:11 2017
Acct-Status-Type = Interim-Update
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Session-Time = 326
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:34:28 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Alc-Acct-Triggered-Reason = regular
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x0001000000000000b220
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000001c8
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502727611
Request-Authenticator = Verified
Mon Aug 14 09:20:16 2017
Acct-Status-Type = Interim-Update
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003259916D70"
Acct-Session-Time = 313
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:34:33 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:01"
Alc-Acct-Triggered-Reason = regular
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x0001000000000000b734
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000001d5
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "57659d99038f7c0d"
Timestamp = 1502727616
Request-Authenticator = Verified
Mon Aug 14 09:30:34 2017
Acct-Status-Type = Stop
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000002E59916D5E"
Acct-Session-Time = 949
Acct-Terminate-Cause = User-Request
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:44:51 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:01"
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00010000000000037974
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000008e5
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "fe5e55d7102d3f81"
Timestamp = 1502728234
Request-Authenticator = Verified
Mon Aug 14 09:30:34 2017
Acct-Status-Type = Stop
NAS-IP-Address = 192.0.2.2
Framed-IP-Address = 10.10.1.1
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003259916D70"
Acct-Session-Time = 931
Acct-Terminate-Cause = User-Request
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:44:51 PDT"
NAS-Port-Type = Ethernet
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-1"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:01"
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x000100000000000378ac
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000008e3
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "57659d99038f7c0d"
Timestamp = 1502728234
Request-Authenticator = Verified
Mon Aug 14 09:30:47 2017
Acct-Status-Type = Stop
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003159916D66"
Acct-Session-Time = 954
Acct-Terminate-Cause = User-Request
Acct-Multi-Session-Id = "D896FF0000002F59916D5E"
Event-Timestamp = "Aug 14 2017 02:45:04 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.1"
ADSL-Agent-Circuit-Id = "sub-1"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-1"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 1024-3023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 1024-3023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 1024-3023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:01:02"
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x00010000000000037974
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000008e5
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "cc1701cf565fcdf5"
Timestamp = 1502728247
Request-Authenticator = Verified
Mon Aug 14 09:30:47 2017
Acct-Status-Type = Stop
NAS-IP-Address = 192.0.2.2
Service-Type = Framed-User
Framed-Protocol = PPP
Framed-IP-Address = 10.10.1.2
NAS-Identifier = "BNG1"
Acct-Session-Id = "D896FF0000003559916D76"
Acct-Session-Time = 938
Acct-Terminate-Cause = User-Request
Acct-Multi-Session-Id = "D896FF0000003359916D70"
Event-Timestamp = "Aug 14 2017 02:45:04 PDT"
NAS-Port-Type = PPPoEoQinQ
NAS-Port-Id = "1/1/5:1.2"
ADSL-Agent-Circuit-Id = "sub-2"
ADSL-Agent-Remote-Id = "host-2"
Alc-Subsc-ID-Str = "sub-2"
Alc-Subsc-Prof-Str = "sub-prof-1"
Alc-SLA-Prof-Str = "sla-1"
Alc-Nat-Port-Range = "172.16.3.3 3024-5023 router base l2-aware-base"
Alc-Nat-Port-Range = "172.16.1.1 3024-5023 router 1 l2-aware-vrf1"
Alc-Nat-Port-Range = "172.16.2.2 3024-5023 router 2 l2-aware-vrf2"
Alc-Client-Hardware-Addr = "00:00:65:01:02:02"
Alc-Acct-I-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Octets-64 = 0x000100000000000378ac
Alc-Acct-I-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-I-Outprof-Pkts-64 = 0x000100000000000008e3
Alc-Acct-O-Inprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Octets-64 = 0x00010000000000000000
Alc-Acct-O-Inprof-Pkts-64 = 0x00010000000000000000
Alc-Acct-O-Outprof-Pkts-64 = 0x00010000000000000000
Acct-Unique-Session-Id = "433924b3304e2d9e"
Timestamp = 1502728247
Request-Authenticator = Verified
root@linux:/var/log/freeradius/radacct/192.168.114.2#