Rate Limit Filter Action
This chapter provides information about Rate Limit Filter Action.
Topics in this chapter include:
Applicability
This chapter is applicable to SR OS routers and is based on SR OS Release 24.3.R1.
Overview
Filter-based rate limiting can be used by operators for security reasons to protect their network resources or mitigate DDoS attacks; see Filter Based Rate Limiting.
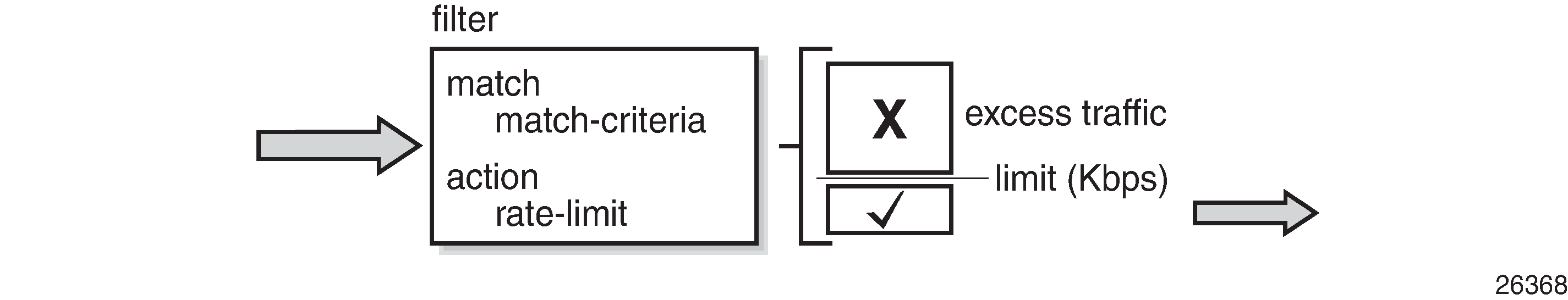
SR OS supports filter-based rate limiting on ingress (SR OS Release 14.0.R1) and on egress (SR OS Release 14.0.R4) for IPv4, IPv6, and MAC filter policies
The rate-limit value is configurable in kilobits per second and applicable to traffic matching the filter condition. Packets matching the filter condition are dropped when the traffic rate is above the configured policer rate value and forwarded when the traffic rate is below the configured policer rate value.
QoS Interaction
On ingress, if the MAC or IPv4/IPv6 filter action indicates that traffic must be rate limited, this traffic is redirected to a rate-limiting filter policer before delivery to the switching fabric. Traffic not matching the MAC or IP filter will pass through the regular packet processing chain, and can be limited through SAP-ingress policies. Control traffic that is extracted to the CPM is not rate limited. Rate-limiting filter policies can coexist with the cflowd, log, and mirror features.
On egress, control and data traffic matching an egress rate-limiting filter policy bypasses egress QoS policing, but the usual egress QoS queueing still applies.
Rate-Limiting with Single or Multiple FlexPaths
Filter-based rate limiting can be applied to Layer 2 and Layer 3 services, and is supported on following items, including but not limited to:
SAPs
Network interface
Spoke-SDPs
group interfaces
ESM subscribers
Filter-based rate limiting can also be used when the underlying infrastructure uses link aggregation.
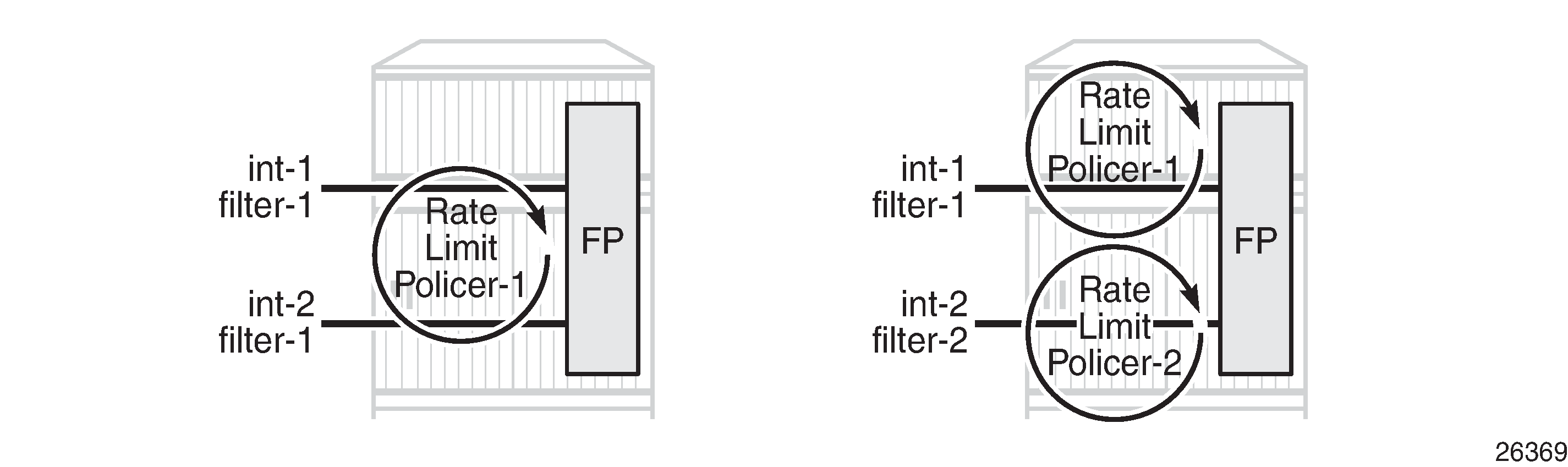
If multiple interfaces use the same rate-limiting filter policy on the same FP, the system will allocate a single rate-limiter resource to the FP; a common aggregate rate limit is applied to those interfaces.
If multiple interfaces use the same rate-limiting filter policy on different FPs, the system will allocate a rate-limiter resource for each FP; an independent rate limit applies to each FP.
The example to the left in Rate Limit Filters and FlexPaths has two interfaces with the same filter applied, and terminated on the same FP. Therefore, there is only one policer, and the aggregate traffic is topped at the rate defined in the filter. The example to the right has two interfaces with different filters, again terminated on the same FP. Because the interfaces have distinct filters, two different rate-limiting policers are created, which could (but not necessarily) define the same rate.
The actual packet length is used for the rate limit, not factoring in the encapsulation.
Use caution when applying filter-based rate limiting to SAPs on group interfaces, because group interfaces can host many ESM subscribers, which could defeat per-subscriber and per-ESM host rate limiting.
Syntax
The following syntax defines an IPv4/IPv6 filter or a MAC filter with rate-limiting action:
# on PE-1:
[ex:/configure filter]
A:admin@PE-1# info
ip-filter | ipv6-filter | mac-filter "<filter-name>" {
description "<filter-description>"
default-action accept | forward | drop
filter-id <filter-id>
entry <entry-id> {
match {
** match criteria, e.g.: IP/Port/MAC **
}
action {
accept
rate-limit {
pir <value-Kbps>
}
}
}
}All regular IP and MAC match criteria are supported with the action rate-limit.
Configuration
Example Configuration shows the example configuration. Traffic is sourced on Tester T1, port //8/1, passes through VPRN 1, and is received on port //8/5 of Tester T2.
Ingress IPv4 filtering applies at the ingress SAP in VPRN 1. Ingress IPv6 filtering and ingress MAC filtering are similar to ingress IPv4 filtering and are not shown in this chapter.
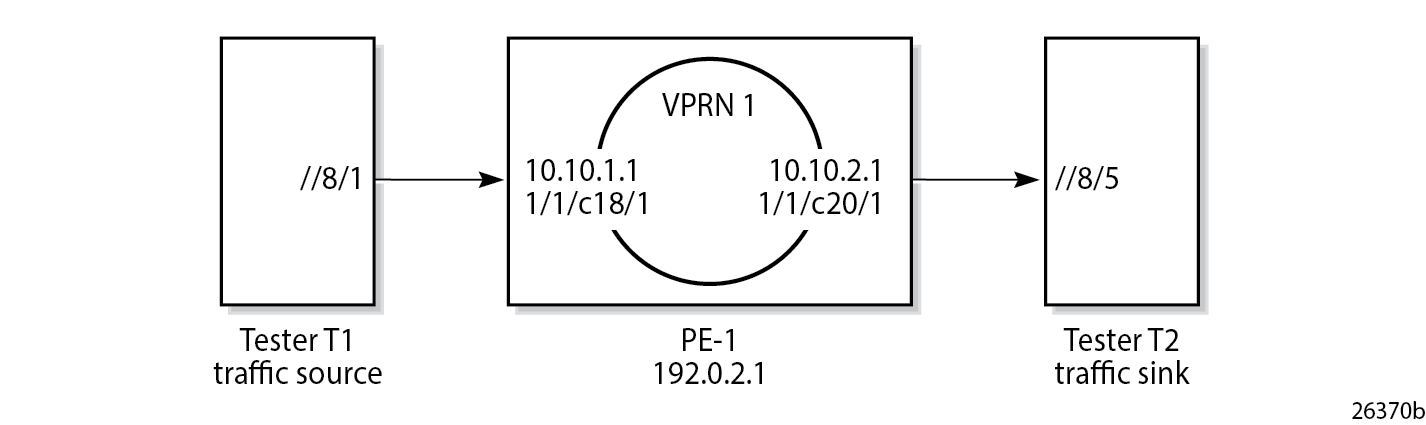
The configuration of VPRN 1 on PE-1 is as follows:
# on PE-1:
configure {
service {
vprn "VPRN 1" {
admin-state enable
description "rate limit action for ip filter"
service-id 1
customer "1"
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "65536:1"
}
}
interface "int-TST-receiver" {
ipv4 {
primary {
address 10.10.2.1
prefix-length 24
}
}
sap 1/1/c20/1 { }
}
interface "int-TST-source" {
ipv4 {
primary {
address 10.10.1.1
prefix-length 24
}
}
sap 1/1/c18/1 {
ingress {
filter {
ip "ip-filter-1M"
}
}
}
}
}The filter configuration is as follows:
# on PE-1:
configure {
filter {
ip-filter "ip-filter-1M" {
description "IP filter test for rate limit action"
default-action accept
filter-id 3
entry 10 {
match {
src-ip {
address 10.10.1.2/32
}
dst-ip {
address 10.10.2.2/32
}
}
action {
accept
rate-limit {
pir 1024 # in Kbps ; 1024000/8/128 = 1000 packets/s
}
}
}
}A stream of UDP packets with a fixed size of 128 bytes is sent out of Tester T1 at a rate of 500 packets/s, accounting for a data rate of 500 x 128 x 8 = 512Kbit/s. At this rate, all packets pass through because the actual rate is lower than the rate-limit 1024Kbit/s, as follows:
[/]
A:admin@PE-1# monitor filter ip "ip-filter-1M" entry 10 rate repeat 6 interval 11
===============================================================================
Monitor statistics for IP filter 3 entry 10
===============================================================================
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
Ing. Matches : 2 pkts (256 bytes)
Egr. Matches : 0 pkts
Ing. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
Egr. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
-------------------------------------------------------------------------------
At time t = 11 sec (Mode: Rate)
-------------------------------------------------------------------------------
Ing. Matches : 500 pkts (63988 bytes)
Egr. Matches : 0 pkts
Ing. Rate-limiter
Offered : 500 pkts (64012 bytes)
Forwarded : 500 pkts (64012 bytes)
Dropped : 0 pkts
Egr. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
---snip---[/]
A:admin@PE-1# monitor filter ip "ip-filter-1M" entry 10 rate repeat 6 interval 11
===============================================================================
Monitor statistics for IP filter 3 entry 10
===============================================================================
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
Ing. Matches : 7 pkts (896 bytes)
Egr. Matches : 0 pkts
Ing. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
Egr. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
-------------------------------------------------------------------------------
At time t = 11 sec (Mode: Rate)
-------------------------------------------------------------------------------
Ing. Matches : 1500 pkts (191965 bytes)
Egr. Matches : 0 pkts
Ing. Rate-limiter
Offered : 1500 pkts (192047 bytes)
Forwarded : 996 pkts (127523 bytes)
Dropped : 504 pkts (64524 bytes)
Egr. Rate-limiter
Offered : 0 pkts
Forwarded : 0 pkts
Dropped : 0 pkts
---snip---[/]
A:admin@PE-1# monitor service id "VPRN 1" sap "1/1/c18/1" rate repeat 6 interval 11
===============================================================================
Monitor statistics for Service 1 SAP 1/1/c18/1
===============================================================================
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
---snip---
-------------------------------------------------------------------------------
At time t = 11 sec (Mode: Rate)
-------------------------------------------------------------------------------
---snip---
-------------------------------------------------------------------------------
At time t = 22 sec (Mode: Rate)
-------------------------------------------------------------------------------
---snip---
-------------------------------------------------------------------------------
At time t = 33 sec (Mode: Rate)
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Sap Aggregate Stats
-------------------------------------------------------------------------------
Packets Octets
Ingress
Aggregate Offered : 0 0
Aggregate Forwarded : 0 0
Aggregate Dropped : 0 0
Egress
Aggregate Forwarded : 0 0
Aggregate Dropped : 0 0
-------------------------------------------------------------------------------
Sap Statistics
-------------------------------------------------------------------------------
Last Cleared Time : 04/12/2024 18:53:07
Packets Octets % Port
Util.
CPM Ingress : 0 0 0.00
Forwarding Engine Stats
Dropped : 0 0 0.00
Received Valid : 455 58193 ~0.00
Off. HiPrio : 0 0 0.00
Off. LowPrio : 0 0 0.00
Off. Uncolor : 0 0 0.00
Off. Managed : 0 0 0.00
---snip---When sending traffic at a rate of 1500 packets/s with a 128 bytes packet-size and monitoring at exit-point SAP 1/1/c20/1 over 11 s intervals, only 1000 packets/s are sent out of interface int-TST-receiver, accounting for 128000 octets/s. The output shows:
[/]
A:admin@PE-1# monitor service id "VPRN 1" sap "1/1/c20/1" rate repeat 6 interval 11
===============================================================================
Monitor statistics for Service 1 SAP 1/1/c20/1
===============================================================================
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
---snip---
-------------------------------------------------------------------------------
At time t = 11 sec (Mode: Rate)
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Sap Aggregate Stats
-------------------------------------------------------------------------------
Packets Octets
Ingress
Aggregate Offered : 0 0
Aggregate Forwarded : 0 0
Aggregate Dropped : 0 0
Egress
Aggregate Forwarded : 996 127488
Aggregate Dropped : 0 0
-------------------------------------------------------------------------------
Sap Statistics
-------------------------------------------------------------------------------
Last Cleared Time : 04/12/2024 18:58:38
Packets Octets % Port
Util.
CPM Ingress : 0 0 0.00
Forwarding Engine Stats
Dropped : 0 0 0.00
Received Valid : 0 0 0.00
Off. HiPrio : 0 0 0.00
Off. LowPrio : 0 0 0.00
Off. Uncolor : 0 0 0.00
Off. Managed : 0 0 0.00
Queueing Stats(Ingress QoS Policy 1)
Dro. HiPrio : 0 0 0.00
Dro. LowPrio : 0 0 0.00
For. InProf : 0 0 0.00
For. OutProf : 0 0 0.00
Queueing Stats(Egress QoS Policy 1)
Dro. In/InplusProf : 0 0 0.00
Dro. Out/ExcProf : 0 0 0.00
For. In/InplusProf : 996 127488 ~0.00
For. Out/ExcProf : 0 0 0.00
-------------------------------------------------------------------------------
Sap per Queue Stats
-------------------------------------------------------------------------------
Packets Octets % Port
Util.
Ingress Queue 1 (Unicast) (Priority)
Off. HiPrio : 0 0 0.00
Off. LowPrio : 0 0 0.00
Dro. HiPrio : 0 0 0.00
Dro. LowPrio : 0 0 0.00
For. InProf : 0 0 0.00
For. OutProf : 0 0 0.00
Ingress Queue 11 (Multipoint) (Priority)
Off. Combined : 0 0 0.00
Off. Managed : 0 0 0.00
Dro. HiPrio : 0 0 0.00
Dro. LowPrio : 0 0 0.00
For. InProf : 0 0 0.00
For. OutProf : 0 0 0.00
Egress Queue 1
For. In/InplusProf : 996 127488 ~0.00
For. Out/ExcProf : 0 0 0.00
Dro. In/InplusProf : 0 0 0.00
Dro. Out/ExcProf : 0 0 0.00
---snip---- clear service statistics id "<service-name>" counters, or clear service statistics sap "<sap-id>" all or clear service statistics sap "<sap-id>" counters, followed by: show service id "<service-name>" sap "<sap-id>" base, show service id "<service-name>" sap "<sap-id>" stats and show service id "<service-name>" sap "<sap-id>" sap-stats after the end of the counting period
- clear filter ip|ipv6|mac "<filter-name>", followed by: show filter ip|ipv6|mac "<filter-name>" counters [detail] after the end of the counting period
Conclusion
Rate-limiting filter actions can be used by network operators for security purposes to protect network resources and can also be used to mitigate DDoS attacks.