ESM Basics
This chapter provides information about Enhanced Subscriber Management.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 11.0.R4.
Overview
Subscriber management in general includes the following functions:
-
subscriber host authentication, identification, addressing, authorization and accounting:
-
authentication – Check whether the subscriber host is allowed access via a Local User Data Base (LUDB) or via a RADIUS server.
-
identification – Fetch the data to use for the subscriber host, including the definition of the subscriber-ID.
-
addressing – Fetch the address information to use, IPv4 and/or IPv6.
-
authorization – Check what the subscriber host is allowed to do.
-
accounting – Both off-line charging (RADIUS and XML) and on-line charging (RADIUS credit control and Diameter credit control application) are supported.
-
-
subscriber host instantiation, based on:
-
a protocol (DHCP, PPPoE/oA/oEoA or ARP) for dynamic hosts, and started through a trigger packet.
-
a static configuration for static hosts.
-
-
subscriber QoS - Ensure per service and per application SLAs, based on:
-
the overall subscriber rate
-
subscriber profiles
-
service level agreement profiles
-
-
subscriber security:
-
Avoid malicious access through anti-spoofing and based on access control lists (ACLs) / IP-filters.
-
DDOS mitigation.
-
-
subscriber persistency – The subscriber state is written to flash-disk (a.k.a. persistent data) and automatically restored on node reboot.
-
subscriber resiliency – The subscriber state is retained in case of a node failure in redundant environments, through Multi Chassis Synchronization (MCS).
-
subscriber troubleshooting, using:
-
OAM test.
-
mirroring.
-
debugging and event logging.
-
Enhanced Subscriber Management (ESM) implies subscriber management functions are applied at subscriber level. Subscriber hosts are created, and all of the features listed above apply.
Basic Subscriber Management (BSM) implies subscriber management functions are applied at SAP level. Only a subset of the functions listed above apply.
This example gives an overview of the ESM data required to perform subscriber management functions, and how the ESM data is organized.
The following terminology is used extensively in Triple Play Service Delivery Architecture (TPSDA) and is key to understanding ESM:
device
subscriber host
subscriber
A device is equipment located at the customer premises. Example devices are computers, smartphones, set-top boxes, etc including the Residential Gateway (RGW) providing the connection towards the Internet. The RGW is connected to the access network using an XDSL-connection, a PON-connection, and so on.
A subscriber is a collection of subscriber hosts connected to a single RGW. The subscriber is identified by its subscriber ID, a character string of 32 characters maximum which is used for administrative purposes.
Unlike devices, which are physical entities, subscribers and subscriber hosts are logical entities. These are created dynamically and resources are allocated when a device connects to the network and becomes active.
The following host types are recognized by the Broadband Network Gateway (BNG):
DHCP hosts
PPPoE hosts
ARP hosts
The BNG uses the combination of following parameters to uniquely identify a single subscriber host:
SAP ID
IP address
MAC address
session ID (PPPoE only)
Multiple subscriber hosts can be associated with a single device.
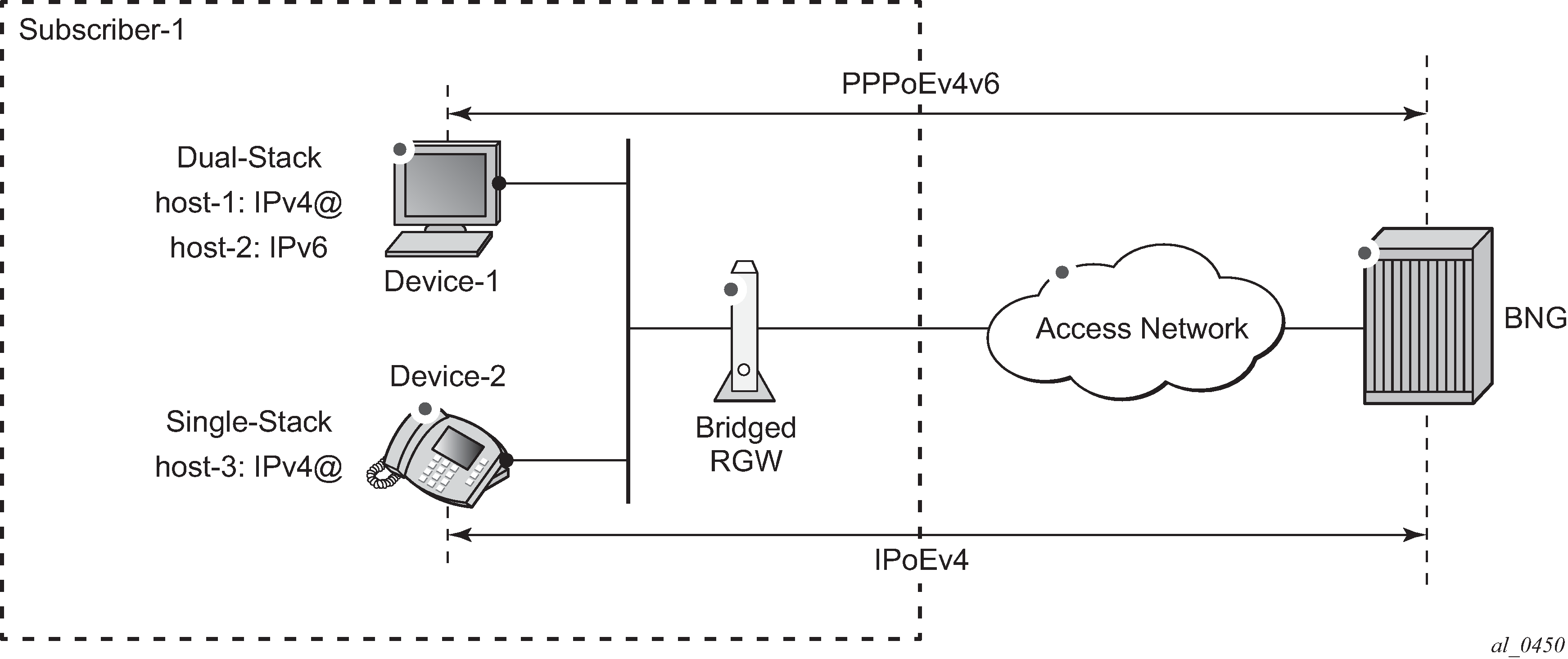
Bridged RGW Scenario shows a bridged RGW scenario. Subscriber-1has two devices, device-1 and device-2. Device-1 is a dual stack PPPoE device and is assigned an IPv4 address for host-1 and an IPv6 SLAAC prefix for host-2, both running over a single PPPoE session. Device-2 is a single stack IPoE device and is assigned an IPv4 address for host-3.
Routed RGW Scenario shows a routed dual stack RGW scenario. Subscriber-2 has two devices but they are hidden behind the RGW. The IP-addresses used by these devices are not known by the BNG. The RGW contains three hosts:
Host-1 is assigned an outside IPv4 address, which the RGW uses for Network Address Translation (NAT).
Host-2 is assigned an IPv6 wan host address or SLAAC prefix, which the RGW uses towards the outside network.
Host-3 is assigned an IPv6 prefix for prefix delegation, which the RGW uses for allocating IPv6 addresses to IPv6 capable devices in the home network.
Figure 2. Routed RGW Scenario 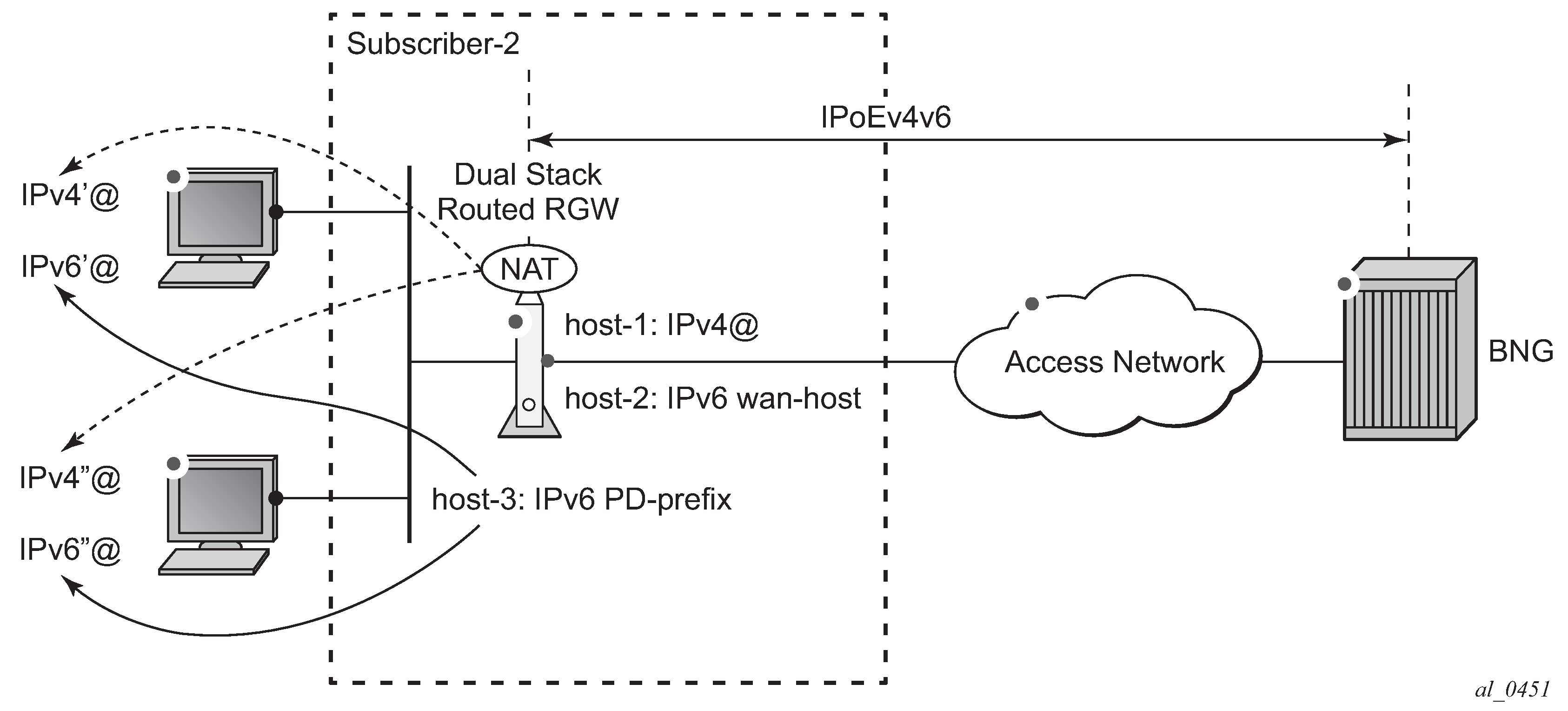
Detailed information on both scenarios can be found in ESMv6: IPoE Dual Stack Hosts and the ESMv6: PPPoE Dual Stack Hosts respectively.
Configuration
SLA-Profile and Sub-Profile shows two objects closely related to subscribers and subscriber hosts:
SLA profile
Subscriber profile
Figure 3. SLA-Profile and Sub-Profile 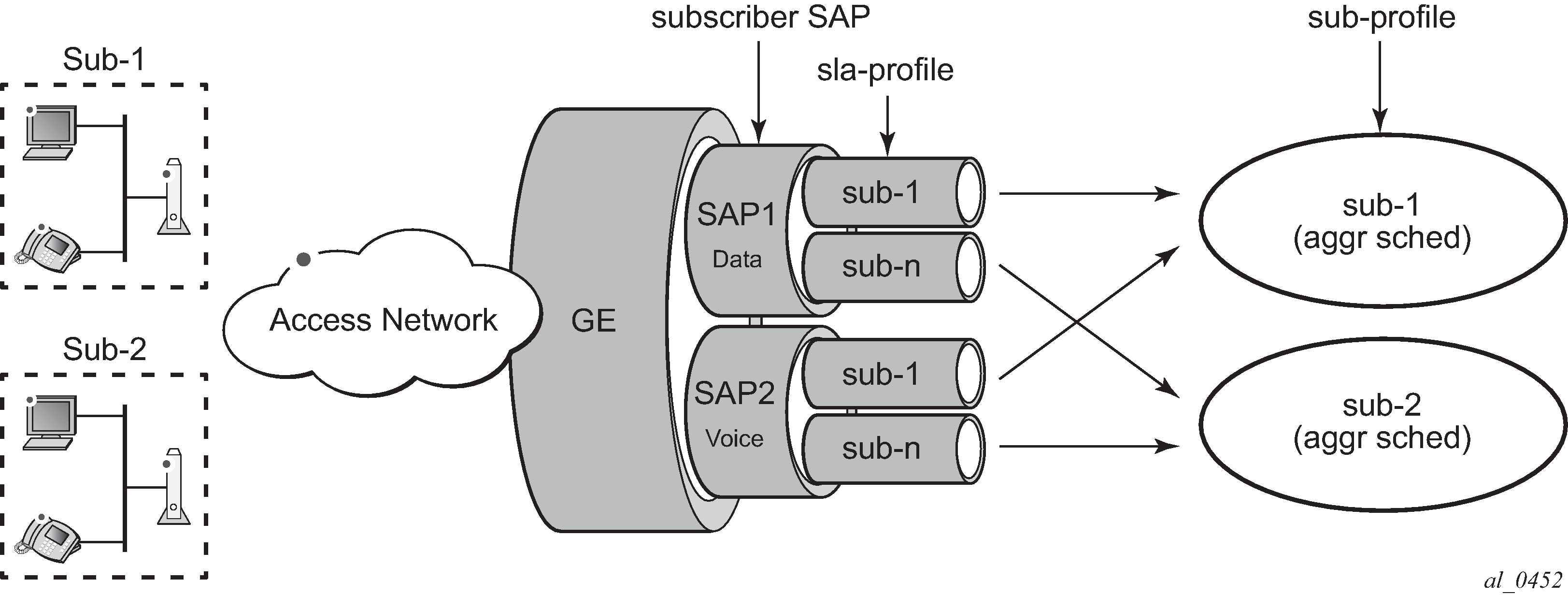
SLA Profile
A Service Level Agreement profile (SLA profile) is a template identified by name (maximum 32 chars) which defines:
per service QoS settings as part of the QoS policy (ingress and egress):
queue/policer
scheduling/priority levels
bandwidth limits (CIR/PIR) and queue/policer depths (MBS/CBS)
classification
(re-)marking
IP-filters for IPv4 and/or IPv6 (ingress and egress):
Access Control Lists (ACL)/Filters
host-limit
credit-control
An example SLA profile is shown below.
configure
subscriber-mgmt
sla-profile "sla-prof-1" create
ingress
qos 100
exit
exit
egress
qos 100
exit
exit
exit
An instance of the sla-profile is created at host instantiation time.
The SLA profile enforces traffic control on a per service per subscriber basis. When multiple hosts for the same subscriber use the same SLA profile they share the same set of queues/policers as long as they are on the same SAP. The combined traffic for these hosts is controlled by the settings defined in the SLA profile.
Subscriber Profile
The subscriber profile (sub-profile) is a template identified by name (maximum 32 chars) which defines:
per subscriber QoS settings:
aggregate rate (egress only)
scheduler policy (ingress and egress)
policer control policy (ingress and egress)
the accounting profile (RADIUS or XML)
multicast parameters (igmp-policy, etc.)
Network Address Translation (NAT) parameters
the ANCP (Access Node Control Protocol) parameters
the default sla-profile mappings
etc.
An example subscriber profile is shown below.
configure
subscriber-mgmt
sub-profile "sub-prof-1" create
ingress
policer-control-policy "pol-ctrl-1"
exit
exit
egress
scheduler-policy "down-1"
exit
exit
exit
An instance of the sub-profile is created at host instantiation time.
The sub-profile enforces traffic control on a per subscriber basis. he aggregate traffic of all hosts of a particular subscriber is controlled by the settings defined in the sub-profile, as long as the subscriber hosts are terminated on the same card.
QoS details are out of the scope of this example.
Subscriber SAP
A subscriber SAP is a SAP in a VPLS (Bridged CO model, which is not covered), VPRN or IES service (both in the Routed CO model) on which the queues/policers and other resources are allocated and de-allocated on a per subscriber basis.
A static SAP is a subscriber SAP when sub-sla-mgmt is enabled and becomes operational when in the no shutdown state. Multiple subscribers can connect through this SAP simultaneously when multi-sub-sap is enabled.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
sap 1/1/1:101 create
description "data SAP for DLSAM-1"
sub-sla-mgmt
multi-sub-sap 400
---snip---
no shutdown
exit
exit
Single SAP parameters (profiled-traffic-only and non-sub-traffic) are taken into account only when multi-sub-sap is left at its default of 1.
Subscriber Host Identification and Instantiation
The general subscriber host identification (authentication) process is depicted in Subscriber Host Identification and Instantiation Process and encompasses fetching the ESM data for a connecting device.
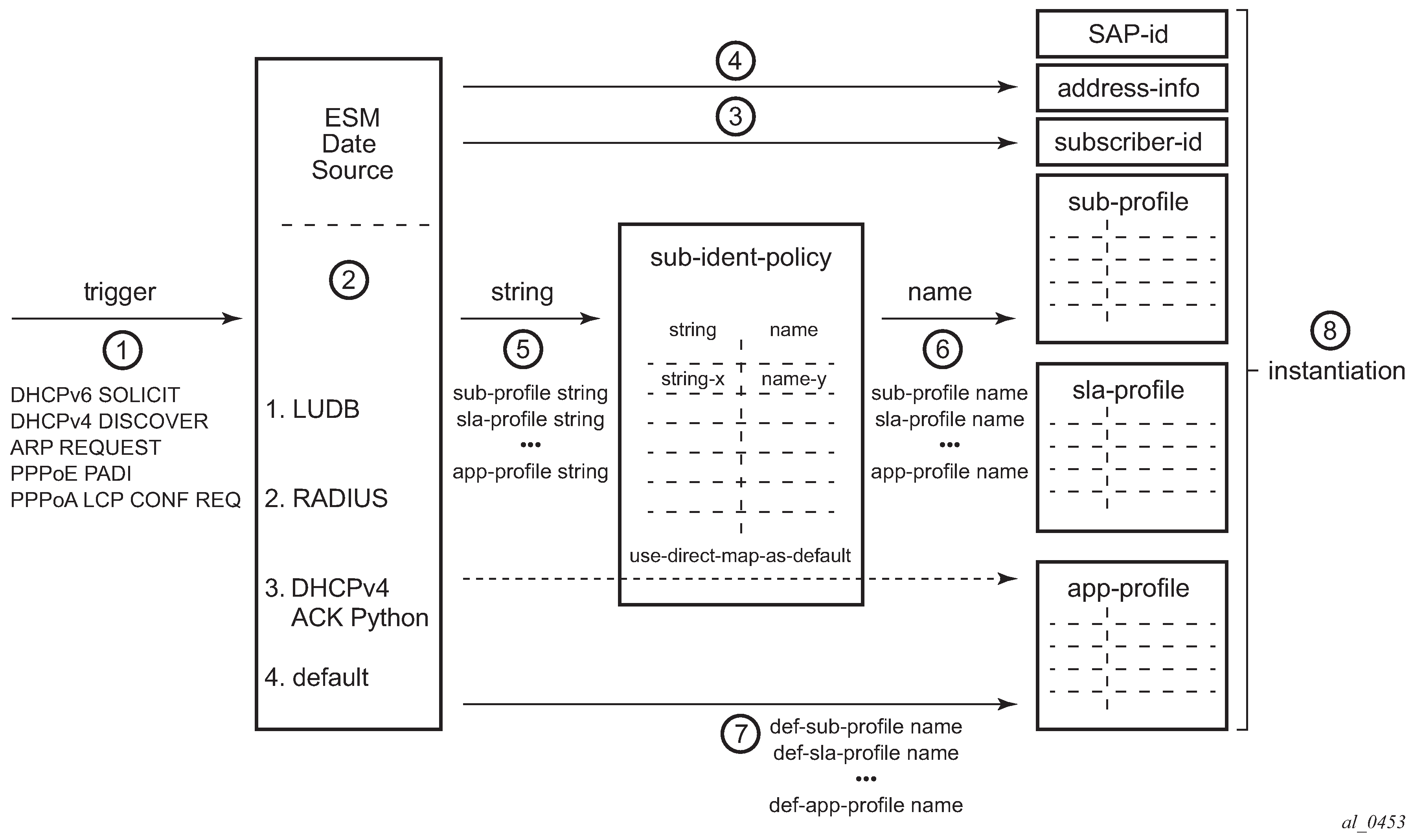
ESM data is organized as a set of profiles which control the behavior of individual subscribers and subscriber hosts.
Static hosts are instantiated using the manually provisioned ESM data.
For dynamic hosts, the host identification and instantiation process is started by a trigger message (1 in Subscriber Host Identification and Instantiation Process) which can be one of the following:
DHCPv4 DISCOVER
DHPCv6 SOLICIT
PPPoE PADI
PPPoA LCP Configuration Request
ARP REQUEST
The following types of ESM data are distinguished as mandatory or optional ESM data.
Mandatory ESM data is:
address information (IPv4 and/or IPv6)
subscriber ID
sub-profile data
sla-profile data
Optional ESM data includes:
app-profile data
inter-dest-id
Access Node Control Protocol (ANCP) data
A host is instantiated only when all mandatory ESM data is available for that host.
The ESM data sources (2) are consulted in following predefined sequence:
LUDB
RADIUS
DHCPv4 ACK python
Default
The ESM data sources provide:
the subscriber-id (3)
the profile strings (5)
Address information (IPv4 and/or IPv6) (4) can be provided by:
the LUDB or RADIUS ESM data sources
a DHCP server
The LUDB, RADIUS or DHCPv4 ACK python ESM data sources provide profile strings (5) which have a maximum length of 16 characters. They must be translated into profile names (6) which have a maximum length of 32 characters. The profile name is the key to access the actual profile data. The ESM data source default directly returns profile names (7), which do not need any translation.
The ESM string to profile name translation is defined in configurable mapping tables which are part of the subscriber identification policy (sub-ident-policy). Mapping tables can be defined for:
the sub-profile
the sla-profile
the app-profile
In case no mapping is needed because the strings and names are set to the same set of values, then a subscriber identification policy is needed with the attribute use-direct-map-as-default. (See section Subscriber Identification Policy.)
Note the subscriber-id does not need to be translated.
The instantiation process (8) ensures the subscriber host is created:
The subscriber host is added to the active subscriber list.
Resources (queues, policers, filters, etc) are allocated for SLA enforcement.
Status information is updated.
As a result the system starts forwarding user data to and from that subscriber host.
A subscriber is instantiated as soon as the first subscriber host for this subscriber is instantiated, and deleted when the last subscriber host for this subscriber is deleted.
Subscriber Identification Policy
The subscriber identification policy is identified by name and defines:
a description (optional)
the sub-profile map
the sla-profile map
the app-profile map (optional)
the location of a DHCPv4 ACK python script (optional):
primary, secondary and tertiary locations are possible
the DHCP option used to get the identification strings from (optional)
A subscriber identification policy is needed for dynamic hosts only. In that case one of the ESM data sources from Subscriber Host Identification and Instantiation Process is used.
Using a python script for subscriber host identification and instantiation is restricted to IPv4 hosts when triggered by the DHCPv4 ACK message.
The first example has no explicit mappings.
configure
subscriber-mgmt
sub-ident-policy "sub-id-pol-1" create
description "direct mapping policy"
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
app-profile-map
use-direct-map-as-default
exit
exit
The second example contains explicit mappings.
configure
subscriber-mgmt
sub-ident-policy "sub-id-pol-2" create
description "explicit mapping policy"
sub-profile-map
entry key "sub-string-1" sub-profile "sub-prof-1"
entry key "sub-string-2" sub-profile "sub-prof-2"
entry key "sub-string-3" sub-profile "sub-prof-3"
exit
sla-profile-map
entry key "sla-string-1" sla-profile "sla-prof-1"
entry key "sla-string-2" sla-profile "sla-prof-2"
entry key "sla-string-21" sla-profile "sla-prof-20"
entry key "sla-string-22" sla-profile "sla-prof-20"
exit
exit
Note that multiple strings can be mapped to the same profile, as the example above shows.
The subscriber identification policy is applied at SAP level in the sub-sla-mgmt context, as shown below.
configure
service
ies 1
subscriber-interface "sub-int-1" create
---snip---
group-interface "grp-int-1-1" create
---snip---
sap 1/1/1:111 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-1"
multi-sub-sap 400
no shutdown
exit
exit
exit
exit
Combining Multiple ESM Data Sources
Multiple ESM data sources from Subscriber Host Identification and Instantiation Process can be consulted for instantiating a subscriber host. When multiple ESM data sources are used, they are accessed in following sequence:
LUDB
RADIUS
DHCPv4 ACK python
Default
The outputs from the different data sources are merged. Data is appended as explained in the Flexible Authentication Model in ESM section of this guide.
Default ESM Data Profiles
Default ESM data profiles are used when the other ESM data sources (LUDB, RADIUS, DHCPv4 ACK python) only provide partial data, or no data at all. The default data complements the data provided by the data sources in order to get the full set of ESM data needed for host instantiation.
Default ESM data profiles are defined per SAP in the sub-sla-mgmt context, as shown in the following example.
configure
service
ies 1
subscriber-interface "sub-int-1-1"
group-interface "grp-int-1-1"
sap 1/1/1:111 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-1"
multi-sub-sap 400
no shutdown
exit
Address Information
Address information for both IPv4 as well as IPv6 is provided to subscriber hosts using a DHCPv4/v6 server, an LUDB or a RADIUS server.
The IPv4 and IPv6 address information encompasses:
IPv4 and/or IPv6 address/mask and prefix
default gateway (in IPv6 announced through RA messages)
DNS server(s)
etc
The following cases can be distinguished to obtain an IPv4 or IPv6 address/prefix upon LUDB/RADIUS authentication:
LUDB/RADIUS returns a unique IPv4/IPv6 address/prefix, directly.
LUDB/RADIUS returns a pool name, which then is resolved to a unique IP address/prefix through:
a DHCP server
or Local Address Assignment (LAA)
LUDB/RADIUS does not return a unique IPv4/IPv6 address/prefix, nor a pool-name. In that case a DHCP server is contacted using a gi-address or link-address to obtain an address/prefix.
Configuring a DHCP server is out of the scope of this example.
Direct Address Assignment using LUDB/RADIUS
In the example shown in Direct Address Assignment using LUDB/RADIUS, a unique IP address is retrieved from LUDB/RADIUS. No interaction with a DHCP server is needed at all.
This scenario applies to IPoE (DHCPv4, DHCPv6 and SLAAC) as well as to PPPoE (IPCP, DHCPv6, and SLAAC).
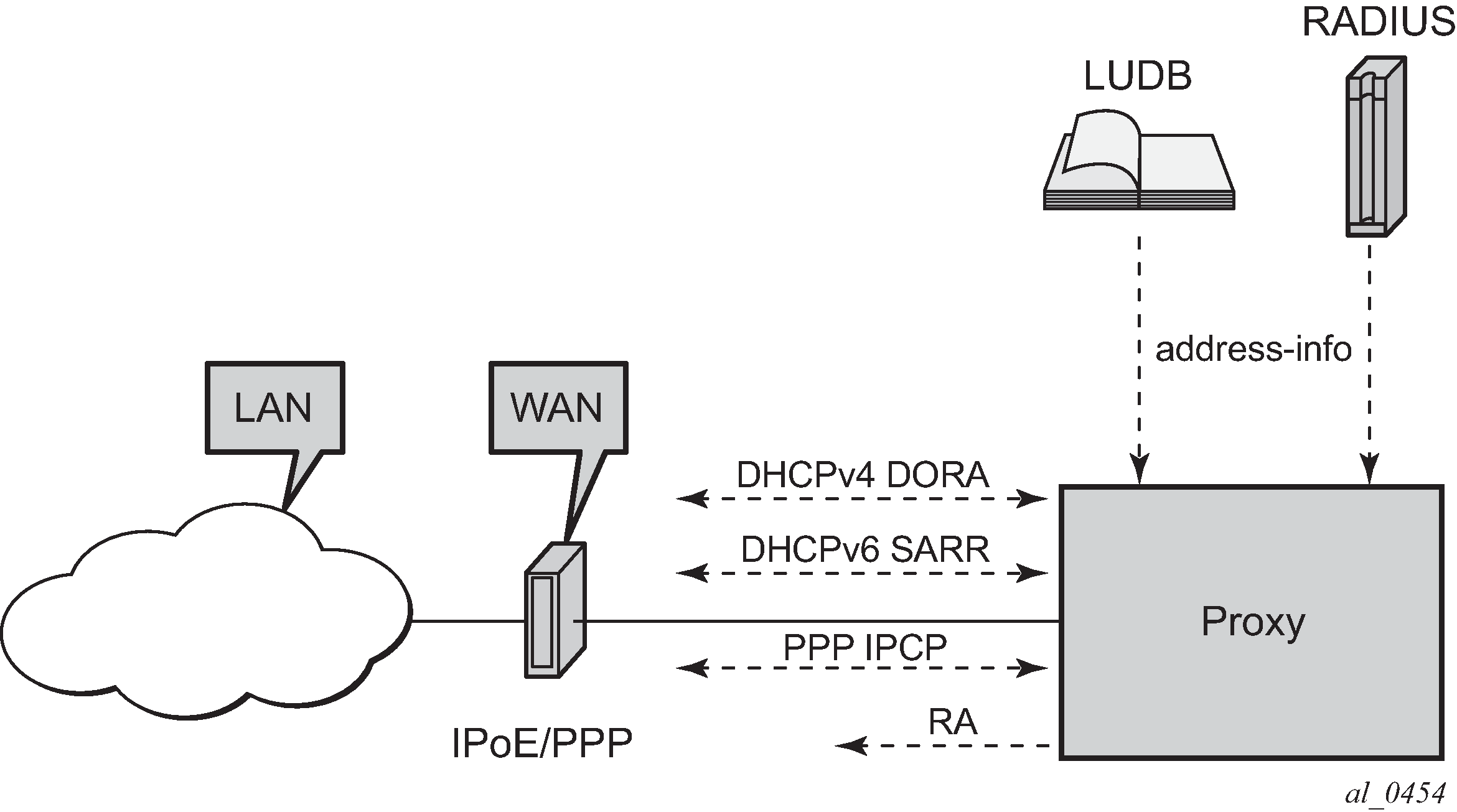
DHCP clients require a DHCP server address in the DHCP messages, and as such a server-id (IPv6) and/or an emulated-server (IPv4) must be configured, see the example below. IPCP and SLAAC do not require a DHCP server so these commands can be omitted.
configure
service
ies 1
subscriber-interface "sub-int-1" create
---snip---
group-interface "grp-int-1-1" create
ipv6
dhcp6
---snip---
proxy-server
server-id duid-ll
client-applications dhcp ppp
no shutdown
exit
exit
exit
arp-populate
dhcp
proxy-server
emulated-server 10.1.1.254
no shutdown
exit
---snip---
exit
The emulated-server address must be a unique address in one of the subnets allowed on this subscriber interface.
Indirect Address Assignment using a DHCP server
In the example shown in Indirect Address Assignment using a DHCP Server, the IPv4/IPv6 address/prefix is obtained from a DHCP server, using a pool-name as returned by LUDB/RADIUS.
The DHCP server (DHCPv4/DHCPv6) can be co-located with the BNG node (internal DHCP server) or can be external to the BNG node.
This scenario applies to both DHCPv4/DHCPv6 as well as to PPP. PPP relies on an internal DHCP client and communicates with the PPP client through IPCP.
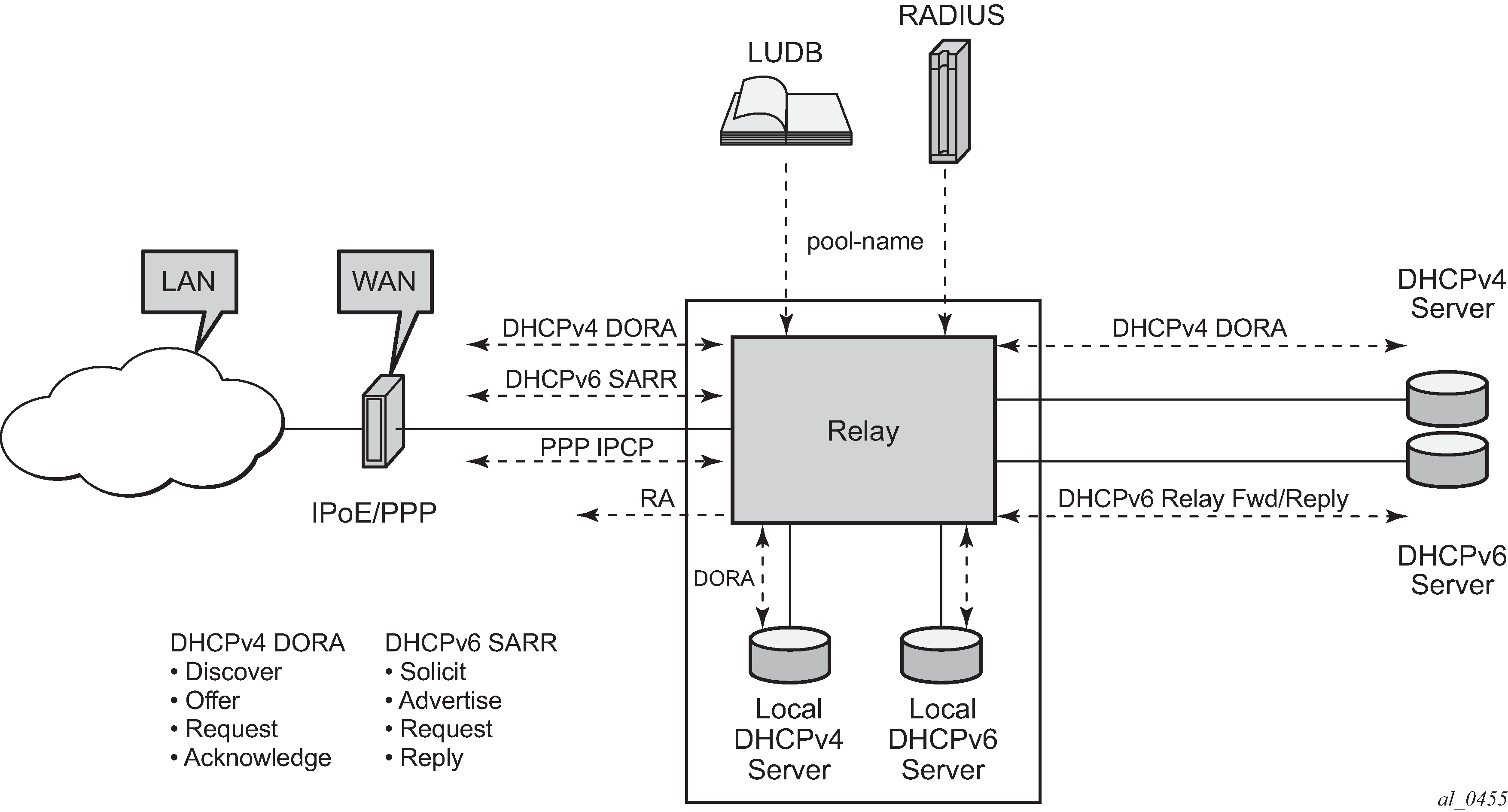
Relaying is configured for IPv4 and for IPv6 separately, at group-interface level.
The DHCPv4 relay agent is configured in the dhcp context:
gi-address – The gateway IPv4-address used by the relay-agent.
server - The DHCP server IPv4-address, 10.11.11.11 in the example.
client-applications dhcp ppp
The DHCP server accepts requests for DHCP and for PPP.
option – The options added/removed to/from messages towards the server. In the example the circuit-id, the remote-id and the pool-name are added.
trusted – This parameter ensures that DHCP messages with option 82 included and the gi-address set to zero are being processed instead of being dropped.
The DHCPv6 relay agent is configured in the ipv6 dhcp6 relay context:
server - The DHCP server IPv6 address, 2001:DB8::11 in the example.
client-applications dhcp ppp
The DHCP server accepts requests for DHCP and for PPP.
configure
service
ies 1
subscriber-interface "sub-int-1"
---snip---
group-interface "grp-int-1-1"
ipv6
---snip---
dhcp6
relay
server 2001:DB8::11
client-applications dhcp ppp
no shutdown
exit
exit
exit
dhcp
option
action replace
circuit-id
remote-id
vendor-specific-option
pool-name
exit
exit
server 10.11.11.1
trusted
lease-populate 100
client-applications dhcp ppp
gi-address 10.1.1.254
no shutdown
exit
Indirect Address Assignment using LAA
In the example shown in Indirect Address Assignment using LAA LUDB/RADIUS returns a pool-name which is resolved into an IP address using Local Address Assignment (LAA). LAA is implemented using a procedure call to an internal DHCP server, and not through the typical DHCPv4 DORA or DHCPv6 SARR sequence.
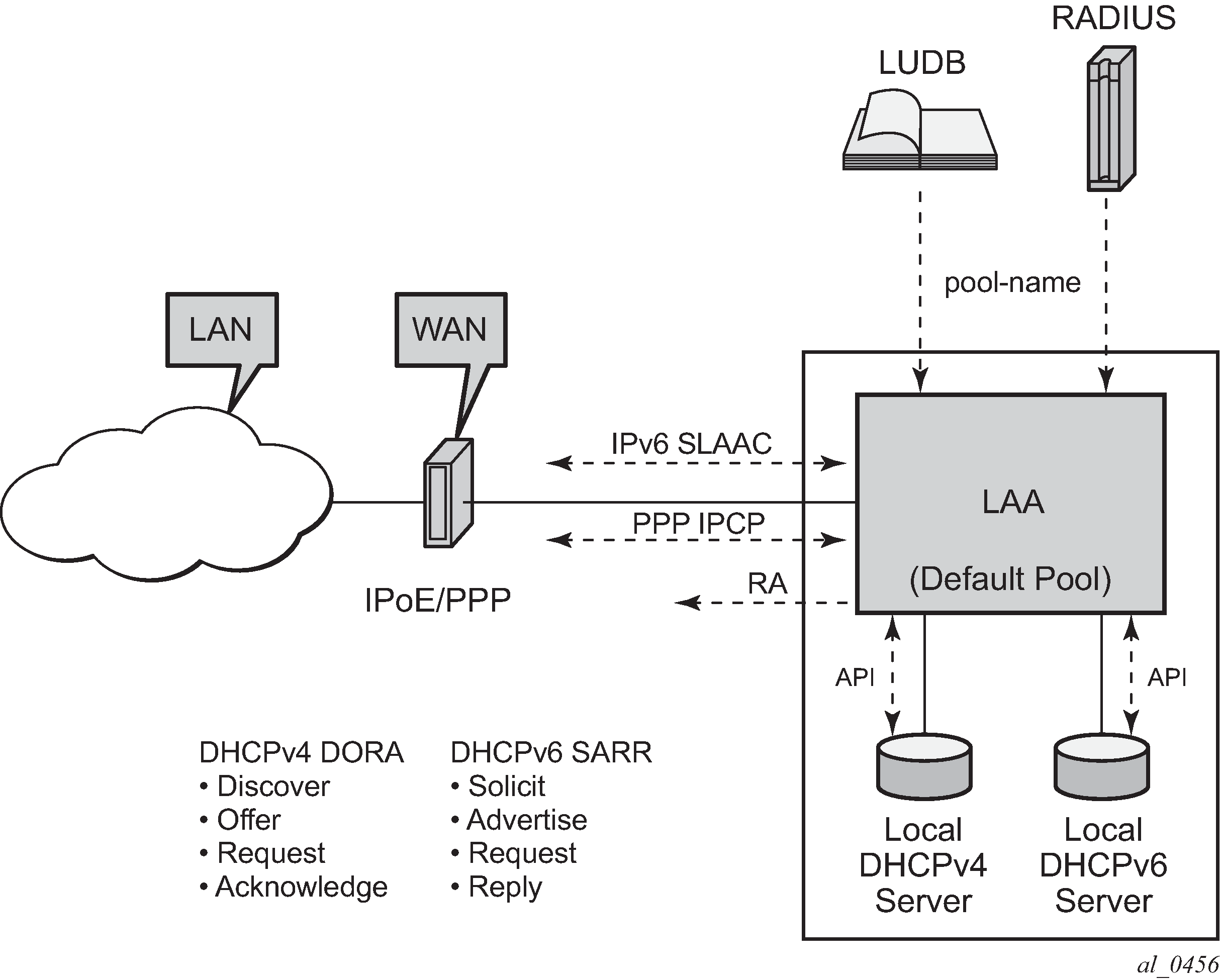
This scenario applies to PPPv4 hosts as well as to IPv6 SLAAC hosts. LAA can also be used to provide the IA-NA address in DHCPv6 proxy scenarios where an LUDB or a RADIUS server provides an IPv6 Delegated Prefix (Delegated-IPv6-Prefix) and an IPv6 WAN Address Pool (Framed-IPv6-Pool).
LAA is configured at group-interface level and overrules the relay scenario for the IPCP DHCP client (PPP) when both are configured.
The IPv4 parameters are configured in the local-address-assignment context:
server – The internal DHCPv4 server to contact, identified by name.
default-pool – Defines the pool name to use in case neither the LUDB nor the RADIUS server provides a pool-name.
client-application – ppp-v4.
The IPv6 parameters are configured in the local-address-assignment ipv6 context:
server – the DHCPv6 server to contact, identified by name.
client-application – ppp-slaac and/or ipoe-wan.
An example is show below.
configure
service
ies 1
subscriber-interface "sub-int-1" create
---snip---
group-interface "grp-int-1-1" create
local-address-assignment
server "int-dhcp-v4"
client-application ppp-v4
default-pool "pool4-2"
ipv6
server "int-dhcp-v6"
client-application ppp-slaac ipoe-wan
exit
no shutdown
exit
LAA details are out of the scope of this example.
ESM Data Retrieval Examples
The following ESM data source scenarios are examined below:
static host ESM data retrieval
dynamic host ESM data retrieval:
RADIUS
LUDB + RADIUS access
DHCPv4 ACK python details are out of the scope of this example.
ESM Data Retrieval for Static Hosts
The example below shows the creation of a static host. The IP address is mandatory, a MAC address is optional.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
sap 1/1/1:111
description "sap for customer 1"
static-host ip 10.1.1.101 create
sla-profile "sla-prof-2"
sub-profile "sub-prof-2"
subscriber 03-7654321
no shutdown
exit
exit
Identification is not needed for static hosts: the subscriber-id, sub-profile and sla-profile used, are configured explicitly. Instantiation takes place at host creation time (no shutdown).
The following command shows the details for a single static host. The forwarding state is Not Fwding, meaning that no traffic can be forwarded to and from that host in this state.
*A:BNG# show service id 1 static-host ip-address 10.1.1.101 detail
===============================================================================
Static Hosts for service 1
===============================================================================
Sap IP Address Configured MAC Dynamic MAC
Subscriber Admin State Fwding State
-------------------------------------------------------------------------------
1/1/1:111 10.1.1.101 N/A N/A
03-7654321 Up Not Fwding
-------------------------------------------------------------------------------
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-1
Sub Profile : sub-prof-2
SLA Profile : sla-prof-2
App Profile : N/A
-------------------------------------------------------------------------------
Number of static hosts : 1
===============================================================================
*A:BNG# #
Once the MAC address of the host is learned through the ARP protocol, the forwarding state is set to Fwding and traffic now can be forwarded to and from that host.
*A:BNG# show service id 1 static-host
===============================================================================
Static Hosts for service 1
===============================================================================
Sap IP Address Configured MAC Dynamic MAC
Subscriber Admin State Fwding State
-------------------------------------------------------------------------------
1/1/1:111 10.1.1.101 N/A 00:00:00:99:99:99
03-7654321 Up Fwding
-------------------------------------------------------------------------------
Number of static hosts : 1
===============================================================================
*A:BNG# #
ESM Data Retrieval through RADIUS
A RADIUS server can provide ESM data, including:
subscriber-id
address information
sub-profile-string
sla-profile-string
etc.
The BNG sends a RADIUS Access-Request including the User-Name attribute identifying the host for authentication purposes. The User-Name format is configurable on the BNG:
MAC-address
circuit-ID, remote-ID
user@domain
etc.
An excerpt from the Free-RADIUS user file used for this example is shown below. The first line of a block contains the User-Name with the credentials.
00:00:00:22:22:22 Auth-Type := Local, Cleartext-Password := ""
Alc-Subsc-ID-Str = "sub-22",
Alc-Subsc-Prof-Str = "sub-string-1",
Alc-SLA-Prof-Str = "sla-string-1"
BSAN64|40|1/1/2:300 Auth-Type := Local, User-Password == "LetMeIn"
Alc-Subsc-ID-Str = "subscriber-300",
Alc-Subsc-Prof-Str = "subpro1-string",
Alc-SLA-Prof-Str = "slapro1-string",
Session-Timeout = 600
sub202@provider Cleartext-Password := "sub202"
Alc-Subsc-ID-Str = "sub-44",
Alc-Subsc-Prof-Str = "sub-string-3",
Alc-SLA-Prof-Str = "sla-string-22",
Framed-IP-Address = 10.2.1.202,
Framed-IP-Netmask = 255.255.255.0
The lines following the User-Name with the credentials lists the attributes the RADIUS server returns after successfully authenticating the user, and include:
Alc-Subsc-ID-Str
Alc-Subsc-Prof-Str
Alc-SLA-Prof-Str
Framed-IP-Address
Framed-IP-Netmask
etc.
Authentication Policy
An authentication policy is needed for retrieval of the data from a RADIUS server, indirectly indicating the RADIUS server(s) to contact.
The following steps are needed to create an authentication policy:
Define one or more RADIUS servers.
Define a RADIUS server policy.
Define an authentication policy.
The example defines a single RADIUS server, indicating the name, the address and the secret to use.
configure router radius-server server "server-1" address 192.168.202.84 secret secret-1 create exitThe radius-server-policy refers to the server defined above. In this example the Base router is used to reach the RADIUS server.
configure aaa radius-server-policy "rad-serv-pol-1" create description "Radius AAA server policy" servers router "Base" server 1 name "server-1" exit exitThe authentication policy specifies to include the circuit-id and the remote-id attributes towards the RADIUS server as well as the radius-server-policy to use. Multiple authentication policies can be defined.
configure subscriber-mgmt authentication-policy "auth-pol-1" create pppoe-access-method pap-chap include-radius-attribute circuit-id remote-id exit radius-server-policy "rad-serv-pol-1"
The authentication policy is applied at a group-interface. The example below shows both group interfaces using the same authentication policy.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
---snip---
authentication-policy "auth-pol-1"
---snip---
exit
group-interface "grp-int-1-2"
---snip---
authentication-policy "auth-pol-1"
---snip---
exit
DHCP Host
The following command shows the strings returned by the RADIUS server for the DHCPv4 host with MAC-address 00:00:00:22:22:22.
A:BNG# show service id 1 dhcp lease-state mac 00:00:00:22:22:22 detail
===============================================================================
DHCP lease states for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.1.9
Client HW Address : 00:00:00:22:22:22
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-1
SAP : 1/1/1:112
Up Time : 0d 00:03:30
Remaining Lease Time : 9d 23:56:30
Remaining SessionTime: N/A
Persistence Key : N/A
Sub-Ident : "sub-22"
Sub-Profile-String : "sub-string-2" # profile string before translation
SLA-Profile-String : "sla-string-2" # profile string before translation
App-Profile-String : ""
Lease ANCP-String : ""
Lease Int Dest Id : ""
Category-Map-Name : ""
---snip---
Lease-Time : 10d 00:00:00
DHCP Server Addr : 10.11.11.1
Radius User-Name : "00:00:00:22:22:22"
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
A:BNG#
The strings returned by the RADIUS server are translated according the subscriber identification profile for retrieval of the actual profile data.
The actual profiles being used can be found using following command.
*A:BNG# show service id 1 subscriber-hosts mac 00:00:00:22:22:22 detail
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
1/1/1:112 sub-22
10.1.1.6
00:00:00:22:22:22 N/A DHCP Fwding
-------------------------------------------------------------
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-1
Sub Profile : sub-prof-2 # profile name after translation
SLA Profile : sla-prof-2 # profile name after translation
App Profile : N/A
Egress Q-Group : N/A
---snip---
-------------------------------------------------------------
Number of subscriber hosts : 1
=============================================================
*A:BNG#
PPP Host
The following command shows the strings returned by the RADIUS server for the PPP host with user-name sub202@provider.
*A:BNG# show service id 1 ppp session user-name sub202@provider detail
===============================================================================
PPP sessions for service 1
==============================================================================
User-Name : sub202@provider
Description : svc:1 sap:1/1/1:212 mac:00:00:00:44:44:44 sid:1
Up Time : 0d 00:17:13
Type : oE
Termination : local
IP/L2TP-Id/If-Id : 10.2.1.202
MC-Standby : No
Session Time Left : N/A
---snip---
Subscriber : "sub-44"
Sub-Profile-String : "sub-string-3" # profile string before translation
SLA-Profile-String : "sla-string-22" # profile string before translation
ANCP-String : ""
Int-Dest-Id : ""
App-Profile-String : ""
Category-Map-Name : ""
---snip---
Radius Class :
Radius User-Name : sub202@provider
---snip---
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
*A:BNG# #
The actual profiles being used can be found using following command.
*A:BNG# show service id 1 subscriber-hosts mac 00:00:00:44:44:44 detail
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
1/1/1:212 sub-44
10.2.1.202
00:00:00:44:44:44 1 IPCP Fwding
-------------------------------------------------------------
Subscriber-interface : sub-int-2
Group-interface : grp-int-2-1
Sub Profile : sub-prof-3 # profile name after translation
SLA Profile : sla-prof-20 # profile name after translation
App Profile : N/A
---snip---
-------------------------------------------------------------
Number of subscriber hosts : 1
=============================================================
*A:BNG#
For both the DHCPv4 host as well as the PPPv4 host, the output aligns with the data provided by the RADIUS server and the defined profile maps.
ESM Data Retrieval through a Local User Database
A Local User Database (LUDB) can provide ESM data for DHCP and PPP hosts, including:
subscriber-id
address information
sub-profile string
sla-profile string
MSAP service-id
retail service-id
etc.
Retrieval of data in an LUDB requires matching criteria, which can be one of the following items, or a combination of the following items, including:
MAC-address
circuit-id/remote-id
username
SAP-id
etc.
The example below defines an LUDB named ludb-1 which matches DHCP hosts by means of MAC address, and PPP hosts by means of username.
configure
subscriber-mgmt
local-user-db "ludb-1" create
dhcp
match-list mac
host "host-121" create
host-identification
mac 00:00:00:aa:aa:aa
exit
address 10.1.1.121
identification-strings 254 create
subscriber-id "sub-121"
sla-profile-string "sla-string-3"
sub-profile-string "sub-string-2"
exit
options
subnet-mask 255.255.255.0
default-router 10.1.1.254
exit
ipv6-wan-address-pool "pool6-2"
ipv6-delegated-prefix-pool "pool6-2"
no shutdown
exit
host "host-122" create
host-identification
mac 00:00:00:bb:bb:bb
exit
auth-policy "auth-pol-1"
no shutdown
exit
exit
ppp
match-list username
host "host-123" create
host-identification
username "user@domain"
exit
address 10.1.1.123/32
password pap user
identification-strings 254 create
subscriber-id "sub-123"
sla-profile-string "sla-string-3"
sub-profile-string "sub-string-1"
exit
no shutdown
exit
exit
no shutdown
exit
The entire LUDB can be disabled.
Individual host entries can be disabled.
An LUDB can be applied at group interface level in different contexts:
dhcp
ipv6 dhcp6
ppp
pppoe
For the LUDB to provide ESM data, no authentication policy may be applied at group interface level, and the LUDB itself must be in the no shutdown state.
The following example shows the LUDB named ludb-1 applied to group-interface grp-int-1-2 in the dhcp and the pppoe context.
configure
service
ies 1
subscriber-interface "sub-int-1"
address 10.1.1.254/24
address 10.1.2.254/24
group-interface "grp-int-1-2"
dhcp
---snip---
gi-address 10.1.1.254
user-db "ludb-1"
no shutdown
exit
no authentication-policy
sap 1/1/1:121 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-1"
multi-sub-sap
no shutdown
exit
exit
sap 1/1/1:122 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-1"
multi-sub-sap
no shutdown
exit
exit
pppoe
session-limit 100
user-db "ludb-1"
no shutdown
exit
exit
For host-121, with MAC-address 00:00:00:aa:aa:aa, all ESM data is provided by the LUDB. The detailed DHCP lease state shows the actual profile strings, the subscriber-ID and the IP address used. The Lease Info origin is set to UserDb.
A:BNG# show service id 1 dhcp lease-state mac 00:00:00:aa:aa:aa detail
===============================================================================
DHCP lease states for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.1.121
Client HW Address : 00:00:00:aa:aa:aa
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-2
SAP : 1/1/1:121
---snip---
Sub-Ident : "sub-121"
Sub-Profile-String : "sub-string-2"
SLA-Profile-String : "sla-string-3"
---snip---
Lease Info origin : UserDb
---snip---
Ip-Netmask : 255.255.255.0
Broadcast-Ip-Addr : 10.1.1.255
Default-Router : 10.1.1.254
Primary-Dns : N/A
Secondary-Dns : N/A
---snip---
Relay Agent Information
Circuit Id : BNG|1|grp-int-1-2|1/1/1:121
Radius User-Name : ""
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
*A:BNG#
The detailed DHCPv6 lease state for the same host is shown below. The Lease State info now is DHCP for both IA-NA as well as for IA-PD where the IA-NA and the IA-PD are allocated by the DHCP server based on the ipv6-wan-address-pool and the ipv6-delegated-prefix-pool respectively, as indicated by the LUDB.
*A:BNG# show service id 1 dhcp6 lease-state mac 00:00:00:aa:aa:aa detail
===============================================================================
DHCP lease states for service 1
===============================================================================
Service ID : 1
IP Address : 2001:DB8:201::1/128
Client HW Address : 00:00:00:aa:aa:aa
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-2
SAP : 1/1/1:121
---snip---
Sub-Ident : "sub-121"
Sub-Profile-String : "sub-string-2"
SLA-Profile-String : "sla-string-3"
---snip---
Pool Name : "pool6-2"
Dhcp6 Server Addr : 2001:DB8::11
---snip---
Lease Info origin : DHCP
---snip---
Radius User-Name : ""
-------------------------------------------------------------------------------
Service ID : 1
IP Address : 2001:DB8:202::/56
Client HW Address : 00:00:00:aa:aa:aa
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-2
SAP : 1/1/1:121
---snip---
Sub-Ident : "sub-121"
Sub-Profile-String : "sub-string-2"
SLA-Profile-String : "sla-string-3"
---snip---
Pool Name : "pool6-2"
Dhcp6 Server Addr : 2001:DB8::11
---snip---
Lease Info origin : DHCP
---snip---
Radius User-Name : ""
-------------------------------------------------------------------------------
Number of lease states : 2
===============================================================================
*A:BNG#
Because only an authentication policy is defined for host-122, with MAC address 00:00:00:bb:bb:bb, the profile strings and the subscriber-ID are provided by the RADIUS server. The IP address is provided by the DHCP server. The Lease Info origin is set to DHCP.
A:BNG# show service id 1 dhcp lease-state mac 00:00:00:bb:bb:bb detail
===============================================================================
DHCP lease states for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.1.5
Client HW Address : 00:00:00:bb:bb:bb
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-2
SAP : 1/1/1:122
---snip---
Sub-Ident : "sub-122"
Sub-Profile-String : "sub-string-3"
SLA-Profile-String : "sla-string-1"
---snip---
Lease Info origin : DHCP
Ip-Netmask : 255.255.255.0
Broadcast-Ip-Addr : N/A
Default-Router : 10.1.1.254
---snip---
Lease-Time : 10d 00:00:00
DHCP Server Addr : 10.11.11.1
Relay Agent Information
Circuit Id : BNG|1|grp-int-1-2|1/1/1:122
Radius User-Name : "00:00:00:bb:bb:bb"
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
A:BNG#
For host-123, the subscriber-ID, the profile strings and the IP-address are provided by the LUDB. Similar to host-121, no interaction with a RADIUS server is needed at all. The IP origin is set to local-user-db.
A:BNG# show service id 1 ppp session user-name "user@domain" detail
===============================================================================
PPP sessions for service 1
===============================================================================
User-Name : user@domain
Description : svc:1 sap:1/1/1:122 mac:00:00:00:cc:cc:cc sid:1
Up Time : 0d 00:46:10
Type : oE
---snip---
PPP MTU : 1492
PPP Auth-Protocol : PAP
PPP User-Name : user@domain
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-2
IP Origin : local-user-db
DNS Origin : none
NBNS Origin : none
Subscriber : "sub-123"
Sub-Profile-String : "sub-string-1"
SLA-Profile-String : "sla-string-3"
---snip---
IP Address : 10.1.1.123/32
---snip---
Circuit-Id :
Remote-Id :
Radius Session-TO : N/A
Radius Class :
Radius User-Name :
Logical-Line-Id :
-------------------------------------------------------------------------------
No. of sessions: 1
===============================================================================
A:BNG#
LUDB details are out of the scope of this example.
Optional ESM Data
Limits
The maximum number of hosts, subscribers, sessions and leases are checked during the host instantiation process, and can be defined at following levels:
sla-profile level: host-limit
sap-level: multi-sub-sap
group-interface level: lease-populate, session-limit, sap-session-limit
The sla-profile optionally defines a maximum number of hosts allowed by this profile. An example is shown below.
configure
subscriber-mgmt
sla-profile "sla-prof-3" create
host-limit 4
ingress
qos 100
exit
exit
egress
qos 100
exit
exit
exit
By default only hosts from a single subscriber can connect through a SAP. This condition can be lifted as follows.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"sub-sla-mgmt
sap 1/1/1:112 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-2"
multi-sub-sap
no shutdown
exit
exit
The maximum number of leases assigned to subscriber hosts by the DHCP server can be defined at group interface level as follows.
configure
service
ies 1
subscriber-interface "sub-int-1"
address 10.1.1.254/24
group-interface "grp-int-1-1"
dhcp
proxy-server
emulated-server 10.1.1.254
no shutdown
exit
server 10.11.11.1
trusted
lease-populate 100
client-applications dhcp ppp
gi-address 10.1.1.254
no shutdown
exit
The maximum number of sessions for PPP as well as for PPPoE, including the sap-session-limit, is also defined at group interface level, as the example below shows.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
ppp
session-limit 50
exit
pppoe
session-limit 40
sap-session-limit 30
no shutdown
exit
Filtering
Filter policies allow for selectively dropping, forwarding or redirecting ingress/egress traffic. They are also known as access control lists (ACLs) and can optionally be included in the SLA-profile.
An example sla-profile with IP-filters is show below.
configure
subscriber-mgmt
sla-profile "sla-prof-3" create
host-limit 4
ingress
qos 100
exit
ip-filter 1
ipv6-filter 1
exit
egress
qos 100
exit
ip-filter 2
ipv6-filter 2
exit
Filter policies must be defined before they can be used in an SLA profile.
Accounting
Accounting policies define how to count the traffic for billing purposes on a per service basis. Two types of accounting are available:
RADIUS accounting
XML accounting
For RADIUS accounting, the accounting data is stored on the RADIUS accounting server. For XML accounting, the accounting data is stored locally on a flash-disk on the node.
The example below shows the definition of a radius-accounting-policy and reuses the radius-server-policy defined before.
configure
subscriber-mgmt
radius-accounting-policy "rad-acct-pol-1" create
host-accounting interim-update
update-interval 5
include-radius-attribute
framed-ip-addr
sla-profile
sub-profile
exit
radius-accounting-server
router "Base"
server 1 address 192.168.202.84 secret secret-1
exit
radius-server-policy "rad-serv-pol-1"
exit
The radius-accounting policy is referred to from the SUB profile as shown in the example below.
configure
subscriber-mgmt
sub-profile "sub-prof-1" create
radius-accounting-policy "rad-acct-pol-1"
ingress
policer-control-policy "pol-ctrl-1"
exit
exit
egress
scheduler-policy "down-1"
exit
exit
exit
For XML accounting, an accounting policy is referred to from the SUB profile.
configure
subscriber-mgmt
sub-profile "sub-prof-2" create
accounting-policy 10
collect-stats
ingress
scheduler-policy "sched-up-1"
exit
egress
scheduler-policy "sched-down-1"
exit
exit
exit
The collect-stats command activates the generation of accounting files.
Accounting policies must be defined before they can be used in a SUB profile.
RADIUS accounting and XML accounting details are out of the scope of this example.
Application Profile
An application profile is needed for supporting Application Assurance.
Traffic is diverted to an MS-ISA MDA which processes the traffic according the application profile, which for that purpose is assigned to:
an ESM subscriber, or an group of ESM subscribers
a SAP
a spoke SDP
ESM subscribers are assigned an application profile either statically or dynamically.
The example below shows the assignment of an application profile to a static host.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
sap 1/1/1:111
description "sap for customer 1"
static-host ip 10.1.1.101 create
app-profile "app-prof-3"
sla-profile "sla-prof-2"
sub-profile "sub-prof-1"
subscriber 03-7654321
no shutdown
exit
exit
For dynamic hosts, the same rules apply as for the sub-profile scriber and the sla-profile, meaning that the app-profile can be found through:
LUDB
RADIUS
DHCPv4 ACK python
Default
The example below shows the assignment of a default application profile at the SAP level.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"sub-sla-mgmt
sap 1/1/1:112 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
def-app-profile "app-prof-1"
sub-ident-policy "sub-id-pol-2"
multi-sub-sap
no shutdown
exit
exit
Application profiles must be defined before they can be referenced.
Application Assurance and Application Assurance subscribers details are out of the scope of this example.
Intermediate Destinations
An intermediate destination is an aggregation point in the network and identified through the intermediate destination identity (inter-dest-id).
Most typically Access Nodes (ANs) are considered intermediate destinations.
The inter-dest-id is an optional per subscriber attribute.
The intermediate destination is used in the BNG for supporting QoS, as an example:
By shaping the aggregate rate of all egress traffic of subscribers connected to an AN to prevent congestion of the link towards that AN.
To ensure fairness amongst the subscriber hosts connected to that AN. For that purpose the inter-dest-id is linked to an hierarchical scheduler via a virtual port (Vport).
The example below shows the assignment of the inter-dest-id to a static host.
configure
service
ies 1
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
sap 1/1/1:111
description "sap for customer 1"
static-host ip 10.1.1.101 create
inter-dest-id "bsan-1"
sla-profile "sla-prof-2"
sub-profile "sub-prof-1"
subscriber 03-7654321
no shutdown
exit
exit
The inter-dest-id does not to be translated.
Intermediate destination details are is out of the scope of this example.
Conclusion
This chapter explains basic ESM concepts including the definition of subscribers and subscriber hosts. The host identification and instantiation process was explained, indicating the mandatory and optional ESM data fetched during the process (address information, sub-profile, sla-profile, app-profile, inter-dest-id, etc.). The address information retrieval process was explained. The different sources from where the ESM data can originate were mentioned, including some examples. Also the sub-ident-policy and the authentication-policy, needed during the identification and instantiation process, are explained in detail.