BGP Unresolved Route Leaking from Base Router to VPRN
This chapter describes BGP unresolved route leaking from base router to VPRN.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 22.10.R2. BGP resolved route leaking between BGP routing instances is supported in SR OS Release 12.0.R7, and later; BGP unresolved route leaking from base router to VPRN is supported in SR OS Release 19.10.R1, and later.
Overview
The BGP Route Leaking chapter describes how BGP resolved routes can be leaked from one BGP routing instance to other BGP routing instances; for example, from the base router to a VPRN, from one VPRN to another VPRN, or from a VPRN to the base router. The first BGP routing instance (source) makes selected BGP routes in its RIB-IN leakable, so that these routes are available for import by BGP in other routing instances (destinations). BGP route leaking process between BGP routing instances X and Y shows the BGP route leaking process between BGP routing instances.
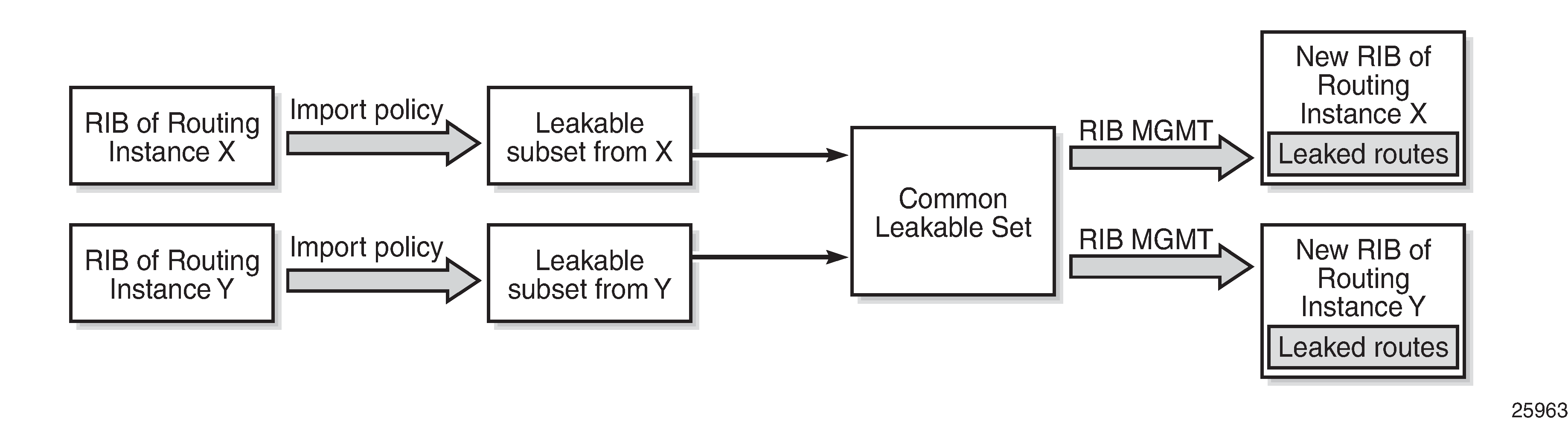
In SR OS Releases earlier than 19.10.R1, a BGP route is leakable if it meets the following conditions:
It must have been received from a BGP neighbor and matched by a BGP import policy that accepts the route with a bgp-leak true action.
It must have a BGP next-hop that is resolved by a route or tunnel belonging to the source routing instance.
Those leakable BGP routes can be imported into other destination BGP routing instances. A BGP RIB imports a leakable BGP route when it has a leak-import policy that matches and accepts the route.
Leaked BGP routes are compared to other (leaked and non-leaked) BGP routes for the same prefix to come up with the best path, Equal Cost Multi-Path (ECMP), backup path, and so on. A leaked route can be advertised to BGP peers of the importing BGP instance. A leaked route imported into a VPRN BGP instance can even be re-advertised as a VPN-IP route subject to the vrf-export policies of the VPRN.
The following use cases require that unresolved BGP routes are leaked from base router to VPRN. To avoid per-VPRN BGP sessions, a Route Reflector (RR) advertises BGP routes toward a PE over a single BGP session with the base router, even though some of the routes belong to VPRNs of the PE. The PE can determine the VPRN owner of a route from an attached community value. The BGP routes that belong to VPRNs can be marked as leakable in the base router, then imported into the correct VPRN based on community matching in the leak-import policies.
When the RR advertises a BGP route intended for a VPRN, the BGP next-hop of the route is resolvable in the VPRN instance, but not in the base router. The allow-unresolved-leaking true command must be added to the BGP next-hop-resolution context for the base router to allow any leakable route to be imported into any VPRN, even when the BGP next-hop is unresolved. The BGP next-hop is resolved as follows:
If the next-hop of a valid BGP route is resolvable in the base router, any VPRN that imports the route uses the next-hop resolution result of the base router, even if that VPRN is also able to resolve the BGP next-hop using its own routing table.
If the next-hop of a valid BGP route is unresolvable in the base router and allow-unresolved-leaking is set to true, any VPRN can import the route. A VPRN that imports the route then uses its own routing table to resolve the BGP next-hop:
By default, the importing VPRN can only use IGP routes, such as OSPFv2, OSPFv3, IS-IS, RIP, RIPng, and static routes to resolve the BGP next-hop of the leaked route.
If use-bgp-routes true is configured in the BGP next-hop-resolution context, the importing VPRN can also use BGP and BGP-VPN routes to resolve the BGP next-hop of the leaked route.
If a leaked BGP route is resolved by a VPRN, the VPRN can re-advertise the route to VPRN BGP peers or export the route as a VPN-IP route. However, if a leaked route is resolved over a BGP-VPN route, it can only be exported as a VPN-IP route if allow-bgp-vpn-export is enabled in the VPRN.
If a BGP route is invalid in the base router for reasons other than next-hop reachability, it is not leakable into any VPRN, regardless of the allow-unresolved-leaking setting.
Configuration
Example topology shows the example topology with an RR and two PEs.
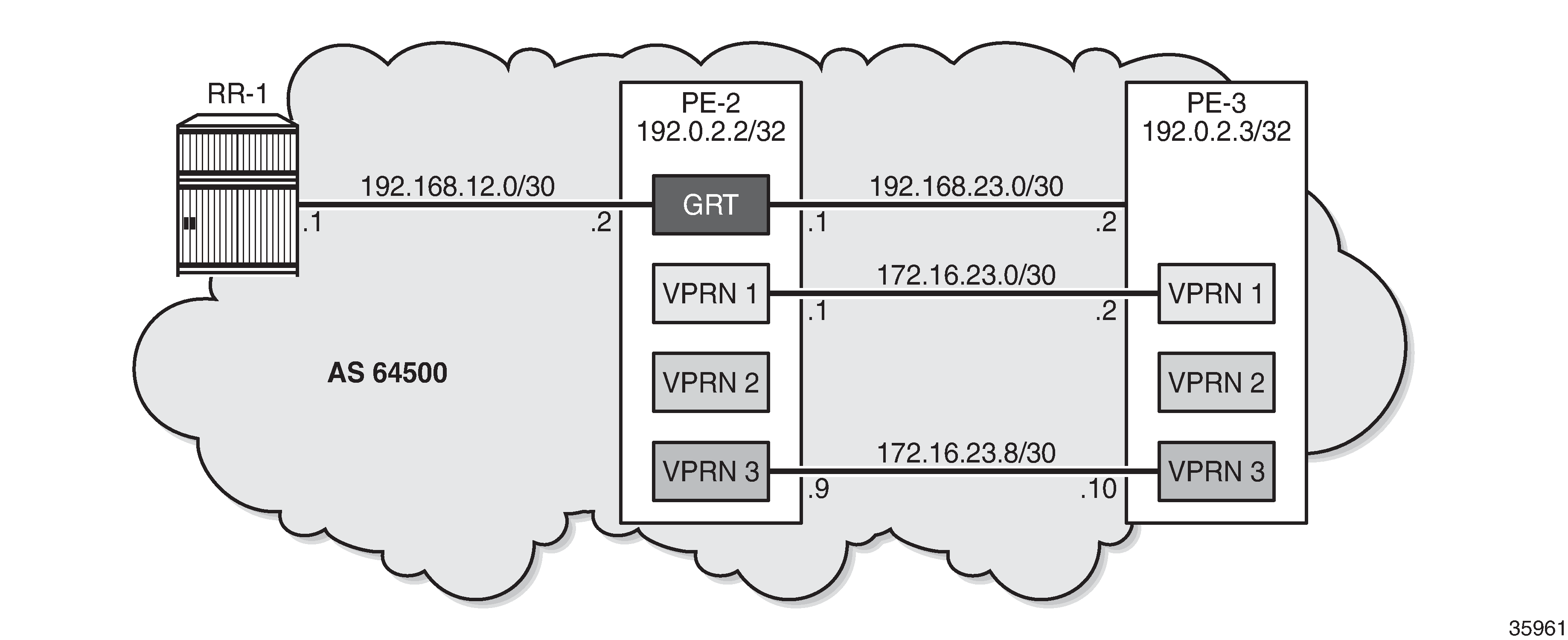
The initial configuration on the PEs includes the following:
Cards, MDAs, ports
Router interfaces
SR-ISIS
The initial configuration on PE-2 is as follows:
# on PE-2:
configure {
router "Base" {
autonomous-system 64500
interface "int-PE-2-PE-3" {
port 1/1/c1/1:100
ipv4 {
primary {
address 192.168.23.1
prefix-length 30
}
}
}
interface "int-PE-2-RR-1" {
port 1/1/c1/3:100
ipv4 {
primary {
address 192.168.12.2
prefix-length 30
}
}
}
interface "system" {
ipv4 {
primary {
address 192.0.2.2
prefix-length 32
}
}
}
mpls-labels {
sr-labels {
start 32000
end 32999
}
}
isis 0 {
admin-state enable
advertise-router-capability area
area-address [49.0001]
segment-routing {
admin-state enable
prefix-sid-range {
global
}
}
interface "int-PE-2-PE-3" {
interface-type point-to-point
}
interface "system" {
ipv4-node-sid {
index 2
}
}
}
}
}A BGP session is established between RR-1 and the base router on PE-2. The BGP configuration on PE-2 is as follows:
# on PE-2:
configure {
router "Base" {
bgp {
split-horizon true
group "iBGP" {
peer-as 64500
family {
ipv4 true
}
}
neighbor "192.168.12.1" {
group "iBGP"
}
}
}
}RR-1 advertises BGP routes with different communities for the different VPRNs on PE-2:
prefix 10.14.0.0/16 with community "target:64501:1" for VPRN 1
prefix 10.24.0.0/16 with community "target:64501:2" for VPRN 2
prefix 10.34.0.0/16 with community "target:64501:3" for VPRN 3
PE-2 receives the following BGP routes from RR-1:
[/]
A:admin@PE-2# show router bgp neighbor 192.168.12.1 received-routes
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
i 10.14.0.0/16 100 None
10.13.0.1 None 0
64501 -
i 10.24.0.0/16 100 None
10.23.0.1 None 0
No As-Path -
i 10.34.0.0/16 100 None
10.33.0.1 None 0
64503 -
-------------------------------------------------------------------------------
Routes : 3
===============================================================================
These routes are invalid in the base router because the next-hop is unresolved, as indicated by the flags in the BGP route details:
[/]
A:admin@PE-2# show router bgp routes hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved
Flags : Invalid IGP Nexthop-Unresolved
Flags : Invalid IGP Nexthop-Unresolved
On PE-2, the following import policy is created to make the prefixes leakable:
# on PE-2:
configure {
policy-options {
prefix-list "10.0.0.0/8" {
prefix 10.0.0.0/8 type longer {
}
}
policy-statement "leak-10.x" {
entry 10 {
from {
prefix-list ["10.0.0.0/8"]
}
action {
action-type accept
bgp-leak true
}
}
}
}
router "Base" {
bgp {
group "iBGP" {
peer-as 64500
family {
ipv4 true
}
}
neighbor "192.168.12.1" {
group "iBGP"
import {
policy ["leak-10.x"]
}
}
}
}
}The routes are now marked as leakable:
[/]
A:admin@PE-2# show router bgp routes hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved Leakable
Flags : Invalid IGP Nexthop-Unresolved Leakable
Flags : Invalid IGP Nexthop-Unresolved Leakable
[/]
A:admin@PE-2# show router bgp routes ipv4 leakable
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
i 10.14.0.0/16 100 None
10.13.0.1 None 0
64501 -
i 10.24.0.0/16 100 None
10.23.0.1 None 0
No As-Path -
i 10.34.0.0/16 100 None
10.33.0.1 None 0
64503 -
-------------------------------------------------------------------------------
Routes : 3
===============================================================================
Even though the routes are marked as leakable, these BGP routes with unresolved next-hop are only leaked from the base router to a VPRN context when the command allow-unresolved-leaking true is configured in the BGP next-hop-resolution context of the base router, as shown later in the examples.
The following use cases are shown:
BGP route 10.14.0.0/16 leaked to VPRN 1 with BGP next-hop resolved using IS-IS
BGP route 10.24.0.0/16 leaked to VPRN 2 with BGP next-hop resolved using VPN-IP
BGP route 10.34.0.0/16 leaked to VPRN 3 with BGP next-hop resolved using eBGP
Use case 1: BGP route leaked to VPRN 1 with next-hop resolved using IS-IS
Leaked route 10.14.0.0/16 with next-hop resolved in VPRN 1 using IS-IS shows that RR-1 advertises prefix 10.14.0.0/16 with next-hop 10.13.0.0/16, which is unresolvable in the base router of PE-2, but can be resolved in VPRN 1.
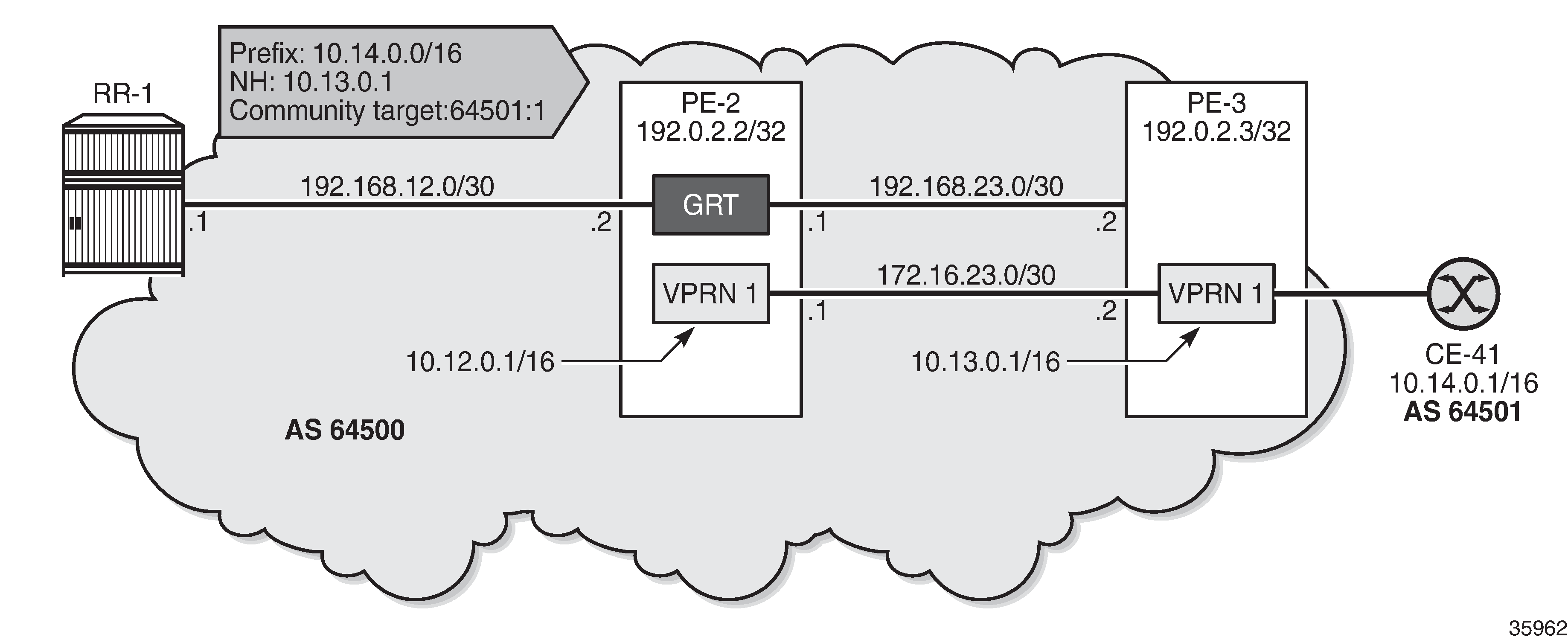
On PE-3, VPRN 1 has a loopback interface "lo1" configured with IP address 10.13.0.1/32. IS-IS on PE-3 is only enabled on the loopback interface and on the interface facing VPRN 1 on PE-2, not on the interface toward CE-41. VPRN 1 is configured as follows:
# on PE-3:
configure {
service {
vprn "VPRN 1" {
admin-state enable
service-id 1
customer "1"
autonomous-system 64500
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64500:1"
vrf-target {
community "target:64500:1"
}
}
}
interface "int-VPRN1-PE-3-PE-2" {
ipv4 {
primary {
address 172.16.23.2
prefix-length 30
}
}
sap 1/1/c1/2:1 {
}
}
interface "int-VPRN3-PE-3-CE-41" {
ipv4 {
primary {
address 172.16.34.1
prefix-length 30
}
}
sap 1/1/c1/1:1 {
}
}
interface "lo1" {
loopback true
ipv4 {
primary {
address 10.13.0.1
prefix-length 32
}
}
}
static-routes {
route 10.14.0.0/16 route-type unicast {
next-hop "172.16.34.2" {
admin-state enable
}
}
}
isis 0 {
admin-state enable
area-address [49.0001]
interface "int-VPRN1-PE-3-PE-2" {
interface-type point-to-point
}
interface "lo1" {
interface-type point-to-point
}
}
}
}
}On PE-2, the route table for VPRN 1 shows the following IS-IS route for prefix 10.13.0.1/32:
[/]
A:admin@PE-2# show router 1 route-table
===============================================================================
Route Table (Service: 1)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.12.0.1/32 Local Local 00h10m07s 0
lo1 0
10.13.0.1/32 Remote ISIS 00h09m34s 15
172.16.23.2 10
172.16.23.0/30 Local Local 00h10m07s 0
int-VPRN1-PE-2-PE-3 0
-------------------------------------------------------------------------------
No. of Routes: 3
---snip---
===============================================================================
PE-2 receives the following BGP route from RR-1 in the base routing instance with community "target 64500:1":
[/]
A:admin@PE-2# show router bgp routes community target:64500:1
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
i 10.14.0.0/16 100 None
10.13.0.1 None 0
64501 -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
This route is leakable:
[/]
A:admin@PE-2# show router bgp routes community target:64500:1 hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved LeakableOn PE-2, the following leak-import policy is configured in VPRN 1 to import the leakable routes with community "target:64500:1":
# on PE-2:
configure {
policy-options
community "target:64500:1" {
member "target:64500:1" { }
}
policy-statement "leak-import-1" {
entry 10 {
from {
community {
name "target:64500:1"
}
}
action {
action-type accept
}
}
default-action {
action-type reject
}
}
}
service {
vprn "VPRN 1" {
admin-state enable
service-id 1
customer "1"
autonomous-system 64500
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64500:1"
vrf-target {
community "target:64500:1"
}
}
}
bgp {
rib-management {
ipv4 {
leak-import {
policy ["leak-import-1"]
}
}
}
}
}
}
}By default, the base router does not leak unresolved routes, so the list of leaked BGP routes in VPRN 1 remains empty:
[/]
A:admin@PE-2# show router 1 bgp routes ipv4 leaked
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
No Matching Entries Found.
===============================================================================
The allow-unresolved-leaking true command in the BGP next-hop resolution context of the base router allows unresolved BGP routes to be leaked:
# on PE-2:
configure {
router "Base" {
bgp {
next-hop-resolution {
allow-unresolved-leaking true
}
}
}
}When routes with unresolved BGP next-hop in the base router are leaked, VPRN 1 receives the BGP route for prefix 10.14.0.0/16, and the next-hop can be resolved in the VPRN, so the leaked route is valid, best, and used:
[/]
A:admin@PE-2# show router 1 bgp routes ipv4 leaked
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
u*>li 10.14.0.0/16 100 None
10.13.0.1 (Base) None 10
64501 -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
The route table for VPRN 1 includes a BGP route for prefix 10.14.0.0/16 with next-hop 172.16.23.2:
[/]
A:admin@PE-2# show router 1 route-table
===============================================================================
Route Table (Service: 1)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.12.0.1/32 Local Local 00h16m47s 0
lo1 0
10.13.0.1/32 Remote ISIS 00h16m14s 15
172.16.23.2 10
10.14.0.0/16 Remote BGP 00h00m17s 170
172.16.23.2 10
172.16.23.0/30 Local Local 00h16m47s 0
int-VPRN1-PE-2-PE-3 0
-------------------------------------------------------------------------------
No. of Routes: 4
---snip---
===============================================================================
Use case 2: BGP route leaked to VPRN 2 with next-hop resolved using VPN-IP
Leaked route 10.24.0.0/16 with next-hop resolved in VPRN 2 using VPN-IP shows that RR-1 advertises prefix 10.24.0.0/16 with next-hop 10.23.0.1 while PE-3 advertises prefix 10.23.0.1/32 in a VPN-IP route to PE-2.
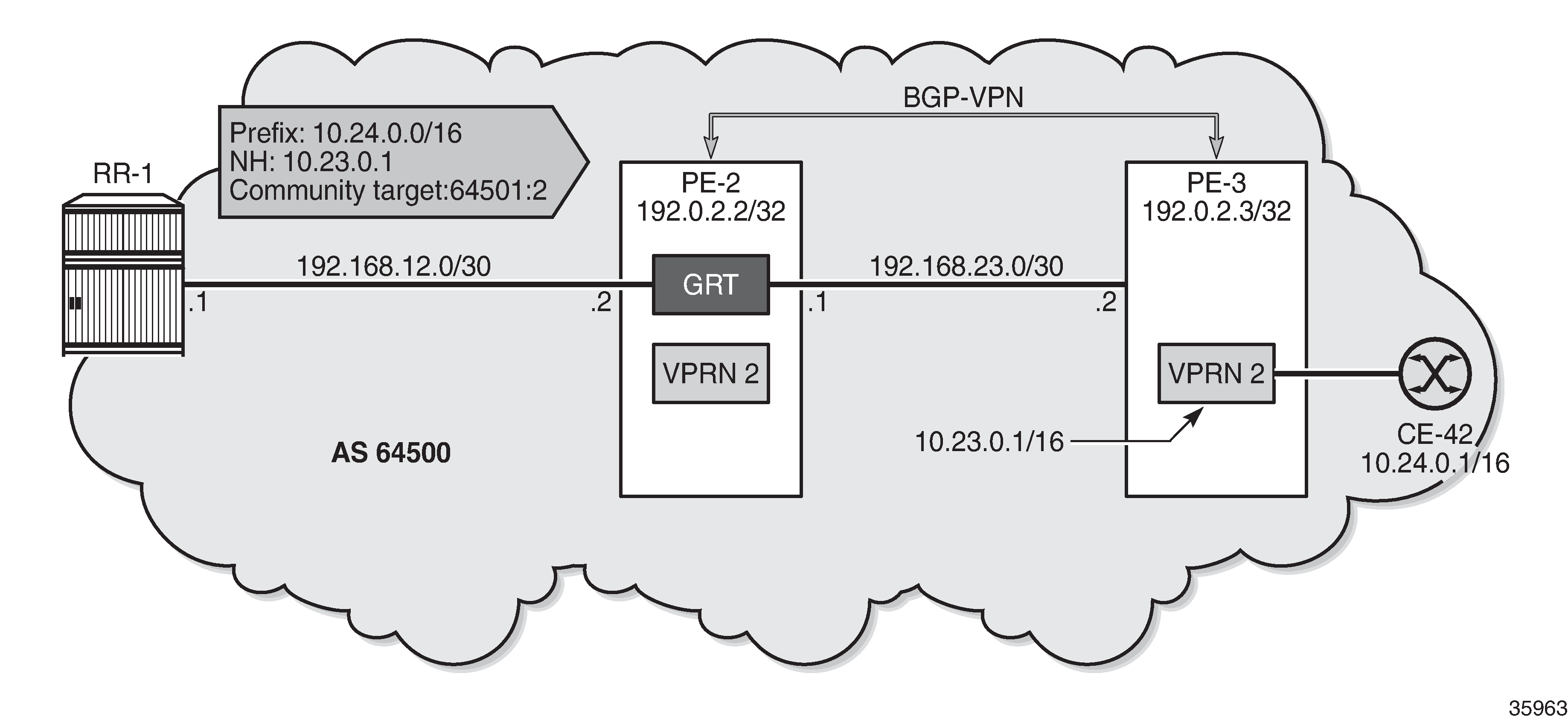
On PE-3, VPRN 2 has a loopback interface "lo1" configured with IP address 10.23.0.1/32, which is the BGP next-hop of the leakable route received from RR-1. VPRN 2 is configured with auto-bind-tunnel with resolution to SR-ISIS tunnels.
# on PE-3:
configure {
service {
vprn "VPRN 2" {
admin-state enable
service-id 2
customer "1"
autonomous-system 64500
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64500:2"
vrf-target {
community "target:64500:2"
}
auto-bind-tunnel {
resolution filter
resolution-filter {
sr-isis true
}
}
}
}
interface "lo1" {
loopback true
ipv4 {
primary {
address 10.23.0.1
prefix-length 32
}
}
}
}
}
}Prefix 10.23.0.1/32 is advertised in a VPN-IPv4 route to PE-2. On PE-3, the BGP configuration is as follows:
# on PE-3:
configure {
router "Base" {
bgp {
split-horizon true
group "iBGP-VPN" {
peer-as 64500
family {
vpn-ipv4 true
}
}
neighbor "192.0.2.2" {
group "iBGP-VPN"
}
}
}
}When the prefix 10.23.0.1/32 is advertised by PE-3, the route table for VPRN 2 on PE-2 is as follows:
[/]
A:admin@PE-2# show router 2 route-table
===============================================================================
Route Table (Service: 2)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.22.0.1/32 Local Local 00h19m19s 0
lo1 0
10.23.0.1/32 Remote BGP VPN 00h17m59s 170
192.0.2.3 (tunneled:SR-ISIS:524290) 10
-------------------------------------------------------------------------------
No. of Routes: 2
---snip---
===============================================================================
RR-1 advertises the following BGP route for prefix 10.24.0.0/16 with next-hop 10.23.0.1 and community "target:64500:2":
[/]
A:admin@PE-2# show router bgp routes community target:64500:2
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
i 10.24.0.0/16 100 None
10.23.0.1 None 0
No As-Path -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
This route is not resolved in BGP, as indicated by the flags:
[/]
A:admin@PE-2# show router bgp routes community target:64500:2 hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved LeakableThe route is leakable and, by configuration, routes with unresolved next-hop can be leaked. The following leak-import policy is configured on PE-2 to import routes with community "target:64500:2":
# on PE-2:
configure {
policy-options {
community "target:64500:2" {
member "target:64500:2" { }
}
policy-statement "leak-import-2" {
entry 10 {
from {
community {
name "target:64500:2"
}
}
action {
action-type accept
}
}
default-action {
action-type reject
}
}
}
service {
vprn "VPRN 2" {
admin-state enable
service-id 2
customer "1"
autonomous-system 64500
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64500:2"
vrf-target {
community "target:64500:2"
}
auto-bind-tunnel {
resolution filter
resolution-filter {
sr-isis true
}
}
}
}
bgp {
rib-management {
ipv4 {
leak-import {
policy ["leak-import-2"]
}
}
}
}
}
}
}The route is now leaked even though the next-hop is not only unresolved in the base router, but also unresolved in VPRN 2:
[/]
A:admin@PE-2# show router 2 bgp routes ipv4 leaked
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
li 10.24.0.0/16 100 None
10.23.0.1 (Base) None 0
No As-Path -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
[/]
A:admin@PE-2# show router 2 bgp routes hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved Leaked
By default, the BGP next-hop in the VPRN is resolved using IGP or static routes, but in this example, the route for 10.23.0.1/23 is resolved using the BGP VPN-IPv4 address family. Therefore, the BGP next-hop resolution context in VPRN 2 must be configured to allow the use of BGP routes:
# on PE-2:
configure {
service {
vprn "VPRN 2" {
admin-state enable
service-id 2
customer "1"
autonomous-system 64500
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64500:2"
vrf-target {
community "target:64500:2"
}
auto-bind-tunnel {
resolution filter
resolution-filter {
sr-isis true
}
}
}
}
bgp {
next-hop-resolution {
use-bgp-routes true # for BGP and BGP-VPN routes
}
rib-management {
ipv4 {
leak-import {
policy ["leak-import-2"]
}
}
}
}
}
}
}When the next-hop can be resolved using a VPN-IPv4 route, the leaked route becomes used, valid, and best in VPRN 2:
[/]
A:admin@PE-2# show router 2 bgp routes ipv4 leaked
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
u*>li 10.24.0.0/16 100 None
10.23.0.1 (Base) None 10
No As-Path -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
[/]
A:admin@PE-2# show router 2 bgp routes hunt | match Flags
Flags : Used Valid Best IGP Leaked In-RTM
The route table for VPRN 2 on PE-2 now includes a BGP route for prefix 10.24.0.0/16:
[/]
A:admin@PE-2# show router 2 route-table
===============================================================================
Route Table (Service: 2)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.22.0.1/32 Local Local 00h25m07s 0
lo1 0
10.23.0.1/32 Remote BGP VPN 00h23m46s 170
192.0.2.3 (tunneled:SR-ISIS:524290) 10
10.24.0.0/16 Remote BGP 00h00m22s 170
192.0.2.3 (tunneled:SR-ISIS:524290) 10
-------------------------------------------------------------------------------
No. of Routes: 3
---snip---
===============================================================================
Use case 3: BGP route leaked to VPRN 3 with next-hop resolved using eBGP
Leaked route 10.34.0.0/16 with next-hop resolved in VPRN 2 using eBGP shows that RR-1 advertises prefix 10.34.0.0/16 with next-hop 10.33.0.1. A BGP session is established within VPRN 3 on PE-2 and PE-3.
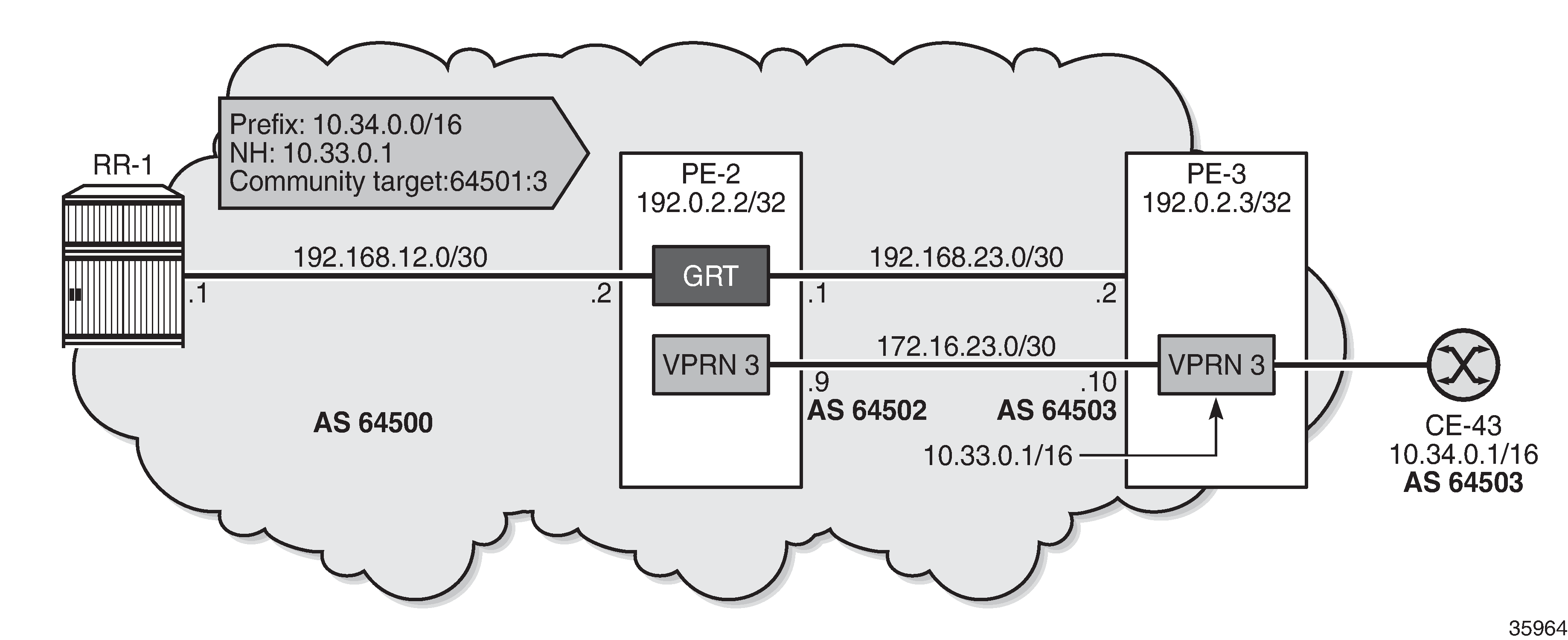
On PE-3, VPRN 3 has a loopback Interface "lo1" configured with IP address 10.33.0.1/32, which is the BGP next-hop of the leakable route received from RR-1. Prefix 10.33.0.0/16 is advertised by BGP in VPRN 3.
# on PE-3:
configure {
policy-options {
prefix-list "10.33.0.0/16" {
prefix 10.33.0.0/16 type longer {
}
}
policy-statement "export_10.33" {
entry 10 {
from {
prefix-list ["10.33.0.0/16"]
}
to {
protocol {
name [bgp]
}
}
action {
action-type accept
}
}
}
}
service {
vprn "VPRN 3" {
admin-state enable
service-id 3
customer "1"
autonomous-system 64503
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64503:3"
vrf-target {
community "target:64500:3"
}
}
}
bgp {
router-id 10.33.0.1
split-horizon true
group "eBGP" {
peer-as 64502
}
neighbor "172.16.23.9" {
group "eBGP"
export {
policy ["export_10.33"]
}
}
}
interface "int-VPRN3-PE-3-CE-43" {
ipv4 {
primary {
address 172.16.34.9
prefix-length 30
}
}
sap 1/1/c1/1:3 {
}
}
interface "int-VPRN3-PE-3-PE-2" {
ipv4 {
primary {
address 172.16.23.10
prefix-length 30
}
}
sap 1/1/c1/2:3 {
}
}
interface "lo1" {
loopback true
ipv4 {
primary {
address 10.33.0.1
prefix-length 32
}
}
}
static-routes {
route 10.34.0.0/16 route-type unicast {
next-hop "172.16.34.10" {
admin-state enable
}
}
}
}
}
}The route table for VPRN 3 on PE-2 contains the loopback address from VPRN 3 on PE-3:
[/]
A:admin@PE-2# show router 3 route-table
===============================================================================
Route Table (Service: 3)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.32.0.1/32 Local Local 00h26m59s 0
lo1 0
10.33.0.1/32 Remote BGP 00h25m56s 170
172.16.23.10 0
172.16.23.8/30 Local Local 00h26m59s 0
int-VPRN3-PE-2-PE-3 0
-------------------------------------------------------------------------------
No. of Routes: 3
---snip---
===============================================================================
PE-2 receives the following BGP route with community "target:64500:3" from RR-1:
[/]
A:admin@PE-2# show router bgp routes community target:64500:3
===============================================================================
BGP Router ID:192.0.2.2 AS:64500 Local AS:64500
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
i 10.34.0.0/16 100 None
10.33.0.1 None 0
64503 -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
This route is leakable, but the next-hop 10.33.0.1 cannot be resolved in the base router of PE-2:
[/]
A:admin@PE-2# show router bgp routes community target:64500:3 hunt | match Flags
Flags : Invalid IGP Nexthop-Unresolved LeakableThe only BGP route used in VPRN 3 on PE-2 is for prefix 10.33.0.1/32:
[/]
A:admin@PE-2# show router 3 bgp routes
===============================================================================
BGP Router ID:10.32.0.1 AS:64502 Local AS:64502
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
u*>i 10.33.0.1/32 None None
172.16.23.10 None 0
64503 -
-------------------------------------------------------------------------------
Routes : 1
===============================================================================
The following leak-import policy is configured on PE-2 to import leakable BGP routes with community "64500:3":
# on PE-2:
configure {
policy-options {
community "target:64500:3" {
member "target:64500:3" { }
}
policy-statement "leak-import-3" {
entry 10 {
from {
community {
name "target:64500:3"
}
}
action {
action-type accept
}
}
default-action {
action-type reject
}
}
}
}This leak-import policy is applied in VPRN 3 and the BGP next-hop-resolution is configured as use-bgp-routes true:
# on PE-2:
configure {
service {
vprn "VPRN 3" {
admin-state enable
service-id 3
customer "1"
autonomous-system 64502
bgp-ipvpn {
mpls {
admin-state enable
route-distinguisher "64502:3"
vrf-target {
community "target:64500:3"
}
}
}
bgp {
next-hop-resolution {
use-bgp-routes true # for BGP and BGP-VPN routes
}
rib-management {
ipv4 {
leak-import {
policy ["leak-import-3"]
}
}
}
}
}
}
}With this configuration, the received RR-1 route for prefix 10.34.0.0/16 is leaked to VPRN 3 and the next-hop is resolved using a BGP route. The BGP routes in VPRN 3 on PE-2 are the following:
[/]
A:admin@PE-2# show router 3 bgp routes
===============================================================================
BGP Router ID:10.32.0.1 AS:64502 Local AS:64502
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
u*>i 10.33.0.1/32 None None
172.16.23.10 None 0
64503 -
u*>li 10.34.0.0/16 100 None
10.33.0.1 (Base) None 0
64503 -
-------------------------------------------------------------------------------
Routes : 2
===============================================================================
The route table for VPRN 3 on PE-2 now includes a route for prefix 10.34.0.0/16:
[/]
A:admin@PE-2# show router 3 route-table
===============================================================================
Route Table (Service: 3)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.32.0.1/32 Local Local 00h32m42s 0
lo1 0
10.33.0.1/32 Remote BGP 00h31m38s 170
172.16.23.10 0
10.34.0.0/16 Remote BGP 00h00m09s 170
172.16.23.10 0
172.16.23.8/30 Local Local 00h32m42s 0
int-VPRN3-PE-2-PE-3 0
-------------------------------------------------------------------------------
No. of Routes: 4
---snip---
===============================================================================
Conclusion
BGP routes can be leaked from the base router to a VPRN routing instance, even when the next-hop is unresolved in the base router. This feature reduces the number of BGP sessions toward an RR, because all VPRN-related routes can now be leaked from the base router using a single BGP session. The VPRNs distinguish the routes based on the community value.