Figure 377 depicts the complete PPP session setup, using RADIUS authentication on both LAC and LNS. After the discovery phase (PADI/PADO/PADR/PADS) and LCP negotiation phase (LCP config_request/Ack), the LAC initiates the L2TP tunnel setup based on Radius authentication information (Radius Request/Accept) and includes the negotiated PPP user-LAC information (called LCP proxy information). The LNS replies directly with a successful CHAP authentication if it agrees with the received proxy information. IP negotiation (IPCP config_request/Ack) is further handled between the user and the LNS and therefore the LAC has no IP knowledge of this PPP session.
Figure 378 shows the scenario were the LNS does not agree with the received LCP proxy information and (re)starts the LCP phase (LCP config_request/Ack) directly with the PPP user. The rest of this scenario is the same as shown in
Figure 377.
Figure 379 shows multiple PPP sessions tunneled over a single L2TP Tunnel. The LAC encapsulates each PPP session with a different L2TP session-id (SID) but with the same L2TP Tunnel-id (TID).
Figure 380 shows the user initiated terminate_request tunneled by the LAC followed by the user initiated PADT terminated on the LAC. The LAC informs the LNS about the termination of the session via the L2TP CDN message. The L2TP tunnel can be optionally (idle-timeout) terminated via the L2TP StopCCN message.
Figure 381 gives an overview of the main L2TP tunnel and session states. An L2TP tunnel in the establishedIdle state is a tunnel without sessions. A
tools command (see
Advanced Topics ) can put an L2TP tunnel in a draining state (this prevents adding new sessions on tunnel but the leaves the current sessions intact) or in a drained state (moved from draining to drained when all sessions terminated). The draining and drained state are not shown in the state diagram.
The L2TP tunnel setup occurs first with the triggers being: session activation, auto-establish and a tools start command (see the advanced section). An L2TP session setup trigger is always session based.
configure service ies 1
subscriber-interface "sub-lt2p"
unnumbered "system"
group-interface "grp-l2tp"
authentication-policy "authentication-1" #Radius authentication
sap 1/1/2:100.1
sub-sla-mgmt
sub-ident-policy "sub-ident-1"
no shutdown
exit
exit
pppoe
no shutdown
exit
exit
exit
service-name "L2TP"
no shutdown
user1@wholesale.com Cleartext-Password := "ALU" ,NAS-Identifier == "pe1"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-func1",
Alc-SLA-Prof-Str = "sla-func1",
# Tunnel 1 related (tag 1) #Tunnel 1
Tunnel-Type:1 += L2TP, #
Tunnel-Medium-Type:1 += IP, #
Tunnel-Server-Endpoint:1 += 192.168.2.6, #LNS peer address
configure router l2tp
calling-number-format "%S %s" # L2TP AVP 22 format
# Default format ‘system-name sap-id’
<snip>
no local-name # default name equals system-name
no max-retries-estab # default value equals 5
<snip>
no shutdown # enable L2TP
user1@wholesale.com Cleartext-Password := "ALU" ,NAS-Identifier == "pe1"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-func1",
Alc-SLA-Prof-Str = "sla-func1",
# group related (tag 0)parameters applicable for all tunnels
Tunnel-Client-Endpoint:0 = 192.168.2.2, #LAC L2TP source IP
Alc-Tunnel-Algorithm:0 = weighted-access, #tunnel selection
Tunnel-Assignment-Id:0 = "l2tp-functional-radius", #L2TP group name
Tunnel-Client-Auth-Id:0 = "lac-pe1", #LAC name
Alc-Tunnel-Max-Retries-Estab:0 = 2,
#
# Tunnel 1 related (tag 1) #Tunnel 1
Tunnel-Type:1 += L2TP, #
Tunnel-Medium-Type:1 += IP, #
Tunnel-Server-Endpoint:1 += 192.168.2.6, # LNS peer address
Tunnel-Assignment-Id:1 += "LNS1-T1", # tunnel name
Tunnel-Preference:1 += 100, # preference 100
#
# Tunnel 2 related (tag 2) #Tunnel 2
Tunnel-Type:2 += L2TP,
Tunnel-Medium-Type:2 += IP,
Tunnel-Server-Endpoint:2 += 192.168.2.7,
Tunnel-Assignment-Id:2 += "LNS2-T2",
Tunnel-Preference:2 += 100,
#
# Tunnel 3 related (tag 3) #Tunnel 3
Tunnel-Type:3 += L2TP,
Tunnel-Medium-Type:3 += IP,
Tunnel-Server-Endpoint:3 += 192.168.2.8,
Tunnel-Assignment-Id:3 += "LNS3-T3",
Tunnel-Preference:3 += 120,
#
# Tunnel 4 related (tag 4) #Tunnel 4
Tunnel-Type:4 += L2TP,
Tunnel-Medium-Type:4 += IP,
Tunnel-Server-Endpoint:4 += 192.168.2.9,
Tunnel-Assignment-Id:4 += "LNS4-T4",
Tunnel-Preference:4 += 140,
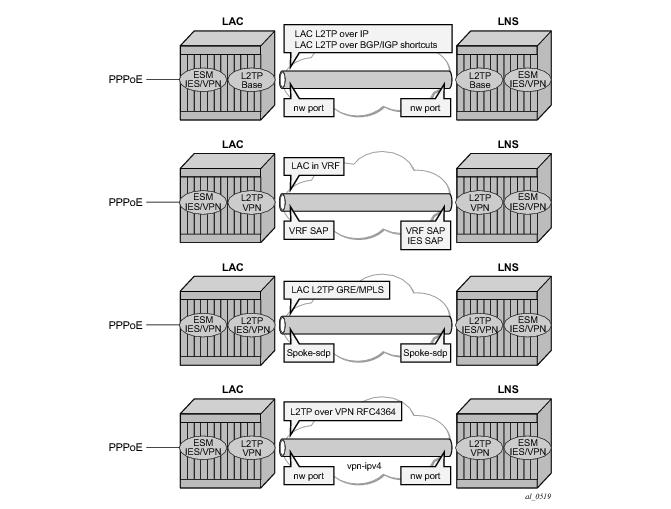
Figure 384 shows the PPPoE session termination (base IES service 1) and the L2TP tunnel setup in a different router instance (VPRN 65536).
user1@wholesale.com Cleartext-Password := "ALU" ,NAS-Identifier == "pe1"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-func1",
Alc-SLA-Prof-Str = "sla-func1",
Alc-Tunnel-Serv-Id = 65536, #L2TP starts in VRF 65536
Tunnel-Assignment-Id:0 = "l2tp-functional-radius",
Tunnel-Client-Auth-Id:0 = "lac-pe1",
Tunnel-Type:1 += L2TP,
Tunnel-Medium-Type:1 += IP,
Tunnel-Server-Endpoint:1 += 192.168.2.6,
Tunnel-Assignment-Id:1 += "LNS1-T1",
configure service vprn 65536
<snip>
interface "system" #source IP for tunnel
address 192.168.2.2/32
loopback
exit
l2tp
no shutdown
exit
user1@wholesale.com Cleartext-Password := "ALU" ,NAS-Identifier == "pe1"
Alc-Subsc-ID-Str = "%{User-name}",
Alc-Subsc-Prof-Str = "sub-func1",
Alc-SLA-Prof-Str = "sla-func1",
Alc-Tunnel-Serv-Id = 65536, #LAC in VRF
Alc-Tunnel-Group = wholesale.com, #points to L2TP node group name
configure service vprn 65536
<snip>
interface "system" #interface with name system is
address 192.168.2.2/32 #used as LAC L2TP source ip-address
loopback
exit
l2tp
group "wholesale.com" #corresponds with Alc-Tunnel-Group
tunnel "wholesale.com"
local-address 192.168.2.2 #optional since system itf exists
local-name "lac-pe1"
peer 192.168.2.6
no auto-establish #use session-trigger iso auto-establish
no shutdown
exit
no shutdown
exit
no shutdown
exit
An L2TP tunnel is set up by either a PPP session-trigger, a tools command or by the l2tp group tunnel auto-establish parameter configuration. See the advanced section below for the non-session-triggered tunnel setup.
configure service ies 1
subscriber-interface "sub-lt2p"
unnumbered "system"
group-interface "grp-l2tp"
sap 1/1/2:100.1
sub-sla-mgmt
sub-ident-policy "sub-ident-1"
no shutdown
exit
exit
pppoe
no shutdown
user-db "l2tp"
exit
exit
exit
service-name "L2TP"
no shutdown
The referenced local user database l2tp configuration provides all of the required L2TP and ESM information.
configure subscriber-mgmt local-user-db "l2tp"
ppp
match-list username
host "wholesale.com" create
host-identification
username "wholesale.com" domain-only
exit
password ignore
identification-strings 254 create
subscriber-id "user1@wholesale.com"
sla-profile-string "sla-func1"
sub-profile-string "sub-func1"
exit
l2tp
group "wholesale.com" service-id 65536 #points to L2TP group
exit #name and LAC in VRF
no shutdown
exit
exit
# useful show commands
show service id <service-id> ppp session [detail]
show router l2tp tunnel [detail]
show router l2tp session [detail]
show router l2tp peer [ip-address]
# debug to show PPPoE packet interaction
debug service id <service-id> ppp packet mode egr-ingr-and-dropped
debug service id <service-id> ppp packet detail-level medium
# debug to show RADIUS authentication interaction
debug router radius packet-type authentication
#debug to show LUDB authentication interaction
debug subscriber-mgmt local-user-db <local-user-db-name> detail all
# debug to show LAC Tunnel selection process and L2TP state-machine
debug router l2tp event lac-session-setup
debug router l2tp event finite-state-machine
# debug to show L2TP Tunnel and session setup
debug router l2tp packet direction both
debug router l2tp packet detail-level high
The L2TP ICRQ message extract shown below (debug router l2tp packet) is used to explain how the displayed debug output should be interpreted. See
Recap of the L2TPv2 Protocol -
L2TP Header and AVP Layout for more details.
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 1240 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
<snip>
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"pe1 1/1/2:100.1"
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0"
<snip>
The ‘debug service id <service-id> ppp packet mode egr-ingr-and-dropped command shows PPPoE packet interaction. Below is a snapshot from the PADI packet showing the service, SAP and received PPPoE Tags. The received PPPoE DSL forum tags are by default copied during the LAC L2TP tunnel setup into the Incoming Call Request (ICRQ) DSL Forum AVP’s (RFC 5515).
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE
"PPPoE: RX Packet
IES 1, SAP 1/1/2:100.1
DMAC: ff:ff:ff:ff:ff:ff
SMAC: 00:00:00:01:01:01
Ether Type: 0x8863 (Discovery)
PPPoE Header:
Version: 1 Type : 1
Code : 0x09 (PADI) Session-Id: 0x0000 (0)
Length : 58
PPPoE Tags:
[0x0101] Service-Name: "AGILENT"
[0x0103] Host-Uniq: len = 4, value = 00 0f 00 00
[0x0105] Vendor-Specific: vendor-id = 0x0de9 (ADSL Forum)
[0x01] Agent-Circuit-Id: "circuit0" #copied in ICRQ DSL forum AVP’s
[0x02] Agent-Remote-Id: "remote0" #copied in ICRQ DSL forum AVP’s
[0x81] Actual-Upstream: 2000 #copied in ICRQ DSL forum AVP’s
[0x82] Actual-Downstream: 4000" #copied in ICRQ DSL forum AVP’s
The debug router radius packet-type authentication command shows the actual authentication parameters returned by RADIUS. This example returns the minimum set of L2TP related RADIUS attributes.
<date> <time> CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 165 len 103 from 172.16.1.1:1812 vrid 1 pol subscr-mgmt
VSA [26] 21 Alcatel(6527)
SUBSC ID STR [11] 19 user1@wholesale.com
VSA [26] 11 Alcatel(6527)
SUBSC PROF STR [12] 9 sub-func1
VSA [26] 11 Alcatel(6527)
SLA PROF STR [13] 9 sla-func1
TUNNEL TYPE [64] 4 1 L2TP(3) # L2TP
TUNNEL MEDIUM TYPE [65] 4 1 IPv4(1) # IPv4
TUNNEL SERVER ENDPOINT [67] 8 1 192.168.2.6 # L2TP peer LNS address
"
The debug router l2tp event lac-session-setup command shows the LAC tunnel selection for this example. An L2TP group-name ‘default_radius_group’ with tunnel-name ‘unnamed’ is created in this case.
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE 29->L2TP
"PPPoE 29->L2TP: UDP 0.0.0.0:1701 -> 192.168.2.6:1701
pref 50 tunnel default_radius_group:unnamed #group-name=default_radius_group
request to open new tunnel 3288" #tunnel-name=unnamed
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE 29->L2TP
"PPPoE 29->L2TP: UDP 0.0.0.0:1701 -> 192.168.2.6:1701
pref 50 tunnel default_radius_group:unnamed
create session 215482368"
The ‘debug router l2tp packet detail-level’ command shows the L2TP tunnel and session setup for this example.
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 0 session 0, ns 0 nr 0, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionRequest(1) #SCCRQ
AVP ProtocolVersion(0,2), flags: mandatory, reserved=0
version=1, revision=0
AVP HostName(0,7), flags: mandatory, reserved=0 #default=system-name
"pe1"
AVP WindowSize(0,10), flags: mandatory, reserved=0
64 #default=64
AVP FramingCapabilities(0,3), flags: mandatory, reserved=0
sync=no, async=no
AVP BearerCapabilities(0,4), flags: mandatory, reserved=0
digital=yes, analogue=no
AVP FirmwareRevision(0,6), flags:, reserved=0
2816
AVP VendorName(0,8), flags:, reserved=0
"Alcatel-Lucent"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0 #LAC Tunnel-id
3288"
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, ingress)
"L2TP(v2,ctrl,ingress): UDP 192.168.2.6:1701 -> 192.0.2.2:1701 #LNS TO LAC
tunnel 3288 session 0, ns 0 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionReply(2) #SCCRP
AVP ProtocolVersion(0,2), flags: mandatory, reserved=0
version=1, revision=0
AVP HostName(0,7), flags: mandatory, reserved=0
"pe3"
AVP WindowSize(0,10), flags: mandatory, reserved=0
64
AVP FramingCapabilities(0,3), flags: mandatory, reserved=0
sync=no, async=no
AVP BearerCapabilities(0,4), flags: mandatory, reserved=0
digital=yes, analogue=no
AVP FirmwareRevision(0,6), flags:, reserved=0
2816
AVP VendorName(0,8), flags:, reserved=0
"Alcatel-Lucent"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0 #LNS Tunnel-id
1240"
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701 #LAC TO LNS
tunnel 1240 session 0, ns 1 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StartControlConnectionConnected(3)" #SCCN
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701 #LAC TO LNS
tunnel 1240 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10) #ICRQ
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
256
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
31
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"pe1 1/1/2:100.1" #calling-number-format ‘%S %s’
AVP AgentCircuitId(3561,1), flags:, reserved=0
"circuit0" #copy from PADI by default
AVP AgentRemoteId(3561,2), flags:, reserved=0
"remote0" #copy from PADI by default
AVP ActDataRateUp(3561,129), flags:, reserved=0
2000000 #copy from PADI by default
AVP ActDataRateDown(3561,130), flags:, reserved=0
4000000" #copy from PADI by default
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, ingress)
"L2TP(v2,ctrl,ingress): UDP 192.168.2.6:1701 -> 192.0.2.2:1701 #LNS TO LAC
tunnel 3288 session 256, ns 1 nr 3, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallReply(11) #ICRP
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
31234"
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701 #LAC TO LNS
tunnel 1240 session 31234, ns 3 nr 2, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallConnected(12) #ICCN
AVP FramingType(0,19), flags: mandatory, reserved=0
sync=no, async=no
AVP TxConnectSpeed(0,24), flags: mandatory, reserved=0
4000000 #report-rate: More on this in the Advanced section
AVP InitialRxLcpConfReq(0,26), flags:, reserved=0 #copy from the PPP users
05 06 19 cc 71 18 01 04 ff fb #first LCP-conf-request
[5] Magic-Number: 0x19cc7118
[1] MRU: 1500
AVP LastTxLcpConfReq(0,27), flags:, reserved=0
01 04 05 d4 03 05 c2 23 05 05 06 0f 4d f8 18
[1] MRU: 1492
[3] Authentication-Protocol: 0xc223 (CHAP), Algorithm = 5 (MD5)
[5] Magic-Number: 0x0f4df818
AVP LastRxLcpConfReq(0,28), flags:, reserved=0 #copy from the PPP users
05 06 19 cc 71 18 01 04 ff fb #last LCP-conf-request
[5] Magic-Number: 0x19cc7118
[1] MRU: 1500
AVP ProxyAuthenType(0,29), flags:, reserved=0 #user-LAC negotiated
chap(2) #authentication type
AVP ProxyAuthenName(0,30), flags:, reserved=0
"user1@wholesale.com"
AVP ProxyAuthenChallenge(0,31), flags:, reserved=0
92 59 c2 53 04 72 06 8f a8 87 cc c6 7d 09 8e d0
95 43 16 33 70 7e 65 86 d3 c4 16 94 1e 54 e5 30
2e 28 04 b1 9b 0a c1 c3 12 8e 8b 8f 18 99 e0 ad
5d
AVP ProxyAuthenId(0,32), flags:, reserved=0
id=1, reserved=0
AVP ProxyAuthenResponse(0,33), flags:, reserved=0
50 cb bd 10 3c 7c ec 47 0b 04 0d 7d 49 c2 7f bd
AVP RxConnectSpeed(0,38), flags:, reserved=0
2000000" #report-rate. More on this
#in the Advanced section
show service id 1 ppp session
==============================================================================
PPP sessions for service 1
==============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id
------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/2:100.1 mac:00:00:00:01:01:01 sid:1
0d 00:00:14 oE lac 215482624 #L2TP session-id
------------------------------------------------------------------------------
No. of PPP sessions: 1
show router l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
215482368 3288 1240 established not-blacklisted 1
default_radius_group 1
unnamed
------------------------------------------------------------------------------
No. of tunnels: 1
show router l2tp tunnel detail
==============================================================================
L2TP Tunnel Status
==============================================================================
Connection ID: 215482368
State : established
IP : 192.0.2.2
UDP : 1701
Peer IP : 192.168.2.6
Peer UDP : 1701
Tx dst-IP : 192.168.2.6
Tx dst-UDP : 1701
Rx src-IP : 192.168.2.6
Rx src-UDP : 1701
Name : pe1
Remote Name : pe3
Assignment ID: unnamed
Group Name : default_radius_group
Acct. Policy : N/A
Error Message: N/A
Remote Conn ID : 81264640
Tunnel ID : 3288 Remote Tunnel ID : 1240
Preference : 50 Receive Window : 64
Hello Interval (s): 300
Idle TO (s) : infinite Destruct TO (s) : 60
Max Retr Estab : 5 Max Retr Not Estab: 5
Session Limit : 32767 AVP Hiding : never
Transport Type : udpIp Challenge : never
Time Started : 10/04/2013 15:37:10 Time Idle : N/A
Time Established : 10/04/2013 15:37:10 Time Closed : N/A
Stop CCN Result : noError General Error : noError
Blacklist-state : not-blacklisted
show router l2tp session
==============================================================================
L2TP Session Summary
==============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
------------------------------------------------------------------------------
215482624 215482368 3288 256 established
------------------------------------------------------------------------------
No. of sessions: 1
show router l2tp session detail
==============================================================================
L2TP Session 215482624
==============================================================================
Connection ID: 215482624
State : established
Tunnel Group : default_radius_group
Assignment ID: unnamed
Error Message: N/A
Control Conn ID : 215482368 Remote Conn ID : 81295874
Tunnel ID : 3288 Remote Tunnel ID : 1240
Session ID : 256 Remote Session ID : 31234
Time Started : 10/04/2013 15:37:10
Time Established : 10/04/2013 15:37:10 Time Closed : N/A
CDN Result : noError General Error : noError
------------------------------------------------------------------------------
No. of sessions:
The debug router radius packet-type authentication command shows the actual RADIUS authentication parameters returned. This example returns multiple tunnel endpoints from which the LAC selects one. This example uses weighted load balancing. (The L2TP tunnel selection process is out of the scope of this example).
<date> <time> CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 190 len 299 from 172.16.1.1:1812 vrid 1 pol subscr-mgmt
VSA [26] 21 Alcatel(6527)
SUBSC ID STR [11] 19 user1@wholesale.com
VSA [26] 11 Alcatel(6527)
SUBSC PROF STR [12] 9 sub-func1
VSA [26] 11 Alcatel(6527)
SLA PROF STR [13] 9 sla-func1
#
TUNNEL CLIENT ENDPOINT [66] 7 192.168.2.2
VSA [26] 6 Alcatel(6527)
TUNNEL ALGORITHM [47] 4 weighted access(1) #input for tunnel selection
TUNNEL ASSIGNMENT ID [82] 22 l2tp-functional-radius
TUNNEL CLIENT AUTH ID [90] 7 lac-pe1
VSA [26] 6 Alcatel(6527)
TUNNEL MAX RETRIES ESTAB [52] 4 0 2
#
TUNNEL TYPE [64] 4 1 L2TP(3) #Tunnel 1
TUNNEL MEDIUM TYPE [65] 4 1 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 8 1 192.168.2.6
TUNNEL ASSIGNMENT ID [82] 8 1 LNS1-T1
TUNNEL PREFERENCE [83] 4 1 100 #input for tunnel selection
#
TUNNEL TYPE [64] 4 2 L2TP(3) #Tunnel 2
TUNNEL MEDIUM TYPE [65] 4 2 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 8 2 192.168.2.7
TUNNEL ASSIGNMENT ID [82] 8 2 LNS2-T2
TUNNEL PREFERENCE [83] 4 2 100 #input for tunnel selection
#
TUNNEL TYPE [64] 4 3 L2TP(3) #Tunnel 3
TUNNEL MEDIUM TYPE [65] 4 3 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 8 3 192.168.2.8
TUNNEL ASSIGNMENT ID [82] 8 3 LNS3-T3
TUNNEL PREFERENCE [83] 4 3 120 #input for tunnel selection
#
TUNNEL TYPE [64] 4 4 L2TP(3) #Tunnel 4
TUNNEL MEDIUM TYPE [65] 4 4 IPv4(1)
TUNNEL SERVER ENDPOINT [67] 8 4 192.168.2.9
TUNNEL ASSIGNMENT ID [82] 8 4 LNS4-T4
TUNNEL PREFERENCE [83] 4 4 140
The debug router l2tp event lac-session-setup command shows the LAC tunnel LNS1-T1 is selected for this example.
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE 15->L2TP
"PPPoE 15->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.6:1701 #end 192.168.2.6
preference 100 tunnel l2tp-functional-radius:LNS1-T1 #preference 100
request to open new tunnel 11212"
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE 15->L2TP
"PPPoE 15->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.7:1701 #end 192.168.2.7
preference 100 tunnel l2tp-functional-radius:LNS2-T2 #preference 100
skipped as another tunnel was selected"
<date> <time> CEST MINOR: DEBUG #2001 Base PPPoE 15->L2TP
"PPPoE 15->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.6:1701
preference 100 tunnel l2tp-functional-radius:LNS1-T1 #selects 192.168.2.6
create session 734820645"
show service id 1 ppp session
==============================================================================
PPP sessions for service 1
==============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id
------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/2:100.1 mac:00:00:00:01:01:01 sid:1
0d 00:00:20 oE lac 734820645
------------------------------------------------------------------------------
No. of PPP sessions: 1
show router l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
734789632 11212 13723 established not-blacklisted 1
l2tp-functional-radius 1
LNS1-T1
------------------------------------------------------------------------------
No. of tunnels: 1
show router l2tp session
==============================================================================
L2TP Session Summary
==============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
------------------------------------------------------------------------------
734820645 734789632 11212 31013 established
------------------------------------------------------------------------------
No. of sessions: 1
show router l2tp peer
======================================================
L2TP Peers
======================================================
Peer IP Port Tun Active Ses Active
Drain Reachability Tun Total Ses Total
------------------------------------------------------
192.168.2.6 1701 1 1 #LNS endpoint 192.168.2.6
1 1
192.168.2.7 1701 0 0
0 0
192.168.2.8 1701 0 0
0 0
192.168.2.9 1701 0 0
0 0
------------------------------------------------------
No. of peers: 4
show subscriber-mgmt statistics session system
=======================================================================
Subscriber Management Statistics for System
=======================================================================
Type Current Peak Peak Timestamp
-----------------------------------------------------------------------
Session Statistics
-----------------------------------------------------------------------
Local PPP Sessions - PPPoE 0 1 11/13/2013 17:04:23
PPP Sessions - PPPoEoA 0 0
PPP Sessions - PPPoA 0 0
PPP Sessions - L2TP (LNS) 0 0
-----------------------------------------------------------------------
LAC PPP Sessions - PPPoE 1 1 11/19/2013 15:46:40
PPP Sessions - PPPoEoA 0 0
PPP Sessions - PPPoA 0 0
PPP Sessions - L2TP (LTS) 0 0
-----------------------------------------------------------------------
Total PPP Sessions - established 1 2 11/19/2013 15:46:40
PPP Sessions - in setup 0 1 11/19/2013 15:46:39
PPP Sessions - local 0 1 11/13/2013 17:04:23
PPP Sessions - LAC 1 1 11/19/2013 15:46:40
-----------------------------------------------------------------------
-----------------------------------------------------------------------
L2TP L2TP Tunnels - originator 1 2 11/19/2013 15:40:13
L2TP Tunnels - receiver 0 0
Total L2TP Tunnels 1 2 11/19/2013 15:40:13
-----------------------------------------------------------------------
=======================================================================
Peak values last reset at : n/a
show router 65536 route-table
==============================================================================
Route Table (Service: 65536)
==============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
------------------------------------------------------------------------------
<snip>
192.168.2.2/32 Local Local 11h10m45s 0
system 0
192.168.2.6/32 Remote BGP VPN 11h10m12s 170
192.0.2.6 (tunneled) 0
show service id 1 ppp session
==============================================================================
PPP sessions for service 1
==============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id
------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/2:100.1 mac:00:00:00:01:01:01 sid:1
0d 00:00:12 oE lac 718372593
------------------------------------------------------------------------------
No. of PPP sessions: 1
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
718340096 10961 15559 established not-blacklisted 1
l2tp-functional-radius 1
LNS1-T1
------------------------------------------------------------------------------
No. of tunnels: 1
show router 65536 l2tp session
==============================================================================
L2TP Session Summary
==============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
------------------------------------------------------------------------------
718372593 718340096 10961 32497 established
------------------------------------------------------------------------------
No. of sessions: 1
<date> <time> CET MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 73 len 114 from 172.16.1.1:1812 vrid 1 pol subscr-mgmt
VSA [26] 21 Alcatel(6527)
SUBSC ID STR [11] 19 user1@wholesale.com
VSA [26] 11 Alcatel(6527)
SUBSC PROF STR [12] 9 sub-func1
VSA [26] 11 Alcatel(6527)
SLA PROF STR [13] 9 sla-func1
VSA [26] 6 Alcatel(6527)
TUNNEL SERVICE ID [104] 4 65536 #LAC in VRF
VSA [26] 15 Alcatel(6527)
TUNNEL GROUP [46] 13 wholesale.com #points to L2TP node group name
*A:pe1# show service id 1 ppp session
==============================================================================
PPP sessions for service 1
==============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id
------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/2:100.1 mac:00:00:00:01:01:01 sid:1
0d 00:00:11 oE lac 768347764
------------------------------------------------------------------------------
No. of PPP sessions: 1
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
768344064 11724 14445 established not-blacklisted 1
wholesale.com 1
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
show router 65536 l2tp session
==============================================================================
L2TP Session Summary
==============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
------------------------------------------------------------------------------
768347764 768344064 11724 3700 established
------------------------------------------------------------------------------
No. of sessions: 1
The debug subscriber-mgmt local-user-db "l2tp" detail all command shows the LUDB authentication access (The returned parameter details are not shown).
<date> <time> CET MINOR: DEBUG #2001 Base LUDB
"LUDB: User lookup success - host found
user-name:
original: user1@wholesale.com
masked: user1@wholesale.com
Host wholesale.com found in user data base l2tp #host found
show subscriber-mgmt local-user-db "l2tp" ppp-host "wholesale.com" | match N/A invert-match | match none invert-match
==============================================================================
PPP Host "wholesale.com"
==============================================================================
Admin State : Up
Last Mgmt Change : 11/22/2013 17:35:28
Host Identification
User Name : wholesale.com (domain only)
Matched Objects : userName
Password Type : ignore
PADO Delay : 0msec
Force IPv6 CP : Disabled
Identification Strings (option 254)
Subscriber Id : user1@wholesale.com
SLA Profile String : sla-func1
Sub Profile String : sub-func1
L2TP
Service : 65536 #LAC in VRF
Tunnel Group : wholesale.com #points to L2TP group name
The debug router l2tp event lac-session-setup command shows the LAC tunnel selected for this example.
<date> <time> CET MINOR: DEBUG #2001 vprn65536 PPPoE 28->L2TP
"PPPoE 28->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.6:1701
preference 50 tunnel wholesale.com:wholesale.com #group and tunnel name
request to open new tunnel 15501"
462 2013/11/22 17:39:13.21 CET MINOR: DEBUG #2001 vprn65536 PPPoE 28->L2TP
"PPPoE 28->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.6:1701
preference 50 tunnel wholesale.com:wholesale.com
create session 1015877546"
show service id 1 ppp session
==============================================================================
PPP sessions for service 1
==============================================================================
User-Name
Descr.
Up Time Type Termination IP/L2TP-Id/Interface-Id
------------------------------------------------------------------------------
user1@wholesale.com
svc:1 sap:1/1/2:100.1 mac:00:00:00:01:01:01 sid:1
0d 00:00:10 oE lac 1015877546
------------------------------------------------------------------------------
No. of PPP sessions: 1
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
1015873536 15501 11826 established not-blacklisted 1
wholesale.com 1
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
show router 65536 l2tp session
==============================================================================
L2TP Session Summary
==============================================================================
ID Control Conn ID Tunnel-ID Session-ID State
------------------------------------------------------------------------------
1015877546 1015873536 15501 4010 established
------------------------------------------------------------------------------
No. of sessions: 1
configure service vprn 65536
<snip>
l2tp
group "wholesale.com"
tunnel "wholesale.com"
local-address 192.168.2.2
local-name "lac-pe1"
peer 192.168.2.6
auto-establish #triggers tunnel setup
no shutdown
exit
no shutdown
exit
no shutdown
exit
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
960495616 14656 721 establishedIdle not-blacklisted 0
wholesale.com 0
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
configure service vprn 65536
<snip>
l2tp
group "wholesale.com"
tunnel "wholesale.com"
local-address 192.168.2.2
local-name "lac-pe1"
peer 192.168.2.6
no auto-establish #no triggers tunnel setup
no shutdown
exit
no shutdown
exit
no shutdown
exit
tools perform router 65536 l2tp group wholesale.com tunnel wholesale.com start
configure router l2tp | configure service vprn l2tp
idle-timeout [0..3600]seconds
<snip>
group <tunnel-group-name>
idle-timeout [0..3600]secondzs | infinite
<snip>
tunnel <tunnel-name>
idle-timeout [0..3600]seconds | infinite
<snip>
show router l2tp tunnel detail # Example persistent tunnel
==============================================================================
Connection ID: 111804416
State : establishedIdle # moves from established to establishedIdle
# after last session is closed
<snip>
Assignment ID: unnamed
Group Name : default_radius_group
Error Message: N/A
Remote Conn ID : 586874880
Tunnel ID : 1706 Remote Tunnel ID : 8955
Preference : 50 Receive Window : 64
Hello Interval(s): 300
Idle TO (s) : infinite Destruct TO (s) : 60
<snip>
show router l2tp tunnel detail # Example non-persistent tunnel
==============================================================================
Connection ID: 1039335424
State : closed # moves from established to establishedIdle
# after last session is terminated. Ten
# seconds later state becomes closed(tunnel
# destroyed). Operational tunnel data
# stays available (trouble shooting
# purposes)for a short period of time.(see
# further destruct-timeout).
<snip>
Assignment ID: unnamed
Group Name : default_radius_group
Error Message: idle timeout (10 seconds) expired
Remote Conn ID : 218169344
Tunnel ID : 15859 Remote Tunnel ID : 3329
Preference : 50 Receive Window : 64
Hello Interval(s): 300
Idle TO (s) : 10 Destruct TO (s) : 60
<snip>
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
462749696 7061 9070 establishedIdle not-blacklisted 0
wholesale.com 0
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
tools perform router 65536 l2tp group wholesale.com tunnel wholesale.com stop
#
tools perform router 65536 l2tp tunnel 462749696 stop
<date> <time> CET MINOR: DEBUG #2001 vprn65536 L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.168.2.2:1701 -> 192.168.2.6:1701
tunnel 9070 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
StopControlConnectionNotification(4)
AVP ResultCode(0,1), flags: mandatory, reserved=0
result-code: "generalRequestToClearControlConnection"(1), error-code:
"noGeneralError"(0)
error-msg: "operator request"
AVP AssignedTunnelId(0,9), flags: mandatory, reserved=0
7061"
configure router l2tp | configure service vprn l2tp
hello-interval [60..3600]seconds | infinite #default 300s
max-retries-estab [2..7] #default 5
<snip>
group <tunnel-group-name>
hello-interval [60..3600]seconds | infinite
max-retries-estab [2..7]
<snip>
tunnel <tunnel-name>
hello-interval [60..3600]seconds | infinite
max-retries-estab [2..7]
<snip>
LAC > show router l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
148635648 2268 13918 established not-blacklisted 1
l2tp-functional-radius 1
LNS1-T1
Figure 386 shows the tunnel being closed after 5 unsuccessful Hello deliveries with error-message
connection with peer lost.
LAC > show router l2tp tunnel detail
==============================================================================
L2TP Tunnel Status
==============================================================================
Connection ID: 148635648
State : closed
<snip>
Error Message: connection with peer lost
Remote Conn ID : 912130048
Tunnel ID : 2268 Remote Tunnel ID : 13918
Preference : 100 Receive Window : 64
Hello Interval(s): 60
<snip>
configure router l2tp | configure service vprn l2tp
destruct-timeout [60..86400]
<snip>
group <tunnel-group-name>
destruct-timeout [60..86400]
<snip>
tunnel <tunnel-name>
destruct-timeout [60..86400]
show router l2tp session detail
==============================================================================
L2TP Session 228095933
==============================================================================
Connection ID: 228095933
State : closed #session destroyed but data still available
Tunnel Group : default_radius_group
Assignment ID: unnamed
Error Message: Terminated by PPPoE: RX PADT
Control Conn ID : 228065280 Remote Conn ID : 609491118
Tunnel ID : 3480 Remote Tunnel ID : 9300
Session ID : 30653 Remote Session ID : 6318
Time Started : 10/08/2013 17:14:36
Time Established : 10/08/2013 17:14:36 Time Closed : 10/08/2013 17:14:43
CDN Result : generalError General Error : vendorSpecific
show router l2tp tunnel detail
==============================================================================
L2TP Tunnel Status
==============================================================================
Connection ID: 228065280
State : closed #tunnel destroyed but data still available
<snip>
Assignment ID: unnamed
Group Name : default_radius_group
Error Message: idle timeout (0 seconds) expired
Remote Conn ID : 609484800
Tunnel ID : 3480 Remote Tunnel ID : 9300
Preference : 50 Receive Window : 64
Hello Interval(s): 300
Idle TO (s) : 0 Destruct TO (s) : 60
Max Retr Estab : 5 Max Retr Not Estab: 5
Session Limit : 32767 AVP Hiding : never
Transport Type : udpIp Challenge : never
Time Started : 10/08/2013 17:14:36 Time Idle : 10/08/2013 17:14:43
Time Established : 10/08/2013 17:14:36 Time Closed : 10/08/2013 17:14:43
Stop CCN Result : generalReq General Error : noError
Blacklist-state : not-blacklisted
configure router l2tp | configure service vprn l2tp
peer-address-change-policy accept | ignore | reject #default reject
The values Peer IP, Tx dst-IP and Rx src-IP in the show router l2tp tunnel detail command indicates if floating peers are used or not.
show router l2tp tunnel detail
=======================================
L2TP Tunnel Status
=======================================
Connection ID: 897122304
State : established
IP : 192.0.2.2
UDP : 1701
Peer IP : 192.168.2.6 # (1) peer address used in SCCRQ
Peer UDP : 1701
Tx dst-IP : 192.168.2.7 # (3) peer address used in SCCCN
Tx dst-UDP : 1701
Rx src-IP : 192.168.2.7 # (2) SCCRP different IP received
Rx src-UDP : 1701
<snip>
configure subscriber-mgmt
sla-profile <sla-profile-name>
ingress
report-rate agg-rate-limit|scheduler|pppoe-actual-rate|rfc5515-actual-rate
egress
report-rate agg-rate-limit|scheduler|pppoe-actual-rate|rfc5515-actual-rate
Example 1: Default configuration.
configure router l2tp
calling-number-format "%S %s” #default configuration
<snip>
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 1240 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
<snip>
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"pe1 1/1/2:100.1"
Example 2: Customized configuration and all parameters (%S %s %c) are available to construct the requested AVP 22.
configure router l2tp
calling-number-format "start-%S###%s###%c-end"
<snip>
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 12758 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
<snip>
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"start-pe1###1/1/2:100.1###circuit0-end"
Example 3: Customized configuration and not all parameters are available to construct the requested AVP 22. Option-82 circuit-id (%c) and LLID (%l) information are missing and therefore missing (skipped) in the formatted attribute.
configure router l2tp
calling-number-format "%S#%c#%r#%l#%s"
<snip>
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 8847 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
<snip>
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"pe1##remote0##1/1/2:100.1"
configure router l2tp
exclude-avps calling-number
configure router l2tp
cisco-nas-port ethernet "*12o*10i*3s*2m*5p" atm "*12v*10c*3s*2m*5p"
<date> <time> CEST MINOR: DEBUG #2001 Base L2TP(v2, ctrl, egress)
"L2TP(v2, ctrl, egress): UDP 192.0.2.2:1701 -> 192.168.2.6:1701
tunnel 10948 session 0, ns 2 nr 1, flags:, reserved=0
AVP MessageType(0,0), flags: mandatory, reserved=0
IncomingCallRequest(10)
AVP CiscoNasPort(9,100), flags:, reserved=0
104858786 type=ethernet(0f:10:09:02:03) # 104858786 = 1/1/2:100.1
AVP AssignedSessionId(0,14), flags: mandatory, reserved=0
7556
AVP CallSerialNumber(0,15), flags: mandatory, reserved=0
41
AVP CallingNumber(0,22), flags: mandatory, reserved=0
"pe1 1/1/2:100.1"
<snip>
After the drain command is issued, the group, peer, or tunnel moves from a draining to drained state when the last session is closed. A drained group, peer, or tunnel can then be managed (reconfigured, deleted) without any user impact.
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
270073856 4121 3238 established not-blacklisted 1
wholesale.com 1
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
The following tools drain command puts the tunnel in a draining state and leaves the sessions intact.
tools perform router 65536 l2tp tunnel 270073856 drain
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
270073856 4121 3238 draining not-blacklisted 1
wholesale.com 1
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
show router 65536 l2tp tunnel
==============================================================================
Conn ID Loc-Tu-ID Rem-Tu-ID State Blacklist-state Ses Active
Group Ses Total
Assignment
------------------------------------------------------------------------------
270073856 4121 3238 drained not-blacklisted 1
wholesale.com 1
wholesale.com
------------------------------------------------------------------------------
No. of tunnels: 1
<date> <time> CET MINOR: DEBUG #2001 vprn65536 PPPoE 30->L2TP
"PPPoE 30->L2TP: UDP 192.168.2.2:1701 -> 192.168.2.6:1701
preference 50 tunnel wholesale.com:wholesale.com #tunnelis drained
no additional session can be created in tunnel 4121"
785 2013/11/24 16:11:39.05 CET MINOR: DEBUG #2001 vprn65536 PPPoE 30->L2TP
"PPPoE 30->L2TP:
stop: no more tunnels can be tried"
tools perform router 65536 l2tp tunnel 270073856 stop









