Authentication
Configure authentication for a new MAG-c session, including the RADIUS authentication profile. Learn about the BNG EP and ADB lookup process.
Overview of the authentication process
The authentication process for a new session on MAG-c performs a lookup in the following order:
- BNG EP for fixed sessions or APN for FWA sessions
- authentication flow
The BNG EP or APN lookup returns the following:
- basic configurations for the CP protocol negotiation (for example, the IPoE profile, the PPPoE profile)
- basic session configuration (for example, subscriber identification)
- the authentication flow used to authenticate the session
The authentication flow contains an ordered list of Authentication Databases (ADBs). The MAG-c performs a lookup in each ADB in the list, in the specified order. The lookup returns the following configurations required to create the session:
- session attributes (for example, the SLA profile and the subscriber profile)
- address assignment configuration (for example, the local address pool name)
- optional external AAA authentication (for example, RADIUS)
When both the BNG EP or APN lookup and the authentication flow lookup complete successfully, the MAG-c creates a full forwarding state on the BNG-UP for the session using the session management procedures.
BNG entry point
The BNG entry point (EP) provides information needed in the authentication flow. This section describes how to create and configure a BNG EP.
Use the following command to create a BNG EP.
configure mobile-gateway pdn sx-n4 signaling ibcp bng-entry-pointconfigure mobile-gateway pdn sx-n4To define the control packet types that trigger the BNG EP lookup, use the following command.
configure mobile-gateway pdn sx-n4 signaling ibcp triggers [pppoe-discover] [ipoe-dhcp] [ipoe-dhcpv6] [ipoe-router-solicit] [ipoe-data]configure mobile-gateway profile bng entry-pointThe following example shows an EP configuration in the BNG profile.
A:BNG-CPF>config>mobile>profile>bng# info
----------------------------------------------
entry-point "e1"
match 1 attribute up-ip
exit
entry "10"
ipoe
ipoe-profile "mydefault"
authentication-flow
adb "adb1" "adb2"
exit
exit
match
up-ip 172.16.10.50
exit
pppoe
pppoe-profile "pppoeProf1"
authentication-flow
pap-chap-adb "adb3" "adb4"
exit
exit
no shutdown
exit
no shutdown
exit
----------------------------------------------Authentication database (ADB)
Each ADB entry contains three groups of configuration parameters:
- match criteria
- action parameters
- session creation parameters (for example, sla-profile)
After the MAG-c chooses the best matched entry in the ADB, the MAG-c executes the configured action. The action can be any of the following types:
- reject
The session authentication fails and no subsequent ADB lookups are performed, even if they are configured as part of the authentication flow.
- accept
The MAG-c includes the session creation configuration parameters of the chosen ADB entry for the session creation.
- radiusThe MAG-c performs the RADIUS authentication using the RADIUS authentication profile. Configure the RADIUS authentication profile using the radius-authentication-profile command in the following context.
If the RADIUS authentication succeeds, the MAG-c includes the returned RADIUS authentication attributes and the session creation configuration parameters for the session creation. If the RADIUS authentication fails, the session authentication fails.configure mobile-gateway profile bng - local_authThe MAG-c performs a PAP/CHAP authentication using the configured username and password in the ADB entry for the PPPoE session. Configure the username using the username command in the following context.
Configure the password using the action local-auth command in the following context.configure mobile-gateway profile authentication-database entry matchconfigure mobile-gateway profile authentication-database entry
The MAG-c uses the session creation configuration parameters of all ADBs. The
authentication flow contains an ordered list of ADBs. If ADBx comes before ADBy in the
ordered list of ADBs, the values of the parameters in ADBy have priority over the values
of the parameters in ADBx. For example, an authentication flow contains two ADBs, ADB1
and ADB2. If the matched entry in ADB1 returns sla-profile
foo, and the matched entry in ADB2 returns
sla-profile
bar, a new session is created with sla-profile
bar.
If a session creation configuration is not explicitly configured (for example, it
equals the default value), the ADB lookup returns no value for this configuration. For
example, an authentication flow contains two ADBs, ADB1 and ADB2. If ADB1 returns
sla-profile
bar, and the matched entry in ADB2 does not contain an explicit
configuration for sla-profile (it equals the default value), a new
session is created with sla-profile
bar.
Some session creation configuration parameters support a special discard keyword. The discard keyword means that the previously returned ADB value for the attribute must be discarded. For example, an authentication flow contains two ADBs, ADB1 and ADB2. If ADB1 returns a value for bng-charging-profile, and ADB2 configures bng-charging-profile discard, the MAG-c creates the session without bng-charging-profile.
Authentication flow
An authentication flow contains the following configuration items:
- trigger packet type; for example, DHCPv4 discovery or PPPoE PADI packetNote: For FWA session, the trigger packet type is not explicitly configured. It is always the first session establishment message, such as a GTP Create Session Request message.
- ordered list of one or more ADBs for the specified trigger packet type
When the BNG-UP sends a trigger packet, the MAG-c performs a lookup in each ADB in the list, in the specified order. Each ADB can return session-related configurations. These session-related configurations can be locally configured or returned from an external AAA server.
An IPoE or FWA session has only one authentication flow. A PPPoE session requires at least one of the following independent authentication flows:
- PADI
- PAP/CHAP
If an ADB lookup fails, the session setup fails. The ADB lookup may fail, for example, if an entry is matched with an action reject or if there is an AAA authentication failure.
If all lookups complete successfully, the MAG-c continues session setup using the combined configurations from all ADB lookups. For example, the BNG EP lookup returns two authentication flows for a new PPPoE session. The authentication flows return the following configuration:
- PADI authentication flow with 1 ADB: ADB1 returns PADO delay value
- PAP/CHAP authentication flow with 2 ADBs: ADB2 configures RADIUS authentication, ADB3 returns a local address pool
In this example, the MAG-c uses the combined configuration result from the three ADB lookups to set up the PPPoE session.
Each session requires an APN for service selection, as described in Service selection. The APN can also provide override for specific configurations. If different types of sources return the same type of configuration (for example, an address pool name), the MAG-c uses the value of the source with the highest ranking. The sources are ranked as follows, with the highest ranked first:
- AAA
- Local ADB
- APN
If different sources of the same type (for example, different ADBs) return the same type of configuration, the MAG-c uses the last returned value. For example, if both ADB-1 and ADB-N return an SLA profile name, and ADB-1 returns SLA profile name X and ADB-N returns SLA profile name Y, the system uses SLA profile name Y because it is the last returned value.
BNG EP and ADB lookup
Both the BNG EP entries and the ADB entries contain session configuration and one or more ordered match criteria. The match criteria are used in the lookup. The session configuration is used in the creation of the session.
Match criteria properties
- match-id
The match ID defines the priority. The lower the ID, the higher the priority.
- attribute
The attribute defines the name of the attribute that is used for the lookup. It is the name of a session attribute. The attribute can be a control protocol field (for example, DHCP option 82 circuit-id, vendor-class) or metadata of the session (for example, l2-access-id).
- value
The value defines the criteria value to which the session value must match for the specified attribute. If the attribute is optional, the value can be empty, meaning any session value matches with the criteria value.
- optional
Match criteria can be optional or mandatory. The attribute of optional criteria does need to be present in the session data to match the entry. If the attribute of optional criteria is present in the session data, the session value must equal the criteria value to match the entry. An attribute that is not present in the entry can have any value in the session (including not available).
- string-mask
A string mask is applied to the value of the session attribute before comparing it with the value of the criteria. It can be used for supported attributes (for example, l2-access-id).
The string mask can be length-based or string-based and can be a suffix or a prefix, as follows:
- prefix
- length-based
The MAG-c removes the specified number of characters from the beginning of the session value.
- string-based
The MAG-c removes the specified string from the beginning of the session value. An asterisk (*) can be used as a wild-card in the string mask.
- length-based
- suffix
- length-based
The MAG-c removes the specified number of characters from the end of the session value.
- string-based
The MAG-c removes the specified string from the end of the session value. An asterisk (*) can be used as a wild-card in the string mask.
- length-based
1/2/3.- For string-mask equal to prefix length
2, the MAG-c removes the first two characters of the session value. The resulting
value
2/3is used to match with the end of the criteria value; for example, the resulting value2/3matches with the criteria value4/2/3. - For string-mask equal to suffix string
"/*”, the MAG-c removes the last slash (/) and everything after it at the end of the
session value. The resulting value
1/2is used to match with the beginning of the criteria value; for example, the resulting value1/2matches with the criteria value1/2/4.
Default entries
If a BNG EP entry or an ADB entry does not have any match criteria, this BNG EP entry or ADB entry is the default entry. The MAG-c chooses the default entry when there is no other matched entry. Only one default entry is allowed for the BNG EPs and for the ADBs.
Entry matching
Entries of a BNG EP or of an ADB cannot have the same set of match criteria within the same BNG EP or ADB. In this case, the entry becomes operationally down. The system does allow entries with the same match criteria in different BNG EPs or ADBs.
During a BNG EP or ADB lookup, the MAG-c compares the attributes of the session with the match criteria of all entries in the BNG EP or in the ADB and creates a list of all matched entries. A matched entry is one for which all mandatory match criteria are fulfilled.
- If the list of all matched entries contains only one entry, that entry is the best match.
- If the list of all matched entries contains more than one entry, the MAG-c reduces the list to the entries with the highest number of match criteria. If this list contains only one entry, that entry is the best match.
- If the reduced list of entries with the highest number of match criteria contains more than one entry, the MAG-c selects the entry with matches for the highest priority attributes.
Example mandatory and optional match criteria
As an example, the match criteria for an ADB entry contain the attribute l2-access-id (marked optional) and the attribute up-ip (mandatory). To call the ADB entry a matched entry, one of the following must be true.
- Both up-ip and l2-access-id are present in the session and both match the values in the ADB entry.
- Only up-ip is present in the session and it matches the value in the ADB entry.
If both l2-access-id and up-ip are present in the session, but only l2-access-id matches the value in the ADB entry, the ADB entry is not a matched entry.
Example entry matching and selection
The following output defines the configuration of four ADB entries.
----------------------------------------------
#first match criteria is UP's IP address
match 1 attribute up-ip
optional
exit
#2nd match criteria is Layer 2 access ID
match 2 attribute l2-access-id
optional
exit
#3rd match criteria is SVLAN
match 3 attribute s-vlan
optional
exit
entry "10"
match
l2-access-id "1/1/2"
up-ip 172.16.10.50
vlan
s-vlan start 100 end 200
exit
exit
subscriber-mgmt
sla-profile "entry10"
sub-profile "entry10"
exit
no shutdown
exit
entry "20"
charging
bng-charging-profile "mybngcharging"
exit
match
l2-access-id "1/1/2"
up-ip 172.16.10.50
exit
subscriber-mgmt
sla-profile "entry20"
sub-profile "entry20"
exit
no shutdown
exit
entry "30"
match
l2-access-id "1/1/2"
vlan
s-vlan start 100 end 200
exit
exit
subscriber-mgmt
sla-profile "entry30"
sub-profile "entry30"
exit
no shutdown
exit
entry "40"
match
vlan
s-vlan start 100 end 200
exit
exit
subscriber-mgmt
sla-profile "entry40"
sub-profile "entry40"
exit
no shutdown
exit
no shutdown
----------------------------------------------A new session has the following attributes and values:
- up-ip with value
172.16.10.50 - l2-access-id with value
1/1/2 - s-vlan with value
100
The session matches with all ADB entries. The MAG-c chooses the entry 10 because it has the highest number of matching criteria; that is, three matching criteria.
Assume the entry 10 is shut down. Both the entries 20 and 30 have the highest number of matching criteria; that is, two matching criteria. The MAG-c chooses the entry 20 because it has the matching criteria with the highest priority; that is, up-ip.
Assume all entries except 40 are shutdown. The MAG-c chooses the only matching entry; that is, the entry 40.
Required minimal configuration for a session creation
To create a session, the MAG-c requires a minimal number of session creation configuration parameters. The table lists the parameters that are required for session creation, as well as the source that contains those parameters.
| Configuration | Source |
|---|---|
| ipoe-profile (IPoE session only) | BNG EP |
| pppoe-profile (PPPoE session only) | BNG EP |
| authentication-flow (fixed access) | BNG EP |
| authentication-flow (FWA) | APN |
| APN | ADB, RADIUS |
| address-assignment | ADB, RADIUS |
| sla-profile1 | ADB, RADIUS |
| sub-profile1 | ADB, RADIUS |
| group-interface-template1 | ADB, RADIUS |
| sap-template1 | ADB, RADIUS |
RADIUS authentication profile
configure mobile-gateway profile bngRADIUS authentication is triggered by the ADB lookup; consequently, it is possible to have multiple rounds of RADIUS authentication during the authentication flow lookup. If the same attributes are returned in the Access-Accept message during multiple authentication rounds, the last attribute received is used.
A RADIUS authentication profile contains the following configuration commands:
-
radius-group
The radius-group command contains RADIUS server configuration such as address, port, and shared secret. To define the RADIUS server configuration, use the radius-group command in the configure mobile-gateway profile context. Afterwards, reference this RADIUS group in the following context.configure mobile-gateway profile bng radius-authentication-profile -
user-name-format
Use the following command to define the username format for the RADIUS server.configure mobile-gateway profile bng radius-authentication-profile user-name-formatUse the following command option to send the source IP address of the data-trigger packet.
configure mobile-gateway profile bng radius-authentication-profile user-name-format ipoe format data-trigger-source-ip -
password
Use the following command to define the password of the RADIUS user.configure mobile-gateway profile bng radius-authentication-profile password -
include-attribute
The include-attribute command defines the RADIUS attributes to be included in an Access-Request message. Use the commands in the following context to define the attributes to include.configure mobile-gateway profile bng radius-authentication-profile include-attribute
The username and password configuration is required for IPoE authentication, PPPoE PADI authentication, and FWA authentication if no PAP/CHAP credentials are provided during FWA session setup.
RADIUS CoA and DM
A RADIUS Change of Authorization (CoA) message or a Disconnect Message (DM) asks for changes in the session or subscriber object.
configure mobile-gateway pdn bng radius-coaThe interface defines one or more listening interfaces for incoming CoA and DM messages, and the shared secrets.
When the MAG-c receives a CoA or DM message, it makes the requested change to the target object. The MAG-c RADIUS Attributes and IU Triggers list defines the message attributes that can be used to identify one or multiple sessions as target object. Filter on the value True for the CoA key column to find those attributes in the list. If a subscriber is specified in the request, the MAG-c applies the requested changes to all sessions of the targeted subscriber.
The CoA message contains one or more attributes that define the requested changes; for example, the Alc-SLA-Prof-Str VSA defines a new sla-profile for the target object. For more information about the supported attributes, see the MAG-c RADIUS Attributes and IU Triggers.
If the MAG-c applies all requested changes successfully to all targeted objects, the MAG-c sends a CoA-ACK message back to the RADIUS server. If the MAG-c can only apply the requested changes partially or only on a subset of the target objects, the MAG-c sends a CoA-NAK message with an ERROR-CAUSE code 506, and rolls back the changes as follows.
- If the change request is for multiple attributes on a single session and only part of the attribute changes are successful, the MAG-c sends a CoA-NAK message with an ERROR-CAUSE code 404, and rolls back the already applied changes.
- If the change request is for multiple attributes on multiple sessions and the changes are only successful for a part of all the target sessions, the MAG-c sends a CoA-NAK message with an ERROR-CAUSE code 506, and rolls back the applied changes for the sessions that were only partially changed. For example, a CoA message requests to change three attributes on five sessions. The MAG-c successfully applies all attribute changes on session 1, session 2, and session 3, but only applies one attribute change successfully on session 4 and session 5. The MAG-c sends a CoA-NAK message with an ERROR-CAUSE code 506, and rolls back the attribute change on session 4 and session 5.
A DM message only contains target objects. The MAG-c removes the sessions of the target objects and sends an ACK message. If the target objects do not exist, the MAG-c sends a CoA-NAK message with ERROR-CAUSE code 503.
configure mobile-gateway pdn bng radius-coatools perform mobile-gateway profile bng radius coaExample configuration
The example configuration in this section is for the following setup:
- IPoE session
- RADIUS authentication
- address pool
pool-up-1for sessions from BNG-UP1.1.1.1 - address pool
pool-up-2for sessions from BNG-UP2.2.2.2 - sla-profile
basic, sub-profilebasic, and authentication with radius-auth-profile-1 for sessions with s-vlan100 - sla-profile
premium, sub-profilepremium, and authentication with radius-auth-profile-2 for sessions with s-vlan200
To achieve the above setup, an authentication flow with three ADBs is used. In this example, the following is returned.
- ADB
adb1only returns the address pool. - ADB
adb2only returns the sla-profile and the sub-profile, and performs RADIUS authentication. - ADB
adb3returns the other configuration parameters.
The following example shows the ADB configuration.
authentication-database "adb1"
match 1 attribute up-ip
exit
entry "up-1"
address-assignment
local-dynamic
ipv4-pool "pool-up-1"
exit
exit
match
up-ip 1.1.1.1
exit
no shutdown
exit
entry "up-2"
address-assignment
local-dynamic
ipv4-pool "pool-up-2"
exit
exit
match
up-ip 2.2.2.2
exit
no shutdown
exit
no shutdown
exit
authentication-database "adb2"
match 1 attribute s-vlan
exit
entry "basic"
action radius radius-authentication-profile "radius-auth-profile-1"
match
vlan
s-vlan start 100 end 100
exit
exit
subscriber-mgmt
sla-profile "basic"
sub-profile "basic"
exit
no shutdown
exit
entry "premium"
action radius radius-authentication-profile "radius-auth-profile-2"
match
vlan
s-vlan start 200 end 200
exit
exit
subscriber-mgmt
sla-profile "premium"
sub-profile "premium"
exit
no shutdown
exit
no shutdown
exit
authentication-database "adb3"
entry "default"
apn "mybngvrf"
interface
group-interface-template "defaultgroup"
sap-template "defaultsap"
exit
no shutdown
exit
no shutdown
exitThe following example shows the configuration of the BNG EP.
*A:BNG-CPF>config>mobile>profile>bng# info
----------------------------------------------
entry-point "e1"
entry "10"
ipoe
ipoe-profile "mydefault"
authentication-flow
adb "adb1" "adb2" "adb3"
exit
exit
no shutdown
exit
no shutdown
exitconfigure mobile-gateway pdn sx-n4 signaling ibcp*A:BNG-CPF>config>mobile>pdn>sx-n4# info
----------------------------------------------
pfcp-association-list "pfcpassoc1"
interface
pfcp "system"
ibcp "system"
exit
signaling
pfcp
profile "pfcppro-1"
exit
ibcp
bng-entry-point "e1"
triggers ipoe-dhcp
exit
exitWeb portal authentication
The BNG supports the WPP protocol to authenticate broadband or WLAN users on a web portal.
Web portal authentication uses the WPP protocol between a BNG and a web portal server for broadband or WLAN users. The user provides a username and password on the portal page and the web portal triggers the BNG to perform RADIUS authentication with the specified credentials.
WPP call flow example
The following figure shows a high-level call flow example of WPP authentication for a client using DHCPv4 on a BNG CUPS system.
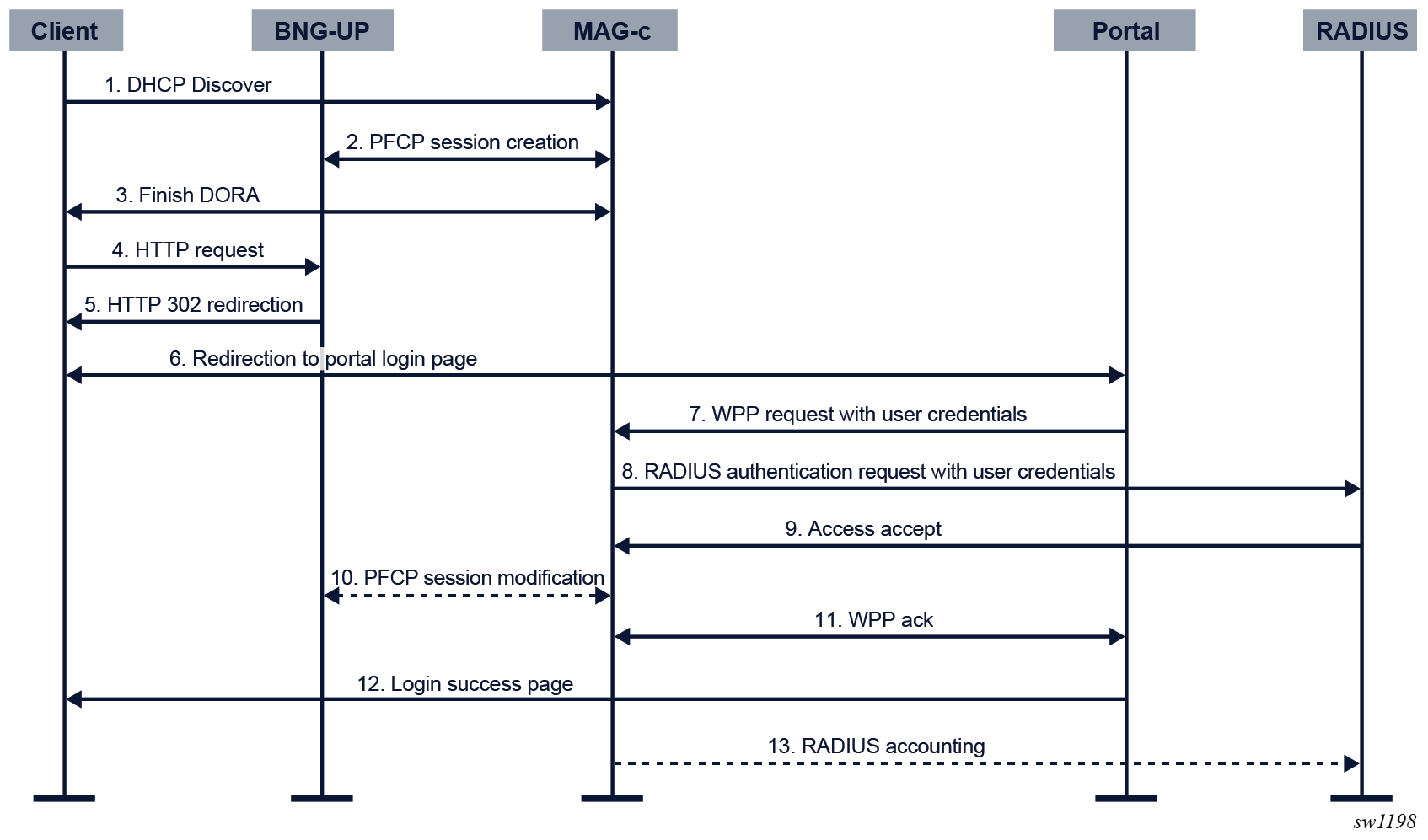
- The client sends a DHCP discovery packet. The BNG-UP
forwards it to the MAG-c. The MAG-c authenticates the packet via the
authentication flow. The authentication returns two sets of SLA profile and
subscriber profile, that is, initial profiles and after-auth profiles.
- Initial profiles are used for the client before portal authentication. The SLA profile includes a filter that contains an HTTP redirection entry to the portal.
- After-auth profiles are used for the client after portal authentication.
- a WPP RADIUS authentication profile, used in step 8.
- an HTTP redirection URL
- The MAG-c creates a session on the BNG-UP with the initial profiles and the redirection URL via PFCP.
- The client finishes DORA with the MAG-c.
- The client sends an HTTP request.
- Because of the redirection filter in the initial SLA profile, the BNG-UP intercepts the HTTP request and sends an HTTP 302 redirection response.
- The client is redirected to the portal. The user provides user credentials (for example, username and password).
- The portal sends the user credentials in a WPP request message to the MAG-c.
- The MAG-c sends a RADIUS authentication request to the RADIUS server with the user credentials received in the WPP request.
- The RADIUS server successfully authenticates the request and sends an Access Accept message. Optionally, the RADIUS server includes an SLA profile and a subscriber profile in the Access Accept message. Those profiles are after-auth profiles that override the after-auth profiles of step 1.
- If the RADIUS server sent after-auth profiles in the Access Accept message of step 9, the MAG-c modifies the session with those profiles.
- The MAG-c and the web portal exchange WPP Ack messages.
- The web portal returns a login successful page to the client.
- Optionally, the MAG-c starts RADIUS accounting.
Variables in the HTTP redirection URL
The initial authentication returns an HTTP redirection URL that optionally contains one or multiple variables. The variables are replaced with session-specific values. The supported variables are:
- $IP — the IPv4 or IPv6 address that triggers the WPP authentication
- $MAC — the MAC address
- $URL — the original requested URL
- $SAP — the Layer 2 access ID and the VLAN tags
- $SUB — the subscriber ID as a string
- $CID — the circuit ID, or the interface ID of the subscriber host (in hexadecimal format)
- $RID — the remote ID of the subscriber host (hexadecimal format)
- $SYSNAME — CPF_SYSTEM_NAME:UPF_IP
For example, when the initial authentication returns
http://www.example.com/login?sub=$SUB, and the subscriber ID
for the session equals sub1, the actual URL is
http://www.example.com/login?sub=sub1
HTTP redirection URL override
If the initial authentication contains RADIUS authentication, and the Access Accept message contains the RADIUS Alc-Portal-Url VSA, the value of the RADIUS attribute is used for HTTP redirection. The URL in the RADIUS Alc-Portal-Url VSA overrides the locally configured HTTP redirection URL.
Portal group
You can configure up to eight WPP portals in a portal group. The MAG-c can receive WPP requests from any of the configured portals in the portal group.
When the MAG-c initiates a WPP NTF_LOGOUT message, it sends the NTF_LOGOUT message to all configured portals in the portal group. The first received ACK_LOGOUT stops the retransmission of the NTF_LOGOUT message.
- A portal can only be configured in one portal group.
- A portal can be in a portal group and at the same time be used as an individual portal.
- Portals supporting different WPP versions (version 1 and version 2) are allowed in the same portal group.
WPP port attribute
The MAG-c uses the WPP port attribute in the WPP protocol messages to identify the port of the session.
The format of the WPP port attribute is CPF_SYSTEM_NAME#UPF_ADDR#L2_ACCESS_ID:VLAN1.VLAN2. If the length of the result string exceeds 35 chars, the system truncates it to the first 35 chars.
- SAP (the Layer 2 access ID and the VLAN tags) = 1/2/10:100.200
- BNG-UP address = 2.2.2.2
- MAG-c system name = CUPSBNG1
Configuring WPP
To configure a minimal WPP configuration, define a WPP listening interface, a WPP portal, a portal group, a RADIUS authentication profile, and configure WPP in the ADB entry.
The steps in this procedure define a minimal WPP configuration.
-
Configure a WPP listening IP interface.
Use the interface command in the following context.
configure mobile-gateway pdn bng wpp -
Define a WPP portal.
Use the portal command in the following context.
configure mobile-gateway profile bng wpp -
Define a portal group and include a reference to the portal defined in the
previous step.
Use the portal-group command in the following context.
configure mobile-gateway profile bng wpp -
Define a RADIUS authentication profile.
Use the radius-authentication-profile in the following context.
configure mobile-gateway profile bng -
Configure the WPP context in an ADB entry.
Use the following commands in the following context.
configure mobile-gateway profile authentication-database entry wpp- Use the portal-group command to reference the portal group defined in step 3.
- Use the wpp-radius-authentication command to reference the RADIUS authentication profile defined in step 4.
- Use the initial-profiles command to specify the names of the initial SLA and subscriber profiles.
- Use the no shutdown command to enable the WPP entity in the ADB entry.
-
Configure the HTTP redirection URL in an ADB entry.
Use the http-redirect url command in the following context.
configure mobile-gateway profile authentication-database entry -
Configure the after-auth profiles in an ADB entry.
Use the subscriber-mgmt command in the following context to define the after-auth SLA and subscriber profiles.
configure mobile-gateway profile authentication-database entry
*A:BNG-CPF>config>mobile>pdn>bng>wpp# info
----------------------------------------------
interface router "Base" name "system"
----------------------------------------------
*A:BNG-CPF>config>mobile>profile>bng>wpp# info
----------------------------------------------
portal "p1"
address 2001:beef::1
router "Base"
source-address 2001:dead::1
no shutdown
exit
portal-group "g1"
realm "mybngvrf"
portal "p1"
no shutdown
exit
----------------------------------------------
*A:BNG-CPF>config>mobile>profile>adb>entry# info
----------------------------------------------
apn "mybngvrf"
dhcp-profile "mydefault"
http-redirect
url "http://www.exampleportal.com"
exit
address-assignment
local-dynamic
ipv4-pool "p1"
exit
exit
interface
group-interface-template "defaultgrp"
sap-template "defaultsap"
exit
subscriber-mgmt
sla-profile "base"
sub-profile "base"
exit
wpp
portal-group "g1"
wpp-radius-authentication "wpp-rad"
initial-profiles
sla-profile "ini-sla"
sub-profile "ini-sub"
exit
no shutdown
exit
no shutdown
----------------------------------------------