Fixed wireless access sessions
Fixed wireless access (FWA) sessions obtain network connectivity through a mobile RAN such as (e-)UTRAN (4G) or NR (5G). FWA sessions use the same BNG-UP, charging, authentication, and address management methods (including ODSA) as fixed BNG sessions.
Introduction to FWA sessions and terminology
FWA sessions obtain network connectivity through a mobile RAN, for example 4G (e-)UTRAN or 5G NR, and therefore they have the following important differences from fixed access sessions:
- FWA sessions perform the initial setup out-of-band and signal directly to the MAG-c, which acts as a 4G SGW-C + PGW-C (combined), or a session management function (SMF), whichever is applicable.
- FWA sessions have tunneled IP connectivity from the client device to the FWA-UP, which acts as a 4G SGW-U + PGW-U (combined), or 5G UPF, whichever is applicable.
FWA sessions are BNG subscriptions, which means they have the same service requirements as fixed sessions. QoS, service selection, pool management, and charging are all applicable to FWA sessions.
FWA sessions often use mobile-specific terminology. The following lists the most common terms and how they map to an FWA deployment.
- APN
- An Access Point Name (APN) identifies a specific PDN but can also be used to
identify a specific gateway within a PDN, or even a specific service type within
a PDN. A single UE can be connected to multiple APNs. Each such session is
called a PDN session. This model maps directly to FWA and is also common with
fixed BNG sessions. An APN consists of the following two sub-fields.
- Network Identifier (NI): defines the network (PDN).
- Operator Identifier (OI): defines the operator’s mobile network in which the PDN gateway resides. This consists of the operator’s MNC and MCC. This field is optional.
- DNN
-
A Data Network Name (DNN) is the 5G equivalent to an APN.
- GPSI
-
Similar to SUPI, the Generic Public Subscription Identifier (GPSI) is introduced in 5G to contain public identifiers such as MSISDN and is also ready to support other type of identifiers. For FWA, the GPSI always contains an MSISDN.
- IMEI
- An International Mobile Equipment Identity (IMEI) is a unique identifier for the hardware device used for the connection. Part of the IMEI is the Type Allocation Code (TAC) which is allocated to a specific device model.
- IMSI
- An International Mobile Subscriber Identity (IMSI) is a globally unique number
identifying the subscriber. For FWA, the IMSI is mapped to a subscriber ID. Its
value consists of the following three sub-fields.
- Mobile Country Code (MCC): uniquely identifies a country
- Mobile Network Code (MNC): uniquely identifies a mobile network within the country
- Mobile Subscriber Identification Number (MSIN): a second globally unique number identifying the subscriber
- MSISDN
- For mobile subscriptions, the Mobile Station International Subscriber Directory Number (MSISDN) is the public and well-known phone number. For FWA sessions, it can be used as an identifier for compatibility with AAA systems that are mostly MSISDN based.
- NSSAI
- Network Slice Selection Assistance Information (NSSAI) is a set of S-NSSAIs that is applicable to a UE. A UE can connect to a single S-NSSAI or to multiple S-NSSAIs.
- PDN
- A Packet Data Network (PDN) is a network the subscriber connects to; for example, the public Internet.
- PEI
- A Permanent Equipment Identifier (PEI) is introduced in 5G that can contain an IMEI and is also ready to support other type of identifiers. For FWA, the PEI always contains an IMEI.
- RAB
- A Radio Access Bearer (RAB) is a radio channel between a UE and the RAN. Multiple RABs per PDN session can exist.
- RAN
- The Radio Access Network (RAN) is antennas providing wireless connectivity.
- S-NSSAI
- Single Network Slice Selection Assistance Information (S-NSSAI) identifies a single network slice, which is a group of mobile functions such as SMF, UPF, and PCF that together provide specific capabilities and characteristics. For example, an FWA slice may contain all FWA UPFs and SMFs, as well as the necessary supporting functions such as CHF or PCF.
- SUPI
-
A global unique Subscription Permanent Identifier (SUPI) is introduced in 5G that can contain an IMSI and is also ready to support other type of identifiers. For FWA the SUPI always contains an IMSI.
- UE
- The User Equipment (UE) is an end device used by the subscriber. The UE and RG can be integrated in one device or can be two separate devices.
Residential Gateway models
For FWA, there are two common models for a RG.
- An integrated model where the RG provides classic BNG RG functions and acts as a mobile UE. A single IP address can be used to manage this entity. The RG or UE authentication is based on mobile SIM authentication.
- A separate model where there is a logical RG function and a logical UE function. The MAG-c abstracts from how these functions are connected. Often both functions require their own address for management purposes. It is possible to do additional RG device authentication based on PAP/CHAP.
- An integrated RG and UE can have a separate outdoor unit for radio signaling and therefore, can consist of two hardware components.
- A separate model can be a single hardware device that implements the RG and UE function separately with an internal link.
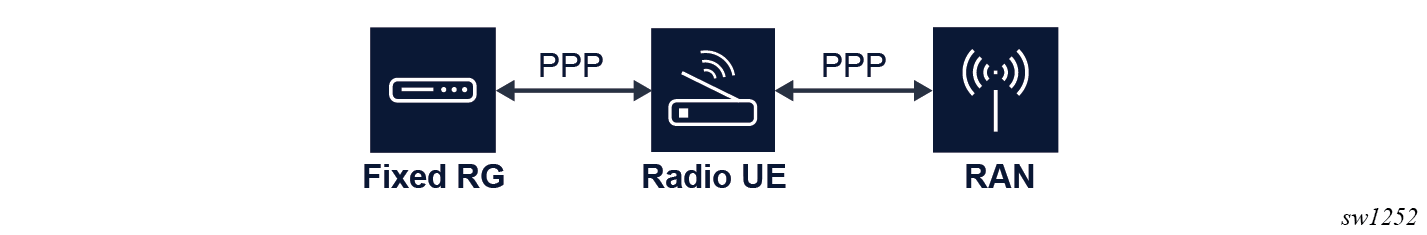
The following figure shows a model using a PPP link between the RG and the UE.
Selected and real APN
configure mobile-gateway pdn apn fixed-wireless-accessAfter initial authentication, a new APN can be returned. This APN is known as the selected APN or the virtual APN. It determines the service selection for the FWA session. If no new APN is returned, the selected service is based on the real APN.
- real
The real, unmodified APN is used as is, including the OI if it was signaled. For example, the received APN equals
internet.mnc001.mcc001.gprsand is used as is. - real-ni-only
The real APN is used, but without the OI part if it was signaled. For example, the received APN equals
internet.mnc001.mcc001.gprsand is used asinternet. - selected
This is the default option. The selected APN is used as is. If no selected APN is available, the system falls back to the real-ni-only option.
| Use case | Context |
|---|---|
|
Use the APN as a match criterion in the ADB. The APN format only applies if the attribute parameter in the match command equals apn. |
|
|
Reflect the APN in the Called-Station-Id attribute for RADIUS authentication. The APN format also applies to the username, if the user-name-format fixed-wireless-access format command in the same context is configured to include the APN. Note: If the mobile UE sends a PPP username as
a PCO during session setup signaling, the username is reflected
as is. The apn-format command in this context
does not modify the username even if it contains an APN.
|
|
|
Reflect the APN in the Called-Station-Id attribute for RADIUS accounting. Note: The user-name attribute from the
authentication is reflected as is in RADIUS accounting. The
apn-format command in this context does
not modify the username in accounting even if it contains an
APN.
|
|
Session identification, subscriber identification, and multi-APN support
For FWA sessions, the MAG-c subscriber key is the IMSI and the FWA session key is the pair (IMSI, APN). So multiple FWA sessions can be set up for the same UE/RG if those sessions use a different APN. This is called multi-APN support. The following lists some use cases of how multi-APN can be used.
- Have a different APN for Internet, video, and voice services.
- Have a different APN for public Internet and private work-from-home VPN connections.
- Have a different APN for a UE management IP address in case of the separated UE/RG model.
Each session can be mapped to a different L3 service and a different FWA-UP. For example, to optimize the BNG-UP resource usage, a low-throughput management-only session can be installed on a different FWA-UP than a high-throughput Internet session.
FWA-UP selection
- Use the following command to define a UP peer list.
configure mobile-gateway profile pfcp up-peer-list - Use the following command to configure all FWA-UPs
as peer in the UP peer list.
The IP address to use as parameter in the peer command is the source IP address of the PFCP association of the FWA-UP.configure mobile-gateway profile pfcp up-peer-list peer - Use the following command to set the FWA-UP
selection to true for each
peer.
configure mobile-gateway profile pfcp up-peer-list peer upf-selection - Use the following command to configure the APNs that are supported on the
peer.
configure mobile-gateway profile pfcp up-peer-list peer apn - Use the following command to make a reference to the configured UP peer list.
configure mobile-gateway pdn up-peer-list
During setup, the FWA session automatically selects a peer from the UP peer list that is enabled for that APN. Load balancing over the FWA-UPs is done in a round-robin fashion.
Additionally, the MAG-c supports a generic policy-based UPF selection. This can include different selection criteria, such as APN and location, where the location can be specified as a list of tracking area identities (TAIs), a list of e-UTRAN cell global identification (ECGI) and NR cell global identification (NCGI) values, or both. See Configuring policy-based UPF selection.
For FWA-UP selection, the MAG-c does not consider a UP for which the PFCP association or path fails, including a headless state, even if the UP is configured under the UP peer list. The MAG-c terminates FWA-UP sessions for which the association or path is down, not including a headless state, and sets a reactivation cause. The affected FWA RGs are expected to reconnect using a new session establishment procedure and chose a new non-failed UP, thereby providing a basic UP resiliency mechanism.
Configuring policy-based UPF selection
The MAG-c supports a generic policy-based UPF selection with different selection criteria, such as APN and location. The location can be specified as a list of TAIs, as a list of ECGI and NCGI values, or both .
The following procedure configures a TAI list, an ECGI and NCGI list, or both as selection criterion for policy-based UPF selection.
-
Create a TAI list, an ECGI and NCGI list, or both.
Create the TAI lists by configuring a range of TAIs or individually listed TAIs.
Create the ECGI and NCGI list by configuring a range of ECGI and NCGI values or individually listed ECGI and NCGI values.configure mobile-gateway profile list tai-list configure mobile-gateway profile list tai-list taiconfigure mobile-gateway profile list cell-id-list -
Define group labels for policy-based UPF selection.
Start a policy editing session to define group labels and then save your changes.
configure mobile-gateway profile node-selection begin configure mobile-gateway profile node-selection group-label configure mobile-gateway profile node-selection commit -
Configure one or more group labels for UP peers in the UP peer list. A maximum
of five group labels can be associated with a UP peer.
configure mobile-gateway profile pfcp up-peer-list peer group-label -
Configure the target profile for UPF node selection. Target profile entries can
be configured with group labels that the MAG-c uses to determine eligible UPF nodes by matching these to the group labels in
the UP peer list that are configured in step 3.
Start a policy editing session and use the target-profile command and commands in its context to configure the target profile.
Each entry in the target profile has a selection priority based on the numeric value of its associated ID. If the number of eligible UPFs for an evaluated entry is below its configured threshold, the entry is not considered for UPF selection and the next entry is evaluated. If a valid entry is found, a UPF from the eligible list of UPF nodes for that entry is selected to anchor the session. To ensure equal distribution of sessions amongst the list of eligible UPFs for the entry, the MAG-c assigns sessions to UPFs on a least-loaded-first basis, where the UPF with the least load is picked to anchor a new session. When multiple UPFs have the same least load, the MAG-c randomly selects one of those UPFs to anchor the new session.configure mobile-gateway profile node-selection begin configure mobile-gateway profile node-selection target-profile ... -
Configure the client profile with one or more entries that match on client
parameters (for example, APN, TAI list, APN and TAI list, or ECGI and NCGI list)
to determine the target profile for the session.
Use the client-profile command and the commands in its context to configure the client profile, and then save your changes.
Each entry in the client profile has a selection priority processing based on the numeric value of its associated ID. The parameters configured per entry (for example, APN, TAI list, APN and TAI list, or ECGI and NCGI list) are applied collectively. The action for the matching entry sets the target profile for the session. If no matching entry is found, the configured fallback default action sets a default target profile for the session. If no fallback default action is configured under the client profile, the session fails.configure mobile-gateway profile node-selection client-profile ... configure mobile-gateway profile node-selection commit -
Configure the client profile to apply on the SMF.
configure mobile-gateway pdn up-peer-list up-selection pgw-u-client-profile
TAI-based UPF selection
The following example shows the configuration for a TAI-based UPF selection.Nokia recommends to also configure throttling limits for the tmnxMobProfNodeSelTrgtSugstRevrt and tmnxMobProfNodeSelTrgtSugstRebal log events when the same BNG-UP is shared across multiple target profiles.
configure mobile-gateway profile list
tai-list "tai-list-1"
tai mcc 206 mnc 01 tac 0x000001
tai mcc 206 mnc 01 tac 0x00000b
exit
tai-list "tai-list-2
mcc 206 mnc 01 tac-range-start 0x123410 tac-range-end 0x123419
exit
configure mobile-gateway profile node-selection
begin
group-label "site_1"
description "Label for UPFs serving TAI 1"
exit
group-label "site_2"
description "Label for UPFs serving TAI 2"
exit
commit
exit
configure mobile-gateway profile pfcp up-peer-list “up-peer-list1”
peer 2.2.2.2
group-label "site_1"
peer 3.3.3.3
group-label “site 1”
peer 4.4.4.4
group-label “site 2”
peer 5.5.5.5
group-label “site 2”
configure mobile-gateway profile node-selection
begin
client-profile "client_profile1"
entry 1
match
tai-list "tai-list-1"
exit
action
set-target-profile "target_prof_1"
exit
exit
entry 2
match
tai-list "tai-list-2"
exit
action
set-target-profile "target_prof_2"
exit
exit
default-action
set-target-profile "default_target_prof"
exit
exit
target-profile "target_prof_1"
entry 1
threshold 2
match
group-label "site_1"
exit
exit
entry 2
threshold 2
match
group-label "site_2"
exit
exit
exit
target-profile "target_prof_2"
entry 1
threshold 2
match
group-label "site_2"
exit
exit
entry 2
threshold 2
match
group-label "site_1"
exit
exit
exit
target-profile “default-target-profile”
description “default for non-matching TAIs”
exit
commit
exit
configure mobile-gateway pdn 1
up-peer-list “up-peer-list1”
up-selection
pgw-u-client-profile “client-profile1”
exitUPF selection based on cell ID
configure mobile-gateway profile list
cell-id cell-id-list-1
plmn mcc 206 mnc 01
eci 0x0000011 end 0x0000014
nci 0x001200001 end 0x0012000F9
exit
exit
configure mobile-gateway profile pfcp up-peer-list “up-peer-list1”
peer 2.2.2.2
group-label "CoLo-site_1"
peer 3.3.3.3
group-label “CoLo-site 1”
peer 4.4.4.4
group-label “site 1”
peer 5.5.5.5
group-label “site 1”
peer 6.6.6.6
group-label “site 2”
configure mobile-gateway profile node-selection
begin
client-profile "client_profile1"
entry 1
match
cell-id-list "cell-id-list-1"
exit
action
set-target-profile "tp-cell-id-primary-selection"
exit
exit
entry 2
match
tai-list "tai-list-1"
exit
action
set-target-profile "tp-tai-primary-selection"
exit
exit
default-action
set-target-profile "default_target_prof"
exit
exit
target-profile "tp-cell-id-primary-selection"
entry 1
threshold 2
match
group-label "CoLoSite_1"
exit
exit
exit
target-profile "tp-tai-primary-selection"
entry 1
threshold 2
match
group-label "site_1"
exit
exit
entry 2
threshold 2
match
group-label "site_2"
exit
exit
exit
target-profile “default-target-profile”
description “default for non-matching TAIs”
exit
commit
exit
configure mobile-gateway pdn 1
up-peer-list “up-peer-list1”
up-selection
pgw-u-client-profile “client-profile1”
exit
Session rebalancing and revert operations
The MAG-c supports a rebalancing operation to restore an equal distribution of sessions among the eligible set of highest-priority UPs, that is, the set of UPs belonging to the highest-priority entry in the target profile for a TAI list or ECGI and NCGI list. Clearing a configurable percentage of sessions on each of the currently active UPs in the highest-priority entry of the target profile via CLI or via a network element management system, such as NSP, triggers the rebalancing operation. When a new UP becomes active and belongs to the highest-priority entry in the target profile for a TAI list or ECGI and NCGI list, a log event is generated to signal that a rebalance operation should be performed.
When the number of surviving UPs in the highest-priority entry of the target profile falls below the configured threshold, sessions may be anchored on UPs that are not highest-priority UPs. When the number of surviving UPs increases up to the configured threshold, a revert operation can be performed to reanchor the sessions from the lower-priority UPs to the highest-priority UPs. Clearing a configurable percentage of sessions on each of the lower-priority UPs for the target profile via CLI or via a network element management system, such as NSP, can trigger the revert operation. A log event is generated to signal that a revert operation should be performed.
clear mobile-gateway pdn bearer-context target-profileConfiguration details
A:MAG-c>config>mobile>profile>node-selection# info
----------------------------------------------
group-label "site1"
exit
group-label "site2"
exit
client-profile "pgw_tai_client_prof"
entry 1
match
tai-list "tai1"
exit
action
set-target-profile "target_prof_tai1"
exit
exit
default-action
exit
exit
target-profile "target_prof_tai1"
entry 1
threshold 3
match
group-label "site1"
exit
exit
entry 2
threshold 2
match
group-label "site2"
exit
exit
exit
----------------------------------------------Revert and rebalance triggers
clear mobile-gateway pdn 1 bearer-context target-profile "target_prof_tai1" action rebalance up-peer 30.0.1.188
clear mobile-gateway pdn 1 bearer-context target-profile "target_prof_tai1" action revert up-peer 30.0.1.241
clear mobile-gateway pdn 1 bearer-context target-profile "target_prof_tai1" action rebalance up-peer 30.0.1.188 percentage 50
clear mobile-gateway pdn 1 bearer-context target-profile "target_prof_tai1" action revert up-peer 30.0.1.241 percentage 50
clear mobile-gateway pdn 1 bearer-context target-profile session-deletion-rate 100 "target_prof_tai1" action rebalance up-peer 30.0.1.188 percentage 50
clear mobile-gateway pdn 1 bearer-context target-profile session-deletion-rate 100 "target_prof_tai1" action revert up-peer 30.0.1.241 percentage 50
Address signaling methods and deferred allocation
The 3GPP specifications define the following methods to signal an allocated IPv4 address:
- directly in NAS messaging during session setup
From MAG-c point of view, the address is included in the session setup messages; for example, in the GTP Create Session Response message for 4G, or the N1 PDU Session Establishment Accept message for 5G.
- via DHCP
The IPv4 address is signaled after the GTP or PDU session setup completes.
The method used depends on the following parameters and configuration, listed in order of precedence (item 1 being highest priority). Each parameter or configuration can be absent, or can have the value NAS or DHCP:
- the RADIUS Alc-FWA-IPv4-Signaling-Method VSA
- the configuration of the ipv4-signaling-method command in the
following
context
configure mobile-gateway profile authentication-database entry fixed-wireless-access - the 00AH (IP address allocation via NAS signaling) and the 000BH (IPv4 address allocation via DHCPv4) PCOs as signaled by the UE. If only one is present, that method is used.
- the configuration of the default-ipv4-signaling-method command in
the following context of the selected APN where the session is
created
configure mobile-gateway pdn apn fixed-wireless-access - NAS, by default
If IPv6 is enabled, a UE/RG interface-identifier is derived from the link-local address of the MAG-c. This interface-identifier is signaled via NAS to the UE/RG, which derives a link-local address from it when needed; for example, to send ICMPv6 RS messages.
IPv6 global addresses always use deferred allocation and are signaled in-band after session setup completion. In case of SLAAC, the UE/RG can optionally use the signaled interface-identifier to construct a global address.
For FWA, deferred allocation can be used to assign an address to an RG function in the separated UE/RG model. In this case, the UE can forward the relevant DHCP, DHCPv6, or ICMPv6 messages to the RG without maintaining the stack itself.
QoS
FWA sessions generally support the generic BNG QoS functionality and are additionally subject to specific mobile QoS constructs. In mobile networks, the concept of a bearer defines 4G QoS functionality and a QoS flow defines the 5G QoS.
This topic gives a high-level overview of how mobile QoS works. For information about the specific subset that is supported for FWA, see 4G QoS attributes and 5G QoS attributes.
In mobile networks, the concept of a bearer (4G), or a QoS flow (5G), defines the QoS. At least one default bearer or QoS flow exists to which all traffic is mapped by default. More dedicated bearers and QoS flows can be created to which specific traffic is mapped using PCC rules.
Each bearer or QoS flow is classified as either GBR or non-GBR, and QoS treatment on the BNG-UP is applied accordingly. The specified rate values are sent to the BNG-UP using PFCP QER IEs.
- GBR bearer or QoS flow: a GBR and an MBR value are applied.
- Non-GBR bearer or QoS flow: a common MBR is applied to all bearers or QoS flows of this session. For 4G, this value is known as the APN-AMBR, for 5G this value is known as the session AMBR.
The following figure shows a high-level example of QoS handling. It shows a setup with four bearers or QoS flows, of which two are GBR and two are non-GBR (including the default).
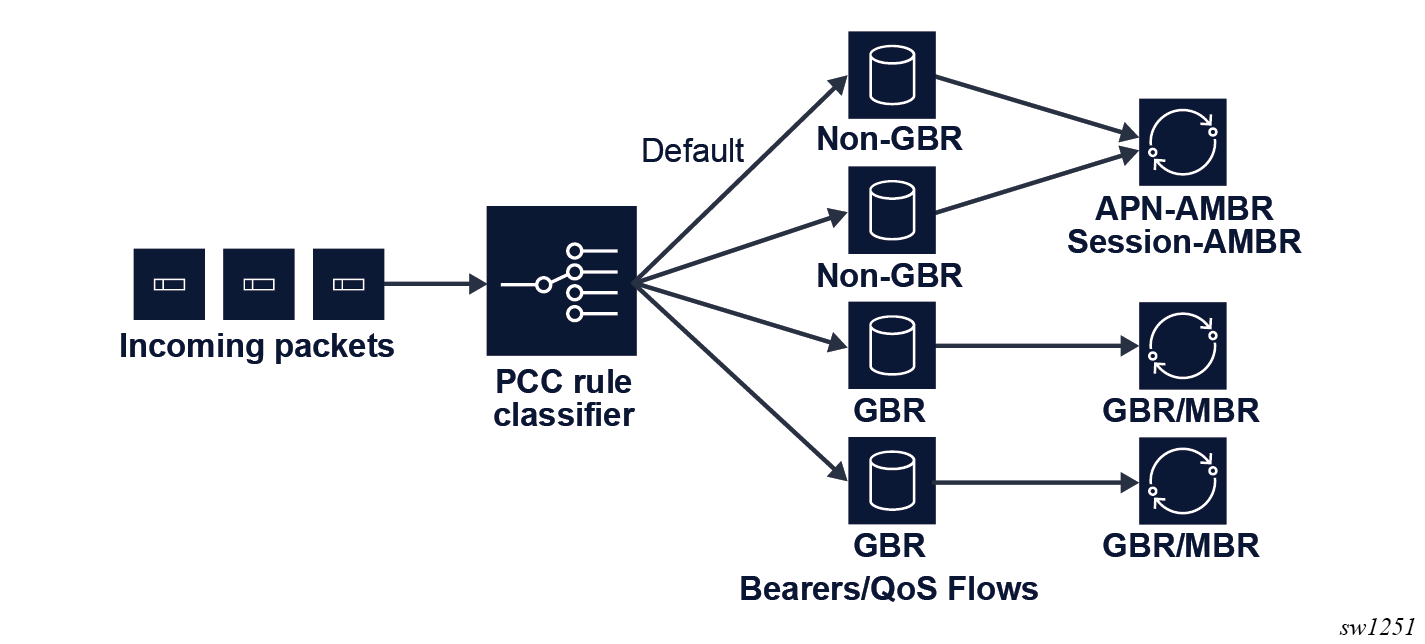
Each bearer or QoS flow has QCI (4G), 5QI (5G), and ARP (4G/5G) values. The RAN uses these values, which are transparent to the MAG-c and the FWA-UP, with the exception of the GBR or non-GBR determination of the bearer or QoS flow.
- For 4G, standardized QCI values and the corresponding GBR or non-GBR classification are specified in 3GPP TS 23.203 section 6.1.7.2.
- For 5G, standardized 5QI values and the corresponding GBR or non-GBR classification are specified in 3GPP TS 23.501 section 5.7.4.
- Both QCI and 5QI can be operator-specific, and in this case GBR or non-GBR classification is provisioned together with the QCI or 5QI provisioning. The operator-specific range is from 128 to 254 as defined in 3GGP TS 24.301 section 9.9.4.3 (4G) and 3GPP TS 24.501 section 9.11.4.12 (5G).
The access technology defines how the system learns the different values.
4G QoS attributes
The concept of a bearer defines the 4G FWA QoS functionality in mobile networks. Sessions support default bearers of the non-GBR type, as determined by specific parameters, and only APN-AMBR is supported for mobile rate-limiting.
4G FWA sessions only support default bearers and these default bearers must be of the non-GBR type. This means that only an APN-AMBR is supported for mobile-specific rate-limiting.
- The MAG-c
retrieves the subscribed values using the following parameters, in order of
precedence:
- from RADIUS, the 3GPP-GPRS-Negotiated-QoS-Profile attribute
The values signaled in the GTP Create Session Request message can, optionally, be sent to a RADIUS authentication server using the 3GPP-GPRS-Negotiated-QoS-Profile attribute. To enable this functionality, use the following command.
configure mobile-gateway profile bng radius-authentication-profile include-attribute gprs-negotiated-qos-profile - from the MME/HSS, the parameters in the GTP Create Session Request message
- from RADIUS, the 3GPP-GPRS-Negotiated-QoS-Profile attribute
- The MAG-c
determines the authorized values using the following parameters, in order of
precedence:
- from the PCF, using the authSessAmbr and authDefQos information elements during
the Npcf_SMPolicyControl_Create service operation
The MAG-c signals the subscribed QoS values to the PCF in this operation, and the PCF replies with the final authorized parameters. Session AMBR is mapped directly to APN-AMBR in this case.
- if the session does not use PCF, or PCF failed but the session continues in
ap-continue mode:
from the ADB, the QoS profile configured using the following command
configure mobile-gateway profile authentication-database entry fixed-wireless-access default-qos-profiles authorized-4gNote: The QoS profile must reference a profile configured using the following command.configure mobile-gateway profile qos-profile - from the subscribed QoS values retrieved in step 1
- from the PCF, using the authSessAmbr and authDefQos information elements during
the Npcf_SMPolicyControl_Create service operation
The authorized QoS parameters are used for the generic mobile QoS functionality. They are installed on the FWA-UP using PFCP QER constructs and included in the GTP Create Session Response message so the MME can signal their values to the eNodeB and the UE.
The APN-AMBR can be dynamically changed during the session lifetime using the following procedures:
- RADIUS CoA including the 3GPP-GPRS-Negotiated-QoS-Profile attribute
- Npcf_SMPolicyControl_Update service operation
- HSS-initiated QoS procedure, where the new APN-AMBR is sent using a GTP Modify Bearer Command message
These procedures trigger a forced change of the APN-AMBR on the FWA-UP using a PFCP Session Modification Request that updates the applicable QER IE. When successful, the MAG-c initiates the PGW-initiated QoS update procedure to signal the new APN-AMBR to the MME/HSS using a GTP Update Bearer Request message.
5G QoS attributes
In 5G mobile networks, the QoS flow is a key concept. The MAG-c interacts with the PCF to create and then signal QoS flows, along with corresponding default-bearer information, to the RAN (gNodeB), UPF, and the UE.
- The MAG-c
retrieves the subscribed values using the following parameters, in order of
precedence:
- from RADIUS, the 3GPP-GPRS-Negotiated-QoS-Profile attribute
- from the UDM, the 5G QoS profile and sessionAmbr information elements
- from the ADB, the QoS profile configured using the following
command
configure mobile-gateway profile authentication-database entry fixed-wireless-access default-qos-profiles subscribed-5gNote: The QoS profile must reference a profile configured using the following command.configure mobile-gateway profile qos-5g-profile
- The MAG-c
determines the authorized values using the following parameters, in order of
precedence:
- from the PCF, using the authSessAmbr and authDefQos information elements during
the Npcf_SMPolicyControl_Create service operation
The MAG-c signals the subscribed QoS values to the PCF in this operation, and the PCF replies with the final authorized parameters.
- if the session does not use PCF, or PCF failed but the session continues in
ap-continue mode:
from the ADB, the QoS profile configured using the following command
configure mobile-gateway profile authentication-database entry fixed-wireless-access default-qos-profiles authorized-5gNote: The QoS profile must reference a profile configured using the following command.configure mobile-gateway profile qos-5g-profile - from the subscribed QoS values retrieved in step 1
- from the PCF, using the authSessAmbr and authDefQos information elements during
the Npcf_SMPolicyControl_Create service operation
configure mobile-gateway profile qfi-mapping-profile 5qi-as-qfi configure mobile-gateway pdn qfi-mapping-profile
configure mobile-gateway pdn apn qfi-mapping-profile- It is not allowed to modify the 5QI for a QoS flow mid-session. This includes the default 5QI for the default QoS flow.
- It is not possible to use standard or vendor-specific 5QI values above 64.
When QoS flows are created, the MAG-c acting as the SMF signals the QoS flows and the corresponding parameters to the RAN (gNodeB), UPF, and the UE. Toward the RAN and UE this includes parameters that are typically not applicable to SMF or UPF and are passed through as they are; for example, averaging window.
Dynamic QoS based on PCC rules
When a session is provisioned with policy and charging control (PCC) rules, the MAG-c enforces QoS as specified in 3GPP TS 23.501 and TS 23.503. The MAG-c supports the following PCC rule parameters for QoS enforcement:
- precedence versus other PCC rules in case of overlapping packet classifiers
- list of service data flows (SDFs) that act as classifiers to associate packets with PCC rules. SDFs can contain the 5-tuple or the type of service (TOS) field classification, and can be bidirectional or unidirectional.
- 5G quality of service identifier (5QI) and allocation and retention priority (ARP) to determine the end-to-end 5G QoS characteristics
- indicator to bind the PCC rule to the default QoS flow, which is created based on the session level 5QI and ARP values. The 5QI and ARP values are ignored for the QoS flow binding.
- indicator to enable reflective QoS
- gate status to allow or disallow the PCC rule to forward traffic
- maximum bit rate (MBR) and guaranteed bit rate (GBR) values
- QoS characteristics specific to a radio access network (RAN) such as priority level,
averaging window, maximum data burst volume, and maximum packet loss rate. These are
passed as is to the RAN and act as overrides for the QoS characteristics associated
with the 5QI.Note: QoS characteristics for a standard 5QI are defined in 3GPP TS 23.503 table 5.7.4-1.
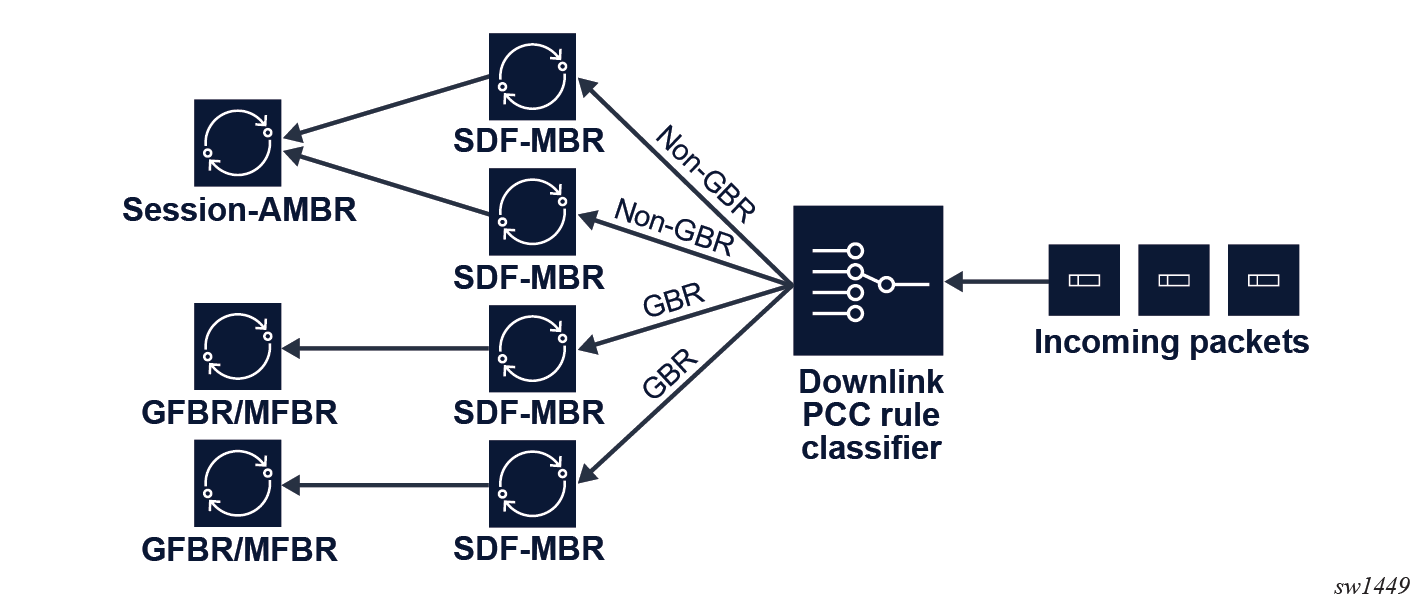
Based on the provided 5QI and ARP values and the default QoS flow binding, the MAG-c generates QoS flows as specified in 5G QoS attributes. For any GBR QoS flows, it sets the guaranteed flow bit rate (GFBR) and the maximum flow bit rate (MFBR) value to the sum of the GBR and MBR values of all PCC rules tied to that QoS flow.
- Downlink packets tied to a GBR flow are first subjected to the SDF MBR, and subsequently to the GFBR and MFBR.
- Downlink packets tied to a non-GBR flow are first subjected to the SDF MBR, and subsequently to the session aggregate maximum bit rate (AMBR).
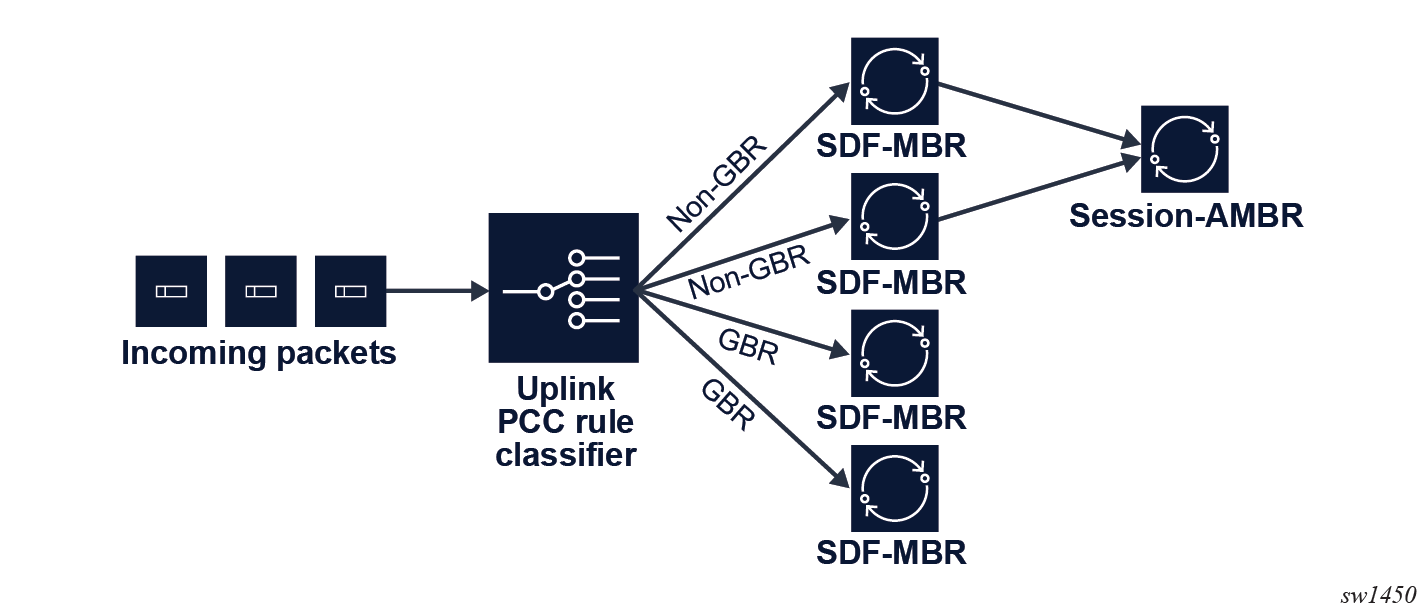
- Uplink packets tied to a GBR flow are only subjected to the SDF MBR because the RAN enforces the GFBR and MFBR.
- Uplink packets tied to a non-GBR flow are first subjected to the SDF MBR, and subsequently to the session AMBR.
The following figures show the rate enforcements.
- QoS flow identifier (QFI) marking
- reflective QoS identifier (RQI) marking
- differentiated services code point (DSCP) marking, if configured on the MAG-c
The MAG-c automatically generates a default any-to-any PCC rule that uses the session level 5QI and ARP in addition to any explicit per-session PCC rules. When the creation of the any-to-any rule is disabled, the MAG-c does not automatically install a default rule and drops any traffic that does not match a specific PCC rule.
Perform the following steps to disable the creation of the any-to-any PCC rule:
- Use the following command to enable 5QI to be used as the QFI
value.
configure mobile-gateway profile qfi-mapping-profile 5qi-as-qfi - Provision a PCC rule with the same 5QI and ARP as the session 5QI and ARP.
DSCP marking
In addition to applying base 4G and 5G QoS, Nokia’s FWA solution can also apply DSCP marking based on QCI/5QI and ARP values. The FWA-UP remarks the DSCP values as follows:
- In the uplink direction, the FWA-UP marks the DSCP value of the forwarded IPv4 and IPv6 PDU packets. This is useful for QoS treatment based on QCI/5QI in the data network beyond the FWA-UP.
- In the downlink direction, the FWA-UP marks the DSCP value of both the forwarded IPv4 and IPv6 PDU packets and marks the DSCP value of the outer GTP-u header. This is useful to honor 4G/5G QoS properties in the aggregation network between UP and RAN.
As shown in the following figure, in both directions statically preprovisioned QoS treatment is applied based on QCI/5QI and ARP via the DSCP values in Network Elements (NEs) that are typically not 4G or 5G QoS aware.
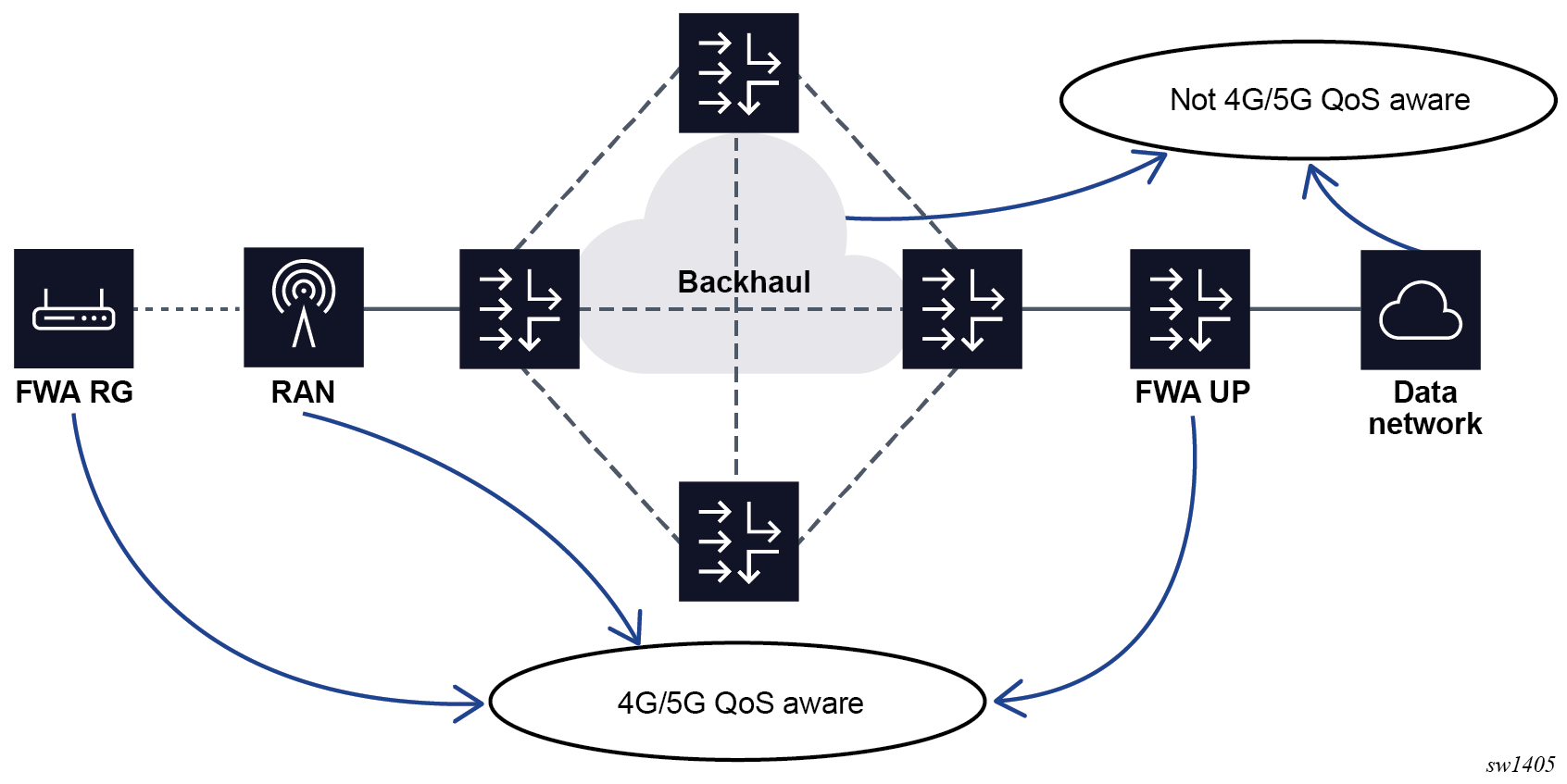
Do the following to apply DSCP marking on the UP:
- Use the following command to configure a QCI
policy.
configure mobile-gateway profile policy-options qci-policy - Use the following commands to configure per QCI and ARP combination, the DSCP value
in the uplink (in) and downlink (out)
directions and to disable DSCP preserve.Note: The no dscp-preserve command specifies that the MAG-c signals the configured DSCP values to the FWA-UP in PFCP messages. See the MAG-c CLI Reference Guide for more information about this command.
configure mobile-gateway profile policy-options qci-policy qci configure mobile-gateway profile policy-options qci-policy qci dscp configure mobile-gateway profile policy-options qci-policy qci no dscp-preserve - Apply the QCI policy in the following
context.
configure mobile-gateway pdn apn qci-policy
PAP/CHAP authentication
A mobile UE can send PAP/CHAP authentication credentials as a PCO option during the session setup signaling. When such a PCO option is received, the MAG-c uses these credentials in the authentication instead of the locally configured credentials.
- The PAP/CHAP username can be used for the relevant ADB match criteria. For RADIUS
authentication, the username has precedence over the configuration of the
user-name-format fixed-wireless-access format command in the
following
context.
configure mobile-gateway profile bng radius-authentication-profile - The PAP/CHAP credentials are reflected in RADIUS instead of the
password configured in the following
context.
configure mobile-gateway profile bng radius-authentication-profile
PAP/CHAP authentication is typically used for separate RG/UE models, where a PPP link is present between the RG and UE. PAP/CHAP authentication is performed over the link. The UE pretends successful authentication of PAP/CHAP and moves the session to the NCP state. The MAG-c gets a CHAP challenge and a CHAP response in PCOs. In cases where the PAP/CHAP based authentication on the MAG-c fails, the UE tears down the PPP session using the LCP terminate messages.
Session lifetime and held addresses
The session management procedures define the lifetime of an FWA session; for example, a GTP Delete Session Request message. An FWA session can exist without any stack being signaled to the client if deferred allocation is used. Stack timeouts do not drive session deletion. If a session management procedure deletes a session with active IP stacks, those stacks are by default released.
For an integrated RG/UE, this is not a problem because the RG/UE knows of the session failure and knows that IP stacks are lost.
For a separated RG/UE model, the UE can have forwarded those stacks to a RG. Depending on the RG/UE connection model, it is possible that the RG is not aware of the failure and keeps using assigned addresses until their signaled lifetimes expire.
configure mobile-gateway profile authentication-database entry fixed-wireless-accessWhen the hold time is configured, the MAG-c keeps a state for these addresses for the specified hold time. If the ODSA local address assignment allocated the addresses, the ODSA address hold time is automatically increased to the configured hold time. Other than that, there is no link between held addresses and the original allocation source of the addresses (for example, ODSA or AAA). For example, if a held address allocated by ODSA is removed, it is not explicitly released for ODSA. It needs to time out independently.
Held addresses are linked to the FWA session key pair (IMSI, APN). If a new session for the key of a held address is created, the held address is picked up and re-used. The interaction with specific address assignment methods is as follows:
- local address assignment (ODSA)
The new session requests the held address from ODSA. The request cancels any running ODSA hold time and ODSA links the address to the new session. In case ODSA cannot assign the address, the session setup fails; for example, ODSA was not the original allocation source of the held address.
- AAA
The held addresses are ignored and removed in favor of the AAA-signaled address.
Because held addresses do not interact with the original allocation method, Nokia recommends to only enable holding addresses when the address assignment source of a particular session is stable over session creation and deletion. If the address assignment source is not stable, session setups can fail or addresses can be hold for a long time. For example, consider a locally assigned ODSA address being put in the hold state for ten days. If the session is re-established but indicates an AAA address, the held address is not used and not released toward ODSA. The ODSA address keeps its ten day hold time and is not usable during that period.
PDN type selection
FWA sessions need an assigned PDN type, which can be ipv4, ipv6, or ipv4v6. During setup, an initial wanted PDN type is signaled as follows:
- GTP for 4G
- N1 NAS/UDM SDM for 5G
The PDN type is checked against the local configuration that is done with the following command.
configure mobile-gateway pdn apn pdn-typeThe PDN type acts as an allow-list. If the signaled PDN type does not match the configured PDN type, but the PDN types are compatible (for example, IPv4 is configured but IPv4v6 is signaled), MAG-c allows the FWA session and performs a downgrade to a compatible PDN type (for example, IPv4). If a downgrade is possible to both IPv4 and IPv6 (for example, both IPv4 and IPv6 are configured and IPv4v6 is signaled), by default MAG-c chooses IPv4, unless the pdn-type-preferred-IPv6 command is enabled.
To optimize IP address usage, only ODSA addresses that are applicable for the selected PDN type are allocated. For example, if a local IPv4 pool and a local IPv6 PD pool are provisioned, and the PDN type is IPv6, no IPv4 address is allocated.
Similarly, if local or AAA based address assignment allocates addresses for only one stack, the PDN type is downgraded to the type matching that stack if applicable.
Mobility and idling
FWA supports mobility and idling procedures, and tracks location.
FWA supports the following mobility and idling procedures:
- mobility procedures — X2-based handover (4G) and Xn-based handover (5G)
- idling procedures — S1 release (4G) and AN release (5G)
- reactivation and paging procedures — UE triggered service request (4G+5G) and network triggered service request (4G+5G).
Most of these procedures require interoperability with standard RAN deployments, which assumes these procedures are available by default. Handover procedures provide RAN resiliency when a UE or RG uses them to switch to a new antenna if its current antenna fails.
Most of these procedures require updating the FWA-UP to handle the new traffic rules. This update is done using the following PFCP Session Modification Request messages.
- For mobility procedures, the F-TEID field in the Forwarding Parameter IE is updated.
- For idling procedures, the forwarding rule is removed and replaced by a buffering rule that instructs the FWA-UP to buffer packets. The FWA-UP is also instructed to notify the MAG-c when buffering a packet such that the MAG-c can start paging procedures.
- When completing reactivation procedures, the buffering rule is removed and replaced by a forwarding rule with an F-TEID. Buffered packets are sent to the new F-TEID by the FWA-UP.
Location tracking
The MAG-c tracks and learns the location of an FWA session using procedures such as X2/Xn-based handover, UE-triggered service request, location reporting, and tracking area update. For 4G, the MAG-c requests the MME to report location if the MME signals the "Change Reporting Support Indication" flag and if the BNG charging profile is enabled to track the location. For 5G the MAG-c does not subscribe to specific location updates and only learns location changes as part of other procedures.
When RADIUS location tracking is enabled, an Interim Update message is triggered whenever the user location changes. The user location is sent in the 3GPP-User-Location-Info attribute.
Use the following commands to configure location tracking for RADIUS:
- Use the following command to enable location
tracking.
configure mobile-gateway profile charging bng-charging radius session update-triggers user-location-change - Use the following command to send the user location in the 3GPP-User-Location-Info
attribute.
configure mobile-gateway profile charging bng-charging radius session include-attribute user-location-info
Headless mode for FWA
Headless mode as described in Headless mode is partially supported for FWA sessions. When the connection between the FWA-UP and the MAG-c fails, the currently installed sessions on the FWA-UP remain unaffected and continue forwarding data.
However, when new FWA procedures are initiated, such as a mobility, idling, or reactivation, the headless mode procedure fails and immediately terminates the session on the MAG-c. Terminated FWA sessions do not wait for the FWA-UP confirmation as described in Headless mode, but release the addresses back to the ODSA while in headless mode. To prevent a FWA-UP from announcing these released addresses, Nokia recommends setting the path restoration time lower than the hold time configured for any ODSA pools used by FWA sessions.
configure mobile-gateway profile pfcp pfcp-profile path-restoration-time4G and 5G NSA option 3 sessions
Basic FWA network shows the elements involved in a simple FWA network with a MAG-c operating as a combined PGW-C and SGW-C, and a FWA-UP operating as a combined PGW-U and SGW-U. The following figure shows the communication between the elements with the interface name if applicable and for the BNG relevant interfaces, the protocol being used. The high-level role of the MME, SGW, and PGW elements is as follows:
- MME
The MME orchestrates the basic connectivity of the UE and how this connectivity evolves during the lifetime of a session (for example, mobility, idling, paging).
- SGW
The SGW provides advanced data forwarding functionality such as buffering packets for idling UEs or providing a mobility anchor for inter-eNodeB mobility. Often this functionality is combined with a PGW in a single network element. In a CUPS environment the SGW is split in an SGW-C and an SGW-U element.
- PGW
The PGW provides PDN connectivity to an IP network. It can perform additional authorization to PDN-specific AAA servers; for example, authorization using the RADIUS protocol. It enforces charging functionality. In a CUPS environment the PGW is split in a PGW-C and a PGW-U element.
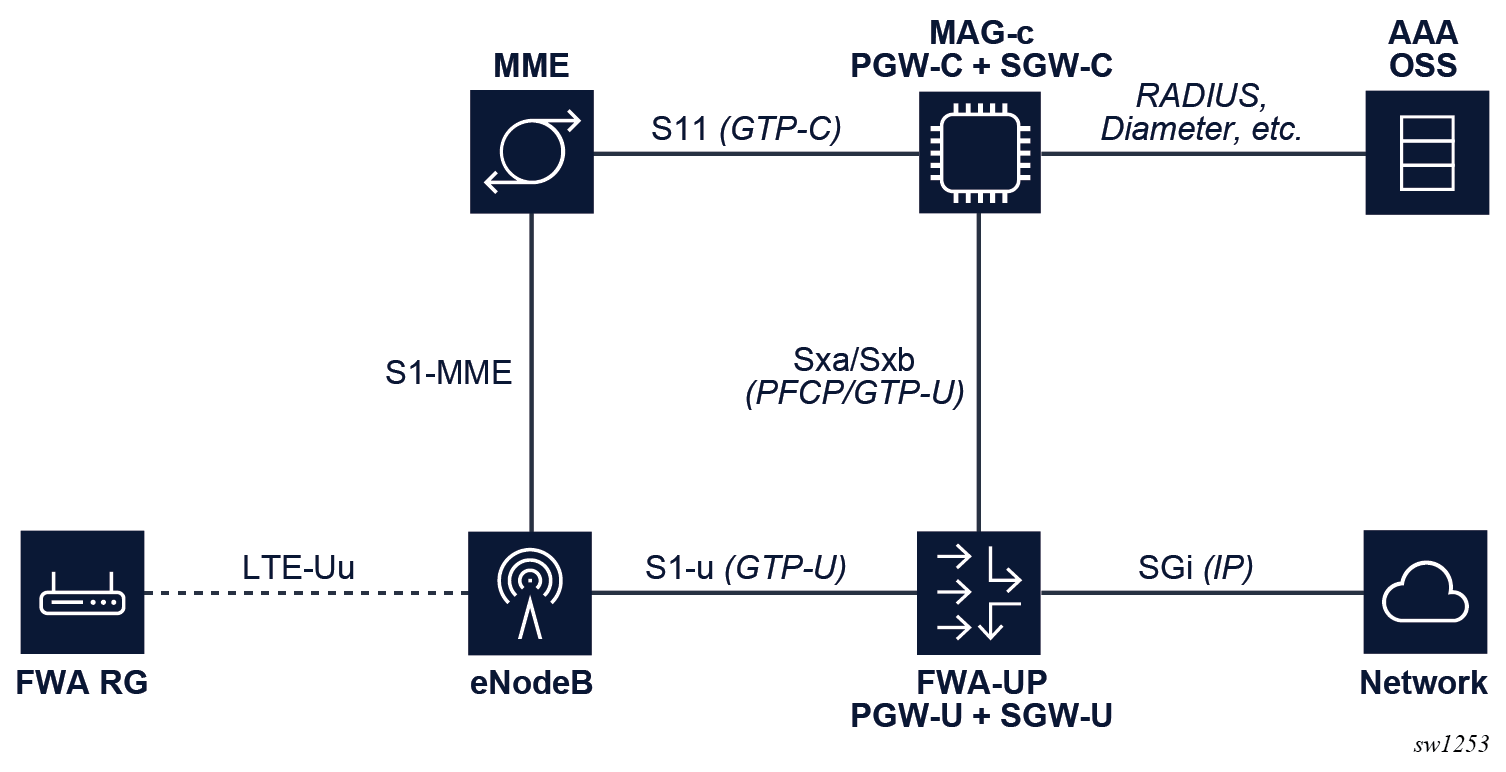
To enable 4G FWA sessions for a combined gateway, the GTP-C S11 and S5 interfaces need to be enabled on the MAG-c. The S5 interface is between the SGW and PGW and is internal for a combined gateway.
- To enable the S5 interface, use the gtp-c command in the
following context.
This interface is not necessarily used to terminate packets, but its IP must match the “PGW S5/S8 Address for Control Plane or PMIP” address that is signaled in the GTP Create Session Request.configure mobile-gateway pdn s5 interface - To enable the S11 interface, use the gtp-c command in the
following context.
This interface transfers the GTP-C packets.configure mobile-gateway pdn s11 interface - To identify the L3 service on the FWA-UP where the GTP-U packets are received, configure the
interface-realm parameter of the
gtp-c command in the following
contexts.
Both realms must be configured the same.configure mobile-gateway pdn s11 interface configure mobile-gateway pdn s5 interface - Configure the EPC node name using the epc-node command in the configure mobile-gateway pdn context. The MCC and MNC value under this node must match the MCC and MNC of the IMSI for new FWA sessions. Otherwise, the session is seen as roaming, which is not supported for FWA.
The following figure shows an example of a 4G FWA session setup.
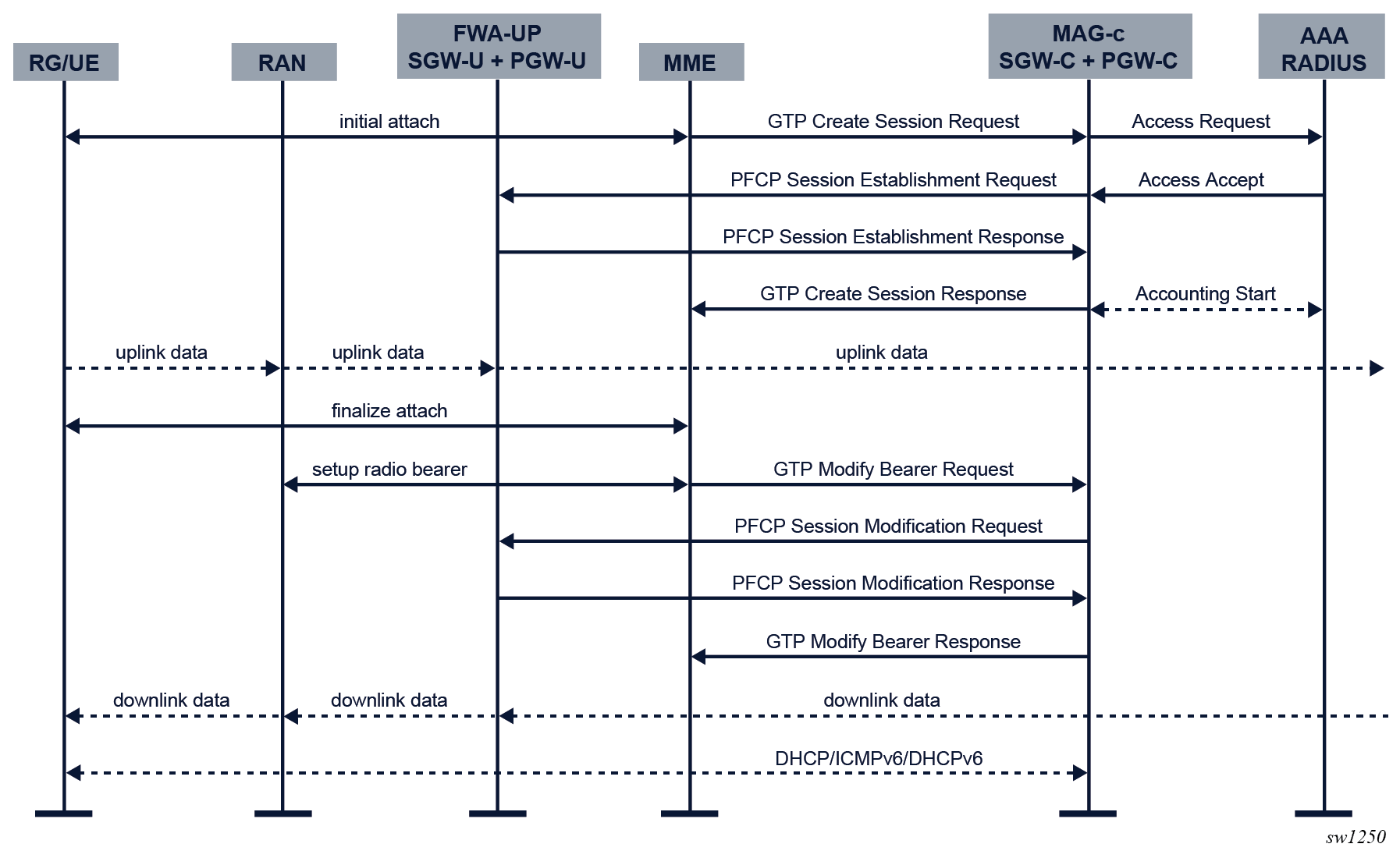
- An initial attach sequence is initiated between the UE and the MME, which leads
to a GTP Create Session Request message toward the MAG-c. This message contains three sets of parameters:
- protocol-specific data to initiate the stateful control session between the MME and the MAG-c
- the required identification and subscription parameters to initiate
session management for the PDN sessionNote: These parameters always include IMSI, IMEI, APN, PDN type, and can be extended with additional values such as MSISDN, static IP addresses, and APN-AMBR.
- PCOs sent from the client; for example, a request for DNS servers, a request for deferred allocation, or PDN-specific authorization using encapsulated PAP/CHAP messages
- Based on the signaled APN, the MAG-c looks up the APN under the following context.
To enable FWA functionality, the APN must be configured with an FWA node in the no shutdown state using the fixed-wireless-access command in the following context.configure mobile-gateway pdn apn
The authentication flow of the FWA node configured using the authentication-flow command in the following context is used to authenticate the session.configure mobile-gateway pdn apn
FWA-specific ADB match criteria or RADIUS include attributes can be used.configure mobile-gateway pdn apn fixed-wireless-access - The MAG-c selects a FWA-UP and sets up a PFCP session. The PFCP session carries the full session data, including all BNG-specific parameters. At this point, the RAN has not yet allocated a downlink GTP-U F-TEID, so the downlink data packet is buffered. For uplink traffic, the FWA-UP allocates an F-TEID and sends it to the MAG-c.
- The MAG-c sends a GTP Create Session Response message to the MME. This message includes the uplink GTP-U F-TEID as allocated by the FWA-UP. It includes the IPv4 address if one was allocated and signaled via NAS. The MME completes the attach toward the UE and sets up the radio bearers toward the RAN. At this point, uplink data traffic can be sent.
- As part of the radio bearer setup, the RAN allocates a downlink GTP-U F-TEID. The MME signals the downlink to the MAG-c using a GTP Modify Bearer Request Message. The MAG-c forwards it to the FWA-UP using a PFCP Session Modification Request message which changes the downlink rules from buffering to forwarding with the provisioned F-TEID. The FWA-UP acknowledges the PFCP message to the MAG-c. The MAG-c acknowledges the GTP message to the MME. At this point, downlink traffic is possible.
- The data layer connectivity is ready, but it is possible that not all IP addresses allocated to the RG are signaled to the UE. The addresses are signaled over the data connection using the DHCP, ICMPv6, and DHCPv6 protocols.
5G standalone sessions
Basic 5G FWA network shows the elements involved in a basic 5G FWA network with a MAG-c operating as an SMF and an FWA-UP operating as a UPF. The figure highlights the direct communication between the interface elements and the protocols used, if applicable. The figure does not include the N1 (NAS signaling from and to the UE) and N2 (RAN control plane) interfaces because these interfaces may terminate on both AMF and SMF depending on the type of control plane signaling.
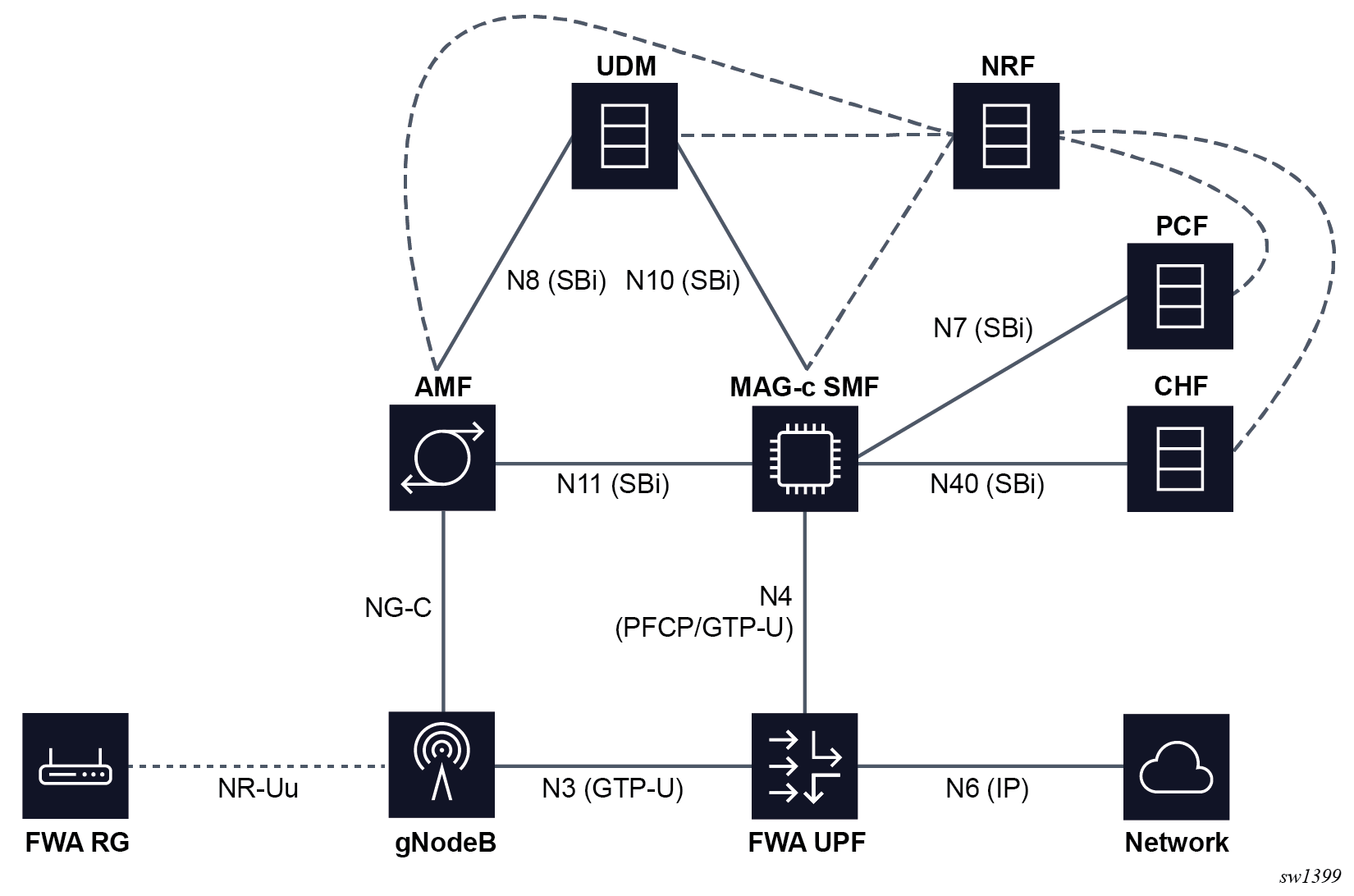
The following are high-level descriptions of the role of each function:
-
AMF
The Access and Mobility Function (AMF) orchestrates the basic connectivity of the UE and how this connectivity evolves during the lifetime of a UE (for example, mobility, idling, and paging).
-
SMF
The Session Management Function (SMF) maintains 5G sessions. It connects to other functions such as AAA, UDM, PCF, and CHF to retrieve and manage subscription, policy (including QoS), and charging data for an active session. The SMF provides a similar function to a SGW-C + PGW-C in 4G, however, in contrast to 4G it performs all the signaling for session management directly. For example, the SMF constructs all N1 (NAS) session-management messages for the UE directly, as compared to 4G, which uses the MME to proxy relevant data over GTP to the UE.
-
UDM
The Unified Data Management (UDM) provides subscription data for a user. This subscription data is queried by multiple functions, for example, the AMF retrieves access and mobility subscription data and the SMF retrieves session management subscription data. Additionally, functions such as the SMF register themselves with the UDM to indicate they are an active function for a specific UE or session.
-
NRF
The Network Repository Function (NRF) keeps a repository of all 5G functions. When a function becomes available, for example the SMF, it registers itself with the NRF. Subsequently, other functions such as the AMF can query the NRF to discover the functions with which they need to communicate.
-
PCF
The SMF queries the Policy Control Function (PCF) at setup to retrieve policy information applicable to a session. This policy information can be QoS, ACL, or charging related. Some policy information is directly applied by the SMF, but most is passed to other functions to enforce, such as the UPF, gNodeB, UE, or CHF. The PCF can also request updated policies on some triggers, such as location changes or revalidation timeouts and make direct requests for a policy update without requiring a trigger.
-
CHF
The Charging Function (CHF) is used for both online and offline charging. In both cases CHF manages charging based on Rating Groups (RGs), which can either represent an entire session or a subset of traffic. For offline charging, the CHF requests to signal statistics upon reaching a specific time or volume threshold; however, it does not enforce any limits. For online charging, the CHF additionally enforces quota limits that trigger the SMF and UPF to take immediate action without communicating to the CHF; for example, to stop forwarding for the RG.
-
UPF
The User Plane Function (UPF) provides connectivity to an IP network, enforcing dataplane policies such as QoS and ACLs, reporting statistics, and quotas.
Enabling 5G FWA sessions requires configuration of the following:
- SMF PDUSession services
- AMF client communication services
- 5G UDM function
- FWA sessions
SMF PDUSession service server configuration
To enable 5G FWA sessions, do the following:
- Use the following command to configure an SMF PDUSession service server instance on
the MAG-c, to handle service calls from the AMF to the
SMF.
configure mobile-gateway pdn sba-server-services nsmf-pdusession - Configure the service instance with the following required elements:
- an interface on which the MAG-c listens for incoming connections from the AMF
- the N3 interface realm that is sent to the FWA UP as the realm (service) where N3 GTP-u tunnels are terminated
Note: When 4G and 5G interworking is required, configure the interface-realm option for the S11 interface using the following command.configure mobile-gateway pdn s11 interface gtp-cSee 4G and 5G NSA option 3 sessions for more information about configuring the S11 interface.
-
Optionally provision the following for the server instance:
- An HTTP2 profile to influence generic HTTP/2 and SBI parameters; see HTTP/2, OpenAPI, and Python for more details.
- An API prefix to be part of the service URI; see URI construction for more information about how URIs are constructed.
- An FQDN to identify the service by other NF peers. For example, the AMF can use this when constructing URIs or when discovering the SMF using DNS.
- Multiple attributes to send to the NRF when registering the service:
- NF domains lists using the following
command.
configure mobile-gateway pdn sba-server-services nsmf-pdusession allowed-nf-domains-list - PLMNS using the following
command.
configure mobile-gateway pdn sba-server-services nsmf-pdusession allowed-plmns - slices using the following
command.
configure mobile-gateway pdn sba-server-services nsmf-pdusession allowed-slicesSee NF registration for more information about how services and related attributes register with the NRF.
- NF domains lists using the following
command.
- Use the following command option to enable the service
instance.
configure mobile-gateway pdn sba-service-realm server-service service-instance
AMF client communication service configuration
In addition to the SMF server instance, you must configure the AMF communication client service. This service generates service calls from the SMF to the AMF, to forward N1 or N2 messages to the UE or RAN.
To configure the AMF client service, do the following:
- Use the following command to configure the AMF
service.
configure mobile-gateway pdn sba-client-services amf-client namf-comm -
Use the following command to configure an interface for the service instance that the MAG-c uses to communicate with the AMF.
configure mobile-gateway pdn sba-client-services amf-client namf-comm interface - Optionally configure the following for the client service instance:
- An FQDN to identify the service by other NF peers. For example, when generating callback functions the SMF can use the FQDN in the URI, rather than the IP address; see URI construction for more information about how URIs are constructed.
- An NF ID list to specify which NF instances can be used for the AMF service; see Enabling discovery based on a local NF ID list for more information. This command is required if the AMF is not dynamically discovered using NRF.
- An HTTP2 profile to influence generic HTTP/2 and SBI parameters; see HTTP/2, OpenAPI, and Python for more information.
- An AMF profile to handle AMF failure handling; see section Failure handling for more information.
- An N1 profile configured using the following command.
configure mobile-gateway profile n1-profileUse the following commands to configure the N1 profile to influence N1 signaling:
- The N1 profile timer governs retransmit behavior for an N1 PDU
SESSION MODIFICATION COMMAND
message.
configure mobile-gateway profile n1-profile n1-t3591 - The N2 profile timer specifies retransmit behavior for an N1 PDU
SESSION RELEASE COMMAND
message.
configure mobile-gateway profile n1-profile n1-t3592 - The cause-code commands in the following context
specify which error codes are signaled to the UE and AMF for several
session removal and rejection
cases.
configure mobile-gateway profile n1-profile
- The N1 profile timer governs retransmit behavior for an N1 PDU
SESSION MODIFICATION COMMAND
message.
- This service generates service calls from SMF to AMF, to forward N1 or N2 messages
to the UE or RAN. Use the following command option to subsequently enable this
service
instance.
configure mobile-gateway pdn sba-service-realm client-service service-instance
UDM function configuration
In 5G, the MAG-c acting as the SMF directly communicates with the UDM function to retrieve session subscription data, such as subscribed default QoS. The MAG-c subscribes to any subscription data changes to apply these changes.
This differs from 4G where a similar function is provided by the HSS, but the PGW does not retrieve this context directly. In 4G, the MME retrieves the subscription data from HSS and signals this via GTP messages to the PGW.
Enabling the UDM SDM client service
The UDM SDM client service enables UDM-based subscription retrieval.
-
Configure a UDM SDM client service.
configure mobile-gateway pdn sba-client-services udm-client nudm-sdm -
Configure an interface for the service instance over which the MAG-c communicates with the UDM.
configure mobile-gateway pdn sba-client-services udm-client nudm-sdm interface -
Configure the following optional parameters:
- An FQDN to identify the service by other NF peers. For example, when generating callback functions, the MAG-c can use the FQDN in the URI, instead of the IP address. See URI construction for more information about how URIs are constructed.
- An NF ID list to specify NF instances that can be used for the UDM function. See Enabling discovery based on a local NF ID list for more information. This configuration is required if the UDM is not dynamically discovered using NRF.
- An HTTP2 profile to influence generic HTTP/2 and SBI parameters. See HTTP/2, OpenAPI, and Python for more information.
- A UDM SDM profile that contains parameters on how to handle UDM failure handling. See Failure handling for more information.
-
Enable this service instance.
configure mobile-gateway pdn sba-service-realm client-service
Enabling the UDM UECM client service
The UDM UECM (UE Context Management) service is used to register the MAG-c as an SMF providing service for the UE.
-
Configure a UDM UECM client service.
configure mobile-gateway pdn sba-client-services udm-client nudm-uecm -
Configure an interface for the service instance over which the MAG-c communicates with the UDM.
configure mobile-gateway pdn sba-client-services udm-client nudm-uecm interface - Configure the optional parameters as described for the UDM client service. See Enabling the UDM SDM client service.
-
Enable this service instance.
configure mobile-gateway pdn sba-service-realm client-service
Configuring a 5G QoS profile for the UDM failure handling
UDM communication supports generic SBI failure handling as specified in Failure handling. When the ap-continue action is used, session setup continues without SDM data, an SDM subscription, or a UECM registration. However, a locally configured 5G QoS profile must be present to provide fallback default QoS values. If this profile is not present, session setup fails anyway.
-
Configure a new 5G QoS profile.
configure mobile-gateway profile qos-5g-profile - In the 5G QoS profile, configure the 5qi, arp, dl-ambr, and ul-ambr parameters as needed.
-
Apply the profile in an ADB entry that is used for the 5G FWA sessions. For
more information about matching sessions to ADB entries, see BNG EP and ADB lookup.
configure mobile-gateway profile authentication-database entry fixed-wireless-access qos-5g-profile
FWA session setup for 5G
Typically a UDM (see UDM function configuration) and PCF (see PCF-based policy management) are configured for a 5G session, in addition to the SMF PDUSession service and the AMF client communication service. The following figure shows the basic 5G FWA session setup when all these components are configured.
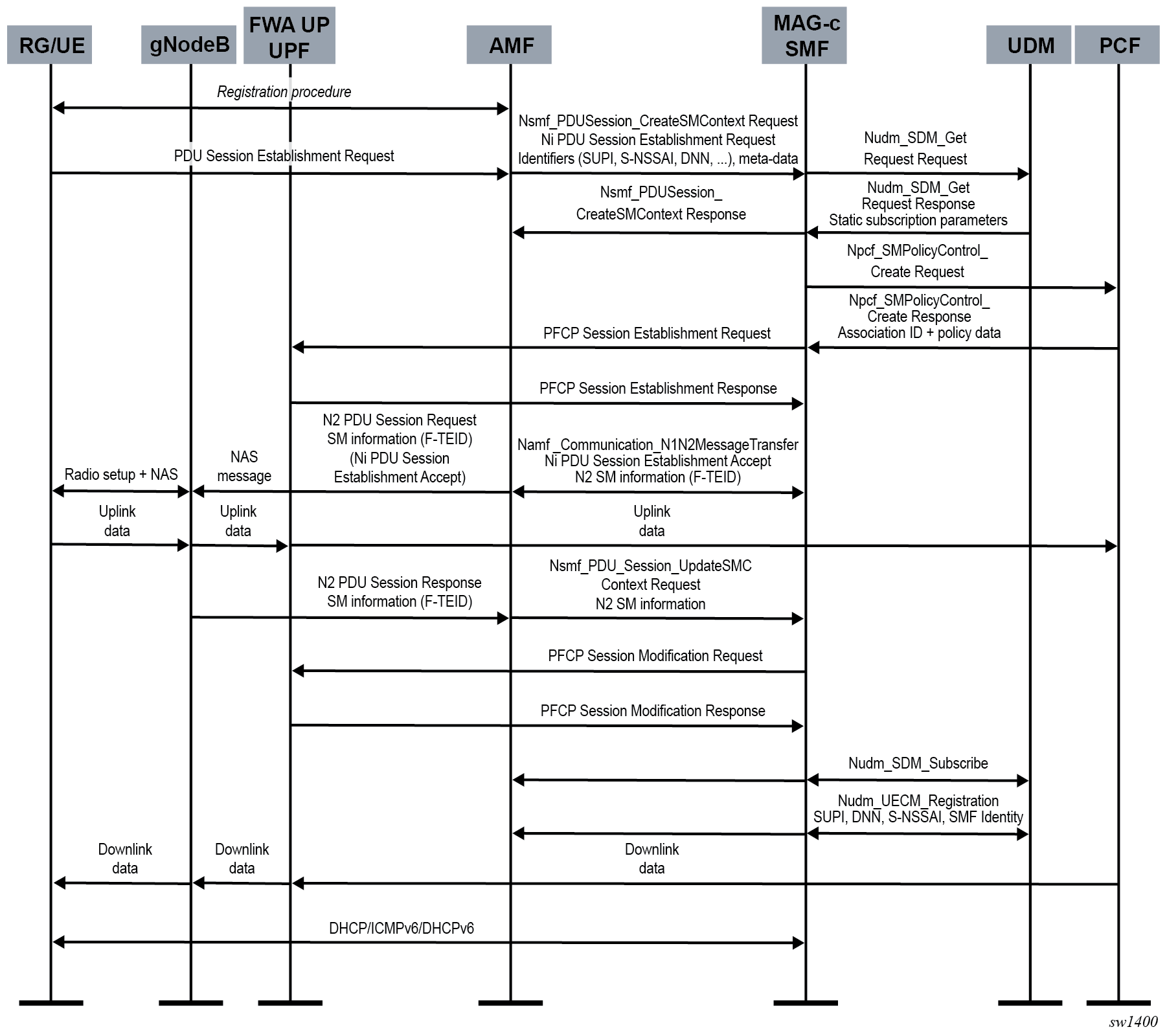
The following describes the message flow and actions to set up a 5G FWA session:
- An initial registration sequence is initiated between the UE and the AMF. This procedure is orthogonal to the SMF because it does not involve any session-management functionality. Upon completion of the registration, an FWA UE requests creation of a PDU session to forward traffic. To do this, it generates a PDU Session Establishment Request NAS message and signals this to the AMF. Upon receipt of this message, the AMF may obtain additional subscription parameters from the UDM and determines which SMF should handle the session based on local configuration. For example, a specific FWA slice (S-NSSAI) could be used, with which the SMF registers (see NF registration) and the AMF discovers this SMF by calling the Nnrf_Discovery service that has the S-NSSAI configured in the query parameters. Upon discovering the SMF, the AMF creates a session management resource on the SMF by calling the Nsmf_PDUSession_CreateSMContextRequest service operation. In this it includes the PDU Session Establishment Request NAS message as it is, and any additional metadata it can provide, for example the DNN.
-
Upon receiving the Nsmf_PDUSession_CreateSMContextRequest the MAG-c uses the signaled DNN to look up the configured APN/DNN in the following context.
configure mobile-gateway pdn apnNote: To enable 5G FWA functionality, the APN must be in the enabled state and configured with an FWA node using the following command.configure mobile-gateway pdn apn fixed-wireless-accessIf a UDM client service is configured (see UDM function configuration ), a Nudm_SDM_Get Request service call is executed to obtain subscription parameters such as session AMBR, default 5QI, default S-NSSAI, and so on.
If the UDM is not configured, these parameters must either be provided by the PDU Session Create message, or locally configured on the MAG-c. Subsequently, the authentication flow of the FWA node (configured using the following command) is used to authenticate the session.
configure mobile-gateway pdn apn authentication-flowFWA-specific ADB match criteria or RADIUS include attributes can be used. Match criteria use data from the PDU Session create call and the UDM. For example, if an S-NSSAI is not provided in the create call, but a default S-NSSAI is provided in UDM subscription data, this is matched.
- After the UDM and authentication flow is completed, the MAG-c answers the call from the AMF Nsmf_PDUSession_CreateSMContext. This creates the session context in the AMF only; it does not yet include an answer to the UE-originated PDU Session Establishment Request message.
- Optionally, after the UDM and authentication flow completes, the MAG-c can obtain policy data from a PCF. See PCF-based policy management for more information about policy management and the PCF service.
- When all authentication and policy management is completed, the MAG-c selects an FWA-UP and sets up the corresponding PFCP session that carries the full session data, including all BNG-specific parameters. The RAN (gNodeB) has not yet allocated a downlink GTP-U F-TEID, so the downlink data packet is buffered. For uplink traffic, the FWA-UP allocates an F-TEID and sends it back to the MAG-c. See the 7750 SR and VSR BNG CUPS User Plane Function Guide for information about the BNG CUPS UPF.
- The MAG-c acknowledges the UE-originated PDU Session Establishment Request message by generating an N1 PDU Session Establishment Accept message. It also generates an N2 SM Information message which is sent to the RAN (gNodeB), including the F-TEID it received from the FWA-UP. Both messages also include any policy QoS rules applicable to either the UE or RAN. It includes these messages in a Namf_Communication MessageTransfer service call toward the AMF. The AMF in turn creates an N2 PDU Session Request call to the RAN to create context on the RAN, including the N2 SM Information and N1 PDU Session Establishment Accept message generated by the SMF. The RAN and UE finalize the radio resources setup. The uplink data can now flow.
- The RAN acknowledges the session context creation using an N2 PDU Session Response message to the AMF. In this message it also includes an N2 SM Information message with its F-TEID for downlink data, which the AMF forwards to the MAG-c using the smf_PDU_Session_UpdateSMContext service. The MAG-c forwards the F-TEID to the FWA-UP using a PFCP Session Modification Request message. This changes the downlink rules from buffering to forwarding with the provisioned F-TEID. The FWA-UP acknowledges the PFCP message to the MAG-c, which in turn acknowledges the smf_PDU_Session_UpdateSMContext call. Downlink traffic is now possible.
- If the UDM is enabled, the MAG-c registers itself for subscription updates for this session context using the Nudm_SDM_Subscription service call. Additionally, it also registers itself as the active SMF for this UE session using the Nudm_UECM_Registration service call.
- The data layer connectivity is now fully ready, although it is possible that not all IP addresses allocated to the RG are signaled to the UE. The addresses are signaled over the data connection using the DHCP, ICMPv6, and DHCPv6 protocols as needed. See Address signaling methods and deferred allocation for more information.
5G slicing
In 5G networks, a slice identifies an end-to-end logical network, from the UE to the network, on top of the shared physical infrastructure. The user can pick the physical or virtual components on a per-slice basis. This is a very flexible and powerful concept that can be used for many purposes. For example, FWA can be expressed as a single slice with dedicated FWA SMF and FWA UPF components.
MAG-c acting as the SMF is not involved in the slice-selection function itself. However, when selecting a peering NF instance via NRF, the MAG-c can use S-NSSAI as a query parameter to discover only peers associated with the selected slice. The MAG-c also passes the S-NSSAI to any peers, such as the UDM, PCF, or CHF, which require the MAG-c S-NSSAI to identify the services to offer. Finally, the SST and SD part of the S-NSSAI can be used as a match parameter in the authentication database, which allows the S-NSSAI to influence a wide set of parameters on itself.
5G-4G interworking
Interworking of 5G-4G allows seamless mobility between a 5G and a 4G radio coverage area.
Overview of interworking between 5G-4G
Interworking between 5G-4G is done using the MAG-c CPF and the 7750 SR UPF call-flow procedures and the N26 interface, which allows seamless mobility between 5G and 4G systems.
Interworking between 5G-4G is performed with support for call-flow procedures using the following:
- a combined SMF and SGW-C/PGW-C for the control plane function (MAG-c)
- a combined UPF and SGW-U/PGW-U for the user plane function (7750 SR)
The 5G-4G interworking is supported with the N26 interface only. N26 is the interface between the AMF and the MME that enables seamless mobility between 5G and 4G systems.
The combined SMF and SGW-C/PGW-C (MAG-c) also supports serving of 4G-only UEs (UEs without 5GS NAS support), while using 5G SBI (N7 and N40) with the PCF and CHF.
To configure the MAG-c for 5G-4G interworking, the following is required:
- To facilitate discovery of the MAG-c for sessions that require 4G interworking support, the PGW FQDN must be
configured for use in the NF profile during NF registration, and for update to the
NRF. Use the following command to configure the PGW
FQDN.
configure mobile-gateway pdn 1 nf-profile-attributes pgw-fqdn - 5G SBI interface support is required for UEs without 5GS NAS support (4G LTE). Use
the following command to configure the 5G SBI interface
support.
configure mobile-gateway pdn sba-client-services converged-interface-support pdu-session-id-base - The serving node IP address that the PGW sends to the various interfaces for
combined SGW/PGW sessions must be configured to send the MME IP address or the SGW
IP address. Use the following command with the corresponding option to configure the
MME or
SGW.
configure mobile-gateway pdn serving-node-for-combo-sessions - Instead of a trigger from a peering node (for example, the PCF) on a call-flow
failure because of a handover or TAU in progress, a retry time and delay are
required for a local retry. The call procedure retry is supported for the procedures
initiated by the SMF/PGW while the handover or TAU is in progress. The retry delay
specifies the duration the SMF/PGW must wait for the next retry attempt after the
TAU/HO is completed. Use the following command to configure these
settings.
configure mobile-gateway pdn call-procedure-retry
Bearer and QoS mapping between 5G-4G
In 5G-4G interworking, the bearer and QoS parameter-mapping mechanisms for a 5G-capable UE depend on the access via 4G/LTE or 4G or 5G handover.
If a 5G-capable UE initially attaches via 4G/LTE access, or moves to 4G/LTE access because of a handover from 5G, the following bearer and QoS parameter mappings apply:
- Mapping of QoS parameters and PDU session takes place during PDN connection establishment via the S11 interface.
- The dedicated bearer is currently not supported. As the UE moves between 4G and 5G access, bearer mapping is handled without support for dedicated bearer. For example, the non-GBR and the GBR QoS flow on 5G is rejected.
- The combined SMF and SGW-C/PGW-C maps the EPS QoS parameters to 5GC QoS parameters; for example, QCI-1=5Q1, QCI-5=5QI-5.
- The 5G UE allocates the PDU session ID to the PDN connection and sends it in the PCO to the PGW-C or SMF. The UE stores the received 5G QoS rules to use when it moves to 5G access.
- 5G QoS parameters (session AMBR, QoS rules (TFT), QoS flow descriptions, and S-NSSAI) corresponding to the PDU connection are sent to the UE in a PCO, while the UE is anchored via 4G access.
If a 5G-capable UE moves to 5G access because of a handover from 4G, the following apply:
- Mapping of the QoS parameters and the bearer ID takes place during the PDU session and GBR flow establishment via the N11 interface.
- The combined SMF and SGW-C/PGW-C maps the 5GS QoS parameters to the EPS QoS parameters; for example, 5QI-1=QCI-1, 5QI-5=QCI-5.
- The AMF manages the bearer ID allocation and the UE/MM context mapping.
SMF support for model D communication
In 5G Service Based Architecture (SBA), the model D method supports indirect communication via a service communication proxy (SCP) that mediates between the NF consumer and producer.
Implementation overview
In the model D method of indirect communication, the SCP is deployed between the NF consumer and the NF producer. The SCP performs the discovery of the NF producer via the NRF. After discovering and selecting the NF producer, further communication between the consumer and the producer only takes place via the SCP. There is never direct communication between the NF consumer and the NF producer while using the model D method.
When the SCP is deployed between the SMF and the UDM, the SMF acts as the NF consumer and the UDM acts as the NF producer. The SMF adds the NF discovery parameters in the HTTP header and the SCP executes the actual NF discovery with the NRF. This is also known as the delegated-discovery method.
SCP client configuration
The SCP client configuration defines the communication model. Use the commands in the following context to configure the SCP client settings:
configure mobile-gateway pdn sba-client-services scp-clientSCP failure handing
The SMF can use the communication model D with an option to fallback to model A, or assume-positive response in the event of a failure from the SCP. The SCP failure handling is triggered if the SCP rejects the request or it does not respond. In the case of a failure between the SMF and the SCP, the client-service configuration defines the communication model and the optional fallback mechanism.
configure mobile-gateway pdn sba-client-services udm-client nudm-sdm mode
configure mobile-gateway pdn sba-client-services udm-client nudm-uecm modeSCP load distribution
The MAG-c supports configuration of active load balancing across multiple SCP peers to enable SMF communication via multiple SCP nodes in parallel.
The SMF can communicate via multiple SCP nodes in parallel. Active load balancing is supported across multiple SCP peers such that the load is evenly distributed across all the peers. In the case of a failure of one SCP peer, the impacted sessions are redistributed to the remaining SCP peers.
Load balancing is implemented by default, based on the number of SCP addresses configured for the NF ID list profile that is referenced in the SCP client configuration. The load is distributed amongst the configured SCPs per service.
Load control, overload control, and congestion mitigation
In the MAG-c system, the load and overload control mechanisms are distinct but complementary concepts that help manage the flow of traffic for subscriber sessions. Load control uses preventive approaches to help avoid overload conditions. For sessions that are experiencing overload conditions, overload control enables the MAG-c node to gracefully reduce traffic for the existing sessions. In addition, the MAG-c provides support for node-level congestion mitigation.
Load control configuration guidelines
Load control is an overload prevention concept. It enables the originator node (for example, SGW-C + PGW-C or SMF) to send its load information to a consumer node (for example, the MME or the AMF). During the session setup, the consumer node uses the load information it receives from multiple originator nodes to select nodes for load balancing the session across all the nodes, according to their effective loads.
Use the following command to enable GTP-C load control.
configure mobile-gateway pdn load-control enable-gtp-load-controlTo support load control with 4G or 5G NSA, the originating node sends the Load Control Information (LCI) IE in the GTP-C messages to the consumer node. The MAG-c can send GTP-C load control information in every nth GTP-C message, or on every x percentage load change.
The load metric reported in the LCI represents the current load level of the MAG-c node as a percentage, within the range of 0 to 100, where 0 means no load and 100 means the maximum or 100% load (no further load is desirable).
Use the following command to configure the GTP-C load control settings based on the percentage of load change.
configure mobile-gateway pdn load-control load-change-triggerUse the following command to configure the GTP-C load control settings to send the load control information in every nth message.
configure mobile-gateway pdn load-control nth-message To support indirect load reporting to the consumer nodes, the producer node updates the NRF with its local load information. The load reported by the producer (originating) node to the NRF is made available to the consumer node during node selection. The consumer node can load balance the signaling load by selecting a producer node that has a lower load compared to a similar node with a higher load. This method is used for load control for SBI interfaces only.
Use the following command to enable SBI load reporting.
configure mobile-gateway pdn enable-sbi-load-reportingOverload control configuration guidelines
Overload control is an overload mitigation concept. It enables an originator node (SGW-C + PGW-C, SMF, MME, or AMF) that is overloaded, or at risk of becoming overloaded, to gracefully reduce the incoming signaling. The originator node is in an overload state when it operates beyond its signaling capacity, resulting in diminished performance and impacting the handling of incoming and outgoing traffic.
Overload control configuration and examples
The MAG-c overload control mechanism supports traffic reduction in overload conditions by instructing the consumer node (MME, AMF) to reduce the volume of traffic it is sending for existing sessions.
Use the following command to enable GTP-C overload control. This automatically enables default threshold and traffic-reduction values for the different overload levels.
configure mobile-gateway pdn overload-control enable-gtp-overload-controlTo support overload control with 4G or 5G NSA, the overloaded originator node sends an Overload Control Information (OCI) message to inform the consumer node about the overload condition. The OCI information includes the traffic-reduction value that the consumer node applies to throttle signaling traffic toward the originator node. Overload levels are identified as minor, major and critical. The thresholds that define when the node reaches a minor, major, or critical overload level, can be configured on the MAG-c.
Use the commands shown in the following example to modify the default thresholds for the different overload levels.
Modify threshold default values for overload levels
configure mobile-gateway pdn overload-control thresholds minor 85
configure mobile-gateway pdn overload-control thresholds major 90
configure mobile-gateway pdn overload-control thresholds critical 95Use the following command to modify the default time period during which the reported overload remains in effect.
configure mobile-gateway pdn overload-control validity-timeUse the commands shown in the following example to modify the default traffic-reduction values that are signaled to the MME node for the overload levels (within the supported ranges).
Modify traffic reduction default values for overload levels
configure mobile-gateway overload-control overload-reduction minor 40
configure mobile-gateway overload-control overload-reduction major 70
configure mobile-gateway overload-control overload-reduction critical 85You can also enable and disable overload throttling at the local level. Use the following command to enable local overload throttling. This automatically enables local overload throttling values for the different overload levels.
configure mobile-gateway pdn overload-control local-throttling local-overload-throttlingUse the commands shown the following example to modify the percent of the traffic to be throttled when the MAG-c node reaches the minor, major, or critical overload level (within the supported ranges).
Modify local throttling default values for overload levels
configure mobile-gateway pdn overload-control local-throttling minor throttling-percent 0
configure mobile-gateway pdn overload-control local-throttling major throttling-percent 50
configure mobile-gateway pdn overload-control local-throttling critical throttling-percent 80The following table describes the overload reporting to the MME and the local throttling applied for the associated overload condition levels, based on the settings used in the preceding overload-reduction and local-throttling examples.
| Overload condition | Overload reporting to the MME | Local throttling |
|---|---|---|
| Minor | The SGW-C + PGW-C reports the minor overload condition to the MME, informing it to reduce traffic by the configured minor overload value of 40%. | Zero (0) percent of the traffic is throttled. The SGW-C + PGW-C does not throttle any GTP-C traffic. At this overload level the MME is permitted to reduce traffic with its own priority procedures. |
| Major | The SGW-C + PGW-C reports the major overload condition to the MME, informing it to reduce traffic by the major overload of 70% (configured, as shown in the preceding example) | 50% of the incoming Create Session Requests are throttled. Any Network initiated modifications that could trigger an Update Bearer Request are also throttled at the same percentage. |
| Critical | The SGW-C + PGW-C reports the critical overload condition to the MME, informing it to reduce traffic by the critical overload of 85% (as configured in the preceding example) |
80% of the traffic is throttled, as configured in the preceding example. 80% of the received GTP-C Create Session Requests, Bearer Resource command, or Modify Bearer command call flows are throttled. Any Network initiated modifications that could trigger an Update Bearer Request are also throttled at the same percentage. |
As a consumer, the SGW-C + PGW-C also receives overload information from the MME. When it receives a GTP-C OCI IE from the MME in overload, the SGW-C + PGW-C throttles signaling traffic toward the MME. Based on the traffic reduction received in the OCI IE from the MME, the SGW-C + PGW-C acts on any network-initiated call flows to the MME, based on the priority shown in the following table.
| Throttling priority | Network-initiated messages |
|---|---|
| Low (dropped last) | Release PDN connection |
| High (dropped first) | Update PDN connection |
Throttling restrictions for overload conditions
Throttling is not applied to the following overload conditions:
- major overload
- Wireless Priority Sessions (WPS)
- handovers, except those based on CSReq which fall into throttling at major overload
- critical overload
- WPS sessions
- Delete PDN session
- handovers, except those based on CSReq which fall into throttling at critical overload
Viewing load and overload control information
Use the following command to view overload throttling information.
show mobile-gateway pdn load-overload-control summaryCongestion mitigation
The MAG-c supports node-level N11 congestion mitigation based on 3GPP TS29.500, 29.502. SBI congestion mitigation is triggered on a consumer node based on the HTTP status codes the node receives from the originator (producer) node.
When acting as an SMF, the MAG-c as the producer node on an N11 interface supports sending the HTTP 503 code during overload conditions. You can configure the overload threshold for congestion mitigation using CLI commands.
During overload, the PDU Session Establishment Create Request is rejected, and the HTTP 503 error code is generated toward the consumer node. The MAG-c responds to the AMF with an HTTP 503 message, including the error attribute ProblemDetails set to “NF_CONGESTION”. If the sbi-retry-after-timer command is also configured, the value is included in the HTTP 503 response.
When no longer in overload, the MAG-c stops rejecting any new PDU Session Establishment Create Requests.
Use the following command to enable SBI overload control.
configure mobile-gateway pdn overload-control enable-sbi-overload-controlUse the following commands to modify the default values of the SBI overload threshold and retry timer.
configure mobile-gateway pdn overload-control sbi-overload-threshold
configure mobile-gateway pdn overload-control sbi-retry-after-timer Wireless Priority Service
Users can configure Wireless Priority Service (WPS) on the MAG-c to enable subscribers who provide national security and emergency services to make priority calls (priority sessions) using public networks during network congestion conditions. The MAG-c can be configured to provide network support for end-to-end session-priority treatment in the core and radio networks.
WPS overview
Government-authorized personnel, emergency management officials, and other authorized users who provide disaster response and management rely on the ability to communicate during congestion conditions. These subscribers are expected to receive priority treatment, in support of mission critical multimedia communications.
There are two methods to qualify a high-priority session:
-
subscription-based WPS
For subscription-based WPS, the Message-Priority value received in the GTP message header on the S11 interface during the initial session setup for 4G/5G NSA would indicate the session is high priority. In this case, the signaling messages toward other peers (UDM, CHF, and PCF) also carry a high-priority indication in the SBI message headers, so that the signaling messages on the receiving node are processed at high priority as well. High-priority indication over the SBI interface is achieved using the Message-Priority value in the HTTP/2 header.
The subscription-based priority service can be enabled on the MAG-c by mapping the Message-Priority value received in the GTP signaling message on S11 for 4G/5G NSA to indicate it is a high-priority session.
-
invocation-based WPS
For invocation-based WPS, the authorized ARP value (received from the PCF) maps the session as a high-priority session. The invocation-based priority service is enabled by mapping the authorized ARP value (for example, received from PCF) for 4G/5G NSA or 5G SA to indicate it is a high-priority session.
In both cases, the authorized ARP value determines the final priority level of the session. The priority level based on authorized ARP value overwrites the priority level assigned based on the Message-Priority value received in the initial GTP messages on the S11 interface.
WPS configuration guidelines
The MAG-c uses a priority-mapping profile configuration to map high-priority sessions based on the Message-Priority value received in the GTP message and on the authorized ARP. The priority level is defined in the priority-mapping profile using a priority value assigned to an authorized ARP value or a GTP Message‑Priority value.
Based on the following priority-mapping profile example configuration, the priority sessions are processed as follows:
- An ARP value of 1 is processed as a high priority session. All other values of ARP are processed at regular priority.
- All Message-Priority values received in GTP message are processed as high-priority sessions.
Mapping-profile configuration
A:MAG-c>config>mobile>profile# info
----------------------------------------------
priority-mapping "profile1"
arp 1
priority 2
exit
gtp-rx-message-priority profile *
priority 2
exit
exit
----------------------------------------------High-priority sessions can be treated with additional priority among themselves. You must define a priority profile for the differentiated treatments among the high-priority sessions, where each high-priority session is identified by one of the priority values (1 to 4).
Use the following commands to configure a priority profile and assign a priority identifier.
configure mobile-gateway priority-profile
configure mobile-gateway priority-profile priorityThe following example shows a priority profile with an egress policy assigned for high-priority sessions that map to a priority level based on the value assigned to the priority command. The following information applies to high-priority sessions, based on the configuration shown in the example:
- The priority identifier value (2 in the example) is assigned under the priority-mapping profile, based on the priority criteria for each option.
- A Message-Priority value 0 is included in GTP messages sent over the s11 interface to the MME, and the GTP messages are marked with DSCP value 56.
- A Message-Priority value 0 is included in the SBI messages sent to peers, for example, the UDM, CHF, or PCF.
- The priority level is
urgentwhile processing PFCP messages marked with DSCP value of 56.
critical PFCP
priority level very sparingly. This level bypasses any overload protection
mechanisms. Instead use the urgent option whenever possible.
Contact your Nokia
customer service representative for information about the recommended configuration
when using the critical option.Priority profile configuration
A:MAG-c>config>mobile>profile# info
----------------------------------------------
priority-profile "profile1"
priority 2
egress
gtp-tx-message-priority 0
sbi-tx-message-priority 0
gtp-dscp 56
pfcp-dscp 56
pfcp-priority-level urgent
exit
exit
----------------------------------------------