PCF-based policy management
The Policy Control Function (PCF) is used to retrieve policy operations related to traffic forwarding, QoS, and charging. This is a pure policy-management function and does not include any authentication functionality, in contrast for example to RADIUS, where authentication and policy management (authorization) are often combined. The PCF uses the SMPolicyControl service. See Service Based Interfaces for more information.
To enable PCF communication, do the following:
-
Use the following command to configure a PCF SMPolicyControl client service.
configure mobile-gateway pdn sba-client-services pcf-client npcf-smpolicycontrol - Use the following command to configure an interface for the MAG-c to use to communicate with the PCF.
configure mobile-gateway pdn sba-client-services pcf-client npcf-smpolicycontrol interface - Provide the following optional configuration:
- An FQDN to identify the service by other NF peers. For example, when generating callback functions, the MAG-c can use the FQDN in the URI, instead of the IP address; see URI construction for more information about how URIs are constructed.
- An NF ID list to specify NF instances that can be used for the PCF function; see Local NF ID list-based discovery for more information. This command is required if the PCF is not dynamically discovered using NRF.
- An HTTP2 profile to influence generic HTTP/2 and SBI parameters; see HTTP/2, OpenAPI, and Python for more information.
- A PCF profile that contains parameters to handle PCF failure handling as
configured using the following command. See Failure handling for more
information.
This also allows configuration of feature support signaling to the PCF using the supported-features commands.configure mobile-gateway profile npcf
- Use the following command to enable the client
service.
configure mobile-gateway pdn sba-service-realm client-service
When a PCF client service is configured, FWA sessions automatically attempt to contact the PCF. Use the following command to configure a dynamic policy in the ADB and bypass PCF for specific sessions.
configure mobile-gateway profile authentication-database entry dynamic-policyYou can also configure per DNN parameters using commands in the following context:
configure mobile-gateway pdn apn pcf-selection Options to configure include the following:
- nf-id-list and npcf-profile commands to override their equivalents in the client service instance
- dnn-format command to modify how the DNN is sent to the PCF
- exclude commands to exclude sending specific IEs to the PCF
PCF interaction is always performed after the authentication flow procedure, including any RADIUS authentication, is completed. The PCF can provide multiple policy decisions, such as an SLA profile, subscriber profile, subscriber filters, and QoS overrides. If any of these values are also provided during the authentication flow, the PCF value overrides these.
Nokia supports vendor-specific attributes in the SMPolicyDecision context, using the vendorSpecific-6527 container. The following attributes are supported:
- subscriberProfile – string indicating the subscriber profile
- slaProfile – string indicating the SLA profile
- sapTemplate – string indicating the SAP template
- groupInterfaceTemplate – string indicating the group interface template
- intermediateDestinationID – string indicating an intermediate destination ID, typically used to apply VPORT QoS
- QoSOverride – string representing specific QoS overrides, using the same format as the RADIUS Alc-Subscriber-QoS-Override attribute which can be present up to 18 times
- A subscriber filter – container that can contain the following sub-objects:
- ingressIpv4 – string representing an IPv4 filter that is applied on ingress
- egressIpv4 – string representing an IPv4 filter that is applied on egress
- ingressIpv6 – string representing an IPv6 filter that is applied on ingress
- egressIpv6 – string representing an IPv6 filter that is applied on egress
The MAG-c can retrieve an updated policy from the PCF using the Npcf_SMPolicyControl Update service call. The SMF only does this if the PCF sets triggers when providing a policy decision. The following trigger codes are supported:
- RES_MO_RE – a PDU Session Modification Request has been received from the UE to add or remove a policy and charging control (PCC) rule
- UE_IP_CH – an IP address is allocated or freed using DHCP/DHCPv6
- DEF_QOS_CH – default QoS parameters are changed via another interface; for example, because of a UDM subscription update
- SE_AMBR_CH – the Session AMBR is changed via another interface; for example, because of a UDM subscription update
- SAREA_CH – a location change was detected that changes the Serving Area
- SCNN_CH – a location change was detected that changes the Serving CN Node
- RE_TIMEOUT – the PCF provided a revalidation timer that triggered the update
- REF_QOS_IND_CH – support for reflective QoS is changed in a PDU Modification Request message
- SCELL_CH – a location change was detected that changed the Serving Cell
- CM_SES_FAIL – a credit control failure was detected; see CHF failure handling for more information
Alternatively, the PCF can directly update the policy on the MAG-c using the SmPolicyUpdateNotification callback service call. This call is executed against an explicit URI provided by the MAG-c during setup, which contains all required session context.
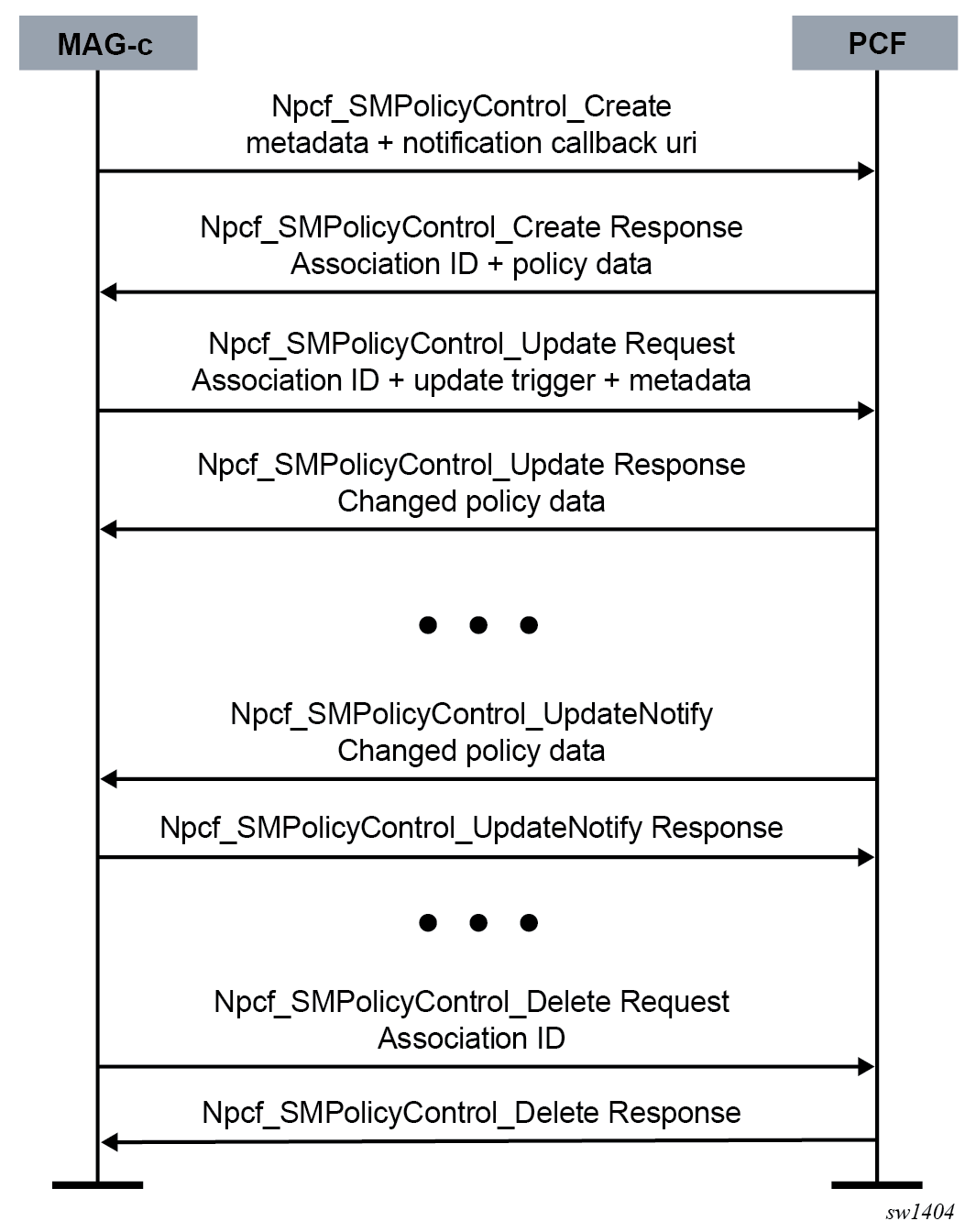
The Npcf_SMPolicyControl service creates a policy association for a session that can be updated or removed at any time. Each policy association has its own identifier assigned by the PCF, which may be different from MAG-c session-specific identifiers such as SUPI. The MAG-c supports the following operations of the Npcf_SMPolicyControl service, as shown in PCF Policy Control Operations:
-
The Create operation is used to create the policy control association. In the request, the MAG-c sends various metadata such as SUPI, GPSI, PEI, DNN, S-NSSAI, and subscribed QoS. The MAG-c also includes a notification callback URI for the UpdateNotify operation. The PCF responds to this request with an association ID identifying the policy association, and the initial policy data.
The Create operation is part of the initial session setup; see FWA session setup for 5G for more information.
- The Update operation that is used to inform the PCF that one or more signaled triggers have been activated. The MAG-c signals the policy association ID, applicable update trigger, and any metadata to the PCF. The PCF responds to the update with the changed policy data, if any.
-
The UpdateNotify operation is used by the PCF when it requires to update a policy decision immediately. In this case it sends the request to the URI provided during the creation of the policy association, including the changed policy data. The MAG-c applies the changed policy and sends a response.
Note: This operation does not use the association ID; the MAG-c provides any local identifier it requires as part of the callback URI. - The Delete operation is used by the MAG-c to stop policy enforcement and remove the policy association. This operation is executed during FWA session deletion.
PCC rule retrieval
The PCF can install PCC rules using the following methods:
- dynamic PCC rules
The PCF fully defines all parameters of the PCC rules, including the packet classifiers. There is no static preconfigured aspect involved in these rules.
- predefined PCC rules
The PCF only defines a PCC rule ID, but no parameters. The PCC rule is assumed to be predefined on the FWA gateway.
For both methods, the PCF can provide a list of PCC rules to enforce. The PCF can add, modify, or remove PCC rules, unsolicited or triggered by the SMF, in any policy association update message. The MAG-c re-evaluates the set of PCC rules and passes through any necessary changes to the other functions, such as the RAN or the UPF.
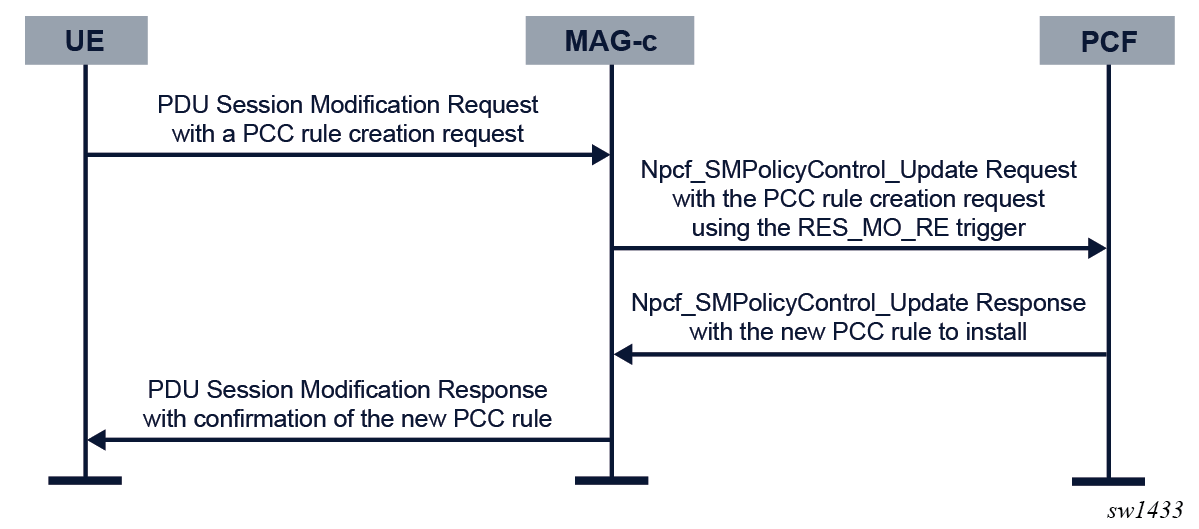
- The MAG-c reflects the request to the PCF using the RES_MO_RE trigger.
- The PCF can accept the PCC rule creation and reflects it to the MAG-c as a regular PCF-provisioned PCC rule.
- The MAG-c sends a PDU Session Modification Response message confirming the new PCC rule toward the UE.
- precedence
- SDF templates for the 5-tuple-based or TOS field-based filtering
- 5QI, ARP, RQI, and bind-to-default QoS flow indicators
- MBR and GBR values
- 5QI QoS characteristics overrides to pass to the RAN
- gate status to control forwarding of the PCC rule
Dynamic PCC rules support the time-of-day (TOD) activation and deactivation by passing condition data in the PCC rule. The MAG-c automatically enables or disables the PCC rule based on the TOD information.
Predefined PCC rules
The MAG-c supports dynamic and predefined PCC rules enforcement on the SMF/GW-C and UPF/GW-U.
The MAG-c supports two methods for policy enforcement on the SMF/GW-C and UPF/GW-U:
-
dynamic PCC rules
The PCF provisions dynamic PCC rules by sending the complete rule description to the SMF/GW-C.
-
predefined PCC rules
The PCF references predefined PCC rules configured on the SMF/GW-C, to activate or deactivate session-level or SDF-level policies.
Configure predefined PCC rules as follows:
- Use the following command to configure individual policy
rules.
configure mobile-gateway profile policy-options policy-rule
- Use the following command to configure a group of rules as a collection of policy
rules.
configure mobile-gateway profile policy-options policy-rule-base
To activate and deactivate predefined policy rules for a PDN session, the PCF references the corresponding policy rule names and policy rule bases configured on the gateway. Use the commands in the following context to configure static predefined PCC rules under an APN.
configure mobile-gateway pdn apn static-predefined-pcc
Static predefined PCC rules are applied to new PDU or PDN sessions that have no PCF control. A PDU or PDN session may be without PCRF control, for example, if the PCF is not deployed or the PCF is unreachable and a fallback to the local policy occurs for new sessions.
Evaluation of predefined PCC rules during session setup
During session setup, the MAG-c evaluates rules referenced by the PCF (policy rule bases, policy rule names, or both), and applies them based on the rule and priority.
The MAG-c evaluates predefined PCC rules that the PCF sends during the session setup as follows:
-
If the PCF sends a reference to a policy rule base during the session setup, the MAG-c evaluates all the policy rules configured under the policy rule base for the final set of policy rules to apply. If multiple policy rules match, the MAG-c applies the one with the highest priority (lowest precedence value) for that session.
-
If the PCF sends a reference to one or more policy rule names during the session setup, the MAG-c evaluates the policy rule against other policy rules sent by the PCF. If multiple policy rules match, the MAG-c applies the one with the highest priority (lowest precedence value) for that session.
-
If the PCF sends a reference to policy rule base and a policy rule name during the session setup, the MAG-c evaluates the policy rules configured under the policy rule base and the policy rules referenced by the PCF. If multiple policy rules match, the MAG-c applies the one with the highest priority (lowest precedence value) for that session.
See Predefined PCC rules configuration example and Use cases for predefined PCC rules for more information about the session setup behavior when the PCF activates and deactivates predefined PCC policy rules.
Evaluation of predefined PCC rules during session update
During session update, the MAG-c evaluates policy rules referenced by the PCF, together with rules referenced during the previous session setup or update. Rules with the highest priority are applied for the session.
If the PCF sends a reference to policy rule base and policy rule name during a session update, the MAG-c evaluates the policy rules configured under the policy rule base and the policy rules referenced by the PCF, together with the policy rules configured under the policy rule base and the policy rules referenced previously during the session setup or update. If multiple policy rules match, the MAG-c applies the one with highest priority (lowest precedence value) for that session.
Nokia recommends deleting the policy rule base and policy rule name during the update by the PCF, in case the intention is to not apply them on existing sessions. Configured precedence for policy rules applies as long as the PCF does not remove the policy-rule references. Relying on the configured precedence to implicitly remove the policy rules could have unintended consequences.
If the PCF is not available, static policies predefined on the SMF can be used as a fallback option.
See Predefined PCC rules configuration example and Use cases for predefined PCC rules for information about the session update behavior when the PCF activates and deactivates predefined PCC policy rules.
Predefined PCC rules configuration example
This topic provides an example of policy options configuration.
The following example shows the configuration of policy options, including policy rules, policy rule units, (PRUs), and action rule units (ARUs). The predefined PCC rules are applied at the APN level, including the policy rules, PRUs, and ARUs.
PCC rules configuration
A:mag-c>config>mobile>profile>policy-options# info
policy-rule-unit "pru-any-normal“
flow-description 1
exit
qos "pr_normal“
down-link gbr 5000 mbr 5000
up-link gbr 5000 mbr 5000
exit
exit
policy-rule-unit "pru-any-degraded“
flow-description 1
exit
qos "pr_degraded“
down-link gbr 250 mbr 250
up-link gbr 250 mbr 250
exit
exit
policy-rule-unit "pru-dns-normal“
flow-description 1
match
port 53
exit
exit
qos "pr_normal“
down-link gbr 5000 mbr 5000
up-link gbr 5000 mbr 5000
exit
exit
policy-rule-unit "pru-dns-degraded“
flow-description 1
match
port 53
exit
exit
qos "pr_normal“
down-link gbr 250 mbr 250
up-link gbr 250 mbr 250
exit
exit
exit
action-rule-unit aru-edr-only
app-profile-name app-prof-edr-only
exit
action-rule-unit aru-edr-redirect
app-profile-name app-prof-edr-redirect
exit
action-rule-unit aru-edr-aa-rate-limit
app-profile-name app-prof-edr-aa-rate-limit
exit
policy-rule "pr-normal-edr-only" policy-rule-unit "pru-any-normal“ \
action-rule-unit “aru-edr-only” qci * arp * precedence 65000
policy-rule "pr-normal-edr-redirect" policy-rule-unit "pru-any-normal“ \
action-rule-unit “aru-edr-redirect” qci * arp * precedence 1300
policy-rule "pr-degraded-edr-only" policy-rule-unit "pru-any-degraded“ \
action-rule-unit “aru-edr-only” qci * arp * precedence 1200
policy-rule "pr-degraded-edr-redirect" policy-rule-unit "pru-any-degraded“\
action-rule-unit “aru-edr-redirect" qci * arp * precedence 1100
policy-rule "pr-normal-5-tuple" policy-rule-unit "pru-dns-normal“ \
qci * arp * precedence 200
policy-rule "pr-degraded-5-tuple" policy-rule-unit "pru-dns-degraded“ \
qci * arp * precedence 100
policy-rule-base "prb-all-cases“
policy-rule "pr-normal-edr-only“
exit
Use cases for predefined PCC rules
Review these use cases to understand the behavior when the PCF references and applies PCC rules during session setup and update.
This topic describes use cases for predefined PCC rules.
Update the application profile to enable redirect
The following table lists session setup and update behavior when the PCF applies policy rules to update the application profile (app-profile) to enable redirect.
| PCC rules applied | Session setup | Session update |
|---|---|---|
| Using policy rules only |
When the PCF sends the policy rule “pr-normal-edr-only”:
|
When the PCF sends the policy rule “pr-normal-edr-redirect”:
|
| Using the configured policy rule base and policy rule |
When the PCF sends the policy rule base “prb-all-cases”:
|
When the PCF sends the rule name “pr-normal-edr-redirect”:
|
Update policy to throttle all traffic
The following table lists the session setup and update behavior when the PCF applies policy rules to throttle all traffic.
| PCC rules applied | Session setup | Session update |
|---|---|---|
| Using policy rules only |
When the PCF sends the policy rule “pr-normal-edr-only”:
|
When the PCF sends the policy rule “pr-degraded-edr-only”:
|
| Using policy-rule-base and policy-rule |
When the PCF sends the policy rule base “prb-all-cases”:
|
When the PCF sends the rule name “pr-degraded-edr-only”:
|
Update policy to throttle selective traffic
The following table lists the behavior when the PCF applies policy rules to throttle selective traffic, for example, all traffic except DNS traffic.
| PCC rules applied | Session setup | Session update |
|---|---|---|
| Using policy rules only |
When the PCF sends the policy rules “pr-normal-edr-only” and “pr-normal-5-tuple”:
|
When the PCF sends the policy rule “pr-degraded-edr-only”:
|
| Using policy-rule-base and policy-rule |
When the PCF sends the policy rule base “prb-all-cases” and policy-rule “pr-normal-5-tuple”:
|
When the PCF sends rule-name “pr-degraded-edr-only”:
|
PCF failure handling
The MAG-c supports failure handling for PCF as defined in Failure handling. During failure handling using the ap-continue option, the MAG-c performs the following actions for the ongoing session:
- If the failure is mid-session, the MAG-c internally terminates the existing SM policy association and sends no further triggers to the PCF, even if the communication with the PCF recovers. The MAG-c does not send any SM Policy Delete procedures to the PCF, even if the communication with the PCF recovers before the session terminates.
- Use the following command to configure the PCC rules to keep in the assume
positive (AP) mode.
The following options are available for this command:configure mobile-gateway profile pcf-profile ap-action- keep-pcf-rules
The MAG-c keeps the latest rules received from the PCF. If the PCF failure occurs during session setup, there are no PCC rules to keep and this option behaves the same as the keep-local-rules-only option.
- keep-local-rules-only
The MAG-c removes all PCC rules signaled by the PCF and only keeps locally-defined rules for the session, that is, the internal any-to-any rule described in Dynamic QoS based on PCC rules.
- keep-pcf-rules
- An optional time or volume limit or both can be specified during AP mode. These
limits do not account for any time or volume before the failure. The MAG-c terminates the sessions as soon as a limit is reached. Use the following
commands to configure the
limits.
configure mobile-gateway profile pcf-profile fh-time-limit configure mobile-gateway profile pcf-profile fh-volume-limit