Residential NAT
Get information about NAT on BNG CUPS, learn about the functional split between MAG-c and BNG-UP, about configuring NAT, logging, and monitoring NAT resources.
NAT terminology and references
- private side or inside NAT
- The terms private side or inside NAT are interchangeable in the context of NAT. They both refer to the side of NAT where the device being translated resides, before translation takes place. The source IP address and protocol port of the devices on the inside are translated to a global IP address and protocol port on the outside. In the scope of this topic, the term inside is used.
- public side or outside NAT
- The terms public side or outside NAT are interchangeable in the context of NAT. They both refer to the side of NAT after the translation takes place. On the outside, the devices are represented by their translated IP addresses and protocol ports. In the scope of this topic, the term outside is used.
- NAT pool
- A NAT pool is a collection of outside prefixes attached to an outside realm and shared by a group of subscribers. The NAT type (1:1, NAPT) is a property of a NAT pool. Multiple NAT pools can be associated with an outside realm.
- NAT flow
- NAT flows result from translations for which states are maintained in NAT. The
following fields represent a NAT flow:
- source IP address
- source port
- translated IP address
- translated port
- destination port
- destination IP address
- protocol
- NAT and NAT44
- The terms NAT and NAT44 are used interchangeably in this topic.
The following guides are related references:
-
7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Guide
This guide describes many concepts of residential NAT on BNG CUPS that are borrowed from L2-aware NAT on SR OS.
-
7750 SR and VSR BNG CUPS User Plane Function Guide
This guide describes the supported NAT functionality on the BNG-UP.
-
7450 ESS, 7750 SR, and VSR RADIUS Attributes Reference Guide
This guide describes the supported RADIUS attributes for SR and VSR.
-
MAG-c RADIUS Attributes and IU Triggers
This guide describes the supported RADIUS attributes for MAG-c.
Residential NAT44 on BNG CUPS
Traditionally, a NAT binding represents a mapping between an IP address with all of its protocol ports on the inside and an IP address with a specific protocol port range on the outside. This allows sharing of a single IP address on the outside by multiple devices on the inside.
The traditional NAT concept can be extended to a residence or a home, where a NAT binding can represent a mapping between a subscriber residence (or home) and an outside IP address with a specific port block. Regardless of whether the residence is bridged with the devices' IP addresses exposed or routed with a single IP address, an entire residence can be mapped to a single outside IP address and a number of port blocks. The advantage of such aggregation of devices in bridged home environments helps to conserve NAT resources. This type of NAT is on BNG CUPS referred to as residential NAT.
A subscriber can have a mix of sessions that are going through NAT processing and sessions that bypass NAT processing. The term "NAT enabled subscriber" used throughout this document refers to a subscriber that has all or some sessions going through NAT processing.
The following figure shows a residential NAT example with two residences.
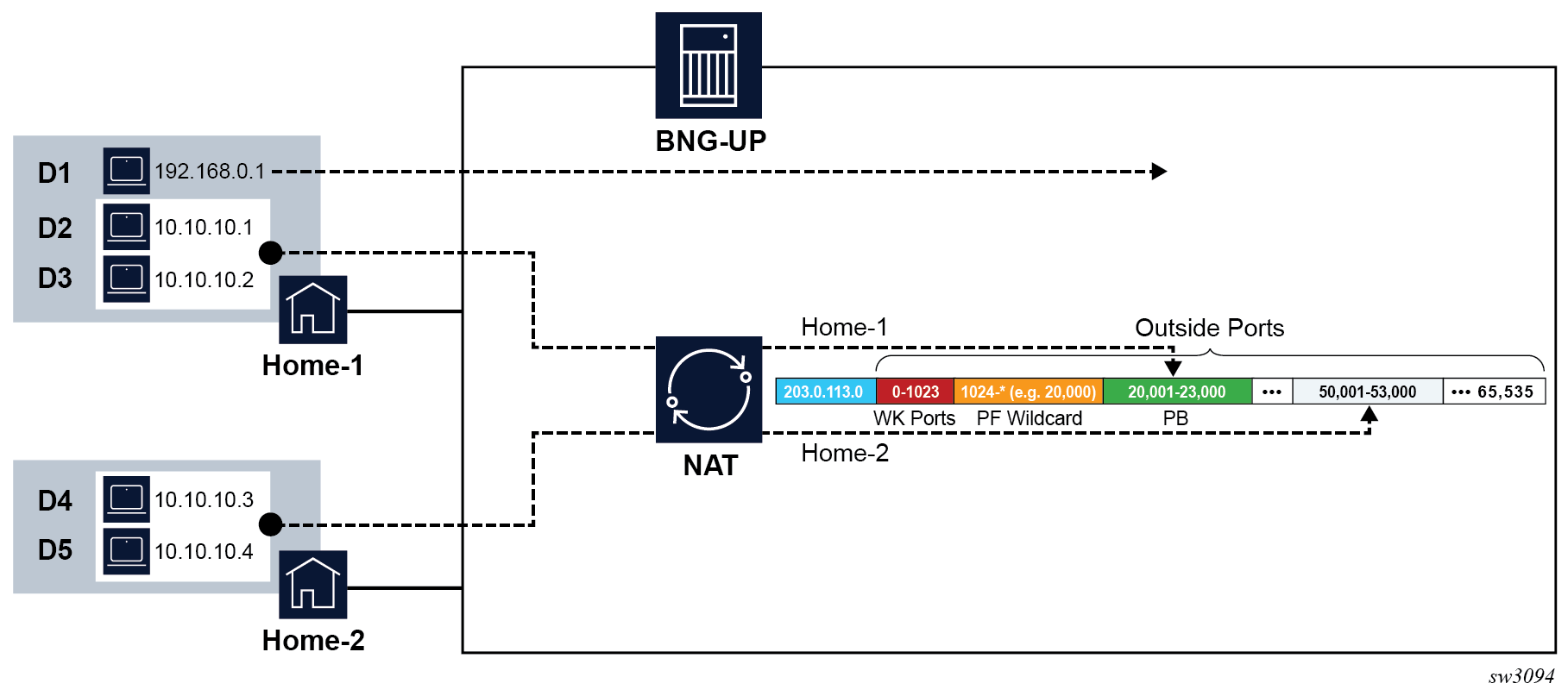
- In the first residence (Home-1), one device (D1) bypasses NAT and two devices (D2 and D3) go through NAT.
- In the second residence (Home-2), both devices (D4 and D5) go through NAT.
Instead of allocating 4 port blocks, one for each device going through NAT, residential NAT allocates only two port blocks, one per residence.
WK ports are the well-known ports such as HTML and SMTP. The PF wildcard range represents the static Port Forward range.
Functional split between MAG-c and BNG-UP
The distribution of NAT related functionality between the MAG-c and the BNG-UP on a BNG CUPS system is as follows.
MAG-c
- During the session authentication phase, the MAG-c determines if a session needs to be associated with NAT.
- If the session is to be associated with NAT, the MAG-c selects the NAT outside prefix (in a NAT pool), an outside IP address and the initial (or the first) port block (in NAPT), and the NAT related policy which determines NAT operational parameters (ALG, protocol timers, and so on).
- The MAG-c logs the NAT resources (outside IP address and port block) via a CUPS session account (RADIUS based). In this way, NAT logging becomes an integral part of the session accounting.
- The MAG-c submits the selected NAT resources to the BNG-UP.
BNG-UP
- Based on the received NAT parameters for the session, the BNG-UP creates a binding and performs NAT translations for data traffic without any further help from the MAG-c.
- BNG-UP can allocate additional extended port blocks for a subscriber and notify MAG-c about port block allocations and deallocations to properly integrate them in the subscriber management logging and accounting on the MAG-c.
- Optionally, flow-based logging can be enabled on the BNG-UP.
Maintaining the management of outside IP addressing on the MAG-c works in favor of multi-chassis redundancy, where existing outside IP addresses and port blocks can be preserved between switchovers.
Management of NAT outside prefixes
Outside NAT prefixes are allocated on demand. This concept follows the On Demand Subnet Allocation (ODSA) approach, in which smaller subnets (or prefixes) are allocated from a preconfigured prefix (supernet). ODSA supports exclusion of IP address ranges from the configured prefix. In NAT this means that an IP address range that is excluded in the configuration is not used in the NAT pools.
An excluded IP address range must align with the ODSA micro-net boundary, however, the CLI does not enforce configuration of an excluded IP address range that covers the ODSA micro-net. If you configure a range that only partially covers the ODSA micro-net, the entire ODSA micro-net is excluded from the NAT pool. The result is more IP addresses than are configured for exclusion are taken from NAT pool.
The following example shows a misaligned IP address range that is excluded.
Misaligned configuration for excluded IP address range
---------------------------------------------
A:node-2>config>mobile>pdn# info
----------------------------------------------
local-address-assignment
network-realm vrf-1
pool pool-1
ipv4
prefix 198.51.100.0/24
exclude-addresses 198.51.100.100 192.51.100.120
micro-net-length 28
---------------------------------------------- In this example, ODSA creates micro-nets, starting from 198.51.100.0/28, 198.51.100.16/28, and so on, to 198.51.100.240/28. The configured excluded range partially covers two such micro-nets: 198.51.100.96/28 and 198.51.100.112/28. In this case, both of these micro-nets are fully excluded from the NAT pool. The micro-net 198.51.100.96/28 has four IP addresses (.96, .97, .98, and .99) that should not be excluded. Similarly, 198.51.100.112/28 has eight IP addresses (.121 to .128) that should not be excluded. This means that twelve additional IP addresses are excluded from the NAT pool that should not be excluded.
The IP address exclusion feature is not supported for a prefix that is configured as dedicated (configure mobile-gateway pdn local-address-assignment network-realm pool dedicated).
See ODSA and local address assignment for more information about NAT prefix allocation.
CP NAT profile
The CP NAT profile defines a set of NAT parameters related to the outside addressing and the type of NAT. The MAG-c uses the parameters in the CP NAT profile, with exception of the up-nat-policy parameter which is a reference to a NAT policy on the BNG-UP.
configure mobile-gateway profile bngThe following are parameters provided via the NAT pool in the CP NAT profile:
-
laa-pool network-realm
The network realm defines the outside routing context (VPRN, Base).
-
laa-pool name
The name points to the ODSA pool name from which the NAT prefix is allocated. The ODSA pool may contain multiple address ranges (supernets).
-
mode
The mode defines the NAT mode (1:1 or NAPT) which is necessary to properly allocate outside IP addresses, port blocks, number of subscribers per outside IP address, and static port range from the pool.
-
up-nat-policy
The UP NAT policy is a reference to the NAT policy that resides in the BNG-UP. This is an optional parameter. When the MAG-c does not provide a UP NAT policy, the system uses the UP NAT policy with name default configured on the BNG-UP.
The inside network realm (or routing context) is determined from the APN. For more information, see Service selection.
The following are characteristics of a CP NAT profile.
- A CP NAT profile is associated with a IPoE or PPPoE session during the session authentication phase. If a session is not associated with a CP NAT profile during the authentication phase, NAT is not performed for that session, and the traffic of that session bypasses NAT.
- In residential NAT, all NAT enabled sessions of a specific subscriber must share the same CP NAT profile. The session setup fails for a session that is associated with a different CP NAT profile than the profile that is already assigned to existing sessions of the same subscriber.
- A CP NAT profile cannot be removed from a session via CoA.
- A CP NAT profile cannot be added to a session that was instantiated without NAT.
Port forwards
Port forwards are a session concept that allows devices on the outside to initiate traffic toward a configured port on the inside through an open NAT pinhole (a fixed mapping between an inside and an outside port). Port forwards can be allocated dynamically via UPnP or statically via RADIUS Access-Accept or CoA messages.
The UPnP policy is configured on the BNG-UP. A UPnP request from the client is forwarded to and served by the ISA or ESA. In UPnP, ports are allocated from the port-block that is allocated to the subscriber, not from the wildcard port forwarding range.
Static port forward requests sent via RADIUS CoA can be addressed to a session or a subscriber. In case of a subscriber, the port forward is accepted only if the subscriber has a single NAT enabled session.
The RADIUS Alc-Static-Port-Forward VSA is used for allocation or deletion of static port forwards. For more information about the VSA, see the MAG-c RADIUS Attributes and IU Triggers.
Extended port blocks
Multiple port blocks per subscriber
Residential NAT supports allocations of multiple port blocks (PBs) for each subscriber, or more accurately for a set of NAT-enabled sessions within a subscriber. The PB space of an outside IP address in a NAT pool is divided into two partitions. The first partition is reserved for the first (or initial) PB of a subscriber. The second partition is dedicated to the extended PBs, which are allocated dynamically on an as-needed basis in case a subscriber needs more ports. The two occupy the port space of an IP address consecutively, where the second port partition extends from the end of the first partition to the end of the port space of an IP address (port 65535).
Although the NAT resource are allocated and deallocated in the BNG-UP, the MAG-c, controls the allocation of the outside IP addresses, the first PBs, and the division of the port space in the BNG-UP. The BNG-UP controls the allocation of the extended PBs for each subscriber.
The BNG-UP notifies the MAG-c, of the allocation and deallocation of the extended PBs. In this way, logging of extended PBs is integrated into the accounting logic on the MAG-c, where the newly allocated and deallocated PBs are reported in triggered RADIUS Interim-Update messages.
Port space division
MAG-c programs the BNG-UP with the first port of the PB space used for extended PB allocations. This first port divides the port space of an outside IP address into two. The first part is reserved for well-known (WK) ports, port forwards and the ports reserved for the initial port blocks of each subscriber. This space is managed by the MAG-c. The second partition that follows the first partition to the end of the entire port space (port 65,535) is reserved for the extended PBs. This port range is managed by BNG-UP.
- maximum number of subscribers per outside IP address (subscriber-limit command)
- size of the first PB for each NAT subscriber (port-reservation port command)
- last port of shared port forwarding range (port-forwarding-range command)
All three parameters are configured in the CP NAT profile on the MAG-c.
configure mobile-gateway profile bng cp-nat-profile nat-pool mode Configuring the subscriber-limit command enables allocation of extended PBs. The extended PB port partition starts at the port determined by the following formula:
While these parameters are configured on the MAG-c, the size of the extended PBs and the maximum number of PBs per subscriber are configured in the UP NAT policy on the BNG-UP; see the 7750 SR and VSR BNG CUPS User Plane Function Guide, "Guidelines for configuring extended port blocks".
Managing port block space
Both the initial and extended port partitions are served on a first-come, first-serve basis. The initial port partition guarantees at least one port block (PB) for each of the preconfigured number of subscribers per outside IP address (subscriber-limit in the pool). If there are more subscribers in the network than the preconfigured number of NAT subscribers, this space becomes oversubscribed.
The extended port partition does not guarantee that each of the existing NAT subscribers receive additional PBs. Each subscriber can allocate additional free PBs only if they are available, up to the maximum combined limit (initial and extended) set in the UP NAT policy (block-limit parameter) configured on the BNG-UP.
For optimized NAT pool management and correct capacity planning, it is essential to understand the following configuration elements in the user's network, which determine the average PBs per subscriber:
- IP address compression ratio – how many subscribers share one outside IP address
- subscriber over subscription ratio – how many NAT subscribers are active simultaneously
- statistical port usage for subscribers – what percentage of subscribers are heavy, medium, and light port users
- PB sizes
After the average PBs per subscriber is determined, the following NAT parameters can be configured:
- the subscriber-limit per outside IP address in the CP NAT profile on MAG-c
- the size of the initial PB in the CP NAT profile on MAG-c
- the size of the extended PB in the UP NAT policy on the BNG-UP
- the maximum number of PBs per subscriber in the UP NAT policy on the BNG-UP
- the outside IP address range as part of the NAT prefix in the ODSA pool in MAG-c
Guidelines for determining traffic patterns and port usage
The following guidelines and examples can serve as an initial configuration for administrators who are unsure of their traffic patterns in terms of port usage for their subscribers. The calculations are based on the following assumptions:
- There are 10,000 subscribers that require NAT, however only 8,000 of them are active simultaneously. This means that over subscription of outside (NAT) IP address is allowed.
- The subscriber's port usage is on average:
- 60% light users with less than 1000 ports
- 30% medium users with less than 2000 ports
- 10% heavy users with less than 4000 ports
The following calculations are based on the stated assumptions:
- There are 12,800,000 ports in total.8,000 active subscribers * (0.6 * 1000 + 0.3 * 2,000 + 0.1 * 4,000) = 12,800,000 ports
- One outside IP address can accommodate approximately 50,000 (64K ports less the
static port forwards and well-known ports), which yields 256 outside IP
addresses (/24) in a pool.12,800,000 / 50,000 = 256
- Based on the compression ratio that follows from the preceding calculations, the
subscriber limit is 32 (32 subscribers share one outside IP
address).8,000/256 = ~32
- Based on the calculations, a reasonable size for the initial port block is 1000 ports and for the extended port block is 335 ports.
- To accommodate heavy users with 4,000 ports, the maximum number of port blocks
per subscriber is set to 10.(1*1000 + 9*335 = 4015)
Based on the calculations, and assuming the subscribers are well load-balanced over ISAs or ESAs, configure the following to achieve the required port usage:
- 32 for the subscriber limit in a pool
- 1,000 initial and 335 extended for the PB sizes
- 10 for the PBs maximum per subscriber
- /24 address range in the pool
The following examples show the provisioning for the MAG-c and BNG-UP.
MAG-c BNG profile configuration
A:MAG-c>config>mobile>profile>bng# info
--------------------------------------------
cp-nat-profile “demo-profile”
nat-pool “demo-pool”
laa-pool network-realm “demo-realm” name “laa-pool-1”
mode napt
port-reservation ports 1000
port-forwarding-range 15000
subscriber-limit 32
exit
exit
exit
--------------------------------------------MAG-c PDN configuration
A:MAG-c>config>mobile>pdn# info
------------------------------------
local-address-assignment network-realm “demo”
pool “laa-pool-1”
dedicated
ipv4
prefix 10.10.10.0/24
exit
exit
-------------------------------------BNG-UP NAT policy configuration
A:node-2>config>service>nat>up-nat-policy# info
-------------------------------------------------
block-limit 10
port-block-extensions
ports 335
exit
-------------------------------------------------See the 7750 SR and VSR BNG CUPS User Plane Function Guide, "Guidelines for configuring extended port blocks", for information about PB configuration in the UP NAT policy on the BNG-UP.
NAT logging
Residential NAT on BNG CUPS supports the following logging methods:
- Outside IP address, port-blocks, and realm via RADIUS logging, which is integrated with the BNG CUPS session accounting on the MAG-c
- IPFIX based flow logging on the BNG-UP
- Outside IP address, port-block, and realm via SYSLOG on the BNG-UP
For description of the principles of IPFIX logging, see 7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Guide and 7750 SR and VSR BNG CUPS User Plane Function Guide.
RADIUS based logging for residential NAT on BNG CUPS is integrated in the subscriber accounting. The logging uses the same RADIUS infrastructure for NAT as for subscriber management.
The relevant VSA used for NAT logging is Alc-Nat-Port-Range.
For a description of the VSA, see MAG-c RADIUS Attributes and IU Triggers.
The following table describes the relation between the accounting message type, the NAT events, and the content of the Alc-Nat-Port-Range VSA.
| Accounting Message Type | NAT event | Alc-Nat-Port-Range VSA |
|---|---|---|
| Start | Initial IP and PB creation | Includes info about the initial allocation |
| Periodic Interim Update | Resources in use | Includes info about the in-use NAT resources |
| Triggered Interim Update | Allocated or de-allocated extended PBs Timestamp precision is 1 second Only deltas are reported |
Includes information about the in use extended PB |
| Stop | Session closed, all PBs freed | Includes info about the released NAT resources |
RADIUS-based logging
Residential NAT on MAG-c uses RADIUS-based logging integrated with subscriber accounting. The logging uses the same RADIUS infrastructure for NAT as for subscriber management.
NAT logging on MAG-c uses the following relevant VSAs:
- Alc-Nat-Port-Range
- Alc-ISA-Event-Timestamp
- Alc-Acct-Triggered-Reason
- NAT-MAP
- NAT-FREE
For a description of the RADIUS accounting attributes, see MAG-c RADIUS Attributes and IU Triggers.
The accounting START message carries the RADIUS Event-Timestamp (type 55) attribute, which correctly reflects the creation of the initial port block (PB) and outside IP address. The initial PB and outside IP address allocation is triggered by the MAG-c at the time when the first session is created. In other words, the initial PB and outside IP address creation in the ISA or ESA is not triggered by data traffic. However, the allocation of extended (non-initial) PBs is triggered by data traffic on BNG-UP.
The Interim-Updates and STOP accounting message carry the following two timestamps:
- The RADIUS Event-Timestamp attribute with a one second resolution is updated by the MAG-c to reflect the time when the Interim-Update message is generated on the MAG-c.
- The RADIUS Alc-ISA-Event-Timestamp VSA is updated only when an event on the ISA or ESA occurs; for example, an extension PB is allocated or deallocated. This timestamp has the same format and resolution as the Event-Timestamp.
The following table describes the integrated subscriber management and RADIUS logging attributes relevant to NAT.
| Accounting message type | Accounting actions (session based) | Comments |
|---|---|---|
|
START |
The accounting START message is generated for every new session of a subscriber. For NAT-enabled sessions, the message carries:
The NAT-related information is carried in the following RADIUS attribute: Alc-Nat-Port-Range (26.6527.121) This attribute includes the outside IP address, PBs, outside realm, and NAT pool. |
Subscribers are not NAT aware, only sessions are. However, IP address and PBs are allocated per subscriber. In other words, all NAT-enabled sessions within a subscriber share the same outside IP address and PBs. |
|
Regular Interim-Update |
In the NAT context, this message is used to periodically report allocated NAT resources (cumulative update) for each NAT enabled session. NAT-related information is carried in the following VSA: Alc-Nat-Port-Range (26.6527.121) This attribute includes the outside IP address, all existing PBs, outside router ID, and NAT policy. Alc-ISA-Event-Timestamp(241.26.6527.86) This attribute includes the time of the last extended PB allocation or deallocation on the ISA or ESA on the BNG-UP. Event-Timestamp (55) This attribute includes the time when the RADIUS message is generated on the CPM This is repeated for all NAT-enabled sessions or hosts of an ESM subscriber. |
— |
|
Triggered Interim-Update |
This message carries differential updates tracking changes for extended PB allocations and deallocations. Alc-Nat-Port-Range (26.6527.121) This attribute includes the IP address, newly allocated or deallocated extended PB, outside realm , and NAT pool. Alc-Acct-Triggered-Reason (26.6527.163)
This attribute includes the reason for this triggered Interim-Update message, which is an extended PB is allocated (MAP) or de-allocated (FREE). Alc-ISA-Event-Timestamp (241.26.6527.86) This attribute includes the time of the extended port-block allocation or deallocation on the ISA or ESA on the BNG-UP . Event-Timestamp (55) This attribute includes the time when the RADIUS message is generated on the MAG-c.This is repeated for all the subscriber's NAT-enabled sessions. For example, a single extended port-block allocation can trigger multiple triggered Interim-Updates (one for each existing NAT-enabled session). |
— |
|
STOP |
An accounting STOP message is sent when a session of a NAT-enabled subscriber terminates. The message reports the initial end of extended PBs, regardless of whether this NAT-enabled session is last for the subscriber. In other words, it reports all PBs currently in use by any of the subscriber's NAT-enabled sessions and indicates that this particular session is dissociated from any NAT resources. Alc-Nat-Port-Range (26.6527.121) This attribute includes outside IP address, initial and extended PBs, outside realm, and NAT pool. Alc-ISA-Event-Timestamp (241.26.6527.86) This attribute includes the time of the last extended PB allocation or deallocation on the ISA or ESA on the BNG-UP. Event-Timestamp (55) This attribute includes the time when the RADIUS message is generated on the on the MAG-c. If the terminated session is not NAT enabled, the STOP message does not carry any NAT-related information. |
Each accounting stream (START, I-U, or STOP) with the same accounting session ID is treated as a separate entity. In the case of session accounting, the streams may contain NAT information that overlaps other accounting streams of the same subscriber. PB allocations and deallocations for NAT-enabled sessions within a subscriber are accounted for in each accounting stream. That is, if a port-block allocation (through accounting START or MAP I-U) is present in an accounting stream, the deallocation of the same PB is also present in the same stream (through accounting STOP or FREE I-U). Similarly, if an allocation is missing, the deallocation is also missing in the same stream. |
NAT-related attributes for NAT logging
The following example describes relevant NAT-related attributes for NAT logging.
-
The first session of a subscriber is a NAT-enabled session. At the time of session instantiation, the following RADIUS accounting START messages is generated. Outside IP address 192.168.20.2 and initial PB [2001-2004] are allocated at time T1 in MAG-c.
Alc-Nat-Port-Range = "192.168.20.2 2001-2024 realm realm-1 nat-pool pool-1" Event-Timestamp = T1 -
Allocation of a new extended PB follows. Differential data is carried in a triggered Interim-Update message.
Only the newly allocated PBs are present in this update with the triggered reason Nat-Map (20). This PB is allocated on the ISA or ESA in BNG-UP at time T2, which may be different than time T3 at which the Interim-Update from MAG-c is sent to the RADIUS server.
Alc-Nat-Port-Range = "192.168.20.2 3000-3023 realm realm-1 nat-pool pool-1" Alc-Acct-Triggered-Reason = Nat-Map (20) Event-Timestamp = T3 Alc-ISA-Event-Timestamp = T2 -
The periodic Interim-Update message is triggered at regular intervals to carry cumulative (or absolute) data.
This update carries previously allocated PBs, the initial PB, and the extended PB. T4 in the Event-Timestamp reflects the time when the message is generated, while the Alc-ISA-Event-Timestamp is unchanged from the previous update because no new event occurred on the ISA or ESA in BNG-UP.
Alc-Nat-Port-Range = "192.168.20.2 2001-2024, 3000-3023 realm realm-1 nat-pool pool-1" Event-Timestamp = T4 Alc-ISA-Event-Timestamp = T2 -
Deallocation of an existing extended PB follows. Differential data is carried in the triggered Interim-Update message.
Only the deallocated PB is present in this update with the triggered reason Nat-Free (19). This PB was deallocated on the ISA or ESA in the BNG-UP at time T5, which may be different than time T6 at which the Interim-Update is sent to the RADIUS server.
Alc-Acct-Triggered-Reason = Nat-Free (19) Alc-Nat-Port-Range = "192.168.20.2 3000-3023 realm realm-1 nat-pool pool-1" Event-Timestamp = T6 Alc-ISA-Event-Timestamp = T5 -
At session termination, a RADIUS accounting STOP message with initial PB is generated.
This final update for the session carries the initial PB that the session no longer uses. Although this session is terminated, the initial PB may be used by other sessions still present under the same subscriber. T7 in the Event-Timestamp reflects the time when the message is generated, while the Alc-ISA-Event-Timestamp is always the same as in the previous triggered accounting Interim-Update message.
Alc-Nat-Port-Range = "192.168.20.2 2001-2024 realm realm-1 nat-pool pool-1" Event-Timestamp = T7 Alc-ISA-Event-Timestamp = T5
Enabling RADIUS logging on MAG-c
Use the nat-port-range and the acct-triggered-reason commands in the following context to enable session accounting with NAT-related information.
configure mobile-gateway profile charging bng-charging radius session include-attributeThe nat-port-range command enables sending the RADIUS Alc-Nat-Port-Range and Alc-ISA-Event-Timestamp VSAs for the session accounting.
The acct-triggered-reason command together with the triggered Interim-Update message conveys information about the event itself.
Timestamp interpretation
The extended port block functionality uses an additional NAT-related timestamp in the logging framework, in addition to the standard Event-Timestamp that is carried in every RADIUS accounting message. This additional timestamp is introduced in the accounting stream when the first extended port block is allocated for the subscriber, and thereafter it is present in every accounting message in the stream. It represents the time of the most recent extended port-block allocation or deallocation, as recoded by the ISA or ESA in the BNG-UP.
- Event-Timestamp (55) – records the time when the accounting message was generated on the MAG-c
- Alc-ISA-Event-Timestamp (241.26.6527.86) – records the time of the most recent NAT-related event (extended port block allocation or deallocation)
Timestamp interpretation
As an example, the following periodic Interim-Update message with the specified NAT-related attributes indicates that at time 1000, a subscriber has two port blocks allocated, [2001-2024] and [3000-3023], and the most recent change to extended port blocks is at time 500.
Alc-Nat-Port-Range = "192.168.20.2 2001-2024,3000-3023 realm realm-1 nat-pool pool-1"
Event-Timestamp = 1000
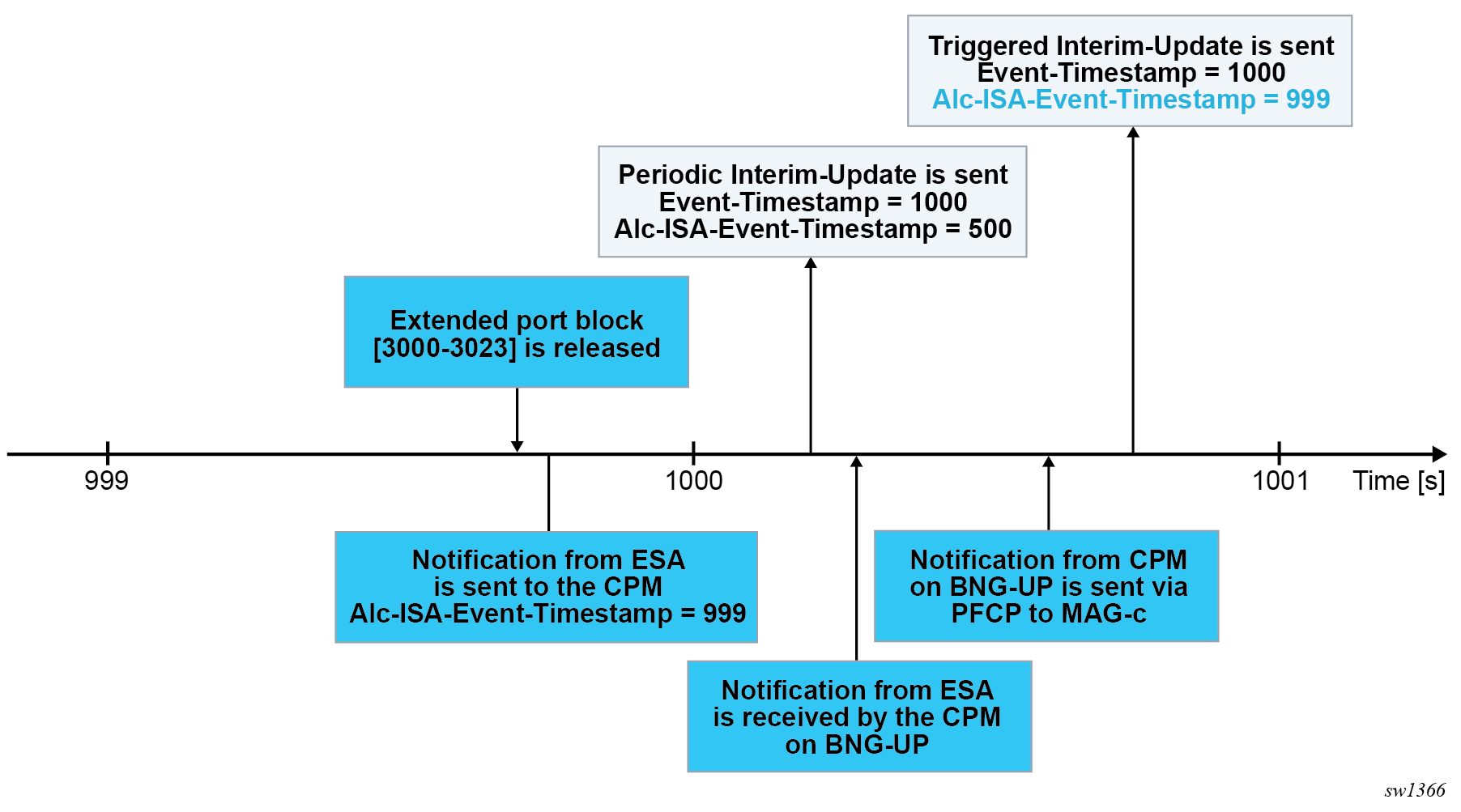
Alc-ISA-Event-Timestamp = 500Consider that the following scenario occurs:
- The extended port block [3000-3023] is released a few milliseconds before the previous periodic Interim-Update message is sent.
- The notification from the ISA or ESA on BNG-UP about this event does not reach MAG-c in time to include the event in the periodic Interim-Update message.
In this scenario, the following triggered Interim-Update message immediately follows the previous periodic Interim-Update message, with the following relevant NAT-related attributes:
Alc-Nat-Port-Range = "192.168.20.2 3000-3023 realm realm-1 nat-pool pool-1"
Alc-Acct-Triggered-Reason = Nat-Free
Event-Timestamp = 1000
Alc-ISA-Event-Timestamp = 999 Both messages have the same Event-Timestamp of 1000 because the timestamp resolution is 1 second. However, the port block [3000-3023] is released at time 999 indicated by the Alc-ISA-Event-Timestamp triggered Interim-Update message.
High logging rates
A system with on-demand port-block allocation is dynamic and possibly generates a high volume of logs. The transport of NAT logs through RADIUS accounting relies on the generic RADIUS accounting infrastructure implemented in MAG-c, which supports multiple RADIUS servers and failover mechanisms. If the rate of accounting messages exceeds the capacity of the entire accounting system, the queue of accounting message toward the RADIUS servers in MAG-c starts filling up. The cause of this could be an internal condition in the CUPS system or slow or even unresponsive RADIUS servers. Considering that NAT is only a contributor to the accounting messages in the larger accounting framework that includes subscriber management, the rate of the allocation and deallocations of extended PBs is internally limited. Although this does not prevent the loss of accounting messages in an overloaded accounting system (for example, because the RADIUS server is slow), it reduces the possibility that the system becomes overloaded in the first place.
Buffering during RADIUS failure
MAG-c provides a mechanism whereby the system can buffer accounting/logging packets for longer periods of time while the accounting servers are unreachable. When the server connections recover, the messages from the buffer are transmitted to the servers, preserving the information during the downtime.
This functionality is not supported with logging of extended PBs. The reason for this is the buffering logic overrides the older messages for the same stream and type with the new ones. For example, the current Interim-Update message (for a specific session) that is in the buffer is overridden by the next one. This is acceptable because the periodic Interim-Update messages carry cumulative information (bytes/octets) and consequently the information is preserved in the most recent message. However, this is not the case for Triggered-Interim-Update messages for extended PBs in NAT, where only the new information (allocation and deallocation) is carried. This means that every message would need to be preserved in the buffer, in which case the higher rate of logs in NAT would overrun the buffer too quickly.
Watermarks
On the MAG-c, a threshold can be configured to monitor the availability of micro-nets. The threshold is set for the minimal number of free micro-nets. When the number of free micro-nets reaches this threshold, a log is generated, alerting the operator about this condition. See ODSA for more information.
In addition to this threshold on MAG-c level, a number of watermarks can be defined on the BNG-UP level. The BNG-UP reports threshold crossing of the watermarks on the BNG-UP level. See 7750 SR and VSR BNG CUPS User Plane Function Guide for more information.
Minimum configuration steps
Learn what minimum configuration residential NAT on MAG-c needs to be operational.
This procedure defines the minimum configuration steps that are necessary to operationalize residential NAT on MAG-c.
-
Configure a local address assignment (ODSA) with an outside NAT prefix, so a
cp-nat-profile can point to it.
To configure a local address assignment pool with an outside NAT prefix, use the pool command in the following context.
configure mobile-gateway pdn local-address-assignment network-realmconfigure mobile-gateway pdn local-address-assignment network-realm “realm-1” pool "laa-pool-1" ipv4 prefix 198.51.100.0/24 prefix 198.51.101.0/24 micro-net-length 28 -
Configure a cp-nat-profile on the MAG-c, so the ADB or
RADIUS can point to it.
To configure a CP NAT profile, use the cp-nat-profile command in the following context.
The minimal configuration of cp-nat-profile consists of a NAT pool with a reference to the local address assignment pool (ODSA), the outside realm, the mode of operation, and a reference to the up-nat-policy.configure mobile-gateway profile bngconfigure mobile-gateway profile bng cp-nat-profile "profile-1" nat-pool "pool-1" laa-pool network-realm "realm-1" name "laa-pool-1" up-nat-policy "up-pol-1" mode napt port-reservation ports 2000 exit -
A new NAT enabled session is associated with a
cp-nat-profile during the authentication phase. Make a
reference to the profile locally in the ADB or have it returned from an external
AAA server.
To reference the CP NAT profile in the ADB, use the cp-nat-profile command in the following context.
configure mobile-gateway profile authentication-database entryA RADIUS server must return the Alc-Cp-Nat-Profile VSA for the session in the Access-Accept message.
-
Integrate NAT Logging in the subscriber accounting.
Use the nat-port-range command in the following context to explicitly enable the Alc-Nat-Port-Range VSA.
configure mobile-gateway profile charging bng-charging radius session include-attributeconfigure mobile-gateway profile charging bng-charging “charging prof” radius session include-attribute nat-port-range -
Configure the parameters on the BNG-UP.
The following parameters must be configured on the BNG-UP:
- nat-group including the ISA redundancy mode
- up-nat-policy (When the MAG-c does not provide a UP NAT policy, the system uses the UP NAT policy with name default.)
- pfcp association with the nat-group
Monitoring NAT resources
Monitor NAT resources using show CLI commands.
Terminology overview
- ODSAThe on-demand subnet allocation (ODSA) subsystem is used for IP address assignment. Use commands in the following context to configure this address assignment.
configure mobile-gateway pdn local-address-assignment - ODSA poolThe ODSA pool (pool-1 in the example configuration) is used for the following applications:
- subscriber session address assignment – addresses for subscriber sessions
- NAT pool addressing – public IP addresses in NAT
- ODSA pool prefix
The ODSA pool prefix (198.51.100.0/24 in the example configuration) is used for the allocation of micro-nets.
- ODSA pool micro-net
An ODSA pool micro-net (198.51.100.224/28 in the example configuration) is an address range in the ODSA pool that is assigned to the BNG-UP.
- NAT member micro-net
A NAT member micro-net is an address range in the ODSA pool micro-net. It is allocated to each NAT member on the BNG-UP.
Typically, a NAT member corresponds to an Extended Services Appliance-Virtual Machine (ESA-VM). In an active/active ESA-VM inter-chassis redundancy configuration in the BNG-UP, however, each ESA-VM is segmented into multiple logical ESA-VMs. In this case, a single ESA-VM houses multiple NAT members.
- NAT subscriber
A NAT subscriber defines sessions that share the same outside IP address and port blocks (PBs).
- initial PB
The initial PB is the first PB assigned to each NAT subscriber.
- shared PB space
The shared PB space on an outside IP address is allocated for PB expansion per NAT subscriber. Each NAT subscriber may get multiple PB allocations from the shared space.
Configuration of NAT pools in the MAG-c
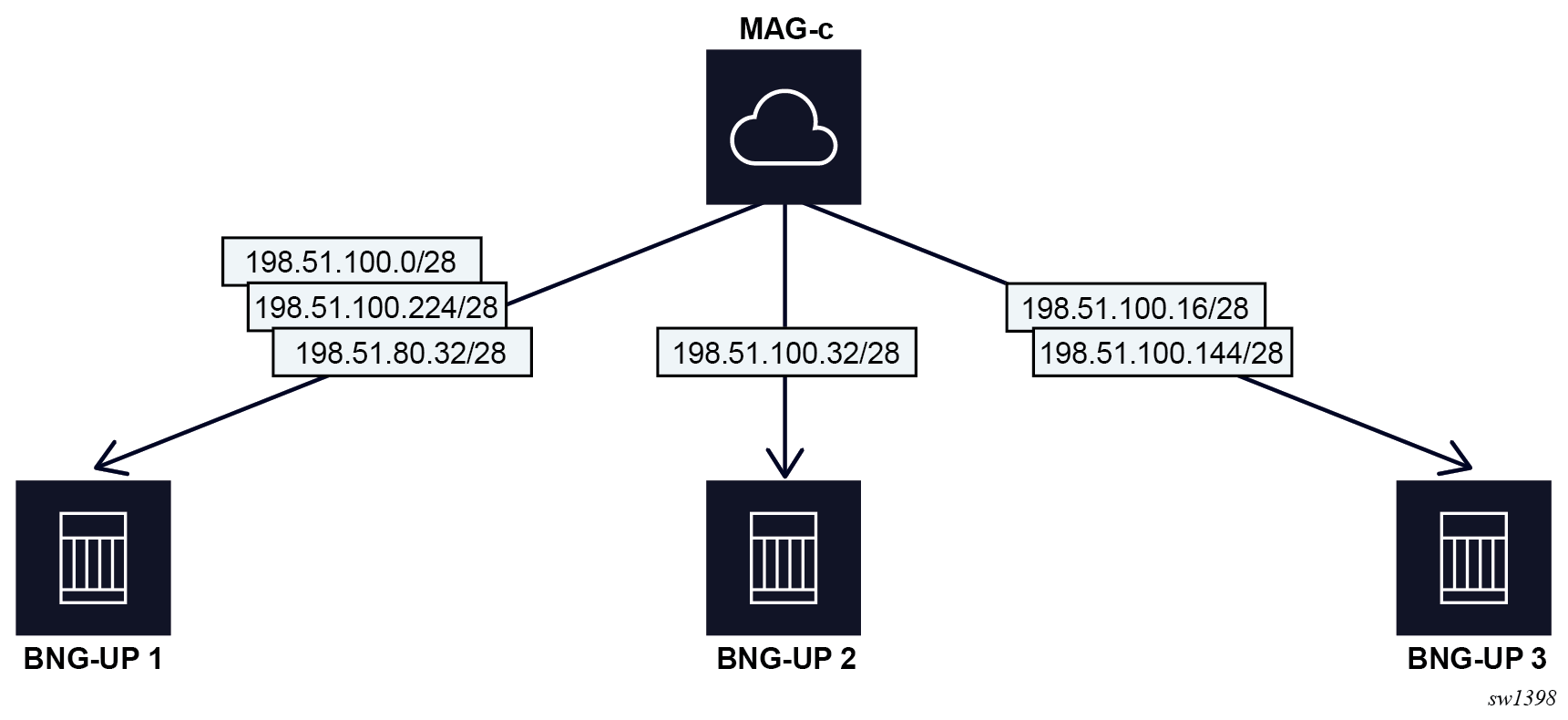
In the preceding figure, the MAG-c is configured as follows.
configure mobile-gateway pdn
local-address-assignment
network-realm “vrf A”
pool "pool-1"
ipv4
prefix 198.51.100.0/24
micro-net-length 28NAT pool resources in ODSA
show mobile-gateway pdn local-address-assignment poolshow mobile-gateway pdn local-address-assignment pool prefixesshow mobile-gateway pdn local-address-assignment pool prefixAn IP address in the hold state that is deallocated from the subscriber cannot be immediately reused because of a default timer of one minute.
show mobile-gateway pdn local-address-assignment pool prefix micronetsHigh-level overview of the ODSA pool
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0"
===============================================================================
Local Address Assignment Pool
===============================================================================
PDN gateway : 1
Network realm : 601
Pool : 601-pool-0
-------------------------------------------------------------------------------
Description : (Not Specified)
Tracking : none
Dedicated : no
Hold time : 00h00m00s
Minimum number of free micro-nets : 1
Rising threshold : 2
IPv4
Default gateway : first-address
Subnet allocation : (Not Specified)
Primary DNS : (Not Specified)
Secondary DNS : (Not Specified)
Micro-net length : 24
Number of prefixes : 1
Number of excludes : 0
Number of micro-nets : 8
IP address usage : 11%
Micro-net usage : 13%
IPv6
Primary DNS : (Not Specified)
Secondary DNS : (Not Specified)
NA
Micro-net length : (Not Specified)
Number of prefixes : 0
Number of excludes : 0
Number of micro-nets : 0
IP address usage : 0%
Micro-net usage : 0%
PD
Delegated prefix : length 56
Micro-net length : (Not Specified)
Number of prefixes : 0
Number of excludes : 0
Number of micro-nets : 0
IP address usage : 0%
Micro-net usage : 0%
SLAAC
Micro-net length : (Not Specified)
Number of prefixes : 0
Number of excludes : 0
Number of micro-nets : 0
IP address usage : 0%
Micro-net usage : 0%
Aggregated usage of the prefixes in the ODSA pool
The following example output shows 11% IP address usage within the prefix.
*A:MAG-c>show>mobile-gateway>pdn>laa pool gateway 1 network-realm "601" name "601-pool-0" prefixes
===============================================================================
Local Address Assignment Pool Prefixes
===============================================================================
Prefix Address Oper IP Addr Drain
Family State Usage
-------------------------------------------------------------------------------
130.0.0.0/21 ipv4 up 11% no
-------------------------------------------------------------------------------
No. of prefixes: 1
High-level information for each prefix with differentiation between applications
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21
===============================================================================
Local Address Assignment Prefix
===============================================================================
PDN gateway : 1
Network realm : 601
Pool : 601-pool-0
Prefix : 130.0.0.0/21
-------------------------------------------------------------------------------
Address family : ipv4
Micro-net length : 24
Operational state : up
Drain : no
Micro-nets : 8
Micro-nets in use (%) : 1 (13%)
NAT
Micro-nets in use (%) : 1 (13%)
IP addresses : 256
IP addresses in use (%) : 218 (85%)
Address assignment
Micro-nets in use (%) : 0 (0%)
IP addresses : 1792
IP addresses reserved : 21
IP addresses in use (%) : 0 (0%)
IP addresses active (%) : 0 (0%)
IP addresses holdoff (%) : 0 (0%)
IP addresses excluded (%) : 0 (0%)
Overview of all micro-nets for a specific prefix
*A:MAG-c>show>mobile-gateway>pdn>laa pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21 micro-nets
===============================================================================
Local Address Assignment Micro-nets for Prefix 130.0.0.0/21
===============================================================================
Micro-net UPF/FSG IP Addresses In Use
Active Hold Usage
-------------------------------------------------------------------------------
130.0.0.0/24 NAT 10.0.1.3 218 85%
130.0.1.0/24 N/A 0 0 0%
130.0.2.0/24 N/A 0 0 0%
130.0.3.0/24 N/A 0 0 0%
130.0.4.0/24 N/A 0 0 0%
130.0.5.0/24 N/A 0 0 0%
130.0.6.0/24 N/A 0 0 0%
130.0.7.0/24 N/A 0 0 0%
-------------------------------------------------------------------------------
No. of micro-nets: 8
Number of subscribers and extended PBs
show mobile-gateway pdn local-address-assignment pool prefix micro-nets natshow mobile-gateway pdn local-address-assignment pool prefix micro-netshow mobile-gateway pdn local-address-assignment pool prefix micro-net nat-membersshow mobile-gateway pdn local-address-assignment pool prefix micro-nets nat extended-port-blocksNumber of subscribers and extended PBs
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21 micro-nets nat
===============================================================================
Local Address Assignment NAT Micro-nets for Prefix 130.0.0.0/21
===============================================================================
Micro-net UPF/FSG Subscribers (%) Ext Port Blocks (%)
-------------------------------------------------------------------------------
130.0.0.0/24 NAT 10.0.1.3 138853 (84%) 483479 (33%)
-------------------------------------------------------------------------------
No. of subscribers : 138853
No. of NAT micronets: 1
Subscriber usage for a specific micro-net
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21 micro-net 130.0.0.0/24
===============================================================================
Local Address Assignment Micro-net
===============================================================================
PDN gateway : 1
Network realm : 601
Pool : 601-pool-0
Prefix : 130.0.0.0/21
Address family : ipv4
Micro-net : 130.0.0.0/24
-------------------------------------------------------------------------------
UPF/FSG : NAT 10.0.1.3
NAT
CP NAT profile : Dut-C_pol_pol1_for_601-pool-0
NAT pool : 601-pool-0
IP addresses : 256
IP addresses in use (%) : 218 (85%)
Maximum subscribers : 165120
Active subscribers (%) : 138853 (84%)
Maximum ext port blocks : 1486336
Active ext port blocks (%) : 377434 (25%)
Subscriber usage and extended PB usage per NAT member micro-net
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21 micro-net 130.0.0.0/24 nat-members
===============================================================================
Local Address Assignment Micro-net nat-members
===============================================================================
PDN gateway : 1
Network realm : 601
Pool : 601-pool-0
Prefix : 130.0.0.0/21
Address family : ipv4
Micro-net : 130.0.0.0/24
UPF/FSG : NAT 10.0.1.3
-------------------------------------------------------------------------------
Member Address Range IP Addresses Subscribers Ext Port Blocks
-------------------------------------------------------------------------------
1 130.0.0.171 - 130.0.0.255 85 46284 86504
2 130.0.0.0 - 130.0.0.85 86 46284 86808
3 130.0.0.86 - 130.0.0.170 85 46285 80243
-------------------------------------------------------------------------------
Extended PB usage per IP address under a specific prefix
*A:MAG-c>show>mobile-gateway>pdn>laa# pool gateway 1 network-realm "601" name "601-pool-0" prefix 130.0.0.0/21 micro-nets nat extended-port-blocks
===============================================================================
Local Address Assignment NAT Micro-nets for Prefix 130.0.0.0/21
===============================================================================
Micro-net UPF/FSG
IP Address Subscribers (%) Ext Port Blocks (%)
-------------------------------------------------------------------------------
130.0.0.0/24 NAT 10.0.1.3
130.0.0.0 645 (100%) 207 (4%)
130.0.0.1 645 (100%) 220 (4%)
130.0.0.2 645 (100%) 93 (2%)
130.0.0.3 645 (100%) 63 (1%)
130.0.0.4 645 (100%) 0 (0%)
130.0.0.5 645 (100%) 0 (0%)
130.0.0.6 645 (100%) 0 (0%)
130.0.0.7 645 (100%) 0 (0%)
130.0.0.8 645 (100%) 0 (0%)
130.0.0.9 645 (100%) 0 (0%)
130.0.0.10 645 (100%) 0 (0%)
130.0.0.11 645 (100%) 0 (0%)
130.0.0.12 645 (100%) 0 (0%)
130.0.0.13 645 (100%) 0 (0%)
130.0.0.14 645 (100%) 0 (0%)
130.0.0.15 645 (100%) 0 (0%)
130.0.0.16 645 (100%) 0 (0%)
130.0.0.17 645 (100%) 0 (0%)
130.0.0.18 645 (100%) 0 (0%)
130.0.0.19 645 (100%) 0 (0%)
130.0.0.20 645 (100%) 0 (0%)
130.0.0.21 645 (100%) 0 (0%)
130.0.0.22 645 (100%) 0 (0%)
130.0.0.23 645 (100%) 0 (0%)
130.0.0.24 645 (100%) 0 (0%)
130.0.0.25 645 (100%) 0 (0%)
130.0.0.26 645 (100%) 0 (0%)
130.0.0.27 645 (100%) 0 (0%)
130.0.0.28 645 (100%) 0 (0%)
130.0.0.29 645 (100%) 0 (0%)
130.0.0.30 645 (100%) 0 (0%)
130.0.0.31 645 (100%) 0 (0%)
130.0.0.32 645 (100%) 18 (<1%)
130.0.0.33 645 (100%) 18 (<1%)
130.0.0.34 645 (100%) 251 (4%)
130.0.0.35 645 (100%) 252 (4%)
130.0.0.36 645 (100%) 12 (<1%)
130.0.0.37 645 (100%) 4 (<1%)
130.0.0.38 645 (100%) 0 (0%)
130.0.0.39 645 (100%) 0 (0%)
130.0.0.40 645 (100%) 0 (0%)
130.0.0.41 645 (100%) 0 (0%)
130.0.0.42 645 (100%) 0 (0%)
Subscriber sessions and CP NAT profile
show mobile-gateway bng sessionshow mobile-gateway bng session natshow mobile-gateway profile bng cp-nat-profileBasic BNG session information to get the CP NAT profile for the session
*A:MAG-c# show mobile-gateway bng session
===============================================================================
BNG Sessions
===============================================================================
[IPoE] MAC : 02:00:00:00:00:01
-------------------------------------------------------------------------------
L2 Access Id : 1/2/8
S-Vlan : 1
C-Vlan : 1
MAC : 02:00:00:00:00:01
Up Time : 0d 00:00:05
Circuit Id : N/A
Remote Id : N/A
Provisioned Addresses : IPv4
Signaled Addresses : IPv4
UP Peer : 10.0.1.3
Selected APN/DNN : 10001
Network Realm : 10001
IPv4 Pool : 10001
IPv4 Address : 172.16.0.2
IPv4 Address Origin : Local pool
IPv4 Prefix Len : 28
IPv4 Gateway : 172.16.0.1
IPv4 Primary DNS : 0.0.0.0
IPv4 Secondary DNS : 0.0.0.0
IPv4 Primary NBNS : 0.0.0.0
IPv4 Secondary NBNS : 0.0.0.0
DHCPv4 Server IP : 172.16.0.1
DHCPv4 Lease Time : 7d 00:00:00
DHCPv4 Renew Time : 3d 12:00:00
DHCPv4 Rebind Time : 6d 03:00:00
DHCPv4 Lease End : 05/29/2023 12:39:39
DHCPv4 Remaining Lease Time : 6d 23:59:55
Subscriber : auto_sub_1 (1)
Acct-Session-Id : X000111002832A30B00000001
Acct-Multi-Session-Id : Y000000012832A30B00000000
State Id : 0x646b628b00000000
Sub Profile : cust_1
Sla Profile : sla-prof
SAP-Template : mySapTemplate
Group-itf-template : myGroupItfTmpl
Number of Framed IPv4 Routes : 0
Number of Framed IPv6 Routes : 0
NAT Profile : Dut-C_pol_l2a-0-1_1
HTTP Redirect URL : N/A
Intermediate Destination Id : N/A
Ingress IPv4 filter override : N/A
Egress IPv4 filter override : N/A
Ingress IPv6 filter override : N/A
Egress IPv6 filter override : N/A
Number of QoS Overrides : 0
PFCP Local SEID : 0x0000000000011100
PFCP Remote SEID : 0x0000000000000002
UE Id : 0x00011100
PDN Session Id : 0x00011100
Group/VM : 2/3
Call-Insight : disabled
Charging Profile 1 : myChargingProfile
Charging enabled : Yes
-------------------------------------------------------------------------------
Number of sessions shown : 1The NAT address range and the realm for the subscriber
*A:MAG-c# show mobile-gateway bng session nat
===============================================================================
BNG Sessions NAT
===============================================================================
[IPoE] MAC : 02:00:00:00:00:01
-------------------------------------------------------------------------------
CP NAT profile : Dut-C_pol_l2a-0-1_1
NAT pool : l2a-0-1
UP NAT policy : l2a-0-1_1
Outside network realm : 123321
Outside IP address : 130.0.0.25
Outside ports : 1024-1024
Extended ports : 1026-1035
: 1036-1045
: 1046-1055
: 1056-1065
: 1066-1075
: 1076-1085
: 1086-1095
: 1096-1105
: 1106-1115
Number of sessions shown : 1CP NAT profile information
*A:MAG-c# show mobile-gateway profile bng cp-nat-profile "Dut-C_pol_l2a-0-1_1"
===============================================================================
CP NAT profile
===============================================================================
Description : Converted old nat-pool of dut Dut-C into CUPS
nat-cp-profile
Access mode : auto
Last management change : 05/22/2023 12:29:30
-------------------------------------------------------------------------------
Pool : l2a-0-1
Description : nat-policy Dut-C_pol_l2a-0-1_1 with nat-pool
l2a-0-1
Mode : napt
Port forwarding range : 1 - 1023
Port reservation : 1 ports
Forwarding port limit : (Not Specified)
Local address assignment pool
Name : l2a-0-1
Network realm : 123321
UP NAT policy : l2a-0-1_1
Last management change : 05/22/2023 12:29:32
Histograms
Histograms provide summarized distribution views for various entities.
show mobile-gateway bng nat histogram port-blocksshow mobile-gateway bng nat histogram extended-port-blocks-per-ipExtended PB allocation in relation to the number of subscribers
In the following example output, 24,241 subscribers have allocated only one extended PB, 229 subscribers have allocated 2 extended PBs, and so on.
*A:MAG-c# show mobile-gateway bng nat histogram port-blocks cp-nat-profile "Dut-C_pol_pol1_for_601-pool-0" nat-pool "601-pool-0" up 10.0.1.3
===============================================================================
Usage histogram UP 10.0.1.3 port blocks per subscriber
===============================================================================
Num port blocks Num subscribers
-------------------------------------------------------------------------------
1 24241
2 229
3 232
4 230
5 236
6 222
7 200
8 245
9 281
10 112737
-------------------------------------------------------------------------------
No. of entries: 10
Aggregated distribution of extended PBs across IP addresses
*A:MAG-c# show mobile-gateway bng nat histogram extended-port-blocks-per-ip cp-nat-profile "Dut-C_pol_pol1_for_601-pool-0" nat-pool "601-pool-0" up 10.0.1.3 bucket-size 100 num-buckets 50
===============================================================================
Usage histogram UP 10.0.1.3 extended port blocks per IP address
===============================================================================
Num extended port blocks Num IP addresses
-------------------------------------------------------------------------------
1-99 0
100-199 0
200-299 0
300-399 14
400-499 2
500-599 1
600-699 6
700-799 11
800-899 50
900-999 65
1000-1099 104
1100-1199 171
1200-1299 201
1300-1399 163
1400-1499 60
1500-1599 23
1600-1699 1
1700-1799 0
1800-1899 0
1900-1999 0
2000-2099 0
2100-2199 0
2200-2299 0
2300-2399 0
2400-2499 0
2500-2599 0
2600-2699 0
2700-2799 0
2800-2899 0
2900-2999 0
3000-3099 0
3100-3199 0
3200-3299 0
3300-3399 0
3400-3499 0
3500-3599 0
3600-3699 0
3700-3799 0
3800-3899 0
3900-3999 0
4000-4099 0
4100-4199 0
4200-4299 0
4300-4399 0
4400-4499 0
4500-4599 0
4600-4699 0
4700-4799 0
4800-4899 0
4900- 0
-------------------------------------------------------------------------------
No. of entries: 50