Application Assurance firewall
The 7705 SAR-Hm series of routers supports Application Assurance (AA) firewall (FW). The AA FW feature extends AA ISA Layer 3 and Layer 4 packet analysis to provide an in-line integrated stateful FW for additional security from malicious attacks. The AA stateful packet filtering feature empowers operators with per-session tracking features to monitor the security of each session. The AA FW runs on the AA ISA.
In a stateful inspection, the AA FW not only inspects Layers 3 and 4, but also monitors and keeps track of each connection’s state. If the operator configures a “deny” action within a session filter, the packets that match the session filter match conditions are dropped and no flow session state or context is created.
The AA FW feature is supported on the following SAP types
- VLLs (Epipes)
- VPLS
- IES/VPRN interfaces
For general information about configuring an AA FW on the 7705 SAR-Hm series of routers, see the topics listed below in the “Application Assurance” chapter of the 7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Guide.
-
AA overview
-
AA: inline policy enforcement
-
Stateful firewall service
-
-
AA system architecture
-
AA ISA resource configuration
-
AA ISA groups
-
-
AA packet processing
- Divert of traffic and subscribers
- Traffic identification
- Statistics and accounting
- AQP
- AA firewall
- Service monitoring and debugging (firewall stastistics)
- CLI batch: begin, commit and abort commands
-
-
Configuring AA with CLI
-
Configuring an AA ISA group
-
Configuring a group policy
- Beginning and committing a policy configuration
- Aborting a policy configuration
- Configuring AA session filters
- Configuring an application group
- Configuring a policer
- Configuring an application QoS policy
-
An AA FW is enabled by assigning an application profile to a SAP that requires flows to be inspected. The assignment enables the AA FW functionality for all traffic that is deemed of interest to and from the SAP. An application profile can be assigned to a VLL (Epipe) via the config>service>epipe>sap>app-profile command, to a VPLS via the config>service>vpls>sap>app-profile command, and to an IES or VPRN via the config>service>ies | vprn>interface>sap>app-profile commands.
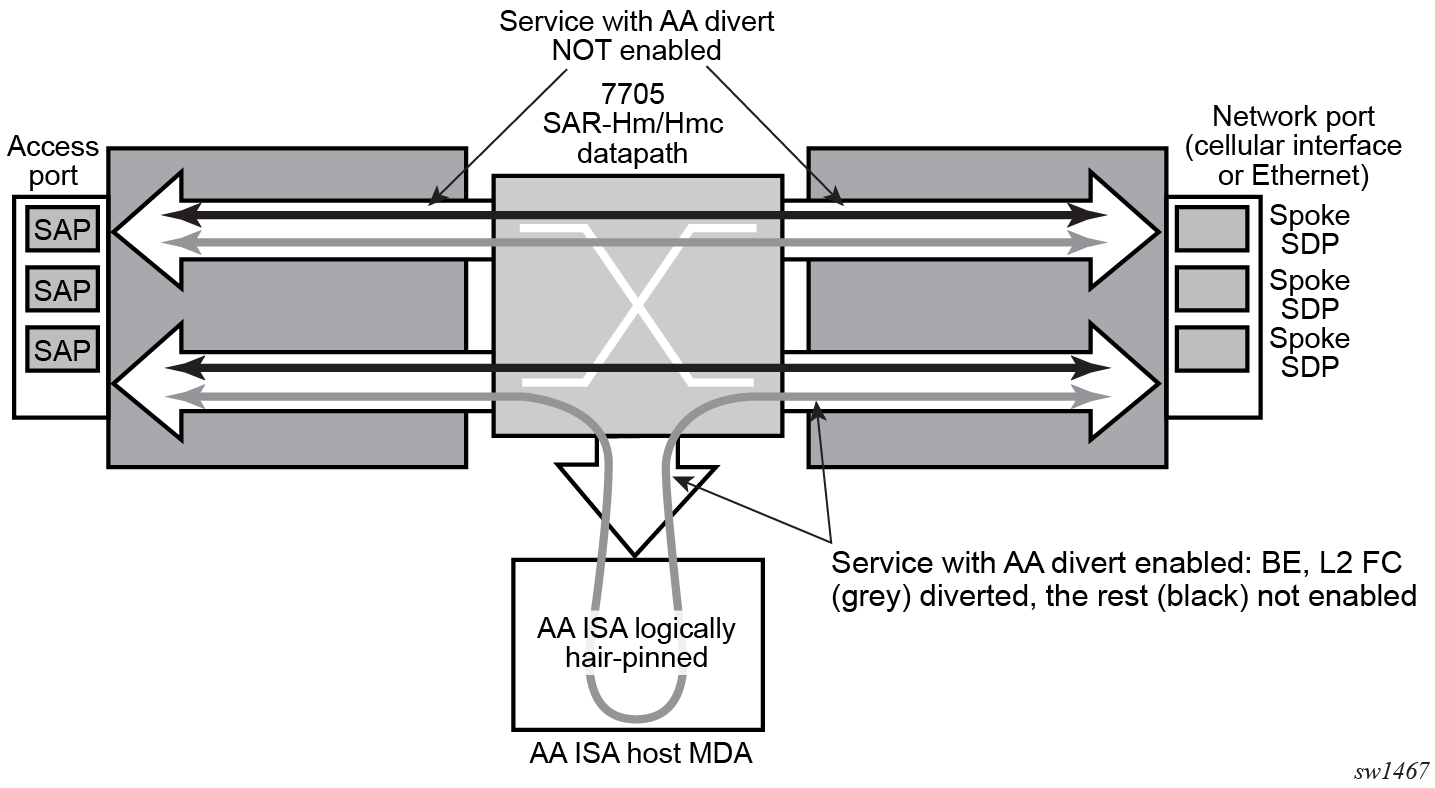
AA FW datapath shows the general mechanism for filtering traffic of interest and diverting this traffic to the AA ISA. This traffic diversion method applies to both bridged and routed configurations.
#--------------------------------------------------
echo "ISA Configuration"
#--------------------------------------------------
isa
application-assurance-group 1 create
description "ISA AA FW Group"
primary 1/6
fail-to-open
divert-fc be
statistics
performance
collect-stats
exit
exit
no shutdown
exit
exit
#--------------------------------------------------
echo "Application-assurance Configuration"
#--------------------------------------------------
application-assurance
flow-table-low-wmark 80
flow-table-high-wmark 90
group 1
policer "flowCountPerSub_DL" type flow-count-limit granularity subscriber create
description "Allow only a certain number of active flows at a time per subscriber"
flow-count 50
tod-override 1 create
time-range daily start 09:00 end 17:00
flow-count 25
no shutdown
exit
exit
policer "flowCountPerSub_UL" type flow-count-limit granularity subscriber create
flow-count 50
tod-override 1 create
time-range daily start 09:00 end 17:00
flow-count 25
no shutdown
exit
exit
policer "singeBucketSub" type single-bucket-bandwidth granularity subscriber create
description "Sample bandwidth policer"
rate 4096
mbs 300
exit
exit
group 1:0 create
description "AA partition config"
ip-prefix-list "IPL" create
description "A sample IP prefix list"
prefix 1.1.1.0/24
prefix 10.1.1.135/32
prefix 2607::/32
exit
event-log "EL" create
buffer-type circular
max-entries 1000
no shutdown
exit
port-list "PL" create
description "Sample port list"
port range 80 443
port 8080
exit
policy
begin
app-service-options
characteristic "ASO" persist-id 1 create
value "val1" persist-id 1
value "val2" persist-id 2
default-value "val1"
exit
exit
app-profile "aa_firewall" create
divert
characteristic "ASO" value "val2"
exit
commit
exit
tcp-validate "TV" create
description "A TCP validate object with strict checked linked to event-log"
event-log "EL"
strict
exit
session-filter "SF" create
description "Deny unsolicited network flows except for a known TCP port"
default-action deny event-log "EL"
entry 1 create
match
ip-protocol-num tcp
src-ip ip-prefix-list "IPL"
src-port port-list "PL"
exit
action permit event-log "EL"
exit
exit
session-filter "SF2" create
description "Deny subscribers from sending ICMP"
default-action permit
entry 1 create
match
ip-protocol-num icmp
exit
action deny
exit
exit
exit
exit
#--------------------------------------------------
echo "Application-assurance Configuration"
#--------------------------------------------------
application-assurance
group 1:0
policy
begin
app-qos-policy
entry 1 create
action
overload-drop
error-drop
fragment-drop all
exit
no shutdown
exit
entry 2 create
action
tcp-mss-adjust 1500
exit
no shutdown
exit
entry 4 create
match
traffic-direction subscriber-to-network
exit
action
flow-count-limit "flowCountPerSub_UL"
exit
no shutdown
exit
entry 5 create
match
traffic-direction network-to-subscriber
exit
action
flow-count-limit "flowCountPerSub_DL"
exit
no shutdown
exit
entry 6 create
match
traffic-direction subscriber-to-network
exit
action
session-filter "SF2"
exit
no shutdown
exit
entry 7 create
match
traffic-direction network-to-subscriber
exit
action
session-filter "SF"
exit
no shutdown
exit
entry 8 create
action
tcp-validate "TV"
exit
no shutdown
exit
entry 9 create
match
characteristic "ASO" eq "val1"
exit
action
remark
fc ef
exit
exit
no shutdown
exit
exit
commit
exit
policy-override
policy aa-sub sap 1/2/3 create
characteristic "ASO" value "val1"
exit
exit
statistics
aa-admit-deny
collect-stats
session-filter-stats
policer-stats-resources
policer-stats
tcp-validate-stats
exit
aa-partition
collect-stats
traffic-type
exit
threshold-crossing-alert
fragment-drop-all direction from-sub create
high-wmark 4294967295 low-wmark 0
exit
session-filter "SF"
default-action direction to-sub create
high-wmark 4294967295 low-wmark 0
exit
exit
exit
exit
exit
exit
The CLI output below shows an example of an Epipe service configured with an "aa_firewall" application profile.
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
sdp 1 create
description "Default sdp description"
signaling off
far-end 10.25.81.103
keep-alive
shutdown
exit
no shutdown
exit
customer 1 name "1" create
description "Default customer"
exit
epipe 1 name "1" customer 1 vpn 1 create
description "Default epipe description for service id 1"
service-mtu 1200
sap 1/2/1 create
description "Default sap description for service id 1"
app-profile "aa_firewall"
no shutdown
exit
spoke-sdp 1:101 create
description "Description for Sdp Bind 1 for Svc ID 1"
ingress
vc-label 101
exit
egress
vc-label 101
exit
no shutdown
exit
no shutdown
exit
The CLI output below shows an example of a VPRN service configured with an "aa-firewall" application profile.
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
customer 1 name "1" create
description "Default customer"
exit
vprn 2 name "Sample VPRN 2" customer 1 create
description "Default Description For VPRN ID 2"
interface "interface_1" create
address 1.1.1.1/24
static-arp 1.1.1.2 8a:5a:47:e5:1d:7f
ipv6
address 1::1/126
neighbor 1::2 8a:5a:47:e5:1d:7f
exit
sap 1/2/3:2 create
description "sap-2-none"
app-profile "aa_firewall"
exit
exit
bgp-ipvpn
mpls
auto-bind-tunnel
resolution-filter
no bgp
exit
resolution disabled
exit
route-distinguisher 100:2
no shutdown
exit
exit
no shutdown
exit
The CLI output below shows an example of an Epipe configured with AA FW event logging.
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
customer 1 name "1" create
description "Default customer"
exit
epipe 1 name "1" customer 1 create
sap 1/2/3:10 create
app-profile "aa_firewall"
no shutdown
exit
sap 1/2/4:10 create
no shutdown
exit
no shutdown
exit
ies 100 name "100" customer 1 vpn 100 create
description "Default Ies description for service id 100"
aa-interface "aa_if" create
address 10.1.1.2/31
sap 1/6/aa-svc:1 create
no shutdown
exit
no shutdown
exit
interface "ies-100-9.9.9.1" create
address 9.9.9.1/24
sap 1/2/6 create
description "sap-100-9.9.9.1"
exit
exit
no shutdown
exit
#--------------------------------------------------
echo "Application-assurance Configuration"
#--------------------------------------------------
application-assurance
group 167:30712 create
event-log "la8PQRgzyz6q87nIdJBolFLCiVRp0IG4" create
buffer-type syslog
max-entries 50000
syslog
address 9.9.9.9
facility kernel
port 20001
severity notice
vlan-id 1
exit
no shutdown
exit
policy
begin
app-profile "aa_firewall" create
description "default-description for AppProfile aa_firewall"
divert
exit
app-qos-policy
entry 10 create
description "default-description for entry 10"
match
aa-sub sap eq 1/2/3:10
exit
action
fragment-drop out-of-order event-log "la8PQRgzyz6q87nIdJBolFLCiVRp0IG4"
exit
no shutdown
exit
exit
commit
exit
statistics
aa-admit-deny
collect-stats
session-filter-stats
policer-stats-resources
policer-stats
exit
exit
exit