IPSec secured interface over cellular
The 7705 SAR-Hm series of routers supports IPSec secured interfaces over cellular interfaces.
IPSec secured interface over a cellular interface shows an example of an IPSec secured interface deployment over a cellular interface in a dual SIM environment.
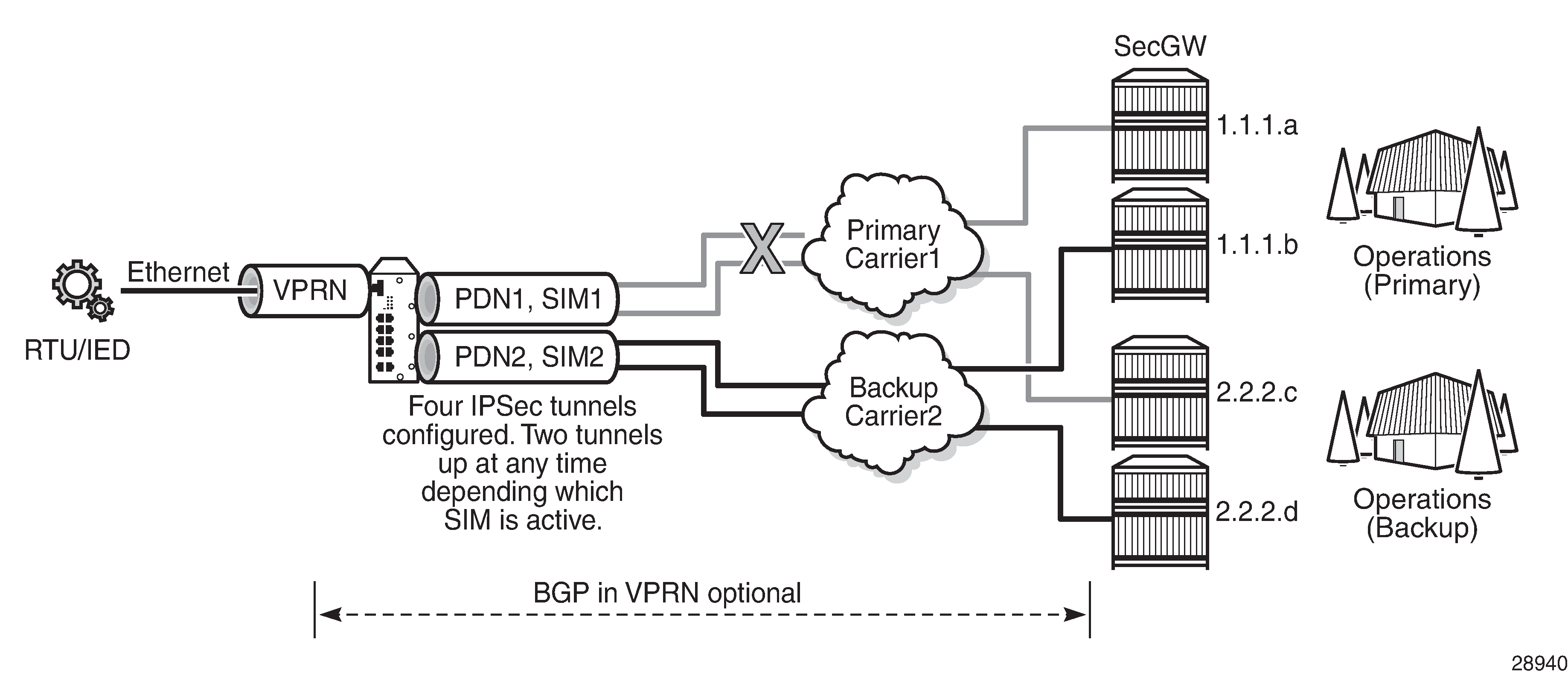
With IPSec secured interfaces, static IPSec tunnels can be created under the PDN router interface associated for each SIM. When the SIM is active and the node attaches to the cellular network, the PDN router interface becomes operational. At that time, IPSec secured interface tunnels configured on the interface also begin to establish toward the security gateway they are configured to connect to. When the tunnel is established, data traffic traverses the IPSec secured interface. In IPSec secured interface over a cellular interface, only the pair of tunnels associated with the active SIM is operational.
The tunnel pair on the second PDN router interface is kept down and becomes operational when the second SIM becomes active.
Each IPSec secured interface tunnel is associated with one service. The supported service types are IES and VPRN.
Each service that needs to be secured over the PDN router interface must be configured with its own IPSec secured interface tunnel. For example if VPRN1, VPRN2, and VPRN3 all need to be secured, then three different IPSec secured interfaces are required, one for each service.
IPSec secured interface is supported on IPv4 and IPv6 PDN router interfaces.
The following CLI output shows an example of IPSec secured interface configured on an IPv6 PDN router interface:
#--------------------------------------------------
echo "ISA Configuration"
#--------------------------------------------------
isa
tunnel-group 1 isa-scale-mode tunnel-limit-32 create
reassembly 2000
multi-active
mda 1/5
no shutdown
exit
exit
#--------------------------------------------------
echo "Router (Network Side) Configuration"
#--------------------------------------------------
router Base
interface "lte-interface1" pdn
port 1/1/1
ip-mtu 1500
ipv6
exit
no shutdown
exit
#--------------------------------------------------
echo "IPsec Configuration"
#--------------------------------------------------
ipsec
ike-transform 1 create
dh-group 21
ike-auth-algorithm sha384
ike-encryption-algorithm des
exit
ike-policy 1 create
ike-version 2
dpd interval 10
ike-transform 1
exit
ipsec-transform 1 create
esp-auth-algorithm auth-encryption
esp-encryption-algorithm aes256-gcm8
exit
exit
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
vprn 1 name "vprn1" customer 1 create
ipsec
security-policy 1 create
entry 1 create
local-v6-ip 463c:f068:d815:e0ee:7ecf:5660::/96
remote-v6-ip c97e:a8fa:1785:52d7:9bb8:9b3b::/96
exit
entry 2 create
local-v6-ip 463c:f068:d815:e0ee:7ecf:5661::/96
remote-v6-ip c97e:a8fa:1785:52d7:9bb8:9b3c::/96
exit
exit
exit
route-distinguisher 1.1.1.1:52
static-route-entry c97e:a8fa:1785:52d7:9bb8::/80
ipsec-tunnel "tunnel1-vprn1"
no shutdown
exit
exit
no shutdown
exit
exit
#--------------------------------------------------
echo "Router (Service Side) Configuration"
#--------------------------------------------------
router Base
interface "lte-interface1" pdn
ipsec tunnel-group 1 public-sap 1
ipsec-tunnel "tunnel1-vprn1" private-sap 1 private-service-
name "vprn1" create
encapsulated-ip-mtu 1300
remote-gateway-address 2001:90:10:3::2
security-policy 1
dynamic-keying
ike-policy 1
pre-shared-key "2KMbfx1sfSVdLxLEJsuVhs/
hfa42V3XyCZMLyubX" hash2
transform 1
exit
no shutdown
exit
no shutdown
exit
exit
exit