Network group encryption
This chapter provides information to configure network group encryption (NGE).
Topics in this chapter include:
NGE overview
The network group encryption (NGE) feature enables end-to-end encryption of MPLS services, Layer 3 user traffic, and IP/MPLS control traffic. NGE is an encryption method that uses a group-based keying security architecture, which removes the need to configure individual encryption tunnels to achieve network-wide encryption.
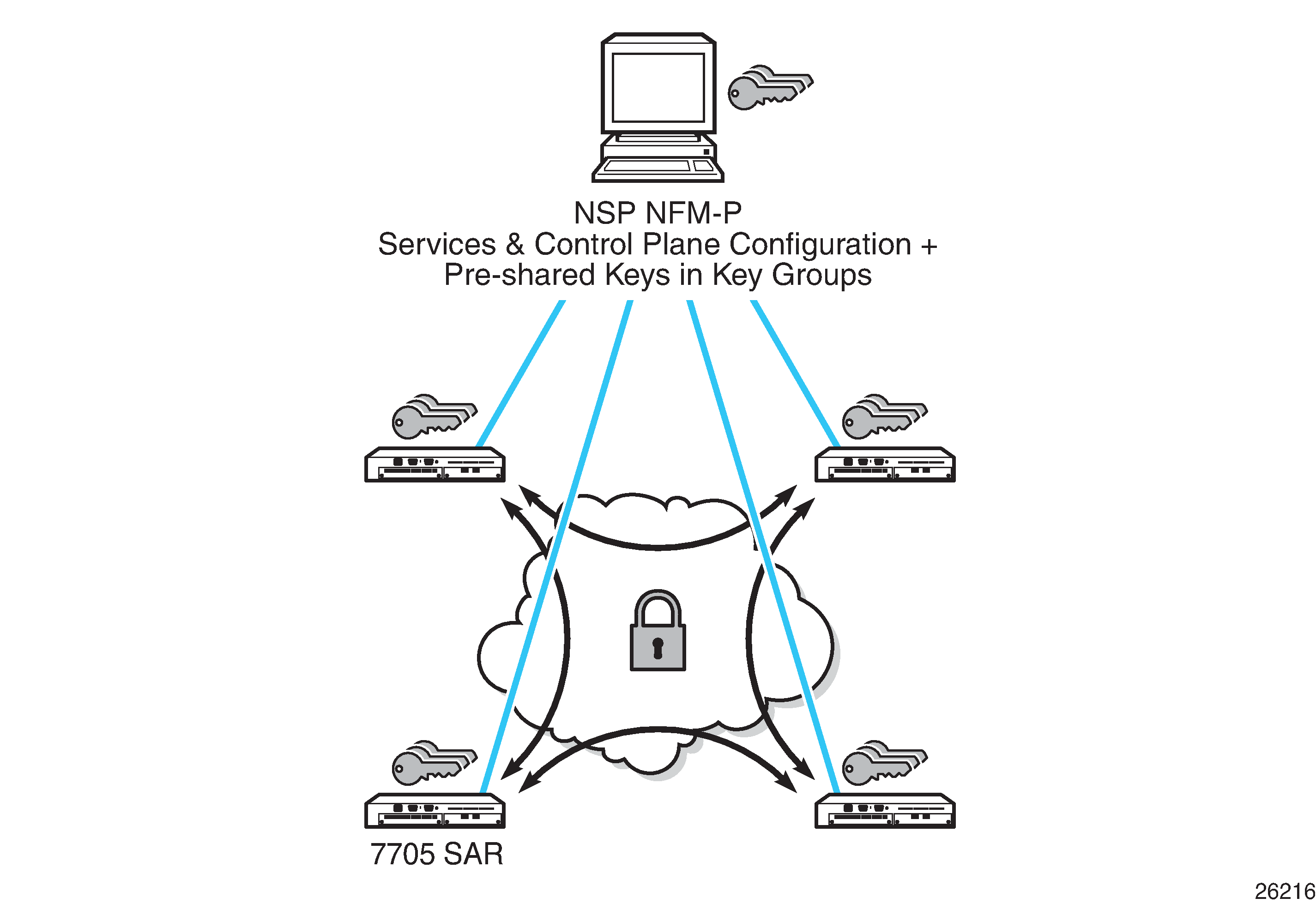
NGE relies on the NSP NFM-P to manage the network and apply encryption to specific MPLS services, Layer 3 user traffic, or control plane traffic depending on the security requirements of the network. Operators designate traffic types that require added security and then apply NGE to those traffic types using the NSP NFM-P. The NSP NFM-P also acts as the network-wide NGE key manager, downloading encryption and authentication keys to nodes and performing hitless rekeying of the network at operator-defined intervals. For more information about managing NGE within a network, see the NSP NFM-P User Guide.
The following figure shows an NGE network with NSP NFM-P services, control plane configuration, and key management.
NGE is enabled on the 7705 SAR and provides three main types of encryption to secure an IP/MPLS network:
SDP encryption – MPLS user plane encryption enabled on MPLS tunnels (SDPs) supporting VPRN or IES services using spoke SDPs, VPLS using spoke or mesh SDPs, routed VPLS into VPRN, Epipes, and Cpipes
VPRN encryption
unicast VPRN – MP-BGP-based VPRN-level encryption using spoke SDPs (spoke-sdp) or autobind SDPs (auto-bind-tunnel) with LDP, GRE, RSVP-TE, or segment routing (SR-ISIS, SR-OSPF, or SR-TE) tunnels
multicast VPRN – NG-MVPN using mLDP with auto-discovery
router interface and Ethernet port Layer 2 encryption – Layer 3 user plane and control plane encryption, Layer 2 encryption of IS-IS and LLDP
NGE is supported on the following adapter cards and platforms:
8-port Gigabit Ethernet Adapter card, version 3
6-port Ethernet 10Gbps Adapter card
10-port 1GigE/1-port 10GigE X-Adapter card, version 2
7705 SAR-Ax
7705 SAR-H (Ethernet and PPP/MLPPP network links)
7705 SAR-Hc
7705 SAR-Wx
7705 SAR-X (Ethernet and PPP/MLPPP network links)
This section contains information about the following topics:
NGE key groups and encryption partitions
The NGE feature allows a tiered approach to managing encryption keys in a network using key groups. This is accomplished by the configuration of services, router interfaces, or Ethernet ports to use specific key groups depending on security policies for the service and network topology.
The following figure shows a typical application of NGE key group partitioning in which there are several critical levels (tiers) of security that need to be considered. In this example, the protection of distribution automation and field area network (DA/FAN) equipment may be considered less critical than the transmission or distribution substation network equipment. It may be ideal to ensure that nodes more at risk of a security breach do not contain more critical information than is necessary. Therefore, encryption keys for the sensitive portions of the network (such as control center traffic) should not be available on nodes that are at risk. The 7705 SAR NGE feature enables operators to partition and distribute encryption keys among different services, NGE domains, or nodal groups in a network. NGE partitions are enabled by configuring different key groups per security partition and applying those key groups as needed.
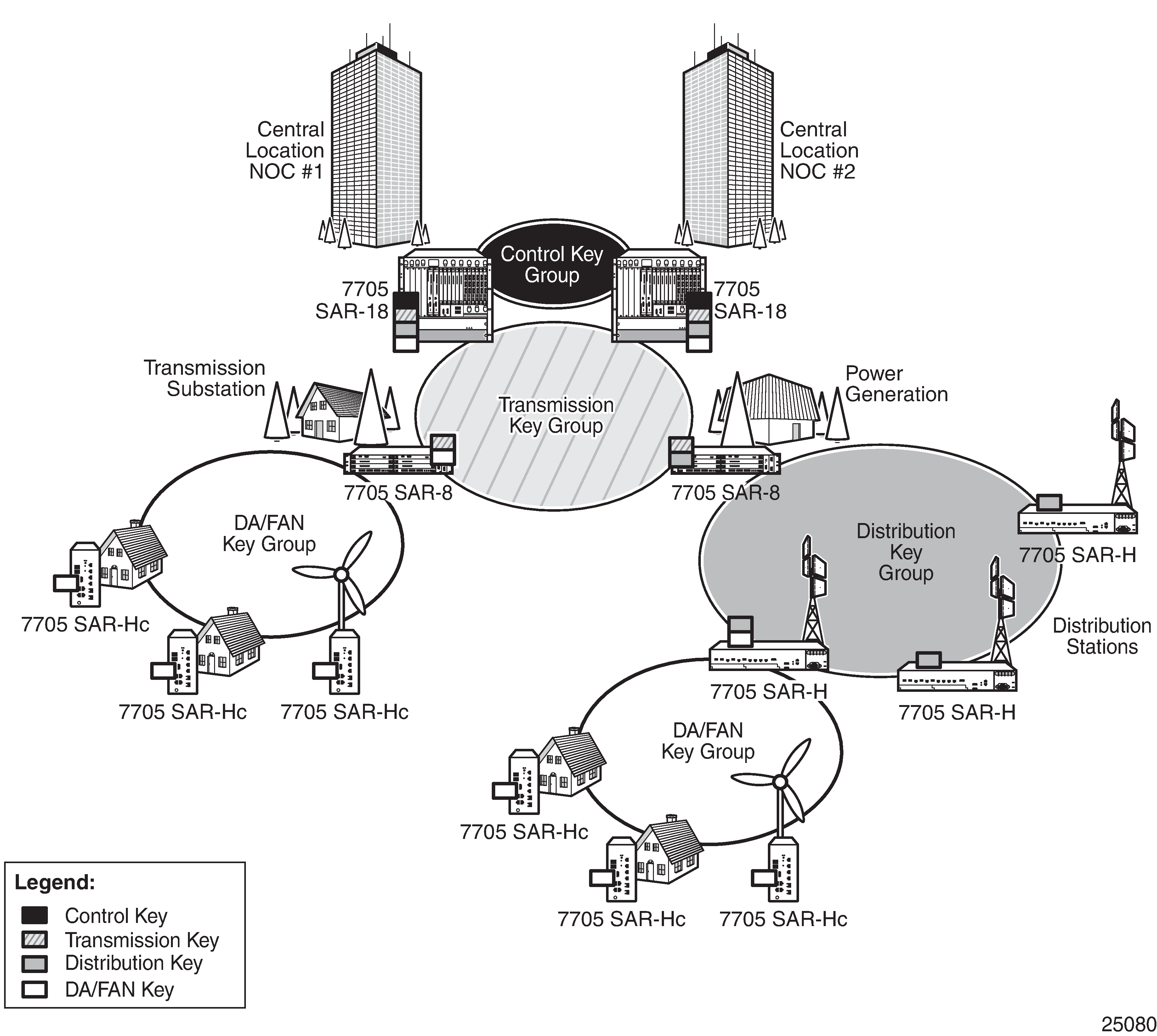
Another application of key group partitioning allows different parts of an organization to have their own method of end-to-end communication without the need to share encryption keys between each organization. If two partitions need to communicate between themselves, gateway nodes configured with both key groups allow inter-organization traffic flows between the key group partitions, as needed.
NGE domains
An NGE domain is a group of nodes and router interfaces forming a network that uses a single key group to create a security domain. NGE domains are created when router interface encryption is enabled on router interfaces that need to participate in the NGE domain. The NSP NFM-P assists operators in managing the nodes and interfaces that participate in the NGE domain. See the NSP NFM-P User Guide for more information.
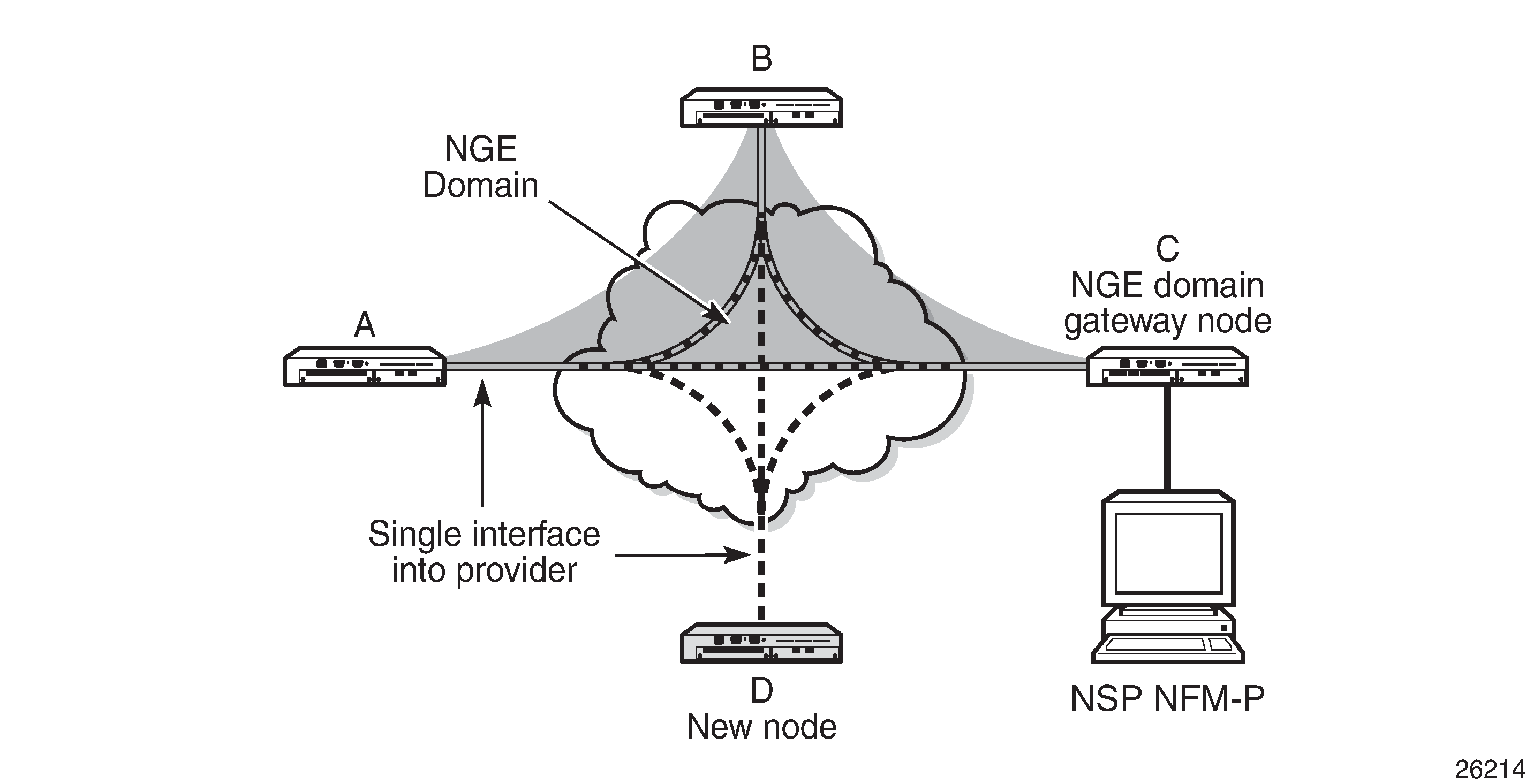
The following figure shows various traffic types crossing an NGE domain.
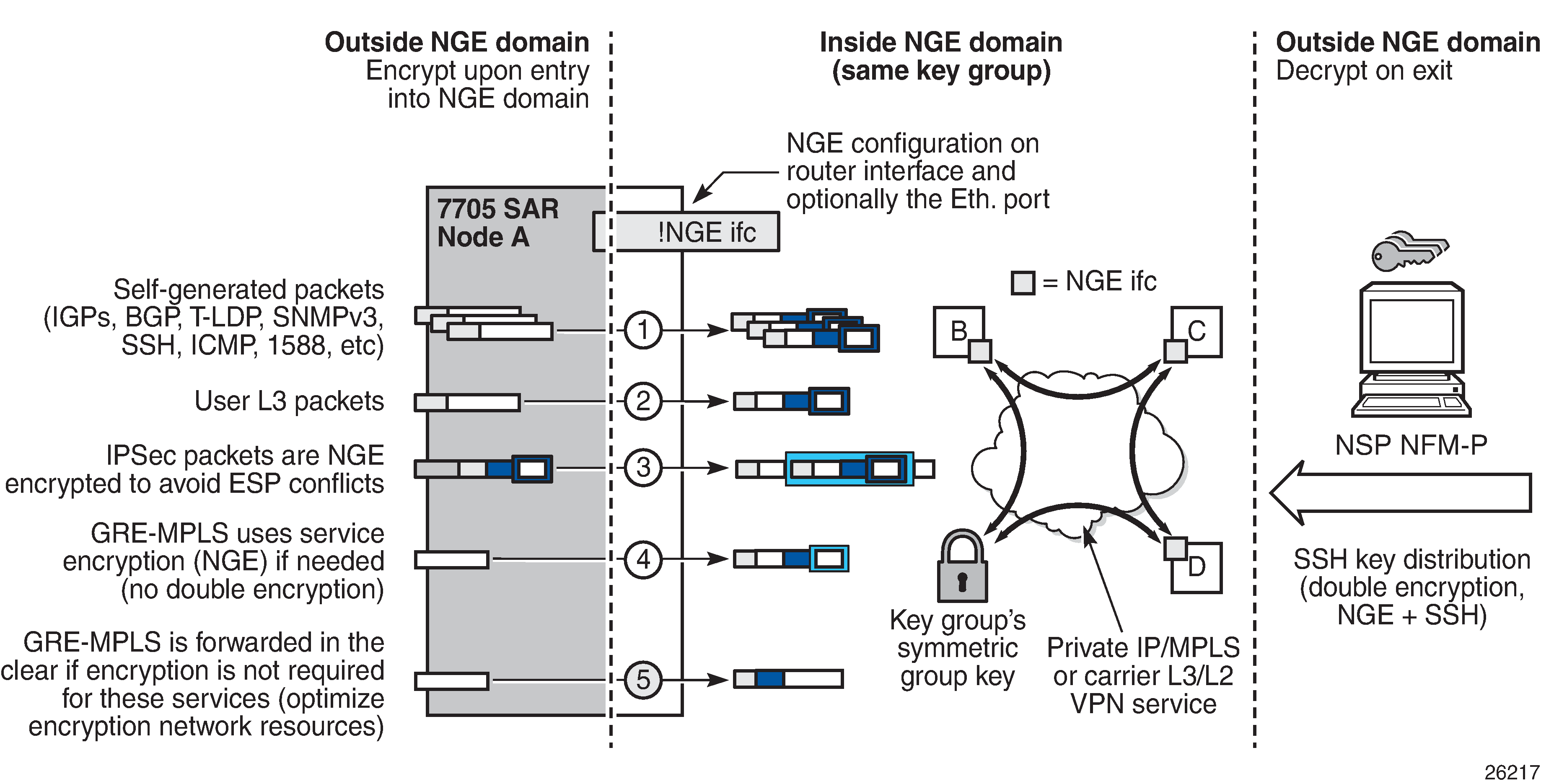
In the figure, nodes A, B, C, and D have router interfaces configured with router interface encryption enabled (and optionally Layer 2 NGE on the Ethernet port). Traffic is encrypted when entering the NGE domain using the key group configured on the router interface and is decrypted when exiting the NGE domain.
Traffic may traverse multiple hops before exiting the NGE domain, yet decryption only occurs on the final node when the traffic exits the NGE domain. Various traffic types are supported and encrypted when entering the NGE domain, as illustrated by the following items on node A in the figure:
item 1: self-generated packets – these packets, which include all types of control plane and management packets such as OSPF, BGP, LDP, SNMPv3, SSH, ICMP, RSVP-TE, and 1588, are encrypted
item 2: user Layer 3 packets – any Layer 3 user packets that are routed into the NGE domain from an interface outside the NGE domain are encrypted
item 3: IPSec packets – IPSec packets are NGE-encrypted when entering the NGE domain to ensure that the IPSec packet’s security association information does not conflict with the NGE domain
GRE-MPLS-based service traffic consists of Layer 3 packets, and router interface NGE is not applied to these types of packets. Instead, service-level NGE is used for encryption to avoid double-encrypting these packets and impacting throughput and latencies. The two types of GRE-MPLS packets that can enter the NGE domain are illustrated by items 4 and 5 in the figure:
item 4: GRE-MPLS packets (SDP or VPRN) with service-level NGE enabled – these encrypted packets use the key group that is configured on the service. The services key group may be different from the key group configured on the router interface where the GRE-MPLS packet enters the NGE domain.
item 5: GRE-MPLS packets (SDP or VPRN) with NGE disabled – these packets are not encrypted and can traverse the NGE domain in clear text. If these packets require encryption, SDP or VPRN encryption must be enabled.
Creating an NGE domain from the NSP NFM-P requires the operator to determine the type of NGE domain being managed. This will indicate whether NGE gateway nodes are required to manage the NGE domain, and other operational considerations. The two types of NGE domains are:
Private IP/MPLS network NGE domain
One type of NGE domain is a private IP/MPLS network, as shown in the following figure.
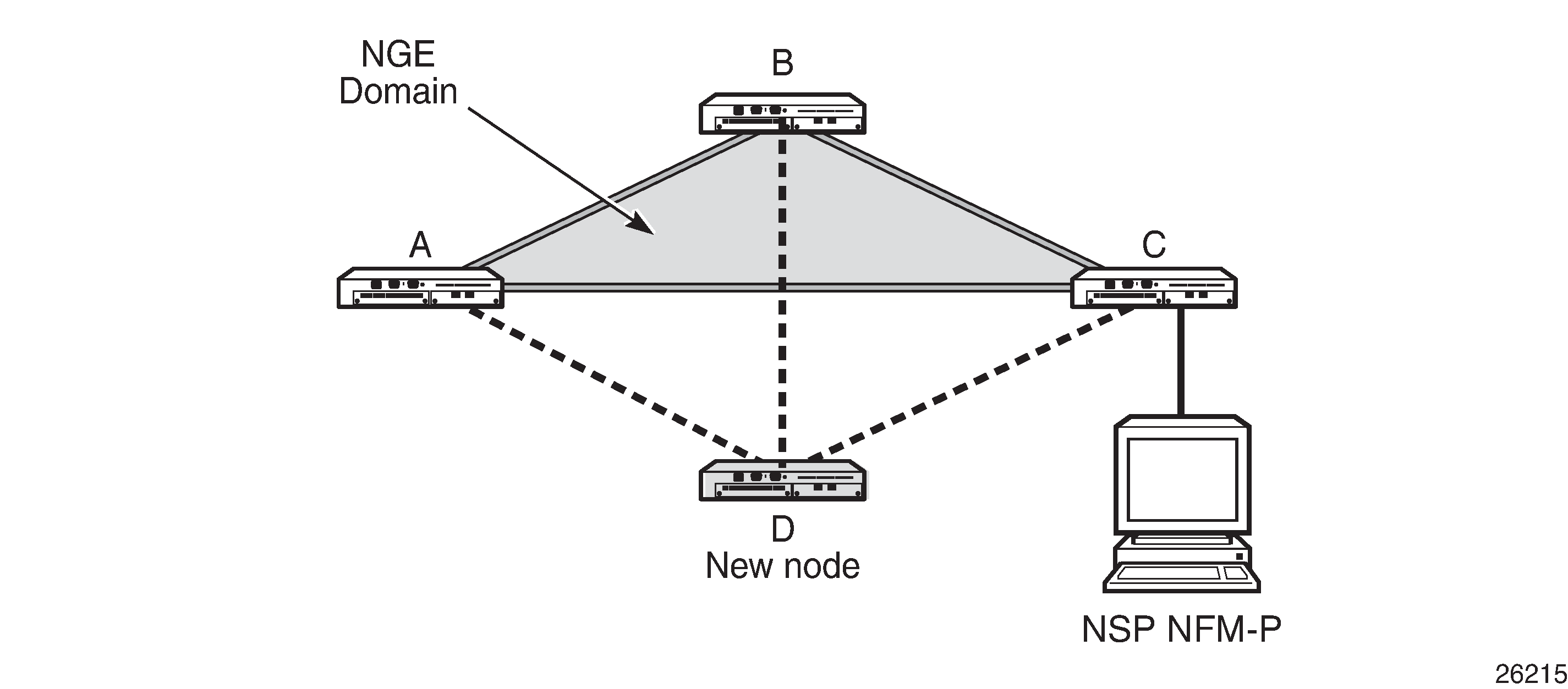
In a private IP/MPLS network NGE domain, all interfaces are owned by the operator and there is no intermediary service provider needed to interconnect nodes. Each interface is a point-to-point private link between private nodes. When a new node is added to this type of NGE domain (node D in the figure), the links that connect node D to the existing nodes in the NGE domain (nodes A, B, and C) must be enabled with NGE router interface encryption. Links from the new node to the existing nodes are enabled one at a time. The NSP NFM-P provides tools that simplify adding nodes to the NGE domain and enabling NGE on their associated interfaces. In this type of NGE domain, each interface is a direct link between two nodes and is not used to communicate with multiple nodes over a broadcast medium offered by an intermediary network. Also, there are no NGE gateway nodes required between the NSP NFM-P and new nodes entering the NGE domain.
Private over intermediary network NGE domain
The other type of NGE domain is a private IP/MPLS network that traverses an intermediary network NGE domain; the intermediary network is used to interconnect nodes in the NGE domain using a multipoint-to-multipoint service. The intermediary network is typically a service provider network that provides a private IP VPN service or a private VPLS service used to interconnect a private network that does not mimic point-to-point links as described in Private IP/MPLS network NGE domain.
This type of NGE domain is shown in the following figure.
Private over intermediary network NGE domains have nodes with links that connect to a service provider network where a single link can communicate with multiple nodes over a Layer 3 service such as a VPRN or a Layer 2 service such as VPLS. In the figure, node A has NGE enabled on its interface with the service provider and uses that single interface to communicate with nodes B and C, and eventually with node D when node D has been added to the NGE domain. This type of NGE domain requires the recognition of NGE gateway nodes that allow the NSP NFM-P to reach new nodes that enter the domain. Node C is designated as a gateway node.
When node D is added to the NGE domain, it must first have the NGE domain key group downloaded to it from the NSP NFM-P. The NSP NFM-P creates an NGE exception ACL on the gateway node, C, to allow communication with node D using SNMPv3 and SSH through the NGE domain. After the key group is downloaded, the NSP NFM-P enables router interface encryption on node D’s interface with the service provider and node D is now able to participate in the NGE domain. The NSP NFM-P automatically removes the IP exception ACL from node C when node D enters the NGE domain.
See Router interface NGE domain concepts for more information.
Network Services Platform management
The NGE feature is tightly integrated with the NSP NFM-P. The following functions are provided by the NSP NFM-P :
-
managing and synchronizing encryption and authentication keys within key groups on a network-wide basis
-
configuring NGE on MPLS services and managing associated key groups
-
configuring NGE on router interfaces and Ethernet ports and managing associated key groups
-
coordinating network-wide rekeying of key groups
The NSP NFM-P acts as the key manager for NGE-enabled nodes and allocates the keys in key groups that are used to perform encryption and authentication. The NSP NFM-P ensures that all nodes in a key group are kept in synchronization and that only the key groups that are relevant to the associated nodes are downloaded with key information.
The NSP NFM-P performs network-wide hitless rekeying for each key group at the rekeying interval specified by the operator. Different key groups can be rekeyed at different times as needed, or all key groups can be rekeyed network-wide at the same time.
For more information about NSP NFM-P management, see the ‟Service Management” section in the NSP NFM-P User Guide.
Key groups
Key groups are used to organize encryption keys into distinct groups that allow a user to partition the network based on security requirements. A key group contains the following elements:
an encryption algorithm – see Key group algorithms
an authentication algorithm – see Key group algorithms
a list of security associations (SAs) – see Security associations
an active outbound SA – see Active outbound SA
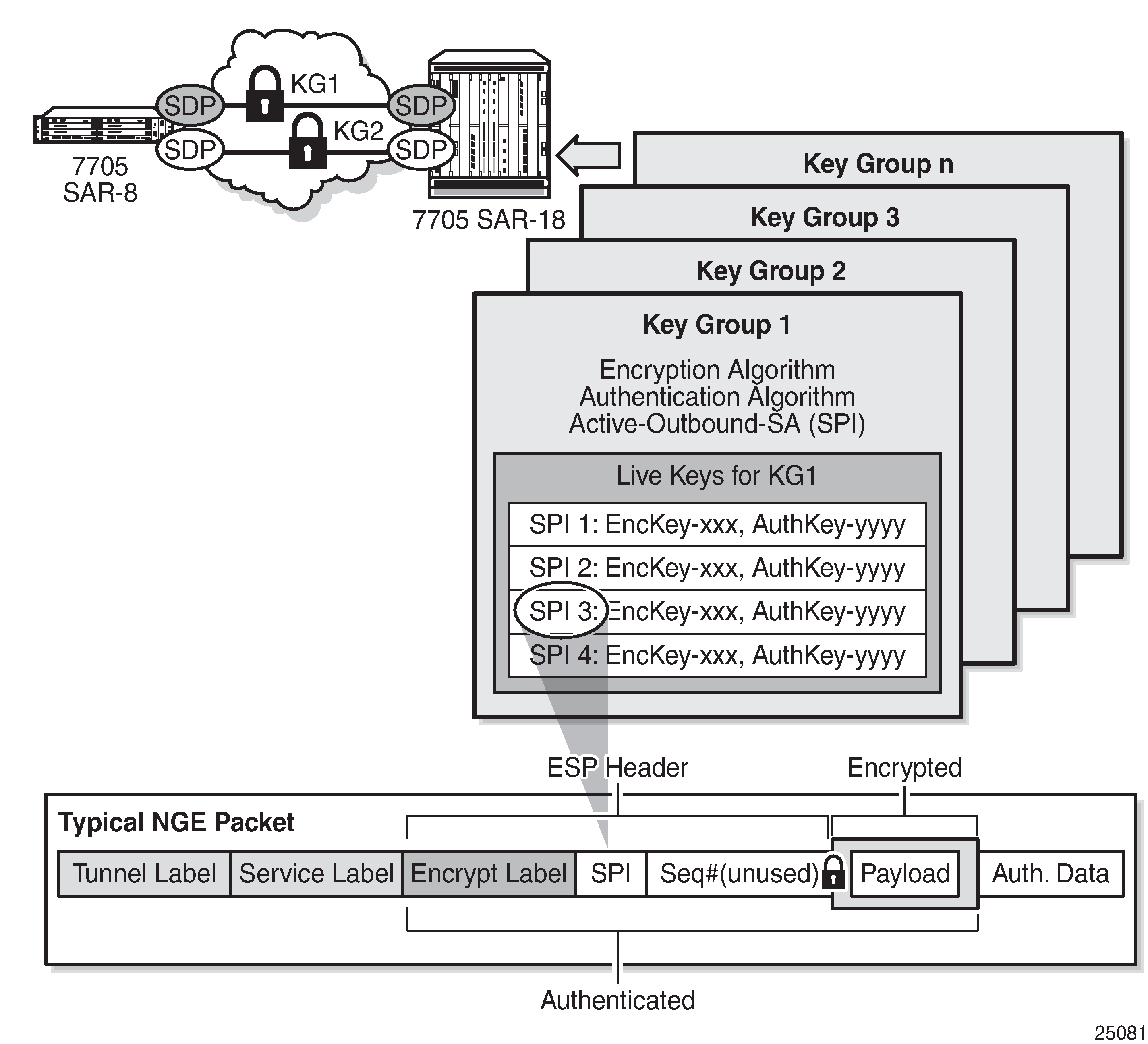
The following figure illustrates the use of key groups (KGs), security associations (SAs), and security parameter indexes (SPIs). The 7705 SAR-8 Shelf V2 and 7705 SAR-18 both have the same set of key groups configured. One path uses key group 1 (KG1) and the other uses key group 2 (KG2). Each key group contains the elements listed above. Key group 1 has four live keys, SPI_1 through SPI_4, and SPI_3 is the active outbound SA. The active outbound SA is identified by its SPI, and this SPI is embedded in the NGE packet.
Each SA listed in a key group, indexed by an SPI, specifies a single key for encryption and a single key for authentication. Packets transmitted or received that reference a particular SPI use the keys in the SA for that SPI when performing encryption and authentication.
Before enabling encryption, key groups must be configured on the node. Only after a key group is configured can it be assigned to an SDP or VPRN services.
Key group algorithms
All SAs configured in a key group share the same encryption algorithm and the same authentication algorithm. The size and values required by a particular key depend on the requirements of the algorithms selected. One encryption algorithm and one authentication algorithm must be selected per key group.
Encryption algorithms available per key group include:
AES128 (a 128-bit key, requiring a 32-digit ASCII hexadecimal string)
AES256 (a 256-bit key, requiring a 64-digit ASCII hexadecimal string)
Authentication algorithms available per key group include:
HMAC-SHA-256 (a 256-bit key, requiring a 64-digit ASCII hexadecimal string)
HMAC-SHA-512 (a 512-bit key, requiring a 128-digit ASCII hexadecimal string)
Encryption and authentication strengths can be mixed depending on the requirements of the application. For example, 256-bit strength encryption can be used with 512-bit strength authentication.
The configured algorithms cannot be changed when there is an existing SA configured for the key group. All SAs in a key group must be deleted before a key group algorithm can be modified.
Key values are not visible in CLI or retrievable using SNMP. Each node calculates a 32-bit CRC checksum for the keys configured against the SPI. The CRC can be displayed in the CLI or read by SNMP. The purpose of the CRC is to provide a tool to check consistency between nodes, thereby verifying that each node is set with the same key values while keeping the actual key values hidden.
Encapsulating security payload
The NGE feature uses the encapsulating security payload (ESP) protocol according to IETF RFC 4303. ESP maintains data integrity, ensuring privacy and confidentiality for encrypted traffic.
The ESP protocol used by NGE relies on symmetric ciphers, meaning that the same key is used for encryption and decryption. The 7705 SAR supports Cipher Block Chaining (CBC) encryption mode. Block ciphers used by NGE include:
AES128 with a 128-bit key using 128-bit blocks
AES256 with a 256-bit key using 128-bit blocks
For authentication, the integrity check value (ICV) size is as follows:
HMAC-SHA-256 (16 bytes or 128 bits)
HMAC-SHA-512 (32 bytes or 256 bits)
Security associations
Each key group has a list of up to four security associations (SAs). An SA is a reference to a pair of encryption and authentication keys that are used to decrypt and authenticate packets received by the node and to encrypt packets leaving the node.
For encrypted ingress traffic, any of the four SAs in the key group can be used for decryption if there is a match between the SPI in the traffic and the SPI in the SA. For egress traffic, only one of the SAs can be used for encryption and is designated as the active outbound SA. Key groups and a typical NGE packet illustrates these relationships.
As shown in the figure, each SA is referenced by an SPI value, which is included in packets during encryption and authentication. SPI values must be numerically unique throughout all SAs in all key groups. If an SPI value is configured in one key group and an attempt is made to configure the same SPI value in another key group, the configuration is blocked.
Active outbound SA
The active outbound SA is specified by the SPI referencing the specific SA used to encrypt and authenticate packets egressing the node for the SDP or service using the key group. The SPI value for the active outbound SA is included in the ESP header of packets being encrypted and authenticated.
Services encryption
The NGE feature provides the ability to encrypt MPLS services using key groups that are configured against these services. These services include:
VLL service (Epipe and Cpipe)
VPRN service using Layer 3 spoke-SDP termination
IES service using Layer 3 spoke-SDP termination
VPLS service using spoke and mesh SDPs
routed VPLS service into a VPRN or IES
MP-BGP-based VPRNs
NG-MVPN
For services that use SDPs, all tunnels may be either MPLS LSPs (RSVP-TE, LDP, or static LSP) or GRE tunnels. NGE is not supported for IP tunnels.
For MP-BGP services, resolving routes using spoke SDPs (spoke-sdp) or autobind SDPs (auto-bind-tunnel) is supported using LDP, GRE, RSVP-TE, or segment routing (SR-ISIS, SR-OSPF, or SR-TE).
In addition, the 7705 SAR supports VLL, VPLS, and VPRN NGE interactions that use segment routing with entropy labels.
This section contains information about the following topics:
Services encryption overview
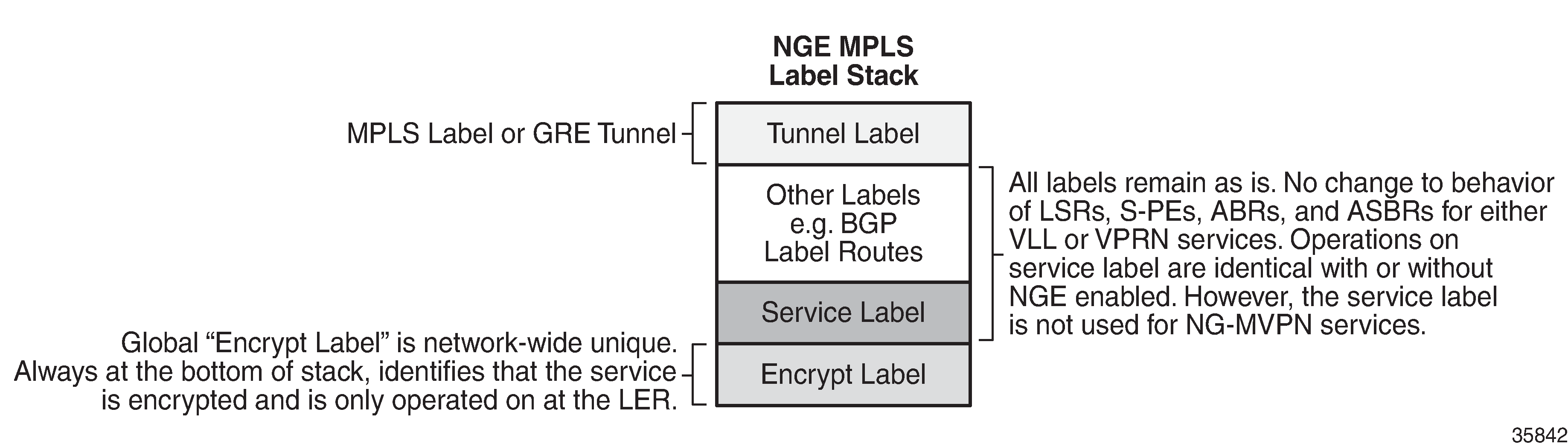
NGE adds a global encryption label to the label stack for encrypting MPLS services. The global encryption label must be a unique network-wide label; in other words, the same label must be used on all nodes in the network that require NGE services. The label must be configured on individual nodes before NGE can become operational on those nodes.
The global encryption label is used to identify packets that have an NGE-encrypted payload and is added to the bottom of the stack. This allows network elements such as LSRs, ABRs, ASBRs, and RRs to forward NGE packets without needing to understand NGE or to know that the contents of these MPLS packets are encrypted. Only when a destination PE (7705 SAR) receives a packet that needs to be understood at the service layer does the PE check for an encryption label and then decrypt the packet.
When the global encryption label is set, it should not be changed. If the label must be changed without impacting traffic, all key groups in the system should first be deleted. Next, the label should be changed, and then all key groups should be reconfigured.
The NSP NFM-P helps to coordinate the distribution of the global encryption label and ensures that all nodes in the network are using the same global encryption label.
The following figure illustrates the NGE MPLS/GRE label stack.
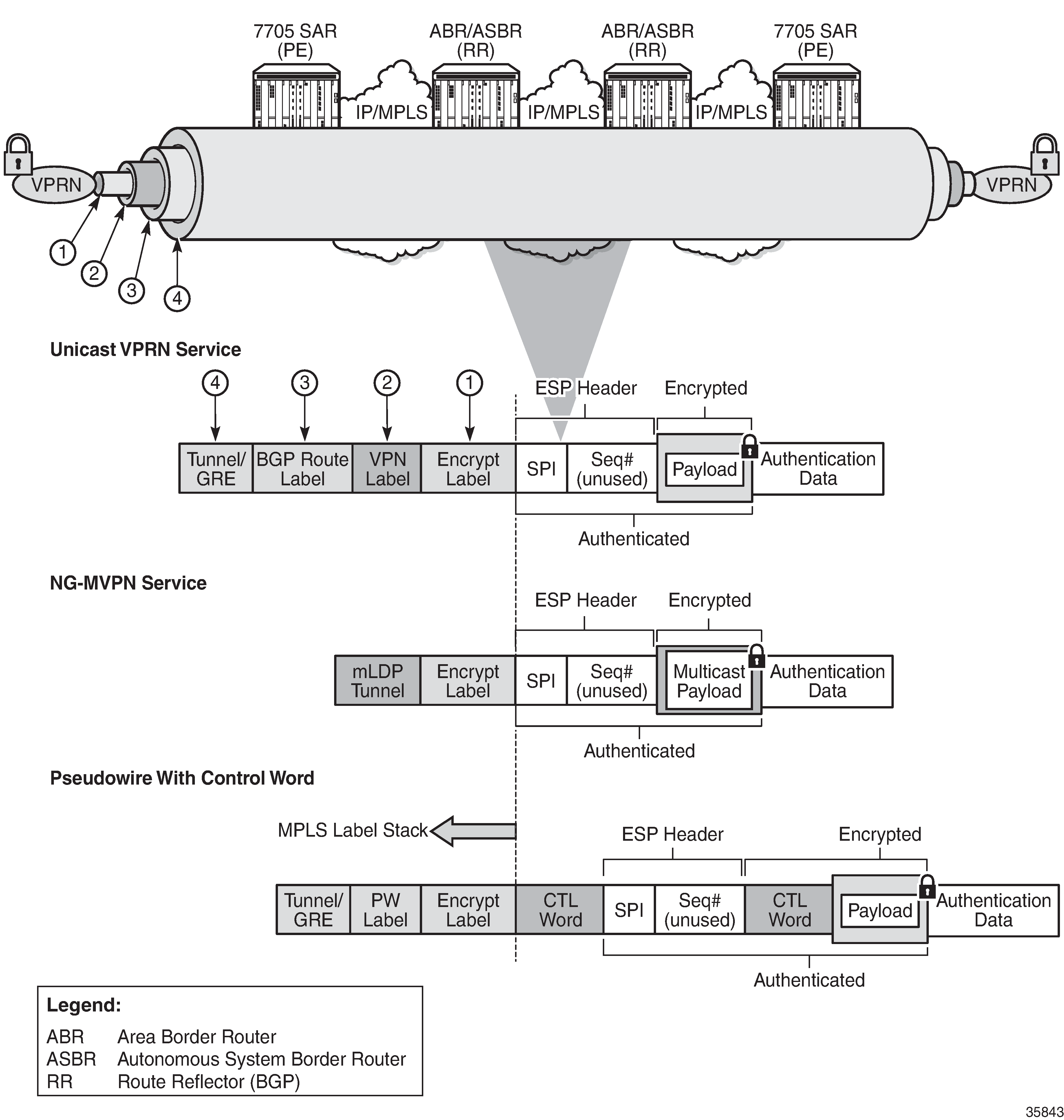
The following figure illustrates VPRN and PW (with control word) packet formats using NGE encryption.
Assigning key groups to services
Assigning key groups to services requires configuring an inbound and outbound key group for directional processing on a per-service basis, as shown in the following figure.
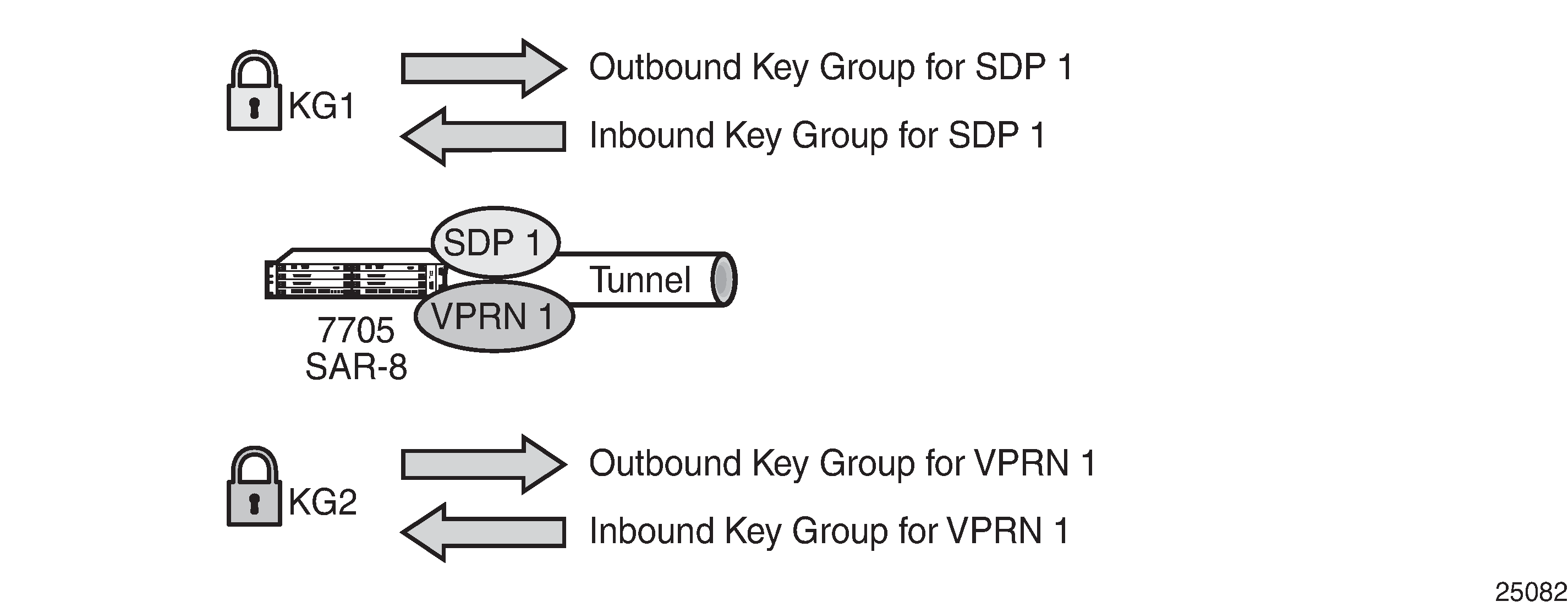
The outbound key group identifies which key group to use for traffic that egresses the node for the service. The inbound key group ensures that ingress traffic is using the correct key group for the service.
If the inbound key group is not set, the node ensures that packets are either unencrypted or are using one of the valid key groups configured in the system.
In most deployment scenarios, the inbound and outbound key groups are identical. However, it is possible to configure different key groups as the outbound and the inbound key groups, as this is not checked by the node. Using different key groups in this way is not typical.
Including an inbound and outbound direction when assigning key groups to services allows users to:
gracefully enable and disable NGE for services
move services from one key group domain to another domain without halting encryption
The NGE feature makes use of the NSP NFM-P to help manage the assignment of key groups to services on a network-wide basis. See the NSP NFM-P User Guide for more information.
Pseudowire switching for NGE traffic
For VLL services, the 7705 SAR supports pseudowire (PW) switching of encrypted traffic from one PW to another. There are three scenarios that are supported on the 7705 SAR with regard to PW switching of traffic:
PW switching using the same key group
When a PW is using an encrypted SDP, the PW may be switched to another PW that is also using an encrypted SDP, and both SDPs are in the same key group. For this case, to perform the PW switch, the 7705 SAR leaves the encrypted payload unchanged and swaps the labels as needed for passing traffic between PWs.
PW switching using different key groups
When a PW is using an encrypted SDP, the PW may be switched to another PW that is also using an encrypted SDP, but both SDPs are in different key groups. For this case, the 7705 SAR decrypts the traffic from the first SDP by using the configured key group for that SDP and then re-encrypts the traffic by using the egress SDP's key group egress SPI ID.
PW switching between an encrypted and unencrypted PW
When traffic is switched from an encrypted PW to an unencrypted PW, the traffic is decrypted before it is sent. When traffic is switched from an unencrypted PW to an encrypted PW, the traffic is encrypted before it is sent.
See Pseudowire switching for more information.
Pseudowire control word for NGE traffic
The control word is a configurable option for PWs and is included in PW packets when it (the control word) is configured. When control-word is enabled and NGE is used, the datapath creates two copies of the CW. One CW is both encrypted and authenticated, and is inserted after the ESP header. The other CW is not encrypted (clear form) and is inserted before the ESP header.
For cases where PW switching is configured, the 7705 SAR ensures—in the CLI and with SNMP—that both segments of the PW have consistent configuration of the control word when encryption is being used.
See Pseudowire control word for more information.
VPRN Layer 3 spoke-SDP encryption and MP-BGP-based VPRN encryption interaction
The encryption configured on an SDP used to terminate the Layer 3 spoke SDP of a VPRN always overrides any VPRN-level configuration for encryption:
-
When VPRN encryption is enabled, all routes resolved via MP-BGP (either with spoke SDPs using spoke-sdp or autobind SDPs using auto-bind-tunnel) are encrypted or decrypted using the VPRN key group.
-
When Layer 3 spoke-SDP encryption is enabled, all routes resolved via the Layer 3 interface are encrypted or decrypted using the SDP's key group.
Some examples are as follows:
-
If a VPRN is enabled for encryption while a Layer 3 spoke SDP for the same VPRN is using an SDP that is not enabled for encryption, then traffic egressing the spoke SDP is not encrypted.
-
If a VPRN is disabled for encryption while a Layer 3 spoke SDP for the same VPRN is using an SDP that is enabled for encryption, then traffic egressing the spoke SDP is encrypted.
-
If a VPRN is enabled for encryption using key group X, while a Layer 3 spoke SDP for the same VPRN is using key group Y, then traffic egressing the spoke SDP is encrypted using key group Y.
The commands used for these scenarios are config>service>sdp>encryption-keygroup and config>service>vprn>encryption-keygroup.
NGE and RFC 3107
When RFC 3107 is enabled on the node and NGE traffic is crossing the RR between two VPRN domains, the same key group must be used between the two domains.
NGE for NG-MVPN
NGE is supported for NG-MVPN services with multicast configurations that include:
-
I-PMSI
-
S-PMSI
-
C-multicast signaling
-
mLDP multicast tunnel LSPs
For more information about MVPN, see Multicast VPN (MVPN).
When r-VPLS is configured for the VPRN, the node can act as a receiver for an NG-MVPN service that is NGE -encrypted. The node cannot act as a source of NG-MVPN traffic from a VPLS service, so the source of this NG-MVPN traffic must originate from another node that supports that capability.
When NGE is enabled in a VPRN with NG-MVPN-based services, transit nodes (LSRs) have no knowledge that NGE is being employed or that the NGE encryption label is being used with an ESP header after the NGE label. Features that inspect packet contents to make further decisions are not supported and must be disabled for mLDP multicast paths that need to carry NG-MVPN traffic that is NGE-encrypted. These features include:
-
ingress multicast path management (7750 SR only)
-
IP-based LSR hashing
The packet inspection restriction includes any third-party routing function that may inspect the packet contents after the mLDP transport label and is expecting a non-encrypted payload in order to make hashing decisions.
Router interface encryption
The 7705 SAR supports Layer 3 encryption on router interfaces for IPv4 traffic. NGE is not supported on dual-stack IPv4/IPv6 or IPv6-only interfaces.
NGE is enabled on a router interface by configuring the group-encryption command on the router interface. The interface is considered part of the NGE domain, and any received packets that are NGE-encrypted are decrypted if the key group is configured on the node. To encrypt packets egressing the interface, the outbound key group must be configured on the interface. All IP packets, such as self-generated traffic or packets forwarded from router interfaces that are not inside the NGE domain, are encrypted when egressing the interface. There are some exceptions to this general behavior, as described in the sections below; for example, GRE-MPLS packets are not encrypted when router interface encryption is enabled.
The outbound and inbound key groups configured on the router interface determine which keys to use to encrypt and decrypt traffic.
To perform encryption, router interface encryption reuses the IPSec transport mode packet format as shown in the following figure.
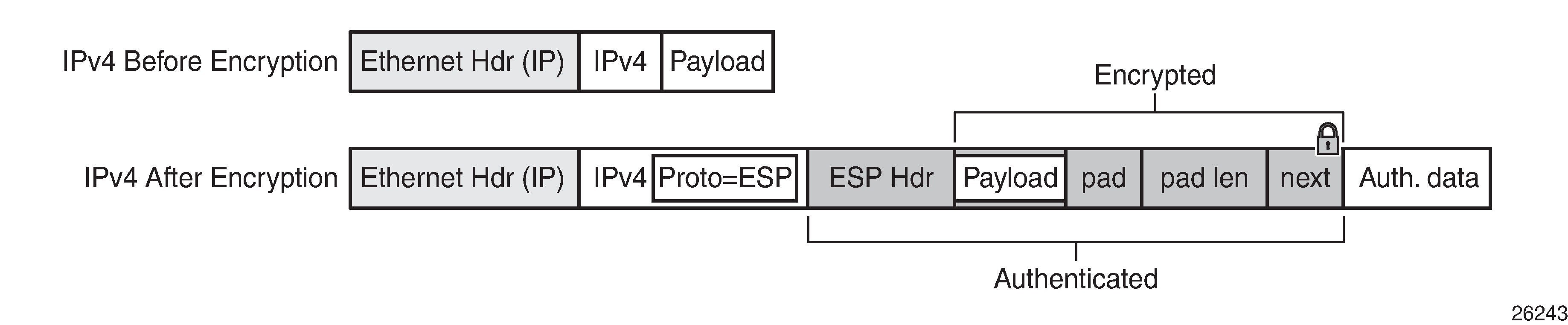
The protocol field in the IP header of an NGE packet is always set to ‟ESP”. Within an NGE domain, the SPI that is included in the ESP header is always an SPI for the key group configured on the router interface. Other fields in the IP header, such as the source and destination addresses, are not altered by NGE router interface encryption. Packets are routed through the NGE domain and decrypted when the packet leaves the NGE domain.
The group keys used on an NGE-enabled router interface provide encryption of broadcast and multicast packets within the GRT. For example, OSPF uses a broadcast address to establish adjacencies, which can be encrypted by NGE without the need to establish point-to-point encryption tunnels. Similarly, multicast packets are also encrypted without point-to-point encryption tunnels.
Router interface NGE domain concepts
An NGE domain is a group of nodes whose router interfaces in the base routing context (GRT) are enabled for router interface NGE or whose ports are enabled for encryption of some types of Layer 2 traffic. An interface without router interface NGE enabled is considered to be outside the NGE domain. NGE domains use only one key group when the domain is created; however, two key groups may be active at once if some links within the NGE domain are in transition from one key group to the other.
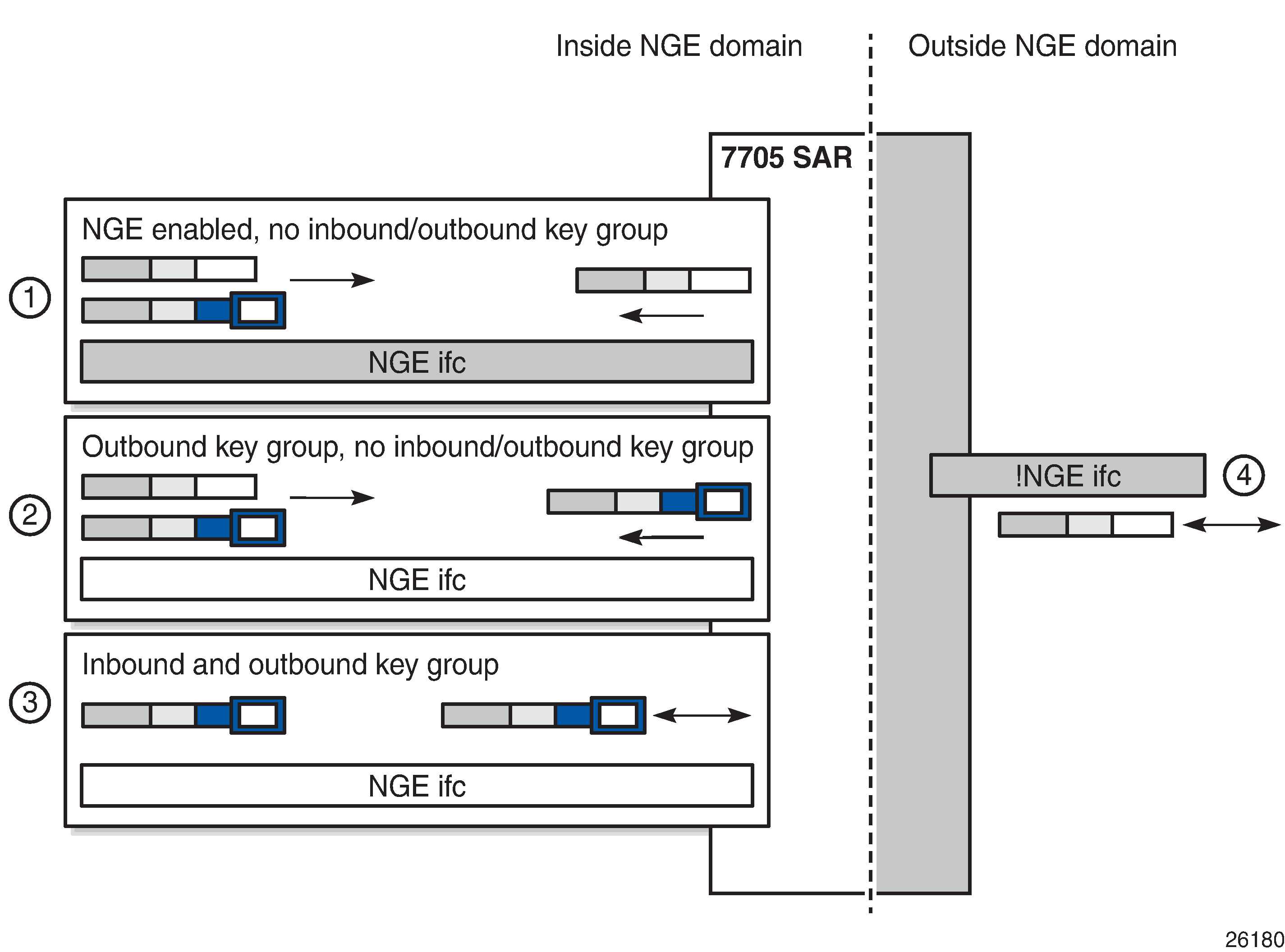
The following figure illustrates the NGE domain concept and the table describes the three configuration scenarios inside the NGE domain.
Key |
Description |
|---|---|
1 |
NGE enabled, no inbound/outbound key group Outbound packets are sent without encrypting. Inbound packets can be NGE-encrypted or clear text. |
2 |
Outbound key group, no inbound key group Outbound packets are encrypted using the interface key group if not already encrypted. Inbound packets can be NGE-encrypted or clear text. |
3 |
Inbound and outbound key group Outbound packets are encrypted using the interface key group if not already encrypted. Inbound packets must be encrypted using the interface key group keys. |
4 |
Outside the NGE domain, the interface is not configured for NGE. Any ESP packets are IPSec packets. |
A router interface is considered to be inside the NGE domain when it has been configured with group-encryption on the interface. When group-encryption is configured on the interface, the router can receive unencrypted packets or NGE-encrypted packets from any configured key group on the router, but any other type of IPSec-formatted packet is not allowed. If an IPSec-formatted packet is received on an interface that has group-encryption enabled, it will not pass NGE authentication and will be dropped. Therefore, IPSec packets cannot exist within the NGE domain without first being converted to NGE packets. This conversion requirement delineates the boundary of the NGE domain and other IPSec services.
When NGE router interface encryption is enabled and only an outbound key group is configured, the interface can receive unencrypted packets or NGE-encrypted packets from any configured key group on the router. All outbound packets are encrypted using the outbound key group if the packet was not already encrypted further upstream in the network.
When NGE router interface encryption has been configured with both an inbound and outbound key group, only NGE packets encrypted with the key group security association can be sent and received over the interface.
When there is no NGE router interface encryption, the interface is considered outside the NGE domain where NGE is not applied.
GRE-MPLS packets inside the NGE domain
NGE router interface encryption is never applied to GRE-MPLS packets that are used to transport MPLS services over Layer 3 networks; for example, GRE with the GRE protocol ID set to MPLS Unicast (0x8847) or Multicast (0x8848). GRE-MPLS packets that enter the NGE domain or transit the NGE domain are forwarded as is.
Because GRE-MPLS packets provide transport for MPLS-based services, they already use the NGE services-based encryption techniques for MPLS, such as SDP or VPRN-based encryption. To avoid double encryption, the packets are left in clear text when entering an NGE domain or crossing intermediate nodes in the NGE domain, and are simply forwarded as needed when exiting an NGE domain.
The payload of these GRE-MPLS packets can also be sent in clear text depending on the security requirements that are configured for the MPLS service.
GRE packets with the protocol set to other protocols are encrypted using NGE router interface encryption.
Router encryption exceptions using ACLs
In some cases, Layer 3 packets may need to cross the NGE domain in clear text, such as when an NGE-enabled router needs to peer with a non-NGE-capable router to exchange routing information. This can be accomplished by using a router interface NGE exception filter applied on the router interface for the required direction, inbound or outbound.
The following figure shows the use of a router interface NGE exception filter.
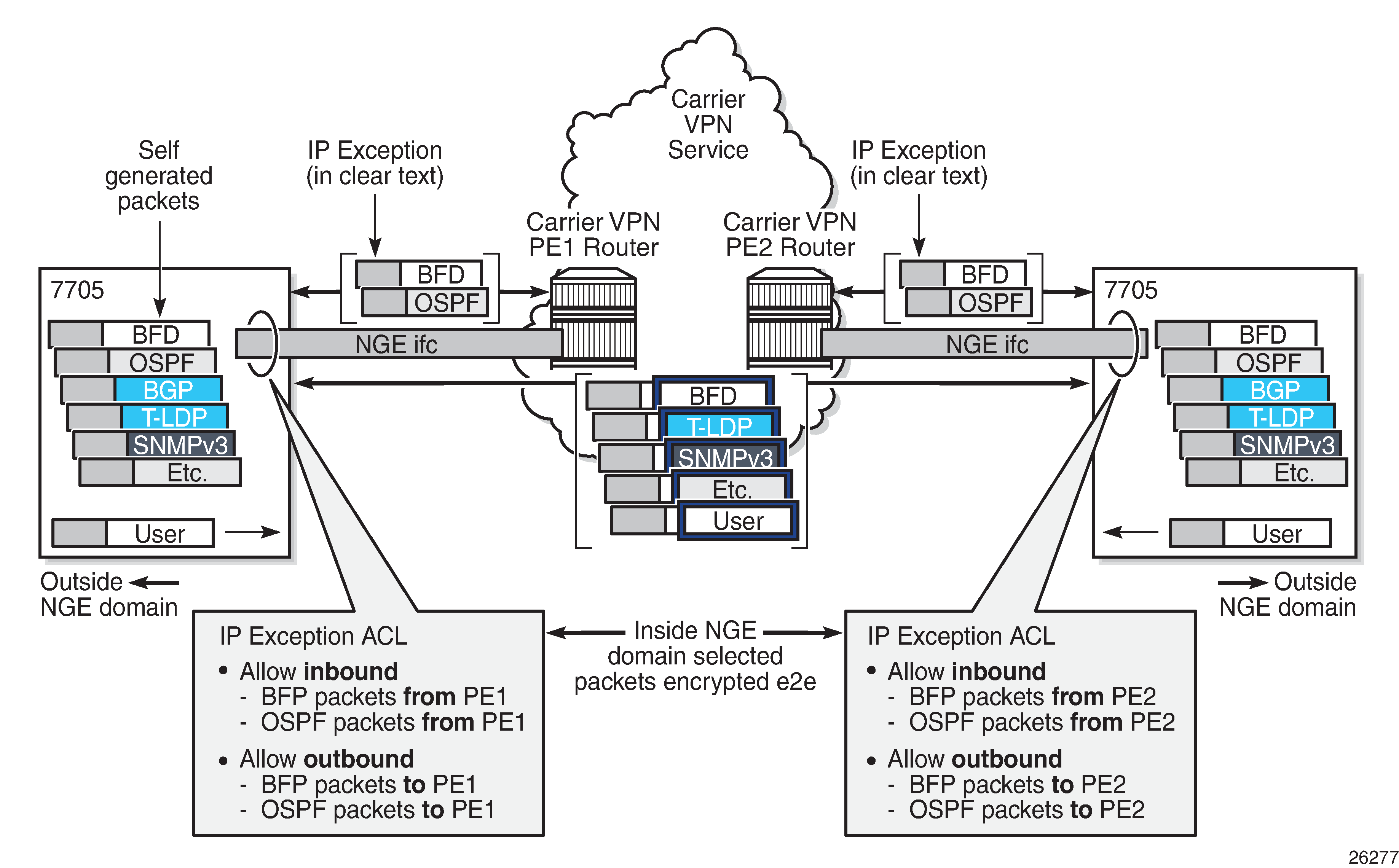
The inbound or outbound exception filter is used to allow specific packet flows through the NGE domain in clear text, where there is an explicit inbound and outbound key group configured on the interface. The behavior of the exception filter for each router interface configuration is as follows:
NGE enabled, no inbound/outbound key group – in this scenario, the router does not encrypt outbound traffic, and so the outbound exception filter is not applied. The router can still receive inbound NGE packets, so the exception filter is applied to inbound packets. If the filter detects a match, clear text packets can be received and forwarded by the router.
outbound key group, no inbound key group – the outbound exception filter is applied to outbound traffic, and packets that match the filter are not encrypted on egress. The router can receive inbound NGE packets without an inbound key group set and applies the exception filter to inbound packets. If the filter detects a match, clear text packets can be received and forwarded by the router.
inbound and outbound key group – the inbound and outbound exception filters are applied, and any packets that match are passed in clear text
IPSec packets crossing an NGE domain
IPSec packets can cross the NGE domain because they are still considered Layer 3 packets. To avoid confusion between the security association used in an IPSec packet and the one used in a router interface NGE packet, the router always applies NGE to any IPSec packet that traverses the NGE domain.
IPSec packets that originate from a router within the NGE domain are not allowed to enter the NGE domain. The only exception to this restriction is OSPFv3 packets.
The following figure shows how IPSec packets can transit an NGE domain.
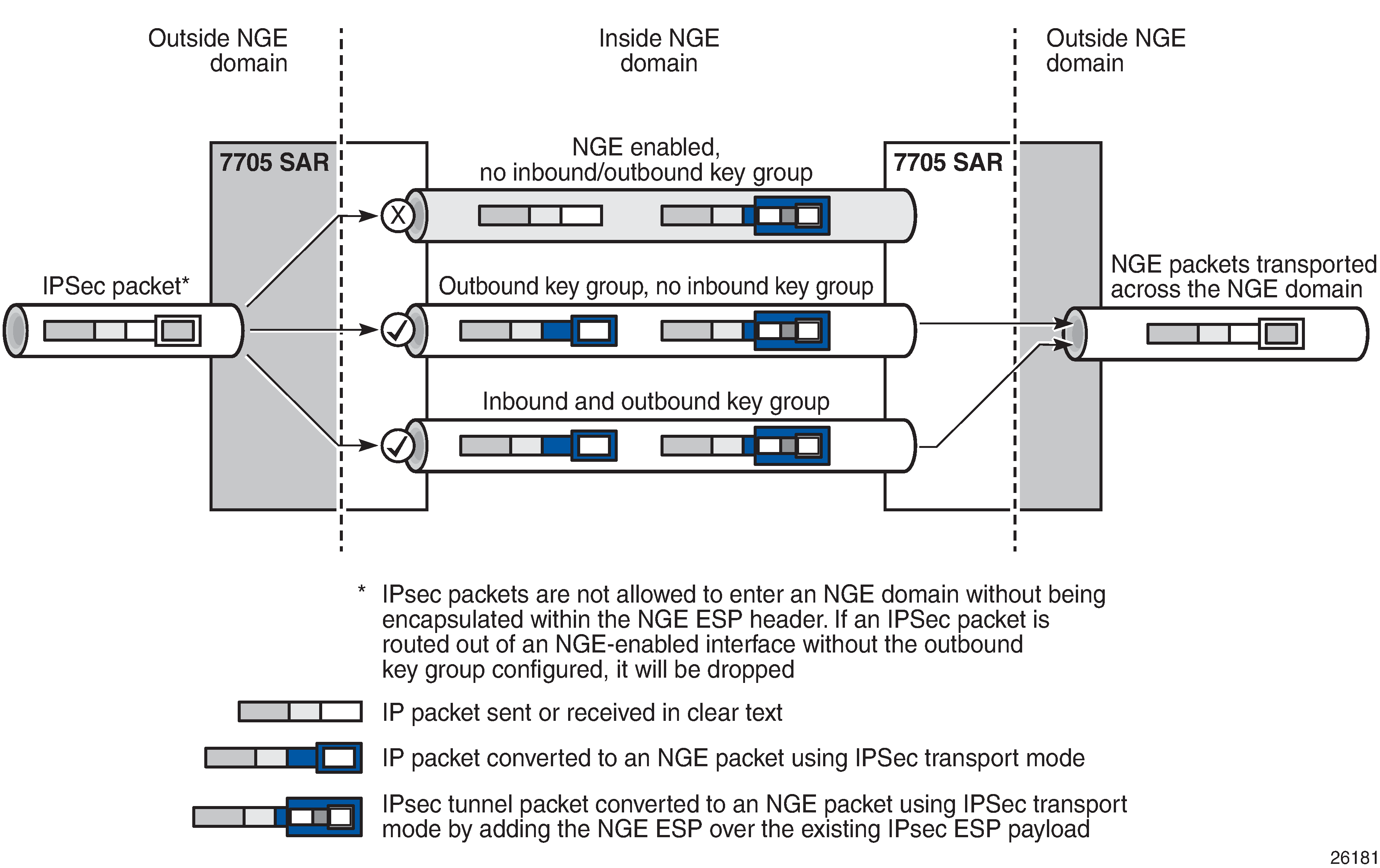
An IPSec packet enters the router from outside the NGE domain. When the router determines that the egress interface to route the packet is inside an NGE domain, it selects an NGE router interface with one of the following configurations:
NGE enabled with no inbound or outbound key group configured – this link cannot forward the IPSec packet without adding the NGE ESP, but because nothing is configured for the outbound key group, the packet must be dropped
NGE enabled with outbound key group configured and no inbound key group configured – the packet originates outside the NGE domain, so the router adds an ESP header over the existing ESP and encrypts the payload using the NGE domain keys for the configured outbound key group
NGE enabled with both inbound and outbound key groups configured – the packet originates outside the NGE domain, so the router adds an ESP header over the existing ESP and encrypts the payload using the NGE domain keys for the configured outbound key group
OSPFv3 IPSec support also uses IPSec transport mode packets. These packets originate from the CSM, which is considered outside the NGE domain; however, the above rules for encapsulating the packets with an NGE ESP apply and allow these packets to successfully transit the NGE domain.
Multicast packets traversing the NGE domain
Multicast packets that traverse an NGE domain can be categorized into two main scenarios:
scenario 1 – multicast packets that ingress the router on an interface that is outside the NGE domain. These packets can egress a variety of interfaces that are either inside or outside the NGE domain.
scenario 2 – multicast packets that ingress the router on an interface that is inside the NGE domain. These packets can egress a variety of interfaces that are either inside or outside the NGE domain. This scenario has two cases:
scenario 2a – the ingress multicast packet is not yet NGE-encrypted
scenario 2b – the ingress multicast packet is NGE-encrypted
The following figure shows these scenarios.
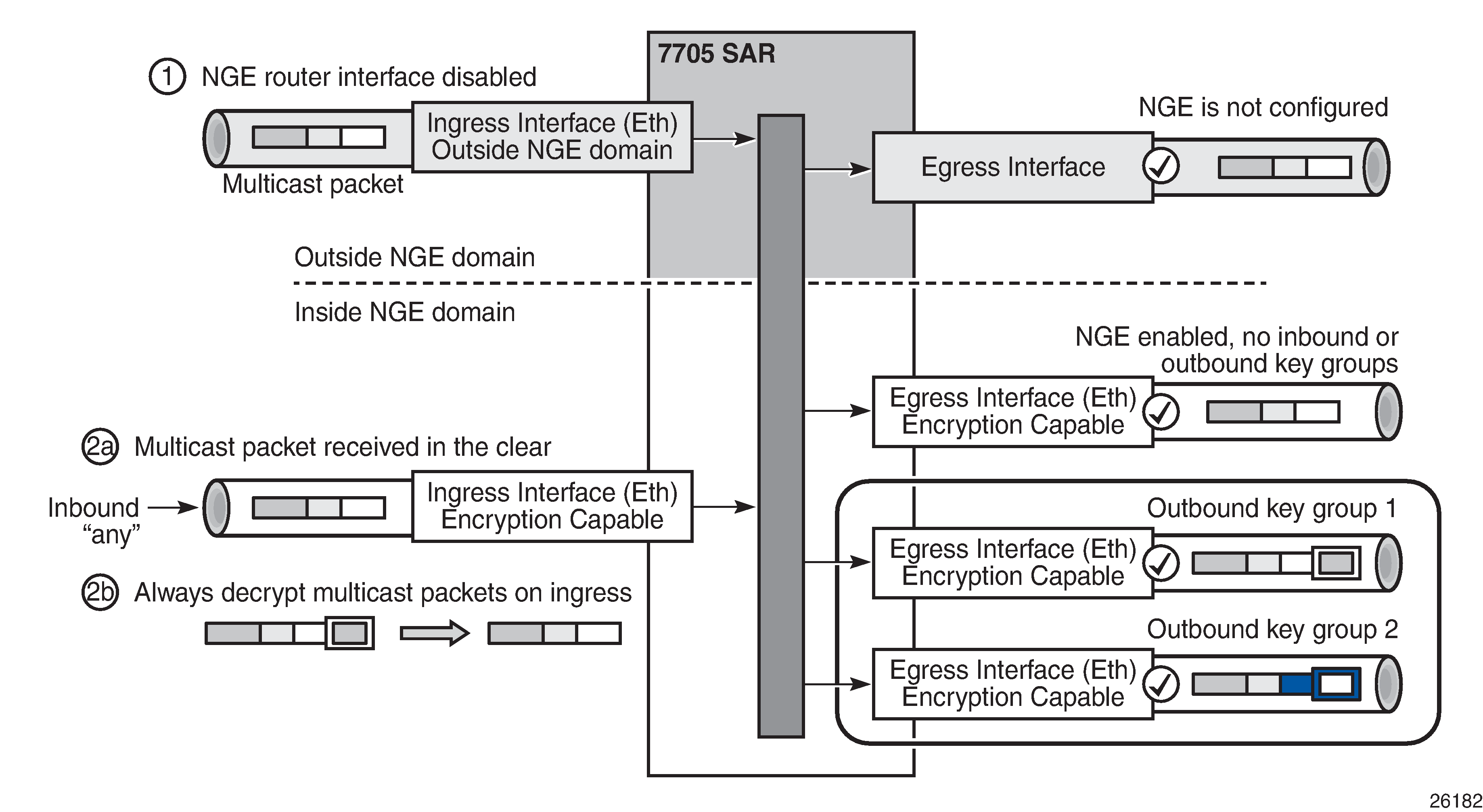
Multicast packets received from outside the NGE domain (scenario 1) are processed similarly to multicast packets received from inside the NGE domain (scenarios 2a and 2b).
The processing rule is that multicast packets are always forwarded as clear text over the fabric. This means that for scenario 2b, when a multicast packet is received on an encryption-capable interface and is NGE-encrypted, the packet is always decrypted first so that it can be processed in the same way as packets in scenarios 1 and 2a.
On egress, the following scenarios apply:
egressing an interface outside the NGE domain – packets are processed in the same way as any multicast packets forwarded out a non-NGE interface
egressing an NGE router interface and no inbound or outbound key group is configured – the router forwards these packets out from the egress interface without encrypting them, because there is no outbound key group configured. This behavior also applies to unicast packets in the same scenario.
egressing an NGE router interface with the outbound key group configured – the router encrypts the multicast packet using the SPI keys of the outgoing SA configured in the key group. This behavior also applies to unicast packets in the same scenario.
Assigning key groups to router interfaces
Assigning key groups to router interfaces involves the following three steps:
Enable NGE with the group-encryption command.
Configure the outbound key group.
Configure the inbound key group.
Step 1 is required so that the router can initialize and differentiate the interface for NGE traffic before accepting or sending NGE packets. This assigns the interface to an NGE domain, and IPSec packets will no longer be accepted on the interface.
Assigning key groups to a router interface in steps 2 and 3 is similar to assigning key groups to SDPs or VPRN-based services. An outbound key group cannot be configured for a router interface without first enabling group-encryption.
When group-encryption is enabled and no inbound key group is configured, the router accepts NGE Layer 3 packets that were encrypted using keys from any security association configured in any key group on the system. If the packet specifies a security association that is not configured in any key group on the node, the packet is dropped.
The outbound key group references the key group to use when traffic egresses the router on the router interface. The inbound key group is used to make sure ingress traffic is using the correct key group on the router interface. If ingress traffic is not using the correct key group, the router counts these packets as errors.
Router interface NGE firewall considerations
An interface that has been configured to exist inside the NGE domain cannot be added to a security zone; firewalls are not supported on NGE router interfaces, as shown in the following figure.
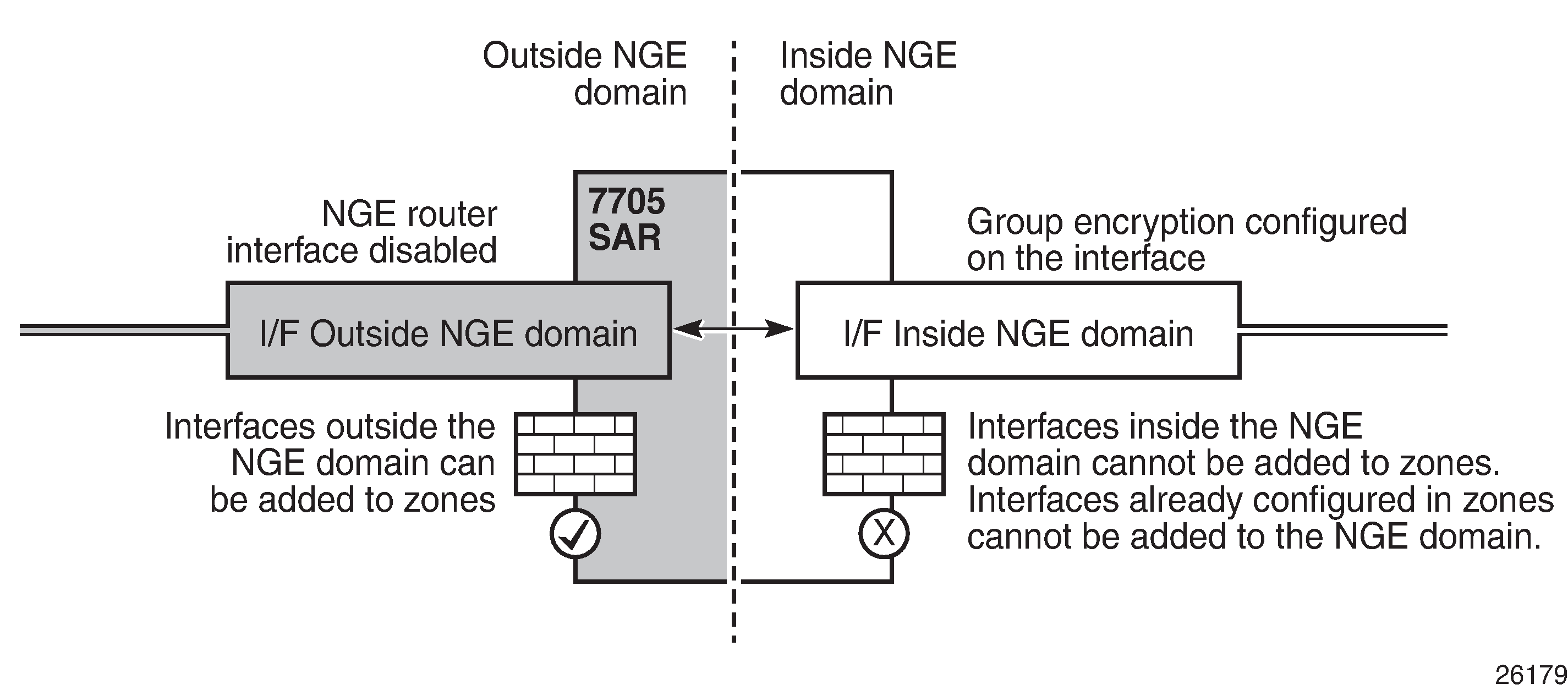
It is recommended that firewall security policies be enabled on interfaces outside the NGE domain before traffic is allowed to enter the NGE domain.
NGE and BFD support
When NGE is enabled on a router interface, BFD packets that originate from the network processor on the adapter card or from the system are encrypted in the same way as BFD packets that are generated by the CSM.
NGE and ACL interactions
When NGE is enabled on a router interface, the ACL function is applied as follows:
on ingress – normal ACLs are applied to traffic received on the interface that can be either NGE-encrypted or clear text. For NGE-encrypted packets, this implies that only the source, destination, and IP options are available to filter on ingress because the protocol is ESP and the packet is encrypted. If an IP exception ACL is also configured on the interface, the IP exception ACL is applied first to allow any clear text packets to ingress as needed. After the IP exception ACL is applied and if another filter or ACL is configured on the interface, the other filter processes the remaining packet stream (NGE-encrypted and IP exception ACL packets), and other ACL functions such as PBR or Layer 4 information filtering could be applied to any clear text packets that passed the exception ACL.
on egress – ACLs are applied to packets before they are NGE-encrypted as per normal operation without NGE enabled
Router interface NGE and ICMP interactions over the NGE domain
Typically, ICMP works as expected over an NGE domain when all routers participating in the NGE domain are NGE-capable; this includes running an NGE domain over a private IP/MPLS network and over a Layer 2 service provider where dedicated point-to-point circuits are used to create single-hop links between NGE nodes. When an ICMP message is required, the NGE packet is decrypted first and the original packet is restored to create a detailed ICMP message using the original packet’s header information.
When the NGE domain crosses a Layer 3 service provider or crosses over routers that are not NGE-aware, it is not possible to create a detailed ICMP message using the original packet’s information because the NGE packet protocol is always set to ESP. Furthermore, the NGE router that receives these ICMP messages will drop them because the messages are not NGE-encrypted.
The combination of dropping ICMP messages at the NGE border node and the missing unencrypted packet details in the ICMP information can cause problems with diagnosing network issues.
To help with diagnosing network issues, additional statistics are available on the interface to show whether ICMP messages are being returned from a foreign node. The following statistics are included in the group encryption NGE statistics for an interface:
Group Enc Rx ICMP DestUnRch Pkts
Group Enc Rx ICMP TimeExc Pkts
Group Enc Rx ICMP Other Pkts
These statistics are used when clear text ICMP messages are received on an NGE router interface. The Invalid ESP statistics are not used in this situation even though the packet does not have a correct NGE ESP header. If there is no ingress exception ACL configured on the interface to allow the ICMP messages to be forwarded, the messages are counted and dropped.
If more information is required for these ICMP messages, such as source or destination address information, a second ICMP filter can be configured on the interface to allow logging of the ICMP messages. If the original packet information is also required, an egress exception ACL can be configured with the respective source or destination address information, or other criteria, to allow the original packet to enter the NGE domain in clear text and determine which flows are causing the ICMP failures.
OAM considerations for router interface encryption
CSM timestamping is supported when NGE router interface encryption is enabled.
Layer 2 encryption
Layer 2 encryption allows IS-IS and LLDP Layer 2 protocols to be encrypted using NGE key groups. The following figure shows the packet format for Layer 2 encryption.
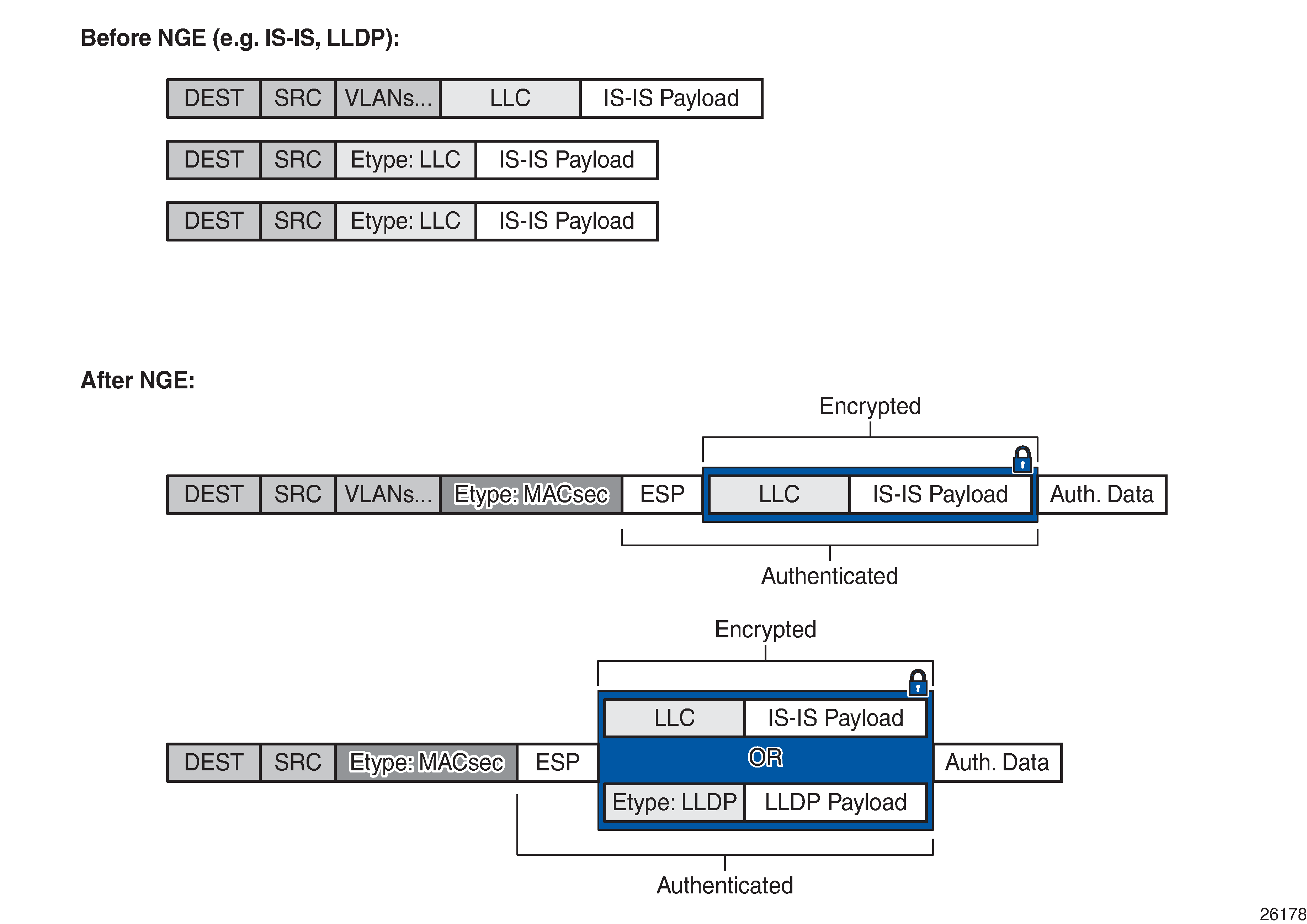
Similar to router interface encryption, which reuses IPSec transport mode formatted packets, Layer 2 NGE encryption reuses the MACsec Ethertype and the ESP protocol, as defined in RFC 4303, to encrypt the payload of a Layer 2 packet.
Layer 2 NGE is configured on network Ethernet ports; access ports and hybrid ports do not support Layer 2 encryption. When Layer 2 encryption is configured, all IS-IS and LLDP packets are encrypted using NGE. Layer 2 encryption does not encrypt any Layer 3 packets using NGE router interface encryption or MPLS packets using MPLS service encryption.
Layer 2 NGE encryption is enabled by configuring an outbound key group and an inbound key group on the Ethernet port and is similar to assigning key groups for router interface encryption as described in Assigning key groups to router interfaces. For example, to configure Layer 2 encryption on port 1/1/1:
config port 1/1/1 ethernet group-encryption encryption-keygroup 1 direction outbound
config port 1/1/1 ethernet group-encryption encryption-keygroup 1 direction inbound
The group-encryption command initializes the port for NGE Layer 2 encryption where both encrypted NGE Layer 2 packets and clear text packets can be received. The group-encryption command is used to add the port to an NGE domain and ensures that any received packets with the MACsec Ethertype are decrypted using NGE Layer 2 encryption.
The outbound key group references the key group to use for encrypting the supported Layer 2 packets egressing the router on the Ethernet port. The inbound key group is used to ensure that ingress traffic is using the correct key group. If ingress traffic that is not using the correct key group is detected, the packets are counted as errors.
If Layer 2 NGE is used for a LAG, each Ethernet port member of the LAG group must be configured with NGE. There is no NGE configuration inheritance from the primary port of a LAG group to its member ports. Each port operates based on its own NGE configuration.
For configuration guidelines for inbound and outbound key groups, see Configuration notes.
NGE packet overhead and MTU considerations
NGE adds overhead packets to services. The following tables show the additional overhead for the worst-case scenario of MPLS services encryption and worst-case scenario of router interface and Layer 2 encryption. Additional overhead depends on which encryption and authentication algorithms are chosen.
Item |
Number of bytes |
|---|---|
Encryption label |
4 |
ESP |
24 |
ICV |
32 |
Padding |
17 |
Control word copy |
4 |
Total |
81 |
For MP-BGP-based VPRNs, the total is 77 bytes because the control word copy is not required.
Item |
Number of bytes |
|---|---|
ESP |
24 |
ICV |
32 |
Padding |
17 |
Total |
73 |
For Layer 3 packets for router interface encryption, and Layer 2 packets for Layer 2 encryption, the total is 73 bytes because the encryption label and control word copy are not required.
The overhead values in NGE overhead for MPLS must be considered for services that are supported by NGE.
The calculations in the table show how NGE overhead affects SDP MTU and service MTU values for MPLS-based, GRE-based, and VPRN-based services. The calculations are with and without NGE enabled.
Service type |
MTU values with and without NGE enabled |
|
|---|---|---|
MPLS-based services |
SDP MTU (MPLS) = 1572 (network port MTU) – 14 (Ethernet header) – 4 (outer label) – 4 (inner label) = 1550 bytes (without NGE enabled) => 1469 bytes (with NGE enabled) |
|
Service MTU (MPLS) considerations with NGE enabled
|
||
GRE-based services |
SDP MTU (GRE) = 1572 (network port MTU) – 14 (Ethernet header) – 20 (IP header) – 4 (GRE header) – 4 (inner label) = 1530 bytes (without NGE enabled) => 1449 bytes (with NGE enabled) |
|
Service MTU (GRE) considerations with NGE enabled
|
||
VPRN-based services |
Each interface inherits its MTU from the SAP or spoke SDP to which it is bound and the MTU value can be manually changed using the ip-mtu command. |
|
MP-BGP-based VPRN services The MTU of the egress IP interface is used. When NGE is enabled on a VPRN service, customers must account for the additional 77 bytes of overhead needed by NGE for any egress IP interface used by the VPRN service. |
||
When an unencrypted Layer 3 packet ingresses the node and routing determines that the egress interface is a router interface NGE-enabled interface, the node calculates whether the packet size will be greater than the MTU of the egress interface after the router interface NGE overhead is added. If the packet cannot be forwarded out from the network interface, an ICMP message is sent back to the sender and the packet is dropped. Users must configure new MTU values to adjust for the overhead associated with NGE.
If an IP exception ACL that matches the ingressing packet exists on the egress interface, the MTU check applied to the ingress packet includes the router interface NGE overhead. This is because the ingress interface cannot determine which IP exceptions are configured on the egress interface, and therefore the worst-case MTU check that includes the router interface NGE overhead is performed.
GRE fragmentation for NGE packets
GRE fragmentation is supported on NGE-encrypted GRE SDP packets on the Ethernet interfaces of the adapter cards and platforms listed in NGE overview.
To determine if an encrypted packet needs to be fragmented, the system compares the total packet size after NGE encryption to the network port MTU. If the encrypted packet size is larger than the MTU, the packet is fragmented. NGE decryption is performed after the packet is fully reassembled.
See GRE fragmentation for more information.
1588v2 encryption with NGE
If a router interface is enabled for encryption and Layer 3 1588v2 packets are sent, they are encrypted using NGE. This means that if port timestamping is enabled on a router interface with NGE, the port timestamp is applied to the Layer 3 1588v2 packet via software-based timestamping instead of hardware-based timestamping, and consequently timing accuracy may degrade. The exact level of timing or synchronization degradation is dependent on many factors, and testing is recommended to measure any impact.
If there is a need to support Layer 3 1588v2 with better accuracy for frequency or better time using port timestamping, an NGE exception ACL is required to keep the Layer 3 1588v2 packets in clear text. The exception ACL must enable UDP packets with destination port 319 to be sent in clear text.
Layer 2 1588v2 packets are always sent and received in clear text. When NGE is enabled on a Layer 2 port, encryption is not applied and existing Layer 2 1588v2 functions are not impacted.
QoS for NGE traffic
The 7705 SAR provides priority and scheduling for traffic into the encryption and decryption engines on nodes that support NGE. This is described for the following traffic directions:
For information about QoS and QoS policies, see the 7705 SAR Quality of Service Guide. Also, because QoS for NGE is similar to QoS for IPSec, see QoS for IPSec for more information.
Network ingress
NGE traffic arriving on network ingress is classified based on the network QoS policy that is assigned to the network router interface. This classification is done using the EXP bits of the outer MPLS tunnel LSP or the DSCP markings on the IP packet of GRE packets.
There are two queues provided for mapping ingress NGE traffic into the decryption engine—an expedited queue and a best-effort queue. The encrypted traffic maps to one of these queues based on the queue-type configuration of the network ingress queue and the FC-to-queue (classification) mapping. Specifically, at network ingress, the following occurs (as shown in the following figure):
the network QoS policy determines the forwarding class (FC) for the packet (item 1)
the ingress network queue QoS policy maps the FC to a queue, where the queue-type has been configured as expedited, best-effort, or auto-expedite (item 2)
the queue-type is used again to map to the appropriate queue into the decryption engine (that is, the expedited and best-effort queue) (item 3)
after decryption, normal QoS processing takes place as if NGE was not enabled for the service (item 4)
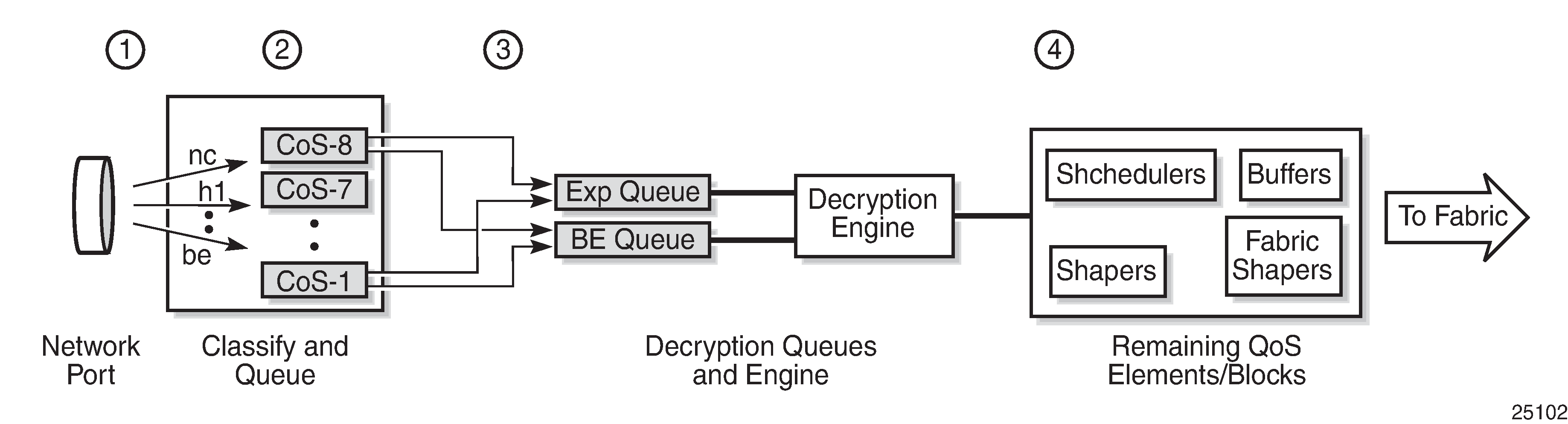
For more information about QoS for network ingress, see the ‟Network ingress” section in the 7705 SAR Quality of Service Guide.
Network egress
Traffic egressing a network interface typically has a known FC based on the traffic management (TM) configuration at SAP ingress.
There are two queues provided for mapping egress NGE traffic into the encryption engine—an expedited queue and a best-effort queue. The traffic maps to one of these queues based on the FC of the packet, as determined at SAP ingress. Specifically, the following occurs:
the SAP ingress QoS policy maps the FC to a queue-type, where the queue-type of the SAP-ingress queue has been configured as expedited, best-effort, or auto-expedite
on the network egress side of the fabric, the ingress queue-type is used to map to the appropriate queue into the encryption engine (that is, the expedited and best-effort queue)
For more information about QoS for network egress, see the ‟Network egress” section in the 7705 SAR Quality of Service Guide.
Statistics
Statistics specific to NGE are counted for the following main areas:
key group
SPI
MDA
service
Remote network monitoring support
Remote network monitoring (RMON) can be used in conjunction with NGE statistics to provide event and alarm reporting. This can be used by customers to detect security breaches of NGE traffic flows and provide real-time reporting of such events.
Threshold crossing alerts and alarms using RMON are supported for SNMP MIB objects, including NGE.
Configuration notes
This section describes NGE configuration guidelines and restrictions. For more information about configuring NGE using the NSP NFM-P, see the NSP NFM-P User Guide.
To enable NGE for an SDP or VPRN service:
Install the outbound direction key group on each node for the service.
Install the inbound direction key group on each node for the service.
To enable NGE for a router interface:
Enable group-encryption on the interface.
Configure the outbound key group.
Configure the inbound key group.
To change NGE from one key group to another key group for an SDP or VPRN service:
Remove the inbound direction key group from each node for the service.
Change the outbound direction key group on each node for the service.
Install the new inbound direction key group on each node for the service.
To change NGE from one key group to another key group for a router interface:
Remove the inbound key group.
Configure the new outbound key group.
Configure the new inbound key group.
To disable NGE for an SDP or VPRN service:
Remove the inbound direction key group from each node providing the service.
Remove the outbound direction key group from each node for the service.
To disable NGE for a router interface:
Remove the inbound key group.
Remove the outbound key group.
Disable group-encryption on the interface.
Restrictions:
The authentication and encapsulation keys must contain the exact number of hexadecimal characters required by the algorithm used. For example, using sha256 requires 64 hexadecimal characters.
The key group bound to an SDP or service must be unbound from that SDP or service before the active outgoing SA for the key group can be removed.
The active outgoing SA must be removed (deconfigured) before the SPI can be deleted from the SA list in the key group.
The encryption or authentication algorithm for a key group cannot be changed if there are any SAs in the key group.
The encryption configured on an SDP used to terminate the Layer 3 spoke SDP of a VPRN (enabled or disabled) always overrides any VPRN-level configuration for encryption. See VPRN Layer 3 spoke-SDP encryption and MP-BGP-based VPRN encryption interaction for more information.
The NSP NFM-P provides configuration parameters that are not configurable using the CLI. See Network Services Platform management for more information.
Configuring NGE with CLI
NGE is fully managed by the NSP NFM-P. The NSP NFM-P ensures correct network synchronization of key groups, services, and NGE domains. Managing NGE without the NSP NFM-P is not recommended. See the NSP NFM-P User Guide for more information.
This section provides information about configuring NGE using the CLI.
Topics in this chapter include:
Basic NGE configuration overview
Perform the following steps to configure NGE for an MPLS service, router interface, or Ethernet port. The steps must be performed in order:
Configure the group encryption label. The label must be unique, and the same label must be used on all nodes in the network group.
Create a key group, duplicating this configuration on all nodes participating in this key group.
Configure the encryption and authentication algorithms for the group.
Configure a security association (SA) that contains the encryption and authentication keys.
Configure the active outbound SA for the group.
Select the SDPs, VPRN services, router interfaces, or Ethernet ports that require encryption.
For each SDP, VPRN service, router interface, or Ethernet port, configure the outbound direction key group.
For each SDP, VPRN service, router interface, or Ethernet port, configure the inbound direction key group.
Configuring NGE components
Use the CLI syntax below to configure the following NGE parameters:
Configuring the global encryption label
The global encryption label is the network-wide, unique MPLS encryption label used for all nodes in the network group. The same encryption label must be configured on each node in the group.
Use the following CLI syntax to configure the global encryption label:
- CLI syntax:
config>group-encryptiongroup-encryption-label encryption-label
The following example displays global encryption label usage:
- Example:
config# group-encryptionconfig>grp-encryp# group-encryption-label 34
The following example displays the global encryption label configuration:
ALU-1>config>grp-encryp# info
-------------------------------------------------------
group-encryption-label 34
-------------------------------------------------------
ALU-1>config>grp-encryp#
Configuring a key group
To configure a key group, set the following parameters:
encryption and authentication algorithms
security association
active outbound SA
The authentication and encapsulation keys must contain the exact number of hexadecimal characters required by the algorithm used. For example, using sha256 requires 64 hexadecimal characters.
Keys are entered in clear text using the security-association command. Once entered, they are never displayed in their original, clear text form. Keys are displayed in a 7705 SAR-encrypted form, which is indicated by the system-appended crypto keyword when an info command is run (see the CLI syntax, Example, and CLI output below). The 7705 SAR also includes the crypto keyword with an admin>save operation so that the 7705 SAR can decrypt the keys when reloading a configuration database. For security reasons, keys encrypted on one node are not usable on other nodes (that is, keys are not exchangeable between nodes).
Use the following CLI syntax to configure key group options:
- CLI syntax:
config# group-encryptionencryption-keygroup keygroup-id [create]description description-stringesp-auth-algorithm {sha256|sha512}esp-encryption-algorithm {aes128|aes256}keygroup-name keygroup-namesecurity-association spi spi authentication-key authentication-key encryption-key encryption-key [crypto]active-outbound-sa spi
The following example displays key group command usage:
- Example:
config>grp-encryp# encryption-keygroup KG1_secureconfig>grp-encryp>encryp-keygrp# description Main_secure_KGconfig>grp-encryp>encryp-keygrp# esp-auth-algorithm sha256config>grp-encryp>encryp-keygrp# esp-encryption-algorithm aes128config>grp-encryp>encryp-keygrp# keygroup-name KG1_secureconfig>grp-encryp>encryp-keygrp# security-association spi 2 authentication-key 0x88433A6DB4FA4F8A490EF661CBE69F010BFAE9C2784BED7059E5ADAAB1A225C6 encryption-key 0x63DCDD501B66F85441E4A55B597DA617config>grp-encryp>encryp-keygrp# security-association spi 6 authentication-key 0x88433A6DB4FA4F8A490EF661CBE69F010BFAE9C2784BED7059E5ADAAB1A225C5 encryption-key 0x63DCDD501B66F85441E4A55B597DA616config>grp-encryp>encryp-keygrp# active-outbound-sa 6 ]
The following example displays the key group configuration:
ALU-1>config>grp-encryp# info detail
----------------------------------------------
group-encryption-label 34
encryption-keygroup 2 create
description "Main_secure_KG"
keygroup-name "KG1_secure"
esp-auth-algorithm sha256
esp-encryption-algorithm aes128
security-association spi 2 authentication-
key 0x78d9e66a6669bd17454fe3184 ee161315b67adb8912949ceda20b6b741eb63604abe17de478e2
4723a7d1d5f7b6ffafc encryption-
key 0x8d51db8f826239f672457442cecc73665f52cbe00aedfb4eda6166001247b4eb crypto
security-association spi 6 authentication-key 0x7fb9fc5553630924ee29973f
7b0a48f801b0ae1cb38b7666045274476a268e8d694ab6aa7ea050b7a43cdf8d80977625 encryption-
key 0x72bd9b87841dbebcb2d114031367ab5d9153a41b7c79c8f889ac56b950d8fffa crypto
active-outbound-sa 6
exit
----------------------------------------------
ALU-1>config>grp-encryp#
Assigning a key group to an SDP or VPRN service
A key group can be assigned to the following entities:
SDPs
VPRN services
NGE supports encryption of the following services when key groups are assigned to an SDP or VPRN service:
VLL services (Epipe and Cpipe)
VPRN services using Layer 3 spoke-SDP termination
IES services using Layer 3 spoke-SDP termination
VPLS services using spoke and mesh SDPs
routed VPLS services into a VPRN or IES
MP-BGP-based VPRNs
NG-MVPN
For services that use SDPs, all tunnels may be either MPLS LSPs (RSVP-TE, LDP, or static LSP) or GRE tunnels. NGE is not supported on IP tunnels.
For VPRNs, the following encryptions are supported:
unicast VPRN – MP-BGP-based VPRN-level encryption using spoke SDPs (spoke-sdp) or autobind SDPs (auto-bind-tunnel) with LDP, GRE, RSVP-TE, or segment routing (SR-ISIS, SR-OSPF, or SR-TE) tunnels
multicast VPRN – NG-MVPN using mLDP with auto-discovery
Use the following CLI syntax to assign a key group to an SDP or a VPRN service:
- CLI syntax:
config>service# sdp sdp-id [create]encryption-keygroup keygroup-id direction {inbound|outbound}
- CLI syntax:
config>service# vprn service-idencryption-keygroup keygroup-id direction {inbound|outbound}
The following examples display a key group assigned to an SDP or a VPRN service:
- Example:
config>service# sdp 61 createconfig>service>sdp# encryption-keygroup 4 direction inboundconfig>service>sdp# encryption-keygroup 4 direction outbound
- Example:
config>service# vprn 22config>service>vprn# encryption-keygroup 2 direction inboundconfig>service>vprn# encryption-keygroup 2 direction outbound
The following example displays key group configuration for an SDP or a VPRN service.
ALU-1:Sar18>config>service# info
----------------------------------------------
...
sdp 61 create
shutdown
far-end 10.10.10.10
exit
encryption-keygroup 4 direction inbound
encryption-keygroup 4 direction outbound
exit
...
vprn 22 customer 1 create
shutdown
encryption-keygroup 2 direction inbound
encryption-keygroup 2 direction outbound
exit
...
----------------------------------------------
Assigning a key group to a router interface
Use the following CLI syntax to assign a key group to a router interface:
- CLI syntax:
config>router# interface ip-int-name [create]group-encryptionencryption-keygroup keygroup-id direction {inbound | outbound}
The following example displays a key group assigned to a router interface:
- Example:
config>router# interface democonfig>router>if# group-encryptionconfig>router>if>group-encryp# encryption-keygroup 6 direction inboundconfig>router>if>group-encryp# encryption-keygroup 6 direction outbound
The following example displays key group configuration for a router interface.
ALU-1:Sar18>config>router# info
----------------------------------------------
...
interface demo
group-encryption
encryption-keygroup 6 direction inbound
encryption-keygroup 6 direction outbound
exit
no shutdown
exit
exit
...
----------------------------------------------
Assigning a key group to an Ethernet port
Use the following CLI syntax to assign a key group to an Ethernet port:
- CLI syntax:
config# port port-idethernetgroup-encryptionencryption-keygroup keygroup-id direction {inbound | outbound}
The following example displays a key group assigned to an Ethernet port:
- Example:
config# port 1/2/2config>port# ethernetconfig>port>ethernet# group-encryptionconfig>port>ethernet>group-encryp# encryption-keygroup 6 direction inboundconfig>port>ethernet>group-encryp# encryption-keygroup 6 direction outbound
The following example displays key group configuration for an Ethernet port.
ALU-1:Sar18>config>port# info
----------------------------------------------
...
ethernet
group-encryption
encryption-keygroup 6 direction inbound
encryption-keygroup 6 direction outbound
exit
no shutdown
exit
exit
...
----------------------------------------------
NGE management tasks
This section discusses the following NGE management tasks:
Modifying a key group
When modifying a key group, observe the following conditions:
The encryption or authentication algorithm for a key group cannot be changed if there are any SAs in the key group.
The active outgoing SA must be removed (deconfigured) before the SPI can be deleted from the SA list in the key group.
Before the outgoing SA can be deconfigured, the key group must be removed from all services on the node that use the key group
In the following example, the active outgoing SA is deconfigured, the SAs are removed, and the encryption algorithm is changed. Then the SAs are reconfigured, followed by reconfiguration of the active outgoing SA. The output display shows the new configuration based on those shown in Configuring a key group.
Use the following CLI syntax to modify a key group. The first syntax deconfigures the key group items and the second syntax reconfigures them.
- CLI syntax:
config# group-encryptionencryption-keygroup keygroup-idno active-outbound-sano security-association spi spiexit
- CLI syntax:
config# group-encryptionencryption-keygroup keygroup-idsecurity-association spi spi authentication-key auth-key encryption-key encrypt-keyesp-encryption-algorithm {aes128|aes256}exit
- Example:
config>grp-encryp# encryption-keygroup KG1_secureconfig>grp-encryp>encryp-keygrp# no active-outbound-saconfig>grp-encryp>encryp-keygrp# no security-association spi 2config>grp-encryp>encryp-keygrp# no security-association spi 6
- Example:
config>grp-encryp# encryption-keygroup KG1_secureconfig>grp-encryp>encryp-keygrp# esp-encryption-algorithm aes256config>grp-encryp>encryp-keygrp# security-association spi 2 authentication-key 0x0123456789012345678901234567890123456789012345678901234567890123 encryption-key 0x0123456789012345678901234567890123456789012345678901234567890123config>grp-encryp>encryp-keygrp# security-association spi 6 authentication-key 0x0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF encryption-key 0x0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF [crypto]config>grp-encryp>encryp-keygrp# active-outbound-sa 2
The following example displays the commands used to modify a key group. The first example deconfigures the key group items and the second example reconfigures them. The encryption algorithm is changed from 128 to 256, the keys are changed, and the active outbound SA is changed to SPI 2.
ALU-1>config>grp-encryp# info detail
----------------------------------------------
group-encryption-label 34
encryption-keygroup 2 create
description "Main_secure_KG"
keygroup-name "KG1_secure"
esp-auth-algorithm sha256
esp-encryption-algorithm aes128
no security-association spi 2
no security-association spi 6
no active-outbound-sa
exit
----------------------------------------------
ALU-1>config>grp-encryp#
ALU-1>config>grp-encryp# info detail
----------------------------------------------
group-encryption-label 34
encryption-keygroup 2 create
description "Main_secure_KG"
keygroup-name "KG1_secure"
esp-auth-algorithm sha256
esp-encryption-algorithm aes256
security-association spi 2 authentication-
key 0x0123456789012345678901234567890123456789012345678901234567890123 encryption-
key 0x0123456789012345678901234567890123456789012345678901234567890123
security-association spi 6 authentication-
key 0x0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF encryption-
key 0x0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF crypto
active-outbound-sa 2
exit
----------------------------------------------
ALU-1>config>grp-encryp#
Removing a key group
Both inbound and outbound direction key groups must be deconfigured before the key group can be removed (unbound). The inbound and outbound key groups must be deconfigured individually. Including keygroup-id is optional.
Removing a key group from an SDP or VPRN service
Use the following CLI syntax to remove a key group from an SDP or a VPRN service:
- CLI syntax:
config>service# sdp sdp-idno encryption-keygroup keygroup-id direction {inbound|outbound}
- CLI syntax:
config>service# vprn service-idno encryption-keygroup keygroup-id direction {inbound|outbound}
The following examples display a key group removed from an SDP or a VPRN service:
- Example:
config>service# sdp 61config>service>sdp# no encryption-keygroup 4 direction inboundconfig>service>sdp# no encryption-keygroup 4 direction outbound
- Example:
config>service# vprn 22config>service>vprn# no encryption-keygroup 2 direction inboundconfig>service>vprn# no encryption-keygroup 2 direction outbound
The following example shows that the key group configuration has been removed from an SDP or a VPRN service.
ALU-1:Sar18>config>service# info
----------------------------------------------
...
sdp 61 create
shutdown
far-end 10.10.10.10
exit
exit
...
...
vprn 22 customer 1 create
shutdown
exit
...
----------------------------------------------
ALU-1:Sar18>config>service# info
Removing a key group from a router interface
Use the following CLI syntax to remove a key group from a router interface:
- CLI syntax:
config>router# interface ip-int-namegroup-encryptionno encryption-keygroup keygroup-id direction {inbound | outbound}
The following example displays a key group removed from a router interface:
- Example:
config>router# interface democonfig>router>if# group-encryptionconfig>router>if>group-encryp# no encryption-keygroup 6 direction inboundconfig>router>if>group-encryp# no encryption-keygroup 6 direction outbound
The following example shows that the key group configuration has been removed from a router interface.
ALU-1:Sar18>config>router# info
----------------------------------------------
...
interface demo
group-encryption
exit
no shutdown
exit
exit
...
----------------------------------------------
Removing a key group from an Ethernet port
Use the following CLI syntax to remove a key group from an Ethernet port:
- CLI syntax:
config# port port-idethernetgroup-encryptionno encryption-keygroup keygroup-id direction {inbound | outbound}
The following example displays a key group removed from an Ethernet port:
- Example:
config# port 1/2/2config>port# ethernetconfig>port>ethernet# group-encryptionconfig>port>ethernet>group-encryp# no encryption-keygroup 6 direction inboundconfig>port>ethernet>group-encryp# no encryption-keygroup 6 direction outbound
The following example shows that the key group configuration has been removed from an Ethernet port.
ALU-1:Sar18>config>port# info
----------------------------------------------
...
ethernet
group-encryption
exit
no shutdown
exit
exit
...
----------------------------------------------
Changing key groups
Use the following sequence of CLI commands to change key groups:
Remove the inbound direction key group.
Change the outbound direction key group.
Install the new inbound direction key group.
Changing the key group for an SDP or VPRN service
Changing key groups for an SDP or VPRN service must be done on all nodes for the service.
The following CLI syntax changes the key group on an SDP. The syntax for a VPRN service is similar. In the example below, the inbound and outbound key groups are changed from key group 4 to key group 6.
- CLI syntax:
config>service# sdp sdp-idno encryption-keygroup keygroup-id direction {inbound|outbound}
- Example:
config>service# sdp 61config>service>sdp# no encryption-keygroup 4 direction inboundconfig>service>sdp# encryption-keygroup 6 direction outboundconfig>service>sdp# encryption-keygroup 6 direction inbound
The following example shows that the key group configuration has been changed for the SDP or the VPRN service.
ALU-1:Sar18>config>service# info
----------------------------------------------
...
sdp 61 create
shutdown
far-end 10.10.10.10
exit
encryption-keygroup 6 direction inbound
encryption-keygroup 6 direction outbound
exit
...
...
vprn 22 customer 1 create
shutdown
encryption-keygroup 2 direction inbound
encryption-keygroup 2 direction outbound
exit
...
----------------------------------------------
ALU-1:Sar18>config>service# info
Changing the key group for a router interface
The following CLI syntax changes the key group on a router interface. In the example below, the inbound and outbound key groups are changed from key group 6 to key group 8.
- CLI syntax:
config>router# interface ip-int-namegroup-encryptionno encryption-keygroup keygroup-id direction {inbound|outbound}
- Example:
config>router# interface democonfig>router>if# group-encryptionconfig>router>if>group-encryp# no encryption-keygroup 6 direction inboundconfig>router>if>group-encryp# encryption-keygroup 8 direction outboundconfig>router>if>group-encryp# encryption-keygroup 8 direction inbound
The following example shows that the key group configuration has been changed for the router interface.
ALU-1:Sar18>config>router# info
----------------------------------------------
...
interface demo
group-encryption
encryption-keygroup 8 direction inbound
encryption-keygroup 8 direction outbound
exit
no shutdown
exit
exit
...
----------------------------------------------
Changing the key group for an Ethernet port
The following CLI syntax changes the key group on an Ethernet port. In the example below, the inbound and outbound key groups are changed from key group 6 to key group 8.
- CLI syntax:
config# port port-idethernetgroup-encryptionno encryption-keygroup keygroup-id direction {inbound|outbound}
- Example:
config# port 1/2/2config>port# ethernetconfig>port>ethernet# group-encryptionconfig>port>ethernet>group-encryp# no encryption-keygroup 6 direction inboundconfig>port>ethernet>group-encryp# encryption-keygroup 8 direction outboundconfig>port>ethernet>group-encryp# encryption-keygroup 8 direction inbound
The following example shows that the key group configuration has been changed for the Ethernet port.
ALU-1:Sar18>config>port# info
----------------------------------------------
...
ethernet
group-encryption
encryption-keygroup 8 direction inbound
encryption-keygroup 8 direction outbound
exit
no shutdown
exit
exit
...
----------------------------------------------
Deleting a key group from a 7705 SAR
To delete a key group from a 7705 SAR, the key group must be removed (unbound) from all SDPs, VPRN services, router interfaces, and Layer 2 NGE-encrypted Ethernet ports that use it.
To locate the key group bindings, use the CLI command show>group-encryption> encryption-keygroup keygroup-id.
Use the following CLI syntax to delete a key group:
- CLI syntax:
-
config# group-encryptionno encryption-keygroup keygroup-id
- Example:
-
config>grp-encryp# no encryption-keygroup 8
NGE command reference
Command hierarchies
Configuration commands
NGE commands
config
- group-encryption
- encryption-keygroup keygroup-id [create]
- no encryption-keygroup keygroup-id
- active-outbound-sa spi
- no active-outbound-sa
- description description-string
- no description
- esp-auth-algorithm {sha256 | sha512}
- no esp-auth-algorithm
- esp-encryption-algorithm {aes128 | aes256}
- no esp-encryption-algorithm
- keygroup-name keygroup-name
- no keygroup-name
- security-association spi spi authentication-key authentication-key encryption-key encryption-key [crypto]
- no security-association spi spi
- group-encryption-label encryption-label
- no group-encryption-label
Services commands
config
- service
- sdp
- encryption-keygroup keygroup-id direction {inbound | outbound}
- no encryption-keygroup direction {inbound | outbound}
- vprn
- encryption-keygroup keygroup-id direction {inbound | outbound}
- no encryption-keygroup direction {inbound | outbound}
See Global service command reference for information about encryption key groups for an SDP and VPRN services command reference for information about encryption key groups for a VPRN service.
Router interface encryption commands
config
- router
- [no] interface ip-int-name
- [no] group-encryption
- encryption-keygroup keygroup-id direction {inbound | outbound}
- no encryption-keygroup direction {inbound | outbound}
- ip-exception filter-id direction {inbound | outbound}
- no ip-exception direction {inbound | outbound}
See the ‟IP router command reference” section in the 7705 SAR Router Configuration Guide for information about router interface encryption commands.
Ethernet port encryption commands
config
- [no] port port-id
- ethernet
- [no] group-encryption
- encryption-keygroup keygroup-id direction {inbound | outbound}
- no encryption-keygroup direction {inbound | outbound}
See the ‟Configuration command reference” section in the 7705 SAR Interface Configuration Guide for information about Ethernet port encryption commands.
Show commands
show
- group-encryption
- encryption-keygroup keygroup-id
- encryption-keygroup keygroup-id spi spi
- summary
Clear commands
clear
- group-encryption
- encryption-keygroup keygroup-id
- encryption-keygroup keygroup-id spi spi
Command descriptions
Configuration commands
Generic commands
description
Syntax
description description-string
no description
Context
config>grp-encryp>encryp-keygrp
Description
This command is used to add a description to the key group being referenced.
The no form of the command reverts to the default value.
Default
n/a
Parameters
- description-string
the description of the key group
Group encryption commands
group-encryption
Syntax
group-encryption
Context
config
Description
This command enables the context to configure group encryption parameters.
encryption-keygroup
Syntax
encryption-keygroup keygroup-id [create]
no encryption-keygroup keygroup-id
Context
config>grp-encryp
Description
This command is used to create a key group. When the key group is created, use the command to enter the key group context or delete a key group.
The no form of the command removes the key group. Before using the no form, the key group association must be deleted from all services that are using this key group.
Default
n/a
Parameters
- keygroup-id
the number or name of the key group being referenced
- create
mandatory keyword when creating a key group
active-outbound-sa
Syntax
active-outbound-sa spi
no active-outbound-sa
Context
config>grp-encryp>encryp-keygrp
Description
This command specifies the security association, referenced by the security parameter index (SPI), to use when performing encryption and authentication on NGE packets egressing the node for all services configured using this key group.
The no form of the command returns the parameter to its default value and is the same as removing this key group from all outbound direction key groups in all services configured with this key group (that is, all packets of services using this key group will egress the node without being encrypted).
Default
n/a
Parameters
- spi
specifies the SPI to use for packets of services using this key group when egressing the node
esp-auth-algorithm
Syntax
esp-auth-algorithm {sha256 | sha512}
no esp-auth-algorithm
Context
config>grp-encryp>encryp-keygrp
Description
This command specifies the hashing algorithm used to perform authentication on the Encapsulating Security Payload (ESP) within NGE packets for services configured using this key group. All SPI entries must be deleted before the no form of the command may be entered or the esp-auth-algorithm value changed from its current value.
The no form of the command reverts to the default value.
Default
sha256
Parameters
- sha256
configures the ESP to use the HMAC-SHA-256 algorithm for authentication
- sha512
configures the ESP to use the HMAC-SHA-512 algorithm for authentication
esp-encryption-algorithm
Syntax
esp-encryption-algorithm {aes128 | aes256}
no esp-encryption-algorithm
Context
config>grp-encryp>encryp-keygrp
Description
This command specifies the encryption algorithm used to perform encryption on the Encapsulating Security Payload (ESP) within NGE packets for services configured using this key group. All SPI entries must be deleted before the no form of the command may be entered or the esp-encryption-algorithm value changed from its current value.
The no form of the command resets the parameter to the default value.
Default
aes128
Parameters
- aes128
configures the AES algorithm with a block size of 128 bits. This is a very strong algorithm choice.
- aes256
configures the AES algorithm with a block size of 256 bits. This is the strongest available version of AES.
keygroup-name
Syntax
keygroup-name keygroup-name
no keygroup-name
Context
config>grp-encryp>encryp-keygrp
Description
This command is used to name the key group. The key group name can be used to reference a key group when configuring services or displaying information.
The no form of the command reverts to the default value.
Default
n/a
Parameters
- keygroup-name
up to 64 characters
security-association
Syntax
security-association spi spi authentication-key authentication-key encryption-key encryption-key [crypto]
no security-association spi spi
Context
config>grp-encryp>encryp-keygrp
Description
This command is used to create a security association for a specific SPI value in a key group. The command is also used to enter the authentication and encryption key values for the security association, or to delete a security association.
The SPI value used for the security association is a node-wide unique value, meaning that no two security associations in any key group on the node may share the same SPI value.
Keys are entered in clear text. When configured, they are never displayed in their original, clear text form. Keys are displayed in a 7705 SAR-encrypted form, which is indicated by the system-appended crypto keyword when an info or an admin>save command is run. For security reasons, keys encrypted on one node are not usable on other nodes (that is, keys are not exchangeable between nodes).
The no form of the command removes the security association and related key values from the list of security associations for the key group. If the no form of the command is attempted using the same SPI value that is configured for active-outbound-sa, then a warning is issued and the command is blocked. If the no form of the command is attempted on the last SPI in the key group and the key group is configured on a service, then the command is blocked.
Default
n/a
Parameters
- spi
specifies the SPI ID of the SPI being referenced for the security association
- authentication-key
specifies the authentication key for the SPI, in hexadecimal format. The number of characters in the hexadecimal string must be 64 or 128, depending on whether the authentication algorithm is set to sha256 or sha512, respectively.
- encryption-key
specifies the encryption key for the SPI, in hexadecimal format. The number of characters in the hexadecimal string must be 32 or 64, depending on whether the encryption algorithm is set to aes128 or aes256, respectively.
- crypto
indicates that the keys showing on the CLI info display are in 7705 SAR-encrypted form
group-encryption-label
Syntax
group-encryption-label encryption-label
no group-encryption-label
Context
config>grp-encryp
Description
This command configures the group encryption label used to identify when an MPLS payload is encrypted. This label must be unique network-wide and must be configured consistently on all nodes participating in a network group encryption domain. The label cannot be changed or deleted when there are any key groups configured on the node.
The no form of the command reverts to the default setting.
Default
n/a
Parameters
- encryption-label
the network-wide, unique reserved MPLS label for group encryption
Show commands
group-encryption
Syntax
group-encryption
Context
show
Description
This command accesses the show>group encryption context.
encryption-keygroup
Syntax
encryption-keygroup keygroup-id
encryption-keygroup keygroup-id spi spi
Context
show>grp-encryp
Description
This command displays NGE information for a key group.
Parameters
- keygroup-id
specifies the key group identifier to use for the output display
- spi
specifies the SPI to use for the output display
Output
The following output is an example of encryption key group information, and Encryption key group field descriptions describes the fields.
Output example*A:7705custDoc:Sar18>show>grp-encryp# encryption-keygroup 2
===============================================================================
Encryption Keygroup Configuration Detail
===============================================================================
Keygroup Id : 2
Keygroup Name : KG1_secure
Description : Most_secure_KG
Authentication Algo: sha256
Encryption Algo : aes128
Active Outbound SA : 6
Activation Time : 04/20/2015 20:07:31
-------------------------------------------------------------------------------
Security Associations
-------------------------------------------------------------------------------
Spi : 2
Install Time : 04/20/2015 20:08:17
Key CRC : 0x806fb970
Spi : 6
Install Time : 04/20/2015 19:43:40
Key CRC : 0xa4f2d262
-------------------------------------------------------------------------------
Encryption Keygroup Forwarded Statistics
-------------------------------------------------------------------------------
Encrypted Pkts : 0 Encrypted Bytes : 0
Decrypted Pkts : 0 Decrypted Bytes : 0
-------------------------------------------------------------------------------
Encryption Keygroup Outbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Unsupported Uplink : 0
Enqueue Error : 0 Other : 0
-------------------------------------------------------------------------------
Encryption Keygroup Inbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Invalid Spi : 0
Authentication Failure *: 0 Control Word Mismatch : 0
Padding Error : 0 Enqueue Error : 0
Other : 0
-------------------------------------------------------------------------------
---------------------------------------------
SDP Keygroup Association Table
---------------------------------------------
SDP ID Direction
---------------------------------------------
61 Inbound Outbound
---------------------------------------------
Inbound Keygroup SDP Association Count: 1
Outbound Keygroup SDP Association Count: 1
---------------------------------------------
VPRN Keygroup Association Table
---------------------------------------------
VPRN SVC ID Direction
---------------------------------------------
12 Inbound Outbound
---------------------------------------------
Inbound Keygroup VPRN Association Count: 1
Outbound Keygroup VPRN Association Count: 1
---------------------------------------------
===============================================================================
* indicates that the corresponding row element may have been truncated.
A:ALU-1:Sar18>show>grp-encryp#
*A:7705:ALU-1# show group-encryption encryption-keygroup 1 spi 1
===============================================================================
Encryption Keygroup Security Association Detail
===============================================================================
Keygroup Id : 1 SPI Id : 1
Install Time : 06/16/2015 11:28:49
Key CRC : 0x36e5af55
-------------------------------------------------------------------------------
Encryption Keygroup Security Association Forwarded Statistics
-------------------------------------------------------------------------------
Encrypted Pkts : 1662534 Encrypted Bytes : 837917136
Decrypted Pkts : 1662333 Decrypted Bytes : 837815832
-------------------------------------------------------------------------------
Encryption Keygroup Security Association Outbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Enqueue Error : 0
Other : 0
-------------------------------------------------------------------------------
Encryption Keygroup Security Association Inbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Authentication Failure : 0
Control Word Mismatch : 0 Padding Error : 0
Enqueue Error : 0 Other : 0
===============================================================================
Label |
Description |
|---|---|
Encryption Keygroup Configuration Detail |
|
Keygroup Id |
The key group identifier |
Keygroup Name |
The key group name |
Description |
The key group description |
Authentication Algo |
The authentication algorithm used for the key group |
Encryption Algo |
The encryption algorithm used for the key group |
Active Outbound SA |
The active outbound SA for the key group |
Activation Time |
The date and time that the key group was activated |
Security Associations |
|
Spi |
The security parameter index for the SA in the key group |
Install Time |
The date and time that the SA was installed in the key group |
Key CRC |
The CRC for the key belonging to the SA |
Encryption Keygroup Forwarded Statistics |
|
Encrypted Pkts |
The number of encrypted packets forwarded by the key group |
Encrypted Bytes |
The number of encrypted bytes forwarded by the key group |
Decrypted Pkts |
The number of decrypted packets forwarded by the key group |
Decrypted Bytes |
The number of decrypted bytes forwarded by the key group |
Encryption Keygroup Outbound Discarded Statistics (Pkts) |
|
Total Discard |
The total number of outbound packets discarded by the key group |
Unsupported Uplink |
The total number of outbound packets discarded by the key group due to an unsupported uplink |
Enqueue Error |
The total number of outbound packets discarded by the key group due to an enqueuing error |
Other |
The total number of outbound packets discarded by the key group due to some other reason, such as an internal configuration error (for example, a key group that points to an SA, but the SA is not valid) |
Encryption Keygroup Inbound Discarded Statistics (Pkts) |
|
Total Discard |
The total number of inbound packets discarded by the key group |
Invalid Spi |
The total number of inbound packets discarded by the key group due to an invalid SPI |
Authentication Failure * |
The total number of inbound packets discarded by the key group due to an authorization failure |
Control Word Mismatch |
The total number of inbound packets discarded by the key group due to a control word (CW) mismatch between the encrypted (protected) CW in the ESP payload and the CW that is not encrypted |
Padding Error |
The total number of inbound packets discarded by the key group due to a padding error |
Enqueue Error |
The total number of inbound packets discarded by the key group due to an enqueuing error |
Other |
The total number of inbound packets discarded by the key group due to some other reason (for example, an incoming packet length is incorrect) |
SDP Keygroup Association Table |
|
SDP ID |
The SDP ID |
Direction |
The direction in which key group authentication and encryption occurs for traffic on the SDP |
Inbound Keygroup SDP Association Count |
The number of SDPs configured to use inbound SA |
Outbound Keygroup SDP Association Count |
The number of SDPs configured to use outbound SA |
VPRN Keygroup Association Table |
|
VPRN SVC ID |
The VPRN service identifier |
Direction |
The direction in which key group authentication and encryption occurs for traffic on the VPRN |
Inbound Keygroup VPRN Association Count |
The number of VPRNs configured to use inbound SA |
Outbound Keygroup VPRN Association Count |
The number of VPRNs configured to use outbound SA |
summary
Syntax
summary
Context
show>grp-encryp
Description
This command shows NGE summary information.
Output
The following output is an example of NGE summary information, and Group encryption summary field descriptions describes the fields.
Output exampleA:ALU-1:Sar18>show>grp-encryp# summary
============================
Group Encryption
============================
Encryption Label : 34
============================
=======================================================
Encryption Keygroup
=======================================================
Id Name Auth Algo Encr Algo Active OutSA
-------------------------------------------------------
2 KG1_secure sha256 aes128 6
4 sha256 aes128 0
-------------------------------------------------------
No. of Encryption Keygroup: 2
=======================================================
A:ALU-1:Sar18>show>grp-encryp#
Label |
Description |
|---|---|
Group Encryption |
|
Encryption Label |
The unique network-wide group encryption label |
Encryption Keygroup |
|
Id |
The key group identifier value |
Name |
The key group name |
Auth Algo |
The authentication algorithm used by the key group |
Encr Algo |
The encryption algorithm used by the key group |
Active OutSA |
The active outbound SA for the key group |
No. of Encryption Keygroup |
The number of encryption key groups currently configured on the node |
Clear commands
group-encryption
Syntax
group-encryption
Context
clear
Description
This command accesses the context to clear group encryption parameters.
encryption-keygroup
Syntax
encryption-keygroup keygroup-id
encryption-keygroup keygroup-id spi spi
Context
clear>grp-encryp
Description
This command clears NGE information for a key group.
Parameters
- keygroup-id
specifies the key group identifier
- spi
specifies the SPI ID