CLI usage
This chapter provides information about using the Command Line Interface (CLI).
Topics in this chapter include:
CLI structure
The 7705 SAR CLI is a command-driven interface accessible through the console, or through Telnet, secure shell (SSH), or SSH file transfer protocol (SFTP). The CLI can be used for configuration and management of 7705 SAR routers.
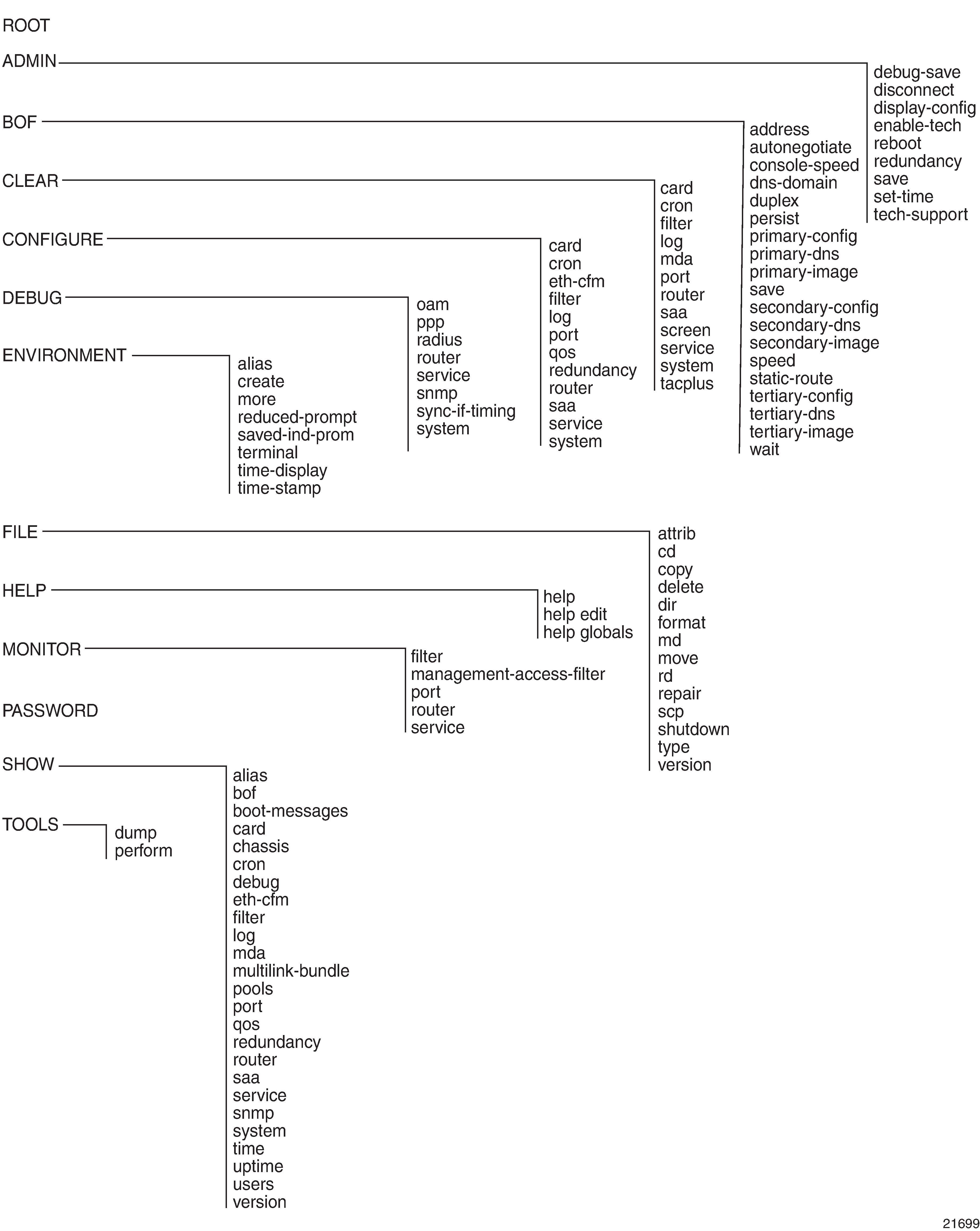
The 7705 SAR CLI command tree is a hierarchical inverted tree. The highest level is the root level. Below this level are other tree levels for the major command groups; for example, configure commands and show commands are below the root level.
The CLI is organized so that related commands with the same scope are at the same level or in the same context. Sublevels or subcontexts have related commands with a more refined scope.
Root-Level Commands displays the major contexts for router configuration. The figure is a sample representation of high-level commands; not all commands are included.
Navigating in the CLI
The following sections describe additional navigational and syntax information:
CLI contexts
The CLI is used to access, configure, and manage 7705 SAR routers. CLI commands are entered at the command line prompt. Access to specific CLI commands is controlled by the permissions set by the system administrator. Entering a CLI command makes navigation possible from one command context (or level) to another. When the user enters a CLI session, they are in the root context. To navigate to other levels, the user enters the name of successively lower contexts. For example, entering the configure or config command at the root level takes the user to the config context. The active CSM slot displays in the command prompt at the beginning of the CLI context as shown below:
A:NOK-12# config
A:NOK-12>config#
In any CLI context, commands can be entered at that context level by entering the text. Pressing <Enter> moves to a lower context. The user can also include commands from lower contexts at one context level as long as the command and parameter syntax is correct.
The following example shows two methods of navigating to a service SDP ingress level:
Method 1: Enter all commands on a single line.
A:NOK-12# configure service cpipe 6 spoke-sdp 2:6 ingress
*A:NOK-12>config>service>cpipe>spoke-sdp>ingress#
Method 2: Enter each command on a separate line.
A:NOK-12>config# service
A:NOK-12>config>service# cpipe 6
*A:NOK-12>config>service>cpipe# spoke-sdp 2:6
*A:NOK-12>config>service>cpipe>spoke-sdp# ingress
*A:NOK-12>config>service>cpipe>spoke-sdp>ingress#
The CLI returns an error message if the syntax is incorrect.
A:NOK-12>config>service# cpipe6
Error: Bad command.
CLI syntax
Command Syntax Symbols lists command syntax symbols. Differences between the syntax used in the CLI and in the Command Reference sections of the 7705 SAR guides is noted in the table.
Symbol |
Description |
Example |
|---|---|---|
| |
A vertical bar represents an OR, indicating that only one of the parameters in the brackets or braces can be selected |
tcp-ack {true | false} |
[ ] |
Brackets indicate optional parameters |
router [router-name] |
< > |
Angle brackets indicate that the user must enter a value for the parameter inside the brackets (Note: angle brackets are not used in the 7705 SAR guides but are used on the CLI; italics are used in these guides to indicate the same rule) |
interface <interface-name> |
{ } |
Braces indicate that one of the parameters must be selected |
default-action {drop | forward} |
[{ }] |
Braces within square brackets indicate that the parameters are optional, but if one is selected, the information in the braces is required; for example, if the user selects the peer parameter, they must enter the keyword peer (ip-address is optional) |
discovery [{peer [ip-address]} | {interface [ip-int-name]}] |
Bold |
In the 7705 SAR guides (not on the CLI), bold indicates commands and keywords that the user must enter exactly as shown |
scope {inclusive | template} |
Italic |
In the 7705 SAR guides (not on the CLI), italics indicate parameters that the user must enter a value for |
dscp dscp-name |
n/a |
In the Command Reference section, n/a in the Default field of a command indicates that a default value is not applicable for the command |
— |
CLI root-level commands
The commands listed in Operational root commands are available at the root level of the CLI hierarchy. For the command descriptions, see the Command Reference sections of the applicable guides.
Command |
Description |
|---|---|
admin |
Enters the administrative context for system operations |
bof |
Enters the context to configure the boot options file |
clear |
Clears statistics or resets the operational state |
configure |
Enters the configuration context |
[no] debug |
Enters the context to enable or disable debugging and specify debug options |
environment |
Enters the environment configuration context |
file |
Enters the context for file system commands |
help |
Displays help in the CLI |
monitor |
Enters the context to monitor statistics |
password |
Enters the context to change the user CLI login password |
show |
Shows operational information |
tools |
Enters the tools context for troubleshooting and debugging |
CLI global commands
The commands listed in CLI global commands are implemented as global commands that can be entered at any level in the CLI hierarchy. The exception is the info command, which can only be entered in a configuration context. To display a list of all system global commands, enter help globals in the CLI.
Command |
Description |
|---|---|
Navigates the user to the parent context |
|
Enters the context to configure candidate parameters |
|
Echoes the text that is typed in; its primary use is to display messages to the screen within an exec file |
|
Enables the user to become a system administrator |
|
Executes the contents of a text file as if they were CLI commands entered at the console |
|
Returns the user to the previous higher context |
|
exit all |
Returns the user to the root context |
Displays help in the CLI |
|
Displays a list of the most recently entered commands |
|
Displays the running configuration for a configuration context; is not supported at the top (config) level |
|
Terminates the CLI session |
|
mrinfo |
Displays multicast information from the target multicast router. See the 7705 SAR OAM and Diagnostics Guide for details. |
mstat |
Traces a multicast path from a source to a receiver and displays multicast packet rate and loss information. See the 7705 SAR OAM and Diagnostics Guide for details. |
mtrace |
Traces a multicast path from a source to a receiver and displays hop-by-hop information. See the 7705 SAR OAM and Diagnostics Guide for details. |
oam |
Provides OAM test suite options. See the 7705 SAR OAM and Diagnostics Guide for details. |
Verifies the reachability of a remote host |
|
Displays the present or previous working context of the CLI session |
|
Causes the console session to pause operation (sleep) for 1 s or for the specified number of seconds; its primary use is to introduce a pause within the execution of an exec file |
|
Opens a secure shell connection to a host |
|
Telnets to a host |
|
Determines the route to a destination address |
|
Displays a list of all commands at the current level and all sublevels |
|
Sends a console message to a specific user or to all users with active console sessions |
CLI environment commands
The CLI environment commands listed in CLI environment commands are found in the root>environment context of the CLI tree. These commands control session preferences for a single CLI session.
Command |
Description |
|---|---|
Enables the substitution of a command line by an alias |
|
Enables or disables the use of a create parameter check |
|
Enables or disables the kernel; the command is enabled with the enable-tech command |
|
Enables the CLI output to be displayed one screen at a time, awaiting user input to continue |
|
Configures the maximum number of higher-level CLI context nodes to display by name in the CLI prompt for the current CLI session |
|
Saves the indicator in the prompt |
|
Enables or disables the shell; the command is enabled with the enable-tech command |
|
Enables the suggestion of internally created objects while auto-completing |
|
Configures the terminal screen length for the current CLI session |
|
Specifies whether time should be displayed in local time or UTC |
|
Specifies whether a timestamp should be displayed before the prompt |
CLI monitor commands
The CLI monitor commands are found in the root>monitor context of the CLI tree. Monitor commands display specified statistical information related to the monitor subject (such as filter, port, router, and service) at a configurable interval until a count is reached.
The monitor command output displays a snapshot of the current statistics. The output refreshes with subsequent statistical information at each configured interval and is displayed as a delta to the previous output.
The <Ctrl-c> keystroke interrupts a monitoring process. Monitor command configurations cannot be saved. The commands must be entered for each monitoring session. If the maximum limits are configured, the statistical information can be monitored for a maximum of 60 ✕ 999 s (approximately 1000 minutes, or 16.6 hours).
The CLI monitor commands are listed in CLI monitor commands . For the command descriptions, see the Command Reference sections of the applicable guides.
Command |
Description |
|---|---|
cpm-filter |
Monitors commands for CPM filters |
fabric-profile |
Monitors fabric traffic statistics |
filter |
Enables IP and MAC filter monitoring at a configurable interval until that count is reached |
lag |
Monitors traffic statistics for LAG ports |
management-access-filter |
Monitors commands for management access filters |
port |
Enables port traffic monitoring. The statistical information for the specified ports displays at the configured interval until the configured count is reached. |
router |
Enables virtual router instance monitoring at a configurable interval until that count is reached |
scada |
Monitors SCADA traffic statistics |
service |
Monitors commands for a particular service |
Getting help in the CLI
The help system commands and the ? key display different types of help in the CLI. Online help commands lists the help commands.
Command |
Description |
|---|---|
help |
Displays instructions for getting CLI help |
? |
Lists all commands in the current context |
command ? |
Displays the command’s syntax and associated keywords |
command keyword ? |
Lists the associated arguments for keyword in command |
string<Tab> string<space> |
Completes a partial command name (auto-completion) or lists available commands that match string |
The tree and tree detail system commands are help commands that are useful when searching for a command in a lower-level context.
The tree flat command displays the command hierarchy on single lines; for example:
card
card card-type
card mda
card mda access
card mda access ingress
card mda access ingress fabric-policy
card mda access ingress security-queue-policy
card mda ais-propagation
card mda clock-mode
CLI Display for CLI Tree Help shows a partial list of the outputs of the tree and tree detail commands entered at the config level.

The CLI command prompt
By default, the CLI command prompt indicates the device being accessed, the active CSM, and the current CLI context. For example, the prompt A:NOK-1>config> router# indicates that the active CSM is CSM A, the user is on the device with hostname NOK-1, and the current context is configure router. In the prompt, the separator used between contexts is the ‟>” symbol.
At the end of the prompt, there is either a pound sign (#) or a dollar sign ($). A ‟#” at the end of the prompt indicates that the context is an existing context. A ‟$” at the end of the prompt indicates that the context has been newly created. Contexts are newly created for logical entities when the user first navigates into the context.
Because there can be a large number of sublevels in the CLI, the system command reduced-prompt no of nodes in prompt allows the user to control the number of levels displayed in the prompt.
All special characters (#, $, and so on) must be enclosed within double quotes; otherwise, the character is seen as a comment character and all characters on the command line following the ‟#” are ignored. For example:
*A:NOK-1>config>router>mpls# authentication-key "router#1"
This example shows a security configuration over a network link. Because the string ‟router#1” is enclosed within double quotes, it is recognized as a password for the link.
When changes are made to the configuration file, a ‟*” appears in the prompt string (*A:NOK-1), indicating that the changes have not been saved. When an admin save command is executed, the ‟*” disappears. This behavior is controlled by the saved-ind-prompt command in the environment context.
Displaying configuration contexts
The info, info detail, and info operational commands display the configuration for the current level. The info command displays non-default configurations. The info detail command displays the entire configuration for the current level, including defaults. The info operational command is used to display the operational configuration of the current configuration context when the user is in candidate edit mode.
The following example shows the output that displays using the info command and the output that displays using the info detail command.
*A:NOK-1>config>router# interface system
*A:NOK-1>config>router>if# info
----------------------------------------------
address 10.221.221.72/8
----------------------------------------------
*A:NOK-1>config>router>if#
*A:NOK-1>config>router>if# info detail
----------------------------------------------
address 10.221.221.72/8
no description
no arp-timeout
icmp
mask-reply
unreachables 100 10
ttl-expired 100 10
exit
no ntp-broadcast
no shutdown
no bfd
----------------------------------------------
*A:NOK-1>config>router>if#
The info commands can be used in every configuration context except for the top (config) level.
EXEC files
The exec command allows the user to execute a text file of CLI commands as if it were typed at a console device.
The exec command and the associated exec files can be used to conveniently execute a number of commands that are always executed together in the same order. For example, an exec command can be used to define a set of commonly used standard command aliases.
The echo command can be used within an exec command file to display messages on screen while the file executes.
CLI script control
The 7705 SAR provides centralized script management for CLI scripts that are used by CRON and the event handling system (EHS). Scripts contain a set of CLI commands that are executed at a scheduled time or when an event is triggered. A set of script policies and script objects can be configured to control such things as:
where scripts are located (local compact flash or remote FTP server)
where the output of the results is stored
how long historical script result records are kept
how long a script may run
Script parameters are configured under the config>system>script-control context.
A script is assigned a script name and optional owner. The owner is an arbitrary string; it is not associated with an actual CLI user. Multiple owners can be associated with a script name, and each script name/owner combination is unique.
A script is also associated with a script text filename and its location. The text file contains the CLI commands to be executed.
When a script has been defined, a script policy is configured under the config>system>script-control context and associated with the script. A script policy is assigned a policy name and optional owner. The owner is an arbitrary string; it is not associated with an actual CLI user. Multiple owners can be associated with a script policy name, and each script policy name/owner combination is unique.
The script policies are referenced by the CRON scheduler and the EHS event handler. All configured script policies can be used by both CRON and EHS.
The script text files can be stored on the local compact flash or on a remote FTP/TFTP server. In CSM-redundant 7705 SAR-8 Shelf V2 or 7705 SAR-18 systems, the script text files must be saved in the compact flash of both CSMs so that CRON or EHS configurations are not lost if a CSM switchover occurs. However, a CSM switchover does cause all queued scripts to be dropped. For remote servers, communication must be reliable; otherwise, there may be undesired pauses during script execution.
Only one script can execute at a time. An SNMP table (smRunTable in the DISMAN-SCRIPT-MIB) is used as both an input queue of scripts waiting to be executed and for storage of records for completed scripts. If the input queue is full, the script request is discarded.
For information about CRON, see CRON in this guide. For information about the EHS, see the 7705 SAR System Management Guide, ‟Event handling system”.
Entering CLI commands
The following sections describe more information about entering CLI commands:
Command completion
The CLI supports both command abbreviation and command completion. If the keystrokes entered are enough to match a valid command, the CLI displays the remainder of the command syntax when Tab or the spacebar is pressed. When typing a command, Tab or the spacebar invokes auto-completion. If the keystrokes entered are sufficient to identify a specific command, auto-completion completes the command. If the letters are not sufficient to identify a specific command, pressing Tab or the spacebar displays commands matching the letters entered.
The command completion functionality works for both keywords and for optional parameters that have already been configured. When using command completion for optional parameters, Tab must be used.
For example, entering ‟i <Tab> returns the following user-configured interface names:
*A:NOK-12>config>router# interface "i
"igmp_interface" "igmp_interface2" "isis_interface"
System commands are available at all CLI context levels.
Unordered parameters
In a command context, the CLI accepts command parameters in any order as long as the command keyword and parameter syntax is correct. Command completion works as long as enough recognizable characters of the command are entered.
Editing keystrokes
When entering a command, special keystrokes allow for editing of the command. Command editing keystrokes lists the command editing keystrokes.
Editing action |
Keystrokes |
|---|---|
Stop current command |
Ctrl-c |
Delete current character |
Ctrl-d |
Delete text up to cursor |
Ctrl-u |
Delete text after cursor |
Ctrl-k |
Move to beginning of line |
Ctrl-a |
Move to end of line |
Ctrl-e |
Get prior command from history |
Ctrl-p |
Get next command from history |
Ctrl-n |
Move cursor left |
Ctrl-b |
Move cursor right |
Ctrl-f |
Move back one word |
Esc-b |
Move forward one word |
Esc-f |
Convert rest of word to uppercase |
Esc-c |
Convert rest of word to lowercase |
Esc-l |
Delete remainder of word |
Esc-d |
Delete word up to cursor |
Ctrl-w |
Transpose current and previous character |
Ctrl-t |
Enter command and return to root prompt |
Ctrl-z |
Refresh input line |
Ctrl-l |
Absolute paths
CLI commands can be executed in any context by specifying the full path from the CLI root. To execute an out-of-context command, enter a forward slash (/) or backward slash (\) at the beginning of the command line. The commands are interpreted as absolute paths. Spaces between the slash and the first command will return an error.
*A:NOK-12# configure router
*A:NOK-12>config>router# interface system address 192.0.2.0
*A:NOK-12>config>router# /admin save
A:NOK-12>config>router# \clear router bfd session all
A:NOK-12>config>router#
The command may or may not change the current context depending on whether it is a leaf command. This is the same behavior the CLI performs when CLI commands are entered individually; for example:
*A:NOK-12# admin
*A:NOK-12>admin# save
or
*A:NOK-12# admin save
*A:NOK-12#
History
The CLI maintains a history of the most recently entered commands. The history command displays the most recently entered CLI commands.
*A:NOK-1# history
1 environment terminal length 48
2 show version
3 configure port 1/1/1
4 info
5 show port 1/1/1
6 \con port 1/1/1
7 \configure router mpls
8 info
9 \configure system login-control
10 info
11 history
*A:NOK-1# !2
*A:NOK-1# show version
TiMOS-B-0.0.I322 both/hops NOKIA SAR 7705
Copyright (c) 2018 Nokia.All rights reserved.
All use subject to applicable license agreements.
Built on Wed Jan 17 01:05:13 EST 2018 by csabuild in /re8.0/I322/panos/main
*A:NOK-1#
Entering numerical ranges or lists
The 7705 SAR CLI allows the use of a single numerical range, a list of values (elements), or a combination of both as an argument in the command line.
A range in a CLI command is limited to positive integers and is denoted with two numbers enclosed in square brackets with two periods (‟..”) between the numbers [x.. y], where x and y are positive integers and y-x is less than 1000. For example, to configure a range of VPLS service IDs from 20 to 30 for a customer, enter:
config service vpls [20..30] customer 1 create no shutdown
A list of values contains discrete integer elements, in any order. For example, to configure a list of VPLS service IDs that are not sequential, enter:
config service vpls [3,5,7] customer 1 create no shutdown
To configure a list of interface names (interface names must begin with a letter), put the alphabetic part of the name outside of the brackets; for example:
config router interface intf[1,4,6] no shutdown
This command creates interfaces with names intf1, intf4, and intf6.
Lists can contain ranges as elements, as well as values. For example, to configure multiple ports on MDA 1, enter:
config port 1/1[1..6,8,10, 21..32] no shutdown
CLI commands can also contain ranges or lists of hexadecimal values; for example, [0x0f..0x13], [0x4,0x8,0xc]. This allows ranges to be used when working with data that is normally expressed in hexadecimal, such as IPv6 addresses or MAC addresses.
A range can also be a reference to a previous range in the same command. This reference takes the form [$x], where x is an integer between 0 and 5, with 0 referring to the first range in the command, 1 to the second, and so on up to the maximum of six ranges. For example:
config service vprn [11..20] router-id 10.20.[$0].1
gives vprn 11 the router ID 10.20.11.1, vprn 12 the router ID 10.20.12.1, and so on.
<Ctrl-c> can be used to abort the execution of a range command.
Specifying a range in the CLI does have limitations. These limitations are summarized in CLI range use limitations .
Limitation |
Description/example |
|---|---|
Up to six ranges (including references) can be specified in a single command but must not combine to more than 1000 iterations of the command |
For example, ports on two adapter cards can be shut down in one command by using two ranges: config port 1/[1..2]/[1..10] shutdown This command shuts down ports 1 to 10 on MDA 1 and MDA 2. |
Ranges within quotation marks are interpreted literally |
Enclosing a string in quotation marks (‟string”) causes the string to be treated literally and as a single parameter. For example, several commands in the 7705 SAR CLI allow the configuration of a descriptive string. If the string is more than one word and includes spaces, it must be enclosed in quotation marks. A range that is enclosed in quotes is also treated literally. For example, config router interface "A[1..10]" no shutdown creates a single router interface with the name ‟A[1..10]”. However, a command such as: config router interface A[1..10] no shutdown creates 10 interfaces with names A1, A2, to A10. |
The range cannot cause a change in contexts |
Commands should be formed in such a way that there is no context change upon command completion. For example, config port 1/1/[1..10] attempts to change 10 different contexts. When a range is specified in the CLI, the commands are executed in a loop. On the first loop execution, the command changes contexts, but the new context is no longer valid for the second iteration of the range loop. A ‟Bad Command” error is reported and the command aborts. Adding shutdown or no shutdown to the command keeps the same context. |
Command completion may not work when entering a range |
After entering a range in a CLI command, command and key completion, which normally occurs by pressing the <Tab> key or spacebar, may not work. If the command line entered is correct and unambiguous, the command works properly; otherwise, an error is returned. |
Pipe/match
The 7705 SAR supports the pipe/match (...| match) feature to search one or more files for a specified character string or pattern.
Match syntax:
match pattern context {parents | children | all} [ignore-case] [max-count lines-count] [expression]
match pattern [ignore-case] [invert-match] [pre-lines pre-lines] [post-lines lines-count] [max-count lines-count] [expression]
where:
pattern: a string or regular expression (maximum 200 characters)
context: displays the context associated with the matching line
parents: displays the parent context information
children: displays the child context information
all: displays both parent and child context information
ignore-case: ignores the case in the string (uppercase or lowercase)
max-count lines-count: displays the matching lines, up to the specified number (1 to 2147483647)
expression: the pattern is interpreted as a regular expression
invert-match: displays all the lines that do not contain the string specified in pattern
pre-lines pre-lines: displays the lines before the matching line, up to the specified number (0 to 100)
post-lines lines-count: displays the lines after the matching line, up to the specified number (1 to 2147483647)
For example:
*A:NOK-12# show service sap-using | match 1/1 pre-lines 10
===============================================================================
Service Access Points
===============================================================================
PortId SvcId Ing. Ing. Egr. Egr. Adm Opr
QoS Fltr QoS Fltr
-------------------------------------------------------------------------------
1/1/1:333 111 1 none 1 none Up Up
1/1/1:444 111 1 none 1 none Up Up
1/1/9:10 200 1 none 1 none Up Up
1/1/9:11 200 1 none 1 none Up Up
1/1/9:12 200 1 none 1 none Up Up
1/1/9:13 200 1 none 1 none Up Up
1/1/9:14 200 1 none 1 none Up Up
1/1/9:15 200 1 none 1 none Up Up
A:NOK-12# show log log-id 98 | match ignore-case "sdp bind"
"Status of SDP Bind 101:1002 in service 1001 (customer 1)changed to admin=up oper=up
flags="
"Processing of a SDP state change event is finished and status of all affected SDP
Bindings on SDP 101 has been updated."
A:NOK-12# show log log-id 98 | match max-count 1 "service 1001"
"Status of service 1001 (customer 1)changed to administrative state: up, operational
state: up"
*A:NOK-12# admin display-config | match post-lines 5 max-count 2 expression "snmp”
snmp
exit
login-control
idle-timeout disable
pre-login-message "csasim2 - " name
exit
snmp
view "testview" subtree "1"
mask ff
exit
view "testview" subtree "1.3.6.1.2"
mask ff type excluded
*A:NOK-12#
Pipe/match characters describes regular expression symbols and interpretation (similar to what is used for route policy regexp matching).
String |
Description |
|---|---|
. |
Matches any single character |
[ ] |
Matches a single character with what is contained within the brackets [abc] matches ‟a”, ‟b”, or ‟c” [a-z] matches any lowercase letter [A-Z] matches any uppercase letter [0-9] matches any number |
[^ ] |
Matches a single character with what is not contained within the brackets [^abc] matches any character other than ‟a”, ‟b”, or ‟c” [^a-z] matches any single character that is not a lowercase letter |
^ |
Matches the start of the line (or any line, when applied in multiline mode) |
$ |
Matches the end of the line (or any line, when applied in multiline mode) |
() |
Defines a ‟marked subexpression” Every matched instance is available to the next command as a variable |
* |
A single character expression followed by ‟*” matches zero or more copies of the expression |
{m,n} |
Matches at least m and at most n repetitions of the term |
{m} |
Matches exactly m repetitions of the term |
{m,} |
Matches m or more repetitions of the term |
? |
The preceding item is optional and matched at most once |
+ |
The preceding item is matched one or more times |
- |
Used between start and end of a range |
\ |
An escape character to indicate that the following character is a match criterion and not a grouping delimiter |
Special characters identifies the special character options.
Options |
Similar to |
Description |
|---|---|---|
[:upper:] |
[A-Z] |
Uppercase letters |
[:lower:] |
[a-z] |
Lowercase letters |
[:alpha:] |
[A-Za-z] |
Uppercase and lowercase letters |
\w |
[A-Za-z_] |
Word characters |
[:alnum:] |
[A-Za-z0-9] |
Digits, uppercase and lowercase letters |
[:digit:] |
[0-9] |
Digits |
\d |
[0-9] |
Digits |
[:xdigit:] |
[0-9A-Fa-f] |
Hexadecimal digits |
[:punct:] |
[.,!?:...] |
Punctuation |
[:blank:] |
[ \t] |
Space and Tab |
[:space:] |
[ \t\n\r\f\v] |
Blank characters |
\s |
[ \t\n\r\f\v] |
Blank characters |
Pipe/count
The 7705 SAR supports a pipe/count command (...| count) that provides a count of the number of lines that would have otherwise been displayed. The pipe/count command is particularly useful when used in conjunction with the pipe/match command to count the number of output lines that match a specified pattern.
For example:
*A:NOK-12# show service service-using vprn
===============================================================================
Services [vprn]
===============================================================================
ServiceId Type Adm Opr CustomerId Service Name
-------------------------------------------------------------------------------
1 VPRN Down Down 1
44 VPRN Up Up 1
100 VPRN Down Down 1
102 VPRN Up Up 1
235 VPRN Down Down 1
1000 VPRN Down Down 1000
-------------------------------------------------------------------------------
Matching Services : 6
-------------------------------------------------------------------------------
===============================================================================
*A:NOK-12# show service service-using vprn | match Down | count
Count: 4 lines
*A:NOK-12#
Redirection
The 7705 SAR supports redirection (>), which allows the operator to store the output of a CLI command as a local or remote file.
‛ping <customer_ip> > cf3:/ping/result.txt’
‛ping <customer_ip> > ftp://ron@ftp.alcatel.com/ping/result.txt’
In some cases, only part of the output may be applicable. The pipe/match and redirection commands can be combined:
ping 10.0.0.1 | match expression ‟time.\d+” > cf3:/ping/time.txt
This records only the RTT portion (including the word ‟time”).
CLI configuration rollback
The CLI configuration rollback feature allows operators to save rollback checkpoint and rescue files that can be used to quickly return the node configuration to a previous state with minimal impacts to services and without restarting the node.
CLI configuration rollback gives operators better control and visibility over router configurations and reduces operational risk while increasing flexibility and providing powerful recovery options.
The location and generic filename of the rollback checkpoint and rescue files must be configured with the rollback-location and rescue-location commands before a rollback file can be saved. Files can be saved locally on the compact flash or on a remote device. The file URL must contain a path or directory and a generic filename with no extension. File suffixes are automatically appended when the file is saved.
Rollback checkpoint and rescue files
Rollback checkpoint files and rescue files are created with the rollback save command. A rollback checkpoint file can be saved at any time or configured to be automatically saved on a recurring schedule using the 7705 SAR CRON feature. For more information, see CRON.
Rollback checkpoint and rescue files contain all current operationally active configurations, including configuration changes from CLI commands in the config context and SNMP sets. Rollback checkpoint files are intended to be saved whenever there have been a moderate number of changes to the configuration, in order to create a series of intermediate checkpoints that operators can return to. The rollback rescue file is intended to be a permanent stable configuration that can be reverted to if needed.
Rollback checkpoint and rescue files do not contain any BOF configuration information or any configuration or state changes performed under the debug branch of the CLI. Similarly, performing a CLI configuration rollback never impacts the BOF configuration or any command from the debug CLI branch.
When a rollback save command is executed, a rollback checkpoint or rescue file is saved in the configured location. The latest rollback checkpoint file is saved with the suffix *.rb. The suffixes of all previously saved rollback checkpoint files are automatically incremented by one (*.rb becomes *.rb.1, *.rb.1 becomes *.rb.2, and so on). The rescue file is saved with the suffix *.rc.
By default, there can be 10 rollback checkpoint files, the latest with suffix *.rb and nine older files with suffixes *.rb.1 through *.rb.9. If the maximum number of checkpoint files is reached and a new one is saved, the oldest checkpoint file is deleted. The maximum number of rollback checkpoint files that can be saved can be configured with the local-max-checkpoints and remote-max-checkpoints commands.
There can only be one rollback rescue file. When a new rescue file is saved, the existing file is deleted. The rescue file is not impacted by the number of rollback checkpoint files — there will always be one rescue file available.
Operators can view a list of rollback checkpoint or rescue files with the rollback view command. The following information is displayed for the files:
date and time stamps
file index and suffix
the user who created the file
release number
comment string
A rollback compare command is also available that allows operators to compare different checkpoint files to each other or to the current operating configuration. The command output highlights any differences between the configurations.
Rollback checkpoint and rescue files are not editable or interchangeable with configuration files, such as those generated with an admin save command.
Both admin save and rollback save should be performed periodically. The admin save command backs up the complete configuration file to be used during a router reboot and should be performed after any major service changes or hardware and software upgrades. The rollback save command should be performed to create intermediate checkpoints whenever a moderate number of changes have been made to the configuration.
Rollback checkpoint files and rescue files can be deleted with the dedicated admin>rollback>delete command. When a checkpoint file is deleted, the suffix ID numbers of all older files are automatically decremented.
If a rollback checkpoint file is manually deleted, using, for example, the file delete command, the suffix ID numbers of older checkpoint files are not decremented, nor is the backup checkpoint file deleted from the standby CSM. This creates a gap in the checkpoint file list. New rollback checkpoint files can still be created, but the gap is not filled until enough files have been created to roll the gap off the end of the list.
Rollback file backup
The rollback checkpoint files can be backed up from the active CSM to the standby CSM on the 7705 SAR-8 Shelf V2 or 7705 SAR-18 with the rollback-sync command in the admin context. Rollback file backups are not supported on fixed platforms because they do not have redundant CSMs.
The 7705 SAR also supports automatic synchronization with the rollback-sync command in the config context. When automatic rollback synchronization is enabled, a rollback save causes the new checkpoint file to be saved on both the active and standby CSMs if the rollback location is a local location. The suffixes of all older checkpoint files on both active and standby CSMs are incremented by one. Automatic synchronization only causes newly created rollback checkpoint files to be copied to both CSMs. Any rollback checkpoint files that were created before automatic synchronization was enabled are not copied to the standby CSM but can be manually backed up with the rollback-sync command in the admin context.
If the config>rollback-sync command is enabled, deleting a rollback checkpoint file also deletes the backup file and decrements the suffix ID numbers on the standby CSM.
The dedicated rollback-sync commands are the only commands that can be used to back up rollback checkpoint files. Existing redundancy synchronization commands are not compatible with rollback checkpoint files.
Performing a CLI configuration reversion
The rollback revert command is used to return the CLI configuration, including all configuration commands and SNMP sets, to the saved configuration in a rollback checkpoint or rescue file. CLI configuration reversion can be used to quickly correct problems in the configuration during network operation or to aid in experimentation by enabling a return to known settings after trying a new configuration.
The CLI configuration reversion is performed without a reboot and with minimal impact on the services being provided by the 7705 SAR. Configuration parameters that have changed since the checkpoint file was created, or items on which changed configurations have dependencies, are first reset to their default values and then restored to their previous values from the rollback checkpoint file. Performing a configuration reversion can be briefly service-impacting in changed areas. There are no service impacts to configuration areas that did not change since the rollback checkpoint file was created.
If a rollback reversion process includes any commands that will remove, rebuild, or reboot an adapter card or fixed platform, the impacted adapter cards and platforms are listed in a warning and the operator is asked whether to proceed or not with a y/n prompt. There is no prompt if the rollback reversion is initiated via SNMP or if the now keyword is used. The following are examples of adapter card and fixed platform commands that may generate a warning:
config>card>card-type
config>card>mda
config>card>mda>mda-type
While the 7705 SAR is processing a rollback revert command, CLI and SNMP commands from other users are still accepted and applied to the system. The only commands that are blocked during this process are other rollback commands including revert, save, and compare. Only one rollback command can be processed at a time.
Performing a rollback reversion does not have any effect on existing rollback checkpoint and rescue files; files are not renumbered or deleted. For example, if an operator reverts to rollback checkpoint file 3, the file remains as *.rb.3. If the operator then executes a rollback save command, the current configuration is saved as the latest rollback (extension *.rb) and *.rb.3 is incremented to *.rb.4. In this scenario, both the latest rollback checkpoint file and checkpoint file 3 will have the same configuration information.
Currently running or scheduled CRON jobs are handled like all other configurations during a rollback reversion. The CRON configuration will revert to the configuration at the time the checkpoint was created.
The boot-good-exec or boot-bad-exec commands must be manually executed after a rollback reversion; they are not automatically run.
Rollback restrictions
Some hardware or software changes can prevent operators from performing the rollback or can affect the operation of the node following the reversion.
If hardware is removed or changed after a rollback checkpoint file is saved, the node may not function as expected after the system reverts to that configuration. There is no effect if new hardware is added into previously empty slots.
A CLI rollback reversion is not supported if the rollback checkpoint file was saved in a previous major software load or if it was saved in a more recent major or minor software load. For example:
a node running Release 20.4.R1 cannot revert to a checkpoint file saved in Release 9.0.R4
a node running Release 9.0.R4 cannot revert to a checkpoint file saved in Release 20.4.R1
a node running Release 9.0.R4 cannot revert to a checkpoint file saved in Release 9.0.R6
CLI rollback reversion is supported if the checkpoint file was saved in a previous minor software release. For example, a node running Release 9.0.R6 can revert to a checkpoint file saved in Release 9.0.R4. It is also supported after an operator performs an admin reboot or changes the primary configuration and then performs an admin reboot. The reboot does not remove any previously saved rollback files.
If the system runs out of memory during a CLI rollback reversion, the process aborts and the node remains in an indeterminate configuration state. The CLI screen displays a warning message that the CLI reversion failed.
A CLI rollback reversion may also fail in rare cases if the node requires a long time to complete the configuration changes. If the CLI rollback reversion fails during execution, it should be attempted again. The second attempt typically completes the remaining configuration changes.
A high availability CSM switchover during a rollback reversion will cause the rollback process to abort, and the newly active CSM will have an indeterminate configuration. This may not be immediately obvious if the CLI rollback reversion was nearly complete when it was interrupted. To assist operators, a log event is created and the results of the last rollback reversion can be displayed with the show system rollback command. If a high availability switchover occurs during a rollback (or within a few seconds of a rollback completing), the Last Revert Result field will display Interrupted and the operator is advised to repeat the rollback revert operation to the same checkpoint.
Although the use of the <Ctrl-c> key combination is not recommended during a rollback revert, it is supported in the CLI and SNMP. Interrupting a rollback revert command may leave the router in an indeterminate state between the active and saved configuration.
If <Ctrl-c> is used during a CLI rollback reversion, the 7705 SAR displays a warning message to indicate that the operator must examine the configuration and potentially issue another rollback revert command to return to a known, complete configuration.
Transactional configuration
Transactional configuration allows a user to make configuration changes inside a candidate configuration without actually causing changes to the active or operational configuration of the router. When the candidate configuration is complete, the user can explicitly commit the changes and cause the new configuration to become active. Transactional configuration gives the user better control and visibility over their router configurations and reduces operational risk while increasing flexibility.
Transactional configuration and CLI configuration rollback combine to provide the operational model depicted in Router configuration with rollback and transactions.
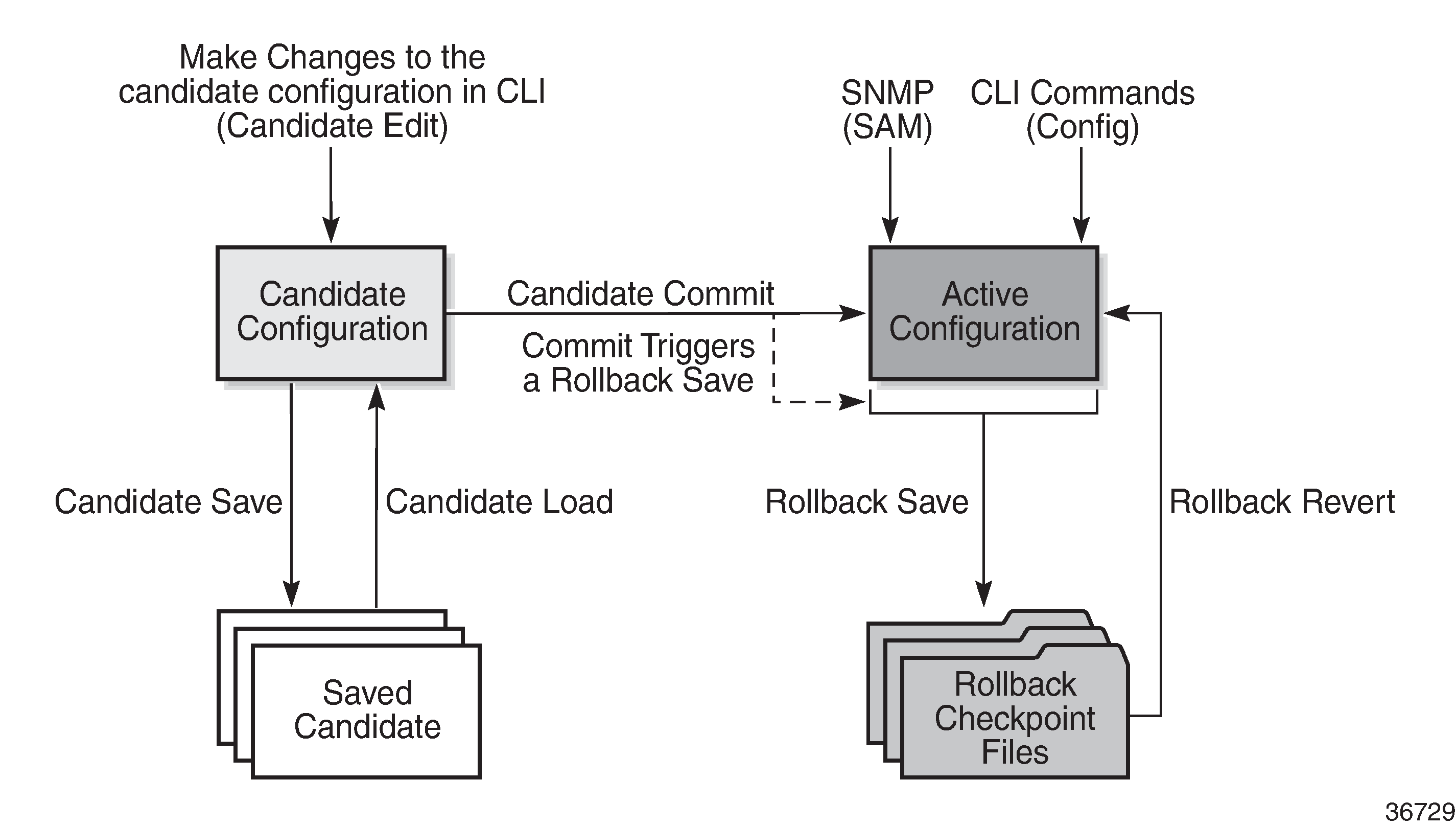
Basic operation
To edit the candidate configuration, the user must first enter candidate edit mode with the candidate>edit command. The user can enter and quit candidate edit mode as many times as they need before committing the candidate configuration.
In candidate edit mode, the user builds a set of candidate configuration changes using the same CLI tree as the standard (line-by-line, non-transactional) configuration. Tab completion and keyword syntax checking is available.
Just as there is a single operational active configuration that can be modified simultaneously by multiple users, there is also a single global candidate configuration instance. All users make changes in the same global candidate configuration and any command that affects the candidate configuration (such as a save or commit) applies to the changes made by all users.
Users can enter an exclusive candidate edit mode by blocking other users, or sessions of the same user, from entering candidate edit mode.
When a candidate configuration is committed, the user can request an additional confirmation of the configuration. If the confirmation is not given with the confirm command within the specified time frame, the router automatically reverts to a configuration state before the candidate configuration changes were applied. If this automatic reversion occurs, the candidate configuration is not cleared and users can continue to edit it and try the commit later.
If the commit operation is successful and the confirm command is issued (if requested during the commit), all the candidate changes take operational effect and the candidate configuration is cleared. If there is an error processing the commit, the router returns to a configuration state before the candidate changes were applied. The candidate configuration is not cleared and users can continue to edit it and try the commit later.
A candidate commit may fail for various reasons, including:
misordering — the candidate configuration has changes that are not in the correct order; for example, an object is referred to before it is actually created
invalid options and combinations — although many syntax errors are eliminated during the candidate editing process, the candidate configuration may contain combinations of configurations and options that are not valid and are rejected when the 7705 SAR attempts to have them take operational effect
resource exhaustion — the application of the candidate configuration may exhaust various system resources, such as queue resources
If a commit fails, the system generates error messages to help the user correct the candidate configuration.
All commands in the candidate configuration must be in the correct order for a commit to be successful. Configuration that depends on other candidate objects must be placed after those objects in the candidate. A set of commands (such as copy, insert, and replace) are available to correct and reorder an existing candidate configuration.
Candidate edit mode is primarily intended for building a candidate configuration using commands from the configure branch of the CLI. Although many CLI commands in other branches are supported, access to some CLI commands and branches are blocked, including:
exec command
enable-admin command
admin branch
bof branch
debug branch
tools branch
The candidate configuration can be saved to a file and loaded into a new candidate configuration later. A saved candidate file is similar to, but not exactly the same as, a 7705 SAR configuration file generated with an admin save command. The saved candidate file cannot be used as a configuration file and may not execute without failures.
There is no SNMP access to the candidate configuration and no SNMP management of candidates. However, when a candidate configuration is committed, any changes to the active or operational configuration are reported via the standard 7705 SAR SNMP change traps. Basic candidate status information is also available via SNMP.
The active or operational configuration can still be modified with standard CLI or SNMP commands that take immediate effect while a candidate configuration is being created or edited or a candidate commit is being processed. While in candidate edit mode, users can view the current state of the operational configuration with the info operational command.
Transactions and rollback
Transactional configuration relies on the rollback mechanism to operate. By default, the 7705 SAR automatically creates a new rollback checkpoint after a successful candidate commit operation. The rollback checkpoint includes the new configuration changes made by the commit. An optional no-checkpoint keyword can be used to prevent the creation of an automatic rollback checkpoint after a successful commit. If the commit fails, no rollback checkpoint is created. If the confirmed option is used during the candidate commit, a rollback checkpoint is created and exists whether or not the confirm command is issued.
Any configurations that are not supported in a rollback revert are also not supported in candidate edit mode. See CLI configuration rollback for more information.
Authorization
Authorization works transparently in candidate edit mode, and no unique or new local profile or TACACS+ permissions rules are required other than allowing access to the candidate branch. For example, if a user has permission to access the configure filter context, they automatically have access to the same context when in candidate edit mode.
The candidate load and save commands load and save only those items that the user is authorized to access.
The candidate view command only displays the items that the user is authorized to access.
The candidate editing commands (such as adding or removing lines) only allow the user to modify items that they are authorized to access.
The candidate commit and discard commands, along with the admin>rollback> revert command, impact all items in the candidate configuration and are not affected by authorization.
Basic command reference
Command hierarchies
CLI root-level and global commands
- back
- clear
- echo [text-to-echo] [extra-text-to-echo] [more-text]
- enable-admin
- exec [-echo] [-syntax] {filename | <<[eof-marker-string]}
- exit [all]
- help
- help edit
- help globals
- help special-characters
- history
- logout
- mrinfo [See the 7705 SAR OAM and Diagnostics Guide for command description]
- mstat [See the 7705 SAR OAM and Diagnostics Guide for command description]
- mtrace [See the 7705 SAR OAM and Diagnostics Guide for command description]
- oam [See the 7705 SAR OAM and Diagnostics Guide for command description]
- password
- ping {ip-address | dns-name} [rapid | detail] [ttl time-to-live] [tos type-of-service] [size bytes] [pattern pattern] [source ip-address] [interval seconds] [{next-hop ip-address} | {interface interface-name} | bypass-routing] [count requests] [do-not-fragment] [router router-instance | service-name service-name] [timeout timeout] [fc fc-name]
- pwc [previous]
- sleep [seconds]
- ssh host [-l username] [router router-instance | service-name service-name] [re-exchange-min minutes] [re-exchange-mbyte megabytes]
- telnet [ip-address | dns-name] [port] [router router-instance]
- telnet [ip-address | dns-name] [port] [service-name service-name]
- traceroute {ip-address | dns-name} [ttl ttl] [wait milliseconds] [no-dns] [source ip-address] [tos type-of-service] [router router-instance | service-name service-name]
- tree [detail] [flat]
- write {user | broadcast} message-string
<root>
- configure
- <level> (any context under configure)
- info [detail] [operational]
Environment commands
<root>
- environment
- alias alias-name alias-command-name
- no alias alias-name
- [no] create
- kernel -password password
- no kernel
- [no] more
- reduced-prompt [no of nodes in prompt]
- no reduced-prompt
- [no] saved-ind-prompt
- shell -password password
- no shell
- [no] suggest-internal-objects
- terminal
- length lines
- width width
- time-display {local | utc}
- [no] time-stamp
Rollback commands
admin
- rollback
- compare [to source2]
- compare source1 to source2
- delete checkpoint-rescue
- revert checkpoint-rescue [now]
- save [comment comment] [rescue]
- view [checkpoint-rescue]
admin
- compare source1 to source2
admin
- redundancy
- rollback-sync
config
- system
- rollback
- local-max-checkpoints number
- no local-max-checkpoints
- remote-max-checkpoints number
- [no] remote-max-checkpoints
- [no] rescue-location file-url | rescue filename
- [no] rollback-location file-url | rollback filename
config
- redundancy
- [no] rollback-sync
Candidate commands
candidate
- edit [exclusive]
- commit [confirmed timeout] [comment comment]
- commit no-checkpoint [confirmed timeout]
- confirm
- copy [line]
- delete [line]
- discard [now]
- goto line
- insert [line]
- load file-url [overwrite | insert | append]
- quit
- redo [count]
- replace [line]
- save file-url
- undo [count]
- view [line]
- config
- system
- management cli
- configuration
- [no] immediateShow commands
Command descriptions
CLI root-level and global commands
back
Syntax
back
Context
<global>
Description
This command moves the context back one level of the command hierarchy. For example, if the current level is the config router mpls context, the back command moves the cursor to the config router context level.
clear
Syntax
clear
Context
<global>
Description
This command clears statistics for a specified entity or clears and resets the entity.
Parameters
- card
reinitializes an I/O module in a specified slot
- cpm-filter
clears CPM filter
- cron
clears CRON history
- eth-cfm
clears ETH-CFM parameters
- external-alarms
accesses external alarms-related clear commands
- filter
clears IP filter counters
- group-encryption
accesses group encryption-related clear commands
- ipsec
accesses IPSec-related clear commands
- lag
accesses LAG-related clear commands
- log
closes and reinitializes the log specified by log-id
- mda
reinitializes the specified MDA in a particular slot
- mw
reboots managed microwave devices
- port
clears port statistics
- radius
clears the RADIUS server state
- router
accesses clear router commands affecting the router instance in which they are entered
- saa
clears the SAA test results
- scada
clears SCADA statistics
- screen
clears the console or Telnet screen
- security
accesses network security-related clear commands
- service
clears service ID and statistical entities
- system
clears (re-enables) a previously failed reference
- tacplus
clears the TACACS+ server state
- test-oam
accesses OAM-related clear statistics commands
- testhead
accesses test head-related clear commands
- trace
clears the trace log
- vrrp
clears and resets the VRRP interface and statistical entities
echo
Syntax
echo [text-to-echo] [extra-text-to-echo] [more-text]
Context
<global>
Description
This command echoes arguments on the command line. The primary use of this command is to allow messages to be displayed to the screen in files executed with the exec command.
Parameters
- text-to-echo
specifies a text string to be echoed, up to 256 characters
- extra-text-to-echo
specifies more text to be echoed, up to 256 characters
- more-text
specifies more text to be echoed, up to 256 characters
enable-admin
Syntax
enable-admin
Context
<global>
Description
This command enables the user to become a system administrator.
The enable-admin command is in the default profile. By default, all users are granted access to this command.
After the enable-admin command is entered, the user is prompted for a password. If the password matches, the user is granted unrestricted access to all the commands.
The minimum length of the password is determined by the minimum-length command. The complexity requirements for the password are determined by the complexity command.
The following displays an example of the password command usage.
- Example:
config>system>security#passwordsecurity>password# admin-password test1234 hashsecurity>password# aging 365security>password# minimum-length 8security>password# attempts 5 time 5 lockout 20security>password# authentication-order radius tacplus localsecurity>password# enable-adminPassword: test1234security>password#
The following example displays the password configuration:
ALU-1>config>system>security# info
----------------------------------------------
...
aging 365
minimum-length 8
attempts 5 time 5 lockout 20
admin-password "rUYUz9XMo6I" hash
...
----------------------------------------------
ALU-1>config>system>security#
There are two ways to verify that a user is in enable-admin mode:
-
enter the show users command——administrator can see which users are in enable-admin mode, indicated by the "A" on the same line as the username
enter the enable-admin command again at the root prompt and an error message returns
The # sign indicates the current session.
A:7705:Dut-C# show users
===============================================================================
Username Type
From
Router instance
Connection ID Login time
Session ID SSH Channel ID Idle time
===============================================================================
Console
--
--
6 --
6 -- 0d 00:03:20 --
-------------------------------------------------------------------------------
admin Telnet
192.168.192.37
management
8 03OCT2023 14:06:52
8 -- 0d 00:01:04 --
-------------------------------------------------------------------------------
bla Telnet
192.168.192.37
management
9 03OCT2023 14:08:42
9 -- 0d 00:00:09 A-
-------------------------------------------------------------------------------
admin SSHv2
192.168.192.37
management
7 03OCT2023 14:06:24
#7 0 0d 00:00:00 --
-------------------------------------------------------------------------------
Number of users: 3
Number of sessions: 3
'#' indicates the current active session
'A' indicates user is in admin mode
===============================================================================
*A:7705:Dut-C#
exec
Syntax
exec [-echo] [-syntax] {filename| <<[eof-marker-string]}
Context
<global>
Description
This command executes the contents of a text file as if they were CLI commands entered at the console.
Exec commands do not have no versions.
Related commands are:
-
Use this command to configure a URL for a CLI script to exec following a successful configuration boot.
-
Use this command to configure a URL for a CLI script to exec following a failed configuration boot.
Parameters
- -echo
echoes the contents of the exec file to the session screen as it executes
- -syntax
performs a syntax check of the file without executing the commands. Syntax checking looks for invalid commands and keywords as well as unprintable characters in configured parameters. An error message is displayed if any are found.
- filename
the text file with CLI commands to execute
- <<
Stdin can be used as the source of commands for the exec command. When stdin is used as the exec command input, the command list is terminated with <Ctrl-c>, ‟EOF<Return>” or ‟eof_string<Return>”.
If an error occurs entering an exec file sourced from stdin, all commands after the command returning the error are silently ignored. The exec command indicates the command error line number when the stdin input is terminated with an end-of-file input.
- eof-marker-string
The ASCII printable string used to indicate the end of the exec file when stdin is used as the exec file source. <Ctrl-c> and ‟EOF” can always be used to terminate an exec file sourced from stdin.
exit
Syntax
exit [all]
Context
<global>
Description
This command returns to the context from which the current level was entered. For example, if you navigated to the current level on a context by context basis, then the exit command only moves the cursor back one level.
ALU-1# configure
ALU-1>config# router
ALU-1>config>router# mpls
ALU-1>config>router>mpls# exit
ALU-1>config>router# exit
ALU-1>config# exit
If you navigated to the current level by entering a command string, then the exit command returns the cursor to the context in which the command was initially entered.
ALU-1# configure router mpls
ALU-1>config>router>mpls# exit
ALU-1#
The exit all command moves the cursor all the way back to the root level.
ALU-1# configure
ALU-1>config# router
ALU-1>config>router# mpls
ALU-1>config>router>mpls# exit all
ALU-1#
Parameters
- all
exits back to the root CLI context
help
Syntax
help
help edit
help globals
help special-characters
Context
<global>
Description
This command provides a brief description of the help system. The following information is displayed:
Help may be requested at any point by hitting a question mark '?'.
In case of an executable node, the syntax for that node will be displayed with an
explanation of all parameters.
In case of sub-commands, a brief description is provided.
Global Commands:
Help on global commands can be observed by issuing "help globals" at any time.
Editing Commands:
Help on editing commands can be observed by issuing "help edit" at any time.
Parameters
- help
displays a brief description of the help system
- help edit
displays help on editing
Available editing keystrokes:
Delete current character.....................Ctrl-d Delete text up to cursor.....................Ctrl-u Delete text after cursor.....................Ctrl-k Move to beginning of line....................Ctrl-a Move to end of line..........................Ctrl-e Get prior command from history...............Ctrl-p Get next command from history................Ctrl-n Move cursor left.............................Ctrl-b Move cursor right............................Ctrl-f Move back one word...........................Esc-b Move forward one word........................Esc-f Convert rest of word to uppercase............Esc-c Convert rest of word to lowercase............Esc-l Delete remainder of word.....................Esc-d Delete word up to cursor.....................Ctrl-w Transpose current and previous character.....Ctrl-t Enter command and return to root prompt......Ctrl-z Refresh input line...........................Ctrl-l
- help globals
displays help on global commands
Available global commands:
back - Go back a level in the command tree candidate + Commands used for editing candidate configurations echo - Echo the text that is typed in enable-admin - Enable the user to become a system administrator exec - Execute a file - use -echo to show the commands and prompts on the screen exit - Exit to intermediate mode - use option all to exit to root prompt help - Display help history - Show command history logout - Log off this system mrinfo - Request multicast router information mstat - Trace multicast path from a source to a receiver and display multicast packet rate and loss information mtrace - Trace multicast path from a source to a receiver oam + OAM Test Suite ping - Verify the reachability of a remote host pwc - Show the present working context sleep - Sleep for specified number of seconds ssh - SSH to a host telnet - Telnet to a host traceroute - Determine the route to a destination address tree - Display command tree structure from the context of execution write - Write text to another user
- help special-characters
displays help on special characters
Use the following CLI commands to display more information about commands and command syntax:
- ?
lists all commands in the current context
- string?
lists all commands available in the current context that start with the string
- command ?
displays command syntax and associated keywords
- string<Tab> or string<Space>
completes a partial command name (auto-completion) or lists available commands that match the string
history
Syntax
history
Context
<global>
Description
This command lists the last 30 commands entered in this session.
Re-execute a command in the history with the !n command, where n is the line number associated with the command in the history output.
For example:
ALU-1# history
68 info
69 exit
70 info
71 filter
72 exit all
73 configure
74 router
75 info
76 interface "test"
77 exit
79 info
80 interface "test"
81 exit all
82 configure router
83 interface
84 info
85 interface "test"
86 info
87 exit all
88 configure
89 card 1
91 exit
92 router
93 exit
94 history
ALU-1# !88
ALU-1# configure
ALU-1>config#
info
Syntax
info [detail] [operational]
Context
configure
Description
This command displays the running configuration for the configuration context. It can be used at any level under configure but not at the top configure level.
The output of this command is similar to the output of a show config command. This command, however, lists the configuration of the context where it is entered and all branches below that context level.
For example:
ALU-1>config>router>mpls# info
------------------------------------------
mpls
interface "system"
exit
interface "to_1/2/1"
label-map 131
pop
no shutdown
exit
exit
static-lsp "to121"
to 10.8.8.8
push 121 nexthop 10.1.3.1
no shutdown
exit
no shutdown
exit
exit
----------------------------------------------
ALU-1>config>router>mpls#
By default, the command only enters the configuration parameters that vary from the default values. The detail keyword causes all configuration parameters to be displayed.
The operational keyword is used to display the operational configuration of the current configuration context when the user is in candidate edit mode. The operational keyword is mandatory when using the info command while in candidate edit mode.
Parameters
- detail
displays all configuration parameters, including parameters at their default values
- operational
displays the operational configuration of the current configuration context
logout
Syntax
logout
Context
<global>
Description
This command logs out of the router session.
When the logout command is issued from the console, the login prompt is displayed and any log IDs directed to the console are discarded. When the console session resumes (regardless of the user), the log output to the console resumes.
When a Telnet session is terminated from a logout command, all log IDs directed to the session are removed. When a user logs back in, the log IDs must be recreated.
password
Syntax
password
Context
<ROOT>
Description
This command changes a user CLI login password.
When a user logs in after the administrator forces a new-password-at-login, or the password has expired (aging), then this command is automatically invoked.
When invoked, the user is prompted to enter the old password, the new password, and then the new password again to verify the correct input.
If a user fails to create a new password after the administrator forces a new-password-at-login or after the password has expired, the user is not allowed access to the CLI.
ping
Syntax
ping {ip-address | dns-name} [rapid | detail] [ttl time-to-live] [tos type-of-service] [size bytes] [pattern pattern] [source ip-address] [interval seconds] [{next-hop ip-address} | {interface interface-name} | bypass-routing] [count requests] [do-not-fragment] [router router-instance | service-name service-name] [timeout timeout] [fc fc-name]
Context
<global>
Description
This command is the TCP/IP utility to verify IP reachability.
Parameters
- ip-address
the IP address of the remote host to ping
- source ip-address
the source IP address to use in the ping requests
- next-hop ip-address
this option disregards the routing table and sends this packet to the specified next hop address. This address must be on an adjacent router that is attached to a subnet that is common between this and the next-hop router.
- dns-name
the DNS name (if DNS name resolution is configured) of the remote host to ping
- rapid | detail
the rapid parameter specifies to send ping requests rapidly. The results are reported in a single message, not in individual messages for each ping request. By default, five ping requests are sent before the results are reported. To change the number of requests, include the count option.
The detail parameter includes in the output the interface on which the ping reply was received.
ALU-1# ping 192.168.xx.xx4 detail PING 192.168.xx.xx4: 56 data bytes 64 bytes from 192.168.xx.xx4 via fei0: icmp_seq=0 ttl=64 time=0.000 ms. 64 bytes from 192.168.xx.xx4 via fei0: icmp_seq=1 ttl=64 time=0.000 ms. 64 bytes from 192.168.xx.xx4 via fei0: icmp_seq=2 ttl=64 time=0.000 ms. 64 bytes from 192.168.xx.xx4 via fei0: icmp_seq=3 ttl=64 time=0.000 ms. 64 bytes from 192.168.xx.xx4 via fei0: icmp_seq=4 ttl=64 time=0.000 ms. ---- 192.168.xx.xx4 PING Statistics ---- 5 packets transmitted, 5 packets received, 0.00% packet loss round-trip min/avg/max/stddev = 0.000/0.000/0.000/0.000 ms ALU-1#
- time-to-live
the IP Time To Live (TTL) value to include in the ping request, expressed as a decimal integer
- type-of-service
the type-of-service (ToS) bits in the IP header of the ping packets, expressed as a decimal integer
- bytes
the size in bytes of the ping request packets
- pattern
16-bit pattern string to include in the ping packet, expressed as a decimal integer
- seconds
the interval in seconds between consecutive ping requests, expressed as a decimal integer
- interface-name
specifies the interface name
- bypass-routing
sends the ping request to a host on a directly attached network bypassing the routing table. The host must be on a directly attached network or an error is returned.
- requests
the number of ping requests to send to the remote host, expressed as a decimal integer
- do-not-fragment
specifies that the request frame should not be fragmented. This option is particularly useful in combination with the size parameter for maximum MTU determination.
- router-instance
specifies the router name or service ID
- service-name
specifies the service name, 64 characters maximum
- timeout
specifies the timeout in seconds
- fc-name
specifies the forwarding class
pwc
Syntax
pwc [previous]
Context
<global>
Description
This command displays the present or previous working context of the CLI session.
The pwc command provides a user who is in the process of dynamically configuring a chassis a way to display the current or previous working context of the CLI session. The pwc command displays a list of the CLI nodes that hierarchically define the current context of the CLI instance of the user.
For example:
A:ALU>config>router>mpls# pwc
----------------------------------------------
Present Working Context :
----------------------------------------------
<root>
configure
router ‟Base”
mpls
----------------------------------------------
A:ALU>config>router>mpls#
When the previous keyword is specified, the previous context is displayed. This is the context entered by the CLI parser upon execution of the exit command. The current context of the CLI is not affected by the pwc command.
Parameters
- previous
displays the previous working context
sleep
Syntax
sleep [seconds]
Context
<global>
Description
This command causes the console session to pause operation (sleep) for 1 second (default) or for the specified number of seconds.
Parameters
- seconds
specifies the number of seconds for the console session to sleep, expressed as a decimal integer
ssh
Syntax
ssh host [-l username] [router router-instance | service-name service-name] [re-exchange-min minutes] [re-exchange-mbyte megabytes]
Context
<global>
Description
This command opens a Secure Shell (SSH) session with another host.
The command initiates a client SSH session with the remote host and is independent from the administrative or operational state of the SSH server. However, to be the target of an SSH or SFTP session, the SSH server must be operational.
The command also allows the user to initiate an SSH session with a key re-exchange to occur after a specified number of minutes have passed or a specified number of megabytes have been transmitted. If both parameters are configured, the key re-exchange occurs at whatever limit is reached first. If neither parameter is set, key re-exchange does not occur.
Quitting SSH while in the process of authentication is accomplished by either executing a <Ctrl-c> or tilde and dot ‟(~.”), assuming the ‟~” is the default escape character for the SSH session.
Parameters
- host
the remote host for an SSH session. The IP address, DNS name (if DNS name resolution is configured), or the username at the IP address can be specified.
For IPv6 addresses, including the ‟-interface” for the link local address is mandatory; otherwise, ‟-interface” is omitted. For example, if the user is ‟alu_admin” and the IPv6 hostname consists of 2001:db8:a0b:12f0::1 along with the link local interface ‟ies1_chicago”, the full command would be (note the ‟-” between the ipv6-address and the interface):
ssh -l alu_admin 2001:db8:a0b:12f0::1-ies1_chicago
- username
the username to use when opening the SSH session
- router-instance
the router name or service ID
- service-name
the service name, 64 characters maximum
- minutes
specifies the time interval after which the SSH client initiates the key re-exchange
- megabytes
specifies the number of megabytes transmitted during an SSH session after which the SSH client initiates the key re-exchange
telnet
Syntax
telnet [ip-address | dns-name] [port] [router router-instance]
telnet [ip-address | dns-name] [port] [service-name service-name]
Context
<global>
Description
This command opens a Telnet session to a remote host.
Telnet servers in 7705 SAR networks limit a Telnet client to three retries to log in. The Telnet server disconnects the Telnet client session after three retries. The number of retry attempts for a Telnet client session is not user-configurable.
Parameters
- ip-address
the IP address of the remote host
- dns-name
the DNS name (if DNS name resolution is configured) of the remote host
- port
the TCP port number to use to Telnet to the remote host, expressed as a decimal integer
- router-instance
the router name or service ID
- service-name
specifies the service name, 64 characters maximum
traceroute
Syntax
traceroute {ip-address| dns-name} [ttl ttl] [wait milliseconds] [no-dns] [source ip-address] [tos type-of-service] [router router-instance | service-name service-name]
Context
<global>
Description
The TCP/IP traceroute utility determines the route to a destination address. Aborting a traceroute with the <Ctrl-c> command could require issuing a second <Ctrl-c> command before the prompt is returned.
ALU-1# traceroute 192.168.xx.xx4
traceroute to 192.168.xx.xx4, 30 hops max, 40 byte packets
1 192.168.xx.xx4 0.000 ms 0.000 ms 0.000 ms
ALU-1#
Parameters
- ip-address
the IP address to trace
- dns-name
the DNS name (if DNS name resolution is configured)
- ttl
the maximum Time-To-Live (TTL) value to include in the traceroute request, expressed as a decimal integer
- milliseconds
the time in milliseconds to wait for a response to a probe, expressed as a decimal integer
- no-dns
when the no-dns keyword is specified, a DNS lookup for the specified hostname does not perform
- source ip-address
the source IP address to use as the source of the probe packets. If the IP address is not one of the device’s interfaces, an error is returned.
- type-of-service
the type-of-service (ToS) bits in the IP header of the probe packets, expressed as a decimal integer
- router-instance
the router name or service ID
- service-name
specifies the service name, 64 characters maximum
tree
Syntax
tree [detail] [flat]
Context
<global>
Description
This command displays the command hierarchy structure from the present working context.
Parameters
- detail
includes parameter information for each command displayed in the tree output
- flat
displays the command hierarchy on single lines
write
Syntax
write {user | broadcast} message-string
Context
<global>
Description
This command sends a console message to a specific user or to all users with active console sessions.
Parameters
- user
the name of a user with an active console session to which to send a console message
- broadcast
specifies that the message-string is to be sent to all users logged in to the router
- message-string
the message string to send, up to 250 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
Environment commands
alias
Syntax
alias alias-name alias-command-name no alias alias-name
Context
environment
Description
This command enables the substitution of a command line by an alias.
Use the alias command to create alternative names for an entity or command string that are easier to understand and remember. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes. The special characters ‟/” and ‟\” cannot be used as the first character inside an alias string. Only a single command can be present in the command string.
The alias command can be entered in any context but must be created in the root>environment context.
For example, to create an alias named soi to display MPLS interfaces, enter:
alias soi ‟show router mpls interface”
An alias can contain embedded quotes if the quote is preceded with the ‟\” character (for example, alias my-alias "| match \"string\""). This enables aliases to be created as shortcuts for complex commands; for example:
environment alias my-summary "| match expression \"----|Description|Interface|Admin State|Oper State|Transceiver Type|Optical Compliance|Link Length\" | match invert-match expression \"Ethernet Interface|OTU Interface\" | match invert-match expression \"----\" post-lines 1"
When applied to the show port 1/1/1 detail command, show port 1/1/1 detail my-summary displays only the output fields that match the conditions in the match expression as shown in the following examples:
Without alias:
*A:Sar18 Dut-B# show port 1/1/1 detail
==============================================================================
Ethernet Interface
==============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/1 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1572
Single Fiber Mode : No
IfIndex : 35684352 Hold time up : 0 seconds
Last State Change : 05/23/2018 18:41:28 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Phys State Chng Cnt: 1
Configured Mode : network Encap Type : 802.1q
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default
Net. Scheduler Mode: 16-priority
Auto-negotiate : true MDI/MDX : unknown
Config Phy-tx-clock: auto-pref-slave Oper Phy-tx-clock: N/A
NetEgr.Unshaped-Cir: 0 Kbps
Allow Eth-BN : False
Egress Rate : Default Ingress Rate : Default
Egr.Rate Incl.FCS : Disabled
Ingress CBS(bytes) : 130816 Src-pause : Disabled
LACP Tunnel : Disabled
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Loopback : none Swap Mac Addr : Disabled
Loopback Time Left : unspecified
Cfm Loopback : Disabled
PTP Asymmetry : 0 Edge Timestamp : Disable
Timestamp Capable : True
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
EFM OAM : Disabled EFM OAM Link Mon : Disabled
Configured Address : d6:65:01:01:00:01
Hardware Address : d6:65:01:01:00:01
Group Encryption
Inbound Keygroup Id : N/A
Inbound Keygroup Id : N/A
Transceiver Data
Transceiver Status : operational
Transceiver Type : Unknown
Model Number : none
TX Laser Wavelength: 0 nm Diag Capable : no
Connector Code : Unknown Vendor OUI : 00:00:00
Manufacture date : 2000/01/01 Media : Ethernet
Serial Number : none
Part Number : none
Optical Compliance :
Link Length support: Unknown
SFP Sync-E Capable : yes
...
With alias:
*A:Sar18 Dut-B# show port 1/1/1 detail my-summary
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/1 Oper Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Transceiver Type : Unknown
Optical Compliance :
Link Length support: Unknown
-------------------------------------------------------------------------------
*A:Sar18 Dut-B#
Parameters
- alias-name
the alias name. Do not use a valid command string for the alias. If the alias specified is an actual command, this causes the command to be replaced by the alias.
- alias-command-name
the command line to be associated
create
Syntax
[no] create
Context
environment
Description
By default, the create command is required to create a new OS entity.
The no form of the command disables requiring the create keyword.
Default
create
kernel
Syntax
kernel -password password
no kernel
Context
environment
Description
This command enables and disables the kernel.
Parameters
- password
specifies the password to access the kernel, up to 256 characters
more
Syntax
[no] more
Context
environment
Description
This command enables per-screen CLI output, meaning that the output is displayed on a screen-by-screen basis. The terminal screen length can be modified with the terminal command.
The following prompt appears at the end of each screen of paginated output:
Press any key to continue (Q to quit)
The no form of the command displays the output all at once. If the output length is longer than one screen, the entire output is displayed, which may scroll the screen.
Default
more
reduced-prompt
Syntax
reduced-prompt [no of nodes in prompt]
no reduced-prompt
Context
environment
Description
This command configures the maximum number of higher CLI context levels to display in the CLI prompt for the current CLI session. This command is useful when configuring features that are several node levels deep, which can cause the CLI prompt to become too long.
By default, the CLI prompt displays the system name and the complete context in the CLI.
The number of nodes specified indicates the number of higher-level contexts that can be displayed in the prompt.
For example, if reduced-prompt is set to 2, the two highest contexts from the present working context are displayed by name with the hidden (reduced) contexts compressed into a ellipsis (‟…”).
ALU-1>environment# reduced-prompt 2
ALU-1>config>router# interface to-103
ALU-1>...router>if#
The setting is not saved in the configuration. It must be reset for each CLI session or stored in an exec script file.
The no form of the command reverts to the default.
Default
no reduced-prompt
Parameters
- no-of-nodes-in-prompt
the maximum number of higher-level nodes displayed by name in the prompt, expressed as a decimal integer
saved-ind-prompt
Syntax
[no] saved-ind-prompt
Context
environment
Description
This command enables a saved indicator in the prompt. When changes are made to the configuration file, a ‟*” appears in the prompt string indicating that the changes have not been saved. When an admin save command is executed, the ‟*” disappears.
*A:ALU-48# admin save
Writing file to ftp://192.0.2.43/./sim48/sim48-config.cfg
Saving configuration .... Completed.
A:ALU-48
Default
saved-ind-prompt
shell
Syntax
shell -password password
no shell
Context
environment
Description
This command enables and disables the shell.
Parameters
- password
specifies the password to enter the shell, up to 256 characters
suggest-internal-objects
Syntax
[no] suggest-internal-objects
Context
environment
Description
This command enables the suggestion of internally created objects while auto-completing in the CLI.
Default
no suggest-internal-objects
terminal
Syntax
terminal
Context
environment
Description
This command enables the context to configure the terminal screen length and width for the current CLI session. The terminal length and width cannot be configured for Telnet or SSH sessions, as the correct display size is automatically negotiated.
length
Syntax
length lines
Context
environment>terminal
Description
This command sets the terminal screen length (number of lines).
Default
24 — terminal dimensions are set to 24 lines long by 80 characters wide
Parameters
- lines
the number of lines for the terminal screen length
width
Syntax
width width
Context
environment>terminal
Description
This command sets the terminal screen width (number of characters).
Default
80 — terminal dimensions are set to 24 lines long by 80 characters wide
Parameters
- width
the number of characters for the terminal screen width
time-display
Syntax
time-display {local | utc}
Context
environment
Description
This command displays timestamps in the CLI session based on local time or Coordinated Universal Time (UTC).
The system keeps time internally in UTC and is capable of displaying the time in either UTC or local time based on the time zone configured.
This configuration command is only valid for times displayed in the current CLI session. This includes displays of event logs, traps and all other places where a timestamp is displayed.
In general, all timestamps are shown in the time selected. This includes log entries destined for console/session, memory, or SNMP logs. Log files on compact flash are maintained and displayed in UTC format.
Default
time-display local
time-stamp
Syntax
[no] time-stamp
Context
environment
Description
This command displays timestamps before the CLI prompt, indicating the last time that the command was completed. The date and time are displayed; the time format is either local or UTC, depending on how it was set with the time-display command.
Default
no time-stamp
Candidate commands
candidate
Syntax
candidate
Context
<root>
Description
This command enables the context to edit candidate configurations and must preface every command in the candidate CLI branch.
Commands in the candidate CLI branch, except for the edit command, are available only when in candidate edit mode.
Default
n/a
edit
Syntax
edit [exclusive]
Context
candidate
Description
This command enables the candidate edit mode where changes can be made to the candidate configuration and sets the edit point to the end of the candidate. The edit point is the point after which new commands are inserted into the candidate configuration. In candidate edit mode, the CLI prompt displays edit-cfg near the root of the prompt. All other commands in the candidate CLI branch are blocked until the user enters candidate edit mode.
The exclusive parameter allows the user to modify the candidate configuration and block all other users (and other sessions of the same user) from entering candidate edit mode. This parameter can only be used if the candidate configuration is empty and no user is already in candidate edit mode. Before quitting exclusive candidate edit mode, the user must either commit or discard their changes. If the user commits a candidate configuration with the confirmed option while in exclusive candidate edit mode, the exclusive lock is removed during the countdown time to allow any user to confirm the changes.
If the CLI session times out while the user is in exclusive candidate edit mode, the contents of the candidate configuration are discarded. If the user has the candidate configuration locked, the admin disconnect command can be used to forcibly disconnect them and to clear the contents of the candidate.
Default
n/a
Parameters
- exclusive
enables exclusive candidate edit mode
commit
Syntax
commit [confirmed timeout] [comment comment]
commit no-checkpoint [confirmed timeout]
Context
candidate
Description
This command applies the changes in the candidate configuration to the active or operational configuration.
When a candidate configuration is committed, the confirmed keyword can be used to require an additional confirmation, which is useful when changes are being made that could impact management reachability to the router. The contents of the candidate configuration remain visible but cannot be edited until the timeout is completed or the commit is confirmed. If the confirmation is not given with the confirm command within the configured timeout period, the router automatically reverts to a configuration state before the candidate configuration changes were applied.
Standard line-by-line, non-transactional configuration commands (including via SNMP) are not blocked during the countdown period, but any changes made to the configuration during the countdown period are rolled back if the timeout expires.
A rollback revert is blocked during the countdown period until the commit has been confirmed.
If the commit operation is successful, all the candidate changes take operational effect and the candidate configuration is cleared. If there is an error processing the commit, or if the candidate confirm command is not issued and an auto-revert occurs, the router automatically reverts to a configuration state before the candidate configuration changes were applied. If the automatic reversion occurs, the candidate configuration is not cleared and users can continue to edit it and try the commit later.
By default, the 7705 SAR automatically creates a new rollback checkpoint after a successful commit operation that contains the new configuration changes made by the commit. The rollback checkpoint remains available even if the commit is not confirmed. The no-checkpoint keyword allows users to commit the candidate configuration without creating a rollback checkpoint.
A commit operation is blocked if a rollback revert is currently being processed.
Default
n/a
Parameters
- confirmed
requires the confirm command to be issued before the end of the timeout period to avoid an auto-revert of the configuration
- timeout
the auto-revert timeout period, in minutes
- no-checkpoint
blocks the creation of a rollback checkpoint for a successful commit
- comment
a string up to 255 characters in length describing the automatic rollback checkpoint file
confirm
Syntax
confirm
Context
candidate
Description
This command is used to confirm a candidate configuration. If the optional confirmed parameter is used with the commit command, this command must be issued before the timeout period expires; otherwise, the router automatically reverts to a configuration state before the candidate configuration changes were applied. After the automatic reversion, the candidate configuration remains available for editing and a subsequent commit.
During the countdown, the contents of the candidate remain visible with the candidate view command but changes to the candidate are blocked until the timeout is completed or this command is issued.
This command also clears the contents of the candidate configuration and allows users to enter candidate edit mode again.
Default
n/a
copy
Syntax
copy [line]
Context
candidate
Description
This command copies the selected CLI branch, including all sub-branches, into a temporary buffer that can be used with a subsequent insert command. The contents of the temporary buffer are deleted when the operator exits candidate edit mode. Line numbers can be displayed with the candidate view command.
Default
edit-point
Parameters
- line
specifies which line to copy
delete
Syntax
delete [line]
Context
candidate
Description
This command deletes the selected CLI branch, including all sub-branches. The deleted lines are also copied into a temporary buffer that can be used with a subsequent insert command. Line numbers can be displayed with the candidate view command.
Default
edit-point
Parameters
- line
specifies which line to delete
discard
Syntax
discard [now]
Context
candidate
Description
This command deletes the entire contents of the candidate configuration and exits candidate edit mode. The undo command cannot be used to recover a candidate configuration that has been discarded with this command.
Default
n/a
Parameters
- now
deletes the candidate configuration with no confirmation prompt for the discard
goto
Syntax
goto line
Context
candidate
Description
This command changes the edit point of the candidate configuration. The edit point is the point after which new commands are inserted into the candidate configuration as an operator navigates the CLI and issues commands in candidate edit mode. Line numbers can be displayed with the candidate view command.
Default
edit-point
Parameters
- line
specifies which line is to be the edit point for the insertion of new commands
insert
Syntax
insert [line]
Context
candidate
Description
This command inserts the contents of the temporary buffer (populated with a previous copy or delete command) into the candidate configuration. The operator can specify any line in the candidate configuration to be the insertion point, but by default, the contents are inserted after the current edit point. The contents of the temporary buffer are deleted when the operator exits candidate edit mode.
Insertions are context-aware. The temporary buffer always stores the CLI context (such as the current CLI branch) for each line deleted or copied. If the contents to be inserted are supported at the context of the insertion point, they are simply inserted into the configuration. If the contents to be inserted are not supported at the context of the insertion point, the following actions are automatically performed by the system:
The context at the insertion point is closed using multiple exit statements.
The context of the lines to be inserted is built (added) into the candidate configuration at the insertion point.
The contents of the temporary buffer are added.
The context of the inserted lines is closed using exit statements.
The context from the original insertion point is rebuilt, leaving the context at the same point as it was before the insertion.
Line numbers can be displayed with the candidate view command.
Default
edit-point
Parameters
- line
specifies where to insert the contents of the temporary buffer
load
Syntax
load file-url [overwrite | insert | append]
Context
candidate
Description
This command loads a previously saved candidate configuration into the current candidate. The edit point is set to the end of the loaded configuration lines. The current candidate configuration cannot be modified while a load is in progress.
If the current candidate configuration is empty, this command loads the file into the candidate without requiring any of the optional parameters. If the current candidate is not empty, the user must specify overwrite, insert, or append.
Default
n/a
Parameters
- file-url
the directory and filename to load
- overwrite
discards the contents of the current candidate and replaces them with the contents of the file
- insert
inserts the contents of the file at the current edit point
- append
inserts the contents of the file at the end of the current candidate
quit
Syntax
quit
Context
candidate
Description
This command exits candidate edit mode. The contents of the current candidate configuration are not deleted and the user can continue editing them later.
Default
n/a
redo
Syntax
redo [count]
Context
candidate
Description
This command reapplies the changes to the candidate that were previously removed using the undo command. All undo or redo history is lost when the operator exits candidate edit mode.
The redo command is blocked if another user has made changes in a CLI branch that would be impacted during the redo operation.
Default
n/a
Parameters
- count
specifies the number of previous changes to reapply
replace
Syntax
replace [line]
Context
candidate
Description
This command displays the specified line (a single line only) and allows it to be changed.
Line numbers can be displayed with the candidate view command.
Default
edit-point
Parameters
- line
specifies the line to replace
save
Syntax
save file-url
Context
candidate
Description
This command saves the current candidate configuration to a file.
Default
n/a
Parameters
- file-url
specifies the directory and filename
undo
Syntax
undo [count]
Context
candidate
Description
This command removes the most recent changes done to the candidate. The changes can be reapplied using the redo command. The undo and redo history is lost when the operator exits candidate edit mode. This command cannot be used to recover a candidate that has been discarded with a candidate discard command.
This command is blocked if another user has made changes in any of the CLI branches that would be impacted during the undo operation.
Default
1
Parameters
- count
specifies the number of previous changes to remove
view
Syntax
view [line]
Context
candidate
Description
This command displays the candidate configuration along with line numbers that can be used for editing the candidate configuration.
Default
edit-point
Parameters
- line
displays the candidate configuration starting at the specified point
management
Syntax
management cli
Context
config>system
Description
This command enables the CLI management context.
Parameters
- cli
-
specifies the management context
configuration
Syntax
configuration
Context
config>system>management
Description
This command enables the CLI management configuration context.
immediate
Syntax
[no] immediate
Context
config>system>management>configuration
Description
This command controls whether CLI commands in the configure context can make changes to the running configuration.
If the command is enabled, any configuration changes are immediately applied to the running configuration.
The no form of this command blocks configuration changes to the running configuration, and the user must use candidate edit mode to modify the configuration.
Default
immediate
Rollback commands
rollback
Syntax
rollback
Context
admin
config>system
Description
This command enables the context to configure rollback command parameters.
Default
n/a
compare
Syntax
compare [to source2]
compare source1 to source2
Context
admin
admin>rollback
config>xx (where xx is any sub-branch at any level below config, but not at the config context itself)
Description
This command compares two configuration files. If the compare command is entered with no parameters defined, it compares the active configuration to the most recent rollback file. If the command is entered with the source2 parameter defined, it compares the active configuration to the specified file. If the command is entered with both source parameters defined, it compares the first specified file to the second specified file.
The compare command with no parameters can only be used in the admin>rollback context. The compare to source2 command can only be used in the admin>rollback or config>xx context. In the admin context, both source parameters must be specified.
The defaults for the source parameters are context-dependent and differ based on the branch in which the command is executed.
Default
admin context: no defaults (source1 and source2 must be specified)
admin>rollback context: source1 = active-cfg, source2 = latest-rb
config>xx context: source1 = active-cfg, no default for source2
Parameters
- source1, source2
the configuration files to compare
delete
Syntax
delete checkpoint-rescue
Context
admin>rollback
Description
This command deletes a rollback checkpoint file and decrements the suffix ID numbers of all older rollback checkpoint files.
If the config>redundancy>rollback-sync command is enabled, deleting a rollback checkpoint file also deletes the backup file and decrements the suffix ID numbers on the standby CSM.
Default
n/a
Parameters
- checkpoint-rescue
identifies a rollback checkpoint or rescue file to delete
revert
Syntax
revert checkpoint-rescue [now]
Context
admin>rollback
Description
This command initiates a CLI configuration rollback revert operation that returns the configuration state of the node to a previously saved checkpoint file or rescue file. The rollback reversion minimizes impacts to running services. Configuration parameters that have changed since the last rollback checkpoint file was created, or items on which changed configurations have dependencies, are first reset to their default values and then restored to their previous values from the rollback checkpoint file.
Performing a configuration reversion can be briefly service-impacting in changed areas. There are no service impacts to configuration areas that did not change since the rollback checkpoint file was created.
Default
n/a
Parameters
- checkpoint-rescue
identifies the rollback checkpoint or rescue file to revert to
- now
forces a rollback reversion without prompting for confirmation
save
Syntax
save [comment comment] [rescue]
Context
admin>rollback
Description
This command saves the current operational configuration as a rollback checkpoint file at the configured rollback location, using the filename specified by the rollback-location command, with the suffix *.rb. The suffixes of all previously saved rollback checkpoint files are automatically incremented by one (*.rb becomes *.rb.1, *.rb.1 becomes *.rb.2, and so on).
By default, there can be a maximum of 10 rollback checkpoint files, the latest with suffix *.rb and nine older files with suffixes *.rb.1 through *.rb.9. If the maximum number of checkpoint files is reached and a new one is saved, the oldest checkpoint file is deleted. The maximum number of rollback checkpoint files that can be saved can be configured with the local-max-checkpoints and remote-max-checkpoints commands.
If the rescue keyword is used, this command saves the current operational configuration as a rescue rollback file at the location and with the filename specified by the rescue-location command. The rescue file uses the suffix *.rc. There can be only one rescue file saved at a time. Saving a new rescue file deletes and replaces any existing rescue file.
A valid rollback checkpoint and rescue location must be configured with the rollback-location and rescue-location commands before saving a checkpoint or rescue file.
Default
n/a
Parameters
- comment
a string up to 255 characters in length describing the associated rollback checkpoint file
- rescue
saves the current operational configuration as a rollback rescue file with the suffix *.rc
view
Syntax
view [checkpoint-rescue]
Context
admin>rollback
Description
This command displays the configuration settings saved in a rollback checkpoint or rescue file, or the active operational system configuration.
Default
latest-rb
Parameters
- checkpoint-rescue
identifies the configuration file to view
local-max-checkpoints
Syntax
local-max-checkpoints [number]
no local-max-checkpoints
Context
config>system>rollback
Description
This command configures the maximum number of rollback checkpoint files that can be saved to the local compact flash.
When the maximum number of files are saved, the oldest rollback checkpoint file has an ID value one less than the configured maximum, because one rollback checkpoint file is always the latest file and does not have an ID number. For example, if you configure the maximum number of checkpoints as 50, after performing 50 rollback save commands, there is a rollback checkpoint file with extension *.rb, and 49 older files with extension *.rb.1 to *.rb.49.
The no form of this command resets the maximum value to the default.
Default
10
Parameters
- number
the maximum number of rollback checkpoint files
remote-max-checkpoints
Syntax
remote-max-checkpoints [number]
no remote-max-checkpoints
Context
config>system>rollback
Description
This command configures the maximum number of rollback checkpoint files that can be saved on a remote device.
When the maximum number of files are saved, the oldest rollback checkpoint file has an ID value one less than the configured maximum, because one rollback checkpoint file is always the latest file and does not have an ID number. For example, if you configure the maximum number of checkpoints as 50, after performing 50 rollback save commands, there is a latest rollback checkpoint file with extension *.rb, and 49 older files with extension *.rb.1 to *.rb.49.
The no form of this command resets the maximum value to the default.
Default
10
Parameters
- number
the maximum number of rollback checkpoint files
rescue-location
Syntax
[no] rescue-location file-url | rescue filename
Context
config>system>rollback
Description
This command configures the location and generic filename of the rollback rescue configuration file.
A rescue file can be saved locally on the compact flash or on a remote device. The file URL must not include a filename extension. The suffix for the rollback rescue configuration file is *.rc and is automatically appended when the file is saved.
A valid rollback rescue location must be configured before a rollback save command is executed.
Default
no rescue-location
Parameters
- file-url
the local or remote file path for the rollback rescue configuration file (see URL types and syntax for parameter descriptions)
- rescue filename
the generic filename for rollback rescue configuration files
rollback-location
Syntax
[no] rollback-location file-url | rollback filename
Context
config>system>rollback
Description
This command configures the location and generic filename of rollback checkpoint files. Files can be saved locally on the compact flash or on a remote device.
The file-url or filename must not include a filename extension. The suffixes for rollback checkpoint files are *.rb and *.rb.1 to *.rb.x, and are automatically appended when the file is saved.
A valid rollback checkpoint location must be configured before a rollback save command is executed.
Default
no rollback-location
Parameters
- file-url
the local or remote file path for rollback checkpoint files (see URL types and syntax for parameter descriptions)
- rollback filename
the generic filename for rollback checkpoint files
rollback-sync
Syntax
rollback-sync
Context
admin>redundancy
Description
This command copies all existing rollback checkpoint files from the active CSM compact flash to the standby CSM compact flash on a 7705 SAR-8 Shelf V2 or 7705 SAR-18. You can also enable the system to save an automatic backup of each new rollback checkpoint file with the command in the config>redundancy context.
Rollback checkpoint files can only be backed up from local sources and only by using the two dedicated rollback-sync commands. The synchronize commands in the config>redundancy and admin>redundancy contexts do not apply to rollback checkpoint files.
Default
n/a
rollback-sync
Syntax
[no] rollback-sync
Context
config>redundancy
Description
This command enables automatic synchronization of locally saved rollback checkpoint files between the active CSM and standby CSM.
When automatic rollback synchronization is enabled, a rollback save causes the new checkpoint file to be saved on both the active and standby CSMs if the rollback location is a local location. The suffixes of all older checkpoint files on both active and standby CSMs are incremented by one. Automatic synchronization only causes new rollback checkpoint files to be copied to both CSMs. Any rollback checkpoint files that were created before rollback-sync was enabled are not copied to the standby CSM. You can manually back up all files using the command in the admin>redundancy context.
Rollback checkpoint files can only be backed up from local sources and only by using the two dedicated rollback-sync commands. The synchronize commands in the config>redundancy and admin>redundancy contexts do not apply to rollback checkpoint files.
The no form of this command disables automatic synchronization of new rollback checkpoint files.
Default
no rollback-sync
Show commands
alias
Syntax
alias
Context
show
Description
This command displays a list of existing aliases.
Output
The following output is an example of alias information, and Alias field descriptions describes the fields.
Output exampleALU-103>config>system# show alias
==============================================================================
Alias-Name Alias-command-name
==============================================================================
sri show router interface
sse show service service-using cpipe
ssvll show service service-using vll
------------------------------------------------------------------------------
Number of aliases : 3
==============================================================================
ALU-103>config>system#
|
Label |
Description |
|---|---|
|
Alias-Name |
Displays the name of the alias |
|
Alias-command-name |
The command and parameter syntax that define the alias |
|
Number of aliases |
The total number of aliases configured on the router |
candidate
Syntax
candidate
Context
show>system
Description
This command shows candidate configuration information.
Default
n/a
Output
The following output is an example of candidate information, and Candidate configuration field descriptions describes the output fields.
Output example*A:Sar8 Dut-A# show system candidate
===============================================================================
Candidate Config Information
===============================================================================
Candidate configuration state : modified
Num editors/viewers : 1
Candidate cfg exclusive locked : no
Last commit state : success
Last commit time : 2021/04/08 21:13:00
Last commit initiated user : admin
Checkpoint created with last commit : yes
Scheduled revert time : N/A
Last commit revert time : N/A
===============================================================================
Users in edit-cfg mode
===============================================================================
Username Type (from)
===============================================================================
admin Telnet (192.0.2.239)
===============================================================================
*A:Sar8 Dut-A#
|
Label |
Description |
|---|---|
|
Candidate configuration state |
empty — there are no uncommitted changes in the candidate configuration modified — there are uncommitted changes in the candidate configuration unconfirmed — there are no uncommitted changes in the candidate configuration but the result of the last commit automatically reverts to a previous configuration unless it is confirmed before the timeout expires |
|
Num editors/viewers |
The number of CLI sessions currently in candidate edit mode |
|
Candidate cfg exclusive locked |
Indicates if a user has exclusively locked the candidate configuration using the candidate edit exclusive command |
|
Last commit state |
none — there have been no commits since the last reboot of the node in-progress — the system is currently committing the candidate configuration success — the last commit finished successfully revert-pending — the last commit finished successfully but has not been confirmed yet and an auto-revert will occur if it is not confirmed before the timeout expires failed — the last commit failed and has been undone revert-in-progress — the last commit finished successfully but was not confirmed in time and the system is currently reverting to a previous configuration reverted — the last commit finished successfully but was not confirmed in time and the system has reverted to a previous configuration revert-failed — the last commit finished successfully but was not confirmed in time and the system attempted a reversion but failed |
|
Last commit time |
The time at which the last commit attempt was started |
|
Last commit initiated user |
The name of the user who initiated the last candidate commit |
|
Checkpoint created with last commit |
Indicates if a rollback checkpoint was created after the previous commit completed |
|
Scheduled revert time |
The currently scheduled auto-revert time if the confirmed option is being used with a candidate commit |
|
Last commit revert time |
The time the system was last reverted to a previous configuration |
|
Users in edit-cfg mode |
Lists all the user sessions that are currently in candidate edit mode |
|
Username |
The name of the user that is currently in candidate edit mode |
|
Type (from) |
The type of session (such as console or Telnet) and the source of the session (such as the source IP address of the remote host) |