Filter Policies
This chapter provides information about filter policies and management.
Topics in this chapter include:
Configuring Filter Policies
Topics in this section include:
Overview of Filter Policies
Filter policies (or filters), also referred to as Access Control Lists (ACLs), are sets of rules that can be applied to network interfaces and services (VLL (Ethernet and IP), VPLS, VPRN and IES, and IES in-band management). Filter policies constrain network or user traffic based on match criteria and determine the action that will be invoked against the subject packet (that is, the default action can be either ‟drop” or ‟forward”).
The 7705 SAR supports seven types of filter policies:
IP filters
MAC filters
VLAN filters
CSM filters
IP exception filters
management access filters
match-list filters
The 7705 SAR also supports policy-based routing (PBR), which is based on IP filters, and multi-field classification (MFC).
IP, MAC, and VLAN filters scan all traffic and take the appropriate (configured) action against matching packets. Packets that are not filtered by one of these filters and are destined for the 7705 SAR are then scanned by the CSM filter, if configured.
IP exception filters scan all outbound traffic entering a Network Group Encryption (NGE) domain and allow packets that match the exception filter criteria to transit the NGE domain unencrypted.
IP and MAC filter support for SAP and SDP is described in the following sections and is summarized in IP and MAC Filter Support on SAPs and IP and MAC Filter Support on SDPs . Ingress filter override support for routed VPLS on IES and VPRN services is summarized in Routed VPLS Ingress Filter Override Support . IPv4 and IPv6 filter support (ingress and egress) for network interfaces is described in the lists following Routed VPLS Ingress Filter Override Support . MAC filters do not support network interfaces.
Configuring an entity for a filter policy is optional. If a network or service interface is not configured with filter policies, all traffic is allowed on the interface. By default, there are no filters associated with interfaces or services. The filters must be explicitly created and associated. When you create a new filter, you must specify a unique filter ID value for each new filter policy, as well as each new filter entry and associated actions. The filter entries specify the filter matching criteria. See Filter Policy Entries. After creating a filter policy you can also, optionally, assign filters a unique name. Filter IDs or filter names can be used throughout the system to manage filter policies and assign them to interfaces.
Service SAP |
Ingress Filter |
Egress Filter |
||||
|---|---|---|---|---|---|---|
IPv4 |
IPv6 |
MAC |
IPv4 |
IPv6 |
MAC |
|
Epipe |
Yes |
No |
No |
No |
No |
No |
IES |
Yes |
Yes |
No |
Yes |
Yes |
No |
Ipipe |
Yes |
No |
No |
No |
No |
No |
VPLS |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
VPRN |
Yes |
Yes |
No |
Yes |
Yes |
No |
Service SDP |
Ingress Filter |
Egress Filter |
||||
|---|---|---|---|---|---|---|
IPv4 |
IPv6 |
MAC |
IPv4 |
IPv6 |
MAC |
|
Epipe |
No |
No |
No |
No |
No |
No |
IES |
Yes |
No |
No |
No |
No |
No |
Ipipe |
No |
No |
No |
No |
No |
No |
VPLS |
Yes |
Yes |
Yes |
No |
No |
No |
VPRN |
Yes |
Yes |
No |
No |
No |
No |
Service |
Ingress Override IPv4 |
Ingress Override IPv6 |
|---|---|---|
IES |
Yes |
Yes |
VPRN |
Yes |
Yes |
IP Filters
IPv4 filters can be applied to the following entities:
network interfaces
ingress and egress network interfaces, affecting incoming traffic from the network link and outgoing traffic to the network link
SAPs
ingress IES management SAPs, affecting incoming node management traffic
ingress pseudowire SAPs (Epipe and Ipipe), affecting incoming user traffic
ingress VPLS SAPs, affecting incoming user traffic
ingress VPRN SAPs and IES SAPs, affecting incoming user traffic
egress VPLS SAPs (Ethernet SAPs only), affecting outgoing user traffic
egress VPRN and IES SAPs, affecting outgoing user traffic
SDPs
ingress VPLS SDPs (spoke and mesh), affecting incoming traffic from the remote end of the service
ingress IES and VPRN interface spoke SDPs, affecting incoming traffic from the remote end of the service
Ingress filters affect only incoming packets regardless of whether the packets need to be forwarded to a downstream router or are destined for the 7705 SAR.
IPv6 filters can be applied to the following entities:
network interfaces
ingress and egress Ethernet network interfaces (with null or dot1q encapsulation)
ingress and egress network interfaces on the 4-port OC3/STM1 Clear Channel Adapter card (with POS encapsulation)
SAPs
ingress IES SAPs
ingress and egress VPLS SAPs
ingress and egress VPRN SAPs
SDPs
ingress VPLS SDPs (spoke and mesh), affecting incoming traffic from the remote end of the service
ingress VPRN interface spoke SDPs, affecting incoming traffic from the remote end of the service
MAC Filters
MAC filters can be applied to the following entities:
SAPs
ingress and egress VPLS SAPs, affecting incoming or outgoing user traffic
SDPs
ingress VPLS SDPs (spoke and mesh), affecting outgoing user traffic
VLAN Filters
VLAN filters can be applied to ring ports at the ingress point on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. VLAN filters are blocked on all other adapter cards and modules.
CSM Filters
The 7705 SAR supports IPv4 and IPv6 CSM filters. For information on CSM filters, refer to the 7705 SAR System Management Guide, ‟CSM Filters and CSM Security”.
IP Exception Filters
The 7705 SAR supports IPv4 exception filters. For information on IP exception filters, refer to the 7705 SAR Services Guide, ‟Router Encryption Exceptions using ACLs”.
Match List for Filter Policies
The filter match-list ip-prefix-list and ipv6-prefix-list commands define a list of IP prefixes that can be used as match criteria for adapter card IP and IPv6 filters. These commands can also be used for CPM (CSM) filters, IP exception filters, and management access filters.
A match list simplifies the filter policy configuration by allowing multiple prefixes to be listed in a single filter entry instead of creating an entry for each.
The same match list can be used in more than one filter policy. A change in match list content is automatically propagated across all policies that use that list.
To modify any existing IP prefix list, remove any filter that uses it from where it is applied, i.e. a router or service interface, or a SAP or an SDP (spoke and mesh), or for an IP exception in the group-encryption context. For CPM filters, the filter must be shut down.
Similar removal as above is required to modify the filter’s match source and destination IP address values to add, delete, or modify an IP prefix list.
Prefix-exclude
A prefix can be excluded from an IPv4 or IPv6 prefix list with the prefix-exclude command.
For example, when traffic needs to be rate limited to 10.0.0.0/16 with the exception of 10.0.2.0/24, the following options are available.
By applying prefix-exclude, a single IP prefix list is configured with two prefixes:
ip-prefix-list "list-1" create prefix 10.0.0.0/16 prefix-exclude 10.0.2.0/24 exitWithout applying prefix-exclude, all eight included subnets must be manually configured in the IP prefix list:
ip-prefix-list "list-1" create prefix 10.0.0.0/23 prefix 10.0.3.0/24 prefix 10.0.4.0/22 prefix 10.0.8.0/21 prefix 10.0.16.0/20 prefix 10.0.32.0/19 prefix 10.0.64.0/18 prefix 10.0.128.0/17 exit
Manually configuring an IP prefix list is time consuming and error-prone compared to using the prefix-exclude command.
The filter resources, consumed in hardware, are identical between the two configurations.
Configured prefix-exclude prefixes are ignored when no overlapping larger subnet is configured in the prefix list. For example: prefix-exclude 1.1.1.1/24 is ignored if the only included subnet is 10.0.0.0/16.
Network and Service (Access) Interface-based Filtering
IP and MAC filter policies specify either a forward or a drop action for packets, based on information specified in the match criteria. Within each filter policy, you can create entries that define matching criteria.
The same IP filter policy can be assigned to any entity (network interfaces, IP pseudowires, Ethernet pseudowires, VPLS services, VPRN services, and IES services), all of which can be configured on the same adapter card. For example, a filter policy with filter-id defined as filter-5 can be assigned to multiple Ipipe SAPs and, simultaneously, to network interfaces on the same adapter card.
A filter policy assigned to an entity on one adapter card can also be assigned to any entity on another adapter card. For example, a filter policy with filter-id defined as filter-2 can be assigned to an Epipe on an Ethernet adapter card and to a network interface on another Ethernet adapter card.
Only one type of filter (IP or MAC) can be assigned to an interface at a time, and only one filter of that type can be assigned to an interface at a time. The exception is a dual-stack interface (one that supports both IPv4 and IPv6); the interface can have both an IPv4 and an IPv6 filter assigned to it.
Both IP and MAC filter policies are supported per adapter card, and assigning the same filter policy to different entities on a card counts as using one filter policy.
Filter entry matching criteria can be as general or specific as required, but all conditions in the entry must be met in order for the packet to be considered a match and the specified entry action performed. The process stops when the first complete match is found and the action defined in the entry is executed (that is, packets that match the criteria are either dropped or forwarded).
Configuration and assignment of IP and MAC filter policies is similar for network interfaces, IES management SAPs, Ethernet and IP pseudowire SAPs, VPRN and IES interface SAPs and spoke SDPs, and VPLS SAPs and SDPs (spoke and mesh). This guide describes the assignment of filter policies to network interfaces. For detailed information on assigning filters to a service, refer to the 7705 SAR Services Guide; see ‟IP Filters” (under ‟Ethernet VLL (Epipe) Services” and ‟IP Interworking VLL (Ipipe) Services”) for information on assigning IP filter policies to SAPs and spoke SDPs, and see ‟MAC Filters” (under VPLS Features), for information on assigning MAC filter policies to VPLS SAPs and SDPs.
Policy-Based Routing
Traditionally, IP routing is done by making routing decisions based on the destination IP address of the incoming packet. PBR expands the routing decision from one based solely on the destination IP address to include any other IP criteria, such as source IP address, DSCP, or source/destination UDP/TCP port.
Using PBR at the iLER node provides filtering needed to route IP traffic over multiple uplink interfaces or tunnels using IP criteria. For example, a service provider can use PBR to separate high-value traffic (signaling) from user data by examining the source IP address or DSCP bits (or both) of the incoming IP packets and assign a separate transport tunnel to each traffic flow. The transport tunnels can be engineered by using RSVP-TE throughout the entire mobile backhaul network with specific reservation values. The LSP is signaled throughout the network and reserves the needed resources at each node, ensuring the QoS for the high-value traffic.
PBR can also be used to extract packets from the data path and send them to the CSM for debugging or slow path forwarding.
PBR Filtering Based on the DSCP of Incoming Packets illustrates a PBR implementation for VPRN services in an LTE network, and includes CLI command syntax. The 7705 SAR-8 Shelf V2 at the cell site makes routing decisions based on the incoming packet DSCP only, as follows:
BE packets are forwarded to 7750 SR_1 over SDP1
AF11 packets are forwarded to 7750 SR_2 over SDP2
each SDP (SDP1 and SDP2) is signaled throughout the network using RSVP-TE protocol with its own separate TE criteria
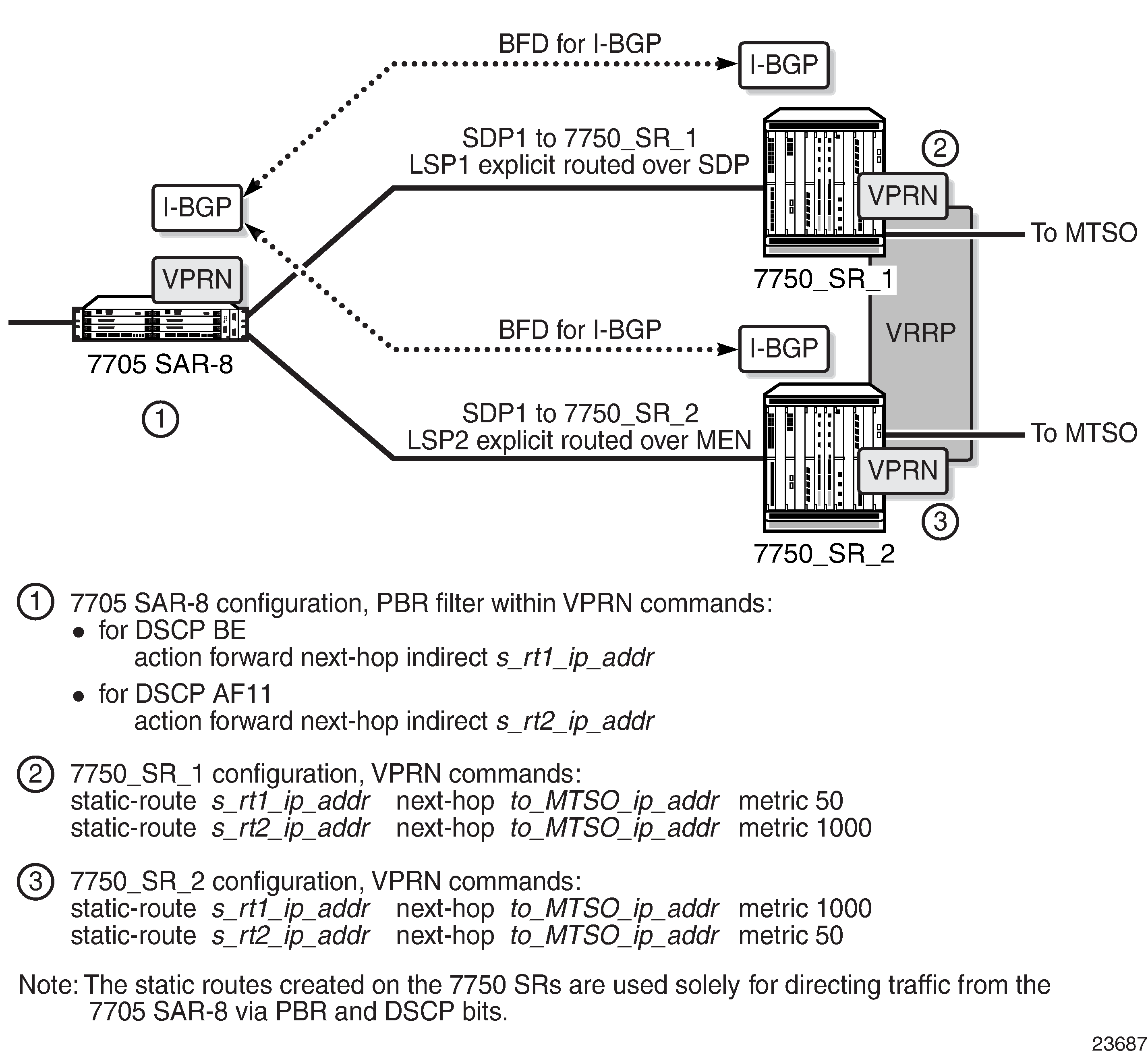
PBR is supported at ingress for the following services and interfaces:
IES and VPRN service
SAP
Layer 3 spoke SDP
routed VPLS
router network interface (Global Routing Table (GRT))
PBR is supported on the private IPSec service (VPRN). For more information about IPSec and PBR, see the ‟PBR” section in the 7705 SAR Services Guide.
Multi-field Classification (MFC)
Multi-field classification (MFC) allows untrusted traffic arriving on the access ports of the 7705 SAR to be reclassified and queued according to a forwarding class assigned to the traffic.
Traffic is classified based on IP criteria. Arriving traffic has an ACL (also known as filter policies) applied to it. If the ACL action is forward fc, a match results in the assignment of the corresponding configured Forwarding Class (FC). This FC is used for queuing of the packet through the 7705 SAR. The match can be based on any IP criteria currently supported by the 7705 SAR IP filter policies.
When MFC is configured and a match is made on an arriving packet, the FC is based only on the MFC configuration. The access ingress policy is no longer active for this packet.
Both PBR and MFC are configured under the IP filter configuration and the action of the filter policy can include both PBR (next-hop ip-address) and MFC (fc fc-name).
If MFC is assigned to a Layer 3 spoke-SDP termination interface, MFC classification is based on the traffic’s customer-assigned inner IP packet. The filter policy rules are applied to the IP criteria of the inner packet after the VC label and transport tunnel label have been removed from the packet. Based on the matching criteria, the appropriate FC is assigned to the packet. This functionality allows the customer packet to be marked with the correct DSCP before it egresses the 7705 SAR. This applies only to an untrusted SAP configuration that has a SAP egress QoS policy assigned to it.
MFC is supported at ingress for the following services and interfaces:
IES and VPRN service
SAP
Layer 3 spoke SDP
routed VPLS
router network interface (Global Routing Table (GRT))
VLLs
Epipe
Ipipe
VPLS
SAP
spoke or mesh SDP
Multi-field classification (MFC) is also supported on the private IPSec service (VPRN). MFC functions in the same manner as the VPRN configuration of traditional services.
VLAN-based Filtering
VLAN filter policies specify either a forward or a drop action for packets, based on VLAN ID information specified in the policy match criteria.
Only one VLAN filter is allowed per ring port on the 2-port 10GigE (Ethernet) Adapter card or 2-port 10GigE (Ethernet) module. The same VLAN filter can be applied to both ring ports. Each VLAN filter supports up to 64 matching criteria entries. The filter acts on ingress traffic and the forwarding action sends packets to the other ring port or to the v-port, depending on the packet’s destination.
The number of VLAN filters that can be created depends on the memory available on the 2-port 10GigE (Ethernet) Adapter card or 2-port 10GigE (Ethernet) module.
The 7705 SAR does not support filter logging or statistics collection for VLAN filters.
Filter Policy Entries
Topics in this section include:
A filter policy compares the match criteria specified within a filter entry to packets coming into the system, in the order the entries are numbered in the policy. When a packet matches all the parameters specified in the entry, the system takes the specified action to either drop or forward the packet. If a packet does not match the entry parameters, the packet continues through the filter process and is compared to the next filter entry, and so on.
If the packet does not match any of the entries, the system executes the default action specified in the filter policy, which is to either drop or forward the packet. Each filter policy is assigned a unique filter ID. Each filter policy is defined with:
scope (exclusive or template) (except VLAN filter policies, which always have a template scope)
default action (drop or forward)
description
at least one filter entry
Each filter entry contains:
match criteria
an action
Applying Filter Policies
IPv4 filter policies can be applied at:
network interfaces
ingress and egress of network IP interfaces
SAPs
ingress of Ethernet and IP pseudowire SAPs (Epipe and Ipipe), VPLS SAPs, VPRN SAPs, and IES SAPs
ingress of IES in-band management SAPs
egress of VPRN and IES SAPs
egress of VPLS SAPs (Ethernet only)
SDPs
ingress of VPLS SDPs (spoke and mesh)
ingress of VPRN and IES spoke SDPs
IPv6 filters can be applied at:
network interfaces
ingress and egress of Ethernet network interfaces (with null or dot1q encapsulation)
ingress and egress of network interfaces on the 4-port OC3/STM1 Clear Channel Adapter card (with POS encapsulation)
SAPs
ingress and egress of IES SAPs
ingress and egress of VPRN SAPs
ingress and egress of VPLS SAPs
SDPs
ingress of VPRN spoke SDPs
ingress of VPLS SDPs
MAC filter policies can be applied at the ingress of VPLS SAPs (Ethernet, and ATM on clear channel OC3 adapter cards) and SDPs (spoke and mesh).
VLAN filters can only be applied to ring ports on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module.
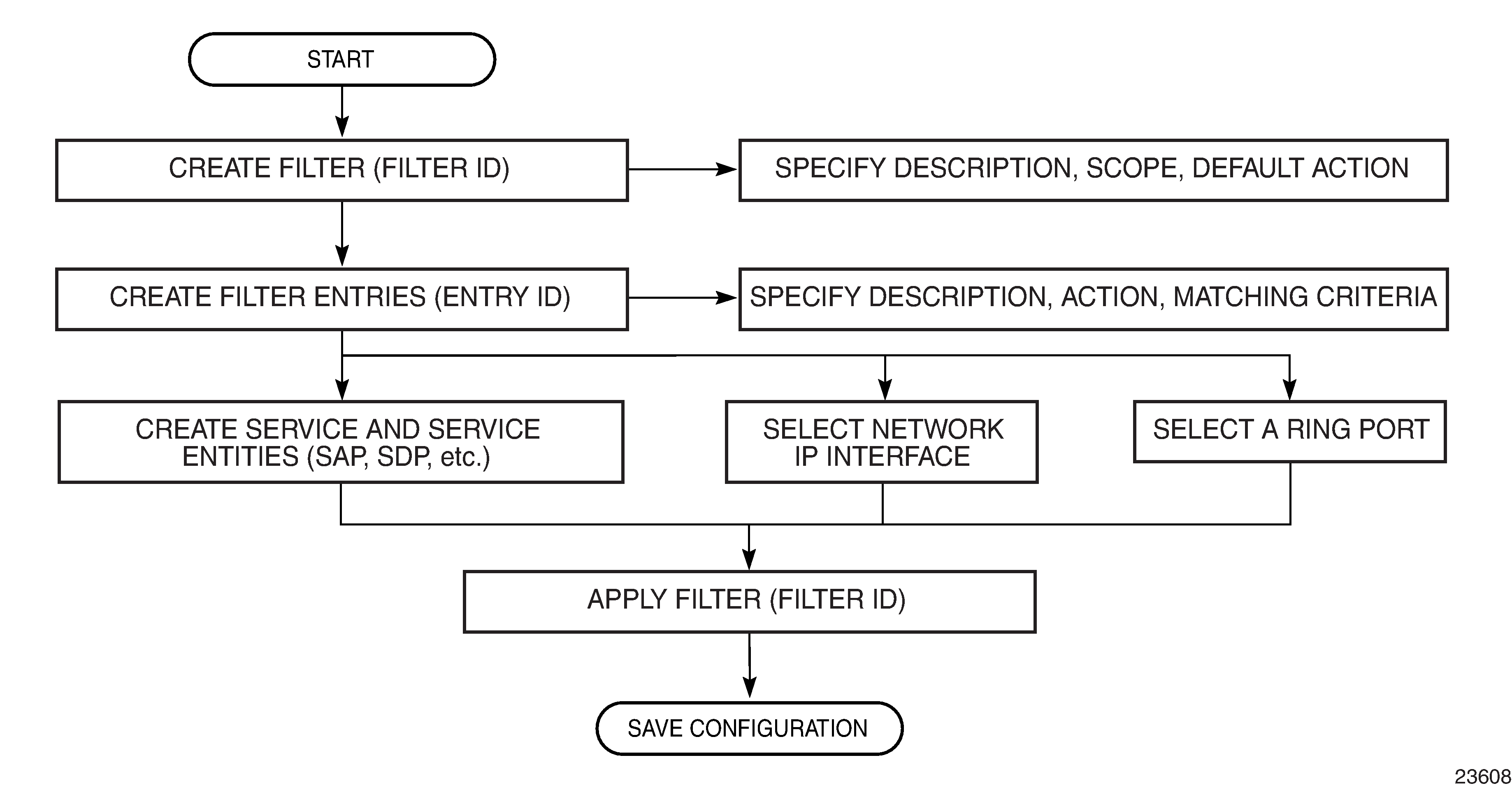
Creating and Applying Filter Policies shows the process to create filter policies and apply them to a network interface.
Packet Matching Criteria
IPv4 and IPv6 filter entries can specify one or more matching criteria. However, to support the maximum 256 entries for IPv4 or IPv6 filters, any entry that uses source port (src-port) and/or destination port (dst-port) ranges (lt, gt, or range keywords) as match criteria must be within the first 64 entries.
For IPv6 filters, the combined number of fields for all entries in a filter must not exceed 16 fields (or 256 bits), where a field contains the bit representation of the matching criteria.
All conditions must be met in order for the packet to be considered a match and the specified action performed. The process stops when the first complete match is found and the action defined in the entry is executed (that is, packets that match the criteria are either dropped or forwarded). If no match is found, the default action is to drop the packet.
Matching criteria for IP filters, MAC filters, and VLAN filters are described in IP Filter Policy Criteria, MAC Filter Policy Criteria, and VLAN Filter Policy Criteria, respectively.
IP Filter Matching Criteria
IPv4 and IPv6 filter policies compare the matching criteria to traffic at a network interface. Matching criteria to drop or forward IP traffic are described in IP Filter Policy Criteria.
Criteria |
Description |
|---|---|
Protocol identifier/next header |
For IPv4, entering a protocol identifier allows the filter to match the IP protocol. Common protocol numbers include ICMP(1), TCP(6), and UDP(17). For a full list of protocol numbers, see the config>filter>ip-filter>entry>match command in the Filter Command Reference. For IPv6, entering a next header allows the filter to match the first next header following the IPv6 header. |
DSCP name |
Entering a DSP name allows the filter to match DiffServ Code Point (DSCP) names |
Destination IP address and mask |
Entering a destination IP address and mask allows the filter to match destination IP address and mask values (for IPv4) and matching destination IP address and prefix length (for IPv6). The IPv4 address scheme consists of 32 bits expressed in dotted-decimal notation. The IPv6 address scheme consists of 128 bits expressed in colon-hexadecimal format. |
Destination port/range |
Entering a destination port/range allows the filter to match TCP or UDP values |
Fragmentation |
Entering a fragment allows the filter to match the fragmentation state of packets (fragmented or non-fragmented) (not applicable to IPv6) |
ICMP code |
Entering an ICMP code allows the filter to match an ICMP code in the ICMP header |
ICMP type |
Entering an ICMP type allows the filter to match an ICMP type in the ICMP header |
IP option |
Entering an IP option allows the filter to match an option or range of options in the IP header (not applicable to IPv6) |
Multiple IP options |
Entering multiple IP options allows the filter to match the state of multiple option fields in the IP header (true or false) (not applicable to IPv6) |
Option present |
Entering option present allows the filter to match the state of the option field in the IP header (present or absent) (not applicable to IPv6) |
Source IP address and mask |
Entering a source IP address and mask allows the filter to match a source IP address and mask values (for IPv4) or a source IP address and prefix length (for IPv6). The IPv4 address scheme consists of 32 bits expressed in dotted-decimal notation. The IPv6 address scheme consists of 128 bits expressed in colon-hexadecimal format. |
Source port/range |
Entering a source port/range allows the filter to match a TCP or UDP port and range values |
TCP ACK |
Entering TCP ACK allows the filter to match the state of the ACK bit set in the control bits of the TCP header of an IP packet (set or not set) |
TCP SYN |
Entering a TCP SYN allows the filter to match the state of the SYN bit set in the control bits of the TCP header of an IP packet (set or not set) |
MAC Filter Matching Criteria
MAC filter policies compare the matching criteria to traffic at the ingress of a VPLS SAP or SDP (spoke or mesh). Matching criteria to drop or forward MAC traffic are described in MAC Filter Policy Criteria.
Criteria |
Description |
|---|---|
Frame type |
Entering the frame type allows the filter to match a specific type of frame format; for example, Ethernet-II only matches Ethernet-II frames |
Source MAC address |
Entering the source MAC address allows the filter to search for a matching source MAC address. Enter the source MAC address in the form xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 00:dc:98:1d:00:00. |
Destination MAC address |
Entering the destination MAC address allows the filter to search for a matching destination MAC address. Enter the destination MAC address in the form xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 02:dc:98:1d:00:01. |
Ethertype |
Entering an Ethernet type II Ethertype value allows the value to be used as a filter match criterion. The Ethernet type field is a 2-byte field used to identify the protocol carried by the Ethernet frame. The Ethertype accepts decimal, hex, or binary in the range of 1536 to 65535. |
VLAN Filter Matching Criteria
VLAN filter policies compare the matching criteria to traffic at the ingress of a ring port on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. Matching criteria to drop or forward traffic are described in VLAN Filter Policy Criteria.
Criteria |
Description |
|---|---|
VLAN ID or VLAN range |
Entering a VLAN identifier or range allows the filter to match VLAN ID values |
Untagged |
Selecting untagged allows the filter to match on Ethernet frames with no tag or dot1q header. Having no tag or dot1q header is also referred to as null encapsulation. |
Ordering Filter Entries
When entries are created, they should be arranged sequentially from the most explicit entry to the least explicit. Filter matching ceases when a packet matches an entry. The entry action is performed on the packet, either drop or forward. To be considered a match, the packet must meet all the conditions defined in the entry.
Sufficient free space is required to renumber a filter entry, as there may be multiple sub-entries if IP prefix lists are in use.
The following example displays the number of sub-entries that an entry uses:
*A:SAR8-39-7>config>filter>ip-filter# show filter ip 1 entry 1
===============================================================================
IP Filter
===============================================================================
Filter Id : 1 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Sub-Entries : 16
Packets are compared to entries in a filter policy in ascending entry ID order. To reorder entries in a filter policy, for example, to reposition entry ID 6 as entry ID 2, use the renum command (renum 6 2).
When a filter policy consists of a single entry, the filter executes actions as follows.
If a packet matches all the entry criteria, the entry’s specified action is performed (drop or forward).
If a packet does not match all of the entry criteria, the policy’s default action is performed (drop or forward).
If a filter policy contains two or more entries, packets are compared in ascending entry ID order (for example, 1, 2, 3 or 10, 20, 30).
Packets are compared with the criteria in the first entry ID.
If a packet matches all the properties defined in the entry, the entry’s specified action is executed.
If a packet does not completely match, the packet continues to the next entry, and then subsequent entries.
If a packet does not completely match any subsequent entries, the default action is performed (drop or forward).
Note: By default, all created filters have a default action of drop (implicit drop). That is, if none of the entries in the filter match the packet, and a default action is not explicitly configured by the user, the packet is dropped.
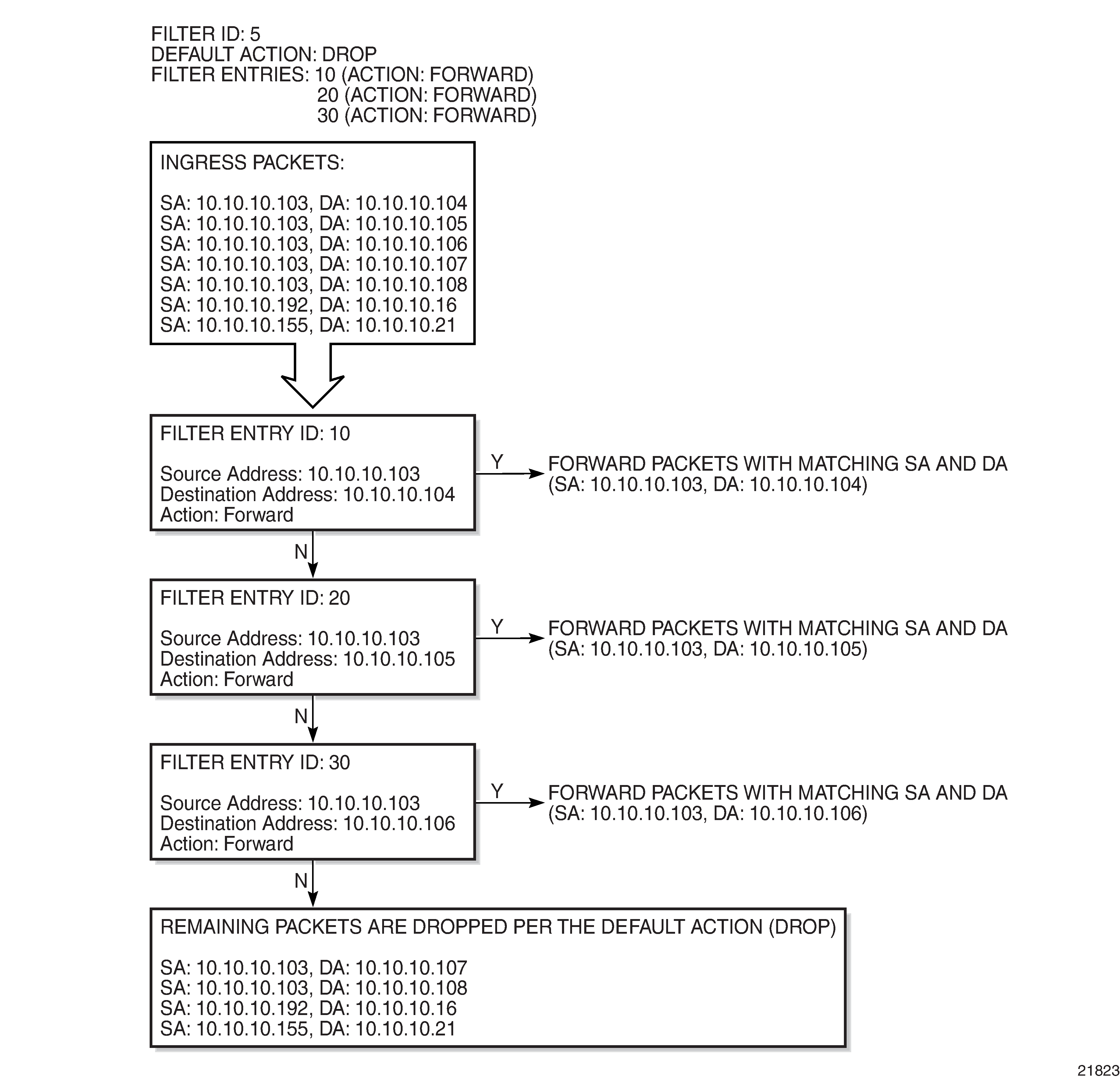
Filtering Process Example displays an example of several packets forwarded upon matching the filter criteria and several packets traversing through the filter entries and then dropped.
Policy-based Forwarding Over VPLS
The 7705 SAR supports policy-based forwarding over VPLS. PBF enables users to allow ingress traffic but change the regular forwarding that a packet would be subject to. PBF applies to unicast traffic and to broadcast, multicast, and unknown unicast (BMU) traffic. The following PBF actions are supported:
-
SAP
This action forwards incoming traffic onto the specified VPLS SAP and is supported for ingress IPv4/IPv6 and MAC filter policies deployed in the VPLS service. The SAP that the traffic is to egress on must be in the same VPLS service as the incoming interface. If the configured SAP is down, traffic is forwarded according to the forwarding database (FDB).
-
SDP
This action forwards incoming traffic onto the specified VPLS SDP and is supported for ingress IPv4/IPv6 and MAC filter policies deployed in the VPLS service. The SDP that the traffic is to egress on must be in the same VPLS service as the incoming interface. If the configured SDP is down, traffic is forwarded according to the FDB.
Additionally, users can select a default action for a filter policy. The default action is executed on packets if the packets to not match the filter entries. By default, filter policies have a default action set to drop the packet but users can select a default action to forward instead.
PBF Behavior
- If VPLS is attached to an IP interface, the following scenarios apply:
- For traffic destined for r-VPLS interfaces where the Layer 2 destination address of the packets matches the r-VPLS MAC address, Layer 3 forwarding is used and the PBF filter is bypassed.
- If the destination address does not match the r-VPLS MAC address, Layer 2 forwarding to a particular endpoint SAP or SDP and PBF is used (or traffic is flooded if the destination address is not yet known); that is, PBF is performed.
- If the PBF filter entry matches BMU traffic, PBF is performed.
- For mesh SDPs, PBF can be used to direct a packet from the mesh SDP source or ingress to the mesh SDP destination or egress.
- If the filter entry forward destination is an SDP in an endpoint group (spoke-SDP redundancy) and the SDP is inactive, traffic is forwarded according to the FDB.
- Filter statistics:
- The following are scenarios where filter entry statistics are
incremented but the packets may be discarded or forwarded to a different
destination:
- the PBF destination address is down – in this case, the packets are forwarded according to the FDB
- pseudowire redundancy where the PBF destination is the inactive SDP – in this case, packets are forwarded according to the FDB. This is essentially the same action as when the PBF destination address is down.
- packets are forwarded to an r-VPLS interface – when packets cross to the Layer 3 boundary, Layer 2 destinations are no longer available and IP routing is used to forward the packets.
In these cases, the PBF destination status and PBF down behavior are shown in the CLI as part of the filter entry statistics display. This information can be used to assess if the traffic is going to the PBF destination.
- If the packets are dropped before forwarding due to reasons such as source address suppression, mesh SDP-to-mesh SDP forwarding, or unknown destination MAC address discards, the filter statistics only show that there was a match. To see how the packets are ultimately forwarded or dropped, the user can check the SAP or spoke SDP forwarding or discard statistics.
- The following are scenarios where filter entry statistics are
incremented but the packets may be discarded or forwarded to a different
destination:
Filter Log Files
Filter entries can be configured to be written to a filter log file. The log file must exist before any entries can be logged. To create a log file, use the config>filter>log log-id create command. Filter logs can be sent to either memory or an existing syslog server. See Filter Logs for more information.
The 7705 SAR supports filter logging for the following filters:
ingress spoke SDP IPv4, IPv6, or MAC filters (VPLS only)
ingress mesh SDP IPv4, IPv6, or MAC filters (VPLS only)
ingress spoke SDP IPv4 or IPv6 filters (VPRN)
The 7705 SAR does not support filter logging for VLAN filters.
See the 7705 SAR System Management Guide, ‟Syslog”, for information about syslogs.
Configuration Notes
The following information describes the conditions for filter policy implementation.
Creating a filter policy is optional.
Using a filter policy is optional.
A filter policy must be created before it can be applied to a service.
When a filter policy is configured, it must be defined as having either an exclusive scope (for use with one interface), or a template scope (meaning that the filter can be applied to multiple interfaces). VLAN filter policies always have a template scope.
A specific filter must be explicitly associated with a specific interface in order for packets to be matched.
Each filter policy must consist of at least one filter entry. Each entry represents a collection of filter match criteria. When packets enter an ingress port or SAP or SDP, or exit an egress SAP, the packets are compared to the criteria specified within the entry or entries.
When you configure a large (complex) filter, it may take a few seconds to load the filter policy configuration.
The action keyword must be entered for the entry to be active. Any filter entry without the action keyword is considered incomplete and will be inactive.
See the following sections for specific notes on:
IP Filters
Define filter entry packet matching criteria — if a filter policy is created with an entry and an entry action specified, but the packet matching criteria is not defined, then all packets processed through this filter policy entry pass and take the action specified. There are no default parameters defined for matching criteria.
Action — an action keyword must be specified for the entry to be active. Any filter entry without an action keyword specified is considered incomplete and be inactive.
IPv6 Filters
IPv6 packets with extension headers can be filtered with an IPv6 filter, but are subject to some restrictions:
if the packet contains the Hop-by-Hop Options header, slow path extraction occurs and the packet is processed by the CSM's CPM filter (if present); however, the main (fast path) IPv6 filter (service or network filter) filters packets with the Hop-by-Hop Options header
if the authentication header is present in the packet and the target fields for the filter are offset by the presence of the authentication header, the filter does not detect the target header fields and no filter action occurs
No alarms, logs, or statistics are reported in the above cases.
MAC Filters
If a MAC filter policy is created with an entry and entry action specified but the packet matching criteria is not defined, then all packets processed through this filter policy entry pass and take the action specified. There are no default parameters defined for matching criteria.
MAC filters cannot be applied to network interfaces, routable VPRN or IES services.
Some of the MAC match criteria fields are exclusive to each other, based on the type of Ethernet frame. Use MAC Match Criteria Exclusivity Rules to determine the exclusivity of fields.
Table 7. MAC Match Criteria Exclusivity Rules Frame Format
Ethertype
Ethernet – II
Yes
802.3
No
802.3 – snap
No
VLAN Filters
-
VLAN filters are applied to physical ring ports on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. VLAN filters are exclusive to the ring adapter card and module.
-
Only one VLAN filter is allowed per ingress ring port.
-
The same VLAN filter can be applied to both ring ports.
-
The forwarding action sends packets to the other ring port or to the v-port, depending on the packet’s destination.
-
The 7705 SAR does not support filter logging or statistics collection for VLAN filters.
Filter Logs
Summarization logging is the collection and summarization of log messages for one specific log ID within a period of time.
The summarization interval is 100 s.
The filter log can be applied to IP filters, MAC filters, or CPM filters.
For VPLS scenarios, both Layer 2 and Layer 3 are applicable.
Layer 2: source MAC or (optionally) destination MAC
Layer 3: source IPv6 or (optionally) destination IPv6 for Layer 3 filters
Upon activation of a fixed summarization interval, a mini-table with source/destination address and count is created for each filter type (IP, MAC, or CPM).
Every received log packet is examined for the source or destination address.
If the log packet (source/destination address) matches a source/destination address entry in the mini-table (meaning that a packet was received previously), the summary counter of the matching address is incremented.
Configuring Filter Policies with CLI
This section provides information to configure and manage filter policies using the command line interface.
Topics in this section include:
Basic Configuration
The most basic IPv4, IPv6, MAC, and VLAN filter policy must have the following:
a filter ID
scope, either exclusive or template (VLAN filter policies always have a template scope)
default action (drop or forward)
at least one filter entry
specified action, either drop or forward
specified matching criteria
The most basic IP exception filter policy must have the following:
an exception filter policy ID
scope, either exclusive or template
at least one filter entry with a specified matching criteria
Common Configuration Tasks
This section provides a brief overview of the tasks that must be performed for IP filter configuration and provides the CLI commands.
Creating an IPv4 or IPv6 Filter Policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
the filter type specified (IP)
a filter policy ID
a default action (drop or forward)
scope specified, either exclusive or template
at least one filter entry with matching criteria specified
IP Filter Policy
Use the following CLI syntax to create a template IPv4 or IPv6 filter policy:
- CLI Syntax:
config>filter# ip-filter filter-id [create]description description-stringscope {exclusive | template}default-action {drop | forward}
- Example:
config>filter# ip-filter12createconfig>filter# description "IP-filter"config>filter$ scopetemplate
- CLI Syntax:
config>filter# ipv6-filter ipv6-filter-id[create]description description-stringscope {exclusive | template}default-action {drop | forward}
- Example:
config>filter# ipv6-filter10createconfig>filter# description "ipv6-filter"config>filter# scopetemplate
The following example displays a template filter policy configuration.
A:ALU-7>config>filter# info
----------------------------------------------
...
ip-filter 12 create
description "IP-filter"
scope template
exit
...
----------------------------------------------
A:ALU-7>config>filter#
Use the following CLI syntax to create an exclusive IPv4 or IPv6 filter policy:
- CLI Syntax:
config>filter# ip-filter filter-iddescription description-stringscope {exclusive | template}default-action {drop | forward}
- Example:
config>filter# ip-filter11createconfig>filter# description "filter-main"config>filter# scopeexclusive
- CLI Syntax:
config>filter# ipv6-filter ipv6-filter-iddescription description-stringscope {exclusive | template}default-action {drop | forward}
- Example:
config>filter# ipv6-filter9createconfig>filter# description "ipv6-filter-main"config>filter# scopeexclusive
The following example displays an exclusive filter policy configuration.
A:ALU-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
exit
...
----------------------------------------------
A:ALU-7>config>filter#
IP Filter Entry
Within a filter policy, configure filter entries that contain criteria against which ingress, egress, and network traffic is matched. The action specified in the entry determines how the packets are handled, either dropped or forwarded.
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria (see IP Filter Entry Matching Criteria).
The forward next-hop command is used to implement policy-based routing. For details, see Policy-Based Routing. Use the indirect keyword to identify the indirect next-hop router to which packets with matching criteria will be forwarded. The forward fc command is used to implement multi-field classification. For details, see Multi-field Classification (MFC).
Use the following CLI syntax to create an IP filter entry:
- CLI Syntax:
config>filter# ip-filter {filter-id | filter-name}entry entry-iddescription description-stringaction [drop]action forward [next-hop {ip-address | indirect ip-address}] [fc fc-name [priority low | high]]
- Example:
config>filter# ip-filter 11config>filter>ip-filter# entry10createconfig>filter>ip-filter>entry$ description "no-91"config>filter>ip-filter>entry$ action dropconfig>filter>ip-filter>entry# exit
- CLI Syntax:
config>filter# ip-filter {filter-id | filter-name}entry entry-iddescription description-stringaction {drop | forward}]
- Example:
config>filter# ipv6-filter 9config>filter>ipv6-filter# entry10createconfig>filter>ipv6-filter>entry$ description "no-91"config>filter>ipv6-filter>entry$ action dropconfig>filter>ipv6-filter>entry# exit
The following example displays an IP filter entry configuration.
A:ALU-7>config>filter>ip-filter# info
----------------------------------------------
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
action drop
exit
exit
----------------------------------------------
IP Filter Entry Matching Criteria
Use the following CLI syntax to configure IPv4 filter matching criteria:
- CLI Syntax:
config>filter>ip-filter>entry#matchdscp dscp-namedst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}dst-port {{lt | gt | eq} dst-port-number} | {range start end}fragment {true | false}icmp-code icmp-codeicmp-type icmp-typeip-option ip-option-value [ip-option-mask]multiple-option {true | false}option-present {true | false}src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}src-port {{lt | gt | eq} src-port-number} | {range start end}tcp-ack {true | false}tcp-syn {true | false}
- Example:
config>filter>ip-filter>entry# matchconfig>filter>ip-filter>entry>match# src-ip 10.10.10.10/8config>filter>ip-filter>entry>match#dst-ip 10.10.10.91/8config>filter>ip-filter>entry>match# exit
The following example displays a matching configuration.
A:ALU-7>config>filter>ip-filter# info
----------------------------------------------
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/8
src-ip 10.10.10.10/8
exit
action forward
exit
----------------------------------------------
A:ALU-7>config>filter>ip-filter#
Use the following CLI syntax to configure IPv6 filter matching criteria:
- CLI Syntax:
config>filter>ipv6-filter>entry#matchdscp dscp-namedst-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}dst-port {{lt | gt | eq} dst-port-number} | {range start end}icmp-code icmp-codeicmp-type icmp-typesrc-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}src-port {{lt | gt | eq} src-port-number} | {range start end}tcp-ack {true | false}tcp-syn {true | false}
- Example:
config>filter>ipv6-filter>entry# matchconfig>filter>ipv6-filter>entry>match#src-ip2001:db8:a0b:12f0::1/128config>filter>ipv6-filter>entry>match#dst-ip2001:db8:a0b:12f0::2/128config>filter>ipv6-filter>entry>match# exit
The following example displays a matching configuration.
A:ALU-7>config>filter>ipv6-filter# info
----------------------------------------------
description "ipv6-filter-main"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 2001:db8:a0b:12f0::2/128
src-ip 2001:db8:a0b:12f0::1/128
exit
action forward exit
IP Filter Entry for PBR to a System IP or Loopback Address
A PBR rule can be set up to extract packets from the data path and send them to the CSM for debugging or slow path forwarding, by having the next-hop point to a system IP or loopback interface of the 7705 SAR.
The extracted traffic can be rerouted to a final destination based on a RIB lookup on the CSM. The traffic is reinjected to the datapath based on the next-hop address.
PBR CSM Extraction Queue Parameters summarizes the queuing parameters for this functionality. These parameters are for slow path queues created for PBR and are not user-configurable.
Parameter |
Maximum Value |
|---|---|
PIR |
1500 kb/s |
CIR |
100 kb/s |
MBS |
20 (non-buffer-chained adapter cards) 80 (buffer-chained adapter cards) |
CBS |
8 buffers |
The following syntax shows an example of extracting and reinjecting packets to a system IP address. An example for a loopback address would be similar.
- CLI Syntax:
config>filter# ip-filter {filter-id | filter-name}entry entry-idaction forward [next-hop {ip-address | indirect ip-address}] [fc fc-name [priority low | high]]matchdscp dscp-name
- Example:
config>filter# ip-filter 12config>filter>ip-filter# entry112createconfig>filter>ip-filter>entry$ action forward next-hop indirect 10.10.10.10config>filter>ip-filter>entry# matchconfig>filter>ip-filter>entry>match# dscp beconfig>filter>ip-filter>entry>match# exit
A:ALU-7>config>filter>ip-filter# info
----------------------------------------------
scope exclusive
entry 12 create
match
dscp be
exit
action forward next-hop indirect 10.10.10.10
exit
----------------------------------------------
A:ALU-7>config>filter>ip-filter#
Creating a MAC Filter Policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
the filter type specified (MAC)
a filter policy ID
a default action, either drop or forward
filter policy scope, either exclusive or template
at least one filter entry
matching criteria specified
MAC Filter Policy
Use the following CLI syntax to configure a MAC filter with exclusive scope:
- CLI Syntax:
config>filter>mac-filter filter-id [create]description description-stringscope {exclusive | template}default-action {drop | forward}
- Example:
config>filter>mac-filter 90 createconfig>filter>mac-filter# description filter-westconfig>filter>mac-filter# scope exclusiveconfig>filter>mac-filter# default-action drop
The following example displays an exclusive scope configuration.
A:ALU-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "filter-west"
scope exclusive
default-action drop
exit
----------------------------------------------
A:ALU-7>config>filter#
MAC Filter Entry
Within a filter policy, configure filter entries that contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determines how the packets are handled, either dropped or forwarded.
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria (see MAC Entry Matching Criteria).
Use the following CLI syntax to configure a MAC filter entry:
- CLI Syntax:
config>filter>mac-filter {filter-id | filter-name}entry entry-id [create]description description-stringaction [drop]action forwardexit
- Example:
config>filter>mac-filter 90config>filter>mac-filter# entry 1 createconfig>filter>mac-filter>entry# description ‟allow-104”config>filter>mac-filter>entry# action dropconfig>filter>mac-filter>entry# exit
The following example displays a MAC filter entry configuration.
A:sim1>config>filter# info
----------------------------------------------
mac-filter 90 create
entry 1 create
description "allow-104"
match
exit
action drop
exit
exit
----------------------------------------------
A:sim1>config>filter#
MAC Entry Matching Criteria
Use the following CLI syntax to configure a MAC filter entry with matching criteria:
- CLI Syntax:
config>filter>mac-filter {filter-id | filter-name}entry entry-idmatch [frame-type {802dot3 | 802dot2-llc | 802dot2-snap | ethernet_II}]src-mac ieee-addressdst-mac ieee-addressetype 0x0600..0xffff
- Example:
config>filter>mac-filter 90config>filter>mac-filter# entry 1config>filter>mac-filter>entry# match frame-type802dot3config>filter>mac-filter>entry>match# src-mac00:dc:98:1d:00:00config>filter>mac-filter>entry>match# dst-mac02:dc:98:1d:00:01config>filter>mac-filter>entry>match# etype 0x8100
The following example displays a filter matching configuration.
A;ALU-7>config>filter# info
----------------------------------------------
description "filter-west"
scope exclusive
entry 1 create
description "allow-104"
match
src-mac 00:dc:98:1d:00:00
dst-mac 02:dc:98:1d:00:01
etype 0x8100
exit
action drop
exit
----------------------------------------------
A:ALU-7>config>filter#
Creating a VLAN Filter Policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
the filter type specified (VLAN)
a filter policy ID
a default action, either drop or forward
at least one filter entry
specified matching criteria (see VLAN Entry Matching Criteria)
VLAN Filter Policy
Use the following CLI syntax to configure a VLAN filter policy:
- CLI Syntax:
config>filter>vlan-filter filter-id [create]description description-stringdefault-action {drop | forward}
- Example:
config>filter>vlan-filter 2 createconfig>filter>vlan-filter# description VLAN_filter_2config>filter>vlan-filter# default-action drop
The following example displays a VLAN filter configuration.
A:ALU-7>config>filter# info
----------------------------------------------
...
vlan-filter 2 create
description "VLAN_filter_2"
default-action drop
exit
----------------------------------------------
A:ALU-7>config>filter#
VLAN Filter Entry
Within a VLAN filter policy, configure filter entries that contain criteria against which ingress traffic on a ring port is matched. The action specified in the entry determines how the packets are handled, either dropped or forwarded. Forwarded packets are sent to the other ring port or the v-port, depending on the destination.
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria (see VLAN Entry Matching Criteria).
Use the following CLI syntax to configure a VLAN filter entry:
- CLI Syntax:
config>filter>vlan-filter {filter-id | filter-name}entry entry-id [create]description description-stringaction {drop | forward}exit
- Example:
config>filter>vlan-filter 2config>filter>vlan-filter# entry 2 createconfig>filter>vlan-filter>entry# description ‟drop-104”config>filter>vlan-filter>entry# action dropconfig>filter>vlan-filter>entry# exit
The following example displays a VLAN filter entry configuration.
A:sim1>config>filter# info
----------------------------------------------
vlan-filter 2 create
entry 2 create
description "drop-104"
match
action drop
exit
exit
exit
----------------------------------------------
A:sim1>config>filter#
VLAN Entry Matching Criteria
Use the following CLI syntax to configure a VLAN filter entry with matching criteria:
- CLI Syntax:
config>filter>vlan-filter {filter-id | filter-name}entry entry-idmatch vlan {lt|gt|eq} vlan-idmatch vlan range vlan-id to vlan-idmatch untagged
- Example:
config>filter>vlan-filter 2config>filter>vlan-filter# entry 2config>filter>vlan-filter# description drop_104config>filter>vlan-filter>entry# match vlan eq 104
The following example displays a filter matching configuration.
A;ALU-7>config>filter# info
----------------------------------------------
description "drop-104"
entry 2 create
description "drop-104"
match vlan eq 104
action drop
exit
exit
----------------------------------------------
A:ALU-7>config>filter#
Creating a Bypass Policy for a Firewall in a Layer 2 Service
Configuring and applying bypass filter policies is optional. The bypass policy must be given an ID or a name that must be unique within the system. If given a name, the system automatically assigns the first available ID number to the policy.
Use the following CLI syntax to configure a bypass policy.
- CLI Syntax:
config>security>bypass bypass-id | name [create]entry entry-id [create]match [protocol protocol-id]dst-port {lt | gt | eq} dst-port-numberdst-port range dst-port-number dst-port-numbersrc-port {lt | gt | eq} src-port-numbersrc-port range src-port-number src-port-number
- Example:
config>security>bypass 5 createconfig>security>bypass# description ‟Sample Bypass Filter”config>security>bypass# entry 1 createconfig>security>bypass>entry# description ‟Sample Entry”config>security>bypass>entry# match protocol ‟pim”config>security>bypass>entry# exit
The following example displays a bypass filter configuration.
----------------------------------------------
*A:Sar8 Dut-A>conf>security>bypass# info
----------------------------------------------
name "5"
description "Sample Bypass Filter"
entry 1 create
description ‟Sample Entry”
match protocol 103
exit
----------------------------------------------
*A:Sar8 Dut-A>conf>security>bypass#
Creating an IP Exception Filter Policy
Configuring and applying IP exception filter policies is optional. Each exception filter policy must have the following:
an exception filter policy ID
scope specified, either exclusive or template
at least one filter entry with matching criteria specified
IP Exception Filter Policy
Use the following CLI syntax to create an IP exception filter policy:
- CLI Syntax:
config>filter# ip-exception filter-id[create]description description-stringscope {exclusive | template}
- Example:
config>filter# ip-exception1createconfig>filter>ip-except# description "IP-exception"config>filter>ip-except# scopetemplate
The following example displays a template IP exception filter policy configuration.
A:ALU-7>config>filter# info
----------------------------------------------
...
ip-exception 1 create
description "IP-exception"
scope template
exit
...
----------------------------------------------
A:ALU-7>config>filter#
IP Exception Entry Matching Criteria
Within an exception filter policy, configure exception entries that contain criteria against which ingress, egress, and network traffic is matched. Packets that match the entry criteria are allowed to transit the NGE domain in clear text.
Enter an exception filter entry ID. The system does not dynamically assign a value.
Specify matching criteria.
Use the following CLI syntax to configure IP exception filter matching criteria:
- CLI Syntax:
config>filter# ip-exception filter-identry entry-id [create]description description-stringmatchdst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}dst-port {lt | gt | eq} dst-port-numberdst-port range dst-port-number dst-port-numbericmp-code icmp-codeicmp-type icmp-typesrc-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}src-port {lt | gt | eq} src-port-numbersrc-port range src-port-number src-port-number
- Example:
config>filter>ip-except# entry 1createconfig>filter>ip-except>entry# matchconfig>filter>ip-except>entry>match# src-ip 10.10.10.10/8config>filter>ip-except>entry>match#dst-ip 10.10.10.91/8config>filter>ip-except>entry>match# exit
The following example displays a matching configuration.
A:ALU-7>config>filter>ip-exception# info
----------------------------------------------
description "exception-main"
scope exclusive
entry 1
match
dst-ip 10.10.10.91/8
src-ip 10.10.10.10/8
exit
exit
----------------------------------------------
A:ALU-7>config>filter>ip-except#
Configuring Filter Log Policies
Use the following CLI syntax to configure filter log policy:
- CLI Syntax:
config>filter# log log-iddescription description-stringdestination memory num-entriesdestination syslog syslog-idsummaryno shutdownsummary-crit dst-addrsummary-crit src-addrwrap-around
The following example displays a filter log configuration.
A:ALU-48>config>filter>log# info detail
---------------------------------------------
description "Test filter log."
destination memory 1000
wrap-around
no shutdown
---------------------------------------------
A:ALU-48>config>filter>log#
Configuring a NAT Security Profile
To configure NAT, you must first:
configure a NAT security profile and policy in the config>security context
in the config>security>profile context, specify the timeouts for the tcp/udp/icmp protocols. This step is optional. If you do not configure the profile, a default profile is assigned.
in the config>security>policy context, configure a NAT security policy, and specify the match criteria and the action to be applied to a packet if a match is found
then configure a NAT zone and apply the policy ID to the zone
To configure a NAT security profile, you must create the profile ID. Once created, the profile ID is referenced when you set up a NAT policy.
- CLI Syntax:
config>security# profile profile-id [create]description description-stringname profile-nametimeoutsicmp-request minutes secondstcp-established days hours minutes secondstcp-syn days hours minutes secondstcp-time-wait minutes secondstcp-transitory days hours minutes secondsudp days hours minutes secondsudp-dns days hours minutes secondsudp-initial minutes seconds
The following example displays a profile configuration.
- Example:
config>security# beginconfig>security# session-high-wmark 90config>security# session-low-wmark 70config>security# profile 2 createconfig>security>profile# name "default"config>security>profile# description "session timer check"config>security>profile# timeoutsconfig>security>profile>timeouts# icmp-request sec 59config>security>profile>timeouts# tcp-time-wait min 1config>security>profile>timeouts# exitconfig>security>profile# exitconfig>security# commit
The following output displays a modified NAT profile.
A:ALU-7>config>security# info
----------------------------------------------
..
session-high-wmark 90
session-low-wmark 70
profile 2 create
name "default"
description "For session timer check"
timeouts
exit
exit
..
----------------------------------------------
A:ALU-7>config>security#
Configuring a NAT Security Policy
To configure NAT, you must first:
configure a NAT security profile and policy in the config>security context
in the config>security>profile context, specify the timeouts for the tcp/udp/icmp protocols. This step is optional. If you do not configure the profile, a default profile is assigned.
in the config>security>policy context, configure a NAT security policy, and specify the match criteria and the action to be applied to a packet if a match is found
then configure a NAT zone and apply the policy ID to the zone
To configure a NAT policy, you must create the policy ID.
- CLI Syntax:
config>security# policy policy-id [create]description description-stringentry entry-id [create]description description-stringmatch [local] protocol protocol-iddirection {zone-outbound | zone-inbound | both}dst-ip ip-address to ip-addressdst-port {lt | gt | eq} port range start endicmp-code icmp-codeicmp-type icmp-typesrc-ip ip-address to ip-addresssrc-port {lt | gt | eq} port range start endaction {forward | reject | nat}action nat [destination ip-address port tcp-udp-port]limitconcurrent-sessions numberprofile profile-id | profile-namename policy-name
For the action nat command, destination ip-address and port tcp-udp-port parameters apply only to static destination NAT (port forwarding).
The following example displays a policy configuration for source NAT.
- Example:
config>security# beginconfig>security# policy 1 createconfig>security>policy# name "inbound policy"config>security>policy# description "common egress policy"config>security# entry 1 createconfig>security>policy>entry# description "Source NAT"config>security>policy>entry# matchconfig>security>policy>entry>match# direction zone-inboundconfig>security>policy>entry>match# exitconfig>security>policy>entry># limitconfig>security>policy>entry># exitconfig>security>policy>entry># action natconfig>security>policy>entry># profile 2config>security>policy>entry># exitconfig>security>policy># exitconfig>security># commit
The following example displays a policy configuration for static destination NAT.
- Example:
config>security# beginconfig>security# policy 1 createconfig>security# entry 2 createconfig>security>policy>entry# description "Dest NAT"config>security>policy>entry# match local protocol udpconfig>security>policy>entry>match# dst-port eq 4000config>security>policy>entry>match# exitconfig>security>policy>entry># limitconfig>security>policy>entry># exitconfig>security>policy>entry># action nat destination 198.51.100.1 port 4000config>security>policy>entry># profile 2config>security>policy>entry># exitconfig>security>policy># exitconfig>security># commit
The following output displays a modified NAT policy output.
A:ALU-7>config>security# info
----------------------------------------------
..
policy 1 create
name "inbound policy"
description "common egress policy"
entry 1 create
description "Source NAT"
match
direction zone-inbound
exit
limit
action nat
profile 2
exit
entry 2 create
description "Dest NAT"
match local protocol udp
dst-port eq 4000
exit
limit
action nat destination 198.51.100.1 port 4000
profile 2
exit
commit
..
----------------------------------------------
A:ALU-7>config>security#
Applying IP and MAC Filter Policies to a Service
Filter policies must be created before they can be applied to a service. Create filter policies in the config>filter context.
The following CLI syntaxes show how to apply filter policies to services. Use the first CLI syntax to apply an IP or MAC filter policy to a VPLS SAP, mesh SDP, or spoke SDP. Use the second CLI syntax for Epipe or Ipipe services. Use the third CLI syntax for VPRN or IES interface SAPs and spoke SDPs. (For IES SAPs, IPv6 ingress and egress filters can also be applied.)
- CLI Syntax:
config>service# vpls service-idsap sap-idegressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idfilter mac mac-filter-idingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idfilter mac mac-filter-idmesh-sdp sdp-id:vc-id [vc-type {ether | vlan}]ingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idspoke-sdp sdp-id:vc-id [vc-type {ether | vlan}]ingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-id
- CLI Syntax:
config>service# epipe service-idsap sap-idingressfilter ip ip-filter-id
- CLI Syntax:
config>service# vprn service-idinterface ip-int-namesap sap-idegressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idspoke-sdp sdp-id:vc-idingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-id
The following example is for VPLS. A VPRN example includes the interface command (config>service>vprn>interface).
- Example:
config>service# vpls 5000config>service>vpls# sap 1/5/5config>service>vpls>sap# ingress filter mac 92config>service>vpls>sap# egress filter ip 10config>service>vpls>sap# exitconfig>service>vpls# mesh-sdp 15:5000config>service>vpls>mesh-sdp# ingress filter mac 93config>service>vpls>mesh-sdp# exitconfig>service>vpls# spoke-sdp 15:5001config>service>vpls>spoke-sdp# ingress filter mac 94config>service>vpls>spoke-sdp# exit
The following example displays an IP and MAC filter assignment for a VPLS service configuration:
A:ALU-48>config>service>vpls# info
----------------------------------------------
...
sap 1/5/5 create
ingress
filter mac 92
exit
egress
filter ip 10
exit
exit
mesh-sdp 15:5000 create
ingress
filter mac 93
exit
exit
spoke-sdp 15:5001 create
ingress
filter mac 94
exit
exit
no shutdown
...
----------------------------------------------
A:ALU-48>config>service>vpls#
Applying IP Filter Policies to Network Interfaces
IP filter policies can be applied to ingress and egress network IP interfaces.
IPv4 filters are supported on all ingress and egress network interfaces. IPv6 filters are supported on all Ethernet ingress and egress network interfaces (with null or dot1q encapsulation) and on ingress and egress interfaces on the 4-port OC3/STM1 Clear Channel Adapter card (with POS encapsulation).
Filter policies must be created before they can be applied to a network interface. Create filter policies in the config>filter context.
- CLI Syntax:
config>router# interface ip-int-nameegressfilter ip ip-filter-idfilter ipv6 ipv6-filter-idingressfilter ip ip-filter-idfilter ipv6 ipv6-filter-id
- Example:
config>router# interface to-104config>router>if#ingressconfig>router>if>ingress#filter ip 10config>router>if# exit
A:ALU-48>config>router# info
#------------------------------------------
# IP Configuration
#------------------------------------------
...
interface "to-104"
address 10.10.10.0/8
port 1/1/1
ingress
filter ip 10
exit
exit
...
#------------------------------------------
A:ALU-48>config>router#
Applying VLAN Filter Policies to a Ring Port
VLAN filter policies can be applied to a ring port on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. The filter operates on ingress traffic. Filter policies must be created before they can be applied. Create filter policies in the config>filter context.
- CLI Syntax:
config>port>ethernet# vlan-filter filter-id
- Example:
config>port>ethernet# vlan-filter 2
A:ALU-48>config>port>ethernet# info
#------------------------------------------
...
vlan-filter 2
...
#------------------------------------------
A:ALU-48>config>port>ethernet#
Creating a Match List for Filter Policies
IP filter policies support the use of match lists as a single match criterion. To create a match list, you must:
-
specify the type of match list (for example, an IPv4 address prefix list)
-
define a unique match list name (for example, ‟IPv4PrefixDenylist”)
-
specify at least one valid IPv4 or IPv6 address prefix
Optionally, a description can also be defined.
The following example shows an IPv4 address prefix list configuration and its use in an IPv4 filter policy:
*A:ala-48>config>filter# info
----------------------------------------------
match-list
ip-prefix-list "IPv4PrefixDenylist"
description "default IPv4 prefix denylist"
prefix 10.0.0.0/21
prefix 10.254.0.0/24
exit
exit
ip-filter 10
scope template
filter-name "IPv4PrefixDenylistFilter"
entry 10
match
src-ip ip-prefix-list IPv4PrefixDenylist
exit
action drop
exit
exit
---------------------------------------------
Filter Management Tasks
This section discusses the following filter policy management tasks:
Renumbering Filter Policy Entries
The 7705 SAR exits the matching process when the first match is found and then executes the actions in accordance with the specified action. Because the ordering of entries is important, the numbering sequence can be rearranged. Entries should be numbered from the most explicit to the least explicit.
Use the following CLI syntax to resequence existing IP, MAC, and VLAN filter entries:
- CLI Syntax:
config>filterip-filter {filter-id | filter-name}renum old-entry-idnew-entry-id
- Example:
config>filter>ip-filter# renum 10 15config>filter>ip-filter# renum 30 40config>filter>ip-filter# renum 40 1
- CLI Syntax:
config>filteripv6-filter {ipv6-filter-id | filter-name}renum old-entry-idnew-entry-id
- Example:
config>filter>ipv6-filter# renum 10 15config>filter>ipv6-filter# renum 30 40config>filter>ipv6-filter# renum 40 1
- CLI Syntax:
config>filtermac-filter {filter-id | filter-name}renum old-entry-idnew-entry-id
- Example:
config>filter>mac-filter# renum 10 15config>filter>mac-filter# renum 30 40config>filter>mac-filter# renum 40 1
- CLI Syntax:
config>filtervlan-filter {filter-id | filter-name}renum old-entry-idnew-entry-id
- Example:
config>filter>vlan-filter# renum 10 15config>filter>vlan-filter# renum 30 40config>filter>vlan-filter# renum 40 1
The following output displays the original IPv4 filter entry order followed by the reordered filter entries:
A:ALU-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/8
src-ip 10.10.10.10/8
exit
action forward
exit
entry 30 create
match
dst-ip 10.10.10.91/8
src-ip 10.10.0.100/8
exit
action drop
exit
entry 35 create
match
dst-ip 10.10.10.91/8
src-ip 10.10.0.200/8
exit
action forward
exit
entry 40 create
match
dst-ip 10.10.10.0/8
src-ip 10.10.10.106/8
exit
action drop
exit
exit
...
----------------------------------------------
A:ALU-7>config>filter#
A:ALU-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.0/8
src-ip 10.10.10.106/8
exit
action drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/8
src-ip 10.10.0.10/8
exit
action forward
exit
entry 35 create
match
dst-ip 10.10.10.91/8
src-ip 10.10.10.200/8
exit
action forward
exit
entry 40 create
match
dst-ip 10.10.10.91/8
src-ip 10.10.0.100/8
exit
action drop
exit
exit
...
----------------------------------------------
A:ALU-7>config>filter#
Modifying an IP Filter Policy
To access a specific IPv4 or IPv6 filter, you must specify the filter ID or the filter name (if a filter name is configured). Use the no form of the command to remove the command parameters or return the parameter to the default setting.
- Example:
config>filter>ip-filter# description "New IP filter info"config>filter>ip-filter# entry 2 createconfig>filter>ip-filter>entry# description "new entry"config>filter>ip-filter>entry# action dropconfig>filter>ip-filter>entry# match dst-ip10.10.10.104/32config>filter>ip-filter>entry# exitconfig>filter>ip-filter#config>filter>ipv6-filter# description "IPv6 filter info"config>filter>ipv6-filter# entry 3 createconfig>filter>ipv6-filter>entry# description "new entry"config>filter>ipv6-filter>entry# action dropconfig>filter>ipv6-filter>entry# match dst-ip10::12/128config>filter>ipv6-filter>entry# exitconfig>filter>ipv6-filter#
The following output displays a modified IPv4 filter output.
A:ALU-7>config>filter# info
----------------------------------------------
..
ip-filter 11 create
description "New IP filter info"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.0/8
src-ip 10.10.10.106/8
exit
action drop
exit
entry 2 create
description "new entry"
match
dst-ip 10.10.10.104/8
exit
action drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/8
src-ip 10.10.10.10/8
exit
action forward
exit
entry 35 create
match
dst-ip 10.10.10.91/8
src-ip 10.10.0.200/8
exit
action forward
exit
exit
..
----------------------------------------------
A:ALU-7>config>filter#
Modifying a MAC Filter Policy
To access a specific MAC filter, you must specify the filter ID or the filter name (if a filter name is configured). Use the no form of the command to remove the command parameters or return the parameter to the default setting. The example below changes the action to forward.
- Example:
config>filter# mac-filter 90config>filter>mac-filter# description "Mac_filter90"config>filter>mac-filter# entry 1config>filter>mac-filter>entry# description "Mac_entry90_1"config>filter>mac-filter>entry# action forwardconfig>filter>mac-filter>entry# exit
The following output displays the modified MAC filter output:
A:ALU-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "Mac_filter90"
scope exclusive
entry 1 create
description "Mac_entry90_1"
match
src-mac 00:dc:98:1d:00:00
dst-mac 02:dc:98:1d:00:01
exit
action forward
exit
exit
...
----------------------------------------------
A:ALU-7>config>filter#
Modifying a VLAN Filter Policy
To access a specific VLAN filter, you must specify the filter ID or the filter name (if a filter name is configured). Use the no form of the command to remove the command parameters or return the parameter to the default setting. The example below adds entry 65535.
- Example:
config>filter# vlan-filter 2config>filter>vlan-filter# entry 65535 createconfig>filter>vlan-filter>entry# description "entry_65535"config>filter>vlan-filter>entry# action forwardconfig>filter>vlan-filter>entry# match vlan range 2000 to 3000config>filter>vlan-filter>entry# exit
The following output displays the modified VLAN filter output:
*A:7705custDoc:Sar18>config>filter>vlan-filter# info
----------------------------------------------
description "VLAN_filter_2"
entry 2 create
description "vlan_fltr_entry2"
action forward
match vlan eq 104
exit
entry 65535 create
description "entry_65535"
action forward
match vlan range 2000 to 3000
exit
----------------------------------------------
*A:7705custDoc:Sar18>config>filter>vlan-filter#
Removing and Deleting a Filter Policy
Before you can delete a filter, you must remove the filter association from the applied ingress and egress SAPs, ingress SDPs, and ingress network interfaces.
You can remove a filter policy and then delete it from the following entities:
Removing a Filter from a Service
To remove an IP or MAC filter from a VPLS SAP or VPLS SDP (spoke or mesh), use the first CLI syntax (below). For a VPRN or IES interface SAP or spoke SDP, use the second CLI syntax:
- CLI Syntax:
config>service# vpls service-idsap sap-idegressno filter ip ip-filter-idno filter ipv6 ipv6-filter-idingressno filter [ip ip-filter-id | ipv6 ipv6-filter-id | mac mac-filter-id]spoke-sdp sdp-id:vc-idingressno filter [ip ip-filter-id | ipv6 ipv6-filter-id | mac mac-filter-id]mesh-sdp sdp-id:vc-idingressno filter [ip ip-filter-id | ipv6 ipv6-filter-id | mac mac-filter-id]
- CLI Syntax:
config>service# vprn service-idinterface ip-int-namesap sap-idegressno filter [ip ip-filter-id | ipv6 ipv6-filter-id ]ingressno filter [ip ip-filter-id | ipv6 ipv6-filter-id ]spoke-sdp sdp-id:vc-idingressno filter [ip ip-filter-id | ipv6 ipv6-filter-id ]
The following example is for VPLS. A VPRN example includes the interface command (config>service>vprn>interface).
- Example:
config>service# vpls 5000config>service>vpls# sap 1/1/2config>service>vpls>sap# ingressconfig>service>vpls>sap>ingress# no filter ip 232config>service>vpls>sap>ingress# exitconfig>service>vpls>sap# exitconfig>service>vpls>spoke-sdp 15:5001config>service>vpls>spoke-sdp# ingressconfig>service>vpls>spoke-sdp>ingress# no filter mac 55config>service>vpls>spoke-sdp>ingress# exitconfig>service>vpls>spoke-sdp# exitconfig>service>vpls>mesh-sdp 15:5000config>service>vpls>mesh-sdp# ingressconfig>service>vpls>mesh-sdp>ingress# no filter mac 54
Removing a Filter from a Network Interface
To remove an IPv4 or IPv6 filter from a network interface, enter the following CLI commands:
- CLI Syntax:
config>router# interface ip-int-nameegressno filter [ip ip-filter-id]no filter [ipv6 ipv6-filter-id]ingressno filter [ip ip-filter-id]no filter [ipv6 ipv6-filter-id]
- Example:
config>router# interface b11config>router>if# egressconfig>filter>if>egress# no filter ip 12config>router>if>egress# exitconfig>filter>if># ingressconfig>filter>if>ingress# no filter ip 2config>filter>if>ingress# exit
Removing a Filter from a Ring Port
To remove a VLAN filter from a ring port, enter the following CLI command. Including filter-id is optional because only one filter can be applied to a port.
- CLI Syntax:
config>port>ethernet# no vlan-filter [filter-id]
- Example:
config>port>ethernet# no vlan-filter 2
Deleting a Filter
After you have removed the filter from all the network interfaces, SAPs, and SDPs (spoke and/or mesh) where it was applied, use the following CLI syntax to delete the filter:
- CLI Syntax:
config>filter# no ip-filter {filter-id | filter-name}config>filter# no ipv6-filter {ipv6-filter-id | filter-name}config>filter# no mac-filter {filter-id | filter-name}config>filter# no vlan-filter {filter-id | filter-name}
- Example:
config>filter# no ip-filter 2config>filter# no mac-filter 55
Filter Command Reference
Command Hierarchies
Configuration Commands
IP Filter Log Configuration Commands
config
- filter
- log log-id [create]
- no log log-id
- description description-string
- no description
- destination memory num-entries
- destination syslog syslog-id
- no destination
- [no] shutdown
- summary
- [no] shutdown
- summary-crit dst-addr
- summary-crit src-addr
- no summary-crit
- [no] wrap-around
IP Filter Policy Configuration Commands
config
- filter
- ip-filter filter-id [create]
- ip-filter {filter-id | filter-name}
- no ip-filter filter-id
- default-action {drop | forward}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- action [drop]
- action forward
- action forward fc fc-name [priority priority]
- action forward next-hop ip-address
- action forward next-hop ip-address fc fc-name [priority priority]
- action forward next-hop indirect ip-address
- action forward next-hop indirect ip-address fc fc-name[priority priority]
- action forward sap sap-id
- action forward sdp sdp-id:vc-id
- no action
- description description-string
- no description
- log log-id
- no log
- match [protocol protocol-id]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no dst-ip
- dst-port {lt | gt | eq} dst-port-number
- dst-port range dst-port-number dst-port-number
- no dst-port
- fragment {true | false}
- no fragment
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- ip-option ip-option-value [ip-option-mask]
- no ip-option
- multiple-option {true | false}
- no multiple-option
- option-present {true | false}
- no option-present
- src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no src-ip
- src-port {lt | gt | eq} src-port-number
- src-port range src-port-number src-port-number
- no src-port
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
IPv6 Filter Policy Configuration Commands
config
- filter
- ipv6-filter ipv6-filter-id [create]
- ipv6-filter {filter-id | filter-name}
- no ipv6-filter ipv6-filter-id
- default-action {drop | forward}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- action [drop]
- action forward [sap sap-id] | [sdp sdp-id:vc-id]
- no action
- description description-string
- no description
- log log-id
- no log
- match [next-header next-header]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}
- no dst-ip
- dst-port {lt | gt | eq} dst-port-number
- dst-port range dst-port-number dst-port-number
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- src-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}
- no src-ip
- src-port {lt | gt | eq} src-port-number
- src-port range src-port-number src-port-number
- no src-port
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
MAC Filter Policy Commands
config
- filter
- mac-filter filter-id [create]
- mac-filter {filter-id | filter-name}
- no mac-filter filter-id
- default-action {drop | forward}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- action [drop]
- action forward [sap sap-id] | [sdp sdp-id:vc-id]
- no action
- description description-string
- no description
- log log-id
- no log
- match frame-type {802dot3 | 802dot2-llc | 802dot2-snap | ethernet_II}
- no match
- dst-mac ieee-address
- no dst-mac
- etype 0x0600..0xffff
- no etype
- src-mac ieee-address
- no src-mac
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
VLAN Filter Policy Commands
config
- filter
- vlan-filter filter-id [create]
- vlan-filter {filter-id | filter-name}
- no vlan-filter filter-id
- default-action {drop | forward}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- action {drop | forward}
- no action
- description description-string
- no description
- match vlan {lt | gt | eq} vlan-id
- match vlan range vlan-id to vlan-id
- match untagged
- no match
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
IP Exception Filter Policy Configuration Commands
config
- filter
- ip-exception filter-id [create]
- [no] ip-exception {filter-id | filter-name}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- description description-string
- no description
- match [protocol protocol-id]
- no match
- dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no dst-ip
- dst-port {lt | gt | eq} dst-port-number
- dst-port range dst-port-number dst-port-number
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no src-ip
- src-port {lt | gt | eq} src-port-number
- src-port range src-port-number src-port-number
- no src-port
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
Security Policy Commands
config
- security
- abort
- app-group {group-id | name} [create]
- no app-group {group-id | name}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- match [protocol protocol-id]
- no match
- dst-port {lt | gt | eq} port
- dst-port range start end
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- src-port {lt | gt | eq} port
- src-port range start end
- no src-port
- name name
- no name
- begin
- bypass {bypass-id | name} [create]
- no bypass {bypass-id | name}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- description description-string
- no description
- match [protocol protocol-id]
- no match
- dst-port {lt | gt | eq} dst-port-number
- dst-port range dst-port-number dst-port-number
- no dst-port
- src-port {lt | gt | eq} src-port-number
- src-port range src-port-number src-port-number
- no src-port
- name name
- no name
- commit
- host-group {group-id | name} [create]
- no host-group {group-id | name}
- description description-string
- no description
- host ip-address [to ip-address]
- no host
- name name
- no name
- logging
- log-id {log-id | log-name} [create]
- no log-id {log-id | log-name}
- description description-string
- no description
- destination {memory [size] | syslog syslog-id}
- no destination
- name name
- no name
- profile {logging-profile-id | logging-profile-name}
- [no] shutdown
- [no] wrap-around
- profile {profile-id | profile-name} [create]
- no profile {profile-id | profile-name}
- description description-string
- no description
- event-control event-type [event event] {suppress | throttle | off}
- name name
- no name
- policer-group {group-id | name} [create]
- no policer-group {group-id | name}
- description description-string
- no description
- name name
- no name
- rate rate cbs size [bytes | kilobytes]
- no rate
- policy {policy-id | policy-name} [create]
- no policy {policy-id | policy-name}
- description description-string
- no description
- entry entry-id [create]
- no entry entry-id
- action {forward | reject | drop | nat}
- action nat [destination ip-address port tcp-udp-port]
- description description-string
- no description
- [no] limit
- concurrent-sessions number
- no concurrent-sessions
- [no] fwd-direction-only
- logging {to log-id {log-id | name} | suppressed | to zone}
- no logging
- match [local] [protocol protocol-id ]
- match [app-group {group-id | name}]
- no match
- direction {zone-outbound | zone-inbound | both}
- dst-ip ip-address to ip-address
- dst-ip host-group {group-id | name}
- no dst-ip
- dst-port {lt | gt | eq} port
- dst-port range start end
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- src-ip ip-address to ip-address
- src-ip host-group {group-id | name}
- no src-ip
- src-port {lt | gt | eq} port
- src-port range start end
- no src-port
- profile {profile-id | profile-name}
- no profile
- name policy-name
- no name
- profile {profile-id | profile-name} [create]
- no profile {profile-id | profile-name}
- application
- alg {auto | ftp | tftp}
- no alg
- [no] assurance
- dns
- [no] reply-only
- icmp
- [no] limit-type3
- request-limit packets
- no request-limit
- ip
- options {permit ip-option-mask | permit-any}
- options ip-option-name [ip-option-name]
- tcp
- [no] strict
- description description-string
- no description
- fwd-policer-group {group-id | name}
- no fwd-policer-group
- [no] name profile-name
- rev-policer-group {group-id | name}
- no rev-policer-group
- [no] timeouts
- icmp-request [min minutes] [sec seconds] [strict | idle]
- no icmp-request
- other-sessions [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
- no other-sessions
- tcp-established [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
- no tcp-established
- tcp-syn [days days] [hrs hours] [min minutes] [sec seconds]
- no tcp-syn
- tcp-time-wait [min minutes] [sec seconds]
- no tcp-time-wait
- tcp-transitory [days days] [hrs hours] [min minutes] [sec seconds]
- no tcp-transitory
- udp [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
- no udp
- udp-dns [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
- no udp-dns
- udp-initial[ min minutes] [sec seconds]
- no udp-initial
- session-high-wmark percentage
- no session-high-wmark
- session-low-wmark percentage
- no session-low-wmark
Filter Match List Commands
config
- filter
- match-list
- ip-prefix-list ip-prefix-list-name [create]
- no ip-prefix-list ip-prefix-list-name
- description description-string
- no description
- [no] prefix ip-prefix/prefix-length
- [no] prefix-exclude ip-prefix/prefix-length
- ipv6-prefix-list ipv6-prefix-list-name [create]
- no ipv6-prefix-list ipv6-prefix-list-name
- description description-string
- no description
- [no] prefix ipv6-prefix/prefix-length
- [no] prefix-exclude ipv6-prefix/prefix-length
Show Commands
show
- filter
- ip
- ip ip-filter-id [detail]
- ip ip-filter-id [associations | counters]
- ip ip-filter-id entry entry-id counters
- ip-exception
- ip-exception ip-filter-id
- ip-exception ip-filter-id [associations | counters]
- ip-exception ip-filter-id entry entry-id counters
- ipv6
- ipv6 ipv6-filter-id [detail]
- ipv6 ipv6-filter-id [associations | counters]
- ipv6 ipv6-filter-id entry entry-id counters
- log [bindings]
- log log-id [match string]
- mac {mac-filter-id [entry entry-id] [association | counters]}
- match-list
- ip-prefix-list [prefix-list-name]
- ip-prefix-list prefix-list-name references
- ipv6-prefix-list [prefix-list-name]
- ipv6-prefix-list prefix-list-name references
- vlan [filter-id [entry entry-id]]
show
- security
- app-group [group-id | name] [entry entry-id] [detail]
- capture [format {decode | raw}]
- control-summary
- engine
- host-group
- log [log-id | name]
- log events [type event-type]
- log profile {log-profile-id | name} [type event-type]
- log profiles
- policer-group [group-id | name] [statistics]
- policing-summary [group-id | name] [statistics]
- policy [policy-id | name] [detail | association]
- policy [policy-id | name] [entry entry-id] [detail | association]
- profile [profile-id | name] [detail | association]
- session-summary [service service-id] [router router-instance]
- summary
- zone [service service-id ] [router router-instance]
- zone [zone-id | name] [detail | interface | statistics]
- nat pool [pool-id | name] [detail]
- policy [entry entry-id] [detail | statistics]
- session [inbound | outbound] [forward | nat]
- session session-id [detail | statistics]}
Clear Commands
clear
- filter
- ip ip-filter-id [entry entry-id] [ingress | egress]
- ipv6 ipv6-filter-id [entry entry-id] [ingress | egress]
- log log-id
- mac mac-filter-id [entry entry-id] [ingress | egress]
- security
- session session-id statistics
- zone [zone-id | name] statistics
- zone [zone-id | name] sessions [inbound | outbound | all]
- zone [zone-id | name] statistics
Monitor Commands
Command Descriptions
Configuration Commands
Generic Commands
description
Syntax
description description-string
no description
Context
config>filter>ip-exception
config>filter>ip-exception>entry
config>filter>ip-filter
config>filter>log
config>filter>ip-filter>entry
config>filter>ipv6-filter
config>filter>ipv6-filter>entry
config>filter>mac-filter
config>filter>mac-filter>entry
config>filter>match-list>ip-prefix-list
config>filter>match-list>ipv6-prefix-list
config>filter>vlan-filter
config>filter>vlan-filter>entry
config>security>app-group
config>security>bypass
config>security>bypass>entry
config>security>host-group
config>security>logging>log
config>security>logging>profile
config>security>policer-group
config>security>policy
config>security>policy>entry
config>security>profile
Description
This command creates a text description for a configuration context to help identify the content in the configuration file.
The no form of the command removes any description string from the context.
Default
n/a
Parameters
- description-string
the description character string. Allowed values are any string up to 80 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>filter>log
config>filter>log>summary
Description
The shutdown command administratively disables the entity. The operational state of the entity is disabled as well as the operational state of any entities contained within. When disabled, an entity does not change, reset, or remove any configuration settings or statistics. Many objects must be shut down before they may be deleted. Many entities must be explicitly enabled using the no shutdown command.
Unlike other commands and parameters where the default state is not indicated in the configuration file, shutdown and no shutdown are always indicated in system-generated configuration files.
The no form of the command puts an entity into the administratively enabled state.
Default
no shutdown
Filter Log Commands
log
Syntax
log log-id [create]
no log log-id
Context
config>filter
Description
This command enables the context to create a filter log policy.
The no form of the command deletes the filter log ID. The log cannot be deleted if there are filter entries configured to write to the log. All filter entry logging associations need to be removed before the log can be deleted.
Default
log 101
Special Cases
- Filter log 101
filter log 101 is the default log and is automatically created by the system. Filter log 101 is always a memory filter log and cannot be changed to a syslog filter log. The log size defaults to 1000 entries. The number of entries and wraparound behavior can be edited.
Parameters
- log-id
the filter log ID destination expressed as a decimal integer
destination
Syntax
destination memory num-entries
destination syslog syslog-id
no destination
Context
config>filter>log
Description
This command configures the destination for filter log entries for the specified filter log ID.
Filter logs can be sent to either memory or an existing syslog server. If the filter log destination is memory, the maximum number of entries in the log must be specified.
The no form of the command deletes the filter log association.
Default
no destination
Parameters
- num-entries
specifies that the destination of the filter log ID is a memory log. The num-entries value is the maximum number of entries in the filter log expressed as a decimal integer.
- syslog-id
specifies that the destination of the filter log ID is a syslog server. The syslog-id parameter is the identifier of the syslog server.
summary
Syntax
summary
Context
config>filter>log
Description
This command enables the context to configure log summarization. These settings apply only if syslog is the log destination.
summary-crit
Syntax
summary-crit dst-addr
summary-crit src-addr
no summary-crit
Context
config>filter>log>summary
Description
This command defines the key of the index of the mini-table. If key information is changed while summary is in the no shutdown state, the filter summary mini-table is flushed and reconfigured with different key information. Log packets received during the reconfiguration time will be handled as if summary was not active.
The no form of the command reverts to the default parameter.
Default
dst-addr
Parameters
- dst-addr
specifies that received log packets are summarized based on the destination IP address
- src-addr
specifies that received log packets are summarized based on the source IP address
wrap-around
Syntax
[no] wrap-around
Context
config>filter>log
Description
This command configures a memory filter log to store log entries until full or to store the most recent log entries (circular buffer).
Specifying wrap-around configures the memory filter log to store the most recent filter log entries (circular buffer). When the log is full, the oldest filter log entries are overwritten with new entries.
The no form of the command configures the memory filter log to accept filter log entries until full. When the memory filter log is full, filter logging for the log filter ID ceases.
Default
wrap-around
Filter Policy Commands
ip-exception
Syntax
ip-exception filter-id [create]
[no] ip-exception {filter-id | filter-name}
Context
config>filter
Description
This command creates a configuration context for an IPv4 exception filter policy. After creating an exception filter ID, you can optionally assign it to a unique name with the filter-name command. The exception filter name can be used instead of the ID for exception configuration commands, show commands, monitor commands, clear commands, and port and interface association commands.
IP exception filter policies specify matching criteria that allow a packet to be an exception to where it is applied. For more information, see the ip-exception command in Router Interface Commands.
The IP exception filter policy is a template that can be applied to multiple router interface group encryption contexts as long as the scope of the policy is configured as template.
Any changes made to the existing policy, using any subcommands, are applied immediately to all network interfaces where the policy is applied.
The no form of the command deletes the IP exception filter policy. An exception filter policy cannot be deleted until it is removed from all network interfaces where it is applied.
Parameters
- filter-id
the IP exception filter policy ID number
- filter-name
the IP exception filter policy name, up to 64 characters in length. The name must already exist within the created IP exceptions.
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
ip-filter
Syntax
ip-filter filter-id [create]
ip-filter {filter-id | filter-name}
no ip-filter {filter-id | filter-name}
Context
config>filter
Description
This command creates a configuration context for an IPv4 filter policy. After creating a filter, you can optionally assign it a unique filter name with the filter-name command. The filter name can be used instead of the filter ID to refer to a filter for filter configuration commands, show commands, monitor commands, clear commands, and port association commands.
Filter IDs and filter names support CLI auto-completion. For more information, see the 7705 SAR Basic System Configuration Guide, ‟Entering CLI Commands”.
IP filter policies specify either a forward or a drop action for packets based on the specified match criteria.
The IP filter policy, sometimes referred to as an access control list (ACL), is a template that can be applied to multiple network ports as long as the scope of the policy is template.
Any changes made to the existing policy, using any of the subcommands, are applied immediately to all network interfaces where this policy is applied.
The no form of the command deletes the IP filter policy. A filter policy cannot be deleted until it is removed from all network interfaces where it is applied.
Parameters
- filter-id
the IP filter policy ID number
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
- filter-name
the filter name, up to 64 characters in length
ipv6-filter
Syntax
ipv6-filter ipv6-filter-id [create]
ipv6-filter {ipv6-filter-id | filter-name}
no ipv6-filter {ipv6-filter-id | filter-name}
Context
config>filter
Description
This command creates a configuration context for an IPv6 filter policy. After creating a filter, you can optionally assign it a unique filter name with the filter-name command. The filter name can be used instead of the filter ID to refer to a filter for filter configuration commands, show commands, monitor commands, clear commands, and port association commands.
Filter IDs and Filter names support CLI auto-completion. For more information, see the 7705 SAR Basic System Configuration Guide, ‟Entering CLI Commands”.
IP filter policies specify either a forward or a drop action for packets based on the specified match criteria.
The IP filter policy, sometimes referred to as an access control list (ACL), is a template that can be applied to multiple network ports as long as the scope of the policy is template.
Any changes made to the existing policy, using any of the subcommands, are applied immediately to all network interfaces where this policy is applied.
The no form of the command deletes the IP filter policy. A filter policy cannot be deleted until it is removed from all network interfaces where it is applied.
Parameters
- ipv6-filter-id
the IPv6 filter policy ID number
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
- filter-name
the filter name, up to 64 characters in length
mac-filter
Syntax
mac-filter filter-id [create]
mac-filter {filter-id | filter-name}
no mac-filter {filter-id | filter-name}
Context
config>filter
Description
This command enables the context for a MAC filter policy. After creating a filter, you can optionally assign it a unique filter name with the filter-name command. The filter name can be used instead of the filter ID to refer to a filter for filter configuration commands, show commands, monitor commands, clear commands, and port association commands.
Filter IDs and filter names support CLI auto-completion. For more information, see the 7705 SAR Basic System Configuration Guide, ‟Entering CLI Commands”.
The MAC filter policy specifies either a forward or a drop action for packets based on the specified match criteria.
The MAC filter policy, sometimes referred to as an access control list (ACL), is a template that can be applied to multiple services as long as the scope of the policy is template. It can also be used to refine port mirroring so that only the desired MAC addresses are mirrored.
A MAC filter policy can be applied to VPLS ingress and egress SAPs and ingress SDPs. MAC filter policies cannot be applied to a network interface, a VPRN service, or an IES service.
Any changes made to the existing policy, using any of the sub-commands, are applied immediately to all services where this policy is applied.
The no form of the command deletes the MAC filter policy. A filter policy cannot be deleted until it is removed from all SAPs or SDPs where it is applied.
Parameters
- filter-id
the MAC filter policy ID number
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
- filter-name
the filter name, up to 64 characters in length
vlan-filter
Syntax
vlan-filter filter-id [create]
vlan-filter {filter-id | filter-name}
no vlan-filter {filter-id | filter-name}
Context
config>filter
Description
This command enables the context for a VLAN filter policy. After creating a filter, you can optionally assign it a unique filter name with the filter-name command. The filter name can be used instead of the filter ID to refer to a filter for filter configuration commands, show commands, monitor commands, clear commands, and port association commands.
Filter IDs and Filter names support CLI auto-completion. For more information, see the 7705 SAR Basic System Configuration Guide, ‟Entering CLI Commands”.
The VLAN filter policy specifies either a forward or a drop action for packets based on the specified match criteria.
The VLAN filter policy, sometimes referred to as an access control list (ACL), is a template that can be applied to ring ports on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. Each ring port can support one VLAN filter, and the same VLAN filter can be applied to both ring ports. The scope of a VLAN policy is always template.
A VLAN filter policy cannot be applied to any other type of adapter card.
Any changes made to an existing policy, using any of the sub-commands, is applied immediately to all ring ports where this policy is applied.
The no form of the command deletes the VLAN filter policy. A filter policy cannot be deleted until it is removed from all the ring ports where it is applied.
Parameters
- filter-id
the VLAN filter policy ID number
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
- filter-name
the filter name, up to 64 characters in length
default-action
Syntax
default-action {drop | forward}
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
config>filter>vlan-filter
Description
This command specifies the action to be applied to packets when the packets do not match the specified criteria in all of the IP, MAC, or VLAN filter entries of the filter.
Default
drop
Parameters
- drop
specifies that all packets are dropped unless there is a specific filter entry that causes the packet to be forwarded
- forward
specifies that all packets are forwarded unless there is a specific filter entry that causes the packet to be dropped
filter-name
Syntax
filter-name filter-name
no filter-name
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
config>filter>vlan-filter
config>filter>ip-exception
Description
This command creates a unique name to associate with this filter. The filter name can be used instead of the filter ID to refer to a filter for filter configuration commands, show commands, monitor commands, clear commands, and port and interface association commands.
Parameters
- filter-name
the filter name, up to 64 characters in length
renum
Syntax
renum old-entry-id new-entry-id
Context
config>filter>ip-exception
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
config>filter>vlan-filter
Description
This command renumbers existing IP, MAC, VLAN, or IP exception filter entries to properly sequence filter entries.
This may be required in some cases since the software exits when the first match is found and executes the actions according to the accompanying action command. This requires that entries be sequenced correctly from most to least explicit.
Parameters
- old-entry-id
the entry number of an existing entry
- new-entry-id
the new entry number to be assigned to the old entry
scope
Syntax
scope {exclusive | template}
no scope
Context
config>filter>ip-exception
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Description
This command configures the filter policy scope as exclusive or template. If the scope of the policy is template and is applied to one or more network interfaces, the scope cannot be changed.
The no form of the command sets the scope of the policy to the default of template.
Default
template
Parameters
- exclusive
when the scope of a policy is defined as exclusive, the policy can only be applied to a single entity (network port). If an attempt is made to assign the policy to a second entity, an error message results. If the policy is removed from the entity, it becomes available for assignment to another entity.
- template
when the scope of a policy is defined as template, the policy can be applied to multiple network ports
General Filter Entry Commands
entry
Syntax
entry entry-id [create]
no entry entry-id
Context
config>filter>ip-exception
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
config>filter>vlan-filter
Description
This command creates or edits a filter entry. Multiple entries can be created using unique entry-id numbers within the filter. The 7705 SAR implementation exits the filter on the first match found and executes the actions in accordance with the accompanying action command. For this reason, entries must be sequenced correctly, from most to least explicit.
Filter entry IDs support CLI auto-completion. For more information, see the 7705 SAR Basic System Configuration Guide, ‟Entering CLI Commands”.
IPv4 and IPv6 filter entries can specify one or more matching criteria. However, to support the maximum 256 entries for IPv4 or IPv6 filters, any entry that uses source port (src-port) or destination port (dst-port) ranges (lt, gt, or range keywords) as match criteria must be within the first 64 entries. See the dst-port and src-port commands for more information.
For IPv6 filters, the combined number of fields for all entries in a filter must not exceed 16 fields (or 256 bits), where a field contains the bit representation of the matching criteria.
Some adapter cards have limitations on the size of ACLs that can be supported and therefore cannot support the maximum number of IPv6 filter entries. If you attempt to configure more entries than the card can support, the following error log event and SNMP trap are generated:
‟Class MDA Module : runtime event, details: Filter <filter id> ACL_STATUS_IPV6_ FILTER_ENTRIES_EXCEEDED Config Error!”
SNMPv2-MIB:snmpTrapOID.0 : (1.3.6.1.4.1.6527.6.1.2.3.2.1.0.13 (ALU-CHASSIS-MIB:aluEqMdaCriticalRuntimeError)) Syntax: ObjectID ALU-CHASSIS-MIB:aluChassisNotifyMdaRuntimeStatusContext.0 : (runtime event, details: Filter <filter id> ACL_STATUS_IPV6_FILTER_ENTRIES_EXCEEDED Config Error!) Syntax: SNMPv2-TC:DisplayString
where <filter id> is the filter policy ID
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action for it to be considered complete. Entries without the action keyword are considered incomplete and are rendered inactive.
The no form of the command removes the specified entry from the filter. Entries removed from the filter are immediately removed from all entities to which that filter is applied.
Default
n/a
Parameters
- entry-id
an entry-id uniquely identifies a match criteria and the corresponding action. It is recommended that multiple entries be given entry-ids in staggered increments. This allows users to insert a new entry in an existing policy without requiring renumbering of all the existing entries.
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
IP, MAC, VLAN, and IP Exception Filter Entry Commands
action
Syntax
action [drop]
action forward
action forward fc fc-name [priority priority]
action forward next-hop ip-address
action forward next-hop ip-address fc fc-name [priority priority]
action forward next-hop indirect ip-address
action forward next-hop indirect ip-address fc fc-name [priority priority]
action forward sap sap-id
action forward sdp sdp-id:vc-id
no action
Context
config>filter>ip-filter>entry
Description
This command specifies what action to take (drop or forward) when packets match the entry criteria. The action keyword must be entered for the entry to be active. If neither drop nor forward is specified, the filter action is drop.
The action forward next-hop keywords cannot be applied to multicast traffic.
Multiple action statements entered overwrite previous action statements when defined.
The no form of the command removes the specified action statement. The filter entry is considered incomplete and is rendered inactive without the action keyword.
Default
no action
Parameters
- drop
specifies that packets matching the entry criteria are dropped
- forward
specifies that packets matching the entry criteria are forwarded
- next-hop ip-address
specifies the IPv4 address of the direct next hop to which packets matching the entry criteria are forwarded
- indirect ip-address
specifies the IPv4 address of the indirect next hop to which packets matching the entry criteria are forwarded
- fc-name
specifies the forwarding class (FC) to be used for queuing packets through the 7705 SAR. Each FC can be mapped to a different queue, or multiple FCs can be handled by the same queue.
There are eight forwarding classes, providing different classes of service. The forwarding classes are: nc (network control), h1 (high 1), ef (expedited forwarding), h2 (high 2), l1 (low 1), l2 (low 2), af (assured forwarding), be (best effort).
- priority
specifies the priority assigned to incoming traffic. Traffic priority is important for internal processes when some traffic may be dropped because of congestion. Low-priority traffic is dropped first.
- sap-id
-
specifies the VPLS SAP to which packets matching the entry criteria are forwarded
The SAP ID can be configured in one of the formats described in the SAP ID Configurations table under the sap command description in the "VLL Services Command Reference" section of the 7705 SAR Services Guide
- sdp-id:vc-id
-
specifies the VPLS SDP to which packets matching the entry criteria are forwarded
- sdp-id
- uniquely identifies the SDP
- vc-id
- identifies the virtual circuit
action
Syntax
action [drop]
action forward [sap sap-id] | [sdp sdp-id:vc-id]
no action
Context
config>filter>ipv6>entry
Description
This command specifies what action to take (drop or forward) when packets match the entry criteria. The action keyword must be entered and for the entry to be active. If neither drop nor forward is specified, the filter action is drop.
Multiple action statements entered overwrite previous action statements when defined.
The no form of the command removes the specified action statement. The filter entry is considered incomplete and is rendered inactive without the action keyword.
Default
no action
Parameters
- drop
-
specifies that packets matching the entry criteria are dropped
- forward
-
specifies that packets matching the entry criteria are forwarded
- sap-id
-
specifies the VPLS SAP to which packets matching the entry criteria are forwarded
The SAP ID can be configured in one of the formats described in the SAP ID Configurations table under the sap command description in the "VLL Services Command Reference" section of the 7705 SAR Services Guide
- sdp-id:vc-id
-
specifies the VPLS SDP to which packets matching the entry criteria are forwarded
- sdp-id
- uniquely identifies the SDP
- vc-id
- identifies the virtual circuit
action
Syntax
action [drop]
action forward [sap sap-id] | [sdp sdp-id:vc-id]
no action
Context
config>filter>mac-filter>entry
Description
This command specifies what action to take (drop or forward) when packets match the entry criteria. The action keyword must be entered and for the entry to be active. If neither drop nor forward is specified, the filter action is drop.
Multiple action statements entered overwrite previous action statements when defined.
The no form of the command removes the specified action statement. The filter entry is considered incomplete and is rendered inactive without the action keyword.
Default
no action
Parameters
- drop
-
specifies that packets matching the entry criteria are dropped
- forward
-
specifies that packets matching the entry criteria are forwarded
- sap-id
-
specifies the VPLS SAP to which packets matching the entry criteria are forwarded
The SAP ID can be configured in one of the formats described in the SAP ID Configurations table under the sap command description in the "VLL Services Command Reference" section of the 7705 SAR Services Guide
- sdp-id:vc-id
-
specifies the VPLS SDP to which packets matching the entry criteria are forwarded
- sdp-id
- uniquely identifies the SDP
- vc-id
- identifies the virtual circuit
action
Syntax
action {drop | forward}
no action
Context
config>filter>vlan-filter>entry
Description
This command specifies what action to take (drop or forward) when packets match the entry criteria. The action keyword must be entered and for the entry to be active. If neither drop nor forward is specified, the filter action is drop.
Multiple action statements entered overwrite previous action statements when defined.
The no form of the command removes the specified action statement. The filter entry is considered incomplete and is rendered inactive without the action keyword.
Default
drop
Parameters
- drop
specifies that packets matching the entry criteria are dropped
- forward
specifies that packets matching the entry criteria are forwarded
- sap-id
-
specifies the physical port or SCADA bridge identifier portion of the SAP definition
The sap-id can be configured in one of the formats described in the SAP ID Configurations table under the sap command description in the "VLL Services Command Reference" section of the 7705 SAR Services Guide.
- sdp
-
specifies that packet matching the entry are forwarded using the configured SDP
log
Syntax
log log-id
no log
Context
config>filter>ip-filter>entry
config>filter>ipv6-filter>entry
config>filter>mac-filter>entry
Description
This command enables the context to enable filter logging for a filter entry and specifies the destination filter log ID.
The filter log ID must exist before a filter entry can be enabled to use the filter log ID.
The no form of the command disables logging for the filter entry.
Default
no log
Parameters
- log-id
the filter log ID destination expressed as a decimal integer
match
Syntax
match [protocol protocol-id]
no match
Context
config>filter>ip-filter>entry
config>filter>ip-exception>entry
Description
This command enables the context to enter match criteria for the IPv4 or IP exception filter entry. When the match criteria have been satisfied, the action associated with the match criteria is executed.
If more than one match criterion (within one match statement) is configured, all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
This command also optionally specifies the IP protocol to be used as an IP filter match criterion. See the following table for a list of IP protocol numbers and names.
|
Protocol ID |
Protocol |
Description |
|---|---|---|
|
1 |
icmp |
Internet Control Message |
|
2 |
igmp |
Internet Group Management |
|
4 |
ip |
IP in IP (encapsulation) |
|
6 |
tcp |
Transmission Control |
|
8 |
egp |
Exterior Gateway Protocol |
|
9 |
igp |
Any private interior gateway |
|
17 |
udp |
User Datagram |
|
27 |
rdp |
Reliable Data Protocol |
|
41 |
ipv6 |
IPv6 |
|
43 |
ipv6-route |
Routing Header for IPv6 |
|
44 |
ipv6-frag |
Fragment Header for IPv6 |
|
45 |
idrp |
Inter-Domain Routing Protocol |
|
46 |
rsvp |
Reservation Protocol |
|
47 |
gre |
General Routing Encapsulation |
|
58 |
ipv6-icmp |
ICMP for IPv6 |
|
59 |
ipv6-no-nxt |
No Next Header for IPv6 |
|
60 |
ipv6-opts |
Destination Options for IPv6 |
|
80 |
iso-ip |
ISO Internet Protocol |
|
88 |
eigrp |
EIGRP |
|
89 |
ospf-igp |
OSPFIGP |
|
97 |
ether-ip |
Ethernet-within-IP Encapsulation |
|
98 |
encap |
Encapsulation Header |
|
102 |
pnni |
PNNI over IP |
|
103 |
pim |
Protocol Independent Multicast |
|
112 |
vrrp |
Virtual Router Redundancy Protocol |
|
115 |
l2tp |
Layer Two Tunneling Protocol |
|
118 |
stp |
Schedule Transfer Protocol |
|
123 |
ptp |
Performance Transparency Protocol |
|
124 |
isis |
ISIS over IPv4 |
|
126 |
crtp |
Combat Radio Transport Protocol |
|
127 |
crudp |
Combat Radio User Datagram |
|
132 |
sctp |
Stream Control Transmission Protocol |
|
137 |
mpls-in-ip |
MPLS in IP |
The no form of the command removes the match criteria for the entry-id.
Parameters
- protocol-id
protocol-number or protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, representing the IP protocol to be used as a filter match criterion
- protocol-name
configures the protocol name representing the IP protocol to be used as a filter match criterion
match
Syntax
match [next-header next-header]
no match
Context
config>filter>ipv6-filter>entry
Description
This command enables the context to enter match criteria for the IPv6 filter entry. When the match criteria have been satisfied, the action associated with the match criteria is executed.
If more than one match criterion (within one match statement) is configured, all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
This command also optionally specifies the IPv6 next header (protocol number or protocol name) to be used as an IPv6 match criterion. See IP Protocol IDs and Descriptions.
The no form of the command removes the match criteria for the entry-id.
Parameters
- next-header
protocol-number or protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, representing the IP protocol to be used as the IPv6 next header filter match criterion This parameter is similar to the protocol parameter used in IPv4 filter match criteria.
- protocol-name
the protocol name to be used as the IPv6 next header filter match criterion. This parameter is similar to the protocol parameter used in IPv4 filter match criteria.
match
Syntax
match frame-type {802dot3 | 802dot2-llc | 802dot2-snap | ethernet_II}
no match
Context
config>filter>mac-filter>entry
Description
This command enables the context for entering/editing match criteria for the filter entry and specifies an Ethernet frame type for the entry. When the match criteria have been satisfied, the action associated with the match criteria is executed.
If more than one match criterion (within one match statement) is configured, then all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
The no form of the command removes the match criteria for the entry-id.
Default
frame-type 802dot3
Parameters
- frame-type
configures an Ethernet frame type to be used for the MAC filter match criteria
- 802dot3
specifies the frame type as Ethernet IEEE 802.3
- 802dot2-llc
specifies the frame type as Ethernet IEEE 802.2 LLC
- 802dot2-snap
specifies the frame type as Ethernet IEEE 802.2 SNAP
- ethernet_II
specifies the frame type as Ethernet Type II
match
Syntax
match vlan {lt | gt | eq} vlan-id
match vlan range vlan-id to vlan-id
match untagged
no match
Context
config>filter>vlan-filter>entry
Description
This command accesses the match criteria for the filter entry and specifies a match criteria. If the match criteria are satisfied, the action associated with the match criteria is executed.
Only one match criterion (within one match statement) is allowed.
The no form of the command removes the match criteria for the entry-id.
Default
no match
Parameters
- vlan {lt | gt | eq}vlan-id
specifies an operator and a vlan-id to be used for the VLAN filter match criteria (lt for less than, gt for greater than, and eq for equal to)
- vlan range vlan-id to vlan-id
specifies a range of VLAN IDs to be used for the VLAN filter match criteria.
- untagged
specifies that Ethernet frames with no tag or dot1q header (null encapsulation) are used for the VLAN filter match criteria
IP, MAC, and IP Exception Filter Match Criteria Commands
dscp
Syntax
dscp dscp-name
no dscp
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures a DiffServ Code Point (DSCP) name to be used as an IP filter match criterion.
The no form of the command removes the DSCP match criterion.
Default
no dscp
Parameters
- dscp-name
a DSCP name that has been previously mapped to a value using the dscp-name command. The DiffServ Code Point may only be specified by its name.
dst-ip
Syntax
dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
no dst-ip
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
Description
This command configures a destination IPv4 address range or specifies an IP prefix list configured under the match-list ip-prefix-list command to be used as a match criterion for an IP filter or IP exception filter.
To match on the destination IP address, specify the address and its associated mask; for example, 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of the command removes the destination IP address or prefix list match criterion.
Default
n/a
Parameters
- ip-address
the IP prefix for the IP match criterion in dotted-decimal notation
- mask
the subnet mask length expressed as a decimal integer
- ipv4-address-mask
any mask expressed in dotted-decimal notation
- prefix-list-name
the name of the IP prefix list configured under the match-list ip-prefix-list command
dst-ip
Syntax
dst-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}
no dst-ip
Context
config>filter>ipv6-filter>entry>match
Description
This command configures a destination IPv6 address range or specifies an IPv6 prefix list configured under the match-list ipv6-prefix-list command to be used as a match criterion for an IP filter.
To match on the destination IP address, specify the address and prefix length; for example, 11::12/128.
The no form of the command removes the destination IPv6 address or prefix list match criterion.
Default
n/a
Parameters
- ipv6-address
the IPv6 address on the interface
- prefix-length
the prefix length associated with the IPv6 address
- ipv6-address-mask
the IPv6 address mask
- prefix-list-name
the name of the IPv6 prefix list configured with the match-list ipv6-prefix-list command
dst-mac
Syntax
dst-mac ieee-address
no dst-mac
Context
config>filter>mac-filter>entry>match
Description
This command configures a destination MAC address to be used as a MAC filter match criterion.
To match on the destination MAC address, specify the IEEE address.
The no form of the command removes the destination MAC address match criterion.
Default
no dst-mac
Parameters
- ieee-address
the MAC address to be used as a match criterion
dst-port
Syntax
dst-port {lt | gt | eq} dst-port-number
dst-port range dst-port-number dst-port-number
no dst-port
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures a destination TCP or UDP port number or port range for an IP filter or IP exception filter match criterion.
The no form of the command removes the destination port match criterion.
Default
n/a
Parameters
- lt | gt | eq
use relative to dst-port-number for specifying the port number match criteria:
lt specifies that all port numbers less than dst-port-number match
gt specifies that all port numbers greater than dst-port-number match
eq specifies that dst-port-number must be an exact match
- dst-port-number
the destination port number to be used as a match criteria expressed as a decimal integer
- range
specifies an inclusive range of port numbers to be used as a match criteria. The first dst-port-number specifies the start of the range, and the second dst-port-number specifies the end of the range.
etype
Syntax
etype 0x600...0xffff
no etype
Context
config>filter>mac-filter>entry>match
Description
This command configures an Ethernet type II Ethertype value to be used as a MAC filter match criterion.
The Ethernet type field is a 2-byte field used to identify the protocol carried by the Ethernet frame. For example, 0800 is used to identify IPv4 packets. The Ethernet type II frame Ethertype value to be used as a match criterion can be expressed as a hexadecimal (0x0600 to 0xFFFF) or a decimal (1536 to 65535) value.
The Ethernet type field is used by the Ethernet version-II frames.
The no form of the command removes the previously entered etype field as the match criteria.
Default
no etype
fragment
Syntax
fragment {true | false}
no fragment
Context
config>filter>ip-filter>entry>match
Description
This command configures fragmented or non-fragmented IP packets as an IP filter match criterion.
The no form of the command removes the match criterion.
This command applies to IPv4 filters only.
Default
false
Parameters
- true
configures a match on all fragmented IP packets. A match occurs for all packets that have either the MF (more fragment) bit set or have the Fragment Offset field of the IP header set to a non-zero value.
- false
configures a match on all non-fragmented IP packets. Non-fragmented IP packets are packets that have the MF bit set to zero and have the Fragment Offset field also set to zero.
icmp-code
Syntax
icmp-code icmp-code
no icmp-code
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures matching on the ICMP code field in the ICMP header of an IPv4 or IPv6 packet as a filter match criterion, or configures matching on the ICMP code field in the ICMP header of an IPv4 packet as an exception filter match criterion.
This command applies only if the protocol match criteria specifies ICMP (1).
The no form of the command removes the criterion from the match entry.
Default
no icmp-code
Parameters
- icmp-code
icmp-code-number or icmp-code-keyword
- icmp-code-number
the ICMP code number in decimal, hexadecimal, or binary, to be used as a match criterion
- icmp-code-keyword
the ICMP code keyword to be used as a match criterion
icmp-type
Syntax
icmp-type icmp-type
no icmp-type
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures matching on the ICMP type field in the ICMP header of an IPv4 or IPv6 packet as a filter match criterion, or configures matching on the ICMP type field in the ICMP header of an IPv4 packet as an exception filter match criterion.
This command applies only if the protocol match criteria specifies ICMP (1).
The no form of the command removes the criterion from the match entry.
Default
no icmp-type
Parameters
- icmp-type
icmp-type-number or icmp-type-keyword
- icmp-type-number
the ICMP type number in decimal, hexadecimal, or binary, to be used as a match criterion
- icmp-type-keyword
the ICMP type to be used as a match criterion
ip-option
Syntax
ip-option ip-option-value [ip-option-mask]
no ip-option
Context
config>filter>ip-filter>entry>match
Description
This command configures matching packets with a specific IP option or a range of IP options in the IP header as an IP filter match criterion.
The option type octet contains three fields:
1 bit copied flag (copy options in all fragments)
2 bits option class
5 bits option number
The no form of the command removes the match criterion.
This command applies to IPv4 filters only.
Default
no ip-option
Parameters
- ip-option-value
the 8-bit option type (can be entered using decimal, hexadecimal, or binary formats). The mask is applied as an AND to the option byte and the result is compared with the option value.
The decimal value entered for the match should be a combined value of the 8-bit option type field and not just the option number. Therefore, to match on IP packets that contain the Router Alert option (option number = 20), enter the option type of 148 (10010100).
- ip-option-mask
specifies a range of option numbers to use as the match criteria
This 8-bit mask can be entered using decimal, hexadecimal, or binary formats (see 8-bit Mask Formats).
Table 10. 8-bit Mask Formats Format Style
Format Syntax
Example
Decimal
DDD
20
Hexadecimal
0x
0x14
Binary
0bBBBBBBBB
0b0010100
multiple-option
Syntax
multiple-option {true | false}
no multiple-option
Context
config>filter>ip-filter>entry>match
Description
This command configures matching packets that contain more than one option field in the IP header as an IP filter match criterion.
The no form of the command removes the checking of the number of option fields in the IP header as a match criterion.
This command applies to IPv4 filters only.
Default
no multiple-option
Parameters
- true
specifies matching on IP packets that contain more than one option field in the header
- false
specifies matching on IP packets that do not contain multiple option fields in the header
option-present
Syntax
option-present {true | false}
no option-present
Context
config>filter>ip-filter>entry>match
Description
This command configures matching packets that contain the option field or have an option field of 0 in the IP header as an IP filter match criterion.
The no form of the command removes the checking of the option field in the IP header as a match criterion.
This command applies to IPv4 filters only.
Parameters
- true
specifies matching on all IP packets that contain the option field in the header. A match occurs for all packets that have the option field present. An option field of 0 is considered as no option present.
- false
specifies matching on IP packets that do not have any option field present in the IP header (an option field of 0)
src-ip
Syntax
src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
no src-ip
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
Description
This command configures a source IPv4 address range or specifies an IP prefix list configured under the match-list ip-prefix-list command to be used as a match criterion for an IP filter or IP exception filter.
To match on the source IP address, specify the address and its associated mask; for example, 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of the command removes the source IP address or prefix list match criterion.
Default
no src-ip
Parameters
- ip-address
the IP prefix for the IP match criterion in dotted-decimal notation
- mask
the subnet mask length expressed as a decimal integer
- ipv4-address-mask
any mask expressed in dotted-decimal notation
- prefix-list-name
the name of the IP prefix list configured with the match-list ip-prefix-list command
src-ip
Syntax
src-ip {ipv6-address/prefix-length | ipv6-address ipv6-address-mask | ipv6-prefix-list prefix-list-name}
no src-ip
Context
config>filter>ipv6-filter>entry>match
Description
This command configures a source IPv6 address range or specifies an IPv6 prefix list configured under the match-list ipv6-prefix-list command to be used as a match criterion for an IP filter.
To match on the source IP address, specify the address and prefix length; for example, 11::12/128.
The no form of the command removes the source IPv6 address or prefix list match criterion.
Default
n/a
Parameters
- ipv6-address
the IPv6 address on the interface
- prefix-length
the prefix length associated with the IPv6 address
- ipv6-address-mask
the IPv6 address mask
- prefix-list-name
the name of the IPv6 prefix list configured with the match-list ipv6-prefix-list command
src-mac
Syntax
src-mac ieee-address
no src-mac
Context
config>filter>mac-filter>entry>match
Description
This command configures a source MAC address to be used as a MAC filter match criterion.
The no form of the command removes the source MAC address as the match criterion.
Default
no src-mac
Parameters
- ieee-address
the 48-bit IEEE MAC address to be used as a match criterion
src-port
Syntax
src-port {lt | gt | eq} src-port-number
src-port range src-port-number src-port-number
no src-port
Context
config>filter>ip-exception>entry>match
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures a source TCP or UDP port number or port range for an IP filter or IP exception filter match criterion.
The no form of the command removes the source port match criterion.
Default
no src-port
Parameters
- lt | gt | eq
use relative to src-port-number for specifying the port number match criteria:
lt specifies that all port numbers less than src-port-number match
gt specifies that all port numbers greater than src-port-number match
eq specifies that src-port-number must be an exact match
- src-port-number
the source port number to be used as a match criteria expressed as a decimal integer
- range
specifies an inclusive range of port numbers to be used as a match criteria. The first src-port-number specifies the start of the range, and the second src-port-number specifies the end of the range.
tcp-ack
Syntax
tcp-ack {true | false}
no tcp-ack
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures matching on the ACK bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion.
The no form of the command removes the criterion from the match entry.
Default
no tcp-ack
Parameters
- true
specifies matching on IP packets that have the ACK bit set in the control bits of the TCP header of an IP packet
- false
specifies matching on IP packets that do not have the ACK bit set in the control bits of the TCP header of the IP packet
tcp-syn
Syntax
tcp-syn {true | false}
no tcp-syn
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Description
This command configures matching on the SYN bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion.
The SYN bit is normally set when the source of the packet wants to initiate a TCP session with the specified destination IP address.
The no form of the command removes the criterion from the match entry.
Default
no tcp-syn
Parameters
- true
specifies matching on IP packets that have the SYN bit set in the control bits of the TCP header
- false
specifies matching on IP packets that do not have the SYN bit set in the control bits of the TCP header
Security Policy Commands
abort
Syntax
abort
Context
config>security
Description
This command discards changes made to a security feature.
Default
n/a
begin
Syntax
begin
Context
config>security
Description
This command enters the mode to create or edit security features.
Default
n/a
commit
Syntax
commit
Context
config>security
Description
This command saves changes made to security features.
Default
n/a
app-group
Syntax
app-group {group-id | name} [create]
no app-group {group-id | name}
Context
config>security
Description
This command enters the context for creating an application group to be used in a security policy.
The no form of the command removes the configured application group.
Default
n/a
Parameters
- group-id
the application group ID, from 1 to 100
- name
the name of the application group, up to 32 characters in length (must start with a letter)
name
Syntax
name name
no name
Context
config>security>app-group
config>security>host-group
config>security>policer-group
Description
This command configures a name for an application group, host group, or policer group.
The no form of the command removes the configured name.
Parameters
- name
the name of the application group, host group, or policer group, up to 32 characters in length (must start with a letter)
bypass
Syntax
bypass {bypass-id | name} [create]
no bypass {bypass-id | name}
Context
config>security
Description
This command creates a bypass policy that allows packets to bypass a firewall in a Layer 2 service security zone based on specified match criteria. The bypass policy must be given an ID or a name that is unique within the system. If given a name, the system automatically assigns the first available ID number to the policy. The bypass name can be used instead of the bypass ID to refer to a bypass policy for firewall configuration commands, show commands, monitor commands, clear commands, and service endpoint association commands. The bypass policy can be associated with a VPLS or Epipe service with the fw-bypass-policy command under the config>service>vpls or config>service>epipe context.
Each bypass policy that is created uses one of the system’s filter entry slots.
The no form of the command deletes the bypass policy.
Default
n/a
Parameters
- bypass-id
the bypass ID number
- name
the name of the bypass policy
- create
keyword required when first creating the bypass policy. When the policy is created, you can enter the context without the create keyword.
entry
Syntax
entry entry-id [create]
no entry entry-id
Context
config>security>bypass
Description
This command configures an entry in a bypass policy.
The no form of this command deletes the entry with the specified ID. When an entry is deleted, all configuration parameters for the entry are also deleted.
Default
n/a
Parameters
- entry-id
the entry ID number
- create
keyword required when first creating the entry. When the entry is created, you can enter the context without the create keyword.
match
Syntax
match [protocol protocol-id]
no match
Context
config>security>bypass>entry
Description
This command defines the protocols that are allowed to bypass a firewall in a Layer 2 service. See IP Protocol IDs and Descriptions.
When processing protocol packets defined in the bypass policy, the 7705 SAR ignores the firewall lookup table, even if there is a more specific matching rule for the firewall. The bypass policy must be created carefully to ensure that it does not cause any security holes on the node.
The no form of the command removes the protocol from the bypass policy.
Default
no protocol
Parameters
- protocol-id
protocol-number | protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, that is allowed to bypass the firewall
- protocol-name
the name of the protocol that is allowed to bypass the firewall
dst-port
Syntax
dst-port {lt | gt | eq} dst-port-number
dst-port range dst-port-number dst-port-number
no dst-port
Context
config>security>bypass>entry>match
Description
This command configures a destination protocol TCP or UDP port number or port range for the bypass policy match criterion.
The no form of the command removes the destination port match criterion.
Default
no dst-port
Parameters
- lt | gt | eq
use relative to dst-port-number for specifying the port number match criterion:
lt specifies that all port numbers less than the dst-port-number match
gt specifies that all port numbers greater than the dst-port-number match
eq specifies that the dst-port-number must be an exact match
- dst-port-number
the destination port number to be used as a match criterion, expressed as a decimal integer
- range
specifies an inclusive range of port numbers to be used as a match criterion. The first dst-port-number specifies the start of the range, and the second dst-port-number specifies the end of the range.
src-port
Syntax
src-port {lt | gt | eq} src-port-number
src-port range src-port-number src-port-number
no src-port
Context
config>security>bypass>entry>match
Description
This command configures a source protocol TCP or UDP port number or port range for the bypass policy match criterion.
The no form of the command removes the source port match criterion.
Default
no src-port
Parameters
- lt | gt | eq
use relative to src-port-number for specifying the port number match criterion:
lt specifies that all port numbers less than the src-port-number number match
gt specifies that all port numbers greater than the src-port-number number match
eq specifies that the src-port-number must be an exact match
- src-port-number
the source port number to be used as a match criterion, expressed as a decimal integer
- range
specifies an inclusive range of port numbers to be used as a match criterion. The first src-port-number specifies the start of the range, and the second src-port-number specifies the end of the range.
name
Syntax
name name
no name
Context
config>security>bypass
Description
This command configures the bypass policy name. The bypass policy name must be unique within the system. If the policy name was already configured with the bypass command, this command renames the policy.
The no form of the command deletes the bypass name.
Default
no name
Parameters
- name
the name of the bypass policy
host-group
Syntax
host-group {group-id | name} [create]
no host-group {group-id | name}
Context
config>security
Description
This command enters the context for creating a host group to be used in a security policy.
The no form of the command removes the configured host group.
Default
n/a
Parameters
- group-id
the host group ID, from 1 to 100
- name
the name of the host group, up to 32 characters in length (must start with a letter)
host
Syntax
host ip-address [to ip-address]
no host
Context
config>security>host-group
Description
This command configures a range of hosts to be used in a host group. Up to 10 entries can be configured for a host group.
Default
n/a
Parameters
- ip-address
the IPv4 address of the host
logging
Syntax
logging
Context
config>security
Description
This command enters the security logging context.
Default
n/a
log-id
Syntax
log-id {log-id | log-name} [create]
no log-id {log-id | log-name}
Context
config>security>logging
Description
This command configures the identifier for the security log. The 7705 SAR supports up to 100 security logs. This log ID can be applied at the zone level or at the rule level, but not to both at the same time.
The no form of the command removes the configured security group.
Default
n/a
Parameters
- log-id
the security log ID, from 1 to 100
- log-name
the name of the security log, up to 32 characters in length (must start with a letter)
destination
Syntax
destination {memory [size] | syslog syslog-id}
no destination
Context
config>security>logging>log
Description
This command configures the destination location of the specified security log.
Default
n/a
Parameters
- memory
specifies that the log destination is the 7705 SAR local memory (compact flash or flash drive)
- size
the number of log events that can be held in memory, up to 1024
- syslog
specifies that the log destination is the system log
- syslog-id
the identifier of the system log, up to 32 characters in length
name
Syntax
name name
no name
Context
config>security>logging>log
Description
This command configures the name of the specified security log.
Default
n/a
Parameters
- name
the name of the security log, up to 32 characters in length
profile
Syntax
profile {logging-profile-id | logging-profile-name}
Context
config>security>logging>log
Description
This command configures the logging profile to which the specified security logs match events.
Default
n/a
Parameters
- logging-profile-id
the logging profile ID for the security log
- logging-profile-name
the logging profile name for the security log, up to 32 characters in length
shutdown
Syntax
[no] shutdown
Context
config>security>logging>log
Description
This command disables logging to the specified security log. Logging is enabled by default.
The no form of this command enables logging to the specified security profile.
Default
no shutdown
wrap-around
Syntax
[no] wrap-around
Context
config>security>logging>log
Description
This command enables log wraparound when the maximum log size has been reached in the log destination location. When wraparound is enabled, the log starts over at 1 and overwrites the existing logs when the log size is at maximum. When wraparound is disabled, the log stops adding entries when the log size is at maximum.
The no form of this command disables log wraparound.
Default
no wrap-around
profile
Syntax
profile {profile-id | profile-name} [create]
no profile {profile-id | profile-name}
Context
config>security>logging
Description
This command configures the security logging profile.
The no form of the command removes the configured profile.
Default
n/a
Parameters
- profile-id
the ID of the profile group, from 1 to 65535
- profile-name
the name of the profile group, up to 32 characters in length
event-control
Syntax
event-control event-type [event event] {suppress | throttle | off}
Context
config>security>logging>profile
Description
This command controls the generation of security log events. A log can be configured to generate all event types and events, or to generate specific event types and events. In addition, for each event type or event, one of three actions can be configured: suppress, throttle, or off. These configurations all become part of the specified logging profile. Event Types and Events Supported on 7705 SAR Firewalls lists the supported event types and events on 7705 SAR firewalls.
Event Type |
Event |
|---|---|
Packet |
TcpInvalidHeader DnsInvalidHeader DnsUnmatchedAnswer IcmpUnmatchedReply TcpInvalidFlagCombination TcpRst PolicyErrorFrag FragDropAction DuplicateFrag LandAttack |
Zone |
NoRuleMatched SessionLimitReached |
Policy |
Matched MatchedNAT ActionReject MaxConcurrentUsesReached FragsNotAccepted TcpSynReqdtoEstablish |
Session |
SessionBegin SessionEnd SessionBeginEnd RuleActionDrop ProhibitedIpOption InvalidIcmpT3 PktLimitReached |
Application |
Summary HandshakeMissing HandshakeCtlInvalid HandshakeDataUnexpected OptError OptBadLen OptTTcpForbidden OptNonStdForbidden OptTStampMissing OptTStampUnexpected TStampTooOld TStampEchoInvalid ScaleUnexpected SeqNumOutside AckNumOutside AckNumNotZero AckNumStale AckUnexpected AckMissing FlagsSynRst SynUnexpected SynMissing FinUnexpected InvCksum ConnReused RstSeqNumUnexpected TTL NotFullHeader FlagsSynFin SplitHandshake |
ALG |
CmdIncomplete DynamicRuleInserted DynamicRuleInsertedPASV CannotInsertDynamicRule CannotInsertDynamicRulePASV BadCmdSyntax BadPortCmdSyntax BadPasvCmdSyntax BadAddrSyntax TftpDynRuleInsertErr TftpDynRuleInserted |
Default
n/a
Parameters
- event-type
the type of event to be controlled for in this logging profile, as shown in Event Types and Events Supported on 7705 SAR Firewalls
- event
the name of the event to be controlled for in this logging profile as shown in Event Types and Events Supported on 7705 SAR Firewalls
- suppress
suppresses the specified event type or event in this logging profile
- throttle
throttles a repeating event type or event when the same event type or event is generated repeatedly within 1 s in this logging profile
- off
allows the event type or event to be logged in this logging profile
name
Syntax
name name
no name
Context
config>security>logging>profile
Description
This command configures a name for this logging profile.
The no form of the command removes the configured name for this logging profile.
Default
n/a
Parameters
- name
the name of the logging profile, up to 32 characters in length
profile
Syntax
profile {profile-id | profile-name} [create]
no profile {profile-id | profile-name}
Context
config>security
Description
This command configures a profile group that provides a context within which you can configure security features such as session idle timeouts and application assurance parameters. Profile 1 is a default profile and cannot be modified.
The no form of the command removes the configured profile group.
Default
1
Parameters
- profile-id
the ID of the profile group, from 1 to 100
- profile-name
the name of the profile group, up to 32 characters in length
application
Syntax
application
Context
config>security>profile
Description
This command enters the application context for firewall configuration.
alg
Syntax
alg {auto | ftp | tftp}
no alg
Context
config>security>profile>app
Description
This command enables application level gateway (ALG) inspection by the firewall.
The no form of the command disables ALG inspection by the firewall.
Default
n/a
Parameters
- auto
specifies that the firewall automatically determines the application traffic that requires inspection
- ftp
specifies that the firewall must inspect FTP application traffic as determined by the port matching criteria in the security policy and apply the FTP ALG to the command traffic. This option should be used when FTP ALG is required on any TCP port being used for FTP.
- tftp
specifies that the firewall must inspect TFTP application traffic as determined by the port matching criteria in the security policy and apply the TFTP ALG to the command traffic. This option should be used when TFTP ALG is required on any UDP port being used for TFTP.
assurance
Syntax
[no] assurance
Context
config>security>profile>app
Description
This command enables the context for configuring application assurance parameters. Enabling application assurance automatically sets the defaults for the parameters as listed in Application Assurance Parameter Default Values.
Parameter |
Default Value |
|---|---|
DNS |
reply-only |
ICMP |
limit-type3 |
IP |
options permit-any |
TCP |
no strict |
The no form of the command disables application assurance on the firewall.
Default
n/a
dns
Syntax
dns
Context
config>security>profile>aa
Description
This command enables the context for configuring DNS inspection parameters on a firewall in the application assurance parameters context.
Default
n/a
reply-only
Syntax
[no] reply-only
Context
config>security>profile>aa>dns
Description
This command limits the number of replies to DNS requests. When enabled, the firewall permits a single reply to each DNS request.
The no form of the command disables the limiting of DNS replies; the firewall permits all replies to each DNS request.
Default
reply-only
icmp
Syntax
icmp
Context
config>security>profile>aa
Description
This command enables the context for configuring ICMP limit parameters on a firewall in the application assurance parameters context.
Default
n/a
limit-type3
Syntax
[no] limit-type3
Context
config>security>profile>aa>icmp
Description
This command limits the number of ICMP type 3 replies through a firewall. When enabled, only 15 ICMP type 3 replies are permitted through the firewall for each ICMP and IP session.
The no form of the command disables the limiting of ICMP type 3 replies through a firewall; all ICMP type 3 replies are permitted through the firewall for each ICMP and IP session.
Default
limit-type3
request-limit
Syntax
request-limit packets
no request-limit
Context
config>security>profile>aa>icmp
Description
This command configures the number of ICMP requests and replies allowed through the firewall for each ICMP session. Any requests or replies that are received beyond the configured limit are discarded until the ICMP session times out.
The no form of the command allows all ICMP requests and replies through the firewall for each ICMP session.
Default
5
Parameters
- packets
the maximum number of ICMP request and reply packets permitted through the firewall for each ICMP session, from 1 to 15
ip
Syntax
ip
Context
config>security>profile>aa
Description
This command enables the context for configuring IP layer inspection on a firewall in the application assurance parameters context.
Default
n/a
options
Syntax
options {permit ip-option-mask | permit-any}
options ip-option-name [ip-option-name]
Context
config>security>profile>aa>ip
Description
This command controls the inspection of IP options in an IP packet header. The IP options can be specified using either the bit mask value or the name.
The permit command only applies when using bit mask values. It allows packets through the firewall when the IP options on those packets match the bit mask value specified in the ip-option-mask parameter. The ip-option-mask is a flat bit representation of the IP Option Number. The IP Option Copy Bit and IP Option Class Bits are omitted from the ip-option-mask. For example, to permit a packet with the router alert option (which uses IP Option Number 20), bit 20 of the ip-option-mask should be set, which configures the ip-option-mask parameter as 0x00100000. To discard all IP packets with IP options, configure the ip-option-mask parameter as 0x0. To permit any option, configure the ip-option-mask parameter as 0xffffffff or use the permit-any command. When permit-any is configured, the 7705 SAR does not examine IP options and allows all packets through the firewall.
Multiple options can be allowed in a single line of configuration by ‟AND”ing the IP option bit mask values. For example, to permit packets with the router alert, EOOL, and NOP options, configure the ip-option-mask parameter as 0x00100003.
When IP options are specified using ip-option-name, the permit command is implied. Multiple options can be specified by listing multiple names.
Supported IP Options lists the names and bit mask values of the supported IP options.
IP Option Number |
IP Option Value |
IP Option Name |
Bit Mask Value |
|---|---|---|---|
0 |
0 |
EOOL – End of Options List |
0x00000001 |
1 |
1 |
NOP – No Operation |
0x00000002 |
2 |
130 |
SEC – Security |
0x00000004 |
3 |
131 |
LSR – Loose Source Route |
0x00000008 |
4 |
68 |
TS – time Stamp |
0x00000010 |
5 |
133 |
E-SEC – Extended Security |
0x00000020 |
6 |
134 |
CIPSO – Commercial Security |
0x00000040 |
7 |
7 |
RR – Record Route |
0x00000080 |
8 |
136 |
SID – Stream ID |
0x00000100 |
9 |
137 |
SSR – Strict Source Route |
0x00000200 |
10 |
10 |
ZSU – Experimental Measurement |
0x00000400 |
11 |
11 |
MTUP – MTU Probe |
0x00000800 |
12 |
12 |
MTUR – MTU Reply |
0x00001000 |
13 |
205 |
FINN – Experimental Flow Control |
0x00002000 |
14 |
142 |
VISA – Experimental Access Control |
0x00004000 |
15 |
15 |
Encode |
0x00008000 |
16 |
144 |
IMITD – IMI Traffic Descriptor |
0x00010000 |
17 |
145 |
EIP – Extended Internet Protocol |
0x00020000 |
18 |
82 |
TR – Traceroute |
0x00040000 |
19 |
147 |
ADDEXT – Address Extension |
0x00080000 |
20 |
148 |
RTRALT – Router Alert |
0x00100000 |
21 |
149 |
SDB – Selective Directed Broadcast |
0x00200000 |
22 |
150 |
unassigned |
0x00400000 |
23 |
151 |
DPS – Dynamic Packet State |
0x00800000 |
24 |
152 |
UMP – Upstream Multicast Packet |
0x01000000 |
25 |
25 |
QS – Quick-Start |
0x02000000 |
30 |
30 |
EXP – RFC3692-style experiment |
0x40000000 |
30 |
94 |
EXP – RFC3692-style experiment |
0x40000000 |
30 |
158 |
EXP – RFC3692-style experiment |
0x40000000 |
30 |
222 |
EXP – RFC3692-style experiment |
0x40000000 |
Default
permit-any
Parameters
- permit
allows packets with the specified IP options through the firewall
- ip-option-mask
the IP options to be matched by the firewall, up to 11 characters (in decimal, hexadecimal, or binary)
- ip-option-name
the IP option name to be matched by the firewall; up to 30 option names can be specified
- permit-any
allows packets with any IP options through the firewall
tcp
Syntax
tcp
Context
config>security>profile>aa
Description
This command enables the context for configuring TCP layer inspection on a firewall in the application assurance parameters context.
Default
n/a
strict
Syntax
[no] strict
Context
config>security>profile>aa>tcp
Description
This command enables strict examination of TCP packets through the firewall. When enabled, the firewall examines the header of each TCP packet for that session to ensure compliance with RFC 793.
The no form of the command disables examination of the TCP header on each TCP packet.
Default
no strict
fwd-policer-group
Syntax
fwd-policer-group {group-id | name}
no fwd-policer-group
Context
config>security>profile
Description
This command configures a forward policer group for a security profile. A TCP/UDP security session is bidirectional. When a security sessions is created from a private domain to a public domain, the session’s forward direction is from the private to the public domain and the session’s reverse direction is from the public to the private domain. A forward-direction policer group acts on traffic that is traversing from the private domain to the public domain.
The no form of the command removes the configured forward policer group.
Parameters
- group-id
the identifier of the forward policer group associated with this security profile, from 1 to 1024
- name
the name of the forward policer group associated with this security profile, up to 32 characters in length (must start with a letter)
name
Syntax
[no] name profile-name
Context
config>security>profile
Description
This command configures a profile group name.
The no form of the command removes the configured profile group name.
Parameters
- profile-name
the name of the profile, up to 32 characters in length (must start with a letter)
rev-policer-group
Syntax
rev-policer-group {group-id | name}
no rev-policer-group
Context
config>security>profile
Description
This command configures a reverse policer group for a security profile. A TCP/UDP security session is bidirectional. When a security sessions is created from a private domain to a public domain, the session’s forward direction is from the private to the public domain and the session’s reverse direction is from the public to the private domain. A reverse-direction policer group acts on traffic that is traversing from the public domain to the private domain.
The no form of the command removes the configured reverse policer group.
Parameters
- group-id
the identifier of the reverse policer group associated with this security profile, from 1 to 1024
- name
the name of the reverse policer group associated with this security profile, up to 32 characters in length (must start with a letter)
timeouts
Syntax
timeouts
Context
config>security>profile
Description
This command configures session idle timeouts for this profile.
icmp-request
Syntax
icmp-request [min minutes] [sec seconds] [strict | idle]
no icmp-request
Context
config>security>profile>timeouts
Description
This command sets the timeout for an ICMP security session. An ICMP session is based on the packet source and destination IP addresses and ICMP identifier. This timer removes the ICMP session if no ICMP packets have been received for the configured time.
The no form of the command removes the timeout set for icmp-request.
Default
60 s
Parameters
- minutes
the timeout in minutes
- seconds
the timeout in seconds
other-sessions
Syntax
other-sessions [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
no other-sessions
Context
config>security>profile>timeouts
Description
This command sets the timeout for protocol sessions other than TCP, UDP, or ICMP. These other protocol sessions are based on a 3-tuple match of source IP address, destination IP address, and protocol, except for SCTP (protocol 132), which uses a 5-tuple match like UDP. If no packets are received after the configured time, the firewall session is discontinued and removed from the 7705 SAR.
The no form of the command removes the timeout set for other-sessions.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
- strict
configures the timer to time out after the last session transition state
- idle
configures the timer to time out when no packets have arrived on the session for the configured period
tcp-established
Syntax
tcp-established [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
no tcp-established
Context
config>security>profile>timeouts
Description
This command sets the timeout for a TCP session in the established state.
The no form of the command removes the timeout set for tcp-established.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
tcp-syn
Syntax
tcp-syn [days days] [hrs hours] [min minutes] [sec seconds]
no tcp-syn
Context
config>security>profile>timeouts
Description
This command configures the timeout applied to a TCP session in the SYN state.
The no form of the command removes the timeout set for tcp-syn.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
tcp-time-wait
Syntax
tcp-time-wait [min minutes] [sec seconds]
no tcp-time-wait
Context
config>security>profile>timeouts
Description
This command configures the timeout applied to a TCP session in a time-wait state.
The no form of the command removes the timeout set for tcp-time-wait.
Default
n/a
Parameters
- minutes
the timeout in minutes
- seconds
the timeout in seconds
tcp-transitory
Syntax
tcp-transitory [days days] [hrs hours] [min minutes] [sec seconds]
no tcp-transitory
Context
config>security>profile>timeouts
Description
This command configures the idle timeout applied to a TCP session in a transitory state.
The no form of the command removes the timeout set for tcp-transitory.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
udp
Syntax
udp [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
no udp
Context
config>security>profile>timeouts
Description
This command configures the UDP mapping timeout.
The no form of the command removes the UDP mapping timeout.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
udp-dns
Syntax
udp-dns [days days] [hrs hours] [min minutes] [sec seconds] [strict | idle]
no udp-dns
Context
config>security>profile>timeouts
Description
This command configures the timeout applied to a UDP session with destination port 53.
The no form of the command removes the udp-dns timeout.
Default
n/a
Parameters
- days
the timeout in days
- hours
the timeout in hours
- minutes
the timeout in minutes
- seconds
the timeout in seconds
udp-initial
Syntax
udp-initial [min minutes] [sec seconds]
no udp-initial
Context
config>security>profile>timeouts
Description
This command configures the timeout applied to a UDP session in its initial state.
The no form of the command removes the udp-initial timeout.
Default
n/a
Parameters
- minutes
the timeout in minutes
- seconds
the timeout in seconds
policer-group
Syntax
policer-group {group-id | name} [create]
no policer-group {group-id | name}
Context
config>security
Description
This command enters the context for creating a policer group to be used in a security profile.
The no form of the command removes the configured policer group.
Parameters
- group-id
the ID of the policer group, from 1 to 1024
- name
the name of the policer group, up to 32 characters in length (must start with a letter)
rate
Syntax
rate rate cbs size [bytes | kilobytes]
no rate
Context
config>security>policer-group
Description
This command sets the policer rate and CBS buffer size for the policer group.
Parameters
- rate
the policer rate, in Mb/s
- size
the CBS buffer size, in bytes
policy
Syntax
policy {policy-id | policy-name} [create]
no policy {policy-id | policy-name}
Context
config>security
Description
This command configures a policy group that provides a context within which you can configure a security policy.
The no form of the command removes the configured policy group.
Default
n/a
Parameters
- policy-id
the ID of the policy group, from 1 to 65535
- policy-name
the name of the policy group, up to 32 characters in length
entry
Syntax
entry entry-id [create]
no entry entry-id
Context
config>security>app-group
config>security>policy
Description
This command configures an entry in a security policy or in an application group.
The no form of this command deletes the entry with the specified ID. When an entry is deleted, all configuration parameters for the entry are also deleted.
Parameters
- entry-id
the entry ID number
action
Syntax
action {forward | reject | drop | nat}
Context
config>security>policy>entry
Description
This command specifies what action to take (forward, reject, drop, or NAT) when packets match the entry criteria. An action must be specified in order for the entry to be active. If no action is specified, the entry is inactive.
The nat and forward actions each cause a 6-tuple lookup (source/destination IP address, source/destination port number, protocol, and source zone).
The drop action configures a firewall session on the datapath with the action to drop packets that match the entry criteria. The drop action should be used when an IP connection is carrying a large amount of traffic and CSM processing resources need to be preserved, because the drop action means that packets will not be extracted to the CSM to be rejected. Drop sessions are unidirectional and can be used as a way of blocking traffic from a source issuing a denial of service (DoS) attack.
Entering multiple action statements overwrites previous action statements.
The no form of the command removes the specified action statement.
Default
no action
Parameters
- reject
specifies that packets matching the entry criteria are rejected on the CSM and no firewall session is created on the datapath
- forward
specifies that packets matching the entry criteria are forwarded and a firewall session is created on the datapath
- drop
specifies that a firewall session is created on the datapath with the action to drop packets that match the entry criteria
- nat
specifies that packets matching the entry criteria have NAT applied to them and a NAT session is created on the datapath
action nat
Syntax
action nat [destination ip-address port tcp-udp-port]
Context
config>security>policy>entry
Description
This command specifies the destination IP address and port to which packets that have NAT applied to them are sent.
NAT actions cause a 6-tuple lookup (source/destination IP address, source/destination port number, protocol, and source zone). If there is a match, NAT is applied and the packet is routed based on the datapath session table.
Entering multiple action statements overwrite previous action statements.
The no form of the command removes the specified action statement. An entry is considered incomplete and is rendered inactive if no action is specified.
Default
no action
Parameters
- ip-address
the static NAT (port forwarding) inside destination IP address to be used for port forwarding. When configured, the original packet destination IP address is overwritten with this IP address. This parameter applies only to static destination NAT (port forwarding).
- tcp-udp-port
the static NAT inside port IP number used for port forwarding. When configured, the original packet destination port number is overwritten with this port number. This parameter applies only to static destination NAT (port forwarding).
limit
Syntax
[no] limit
Context
config>security>policy>entry
Description
This command is used to enter the limit context.
Default
n/a
concurrent-sessions
Syntax
concurrent-sessions number
no concurrent-sessions
Context
config>security>policy>entry>limit
Description
This command specifies the maximum number of concurrent security sessions that can be created for the specified policy.
The no form of the command returns the system to the default.
Default
no concurrent-sessions
Parameters
- number
the number of concurrent sessions that can be programmed for the policy
fwd-direction-only
Syntax
[no] fwd-direction-only
Context
config>security>policy>entry>limit
Description
This command forces a firewall to create a unidirectional session when a packet matches the criteria of the policy entry. In normal operating mode, when a packet matches the criteria and the packet is allowed through, the firewall creates a bidirectional session so that packets traveling in the reverse direction on that session are also allowed through the firewall.
The no form of the command creates a bidirectional firewall session for a matched packet.
Default
no fwd-direction-only
logging
Syntax
logging {to log-id {log-id | name} | suppressed | to zone}
no logging
Context
config>security>policy>entry
Description
This command configures logging control for this security policy entry. Logging can be enabled per entry using the to log-id command, or per zone using the to zone command. Logging is suppressed by default.
Default
suppressed
Parameters
- to log-id
specifies to log events per entry
- log-id
the log ID
- name
the log name, up to 32 characters in length
- suppressed
specifies to suppress all logs generated by the entry
- to zone
specifies to use the zone log settings
match
Syntax
match [protocol protocol-id]
no match
Context
config>security>app-group>entry
Description
This command configures match criteria for an application group entry based on the specified protocol. An application group must be configured with at least one matching protocol before it can be assigned to a security policy. See IP Protocol IDs and Descriptions.
When an application group is applied to NAT, the only protocols supported as match criteria are TCP, UDP, and ICMP.
The no form of the command removes the match criteria for the entry.
Default
no match
Parameters
- protocol-id
protocol-number | protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, to be used as a match criterion.
- protocol-name
the name of a protocol to be used as a match criterion. The 7705 SAR supports the protocols listed below.
match
Syntax
match [local] [protocol protocol-id]
match [app-group {group-id | name}]
no match
Context
config>security>policy>entry
Description
This command configures match criteria for an entry based on the specified protocol or application group. See IP Protocol IDs and Descriptions for a list of protocol IDs.
When a security policy is applied to NAT, the only protocols supported as match criteria are TCP, UDP, ICMP, and *.
The no form of the command removes the match criteria for the entry.
Default
n/a
Parameters
- local
specifies that the destination IP address must be a local interface. The local parameter applies only to static destination NAT (port forwarding).
- protocol-id
protocol-number | protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, to be used as a match criterion
- protocol-name
the name of a protocol to be used as a match criterion. The 7705 SAR supports the protocols listed below.
- group-id
the application group ID, from 1 to 100
- name
the name of the application group, up to 32 characters in length (must start with a letter)
direction
Syntax
direction {zone-outbound | zone-inbound | both}
Context
config>security>policy>entry>match
Description
This command sets the direction of the traffic to be matched against the IP criteria. For example, if zone-inbound is configured, then all inbound traffic to the zone has the match criteria applied to it.
Default
both
Parameters
- zone-outbound
specifies packets that are outbound from the zone
- zone-inbound
specifies packets that are inbound to the zone
- both
specifies packets that are inbound to and outbound from the zone
dst-ip
Syntax
dst-ip ip-address to ip-address
dst-ip host-group {group-id | name}
no dst-ip
Context
config>security>policy>entry>match
Description
This command configures the destination IP address or address range to be used in the matching criteria of a policy entry. All packets within the specified IP address range are processed for matching criteria. For host group matching criteria, the host group must be configured before adding it to the policy.
The no form of the command removes the destination IP address match criterion.
Default
n/a
Parameters
- ip-address
the IPv4 address or address range to be matched
- group-id
the identifier of the host group to be matched
- name
the name of the host group to be matched, up to 32 characters in length (must start with a letter)
dst-port
Syntax
dst-port {lt | gt | eq} port
dst-port range start end
no dst-port
Context
config>security>policy>entry>match
config>security>app-group>entry>match
Description
This command configures a destination protocol TCP or UDP port number or port range for the match criterion.
The no form of the command removes the destination port match criterion.
Default
no dst-port
Parameters
- lt | gt | eq
use relative to port for specifying the port number match criterion:
lt specifies that all port numbers less than the port number match
gt specifies that all port numbers greater than the port number match
eq specifies that the port number must be an exact match
- port
the destination port number to be used as a match criterion, expressed as a decimal integer
- startend
specifies an inclusive range of port numbers to be used as a match criterion. The destination port numbers start and end are expressed as decimal integers.
icmp-code
Syntax
icmp-code icmp-code
no icmp-code
Context
config>security>policy>entry>match
config>security>app-group>entry>match
Description
This command configures matching on an ICMP code field in the ICMP header of an IPv4 packet as a match criterion.
This option is only meaningful if the protocol match criterion specifies ICMP (1).
The no form of the command removes the criterion from the match entry.
Default
no icmp-code
Parameters
- icmp-code
icmp-code-number | icmp-code-keyword
- icmp-code-number
the ICMP code number in decimal, hexadecimal, or binary, to be used as a match criterion
- icmp-code-keyword
the name of an ICMP code to be used as a match criterion
icmp-type
Syntax
icmp-type icmp-type
no icmp-type
Context
config>security>policy>entry>match
config>security>app-group>entry>match
Description
This command configures matching on the ICMP type field in the ICMP header of an IPv4 packet as a match criterion.
This option is only meaningful if the protocol match criterion specifies ICMP (1).
The no form of the command removes the criterion from the match entry.
Default
no icmp-type
Parameters
- icmp-type
icmp-type-number | icmp-type-keyword
- icmp-type-number
the ICMP type number in decimal, hexadecimal, or binary, to be used as a match criterion
- icmp-type-keyword
the name of an ICMP type to be used as a match criterion
src-ip
Syntax
src-ip ip-address to ip-address
src-ip host-group {group-id | name}
no src-ip
Context
config>security>policy>entry>match
Description
This command configures the source IP address or address range to be used in the matching criteria of a policy entry. All packets within the specified IP address range are processed for matching criteria. For host group matching criteria, the host group must be configured before adding it to the policy.
The no form of the command removes the source IP address match criterion.
Default
n/a
Parameters
- ip-address
the IPv4 address to be matched
- group-id
the identifier of the host group to be matched
- name
the name of the host group to be matched, up to 32 characters in length (must start with a letter)
src-port
Syntax
src-port {lt | gt | eq} port
src-port range start end
no src-port
Context
config>security>policy>entry>match
config>security>app-group>entry>match
Description
This command configures a source protocol TCP or UDP port number or port range for the match criterion.
The no form of the command removes the source port match criterion.
Default
no src-port
Parameters
- lt | gt | eq
use relative to port for specifying the port number match criterion:
lt specifies that all port numbers less than the port number match
gt specifies all port numbers greater than the port number match
eq specifies that the port number must be an exact match
- port
the source port number to be used as a match criterion, expressed as a decimal integer
- startend
specifies an inclusive range of port numbers to be used as a match criterion. The destination port numbers start and end are expressed as decimal integers.
profile
Syntax
profile {profile-id | profile-name}
no profile
Context
config>security>policy>entry
Description
This command assigns an already configured profile to a policy.
The no form of the command removes the assigned profile.
Default
1
Parameters
- profile-id
the ID of the profile group, from 1 to 65535
- profile-name
the name of the profile group, up to 32 characters in length (must start with a letter)
name
Syntax
name policy-name
no name
Context
config>security>policy
Description
This command configures a policy group name.
The no form of the command removes the configured policy group name.
Parameters
- policy-name
the name of the policy, up to 32 characters in length (must start with a letter)
session-high-wmark
Syntax
session-high-wmark percentage
no session-high-wmark
Context
config>security
Description
This command configures the high-water mark threshold for security sessions. An alarm is raised when the high-water mark threshold is reached or exceeded. The value must be greater than or equal to the session-low-wmark value.
The no form of the command removes the high-water mark setting.
Default
no session-high-wmark
Parameters
- percentage
specifies the high-water mark threshold
session-low-wmark
Syntax
session-low-wmark percentage
no session-low-wmark
Context
config>security
Description
This command configures the low-water mark threshold for security sessions. The alarm is cleared when the session utilization percentage is equal to or less than the low-water mark threshold. The value must be less than or equal to the session-high-wmark value.
The no form of the command removes the low-water mark setting.
Default
no session-low-wmark
Parameters
- percentage
specifies the low-water mark threshold
Match List Configuration Commands
match-list
Syntax
match-list
Context
config>filter
Description
This command enables the context to configure a match list for use in IPv4, IPv6, IP exception, CSM, or management access filter policies.
Default
n/a
ip-prefix-list
Syntax
ip-prefix-list ip-prefix-list-name [create]
no ip-prefix-list ip-prefix-list-name
Context
config>filter>match-list
Description
This command creates an IPv4 prefix list that can be used as match criteria in filter policies.
An ip-prefix-list must contain only IPv4 address prefixes.
The no form of this command deletes the specified list. The list cannot be deleted if it is referenced by a filter policy.
Default
n/a
Parameters
- ip-prefix-list-name
a string of up to 32 printable ASCII characters. If special characters are used, the string must be enclosed within double quotes.
- create
keyword, mandatory when creating an ip-prefix-list
prefix
Syntax
[no] prefix ip-prefix/prefix-length
Context
config>filter>match-list>ip-prefix-list
Description
This command adds an IPv4 prefix to the IPv4 address prefix match list.
To add a set of unique prefixes, execute the command with all unique prefixes. The prefixes are allowed to overlap IPv4 address space.
An IPv4 prefix addition is blocked if resource exhaustion is detected anywhere in the system due to filter policies using this IPv4 address prefix list.
The no form of this command deletes the specified prefix from the list.
Default
n/a
Parameters
- ip-prefix/prefix-length
a valid IPv4 address in dotted-decimal notation
prefix-exclude
Syntax
[no] prefix-exclude ip-prefix/prefix-length
Context
config>filter>match-list>ip-prefix-list
Description
This command excludes an IPv4 prefix from the IPv4 address prefix match list.
The no form of this command deletes the specified excluded IPv4 prefix from the list.
Default
n/a
Parameters
- ip-prefix/prefix-length
a valid IPv4 address in dotted-decimal notation
ipv6-prefix-list
Syntax
ipv6-prefix-list ipv6-prefix-list-name [create]
no ipv6-prefix-list ipv6-prefix-list-name
Context
config>filter>match-list
Description
This command creates an IPv6 prefix list that can be used as match criteria in filter policies.
An ipv6-prefix-list must contain only IPv6 address prefixes.
The no form of this command deletes the specified list. The list cannot be deleted if it is referenced by a filter policy.
Default
n/a
Parameters
- ipv6-prefix-list-name
a string of up to 32 printable ASCII characters. If special characters are used, the string must be enclosed within double quotes.
- create
keyword, mandatory when creating an ipv6-prefix-list
prefix
Syntax
[no] prefix ipv6-prefix/prefix-length
Context
config>filter>match-list>ipv6-prefix-list
Description
This command adds an IPv6 address prefix to the IPv6 address prefix match list.
To add a set of unique prefixes, execute the command with all unique prefixes. The prefixes are allowed to overlap IPv6 address space.
An IPv6 prefix addition will be blocked if resource exhaustion is detected anywhere in the system due to filter policies using this address prefix list.
The no form of this command deletes the specified IPv6 address prefix from the list.
Default
n/a
Parameters
- ipv6-prefix/prefix-length
a valid IPv6 address prefix
prefix-exclude
Syntax
[no] prefix-exclude ipv6-prefix/prefix-length
Context
config>filter>match-list>ipv6-prefix-list
Description
This command excludes an IPv6 prefix from the IPv6 address prefix match list.
The no form of this command deletes the specified excluded IPv6 prefix from the list.
Default
n/a
Parameters
- ipv6-prefix/prefix-length
a valid IPv6 address prefix
Show Commands
ip
Syntax
ip
ip ip-filter-id [detail]
ip ip-filter-id [associations | counters]
ip ip-filter-id entry entry-id counters
Context
show>filter
Description
This command displays IPv4 filter information.
Parameters
- ip
displays all configured IPv4 filter information
- ip-filter-id
displays information for the specified filter ID or filter name and its filter entries
- detail
displays detailed information for the specified IPv4 filter
- associations
appends information as to where the specified filter policy ID is applied to the detailed filter policy ID output
- counters
displays counter information for the specified filter ID or filter entry
- entry-id
displays information for the specified filter entry ID only
Output
The following outputs are examples of IP filter information:
IP filter information (Output Example, Filter Field Descriptions)
IP filter information with filter ID specified (Output Example, Filter Field Descriptions (Filter ID Specified))
IP filter associations (Output Example, Filter Associations Field Descriptions)
IP filter counters (Output Example, Filter Counters Field Descriptions)
*A-ALU-1# show filter ip
===============================================================================
IP Filters
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
1 Template Yes
3 Template Yes
6 Template Yes
10 Template No
11 Template No
-------------------------------------------------------------------------------
Num IP filters: 5
Label |
Description |
|---|---|
Filter Id |
The IP filter ID |
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Description |
The IP filter policy description |
*A:7705:Dut-D# show filter ip 65535
===============================================================================
IP Filter
===============================================================================
Filter Id : 65535 Applied : No
Scope : Template Def. Action : Drop
Entries : 3
Sub-Entries : 35
Description : Description for Ip Filter Policy id # 65535
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 64
Description : Description for Ip Filter Policy id # 65535 entry 64
Log Id : 102
Src. IP : ip-prefix-list "prefList2"
Src. Port : n/a
Dest. IP : ip-prefix-list "prefList1"
Dest. Port : n/a
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Primary Action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : 128
Description : Description for Ip Filter Policy id # 65535 entry 128
Log Id : 105
Src. IP : ip-prefix-list "prefList2"
Src. Port : n/a
Dest. IP : ip-prefix-list "prefList1"
Dest. Port : n/a
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Primary Action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : 256
Description : Description for Ip Filter Policy id # 65535 entry 256
Log Id : 199
Src. IP : ip-prefix-list "prefList"
Src. Port : n/a
Dest. IP : 0.0.0.0/0
Dest. Port : n/a
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Primary Action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
===============================================================================
Label |
Description |
|---|---|
IP Filter |
|
Filter Id |
The IP filter policy ID |
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Def. Action |
The default action for packets that do not match the filter entries, either drop or forward |
Entries |
The number of entries configured in this filter ID |
Sub-Entries |
The number of sub-entries configured in this filter ID |
Description |
The IP filter policy description, if specified |
Filter Match Criteria |
|
Entry |
The filter entry ID; Inactive indicates that the filter entry is incomplete because no action has been specified. |
Description |
The IP filter policy description, if specified |
Log Id |
The filter log identifier |
Src. IP |
The source IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
Src. Port |
The source TCP or UDP port match criterion |
Dest. IP |
The destination IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
Dest. Port |
The destination TCP or UDP port match criterion |
Protocol |
The protocol ID for the match criterion; Undefined indicates that no protocol is specified (IPv4 filters only) |
Dscp |
The DSCP name to be used as match criterion; Undefined indicates that no DSCP name is specified |
ICMP Type |
The ICMP type match criterion; Undefined indicates that no ICMP type is specified |
ICMP Code |
The ICMP code match criterion; Undefined indicates that no ICMP code is specified |
Fragment (IPv4 filters only |
Off — configures a match on all unfragmented packets |
On — configures a match on all fragmented packets |
|
Next Header |
The next header ID used for the match criterion; Undefined indicates that no next header is specified (IPv6 filters only) |
Option-pres (IPv4 filters only |
Off — does not search for packets that contain the option field or have an option field of zero |
On — matches packets that contain the option field or have an option field of zero |
|
Sampling |
Off — specifies that traffic sampling is disabled |
On — specifies that traffic sampling is enabled |
|
Int. Sampling |
Off — specifies that interface traffic sampling is disabled |
On — specifies that interface traffic sampling is enabled |
|
IP-Option |
Specifies matching packets with a specific IP option or range of IP options in the IP header for IP filter match criteria |
Multiple Option (IPv4 filters only |
Off — the option fields are not checked |
On — packets containing one or more option fields in the IP header will be used as IP filter match criteria |
|
TCP-syn |
Off — the SYN bit is not matched |
On — matches the SYN bit being set or reset in the control bits of the TCP header of an IP packet |
|
TCP-ack |
Off — the ACK bit is not matched |
On — matches the ACK bit being set or reset in the control bits of the TCP header of an IP packet |
|
Primary Action |
Forward — the primary action for packets that do not match the filter entries is to forward |
Drop — the primary action for packets that do not match the filter entries is to drop |
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
*A-ALU-49# show filter ip 1 associations
===============================================================================
IP Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 1
-------------------------------------------------------------------------------
Filter Association : IP
-------------------------------------------------------------------------------
===============================================================================
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10
Log Id : n/a
Src. IP : 10.1.1.1/24 Src. Port : None
Dest. IP : 10.0.0.0/0 Dest. Port : None
Protocol : 2 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 0 Egr. Matches : 0
===============================================================================
*A-ALU-49#
*A-ALU-49# show filter ip 1 associations
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Association : IPv6
-------------------------------------------------------------------------------
No Match Found
===============================================================================
*A-ALU-49#
Label |
Description |
|---|---|
IP Filter/IPv6 Filter |
|
Filter Id |
The IP filter policy ID |
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Def. Action |
The default action for packets that do not match the filter entries, either drop or forward |
Entries |
The number of entries configured for this filter policy |
Description |
The IP filter policy description, if specified |
Filter Association |
IP or IPv6 |
Filter Match Criteria: IP or IPv6 |
|
Entry |
The filter entry ID; Inactive indicates that the filter entry is incomplete because no action has been specified |
Log Id |
The filter log identifier |
Src. IP |
The source IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
Src. Port |
The source TCP or UDP port match criterion |
Dest. IP |
The destination IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
Dest. Port |
The destination TCP or UDP port match criterion |
Protocol |
The protocol ID for the match criterion; Undefined indicates that no protocol is specified (IPv4 filters only) |
Dscp |
The DSCP name to be used as match criterion; Undefined indicates that no DSCP name is specified |
ICMP Type |
The ICMP type match criterion; Undefined indicates that no ICMP type is specified |
ICMP Code |
The ICMP code to be used as a match criterion; Undefined indicates that no ICMP code is specified |
Fragment (IPv4 filters only) |
Off — configures a match on all unfragmented packets |
On — configures a match on all fragmented packets |
|
Option-present (IPv4 filters only) |
Off — does not search for packets that contain the option field or have an option field of zero |
On — matches packets that contain the option field or have an option field of zero |
|
Sampling |
Off — specifies that traffic sampling is disabled |
On — specifies that traffic sampling is enabled |
|
Int. Sampling |
Off — specifies that interface traffic sampling is disabled |
On — specifies that interface traffic sampling is enabled |
|
IP-Option |
Specifies matching packets with a specific IP option or range of IP options in the IP header for IP filter match criteria |
Multiple Option (IPv4 filters only) |
Off — the option fields are not checked |
On — packets containing one or more option fields in the IP header will be used as IP filter match criteria |
|
TCP-syn |
Off — the SYN bit is not matched |
On — matches the SYN bit being set or reset in the control bits of the TCP header of an IP packet |
|
TCP-ack |
Off — the ACK bit is not matched |
On — matches the ACK bit being set or reset in the control bits of the TCP header of an IP packet |
|
Next Header |
The next header ID for the match criteria; Undefined indicates that no next header is specified (IPv6 filters only) |
Match action |
Default — the filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates the entry is inactive, the filter entry is incomplete (no action was specified). |
Drop — drop packets matching the filter entry |
|
Forward — forward packets matching the filter entry |
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
*A-ALU-1# show filter ip 3 counters
===============================================================================
IP Filter : 100
===============================================================================
Filter Id : 3 Applied : Yes
Scope : Template Def. Action : Drop
Entries : Not Available
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10
Ing. Matches: 749 Egr. Matches : 0
Entry : 200
Ing. Matches: 0 Egr. Matches : 0
===============================================================================
*A-ALU-1#
*A-ALU-1# show filter ipv6 1 counters
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 1 (Inactive)
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
===============================================================================
*A-ALU-1#
Label |
Description |
|---|---|
IP Filter/IPv6 Filter |
|
Filter Id |
The IP filter policy ID |
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Def. Action |
The default action for packets that do not match the filter entries, either drop or forward |
Entries |
The number of entries configured in this filter ID |
Description |
The IP filter policy description, if specified |
Filter Match Criteria: IP/IPv6 |
|
Entry |
The filter entry ID; Inactive indicates that the filter entry is incomplete because no action has been specified |
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
ip-exception
Syntax
ip-exception
ip-exception ip-filter-id
ip-exception ip-filter-id [associations | counters]
ip-exception ip-filter-id entry entry-id counters
Context
show>filter
Description
This command shows IPv4 exception filter information.
Parameters
- ip-exception
displays all configured IPv4 exception filter information
- ip-filter-id
displays information for the specified IPv4 exception filter
- associations
appends information as to where the specified IPv4 exception filter is applied to the detailed IPv4 exception filter output
- counters
displays counter information for the specified IPv4 exception filter or filter entry
- entry-id
displays information for the specified IPv4 exception filter entry ID only
Output
The following output is an example of IP exception information with a specified ip-filter-id, and IP Exception Field Descriptions describes the fields.
Output Example*A:7705:Dut-D# show filter ip-exception 99
===============================================================================
IP Exception Filter
===============================================================================
Filter Id : 99 Applied : No
Scope : Template
Entries : 1
Sub-Entries : 51
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Src. IP : ip-prefix-list "prefList1"
Src. Port : n/a
Dest. IP : ip-prefix-list "prefList"
Dest. Port : n/a
Protocol : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
Primary Action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
|
Label |
Description |
|---|---|
|
IP Exception Filter |
|
|
Filter Id |
The IP exception filter policy ID |
|
Applied |
No — the IP exception filter ID has not been applied |
|
Yes — the IP exception filter ID is applied |
|
|
Scope |
Template — the filter policy is of type template |
|
Exclusive — the filter policy is of type exclusive |
|
|
Entries |
The number of entries configured in this filter ID |
|
Sub-Entries |
The number of sub-entries configured in this filter ID |
|
Description |
The IP filter policy description, if specified |
|
Filter Match Criteria: IP |
|
|
Entry |
The number of entries configured in this filter ID |
|
Description |
The IP filter policy entry description string, if specified |
|
Src. IP |
The source IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
|
Src. Port |
The source TCP or UDP port match criterion |
|
Dest. IP |
The destination IP address, IP address and prefix length, or referenced prefix match list match criterion; 0.0.0.0/0 indicates that no criterion is specified for the filter entry |
|
Dest. Port |
The destination TCP or UDP port match criterion |
|
Protocol |
The protocol ID for the match criterion; Undefined indicates that no protocol is specified (IPv4 filters only) |
|
ICMP Type |
The ICMP type match criterion; Undefined indicates that no ICMP type is specified |
|
ICMP Code |
The ICMP code to be used as a match criterion; Undefined indicates that no ICMP code is specified |
|
Sampling |
Off — specifies that traffic sampling is disabled |
|
On — specifies that traffic sampling is enabled |
|
|
Int. Sampling |
Off — specifies that interface traffic sampling is disabled |
|
On — specifies that interface traffic sampling is enabled |
|
|
Primary Action |
Forward — the primary action for packets that do not match the filter entries is to forward |
|
Drop — the primary action for packets that do not match the filter entries is to drop |
|
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
|
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
ipv6
Syntax
ipv6
ipv6 ipv6-filter-id [detail]
ipv6 ipv6-filter-id [associations | counters]
ipv6 ipv6-filter-id entry entry-id counters
Context
show>filter
Description
This command displays IPv6 filter information.
Parameters
- ipv6
displays all configured IPv6 filter information
- ipv6-filter-id
displays information for the specified filter ID or filter name and its filter entries
- detail
displays detailed information for the specified IPv6 filter
- associations
appends information as to where the specified filter policy ID is applied to the detailed filter policy ID output
- counters
displays counter information for the specified filter ID or filter entry
- entry-id
displays information for the specified filter entry ID only
Output
The following outputs are examples of IPv6 filter information:
IPv6 filter information with filter ID specified (Output Example, IPv6 Filter Field Descriptions (Filter ID Specified))
detailed IPv6 filter information with filter ID specified (Output Example, Detailed IPv6 Filter Field Descriptions (Filter ID Specified))
*A-ALU-1# show filter ipv6 1
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 1 (Inactive)
Description : (Not Specified)
Log Id : n/a
Src. IP : ::/0 Src. Port : None
Dest. IP : ::/0 Dest. Port : None
Next Header : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
===============================================================================
*A-ALU-1#
Label |
Description |
|---|---|
IPv6 Filter |
|
Filter Id |
The IPv6 filter policy ID |
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Def. Action |
The default action for packets that do not match the filter entries, either drop or forward |
Entries |
The number of entries configured for this filter policy |
Description |
The filter policy description, if specified |
Filter Match Criteria: IPv6 |
|
Entry |
The filter entry ID |
Description |
The IP filter policy description, if specified |
Log Id |
Not applicable for IPv6 filter policies |
Src. IP |
The source IP address, IP address and prefix length, or referenced prefix match list match criterion |
Src. Port |
The source TCP or UDP port match criterion |
Dest. IP |
The destination IP address, IP address and prefix length, or referenced prefix match list match criterion |
Dest. Port |
The destination TCP or UDP port match criterion |
Next Header |
The next header ID for the match criteria; Undefined indicates no next header is specified |
Dscp |
The DSCP name to be used as match criterion; Undefined indicates that no DSCP name is specified |
ICMP Type |
The ICMP type match criterion; Undefined indicates that no ICMP type is specified |
ICMP Code |
The ICMP code to be used as a match criterion; Undefined indicates that no ICMP code is specified |
TCP-syn |
Off — the SYN bit is not matched |
On — matches the SYN bit being set or reset in the control bits of the TCP header of an IP packet |
|
TCP-ack |
Off — the ACK bit is not matched |
On — matches the ACK bit being set or reset in the control bits of the TCP header of an IP packet |
|
Match action |
Default — the filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates that the entry is Inactive, the filter entry is incomplete (no action was specified). |
Drop — drop packets matching the filter entry |
|
Forward — forward packets matching the filter entry |
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
*A:7705:Dut-D# show filter ipv6 1 detail
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Sub-Entries : 64
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Log Id : n/a
Src. IP : ::/0
Src. Port : n/a
Dest. IP : ipv6-prefix-list "prefList"
Dest. Port : n/a
Next Header : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Sampling : Off Int. Sampling : On
TCP-syn : Off TCP-ack : Off
Flow-label : n/a Flow-label Mask: n/a
Primary Action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
-------------------------------------------------------------------------------
Filter Match IPv6 Prefix Lists
-------------------------------------------------------------------------------
ipv6-prefix-list "prefList"
===============================================================================
configured prefixes:
-------------------------------------------------------------------------------
3000:20:10::/64
-------------------------------------------------------------------------------
generated prefixes:
-------------------------------------------------------------------------------
3000:20:10::/123 3000:20:10::21/128
3000:20:10::22/127 3000:20:10::24/126
3000:20:10::28/125 3000:20:10::30/124
3000:20:10::40/122 3000:20:10::80/121
3000:20:10::100/120 3000:20:10::200/119
3000:20:10::400/118 3000:20:10::800/117
3000:20:10::1000/116 3000:20:10::2000/115
3000:20:10::4000/114 3000:20:10::8000/113
3000:20:10::1:0/112 3000:20:10::2:0/111
3000:20:10::4:0/110 3000:20:10::8:0/109
3000:20:10::10:0/108 3000:20:10::20:0/107
3000:20:10::40:0/106 3000:20:10::80:0/105
3000:20:10::100:0/104 3000:20:10::200:0/103
3000:20:10::400:0/102 3000:20:10::800:0/101
3000:20:10::1000:0/100 3000:20:10::2000:0/99
3000:20:10::4000:0/98 3000:20:10::8000:0/97
3000:20:10::1:0:0/96 3000:20:10::2:0:0/95
3000:20:10::4:0:0/94 3000:20:10::8:0:0/93
3000:20:10::10:0:0/92 3000:20:10::20:0:0/91
3000:20:10::40:0:0/90 3000:20:10::80:0:0/89
3000:20:10::100:0:0/88 3000:20:10::200:0:0/87
3000:20:10::400:0:0/86 3000:20:10::800:0:0/85
3000:20:10::1000:0:0/84 3000:20:10::2000:0:0/83
3000:20:10::4000:0:0/82 3000:20:10::8000:0:0/81
3000:20:10:0:1::/80 3000:20:10:0:2::/79
3000:20:10:0:4::/78 3000:20:10:0:8::/77
3000:20:10:0:10::/76 3000:20:10:0:20::/75
3000:20:10:0:40::/74 3000:20:10:0:80::/73
3000:20:10:0:100::/72 3000:20:10:0:200::/71
3000:20:10:0:400::/70 3000:20:10:0:800::/69
3000:20:10:0:1000::/68 3000:20:10:0:2000::/67
3000:20:10:0:4000::/66 3000:20:10:0:8000::/65
-------------------------------------------------------------------------------
NUM prefixes: 65
References:
-------------------------------------------------------------------------------
IPv6-filter 1 entry 1 Dst-Ip
-------------------------------------------------------------------------------
NUM references: 1
NUM IPv6 Prefix Lists: 1
-------------------------------------------------------------------------------
Filter Match Port Lists
-------------------------------------------------------------------------------
No Port Lists
===============================================================================
Label |
Description |
|---|---|
IPv6 Filter |
|
Filter Id |
The filter policy ID |
Applied |
No — the filter policy ID has not been applied |
Yes — the filter policy ID is applied |
|
Scope |
Template — the filter policy is of type template |
Exclusive — the filter policy is of type exclusive |
|
Def. Action |
The default action for packets that do not match the filter entries, either drop or forward |
Entries |
The number of entries configured for this filter policy |
Description |
The filter policy description, if specified |
Filter Match Criteria: IPv6 |
|
Entry |
The filter entry ID |
Description |
The filter policy description; if no description is assigned, (Not Specified) is displayed |
Log Id |
Not applicable for IPv6 filter policies |
Src. IP |
The source IP address, IP address and prefix length, or referenced prefix match list match criterion |
Src. Port |
The source TCP or UDP port match criterion |
Dest. IP |
The destination IP address, IP address and prefix length, or referenced prefix match list match criterion |
Dest. Port |
The destination TCP or UDP port match criterion |
Next Header |
The next header ID for the match criteria; Undefined indicates no next header is specified |
Dscp |
The DSCP name to be used as match criterion; Undefined indicates that no DSCP name is specified |
ICMP Type |
The ICMP type match criterion; Undefined indicates that no ICMP type is specified |
ICMP Code |
The ICMP code to be used as a match criterion; Undefined indicates that no ICMP code is specified |
Sampling |
Off — specifies that traffic sampling is disabled |
On — specifies that traffic sampling is enabled |
|
Int. Sampling |
Off — specifies that interface traffic sampling is disabled |
On — specifies that interface traffic sampling is enabled |
|
TCP-syn |
Off — the SYN bit is not matched |
On — matches the SYN bit being set or reset in the control bits of the TCP header of an IP packet |
|
TCP-ack |
Off — the ACK bit is not matched |
On — matches the ACK bit being set or reset in the control bits of the TCP header of an IP packet |
|
Flow-label |
Not applicable for IPv6 filters |
Flow-label Mask |
Not applicable for IPv6 filters |
Primary Action |
Forward — the primary action for packets that do not match the filter entries is to forward |
Drop — the primary action for packets that do not match the filter entries is to drop |
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
Filter Match IPv6 Prefix Lists |
|
ipv6-prefix-list |
The prefix list name |
configured prefixes |
The address and prefix length of the configured prefixes |
generated prefixes |
The address and prefix length of the generated prefixes |
NUM prefixes |
The total number of configured and generated prefixes |
References |
The policies, policy entries, and source/destination IPv6 match type per entry referring to the specified match list |
NUM references |
The total number of configured references |
NUM IPv6 Prefix Lists |
The total number of configured IPv6 prefix lists |
Filter Match Port Lists |
Not applicable for the 7705 SAR |
log
Syntax
log [bindings]
log log-id [match string]
Context
show>filter
Description
This command displays filter log information. When a filter log command is used with a MAC filter and a packet is matched, the log entry is different from an IP filter entry. For a MAC filter, the source and destination IP address of incoming packets are not included in the log.
Parameters
- bindings
displays the number of filter logs currently available
- log-id
the filter log ID destination expressed as a decimal integer
- string
specifies to display the log entries starting from the first occurrence of the specified string
Output
The following outputs are examples of filter log information:
filter log information (Output Example, Filter Log Field Descriptions)
filter log bindings (Output Example, Filter Log Bindings Field Descriptions)
*A-ALU-1# show filter log
===============================================================================
Filter Logs
===============================================================================
Log-Id Dest. Id/Entries Enabled Description
-------------------------------------------------------------------------------
101 Memory 1000 Yes Default filter log
Wrap: Enabled
1 Entries Found
===============================================================================
*A-ALU-1#
*A-ALU-1# show filter log 101
===============================================================================
Filter Log
===============================================================================
Admin state : Enabled
Description : Default filter log
Destination : Memory
Wrap : Enabled
-------------------------------------------------------------------------------
Maximum entries configured : 1000
Number of entries logged : 4
2011/1124 22:10:03 Ip Filter: 1:12 Desc: Descr. for Ip Fltr Policy id # 1 entry 12
SDP: 1:60000 Direction: Ingress Action: Drop
Src MAC: 1f-ff-f0-1f-ff-c5 Dst MAC: aa-bb-cc-dd-ee-ff EtherType: 0800
Src IP: 10.50.1.144:3216 Dst IP: 10.10.11.2:0 Flags: 0 TOS: b8 TTL: 64
Protocol: UDP
2011/1124 22:10:03 Ip Filter: 1:12 Desc: Descr. for Ip Fltr Policy id # 1 entry 12
SDP: 1:60000 Direction: Ingress Action: Drop
Src MAC: 1f-ff-f0-1f-ff-c5 Dst MAC: aa-bb-cc-dd-ee-ff EtherType: 0800
Src IP: 10.50.1.144:3216 Dst IP: 10.10.11.2:0 Flags: 0 TOS: b8 TTL: 64
Protocol: UDP
2011/1124 22:10:06 Ip Filter: 1:13 Desc: Descr. for Ip Fltr Policy id # 1 entry 13
SDP: 1:60000 Direction: Ingress Action: Drop
Src MAC: 1f-ff-f0-1f-ff-c5 Dst MAC: aa-bb-cc-dd-ee-ff EtherType: 0800
Src IP: 10.50.1.16:0 Dst IP: 10.10.11.2:31 Flags: 0 TOS: b8 TTL: 64
Protocol: UDP
2011/1124 22:10:06 Ip Filter: 1:13 Desc: Descr. for Ip Fltr Policy id # 1 entry 13
SDP: 1:60000 Direction: Ingress Action: Drop
Src MAC: 1f-ff-f0-1f-ff-c5 Dst MAC: aa-bb-cc-dd-ee-ff EtherType: 0800
Src IP: 10.50.1.16:0 Dst IP: 10.10.11.2:31 Flags: 0 TOS: b8 TTL: 64
Protocol: UDP
===============================================================================
Label |
Description |
|---|---|
Log-Id |
The filter log ID |
Dest./Destination |
The destination of the filter log: memory or syslog |
Id/Entries |
The number of entries configured for this filter log |
Enabled |
Indicates whether the log is administratively enabled |
Admin State |
The administrative state of the log: enabled or disabled |
Description |
The description string configured for the filter log |
Wrap |
Indicates whether the wraparound function (circular buffer) is enabled |
Maximum entries configured |
The maximum number of entries allowed in this filter log |
Number of entries logged |
The number of entries in this filter log |
(date) |
The timestamp of the entry |
Ip Filter |
The filter ID and entry ID |
Desc. |
The description string for the filter log |
SDP |
The SDP using this filter |
Direction |
The direction of the traffic being filtered |
Action |
The action taken as a result of the filter |
Src MAC |
The source MAC address of the packet |
Dst MAC |
The destination MAC address of the packet |
EtherType |
The Ethertype of the packet |
Src IP |
The source IP address of the packet |
Dst IP |
The destination IP address of the packet |
Flags |
The number of flags associated with the packet |
TOS |
The type of service for the packet expressed as a hexadecimal number. Use the show>qos>dscp-table command to see the definitions of the numbers. |
TTL |
The time to live setting remaining for the packet |
Protocol |
The protocol used for the packet |
*A-ALU-1# show filter log bindings
===============================================================================
Filter Log Bindings
===============================================================================
Total Log Instances (Allowed) : 2047
Total Log Instances (In Use) : 1
Total Log Bindings : 1
-------------------------------------------------------------------------------
Type FilterId EntryId Log Instantiated
-------------------------------------------------------------------------------
Cpm 1 2 101 Yes
====================================================================
Label |
Description |
|---|---|
Total Log Instances (Allowed) |
The maximum allowed instances of filter logs allowed on the system |
Total Log Instances (In Use) |
The instances of filter logs presently existing on the system |
Total Log Bindings |
The count of the filter log bindings presently existing on the system |
Type |
The type of filter: CPM, IP, or MAC |
FilterID |
The unique identifier of the filter |
EntryID |
The unique identifier of an entry in the filter table |
Log |
The filter log identifier |
Instantiated |
Specifies if the filter log for this filter entry has been enabled |
mac
Syntax
mac {mac-filter-id [entry entry-id] [associations | counters]}
Context
show>filter
Description
This command displays MAC filter information.
Parameters
- mac-filter-id
displays detailed information for the specified filter ID or filter name and its filter entries
- entry entry-id
displays information about the specified filter entry ID for the specified filter ID
- associations
displays information about where the filter policy ID is applied to the detailed filter policy ID output
- counters
displays counter information for the specified filter ID
Output
The following outputs are examples of MAC filter information:
-
no parameters specified (Output Example, Filter MAC Field Descriptions (No Filter ID Specified))
-
mac-filter-id specified (Output Example , Filter MAC Field Descriptions (Filter ID Specified))
-
associations specified (Output Example , Filter MAC Associations Field Descriptions)
-
counters specified (Output Example , Filter MAC Counters Field Descriptions)
When no parameters are specified, a brief listing of MAC filters is produced.
*A-ALU-1>show>filter# mac
===============================================================================
Mac Filters Total: 3
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
11 Template No
232 Template Yes filter-west
5000 Template No
-------------------------------------------------------------------------------
Num MAC filters: 3
===============================================================================
*A-ALU-1#
|
Label |
Description |
|---|---|
|
Filter-Id |
The MAC filter ID |
|
Scope: |
Template — the filter policy is of type Template |
|
Exclusive — the filter policy is of type Exclusive |
|
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Description |
The MAC filter policy description |
When the filter ID is specified, detailed filter information for the filter ID and its entries is displayed.
*A-ALU-1# show filter# mac 5000
===============================================================================
Mac Filter
===============================================================================
Filter Id : 5000 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : Mac
-------------------------------------------------------------------------------
Entry : 5000 (Inactive) FrameType : Ethernet
Description : (Not Specified)
Log Id : n/a
Src Mac : ff:ff:ff:ff:ff:ff
Dest Mac :
Dot1p : Undefined Ethertype : Undefined
DSAP : Undefined SSAP : Undefined
Snap-pid : Undefined ESnap-oui-zero : Undefined
Match action: Drop
Ing. Matches: 0 pkts
Egr. Matches: 0 pkts
===============================================================================
*A-ALU-1#
|
Label |
Description |
|---|---|
|
MAC Filter |
|
|
Filter Id |
The MAC filter policy ID |
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Scope |
Template — the filter policy is of type Template |
|
Exclusive — the filter policy is of type Exclusive |
|
|
Def. Action |
Forward — the default action for the filter ID for packets that do not match the filter entries is to forward |
|
Drop — the default action for the filter ID for packets that do not match the filter entries is to drop |
|
|
Entries |
The number of entries in the filter policy |
|
Description |
The MAC filter policy description |
|
Filter Match Criteria: Mac |
|
|
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
|
FrameType |
Ethernet — the entry ID match frame type is Ethernet IEEE 802.3 |
|
Ethernet II — the entry ID match frame type is Ethernet Type II. |
|
|
Description |
The filter entry description |
|
Log Id |
The filter log identifier |
|
Src Mac |
The source MAC address match criterion. If the MAC address is all zeros, no criterion is specified for the filter entry. |
|
Dest Mac |
The destination MAC address match criterion. If the MAC address is all zeros, no criterion is specified for the filter entry. |
|
Dot1p |
The IEEE 802.1p value for the match criterion. Undefined indicates that no value is specified |
|
Ethertype |
The Ethertype value match criterion |
|
DSAP |
The DSAP value match criterion. Undefined indicates that no value is specified |
|
SSAP |
The SSAP value match criterion. Undefined indicates that no value is specified |
|
Snap-pid |
The Ethernet SNAP PID value match criterion. Undefined indicates that no value is specified |
|
Esnap-oui-zero |
Non-Zero — filter entry matches a non-zero value for the Ethernet SNAP OUI |
|
Zero — filter entry matches a zero value for the Ethernet SNAP OUI |
|
|
Undefined — no Ethernet SNAP OUI value is specified |
|
|
Match action |
Default— the filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates the entry is Inactive, the filter entry is incomplete, no action was specified |
|
Drop — packets matching the filter entry criteria will be dropped |
|
|
Forward — packets matching the filter entry criteria are forwarded |
|
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
|
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
*A-ALU-1# show filter# mac 11 associations
===============================================================================
Mac Filter
===============================================================================
Filter Id : 11 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Association : Mac
-------------------------------------------------------------------------------
No Match Found
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Id |
The IP filter ID |
|
Scope |
Template — the filter policy is of type Template |
|
Exclusive — the filter policy is of type Exclusive |
|
|
Entries |
The number of entries in the filter |
|
Description |
The MAC filter policy description |
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Def. Action |
Forward — the default action for the filter ID for packets that do not match the filter entries is to forward |
|
Drop — the default action for the filter ID for packets that do not match the filter entries is to drop |
|
|
Filter Association |
The type of filter association |
*A-ALU-1# show filter# mac 11 counters
===============================================================================
Mac Filter
===============================================================================
Filter Id : 11 Applied : No
Scope : Template Def. Action : Drop
Entries : 1
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : Mac
-------------------------------------------------------------------------------
Entry : 11 (Inactive) FrameType : Ethernet II
Ing. Matches: 0 pkts
Egr. Matches: 0 pkts
===============================================================================
*A-ALU-1#
|
Label |
Description |
|---|---|
|
Filter Id |
The IP filter ID |
|
Scope |
Template — the filter policy is of type Template |
|
Exclusive — the filter policy is of type Exclusive |
|
|
Entries |
The number of entries in the filter |
|
Description |
The MAC filter policy description |
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Def. Action |
Forward — the default action for the filter ID for packets that do not match the filter entries is to forward |
|
Drop — the default action for the filter ID for packets that do not match the filter entries is to drop |
|
|
Filter Match Criteria: Mac |
|
|
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
|
FrameType |
Ethernet — the entry ID match frame type is Ethernet IEEE 802.3 |
|
Ethernet II — the entry ID match frame type is Ethernet Type II |
|
|
Ing. Matches |
The number of ingress filter matches/hits for the filter entry |
|
Egr. Matches |
The number of egress filter matches/hits for the filter entry |
match-list
Syntax
match-list
Context
show>filter
Description
This command enables the context to display information for match lists used in IPv4, IPv6, IP exception, CSM, or management access filter policies.
ip-prefix-list
Syntax
ip-prefix-list [prefix-list-name]
ip-prefix-list prefix-list-name references
Context
show>filter>match-list
Description
This command displays IPv4 prefix information for match criteria in filter policies.
Parameters
- prefix-list-name
the name of a configured IPv4 prefix match list
- references
displays the filter policies, policy entries, and source/destination IPv4 match type per entry referring to the specified match list
Output
The following outputs are examples of filter match list information:
-
when a prefix list name is specified (Output Example, Filter Match List Field Descriptions (IPv4 Prefix List Name Specified))
-
when references is used with a specified prefix list (Output Example, Filter Match List Field Descriptions (IPv4 Prefix List Name and References Specified))
-
when prefix-exclude is used to exclude IPv4 prefixes from an IP prefix list (Output Example, Filter Match List Field Descriptions (IPv4 Prefix List with Excluded Prefixes))
When a prefix list name is specified:
*A:7705:Dut-D# show filter match-list ip-prefix-list "prefList1"
===============================================================================
Filter Match IP Prefix Lists
===============================================================================
ip-prefix-list "prefList1"
===============================================================================
configured prefixes:
-------------------------------------------------------------------------------
100.1.1.1/32 100.1.1.2/32 100.1.1.3/32
-------------------------------------------------------------------------------
NUM prefixes: 3
References:
-------------------------------------------------------------------------------
IP-filter 65535 entry 64 Dst-Ip
IP-filter 65535 entry 128 Dst-Ip
IP Exception-filt*
-------------------------------------------------------------------------------
NUM references: 3
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IP Prefix Lists |
|
|
ip-prefix-list |
The prefix list name |
|
configured prefixes |
The address and prefix length of the configured prefixes |
|
NUM prefixes |
The total number of configured prefixes |
|
References |
The policies, policy entries, and source/destination IPv4 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
When references is used with a specified prefix list name:
*A:7705:Dut-D# show filter match-list ip-prefix-list "prefList1" references
===============================================================================
Filter Match IP Prefix Lists
===============================================================================
ip-prefix-list "prefList1"
===============================================================================
References:
-------------------------------------------------------------------------------
IP-filter 65535 entry 64 Dst-Ip
IP-filter 65535 entry 128 Dst-Ip
IP Exception-filt*
-------------------------------------------------------------------------------
NUM references: 3
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IP Prefix Lists |
|
|
ip-prefix-list |
The prefix list name |
|
References |
The policies, policy entries, and source/destination IPv4 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
When prefix-exclude is used to exclude IPv4 prefixes from an IP prefix list:
A:7705:Dut-D# show filter match-list ip-prefix-list "prefList"
===============================================================================
Filter Match IP Prefix Lists
===============================================================================
ip-prefix-list "prefList"
===============================================================================
configured prefixes:
-------------------------------------------------------------------------------
100.100.0.0/24 100.200.0.0/24 100.200.1.0/24
-------------------------------------------------------------------------------
generated prefixes:
-------------------------------------------------------------------------------
100.100.0.0/28 100.100.0.16/29 100.100.0.28/30 100.100.0.32/29
100.100.0.44/30 100.100.0.48/28 100.100.0.64/26 100.100.0.128/25
100.200.0.0/28 100.200.0.16/29 100.200.0.28/30 100.200.0.32/29
100.200.0.44/30 100.200.0.48/28 100.200.0.64/26 100.200.0.128/25
-------------------------------------------------------------------------------
NUM prefixes: 19
References:
-------------------------------------------------------------------------------
IP-filter 65535 entry 256 Src-Ip
IP Exception-filt*
-------------------------------------------------------------------------------
NUM references: 2
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IP Prefix Lists |
|
|
ip-prefix-list |
The prefix list name |
|
configured prefixes |
The address and prefix length of the configured prefixes |
|
generated prefixes |
The address and prefix length of the generated prefixes |
|
NUM prefixes |
The total number of configured and generated prefixes |
|
References |
The policies, policy entries, and source/destination IPv4 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
ipv6-prefix-list
Syntax
ipv6-prefix-list [prefix-list-name]
ipv6-prefix-list prefix-list-name references
Context
show>filter>match-list
Description
This command displays IPv6 prefix information for match criteria in filter policies.
Parameters
- prefix-list-name
the name of a configured IPv6 prefix match list
- references
displays the filter policies, policy entries, and source/destination IPv6 match type per entry referring to the specified match list
Output
The following outputs are examples of filter match list information:
-
when an IPv6 prefix list name is specified (Output Example, Filter Match List Field Descriptions (IPv6 Prefix List Name Specified))
-
when references is used with a specified IPv6 prefix list (Output Example, Filter Match List Field Descriptions (IPv6 Prefix List Name and References Specified))
-
when prefix-exclude is used to exclude IPv6 prefixes from an IPv6 prefix list (Output Example, Filter Match List Field Descriptions (IPv6 Prefix List with Excluded Prefixes))
When an IPv6 prefix list name is specified:
*A:7705:Dut-D# show filter match-list ipv6-prefix-list "prefList1"
===============================================================================
Filter Match IPv6 Prefix Lists
===============================================================================
ipv6-prefix-list "prefList1"
===============================================================================
configured prefixes:
-------------------------------------------------------------------------------
3000:20:10::/64 3000:20:10::/123 3000:20:10::21/128
-------------------------------------------------------------------------------
NUM prefixes: 3
References:
-------------------------------------------------------------------------------
IPv6-filter 1 entry 1 Dst-Ip
-------------------------------------------------------------------------------
NUM references: 1
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IPv6 Prefix Lists |
|
|
ipv6-prefix-list |
The IPv6 prefix list name |
|
configured prefixes |
The address and prefix length of the configured prefixes |
|
NUM prefixes |
The total number of configured prefixes |
|
References |
The policies, policy entries, and source/destination IPv6 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
When references is used with a specified IPv6 prefix list name:
*A:7705:Dut-D# show filter match-list ipv6-prefix-list "prefList1" references
===============================================================================
Filter Match IPv6 Prefix Lists
===============================================================================
ipv6-prefix-list "prefList1"
===============================================================================
References:
-------------------------------------------------------------------------------
IPv6-filter 1 entry 1 Dst-Ip
IPv6-filter 1 entry 24 Dst-Ip
-------------------------------------------------------------------------------
NUM references: 2
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IPv6 Prefix Lists |
|
|
ipv6-prefix-list |
The IPv6 prefix list name |
|
References |
The policies, policy entries, and source/destination IPv6 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
When prefix-exclude is used to exclude IPv6 prefixes from an IPv6 prefix list:
A:7705:Dut-D# show filter match-list ipv6-prefix-list "prefList"
===============================================================================
Filter Match IPv6 Prefix Lists
===============================================================================
ipv6-prefix-list "prefList"
===============================================================================
configured prefixes:
-------------------------------------------------------------------------------
3000:20:10::/64
-------------------------------------------------------------------------------
generated prefixes:
-------------------------------------------------------------------------------
3000:20:10::/123 3000:20:10::21/128
3000:20:10::22/127 3000:20:10::24/126
...
3000:20:10:0:10::/76 3000:20:10:0:20::/75
3000:20:10:0:40::/74 3000:20:10:0:80::/73
3000:20:10:0:100::/72 3000:20:10:0:200::/71
3000:20:10:0:400::/70 3000:20:10:0:800::/69
3000:20:10:0:1000::/68 3000:20:10:0:2000::/67
3000:20:10:0:4000::/66 3000:20:10:0:8000::/65
-------------------------------------------------------------------------------
NUM prefixes: 65
References:
-------------------------------------------------------------------------------
IPv6-filter 1 entry 1 Dst-Ip
-------------------------------------------------------------------------------
NUM references: 1
===============================================================================
|
Label |
Description |
|---|---|
|
Filter Match IPv6 Prefix Lists |
|
|
ipv6-prefix-list |
The IPv6 prefix list name |
|
configured prefixes |
The address and prefix length of the configured prefixes |
|
generated prefixes |
The address and prefix length of the generated prefixes |
|
NUM prefixes |
The total number of configured and generated prefixes |
|
References |
The policies, policy entries, and source/destination IPv6 match type per entry referring to the specified match list |
|
NUM references |
The total number of configured references |
vlan
Syntax
vlan [filter-id] [entry entry-id]]
Context
show>filter
Description
This command displays VLAN filter information.
Parameters
- filter-id
displays detailed information for the specified filter ID or filter-name and its filter entries
- entry-id
displays information on the specified filter entry ID for the specified filter ID
Output
The following outputs are examples of VLAN filter information:
-
no parameters specified (Output Example, Filter VLAN Field Descriptions (No Filter Specified))
-
filter-id specified (Output Example , Filter VLAN Field Descriptions (Filter ID Specified))
When no parameters are specified, a brief listing of VLAN filters is displayed.
*A-ALU-1:show>filter# vlan
===============================================================================
VLAN Filters Total: 2
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
2 Template Yes VLAN_filter_2
65535 Template No
-------------------------------------------------------------------------------
Num VLAN filters: 2
===============================================================================
*A-ALU-1:show>filter#
|
Label |
Description |
|---|---|
|
Filter-Id |
The VLAN filter ID |
|
Scope |
Template — the VLAN filter policy is always of type Template |
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Description |
The VLAN filter policy description |
When the filter ID is specified, detailed filter information for the filter and its entries is displayed.
*A:7705custDoc:Sar18>show>filter# vlan 2
===============================================================================
VLAN Filter
===============================================================================
Filter Id : 2 Applied : Yes
Scope : Template Def. Action : drop
Entries : 4
Description : VLAN_filter_2
-------------------------------------------------------------------------------
Filter Match Criteria :
-------------------------------------------------------------------------------
Entry : 2
Description : vlan_fltr_entry2
Match : Untagged Action : forward
Entry : 3
Description : vlan_fltr_entry3
Match : VLAN Action : drop
Operation : eq
Vlan-Id : 2
Entry : 4
Description : vlan_fltr_entry4
Match : VLAN Action : drop
Operation : eq
Vlan-Id : 445
Entry : 65535
Description : (Not Specified)
Match : VLAN Action : drop
Operation : range
From : 2000 To : 3000
===============================================================================
*A:7705custDoc:Sar18>show>filter#
|
Label |
Description |
|---|---|
|
VLAN Filter |
|
|
Filter Id |
The VLAN filter policy ID |
|
Applied |
No — the filter policy ID has not been applied |
|
Yes — the filter policy ID is applied |
|
|
Scope |
Template — the filter policy is always of type Template |
|
Def. Action |
Forward — the default action for the filter ID for packets that do not match the filter entries is to forward |
|
Drop — the default action for the filter ID for packets that do not match the filter entries is to drop |
|
|
Entries |
The number of entries in the filter policy |
|
Description |
The VLAN filter policy description |
|
Filter Match Criteria: |
|
|
Entry |
The filter entry ID. If the filter entry ID indicates that the entry is (Inactive), then the filter entry is incomplete as no action has been specified |
|
Description |
The filter entry description |
|
Match |
VLAN— the type of match criteria for the entry is VLAN |
|
Untagged — the type of match criteria for the entry is untagged |
|
|
Action |
Drop — packets matching the filter entry criteria will be dropped |
|
Forward — packets matching the filter entry criteria will be forwarded |
|
|
Operation |
The match criteria operator. Valid operators are: lt (less than), gt (greater than), eq (equal to), and range (for a range of VLAN IDs). |
|
Vlan-Id |
The VLAN ID when the match criteria defines a specific VLAN ID |
|
From |
The start VLAN ID when the match criteria defines a VLAN ID range |
|
To |
The end VLAN ID when the match criteria defines a VLAN ID range |
app-group
Syntax
app-group [group-id | name] [entry entry-id] [detail]
Context
show>security
Description
This command displays firewall application group information.
Parameters
- group-id
displays information for the specified application group ID
- name
displays information for the specified application group name
- entry-id
displays information for the specified application group entry ID
- detail
displays detailed information about the specified application group
capture
Syntax
capture [format {decode | raw}]
Context
show>security
Description
This command displays summary information about the captured packets stored in the debug security log.
Parameters
- format decode
the debug security log displays the packet IP header and relevant Layer 4 headers
- format raw
the debug security log displays the raw packet in hexadecimal format
Output
The following output is an example of captured packet information.
Output Example*A-ALU-1# show security capture
===============================================================================
Security Packet Capture
===============================================================================
State :STOPPED
Start Time :NEVER
Running Time : 0 days 0 hours 0 mins 0 secs
Memory Capture Contents: [size=1024 count=0 <continuous>]
===============================================================================
*A-ALU-1#
control-summary
Syntax
control-summary
Context
show>security
Description
This command displays a summary of the receive control queues for a security zone.
Output
The following output is an example of receive control queue information.
Output Example*A-ALU-1# show security control-summary
===============================================================================
Zone Control Summary (Packets)
===============================================================================
Zone Forwarded Dropped
-------------------------------------------------------------------------------
VPRN_ZONE 0 0
ACCESS-POINT 0 0
PUBLIC-INTERNET 1 0
60 0 0
-------------------------------------------------------------------------------
Num of Zones: 4
===============================================================================
*A-ALU-1#
engine
Syntax
engine
Context
show>security
Description
This command displays a system-level security engine statistics. During a CSM switch, security statistics roll back to zero.
Output
The following output is an example of security engine statistics.
Output Example*A-ALU-1# show security engine
===============================================================================
Security Engine
===============================================================================
Packets
-------------------------------------------------------------------------------
Rx Queue
Forwarded – Control 1
– Session Data 96932032
Dropped 19944168792
Security Processing
Passed 96932033
Dropped 0
CPU Utilization (Sample period: 1 sec): 100 %
===============================================================================
*A-ALU-1#
host-group
Syntax
host-group [group-id | name] [detail]
Context
show>security
Description
This command displays firewall host group information.
Parameters
- group-id
displays information for the specified host group ID
- name
displays information for the specified host group name
- detail
displays detailed information about the specified host group
log
Syntax
log [log-id | name]
log events [type event-type]
log profile {log-profile-id | name} [type event-type]
log profiles
Context
show>security
Description
This command displays firewall logging information.
Parameters
- log-id
displays information for the specified log ID
- name
displays information for the specified log name or log profile name
- event-type
displays information about the specified log event type
- log-profile-id
displays information for the specified log profile ID
- events
displays information for all log events
- profiles
displays information for all log profiles
Output
The following output is an example of security log information, and Security Log Field Descriptions describes the fields.
Output Example*A-ALU-1# show security log SecurityLog11
===============================================================================
Security Log: SecurityLog11
===============================================================================
Description: Security Log ID 11
Profile : DEFAULT
Memory log contents [size=1024 next-event=3 (wrapped)]
1 06/11/2015 17:25:56 SECURITY:Packet Base IF:ies-201-10.1.0.1
Outbound : Forward Zone (Rule:1)
Inbound : GRT Zone (Rule:1)
Session : 1-FWD
Report : SessionBegin
IP header :
ver:4 hlen:20 tos:0x00 len:84 hxsum:0x4fa3
id:0x0001 frag:000 (offset:0)
10.1.1.1->10.1.1.2 proto:ICMP
ICMP header:
type:8 code:0 xsum:0x059e (echo-request)
2 06/11/2015 17:26:56 SECURITY:Audit SESSION:1
Outbound : <None>
Inbound : GRT Zone
Session : 1-FWD
Report : SessionEnd (TIMER-EXPIRED)
===============================================================================
*A-ALU-1#
*A-ALU-1# show security log events
===============================================================================
Security Logging Events
===============================================================================
Name ID Severity State
--------------------------------------------------------------
PACKET
TcpInvalidHeader 01 INFORM throttle
DnsInvalidHeader 02 INFORM throttle
DnsUnmatchedAnswer 03 INFORM throttle
...
ZONE
NoRuleMatched 01 INFORM throttle
SessionLimitReached 02 INFORM throttle
POLICY
Matched 01 INFORM suppress
MatchedNAT 02 INFORM suppress
ActionReject 03 INFORM throttle
...
SESSION
SessionBegin 01 INFORM throttle
SessionEnd 02 INFORM throttle
SessionBeginEnd 03 INFORM throttle
APPLICATION
Summary 01 INFORM throttle
HandshakeMissing 02 INFORM throttle
HandshakeCtlInvalid 03 INFORM throttle
HandshakeDataUnexpected 04 INFORM throttle
...
ALG
CmdIncomplete 01 INFORM throttle
DynamicRuleInserted 02 INFORM throttle
DynamicRuleInsertedPASV 03 INFORM throttle
...
--------------------------------------------------------------
Num of Events: 61
==============================================================
Label |
Description |
|---|---|
Security Logs |
|
Description |
The security log identifier |
Profile |
The security logging profile to which the log applies |
Memory log contents |
Details of the log content |
Outbound |
Session location of the zone in the outbound direction |
Inbound |
Session location of the zone in the inbound direction |
Session |
The session ID |
Report |
The security log event code |
IP header |
The IPv4 packet header |
Security Logging Events |
|
Name |
The name of the event type and event |
ID |
The event identifier |
Severity |
The severity of the event |
State |
Indicates how each event is being handled |
policer-group
Syntax
policer-group [group-id | name] [statistics]
Context
show>security
Description
This command displays policer group information.
Parameters
- group-id
displays detailed information for the specified policer group ID
- name
displays detailed information for the specified policer group name
- statistics
displays policer group statistics when a group is specified
Output
The following output is an example of policer group information.
Output Example*A:7705:Dut-C# show security policer-group 1 statistics
===============================================================================
Security Policer-Group
===============================================================================
Group Id : 1 Applied : Yes
Name : policer-group 1
Description : session rate created by SNMP
Ingress Rate : 1 mbps
CBS (bytes) : 1024
===============================================================================
===============================================================================
Policer Traffic Statistics
===============================================================================
Forward Reverse
-------------------------------------------------------------------------------
Passed
Packets 247690 101822
Octets 36162740 14866012
Dropped Packets
Rate-Exceeded 2777461 2919967
===============================================================================
policing-summary
Syntax
policing-summary
Context
show>security
Description
This command displays a summary of traffic statistics for policers.
Output
The following output is an example of traffic statistics for policers.
Output Example*A:7705:Dut-C# show security policing-summary
==============================================================================
Policing Summary (Packets)
==============================================================================
Policer Forwarded Dropped
------------------------------------------------------------------------------
policer-group 1 432001 7042904
policer-group 2 863995 6610910
policer-group 3 808609 4096798
policer-group 4 436480 1656494
policer-group 5 405590 1164140
policer-group 6 321247 725240
policer-group 7 320532 576457
policer-group 8 336382 488707
------------------------------------------------------------------------------
Num of Groups: 8
==============================================================================
policy
Syntax
policy [policy-id | policy-name] [detail] [association]
policy [policy-id | policy-name] [entry entry-id] [detail] [association]
Context
show>security
Description
This command displays security policy information.
Parameters
- policy-id
displays detailed information for the specified policy ID
- policy-name
specifies the name of the policy
- entry-id
displays information about the specified policy entry ID
- detail
displays detailed information about the specified policy or filter
- association
displays counter information for the specified policy or entry ID
Output
The following output is an example of security policy information, and Security Policy Field Descriptions (Detail) describes the fields.
Output Example*A-ALU-1# show security policy
===============================================================================
Security Policies
===============================================================================
Policy Id Scope Applied Name
-------------------------------------------------------------------------------
1 Template Yes Inbound Policy
2 Template Yes IES Policy
-------------------------------------------------------------------------------
Num of Policies: 2
===============================================================================
*A-ALU-1#
*A-ALU-1# show security policy 1 detail
===============================================================================
Security Policy
===============================================================================
Policy Id : 1 Applied : Yes
Name : Inbound Policy
Scope : Template Def. Action : Reject
Entries : 1
Description : common egress policy
-------------------------------------------------------------------------------
Policy Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1 Active : yes
Description : match TCP and port
Match direction : zone-inbound
Src. IP : None Src. Port : eq21
Dest. IP : None Dest. Port : None
Protocol : tcp
ICMP Type : Undefined ICMP Code : Undefined
Profile ID : DEFAULT Session : Fwd-Dir-O*
Action : nat Session Limit : None
Logging : suppressed
Entry : 2 Active: Yes
Description : match UDP and IP TCP-ack : Off
Match direction : zone-inbound
Src. IP : 10.100.0.2 Src. Port : None
Dest. IP : None Dest. Port : None
Protocol : udp
ICMP Type : Undefined ICMP Code : Undefined
Profile ID : DEFAULT Session : Bi-Direct*
Action : reject Session Limit : None
Logging : suppressed
===============================================================================
*A-ALU-1#
*A-ALU-1# show security policy 1 association
===============================================================================
Security Policy
===============================================================================
Policy Id : 1 Applied : Yes
Name : Inbound Policy
Scope : Template Def. Action : Reject
Entries : 1
Description : common egress policy
-------------------------------------------------------------------------------
Policy Match Criteria : IP
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
Associations
Zone-Id Name Type Svc-Id Bypass
-------------------------------------------------------------------------------
1 Service Inbound Zone IES 100 No
-------------------------------------------------------------------------------
Num of Associations: 1
===============================================================================
*A-ALU-1#
*A-ALU-1# show security policy 1 entry 1 detail
===============================================================================
Security Policy
===============================================================================
Policy Id : 1 Applied : Yes
Name : Inbound Policy
Scope : Template Def. Action : Reject
Entries : 2
Description : common egress policy
-------------------------------------------------------------------------------
Policy Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1 Active : yes
Description : match TCP and port
Match direction : zone-inbound
Src. IP : None Src. Port : eq21
Dest. IP : None Dest. Port : None
Protocol : tcp
ICMP Type : Undefined ICMP Code : Undefined
Profile ID : DEFAULT Session : Fwd-Dir-O*
Action : nat Session Limit : None
Logging : Suppressed
===============================================================================
*A-ALU-1#
Label |
Description |
|---|---|
Policy Id |
The security policy ID |
Name |
The name of the policy |
Scope |
Template — the policy is of type template |
Exclusive — the policy is of type exclusive |
|
Entries |
The number of entries configured in this policy ID |
Description |
The security policy description |
Applied |
No — the security policy ID has not been applied |
Yes — the security policy ID is applied |
|
Def. Action |
Reject — the default action for packets that do not match the policy entries is to reject |
Policy Match Criteria |
|
Entry |
The policy entry ID |
Description |
The policy entry description |
Match Direction |
Zone inbound — the match criteria is applied to packets inbound to the zone |
Zone outbound — the match criteria is applied to packets outbound from the zone |
|
Both — the match criteria is applied to packets both inbound to and outbound from the zone |
|
Src. IP |
The source IP address and prefix length match criterion |
Dest. IP |
The destination IP address and prefix length match criterion |
Protocol |
The protocol for the match criteria. Undefined indicates no protocol specified. |
ICMP Type |
The ICMP type match criterion. Undefined indicates no ICMP type is specified. |
Profile ID |
The profile ID |
Active |
No — the policy match criteria entry is not active |
Yes — the policy match criteria entry is active |
|
Action |
nat — applies NAT to the packets matching the profile entry |
reject — rejects packets matching the profile entry on the CSM session |
|
forwards — forward packets matching the profile entry |
|
drops — drop the packets matching the profile entry on the datapath session |
|
Src. Port |
The source TCP or UDP port number or port range |
Dest. Port |
The destination TCP or UDP port number or port range |
ICMP Code |
The ICMP code field in the ICMP header of an IP packet |
Session |
Indicates whether the security session is bidirectional or unidirectional (forward only) |
Session Limit |
The maximum number of concurrent sessions |
Logging |
Indicates whether logging has been enabled per policy entry or per zone, or whether all logs generated by the entry are suppressed |
profile
Syntax
profile [profile-id | name] [detail] [association]
Context
show>security
Description
This command displays security profile information.
Parameters
- profile-id
displays detailed information for the specified profile ID
- name
displays information about the specified profile name
- detail
displays detailed information about the specified profile ID
- association
displays counter information for the specified profile ID
Output
The following output is an example of security profile information, and Security Profile Field Descriptions (Detail) describes the fields.
Output Example*A-ALU-1# show security profile 1 detail
===============================================================================
Security Profile
===============================================================================
Profile Id : 1 Applied : Yes
Name : DEFAULT
Description : Default Session Profile
Packet :
Fragmentation : Allowed
Application : Inspection-Disabled ALG : Auto
Timeouts :
TCP Syn-Rcvd : strict 15 seconds
TCP Transitory : strict 4 min
TCP Established : idle 2 hrs 4 min
TCP Time-Wait : None
UDP Initial : strict 15 seconds
UDP Established : idle 5 min
UDP DNS : strict 15 seconds
ICMP Request : strict 1 min
OTHER Sessions : strict 10 min
===============================================================================
*A-ALU-1#
Label |
Description |
|---|---|
Profile Id |
The security profile ID |
Name |
The name of the profile |
Description |
The profile description |
Packet |
The configured packet level options |
Fragmentation |
Controls processing of IP packet fragments on a session |
Application |
The configured profile application parameters |
TCP Syn-Rcvd |
Timeout configured for a TCP session in a SYN state |
TCP Transitory |
Timeout configured for a TCP session in a transitory state |
TCP Established |
Timeout configured for a TCP session in an established state |
TCP Time-Wait |
Timeout configured for a TCP session in a time-wait state |
UDP Initial |
Timeout configured for a UDP session in an initial state |
UDP Idle |
Timeout configured for a UDP session in an idle state |
UDP DNS |
Timeout configured for a UDP session with destination port 53 |
ICMP Request |
Timeout configured for an ICMP session in which an ICMP request is sent but no ICMP response is received |
Other Sessions |
Timeout for sessions other than TCP, UDP, or ICMP |
Applied |
No — the security profile ID has not been applied |
Yes — the security profile ID is applied |
|
ALG |
Application level gateway: auto, FTP, or TFTP |
session-summary
Syntax
session-summary [service service-id] [router router-instance]
Context
show>security
Description
This command displays a summary of active security sessions for zones.
Output
The following output is an example of security session summary information, and Session Summary Field Descriptions describes the fields.
Output Example*A-ALU-1# show security session-summary
===============================================================================
Session Summary
===============================================================================
Total Created : 7
Active : 7 Limit : 16383
Utilization : 0% (OK)
Hi-Wtr-Mark : None Lo-Wtr-Mark : None
===============================================================================
===============================================================================
Zone Session Summary
===============================================================================
Inbound Outbound
Zone-Id Name Type Svc-Id Sessions Sessions
------------------------------------------------------------------------------
1 Service Inbound Zone IES 100 4 3
2 Service Outbound Zone IES 200 0 0
-------------------------------------------------------------------------------
Num of Zones: 2
===============================================================================
*A-ALU-1# show security session-summary service 100
===============================================================================
Session Summary
===============================================================================
Total Created : 7
Active : 7 Limit : 16383
Utilization : 0% (OK)
Hi-Wtr-Mark : None Lo-Wtr-Mark : None
===============================================================================
===============================================================================
Zone Session Summary
===============================================================================
Inbound Outbound
Zone-Id Name Type Svc-Id Sessions Sessions
1 Service Inbound Zone IES 100 4 3
-------------------------------------------------------------------------------
Num of Zones: 1
===============================================================================
*A-ALU-1# show security session-summary router 1
===============================================================================
Session Summary
===============================================================================
Total Created : 7
Active : 7 Limit : 16383
Utilization : 0% (OK)
Hi-Wtr-Mark : None Lo-Wtr-Mark : None
No Matching Zones
===============================================================================
Zone Session Summary
===============================================================================
Inbound Outbound
Zone-Id Name Type Svc-Id Sessions Sessions
-------------------------------------------------------------------------------
===============================================================================
*A-ALU-1#
Label |
Description |
|---|---|
Total Created |
The total number of security sessions created since node startup or last cleared statistics |
Active |
The number of security sessions that are currently active |
Limit |
The total number of security sessions allowed |
Utilization |
The number of active security sessions, expressed as a percentage of the total allowed |
Hi-Wtr-Mark |
Indicates the high-water mark threshold configured for security sessions |
Lo-Wtr-Mark |
Indicates the low-water mark threshold configured for security sessions |
Zone-Id |
The zone ID |
Name |
The name of the zone |
Type |
The zone type |
Svc-Id |
The service ID |
Inbound Sessions |
The number of sessions inbound to the zone |
Outbound Sessions |
The number of sessions outbound from the zone |
summary
Syntax
summary
Context
show>security
Description
This command displays a summary of security information.
Output
The following output is an example of security summary information.
Output Example*A-ALU-1# show security summary
===============================================================================
Security
===============================================================================
Policy State : Committed
Last Commit : 05/07/2015 03:05:34
Policies : 2
Profiles : 2
Zones : 2
Sessions
Active : 5223 Limit : 16383
Utilization : 85% (ALARM)
Hi-Wtr-Mark : 80% Lo-Wtr-Mark : 50%
===============================================================================
*A-ALU-1#
zone
Syntax
zone [service service-id] [router router-instance]
zone [zone-id | zone-name] [detail]
zone [zone-id | zone-name] interface
zone [zone-id | zone-name] statistics
Context
show>security
Description
This command displays security zone information. During a CSM activity switch, security session statistics roll back to zero; however, statistics for active security sessions do not.
Parameters
- service-id
displays detailed information for the specified service ID
- router-instance
displays detailed information for the specified router instance
- zone-id
displays detailed information for the specified zone ID
- zone-name
displays information for the specified name
- detail
displays detailed information about the specified zone
- interface
specifies the router interface
- statistics
displays statistics for the specified zone ID
Output
The following output is an example of zone information.
Output Example*A:7705:Dut-A# show security zone 1 detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
Description : NAT on public
Type : IES Service Id : 100
Policy : Inbound Policy Bypass : No
Log : SecurityLog11
Last Commit : 10/22/2015 01:07:57
===============================================================================
===============================================================================
Interfaces
===============================================================================
Name IP-Address Type Bypass Filtering
-------------------------------------------------------------------------------
ies-100-10.30.10.1 10.30.10.1 IES No Active
-------------------------------------------------------------------------------
Num of Interfaces: 1
===============================================================================
===============================================================================
Zone Queue Statistics
===============================================================================
Rx Queue CTL Packets Octets
Forwarded : 24852 54632962
Dropped : 0 0
===============================================================================
===============================================================================
Zone Policy Statistics
===============================================================================
Inbound Outbound
-------------------------------------------------------------------------------
Total Sessions Created 4 3
Action: Forward 0 0
NAT 4 3
Drop 0 0
Policy Discards
Reject Action 0 0
No Rule Matched 0 12400
===============================================================================
===============================================================================
Zone Active Session Summary
===============================================================================
Active Limit
-------------------------------------------------------------------------------
Inbound 4
TCP 1 None
UDP 2 None
ICMP 1 None
Other 0 None
Outbound 3
TCP 1 None
UDP 2 None
ICMP 0 None
Other 0 None
===============================================================================
*A:7705:Dut-A#
*A:7705:Dut-A# show security zone 1 statistics
===============================================================================
Zone Queue Statistics
===============================================================================
Rx Queue CTL Packets Octets
Forwarded : 24732 54368782
Dropped : 0 0
===============================================================================
===============================================================================
Zone Policy Statistics
===============================================================================
Inbound Outbound
-------------------------------------------------------------------------------
Total Sessions Created 4 3
Action: Forward 0 0
NAT 4 3
Drop 0 0
Policy Discards
Reject Action 0 0
No Rule Matched 0 12340
===============================================================================
===============================================================================
Zone Active Session Summary
===============================================================================
Active Limit
-------------------------------------------------------------------------------
Inbound 4
TCP 1 None
UDP 2 None
ICMP 1 None
Other 0 None
Outbound 3
TCP 1 None
UDP 2 None
ICMP 0 None
Other 0 None
===============================================================================
*A:7705:Dut-A#
nat pool
Syntax
nat pool [pool-id | pool-name] [detail]
Context
show>security>zone
Description
This command displays NAT pool information.
Parameters
- pool-id
displays detailed information for the specified zone pool ID
- pool-name
displays information for the specified zone pool name
- detail
displays detailed information about the specified pool ID
Output
The following output is an example of zone pool information.
Output Example*A-ALU-1# show security zone 1 nat pool 1 detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
===============================================================================
===============================================================================
NAT Pool
===============================================================================
Pool Id : 1 Direction : Inbound
Type : source-nat
Name : (Not Specified)
Description : Pool 1:
-------------------------------------------------------------------------------
Entry Id : 1 Direction : Inbound
IP Address : ies-100-10.30.10.1 Port : Any
-------------------------------------------------------------------------------
Num of Entries : 1
===============================================================================
*A-ALU-1#
policy
Syntax
policy [entry entry-id] [detail] [statistics]
Context
show>security>zone
Description
This command displays security zone policy information.
Parameters
- entry-id
displays detailed information for the specified entry ID
- detail
displays detailed information about the zone policy
- statistics
displays statistics for the zone policy
Output
The following output is an example of zone policy information.
Output Example*A-ALU-1# show security zone 1 policy statistics
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
===============================================================================
===============================================================================
Policy
===============================================================================
Pool Id : 1 Direction : Inbound
Type : source-nat
Name : (Not Specified)
Description : Pool 1:
-------------------------------------------------------------------------------
Entry : 1 Active : yes
Active Matches : 1 Session Limit : Any
Total Matches : 1
Entry : 2 Active : yes
Active Matches : 1 Session Limit : None
Total Matches : 1
-------------------------------------------------------------------------------
Num of Entries : 2
===============================================================================
*A-ALU-1#
session
Syntax
session [inbound | outbound] [forward | nat]
session [session-id] [detail]
session [session-id] [statistics]
Context
show>security>zone
Description
This command displays security zone session information.
The detail command shows detailed session information about the master node in a multi-chassis firewall configuration. The command does not show state, session, or time remaining information for the slave node.
Parameters
- session-id
displays detailed information for the specified session ID
- inbound
displays zone inbound sessions
- outbound
displays zone outbound sessions
- forward
displays forwarded packets
- nat
displays packets that have had NAT applied to them
- detail
displays detailed information about the zone policy
- statistics
displays statistics for the zone policy
Output
The following output is an example of zone session information.
Output Example*A-ALU-1# show security zone 1 session
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
===============================================================================
===============================================================================
Inbound Sessions
===============================================================================
Sess-Id Source Outside NAT Mapping
Proto Action From Destination
-------------------------------------------------------------------------------
00000001 NAT <Base> 10.100.0.2:161 -->10.30.10.1:5000
udp 10.100.0.2:161
00000002 NAT <Base> 10.100.0.2:21 -->10.30.10.1:5000
udp 10.100.0.2:21
-------------------------------------------------------------------------------
Num of Sessions : 2
===============================================================================
===============================================================================
Outbound Sessions
===============================================================================
Sess-Id Source Outside NAT Mapping
Proto Action To Destination
-------------------------------------------------------------------------------
No Outbound Sessions
===============================================================================
*A-ALU-1#
*A-ALU-1# show security zone 1 session 1 statistics
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
===============================================================================
===============================================================================
Session 1 Traffic Statistics
===============================================================================
Forward Reverse
-------------------------------------------------------------------------------
Passed
Packets 2042929 2042589
Octets 216550474 224684790
===============================================================================
*A-ALU-1#
A:7705:Dut-A# show security zone 1 session 6 detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : Service Inbound Zone
===============================================================================
===============================================================================
Security Session Details
===============================================================================
Session Id : 6 Action : NAT
Created : 04/11/2019 17:33:56
Protocol : UDP ALG : None
State : UDP-ESTABLISHED Session : Active
Time Remaining: -
Source : Destination :
Zone : <BASE> Zone : 1
Ip-Address : 10.100.0.2 Ip-Address : 30.100.0.2
Port : 3010 Port : 161
Session Profile
Bidirection*: Yes
CSM Inspect*: No
Fwd Policer : None
Rev Policer : None
IP
Fragments : Allowed
Options : Permit-Any
ICMP Type 3 : Restrict
Timeouts
Init : strict 15 sec
Establish*: idle 5 min
-------------------------------------------------------------------------------
Session Security Trace
-------------------------------------------------------------------------------
[INGRESS] Base:ip-10.50.10.1
[EGRESS] INBOUND-PLCY:1-2 Profile:10 Action:nat
[ACTION] SRC-NAT: 10.100.0.2:3010 -> 10.30.60.1:5000
===============================================================================
* indicates that the corresponding row element may have been truncated.
A:7705:Dut-A#
Clear Commands
ip
Syntax
ip ip-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Description
This command clears the counters associated with the IPv4 filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Default
clears all counters associated with the IPv4 filter policy entries
Parameters
- ip-filter-id
the IPv4 filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are cleared
- ingress
only the ingress counters are cleared
- egress
only the egress counters are cleared
ipv6
Syntax
ipv6 ipv6-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Description
This command clears the counters associated with the IPv6 filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Default
clears all counters associated with the IPv6 filter policy entries
Parameters
- ipv6-filter-id
the IPv6 filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are cleared
- ingress
only the ingress counters are cleared
- egress
only the egress counters are cleared
log
Syntax
log log-id
Context
clear>filter
Description
This command clears the entries associated with the specified filter log. The clear command applies only to logs whose destination is to memory.
Parameters
- log-id
the filter log ID destination expressed as a decimal integer
mac
Syntax
mac mac-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Description
This command clears the counters associated with the MAC filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Default
clears all counters associated with the MAC filter policy entries
Parameters
- mac-filter-id
the MAC filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are cleared
- ingress
only the ingress counters are cleared
- egress
only the egress counters are cleared (currently not supported on the 7705 SAR)
session
Syntax
session [session-id] [statistics]
Context
clear>security
Description
This command clears the specified sessions and can also clear the associated session statistics.
Parameters
- session-id
clears the sessions associated with the specified session ID
- statistics
clears statistics for the specified session ID
zone
Syntax
zone [zone-id | zone-name]
zone [zone-id | zone-name] sessions [inbound | outbound | all]
zone [zone-id | zone-name] statistics
Context
clear>security
Description
This command clears security zone information.
Parameters
- zone-id
specifies the zone ID
- zone-name
specifies the zone name
- sessions
removes sessions associated with the specified zone ID
- inbound
removes inbound sessions associated with the specified zone ID
- outbound
removes outbound sessions associated with the specified zone ID
- all
removes all sessions associated with the specified zone ID
- statistics
clears statistics for the specified zone ID
Monitor Commands
filter
Syntax
filter
Context
monitor
Description
This command displays monitor command output for IP and MAC filters.
ip
Syntax
ip ip-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Description
This command monitors the counters associated with the IPv4 filter policy.
Parameters
- ip-filter-id
the IPv4 filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are monitored
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
the raw statistics are displayed without processing. No calculations are performed on the delta or rate statistics.
- rate
the rate per second for each statistic is displayed instead of the delta
ipv6
Syntax
ipv6 ipv6-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Description
This command monitors the counters associated with the IPv6 filter policy.
Parameters
- ipv6-filter-id
the IPv6 filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are monitored
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
the raw statistics are displayed without processing. No calculations are performed on the delta or rate statistics.
- rate
the rate per second for each statistic is displayed instead of the delta
mac
Syntax
mac mac-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Description
This command monitors the counters associated with the MAC filter policy.
Parameters
- mac-filter-id
the MAC filter policy ID or filter name
- entry-id
only the counters associated with the specified filter policy entry are monitored
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
the raw statistics are displayed without processing. No calculations are performed on the delta or rate statistics.
- rate
the rate per second for each statistic is displayed instead of the delta