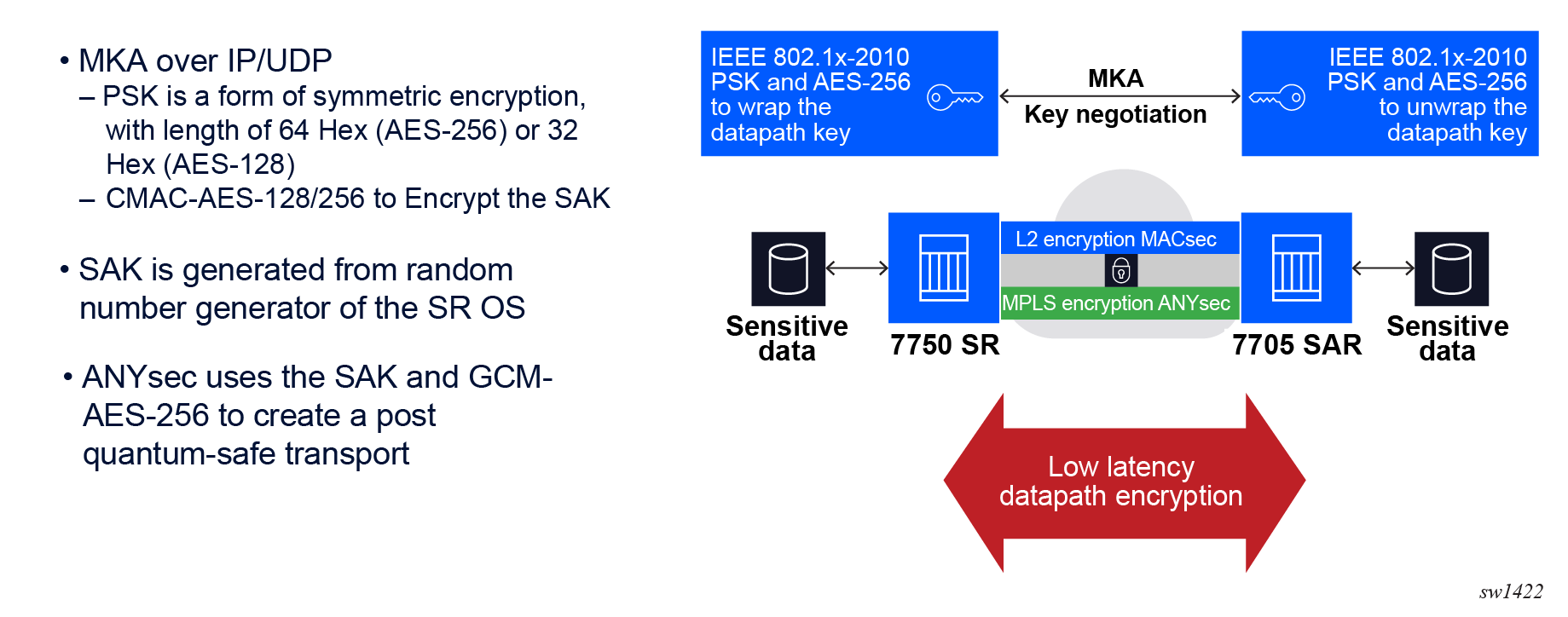
ANYsec overview
Nokia ANYsec uses the IEEE 802.1AE (MACsec) standard in its datapath encryption engine and IEEE 802.1x (dot1x/MKA) as its control plane signaling protocol. ANYsec uses the user-configured MACsec connectivity association (CA) with a set of pre-shared keys (PSKs), the same way MACsec does, to negotiate datapath keys between two or more peers.
The following is a high-level overview of the ANYsec encryption process.
1. The user configures the ANYsec-specific CA, which supports the exclusive use of the CA with ANYsec encryption.
config>macsec>connectivity-association>anysec
2. The MACsec key agreement (MKA) key server generates the datapath security association keys (SAKs) locally on the 7705 SAR. The user configures the key-server selection priority using the mka-key-server-priority command.
3. The MKA uses CMAC-AES-128/256 to encrypt the SAKs using PSK and distributes the SAKs.
4. ANYsec modifies the MKA for transport over IP/UDP (described in more detail in later topics). MKA distributes the SAKs between peers, and ANYsec uses the SAKs to encrypt and decrypt the MPLS payload via the IEEE 802.1AE standard using the encryption engine.
The following figure shows a high-level implementation of ANYsec in a network.