7210 SAS interfaces
This chapter provides information about configuring chassis slots, cards, and ports.
Configuration overview
This document uses the term preprovisioning in the context of preparing or preconfiguring entities such as chassis slots, media dependent adapters (MDAs), ports, and interfaces, before initialization. These entities can be installed but not enabled. When the entity is in a no shutdown state (administratively enabled), the entity is considered to be provisioned.
The 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C and the variants are platforms with a fixed port configuration, and no expansion slots. The 7210 SAS software inherits the concept of CPM, IOM and MDA from the 7750 SR to represent the hardware logically. These components are fixed and are not removable. The software creates two logical cards to represent the CPM and IOM and these are preprovisioned on boot-up. The IOM card is modeled with a single MDA, a logical entity to represent the fixed ports on the system. This MDA is auto-provisioned on boot-up and the user does not need to provision it. Ports and interfaces can also be preprovisioned.
Chassis slots and cards
The 7210 SAS-D supports the following ports:
6 ✕ 10/100/1000 SFP ports
4 ✕ 10/100/1000 Base-T ports
1 management console port
The 7210 SAS-Dxp supports the following ports:
2 ✕ 1GE/10GE SFP+ ports
6 ✕ 10/100/1000 Base-T ports
4 ✕ 100/1000 SFP ports
1 management console port
The 7210 SAS-K 2F1C2T supports the following ports:
2 ✕ 10/100/1000 Base-T fixed copper ports
1 management console port
The 7210 SAS-K 2F6C4T supports the following ports:
2 ✕ 100/1000 SFP ports
4 ✕ 10/100/1000 Base-T fixed copper ports
6 Combo ports (100/1000 SFP or 10/100/1000 Base-T)
1 management console port
The 7210 SAS-K 3SFP+ 8C ports supports the following ports:
3 ✕ 10GE SFP+ ports
8 Combo ports (100/1000 SFP or 10/100/1000 Base-T)
1 management console port
The 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C have a set of fixed ports. The software preprovisions the cards on bootup.
The show card command lists the cards auto-provisioned on 7210 SAS platforms.
The following show card sample output lists the cards auto-provisioned on the 7210 SAS-D.
A:dut-b#
show card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
A:dut-b#
The following show card sample output lists the cards auto-provisioned on the 7210 SAS-Dxp.
A:dut-m#
show card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
A:dut-m#
The following show card sample output lists the cards auto-provisioned on the 7210 SAS-K 2F1C2T.
A:dut-i#
show card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
A:dut-i#
The following show card sample output lists the cards auto-provisioned on the 7210 SAS-K 2F6C4T:
A:dut-k#
show card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
A:dut-k#
The following show card sample output lists the cards auto-provisioned on the 7210 SAS-K 3SFP+ 8C.
A:dut-l#
show card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
A:dut-l#
Digital Diagnostics Monitoring
Some Nokia SFPs, XFPs, and the MSA DWDM transponder support the Digital Diagnostics Monitoring (DDM) capability, which allows the transceiver module to maintain information about its working status in device registers, including:
temperature
supply voltage
transmit (Tx) bias current
Tx output power
received (Rx) optical power
The optical transceiver DDM feature provides real-time values for guidance. For the specific values, the optical power data provides an accuracy of ±3 dB or better. The accuracy of this data is defined in the relevant standard for the transceiver type, such as SFF-8472 for SFP+. Use an optical power meter where precise optical power data is required. Contact your Nokia technical support representative for further assistance or clarification.
The transceiver is also programmed with warning and alarm thresholds for low and high conditions that can generate system events. These thresholds are programmed by the transceiver manufacturer.
No CLI command configuration is required to support DDM operations. However, the show port port-id detail command displays DDM information in the Transceiver Digital Diagnostics Monitoring output section.
The Tx and Rx power displayed in the DDM output are average optical power in dBm.
DDM information is populated into the router MIBs, so the DDM data can be retrieved by Network Management using SNMP. Also, RMON threshold monitoring can be configured for the DDM MIB variables to set custom event thresholds if the factory-programmed thresholds are not at the wanted levels.
The following are potential uses of the DDM data:
optics degradation monitoring
With the information returned by the DDM-capable optics module, degradation in optical performance can be monitored and trigger events based on custom or the factory-programmed warning and alarm thresholds.
link/router fault isolation
With the information returned by the DDM-capable optics module, any optical problem affecting a port can be quickly identified or eliminated as the potential problem source.
The following table describes supported real-time DDM features.
Parameter |
User units |
SFP/XFP units |
SFP |
XFP |
MSA DWDM |
|---|---|---|---|---|---|
Temperature |
Celsius |
C |
Supported |
Supported |
Supported |
Supply Voltage |
Volts |
µV |
Supported |
Supported |
Not supported |
TX Bias Current |
mA |
µA |
Supported |
Supported |
Supported |
TX Output Power |
dBm (converted from mW) |
mW |
Supported |
Supported |
Supported |
RX Received Optical Power4 |
dBm (converted from dBm) (Avg Rx Power or OMA) |
mW |
Supported |
Supported |
Supported |
AUX1 |
parameter dependent (embedded in transceiver) |
- |
Not supported |
Supported |
Not supported |
AUX2 |
parameter dependent (embedded in transceiver) |
- |
Not supported |
Supported |
Not supported |
The following table describes supported factory-programmed DDM alarms and warnings.
Parameter |
SFP/XFP units |
SFP |
XFP |
Required? |
MSA DWDM |
|---|---|---|---|---|---|
Temperature - High Alarm - Low Alarm - High Warning - Low Warning |
C |
Yes |
Yes |
Yes |
Yes |
Supply Voltage - High Alarm - Low Alarm - High Warning - Low Warning |
µV |
Yes |
Yes |
Yes |
No |
TX Bias Current - High Alarm - Low Alarm - High Warning - Low Warning |
µA |
Yes |
Yes |
Yes |
Yes |
TX Output Power - High Alarm - Low Alarm - High Warning - Low Warning |
mW |
Yes |
Yes |
Yes |
Yes |
RX Optical Power - High Alarm - Low Alarm - High Warning - Low Warning |
mW |
Yes |
Yes |
Yes |
Yes |
AUX1 - High Alarm - Low Alarm - High Warning - Low Warning |
parameter dependent (embedded in transceiver) |
No |
Yes |
Yes |
No |
AUX2 - High Alarm - Low Alarm - High Warning - Low Warning |
parameter dependent (embedded in transceiver) |
No |
Yes |
Yes |
No |
SFPs and XFPs
The availability of the DDM real-time information and the warning and alarm status is based on the transceiver. The transceiver may or may not indicate that DDM is supported. Although some Nokia SFPs support DDM, Nokia SFPs support DDM releases later than Release 2.0. Contact a Nokia technical support representative for more information about DDM support for specific 7210 SAS releases. Non-DDM and DDM-supported SFPs are distinguished by a specific value in their EEPROM.
Although DDM data may be available for SFPs that do not indicate DDM support in their EEPROM, Nokia has not validated or verified the accuracy of this information.
DDM information can be displayed for non-Nokia transceivers, but Nokia is not responsible for the formatting, accuracy, and other informational details.
Statistics collection
The DDM information and warnings/alarms are collected at one minute intervals, so the minimum resolution for any DDM events when correlating with other system events is one minute.
In the Transceiver Digital Diagnostic Monitoring section of the show port port-id detail command output:
If the present measured value is higher than the either or both High Alarm, High Warn thresholds; an exclamation mark ‟!” displays along with the threshold value.
If the present measured value is lower than the either or both Low Alarm, Low Warn thresholds; an exclamation mark ‟!” displays along with the threshold value.
B:SR7-101# show port 2/1/6 detail
......
===============================================================================
Transceiver Digital Diagnostic Monitoring (DDM), Internally Calibrated
===============================================================================
Value High Alarm High Warn Low Warn Low Alarm
-------------------------------------------------------------------------------
Temperature (C) +33.0+98.0 +88.0 -43.0-45.0
Supply Voltage (V) 3.31 4.12 3.60 3.00 2.80
Tx Bias Current (mA)5.7 60.0 50.00.1 0.0
Tx Output Power (dBm) -5.45 0.00 -2.00 -10.50 -12.50
Rx Optical Power (avg dBm) -0.65-3.00! -4.00! -19.51 -20.51
===============================================================================
Ports
This section describes 7210 SAS ports.
Port types
The following table lists supported Ethernet port types on the 7210 SAS platforms.
7210 SAS platforms |
Copper ports (10/100/1000 Base-T) |
Ethernet SFP ports |
10 Gigabit SFP+ ports |
|---|---|---|---|
7210 SAS-D |
✓ |
✓ |
|
7210 SAS-Dxp |
✓ |
✓1 |
✓ |
7210 SAS-K 2F1C2T |
✓ |
✓ |
|
7210 SAS-K 2F6C4T |
✓ |
✓ |
|
7210 SAS-K 3SFP+ 8C |
✓ |
✓ |
✓ |
Port modes
On 7210 SAS devices, a port must be configured as one of the following: access, access uplink, network, or hybrid. The following list describes the significance of the different port modes and the support available on different platforms:
access ports
Access ports are configured for customer-facing traffic on which services are configured. If a Service Access Port (SAP) is to be configured on the port, it must be configured as an access port. When a port is configured for access mode, the appropriate encapsulation type must be configured to distinguish the services on the port. When a port has been configured for access mode, one or more services can be configured on the port depending on the encapsulation value.
access-uplink ports
Access-uplink ports are used to provide native Ethernet connectivity in service provider transport or infrastructure network. This can be achieved by configuring port mode as access uplink. With this option, the encap-type can be configured to QinQ only. Access-uplink SAPs, which are QinQ SAPs, can only be configured on an access uplink port to allow the operator to differentiate multiple services being carried over a single access uplink port.
network ports (applicable only to the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C)
Network ports are configured for network-facing traffic. These ports participate in the service provider transport or infrastructure network. Dot1q is supported on network ports.
hybrid ports (applicable only to the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C)
Hybrid ports are configured for access and network-facing traffic. The default mode of an Ethernet port is ‟network”. The mode of a port cannot be changed unless the port is shut down and the configured SAPs and interfaces are deleted. Hybrid ports allow a single port to operate in both access and network modes. The MTU of a port in hybrid mode is the same as in network mode. The default encapsulation for ports in hybrid mode is dot1q; QinQ encapsulation is also supported at the port level.
When the port is changed to hybrid, the default MTU of the port is changed to match the value of 9212 bytes, which is used in network mode (higher than in access mode); this ensures that both SAP and network VLANs can be accommodated.
The only exception is when the port is a 10/100 fast Ethernet port. In this case, the MTU in hybrid mode is set to 1522 bytes, which corresponds to the default access MTU with QinQ, which is larger than the network dot1q MTU or access dot1q MTU for this type of Ethernet port. All parameters in access and network contexts are configured within the port using the same CLI hierarchy as in the existing implementation. A hybrid port allows both ingress and egress contexts to be configured concurrently.
An Ethernet port configured in hybrid mode can have the following encapsulation type values: dot1q and QinQ. The NULL value is not supported because only a single SAP or network IP interface is allowed, achieved by configuring the port as either access or network, respectively. Hybrid mode can be enabled on a LAG port when the port is part of a single chassis LAG configuration. When the port is part of a multi-chassis LAG (MC-LAG) configuration, only access mode can be configured. MC-LAG is not supported on network ports and consequently cannot be supported on hybrid ports.
The following table describes supported port modes on the 7210 SAS platforms.
Port mode platforms |
Access |
Network |
Hybrid |
Access-uplink |
|---|---|---|---|---|
7210 SAS-D |
Yes |
No |
No |
Yes |
7210 SAS-Dxp |
Yes |
No |
No |
Yes2 |
7210 SAS-K 2F1C2T |
Yes |
No |
No |
Yes |
7210 SAS-K 2F6C4T |
Yes |
Yes |
Yes |
Yes |
7210 SAS-K 3SFP+ 8C |
Yes |
Yes |
Yes |
Yes |
Port dot1q VLAN Etype on 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
The 7210 SAS supports an option to allow the user to use a different dot1q VLAN Ethernet Type (Etype). It allows for interoperability with third-party switches that use some non-standard (other than 0x8100) dot1q VLAN Etype.
Configuration guidelines for dot1q-Etype for 7210 SAS-D and 7210 SAS-Dxp
The following are the configuration guidelines for Dot1q-Etype configured for dot1q encap port on 7210 SAS-D and 7210 SAS-Dxp:
Dot1q-Etype configuration is supported for all ports - Access and Access-uplink ports.
Dot1q-preserve SAPs cannot be configured on dot1q encap ports configured to use ether type other than 0x8100.
Priority tagged packet received with Etype 0x8100 on a dot1q port configured with Etype 0x9100 are classified as priority tagged packet and mapped to a dot1q :0 SAP (if configured) and the priority tag is removed.
Priority tagged packets received with Etype 0x6666 (any value other than 0x8100) on a dot1q port configured with Etype 0x9100 is classified as null-tagged packet and mapped to a dot1q :0 SAP (if configured) and the priority tag is retained and forwarded.
The dot1q-Etype is modified only for the dot1q encap access port.
Support for power over Ethernet
Power over Ethernet (PoE) is supported only on the 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p.
The 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p support PoE in accordance with the 802.3af, 802.3at, and 802.3bt standards. This feature allows these platforms to supply power to connected PoE devices, such as telephones, CCTV cameras, and other PoE standard compliant devices.
The following PoE functionalities are available:
The 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p support 802.3af (PoE), 802.3at (PoE+), and 802.bt (PoE++ and HPoE). All ports support PoE and PoE+. only the first four copper ports support PoE++ and HPoE. The ports can be used to connect PoE, PoE+, PoE++, or HPoE devices, or a combination of both simultaneously, as long as the power drawn is within the device system limits.
Only Alternative A, as described in the 802.3af and 802.3at standards, is supported on the 7210 SAS.
The 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p support classification Type 1, Type 2, Type 3, and Type 4 PoE devices (PDs) using the physical layer classification mechanism. The physical layer classification mechanism supports both the single-signature and dual-signature classification mechanisms.
The user must configure the maximum available PoE power budget using the configure system poe max-poe-power-budget command before enabling PoE on any of the ports. See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide for more information about this command.
The 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p support the PoE type and class-based power allocation method, which allocates power based on the identified PoE type and class using a physical layer classification mechanism. The 802.3af, 802.3at, and 802.3bt standards define four PoE types (Type 1 (up to 15W, Type 2 (up to 30 W), Type 3 (up to 60W), and Type 4 (up to 90 W)) and the power that can be allocated or requested by a particular class. The standards define eight classes: Class 1, Class 2, Class 3, Class 4, Class 5, Class 6, Class 7, and Class 8. These classes are used to allow PoE devices to request power based on their needs. If there is not enough power available to supply the identified class, power is denied to the connected PoE device. Each 7210 SAS device has a limit on the maximum amount of power it can provide. If the total power requested by the PDs connected to PoE-enabled ports exceeds this threshold, the 7210 SAS device denies power to the other PD. When power is denied to the PD, the port is operationally up, even though power is not supplied to the port. If power is applied successfully or denied to the port, the system logs an event.
Note:The software accounts for power requirements based on the PD type and does not consider the PoE class within a type (a PoE device uses 15 W, a PoE+ device uses 30 W, a PoE++ device uses 60 W, and a HPoE device uses 90 W).
For example, if the user configures one PoE port, the software deducts 15 W from the configured max-poe-power-budget. If the user configures two PoE ports and two PoE + ports, the software deducts 90 W from the configured max-poe-power-budget (assuming the configured value is greater than or equal to 90 W). If the user configures a value of 100 W and attempts to configure four PoE+ ports, the software deducts 30 W from the configured max-poe-power-budget for the first three configured PoE+ ports using a total of 90 W (10 W are remaining). When the user configures the fourth port, the configuration fails because only 10 W are available, which does not meet the power requirement for the fourth PoE+ port.
Only DC power is supplied to connected PDs. It is supported for PDs that use injectors where an AC/DC wall device is used to power a remote PoE device.
The software monitors the PoE port, detects faults and events, and raises traps. The software displays this information in the status report. The following events and faults are detected and are notified to the user:
supplying power event
This event is generated when power is supplied to a connected PoE device after successful detection and classification.
denied power event
This event is generated when power is denied to a connected PoE device after successful detection and classification.
disconnect event
This event is generated when a connected PoE device is disconnected from the port and stops drawing power from the node.
fault events
These events are generated for overload, short-circuit, and other events. Software clears the fault when the fault no longer exists.
If a port enabled for PoE is shut down, the power supplied to the port is disabled. It restores power when the no shutdown command is executed, if the request does not exceed the power budget.
PoE configuration notes
The following configuration notes apply for PoE:
On the 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p, all ports are available to connect PoE and PoE+ devices, and up to four fixed copper ports are available to connect PoE++ and HPoE devices.
The 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p can be equipped with the following external power module types to support required PoE devices:
100 W AC
290 W DC
480 W AC
960 W AC
The user can configure the maximum power budget for PoE devices using the config>system>poe>max-poe-power-budget command. See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide for more information about this command.
MACsec
- Media Access Control Security (MACsec) is supported only on the 7210 SAS-K 2F6C4T ETR, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p.
- On the 7210 SAS-Dxp 24p, MACsec is available on four ports:
- 1 GE SFP ports 1/1/19 and 1/1/20
- 1/10 GE SFP+ ports 1/1/17 and 1/1/18
MACsec is a security technology that provides secure communication for almost all types of traffic on Ethernet links. MACsec provides point-to-point and point-to-multipoint security on Ethernet links between directly connected nodes, or nodes connected using a Layer 2 cloud.
MACsec can identify and prevent most security threats, including:
denial of service
intrusion
man-in-the-middle
masquerading
passive wiretapping
playback attacks
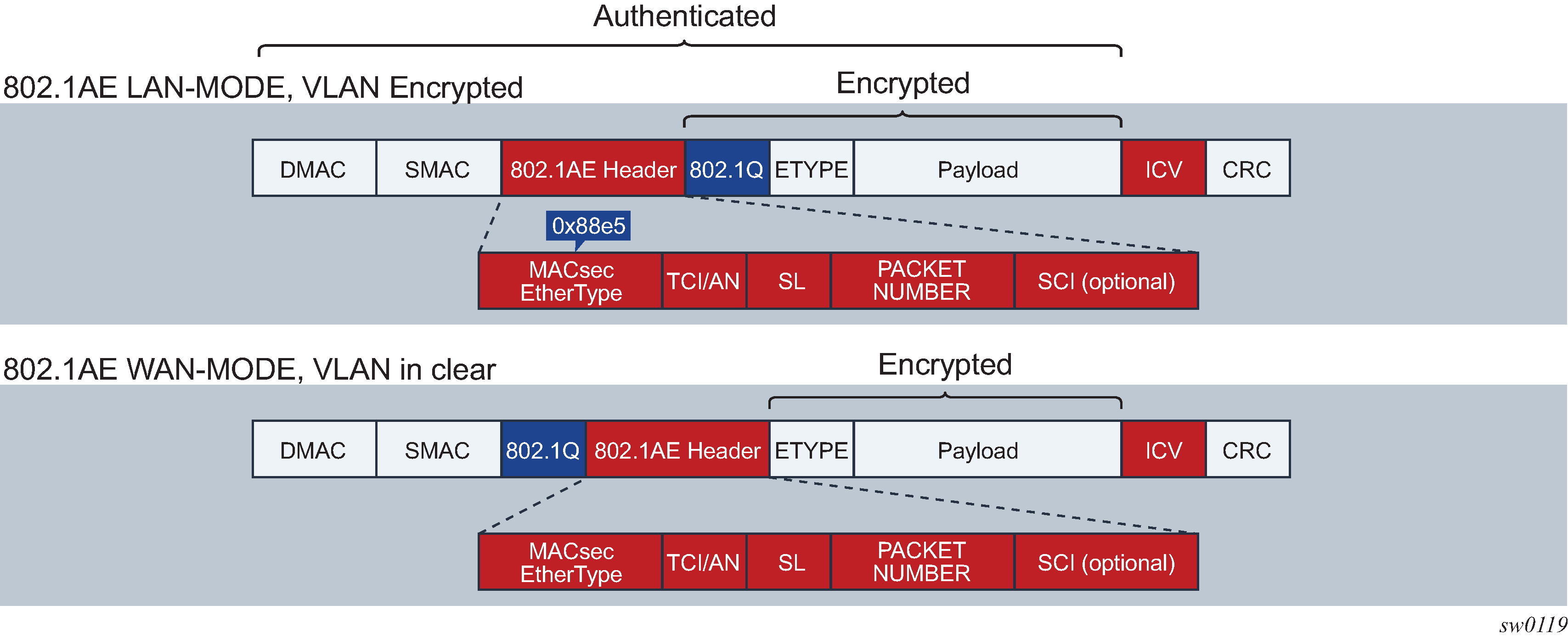
MACsec, defined in IEEE 802.1AE, uses Layer 2 to encrypt MACsec to encrypt anything from the 802.1AE header to the end of the payload, including 802.1Q. MACsec leaves the DMAC and SMAC in cleartext.
The following figure shows the 802.1AE LAN-mode structure.

Forwarding a MACsec packet uses the destination MAC address, which is in cleartext.
MACsec 802.1AE header (SecTAG)
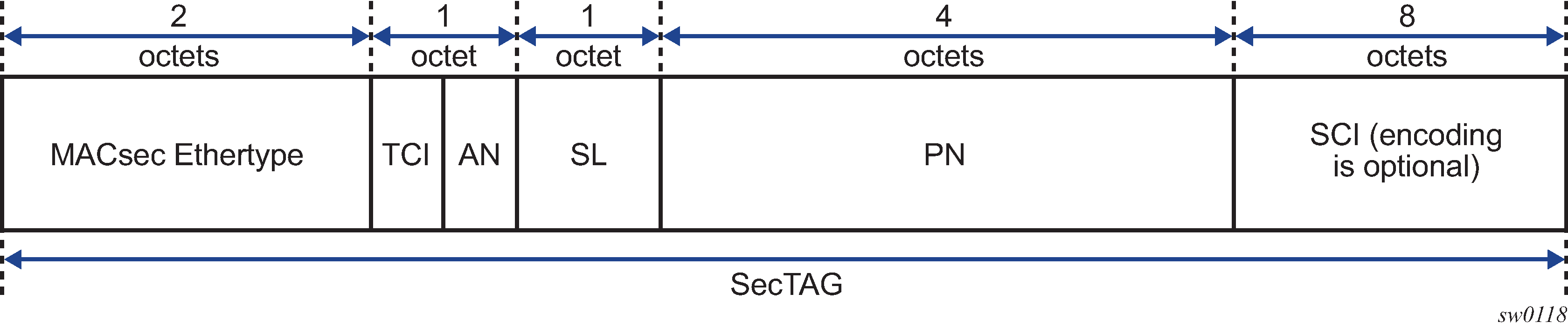
The 802.1AE header has a security tag (SecTAG) which includes:
the association number within the channel
the packet number to provide a unique initialization vector for encryption and authentication algorithms, as well as protection against replay attack
an optional LAN-wide secure channel identifier
The SecTAG is identified by the MACsec Ethertype and includes the following fields:
TAG Control Information (TCI)
Association Number (AN)
Short Length (SL)
Packet Number (PN)
Optionally-encoded Secure Channel Identifier (SCI)
The following figure shows the format of the SecTAG.
MACsec encryption mode
MACsec uses the following main modes of encryption:
VLAN in cleartext (WAN Mode)
VLAN encrypted
The 802.1AE standard requires that the 802.1Q VLAN is encrypted. Some vendors provide the option of configuring MACsec on a port with VLAN in cleartext form. The 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p support both modes on both 1GE and 10GE ports.
The following figure shows VLAN in encrypted and cleartext form.
MACsec encryption per traffic flow encapsulation matching
MACsec can be applied to a selected subset of the port traffic based on the type and value of the packet encapsulation. The user can configure the system to match and encrypt all encapsulated traffic arriving on a port, including untagged, single-tagged, and double-tagged. This is the default behavior of MACsec and the only option supported.
MKA PDUs are generated specifically for the matched traffic encapsulation type.
MACsec terminology
The following table describes MACsec terminology.
MACsec term |
Description |
|---|---|
Connectivity Association (CA) |
A security relationship, established and maintained by the MKA, that comprises a fully connected subset of the service access points in stations attached to a single LAN that are to be supported by MACsec. |
MACsec Key Agreement Protocol (MKA) |
Control protocol between MACsec peers, which is used for peer aliveness and encryption key distribution. MKA is responsible for discovering, authenticating, and authorizing the potential participants in a CA. |
MAC Security Entity (SecY) |
Operates the MAC security protocol within a system. Manages and identifies the SC and the corresponding active SA. |
Port Access Entity (PAE) |
The protocol entity associated with a port. May support the functionality of authenticator, supplicant, or both. |
Security Channel (SC) |
Provides a unidirectional point-to-point or point-to-multipoint communication. Each SC contains a succession of SAs, and each SC has a different SAK. |
Security Association Key (SAK) |
The key used to encrypt the datapath of MACsec. |
Security Association (SA) |
A security relationship that provides security guarantees for frames transmitted from one member of a CA to the others. In the case of two SAs per SC, each with a different SAK, each SC comprises a succession of SAs. Each SA has an SC identifier, concatenated with a two-bit association number. The Secure Association Identifier (SAI) that has been created allows the receiving SecY to identify the SA, and consequently, the SAK used to decrypt and authenticate the received frame. The AN (and the SAI) is only unique for the SAs that can be used or recorded by participating SecYs at any time. The MKA creates and distributes SAKs to each of the SecYs in a CA. This key creation and distribution is independent of the cryptographic operation of each of the SecYs. The decision to replace one SA with its successor is made by the SecY that transmits using the SC, after the MKA has informed it that all the other SecYs are prepared to receive using that SA. No notification, other than receipt of a secured frame with a different SAI, is sent to the receiver. A SecY must always be capable of storing SAKs for two SAs for each inbound SC, and of swapping from one SA to another without notice. Certain LAN technologies can reorder frames of different priority, so reception of frames on a single SC can use interleaved SA. |
MACsec key management modes
The following table describes the key management modes in MACsec.
Keying |
Explanation |
SR OS support |
Where used |
|---|---|---|---|
Static Secure Association Key (SAK) |
Manually configures each node with a static SAK using CLI or NSP. |
N/A |
Switch to switch |
Static Connectivity Association Key (CAK) preshared key |
Uses dynamic MACsec Key Agreement (MKA) and uses a configured pre-shared key to derive the CAK. The CAK encrypts the SAK between two peers and authenticates the peers. |
Supported |
Switch to switch |
Dynamic CAK EAP Authentication |
Uses dynamic MKA and an EAP Master System Key (MSK) to derive the CAK. The CAK encrypts the SAK between two peers and authenticates the peers. |
Not Supported |
Switch to switch |
Dynamic CAK MSK Distribution via RADIUS and EAP-TLS |
MSKs are stored in the RADIUS server and distributed to the hosts via EAP-TLS. This is typically used in access networks where there are a large number of hosts using MACsec and connecting to an access switch. MKA uses MSK to derive the CAK. The CAK encrypts the SAK between 2 peers and authenticates the peers. |
Not Supported |
Host to switch |
MACsec static CAK
The following figure shows the main MACsec concepts used in the static CAK scenario.
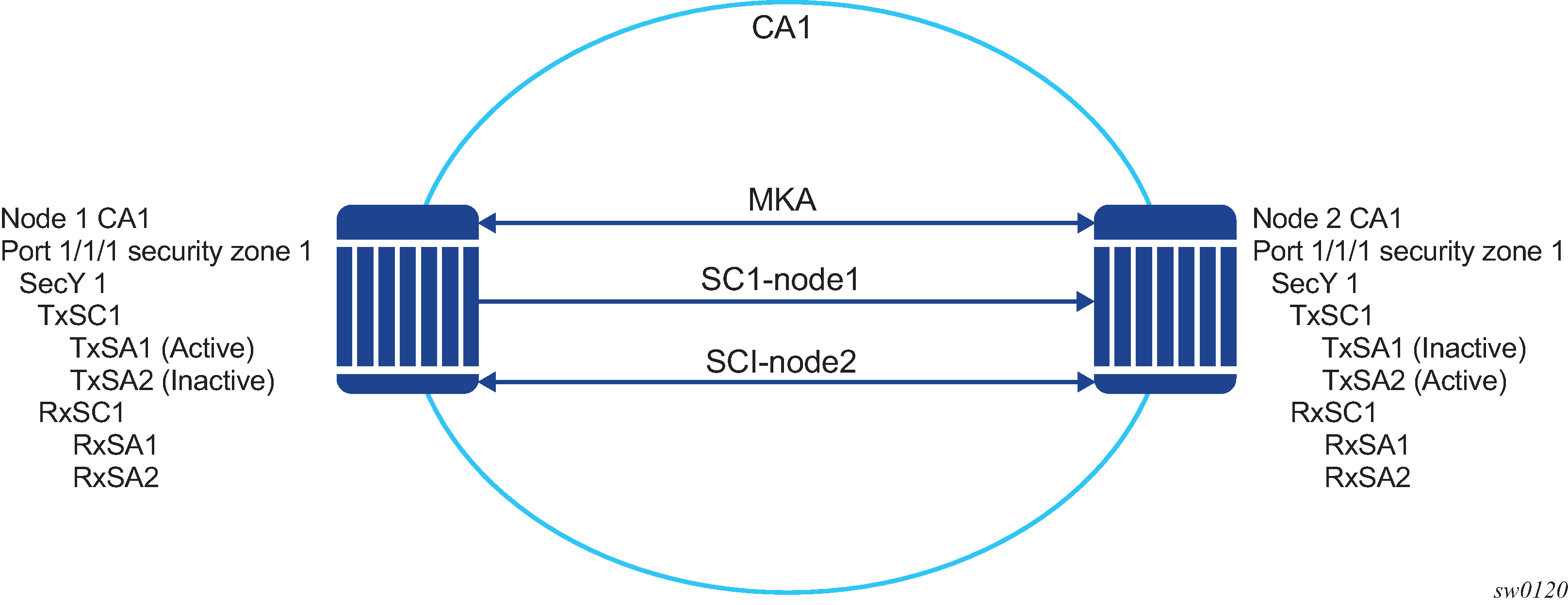
MACsec uses SAs to encrypt packets. Each SA has a single SAK that contains the cryptographic operations used to encrypt the datapath PDUs.
The SAK is the secret key used by an SA to encrypt the channel.
When enabled, MACsec uses a static CAK security mode, which has two security keys: a CAK that secures control plane traffic and a randomly generated SAK that secures data plane traffic. Both keys are used to secure the point-to-point or point-to-multipoint Ethernet link and are regularly exchanged between devices on each end of the Ethernet link.
The following figure shows MACsec generating the CAK.
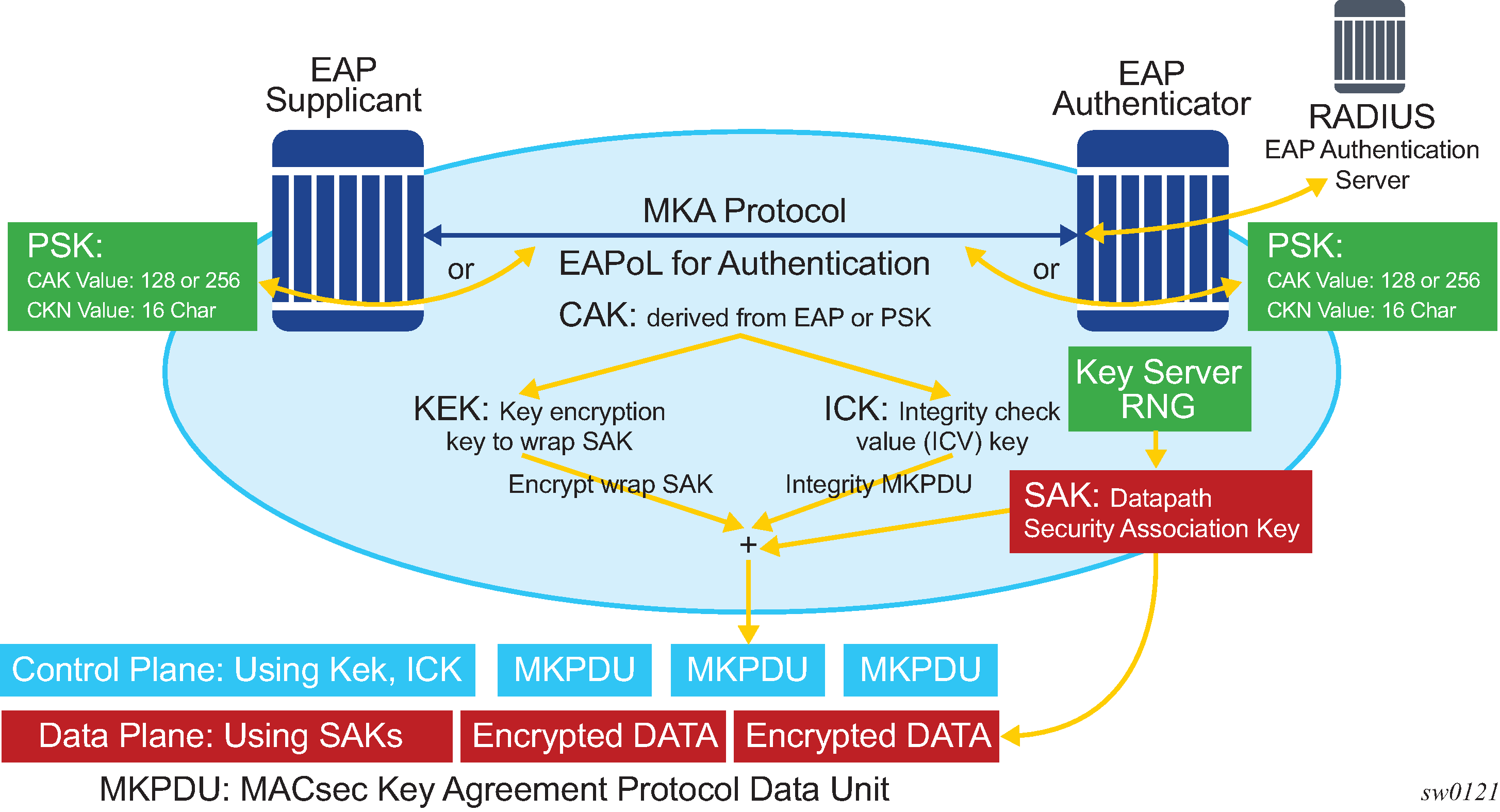
The node initially needs to secure the control plane communication to distribute the SAKs between two or more members of a CA domain.
The control plane is secured using a CAK, which is generated using one of the following methods:
EAPoL
preshared key
(CAK and CKN values are configured using the CLI). The following CAK and CKN rules apply.
CAK uses 32 hexadecimal characters for a 128-bit key, and 64 hexadecimal characters for a 256-bit key, depending on the algorithm used for control plane encryption; for example, aes-128-cmac or aes-256-cmac.
CKN is a 32-octet character (64 hex) and is the name that identifies the CAK. This allows each of the MKA participants to select which CAK to use to process a received MKPDU. MKA places the following restrictions on the format of the CKN:
it must comprise an integral number of octets, between 1 and 32 (inclusive)
all potential members of the CA must use the same CKN
CAK and CKN must match on peers to create a MACsec-secure CA.
The following figure shows MACsec control plane authentication and encryption.
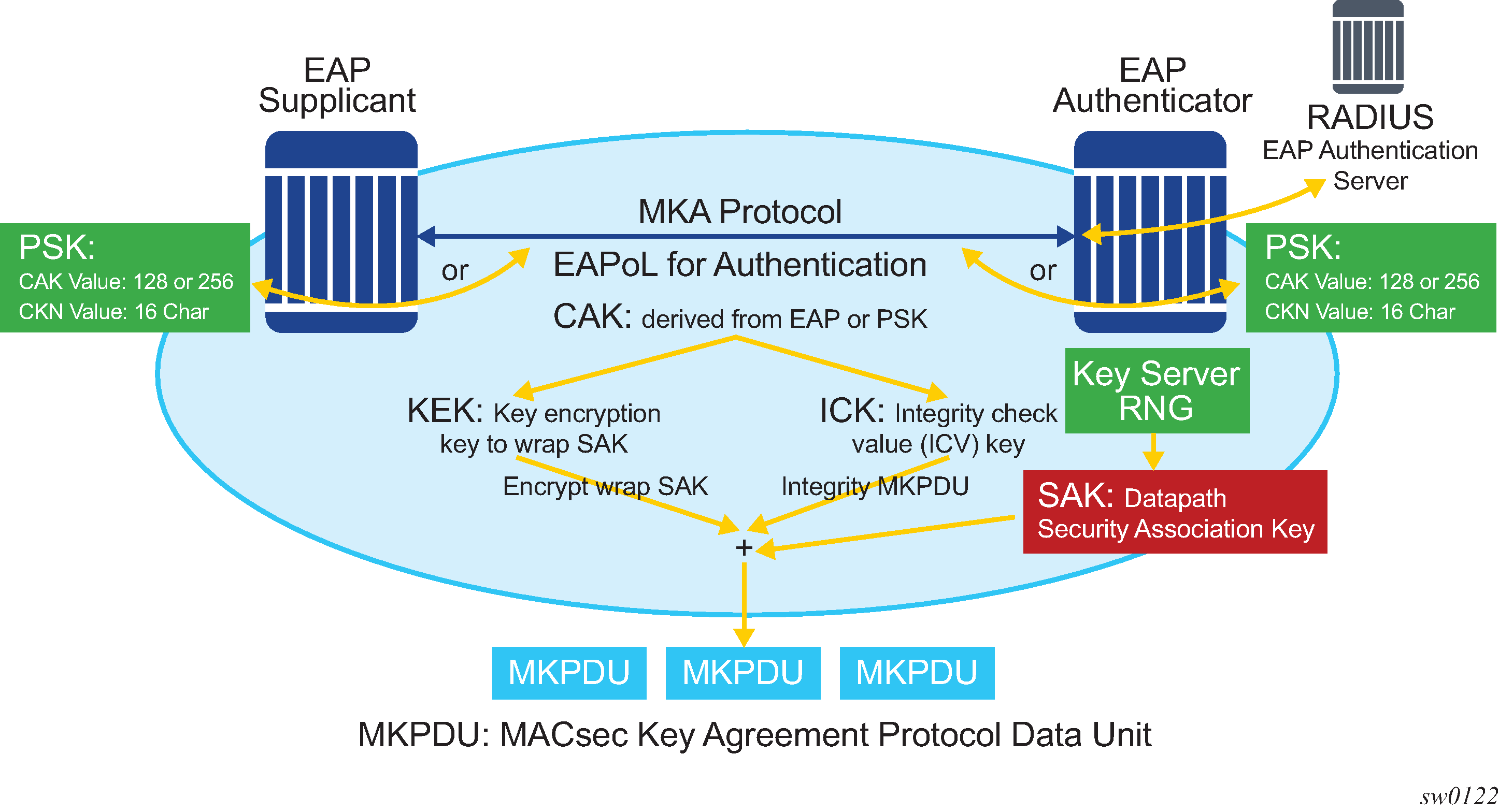
After the CAK is generated, it can obtain the following additional keys:
KEK (Key Encryption Key)
The KEK is used to wrap and encrypt the SAKs.
ICK (Integrity Connection Value (ICV) Key)
The ICK is used for an integrity check of each MKPDU send between two CAs.
The key server then creates a SAK and shares it with the CAs of the security domain, and that SAK secures all data traffic traversing the link. The key server periodically creates and shares a randomly created SAK over the point-to-point link for as long as MACsec is enabled.
The SAK is encrypted using the AES-CMAC, the KEK as the encryption key, and ICK as the integration key.
SAK rollover
The SAK is regenerated after the following events:
when a new host has joined the CA domain and MKA hellos are received from this host
when the sliding window is reaching the end of its 32-bit or 64-bit length
when a new PSK is configured and a rollover of PSK is executed
MKA
Each MACsec peer operates the MKA. Each node can operate multiple MKAs based on the number of CAs that it belongs to. Each instance of MKA is protected by a distinct secure CAK, that allows each Port Access Entity (PAE), or port, to ensure that information for a specific MKA instance is accepted only from other peers that also possess that CAK, therefore identifying themselves as members or potential members of the same CA. For a description of how the CAK identification is performed using CKN, see MACsec static CAK.
MKA PDU generation
The following table describes the MKA PDUs generated for different traffic encapsulation matches.
|
Configuration |
Configuration example (<s-tag>.<c-tag>) |
MKA packet generation |
Traffic pattern match/behavior |
Supported on 7210 SAS |
|---|---|---|---|---|
|
All-encap |
|
untagged MKA packet |
Matches all traffic on port, including untagged, single-tag, and double-tag. Default behavior. |
Yes |
|
UN-TAG |
|
untagged MKA packet |
Matches only untagged traffic on port |
No |
|
802.1Q single S-TAG (specific S-TAG) |
|
MKA packet generated with S-TAG=1 |
Matches only single-tag traffic on port with tagID of 1 |
No |
|
802.1Q single S-TAG (any S-TAG) |
|
untagged MKA packet |
Matches any dot1q single-tag traffic on port |
No |
|
802.1ad double tag (both tag have specific TAGs) |
|
MKA packet generated with S-tag=1 and C-TAG=1 |
Matches only double-tag traffic on port with service tag of 1 and customer tag of 1 |
No |
|
802.1ad double tag (specific S-TAG, any C-TAG) |
|
MKA packet generated with S-TAG=1 |
Matches only double-tag traffic on port with service tag of 1 and customer tag of any |
No |
|
802.1ad double tag (any S-TAG, any C-TAG) |
|
untagged MKA packet |
Matches any double-tag traffic on port |
No |
Tags in clear behavior by traffic encapsulation types
By default, all tags are encrypted in CA. An MKA can be generated without any tags (untagged), but the data being matched can be based on dot1q or q-in-q.
The following table describes how single or double tags in clear configuration under a CA affect different traffic flow encryptions.
Configuration |
Traffic pattern match/behavior |
CA configuration: no tag in cleartext form |
CA configuration: single-tag in cleartext form |
CA configuration: double-tag in cleartext form |
|---|---|---|---|---|
Port |
Matches all traffic on port, including untagged, single-tagged, double-tagged (default behavior) |
MKA PDU: untagged Untagged traffic: encrypted Single-tagged traffic: encrypted, no tag in clear Double-tagged traffic: encrypted, no tag in clear |
MKA PDU: untagged Untagged traffic: in clear Single-tagged traffic: encrypted, single-tag in clear Double-tagged traffic: encrypted, single-tagged in clear |
MKA PDU: untagged Untagged traffic: in clear Single-tagged traffic: in clear Double-tagged traffic: encrypted, double-tagged in clear |
PSK
A peer may support the use of one or more preshared keys (PSKs). An instance of MKA operates for each PSK that is administratively configured as active.
A preshared key is either created by NSP or configured using the CLI. Each PSK is configured using the following fields:
CKN
CAK value
The CKN must be unique for each port among the configured sub-ports, and can be used to identify the key in subsequent management operations.
Each static CAK configuration can have two preshared key entries for rollover. The active PSK index dictates which CAK is being used for encrypting the MKA PDUs.
NSP has additional functionality to rollover and configure the PSK. The rollover using NSP can be based on a configured timer.
MKA hello timer
MKA uses a member identifier (MI) to identify each node in the CA domain.
A participant proves liveness to each of its peers by including the MI, together with an acceptably recent message number (MN), in an MKPDU.
To avoid a new participant having to respond to each MKPDU from each partner as it is received, or trying to delay its reply until it is likely that MI MN tuples have been received from all potential partners, each participant maintains and advertises both a live peers list and a potential peers list.
The live peers list includes peers that have included the participant MI and a recent MN in a recent MKPDU. The potential peers list includes all other peers that have transmitted an MKPDU that has been directly received by the participant or that were included in the live peers list of a MKPDU transmitted by a peer that has proved liveness. Peers are removed from each list when an interval of between MKA lifetime and MKA lifetime plus MKA Hello Time has elapsed since the participant's recent MN was transmitted. This time is sufficient to ensure that two or more MKPDUs will have been lost or delayed before the incorrect removal of a live peer.
The specified use of the live peers and potential peers lists allows rapid removal of participants that are no longer active or attached to the LAN, while reducing the number of MKPDUs transmitted during group formation; for example, a new participant is admitted to an established group after receiving, then transmitting, one MKPDU.
MKA Hello packets are sent once every 2 seconds with a timeout interval of 3 packets or 6 seconds. These values are not configurable.
The following table lists the MKA participant timer values.
Timer use |
Timeout (parameter) |
Timeout (parameter) |
|---|---|---|
Per participant periodic transmission, initialized on each transmission on expiry |
MKA Hello Time or MKA Bounded Hello Time |
2.0 0.5 |
Per peer lifetime, initialized when adding to or refreshing the potential peers list or live peers list, expiry causes removal from the list |
MKA Life Time |
6.0 |
Participant lifetime, initialized when participant created or following receipt of an MKPDU, expiry causes participant to be deleted |
||
Delay after last distributing a SAK, before the key server distributes a fresh SAK following a change in the live peers list while the potential peers list is still not empty |
MACsec capability, desire, and encryption offset
The IEEE 802.1x-2010 standard identifies the following fields in the MKA PDU:
MACsec Capability
Desire
MACsec capability signals whether MACsec is capable of integrity and confidentiality. For information about the basic settings for MACsec capability, see the encryption-offset command description.
Encryption offset of 0, 30, or 50 starts from the byte after the SecTAG (802.1AE header). Ideally, the encryption offset should be configured for IPv4 (offset 30) and IPv6 (offset 50) to leave the IP header in cleartext. This allows routers and switches to use the IP header for LAG or ECMP hashing.
Key server
The participants in an MKA instance that agree on a key server are responsible for the following:
deciding on the use of MACsec
cipher suite selection
SAK generation and distribution
SA assignment
identifying the CA when two or more CAs merge
Each participant in an MKA instance uses the key server priority (an 8-bit integer) encoded in each MKPDU to agree on the key server. Each participant selects the live participant advertising the highest priority as its key server whenever the live peers list changes, provided that highest priority participant has not selected another as its key server or is unwilling to act as the key server.
If a key server cannot be selected, SAKs are not distributed. In the event of a tie for highest priority key server, the member with the highest priority SCI is chosen. For consistency with other uses of the SCI MAC address component as a priority, numerically lower values of the key server priority and SCI receive the highest priority.
Each SC is identified by an SCI that comprises a globally unique MAC address, and a port identifier unique within the system that has been allocated that address.
SA limits and network design
Each MACsec device supports 64 Tx-SAs and 64 Rx-SAs. An SA (Security Association) is the key to encrypt or decrypt the data.
As defined in IEEE 802.1AE, each SecY contains an SC. An SC is a unidirectional concept; for example, Rx-SC or Tx-SC. Each SC contains at least one SA for encryption on Tx-SC and decryption on Rx-SC. Also, for extra security, each SC should be able to roll over the SA, therefore, Nokia recommends for each SC to have two SAs for rollover purposes.
MACsec PHY is known as a MACsec security zone. Each MACsec security zone supports 64 Tx-SAs and 64 Rx-SAs. Assuming two SAs for each SC for SA rollover, each zone supports 32 Rx-SCs and 32 Tx-SCs.
The following table describes the port mapping to security zones.
|
Platform |
Ports in security zone 1 |
Ports in security zone 2 |
Ports in security zone 3 |
Ports in security zone 5 |
SA limit per security zone |
|---|---|---|---|---|---|
|
7210 SAS-K 2F6C4T |
Ports 1, 2, 3, 4 |
Ports 5, 6, 7, 8 |
Ports 9, 10, 11, 12 |
— |
Rx-SA = 64 Tx-SA = 64 |
|
7210 SAS-K 3SFP+ 8C |
Ports 1, 2, 3, 4 (1, 2, and 3 are 10GE ports) |
Ports 5, 6, 7, 8 |
Ports 9, 10, 11 |
— |
Rx-SA = 64 Tx-SA = 64 |
| 7210 SAS-Dxp 24p | — | — | — |
Ports 1/1/19 and 1/1/20 (1 GE ports) Ports 1/1/17 and 1/1/18 (10 GE ports) |
Rx-SA = 64 Tx-SA = 64 |
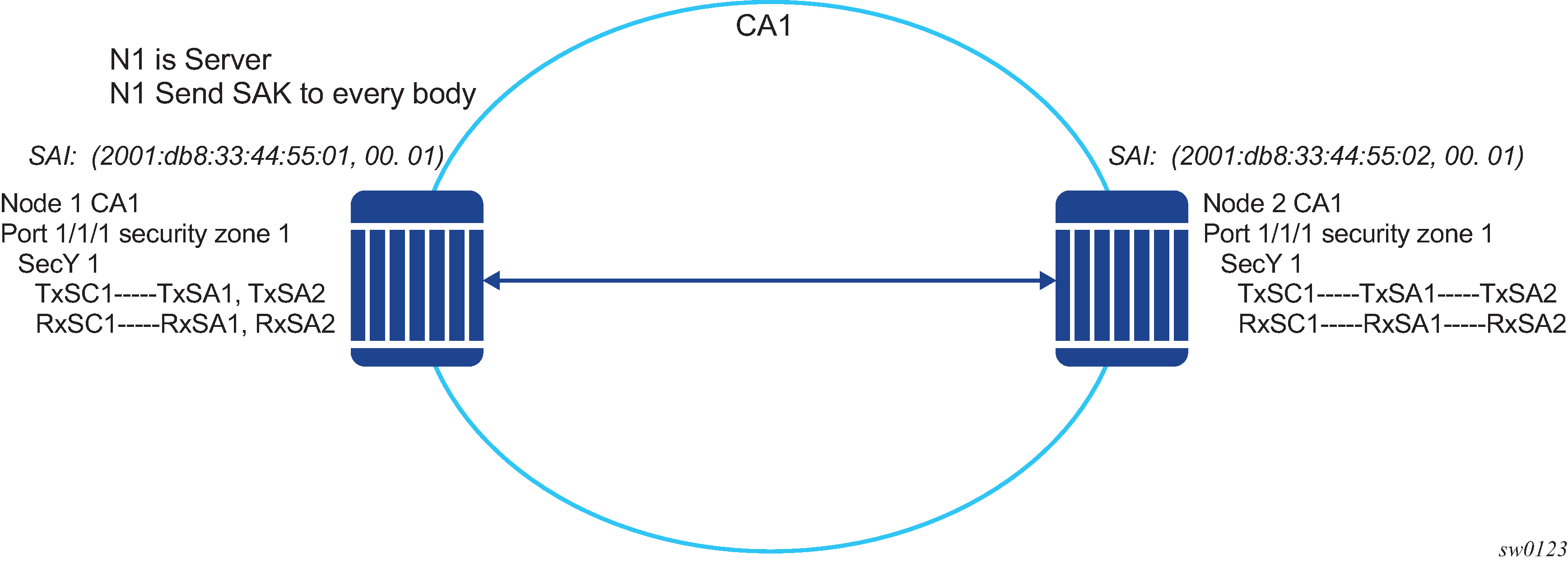
P2P (switch-to-switch) topology
In a point-to-point topology, each router needs a single security zone, a single Tx-SC for encryption, and a single Rx-SC for decryption. Each SC has two SAs. In total, for point-to-point topology, four SAs are needed: two Rx-SAs for Rx-SC1 and two Tx-SAs for Tx-SC1.
The following figure shows the P2P topology.
P2MP (switch to switch) topology
In a multi-point topology with N nodes, each node needs a single Tx-SC and N Rx-SC, one for each one of the peers. As such, 64 maximum Rx-SAs for each security zone translates to 32 Rx-SCs, which breaks down to only 32 peers; for example, only 33 nodes in the multipoint topology for each security zone. So from the perspective of each node, there is one Tx-SC and 32 Rx-SCs.
As shown in the following figure, when the 34th node joins the multi-point topology, the other 33 nodes that are already part of this domain do not have SAs to create an Rx-SC for this 34th node; however, the 34th node has a Tx-SC and can accept 32 peers. The 34th node starts to transmit and encrypt the PDUs based on its Tx-SC. However, because all other nodes do not have as SC for this SAI, all Rx PDUs are dropped.
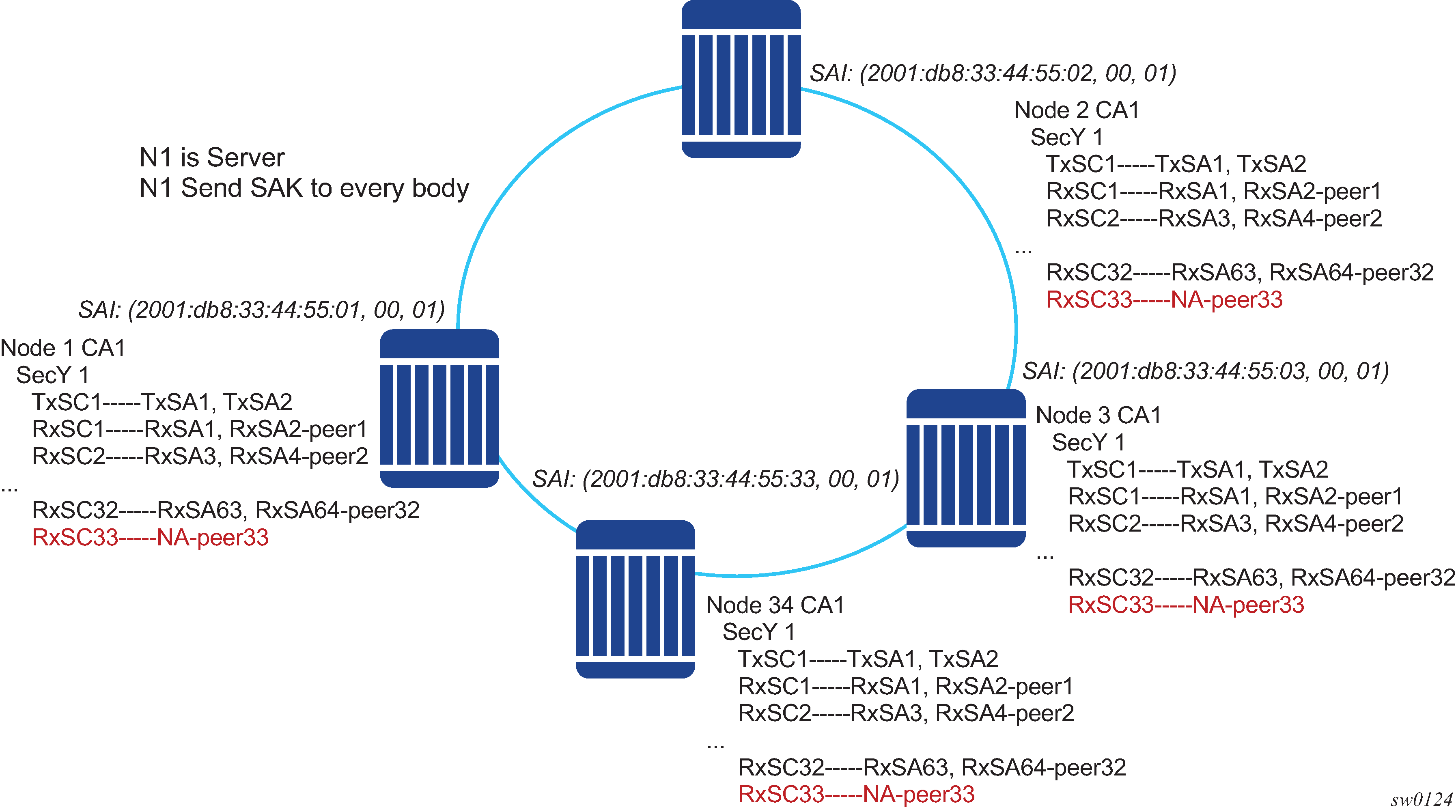
Nokia recommends that a multicast domain, for a single security zone, should not exceed 32 peers, or the summation of all the nodes in a security zone CA domain should not exceed 33. This is the same as if a security zone has four CAs; the summation of all nodes in the four CAs should be 33 or less.
SA exhaustion behavior
A security zone has 64 Rx-SAs and 64 Tx-SAs, as described in SA limits and network design. Two Rx-SAs are used for each Rx-SC for rollover purposes, and two Tx-SAs are used for Tx-SC for rollover purposes. This translates to 32 peers for each security zone.
Under each port, you can configure a max-peer command to assign the number of peers allowed on that port.
Ensure that the number of peers does not exceed the limit of maximum peers per security zone or maximum peers per port.
If the maximum peer is exceeded, the peer connectivity becomes random. In the case of a node failure or packet loss, peers join the CA randomly, on a first-come-first-served basis.
Nokia strongly recommends that the maximum peer value is not exceeded per security zone or port.
Clear tag mode
In most Layer 2 networks, MAC forwarding is done using a destination MAC address. The 802.1AE standard requires that any field after source and destination MAC address and after the SecTAG must be encrypted. This includes the 802.1Q tags. In some VLAN switching networks, it may be needed to leave the 802.1Q tag in cleartext form.
7210 SAS allows the configuration of 802.1Q tag in cleartext form by placing the 802.1Q tag before the SecTAG, or encrypts it by placing it after the SecTAG.
The following table lists the MACsec encryption of 802.1Q tags when the clear-tag is configured.
Unencrypted format |
Clear-tag-mode configuration |
Pre-encryption (Tx) |
Pre-decryption (Rx) |
|---|---|---|---|
Single tag (dot1q) |
Single-tag |
DA, SA, TPID, VID, Etype |
DA, SA, TPID, VID, SecTAG |
Single tag (dot1q) |
Double-tag |
DA, SA, TPID, VID, Etype |
DA, SA, TPID, VID, SecTAG |
Double tag (q-in-q) |
Single-tag |
DA, SA, TPID1, VID1, IPID2, VID2, Etype |
DA, SA, TPID1, VID1, SecTAG |
Double tag (q-in-q) |
Double-tag |
DA, SA, TPID1, VID1, IPID2, VID2, Etype |
DA, SA, TPID1, VID1, IPID2, VID2, SecTAG |
802.1X tunneling and multihop MACsec
MACsec is an Ethernet packet and, as with any Ethernet packet, can be forwarded through multiple switches using Layer 2 forwarding. The encryption and decryption of the packets is done using the 802.1x (MKA) capable ports.
To ensure that the MKA is not terminated on an intermediate switch or router, enable 802.1x tunneling on the corresponding port.
Verify if tunneling is enabled using the following command.
*A:SwSim28>config>port>ethernet>dot1x# info
----------------------------------------------
tunneling
By enabling tunneling, the 802.1x MKA packets transit that port without being terminated, because such MKA negotiation does not occur on a port that has 802.1x tunneling enabled.
EAPoL destination address
The MKA packets are transported over EAPoL with a multicast destination MAC address.
In cases where a point-to-point connection from the MKA to a peer node over a Layer 2 multihop cloud is required, you can set the EAPoL destination MAC address to the peer MAC address. This forces the MKA to traverse multiple nodes and establish an MKA session with the specific peer.
Mirroring consideration
Mirroring is performed before MACsec encryption. Therefore, if a port is MACsec-enabled and is also mirrored, all the mirror packets are in cleartext form.
Ethernet combo ports on 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
The 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C support combo ports. The combo port provides two physical interface options to the user. One option is to configure it as an SFP port allowing for fiber-based connectivity and speeds of 100/1000 Mb/s with the advantages of using suitable optics for longer reach. The other option is to configure it as a fixed copper port, which provides cheaper connectivity for shorter reach. The SFP port support 100/1000 Mb/s speeds and the copper port can support 10/100/1000Mbps speed. The combo port can be configured either as an SFP port or a copper port. Both interfaces cannot be used simultaneously.
7210 SAS-K 2F1C2T provide one Combo port
7210 SAS-K 2F6C4T provides six Combo ports
7210 SAS-K 3SFP+ 8C provides eight Combo ports
Link Layer Discovery Protocol
The IEEE 802.1ab Link Layer Discovery Protocol (LLDP) standard defines protocol and management elements suitable for advertising information to stations attached to the same IEEE 802 LAN. The protocol facilitates the identification of stations connected by IEEE 802 LANs or MANs, their points of interconnection, and access points for management protocols.
The LLDP helps the network operators to discover topology information. This information is used to detect and resolve network problems and inconsistencies in the configuration.
The following list is the information included in the protocol defined by the IEEE 802.1ab standard:
Connectivity and management information about the local station to adjacent stations on the same IEEE 802 LAN is advertised.
Network management information from adjacent stations on the same IEEE 802 LAN is received.
Operates with all IEEE 802 access protocols and network media.
Network management information schema and object definitions that suitable for storing connection information about adjacent stations is established.
Provides compatibility with a number of MIBs. For more information, see LLDP internal architecture for a network node.
The following figure shows LLDP internal architecture for a network node.

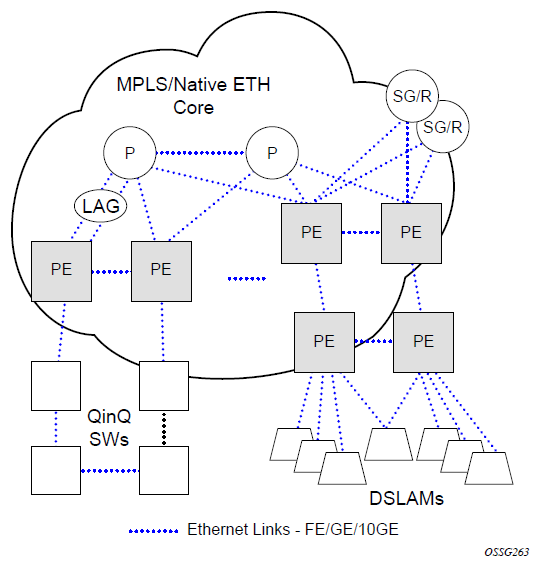
To detect and address network problems and inconsistencies in the configuration, the network operators can discover the topology information using LLDP. The Standard-based tools address the complex network scenarios where multiple devices from different vendors are interconnected using Ethernet interfaces.
The following figure shows an MPLS network that uses Ethernet interfaces in the core or as an access/handoff interfaces to connect to different kind of Ethernet enabled devices such as service gateway/routers, QinQ switches DSLAMs, or customer equipment.
The topology information of the network in the following figure can be discovered if, IEEE 802.1ab LLDP is running on each of the Ethernet interfaces in network.
LLDP protocol features
LLDP is an unidirectional protocol that uses the MAC layer to transmit specific information related to the capabilities and status of the local device. Separately from the transmit direction, the LLDP agent can also receive the same kind of information for a remote device which is stored in the related MIBs.
LLDP does not contain a mechanism for soliciting specific information from other LLDP agents, nor does it provide a specific means of confirming the receipt of information. LLDP allows the transmitter and the receiver to be separately enabled, making it possible to configure an implementation so the local LLDP agent can either transmit only or receive only, or can transmit and receive LLDP information.
The information fields in each LLDP frame are contained in a LLDP Data Unit (LLDPDU) as a sequence of variable length information elements, that each include type, length, and value fields (known as TLVs), where:
Type identifies what kind of information is being sent.
Length indicates the length of the information string in octets.
Value is the actual information that needs to be sent (for example, a binary bit map or an alphanumeric string that can contain one or more fields).
Each LLDPDU contains four mandatory TLVs and can contain optional TLVs as selected by network management:
Chassis ID TLV
Port ID TLV
Time To Live TLV
Zero or more optional TLVs, as allowed by the maximum size of the LLDPDU
End Of LLDPDU TLV
The chassis ID and the port ID values are concatenated to form a logical identifier that is used by the recipient to identify the sending LLDP agent/port. Both the chassis ID and port ID values can be defined in a number of convenient forms. When selected however, the chassis ID/port ID value combination remains the same as long as the particular port remains operable.
A non-zero value in the TTL field of the Time To Live TLV tells the receiving LLDP agent how long all information pertaining to this LLDPDU identifier will be valid so that all the associated information can later be automatically discarded by the receiving LLDP agent if the sender fails to update it in a timely manner. A zero value indicates that any information pertaining to this LLDPDU identifier is to be discarded immediately.
A TTL value of 0 can be used, for example, to signal that the sending port has initiated a port shutdown procedure. The End Of LLDPDU TLV marks the end of the LLDPDU.
The implementation defaults to setting the port-id field in the LLDP OAMPDU to tx-local. This encodes the port-id field as ifIndex (sub-type 7) of the associated port. This is required to support some releases of SAM. SAM may use the ifIndex value to properly build the Layer Two Topology Network Map. However, this numerical value is difficult to interpret or readily identify the LLDP peer when reading the CLI or MIB value without SAM. Including the port-desc option as part of the tx-tlv configuration allows an ALU remote peer supporting port-desc preferred display logic to display the value in the port description TLV instead of the port-id field value. This does not change the encoding of the port-id field. That value continues to represent the ifIndex. In some environments, it may be important to select the specific port information that is carried in the port-id field. The operator has the ability to control the encoding of the port-id information and the associated subtype using the port-id-subtype option. Three options are supported for the port-id-subtype:
-
tx-if-alias — Transmit the ifAlias String (subtype 1) that describes the port as stored in the IFMIB, either user configured description or the default entry (that is,10/100/Gig ethernet SFP)
-
tx-if-name — Transmits the ifName string (subtype 5) that describes the port as stored in the IFMIB, ifName info.
-
tx-local — The interface ifIndex value (subtype 7)
IPv6 (address subtype 2) and IPv4 (address subtype 1) LLDP System Management addresses are supported.
LLDP tunneling for Epipe service
Customers who subscribe to Epipe service consider the Epipe as a wire, and run LLDP between their devices which are located at each end of the Epipe. To facilitate this, the 7210 devices support tunneling of LLDP frames that use the nearest bridge destination MAC address.
If enabled using the command tunnel-nearest-bridge-dest-mac, all frames received with the matching LLDP destination mac address are forwarded transparently to the remote end of the Epipe service. To forward these frames transparently, the port on which tunneling is enabled must be configured with NULL SAP and the NULL SAP must be configured in an Epipe service. Tunneling is not supported for any other port encapsulation or other services.
Additionally, before enabling tunneling, admin status for LLDP dest-mac nearest-bridge must be set to disabled or Tx only, using the command admin-status available under config>port>ethernet>lldp>destmac-nearest-bridge. If the admin-status for dest-mac nearest-bridge is set to receive and process nearest-bridge LLDPDUs (that is, if either rx or tx-rx is set), then it overrides the tunnel-nearest-bridge-dest-mac command.
The following table lists the behavior for LLDP with different values set in use for admin-status and when tunneling is enabled or disabled:
Transparent forwarding of LLDP frames can be achieved using the standard defined mechanism when using the either nearest-non-tmpr or the nearest-customer as the destination MAC address in the LLDP frames. It is recommended that the customers use these MAC address where possible to conform to standards. This command allows legacy LLDP implementations that do not support these additional destinations MAC addresses to tunnel LLDP frames that use the nearest-bridge destination MAC address.
LLDP media endpoint discovery
This feature is only supported on the 7210 SAS-Dxp.
The IEEE standard 802.1AB is designed to provide a multivendor solution for the discovery of elements on an Ethernet Layer 2 data network. The LLDP standard allows nodes, which are attached to an Ethernet LAN or WAN, to advertise their supported functionalities to other nodes attached to the same LAN segment. See Link Layer Discovery Protocol for more information about IEEE 802.1AB.
The ANSI/TIA-1057 standard, Link Layer Discovery Protocol for Media Endpoint Devices, provides extensions to IEEE 802.1AB that are specific to media endpoint devices (MEDs), for example, voice phone and video terminal, in an IEEE 802 LAN environment. This standard defines specific usage of the IEEE 802.1AB LLDP base specification and interaction behavior between MEDs and LAN infrastructure elements.
LLDP media endpoint discovery (LLDP-MED) is an extension of LLDP that provides basic provisioning information to connected media endpoint devices. LLDP-MED extends LLDP protocol messages with more information to support voice over IP (VoIP) applications.
On the 7210 SAS, LLDP-MED supports the exchange of network policy information to provide the VLAN ID, dot1p bits, and IP DSCP value to media endpoint devices, such as a VoIP phone.
The following TLVs are supported for LLDP-MED:
LLDP-MED Capabilities TLV
Network Policy TLV
LLDP-MED reference model
LLDP-MED devices are composed of two primary device types: network connectivity devices and endpoint devices.
The LLDP-MED network connectivity devices provide access to the IEEE 802 LAN infrastructure for LLDP-MED endpoint devices. An LLDP-MED network connectivity device is a LAN access device based on any of the following technologies:
LAN switch or router
IEEE 802.1 bridge
IEEE 802.3 repeater
IEEE 802.11 wireless access point
any device that supports the IEEE 802.1AB and MED extensions defined by the standard and that can relay IEEE 802 frames using any method
The LLDP-MED endpoint devices are composed of three subtypes, as defined in ANSI/TIA-1057:
generic endpoints (Class I)
This endpoint device class is for basic endpoints in LLDP-MED (for example, IP communications controllers).
media endpoints (Class II)
This endpoint device class supports IP media streams (for example, media gateways and conference bridges).
communication device endpoints (Class III)
This endpoint device class support the IP communication system end user (for example, IP telephones and softphones).
The following figure shows the LLDP-MED reference model.
Acting as the network connectivity device, the 7210 SAS only supports the configuration of LLDP-MED communication device endpoints (Class III), such as VoIP phone, using the Network Policy TLV.

LLDP-MED network connectivity device functions
To enable LLDP-MED network connectivity device functions, configure the config port ethernet lldp dest-mac lldp-med admin-status command. When this command is configured, the behavior of the node is as follows.
If admin-status is set to rx-tx, the LLDP agent transmits and receives LLDP-MED TLVs on the port. The 7210 SAS node includes the LLDP-MED Capabilities TLV and the Network Policy TLV (if configured) in the LLDP message that is generated in response to an LLDP message with the LLDP-MED Capabilities TLV received on the port.
If admin-status is set to disabled, the 7210 SAS ignores and does not process the LLDP-MED Capabilities TLV in the LLDP message received on the port.
The configure port ethernet lldp admin-status command must be enabled for LLDP-MED TLV processing. The admin-status configuration in the lldp context must not conflict with the admin-status configuration in the lldp-med context.
When LLDP-MED is enabled on the port, the Network Policy TLV is sent out of the port using the parameters configured for the network policy that is associated with the port.
See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide for more information about configuring network policy parameters using commands in the config>system>lldp>lldp-med context.
LLDP-MED endpoint device move notification
The endpoint move detection notification enables VoIP management systems to track the movement of VoIP phones. On the 7210 SAS, the user has the option to generate the lldpXMedTopologyChangeDetected event on detection of movement of the endpoint device. By default, this event is disabled. To enable the event, configure the config>log>event-control lldp generate and config>port>ethernet>lldp> dest-mac>nearest-bridge>notification commands.
Modified use of TLVs defined in LLDP
LLDP-MED modifies the usage of some LLDP base TLVs for network connectivity devices. Specifically, the 7210 SAS supports the transmission of the MAC/PHY Configuration Status TLV when LLDP-MED is enabled. The transmission of this TLV is enabled using the config>port>ethernet>lldp>dest-mac>lldp-med>tx-tlvs mac-phy-config-status CLI command option.
Port loopback for Ethernet ports
The 7210 SAS supports port loopback for Ethernet ports. There are two flavors of port loopback commands - port loopback without mac-swap and port loopback with mac-swap. Both these commands are helpful for testing the service configuration and measuring performance parameters such as throughput, delay, and jitter on service turn-up. Typically, a third-party external test device is used to inject packets at desired rate into the service at a central office location.
The following sections describe the port loopback functionality.
Port loopback without MAC swap
Port loopback without MAC swap is supported on all 7210 SAS platforms as described in this document.
When the port loopback command is enabled, the system enables PHY/MAC loopback on the specified port. All the packets are sent out the port configured for loopback and received back by the system. On ingress to the system after the loopback, the node processes the packets as per the service configuration for the SAP.
This is recommended for use with only Epipe services. This command affects all the services configured on the port, therefore the user is advised to ensure all the configuration guidelines mentioned for this feature in the command description are followed.
Port loopback with MAC swap
Port loopback with MAC swap is only supported on the 7210 SAS-D and 7210 SAS-Dxp.
The 7210 SAS provides port loopback support with MAC swap. When the port loopback command is enabled, the system enables PHY/MAC loopback on the specified port. All the packets are sent out the port configured for loopback and received back by the system. On ingress to the system after the loopback, the node swaps the MAC addresses for the specified SAP and the service. It only processes packets that match the specified source MAC address and destination MAC address, while dropping packets that do not match. It processes these packets as per the service configuration for the SAP.
This is recommended for use with only VPLS and Epipe services. This command affects all the services configured on the port, therefore the user is advised to ensure all the configuration guidelines mentioned for this feature in the command description are followed.
Per-SAP loopback with MAC swap
Per-SAP loopback with MAC swap is only supported on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C.
The 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C provide per-SAP loopback support with MAC swap. When the SAP loopback command is enabled, all the packets that are sent out the SAP configured with loopback are looped back at the egress of the SAP back into the ingress of the SAP. The node swaps the MAC addresses before the packet hits the ingress of the SAP. After it is received back at SAP ingress, it processes these packets as per the service configuration for the SAP. Only traffic sent out of the test SAP is looped back. The loopback does not affect other SAPs and services configured on the same port. Per-SAP loopback is supported for use with both VPLS and Epipe services.
LAG
Based on the IEEE 802.3ax standard (formerly 802.3ad), Link Aggregation Groups (LAGs) can be configured to increase the bandwidth available between two network devices, depending on the number of links installed. LAG also provides redundancy if one or more links participating in the LAG fail. All physical links in a specific LAG links combine to form one logical interface.
Packet sequencing must be maintained for any specific session. The hashing algorithm deployed by Nokia routers is based on the type of traffic transported to ensure that all traffic in a flow remains in sequence while providing effective load sharing across the links in the LAG.
LAGs must be statically configured or formed dynamically with Link Aggregation Control Protocol (LACP). The optional marker protocol described in IEEE 802.3ax is not implemented. LAGs can be configured on access uplink and access ports.
LAG features
Hardware capabilities: The LAG load sharing is executed in hardware, which provides line rate forwarding for all port types.
Software capabilities: Conforms to the IEEE LAG implementation.
Configuring LAGs
LAG configuration guidelines include:
The 7210 SAS-D and 7210 SAS-Dxp support up to four 1GE ports in a LAG. The 7210 SAS-Dxp also supports up to two 10GE ports in a LAG.
The 7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T support up to three 1GE ports in a LAG.
The 7210 SAS-K 3SFP+ 8C supports up to three 1GE ports or two 10GE ports in a LAG.
Ports can be added or removed from the LAG while the LAG and its ports (other than the port being removed) remain operational. When ports to and from the LAG are added or removed, the hashing algorithm is adjusted for the new port count.
The show commands display physical port statistics on a port-by-port basis, or the entire LAG can be displayed.
On the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, a single set of counters is used to account for the traffic received on the LAG.
LAG is supported on Ethernet ports.
Ports of a particular LAG can be of different types, but they must be the same speed and duplex. To guarantee the same port speed is used for all ports in a LAG, autonegotiation must be disabled or set to limited mode to ensure only a specific speed is advertised.
The following figure shows traffic routed between ALA-1 and ALA-2 as a LAG consisting of four ports.
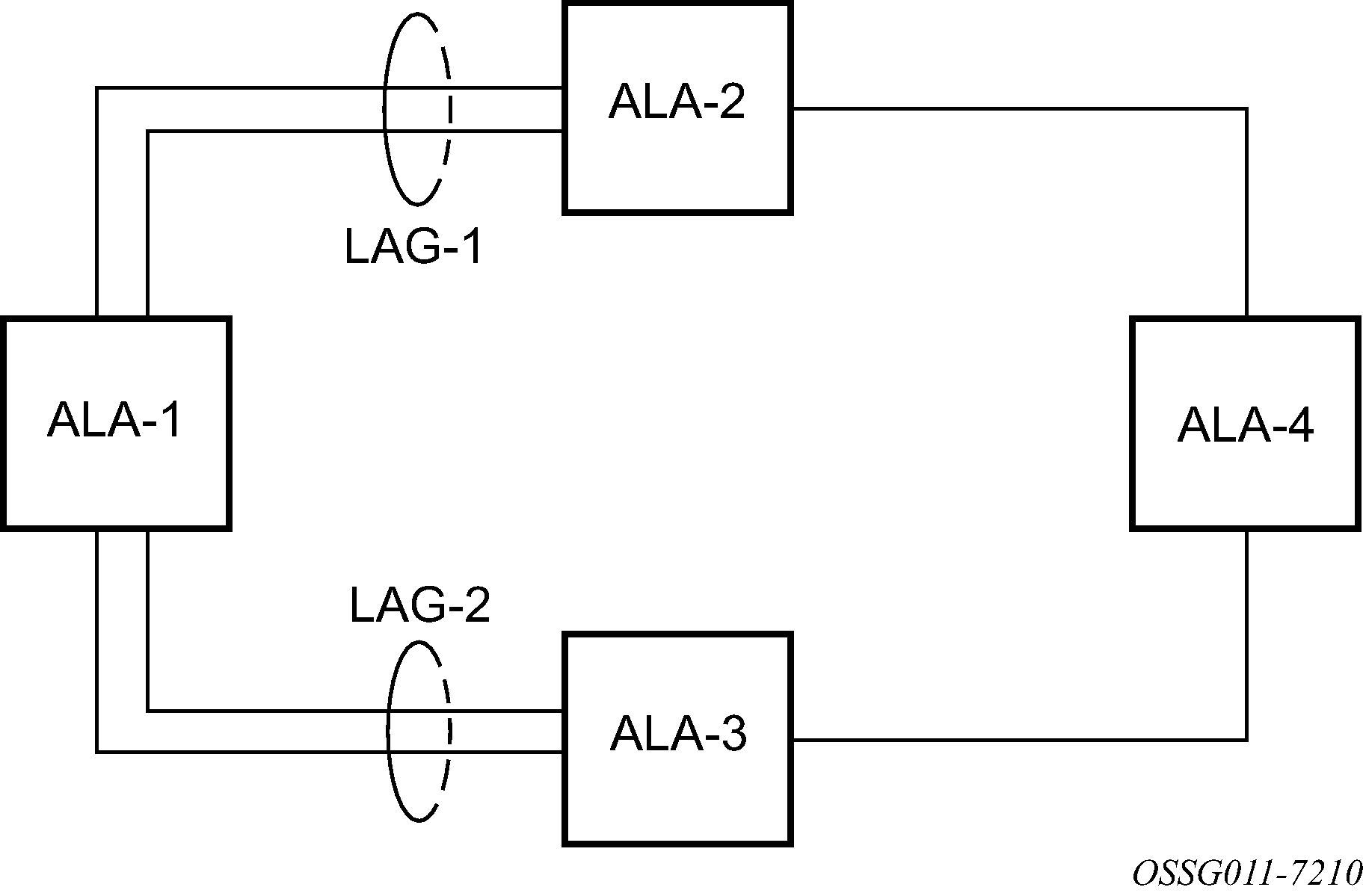
LAG and QoS policies on 7210 SAS-D and 7210 SAS-Dxp
On the 7210 SAS-D and 7210 SAS-Dxp, an ingress QoS policy is applied to the aggregate traffic that is received on all the member ports of the LAG. For example, if an ingress policy is configured with a policer of PIR 100Mbps, for a SAP configured on a LAG with two ports, then the policer limits the traffic received through the two ports to a maximum of 100Mbps.
On the 7210 SAS-D and 7210 SAS-Dxp, an egress QoS policy parameters are applied to all the ports that are members of the LAG (all ports get the full SLA). For example, if an egress policy is configured with a queue shaper rate of PIR 100Mbps, and applied to an access-uplink or access LAG configured with two port members, then each port would send out 100 Mbps of traffic for a total of 200Mbps of traffic out of the LAG. The advantage of this method over a scheme where the PIR is divided equally among all the member ports of the LAG is that, a single flow can use the entire SLA. The disadvantage is that, the overall SLA can be exceeded if the flows span multiple ports.
LAG and QoS policies on 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
On the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, an ingress QoS policy is applied to the aggregate traffic that is received through all the member ports of the LAG and mapped to that service entity (for example: access-uplink port). For example, if an ingress policy is configured with a queue shaper rate of PIR 100Mbps for an access-uplink LAG configured with two ports, then the queue shaper limits the traffic received through the two ports to a maximum of 100Mbps.
On the 7210 SAS-K 2F1C2T,7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, egress QoS policy parameters are applied to all the ports that are members of the LAG (all ports get the full SLA). For example, if an egress policy is configured with a queue shaper rate of PIR 100Mbps, and applied to an access-uplink LAG configured with two port members, then each port can send out 100 Mbps of traffic for a total of 200Mbps of traffic out of the LAG (assuming flows are distributed among the 2 ports). The advantage of this method over a scheme where the PIR is divided equally among all the member ports of the LAG is that a single flow can use the entire SLA. The disadvantage is that the overall SLA can be exceeded if the flows span multiple ports.
Port link damping
Hold time controls enable port link damping timers that reduce the number of link transitions reported to upper layer protocols.
The 7210 SAS port link damping feature guards against excessive port transitions. Any initial port transition is immediately advertised to upper layer protocols, but any subsequent port transitions are not advertised to upper layer protocols until a configured timer has expired.
An ‟up” timer controls the dampening timer for link up transitions, and a ‟down” timer controls the dampening timer for link down transitions.
LACP
Generally, link aggregation is used for two purposes: provide an increase in bandwidth and provide redundancy. Both aspects are addressed by aggregating several Ethernet links in a single LAG.
LACP enhancements allow active lag-member selection based on particular constrains. The mechanism is based on the IEEE 802.3ax standard so interoperability is ensured.
LAG and ECMP hashing
See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Router Configuration Guide for more information about ECMP support for 7210 SAS platforms.
When a requirement exists to increase the available bandwidth for a logical link that exceeds the physical bandwidth or add redundancy for a physical link, typically one of the following methods is applied:
equal cost multi-path (ECMP)
Link Aggregation (LAG)
A 7210 SAS can deploy both methods at the same time, meaning it can use ECMP of two or more Link Aggregation Groups (LAG) or single links.The Nokia implementation supports per flow hashing used to achieve uniform loadspreading and per service hashing designed to provide consistent per service forwarding. Depending on the type of traffic that needs to be distributed into an ECMP or a LAG, different variables are used as input to the hashing algorithm.
The following tables list the packets used for hashing on 7210 SAS platforms.
LAG hashing algorithm for the 7210 SAS-D
The following table describes the packet fields used for hashing for services configured on the 7210 SAS-D.
The following notes apply to LAG hashing algorithm for services configured on 7210 SAS-D:
The term ‟learned” corresponds to the Destination MAC.
the term ‟Source and Destination MAC” refers to customer source and destination MACs unless otherwise specified.
The VLAN ID is considered for learned PBB and non-IP traffic in the VPLS service only for traffic ingressing at dot1q, Q.*, Q1.Q2 SAPs.
Only the outer VLAN tag is used for hashing.
Traffic type |
Packet fields used |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
BDA |
BSA |
EtherType |
Ingress Port-ID |
ISID |
Source and destination |
VLAN |
|||
|
MAC |
IP |
L4 Ports |
|||||||
VPLS service SAP to SAP |
|||||||||
IP traffic (learned) |
✓ |
✓ |
|||||||
IP traffic (unlearned) |
✓ |
✓ |
✓ |
||||||
PBB traffic (learned) |
✓ |
✓ |
✓ |
||||||
PBB traffic (unlearned) |
✓ |
✓ |
✓ |
✓ |
|||||
Non-IP traffic (learned) |
✓ |
✓ |
✓ |
||||||
Non-IP traffic (unlearned) |
✓ |
✓ |
✓ |
✓ |
|||||
Epipe service SAP to SAP |
|||||||||
IP traffic |
✓ |
✓ |
✓ |
||||||
PBB traffic |
✓ |
✓ |
✓ |
✓ |
|||||
Non-IP traffic |
✓ |
✓ |
✓ |
✓ |
|||||
IES service (IPv4): IES SAP to IES SAP |
|||||||||
IPv4 unicast traffic |
✓ |
✓ |
|||||||
LAG hashing algorithm for the 7210 SAS-Dxp
The following table describes the packet fields used for hashing for services configured on the 7210 SAS-Dxp.
The following notes apply to LAG hashing algorithm for services configured on 7210 SAS-Dxp:
The term ‟learned” corresponds to the Destination MAC.
The term ‟Source and Destination MAC” refers to customer source and destination MACs unless otherwise specified.
The VLAN ID is considered for learned PBB and non-IP traffic in the VPLS service only for traffic ingressing at dot1q, Q.*, Q1.Q2 SAPs.
Only the outer VLAN tag is used for hashing.
Traffic type |
Packet fields used |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
BDA |
BSA |
EtherType |
Ingress Port-ID |
ISID |
Source and destination |
VLAN |
|||
|
MAC |
IP |
L4 Ports |
|||||||
VPLS service SAP to SAP |
|||||||||
IP traffic (learned) |
✓ |
✓ |
|||||||
IP traffic (unlearned) |
✓ |
✓ |
|||||||
PBB traffic (learned) |
✓ |
✓ |
|||||||
PBB traffic (unlearned) |
✓ |
✓ |
✓ |
||||||
Non-IP traffic (learned) |
✓ |
✓ |
|||||||
Non-IP traffic (unlearned) |
✓ |
✓ |
|||||||
Epipe service SAP to SAP |
|||||||||
IP traffic |
✓ |
✓ |
|||||||
PBB traffic |
✓ |
✓ |
✓ |
||||||
Non-IP traffic |
✓ |
✓ |
|||||||
IES service (IPv4): IES SAP to IES SAP |
|||||||||
IPv4 unicast traffic |
✓ |
✓ |
|||||||
LAG hashing algorithm for the 7210 SAS-K 2F1C2T
The following table describes the packet fields used for hashing for services configured on the 7210 SAS-K 2F1C2T.
The following notes apply to LAG hashing algorithm for services configured on 7210 SAS-K 2F1C2T:
The term ‟learned” corresponds to the Destination MAC.
The term ‟Source and Destination MAC” refers to customer source and destination MACs unless otherwise specified.
Traffic type |
Packet fields used |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
BDA |
BSA |
Ingress Port-ID |
IP Protocol |
Source and destination |
VLAN |
||||
|
MAC |
IP |
L4 Ports |
Outer |
Inner |
|||||
VPLS Service SAP to SAP |
|||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
✓ |
||||
PBB traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
✓ |
||||
MPLS traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
|||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
|||||
Epipe Service SAP to SAP |
|||||||||
IP traffic |
✓ |
✓ |
✓ |
✓ |
✓ |
||||
PBB traffic |
✓ |
✓ |
✓ |
✓ |
✓ |
||||
MPLS traffic |
✓ |
✓3 |
✓ |
✓ |
|||||
Non-IP traffic |
✓ |
✓ |
✓ |
✓ |
|||||
LAG hashing algorithm for the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
The following table describes the packet fields used for hashing for services configured on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C.
The following notes apply to LAG hashing algorithm for services configured on 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C:
The term ‟learned” corresponds to the destination MAC.
The term ‟Source and Destination MAC” refers to customer source an destination MACs unless otherwise specified.
SAP to SAP and SAP to SDP: Packet fields for IP traffic are used for hashing only if the number of VLAN tags is two or fewer. IP packets with more than two tags use the same hashing parameters as non-IP traffic.
SDP to SAP and SDP to SDP: Packet fields for IP traffic are used for hashing only if the number of VLAN tags is 1 or 0. IP packets with more than one tag use the same hashing parameters as non-IP traffic.
RVPLS routed traffic uses the same parameters as traffic in IES service.
For IPv6 packets, the source and destination IP addresses are XORed and collapsed into a 32-bit value.
Traffic type |
Packet fields used |
|||||||
|---|---|---|---|---|---|---|---|---|
|
Ingress Port-ID |
IP Protocol |
MPLS Label Stack |
Source and destination |
VLAN |
||||
|
MAC |
IP |
L4 Ports |
Outer |
Inner |
||||
VPLS Service SAP to SAP |
||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
✓ |
|||
MPLS traffic (learned and unlearned) |
✓ |
✓4 |
✓ |
✓ |
||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
||||
VPLS Service SAP to SDP |
||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
✓ |
|||
MPLS traffic |
✓ |
✓4 |
✓ |
✓ |
||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
||||
VPLS Service SDP to SAP5 |
||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
||||||
VPLS Service SDP to SDP5 |
||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
||||||
Epipe Service SAP to SAP |
||||||||
IP traffic |
✓ |
✓ |
✓ |
✓ |
✓ |
|||
MPLS traffic |
✓ |
✓4 |
✓ |
✓ |
||||
Non-IP traffic |
✓ |
✓ |
✓ |
✓ |
||||
Epipe Service SAP to SDP |
||||||||
IP traffic |
✓ |
✓ |
✓ |
✓ |
✓ |
|||
MPLS traffic |
✓ |
✓4 |
✓ |
✓ |
||||
Non-IP traffic |
✓ |
✓ |
✓ |
✓ |
||||
Epipe Service SDP to SAP5 |
||||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
||||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
||||||
MPLS - LSR |
||||||||
All traffic |
✓ |
✓ 6 |
✓ |
|||||
IES Service (IPv4) IES SAP to IES SAP |
||||||||
— |
✓ |
✓ |
|
✓ 7 |
✓ |
✓ |
||
IES Service (IPv6) IES SAP to IES SAP |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
IES Service (IPv4) IES SAP to IPv4 network port interface |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
IES Service (IPv6) IES SAP to IPv6 network port interface |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
IES Service (IPv4) interface IPv4 network port interface to IES SAP |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
IES Service (IPv6) IPv6 network port interface to IES SAP |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
Network port (IPv4) interface IPv4 network interface to IPv4 network interface |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
Network port (IPv6) interface IPv6 network interface to IPv6 network interface |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
VPRN SAP to SAP, SDP to SAP, SAP to SDP |
||||||||
— |
✓ |
✓ |
|
✓7 |
✓ |
✓ |
||
Packet fields used for pseudowire hash-label generation on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
The following table describes the packet fields used by different services and traffic types to generate the PW hash label.
Traffic type |
Packet fields used |
||||||
|---|---|---|---|---|---|---|---|
|
Ingress Port-ID |
IP Protocol |
Source and destination |
VLAN |
||||
|
MAC |
IP |
L4 Ports |
Outer |
Inner |
|||
VPLS and Epipes services SAP to SDP |
|||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
✓ |
||
MPLS traffic (learned and unlearned) |
✓ |
✓8 |
✓ |
✓ |
|||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
|||
VPLS services SDP to SDP |
|||||||
IP traffic (learned and unlearned) |
✓ |
✓ |
✓ |
✓ |
|||
Non-IP traffic (learned and unlearned) |
✓ |
✓ |
|||||
LDP ECMP hashing algorithm for the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
The following table describes the packet fields used for LDP ECMP hashing for label edge router (LER) and label switching router (LSR) devices on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C.
Traffic type |
Packet fields used |
|||||||
|---|---|---|---|---|---|---|---|---|
|
Ingress Port-ID |
IP Protocol |
MPLS Label Stack |
Source and destination |
VLAN |
||||
|
MAC |
IP |
L4 Ports |
Outer |
Inner |
||||
VPLS and Epipe services SAP to SDP (iLER) |
||||||||
IP traffic |
✓ |
✓ |
✓ |
✓ |
✓ |
|||
MPLS traffic |
✓ |
✓9 |
✓ |
✓ |
||||
Non-IP traffic |
✓ |
✓ |
✓ |
✓ |
||||
LSR |
||||||||
MPLS traffic |
✓ |
✓10 |
✓ |
|||||
Multi-Chassis LAG
This section describes the Multi-Chassis LAG (MC-LAG) concept. MC-LAG is an extension of a LAG concept that provides node-level redundancy in addition to link-level redundancy provided by ‟regular LAG”.
MC-LAG is supported on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C.
Typically, MC-LAG is deployed in a network-wide scenario and provides redundant connection between different end points. The whole scenario is then built by a combination of different mechanisms (for example, MC-LAG and redundant pseudowire to provide end-to-end (e2e) redundant point-to-point (p2p) connection or dual homing of CPE devices in Layer 2/3 VPNs).
Overview
MC-LAG is a method of providing redundant Layer 2/3 access connectivity that extends beyond link level protection by allowing two systems to share a common LAG end point.
The CPE/access node is connected with multiple links toward a redundant pair of Layer 2/3 access aggregation nodes such that both link and node level redundancy is provided. By using a multi-chassis LAG protocol, the paired Layer 2/3 aggregation nodes (referred to as the redundant-pair) appear to be a single node that is utilizing LACP toward the access node. The multi-chassis LAG protocol between the redundant-pair ensures a synchronized forwarding plane to and from the CPE/access node. It is used to synchronize the link state information between the redundant-pair nodes and provide correct LACP messaging to the CPE/access node from both redundant-pair nodes.
To ensure SLAs and deterministic forwarding characteristics between the CPE/access and the redundant-pair node, the multi-chassis LAG function provides an active/standby operation toward/from the CPE/access node. LACP is used to manage the available LAG links into active and standby states so that only links from one aggregation node are active at a time to and from the CPE/access node.
MC-LAG has the following characteristics:
Selection of the common system ID, system-priority, and administrative-key are used in LACP messages to ensure that partner systems consider all links part of the same LAG.
The selection algorithm is extended to allow the selection of the active subgroup.
The subgroup definition in the LAG context is still local to the single box. Consequently, even when subgroups configured on two different systems have the same subgroup-id, they are still considered two separate subgroups within the specific LAG.
The configuration of multiple subgroups per PE in an MC-LAG is supported.
If there is a tie in the selection algorithm, for example, two subgroups with identical aggregate weight (or number of active links), the group that is local to the system with lower system LACP priority and LAG system ID is selected.
Providing an inter-chassis communication channel allows the inter-chassis communication to support LACP on both systems. The communication channel enables the following functionality:
It supports connections at the IP level that do not require a direct link between two nodes. The IP address configured at the neighbor system is one of the addresses of the system (interface or loop-back IP address).
The communication protocol provides heartbeat mechanism to enhance robustness of the MC-LAG operation and detect node failures.
It supports operator actions that force an operational change on nodes.
The LAG group-ids do not have to match between neighbor systems. At the same time, multiple LAG groups between the same pair of neighbors is also allowed.
It verifies that the physical characteristics, such as speed and auto-negotiation are configured and initiates operator notifications (traps) if errors exist. Consistency of MC-LAG configuration (system-id, administrative-key and system-priority) is provided. Load-balancing must be consistently configured on both nodes.
Traffic over the signaling link is encrypted using a user-configurable message digest key.
The MC-LAG function provides active/standby status to other software applications to build reliable solutions.
MC-LAG L2 dual homing to remote PE pairs and MC-LAG L2 dual homing to local PE-pairs show different combinations of supported MC-LAG attachments. The supported configurations can be divided into the following subgroups:
dual-homing to remote PE pairs
both end-points attached with MC-LAG
one end-point attached
dual-homing to local PE pair
both end-points attached with MC-LAG
one end-point attached with MC-LAG
both end-points attached with MC-LAG to two overlapping pairs
The following figure shows dual homing to remote PE pairs.
The following figure shows dual homing to local PE pairs.
The forwarding behavior of the nodes is governed by the following principles. Note that the logical destination (actual forwarding decision) is primarily determined by the service (VPLS or VLL), and the following principle apply only if the destination or source is based on MC-LAG.
Packets received from the network will be forwarded to all local active links of the specific destination-sap based on conversation hashing. If there are no local active links, the packets will be cross-connected to the inter-chassis pseudowire.
Packets received from the MC-LAG sap will be forwarded to the active destination pseudowire or active local links of destination-sap. If no such objects are available at the local node, the packets will be cross-connected to inter-chassis pseudowire.
Point-to-point redundant connection across Layer 2/3 VPN network
The following figure shows the connection between two CPE/access nodes across network based on Layer 2/3 VPN pseudowires. The connection between a CPE/access node and a pair of access aggregation PE routers is realized by MC-LAG. From the CPE/access node perspective, a redundant pair of access aggregation PE routers acts as a single partner in LACP negotiation. At any point in time, only one of the routers has active links in a specific LAG. The status of LAG links is reflected in the status signaling of pseudowires set between all participating PEs. The combination of active and standby states across LAG links and pseudowires give only one unique path between a pair of MSANs.
Note that the configuration in the following figure shows an example configuration of VLL connections based on MC-LAG. Specifically, it shows a VLL connection where the two ends (SAPs) are located on two different redundant-pairs. However, additional configurations are possible, for example:
both ends of the same VLL connections are local to the same redundant-pair
one end of the VLL endpoint is on a redundant-pair and the other on a single (local or remote) node

Configuration guidelines
The following guidelines apply to MC-LAG configurations:
MC-LAG peer nodes must be of the same platform type. For example, 7210 SAS-K 2F6C4T can only peer with another 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C can only peer with another 7210 SAS-K 3SFP+ 8C. 7210 SAS-K 2F6C4T cannot be configured with 7210 SAS-K 3SFP+ 8C as its MC-LAG peer.
MC-LAG is only supported when using MPLS uplinks with network ports. It is not supported with access-uplink ports.
The 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C can also be MC-LAG clients, with an active/standby LAG configuration used to dual-home to access-aggregation routers when using access-uplink ports. In this scenario the user has an option to provision the uplinks as access-uplink ports to dual-home into two aggregation PE routers that are configured as MC-LAG peers.
Configuring multi-chassis redundancy
When configuring associated LAG ID parameters, the LAG must be in access mode and LACP must be enabled.
Use the following syntax to configure multi-chassis redundancy features.
config>redundancy
multi-chassis
peer ip-address
authentication-key [authentication-key | hash-key][hash | hash2]
description description-string
mc-lag
hold-on-neighbor-failure duration
keep-alive-interval interval
lag lag-id lacp-key admin-key system-id system-id [remotelag lag-
id] system-priority system-priority
no shutdown
no shutdown
source-address ip-address
sync
igmp-snooping
port [port-id | lag-id] [sync-tag]range encap-range sync-tag
no shutdown
config>redundancy# multi-chassis
config>redundancy>multi-chassis# peer 10.10.10.2 create
config>redundancy>multi-chassis>peer# description "Mc-Lag peer 10.10.10.2"
config>redundancy>multi-chassis>peer# mc-lag
config>redundancy>mc>peer>mc-lag# lag 1 lacp-key 32666 system-
id 00:00:00:33:33:33 system-priority 32888
config>redundancy>mc>peer>mc-lag# no shutdown
config>redundancy>mc>peer>mc-lag# exit
config>redundancy>multi-chassis>peer# no shutdown
config>redundancy>multi-chassis>peer# exit
config>redundancy>multi-chassis# exit
config>redundancy#
The following is a sample configuration output.
*7210-SAS>config>redundancy# info
----------------------------------------------
multi-chassis
peer 1.1.1.1 create
shutdown
sync
shutdown
port 1/1/1 create
exit
exit
peer 10.20.1.3 create
mc-lag
lag 3 lacp-key 1 system-id 00:00:00:aa:bb:cc remote-
lag 1 system-priority 1
no shutdown
exit
no shutdown
exit
exit
----------------------------------------------
*7210-SAS>config>redundancy#
MC-LAG support on 7210 SAS-D and 7210 SAS-K 2F1C2T
Multi-Chassis LAG (MC-LAG) is an extension of a LAG concept that provides node-level redundancy in addition to the link-level redundancy provided by ‟regular LAG”. Typically, MC-LAG is deployed network-wide, along with IP/MPLS, providing redundant connections between different access end points. In a typical MC-LAG deployment, a pair of nodes are configured to be MC-LAG peers (also referred to as MC-LAG servers), and access devices are connected to the MC-LAG peers using LAGs with active/standby LAG groups.
The 7210 SAS-D, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C platforms can be connected to an MC-LAG-enabled node, such as an MC-LAG server. In particular, these platforms allow for provisioning of links into subgroups in a LAG and support active/standby links. The MC-LAG solution can be achieved with or without subgroups configured.
G.8032 protected Ethernet rings
Ethernet ring protection switching provides ITU-T G.8032 specification compliance to achieve resiliency for Ethernet Layer 2 networks. G.8032 (Eth-ring) is built on Ethernet OAM and is often referred to as Ring Automatic Protection Switching (R-APS).
See ‟G.8032 Protected Ethernet Rings” in the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Services Guide for more information about Ethernet rings.
802.1x network access control
The Nokia 7210 SAS supports network access control of client devices (PCs, STBs, and so on) on an Ethernet network using the IEEE. 802.1x standard. 802.1x is known as Extensible Authentication Protocol (EAP) over a LAN network or EAPOL.
802.1x modes
The 7210 SAS supports port-based network access control for Ethernet ports only. Every Ethernet port can be configured to operate in one of three different operation modes, controlled by the port-control parameter:
force-auth
Disables 802.1x authentication and causes the port to transition to the authorized state without requiring any authentication exchange. The port transmits and receives normal traffic without requiring 802.1x-based host authentication. This is the default setting.
force-unauth
Causes the port to remain in the unauthorized state, ignoring all attempts by the hosts to authenticate. The switch cannot provide authentication services to the host through the interface.
auto
Enables 802.1x authentication. The port starts in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. Both the router and the host can initiate an authentication procedure that is described as follows. The port will remain in an unauthorized state (no traffic except EAPOL frames is allowed) until the first client is authenticated successfully. After this, traffic is allowed on the port for all connected hosts.
802.1x basics
The supplicant — This is the end-user device that requests access to the network.
The authenticator — Controls access to the network. Both the supplicant and the authenticator are referred to as PAEs.
The authentication server — Performs the actual processing of the user information.
The authentication exchange is carried out between the supplicant and the authentication server, the authenticator acts only as a bridge. The communication between the supplicant and the authenticator is done through the Extended Authentication Protocol (EAP) over LANs (EAPOL). On the back end, the communication between the authenticator and the authentication server is done with the RADIUS protocol. The authenticator is therefore a RADIUS client, and the authentication server a RADIUS server.
The router initiates the procedure when the Ethernet port becomes operationally up, by sending a special PDU called EAP-Request/ID to the client. The client can also initiate the exchange by sending an EAPOL-start PDU, if it does not receive the EAP-Request/ID frame during bootup. The client responds on the EAP-Request/ID with a EAP-Response/ID frame, containing its identity (typically username + password).
After receiving the EAP-Response/ID frame, the router will encapsulate the identity information into a RADIUS AccessRequest packet, and send it off to the configured RADIUS server.
The RADIUS server checks the supplied credentials, and if approved will return an Access Accept message to the router. The router notifies the client with an EAP-Success PDU and puts the port in authorized state.
802.1x timers
The 802.1x authentication procedure is controlled by a number of configurable timers and scalars. There are two separate sets, one for the EAPOL message exchange and one for the RADIUS message exchange.
EAPOL timers:
transit-period
Indicates how many seconds the Authenticator will listen for an EAP-Response/ID frame. If the timer expires, a new EAP-Request/ID frame will be sent and the timer restarted. The default value is 60. The range is 1 to 3600 seconds.
supplicant-timeout
This timer is started at the beginning of a new authentication procedure (transmission of first EAP-Request/ID frame). If the timer expires before an EAP-Response/ID frame is received, the 802.1x authentication session is considered as having failed. The default value is 30. The range is 1 to 300.
quiet-period
Indicates number of seconds between authentication sessions. It is started after logout, after sending an EAP-Failure message or after expiry of the supplicant-timeout timer. The default value is 60. The range is 1 to 3600.
RADIUS timer and scaler:
max-auth-req
Indicates the maximum number of times that the router will send an authentication request to the RADIUS server before the procedure is considered as having failed. The default value is value 2. The range is 1 to 10.
server-timeout
Indicates how many seconds the authenticator will wait for a RADIUS response message. If the timer expires, the access request message is sent again, up to max-auth-req times. The default value is 60. The range is 1 to 3600 seconds.
The router can also be configured to periodically trigger the authentication procedure automatically. This is controlled by the enable re-authentication and reauth-period parameters. Reauth-period indicates the period in seconds (since the last time that the authorization state was confirmed) before a new authentication procedure is started. The range of reauth-period is 1 to 9000 seconds (the default is 3600 seconds, one hour). Note that the port stays in an authorized state during the re-authentication procedure.
802.1x configuration and limitations
Configuration of 802.1x network access control on the router consists of two parts:
Generic parameters, which are configured under config>security>dot1x
Port-specific parameters, which are configured under config>port>ethernet>dot1x
801.x authentication:
Provides access to the port for any device, even if only a single client has been authenticated.
Can only be used to gain access to a predefined Service Access Point (SAP). It is not possible to dynamically select a service (such as a VPLS service) depending on the 802.1x authentication information.
802.1x tunneling for Epipe service
Customers who subscribe to Epipe service considers the Epipe as a wire, and run 802.1x between their devices which are located at each end of the Epipe.
This feature applies only to port-based Epipe SAPs because 802.1x runs at the port level not the VLAN level. Therefore such ports must be configured as null encapsulated SAPs.
When 802.1x tunneling is enabled, the 802.1x messages received at one end of an Epipe are forwarded through the Epipe. When 802.1x tunneling is disabled (by default), 802.1x messages are dropped or processed locally according to the 802.1x configuration (shutdown or no shutdown).
Enabling 802.1x tunneling requires the 802.1x mode to be set to force-auth. Enforcement is performed at the CLI level.
802.3ah OAM
802.3ah Clause 57 (EFM OAM) defines the Operations, Administration, and Maintenance (OAM) sublayer, which provides mechanisms useful for monitoring link operation such as remote fault indication and remote loopback control. In general, OAM provides network operators the ability to monitor the health of the network and quickly determine the location of failing links or fault conditions. EFM OAM described in this clause provides data link layer mechanisms that complement applications that may reside in higher layers.
OAM information is conveyed in slow protocol frames called OAM protocol data units (OAMPDUs). OAMPDUs contain the appropriate control and status information used to monitor, test and troubleshoot OAM-enabled links. OAMPDUs traverse a single link, being passed between peer OAM entities, and therefore are not forwarded by MAC clients (like bridges or switches).
The following EFM OAM functions are supported:
EFM OAM capability discovery.
Active and passive modes.
Remote failure indication — Handling of critical link events (for example, link fault, critical event, dying gasp)
Loopback — A mechanism is provided to support a data link layer frame-level loopback mode. Both remote and local loopback modes are supported.
Generation of dying gasp message on access uplink ports on power failure.
EFM OAMPDU tunneling.
Timer for EFM OAM in 500ms interval (minimum).
OAM events
EFM OAM defines a set of events that may impact link operation. The following critical link events (defined in 802.3ah clause 57.2.10.1) are supported:
-
Link fault: the PHY has determined a fault has occurred in the receive direction of the local DTE.
-
Dying gasp: an unrecoverable local failure condition has occurred.
-
Critical event: an unspecified critical event has occurred.
The dying gasp event is not supported on the 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p.
These critical link events are signaled to the remote DTE by the flag field in OAM PDUs.
The 7210 SAS does not generate EFM OAM PDUs with these flags except for the dying gasp flag. However, it supports processing of these flags in EFM OAM PDUs received from the peer.
Remote loopback
EFM OAM provides a link-layer frame loopback mode that can be remotely controlled.
To initiate remote loopback, the local EFM OAM client sends a loopback control OAM PDU by enabling the OAM remote-loopback command. After receiving the loopback control OAM PDU, the remote OAM client puts the remote port into local loopback mode.
To exit remote loopback, the local EFM OAM client sends a loopback control OAM PDU by disabling the OAM remote-loopback command. After receiving the loopback control OAM PDU, the remote OAM client puts the port back into normal forwarding mode.
Note that during remote loopback test operation, all frames except EFM OAM PDUs are dropped at the local port for the receive direction, where remote loopback is enabled. If local loopback is enabled, then all frames except EFM OAM PDUs are dropped at the local port for both the receive and transmit directions. This behavior may result in many protocols (such as STP or LAG) resetting their state machines.
Note that when a port is in loopback mode, service mirroring will not work if the port is a mirror-source or a mirror-destination.
802.3ah OAM PDU tunneling for Epipe service
The 7210 SAS routers support 802.3ah. Customers who subscribe to Epipe service treat the Epipe as a wire, so they demand the ability to run 802.3ah between their devices which are located at each end of the Epipe.
Note: This feature only applies to port-based Epipe SAPs because 802.3ah runs at port level not VLAN level. Therefore, such ports must be configured as null encapsulated SAPs.
When OAM PDU tunneling is enabled, 802.3ah OAM PDUs received at one end of an Epipe are forwarded through the Epipe. 802.3ah can run between devices that are located at each end of the Epipe. When OAM PDU tunneling is disabled (by default), OAM PDUs are dropped or processed locally according to the efm-oam configuration (shutdown or no shutdown).
Note that enabling 802.3ah for a port and enabling OAM PDU tunneling for the same port are mutually exclusive. That is, on a specific port either 802.3ah tunneling can be enabled or 802.3ah can be enabled, but both cannot be enabled together.
MTU configuration guidelines
Observe the following general rules when planning your physical MTU configurations:
The 7210 SAS must contend with MTU limitations at many service points. The physical (access and access uplink) port, MTU values must be individually defined.
Identify the ports that are designated as access uplink ports as these are intended to carry service traffic.
MTU values should not be modified frequently.
-
The access uplink port MTU on the 7210 SAS-D and 7210 SAS-Dxp must be greater than or equal to the access port MTU plus the overhead added by the system (for example, typically 4 bytes of VLAN tag are added when a packet is transmitted using the QinQ access uplink).
The 7210 SAS-K 2F1C2T supports service-mtu. The service MTU values must conform to the following conditions:
The service MTU must be less than or equal to the access-uplink port MTU.
The service MTU must be less than or equal to the access port (SAP) MTU.
The 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C support service-mtu. The service MTU values must conform to the following conditions:
The service MTU must be less than or equal to the access-uplink port MTU.
The service MTU must be less than or equal to the SDP path MTU when the service is configured to use MPLS SDPs.
The service MTU must be less than or equal to the access port (SAP) MTU.
Default MTU values
The following table describes the default MTU values that are dependent upon the (sub-) port type, mode, and encapsulation.
Port type |
Mode |
Encap type |
Default (bytes) |
|---|---|---|---|
Ethernet |
access |
null |
1514 |
Ethernet |
access |
dot1q |
1518 |
Port mode |
access |
qinq |
1522 |
Fast Ethernet |
uplink |
— |
1522 |
Other Ethernet |
uplink |
— |
9212 |
Ethernet |
hybrid |
— |
9212 |
Modifying MTU defaults on 7210 SAS-D and 7210 SAS-Dxp
On the 7210 SAS-D and 7210 SAS-Dxp, MTU parameters can be modified only on the port level.
The port-level MTU parameters configure the maximum payload MTU size for an Ethernet port that is part of a multilink bundle or LAG.
The default MTU values should be modified to ensure that packets are not dropped because of frame size limitations.
Modifying MTU defaults on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
MTU parameters can be modified on the port level and at the service level.
The port-level MTU parameters configure the maximum payload MTU size for an Ethernet port that is part of a multi-link bundle or LAG.
The service-level MTU parameters configure the service payload (Maximum Transmission Unit – MTU) in bytes for the service ID overriding the service-type default MTU.
The default MTU values should be modified to ensure that packets are not dropped because of frame size limitations.
The service MTU must be less than or equal to both the access SAP port MTU and the access-uplink port MTU values. If the service from the 7210 SAS-K 2F1C2T is transported over an SDP in the IP/MPLS network (the SDP is not originating or terminating on the node), the operational path MTU can be less than the service MTU. In this case, user may need to modify the MTU value accordingly.
Configuration example for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C using SAPs in the service
In order for the maximum length service frame to successfully travel from a local ingress SAP to a remote egress SAP, the MTU values configured on the port on which the local ingress SAP is provisioned and the port on which the egress SAP is provisioned must be coordinated to accept the maximum frame size the service can forward.
The following figure shows an example of the targeted MTU values to configure for an Epipe service (ALA-A and ALA-B).
Because ALA-A uses Dot1q encapsulation, the port 1/1/1 MTU must be set to 1518 to be able to accept a 1514-byte service frame (see the following table for MTU default values). Each of the access uplink port MTU must be set to at least 1518 as well. Finally, the MTU of ALA-B SAP (access port 1/1/2) must be at least 1514, as it uses null encapsulation.
The following table describes sample MTU configuration values.
ALA-A |
ALA-B |
|||
|---|---|---|---|---|
Access (SAP) |
Access Uplink (SAP) |
Access Uplink (SAP) |
Access (SAP) |
|
Port (slot/MDA/port) |
1/1/1 |
1/1/24 |
1/1/18 |
1/1/2 |
Mode type |
access (dot1q) |
access-uplink (QinQ) |
access-uplink (QinQ) |
access (null) |
MTU |
1518 |
1518 |
1518 |
1514 |
Instead, if ALA-A uses a dot1q-preserve SAP on port 1/1/1, then port 1/1/1 MTU must be set to 1518 to be able to accept a 1514-byte service frame (see the following table for MTU default values). Each of the access uplink port MTU must be set to at least 1522 as well. Finally, the MTU of ALA-B SAP (access port 1/1/2) must be at least 1518, as it uses Dot1q encapsulation.
The following table describes sample MTU configuration values.
ALA-A |
ALA-B |
|||
|---|---|---|---|---|
Access (SAP) |
Access Uplink (SAP) |
Access Uplink (SAP) |
Access (SAP) |
|
Port (slot/MDA/port) |
1/1/1 |
1/1/24 |
1/1/18 |
1/1/2 |
Mode type |
access (dot1q-preserve) |
access-uplink (QinQ) |
access-uplink (QinQ) |
access (dot1q-preserve) |
MTU |
1518 |
1522 |
1522 |
1518 |
Modifying MTU defaults on 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C when using SDP in the service
MTU parameters must be modified on the service level as well as the port level.
The service-level MTU parameters configure the service payload (Maximum Transmission Unit – MTU) in bytes for the service ID overriding the service-type default MTU.
The port-level MTU parameters configure the maximum payload MTU size for an Ethernet port or LAG.
The default MTU values must be modified to ensure that packets are not dropped because of frame size limitations.
In a service configured to use access SAPs and access-uplinks SAPs, the service MTU must be less than or equal to both the access SAP port MTU and the access uplink port MTU values. If the service from the 7210 SAS-K 2F6C4T or 7210 SAS-K 3SFP+ 8C is transported over an SDP in the IP/MPLS network (the SDP is not originating or terminating on the node), the operational path MTU can be less than the service MTU. In this case, the user may need to modify the MTU value accordingly.
In a service configured to use access SAPs and MPLS SDPs, the service MTU must be less than or equal to both the SAP port MTU and the SDP path MTU values. When an SDP is configured on a network port using default port MTU values, the operational path MTU can be less than the service MTU. In this case, enter the show service sdp command to check the operational state. If the operational state is down, modify the MTU value accordingly.
Deploying preprovisioned components
Cards and MDAs are auto-provisioned by the system and do not need to be provisioned by the user.
MAC authentication
MAC authentication is only supported on 7210 SAS-Dxp.
The 7210 SAS supports the 802.1x EAP standard for authenticating Ethernet devices before they can access the network. However, if a client device does not support 802.1x EAP, MAC authentication can be used to prevent unauthorized traffic from being transmitted through the 7210 SAS.
Because MAC authentication is a fallback mechanism, the user must first enable 802.1x EAP to use MAC authentication on the 7210 SAS. To authenticate a port using MAC authentication, first configure 802.1x authentication on the 7210 SAS by enabling port-control auto, and then configure mac-auth on the 7210 SAS to enable MAC authentication.
Layer 2 control protocols affect MAC authentication behavior differently depending on the protocol in use; see Layer 2 control protocol interaction with authentication methods for more information.
MAC authentication basics
When a port becomes operationally up with MAC authentication enabled, the 7210 SAS (as the authenticator) performs the following steps.
After transmission of the first EAP-Request/ID PDU, the 7210 SAS starts the mac-auth-wait timer and begins listening on the port for EAP-Response/ID PDUs. At this point, the 7210 SAS only listens to EAPOL frames. If EAPOL frames are received, 802.1x authentication is chosen.
Note:If it is known that the attached equipment does not support EAP, you can configure no mac-auth-wait so that MAC authentication is used as soon as the port is operationally up.
If the mac-auth-wait timer expires, and no EAPOL frames have been received, the 7210 SAS begins listening on the port for any Ethernet frames.
If the 7210 SAS receives an Ethernet frame, the 7210 SAS scans the client source MAC address in the frame and transmits the MAC address to the configured RADIUS server for comparison against the MAC addresses configured in its database.
The following attributes are contained in the RADIUS message:
User-Name
This attribute specifies the source MAC address of the client device.
User-Password
This attribute specifies the source MAC address of the client device in an encrypted format.
Service-Type
This attribute specifies the type of service that the client has requested; the value is set to 10 (call-check) for MAC authentication requests.
Calling-Station-Id
This attribute specifies the source MAC address of the client device.
NAS-IP-Address
This attribute specifies the IP address of the device acting as the authenticator.
NAS-Port
This attribute specifies the physical port of the device acting as the authenticator.
Message-Authenticator
This attribute is used to authenticate and protect the integrity of Access Request messages to prevent spoofing attacks.
If the MAC address is approved by the RADIUS server, the 7210 SAS enables the port for traffic transmission by that particular MAC address, which is successfully authenticated.
If the MAC address is rejected by the RADIUS server, the 7210 SAS will not authenticate the port using either 802.1x or MAC authentication. If an Ethernet frame with the same MAC address is received, the 7210 SAS returns to step3 and reattempts approval of the MAC address.
If a port that was previously authenticated with MAC authentication receives an EAPOL-Start frame, the port will not reauthenticate using 802.1x EAPOL.
While the port is unauthenticated, the port will be down to all upper layer protocols or services.
When a MAC address is authenticated, only packets whose source MAC address matches the authenticated MAC address are forwarded when the packets are received on the port, and only packets whose destination MAC address matches the authenticated MAC address are forwarded out of the port.
Broadcast and multicast packets at ingress are sent for source MAC address authentication. Broadcast and multicast packets at egress are forwarded as normal.
Unknown destination packets at ingress are copied to the CPU and MAC authentication is attempted. Unknown destination packets at egress are dropped.
MAC authentication limitations
MAC authentication is subject to the following limitations:
If MAC authentication is configured on ports that are part of a LAG, the authenticated MAC address is forwarded in the egress direction out of any port in the LAG.
If MAC authentication is configured on a port and the port is added to or removed from a LAG, all previously authenticated MACs are reauthenticated by the system.
Caution:A small amount of traffic loss may occur while MAC reauthentication is in progress.
VLAN authentication
VLAN authentication is only supported on 7210 SAS-Dxp.
The 7210 SAS supports VLAN authentication, which operates similarly to 802.1x network access control but only uses VLAN-tagged EAPOL frames to trigger the authentication process on a per-VLAN basis, or uses null-tagged EAPOL frames to authenticate and authorize processing of service traffic received in the context of a Dot1q explicit null SAP. See 802.1x network access control for information about 802.1x network access control and authentication.
To authenticate a port using VLAN authentication, you must first configure 802.1x authentication on the 7210 SAS by enabling port-control auto, and then configure vlan-auth on the 7210 SAS to enable VLAN authentication and allow VLAN authentication functionality to supersede that of basic 802.1x authentication.
VLAN authentication and MAC authentication are mutually exclusive. MAC authentication cannot be configured on a port while VLAN authentication is already configured on the same port. See MAC authentication for information about MAC authentication.
Layer 2 control protocols affect VLAN authentication behavior differently depending on the protocol in use; see Layer 2 control protocol interaction with authentication methods for more information.
VLAN authentication basics
When a port becomes operationally up with VLAN authentication enabled, the 7210 SAS (as the authenticator) performs the following steps.
After transmission of the first EAP-Request/ID PDU, the 7210 SAS begins listening on the port for VLAN-tagged EAPOL Start, Request-Identity frames from the access device connected to the port. Null-tagged EAPOL frames also trigger the authentication process if a Dot1q explicit null SAP is configured.
If the 7210 SAS receives a VLAN-tagged EAPOL frame (or a null-tagged EAPOL frame if a Dot1q explicit null SAP is configured), the 7210 SAS transmits the frame to the configured RADIUS server for comparison of the VLAN against the usernames configured in its database.
The User-Name attribute is contained in the RADIUS message. This attribute specifies the username received in the EAPOL frame from the client device.
If the VLAN is approved by the RADIUS server, the 7210 SAS maps all traffic received from the VLAN to a SAP and processes it in the context of the configured service.
If the VLAN is rejected by the RADIUS server, all traffic from the VLAN is dropped. The 7210 SAS enters a quiet period, configured using the quiet-period command, and will not authenticate the port using VLAN authentication. After the quiet period expires, the 7210 SAS returns to step1.
While the port is unauthenticated, the port will be down to all upper layer protocols or services.
VLAN authentication limitations
VLAN authentication is subject to the following limitations:
VLAN authentication is only supported on Dot1q-encapsulated ports. It is not supported on NULL or QinQ-encapsulated ports.
VLAN authentication only uses the outermost VLAN tag received in the packets. Packets with more than one tag are processed only if the outermost tag matches the SAP tag.
Restrictions on processing of SAP tags also apply to VLAN authenticated frames. VLAN authentication does not change the current behavior for frames mapped to different SAPs and services.
VLAN range SAPs are not supported on a port with VLAN authentication enabled.
Dot1q default SAPs configured on a port with Dot1q encapsulation do not support VLAN authentication.
Dot1q explicit null SAPs can be configured on a port with Dot1q encapsulation, which requires authentication of null-tagged EAPOL frames.
Layer 2 control protocol interaction with authentication methods
The following table describes the interactions of Layer 2 control protocols with 802.1x authentication, MAC authentication, and VLAN authentication.
Layer 2 control protocol |
802.1x port authentication enabled |
MAC authentication enabled |
VLAN authentication enabled |
|
|---|---|---|---|---|
Dot1q explicit null SAP not configured |
Dot1q explicit null SAP configured |
|||
EFM OAM |
Allow |
Allow |
Allow |
Allow |
LLDP |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Allow |
Allow |
LACP |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
LAG and LACP are not supported on ports with VLAN authentication enabled |
LAG and LACP are not supported on ports with VLAN authentication enabled |
CFM |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Block if VLAN (SAP) is unauthenticated Allow only if specific VLAN is authenticated |
Block if null SAP is unauthenticated Allow if null SAP is authenticated |
xSTP (STP/RSTP/MSTP) |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Block if VLAN (SAP) is unauthenticated Allow if VLAN (SAP) is authenticated |
Block if null SAP is unauthenticated Allow if null SAP is authenticated |
Configuration process overview
The following figure shows the process to provision chassis slots, line cards, MDAs, and ports.
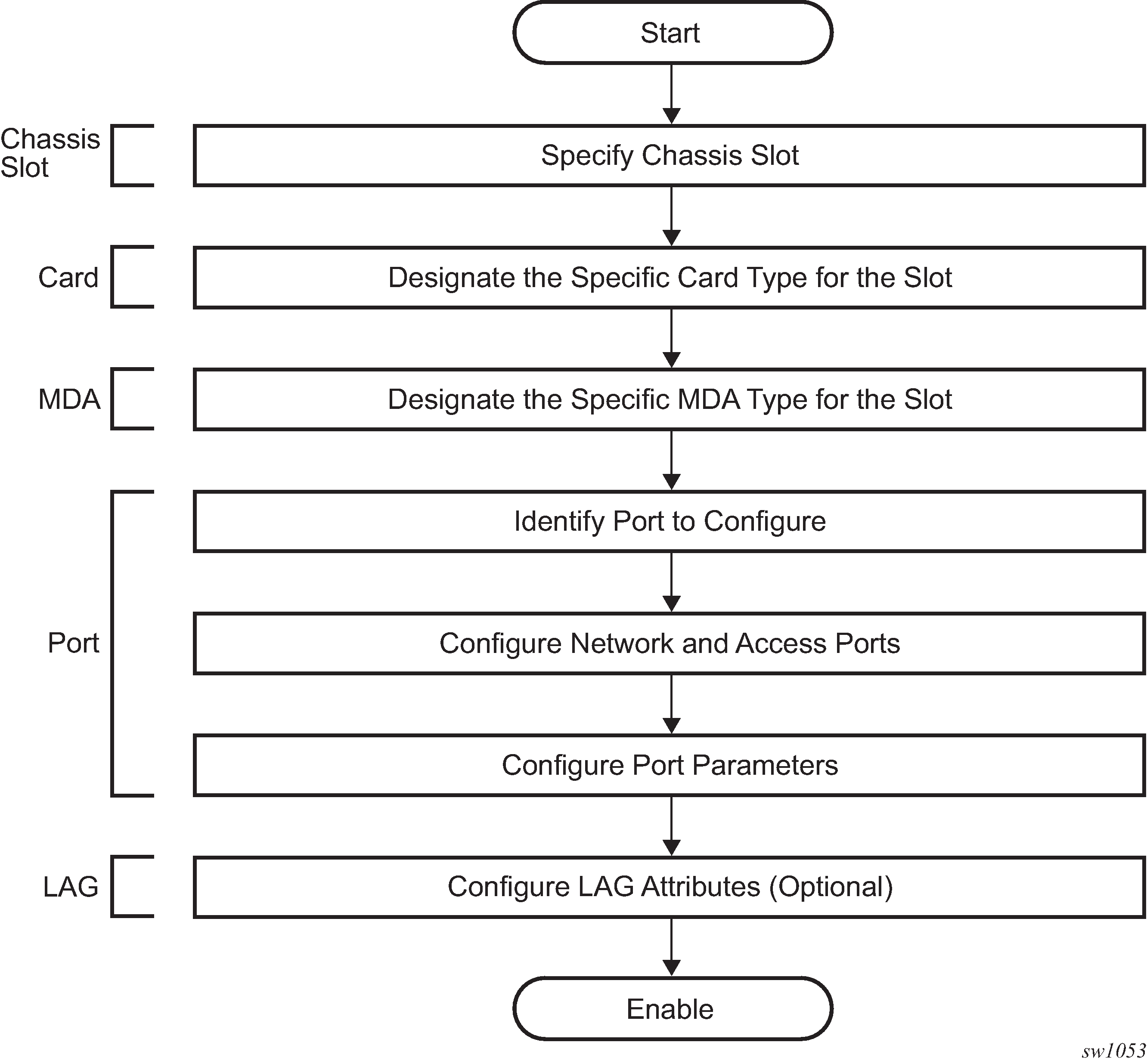
Configuring physical ports with CLI
This section provides information to configure cards, MDAs, and ports.
Preprovisioning guidelines
7210 SAS routers have a console port to connect terminals to the router. The 7210 SAS does not support a management port.
Configure parameters from a system console connected to a console port, using Telnet to access a the device remotely or SSH to open a secure shell connection.
Predefining entities
The 7210 SAS auto-provisions card and MDA types.
On 7210 SAS platforms, where cards/MDAs are not auto-provisioned, to initialize a card, the chassis slot, line card type, and MDA type must match the preprovisioned parameters. In this context, preprovisioning means to configure the entity type (such as the line card type, MDA type, port, and interface) that is planned for a chassis slot, line card, or MDA. Preprovisioned entities can be installed but not enabled or the slots can be configured but remain empty until populated. Provisioning means that the preprovisioned entity is installed and enabled.
You can:
Preprovision ports and interfaces after the line card and MDA types are specified.
Install line cards in slots with no preconfiguration parameters specified. When the card is installed, the card and MDA types must be specified. This is required on 7210 SAS chassis based platforms or on those platforms that support expansion slots. Typically, on 7210 SAS platforms that do not support any removable cards and MDAs, the cards are preprovisioned for fixed ports.
Install a line card in a slot provisioned for a different card type (the card will not initialize). The existing card and MDA configuration must be deleted and replaced with the current information. This is required on 7210 SAS chassis based platforms or on those platforms that support expansion slots. Typically, on 7210 SAS platforms that do not support any removable cards and MDAs, the MDAs are preprovisioned for all fixed ports.
Preprovisioning a port
It is recommended to configure an access Ethernet port for customer-facing traffic on which services are configured.
An encapsulation type may be specified to distinguish services on the port or channel. Encapsulation types are not required for network ports.
To configure an Ethernet access port, see Configuring Ethernet port parameters.
Basic configuration
On 7210 SAS platforms that do not support any removable cards and MDAs, the most basic configuration must have the following:
Identify chassis slot.
Specify line card type (must be an allowed card type).
Identify MDA slot.
Specify MDA type (must be an allowed MDA type).
Identify specific port to configure.
Common configuration tasks
This section describes common configuration tasks.
Configuring Ethernet port parameters
This section describes Ethernet port configuration.
Ethernet network port
A network port is network facing and participates in the service provider transport or infrastructure network processes.
The following is a sample network port configuration output.
A:ALA-B>config>port# info
----------------------------------------------
description ‟Ethernet network port”
ethernet
exit
no shutdown
----------------------------------------------
A:ALA-B>config>port#
Ethernet network port configuration is supported only on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C.
Ethernet access-uplink port
An access-uplink port is network facing and participates in the service provider transport or infrastructure network processes. This is similar to a network port concept.
A SAP can be created when a port is configured in access uplink mode. When a port is configured in access uplink mode, then the encapsulation type of the port is set to QinQ.
The following is a sample network port configuration output.
A:ALA-B>config>port# info
----------------------------------------------
description "Ethernet Access Uplink port"
----------------------------------------------
ethernet
mode access uplink
exit
no shutdown
----------------------------------------------------
A:ALA-B>config>port#
Access uplink port configuration is supported on the 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C.
Ethernet access port
Services are configured on access ports used for customer-facing traffic. If a Service Access Port (SAP) is to be configured on a port, it must be configured as access mode or access uplink mode. When a port is configured for access mode, the appropriate encapsulation type can be specified to distinguish the services on the port. When a port has been configured for access mode, multiple services may be configured on the port.
The following is a sample Ethernet access port configuration (for 7210 SAS-D) output.
*A:7210-SAS>config>port# info
----------------------------------------------
ethernet
mode access
access
egress
exit
exit
encap-type dot1q
mtu 9212
exit
no shutdown
----------------------------------------------
*A:7210-SAS>
Access port configuration is supported on the 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C.
Configuring 802.1x authentication port parameters
The following is a sample of an 802.1x port configuration output.
A:ALA-A>config>port>ethernet>dot1x# info detail
----------------------------------------------
port-control auto
radius-plcy dot1xpolicy
re-authentication
re-auth-period 3600
max-auth-req 2
transmit-period 30
quiet-period 60
supplicant-timeout 30
server-timeout 30
----------------------------------------------
Configuring MAC authentication port parameters
MAC authentication is only supported on 7210 SAS-Dxp.
The 7210 SAS supports a fallback MAC authentication mechanism for client devices (for example, PCs and cameras) on an Ethernet network that do not support 802.1x EAP.
MAC authentication provides protection against unauthorized access by forcing the device connected to the 7210 SAS to have its MAC address authenticated by a RADIUS server before the device is able to transmit packets through the 7210 SAS.
Use the following CLI syntax to configure MAC authentication for an Ethernet port.
port port-id ethernet
dot1x
mac-auth
mac-auth-wait seconds
port-control auto
quiet-period seconds
radius-plcy name
Command usage to configure MAC authentication for an Ethernet port
config# port 1/1/2 ethernet dot1x
config>port>ethernet>dot1x# mac-auth
config>port>ethernet>dot1x# mac-auth-wait 20
config>port>ethernet>dot1x# port-control auto
config>port>ethernet>dot1x# quiet-period 60
config>port>ethernet>dot1x# radius-plcy dot1xpolicy
Sample port configuration output
Use the info detail command to display port configuration information.
SAS-T>config>port>ethernet>dot1x# info detail
----------------------------------------------
port-control auto
radius-plcy dot1xpolicy
re-authentication
re-auth-period 3600
max-auth-req 2
transmit-period 30
quiet-period 60
supplicant-timeout 30
server-timeout 30
mac-auth
mac-auth-wait 20
----------------------------------------------
SAS-T>config>port>ethernet>dot1x#
Configuring VLAN authentication port parameters
VLAN authentication is only supported on 7210 SAS-Dxp.
The 7210 SAS supports VLAN authentication for client devices (for example, PCs and STBs) on an Ethernet network.
VLAN authentication provides protection against unauthorized access by forcing the device connected to the 7210 SAS to be authenticated by a RADIUS server before the device is able to transmit packets through the 7210 SAS.
Use the following CLI syntax to configure VLAN authentication for an Ethernet port.
port port-id ethernet
dot1x
vlan-auth
port-control auto
quiet-period seconds
radius-plcy name
Command usage to configure VLAN authentication for an Ethernet port
config# port 1/1/2 ethernet dot1x
config>port>ethernet>dot1x# vlan-auth
config>port>ethernet>dot1x# port-control auto
config>port>ethernet>dot1x# quiet-period 60
config>port>ethernet>dot1x# radius-plcy dot1xpolicy
Sample port configureation output
Use the info detail command to display port configuration information.
SAS-T>config>port>ethernet>dot1x# info detail
----------------------------------------------
port-control auto
radius-plcy dot1xpolicy
re-authentication
re-auth-period 3600
max-auth-req 2
transmit-period 30
quiet-period 60
supplicant-timeout 30
server-timeout 30
vlan-auth
----------------------------------------------
SAS-T>config>port>ethernet>dot1x#
Configuring LAG parameters
The following are general rules for configuring LAGs:
The 7210 SAS-D and 7210 SAS-Dxp support up to four 1GE ports in a LAG. The 7210 SAS-Dxp also supports up to two 10GE ports in a LAG.
The 7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T support up to three 1GE ports in a LAG.
The 7210 SAS-K 3SFP+ 8C supports up to three 1GE ports or two 10GE ports in a LAG.
All ports in the LAG must share the same characteristics (speed, duplex, hold-timer, and so on). The port characteristics are inherited from the primary port.
Autonegotiation must be disabled or set to limited mode for ports that are part of a LAG to guarantee a specific port speed.
Ports in a LAG must be configured as full duplex.
The following is a sample LAG configuration output.
A:ALA-A>config>lag# info detail
----------------------------------------------
description "LAG2"
mac 04:68:ff:00:00:01
port 1/1/1
port 1/3/1
----------------------------------------------
A:ALA-A>config>lag#
A:ALA-A>config>lag# info detail
----------------------------------------------
description "LAG2"
mac 04:68:ff:00:00:01
port 1/1/1
port 1/1/2
port 1/1/3
dynamic-cost
port-threshold 2 action down
----------------------------------------------
A:ALA-A>config>lag#
CRC error monitoring
This feature is supported on all 7210 SAS platforms as described in this document, except the 7210 SAS-K 2F1C2T.
This feature allows the user to track CRC (cyclic redundancy check) errors received on a specific port and notify them. The detection mechanism is based around a configurable threshold specified by the administrator. Two thresholds are configurable, one for CRC degrade and one for CRC signal fail. The first threshold crossing generates an alarm, log entry, trap, but does not bring the physical port down, while the second (signal fail) threshold crossing logs an alarm, trap generation, and brings the port operationally down.
The thresholds are configurable with the following CLI command config>port>ethernet crc-monitor.
This behavior is enabled on a per-port basis. By default, the command and functionality is disabled for the signal degrade and the signal fail.
The user can configure different values for the sf-threshold and the sd-threshold. However, sf-threshold value must be less than or equal to the sd-threshold value.
The values provided by the user for threshold and multiplier is used to compute the error ratio as (Multiplier * (10 ^ - (threshold value)). Port Stats are collected once per second and accumulated over the configured window size. Each second, the oldest sample is discarded and the new sample is added to a running total. If the error ratio exceeds the configured threshold (the preceding computation) over the window size for two consecutive seconds, appropriate actions are taken as follows:
If the number of CRC errors exceeds the signal degrade threshold value, a log warning message, syslog event and SNMP trap with the message ‟CRC errors in excess of the configured degrade threshold <M>*10e-<N> Set” is raised.
If the CRC error rate increases further and exceeds configured the signal fail threshold value, an alarm log message, syslog event and SNMP trap should be raised, and the port should be brought operationally down.
When the condition is cleared, a SNMP trap message to clear the event is sent out.
Service management tasks
This section describes basic procedures of the service management tasks:
To change an MDA type already provisioned for a specific slot/card, first you must shut down the slot/MDA/port configuration and then delete the MDA from the configuration. Modify and delete operations can be performed only on the MDAs that are not auto equipped or auto provisioned.
Use the following syntax to modify an MDA.
config> port port-id
shutdown
config> card slot-number
shutdown
[no] mda mda-number
[no] mda-type mda-type
shutdown
Modifying a card type
The modify operation cannot be performed on an IOM card that is auto equipped and auto provisioned during bootup and is fixed.
Deleting a card
The delete operation cannot be performed on an IOM card that is auto equipped and auto provisioned during bootup and is fixed.
Deleting port parameters
Use the following syntax to delete a port provisioned for a specific card.
config>port port-id
shutdown
no port port-id
Card, MDA, and port command reference
Command hierarchies
Configuration commands
Port buffer pool configuration commands for 7210 SAS-D and 7210 SAS-Dxp
Port-based split horizon group configuration commands for 7210 SAS-D and 7210 SAS-Dxp
Port commands for reserving resources of ports on 7210 SAS-Dxp
MACsec commands for 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
LAG commands for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Multi-chassis redundancy commands for 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Hardware commands
Port buffer pool configuration commands for 7210 SAS-D and 7210 SAS-Dxp
config
- port
- no port
- access
- egress
- [no] pool [name]
- slope-policy name
- no slope-policy
Port configuration commands
config
- port port-id
- no port
- description long-description-string
- no description
- ethernet
- [no] shutdown
Port configuration commands for PTP Port-based timestamp
config
- port port-id
- no port
- [no] ptp-hw-timestamp
Port-based split horizon group configuration commands for 7210 SAS-D and 7210 SAS-Dxp
Port Configuration Commands
config
- port
- no port
- split-horizon-group group-name
- no split-horizon-group
LAG Commands
config
- [no] lag [lag-id]
- [no] split-horizon-group group-name
Port commands for reserving resources of ports on 7210 SAS-Dxp
configure
- system
- loopback-no-svc-port [mirror | mac-swap | testhead] port-id
- no loopback-no-svc-port
MACsec commands for 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
config
- macsec
- connectivity-association ca-name [create]
- no connectivity-association ca-name
- cipher-suite {cipher-suite}
- no cipher-suite
- clear-tag-mode clear-tag-mode
- no clear-tag-mode
- description description-string
- no description
- encryption-offset encryption-offset
- no encryption-offset
- [no] macsec-encrypt
- [no] replay-protection
- replay-window-size number-of-packets
- no replay-window-size
- [no] shutdown
- [no] static-cak
- active-psk active-pre-shared-key
- no active-psk
- mka-key-server-priority priority
- no mka-key-server-priority
- pre-shared-key pre-shared-key-index [encryption-type encryption-type] [create]
- no pre-shared-key pre-shared-key-index
- cak hex-string [hash | hash2]
- no cak
- ckn hex-string
- no ckn
Ethernet commands
Port Ethernet QoS commands
config
- [no] port {port-id}
- ethernet
- access
- accounting-policy acct-policy-id
- no accounting-policy
- [no] collect-stats
- egress
- qos policy-id
- no qos
- uplink
- accounting-policy acct-policy-id
- no accounting-policy
- [no] collect-stats
- qos policy-id
- no qos
- queue-policy name
- no queue-policy
- egress-rate sub-rate [max-burst size-in-kbits]
- no egress-rate
- egress-scheduler-policy port-scheduler-policy-name
- no egress-scheduler-policy
- [no] enable-dei
- network
- accounting-policy policy-id
- no accounting-policy
- [no] collect-stats
- nw-egr-agg-shaper-rate rate
- no nw-egr-agg-shaper-rate
- qos policy-id
- no qos
- queue-policy name
- no queue-policy
- statistics
- egress
Port Ethernet commands
config
- [no] port {port-id}
- ethernet
- autonegotiate [limited]
- [no] autonegotiate
- connection-type connection-type
- down-on-internal-error
- no down-on-internal-error
- duplex {full | half}
- dot1q-etype value
- no dot1q-etype
- encap-type {dot1q | null | qinq}
- no encap-type
- [no] eth-bn-egress-rate-changes
- eth-cfm
- [no] mep mep-id domain md-index association ma-index
- eth-bn
- [no] receive
- rx-update-pacing seconds
- frame-based-accounting
- no frame-based-accounting
- hold-time {[up hold-time up] [down hold-time down] [seconds| centiseconds]}
- no hold-time
- [no] lacp-tunnel
- [no] loopback {internal} [service svc-id sap sap-id src-mac SA dst-mac DA]
- mac ieee-address
- no mac
- mode access [uplink]
- mode hybrid
- mode network
- no mode
- monitor-oper-group name
- no monitor-oper-group
- mtu mtu-bytes
- no mtu
- no oper-group
- oper-group name
- poe [plus] [plusplus] [hpoe]
- no poe
- qinq-etype value
- no qinq-etype
- speed {10 | 100 | 1000}
- [no] shutdown
Port Ethernet CRC monitoring commands for 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
config
- [no] port {port-id}
- ethernet
- crc-monitor
- [no] sd-threshold threshold [multiplier multiplier]
- [no] sf-threshold threshold [multiplier multiplier]
- [no] window-size seconds
Port Ethernet 802.1x commands
config
- [no] port {port-id}
- ethernet
- dot1x
- [no] mac-auth
- mac-auth-wait seconds
- no mac-auth-wait
- max-auth-req max-auth-request
- port-control {auto | force-auth | force-unauth}
- quiet-period seconds
- [no] radius-plcy name
- re-auth-period seconds
- [no] re-authentication
- server-timeout seconds
- no server-timeout
- supplicant-timeout seconds
- no supplicant-timeout
- transmit-period seconds
- no transmit-period
- [no] tunneling
- [no] vlan-auth
Port Ethernet 802.1x MACsec commands for 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
config
- [no] port {port-id}
- ethernet
- dot1x
- [no] macsec
- ca-name ca-name
- no ca-name
- eapol-destination-address mac
- no eapol-destination-address
- [no] exclude-protocol {protocol-name}
- max-peer max-peer
- no max-peer
- [no] rx-must-be-encrypted
- [no] shutdown
Port Ethernet down-when-looped commands
config
- [no] port {port-id}
- ethernet
- down-on-internal-error
- no down-on-internal-error
- down-when-looped
- keep-alive timer
- no keep-alive
- retry-timeout timer
- no retry-timeout
- [no] shutdown
Port Ethernet EFM OAM commands
config
- [no] port {port-id}
- ethernet
- egress-rate
- [no] accept-remote-loopback
- mode {active | passive}
- [no] shutdown
- [no] transmit-interval interval [multiplier multiplier]
- [no] tunneling
Port Ethernet LLDP commands
config
- [no] port {port-id}
- ethernet
- lldp
- [no] tunnel-nearest-bridge-dest-mac
- dest-mac {nearest-bridge | nearest-non-tpmr | nearest-customer}
- admin-status {rx | tx | tx-rx | disabled}
- lldp-med
- admin-status {tx-rx | disabled}
- no admin-status
- network-policy policy-id [policy-id...(up to 4 max)]
- no network-policy
- tx-tlvs [network-policy] [mac-phy-config-status]
- no tx-tlvs
- [no] notification
- port-id-subtype {tx-if-alias | tx-if-name | tx-local}
- no port-id-subtype
- tx-mgmt-address [system] [system-ipv6]
- no tx-mgmt-address
- tx-tlvs [port-desc] [sys-name] [sys-desc] [sys-cap]
- no tx-tlvs
Port Ethernet sync commands for 7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
config
- [no] port {port-id}
- ethernet
- no port-clock
- port-clock {master | slave | automatic}
- ssm
- [no] shutdown
- [no] code-type sonet | sdh
- [no] tx-dus
LAG commands for 7210 SAS-D and 7210 SAS-Dxp
config
- [no] lag [lag-id]
- description long-description-string
- no description
- [no] enable-dei
- encap-type {dot1q | null | qinq}
- no encap-type
- hold-time down hold-down-time
- no hold-time
- lacp [mode] [administrative-key admin-key] [system-id system-id] [system-priority priority]
- lacp-xmit-interval {slow | fast}
- no lacp-xmit-interval
- [no] lacp-xmit-stdby
- mac ieee-address
- no mac
- mode access [uplink]
- no mode
- port port-id [port-id …up to N total] [priority priority] [sub-group sub-group-id]
- no port port-id [port-id …up to N total]
- port-threshold value [action {down}]
- no port-threshold
- selection-criteria [{highest-count | highest-weight | best-port}] [slave-to-partner]
- no selection-criteria
- standby-signalling {lacp | power-off}
- no standby-signalling
- [no] shutdown
LAG commands for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
config
- [no] lag [lag-id]
- description long-description-string
- no description
- [no] dynamic-cost
- encap-type {dot1q|null|qinq}
- no encap-type
- hold-time down hold-down-time
- no hold-time
- lacp [mode] [administrative-key admin-key] [system-id system-id] [system-priority priority]
- lacp-xmit-interval {slow | fast}
- no lacp-xmit-interval
- mac ieee-address
- no mac
- mode access [uplink]
- mode network
- no mode
- port port-id [port-id …up to 4 total] [priority priority]
- no port port-id [port-id …up to 4 total]
- port-threshold value [action {down}]
- no port-threshold
- selection-criteria [{highest-count| highest-weight | best-port}] [slave-to-partner]
- no selection-criteria
- standby-signalling {lacp | power-off}
- no standby-signalling
- [no] shutdown
Multi-chassis redundancy commands for 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
config
- redundancy
- multi-chassis
- [no] peer ip-address [create]
- authentication-key [authentication-key | hash-key] [hash | hash2]
- no authentication-key
- description description-string
- no description
- [no] mc-lag
- hold-on-neighbor-failure multiplier
- no hold-on-neighbor-failure
- keep-alive-interval interval
- no keep-alive-interval
- lag lag-id lacp-key admin-key system-id system-id [remote-lag remote-lag-id] system-priority system-priority
- lag remote-lag remote-lag-id]
- no lag lag-id
- [no] shutdown
- peer-name
- no peer-name
- [no] shutdown
- source-address ip-address
- no source-address
- [no] sync
- [no] igmp-snooping
- port [port-id | lag-id] [sync-tag sync-tag] [create]
- no port [port-id | lag-id]
- range encap-range [sync-tag sync-tag]
- no range encap-range
- [no] shutdown
Ethernet ring commands
config
- eth-ring ring-id
- no eth-ring
- [no] ccm-hold-time {down down-timeout | up up-timeout}
- [no] compatible-version version
- description description-string
- no description
- [no] guard-time time
- [no] revert-time time
- [no] rpl-node {owner | nbr}
- [no] node-id mac
- [no] sub-ring {virtual-link | non-virtual-link}
- [no] path {a | b} [{port-id} raps-tag qtag[.qtag] ]
- description description-string
- [no] rpl-end
- eth-cfm
- [no] mep mep-id domain md-index association ma-index
- [no] ccm-enable
- [no] ccm-ltm-priority priority
- [no] control-mep
- [no] description description-string
- [no] eth-test-enable
- [no] test-pattern {all-zeros | all-ones} [crc-enable]
- bit-error-threshold bit-errors
- mac-address mac-address
- one-way-delay-threshold seconds
- [no] shutdown
- [no] shutdown
Show commands
show
- chassis [environment] [power-supply]
- card [slot-number] [detail]
- card state
- pools mda-id[/port] [access-app [pool-name]]
- pools mda-id[/port] [network-app [pool-name]]
- lag [lag-id] [detail] [statistics]
- lag lag-id associations
- lag [lag-id] description
- lag [lag-id] port
- port port-id [count] [statistics] [detail]
- port port-id description
- port port-id associations
- port port-id dot1x [detail]
- port port-id ethernet [efm-oam | detail]
- port port-id optical
- port [A1] [detail] [statistics] [description]
- ethernet
- lldp [nearest-bridge | nearest-non-tpmr | nearest-customer] [remote-info] [detail] [lldp-med]
- redundancy
- multi-chassis all
- mc-lag peer ip-address [lag lag-id]
- mc-lag [peer ip-address [lag lag-id]] statistics
- sync peer [ip-address]
- sync peer [ip-address] detail
- sync peer [ip-address] statistics
- system
- internal-loopback-ports [detail]
- lldp
- lldp neighbor
- poe [detail]
MACsec show commands for 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
show
- macsec
- connectivity-association [ca-name] [detail]
- mka-session [port port-id]
- mka-session [port port-id] detail
- mka-session [port port-id] statistics
Monitor commands
Monitor
- port port-id [port-id...(up to 5 max)] [interval seconds] [repeat repeat] [absolute | rate]
Clear commands
Debug commands
Command descriptions
Configuration commands
Generic commands
description
Syntax
description long description-string
no description
Context
config>port
config>lag
config>split-horizon-group
config>macsec>connectivity-association
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates a text description for a configuration context to help identify the content in the configuration file.
The no form of this command removes any description string from the context.
Parameters
- long-description-string
The description character string. Strings can be up to 160 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>card
config>card>mda
config>port
config>port>ethernet
config>lag
config>port>ethernet>ssm
config>redundancy>multi-chassis>peer
config>redundancy>multi-chassis>peer>mc-lag
config>redundancy>multi-chassis>peer>sync
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively disables an entity. When disabled, an entity does not change, reset, or remove any configuration settings or statistics. The operational state of the entity is disabled as well as the operational state of any entities contained within.
The no form of this command administratively enables an entity.
Default
the default state for a card is no shutdown
the default state for an mda is no shutdown
the default state for a Link Aggregation Group (LAG) is shutdown
the default state for a port is shutdown
Card commands
card
Syntax
card slot-number
Context
config
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This mandatory command enables the context to access the chassis card Input/Output Module (IOM), slot, and MDA CLI context.
The no form of this command cannot be used on fixed IOM and MDA cards that are auto equipped and auto provisioned. The IOM card is equipped and provisioned for slot 1.
Parameters
- slot-number
Specifies the slot number of the card in the chassis.
card-type
Syntax
card-type card-type
Context
config>card
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This mandatory command adds a card type to the device configuration for the slot. The card type can be preprovisioned, meaning that the card does not need to be installed in the chassis.
A card must be provisioned before an MDA or port can be configured.
A card can only be provisioned in a slot that is vacant, meaning no other card can be provisioned (configured) for that particular slot.
A card can only be provisioned in a slot if the card type is allowed in the slot. An error message is generated if an attempt is made to provision a card type that is not allowed.
A high severity alarm is raised if an administratively enabled card is removed from the chassis. The alarm is cleared when the correct card type is installed or the configuration is modified. A low severity trap is issued when a card is removed that is administratively disabled.
An appropriate alarm is raised if a partial or complete card failure is detected. The alarm is cleared when the error condition ceases.
The no form of this command cannot be used as the card is fixed.
Default
the card is equipped and preprovisioned for slot 1
Parameters
- card-type
Specifies the type of card to be configured and installed in that slot.
MDA commands
mda
Syntax
mda mda-slot
no mda mda-slot
Context
config>card
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This mandatory command enables the MDA CLI context to configure MDAs.
Default
1
Parameters
- mda-slot
Specifies the MDA slot number to be configured. Fixed ports on the panel of the chassis belong to MDA 1.
mda-type
Syntax
mda-type mda-type
no mda-type
Context
config>card>mda
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This mandatory command provisions a specific MDA type to the device configuration for the slot. The MDA can be preprovisioned but an MDA must be provisioned before ports can be configured. Ports can be configured when the MDA is properly provisioned.
7210 SAS-D and 7210 SAS-Dxp (all platform variants) support only a fixed MDA. These platforms do not support an expansion slot. The fixed MDA (addressed as mda 1) is auto-equipped and auto-provisioned on bootup. It cannot be deleted.
The no form of this command displays an error message if performed on fixed MDAs.
Default
MDA 1 is auto-equipped and auto-provisioned by default during bootup.
Parameters
- mda-type
Specifies the type of MDA selected for the slot position.
sync-e
Syntax
[no] sync-e
Context
config>card>mda
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables Synchronous Ethernet on the Ethernet ports that support Synchronous Ethernet. When Synchronous Ethernet is enabled, the timing information is derived from the Ethernet ports.
Synchronous Ethernet is supported for both Ethernet SFP ports and fixed copper ports.
See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide for more information about Synchronous Ethernet.
The no form of this command disables Synchronous Ethernet on the MDA.
Default
no sync-e
Interface QoS commands
access
Syntax
access
Context
config>port
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure QoS policy parameters on an access port.
uplink
Syntax
uplink
Context
config>port>access
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure QoS policy parameters on an access-uplink port.
egress
Syntax
egress
Context
config>port>access
config>port>access>uplink
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure QoS egress policy parameters for the access port on 7210 SAS-D and 7210 SAS-Dxp, and for the access-uplink port on 7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C respectively.
pool
Syntax
[no] pool [name]
Context
config>port>access>egress
config>port>access>uplink>egress
Platforms
7210 SAS-D, 7210 SAS-Dxp
Description
This command configures pool policies.
The default pool cannot be modified, deleted or created.
Default
default
Parameters
- name
Specifies the pool name, a string up to 32 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
slope-policy
Syntax
slope-policy name
no slope-policy
Context
config>port>access>egress>pool
config>port>access>uplink>egress>pool
Platforms
7210 SAS-D, 7210 SAS-Dxp
Description
This command specifies an existing slope policy which defines high and low priority RED slope parameters. The policy is defined in the config>qos>slope-policy context.
Parameters
- name
Specifies the policy name, a string up to 32 characters.
qos
Syntax
qos policy-id
no qos
Context
config>port>ethernet>access>egress
Platforms
7210 SAS-D, 7210 SAS-Dxp
Description
This command associates a access-egress QoS policy to the access port.
The no form of this policy removes the explicit association of a user configured QoS policy and associates a default QoS policy with the port.
Parameters
- policy-id
Specifies an existing QoS policy to be assigned to the port.
qos
Syntax
qos policy-id
no qos
Context
config>port>ethernet>access>uplink
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command associates a network QoS policy with the access-uplink port.
Parameters
- policy-id
Specifies an existing QoS policy to be assigned to the port.
nw-egr-agg-shaper-rate
Syntax
nw-egr-agg-shaper-rate rate
no nw-egr-agg-shaper-rate
Context
config>port>ethernet>network
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the network egress aggregate shaper rate for port queues. The shaper value limits the maximum bandwidth that port queues can receive from the total port bandwidth, with remaining port bandwidth shared by SAPs on the port. This command is only supported on hybrid ports.
The no form of this command removes the configured egress aggregate shaper rate.
Default
no nw-egr-agg-shaper-rate
Parameters
- rate
Specifies the egress aggregate shaper rate in kb/s.
qos
Syntax
qos policy-id
no qos
Context
config>port>ethernet>network
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command associates a network QoS policy to a network port.
Parameters
- policy-id
Specifies an existing QoS policy to be assigned to the port.
General port commands
port
Syntax
port port-id
no port
Context
config
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures ports. Before a port can be configured, the chassis slot must be provisioned with a valid card type and the MDA parameter must be provisioned with a valid MDA type. (See card and mda commands.) All ports must be explicitly configured and enabled
Parameters
- port-id
Specifies the physical port ID in the slot/mda/port format.
enable-dei
Syntax
[no] enable-dei
Context
config>port>ethernet
config>lag
Platforms
7210 SAS-D, 7210 SAS-Dxp
Description
This command enables DEI-based classification on access ports, network ports, access-uplink or hybrid ports.
If enabled, DEI value in the Ethernet packet header is used to determine the initial profile/color of the packet when the meter/policer used to police the FC is configured in color-aware mode. If the meter used to police the FC is configured in color-blind mode, then the DEI value of the packet has no effect. When in color-aware mode, DEI value of 0 is interpreted as in-profile or green packet and DEI value of 1 is interpreted as out-of-profile or yellow packet. In color-aware mode, the following behavior is accorded to packets classified with initial profile/color as in-profile/green and out-of-profile/yellow:
If a green packet is received and the color-aware meter is within the CIR rate, then packet is assigned a final profile of green and it is assigned a final profile of yellow if the meter exceeds the CIR rate and is within the PIR rate.
If a yellow packet is received and the color-aware meter is above the CIR rate and within the PIR rate, then the packet is assigned a final profile of yellow.
That is, in color-aware mode, yellow/out-of-profile packets cannot eat into the CIR bandwidth. It is exclusively reserved for green/in-profile packets.
The final profile assigned at ingress is used by egress to determine the WRED slope to use. The WRED slope determines whether the packet is eligible to be assigned a buffer and can be queued up on egress queue for transmission.
See the 7210 SAS-D, Dxp Quality of Service Guide for more information.
Default
no enable-dei
egress-scheduler-policy
Syntax
egress-scheduler-policy port-scheduler-policy-name
no egress-scheduler-policy
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp
Description
This command configures the scheduling behavior to the one specified in the policy (Strict, RR, WRR, WDRR, WRR/WDRR + Strict).
The no form of this command removes the policy from the port and makes the scheduling scheme of the port to strict.
Parameters
- port-scheduler-policy-name
Specifies a port scheduler policy for the port.
mode
Syntax
mode access [uplink]
mode hybrid
mode network
no mode
Context
config>port>ethernet
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures an Ethernet port for access mode, access-uplink mode, hybrid mode, or network mode of operation.
The following modes are supported on the 7210 SAS platforms:
The 7210 SAS-D, 7210 SAS-Dxp, and 7210 SAS-K 2F1C2T support only access and access-uplink mode.
The 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C support access, access-uplink, hybrid, and network mode.
The functionality of the different modes is as follows:
Access — An access port is used for customer facing traffic on which services are configured. A Service Access Point (SAP) can only be configured on an access port. When a port is configured for access mode, the appropriate encap-type must be specified to distinguish the services on the port. When an Ethernet port has been configured for access mode, multiple services can be configured on the Ethernet port.
Access-uplink — Access-uplink ports are used to provide native Ethernet connectivity in service provider transport or infrastructure network. This can be achieved by configuring port mode as access uplink. With this option, the encap-type can be configured to only qinq. Access-uplink SAPs, which are QinQ SAPs, can only be configured on an access uplink port to allow the operator to differentiate multiple services being carried over a single access uplink port.
Network — A network port participates in the service provider transport or infrastructure network when a network mode is selected. When the network option is configured, the encap-type can be configured to either null or dot1q.
Hybrid — A hybrid Ethernet port allows the combination of network and access modes of operation on a per-VLAN basis and must be configured as either dot1q or QinQ encapsulation. When the hybrid port is configured with dot1q encapsulation, SAPs are configured in a service by providing the SAP ID, which must include the port-id value of the hybrid port and an unused VLAN tag value in the format port-id:qtag1. A SAP with the format port-id:* is also supported. Network IP interfaces are configured in the config>router>interface>port context by providing the port name, which consists of the port-id value of the hybrid port and an unused VLAN tag value in the format port-id:qtag1.
A valid value must be entered for qtag1. The port-id:* format is not supported on a network IP interface. The 4096 VLAN tag space on the port is shared among VLAN SAPs and VLAN network IP interfaces. When the hybrid port is configured with QinQ encapsulation, SAPs are configured in a service by providing the SAP ID, which must include the port-id value of the hybrid port and the outer and inner VLAN tag values in the format port-id:qtag1.qtag2. SAPS with the format port-id:qtag1.* are also supported. The outer VLAN tag value must not have been used to create an IP network interface on this port. In addition, the qtag1.qtag2 value combination must not have been used by another SAP on this port.
Network IP interfaces are configured in the config>router>interface>port context by providing the port name, which consists of the port-id value of the hybrid port and a VLAN tag value in the format port-id:qtag1.*. An outer VLAN tag qtag2 of * is used to create a network IP interface. In addition, the qtag1.qtag2 value combination must not have been used by another SAP or network IP interface on this port.
The no form of this command reverts to the default value.
Default
access (7210 SAS-D, 7210 SAS-Dxp, and 7210 SAS-K 2F1C2T)
network (7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C)
Parameters
- access
Specifies the Ethernet port as service access.
- access uplink
Specifies the Ethernet port for transport (Ethernet uplinks available only in access-uplink mode). A limited number of ports can be configured as access-uplink ports at any specified time on the 7210 SAS-Dxp.
- hybrid
Specifies the Ethernet port for hybrid use (available only in network mode).
- network
Specifies the Ethernet port as service access (available only in network mode).
monitor-oper-group
Syntax
monitor-oper-group name
no monitor-oper-group
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the operational group to be monitored by the object under which it is configured. The oper-group name must be already configured under the config>system context before its name is referenced in this command.
The no form of this command removes the association from the configuration.
Default
no monitor-oper-group
Parameters
- name
Specifies a character string of maximum 32 ASCII characters identifying the group instance.
mac
Syntax
mac ieee-address
no mac
Context
config>port>ethernet
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command assigns a specific MAC address to an Ethernet port, Link Aggregation Group (LAG).
Only one MAC address can be assigned to a port. When multiple mac commands are entered, the last command overwrites the previous command. When the command is issued while the port is operational, IP will issue an ARP, if appropriate, and BPDUs are sent with the new MAC address. A default MAC address is assigned by the system from the chassis MAC address pool.
The no form of this command reverts the MAC address to the default value.
Parameters
- ieee-address
Specifies the 48-bit MAC address in the form aa:bb:cc:dd:ee:ff or aa-bb-cc-dd-ee-ff where aa, bb, cc, dd, ee and ff are hexadecimal numbers. Allowed values are any non-broadcast, non-multicast MAC and non-IEEE reserved MAC addresses.
mtu
Syntax
mtu mtu-bytes
no mtu
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the maximum transmission unit (MTU) size for an Ethernet port. The Ethernet port level MTU parameter indirectly defines the largest physical packet the port can transmit or the far-end Ethernet port can receive. Packets received that are larger than the MTU value are discarded. Packets that cannot be fragmented at egress and exceed the MTU are discarded.
The value specified for the MTU includes the destination MAC address, source MAC address, the Ethertype or Length field and the complete Ethernet payload. The MTU value does not include the preamble, start of frame delimiter, or the trailing CRC.
The no form of this command reverts to the default values.
Default
The following table describes the default MTU values that are dependent on the (sub-)port type, mode, and encapsulation.
Type |
Mode |
Encap type |
Default (bytes) |
|---|---|---|---|
10/100, Gig |
Access |
null |
1514 |
10/100, Gig |
Access |
dot1q |
1518 |
10/100, Gig |
Access |
q-in-q |
1522 |
Parameters
- mtu-bytes
Specifies the maximum allowable size of the MTU, expressed as an integer.
ptp-hw-timestamp
Syntax
[no] ptp-hw-timestamp
Context
config>port
Platforms
7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Description
This command enables Precision Time Protocol (PTP) port-based hardware timestamping on the port in both egress and ingress directions. For more information about PTP port-based hardware timestamping, including configuration guidelines, see the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide.
The no version of this command disables PTP port-based hardware timestamping on the port.
Default
ptp-hw-timestamp
Port loopback commands
loopback-no-svc-port
Syntax
[no] loopback-no-svc-port [mirror | mac-swap | testhead] port-id
Context
config>system
Platforms
7210 SAS-Dxp
Description
This command specifies the port to assign for system use when using port loopback or for the mac-swap, mirroring, or testhead OAM tools. The system uses the resources of the port and the port is not available for configuring services.
The user cannot share a single port between multiple tools or applications if they intend to use the tools simultaneously. The system displays an error if the user tries to configure the same port for use with multiple OAM tools or if the user tries to use the tool without first configuring the port resources to be used by the tool.
The system verifies if any services are configured on the port specified with this command and if services are configured the command fails.
The no form of this command disables the use of this port by the specified OAM tool.
On 7210 SAS-Dxp, this command must be used and the user needs to dedicate one front-panel port for use with the mirroring applications.
On 7210 SAS-D (ETR and non-ETR variants), the user can use the 3 available internal ports (that is, port 1/1/11, 1/1/12, and 1/1/13) for use with either mac-swap or mirroring or testhead OAM tool. The user does not need to use this command and the internal port resources are automatically allocated to the ports by software to different OAM tools.
On 7210 SAS-Dxp, the three internal ports (ports 1/1/13, 1/1/14, and 1/1/15) can be used for mac-swap, mirroring, or testhead OAM tools. Port 1/1/13 is a 1GE port and is recommended for applications with traffic up to 1Gbps. Ports 1/1/14 and 1/1/15 are 10GE ports and are recommended for applications with traffic greater than 1Gbps but less than 10Gbps. The loopback-no-svc-port command must be used to associate the port resources with the applications. A port can be used with a single application and cannot be shared by multiple applications.
Parameters
- mac-swap
Specifies that the port is dedicated for use by the mac-swap application/OAM tool.
- mirror
Specifies that the port is dedicated for use by the mirroring application/OAM tool.
- testhead
Specifies that the port is dedicated for use by the testhead application/OAM tool.
- port-id
Specifies the physical port ID in the slot/mda/port format.
MACsec commands for 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
macsec
Syntax
macsec
Context
config
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command enables the context for MACsec configuration. The MACsec MKA profile can be configured in this context.
connectivity-association
Syntax
connectivity-association ca-name [create]
no connectivity-association ca-name
Context
config>macsec
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command configures a connectivity association (CA). MACsec CAs are applied to a port dot1x configuration to enable MACsec on that port.
The no form of this command removes the CA.
Parameters
- ca-name
-
Specifies the name of the CA using a string of up to 32 characters.
- create
-
Specifies a mandatory keyword when creating an entry.
cipher-suite
Syntax
cipher-suite cipher-suite
no cipher-suite
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command configures encryption of datapath PDUs. When all parties in the CA have the security association key (SAK), they use the algorithm specified by the cipher-suite parameter, in conjunction with the SAK, to encrypt the datapath PDUs.
The no form of this command disables encryption of datapath PDUs.
Default
cipher-suite gcm-aes-128
Parameters
- cipher-suite
-
Specifies the algorithm to use for control plane encryption.
clear-tag-mode
Syntax
clear-tag-mode clear-tag-mode
no clear-tag-mode
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command puts 802.1Q tags in clear before SecTAG. The following modes are available: single-tag and dual-tag.
The following table describes the encrypted dot1q and QinQ packet format when clear-tag-mode (single-tag or dual-tag) is configured.
|
Unencrypted format |
Clear-tag-mode |
Pre-encryption (Tx) |
Pre-decryption (Rx) |
|---|---|---|---|
|
Single tag (dot1q) |
single-tag |
DA, SA, TPID, VID, Etype |
DA, SA, TPID, VID, SecTag |
|
Single tag (dot1q) |
dual-tag |
DA, SA, TPID, VID, Etype |
DA, SA, TPID, VID, SecTag |
|
Double tag (q-in-q) |
single-tag |
DA, SA, TPID1, VID1, IPID2, VID2, Etype |
DA, SA, TPID1, VID1, SecTag |
|
Double tag (QinQ) |
dual-tag |
DA, SA, TPID1, VID1, IPID2, VID2, Etype |
DA, SA, TPID1, VID1, IPID2, VID2, SecTag |
The no form of this command puts all dot1q tags after SecTAG and encrypts the tags.
Default
no clear-tag-mode
Parameters
- clear-tag-mode
-
Specifies the clear tag mode.
description
Syntax
description description-string
no description
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command enters a description for the CA.
The no form of this command removes the CA description.
Parameters
- description-string
-
Specifies a brief description of the CA using a string of up to 80 characters.
encryption-offset
Syntax
encryption-offset encryption-offset
no encryption-offset
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies the offset of the encryption in MACsec packets.
The encryption offset is distributed by the MKA to all parties and is signaled via MACsec capabilities.
The following table describes the basic settings.
|
Setting |
Description |
|---|---|
|
0 |
MACsec is not implemented |
|
1 |
Integrity without confidentiality |
|
2 |
The following are supported:
|
3 11 |
The following are supported:
|
The no form of this command rejects all arriving traffic regardless of whether it is MACsec-secured.
Default
encryption-offset 0
Parameters
- encryption-offset
-
Specifies the encryption offset.
macsec-encrypt
Syntax
[no] macsec-encrypt
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command enables encryption and authentication (ICV payload) for all PDUs.
The no form of this command specifies that all PDUs are transmitted in cleartext form but still authenticated and have the trailing ICV.
Default
macsec-encrypt
replay-protection
Syntax
[no] replay-protection
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command configures the size of the replay protection window.
This command must be configured to force packet discard when the system detects a packet that is not within the parameters configured for the replay-window-size command.
When this command is enabled, the sequence of the ID number of the received packets is checked. If the packet arrives out of sequence, and the difference between the packet numbers exceeds the replay window size, the packet is counted by the receiving port and then discarded. For example, if the replay protection window size is set to 5 and a packet assigned the ID of 1006 arrives on the receiving link immediately after the packet assigned the ID of 1000, the packet that is assigned the ID of 1006 is counted and discarded because it falls outside the parameters of the replay-window-size command.
Replay protection is especially useful for fighting man-in-the-middle attacks. A packet that is replayed by a man-in-the-middle attacker on the Ethernet link arrives on the receiving link out of sequence, so replay protection helps ensure the replayed packet is dropped instead of forwarded through the network.
Replay protection should not be enabled in cases where packets are expected to arrive out of order.
Default
replay-protection
replay-window-size
Syntax
replay-window-size number-of-packets
no replay-window-size
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies the size of the replay protection window.
This command must be configured to enable the replay-protection command.
When the number-of-packets parameter is set to 0, all packets that arrive out of order are dropped.
The no form of this command reverts to the default value.
Default
replay-window-size 0
Parameters
- number-of-packets
-
Specifies the window that the packets can arrive out of order.
shutdown
Syntax
[no] shutdown
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command shuts down the CA profile. All ports using this profile do not transmit PDUs because this command shuts down MACsec for this profile.
The no form of this command enables the CA profile.
Default
shutdown
static-cak
Syntax
[no] static-cak
Context
config>macsec>connectivity-association
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
Commands in this context configure a Connectivity Association Key (CAK). A CAK is responsible for managing the MACsec key agreement (MKA).
active-psk
Syntax
active-psk active-pre-shared-key
no active-psk
Context
config>macsec>conn-assoc>static-cak
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies which preshared key is the active transmitting preshared key. If there are two preshared keys configured, the arriving MACsec MKA can be decrypted using CAKs of both preshared keys; however, only the active PSK is used for Tx encryption of MKA PDUs.
Default
active-psk 1
Parameters
- active-pre-shared-key
-
Specifies the value of the preshared key.
mka-key-server-priority
Syntax
mka-key-server-priority priority
no mka-key-server-priority
Context
config>macsec>conn-associ>static-cak
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies the key server priority used by the MKA protocol to select the key server when MACsec is enabled using the static CAK security mode.
The no form of this command disables this command.
Default
mka-key-server-priority 16
Parameters
- priority
-
Specifies the priority of the server.
pre-shared-key
Syntax
pre-shared-key pre-shared-key-index [encryption-type encryption-type] [create]
no pre-shared-key pre-shared-key-index
Context
config>macsec>conn-assoc>static-cak
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies the preshared key used to enable MACsec using the static CAK security mode. This command also specifies the encryption algorithm used for encrypting the SAK.
A preshared key includes a connectivity association key name (CKN) and a CAK. The preshared key (the CKN and CAK) must match on both ends of a link.
A preshared key is configured on both devices at each end of a point-to-point link to enable MACsec using static CAK security mode. The MKA protocol is enabled after the successful MKA liveliness negotiation.
The encryption-type parameter is used to encrypt SAK and authentication of the MKA packet. The symmetric encryption key SAK needs to be encrypted (wrapped) using the encryption algorithm specified with the encryption-type parameter. The AES key is derived using the preshared key.
The no form of this command removes the index.
Parameters
- pre-shared-key-index
-
Specifies the index of this preshared key.
- encryption-type
-
Specifies the type of encryption.
- create
-
Specifies a mandatory keyword when creating an entry.
cak
Syntax
cak hex-string [hash | hash2]
no cak
Context
config>macsec>conn-assoc>static-cak>pre-shared-key
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command configures the CAK for a preshared key. The following values are derived from the CAK:
-
KEK (Key Encryption Key)
KEK is used to encrypt the MKA and SAK (symmetric key used for datapath PDUs) to be distributed between all members.
-
ICK (Integrity Check Value)
ICK is used to authenticate the MKA and SAK PDUs to be distributed between all members.
The no form of this command removes the CAK hexidecimal string value.
Parameters
- hex-string
-
Specifies the value of the CAK using up to 64 hexadecimal characters, 32 hexadecimal characters for a 128-bit key, and 64 hexadecimal characters for a 256-bit key.
- hash
-
Specifies the hash scheme.
- hash2
-
Specifies the hash scheme.
ckn
Syntax
ckn hex-string
no ckn
Context
config>macsec>conn-assoc>static-cak>pre-shared-key
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command specifies the connectivity association key name (CKN) for a preshared key.
The CKN is appended to the MKA for identification of the CAK by the peer.
The no form of this command removes the CKN.
Parameters
- hex-string
-
Specifies the value of the CKN.
Ethernet port commands
ethernet
Syntax
ethernet
Context
config>port
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure access parameters.
This context can only be used when configuring Ethernet LAN ports on an appropriate MDA.
autonegotiate
Syntax
autonegotiate [limited]
no autonegotiate
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables speed and duplex autonegotiation on Fast Ethernet ports and enables far-end fault indicator support on gigabit ports.
There are three possible settings for autonegotiation:
‟on” or enabled with full port capabilities advertised
‟off” or disabled where there are no autonegotiation advertisements
‟limited” where a single speed/duplex is advertised.
When autonegotiation is enabled on a port, the link attempts to automatically negotiate the link speed and duplex parameters. If autonegotiation is enabled, the configured duplex and speed parameters are ignored.
When autonegotiation is disabled on a port, the port does not attempt to autonegotiate and will only operate at the speed and duplex settings configured for the port. Note that disabling autonegotiation on gigabit ports is not allowed as the IEEE 802.3 specification for gigabit Ethernet requires autonegotiation be enabled for far end fault indication.
If the autonegotiate limited keyword option is specified, the port will autonegotiate but will only advertise a specific speed and duplex. The speed and duplex advertised are the speed and duplex settings configured for the port. One use for limited mode is for multispeed gigabit ports to force gigabit operation while keeping autonegotiation enabled for compliance with IEEE 801.3.
7210 SAS requires that autonegotiation be disabled or limited for ports in a Link Aggregation Group to guarantee a specific port speed.
The no form of this command disables autonegotiation on this port.
Default
autonegotiate
Parameters
- limited
Specifies tht the Ethernet interface will automatically negotiate link parameters with the far end, but will only advertise the speed and duplex mode specified by the Ethernet and commands.
connection-type
Syntax
connection-type connection-type
Context
config>port>ethernet
Platforms
7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command configures the connection type on the Ethernet combo port. The combo port provides two physical interface options to the user, SFP or copper. This command allows the user specify the physical interface that will be used.
When configured as SFP port it allows for fiber based connectivity with the flexibility of using suitable optics for longer reach. When configured as a fixed copper port it provides cheaper connectivity for shorter reach. The SFP port support 100/1000 speeds and the copper port can support 10/100/1000Mbps speed.
When configured as 'auto', software will attempt to detect the type of interface in use based on whether the copper cable is plugged in or the SFP optic is plugged in. It is not allowed to plug in copper cable and SFP optics into the Ethernet combo port at the same time.
When combo port is used for SyncE, the connection type has to be set to either sfp or copper. SyncE is not supported with connection-type as auto.
The combo port can be configured either as a SFP port or a copper port or set for automatic detection. That is, both the interfaces cannot be used simultaneously (even when 'auto' is set, software selects one of the ports based on the interface plugged in).
Default
sfp (7210 SAS-K 2F1C2T)
auto (7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C)
Parameters
- connection-type
Specifies the type of Ethernet combo port.
crc-monitor
Syntax
crc-monitor
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command configures Ethernet CRC Monitoring parameters.
sd-threshold
Syntax
[no] sd-threshold threshold [multiplier multiplier]
Context
config>port>ethernet>crc-monitor
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies the error rate at which to declare the Signal Failure condition on an Ethernet interface.
The value represents a ratio of errored frames over total frames received over seconds of the sliding window. The CRC errors on the interface are sampled once per second. A default of 10 seconds is used when there is no additional window-size configured. The multiplier keyword is optional.
The no form of this command reverts to the default value of 1. If the multiplier keyword is omitted, the multiplier will return to the default value of 1.
Default
no sd-threshold
Parameters
- threshold
Specifies the rate of CRC errored Ethernet frames.
- multiplier
Specifies the multiplier used to scale the CRC error ratio.
sf-threshold
Syntax
[no] sf-threshold threshold [multiplier multiplier]
Context
config>port>ethernet>crc-monitor
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies the error rate at which to declare the Signal Degrade condition on an Ethernet interface.
The value represents a ratio of errored frames over total frames received over seconds of the sliding window. The CRC errors on the interface are sampled once per second. A default of 10 seconds is used when there is no additional window-size configured.
The no form of this command reverts to the default value of 1. If the multiplier keyword is omitted, the multiplier will return to the default value of 1.
Default
no sf-threshold
Parameters
- threshold
Specifies the rate of CRC errored Ethernet frames.
- multiplier
Specifies the multiplier used to scale the CRC error ratio.
window-size
Syntax
[no] window-size seconds
Context
config>port>ethernet>crc-monitor
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies sliding window size over which the Ethernet frames are sampled to detect signal fail or signal degrade conditions. The command is used jointly with the sf-threshold and the sd-threshold to configure the sliding window size.
Default
10
Parameters
- seconds
Specifies the size of the sliding window in seconds over which the errors are measured.
down-on-internal-error
Syntax
[no] down-on-internal-error
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command brings a port operationally down in the event the systems has detected internal max transmit errors.
Default
no down-on-internal-error
dot1q-etype
Syntax
dot1q-etype value
no dot1q-etype
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies the Ethertype expected when the port's encapsulation type is dot1q. Dot1q encapsulation is supported only on Ethernet interfaces.
When the dot1-etype is configured to a value other than 0x8100 (the default value) on a port, the outermost tag in the received packet is matched against the configured value and if there is a match then it is treated as a Dot1q packet and the VLAN ID is used to match against the configured Dot1q SAPs on the port to find the Dot1q SAP the packet should be matched to.
This command does not change the etype used to match the inner tag for a QinQ SAP. The 7210 SAS devices always uses 0x8100 for matching the inner tag etype. That is, if this command is configured on a port configured for QinQ encapsulation, then it is ignored and 0x8100 is used always.
This command is supported only for access ports and hybrid ports. On hybrid ports, it applies to all traffic (that is, traffic mapped to SAPs and network IP interfaces). It is not supported for network ports.
Dot1q-preserve SAPs cannot be configured on dot1q encap ports configured to use Ethertype other than 0x8100.
Priority tagged packet received with etype 0x8100 on a dot1q port configured with etype 0x9100 is classified as a priority tagged packet and mapped to a dot1q:0 SAP (if configured) and the priority tag is removed.
Priority tagged packets received with etype 0x6666 (any value other than 0x8100) on a dot1q port configured with etype 0x9100 is classified as null-tagged packet and mapped to a dot1q:0 SAP (if configured) and the priority tag is retained and forwarded as expected.
The maximum number of unique dot1q-etypes configurable per node is limited. The resources needed for configuration of dot1q-etype is shared by the default dot1q-etype, default qinq-etype and user configured values for qinq-etype. That is, the number of unique dot1q-etypes allowed decreases, if the number of unique qinq-etype configured is more. The converse is also true.
The no form of this command reverts the dot1q-etype value to the default.
Parameters
- value
Specifies the Ethertype to expect, in decimal or hexadecimal format.
duplex
Syntax
duplex {full | half}
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the context for the configuration of the duplex mode of a Fast Ethernet port. If the port is configured to autonegotiate, this parameter is ignored.
Default
full
Parameters
- full
Sets the link to full duplex mode.
- half
Sets the link to half duplex mode.
egress-rate
Syntax
egress-rate sub-rate [max-burst size-in-kbits]
no egress-rate
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the rate of traffic leaving the network.
The no form of this command reverts to the default value.
For 7210 SAS-D and 7210 SAS-Dxp devices, the max-burst parameter configures a maximum-burst (in kilobits) associated with the egress-rate. This is an optional parameter; if not defined then, by default, it is set to 64 kbits for a 1G port and 98 kbits for a 10G port. The user cannot configure max-burst without configuring egress-rate. 7210 SAS-D devices do not support 10G ports. See the 7210 SAS-D, Dxp Quality of Service Guide for more information.
Default
no egress-rate
Parameters
- sub-rate
The egress rate in Kbps.
- max-burst size-in-kbits
Specifies the maximum egress burst in kilobits. This parameter is configurable only on 7210 SAS-D and 7210 SAS-Dxp.
efm-oam
Syntax
efm-oam
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure EFM-OAM attributes.
accept-remote-loopback
Syntax
[no] accept-remote-loopback
Context
config>port>ethernet>efm-oam
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables reactions to loopback control OAM PDUs from peers.
The no form of this command disables reactions to loopback control OAM PDUs.
Default
no accept-remote-loopback
mode
Syntax
mode {active | passive}
Context
config>port>ethernet>efm-oam
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the mode of OAM operation for this Ethernet port. These two modes differ in that active mode causes the port to continually send out efm-oam info PDUs while passive mode waits for the peer to initiate the negotiation process. A passive mode port cannot initiate monitoring activities (such as loopback) with the peer.
Default
active
Parameters
- active
Specifies that the port has the capability to initiate negotiation and monitoring activities.
- passive
Specifies that the port relies on peer to initiate negotiation and monitoring activities.
transmit-interval
Syntax
[no] transmit-interval interval [multiplier multiplier]
Context
config>port>ethernet>efm-oam
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the transmit interval of OAM PDUs.
The minimum efm-oam session time-out value supported is 300 milliseconds. That is, user can configure transmit-interval 1 multiplier 3 as the minimum value. This is applicable to all platforms except for the 7210 SAS-D. On the 7210 SAS-D, the minimum transmit interval is 500 msec and multiplier is 4.
Default
transmit-interval 10 multiplier 5
Parameters
- interval
Specifies the transmit interval, in 100 milliseconds.
- multiplier multiplier
Specifies the multiplier for transmit-interval to set local link down timer.
tunneling
Syntax
[no] tunneling
Context
config>port>ethernet>efm-oam
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables EFM OAM PDU tunneling. Enabling tunneling will allow a port mode Epipe SAP to pass OAM frames through the pipe to the far end.
The no form of this command disables tunneling.
Default
no tunneling
encap-type
Syntax
encap-type {dot1q | null | qinq}
no encap-type
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the encapsulation method used to distinguish customer traffic on an Ethernet access port, or different VLANs on a port.
On the 7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, the qinq encapsulation type can be configured for both access and access-uplink ports. The null and dot1q encapsulation types can be specified only for access ports.
On the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C, the null and dot1q encapsulation types can be specified for network ports. The dot1q and qinq encapsulation types can be specified for hybrid ports.
The no form of this command reverts to the default.
Default
encap-type null
Parameters
- dot1q
Specifies that the ingress frames carry 802.1Q tags where each tag signifies a different service.
- null
Specifies that the ingress frames will not use any tags to delineate a service. As a result, only one service can be configured on a port with a null encapsulation type.
- qinq
Specifies QinQ encapsulation for QinQ access SAPs.
eth-bn-egress-rate-changes
Syntax
[no] eth-bn-egress-rate-changes
Context
config>port>ethernet
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
This command allows rate changes received in ETH-BN messages on a port-based MEP to update the egress rate used on the port. The egress rate is capped by the minimum of the configured egress-rate and the maximum port rate.
The no form of this command reverts to the default value.
Default
no eth-bn-egress-rate-changes
eth-cfm
Syntax
eth-cfm
Context
config>port>ethernet
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
Commands in this context configure 802.1ag CFM parameters.
mep
Syntax
[no] mep mep-id domain md-index association ma-index
Context
config>port>ethernet>eth-cfm
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
This command provisions the maintenance endpoint (MEP).
The no form of this command removes the configuration.
Default
no mep
Parameters
- mep-id
Specifies the maintenance association endpoint identifier.
- md-index
Specifies the maintenance domain (MD) index value.
- ma-index
Specifies the MA index value.
eth-bn
Syntax
eth-bn
Context
config>port>ethernet>eth-cfm>mep
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
Commands in this context configure ETH-BN message handling.
receive
Syntax
[no] receive
Context
config>port>ethernet>eth-cfm>mep>eth-bn
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
This command enables the reception and processing of ETH-BN messages, and the retrieval and processing of the current bandwidth field for inclusion in dynamic egress rate adjustments.
The received rate is a Layer 2 rate, and is expected to be in Mb/s. If this rate is a link rate (including preamble, start frame delimiter, and inter-frame gap), it requires the configuration of frame-based accounting in the config>port>ethernet context.
The no form of this command disables the reception and processing of ETH-BN messages.
Default
no receive
rx-update-pacing
Syntax
rx-update-pacing seconds
Context
config>port>ethernet>eth-cfm>mep>eth-bn
Platforms
7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T
Description
This command sets the pace for update messages to and from the ETH-CFM subsystem to the QoS subsystem. The most recent update messages are held by the ETH-CFM subsystem, but the most recent update is held until the expiration of the pacing timer.
Default
rx-update-pacing 5
Parameters
- seconds
Specifies the time to wait before sending subsequent updates (in seconds).
frame-based-accounting
Syntax
frame-based-accounting
no frame-based-accounting
Context
config>port>ethernet
Platforms
7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command configures per port frame-based accounting. It can be enabled or disabled on each port. When enabled, all the shapers rates and queues statistics on that port also account for the Ethernet Layer 1 overhead (of 20 bytes) in both ingress and egress direction. That is all ingress queue shaper rates, egress queue shaper rates and aggregate SAP shaper rate account for the Ethernet overhead.
The no form of this command disables frame-based-accounting.
Default
no frame-based-accounting
hold-time
Syntax
hold-time {[up hold-time up] [down hold-time] [seconds | centiseconds]}
no hold-time
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures port link dampening timers which reduce the number of link transitions reported to upper layer protocols. The hold-time value is used to dampen interface transitions.
When an interface transitions from an up state to a down state, it is immediately advertised to the rest of the system if the hold-time down interval is zero, but if the hold-time down interval is greater than zero, interface down transitions are not advertised to upper layers until the hold-time down interval has expired. Likewise, an interface is immediately advertised as up to the rest of the system if the hold-time up interval is zero, but if the hold-time up interval is greater than zero, up transitions are not advertised until the hold-time up interval has expired.
The no form of this command reverts to the default values.
Default
hold-time up 0 down 0 seconds
Parameters
- up hold-timeup
Specifies the delay, in seconds or centiseconds, to notify the upper layers after an interface transitions from a down state to an up state.
- down hold-time down
Specifies the delay, in seconds or centiseconds, to notify the upper layers after an interface transitions from an up state to a down state.
- seconds | centiseconds
Specifies the units of the hold time in seconds or centiseconds.
lacp-tunnel
Syntax
[no] lacp-tunnel
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command enables LACP packet tunneling for the Ethernet port. When tunneling is enabled, the port will not process any LACP packets but will tunnel them instead. The port cannot be added as a member to a LAG group.
The no form of this command disables LACP packet tunneling for the Ethernet port.
Default
no lacp-tunnel
oper-group
Syntax
no oper-group
oper-group name
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command associates the context to which it is configured to the operational group specified in the group-name. The oper-group group-name must be already configured under config>system context before its name is referenced in this command.
The no form of this command removes the association.
Parameters
- name
Specifies a character string of maximum 32 ASCII characters identifying the group instance.
poe
Syntax
poe [plus] [plusplus] [hpoe]
no poe
Context
config>port>ethernet
Platforms
7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p
Description
This command enables PoE on the specified port and allows the user to configure the PoE device (PD) type that can be connected to the port.
This command must be used to enable PoE on a port before connecting a PD to the port. When a PD is connected to an enabled port, the software attempts to detect the type of device (that is, PoE, PoE+, PoE++, or HPoE) and the power it is requesting. If the detection is successful and the power request is within the maximum PoE power budget configured, power is supplied to the connected device. Otherwise, the request is denied and no power is provided to the port.
The user must configure the maximum PoE power budget for the system using the configure system poe max-poe-power-budget command before enabling PoE on any port. See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Basic System Configuration Guide for more information about this command.
The no form of this command disables PoE, PoE+, PoE++, and HPoE capabilities on the specified port. If PoE is disabled, the software does not attempt to detect the characteristics of the connected PD.
Default
poe
Parameters
- plus
Keyword to support PoE+ and allow 802.3at (Type-2) PoE devices to be connected to the port and request up to 30 W.
- plusplus
Keyword to support PoE++ and allow 802.3bt (Type-3) PoE devices to be connected to the port and request up to 60 W.
- hpoe
Keyword to support HPoE and allow 802.3bt (Type-4) PoE devices to be connected to the port and request up to 90 W.
qinq-etype
Syntax
qinq-etype value
no qinq-etype
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the Ethertype used for Q-in-Q encapsulation.
When the qinq-etype is configured to a value other than the default value on a port, the outermost tag in the received packet is matched against the configured value and the inner tag's etype is matched against the default value. If there is a match, it is treated as a QinQ packet and the outer VLAN ID and inner VLAN ID is used to match against the configured Q1.Q2 SAPs on the port to find the QinQ SAP the packet should be matched to. If only the outermost tag's etype matches the qinq-etype configured on the port and the VLAN ID matches any of the Q1.* SAP configured on the port, the packet is processed in the context of that SAP. If the outermost tag's etype does not match the configured qinq-etype, then the packet is considered to be a untagged packet.
This command is supported only for access ports and hybrid ports. On hybrid ports, it applies to all traffic (that is, traffic mapped to SAPs and network IP interfaces). It is not supported for network ports.
The maximum number of unique qinq-etypes configurable per node is limited. The resources needed for configuration of qinq-etype is shared by the default dot1q-etype, default qinq-etype and user configured values for qinq-etype. That is, the number of unique dot1q-etypes allowed decreases if the number of unique qinq-etype configured is more. The reverse is also true.
The qinq-etype change is not allowed on hybrid port, if there is an interface or a SAP configured on the port.
The no form of this command reverts the qinq-etype value to the default value. The default value is not user configurable.
Default
0x8100
Parameters
- value
Specifies the qinq-etype to expect, in hexadecimal or decimal notation.
statistics
Syntax
statistics
Context
config>port>ethernet
Platforms
7210 SAS-D, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure the counters associated with the egress port.
egress
Syntax
egress
Context
config>port>ethernet>statistics
Platforms
7210 SAS-D, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure egress per queue statistics counter, which counts the total number of packets forwarded.
port-clock
Syntax
port-clock {master | slave | automatic}
Context
config>port>ethernet
Platforms
7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command forces the copper port to be a master or slave or set it for automatic detection. Using a value of master ensures that the local node is the SyncE master. A SyncE master port distributes the system timing over the copper port to the remote peer node. Using a value of slave ensures that the local node is a SyncE slave. A SyncE slave port uses the incoming timing information.
With copper ports using 1G speed, the nodes need to determine who will be the master and slave with respect to clock used for transmission and reception. The master-slave relationship between the two ports of the nodes is determined during autonegotiation of the link parameters and is automated; there is no management intervention in this process. When this process is complete, the master port transmit clock will be used for receiving the packets on the slave port. However, when SyncE is in use, to maintain clock distribution hierarchy (for example, master will be synchronized to a stable reference and will distribute this clock to the slave) one needs to make sure that one of the ports behave as a master while the remote port of the link in question behaves as a slave.
For copper ports, when port-clock is set to automatic, the Ethernet interface will automatically negotiate clock mastership along with other link parameters with the far end. Depending upon the capabilities of the two ends, one will be master the other will be slave for clocking.
This command is ignored for all ports, other than copper ports that support SyncE.
The no form of this command allows the node to automatically determine the master or slave status for the copper port based on the nodes capabilities exchanged during auto-negotiation. That is, depending on the peer setting, the local end could end up as either a master or a slave when the no form of this command is used.
The following conditions must be met before using SyncE on the fixed port copper ports:
Autonegotiation (or autonegotiation limited) must be turned on. This command is required only when the copper port speed is set to 1Gbps. This CLI command is not supported for fiber ports or for fiber ports that use copper SFPs.
The port clock must be set to slave, if the port is used as a source-port for any reference. On the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C platform, when using combo ports, the connection-type must be set to copper. The port-clock parameter is ignored if the connection-type is set to sfp or auto.
Default
automatic
Parameters
- master
Specifies that the local node is the synchronous Ethernet master. A synchronous Ethernet master port distributes the system timing over the copper port to the remote peer node.
- slave
Specifies that the local node is a synchronous Ethernet slave. A synchronous Ethernet slave port uses the incoming timing information.
- automatic
Specifies that the Ethernet interface will automatically negotiate clock mastership along with other link parameters with the far end. Depending upon the capabilities of the two ends, one will be master the other will be slave for clocking.
speed
Syntax
speed {10 | 100 | 1000}
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the port speed of a fast Ethernet port when autonegotiation is disabled. If the port is configured to autonegotiate, the speed parameter is ignored. Speed cannot be configured for ports that are part of a LAG.
On the 7210 SAS-Dxp, the 10 Mb/s port speed is not supported for an SFP port using a copper SFP.
Default
speed 100
Parameters
- 10
Keyword to set the link to 10 Mb/s.
- 100
Keyword to set the link to 100 Mb/s.
- 1000
Keyword to set the link to 1000 Mb/s.
loopback
Syntax
[no] loopback {internal} [service svc-id sap sap-id src-mac SA dst-mac DA]
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This configures simple port loopback and port loopback with MAC swap. When the optional parameter internal is specified, it provides the port loopback without the mac-swap functionality. It enables physical layer loopback of the packets that egress on the SAPs created on an Ethernet port. The packets that egress are looped back into the node instead of being transmitted on to the line. After loopback, the packets ingress the system and are mapped to the same SAP from which they were egressed. The packets that are looped back are processed as per the service configuration of the SAP.
The 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C only support port loopback without MAC swap (that is, only the config>port>ethernet> loopback internal command applies). Port loopback with MAC swap is not supported on these platforms.
This command, when used with service-id and MAC address, provides the port loopback with mac-swap functionality. It enables a physical layer loopback, so that packets which egress on the SAPs created on an Ethernet port are looped back into the system. After loopback, on ingress to the system, the MAC addresses in the Ethernet header are swapped (that is the source MAC address and destination MAC address is exchanged with each other) by the system before being processed as per the service configuration of the SAP.
On 7210 SAS platforms, use of port loopback with mac-swap, requires resources of another port to be assigned for system use. Users need to assign the resources of either internal virtual port or the resource of the front panel port for use with this OAM tool using the command configure> system> loopback-no-svc-port {mirror | mac-swap| testhead} port-id. The number of internal virtual port resources available for use is different for different platforms and can be obtained using the command show> system> internal-loopback-ports detail. Based on the number of internal virtual port resources and the use of other OAM tool that require the resources of another port, the user may need to assign the resources of a front-panel port if the internal virtual port resources are not available.
Port loopback without mac-swap does not require another port to be assigned for system use on any of the 7210 SAS platforms.
The following information describes guidelines for port loopback without mac-swap.
Use this command for testing VLL services.
Enabling this command for testing VPLS services leads to rapid MAC address movement to another port, as source or destination MAC address swap is not performed.
This command affects all services provisioned on the port.
Before enabling this command, turn off all Layer 2 and IP control protocols (such as LACP, EFM, 802.1x and so on) on the device and its peer to prevent errors such as protocol flaps caused by timeout and so on.When port loopback feature is to be used for multicast traffic with IGMP snooping enabled in the service, the corresponding datapath has to be statically created using static IGMP groups.
For loopback to be functional, the following are not required:
SFP or XFPs need not be inserted into the device.
Ethernet cables need not be plugged in for copper ports.
When the loopback command is enabled, ensure that Ethernet parameters such as speed, duplex, autonegotiation and so on are not modified.
The following information describes guidelines for port loopback with mac-swap:
This command is available for testing VLL services and VPLS services only.
When enabled, the command affects all services provisioned on the port.
Before enabling this command, turn off all Layer 2 and IP control protocols (such as LACP, EFM, 802.1x and so on) on the device and its peer to prevent errors such as protocol flaps caused by timeout and so on.When port loopback feature is to be used for multicast traffic with IGMP snooping enabled in the service, the corresponding datapath has to be statically created using static IGMP groups.
When using port loopback with mac-swap enabled, for unicast and unknown-unicast packets, if the packet matches the configured source and destination MAC address it will be swapped and looped back in the service. For broadcast and multicast packets, if the packet matches the configured source MAC address, its source MAC address will be used as the destination MAC address and the system MAC address will be the source MAC address. The packet is looped back in the service as a unicast packet. All other packets sent to the loopback port will be dropped as the forwarding of these packets after loopback can potentially cause network wide problems.
For loopback to be functional, the following are not required:
SFP or XFPs need not be inserted into the device.
Ethernet cables need not be plugged in for copper ports.
When the loopback is enabled, ensure that Ethernet parameters such as, speed, duplex, autonegotiation and so on are not modified.
When the loopback is enabled, ensure that service parameter and attributes such as ingress qos policy, accounting records, ingress/egress ACLs, and so on are not modified.
With port loopback in use, the SAP ingress ACLs with IP-criteria is not recommended for use because only MAC addresses are swapped.
The recommended procedure for using port loopback with mac-swap is:
Configure the service and SAP on which loopback is to be enabled.
Configure the assigned loopback port to be used.
Send bidirectional learning frames on the SAP under test and spoke or uplink from a traffic tester or one can install static MAC for this purpose. Installing a static MAC is highly recommended because the recommended procedure for enabling port loopback is to shutdown the port –> enable loopback and then execute no shutdown the port.
Enable port loopback and specify the service, SAP, and the source MAC address (SA) and the destination MAC address (DA). All packets with source MAC matching SA are the only ones processed in the context of the SAP on ingress after the loopback. Any other traffic, is dropped on ingress, to avoid issues caused by MAC movement and flooding issues in other services/SAPs, since the whole port is in loopback.
When the port is in loopback, software disable learning and aging on the specified SAP. When the loopback configuration is removed for the port, then the software enables learning and aging for specified SAP. Therefore, port loopback with mac-swap cannot be used for learning or aging.
It is not recommend to change the service parameters for the SAP and the service when loopback is active. Additionally use of commands which clears the FDB, and so on is highly discouraged.
Remove the loopback on the SAP port to bring the sap out of MAC swap with loopback mode.
The no form of this command disables physical layer loopback on the Ethernet port.
The loopback command is not saved in the configuration file across a reboot.
The following list is the recommended sequence of commands to be executed to perform loopback:
Disable the port, execute the config>port>shutdown command.
Enable loopback, execute the config>port>ethernet>loopback internal command
Enable the port, execute the config>port>no shutdown command.
Perform the required tests.
Disable the port, execute the config>port>shutdown command.
Disable loopback, execute the config>port>ethernet>no loopback internal command
Enable the port, execute the command config>port> no shutdown.Enable the required services. The following list is the recommended sequence of commands to be executed to perform loopback when SFP or XFPs are inserted into the device:
Insert SFP or XFPs. SFP or XFPs are not required in case of fixed copper ports.
Enable the port and execute the config>port>no shutdown command.
Disable the port and execute the config>port>shutdown command. Enable loopback and execute the config>port>ethernet>loopback internal command.
Enable the port and execute the config>port>no shutdown command.Perform the required tests.
Disable the port and execute the config>port>shutdown command. Disable loopback and execute the config>port>ethernet>no loopback internal command.
Enable the port and execute the config>port>no shutdown command.Enable the required services.
The following list is the sequence of commands to be executed to perform loopback when SFP or XFPs are changed:
Disable the port, execute the config>port>shutdown command.
Insert the new SFP or XFP.
Enable the port and execute the config>port>no shutdown command. Disable the port and execute the config>port>shutdown command. Enable loopback and execute the config>port>ethernet>loopback internal command.
Enable the port and execute the config>port>no shutdown command.
Perform the required tests.
Disable the port and execute the config>port>shutdown command.
Disable loopback and execute the config>port>ethernet>no loopback internal command.
Enable the port and execute the config>port>no shutdown command.
Enable the required services.
Enable loopback and execute the config>port>ethernet>loopback internal command.
Perform the required tests.
Disable loopback and execute the config>port>ethernet>no loopback internal command.
Enable the required services.
Parameters
- internal
Sets the associated port or channel into a internal loopback mode. A internal loopback loops the frames from the local router back at the framer.
- service svc-id
Specifies the unique service identification number or string identifying the service in the service domain. This ID must be unique to this service and may not be used for any other service of any type. The service-id must be the same number used for every on which this service is defined.
- sap sap-id
Specifies the physical port identifier portion of the SAP.
- src-mac SA
Specifies the source MAC address.
- dst-mac DA
Specifies the destination MAC address.
ssm
Syntax
ssm
Context
config>port>ethernet
Platforms
7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command enables Ethernet Synchronous Status Message (SSM) capability on a synchronous Ethernet port. Synchronous Ethernet must be enabled on the MDA (using the sync-e command) before SSM can be enabled.
code-type
Syntax
code-type [sonet | sdh]
Context
config>port>ethernet>ssm
Platforms
7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command configures the encoding of synchronous status messages, that is, to select either SDH or SONET set of values. Configuring the code-type is only applicable to Synchronous Ethernet ports. For the code-type, SDH refers to ITU-T G.781 Option-1,while SONET refers to G.781 Option 2 (equivalent to Telcordia GR-253-CORE).
Default
sdh
Parameters
- sdh
Specifies the values used on a G.781 Option 1 compliant network.
- sonet
Specifies the values used on a G.781 Option 2 compliant network.
tx-dus
Syntax
[no] tx-dus
Context
config>port>ethernet>ssm
config>port>sonet-sdh (not supported on 7210 SAS-Dxp)
Platforms
7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command forces the QL value transmitted from the SSM channel of the SONET/SDH port or the Synchronous Ethernet port to be set to QL-DUS/QL-DNU. This capability is provided to block the use of the interface for timing purposes from the 7210 SAS.
Default
no tx-dus
802.1x port commands
dot1x
Syntax
dot1x
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure port-specific 802.1x authentication attributes. This context can only be used when configuring Fast Ethernet, Gigabit Ethernet, or 10-Gigabit Ethernet LAN ports on an appropriate MDA.
mac-auth
Syntax
[no] mac-auth
Context
config>port>ethernet>dot1x
Platforms
7210 SAS-Dxp
Description
This command enables MAC-based authentication. To use MAC-based authentication, 802.1x authentication must first be enabled using the port-control auto command.
When MAC-based authentication is enabled, and the mac-auth-wait timer expires, the 7210 SAS begins listening on the port for valid Ethernet frames. The source MAC address of a received frame is used for MAC-based authentication.
MAC authentication and Dot1x authentication or VLAN authentication are mutually exclusive and cannot be configured on the same port.
The no form of this command disables MAC-based authentication.
Default
no mac-auth
mac-auth-wait
Syntax
mac-auth-wait seconds
no mac-auth-wait
Context
config>port>ethernet>dot1x
Platforms
7210 SAS-Dxp
Description
This command configures the delay period before MAC authentication is activated.
The no form of this command disables the delay and allows MAC authentication to be used immediately.
Default
no mac-auth-wait
Parameters
- seconds
Specifies the MAC authentication delay period, in seconds.
max-auth-req
Syntax
max-auth-req max-auth-request
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the maximum number of times that the 7210 SAS will send an access request RADIUS message to the RADIUS server. If a reply is not received from the RADIUS server after the specified number attempts, the 802.1x authentication procedure is considered to have failed.
The no form of this command reverts to the default value.
Default
2
Parameters
- max-auth-request
Specifies the maximum number of RADIUS retries.
port-control
Syntax
port-control [auto | force-auth | force-unauth]
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the 802.1x authentication mode.
The no form of this command reverts to the default value.
Default
force-auth
Parameters
- force-auth
Specifies that 802.1x authentication will be disabled and causes the port to transition to the authorized state without requiring any authentication exchange. The port transmits and receives normal traffic without requiring 802.1x-based host authentication.
- force-unauth
Specifies that the port will remain in the unauthorized state, ignoring all attempts by the hosts to authenticate. The switch cannot provide authentication services to the host through the interface.
- auto
Specifies that 802.1x authentication will be enabled. The port starts in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. Both the 7210 SAS and the host can initiate an authentication procedure. The port will remain in an unauthorized state (no traffic except EAPOL frames is allowed) until the first client is authenticated successfully. After this, traffic is allowed on the port for all connected hosts.
quiet-period
Syntax
quiet-period seconds
no quiet-period
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the period between two authentication sessions during which no EAPOL frames are sent by the 7210 SAS.
The no form of this command reverts to the default value.
Default
30
Parameters
- seconds
Specifies the quiet period in seconds.
radius-plcy
Syntax
radius-plcy name
no radius-plcy
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the RADIUS policy to be used for 802.1x authentication. An 802.1x RADIUS policy must be configured (under config>security>dot1x) before it can be associated with a port. If the RADIUS policy-id does not exist, an error is returned. Only one 802.1x RADIUS policy can be associated with a port at a time.
The no form of this command removes the RADIUS policy association.
Default
no radius-plcy
Parameters
- name
Specifies an existing 802.1x RADIUS policy name.
re-auth-period
Syntax
re-auth-period seconds
no re-auth-period
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the period after which re-authentication is performed. This value is only relevant if re-authentication is enabled.
The no form of this command reverts to the default value.
Default
3600
Parameters
- seconds
Specifies the re-authentication delay period in seconds.
re-authentication
Syntax
[no] re-authentication
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables or disables periodic 802.1x re-authentication.
When re-authentication is enabled, the 7210 SAS will re-authenticate clients on the port every re-auth-period seconds.
The no form of this command reverts to the default value.
Default
re-authentication
server-timeout
Syntax
server-timeout seconds
no server-timeout
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the period during which the 7210 SAS waits for the RADIUS server to responds to its access request message. When this timer expires, the 7210 SAS will re-send the access request message, up to the specified number times.
The no form of this command reverts to the default value.
Default
30
Parameters
- seconds
Specifies the server timeout period in seconds.
supplicant-timeout
Syntax
supplicant-timeout seconds
no supplicant-timeout
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the period during which the 7210 SAS waits for a client to respond to its EAPOL messages. When the supplicant-timeout expires, the 802.1x authentication session is considered to have failed.
The no form of this command reverts to the default value.
Default
30
Parameters
- seconds
Specifies the server timeout period in seconds.
transmit-period
Syntax
transmit-period seconds
no transmit-period
Context
config>port>ethernet>dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the period after which the 7210 SAS sends a new EAPOL request message.
The no form of this command reverts to the default value.
Default
30
Parameters
- seconds
Specifies the server transmit period in seconds.
tunneling
Syntax
[no] tunneling
Context
config>port>ethernet>dot1x
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command enables tunneling of dot1x frames. With dot1x tunneling enabled, dot1x frames received on the port are transparently forwarded to the remote end of the service. To forwards dot1x frames transparently the port on which tunneling is enabled must be configured with NULL SAP and the NULL SAP must be configured in an Epipe service. Tunneling is not supported for any other port encapsulation or when using any other service.
Additionally, dot1x protocol must be disabled on the port (using the command configure> port> ethernet> dot1x> port-control force-auth) before dot1x tunneling can be enabled using this command. If dot1x is configured to use either force-unauath or auto, then dot1x tunneling cannot be enabled. If dot1x tunneling is enabled, then the user cannot configure either force-unauth or auto.
The no form of this command disables dot1x tunneling.
Default
no tunneling
vlan-auth
Syntax
[no] vlan-auth
Context
config>port>ethernet>dot1x
Platforms
7210 SAS-Dxp
Description
This command enables VLAN-based authentication. To use VLAN-based authentication, 802.1x authentication must first be enabled using the port-control auto command.
When VLAN-based authentication is enabled, all traffic for all VLANs on the port is blocked. VLAN-tagged EAPOL messages are forwarded to the RADIUS server for authentication. If authentication is successful, the VLAN corresponding to the successfully authenticated VLAN-tagged EAPOL message is unblocked and traffic is processed for the configured service. If authentication fails, the VLAN continues to be blocked.
VLAN authentication and MAC authentication are mutually exclusive and cannot be configured on the same port.
The no form of this command disables VLAN-based authentication.
Default
no vlan-auth
down-when-looped
Syntax
down-when-looped
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures Ethernet loop detection attributes.
keep-alive
Syntax
keep-alive timer
no keep-alive
Context
config>port>ethernet>dwl
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the time interval between keep-alive PDUs.
Default
no keep-alive
Parameters
- timer
Specifies the time interval, in seconds, between keep-alive PDUs.
retry-timeout
Syntax
retry-timeout timer
no retry-timeout
Context
config>port>ethernet>dwl
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the minimum wait time before re-enabling the port after loop detection.
Default
no retry-timeout
Parameters
- timer
Specifies the minimum wait time before re-enabling port after loop detection.
802.1x port MACsec commands
macsec
Syntax
[no] macsec
Context
config>port>ethernet>dot1x
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures MACsec functionality for the port.
When MACsec is configured on an Ethernet port, the oper MTU of the port is reduced by 32 bytes; for example, a configured MTU of 9212 results in an oper MTU of 9180 for a MACsec-enabled port. When a service or IP interface uses a MACsec-enabled port, an appropriate MTU value must be manually configured.
The no form of this command disables MACsec functionality for the port.
ca-name
Syntax
ca-name ca-name
no ca-name
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the CA linked to the MACsec port. The CA provides the MACsec parameter that is used or is negotiated with other peers.
The no form of this command removes the CA from the MACsec port.
Parameters
- ca-name
Specifies the CA to use for the MACsec port, up to 32 characters.
eapol-destination-address
Syntax
eapol-destination-address mac
no eapol-destination-address
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the destination MAC address of the EAPoL to the unicast address of the MACsec peer, so that the EAPoL and MKA signaling is unicast between two peers.
The EAPoL destination MAC address uses a destination multicast MAC address of 01:80:C2:00:00:03. Some networks cannot tunnel these packets over the network or consume them, causing the MKA session to fail.
The no form of this command reverts to the default value.
Default
no eapol-destination-address
Parameters
- mac
Specifies the destination MAC address used by the EAPoL MKA packets of the specified port. The 48-bit MAC address is in the form aa:bb:cc:dd:ee:ff or aa-bb-cc-dd-ee-ff, where aa, bb, cc, dd, ee, and ff are hexadecimal numbers.
exclude-protocol
Syntax
[no] exclude-protocol {protocol-name}
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the protocols for which packets are not secured with MACsec when MACsec is enabled on a port. When this command is enabled in a CA that is attached to an interface, MACsec is not enabled for all packets of the specified protocols that are sent and received on the link.
When this command is enabled on a port where MACsec is configured, packets of the specified protocols are sent and received in clear text.
Default
no exclude-protocol
Parameters
- protocol-name
Specifies the protocol name.
max-peer
Syntax
max-peer max-peer
no max-peer
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the maximum number of peers allowed for the specified MACsec instance.
The peer establishment is a race condition and operates on a first-come-first-served basis. For a security zone, only 32 peers are supported.
The no form of this command reverts to the default value.
Default
no max-peer
Parameters
- max-peer
Specifies the maximum number of peers supported on this port.
rx-must-be-encrypted
Syntax
[no] rx-must-be-encrypted
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies that all non-MACsec-secured traffic that is received on the port is dropped.
When this command is disabled, all arriving traffic is accepted, regardless of whether traffic is MACsec-secured.
This command is available only at the NULL port level and does not have per-VLAN granularity.
The no form of this command disables the command.
Default
rx-must-be-encrypted
shutdown
Syntax
[no] shutdown
Context
config>port>ethernet>dot1x>macsec
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command shuts down MACsec functionality, including MKA negotiation, for the port. In the shutdown state, the port is not MACsec capable and all PDUs are transmitted and expected without encryption and authentication.
A valid CA that is different from another CA configured on a sub-port of this port, and also a max-peer value larger than 0, must be configured. In MACsec-enabled mode, packets are sent in clear text until the MKA session is up, and if the rx-must-be-encrypted command is configured on the port, all incoming packets without MACsec are dropped.
The no form of this command sets the port to MACsec-enabled mode.
Default
shutdown
LLDP port commands
lldp
Syntax
lldp
Context
config>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure Link Layer Discovery Protocol (LLDP) parameters on the specified port.
tunnel-nearest-bridge-dest-mac
Syntax
[no] tunnel-nearest-bridge-dest-mac
Context
config>port>ethernet>lldp
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command configures tunneling for LLDP frames that use the nearest-bridge-dest-mac as destination MAC address. If enabled using the tunnel-nearest-bridge-dest-mac command, all frames received with the appropriate destination MAC address are forwarded transparently to the remote end of the service. To forward these frames transparently the port on which tunneling is enabled must be configured with NULL SAP and the NULL SAP must be configured in an Epipe service. Tunneling is not supported for any other port encapsulation or when using any other service.
Additionally, before enabling tunneling, admin status for LLDP dest-mac nearest-bridge must be set to disabled or Tx only, using the command admin-status available under configure> port> ethernet> lldp> dest-mac nearest-bridge. If admin-status for dest-mac nearest-bridge is set to receive and process nearest-bridge LLDPDUs (that is, if either rx or tx-rx is set) then it overrides the tunnel-nearest-bridge-dest-mac command.
The following table describes the behavior for LLDP with different values set in use for admin-status and when tunneling is enabled or disabled.
Nearest-bridge MAC Admin status |
Tunneling enabled |
Tunneling disabled |
|---|---|---|
Rx |
Process/Peer |
Process/Peer |
Tx |
Tunnel |
Drop |
Rx-Tx |
Process/Peer |
Process/Peer |
Disabled |
Tunnel |
Drop |
Transparent forwarding of LLDP frames can be achieved using the standard defined mechanism when using the either nearest-non-tmpr or the nearest-customer as the destination MAC address in the LLDP frames. It is recommended that the customers use these MAC address where possible to conform to standards. This command allows legacy LLDP implementations that do not support these additional destinations MAC addresses to tunnel LLDP frames that use the nearest-bridge destination MAC address.
The no form of this command disable LLDP tunneling for frames using nearest-bridge destination MAC address.
Default
no tunnel-nearest-bridge-dest-mac
dest-mac
Syntax
dest-mac {nearest-bridge | nearest-non-tpmr | nearest-customer}
Context
config>port>ethernet>lldp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures destination MAC address parameters to use by LLDP.
Parameters
- nearest-bridge
Specifies to use the nearest bridge
- nearest-non-tmpr
Specifies to use the nearest non-Two-Port MAC Relay (TPMR).
- nearest-customer
Specifies to use the nearest customer.
admin-status
Syntax
admin-status {rx | tx | tx-rx | disabled}
Context
config>port>ethernet>lldp>dstmac
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the desired administrative status of the local LLDP agent.
Parameters
- rx
Specifies that the LLDP agent receives LLDP frames on this port, also indicates that the LLDP agent does not transmit LLDP frames.
- tx
Specifies that the LLDP agent transmits LLDP frames on this port and does not store any information about the remote systems connected.
- tx-rx
Specifies that the LLDP agent transmits and receives LLDP frames on this port.
- disabled
Specifies that the LLDP agent does not transmit or receive LLDP frames on this port. If there is remote systems information which is received on this port and stored in other tables, before the port's admin status becomes disabled, then the information will naturally age out.
lldp-med
Syntax
lldp-med
Context
config>port>ethernet>lldp>dest-mac
Platforms
7210 SAS-Dxp
Description
Commands in this context configure the administrative status of the local LLDP-MED agent.
admin-status
Syntax
admin-status {tx-rx | disabled}
no admin-status
Context
config>port>ethernet>lldp>dest-mac>lldp-med
Platforms
7210 SAS-Dxp
Description
This command configures the administrative status of the local LLDP-MED agent.
The no form of this command disables the ability to specify the administrative status of the local LLDP-MED agent.
Default
admin-status disabled
Parameters
- tx-rx
Keyword to configure the LLDP agent to transmit and receive LLDP-MED TLVs on the configured port.
- disabled
Keyword to indicate that the LLDP-MED agent does not transmit or receive LLDP frames with LLDP-MED TLVs on the configured port. If no remote systems information is received on the configured port and stored in other tables before the port administrative status becomes disabled, the information ages out.
network-policy
Syntax
network-policy policy-id [policy-id...(up to 4 max)]
no network-policy
Context
config>port>ethernet>lldp>dest-mac>lldp-med
Platforms
7210 SAS-Dxp
Description
This command configures the network policy information that the node transmits in the Network Policy TLV.
Up to four policies can be configured, as long as the configured application-type for each policy is different. The system includes multiple Network Policy TLVs (if multiple policies are configured), with the policy for each application-type included in its own Network Policy TLV. The Network Policy TLV order in the LLDP message matches the policy order configured in the CLI. If the system cannot fit all configured Network Policy TLVs into the LLDP frame because of size constraints, a log message is generated for the last network policy that exceeds the frame size. The error notification allows the user to adjust the configuration appropriately.
The user must explicitly configure a network policy (with values assigned to the endpoint device) before the transmission and reception of LLDP-MED TLVs on the port is allowed. If a port is configured to transmit the LLDP-MED Network Policy TLV but the user has not configured a network policy, the node will not transmit the Network Policy TLV. The node processes the received Network Policy TLV and displays the TLV values in the LLDP message received from the peer provided that the LLDP-MED receiving processing and Network Policy TLV processing is enabled, regardless of whether network-policy is configured.
The no form of this command removes the association of all network policies with the port.
Default
no network-policy
Parameters
- policy-id
Specifies network policy ID.
tx-tlvs
Syntax
tx-tlvs [network-policy] [mac-phy-config-status]
no tx-tlvs
Context
config>port>ethernet>lldp>dest-mac>lldp-med
Platforms
7210 SAS-Dxp
Description
This command configures the specific transmit TLV from the network connectivity TLV set to be transmitted on the port if LLDP-MED TLV transmission is enabled on the port.
The no form of this command removes the configuration.
Default
no tx-tlvs
Parameters
- network-policy
Keyword to enable the transmission of the network policy TLV.
- mac-phy-config-status
Keyword to enable the transmission of the MAC-PHY Configuration and Status TLV.
notification
Syntax
[no] notification
Context
config>port>ethernet>lldp>dstmac
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables LLDP notifications.
The no form of this command disables LLDP notifications.
port-id-subtype
Syntax
port-id-subtype {tx-if-alias | tx-if-name | tx-local}
no port-id-subtype
Context
config>port>ethernet>lldp>dest-mac
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies how to encode the PortID TLV transmit to the peer. Some versions of the NSP NFM-P require the default tx-local (if Index value) setting to properly build the Layer Two topology map using LLDP. Changing this setting to transmit the ifName (tx-if-name) or ifAlias (tx-if-alias), instead of the ifIndex (tx-local), may affect the ability of the NSP NFM-P to build the Layer 2 topology map using LLDP.
The no form of this command reverts to the default value.
Default
portid-subtype tx-local
Parameters
- tx-if-alias
Keyword to transmit the ifAlias String (subtype 1) that describes the port as stored in the IF-MIB, either user configured or the default entry (for example, 10/100/Gig Ethernet SFP).
- tx-if-name
Keyword to transmit the ifName string (subtype 5) that describes the port as stored in the IF-MIB ifName information.
- tx-local
Keyword to specify the interface ifIndex value (subtype 7) as the PortID.
tx-mgmt-address
Syntax
tx-mgmt-address [system] [system-ipv6]
no tx-mgmt-address
Context
config>port>ethernet>lldp>dstmac
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
This command specifies which management address to transmit. The operator can choose to send the system IPv4 IP Address, system IPv6 address, or both.
The system address is sent only once. When both options are configured, both system addresses are sent. The system address must be configured for the specific version of the protocol to send the management address.
Default
no tx-mgmt-address
Parameters
- system
Keyword to transmit the system IPv4 address.
- system-ipv6
Keyword to transmit the system IPv6 address. This parameter can only be used on platforms that support IPv6.
tx-tlvs
Syntax
tx-tlvs [port-desc] [sys-name] [sys-desc] [sys-cap]
no tx-tlvs
Context
config>port>ethernet>lldp>dstmac
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies which LLDP TLVs to transmit.
The no form of this command reverts to the default value.
Default
no tx-tlvs
Parameters
- port-desc
Specifies that the LLDP agent should transmit port description TLVs.
- sys-name
Specifies that the LLDP agent should transmit system name TLVs.
- sys-desc
Specifies that the LLDP agent should transmit system description TLVs.
- sys-cap
Specifie that the LLDP agent should transmit system capabilities TLVs.
Access-uplink port commands
network
Syntax
network
Context
config>port>ethernet
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure network port parameters.
uplink
Syntax
uplink
Context
config>port>access
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure access uplink egress port parameters.
accounting-policy
Syntax
accounting-policy policy-id
no accounting-policy
Context
config>port>ethernet>network
config>port>ethernet>access>uplink
config>port>ethernet>access
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C; the network context applies only to the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures an accounting policy that can apply to an interface.
An accounting policy must be configured before it can be associated with an interface. If the accounting policy-id does not exist, an error is returned.
Accounting policies associated with service billing can only be applied to SAPs. Accounting policies associated with network ports can only be associated with interfaces. Only one accounting policy can be associated with an interface at a time.
The no form of this command removes the accounting policy association from the network interface, and the accounting policy reverts to the default. No accounting policies are specified by default. You must explicitly specify a policy. If configured, the accounting policy configured as the default is used.
Parameters
- policy-id
Specifies the accounting policy-id of an existing policy. Accounting policies record either service (access) or network information. A network accounting policy can only be associated with the network port configurations. Accounting policies are configured in the config>log>accounting-policy context.
collect-stats
Syntax
[no] collect-stats
Context
config>port>ethernet>access>uplink
config>port>ethernet>access
config>port>ethernet>network
Platforms
7210 SAS-D, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C; the network context applies only to the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command enables the collection of accounting and statistical data for the network interface. When applying accounting policies, the data, by default, is collected in the appropriate records and written to the designated billing file.
The no form of this command ensures that the statistics are still accumulated by the IOM cards, however, the CPU does not obtain the results and write them to the billing file.
If the collect-stats command is issued again (enabled), then the counters written to the billing file will include the traffic collected while the no collect-stats command was in effect.
Default
no collect-stats
queue-policy
Syntax
queue-policy name
no queue-policy
Context
config>port>ethernet>network
config>port>ethernet>access>uplink
Platforms
7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C; the network context applies only to the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the existing network queue policy which defines queue parameters such as CIR and PIR rates, as well as forwarding-class to queue mappings. The network-queue policy is defined in the config>qos>network-queue context.
A default CBS is defined for the queues and this is not configurable.
Default
default
Parameters
- name
Specifies an existing network-queue policy name.
LAG commands
lag
Syntax
[no] lag [lag-id]
Context
config
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the context for configuring Link Aggregation Group (LAG) attributes.
A LAG can be used to group multiple ports into one logical link. The aggregation of multiple physical links allows for load sharing and provides seamless redundancy. If one of the links fails, traffic will be redistributed over the remaining links.
There are three possible settings for autonegotiation:
‟on” or enabled with full port capabilities advertised
‟off” or disabled where there is no autonegotiation advertisements
‟limited” where a single speed/duplex is advertised.
When autonegotiation is enabled on a port, the link attempts to automatically negotiate the link speed and duplex parameters. If autonegotiation is enabled, the configured duplex and speed parameters are ignored.
When autonegotiation is disabled on a port, the port does not attempt to autonegotiate and will only operate at the speed and duplex settings configured for the port. Note that disabling autonegotiation on gigabit ports is not allowed as the IEEE 802.3 specification for gigabit Ethernet requires autonegotiation be enabled for far end fault indication.
If the autonegotiate limited keyword option is specified the port will autonegotiate but will only advertise a specific speed and duplex. The speed and duplex advertised are the speed and duplex settings configured for the port. One use for limited mode is for multispeed gigabit ports to force gigabit operation while keeping autonegotiation is enabled for compliance with IEEE 801.3.
The system requires that autonegotiation be disabled or limited for ports in a LAG to guarantee a specific port speed.
The no form of this command deletes the LAG from the configuration. Deleting a LAG can only be performed while the LAG is administratively shut down. Any dependencies such as IP-Interfaces configurations must be removed from the configuration before issuing the no lag command.
Parameters
- lag-id
The LAG identifier, expressed as a decimal integer.
dynamic-cost
Syntax
[no] dynamic-cost
Context
config>lag
Platforms
Supported on 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command enables OSPF costing of a Link Aggregation Group (LAG) based on the available aggregated operational bandwidth.
The path cost is dynamically calculated based on the interface bandwidth. OSPF path cost can be changed through the interface metric or the reference bandwidth.
If dynamic cost is configured, then costing is applied based on the total number of links configured and the cost advertised is inversely proportional to the number of links available at the time. This is provided that the number of links that are up exceeds the configured LAG threshold value at which time the configured threshold action determines if, and at what cost, this LAG will be advertised.
For example:
Assume a physical link in OSPF has a cost associated with it of 100, and the LAG consists of four physical links. The cost associated with the logical link is 25. If one link fails then the cost would automatically be adjusted to 33.
If dynamic cost is not configured and OSPF autocost is configured, then costing is applied based on the total number of links configured. This cost will remain static provided the number of links that are up exceeds the configured LAG threshold value at which time the configured threshold action determines if and at what cost this LAG will be advertised.
If dynamic cost is configured and OSPF autocost is not configured, the cost is determined by the cost configured on the OSPF metric provided the number of links available exceeds the configured LAG threshold value at which time the configured threshold action determines if this LAG will be advertised.
If neither dynamic-cost nor OSPF autocost are configured, the cost advertised is determined by the cost configured on the OSPF metric provided the number of links available exceeds the configured LAG threshold value at which time the configured threshold action determines if this LAG will be advertised.
The no form of this command removes dynamic costing from the LAG.
Default
no dynamic-cost
encap-type
Syntax
encap-type {dot1q | null | qinq}
no encap-type
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the encapsulation method used to distinguish customer traffic on a LAG. The encapsulation type is configurable on a LAG port. The LAG port and the port member encapsulation types must match when adding a port member.
If the encapsulation type of the LAG port is changed, the encapsulation type on all the port members will also change. The encapsulation type can be changed on the LAG port only if there is no interface associated with it. If the MTU is set to a non default value, it will be reset to the default value when the encap type is changed. All traffic on the port belongs to a single service or VLAN.
On the 7210 SAS-D ETR, 7210 SAS-Dxp, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, the qinq encapsulation type can be configured for both access and access-uplink port LAGs. The null and dot1q encapsulation types can be specified only for access port LAGs.
On the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C, the null and dot1q encapsulation types can be specified for network port LAGs. The dot1q and qinq encapsulation types can be specified for hybrid port LAGs.
The no form of this command reverts the default.
Default
null
Parameters
- dot1q
Specifies that the ingress frames will carry 802.1Q tags where each tag signifies a different service.
- null
Specifies that the ingress frames will not use any tags to delineate a service. As a result, only one service can be configured on a port with a null encapsulation type.
- qinq
Specifies QinQ encapsulation.
hold-time
Syntax
hold-time down hold-down-time
no hold-time
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the timer, in tenths of seconds, which controls the delay between detecting that a LAG is down (all active ports are down) and reporting it to the higher levels.
A non-zero value can be configured, for example, when active/standby signaling is used in a 1:1 fashion to avoid informing higher levels during the small time interval between detecting that the LAG is down and the time needed to activate the standby link.
Default
0
Parameters
- down hold-down-time
Specifies the hold-time for event reporting.
lacp
Syntax
lacp [mode] [administrative-key admin-key] [system-id system-id] [system-priority priority]
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the Link Aggregation Control Protocol (LACP) mode for aggregated Ethernet interfaces only. Per the IEEE 802.3ax standard (formerly 802.3ad), the LACP provides a standardized means for exchanging information between Partner Systems on a link. This allow their Link Aggregation Control instances to reach agreement on the identity of the Link Aggregation Group to which the link belongs, move the link to that Link Aggregation Group, and enable its transmission and reception functions in an orderly manner. LACP can be enabled on a maximum of 256 ports.
Default
no lacp
Parameters
- mode
Specifies the mode in which LACP will operate.
- admin-key
Specifies an administrative key value to identify the channel group on each port configured to use LACP. This value should be configured only in exceptional cases. If it is not specified, a random key is assigned.
- system-id
Specifies a 6 byte value expressed in the same notation as MAC address
- priority
Specifies the system priority to be used for the LAG in the context of the MC-LAG.
lacp-xmit-interval
Syntax
[no] lacp-xmit-interval {slow | fast}
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the interval signaled to the peer and tells the peer at which rate it should transmit.
Default
fast
Parameters
- slow
Specifies that packets will transmit every 30 seconds.
- fast
Specifies that packets will transmit every second.
lacp-xmit-stdby
Syntax
[no] lacp-xmit-stdby
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables LACP message transmission on standby links.
The no form of this command disables LACP message transmission. This command should be disabled for compatibility when using active/standby groups. This forces a timeout of the standby links by the peer. Use the no form if the peer does not implement the correct behavior regarding the lacp sync bit.
Default
lacp-xmit-stdby
port
Syntax
port port-id [port-id …up to n total] [priority priority] [subgroup sub-group-id]
no port port-id [port-id …up to n total]
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds ports (links) to a Link Aggregation Group (LAG).
The port configuration of the first port added to the LAG is used as a basis to compare to subsequently added ports. If a discrepancy is found with a newly added port, that port is not added to the LAG.
The maximum number of ports allowed in a LAG depends on the platform. The following are the limits per platform:
On the 7210 SAS-D and 7210 SAS-Dxp, a maximum of four 1 GE ports can be added to or removed from the LAG. The 7210 SAS-Dxp also supports up to two 10 GE ports in a LAG.
On the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, a maximum of three 1 GE ports can be added to or removed from the LAG.
On the 7210 SAS-K 3SFP+ 8C, a maximum of two 10 GE ports can be added to or removed from a LAG.
All ports added to a LAG must share the same characteristics (speed, duplex, and so on). An error message is displayed when adding ports that do not share the same characteristics. Hold timers must be 0. Ports that are part of a LAG must be configured with autonegotiation set to limited mode or disabled. No ports are defined as members of a LAG.
The no form of this command removes ports from the LAG.
Parameters
- port-id
Specifies the port ID configured or displayed in the slot/mda/port format.
- priority priority
Specifies the port priority used by LACP. The port priority is also used to determine the primary port. The port with the lowest priority is the primary port. In the event of a tie, the smallest port ID becomes the primary port.
- subgroup sub-group-id
Specifies a LAG subgroup. Subgroups in a LAG must be configured on only one side of the LAG, not both. Having only one side perform the active/standby selection guarantees a consistent selection and fast convergence. The active/standby selection is signaled through LACP to the other side. The hold time should be configured when using subgroups to prevent the LAG going down when switching between active and standby links, in the case where no links are usable for a short time, especially in case a subgroup consists of one member.
port-threshold
Syntax
port-threshold value[action {down}]
no port-threshold
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the behavior for the Link Aggregation Group (LAG) if the number of operational links is equal to or below a threshold level.
The no form of this command reverts to the default values.
Default
‟0” action down
Parameters
- value
Specifies the decimal integer threshold number of operational links for the LAG at or below which the configured action will be invoked. If the number of operational links exceeds the port-threshold value, any action taken for being below the threshold value will cease.
- action [{down}]
Specifies the action to take if the number of active links in the LAG is at or below the threshold value.
If the number of operational links is equal to or less than the configured threshold value and action down is specified, the LAG is brought to an operationally down state. The LAG is considered as operationally up only when the number of operational links exceeds the configured threshold value.
selection-criteria
Syntax
selection-criteria [{highest-count | highest-weight | best-port}] [slave-to-partner]
no selection-criteria
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies which selection criteria should be used to select the active sub-group.
Default
highest-count
Parameters
- highest-count
Specifies sub-group with the highest number of eligible members.
- highest-weight
Specifies sub-group with the highest aggregate weight.
- best-port
Specifies the selection criteria used with ‟power-off” mode of operation. The sub-group containing the port with highest priority port. In case of equal port priorities the sub-group containing the port with the lowest port-id is taken
- slave-to-partner
Specifies that, together with the selection criteria, the slave-to-partner keyword should be used to select the active sub-group. An eligible member is a lag-member link which can potentially become active. This means it is operationally up (not disabled) for use by the remote side. The slave-to-partner parameter can be used to control whether or not this latter condition is taken into account.
standby-signalling
Syntax
standby-signalling {lacp | power-off}
no standby-signalling
Context
config>lag
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies how the state of a member port is signaled to the remote side when the status corresponding to this member port has the standby value.
Default
lacp
Parameters
- lacp
Specifies that LACP protocol is used to signal standby links of the LAG.
- power-off
The laser of the standby links in the LAG are shutoff to indicate standby status. It allows user to use LAG standby link feature without LACP, if the peer node does not support LACP.
Multi-chassis redundancy commands
redundancy
Syntax
redundancy
Context
config
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure redundancy operations.
multi-chassis
Syntax
multi-chassis
Context
config>redundancy
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure multi-chassis parameters.
peer
Syntax
[no] peer ip-address create
Context
config>redundancy>multi-chassis
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the MC-LAG peer.
Parameters
- ip-address
Specifies the IP address.
- create
Specifies the mandatory keyword to create the peer.
authentication-key
Syntax
authentication-key [authentication-key| hash-key] [hash | hash2]
no authentication-key
Context
config>redundancy>multi-chassis>peer
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures the authentication key used between this node and the multi-chassis peer. The authentication key can be any combination of letters or numbers.
Parameters
- authentication-key
Specifies the authentication key. Allowed values are any string up to 20 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
- hash-key
Specifies the hash key. The key can be any combination of ASCII characters up to 33 (hash1-key) or 55 (hash2-key) characters (encrypted). If spaces are used in the string, enclose the entire string in quotation marks.
- hash
Specifies that the key is entered in an encrypted form. If the hash or hash2 parameter is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 parameter specified.
- hash2
Specifies that the key is entered in a more complex encrypted form that involves more variables then the key value alone, this means that the hash2 encrypted variable cannot be copied and pasted. If the hash or hash2 parameter is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 parameter specified.
description
Syntax
description long-description-string
no description
Context
config>redundancy>multi-chassis>peer
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command adds a text description for the ring path.
The no form of this command removes the text description.
Default
‟”
Parameters
- string
Specifies the text description up to 160 characters.
MC Endpoint commands
hold-on-neighbor-failure
Syntax
hold-on-neighbor-failure multiplier
no hold-on-neighbor-failure
Context
config>redundancy>multi-chassis>peer>mc-ep
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the number of keep-alive intervals that the local node waits for packets from the MC-EP peer before assuming failure. After this time interval, all the mc-endpoints configured in the service revert to single chassis behavior, activating the best local pseudowire.
The no form of this command reverts the multiplier to the default value.
Default
3
Parameters
- multiplier
Specifies the hold time applied on neighbor failure.
MC-LAG commands
mc-lag
Syntax
[no] mc-lag
Context
config>redundancy>multi-chassis>peer>mc-lag
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure multi-chassis LAG operations and related parameters.
The no form of this command administratively disables multi-chassis LAG. MC-LAG can be issued only when MC-LAG is shutdown.
hold-on-neighbor-failure
Syntax
hold-on-neighbor-failure multiplier
no hold-on-neighbor-failure
Context
config>redundancy>multi-chassis>peer>mc-lag
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the standby node wait interval to receive packets from the active node before assuming a redundant-neighbor node failure. This delay in switchover operation is required to accommodate different factors influencing node failure detection rate, such as IGP convergence or HA switch-over times, and to prevent the standby node from taking action prematurely.
The no form of this command reverts the multiplier to the default value.
Default
3
Parameters
- multiplier
Specifies the time interval that the standby node waits for packets from the active node before assuming a redundant-neighbor node failure.
keep-alive-interval
Syntax
keep-alive-interval interval
no keep-alive-interval
Context
config>redundancy>multi-chassis>peer>mc-lag
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command sets the interval at which keep-alive messages are exchanged between two systems participating in MC-LAG. These keep-alive messages are used to determine remote-node failure and the interval is set in deciseconds.
The no form of this command reverts the interval to the default value.
Default
10
Parameters
- interval
Specifies the time interval expressed in deciseconds.
lag
Syntax
lag lag-id lacp-key admin-key system-id system-id [remote-lag remote-lag-id] system-priority system-priority
lag [remote-lag remote-lag-id]
no lag lag-id
Context
config>redundancy>multi-chassis>peer>mc-lag
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command defines a LAG that forms a redundant-pair for MC-LAG with a LAG configured on the specific peer. The same LAG group can be defined only in the scope of 1 peer. In order for MC-LAG to become operational, all configured parameters (lacp-key, system-id, system-priority) must be the same on both nodes of the same redundant pair.
In the partner system (the system connected to all links forming MC-LAG), all ports using the same lacp-key, system-id, system-priority are considered part of the same LAG. To achieve this in MC operation, both redundant-pair nodes must be configured with the same values. In case of a mismatch, MC-LAG is kept in the oper-down state.
The no form of this command disables MC-LAG for the specific LAG (regardless of the mode).
The correct CLI command to enable MC-LAG for a LAG in standby-signaling power-off mode is lag lag-id [remote-lag remote-lag-id]. In the CLI help output, the first three forms are used to enable MC-LAG for a LAG in LACP mode.
Parameters
- lag-id
Specifies the LAG identifier, expressed as a decimal integer. Specifying the lag-id allows mismatch between lag-id on a redundant-pair. If no lag-id is specified, it is assumed that the neighbor system uses the same lag-id as a part of the specific MC-LAG. If no matching MC-LAG group can be found between neighbor systems, the individual LAGs will operate as usual (no MC-LAG operation is established).
- lacp-key admin-key
Specifies a 16-bit key that needs to be configured in the same manner on both sides of the MC-LAG for the MC-LAG to come up.
- system-id system-id
Specifies a 6-byte value expressed in the same notation as MAC address.
- remote-lag lag-id
Specifies the LAG ID on the remote system.
- system-priority system-priority
Specifies the system priority to be used in the context of the MC-LAG. The partner system will consider all ports using the same lacp-key, system-id, and system-priority as part of the same LAG.
source-address
Syntax
source-address ip-address
no source-address
Context
config>redundancy>multi-chassis>peer
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the source address used to communicate with the multi-chassis peer.
Parameters
- ip-address
Specifies the source address used to communicate with the multi-chassis peer.
peer-name
Syntax
peer-name name
no peer-name
Context
config>redundancy>multi-chassis>peer
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the peer name used to communicate with the multi-chassis peer.
Parameters
- name
Specifies the name used to communicate with the multi-chassis peer.
sync
Syntax
[no] sync
Context
config>redundancy>multi-chassis>peer
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context configure synchronization parameters.
igmp-snooping
Syntax
[no] igmp-snooping
Context
config>redundancy>multi-chassis>peer>sync
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies whether IGMP snooping information should be synchronized with the multi-chassis peer.
Default
no igmp-snooping
port
Syntax
port [port-id | lag-id] [sync-tag sync-tag]
no port [port-id | lag-id]
Context
config>redundancy>multi-chassis>peer>sync
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command specifies the port when synchronized with the multi-chassis peer and the synchronization tag to be use when synchronizing the port with the multi-chassis peer.
Parameters
- port-id
Specifies the port to synchronize with the multi-chassis peer.
- lag-id
Specifies the LAG ID to synchronize with the multi-chassis peer.
- sync-tag sync-tag
Specifies the synchronization tag to use while synchronizing this port with the multi-chassis peer.
range
Syntax
range encap-range sync-tag sync-tag
no range encap-range
Context
config>redundancy>multi-chassis>peer>sync>port
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command configures a range of encapsulation values.
Parameters
- encap-range
Specifies a range of encapsulation values on a port to be synchronized with a multi-chassis peer.
- sync-tag sync-tag
Specifies a synchronization tag, up to 32 characters, to use when synchronizing this encapsulation value range with the multi-chassis peer.
Ethernet ring commands
eth-ring
Syntax
eth-ring ring-id
no eth-ring
Context
config
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a G.8032 protected Ethernet ring. G.8032 Rings may be configured as major rings with two paths (a&b).
The no form of this command deletes the Ethernet ring specified by the ring-id.
Default
no eth-ring
Parameters
- ring-id
Specifies the ring ID.
guard-time
Syntax
guard-time time
no guard-time
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the guard time for an Eth-Ring. The guard timer is standard and is configurable from 100 ms to 2 seconds
The no form of this command reverts to the default guard-time.
Default
5 deciseconds
Parameters
- value
Specifies the guard-time.
revert-time
Syntax
revert-time time
no revert-time
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the revert time for an Eth-Ring. It ranges from 60 seconds to 720 second by 1 second intervals.
The no form of this command means non-revertive mode and revert time essentially is 0 meaning the revert timers are not set.
Default
300 seconds
Parameters
- value
Specifies the guard-time, in seconds.
ccm-hold-time
Syntax
ccm-hold-time {down down-timeout | up up-timeout}
no ccm-hold-time
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures eth-ring dampening timers.
This command specifies the timer, which controls the delay between detecting that ring path is down and reporting it to the G.8032 protection module. If a non-zero value is configured, the CPM will wait for the time specified in the value parameter before reporting it to the G.8032 protection module.
This down-timeout parameter applies only to ring path CCM. It does NOT apply to the ring port link state. To dampen ring port link state transitions, use hold-time parameter from the physical member port.
This command specifies the timer, which controls the delay between detecting that ring path is up and reporting it to the G.8032 protection module. If a non-zero value is configured, the CPM will wait for the time specified in the value parameter before reporting it to the G.8032 protection module.
This parameter applies only to ring path CCM. It does NOT apply to the member port link state. To dampen member port link state transitions, use hold-time parameter from the physical member port.
The no form of this command reverts the up and down timer to the default values.
Parameters
- down-timeout
Specifies the down timeout, in deciseconds.
- up-timeout
Specifies the hold-time for reporting the recovery, in deciseconds.
rpl-node
Syntax
rpl-node <owner | nbr>
no rpl-node
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the G.8032 Ring Protection Link (RPL) type as owner or neighbor. When RPL owner or neighbor is specified, either the a or b path must be configured with the RPL end command. An owner is responsible for operation of the RPL link. Configuring the RPL as neighbor is optional (can be left as no rpl-node) but if the command is used the nbr is mandatory.
The no form of this command removes the connection to the RPL link.
Default
no rpl-node
Parameters
- owner
Specifies a G.8032 RPL type of owner.
- nbr
Specifies a G.8032 RPL type of neighbor.
node-id
Syntax
node-id mac
no node-id
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This optional command configures the MAC address of the RPL control. The default is to use the chassis MAC for the ring control. This command allows the chassis MAC to be overridden with another MAC address.
The no form of this command removes the RPL link.
Default
no node-id
Parameters
- mac
Specifies a MAC address in the format xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx
sub-ring
Syntax
sub-ring {virtual-link | non-virtual-link}
[no] sub-ring
Context
config>eth-ring>sub-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies this ring-id to be sub-ring as defined in G.8032. By declaring the ring as a sub-ring object, the ring will only have one valid path and the sub-ring will be connected to a major ring or a VPLS instance. The virtual-link parameter declares that a sub-ring is connected to another ring and that control messages can be sent over the attached ring to the other side of the sub-ring. The non-virtual channel parameter declares that a sub-ring may be connected to a another ring or to a VPLS instance but that no control messages from the sub-ring use the attached ring or VPLS instance. The non-virtual channel behavior is standard G.8032 capability.
The no form of this command deletes the sub-ring and its virtual channel associations.
Default
no sub-ring
Parameters
- virtual-link
Specifies the interconnection is to a ring and a virtual link will be used.
- non-virtual-link
Specifies the interconnection is to a ring or a VPLS instance and a virtual link will not be used.
compatible-version
Syntax
compatible-version version
[no] compatible-version
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the backward compatibility logic for the Ethernet rings.
Default
2
Parameters
- version
Specifies the Ethernet ring version.
path
Syntax
path {a | b} [{port-id} raps-tag qtag [.qtag]]
[no] path {a | b}
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command assigns the ring (major or sub-ring) path to a port and defines the Ring APS tag. Rings typically have two paths, a and b.
The no form of this command removes the path a or b.
Default
no path
Parameters
- path
Specifies the path.
- port-id
Specifies the port ID.
- qtag[.qtag]
Specifies the qtag. For Dot1q, only the first qtag is used. For QinQ, both qtags can be used.
description
Syntax
description long-description-string
no description
Context
config>eth-ring>path
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds a text description for the ring path.
The no form of this command removes the text description.
Parameters
- string
Specifies the text description up to 160 characters.
rpl-end
Syntax
rpl-end
no rpl-end
Context
config>eth-ring>path
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the G.8032 path as a ring protection link end. The ring should be declared as either a RPL owner or RPL neighbor for this command to be allowed. Only path a or path b can be declared an RPL-end.
The no form of this command sets the rpl-end to default no rpl-end.
Default
no rpl-end
eth-cfm
Syntax
eth-cfm
Context
config>eth-ring>path
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure ETH-CFM parameters.
mep
Syntax
[no] mep mep-id domain md-index association ma-index
Context
config>eth-ring>path>eth-cfm
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command provisions an 802.1ag maintenance endpoint (MEP).
The no form of this command reverts to the default values.
Parameters
- mep-id
Specifies the maintenance association (MA) end point identifier.
- md-index
Specifies the maintenance domain (MD) index value.
- ma-index
Specifies the MA index value.
ccm-enable
Syntax
[no] ccm-enable
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the generation of CCM messages.
The no form of this command disables the generation of CCM messages.
ccm-ltm-priority
Syntax
ccm-ltm-priority priority
no ccm-ltm-priority
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the priority value for CCMs and LTMs transmitted by the MEP.
The no form of this command removes the priority value from the configuration.
Default
the highest priority on the bridge-port
Parameters
- priority
Specifies the priority of CCM and LTM messages.
control-mep
Syntax
no control-mep
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the context of the CC state by the Ethernet ring for consideration in the protection algorithm. The use of control-mep command is recommended if fast failure detection is required, especially when Link Layer OAM does not provide the required detection time.
The no form of this command disables the use of the CC state by the Ethernet ring.
Default
no control-mep
eth-test-enable
Syntax
[no] eth-test-enable
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables eth-test functionality on MEP. For this test to work, operators need to configure ETH-test parameters on both sender and receiver nodes. The ETH-test then can be done using the following OAM commands:
oam eth-cfm eth-test mac-address mep mep-id domain md-index association ma-index [priority priority] [data-length data-length]
A check is done for both the provisioning and test to ensure the MEP is an Y.1731 MEP (MEP provisioned with domain format none, association format icc-based). If not, the operation fails. An error message in the CLI and SNMP will indicate the problem.
test-pattern
Syntax
test-pattern {all-zeros | all-ones} [crc-enable]
no test-pattern
Context
config>eth-ring>path>eth-cfm>mep>eth-test-enable
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the test pattern for eth-test frames.
The no form of this command removes the values from the configuration.
Default
all-zeros
Parameters
- all-zeros
Specifies to use all zeros in the test pattern.
- all-ones
Specifies to use all ones in the test pattern.
- crc-enable
Specifies that a CRC checksum will be generated.
bit-error-threshold
Syntax
bit-error-threshold bit-errors
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the lowest priority defect that is allowed to generate a fault alarm.
Default
1
Parameters
- bit-errors
Specifies the lowest priority defect.
mac-address
Syntax
mac-address mac-address
no mac-address
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the MAC address of the MEP.
The no form of this command reverts the MAC address of the MEP back to that of the port (if the MEP is on a SAP) or the bridge (if the MEP is on a spoke-SDP).
Parameters
- mac-address
Specifies the MAC address of the MEP.
one-way-delay-threshold
Syntax
one-way-delay-threshold seconds
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables one way delay threshold time limit.
Default
3 seconds
Parameters
- priority
Specifies the value for the threshold, in seconds.
shutdown
Syntax
[no] shutdown
Context
config>eth-ring>path>eth-cfm>mep
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively enables or disables the MEP.
The no form of this command disables or enables the MEP.
Default
shutdown
shutdown
Syntax
[no] shutdown
Context
config>eth-ring>path
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively enables or disables the path.
The no form of this command disables or enables the path.
Default
shutdown
shutdown
Syntax
[no] shutdown
Context
config>eth-ring
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively enables/disables the Ethernet ring.
The no form of this command disables/enables the ring.
Default
shutdown
description
Syntax
description long-description-string
no description
Context
config>eth-tunnel
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds a text description for the eth-tunnel.
The no form of this command removes the text description.
Default
‟Eth-tunnel”
Parameters
- string
Specifies the text description up to 160 characters.
split-horizon-group
Syntax
split-horizon-group group-name
no split-horizon-group
Context
config>lag
config>port
Platforms
7210 SAS-D and 7210 SAS-Dxp
Description
This command associates a split horizon group to which this port or LAG belongs. For LAGs, all the member ports of the LAG are added to the split horizon group. The split-horizon-group must be configured in the config context.
Configuring or removing the association of the port requires the following conditions to be satisfied:
There are no applications associated with the port/lag (like SAPs on the port, and so on).
The port or LAG should be administratively shutdown.
The port should not be part of a LAG.
To change split horizon group of a port or LAG, the old split horizon group should be first removed from the port or LAG, and then the new split horizon group can be configured.
The no form of this command removes the port or all member ports of the LAG from the split horizon group.
Parameters
- group-name
Specifies the name of the split horizon group up to 32 characters. The string must be composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
Show commands
Hardware commands
chassis
Syntax
chassis [environment] [power-supply]
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
The environment option is not supported on the 7210 SAS-D.
This command displays general chassis status information.
Parameters
- environment
Displays chassis environmental status information.
- power-supply
Displays chassis power supply status information.
Output
The following output is an example of chassis information, and Output fields: chassis describes the output fields.
Sample outputThis CLI output is obtained only if the hardware supports ‟DC source failure detection”.
A:7210-SAS> show chassis
===============================================================================
Chassis Information
===============================================================================
Name : STU2597
Type : 7210 SAS-D-1
Location :
Coordinates :
CLLI code :
Number of slots : 2
Number of ports : 24
Critical LED state : Red
Major LED state : Off
Minor LED state : Off
Over Temperature state : OK
Base MAC address : 00:25:ba:04:b9:bc
Hardware Data
Part number : 3HE04410ABAC01
CLEI code : IPMK310JRA
Serial number : NS1026C0341
Manufacture date : 06292010
Manufacturing string :
Manufacturing deviations :
Time of last boot : 2010/11/09 16:12:40
Current alarm state : alarm active
-------------------------------------------------------------------------------
Environment Information
Number of fan trays : 1
Number of fans : 3
Fan tray number : 1
Status : up
Speed : half speed
-------------------------------------------------------------------------------
Power Supply Information
Number of power supplies : 2
Power supply number : 1
Configured power supply type : dc
Status : failed
DC power : out of range
Input power : out of range
Output power : within range
Power supply number : 2
Configured power supply type : dc
Status : up
DC power : within range
Input power : within range
Output power : within range
===============================================================================
A:7210-SAS>
A:7210-SAS> show chassis
===============================================================================
Chassis Information
===============================================================================
Name : STU2597
Type : 7210 SAS-D-1
Location :
Coordinates :
CLLI code :
Number of slots : 2
Number of ports : 24
Critical LED state : Off
Major LED state : Off
Minor LED state : Off
Over Temperature state : OK
Base MAC address : 00:25:ba:04:b9:bc
Hardware Data
Part number : 3HE04410ABAC01
CLEI code : IPMK310JRA
Serial number : NS1026C0341
Manufacture date : 06292010
Manufacturing string :
Manufacturing deviations :
Time of last boot : 2010/11/09 16:12:40
Current alarm state : alarm cleared
-------------------------------------------------------------------------------
Environment Information
Number of fan trays : 1
Number of fans : 3
Fan tray number : 1
Status : up
Speed : half speed
-------------------------------------------------------------------------------
Power Supply Information
Number of power supplies : 2
Power supply number : 1
Configured power supply type : dc
Status : up
DC power : within range
Input power : within range
Output power : within range
Power supply number : 2
Configured power supply type : dc
Status : up
DC power : within range
Input power : within range
Output power : within range
===============================================================================
A:7210-SAS>
*A:SAS-D>show# chassis
===============================================================================
Chassis Information
===============================================================================
Name : SAS-D
Type : 7210 SAS-D 6F4T-1
Location :
Coordinates :
CLLI code :
Number of slots : 2
Number of ports : 10
Critical LED state : Off
Major LED state : Off
Minor LED state : Off
Over Temperature state : OK
Base MAC address : 00:3f:11:ab:ca:11
Hardware Data
Part number :
CLEI code :
Serial number : NS1050C0071
Manufacture date :
Manufacturing string :
Manufacturing deviations :
Time of last boot : 1970/01/01 00:00:03
Current alarm state : alarm cleared
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Power Supply Information
Number of power supplies : 1
Power supply number : 1
Configured power supply type : ac single
Status : up
AC power : within range
===============================================================================
*A:SAS-D>show#
Label |
Description |
|---|---|
Name |
The system name for the router. |
Type |
The device model number. |
Location |
The system location for the device. |
Coordinates |
A user-configurable string that indicates the Global Positioning System (GPS) coordinates for the location of the chassis. For example: N 45 58 23, W 34 56 12 N37 37' 00 latitude, W122 22' 00 longitude N36*39.246' W121*40.121' |
CLLI Code |
The Common Language Location Identifier (CLLI) that uniquely identifies the geographic location of places and specific functional categories of equipment unique to the telecommunications industry. |
Number of slots |
The number of slots in this chassis that are available for plug-in cards. The total number includes the IOM slots and the CPM slots. |
Number of ports |
The total number of ports currently installed in this chassis. This count does not include the Ethernet ports on the CPMs that are used for management access. |
Critical LED state |
The current state of the Critical LED in this chassis. |
Major LED state |
The current state of the Major LED in this chassis. |
Minor LED state |
The current state of the Minor LED in this chassis. |
Base MAC address |
The base chassis Ethernet MAC address. |
Admin chassis mode |
The configured chassis mode. |
Oper chassis mode |
The current chassis mode. |
Part number |
The CPM part number. |
CLEI code |
The code used to identify the router. |
Serial number |
The CPM part number. Not user modifiable. |
Manufacture date |
The chassis manufacture date. Not user modifiable. |
Manufacturing string |
Factory-inputted manufacturing text string. Not user modifiable. |
Administrative state |
Up The card is administratively up. |
Down The card is administratively down. |
|
Operational state |
Up The card is operationally up. |
Down The card is operationally down. |
|
Time of last boot |
The date and time the most recent boot occurred. |
Current alarm state |
Displays the alarm conditions for the specific board. |
Number of fan trays |
The total number of fan trays installed in this chassis. |
Number of fans |
The total number of fans installed in this chassis. |
Operational status |
Current status of the fan tray. |
Fan speed |
Half speed The fans are operating at half speed. |
Full speed The fans are operating at full speed. |
|
Number of power supplies |
The number of power supplies installed in the chassis. |
Power supply number |
The ID for each power supply installed in the chassis. |
AC power |
Within range AC voltage is within range. |
Out of range AC voltage is out of range. |
|
DC power |
Within range DC voltage is within range. |
Out of range DC voltage is out of range. |
|
Over temp |
Within range The current temperature is within the acceptable range. |
Out of range The current temperature is above the acceptable range. |
|
Status |
Up The specified power supply is up. |
Down The specified power supply is down |
card
Syntax
card [slot-number] [detail]
card state
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays card information.
If no command line parameters are specified, a card summary for all cards is displayed.
Parameters
- slot-number
Displays information for the specified card slot.
- detail
Displays detailed card information.
Output
The following outputs are examples of card information, and the associated tables describe the output fields.
Sample output for 7210 SAS-K 2F1C2T
*A:SAH01-051>show# card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
A sfm-sas up up/active
===============================================================================
*A:SAH01-051>show#
|
Label |
Description |
|---|---|
|
Slot |
The slot number of the card in the chassis. |
|
Provisioned Card-type |
The card type that is configured for the slot. |
|
Equipped Card-type |
The card type that is actually populated in the slot. |
|
Admin State |
Up The card is administratively up. |
|
Down The card is administratively down. |
|
|
Operational State |
Up The card is operationally up. |
|
Down The card is operationally down. |
*A:SAH01-051>show# card detail
===============================================================================
Card 1
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 iom-sas up up
IOM Card Specific Data
Clock source : none
Named Pool Mode : Disabled
Available MDA slots : 2
Installed MDAs : 1
Hardware Data
Platform type : N/A
Part number :
CLEI code :
Serial number : SAH01-051
Manufacture date :
Manufacturing string : (Not Specified)
Manufacturing deviations : (Not Specified)
Manufacturing assembly number :
Administrative state : up
Operational state : up
Temperature : 49C
Temperature threshold : 58C
Software boot (rom) version : X-0.0.I2282 on Sat Dec 20 14:21:54 IST
2014 by builder
Software version : TiMOS-B-7.0.B1-205 both/xen NOKIA SAS-K *
Time of last boot : 2014/01/14 05:13:59
Current alarm state : alarm cleared
Base MAC address : 00:03:fa:27:15:4e
Last bootup reason : hard boot
Memory capacity : 1,024 MB
* indicates that the corresponding row element may have been truncated.
===============================================================================
Card A
===============================================================================
Slot Provisioned Type Admin Operational Comments
Equipped Type (if different) State State
-------------------------------------------------------------------------------
A sfm-sas up up/active
BOF last modified : N/A
Config file version : THU JAN 01 00:19:52 1970 UTC
Config file last modified : 2014/02/10 05:36:50
Config file last saved : N/A
M/S clocking ref state : primary
Flash - cf1:
Administrative State : up
Operational state : up
Serial number : 4C530007300704117312
Firmware revision : 1.27
Model number : Flash 0
Size : 7,629 MB
Free space : 7,574 MB
Flash - uf1:
Administrative State : up
Operational state : not equipped
Hardware Data
Platform type : N/A
Part number :
CLEI code :
Serial number : SAH01-051
Manufacture date :
Manufacturing string : (Not Specified)
Manufacturing deviations : (Not Specified)
Manufacturing assembly number :
Administrative state : up
Operational state : up
Temperature : 49C
Temperature threshold : 58C
Software boot (rom) version : X-0.0.I2282 on Sat Dec 20 14:21:54 IST
2014 by builder
Software version : TiMOS-B-7.0.B1-205 both/xen NOKIA SAS-K *
Time of last boot : 2014/01/14 05:13:50
Current alarm state : alarm cleared
Base MAC address : 00:03:fa:27:15:4e
Memory capacity : 1,024 MB
* indicates that the corresponding row element may have been truncated.
===============================================================================
*A:SAH01-051>show#
|
Label |
Description |
|---|---|
|
Clock source |
Source of clock for the IOM. Note: Currently this parameter always displays 'none' |
|
Available MDA slots |
The number of MDA slots available on the IOM. |
|
Installed MDAs |
The number of MDAs installed on the IOM |
|
Part number |
The IOM part number. |
|
CLEI code |
The Common Language Location Identifier (CLLI) code string for the router. |
|
Serial number |
The serial number. Not user modifiable. |
|
Manufacture date |
The chassis manufacture date. Not user modifiable. |
|
Manufacturing string |
Factory-inputted manufacturing text string. Not user modifiable. |
|
Manufacturing deviations |
Displays a record of changes by manufacturing to the hardware or software and which is outside the normal revision control process. |
|
Administrative state |
Up The card is administratively up. |
|
Down The card is administratively down. |
|
|
Operational state |
Up The card is operationally up. |
|
Down The card is operationally down. |
|
|
Temperature |
Internal chassis temperature. |
|
Temperature threshold |
The value above which the internal temperature must rise to indicate that the temperature is critical. |
|
Software boot version |
The version of the boot image. |
|
Software version |
The software version number. |
|
Time of last boot |
The date and time the most recent boot occurred. |
|
Current alarm state |
Displays the alarm conditions for the specific board. |
|
Base MAC address |
Displays the base MAC address of the hardware component. |
|
Memory Capacity |
Displays the memory capacity of the card. |
The following output is an example of CPM card information, and Output fields: CPM card describes the output fields.
*A:SAS-D>show# card
===============================================================================
Card Summary
===============================================================================
Slot Provisioned Equipped Admin Operational
Card-type Card-type State State
-------------------------------------------------------------------------------
1 iom-sas iom-sas up up
A sfm-sas sfm-sas up up/active
===============================================================================
*A:SAS-D>show#
|
Label |
Description |
|---|---|
|
Slot |
The slot of the card in the chassis. |
|
Card Provisioned |
The SF/CPM type that is configured for the slot. |
|
Card Equipped |
The SF/CPM type that is actually populated in the slot. |
|
Admin State |
Up The SF/CPM is administratively up. |
|
Down The SF/CPM is administratively down. |
|
|
Operational State |
Up The SF/CPM is operationally up. |
|
Down The SF/CPM is operationally down. |
|
|
BOF last modified |
The date and time of the most recent BOF modification. |
|
Config file version |
The configuration file version. |
|
Config file last modified |
The date and time of the most recent config file modification. |
|
Config file last modified |
The date and time of the most recent config file modification. |
|
Config file last saved |
The date and time of the most recent config file save. |
|
CPM card status |
active The card is acting as the primary (active) CPM in a redundant system. standby The card is acting as the standby (secondary) CPM in a redundant system. |
|
Administrative state |
Up The CPM is administratively up. |
|
Down The CPM is administratively down. |
|
|
Operational state |
Up The CPM is operationally up. |
|
Down The CPM is operationally down. |
|
|
Serial number |
The compact flash part number. Not user modifiable. |
|
Firmware revision |
The firmware version. Not user modifiable. |
|
Model number |
The compact flash model number. Not user modifiable. |
|
Size |
The amount of space available on the compact flash card. |
|
Free space |
The amount of space remaining on the compact flash card. |
|
Part number |
The SF/CPM part number. |
|
CLEI code |
The code used to identify the router. |
|
Serial number |
The SF/CPM part number. Not user modifiable. |
|
Manufacture date |
The chassis manufacture date. Not user modifiable. |
|
Manufacturing string |
Factory-inputted manufacturing text string. Not user modifiable. |
|
Administrative state |
Up The card is administratively up. Down The card is administratively down. |
|
Operational state |
Up The card is operationally up. |
|
Down The card is operationally down. |
|
|
Time of last boot |
The date and time the most recent boot occurred. |
|
Current alarm state |
Displays the alarm conditions for the specific board. |
|
Status |
Displays the current status. |
|
Temperature |
Internal chassis temperature. |
|
Temperature threshold |
The value above which the internal temperature must rise to indicate that the temperature is critical. |
|
Software boot version |
The version of the boot image. |
|
Memory capacity |
The total amount of memory. |
The following table describes the output fields.
|
Label |
Description |
|---|---|
|
Slot/MDA |
The slot number of the card in the chassis. |
|
Provisioned Type |
The card type that is configured for the slot. |
|
Equipped Type |
The card type that is actually populated in the slot. |
|
Admin State |
Up The card is administratively up. |
|
Down The card is administratively down. |
|
|
Operational State |
Up The card is operationally up. |
|
provisioned There is no card in the slot but it has been preconfigured. |
|
|
Num Ports |
The number of ports available on the MDA. |
|
Num MDA |
The number of MDAs installed. |
|
Comments |
Indicates whether the SF/CPM is the active or standby. |
mda
Syntax
mda [slot [/mda]] [detail]
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays MDA information.
If no command line options are specified, a summary output of all MDAs is displayed in table format.
Parameters
- slot
Specifies the slot number for which to display MDA information.
- mda
Specifies the MDA number in the slot for which to display MDA information.
- detail
Displays detailed MDA information.
Output
The following outputs are an example of MDA information, and Output fields: MDA and Output fields: MDA detail describe the output fields.
Sample outputB:Dut-D# show mda 1/1 detail
===============================================================================
MDA 1/1 detail
===============================================================================
Slot Mda Provisioned Equipped Admin Operational
Mda-type Mda-type State State
-------------------------------------------------------------------------------
1 1 m10-1gb-sfp m10-1gb-sfp up up
MDA Specific Data
Maximum port count : 10
Number of ports equipped : 10
Network ingress queue policy : default
Capabilities : Ethernet
Hardware Data
Part number : 3HE00026AAAC01
CLEI code :
Serial number : NS042800525
Manufacture date : 07082004
Manufacturing string :
Manufacturing deviations :
Administrative state : up
Operational state : up
Temperature : 42C
Temperature threshold : 75C
Time of last boot : 2007/04/11 09:37:52
Current alarm state : alarm cleared
Base MAC address : 00:03:fa:0e:9e:03
===============================================================================
B:Dut-D#
*A:SAH01-051>show# mda 1 detail
===============================================================================
MDA 1/1 detail
===============================================================================
Slot Mda Provisioned Type Admin Operational
Equipped Type (if different) State State
-------------------------------------------------------------------------------
1 1 m2-tx+2-sfp+1-combo up up
MDA Specific Data
Maximum port count : 5
Number of ports equipped : 5
Network ingress queue policy : default
Capabilities : Ethernet
Hardware Data
Platform type : N/A
Part number :
CLEI code :
Serial number : SAH01-051
Manufacture date :
Manufacturing string : (Not Specified)
Manufacturing deviations : (Not Specified)
Manufacturing assembly number :
Administrative state : up
Operational state : up
Temperature : 49C
Temperature threshold : 58C
Software version : N/A
Time of last boot : 2014/01/14 05:14:03
Current alarm state : alarm cleared
Base MAC address : 00:03:fa:27:15:50
Firmware version : N/A
===============================================================================
*A:SAH01-051>show#
*A:SAS-D>show# mda 1 detail
===============================================================================
MDA 1/1 detail
===============================================================================
Slot Mda Provisioned Equipped Admin Operational
Mda-type Mda-type State State
-------------------------------------------------------------------------------
1 1 m4-tx+6-sfp m4-tx+6-sfp up up
MDA Specific Data
Maximum port count : 10
Number of ports equipped : 10
Network ingress queue policy : default
Capabilities : Ethernet
Hardware Data
Part number :
CLEI code :
Serial number : NS1050C0071
Manufacture date :
Manufacturing string :
Manufacturing deviations :
Administrative state : up
Operational state : up
Temperature : 44C
Temperature threshold : 55C
Software version : N/A
Time of last boot : 1970/01/01 00:00:30
Current alarm state : alarm cleared
Base MAC address : 00:3f:11:ab:ca:13
-------------------------------------------------------------------------------
QOS Settings
-------------------------------------------------------------------------------
Ing. Named Pool Policy : None
Egr. Named Pool Policy : None
===============================================================================
*A:SAS-D>show#
Label |
Description |
|---|---|
Slot |
The chassis slot number. |
MDA |
The MDA slot number. |
Provisioned MDA-type |
The MDA type provisioned. |
Equipped MDA-type |
The MDA type actually installed. |
Admin State |
Up Administratively up. |
Down Administratively down. |
|
Ops State |
Up Operationally up. |
Down Operationally down. |
Label |
Description |
|---|---|
Slot |
The chassis slot number. |
Slot |
The MDA slot number. |
Provisioned Provisioned-type |
The provisioned MDA type. |
Equipped Mda-type |
The MDA type that is physically inserted into this slot in this chassis. |
Admin State |
Up The MDA is administratively up. |
Down The MDA is administratively down. |
|
Operational State |
Up The MDA is operationally up. |
Down The MDA is operationally down. |
|
Maximum port count |
The maximum number of ports that can be equipped on the MDA card. |
Number of ports equipped |
The number of ports that are actually equipped on the MDA. |
Transmit timing selected |
Indicates the source for the timing used by the MDA. |
Sync interface timing status |
Indicates whether the MDA has qualified one of the timing signals from the CPMs. |
Network Ingress Queue Policy |
Specifies the network queue policy applied to the MDA to define the queuing structure for this object. |
Capabilities |
Specifies the minimum size of the port that can exist on the MDA. |
Part number |
The hardware part number. |
CLEI code |
The code used to identify the MDA. |
Serial number |
The MDA part number. Not user modifiable. |
Manufacture date |
The MDA manufacture date. Not user modifiable. |
Manufacturing string |
Factory-inputted manufacturing text string. Not user modifiable. |
Administrative state |
Up The MDA is administratively up. |
Down The MDA is administratively down. |
|
Operational state |
Up The MDA is operationally up. |
Down The MDA is operationally down. |
|
Time of last boot |
The date and time the most recent boot occurred. |
Current alarm state |
Displays the alarm conditions for the specific MDA. |
Base MAC address |
The base chassis Ethernet MAC address. Special purpose MAC addresses used by the system software are constructed as offsets from this base address. |
pools
Syntax
pools mda-id [/port] [access-app pool-name]
pools mda-id [/port] [network-app pool-name]
Context
show
Platforms
7210 SAS-D and 7210 SAS-Dxp
Description
This command displays pool information.
Parameters
- mda-id[/port]
Displays the pool information of the specified MDA.
- access-app pool-name
Displays the pool information of the specified QoS policy.
- network-app pool-name
Displays the pool information of the specified QoS policy.
Output
The following outputs are examples of pool information, and Output fields: pool describes show the output fields.
Dumping concise pool information for all ports in the MDA:
*A:card-1>config# show pools 1/1
===============================================================================
Type Id App. Pool Name Actual ResvCBS PoolSize
Admin ResvCBS
-------------------------------------------------------------------------------
Port 1/1/1 Acc-Egr default 0 0
Sum
Port 1/1/1 AUp-Egr default 50 99
Sum
Port 1/1/2 Acc-Egr default 26 79
Sum
Port 1/1/2 AUp-Egr default 0 0
Sum
Port 1/1/3 Acc-Egr default 26 79
Sum
Port 1/1/3 AUp-Egr default 0 0
Sum
Port 1/1/4 Acc-Egr default 26 79
Sum
...
Sum
Port 1/1/24 AUp-Egr default 0 0
Sum
===============================================================================
*A:card-1>config#
*A:SAS-D>show# pools 1/1
===============================================================================
===============================================================================
Type Id App. Pool Name Actual ResvCBS PoolSize
Admin ResvCBS
-------------------------------------------------------------------------------
Port 1/1/1 Acc-Egr default 68 186
Sum
Port 1/1/1 Net-Egr default 0 0
Sum
Port 1/1/2 Acc-Egr default 68 186
Sum
Port 1/1/2 Net-Egr default 0 0
Sum
Port 1/1/3 Acc-Egr default 68 186
Sum
Port 1/1/3 Net-Egr default 0 0
Sum
Port 1/1/4 Acc-Egr default 68 186
Sum
Port 1/1/4 Net-Egr default 0 0
Sum
Port 1/1/5 Acc-Egr default 68 186
Sum
Port 1/1/5 Net-Egr default 0 0
Sum
Port 1/1/6 Acc-Egr default 68 186
Sum
Port 1/1/6 Net-Egr default 0 0
Sum
Port 1/1/7 Acc-Egr default 68 186
Sum
Port 1/1/7 Net-Egr default 0 0
Sum
Port 1/1/8 Acc-Egr default 68 186
Sum
Port 1/1/8 Net-Egr default 0 0
Sum
Port 1/1/9 Acc-Egr default 68 186
Sum
Port 1/1/9 Net-Egr default 0 0
Sum
Port 1/1/10 Acc-Egr default 0 0
Sum
Port 1/1/10 Net-Egr default 68 186
Sum
===============================================================================
*A:SAS-D>show#
The following output displays egress pool information for the access port:
*A:card-1>config# show pools 1/1/5 access-egress
===============================================================================
Pool Information
===============================================================================
Port : 1/1/5
Application : Acc-Egr Pool Name : default
Resv CBS : Sum
-------------------------------------------------------------------------------
Utilization State Start-Threshold
-------------------------------------------------------------------------------
High-Slope Down 75%
Low-Slope Down 50%
-------------------------------------------------------------------------------
Queue High Slope Drop Rate(%) Low Slope Drop Rate(%)
-------------------------------------------------------------------------------
Queue 1 6.250000 100.000000
Queue 2 6.250000 100.000000
Queue 3 6.250000 100.000000
Queue 4 6.250000 100.000000
Queue 5 6.250000 100.000000
Queue 6 6.250000 100.000000
Queue 7 6.250000 100.000000
Queue 8 6.250000 100.000000
Pool Total : 79 KB
Pool Shared : 53 KB Pool Resv : 26 KB
Pool Total In Use : 0 KB
Pool Shared In Use : 0 KB Pool Resv In Use : 0 KB
-------------------------------------------------------------------------------
FC-Maps ID CBS Depth A.CIR A.PIR
O.CIR O.PIR
-------------------------------------------------------------------------------
be 1/1/5 3200 0 0 1000000
0 Max
l2 1/1/5 3200 0 0 1000000
0 Max
af 1/1/5 3200 0 0 1000000
0 Max
l1 1/1/5 3200 0 0 1000000
0 Max
h2 1/1/5 3200 0 0 1000000
0 Max
ef 1/1/5 3200 0 0 1000000
0 Max
h1 1/1/5 3200 0 0 1000000
0 Max
nc 1/1/5 3200 0 0 1000000
0 Max
===============================================================================
*A:card-1>config#
*A:SAS-D>show# pools 1/1/2 access-egress
===============================================================================
Pool Information
===============================================================================
Port : 1/1/2
Application : Acc-Egr Pool Name : default
Resv CBS : Sum
-------------------------------------------------------------------------------
High Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 70 90 75
Queue2 Down 70 90 75
Queue3 Down 70 90 75
Queue4 Down 70 90 75
Queue5 Down 70 90 75
Queue6 Down 70 90 75
Queue7 Down 70 90 75
Queue8 Down 70 90 75
-------------------------------------------------------------------------------
Low Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 50 75 75
Queue2 Down 50 75 75
Queue3 Down 50 75 75
Queue4 Down 50 75 75
Queue5 Down 50 75 75
Queue6 Down 50 75 75
Queue7 Down 50 75 75
Queue8 Down 50 75 75
-------------------------------------------------------------------------------
Non Tcp Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 50 75 75
Queue2 Down 50 75 75
Queue3 Down 50 75 75
Queue4 Down 50 75 75
Queue5 Down 50 75 75
Queue6 Down 50 75 75
Queue7 Down 50 75 75
Queue8 Down 50 75 75
-------------------------------------------------------------------------------
Time Avg Factor
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Queue Id Time Avg Factor
-------------------------------------------------------------------------------
Queue1 7
Queue2 7
Queue3 7
Queue4 7
Queue5 7
Queue6 7
Queue7 7
Queue8 7
MMU Pool Total In Use: 0 KB MMU Pool Shared In*: 0 KB
Pool Total : 186 KB
Pool Shared : 118 KB Pool Resv : 68 KB
Pool Total In Use : 0 KB
Pool Shared In Use : 0 KB Pool Resv In Use : 0 KB
-------------------------------------------------------------------------------
ID FC-MAPS CBS (B) Depth A.CIR A.PIR
O.CIR O.PIR
-------------------------------------------------------------------------------
1/1/2 be 8698 0 0 1000000
0 Max
1/1/2 l2 8698 0 0 1000000
0 Max
1/1/2 af 8698 0 0 1000000
0 Max
1/1/2 l1 8698 0 0 1000000
0 Max
1/1/2 h2 8698 0 0 1000000
0 Max
1/1/2 ef 8698 0 0 1000000
0 Max
1/1/2 h1 8698 0 0 1000000
0 Max
1/1/2 nc 8698 0 0 1000000
0 Max
===============================================================================
* indicates that the corresponding row element may have been truncated.
The following output displays egress pool information for an access uplink port:
*A:card-1>config# show pools 1/1/1 access-uplink-egress
===============================================================================
Pool Information
===============================================================================
Port : 1/1/1
Application : AUp-Egr Pool Name : default
Resv CBS : Sum
-------------------------------------------------------------------------------
Utilization State Start-Threshold
-------------------------------------------------------------------------------
High-Slope Down 75%
Low-Slope Down 50%
-------------------------------------------------------------------------------
Queue High Slope Drop Rate(%) Low Slope Drop Rate(%)
-------------------------------------------------------------------------------
Queue 1 6.250000 100.000000
Queue 2 6.250000 100.000000
Queue 3 6.250000 100.000000
Queue 4 6.250000 100.000000
Queue 5 6.250000 100.000000
Queue 6 6.250000 100.000000
Queue 7 6.250000 100.000000
Queue 8 6.250000 100.000000
Pool Total : 99 KB
Pool Shared : 49 KB Pool Resv : 50 KB
Pool Total In Use : 0 KB
Pool Shared In Use : 0 KB Pool Resv In Use : 0 KB
-------------------------------------------------------------------------------
FC-Maps ID CBS Depth A.CIR A.PIR
O.CIR O.PIR
-------------------------------------------------------------------------------
be 1/1/1 3557 0 0 1000000
0 Max
l2 1/1/1 3557 0 250000 1000000
249984 Max
af 1/1/1 10671 0 250000 1000000
249984 Max
l1 1/1/1 3557 0 250000 1000000
249984 Max
h2 1/1/1 10671 0 1000000 1000000
Max Max
ef 1/1/1 10671 0 1000000 1000000
Max Max
h1 1/1/1 3557 0 100000 1000000
100032 Max
nc 1/1/1 3557 0 100000 1000000
100032 Max
===============================================================================
*A:card-1>config#
*A:SASD>config>port# show pools 1/1/9 access-uplink-egress
===============================================================================
Pool Information
===============================================================================
Port : 1/1/9
Application : Net-Egr Pool Name : default
Resv CBS : Sum
-------------------------------------------------------------------------------
High Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 70 90 75
Queue2 Down 70 90 75
Queue3 Down 70 90 75
Queue4 Down 70 90 75
Queue5 Down 70 90 75
Queue6 Down 70 90 75
Queue7 Down 70 90 75
Queue8 Down 70 90 75
-------------------------------------------------------------------------------
Low Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 50 75 75
Queue2 Down 50 75 75
Queue3 Down 50 75 75
Queue4 Down 50 75 75
Queue5 Down 50 75 75
Queue6 Down 50 75 75
Queue7 Down 50 75 75
Queue8 Down 50 75 75
-------------------------------------------------------------------------------
Non Tcp Slope
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
QueueId State Start-Avg(%) Max-Avg(%) Max-Prob(%)
-------------------------------------------------------------------------------
Queue1 Down 50 75 75
Queue2 Down 50 75 75
Queue3 Down 50 75 75
Queue4 Down 50 75 75
Queue5 Down 50 75 75
Queue6 Down 50 75 75
Queue7 Down 50 75 75
Queue8 Down 50 75 75
-------------------------------------------------------------------------------
Time Avg Factor
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Queue Id Time Avg Factor
-------------------------------------------------------------------------------
Queue1 7
Queue2 7
Queue3 7
Queue4 7
Queue5 7
Queue6 7
Queue7 7
Queue8 7
MMU Pool Total In Use: 0 KB MMU Pool Shared In*: 0 KB
Pool Total : 186 KB
Pool Shared : 102 KB Pool Resv : 68 KB
Pool Total In Use : 0 KB
Pool Shared In Use : 0 KB Pool Resv In Use : 0 KB
-------------------------------------------------------------------------------
ID FC-MAPS CBS (B) Depth A.CIR A.PIR
O.CIR O.PIR
-------------------------------------------------------------------------------
1/1/9 be 8698 0 0 40000
0 Max
1/1/9 l2 8698 0 0 40000
0 Max
1/1/9 af 8698 0 0 40000
0 Max
1/1/9 l1 8698 0 0 40000
0 Max
1/1/9 h2 8698 0 0 40000
0 Max
1/1/9 ef 8698 0 0 40000
0 Max
1/1/9 h1 8698 0 0 40000
0 Max
1/1/9 nc 8698 0 0 40000
0 Max
===============================================================================
* indicates that the corresponding row element may have been truncated.
*A:SASD>config>port#
Label |
Description |
|---|---|
Type |
Specifies the pool type. |
ID |
Specifies the card/mda or card/MDA/port designation. |
Application/Type |
Specifies the nature of usage the pool would be used for. The pools could be used for access or access uplink at egress. |
Pool Name |
Specifies the name of the pool being used. |
Resv CBS |
Specifies the percentage of pool size reserved for CBS. |
Utilization |
Specifies the type of the slope policy. |
State |
The administrative status of the port. |
Start-Threshold |
Specifies the percentage of the buffer used after which the drop probability starts to rise above 0. |
Actual ResvCBS |
Specifies the actual percentage of pool size reserved for CBS. |
Admin ResvCBS |
Specifies the percentage of pool size reserved for CBS. |
Pool Total |
Displays the total pool size. |
Pool Shared |
Displays the amount of the pool which is shared. |
Pool Resv |
Specifies the percentage of reserved pool size. |
Pool Total In Use |
Displays the total amount of the pool which is in use. |
Pool Shared In Use |
Displays the amount of the shared pools that is in use. |
For 7210 SAS-D and 7210 SAS-Dxp |
|
Max-Avg |
Specifies the percentage of the buffer used after which the drop probability is 100%.This implies that all packets beyond this point will be dropped. |
Time Avg Factor |
Specifies the time average factor the weighting between the previous shared buffer average utilization result and the new shared buffer utilization in determining the new shared buffer average utilization. |
Port show commands
port
Syntax
port port-id [count] [detail]
port port-id description
port port-id associations
port port-id ethernet [efm-oam | detail]
port port-id optical
port port-id dot1x [detail]
port port-id vport [vport-name] associations
port [A1] [detail] [statistics] [description]
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document.
Description
This command displays port information.
If no command line options are specified, the command port displays summary information for all ports on provisioned MDAs.
The out-of-band Ethernet port is not supported on 7210 SAS-D and 7210 SAS-Dxp platforms.
Parameters
- port-id
Specifies the physical port ID in the form slot/mda/port.
- associations
Displays a list of current router interfaces to which the port is associated.
- description
Displays port description strings.
- dot1x
Displays information.about 802.1x status and statistics.
- ethernet
Displays Ethernet port information.
efm-oam — Displays EFM OAM information.
detail — Displays detailed information about the Ethernet port.
- optical
Displays optical port DDM information retrieved from the cache, which is updated periodically only for ports that are operationally up or operationally down because of loss of Rx signal.
Output
The following outputs are examples of port information, and the associated tables describe the output fields.
Sample output for 7210 SAS-D, Output fields: show general port
Sample output for 7210 SAS-K 2F1C2T and 7210 SAS-K 2F6C4T, Output fields: show general port
Sample output for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, Output fields: show general port
Sample output Ethernet , Output fields: show specific port and Output fields: show port detail
Sample output for 7210 SAS-D, Output fields: show specific port and Output fields: show port detail
Sample output for 7210 SAS-D Ethernet, Output fields: show specific port and Output fields: show port detail
Sample output for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, Output fields: show specific port and Output fields: show port detail
Sample output port associations, Output fields: port associations
Sample output for dot1x detail, Sample output - optical , Output fields: optical
*A:ALU-211# show port 1/1/2
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100 Ethernet TX
Interface : 1/1/2 Oper Speed : 100 mbps
Link-level : Ethernet Config Speed : 100 mbps
Admin State : up Oper Duplex : full
Oper State : up - Active in LAG 10 Config Duplex : full
Physical Link : Yes MTU : 1514
Single Fiber Mode : No : Internal
IfIndex : 35717120 Hold time up : 0 seconds
Last State Change : 12/16/2008 19:31:40 Hold time down : 0 seconds
Last Cleared Time : 12/16/2008 19:31:48
IP MTU : 1000
===============================================================================
*A:ALU-211#
*A:ALU-211# show port 1/1/2
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100 Ethernet TX
Interface : 1/1/2 Oper Speed : 100 mbps
Link-level : Ethernet Config Speed : 100 mbps
Admin State : up Oper Duplex : full
Oper State : down - Standby in LAG 10 Config Duplex : full
Physical Link : Yes MTU : 1514
Single Fiber Mode : No : None
IfIndex : 35717120 Hold time up : 0 seconds
Last State Change : 12/16/2008 18:28:52 Hold time down : 0 seconds
Last Cleared Time : 12/16/2008 18:28:51
IP MTU : 1000
===============================================================================
*A:ALU-211#
*A:SAH01-051>show# port 1/1/3
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet Combo
Interface : 1/1/3 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : N/A
Oper State : down Config Duplex : full
Oper Grp : disabled Monitor Oper Grp : disabled
Physical Link : No MTU : 1514
Config Conn Type : Auto-SFP Oper Conn Type : N/A
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35749888 Hold time up : 0 seconds
Last State Change : 01/16/2014 03:19:32 Hold time down : 0 seconds
Last Cleared Time : 01/16/2014 03:12:24
Phys State Chng Cnt: 0
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Auto-negotiate : limited MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled DEI Classificati*: Disabled
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
Down On Int. Error : Disabled
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
Configured Address : 00:03:fa:27:15:52
Hardware Address : 00:03:fa:27:15:52
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show# ^C
*A:SAH01-051>show# port 1/1/3 de
detail description
*A:SAH01-051>show# port 1/1/3 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet Combo
Interface : 1/1/3 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : N/A
Oper State : down Config Duplex : full
Oper Grp : disabled Monitor Oper Grp : disabled
Physical Link : No MTU : 1514
Config Conn Type : Auto-SFP Oper Conn Type : N/A
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35749888 Hold time up : 0 seconds
Last State Change : 01/16/2014 03:19:32 Hold time down : 0 seconds
Last Cleared Time : 01/16/2014 03:12:24
Phys State Chng Cnt: 0
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Auto-negotiate : limited MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled DEI Classificati*: Disabled
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
Down On Int. Error : Disabled
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
Configured Address : 00:03:fa:27:15:52
Hardware Address : 00:03:fa:27:15:52
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 0
Packets : 0
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 0
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SAH01-051>show#
*A:SAH01-051>show# port 1/1/3
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet Combo
Interface : 1/1/3 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : N/A
Oper State : down Config Duplex : full
Oper Grp : disabled Monitor Oper Grp : disabled
Physical Link : No MTU : 1514
Config Conn Type : Auto-SFP Oper Conn Type : N/A
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35749888 Hold time up : 0 seconds
Last State Change : 01/16/2014 03:19:32 Hold time down : 0 seconds
Last Cleared Time : 01/16/2014 03:12:24
Phys State Chng Cnt: 0
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Auto-negotiate : limited MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled DEI Classificati*: Disabled
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
Down On Int. Error : Disabled
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
Configured Address : 00:03:fa:27:15:52
Hardware Address : 00:03:fa:27:15:52
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show#
*A:SAH01-051>show# ^C
*A:SAH01-051>show# port 1/1/3 de
detail description
*A:SAH01-051>show# port 1/1/3 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet Combo
Interface : 1/1/3 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : N/A
Oper State : down Config Duplex : full
Oper Grp : disabled Monitor Oper Grp : disabled
Physical Link : No MTU : 1514
Config Conn Type : Auto-SFP Oper Conn Type : N/A
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35749888 Hold time up : 0 seconds
Last State Change : 01/16/2014 03:19:32 Hold time down : 0 seconds
Last Cleared Time : 01/16/2014 03:12:24
Phys State Chng Cnt: 0
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Auto-negotiate : limited MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled DEI Classificati*: Disabled
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
Down On Int. Error : Disabled
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
Configured Address : 00:03:fa:27:15:52
Hardware Address : 00:03:fa:27:15:52
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 0
Packets : 0
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 0
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SAH01-051>show#
*A:7210SAS>show# port 1/1/2 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/2 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1518
Single Fiber Mode : No LoopBack Mode : Internal
IfIndex : 35717120 Hold time up : 0 seconds
Last State Change : 01/01/1970 00:18:10 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Configured Mode : access Encap Type : 802.1q
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Ing. Pool Policy : n/a
Egr. Pool Policy : n/a
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Egr. Sched. Pol : default Access Egr. Qos *: 1
Acc Egr Marking : Port-Based Acc Egr Policy ID: 1
Auto-negotiate : true MDI/MDX : MDI
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled
Uplink : No
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Code-Type : SDH Tx Quality Level : N/A
Tx DUS/DNU : Disabled
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:12:ab:34:cd:59
Hardware Address : 00:12:ab:34:cd:59
Cfg Alarm :
Alarm Status :
Transceiver Data
Transceiver Type : SFP
Model Number : 3HE00027AAAA02 ALA IPUIAELDAB
TX Laser Wavelength: 850 nm Diag Capable : yes
Connector Code : LC Vendor OUI : 00:90:65
Manufacture date : 2010/06/14 Media : Ethernet
Serial Number : PHR06BD
Part Number : FTRJ8519P2BNL-A6
Optical Compliance : GIGE-SX
Link Length support: 550m for 50u MMF; 300m for 62.5u MMF
===============================================================================
Transceiver Digital Diagnostic Monitoring (DDM), Internally Calibrated
===============================================================================
Value High Alarm High Warn Low Warn Low Alarm
-------------------------------------------------------------------------------
Temperature (C) +26.8 +95.0 +90.0 -20.0 -25.0
Supply Voltage (V) 3.27 3.90 3.70 2.90 2.70
Tx Bias Current (mA) 6.9 17.0 14.0 2.0 1.0
Tx Output Power (dBm) -4.39 -2.00 -2.00 -11.02 -11.74
Rx Optical Power (avg dBm) -7.24 1.00 -1.00 -18.01 -20.00
===============================================================================
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 0
Packets : 0
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 0
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
===============================================================================
Queue Statistics
===============================================================================
-------------------------------------------------------------------------------
Packets Octets
-------------------------------------------------------------------------------
Egress Queue 1 (be)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 2 (l2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 3 (af)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 4 (l1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 5 (h2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 6 (ef)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 7 (h1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 8 (nc)
Fwd Stats : 0 0
Drop Stats : 0 0
===============================================================================
*A:7210SAS>show#
Entering port ranges:
*A:7210SAS# show port
==============================================================================
Ports on Slot 1
==============================================================================
Port Admin Link Port Cfg Oper LAG/ Port Port Port SFP/XFP/
Id State State MTU MTU Bndl Mode Encp Type MDIMDX
------------------------------------------------------------------------------
1/1/1 Down No Down 1514 1514 - accs null xcme
1/1/2 Up Yes Up 1518 1518 - accs dotq xcme MDI GIGE-SX
1/1/3 Up No Down 1518 1518 - accs dotq xcme
1/1/4 Up No Down 1514 1514 - accs null xcme
1/1/5 Up Yes Up 1518 1518 - accs dotq xcme MDI GIGE-T
1/1/6 Down No Down 1514 1514 - accs null xcme
1/1/7 Down No Down 1514 1514 - accs null xcme
1/1/8 Down No Down 1514 1514 - accs null xcme
1/1/9 Up Yes Up 1522 1522 - l2up qinq xcme MDX
1/1/10 Up Yes Up 1522 1522 - l2up qinq xcme MDI
==============================================================================
*A:7210SAS#
Label |
Description |
|---|---|
Port ID |
Displays the port ID configured or displayed in the slot/mda/port format |
Admin State |
Up — The administrative state is up Down — The administrative state is down |
Link |
Yes — A physical link is present No — A physical link is not present |
Port State |
Up — The port is physically present and has a physical link present Down — The port is physically present but does not have a link Ghost — The port is not physically present None — The port is in its initial creation state or about to be deleted Link Up — The port is physically present and has a physical link present Link Down — The port is physically present but does not have a link |
Cfg MTU |
Displays the configured MTU |
Oper MTU |
Displays the negotiated size of the largest packet which can be sent on the port specified in octets |
LAG ID |
Displays the LAG or multi-link trunk (MLT) that the port is assigned to |
Port Mode |
network — The port is configured for transport network use access — The port is configured for service access |
Port Encap |
Null — Ingress frames do not use tags or labels to delineate a service dot1q — Ingress frames carry 802.1Q tags where each tag signifies a different service |
Port Type |
Displays the type of port or optics installed |
SFP/MDI MDX |
GIG3 — Indicates the GigE SFP type FASTE — Indicates the Fast Ethernet SFP type MDI — Indicates that the Ethernet interface is of type MDI (Media Dependent Interface) MDX — Indicates that the Ethernet interface is of type MDX (Media Dependent Interface with crossovers) |
IP MTU |
Displays the configured IP MTU value |
*A:SN12345678# show port 1/1/15
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet TX
Interface : 1/1/15 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1522
IfIndex : 36143104 Hold time up : 0 seconds
Last State Change : 03/19/2001 21:21:07 Hold time down : 0 seconds
Last Cleared Time : N/A
IP MTU : 1000
Configured Mode : access Encap Type : QinQ
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
Net. Egr. Queue Pol: default Access Egr. Qos *: n/a
Egr. Sched. Pol : default Network Qos Pol : 1
Auto-negotiate : limited MDI/MDX : MDI
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Ingress Rate : Default
Uplink : Yes
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:87:98:76:65:0e
Hardware Address : 00:87:98:76:65:0e
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 2229540275006 0
Packets 2177285416 0
Errors 14 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 2177285416 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 13 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SN12345678#
*A:SN12345678# show port 1/1/15 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet TX
Interface : 1/1/15 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1522
IfIndex : 36143104 Hold time up : 0 seconds
Last State Change : 03/19/2001 21:21:07 Hold time down : 0 seconds
Last Cleared Time : N/A
Configured Mode : access Encap Type : QinQ
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
Net. Egr. Queue Pol: default Access Egr. Qos *: n/a
Egr. Sched. Pol : default Network Qos Pol : 1
Auto-negotiate : limited MDI/MDX : MDI
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Ingress Rate : Default
Uplink : Yes
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:87:98:76:65:0e
Hardware Address : 00:87:98:76:65:0e
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 2199575527230 0
Packets 2148022967 0
Errors 14 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 13
Undersize Pckts : 0 Fragments : 1
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 2199575527230
Packets : 2148022967
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 1
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 12
Packets of 1024 to 1518 Octets : 2148022966
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 2148272026 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 13 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
Meter Statistics
===============================================================================
-------------------------------------------------------------------------------
Packets Octets
-------------------------------------------------------------------------------
Ingress Meter 1 (Unicast)
For. InProf : 0 0
For. OutProf : 0 0
Ingress Meter 9 (Multipoint)
For. InProf : 0 0
For. OutProf : 0 0
===============================================================================
*A:SN12345678#
*A:SAS-D>config# show port 1/1/2
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/2 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : down Oper Duplex : N/A
Oper State : down Config Duplex : full
Physical Link : No MTU : 1514
Single Fiber Mode : No
IfIndex : 35717120 Hold time up : 0 seconds
Last State Change : 01/01/1970 00:00:08 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Ing. Pool Policy : n/a
Egr. Pool Policy : n/a
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Egr. Sched. Pol : default Access Egr. Qos *: 1
Auto-negotiate : true MDI/MDX : unknown
Port-clock : master
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
Load-balance-algo : default LACP Tunnel : Disabled
LACP Tunnel : Disabled
Uplink : No
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Code-Type : SDH Tx Quality Level : N/A
Tx DUS/DNU : Disabled
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:3f:11:ab:ca:14
Hardware Address : 00:3f:11:ab:ca:14
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:ALA-A# show port 1/1/1 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/1 Oper Speed : 0 mbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : N/A
Oper State : down Config Duplex : full
Reason Down : linkLossFwd
Physical Link : No MTU : 1514
IfIndex : 35684352 Hold time up : 0 seconds
Last State Change : 01/22/2010 23:54:49 Hold time down : 0 seconds
Last Cleared Time : 01/21/2010 17:40:16
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
Net. Egr. Queue Pol: default Access Egr. Qos *: 1
Egr. Sched. Pol : default Network Qos Pol : n/a
Auto-negotiate : false MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
Uplink : No
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 28:06:01:01:00:01
Hardware Address : 28:06:01:01:00:01
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
0 Pckts : 0 CRC/Align Errors :
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 0
Packets : 0
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 0
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
*A:ALA-A#
*A:SAS-D>config# show port 1/1/2 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/2 Oper Speed : N/A
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : down Oper Duplex : N/A
Oper State : down Config Duplex : full
Physical Link : No MTU : 1514
Single Fiber Mode : No
IfIndex : 35717120 Hold time up : 0 seconds
Last State Change : 01/01/1970 00:00:08 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Ing. Pool Policy : n/a
Egr. Pool Policy : n/a
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Egr. Sched. Pol : default Access Egr. Qos *: 1
Auto-negotiate : true MDI/MDX : unknown
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
Load-balance-algo : default LACP Tunnel : Disabled
LACP Tunnel : Disabled
Uplink : No
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Code-Type : SDH Tx Quality Level : N/A
Tx DUS/DNU : Disabled
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:3f:11:ab:ca:14
Hardware Address : 00:3f:11:ab:ca:14
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 0
Packets : 0
Packets of 64 Octets : 0
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 0
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 0 0
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
===============================================================================
Queue Statistics
===============================================================================
-------------------------------------------------------------------------------
Packets Octets
-------------------------------------------------------------------------------
Egress Queue 1 (be)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 2 (l2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 3 (af)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 4 (l1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 5 (h2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 6 (ef)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 7 (h1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 8 (nc)
Fwd Stats : 0 0
Drop Stats : 0 0
===============================================================================
*7210SAS-D># show port 1/1/3 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/3 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1514
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35749888 Hold time up : 0 seconds
Last State Change : 01/01/1970 00:15:29 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7 Acc Egr Sch Mode : Fc-Based
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Ing. Pool Policy : n/a
Egr. Pool Policy : n/a
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Egr. Sched. Pol : default Access Egr. Qos *: 1
Auto-negotiate : true MDI/MDX : MDI
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled
Uplink : No
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Enabled Rx Quality Level : 0x2(prc)
Code-Type : SDH Tx Quality Level : 0xf(dnu)
Tx DUS/DNU : Disabled
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:32:fb:04:1a:04
Hardware Address : 00:32:fb:04:1a:04
Cfg Alarm :
Alarm Status :
Transceiver Data
Transceiver Type : SFP
Model Number : 3HE00027AAAA02 ALA IPUIAELDAB
TX Laser Wavelength: 850 nm Diag Capable : yes
Connector Code : LC Vendor OUI : 00:90:65
Manufacture date : 2010/06/02 Media : Ethernet
Serial Number : PHP2JMJ
Part Number : FTRJ8519P2BNL-A6
Optical Compliance : GIGE-SX
Link Length support: 550m for 50u MMF; 300m for 62.5u MMF
===============================================================================
Transceiver Digital Diagnostic Monitoring (DDM), Internally Calibrated
===============================================================================
Value High Alarm High Warn Low Warn Low Alarm
-------------------------------------------------------------------------------
Temperature (C) +44.9 +95.0 +90.0 -20.0 -25.0
Supply Voltage (V) 3.30 3.90 3.70 2.90 2.70
Tx Bias Current (mA) 6.8 17.0 14.0 2.0 1.0
Tx Output Power (dBm) -4.71 -2.00 -2.00 -11.02 -11.74
Rx Optical Power (avg dBm) -5.18 1.00 -1.00 -18.01 -20.00
===============================================================================
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 30976 30720
Packets 308 304
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 0 Drop Events : 0
Multicast Pckts : 612 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 61696
Packets : 612
Packets of 64 Octets : 260
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 352
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 0
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 0 0
Multicast Packets 308 304
Broadcast Packets 0 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
===============================================================================
Queue Statistics
===============================================================================
-------------------------------------------------------------------------------
Packets Octets
-------------------------------------------------------------------------------
Egress Queue 1 (be)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 2 (l2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 3 (af)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 4 (l1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 5 (h2)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 6 (ef)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 7 (h1)
Fwd Stats : 0 0
Drop Stats : 0 0
Egress Queue 8 (nc)
Fwd Stats : 0 0
Drop Stats : 0 0
===============================================================================
*A:SAH01-051>show# port
===============================================================================
Ports on Slot 1
===============================================================================
Port Admin Link Port Cfg Oper LAG/ Port Port Port C/QS/S/XFP/
Id State State MTU MTU Bndl Mode Encp Type MDIMDX
-------------------------------------------------------------------------------
1/1/1 Up Yes Up 1514 1514 - accs null xcme MDX GIGE-T
1/1/2 Down No Down 1514 1514 - accs null xcme
1/1/3 Up No Down 1514 1514 - accs null xcme COMBO
1/1/4 Up Yes Up 1514 1514 - accs null xcme MDI
1/1/5 Up Yes Up 1514 1514 - accs null xcme MDI
===============================================================================
*A:SAH01-051>show# port 1/1/1 ethernet
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100/Gig Ethernet SFP
Interface : 1/1/1 Oper Speed : 1 Gbps
Link-level : Ethernet Config Speed : 1 Gbps
Admin State : up Oper Duplex : full
Oper State : up Config Duplex : full
Oper Grp : disabled Monitor Oper Grp : disabled
Physical Link : Yes MTU : 1514
Config Conn Type : SFP Oper Conn Type : SFP
Single Fiber Mode : No LoopBack Mode : None
IfIndex : 35684352 Hold time up : 0 seconds
Last State Change : 01/16/2014 03:26:46 Hold time down : 0 seconds
Last Cleared Time : N/A DDM Events : Enabled
Phys State Chng Cnt: 5
Configured Mode : access Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Net. Egr. Queue Pol: default Network Qos Pol : n/a
Auto-negotiate : true MDI/MDX : MDX
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
LACP Tunnel : Disabled DEI Classificati*: Disabled
Split Horizon Group: (Not Specified)
Down-when-looped : Disabled Keep-alive : 10
Loop Detected : False Retry : 120
Use Broadcast Addr : False
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Tx DUS/DNU : Disabled Tx Quality Level : N/A
SSM Code Type : sdh
Down On Int. Error : Disabled
CRC Mon SD Thresh : Disabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Disabled
Configured Address : 00:03:fa:27:15:50
Hardware Address : 00:03:fa:27:15:50
Transceiver Data
Transceiver Type : SFP
Model Number : 3HE00062AAAA01 ALA IPUIAEHDAA
TX Laser Wavelength: 0 nm Diag Capable : no
Connector Code : Unknown Vendor OUI : 90:00:00
Manufacture date : 2011/08/09 Media : Ethernet
Serial Number : PL71FG4
Part Number : FCMJ-8521-3-A5
Optical Compliance : GIGE-T
Link Length support: 100m for copper
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 1889792832 38756224
Packets 29528013 605566
Errors 0 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 1577678 605566
Multicast Packets 0 0
Broadcast Packets 27950335 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
*A:SAH01-051>show#
Label |
Description |
|---|---|
Description |
A text description of the port. |
Interface |
The port ID displayed in the slot/mda/port format. |
Speed |
The speed of the interface. |
Link-level |
Ethernet The port is configured as Ethernet. |
MTU |
The size of the largest packet which can be sent/received on the Ethernet physical interface, specified in octets. |
LoopBack Mode |
Indicates if the port is in use by loopback mac-swap application. If 'None' is displayed the port is not enabled for loopback testing. If 'Internal' is displayed, the port is in use by port loopback mac-swap application and no services can be configured on this port. This field is displayed only on the 7210 SAS-D sample output. |
Admin State |
Up The port is administratively up. |
Down The port is administratively down. |
|
Oper State |
Up The port is operationally up. |
Down The port is operationally down. |
|
Additionally, the lag-id of the LAG it belongs to in addition to the status of the LAG member (active or standby) is specified. |
|
Duplex |
Full The link is set to full duplex mode. |
Half The link is set to half duplex mode. |
|
Hold time up |
The link up dampening time in seconds. The port link dampening timer value which reduces the number of link transitions reported to upper layer protocols. |
Hold time down |
The link down dampening time in seconds. The down timer controls the dampening timer for link down transitions. |
Physical Link |
Yes A physical link is present. |
No A physical link is not present. |
|
IfIndex |
Displays the interface's index number which reflects its initialization sequence. |
Last State chg |
Displays the system time moment that the peer is up. |
Configured Mode |
network The port is configured for transport network use. |
access The port is configured for service access. |
|
Dot1Q Ethertype |
Indicates the Ethertype expected when the port's encapsulation type is Dot1Q. |
QinQ Ethertype |
Indicates the Ethertype expected when the port's encapsulation type is QinQ. |
Net. Egr. Queue Pol |
Specifies the network egress queue policy or that the default policy is used. |
Access Egr. Qos |
Specifies the access egress policy or that the default policy 1 is in use |
Egr. Sched. Pol |
Specifies the port scheduler policy or that the default policy default is in use |
Encap Type |
Null Ingress frames will not use any tags or labels to delineate a service. |
dot1q Ingress frames carry 802.1Q tags where each tag signifies a different service. |
|
Active Alarms |
The number of alarms outstanding on this port. |
Auto-negotiate |
True The link attempts to automatically negotiate the link speed and duplex parameters. |
False The duplex and speed values are used for the link. |
|
Port-clock |
Displays the mode of the port-clock. The port-clock can be set either as master, slave, or it can be automatic. |
Alarm State |
The current alarm state of the port. |
Collect Stats |
Enabled The collection of accounting and statistical data for the network Ethernet port is enabled. When applying accounting policies the data by default will be collected in the appropriate records and written to the designated billing file. |
Disabled The collection of accounting and statistical data for the network Ethernet port is disabled. Statistics are still accumulated by the IOM cards, however, the CPU will not obtain the results and write them to the billing file. |
|
Configured Address |
The base chassis Ethernet MAC address. |
Hardware Address |
The interface's hardware or system assigned MAC address at its protocol sublayer. |
Transceiver Type |
Type of the transceiver. |
Model Number |
The model number of the transceiver. |
Transceiver Code |
The code for the transmission media. |
Laser Wavelength |
The light wavelength transmitted by the transceiver's laser. |
Connector Code |
The vendor organizationally unique identifier field (OUI) contains the IEEE company identifier for the vendor. |
Diag Capable |
Indicates if the transceiver is capable of doing diagnostics. |
Vendor OUI |
The vendor-specific identifier field (OUI) contains the IEEE company identifier for the vendor. |
Manufacture date |
The manufacturing date of the hardware component in the mmddyyyy ASCII format. |
Media |
The media supported for the SFP. |
Serial Number |
The vendor serial number of the hardware component. |
Part Number |
The vendor part number contains ASCII characters, defining the vendor part number or product name. |
Input/Output |
When the collection of accounting and statistical data is enabled, the octet, packet, and error statistics are displayed. |
Errors Input/Output |
For packet-oriented interfaces, the number of inbound packets that contained errors preventing them from being deliverable to a higher-layer protocol. For character-oriented or fixed-length interfaces, the number of inbound transmission units that contained errors preventing them from being deliverable to a higher-layer protocol. For packet-oriented interfaces, the number of outbound packets that could not be transmitted because of errors. For character-oriented or fixed-length interfaces, the number of outbound transmission units that could not be transmitted because of errors. |
Unicast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were not addressed to a multicast or broadcast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were not addressed to a multicast or broadcast address at this sublayer, including those that were discarded or not sent. |
Multicast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were addressed to a multicast address at this sublayer. For a MAC layer protocol, this includes both group and functional addresses. The total number of packets that higher-level protocols requested be transmitted, and which were addressed to a multicast address at this sublayer, including those that were discarded or not sent. For a MAC layer protocol, this includes both Group and Functional addresses. |
Broadcast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were addressed to a broadcast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were addressed to a multicast address at this sublayer, including those that were discarded or not sent. For a MAC layer protocol, this includes both Group and Functional addresses. |
Discards Input/Output |
The number of inbound packets chosen to be discarded to possibly free up buffer space. |
Unknown Proto Discards Input/Output |
For packet-oriented interfaces, the number of packets received through the interface which were discarded because of an unknown or unsupported protocol. For character-oriented or fixed-length interfaces that support protocol multiplexing the number of transmission units received via the interface which were discarded because of an unknown or unsupported protocol. For any interface that does not support protocol multiplexing, this counter will always be 0. |
Errors |
This field displays the number of cells discarded because of uncorrectable HEC errors. Errors do not show up in the raw cell counts. |
Sync. Status Msg |
Whether synchronization status messages are enabled or disabled. |
Tx DUS/DNU |
Whether the QL value is forcibly set to QL-DUS/QL-DNU. |
Rx Quality Level |
Indicates which QL value has been received from the interface. |
Tx Quality Level |
Indicates which QL value is being transmitted out of the interface. |
SSM Code Type |
Indicates the SSM code type in use on the port. |
Frame Based Acc |
Indicates if frame-based-accounting is enabled or disabled on the port |
Label |
Description |
|---|---|
Description |
Provides a text description of the port |
Interface |
Displays the port ID in the slot/mda/port format |
Speed |
Displays the speed of the interface |
Link-level |
Ethernet — The port is configured as Ethernet |
MTU |
Displays the size of the largest packet which can be sent or received on the Ethernet physical interface, specified in octets |
Admin State |
Up — The port is administratively up Down — The port is administratively down |
Oper State |
Up — The port is operationally up Down — The port is operationally down |
Duplex |
Full — The link is set to full duplex mode Half — The link is set to half duplex mode |
Hold time up |
Displays the link up dampening time in seconds. The port link dampening timer value reduces the number of link transitions reported to upper layer protocols. |
Hold time down |
Displays the link down dampening time in seconds. The down timer controls the dampening timer for link down transitions. |
IfIndex |
Displays the interface index number, which reflects its initialization sequence |
Phy Link |
Yes — A physical link is present No — A physical link is not present |
Configured Mode |
network — The port is configured for transport network use access — The port is configured for service access |
Network Qos Pol |
Displays the QoS policy ID applied to the port |
Access Egr. Qos |
Specifies the access egress policy or that the default policy 1 is in use |
Egr. Sched. Pol |
Specifies the port scheduler policy or that the default policy default is in use |
Encap Type |
Null — Ingress frames do not use any tags or labels to delineate a service dot1q — Ingress frames carry 802.1Q tags where each tag signifies a different service |
Active Alarms |
Displays the number of alarms outstanding on this port |
Auto-negotiate |
True — The link attempts to automatically negotiate the link speed and duplex parameters False — The duplex and speed values are used for the link |
Alarm State |
Displays the current alarm state of the port |
Collect Stats |
Enabled — The collection of accounting and statistical data for the network Ethernet port is enabled. When applying accounting policies the data by default will be collected in the appropriate records and written to the designated billing file. Disabled — Collection is disabled. Statistics are still accumulated by the IOM cards; however, the CPU does not obtain the results and write them to the billing file. |
Down-When-Looped |
Displays whether the feature is enabled or disabled |
Down On Int. Error |
Indicates whether down-on-internal-error is enabled |
CRC Mon SD Thresh |
Indicates whether signal-degrade threshold is configured |
CRC Mon SF Thresh |
Indicates whether signal-fail threshold is configured |
CRC Mon Window |
Displays the value of window size used for CRC error monitoring when the signal-degrade or signal-fail thresholds are configured. |
Egress Rate |
Displays the maximum amount of egress bandwidth (in kilobits per second) that this Ethernet interface can generate |
Configured Address |
Displays the base chassis Ethernet MAC address. |
Hardware Address |
Displays the interface hardware or system assigned MAC address at its protocol sublayer |
Errors Input/Output |
For packet-oriented interfaces, the number of inbound packets that contained errors preventing them from being deliverable to a higher-layer protocol. For character-oriented or fixed-length interfaces, the number of inbound transmission units that contained errors preventing them from being deliverable to a higher-layer protocol. For packet-oriented interfaces, the number of outbound packets that could not be transmitted because of errors. For character-oriented or fixed-length interfaces, the number of outbound transmission units that could not be transmitted because of errors. |
Unicast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were not addressed to a multicast or broadcast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were not addressed to a multicast or broadcast address at this sublayer, including those that were discarded or not sent. |
Multicast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were addressed to a multicast address at this sublayer. For a MAC layer protocol, this includes both Group and Functional addresses. The total number of packets that higher-level protocols requested be transmitted, and which were addressed to a multicast address at this sublayer, including those that were discarded or not sent. For a MAC layer protocol, this includes both Group and Functional addresses. |
Broadcast Packets Input/Output |
The number of packets, delivered by this sublayer to a higher (sub)layer, which were addressed to a broadcast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were addressed to a multicast address at this sublayer, including those that were discarded or not sent. For a MAC layer protocol, this includes both Group and Functional addresses. |
Discards Input/Output |
Displays the number of inbound packets chosen to be discarded to possibly free up buffer space |
Unknown Proto Discards Input/Output |
For packet-oriented interfaces, the number of packets received through the interface which were discarded because of an unknown or unsupported protocol. For character-oriented or fixed-length interfaces that support protocol multiplexing the number of transmission units received via the interface which were discarded because of an unknown or unsupported protocol. For any interface that does not support protocol multiplexing, this counter will always be 0. |
LLF Admin State |
Displays the Link Loss Forwarding administrative state |
LLF Oper State |
Displays the Link Loss Forwarding operational state |
Rx S1 Byte |
Displays the received S1 byte and its decoded QL value |
Tx DUS/DNU |
Displays whether the QL value is forcibly set to QL-DUS/QL-DNU |
Qinq etype |
Displays the Ethertype used for qinq packet encapsulation |
Sync. Status Msg. |
Enabled — If SSM is enabled Disabled — If SSM is disabled |
Code-Type |
Displays the encoding type of SSM messages as SONET or SDH |
Rx Quality Level |
When SSM is enabled on this port, it displays the Clock Quality level for the clock received through that interface. The Clock Quality level is typically sent by the peer in the ESMC/SSM protocol. The quality level shown depends on the quality level mode used (SONET or SDH). |
Tx Quality Level |
When SSM is enabled on this port, it displays the System Clock Quality level that the system advertises to the peer using the ESMC/SSM protocol. The quality level shown depends on the quality level mode used (SONET or SDH). |
A:ALA-1# show port 1/1/6 associations
==============================================================================
Interface Table
==============================================================================
Router/ServiceId Name Encap Val
------------------------------------------------------------------------------
Router: Base if1000 1000
Router: Base if2000 2000
------------------------------------------------------------------------------
Interfaces
==============================================================================
A;ALA-1#
Label |
Description |
|---|---|
Svc ID |
Displays the service identifier |
Name |
Displays the name of the IP interface |
Encap Value |
Displays the dot1q or qinq encapsulation value on the port for this IP interface |
A:7210>show# port A/1 detail
===============================================================================
Ethernet Interface
===============================================================================
Description : 10/100 Ethernet TX
Interface : A/1 Oper Speed : 10 mbps
Link-level : Ethernet Config Speed : 100 mbps
Admin State : up Oper Duplex : half
Oper State : up Config Duplex : full
Physical Link : Yes MTU : 1514
Single Fiber Mode : No
IfIndex : 67141632 Hold time up : 0 seconds
Last State Change : 07/09/2010 16:30:04 Hold time down : 0 seconds
Last Cleared Time : N/A
Configured Mode : network Encap Type : null
Dot1Q Ethertype : 0x8100 QinQ Ethertype : 0x8100
PBB Ethertype : 0x88e7
Ing. Pool % Rate : 100 Egr. Pool % Rate : 100
Ing. Pool Policy : n/a
Egr. Pool Policy : n/a
Net. Egr. Queue Pol: Network Qos Pol : n/a
Egr. Sched. Pol : default Access Egr. Qos *: n/a
Egr. Sched. Pol : default
Auto-negotiate : true MDI/MDX : MDI
Accounting Policy : None Collect-stats : Disabled
Egress Rate : Default Max Burst : Default
Split Horizon Group: (Not Specified)
Down-when-looped : N/A Keep-alive : N/A
Loop Detected : N/A Retry : N/A
Use Broadcast Addr : N/A
Sync. Status Msg. : Disabled Rx Quality Level : N/A
Down On Int. Error : Disabled
CRC Mon SD Thresh : Enabled CRC Mon Window : 10 seconds
CRC Mon SF Thresh : Enabled
Configured Address : 00:aa:01:ab:02:02
Hardware Address : 00:aa:01:ab:02:02
Cfg Alarm :
Alarm Status :
===============================================================================
Traffic Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Octets 5950409 0
Packets 4274 0
Errors 0 0
===============================================================================
Ethernet Statistics
===============================================================================
Broadcast Pckts : 38 Drop Events : 0
Multicast Pckts : 0 CRC/Align Errors : 0
Undersize Pckts : 0 Fragments : 0
Oversize Pckts : 0 Jabbers : 0
Collisions : 0
Octets : 6102041
Packets : 4382
Packets of 64 Octets : 34
Packets of 65 to 127 Octets : 0
Packets of 128 to 255 Octets : 366
Packets of 256 to 511 Octets : 0
Packets of 512 to 1023 Octets : 0
Packets of 1024 to 1518 Octets : 3982
Packets of 1519 or more Octets : 0
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Port Statistics
===============================================================================
Input Output
-------------------------------------------------------------------------------
Unicast Packets 4416 0
Multicast Packets 0 0
Broadcast Packets 38 0
Discards 0 0
Unknown Proto Discards 0
===============================================================================
===============================================================================
Ethernet-like Medium Statistics
===============================================================================
Alignment Errors : 0 Sngl Collisions : 0
FCS Errors : 0 Mult Collisions : 0
SQE Test Errors : 0 Late Collisions : 0
CSE : 0 Excess Collisns : 0
Too long Frames : 0 Int MAC Tx Errs : 0
Symbol Errors : 0 Int MAC Rx Errs : 0
===============================================================================
Label |
Description |
|---|---|
Description |
Displays a text description of the port |
Interface |
Displays the port ID displayed in the slot/mda/port format |
Oper Speed |
Displays the operating speed of the interface |
Link-level |
Ethernet — the port is configured as Ethernet |
Config Speed |
Displays the configured speed of the interface |
Admin State |
up The port is administratively up. |
down The port is administratively down. |
|
Oper Duplex |
The operating duplex mode of the interface. |
Oper State |
up The port is operationally up. |
down The port is operationally down. |
|
Config Duplex |
full The link is configured to full duplex mode. |
half The link is configured to half duplex mode. |
|
Physical Link |
Yes A physical link is present. |
No A physical link is not present. |
|
MTU |
The size of the largest packet that can be sent/received on the Ethernet physical interface, specified in octets. |
IfIndex |
The interface index number that reflects its initialization sequence. |
Hold time up |
The link-up dampening time in seconds. The port link dampening timer value that reduces the number of link transitions reported to upper layer protocols. |
Last State Change |
The last time that the operational status of the port changed state. |
Hold time down |
The link-down dampening time in seconds. The down timer controls the dampening timer for link down transitions. |
Configured Mode |
network The port is configured for transport. |
network use access The port is configured for service access. |
|
Encap Type |
null Ingress frames will not use any tags or labels to delineate a service. |
dot1q Ingress frames carry 802.1Q tags where each tag signifies a different service. |
|
Dot1Q Ethertype |
The protocol carried in an Ethernet frame. |
Net.Egr. Queue Pol. |
The number of the associated network egress queue QoS policy, or default if the default policy is used. |
ACFC |
Indicates whether Address and Control Field PPP Header Compression is enabled. |
PFC |
Indicates whether Protocol Field PPP Header Compression is enabled. |
Auto-negotiate |
true The link attempts to automatically negotiate the link speed and duplex parameters. |
false The duplex and speed values are used for the link. |
|
Egress Rate |
The maximum amount of egress bandwidth (in kilobits per second) that this Ethernet interface can generate. |
Loopback |
The type of loopback configured on the port, either line, internal, or none. |
Loopback Time Left |
The number of seconds left in a timed loopback If there is no loopback configured or the configured loopback is latched, the value is unspecified. |
Configured Address |
The base chassis Ethernet MAC address. |
Hardware Address |
The interface hardware or system assigned MAC address at its protocol sublayer. |
Traffic Statistics |
Octets input/output — Specifies the total number of octets received and transmitted on the port Packets input/output, or the number of packets, delivered by this sublayer to a higher (sub)layer, which were not addressed to a multicast or broadcast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were not addressed to a multicast or broadcast address at this sublayer, including those that were discarded or not sent. Errors input/output — For packet-oriented interfaces, this field specifies the number of inbound packets that contained errors preventing them from being deliverable to a higher-layer protocol. For character-oriented or fixed-length interfaces, the number of inbound transmission units that contained errors preventing them from being deliverable to a higher-layer protocol. For packet-oriented interfaces, this field specifies the number of outbound packets that could not be transmitted because of errors. For character-oriented or fixed length interfaces, the number of outbound transmission units that could not be transmitted because of errors. |
Ethernet Statistics |
Broadcast Pckts — the number of packets, delivered by this sublayer to a higher (sub)layer, which were not addressed to a unicast or multicast address at this sublayer. The total number of packets that higher-level protocols requested be transmitted, and which were not addressed to a unicast or multicast address at this sublayer, including those that were discarded or not sent. |
A:7210SAS>show# port 1/1/2 dot1x detail
===============================================================================
802.1x Port Status
===============================================================================
Port control : force-auth
Port status : authorized
Authenticator PAE state : force-auth
Backend state : idle
Reauth enabled : no Reauth period : N/A
Max auth requests : 2 Transmit period : 30
Supplicant timeout : 30 Server timeout : 30
Quiet period : 60
Radius-plcy : N/A
Dot1x-Tunnel : Disabled
===============================================================================
802.1x Session Statistics
===============================================================================
authentication method : remote-radius
last session id : PAC-02210000-C28294A4
last session time : 49213d07h
last session username : N/A
last session term cause : N/A
user tx octets : 0 user tx frames : 0
user rx octets : 2648353056 user rx frames : 247852776
===============================================================================
802.1x Authentication Statistics
===============================================================================
tx frames : 0 rx frames : 0
tx req/id frames : 0 rx resp/id frames : 0
tx request frames : 0 rx response frames : 0
rx start frames : 0 rx logoff frames : 0
rx unknown frame type : 0 rx bad eap length : 0
rx last version : 0 rx last source mac :
===============================================================================
802.1x Authentication Diagnostics
===============================================================================
Enters Connecting : 0
EapLogoffs While Connecting : 0
Logoffs While Connecting : 0
Success While Authenticating : 0
Timeouts While Authenticating : 0
Failures While Authenticating : 0
Reauths While Authenticating : 0
EapStarts While Authenticating : 0
EapLogoffs While Authenticating : 0
Reauths While Authenticated : 0
EapStarts While Authenticated : 0
EapLogoffs While Authenticated : 0
Backend Responses : 0
Backend Access Challenges : 0
Backend Requests To Supplicant : 0
Backend Access Challenges : 0
Backend Non Nak Responses : 0
Backend Auth Successes : 0
Backend Auth Failures : 0
The following output is an example of optical information, and Output fields: optical describes the output fields.
A:SAS# show port 1/1/1 optical force
===============================================================================
Optical Interface
===============================================================================
Transceiver Data
Transceiver Status : operational
Transceiver Type : SFP
Model Number : 3HE04824AAAA01 ALA IPU3ANLEAA
TX Laser Wavelength: 850 nm Diag Capable : yes
Connector Code : LC Vendor OUI : 00:01:9c
Manufacture date : 2016/04/10 Media : Ethernet
Serial Number : CG15KT0TF
Part Number : PLRXPLSCS43AL1
Optical Compliance : 10GBASE-SR
Link Length support: 80m for OM2 50u MMF; 30m for OM1 62.5u MMF; 300m for OM3*
===============================================================================
Transceiver Digital Diagnostic Monitoring (DDM), Internally Calibrated
===============================================================================
Value High Alarm High Warn Low Warn Low Alarm
-------------------------------------------------------------------------------
Temperature (C) +41.1 +80.0 +75.0 -5.0 -10.0
Supply Voltage (V) 3.30 3.70 3.63 2.97 2.85
Tx Bias Current (mA) 5.0 10.0 8.5 3.0 2.6
Tx Output Power (dBm) -2.15 -1.00 -1.30 -7.50 -8.00
Rx Optical Power (avg dBm) -26.02 1.50 1.00 -12.00! -14.00!
===============================================================================
Label |
Description |
|---|---|
Transceiver Data |
|
Transceiver Status |
Displays the status of the transceiver |
Transceiver Type |
Displays the type of the transceiver |
Model Number |
Displays the model number of the transceiver |
TX Laser Wavelength |
Indicates the transceiver laser wavelength |
Connector Code |
Displays the vendor Organizationally Unique Identifier field (OUI) contains the IEEE company identifier for the vendor |
Manufacture date |
Displays the manufacturing date of the hardware component in the mmddyyyy ASCII format |
Serial Number |
Displays the vendor serial number of the hardware component |
Part Number |
The vendor part number contains ASCII characters, defining the vendor part number or product name |
Optical Compliance |
Specifies the optical compliance code of the transceiver |
Link Length support |
Specifies the link length support for the transceiver |
Transceiver Digital Diagnostic Monitoring (DDM), Internally Calibrated |
|
Temperature (C) |
Displays the temperature of the transceiver |
Supply Voltage (V) |
Displays the supply voltage of the transceiver |
Tx Bias Current (mA) |
Displays the transmitted bias current of the transceiver |
Tx Output Power (dBm) |
Displays the transmitted output power of the transceiver |
Rx Optical Power (avg dBm) |
Displays the received optical power of the transceiver |
lldp
Syntax
lldp [nearest-bridge | nearest-non-tpmr | nearest-customer] [remote-info] [detail] [lldp-med]
Context
show>port>ethernet
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays Link Layer Discovery Protocol (LLDP) information.
Parameters
- nearest-bridge
Displays nearest bridge information.
- nearest-non-tpmr
Displays nearest Two-Port MAC Relay (TPMR) information.
- nearest-customer
Displays nearest customer information.
- remote-info
Displays remote information about the bridge MAC.
- detail
Displays more information.
- lldp-med
Displays LLDP-MED information. This keyword is supported only on the 7210 SAS-Dxp.
Output
The following output is an example of LLDP information, and Output fields: port Ethernet LLDP describes the output fields.
Sample output*A:hw_sasm_duta>show# port 1/1/1 ethernet lldp
==============================================================================
Link Layer Discovery Protocol (LLDP) Port Information
==============================================================================
Port 1/1/1 Bridge nearest-bridge
-------------------------------------------------------------------------------
Admin State : disabled Notifications : Disabled
Tunnel Nearest Bridge : Disabled
Transmit TLVs : None
PortID TLV Subtype : tx-local
Management Address Transmit Configuration:
Index 1 (system) : Disabled Address : 0.0.0.0
Index 2 (IPv6 system) : Disabled Address : ::
Port 1/1/1 Bridge nearest-non-tpmr
-------------------------------------------------------------------------------
Admin State : disabled Notifications : Disabled
Transmit TLVs : None
PortID TLV Subtype : tx-local
Management Address Transmit Configuration:
Index 1 (system) : Disabled Address : 0.0.0.0
Index 2 (IPv6 system) : Disabled Address : ::
Port 1/1/1 Bridge nearest-customer
-------------------------------------------------------------------------------
Admin State : disabled Notifications : Disabled
Transmit TLVs : None
PortID TLV Subtype : tx-local
Management Address Transmit Configuration:
Index 1 (system) : Disabled Address : 0.0.0.0
Index 2 (IPv6 system) : Disabled Address : ::
==============================================================================
*A:hw_sasm_duta>show#
*A:hw_sasm_duta>show# port 1/1/1 ethernet lldp nearest-bridge
==============================================================================
Link Layer Discovery Protocol (LLDP) Port Information
==============================================================================
Port 1/1/1 Bridge nearest-bridge
-------------------------------------------------------------------------------
Admin State : disabled Notifications : Disabled
Tunnel Nearest Bridge : Disabled
Transmit TLVs : None
PortID TLV Subtype : tx-local
Management Address Transmit Configuration:
Index 1 (system) : Disabled Address : 0.0.0.0
Index 2 (IPv6 system) : Disabled Address : ::
==============================================================================
*A:hw_sasm_duta>show#
*A:7210-SAS# show port 1/1/3 ethernet lldp remote-info detail
===============================================================================
Link Layer Discovery Protocol (LLDP) Port Information
===============================================================================
Port 1/1/3 Bridge nearest-bridge Remote Peer Information
-------------------------------------------------------------------------------
No remote peers found
Port 1/1/3 Bridge nearest-non-tpmr Remote Peer Information
-------------------------------------------------------------------------------
Remote Peer Index 142 at timestamp 06/10/2010 00:23:22:
Supported Caps : bridge router
Enabled Caps : bridge router
Chassis Id Subtype : 4 (macAddress)
Chassis Id : 0a:a5:ff:00:00:00
PortId Subtype : 7 (local)
Port Id : 35749888
Port Description : 10/100/Gig Ethernet SFP
System Name : Dut-B
System Description : TiMOS-B-0.0.I927 both/i386 NOKIA SAS 7210
Copyright (c) 2017 Nokia.
All rights reserved. All use subject to applicable
license agreements.
Built on Wed Dec 1 22:23:12 IST 2010 by builder in
/builder/0.0/panos/main
Remote Peer Index 142 management addresses at time 06/10/2010 00:23:22:
No remote management addresses found
Port 1/1/3 Bridge nearest-customer Remote Peer Information
-------------------------------------------------------------------------------
Remote Peer Index 143 at timestamp 06/10/2010 00:23:22:
Supported Caps : bridge router
Enabled Caps : bridge router
Chassis Id Subtype : 4 (macAddress)
Chassis Id : 0a:a7:ff:00:00:00
PortId Subtype : 7 (local)
Port Id : 35782656
Port Description : 10/100 Ethernet TX
System Name : Dut-G
System Description : TiMOS-B-8.0.R5 both/i386 NOKIA SR 7750 Copyright (c)
2017 Nokia.
All rights reserved. All use subject to applicable
license agreements.
Built on Tue Sep 28 18:24:07 PDT 2010 by builder in
/rel8.0/b1/R5/panos/main
Remote Peer Index 143 management addresses at time 06/10/2010 00:23:22:
*A:Dut-A# /show port 1/1/11 ethernet lldp lldp-med remote-info detail
==============================================================================
Link Layer Discovery Protocol (LLDP) Port Information
==============================================================================
Port 1/1/11 Bridge nearest-bridge Remote Peer Information
-------------------------------------------------------------------------------
Remote Peer Index 2 at timestamp 08/06/2020 11:08:52:
Supported Caps : bridge telephone
Enabled Caps : bridge telephone
Chassis Id Subtype : 5 (networkAddress)
Chassis Id : 01:C0:A8:02:02
PortId Subtype : 3 (macAddress)
Port Id : C0:74:AD:09:C1:4C
Port Description : eth0
System Name : GXP1625_c0:74:ad:09:c1:4c
System Description : GXP1625 1.0.4.138
Remote Peer Index 2 management addresses at time 08/06/2020 11:08:52:
No remote management addresses found
Enabled Caps : capabilities network-policy location extended-pd
inventory
LLDP Med Rem Device Type: Endpoint Class III
LLDP Med Rem App Type*: 1
LLDP Med Rem vlan-tag*: True LLDP Med Rem Vlan Tag*: 444
LLDP Med Rem Dot1p 1 : 4 LLDP Med Rem Ip Dscp 1: 44
Label |
Description |
|---|---|
Admin State |
Displays the LLDP transmission/reception frame handling |
Notifications |
Displays whether LLDP notifications are enabled |
Tunnel Nearest Bridge |
n/a |
Transmit TLVs |
Displays the optional TLVs that are transmitted by this port |
PortID TLV Subtype |
Displays the setting for the port ID subtype: tx-if-alias, tx-fi-name, or tx-local |
Management Address Transmit Configuration |
|
Index 1 (system) Index 2 (IPv6 system) |
Displays details of the management address configuration. The 7705 SAR can only be configured to send or not send the system address Enabled — the management address TLV is included in LLDPDUs sent by the port Disabled — the management address TLV is not included in LLDPDUs sent by the port |
Address |
Displays the address transmitted by the port when tx-mgmt-address command is enabled |
Supported Caps |
Displays the system capabilities supported by the remote peer |
Enabled Caps |
Displays the system capabilities enabled on the remote peer |
Chassis ID Subtype |
Displays an integer value and text definition that indicates the basis for the chassis ID entity listed in the chassis ID field |
Chassis ID |
Displays the chassis identifier of the chassis containing the Ethernet port that sent the LLDPDU |
PortId Subtype |
Displays an integer value and text definition that indicates the basis for the port ID entity listed in the port ID field |
Port ID |
Displays the port identifier of the Ethernet port that sent the LLDPDU |
Port Description |
Displays a description of the port that sent the LLDPDU and indicates that the description is the ifDescr object text string from RFC 2863 - IF MIB |
System Name |
Displays the name of the system that sent the LLDPDU |
System Description |
Displays the description of the system that sent the LLDPDU |
LLDP Med Rem Device Type |
Displays the LLDP-MED remote device type (endpoint Class III) |
LLDP Med Rem App Type |
Displays the application-type value in the Network Policy TLV of the LLDP-MED message received from the remote device |
LLDP Med vlan-tag-present |
Displays the value of the vlan-tag-present flag in the Network Policy TLV of the LLDP-MED message received from the remote device True — The VLAN tag is present False — The VLAN tag is not present |
LLDP Med Rem Vlan Tag |
Displays the VLAN value in the LLDP-MED message received from the remote device |
LLDP Med Rem Dot1p |
Displays the dot1p value in the Network Policy TLV of the LLDP-MED message received from the remote device |
LLDP Med Rem IP DSCP |
Displays the IP DSCP value in the Network Policy TLV of the LLDP-MED message received from the remote device |
internal-loopback-ports
Syntax
internal-loopback-ports [detail]
Context
show>system
Platforms
7210 SAS-D and 7210 SAS-Dxp
Description
This command displays information about internal loopback ports .
Parameters
- detail
Displays application information
Output
The following output is an example of internal loopback port information, and Output fields: show MAC swap application describes the output fields.
Sample output*A:7210SAS>config>port# show system internal-loopback-ports detail
===============================================================================
Internal Loopback Port Status
===============================================================================
Port Loopback Application Service
Id Type Enabled
-------------------------------------------------------------------------------
1/1/2 Physical Mac-Swap Yes
1/1/11 Virtual Mac-Swap No
========================================
Mac-swap Application Status
========================================
Enabled : Yes
Test Service Id : 1
Test Sap Id : 1/1/2:40
Loopback Src Addr : 00:00:01:00:02:00
Loopback Dst Addr : 00:00:01:00:03:00
========================================
===============================================================================
*A:7210SAS>config>port#
Label |
Description |
|---|---|
Port ID |
Displays the port ID. |
LoopBack Type |
The Loopback type indicates whether the port is in Physical Front panel port or Internal Virtual port. |
Application |
Application mentions the application in use of the port. |
Service enabled |
The Service enabled displays, if services can be configured over this port. |
Enabled |
Displays the current status. |
Test Service ID |
The service ID that is used in the configuration of Mac-swap test. |
Test Sap ID |
The SAP ID that is used to configure the loopback SAP for the Mac-swap application. |
Loopback Src Addr |
The source MAC address that is used in the configuration of port loopback mac-swap test. |
Loopback Dst Addr |
The destination MAC address that is used in the configuration of port loopback mac-swap test. |
lldp
Syntax
lldp
lldp neighbor
Context
show>system
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays local Link Layer Discovery Protocol (LLDP) information at the system level. This includes an option keyword to display summary information for all known peers.
Parameters
- neighbor
Display all peer summary information
Output
The following output is an example of system LLDP information.
Sample output*A:hw_sas_duta>show>system# lldp
===============================================================================
LLDP Configuration
===============================================================================
Transmit Interval : 30
Hold Multiplier : 4
Reinit Delay : 2
Notification Interval : 5
Tx Credit Max : 5
Message Fast Tx : 1
Message Fast Tx Init : 4
Admin Enabled : True
-------------------------------------------------------------------------------
LLDP System Information
-------------------------------------------------------------------------------
Chassis Id Subtype : 4
Chassis Id : 00:12:cf:b4:71:b8
System Name : hw_sas_duta
System Description : TiMOS-B-9.0.B1-12 both/mpc Nokia 7210 Copyright
(c) 2000-2016 Nokia.
All rights reserved. All use subject to applicable
license agreements.
Built on Tue Oct 18 15:22:40 IST 2016 by builder in /
home/builder/9.0B1/panos/main
Capabilities Supported : bridge router
Capabilities Enabled : bridge router
-------------------------------------------------------------------------------
LLDP Destination Addresses
-------------------------------------------------------------------------------
Index 1 : 01:80:c2:00:00:0e
Index 2 : 01:80:c2:00:00:03
Index 3 : 01:80:c2:00:00:00
-------------------------------------------------------------------------------
LLDP Remote Statistics
-------------------------------------------------------------------------------
Last Change Time : 10/21/2016 00:08:29
Rem Table Inserts : 0
Rem Table Deletes : 0
Rem Table Drops : 0
Rem Table Ageouts : 0
-------------------------------------------------------------------------------
LLDP System Management Addresses
-------------------------------------------------------------------------------
===============================================================================
*A:hw_sas_duta>show>system#
show system lldp neighbor
Link Layer Discovery Protocol (LLDP) System Information
===============================================================================
NB = nearest-bridge NTPMR = nearest-non-tpmr NC = nearest-customer
===============================================================================
Lcl Port Scope Remote Chassis ID Index Remote Port Remote System Name
-------------------------------------------------------------------------------
1/1/2 NB D8:1D:FF:00:00:00 1 1/2/2 cses-v29
1/1/5 NB D8:1E:FF:00:00:00 2 1/1/4 cses-v30
1/1/7 NB D8:1E:FF:00:00:00 3 1/1/6 cses-v30
1/1/4 NB D8:20:FF:00:00:00 5 1/1/5 cses-v32
1/1/6 NB D8:20:FF:00:00:00 6 1/1/7 cses-v32
1/1/1 NB D8:1C:FF:00:00:00 9 1/2/2 cses-V28
===============================================================================
poe
Syntax
poe [detail]
Context
show>system
Platforms
7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p
Description
This command displays the PoE support status.
Parameters
- detail
Displays detailed PoE information.
Output
The following output is an example of PoE information, and Output fields: PoE describes the output fields.
Sample outputA:Dut-A# show system poe detail
============================================================
PoE Information (Existing)
============================================================
PSE Maximum Power Budget : 540 watts
PSE Power Provisioned : 30 watts
PSE Power Committed : 0 watts
PSE Power Available : 540 watts
-------------------------------------------------------------------------------
PoE provisioned (New)
===============================================================================
PSE Power Provisioned H-PoE : 0 watts
PSE Power Provisioned PoE++ : 0 watts
PSE Power Provisioned PoE+ : 0 watts
PSE Power Provisioned PoE : 0 watts
-------------------------------------------------------------------------------
PoE committed
===============================================================================
PSE Power Committed H-PoE : 0 watts
PSE Power Committed PoE++ : 0 watts
PSE Power Committed PoE+ : 0 watts
PSE Power Committed PoE : 0 watts
===============================================================================
PoE Port Information
===============================================================================
Port-Id PoE Admin PoE Oper PoE Type PoE Class PoE Power
State State Provisioned# Detected Committed
-------------------------------------------------------------------------------
1/1/1 Enabled Off PoE+ None N/A
1/1/2 Disabled None None None N/A
1/1/3 Disabled None None None N/A
1/1/4 Disabled None None None N/A
1/1/5 Disabled None None None N/A
1/1/6 Disabled None None None N/A
1/1/7 Disabled None None None N/A
1/1/8 Disabled None None None N/A
……
-------------------------------------------------------------------------------
Label |
Description |
|---|---|
PoE Information |
|
PSE Maximum Power Budget |
Displays the maximum power budget available for the system |
PSE Power Provisioned |
Displays the power provisioned |
PSE Power Committed |
Displays the sum of power supplied to all ports as determined by PoE type and class |
PSE Power Available |
Displays the power available from the maximum power budget |
PoE provisioned |
|
PSE Power Provisioned H-PoE |
Displays the power provisioned for HPoE devices |
PSE Power Provisioned PoE++ |
Displays the power provisioned for PoE++ devices |
PSE Power Provisioned PoE+ |
Displays the power provisioned for PoE+ devices |
PSE Power Provisioned PoE |
Displays the power provisioned for PoE devices |
PoE committed |
|
PSE Power Committed H-PoE |
Displays the power supplied to HPoE devices |
PSE Power Committed PoE++ |
Displays the power supplied to PoE++ devices |
PSE Power Committed PoE+ |
Displays the power supplied to PoE+ devices |
PSE Power Committed PoE |
Displays the power supplied to PoE devices |
PoE Port Information |
|
Port-Id |
Displays the port ID |
PoE Admin State |
Displays the PoE administrative state Enabled — Specifies that the PoE device is administratively enabled Disabled — Specifies that the PoE device is administratively disabled |
PoE Type Provisioned |
Displays the PoE type provisioned to the port |
PoE Class Detected |
Displays the PoE class, if available |
PoE Power Committed |
Displays the power committed to the PoE device |
LAG commands
lag
Syntax
lag [lag-id] [detail] [statistics]
lag lag-id associations
lag [lag-id] description
lag [lag-id] port
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays Link Aggregation Group (LAG) information.
If no command line options are specified, a summary listing of all LAGs is displayed.
Parameters
- lag-id
Displays only information about the specified LAG ID.
- detail
Displays detailed LAG information.
- statistics
Displays LAG statistics information.
- associations
Displays a list of current router interfaces to which the LAG is assigned.
- description
Displays LAG description strings.
- port
Display the LAG ports
Output
The following outputs are examples of LAG information, and the associated tables describe the output fields.
Sample output for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, Output fields: LAG
Sample output for LAG Statistics, Output fields: LAG statistics
Sample output for LAG Associations, Output fields: LAG associations
Sample output without MC-LAG, Output fields: LAG (no MC-LAG)
*A:SAH01-051>show# lag 1
===============================================================================
Lag Data
===============================================================================
Lag-id Adm Opr Port-Threshold Up-Link-Count MC Act/Stdby
-------------------------------------------------------------------------------
1 down down 0 0 N/A
===============================================================================
*A:SAH01-051>show#
*A:SAH01-051>show# lag 1 de
detail description
*A:SAH01-051>show# lag 1 detail
===============================================================================
LAG Details
===============================================================================
Description : N/A
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 1 Mode : access
Adm : down Opr : down
Thres. Exceeded Cnt : 0 Port Threshold : 0
Thres. Last Cleared : 04/29/2014 20:51:33 Threshold Action : down
Dynamic Cost : false Encap Type : null
Configured Address : 00:03:fa:27:15:6a Lag-IfIndex : 1342177281
Hardware Address : 00:03:fa:27:15:6a
Hold-time Down : 0.0 sec
LACP : disabled
Uplink : No
Standby Signaling : lacp DEI Classification : Disabled
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced Prio
-------------------------------------------------------------------------------
===============================================================================
*A:SAH01-051>show#
Label |
Description |
|---|---|
LAG ID |
The LAG ID that the port is assigned to. |
Adm |
Up The LAG is administratively up. |
Down The LAG is administratively down. |
|
Opr |
Up The LAG is operationally up. |
Down The LAG is operationally down. |
|
Port-Threshold |
The number of operational links for the LAG at or below which the configured action will be invoked. |
Up-Link-Count |
The number of ports that are physically present and have physical links present. |
MC Act/Stdby |
Member port is selected as active or standby link. |
*A:Dut-B# show lag 10 detail
===============================================================================
LAG Details
===============================================================================
Description : N/A
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 10 Mode : access
Adm : up Opr : up
Thres. Exceeded Cnt : 1 Port Threshold : 0
Thres. Last Cleared : 05/17/2009 19:33:00 Threshold Action : down
Dynamic Cost : false Encap Type : qinq
Configured Address : 00:03:fa:8d:45:d2 Lag-IfIndex : 1342177290
Hardware Address : 00:03:fa:8d:45:d2 Adapt Qos : distribute
Hold-time Down : 0.0 sec Port Type : standard
Per FP Ing Queuing : disabled
LACP : enabled Mode : active
LACP Transmit Intvl : fast LACP xmit stdby : enabled
Selection Criteria : highest-count Slave-to-partner : disabled
Number of sub-groups: 1 Forced : -
System Id : 00:03:fa:8d:44:88 System Priority : 32768
Admin Key : 32777 Oper Key : 40009
Prtr System Id : 00:03:fa:13:6f:a7 Prtr System Priority : 32768
Prtr Oper Key : 32777
MC Peer Address : 10.20.1.2 MC Peer Lag-id : 10
MC System Id : 00:02:80:01:00:0a MC System Priority : 100
MC Admin Key : 40009 MC Active/Standby : active
MC Lacp ID in use : true MC extended timeout : false
MC Selection Logic : peer decided
MC Config Mismatch : no mismatch
Source BMAC LSB : use-lacp-key Oper Src BMAC LSB : 9c:49
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced Prio
-------------------------------------------------------------------------------
1/1/10 up active up yes 1 - 32768
-------------------------------------------------------------------------------
Port-id Role Exp Def Dist Col Syn Aggr Timeout Activity
-------------------------------------------------------------------------------
1/1/10 actor No No Yes Yes Yes Yes Yes Yes
1/1/10 partner No No Yes Yes Yes Yes Yes Yes
===============================================================================
*A:ALA-48>show# lag 1 detail
===============================================================================
LAG Details
===============================================================================
Description:
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 1 Mode : access
Adm : up Opr : down
Thres. Exceeded Cnt : 0 Port Threshold : 3
Thres. Last Cleared : 02/21/2007 12:39:36 Threshold Action : dynamic cost
Dynamic Cost : false Encap Type : null
Configured Address : 04:67:01:01:00:01 Lag-IfIndex : 1342177281
Hardware Address : 14:30:ff:00:01:41 Adapt Qos : distribute
Hold-time Down : 0.0 sec
LACP : enabled Mode : active
LACP Transmit Intvl : fast LACP xmit stdby : enabled
Selection Criteria : highest-count Slave-to-partner : enabled
Number of sub-groups: 0 Forced : -
System Id : 14:30:ff:00:00:00 System Priority : 1
Admin Key : 32768 Oper Key : 32666
Prtr System Id : Prtr System Priority : 0
Prtr Oper Key : 0
MC Peer Address : 10.10.10.2 MC Peer Lag-id : 1
MC System Id : 00:00:00:33:33:33 MC System Priority : 32888
MC Admin Key : 32666 MC Active/Standby : active
MC Lacp ID in use : true MC extended timeout : false
MC Selection Logic : peer timed out (no route to peer), selected local
subgroup
MC Config Mismatch : no mismatch
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced Prio
-------------------------------------------------------------------------------
===============================================================================
*A:ALA-48>show#
*A:7210-SAS>show# lag 1 detail
===============================================================================
LAG Details
===============================================================================
Description : N/A
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 1 Mode : access
Adm : up Opr : down
Thres. Exceeded Cnt : 0 Port Threshold : 1
Thres. Last Cleared : 05/31/2011 11:55:49 Threshold Action : down
Encap Type : null
Configured Address : 00:25:ba:0a:33:cc Lag-IfIndex : 1342177281
Hardware Address : 00:25:ba:0a:33:cc
Hold-time Down : 0.0 sec
LACP : disabled
Uplink : No
Split Horizon Group : (Not Specified)
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced Prio
-------------------------------------------------------------------------------
===============================================================================
*A:7210-SAS>show#
*A:PE4-M2>show# lag 1 detail
===============================================================================
LAG Details
===============================================================================
Description : N/A
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 1 Mode : network
Adm : up Opr : up
Thres. Exceeded Cnt : 10 Port Threshold : 0
Thres. Last Cleared : 11/03/2016 18:38:22 Threshold Action : down
Dynamic Cost : false Encap Type : null
Configured Address : c4:08:41:61:61:bf Lag-IfIndex : 1342177281
Hardware Address : c4:08:41:61:61:bf Load Balancing : default
Hold-time Down : 0.0 sec
LACP : enabled Mode : active
LACP Transmit Intvl : fast LACP xmit stdby : enabled
Selection Criteria : highest-count Slave-to-partner : disabled
MUX control : coupled
Subgrp hold time : 0.0 sec Remaining time : 0.0 sec
Subgrp selected : 1 Subgrp candidate : -
Subgrp count : 1
System Id : c4:08:41:61:61:a3 System Priority : 32768
Admin Key : 31776 Oper Key : 31776
Prtr System Id : 4c:5f:d2:c1:5d:3a Prtr System Priority : 32768
Prtr Oper Key : 31776
Standby Signaling : lacp DEI Classification : Disabled
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced Prio
-------------------------------------------------------------------------------
1/1/1 up active up yes 1 - 32768
1/1/7 up active up 1 - 32768
-------------------------------------------------------------------------------
Port-id Role Exp Def Dist Col Syn Aggr Timeout Activity
-------------------------------------------------------------------------------
1/1/1 actor No No Yes Yes Yes Yes Yes Yes
1/1/1 partner No No Yes Yes Yes Yes Yes No
1/1/7 actor No No Yes Yes Yes Yes Yes Yes
1/1/7 partner No No Yes Yes Yes Yes Yes No
===============================================================================
*A:PE4-M2>show#
Label |
Description |
|---|---|
LAG ID |
The LAG or multi-link trunk (MLT) that the port is assigned to. |
Adm |
Up The LAG is administratively up. Down The LAG is administratively down. |
Port Threshold |
If the number of available links is equal or below this number, the threshold action is executed. |
Thres. Last Cleared |
The last time that keepalive stats were cleared. |
Dynamic Cost |
The OSPF costing of a link aggregation group based on the available aggregated, operational bandwidth. |
Configured Address |
The base chassis Ethernet MAC address. |
Hardware Address |
The hardware address. |
Hold-Time Down |
The timer, in tenths of seconds, which controls the delay between detecting that a LAG is down and reporting it to the higher levels. |
LACP |
Enabled LACP is enabled. |
Down LACP is disabled. |
|
LACP Transmit Intvl |
LACP timeout signaled to peer. |
Selection Criteria |
Configured subgroup selection criteria. |
Number of subgroups |
Total subgroups in LAG. |
System ID |
System ID used by actor in LACP messages. |
Admin Key |
Configured LAG key. |
Oper Key |
Key used by actor in LACP messages. |
System Priority |
System priority used by actor in LACP messages. |
Prtr System ID |
System ID used by partner in LACP messages. |
Prtr Oper Key |
Key used by partner in LACP messages. |
Prtr System Priority |
System priority used by partner in LACP messages. |
Mode |
LAG in access or network mode. |
Opr |
Up The LAG is operationally up. |
Down The LAG is operationally down. |
|
Port Threshold |
Configured port threshold. |
Thres. Exceeded Cnt |
The number of times that the drop count was reached. |
Threshold Action |
Action to take when the number of available links is equal or below the port threshold. |
Encap Type |
The encapsulation method used to distinguish customer traffic on a LAG. |
Lag-IFIndex |
A box-wide unique number assigned to this interface. |
Port ID |
The specific slot/MDA/port ID. |
(LACP) Mode |
LACP active or passive mode. |
LACP xmit standby |
LACP transmits on standby links enabled or disabled. |
Slave-to-partner |
Configured enabled or disabled. |
Port-id |
Displays the member port ID. |
Adm |
Displays the member port administrative state. |
Active/stdby |
Indicates that the member port is selected as the active or standby link. |
Opr |
Indicates the member port is in the operational state. |
Primary |
Indicates that the member port is the primary port of the LAG. |
Sub-group |
Displays the member subgroup where the member port belongs to. |
Priority |
Displays the member port priority. |
ALA-1# show lag statistics
===============================================================================
LAG Statistics
===============================================================================
Description:
Lag-id Port-id Input Input Output Output Input Output
Bytes Packets Bytes Packets Errors Errors
-------------------------------------------------------------------------------
1 1/1/3 0 1006 0 2494 0 0
1/1/4 0 435 0 401 0 0
1/1/5 0 9968 0 9833 0 0
-------------------------------------------------------------------------------
Totals 0 11409 0 12728 0 0
===============================================================================
ALA-1#
Label |
Description |
|---|---|
LAG ID |
The LAG or multi-link trunk (MLT) that the port is assigned to. |
Port ID |
The port ID configured or displayed in the slot/mda/port format. |
Input Bytes |
The number of incoming bytes for the LAG on a per-port basis. |
Input Packets |
The number of incoming packets for the LAG on a per-port basis. |
Output Bytes |
The number of outbound bytes for the LAG on a per-port basis. |
Output Packets |
The number of outbound packets for the LAG on a per-port basis. |
Input/Output Errors |
For packet-oriented interfaces, the number of inbound packets that contained errors preventing them from being deliverable to a higher-layer protocol. For character- oriented or fixed-length interfaces, the number of inbound transmission units that contained errors preventing them from being deliverable to a higher-layer protocol. For packet-oriented interfaces, the number of outbound packets that could not be transmitted because of errors. For character-oriented or fixed-length interfaces, the number of outbound transmission units that could not be transmitted because of errors. |
Totals |
Displays the column totals for bytes, packets, and errors. |
A:ALA-1# show lag 5 associations
==============================================================================
Interface Table
==============================================================================
Router/ServiceId Name Encap Val
------------------------------------------------------------------------------
Router: Base LAG2West 0
------------------------------------------------------------------------------
Interfaces
==============================================================================
A:ALA-1#
Label |
Description |
|---|---|
Service ID |
The service associated with the LAG. |
Name |
The name of the IP interface. |
Encap Val |
The values of the port for the IP interface. |
*A:pc5# show lag 2 detail
===============================================================================
LAG Details
===============================================================================
Description:
-------------------------------------------------------------------------------
Details
-------------------------------------------------------------------------------
Lag-id : 2 Mode : access
Adm : up Opr : up
Thres. Exceeded Cnt : 4 Port Threshold : 0
Thres. Last Cleared : 04/11/2007 02:03:49 Threshold Action : down
Dynamic Cost : false Encap Type : dot1q
Configured Address : 8e:8b:ff:00:01:42 Lag-IfIndex :
1342177282
Hardware Address : 8e:8b:ff:00:01:42 Adapt Qos :
distribute
Hold-time Down : 0.0 sec
LACP : enabled Mode : active
LACP Transmit Intvl : fast LACP xmit stdby : enabled
Selection Criteria : highest-count Slave-to-partner : disabled
Number of sub-groups: 2 Forced : -
System Id : 8e:8b:ff:00:00:00 System Priority : 32768
Admin Key : 32768 Oper Key : 32768
Prtr System Id : 8e:89:ff:00:00:00 Prtr System Priority : 32768
Prtr Oper Key : 32768
-------------------------------------------------------------------------------
Port-id Adm Act/Stdby Opr Primary Sub-group Forced
Prio
-------------------------------------------------------------------------------
1/1/1 up active up yes 7 - 99
1/1/2 up standby down 8 - 100
-------------------------------------------------------------------------------
Port-id Role Exp Def Dist Col Syn Aggr Timeout
Activity
-------------------------------------------------------------------------------
1/1/1 actor No No Yes Yes Yes Yes Yes Yes
1/1/1 partner No No Yes Yes Yes Yes Yes Yes
1/1/2 actor No No No No No Yes Yes Yes
1/1/2 partner No No No No Yes Yes Yes Yes
===============================================================================
Label |
Description |
|---|---|
Lag-id |
The LAG identifier |
Mode |
The mode of the LAG: access or network |
Adm |
Up: the LAG is administratively up |
Down: the LAG is administratively down |
|
Opr |
Up: the LAG is operationally up |
Down: the LAG is operationally down |
|
Thres. Exceeded Cnt |
The number of times that the drop count was reached |
Port Threshold |
The number of operational links at or below which the LAG is regarded as operationally down. |
Thres. Last Cleared |
The last time that keepalive statistics were cleared. |
Threshold Action |
Action to take when the number of operational links is equal to or below the port threshold. |
Dynamic Cost |
n/a |
Encap Type |
The encapsulation method used to distinguish customer traffic on a LAG. |
Configured Address |
The base chassis Ethernet MAC address. |
Lag-IfIndex |
A unique number assigned to this interface. |
Hardware Address |
The hardware address. |
Adapt Qos |
The configured QoS mode. |
Hold-time Down |
The hold-time, in tenths of seconds, before a failure is reported to higher levels. |
Port Type |
Standard: standard Ethernet port types are supported. |
LACP |
Enabled LACP is enabled. |
Disabled LACP is disabled. |
|
Mode |
Active LACP operates in active mode. |
Passive LACP operates in passive mode. |
|
Role |
Actor Local device (7705 SAR) participating in LACP negotiation. |
Partner Remote device participating in LACP negotiation. |
|
LACP Transmit Intvl |
LACP timeout signaled to peer. |
LACP xmit stdby |
LACP transmit on standby links enabled or disabled. |
Selection Criteria |
Configured subgroup selection criteria. |
Slave-to-partner |
Slave-to-partner flag enabled or disabled. |
Number of sub-groups |
Total subgroups in LAG. |
Forced |
n/a |
System Id |
System ID used by actor in LACP messages. |
System Priority |
System priority used by actor in LACP messages. |
Admin Key |
Configured LAG key. |
Oper Key |
Key used by actor in LACP messages. |
Prtr System Id |
System ID used by partner in LACP messages. |
Prtr System Priority |
System priority used by partner in LACP messages. |
Prtr Oper Key |
The key used by partner in LACP messages. |
Port-id |
The member physical port ID expressed in slot/mda/port format. |
Adm |
Up The member port is administratively up. |
Down The member port is administratively down. |
|
Act/Stdby |
Active The member port is active. |
Standby The member port is on standby. |
|
Opr |
Up The member port is operationally up. |
Down The member port is operationally down. |
|
Primary |
Indicates whether the member port is the primary port. |
Sub-group |
The member port subgroup. |
Prio |
The member port priority. |
redundancy
Syntax
redundancy
Context
show
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
Commands in this context display multi-chassis redundancy information.
multi-chassis
Syntax
all
mc-lag peer ip-address [lag lag-id]
mc-lag [peer ip-address [lag lag-id]] statistics
sync peer [ip-address]
sync peer [ip-address] detail
sync peer [ip-address] statistics
Context
show>redundancy
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command displays multi-chassis redundancy information.
Parameters
- all
Displays all multi-chassis information.
- mc-lag
Displays multi-chassis LAG information.
- peer ip-address
Displays the address of the multi-chassis peer.
- lag lag-id
Displays the specified LAG ID on this system that forms an multi-chassis LAG configuration with the indicated peer.
- statistics
Displays statistics for the multi-chassis peer.
- sync
Displays synchronization information.
- detail
Displays more information.
Output
The following output is an example of multi-chassis redundancy information, and Output fields: show multi-chassis describes the output fields.
Sample output*A:SAS# show redundancy multi-chassis mc-lag peer 3.3.3.3
===============================================================================
Multi-Chassis MC-Lag Peer 3.3.3.3
===============================================================================
Last State chg : 08/31/2014 07:07:48
Admin State : Up Oper State : Up
KeepAlive : 10 deci-seconds Hold On Ngbr Failure : 3
-------------------------------------------------------------------------------
Lag Id Lacp Remote System Id Sys Last State Changed
Key Lag Id Prio
-------------------------------------------------------------------------------
25 0 1 0 08/31/2014 07:20:10
-------------------------------------------------------------------------------
Number of LAGs : 1
*A:SAS# show redundancy multi-chassis all
===============================================================================
Multi-Chassis Peers
===============================================================================
Peer IP Peer Admin Client Admin Oper State
Src IP Auth
-------------------------------------------------------------------------------
3.3.3.3 Enabled MC-Sync: -- -- --
2.2.2.2 hash2 MC-Ring: -- -- --
MC-Endpt: -- -- --
MC-Lag: Enabled Enabled --
*A:SAS# show redundancy multi-chassis sync peer 10.3.3.3
===============================================================================
Multi-chassis Peer Table
===============================================================================
Peer
-------------------------------------------------------------------------------
Peer IP Address : 10.3.3.3
Description : (Not Specified)
Authentication : Enabled
Source IP Address : 10.2.2.2
Admin State : Enabled
-------------------------------------------------------------------------------
Sync: Not-configured
-------------------------------------------------------------------------------
===============================================================================
*A:SAS# show redundancy multi-chassis sync peer 3.3.3.3 detail
===============================================================================
Multi-chassis Peer Table
===============================================================================
Peer
-------------------------------------------------------------------------------
Peer IP Address : 10.3.3.3
Description : (Not Specified)
Authentication : Enabled
Source IP Address : 10.2.2.2
Admin State : Enabled
-------------------------------------------------------------------------------
Sync: Not-configured
-------------------------------------------------------------------------------
===============================================================================
Ports synced on peer 10.3.3.3
===============================================================================
Port/Encap Tag
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
DHCP Server instances synced on peer 10.3.3.3
===============================================================================
Router-Name Server-Name
Tag
-------------------------------------------------------------------------------
No instances found
===============================================================================
Label |
Description |
|---|---|
Peer IP |
Displays the multi-chassis redundancy peer IP address |
Src IP |
Displays the source IP address used to communicate with the multi-chassis peer |
Auth |
If configured, displays the authentication key used between this node and the multi-chassis peer |
mc-lag
Syntax
mac-lag peer ip-address [lag lag-id]
mac-lag [peer ip-address [lag lag-id]] statistics
Context
show>redundancy>multi-chassis
Platforms
7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C
Description
This command displays multi-chassis LAG information.
Parameters
- peer ip-address
Specifies the peer IP address for which to display multi-chassis LAG information.
- lag lag-id
Displays information about the specified LAG ID
- statistics
Displays LAG statistics information.
Output
The following output is an example of multi-chassis LAG information, and Output fields: MC-LAG describes the output fields.
Sample output*7210-SAS>show>redundancy>multi-chassis# mc-lag peer 1.1.1.1
===============================================================================
Multi-Chassis MC-Lag Peer 1.1.1.1
===============================================================================
Last State chg : 08/13/2011 09:02:31
Admin State : Down Oper State : Down
KeepAlive : 10 deci-seconds Hold On Ngbr Failure : 3
-------------------------------------------------------------------------------
Lag Id Lacp Remote System Id Sys Last State Changed
Key Lag Id Prio
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
No LAGs found
===============================================================================
*7210-SAS>show>redundancy>multi-chassis# ^C
*A:SAS# show redundancy multi-chassis mc-lag peer 3.3.3.3 statistics
===============================================================================
Multi-Chassis Statistics, Peer 3.3.3.3
===============================================================================
Packets Rx : 8333
Packets Rx Keepalive : 8321
Packets Rx Config : 1
Packets Rx Peer Config : 2
Packets Rx State : 9
Packets Dropped State Disabled : 0
Packets Dropped Packets Too Short : 0
Packets Dropped Tlv Invalid Size : 0
Packets Dropped Tlv Invalid LagId : 0
Packets Dropped Out of Seq : 0
Packets Dropped Unknown Tlv : 0
Packets Dropped MD5 : 0
Packets Tx : 9229
Packets Tx Keepalive : 8705
Packets Tx Peer Config : 509
Packets Tx Failed : 1
============================================================================
Label |
Description |
|---|---|
Last State chg |
Displays date and time of the last state change for the MC-LAG peer |
Admin State |
Displays the administrative state of the MC-LAG peer |
KeepAlive |
Displays the time interval between keepalive messages exchanged between peers |
Oper State |
Displays the operational state of the MC-LAG peer |
Hold On Ngbr Failure |
Displays how many keep alive intervals the standby will wait for packets from the active node before assuming a redundant neighbor node failure |
Lag Id |
Displays the LAG identifier, expressed as a decimal integer |
Lacp Key |
Displays the 16-bit Lacp key |
Remote system Id |
Displays the LAG identifier of the remote system, expressed as a decimal integer |
Multi-Chassis Statistics |
|
Packets Rx |
Displays the number of MC-LAG packets received from the peer |
Packets Rx Keepalive |
Displays the number of MC-LAG keepalive packets received from the peer |
Packets Rx Config |
Displays the number of MC-LAG configured packets received from the peer |
Packets Rx Peer Config |
Displays the number of MC-LAG packets configured by the peer |
Packets Rx State |
Displays the number of received MC-LAG ‟lag” state packets received from the peer |
Packets Dropped State Disabled |
Displays the number of packets that were dropped because the peer was administratively disabled |
Packets Dropped Packets Too Short |
Displays the number of packets that were dropped because the packet was too short |
Packets Dropped Tlv Invalid Size |
Displays the number of packets that were dropped because the packet size was invalid |
Packets Dropped Tlv Invalid LagId |
Displays the number of packets that were dropped because the packet referred to an invalid or non-multi-chassis LAG |
Packets Dropped Out of Seq |
Displays the number of packets that were dropped because the packet was out of sequence |
Packets Dropped Unknown Tlv |
Displays the number of packets that were dropped because the packet contained an unknown TLV |
Packets Dropped MD5 |
Displays the number of packets that were dropped because the packet failed MD5 authentication |
Packets Tx |
Displays the number of packets transmitted from this system to the peer |
Packets Tx Keepalive |
Displays the number of keepalive packets transmitted from this system to the peer |
Packets Tx Peer Config |
Displays the number of configured packets transmitted from this system to the peer |
Packets Tx Failed |
Displays the number of packets that failed to be transmitted from this system to the peer |
MACsec show commands
macsec
Syntax
macsec
Context
show
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
Commands in this context display MACsec information.
connectivity-association
Syntax
connectivity-association [ca-name] [detail]
Context
show>macsec
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command displays MACsec CA information.
Parameters
- ca-name
-
Displays CA name information, up to 256 characters.
- detail
-
Displays MACsec CA detailed information.
Output
The following outputs are examples of CA information, and the associated tables describe the output fields:
-
Sample output: MACsec CA , Output fields: MACsec connectivity association
-
Sample output: MACsec CA with CA name, Output fields: MACsec CA with CA name
A:Dut-C# show macsec connectivity-association
===============================================================================
ca-name : dut_B_C_128_01
ca-name : dut_B_C_256_01
ca-name : to_Juniper_1_1_2__1
ca-name : abcdefghijklmnoprstuvxyz@!
===============================================================================
|
Label |
Description |
|---|---|
|
ca-name |
Specifies the CA name |
A:Dut-C# show macsec connectivity-association "abcdefghijklmnoprstuvxyz@!"
===============================================================================
Connectivity Association "abcdefghijklmnoprstuvxyz@!"
===============================================================================
Admin State : Up
Description : alsfjalsfjafja;lsjflasjflasjfl
Replay Protection : Disabled
Replay Window Size : 333
Macsec Encrypt : Enabled
Clear Tag Mode : dual-tag
Cipher Suite : gcm-aes-256
Encryption Offset : 30
Assigned ports : 2/1/9 2/1/10
-------------------------------------------------------------------------------
Static Cak
-------------------------------------------------------------------------------
MKA Key Server Priority : 16
Active Pre-Shared-Key Index : 1
Active Pre-Shared-Key CKN : aabbccddeeff00112233445566778899
===============================================================================
|
Label |
Description |
|---|---|
|
Admin State |
Up — The CA is administratively up |
|
Down — The CA is administratively down If port <x/y/z> ethernet>macsec is shutdown, the admin state is down. Otherwise, the admin state is up. |
|
|
Description |
Displays a user description for this CA |
|
Replay Protection |
Enabled — Replay Protection is enabled |
|
Disabled — Replay Protection is disabled If replay protection is enabled for this CA, the out of window packet is discarded. |
|
|
Replay Window Size |
Displays the size, in packets, of the replay window |
|
Macsec Encrypt |
Enabled MACsec is enabled |
|
Disabled MACsec is disabled |
|
|
Clear Tag Mode |
Displays the clear tag mode: single-tag, dual-tag |
|
Cipher Suite |
Displays the cipher suite used for encrypting the SAK: gcm-aes-128 or gcm-aes-256 |
|
Encryption Offset |
Displays the encryption offset configured on this node: 0, 30, 50 |
|
Assigned ports |
Displays all ports that contain this CA |
|
MKA Key Server Priority |
Displays the MKA key server priority: 0 to 255 (default 16) |
|
Active Pre-Shared Key Index |
Displays the active preshared key index: 1 to 2 (default 1) |
|
Active Pre-Shared Key CKN |
Displays the active PSK CAK name |
mka-session
Syntax
mka-session [port port-id]
mka-session [port port-id] detail
mka-session [port port-id] statistics
Context
show>macsec
Platforms
7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-Dxp 24p
Description
This command displays MACsec MKA session information.
Parameters
- port-id
-
Specifies the port ID, up to 17 characters.
Note: See SA limits and network design for more information about security zones and ports where MACsec can be enabled.
- detail
-
Displays MACsec MKA session detailed information.
- statistics
-
Displays MACsec MKA session statistical information.
Output
The following outputs are examples of MACsec MKA session information, and the associated tables describe the output fields:
-
Sample output: MACsec MKA-session port, Output fields: MACsec MKA-session port
-
Sample output: MACsec MKA-session port (detail), Output fields: MACsec MKA-session port (detail and statistics)
-
Sample output: MACsec MKA-session (statistics), Output fields: MACsec MKA-session port (detail and statistics)
A:Dut-C# show macsec mka-session port 2/1/11
===============================================================================
MKA Session for port 2/1/11
===============================================================================
Port : 2/1/11
Security Zone : 3
===============================================================================
===============================================================================
Live Peer List
===============================================================================
Member Identifier Mesg Num Rx-SCI KS priority
-------------------------------------------------------------------------------
bf4102704294fa1057022bdf 28322 a47b2ce112ef0000 16
===============================================================================
===============================================================================
Potential Peer List
===============================================================================
Member Identifier Mesg Num Rx-SCI KS priority
-------------------------------------------------------------------------------
===============================================================================
|
Label |
Description |
|---|---|
|
MKA Session for port |
Displays the MKA session for the current port |
|
Port |
Displays the MKA session current port |
|
Security Zone |
Displays security zone this port belongs to |
|
Live Peer List |
Displays peers (participants) that have provided their MI and MN via KMA. The peer entry is in the Live Peer List. |
|
Member Identifier |
Displays the MI of the peer entry |
|
Mesg Num |
Displays the latest Member Number of the peer entry |
|
Rx-SCI |
Displays the Peer Rx-SCI |
|
KS-priority |
Displays the Peer Key server priority |
|
Potential Peer List |
Peers (participants) that have Potential Peers List includes all the other peers that have transmitted an MKPDU that has been directly received by the participant or that were included in the Live Peers List of a MKPDU transmitted by a peer that has proved liveness, an MKA PDU. The peer entry is in the Potential Peers List. |
A:Dut-C# show macsec mka-session port 2/1/11 detail
===============================================================================
MKA Session for port 2/1/11
===============================================================================
Port : 2/1/11
Security Zone : 3
MKA Oper State : unknown value
Oper Cipher Suite : unknown value
Oper Encrypt Offset: 0
CAK Name : 11223344556677889900aabbccddeeff11223344556677889900aabbc*
MKA Member ID : f134218784b114eb61dbe834
Transmit Interval : 2000
Outbound SCI : a4:7b:2c:e1:12:8f
Message Number : 28298
Key Number : 878
Key Server : yes
Key Server Priority: 16
Latest SAK AN : 3
Latest SAK KI : f134218784b114eb61dbe8340000036d
Previous SAK AN : 2
Previous SAK KI : f134218784b114eb61dbe83400000000
===============================================================================
* indicates that the corresponding row element may have been truncated.
===============================================================================
Live Peer List
===============================================================================
Member Identifier Mesg Num Rx-SCI KS priority
-------------------------------------------------------------------------------
bf4102704294fa1057022bdf 28323 a47b2ce112ef0000 16
===============================================================================
===============================================================================
Potential Peer List
===============================================================================
Member Identifier Mesg Num Rx-SCI KS priority
-------------------------------------------------------------------------------
===============================================================================
===============================================================================
MKA Session Statistics for port 2/1/11
===============================================================================
Peer Removed Due to Timeout : 0
CKN Not Found : 0
New Live peer : 0
SAK Generated by Server : 0
SAK Installed for TX : 0
SAK Installed for RX : 0
PDU Too Small : 0
PDU Too Big : 0
PDU Not Quad Size : 0
PDU Message Number Invalid : 0
PDU Param Set Size Invalid : 0
PDU Liveness Check Fail : 0
Param Set Not Quad Size : 0
Unsupported Agility : 0
Invalid CAK Name Length : 0
ICV Check Failed : 0
Peer Using Same MID : 0
SAK From Non-Live Peer : 0
SAK From Non-Key Server : 0
SAK Decrypt Fail : 0
SAK Encrypt Fail : 0
Key Number Invalid : 0
SAK Installation Failed : 0
CAK Info Missing : 0
Max Peers Set as Zero : 0
===============================================================================
A:Dut-C# show macsec mka-session statistics
===============================================================================
MKA Session Statistics for port 2/1/11
===============================================================================
Peer Removed Due to Timeout : 0
CKN Not Found : 0
New Live peer : 0
SAK Generated by Server : 0
SAK Installed for TX : 0
SAK Installed for RX : 0
PDU Too Small : 0
PDU Too Big : 0
PDU Not Quad Size : 0
PDU Message Number Invalid : 0
PDU Param Set Size Invalid : 0
PDU Liveness Check Fail : 0
Param Set Not Quad Size : 0
Unsupported Agility : 0
Invalid CAK Name Length : 0
ICV Check Failed : 0
Peer Using Same MID : 0
SAK From Non-Live Peer : 0
SAK From Non-Key Server : 0
SAK Decrypt Fail : 0
SAK Encrypt Fail : 0
Key Number Invalid : 0
SAK Installation Failed : 0
CAK Info Missing : 0
Max Peers Set as Zero : 0
===============================================================================
|
Label |
Description |
|---|---|
|
MKA Oper State |
Displays the operational state of the MKA participant on this port. The operational MKA state will be up if MKA hellos are received on this port and have a valid session. |
|
Oper Cipher Suite |
Displays the operational encryption algorithm used for datapath PDUs when all parties in the CA have the (SAK). This value is specified by the key server: gcm-aes-128 or gcm-aes-256 |
|
Oper Encrypt Offset |
Displays the operational encryption offset used for the datapath PDUs when all parties in the CA have the SAK. This value is specified by the key server: 0, 30, 50. |
|
CAK Name |
Displays the name of the CAK in use by this MKA which is used to find the correct CAK |
|
MKA Member ID |
Displays the Member Identifier (MI) for the MKA instance |
|
Transmit Interval |
Displays the time interval (in ms) at which the MKA broadcasts its liveliness to its peers and is non-configurable |
|
Outbound SCI |
Displays the Secure Channel Identifier (SCI) information for transmitting MACsec frames and consists of the outgoing port MAC Address and a port identifier |
|
Message Number |
Displays the current count of MKA messages that is attached to MKA PDUs |
|
Key Number |
Displays the number of the currently assigned CAK. When a new CAK is generated, this number is incremented. A SAK is identified by 128-bit Key Identifier (KI) and 32-bit Key-Number (KN). |
|
Key Server |
Displays whether this server is the highest priority server in the peer group: no, yes |
|
Key Server Priority |
Displays the priority of the active key server: 0-255 (default 16) |
|
Latest SAK AN |
Displays the Association Number (AN) of the latest SAK. This number is concatenated with an SCI to identify a Secure Association (SA). In SR OS, only two SAKs are supported. |
|
Latest SAK KI |
Displays the Key Identifier (KI) of the latest SAK. This number is derived from the MI of the key server and the key number. |
|
Previous SAK AN |
Displays the AN of the previous SAK. This number is concatenated with an SCI to identify an SA. |
|
Previous SAK KI |
Displays the KI of the previous SAK. This number is derived from the MI of the key server and the key number. |
|
Peer Removed Due to Timeout |
Displays the number of peers removed from the live/potential peer list caused by not receiving an MKPDU within the MKA Live Time (6.0 seconds) and is not configurable |
|
CKN Not Found |
Displays the number of MKPDUs received with a CKN that does not match the CA configured for the port |
|
New Live Peer |
Displays the number of validated peers that have been added to the live peer list |
|
SAK Generated by Server |
Displays the number of SAKs generated by this MKA instance |
|
SAK Installed for TX |
Displays the number of SAKs installed for transmitting |
|
SAK Installed for RX |
Displays the number of SAKs installed for receiving |
|
PDU Too small |
Indicates that the number of MKPDUs received that are less than 32 octets |
|
PDU Too big |
Indicates the number of MKPDUs received where the EAPOL header indicates a size larger than the received packet. |
|
PDU Not Quad Size |
Indicates the number of MKPDUs received with a size that is not a multiple of 4 octets long |
|
PDU Message Number Invalid |
Indicates the number of MKPDUs received out of order as indicated by the Message Number |
|
PDU Param Set Size Invalid |
Indicates the number of MKPDUs received which contain a parameter set body length that exceeds the remaining length of the MKPDU |
|
PDU Liveness Check Fail |
Indicates the number of MKPDUs received which contain an MN that is not acceptably recent |
|
Param Set Not Quad Size |
Indicates the number of MKPDUs received which contain a parameter set that is not a multiple of 4 octets long |
|
Unsupported Agility |
Indicates the number of MKPDUs received which contain an unsupported Algorithm Agility value |
|
Invalid CAK Name Length |
Indicates the number of MKPDUs received which contain a CAK name that exceeds the maximum CAK name length |
|
ICV Check Failed |
Indicates the number of MKPDUs received which contain an ICV value that does not authenticate |
|
Peer Using Same MID |
Indicates the number of MKPDUs received which contain a peer list with an MI entry which conflicts with the local MI |
|
SAK From Non-Live Peer |
Indicates the number of SAKs received from peer that is not a member of the Live Peers List |
|
SAK From Non-Key Server |
Indicates the number of SAKs received from an MKA participant that has not been designated as the Key Server. Only the key server should distribute SAK. |
|
SAK Decrypt Fail |
Indicates the number of AES Key Wrap SAK decryption failures that have occurred |
|
SAK Encrypt Fail |
Indicates the number of AES Key Wrap SAK encryption failures that have occurred |
|
Key Number Invalid |
Indicates the number of SAKs received with an invalid Key Number |
|
SAK Installation Failed |
Indicates the number of Secy SAK installation failures that have occurred |
|
CAK Info Missing |
Indicates the number of times internal CAK data is not available for the generation of the SAK |
|
Max Peers Set as Zero |
Indicates the number of Secy SAK installations that have failed because the max peer entry being set to 0 |
Port monitor commands
port
Syntax
port port-id [port-id...(up to 5 max)] [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables port traffic monitoring. The specified port statistical information displays at the configured interval until the configured count is reached.
The first screen displays the current statistics related to the specified ports. The subsequent statistical information listed for each interval is displayed as a delta to the previous display.
When the keyword rate is specified, the ‟rate per second” for each statistic is displayed instead of the delta.
Monitor commands are similar to show commands but only statistical information displays. Monitor commands display the selected statistics according to the configured number of times at the interval specified.
Parameters
- port-id
Specifies up to five port IDs in the form slot/mda/port.
- interval
Specifies the interval for each display, in seconds.
- repeat repeat
Specifies how many times the command is repeated.
- absolute
Displays raw statistics. No calculations are performed on the delta or rate statistics.
- rate
Displays the rate-per-second for each statistic instead of the delta.
Output
Sample outputA:ALA-12>monitor# port 1/4 interval 3 repeat 3 absolute
===============================================================================
Monitor statistics for Port 1/4
===============================================================================
Input Output
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
Octets 0 0
Packets 39 175
Errors 0 0
-------------------------------------------------------------------------------
At time t = 3 sec (Mode: Absolute)
-------------------------------------------------------------------------------
Octets 0 0
Packets 39 175
Errors 0 0
-------------------------------------------------------------------------------
At time t = 6 sec (Mode: Absolute)
-------------------------------------------------------------------------------
Octets 0 0
Packets 39 175
Errors 0 0
-------------------------------------------------------------------------------
At time t = 9 sec (Mode: Absolute)
-------------------------------------------------------------------------------
Octets 0 0
Packets 39 175
Errors 0 0
===============================================================================
A:ALA-12>monitor#
A:ALA-12>monitor# port 1/4 interval 3 repeat 3 rate
===============================================================================
Monitor statistics for Port 1/4
===============================================================================
Input Output
-------------------------------------------------------------------------------
At time t = 0 sec (Base Statistics)
-------------------------------------------------------------------------------
Octets 0 0
Packets 39 175
Errors 0 0
-------------------------------------------------------------------------------
At time t = 3 sec (Mode: Rate)
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
-------------------------------------------------------------------------------
At time t = 6 sec (Mode: Rate)
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
-------------------------------------------------------------------------------
At time t = 9 sec (Mode: Rate)
-------------------------------------------------------------------------------
Octets 0 0
Packets 0 0
Errors 0 0
===============================================================================
A:ALA-12>monitor#
Clear commands
lag
Syntax
lag lag-id statistics
Context
clear
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command clears statistics for the specified LAG ID.
Parameters
- lag-id
Specifies the LAG ID for which to clear statistics.
- statistics
Specifies to clear statistics for the specified LAG ID.
port
Syntax
port port-id statistics
Context
clear
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command clears port statistics for the specified ports.
Parameters
- port-id
Specifies the port identifier.
- statistics
Specifies that port statistics will be cleared.
Debug commands
lag
Syntax
lag [lag-id lag-id [port port-id]] [all]
lag [lag-id lag-id [port port-id]] [sm] [pkt] [cfg] [red] [iom-upd] [port-state] [timers] [sel-logic]
no lag [lag-id lag-id]
Context
debug
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables debugging for LAG.
Parameters
- lag-id
Specifies the link aggregation group ID.
- port-id
Specifies the physical port ID.
- sm
Specifies to display trace LACP state machine.
- pkt
Specifies to display trace LACP packets.
- cfg
Specifies to display trace LAG configuration.
- red
Specifies to display trace LAG high availability.
- iom-upd
Specifies to display trace LAG IOM updates.
- port-state
Specifies to display trace LAG port state transitions.
- timers
Specifies to display trace LAG timers.
- sel-logic
Specifies to display trace LACP selection logic.