Event and accounting logs
This chapter provides information about configuring event and accounting logs on the 7210 SAS.
Logging overview
The two primary types of logging supported in the 7210 SAS OS are event logging and accounting logs.
Event logging controls the generation, dissemination and recording of system events for monitoring status and troubleshooting faults within the system. The 7210 SAS groups events into three major categories or event sources:
Security events
Events that pertain to attempts to breach system security.
Change events
Events that pertain to the configuration and operation of the node.
Main events
Events that pertain to applications that are not assigned to other event categories/sources.
Debug events
Events that pertain to trace or other debugging information.
The following are events within the 7210 SAS and have the following characteristics:
a time stamp in UTC or local time
the generating application
a unique event ID within the application
the VRF-ID
a subject identifying the affected object
a short text description
Event control assigns the severity for each application event and whether the event should be generated or suppressed. The severity numbers and severity names supported in the 7210 SAS OS conform to ITU standards M.3100 X.733 and X.21 and are listed in the following table.
| Severity number | Severity name |
|---|---|
1 |
cleared |
2 |
indeterminate (info) |
3 |
critical |
4 |
major |
5 |
minor |
6 |
warning |
Events that are suppressed by event control will not generate any event log entries. Event control maintains a count of the number of events generated (logged) and dropped (suppressed) for each application event. The severity of an application event can be configured in event control.
An event log within the 7210 SAS OS associates the event sources with logging destinations. Examples of logging destinations include, the console session, a specific Telnet or SSH session, memory logs, file destinations, SNMP trap groups and syslog destinations. A log filter policy can be associated with the event log to control which events will be logged in the event log based on combinations of application, severity, event ID range, VRF ID, and the subject of the event.
The 7210 SAS accounting logs collect comprehensive accounting statistics to support a variety of billing models. The routers collect accounting data on services and network ports on a per-service class basis. In addition to gathering information critical for service billing, accounting records can be analyzed to provide insight about customer service trends for potential service revenue opportunities. Accounting statistics on network ports can be used to track link utilization and network traffic pattern trends. This information is valuable for traffic engineering and capacity planning within the network core.
Accounting statistics are collected according to the parameters defined within the context of an accounting policy. Accounting policies are applied to access objects (such as access ports and SAPs or network objects (such as SDPs, network ports, network IP interface). Accounting statistics are collected by counters for individual service meters defined on the customer SAP or by the counters within forwarding class (FC) queues defined on the network ports.
The type of record defined within the accounting policy determines where a policy is applied, what statistics are collected and time interval at which to collect statistics.
The ‟location” field of the file ID allows the user to configure the device and store it in any directory. The default value is cf1:, but it can also be uf1: (for devices supporting USB) and uf1: and cf2: for the 7210 SAS-T.
Log destinations
Both event logs and accounting logs use a common mechanism for referencing a log destination.
Only a single log destination can be associated with an event log or with an accounting log. An event log can be associated with multiple event sources, but it can only have a single log destination.
A file destination is the only type of log destination that can be configured for an accounting log.
Console
Sending events to a console destination means the message will be sent to the system console The console device can be used as an event log destination.
Session
A session destination is a temporary log destination which directs entries to the active Telnet or SSH session for the duration of the session. When the session is terminated, for example, when the user logs out, the event log is removed. Event logs configured with a session destination are not stored in the configuration file. Event logs can direct log entries to the session destination.
Memory logs
A memory log is a circular buffer. When the log is full, the oldest entry in the log is replaced with the new entry. When a memory log is created, the specific number of entries it can hold can be specified, otherwise it will assume a default size. An event log can send entries to a memory log destination.
Log files
Log files can be used by both event logs and accounting logs and are stored on the compact flash devices (specifically cf1:) in the file system.
A log file is identified with a single log file ID, but a log file will generally be composed of a number individual files in the file system. A log file is configured with a rollover parameter, expressed in minutes, which represents the length of time an individual log file should be written to before a new file is created for the relevant log file ID. The rollover time is checked only when an update to the log is performed. Therefore, complying to this rule is subject to the incoming rate of the data being logged. For example, if the rate is very low, the actual rollover time may be longer than the configured value.
The retention time for a log file specifies the amount of time the file should be retained on the system based on the creation date and time of the file. The system continuously checks for log files with expired retention periods once every hour and deletes as many files as possible during a ten second interval.
When a log file is created, only the compact flash device for the log file is specified. Log files are created in specific subdirectories with standardized names depending on the type of information stored in the log file.
Event log files are always created in the \log directory on the specified compact flash device. The naming convention for event log files is:
log eeff-timestamp
where:
ee is the event log ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2017)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14 seconds)
Accounting log files are created in the \act-collect directory on a compact flash device (cf1). The naming convention for accounting log files is nearly the same as for log files except the prefix "act" is used instead of the prefix "log". The naming convention for accounting logs is:
act aaff-timestamp.xml.gz
where:
aa is the accounting policy ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2007)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14 seconds)
Accounting logs are .xml files created in a compressed format and have a .gz extension.
The \act-collect directory is where active accounting logs are written. When an accounting log is rolled over, the active file is closed and archived in the \act directory before a new active accounting log file created in \act-collect.
SNMP trap group
An event log can be configured to send events to SNMP trap receivers by specifying an SNMP trap group destination.
An SNMP trap group can have multiple trap targets. Each trap target can have different operational parameters.
A trap destination has the following properties:
The IP address of the trap receiver.
The UDP port used to send the SNMP trap.
SNMP version (v1, v2c, or v3) used to format the SNMP notification.
SNMP community name for SNMPv1 and SNMPv2c receivers.
Security name and level for SNMPv3 trap receivers.
For SNMP traps that will be sent in-band, the source IP address of the trap is the system IP address of the 7210 SAS.
Each trap target destination of a trap group receives the identical sequence of events as defined by the log ID and the associated sources and log filter applied.
Syslog
An event log can be configured to send events to one syslog destination. Syslog destinations have the following properties:
syslog server IP address
the UDP port used to send the syslog message
the Syslog Facility Code (0 - 23) (default 23 - local 7)
the Syslog Severity Threshold (0 - 7) - events exceeding the configured level will be sent
Because syslog uses eight severity levels whereas the 7210 SAS-Series uses six internal severity levels, the severity levels are mapped to syslog severities. The following table lists the severity level mappings to syslog severities.
| Severity level | Numerical severity (highest to lowest) | Syslog configured severity | Definition |
|---|---|---|---|
— |
0 |
emergency |
System is unusable |
critical (3) |
1 |
alert |
Action must be taken immediately |
major (4) |
2 |
critical |
Critical conditions |
minor (5) |
3 |
error |
Error conditions |
warning (6) |
4 |
warning |
Warning conditions |
— |
5 |
notice |
Normal but significant condition |
cleared (1) indeterminate (2) |
6 |
info |
Informational messages |
— |
7 |
debug |
Debug-level messages |
Event logs
Event logs are the means of recording system generated events for later analysis. Events are messages generated by the system by applications or processes within the 7210 SAS.
The following figure shows a function block diagram of event logging.
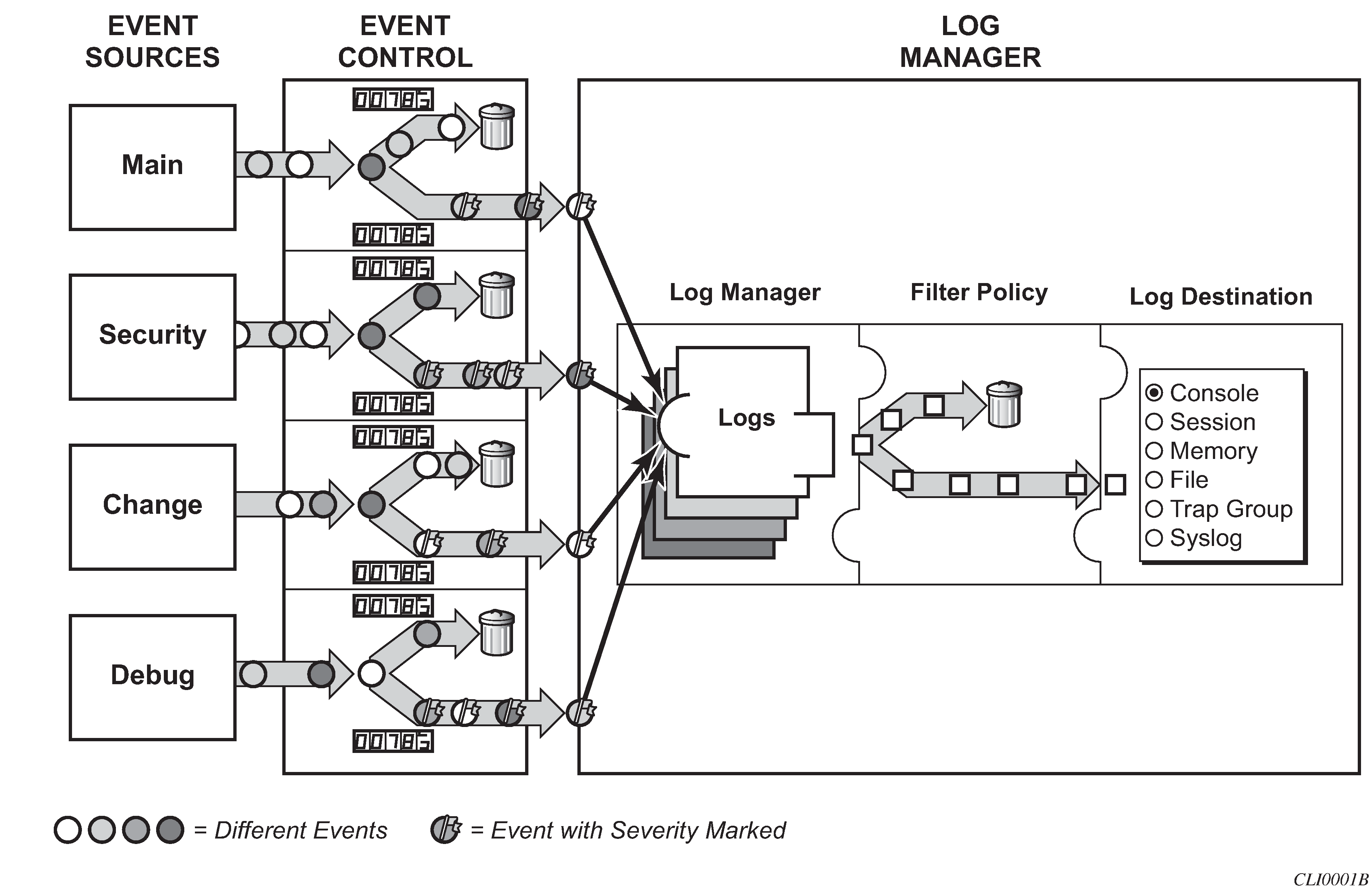
Event sources
In Event logging block diagram, the event sources are the main categories of events that feed the log manager:
Security
The security event source is all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. Security events are generated by the SECURITY application and the authenticationFailure event in the SNMP application.
Change
The change activity event source is all events that directly affect the configuration or operation of the node. Change events are generated by the USER application. The Change event stream also includes the tmnxConfigModify(#2006), tmnxConfigCreate (#2007), tmnxConfigDelete (#2008) and tmnxStateChange (#2009) change events from the SYSTEM application.
Debug
The debug event source is the debugging configuration that has been enabled on the system. Debug events are generated by the DEBUG application.
Main
The main event source receives events from all other applications within the 7210 SAS.
Examples of applications within 7210 SAS include IP, MPLS, OSPF, CLI, services, and so on.
The following output is an example of the show log applications command output, which displays all applications.
*A:ALU-7210# show log applications
==================================
Log Event Application Names
==================================
Application Name
----------------------------------
CHASSIS
DEBUG
DOT1AG
DOT1X
EFM_OAM
FILTER
IGMP
IP
LAG
LOGGER
MIRROR
NTP
OAM
PORT
QOS
SECURITY
SNMP
STP
SVCMGR
SYSTEM
TIP
TOD
USER
VRTR
==================================
*A:ALU-7210#
Event control
Event control preprocesses the events generated by applications before the event is passed into the main event stream. Event control assigns a severity to application events and can either forward the event to the main event source or suppress the event. Suppressed events are counted in event control, but these events will not generate log entries as it never reaches the log manager.
Simple event throttling is another method of event control and is configured similarly to the generation and suppression options. See Simple logger event throttling.
Events are assigned a default severity level in the system, but the application event severities can be changed by the user.
Application events contain an event number and description that describes why the event is generated. The event number is unique within an application, but the number can be duplicated in other applications.
The following example, generated by querying event control for application generated events, displays a partial list of event numbers and names.
router# show log event-control
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
CHASSIS:
2001 cardFailure MA gen 0 0
2002 cardInserted MI gen 2 0
2003 cardRemoved MI gen 0 0
2004 cardWrong MI gen 0 0
2005 EnvTemperatureTooHigh MA gen 0 0
2006 fanFailure CR gen 0 0
...
EFM_OAM:
2001 tmnxDot3OamPeerChanged MI gen 0 0
2002 tmnxDot3OamLoopDetected MI gen 0 0
2003 tmnxDot3OamLoopCleared MI gen 0 0
FILTER:
2001 tIPFilterPBRPacketsDrop WA gen 0 0
2002 tFilterEntryActivationFailed WA gen 0 0
2003 tFilterEntryActivationRestored WA gen 0 0
IGMP:
2001 vRtrIgmpIfRxQueryVerMismatch WA gen 0 0
2002 vRtrIgmpIfCModeRxQueryMismatch WA gen 0 0
2003 vRtrIgmpMaxGrpsLimitExceeded WA gen 0 0
2004 vRtrIgmpMcacPlcyDropped WA gen 0 0
IP:
L 2001 clearRTMError MI gen 0 0
L 2002 ipEtherBroadcast MI gen 0 0
L 2003 ipDuplicateAddress MI gen 0 0
L 2004 ipArpInfoOverwritten MI gen 0 0
L 2005 fibAddFailed MA gen 0 0
...
SYSTEM:
2001 stiDateAndTimeChanged WA gen 0 0
2002 ssiSaveConfigSucceeded MA gen 1 0
2003 ssiSaveConfigFailed CR gen 1 0
2004 sbiBootConfig MA gen 1 0
2005 sbiBootSnmpd MA gen 1 0
...
VRTR:
2001 tmnxVRtrMidRouteTCA MI gen 0 0
2002 tmnxVRtrHighRouteTCA MI gen 0 0
2003 tmnxVRtrHighRouteCleared MI gen 0 0
...
=======================================================================
router#
Log manager and event logs
Events that are forwarded by event control are sent to the log manager. The log manager manages the event logs in the system and the relationships between the log sources, event logs and log destinations, and log filter policies.
An event log has the following properties:
a unique log ID
The log ID is a short, numeric identifier for the event log. A maximum of ten logs can be configured at a time.
one or more log sources
The source stream or streams to be sent to log destinations can be specified. The source must be identified before the destination can be specified. The events can be from the main event stream, events in the security event stream, or events in the user activity stream.
one event log destination
A log can only have a single destination. The destination for the log ID destination can be one of console, session, syslog, snmp-trap-group, memory, or a file on the local file system.
an optional event filter policy
An event filter policy defines whether to forward or drop an event or trap-based on match criteria.
Event filter policies
The log manager uses event filter policies to allow fine control over which events are forwarded or dropped based on various criteria. Like other policies with the 7210 SAS, filter policies have a default action. The default actions are either:
Forward
Drop
Filter policies also include a number of filter policy entries that are identified with an entry ID and define specific match criteria and a forward or drop action for the match criteria.
Each entry contains a combination of matching criteria that define the application, event number, router, severity, and subject conditions. The entry action determines how the packets should be treated if they have met the match criteria.
Entries are evaluated in order from the lowest to the highest entry ID. The first matching event is subject to the forward or drop action for that entry.
Valid operators are described in the following table.
| Operator | Description |
|---|---|
eq |
equal to |
neq |
not equal to |
lt |
less than |
lte |
less than or equal to |
gt |
greater than |
gte |
greater than or equal to |
A match criteria entry can include combinations of:
equal to or not equal to a specific system application
equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to an event number within the application
equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to a severity level
equal to or not equal to a router name string or regular expression match
equal to or not equal to an event subject string or regular expression match
Event log entries
Log entries that are forwarded to a destination are formatted in a way appropriate for the specific destination whether it be recorded to a file or sent as an SNMP trap, but log event entries have common elements or properties. All application generated events have the following properties:
a time stamp in UTC or local time
the generating application
a unique event ID within the application
a router name identifying the VRF-ID that generated the event
a subject identifying the affected object
a short text description
The general format for an event in an event log with either a memory, console or file destination is as follows.
nnnn YYYY/MM/DD HH:MM:SS.SS <severity>:<application> # <event_id> <router-
name> <subject> description
Event log
475 2006/11/27 00:19:40.38 WARNING: SNMP #2007 Base 1/1/1
"interface 1/1/1 came up"
The specific elements that compose the general format are described in the following table.
| Label | Description |
|---|---|
|
nnnn |
The log entry sequence number. |
|
YYYY/MM/DD |
The UTC date stamp for the log entry. YYYY - Year MM - Month DD - - Date |
|
HH:MM:SS.SS |
The UTC time stamp for the event. HH - Hours (24 hour format) MM - Minutes SS.SS - Seconds |
|
<severity> |
The severity level name of the event. CLEARED - a cleared event (severity number 1) INFO - an indeterminate/informational severity event (severity level 2) CRITICAL - a critical severity event (severity level 3) MAJOR - a major severity event (severity level 4) MINOR - a minor severity event (severity level 5) WARNING - a warning severity event (severity 6) |
|
<application> |
The application generating the log message. |
|
<event_id> |
The application event ID number for the event. |
|
<router> |
The router name representing the VRF-ID that generated the event. |
|
<subject> |
The subject/affected object for the event. |
|
<description> |
A text description of the event. |
Simple logger event throttling
Simple event throttling provides a mechanism to protect event receivers from being overloaded when a scenario causes many events to be generated in a very short period of time. A throttling rate, # events/# seconds, can be configured. Specific event types can be configured to be throttled. When the throttling event limit is exceeded in a throttling interval, any further events of that type cause the dropped events counter to be incremented. Dropped events counts are displayed by the show>log>event-control context. Events are dropped before being sent to one of the logger event collector tasks. There is no record of the details of the dropped events and therefore no way to retrieve event history data lost by this throttling method.
A particular event type can be generated by multiple managed objects within the system. At the point this throttling method is applied the logger application has no information about the managed object that generated the event and cannot distinguish between events generated by object ‟A” from events generated by object ‟B”. If the events have the same event-id, they are throttled regardless of the managed object that generated them. It also does not know which events may eventually be logged to destination log-id <n> from events that will be logged to destination log-id <m>.
Throttle rate applies commonly to all event types. It is not configurable for a specific event-type.
A timer task checks for events dropped by throttling when the throttle interval expires. If any events have been dropped, a TIMETRA-SYSTEM-MIB::tmnxTrapDropped notification is sent.
Default system log
Log 99 is a preconfigured memory-based log which logs events from the main event source (not security, debug, and so on). Log 99 exists by default.
Log 99 configuration output
ALA-1>config>log# info detail
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
...
snmp-trap-group 7
exit
...
log-id 99
description "Default system log"
no filter
from main
to memory 500
no shutdown
exit
----------------------------------------------
ALA-1>config>log#
Accounting logs
Before an accounting policy can be created, a target log file must be created to collect the accounting records. The files are stored in system memory on compact flash (cf1:) in compressed (.tar) XML format and can be retrieved using FTP or SCP.
A file ID can only be assigned to either one event log ID or one accounting log.
Accounting records
An accounting policy must define a record name and collection interval. Only one record name can be configured per accounting policy. Also, a record name can only be used in one accounting policy.
The record name, sub-record types, and default collection period for access and network accounting policies are shown as follows.
The 7210 SAS provides 21 accounting records for the following accounting policies:
access
accessport
network
networkIf
sdp
When creating accounting policies, only one (of each) access, accessport, network, networkIf and sdp accounting policy can be defined as default. If statistics collection is enabled on an accounting object and no accounting policy is applied, the default accounting policy is used. If a default policy is not defined, no statistics are collected unless a specifically defined accounting policy is applied.
Each accounting record name is composed of one or more sub-records composed of multiple fields.
For VLL and VPLS services on the 7210 SAS, the user can run the config>service>epipe/vpls>sap>statistics>ingress>counter-mode {in-out-profile-count | forward-drop-count} to change the counter-mode of counters associated with SAP ingress meters or policers. See the 7210 SAS-Mxp, S, Sx, T Services Guide and 7210 SAS-R6, R12 Services Guide for more information about the counter-mode command.
The statistics collected for the following accounting records vary based on the counter-mode selected:
Service-ingress-octets
Service-ingress-packets
Combined-service-ingress
Complete-service-ingress-egress
See Appendix: accounting record name details for 7210 SAS platforms for more information about accounting records and counters for the 7210 SAS platforms.
Configuration guidelines
Before modifying the counter, disable account log generation. Execute the no collect-stats command. Changing the mode of the counter results in loss of previously collected counts and resets the counter.
Accounting files
When a policy has been created and applied to a service or network port, the accounting file is stored on the compact flash in a compressed XML file format. The device creates two directories on the compact flash to store the files.
The following output displays a directory named act-collect that holds accounting files that are open and actively collecting statistics. The directory named act stores the files that have been closed and are awaiting retrieval.
ALA-1>file cf1:\# dir act*
12/19/2006 06:08a <DIR> act-collect
12/19/2006 06:08a <DIR> act
ALA-1>file cf1:\act-collect\ # dir
Directory of cf1:\act-collect#
12/23/2006 01:46a <DIR> .
12/23/2006 12:47a <DIR> ..
12/23/2006 01:46a 112 act1111-20031223-014658.xml.gz
12/23/2006 01:38a 197 act1212-20031223-013800.xml.gz
Accounting files always have the prefix act followed by the accounting policy ID, log ID and timestamp. The accounting log file naming and log file destination properties like rollover and retention are described in more detail in Log files.
Design considerations
When preparing for an accounting policy deployment, verify that data collection, file rollover, and file retention intervals are properly tuned for the amount of statistics to be collected.
If the accounting policy collection interval is too brief, there may be insufficient time to store the data from all the services within the specified interval. If that is the case, some records may be lost or incomplete. Interval time, record types, and number of services using an accounting policy are all factors that should be considered when implementing accounting policies.
The rollover and retention intervals on the log files and the frequency of file retrieval must also be considered when designing accounting policy deployments. The amount of data stored depends on the type of record collected, the number of services that are collecting statistics, and the collection interval that is used.
Configuration notes
This following information describes logging configuration restrictions:
A file or filter cannot be deleted if it has been applied to a log.
File IDs, syslog IDs, or SNMP trap groups must be configured before they can be applied to a log ID.
A file ID can only be assigned to either one log ID or one accounting policy.
Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
The snmp-trap-id must be the same as the log-id.
Configuring logging with CLI
This section provides information to configure logging using the command line interface.
Log configuration overview
Configure logging parameters to save information in a log file or direct the messages to other devices. Logging does the following:
provides you with logging information for monitoring and troubleshooting
allows you to select the types of logging information to be recorded
allows you to assign a severity to the log messages
allows you to select the source and target of logging information
Log types
Logs can be configured in the following contexts:
Log file
Log files can contain log event message streams or accounting/billing information. Log file IDs are used to direct events, alarms/traps and debug information to their respective targets.
SNMP trap groups
SNMP trap groups contain an IP address and community names which identify targets to send traps following specified events.
Syslog
Information can be sent to a syslog host that is capable of receiving selected syslog messages from a network element.
Event control
Configures a particular event or all events associated with an application to be generated or suppressed.
Event filters
An event filter defines whether to forward or drop an event or trap based on match criteria.
Accounting policies
An accounting policy defines the accounting records that will be created. Accounting policies can be applied to one or more s access object or network objects.
Event logs
An event log defines the types of events to be delivered to its associated destination.
Event throttling rate
Defines the rate of throttling events.
Basic event log configuration
The most basic log configuration must have the following:
log ID or accounting policy ID
a log source
a log destination
Configuration output
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
event-control 2001 generate critical
file-id 1
description "This is a test file-id."
location cf1:
exit
file-id 2
description "This is a test log."
location cf1:
exit
snmp-trap-group 7
trap-target 11.22.33.44 "snmpv2c" notify-community "public"
exit
log-id 2
from main
to file 2
exit
----------------------------------------------
A:ALA-12>config>log#
Common configuration tasks
The following sections are basic system tasks that must be performed.
Configuring an event log
A event log file contains information used to direct events, alarms, traps, and debug information to their respective destinations. One or more event sources can be specified. File IDs, SNMP trap groups, or syslog IDs must be configured before they can be applied to an event log ID.
Use the following syntax to configure a log file.
config>log
log-id log-id
description description-string
filter filter-id
from {[main] [security] [change] [debug-trace]}
to console
to file file-id
to memory [size]
to session
to snmp [size]
to syslog syslog-id}
time-format {local|utc}
no shutdown
Log file configuration output
ALA-12>config>log>log-id# info
----------------------------------------------
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
ALA-12>config>log>log-id#
Configuring a file ID
To create a log file, a file ID is defined, the target CF or USB drive is specified, and the rollover retention interval period for the log file is defined. The rollover interval is defined in minutes and determines how long a file will be used before it is closed and a new log file is created. The retention interval determines how long the file will be stored on the storage device before it is deleted.
Use the following syntax to configure a log file.
config>log
file-id log-file-id
description description-string
location cflash-id
rollover minutes [retention hours]
For the 7210 SAS-T:
config>log
file-id log-file-id
description description-string
location cflash|usb-flash-id [backup-cflash-id]
rollover minutes [retention hours]
Log file configuration output
A:ALA-12>config>log# info
------------------------------------------
file-id 1
description "This is a log file."
location cf1:
rollover 600 retention 24
exit
----------------------------------------------
A:ALA-12>config>log#
Configuring an accounting policy
Before an accounting policy can be created a target log file must be created to collect the accounting records. The files are stored in system memory of compact flash (cf1:) in a compressed (.tar) XML format and can be retrieved using FTP or SCP. See Configuring an event log and Configuring a file ID.
Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
The default accounting policy statement cannot be applied to LDP nor RSVP statistics collection records.
An accounting policy must define a record type and collection interval. Only one record type can be configured per accounting policy.
When creating accounting policies, one access, one access port, one network, one network interface and one SDP accounting policy can be defined as default. If statistics collection is enabled on an accounting object, and no accounting policy is applied, then the respective default accounting policy is used. If no default policy is defined, then no statistics are collected unless a specifically-defined accounting policy is applied.
Use the following syntax to configure an accounting policy.
config>log>
accounting-policy acct-policy-id interval minutes
description description-string
default
record record-name
to file log-file-id
no shutdown
Accounting policy configuration output
A:ALA-12>config>log# info
----------------------------------------------
accounting-policy 5
description "This is a test accounting policy."
record service-ingress-packets
to file 3
exit
----------------------------------------------
A:ALA-12>config>log#
Configuring event control
Use the following CLI syntax to configure event control. Note that the throttle parameter used in the event-control command syntax enables throttling for a specific event type. The config>log>throttle-rate command configures the number of events and interval length to be applied to all event types that have throttling enabled by this event-control command.
config>log
event-control application-id [event-name|event-number] generate [severity-level] [throttle]
event-control application-id [event-name|event-number] suppress
throttle-rate events [interval seconds]
Event control configuration output
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration"
#------------------------------------------
throttle-rate 500 interval 10
event-control "oam" 2001 generate throttle
event-control "ospf" 2001 suppress
event-control "ospf" 2003 generate cleared
event-control "ospf" 2014 generate critical
..
----------------------------------------------
A:ALA-12>config>log>filter#
Configuring throttle rate
This command configures the number of events and interval length to be applied to all event types that have throttling enabled by the event-control command.
Use the following syntax to configure the throttle rate.
config>log#
throttle-rate events [interval seconds]
Throttle rate configuration output
*A:gal171>config>log# info
---------------------------------------------
throttle-rate 500 interval 10
event-control "aps" 2001 generate throttle
----------------------------------------------
Configuring a log filter
Use the following syntax to configure a log filter.
config>log
filter filter-id
default-action {drop|forward}
description description-string
entry entry-id
action {drop|forward}
description description-string
match
application {eq|neq} application-id
number {eq|neq|lt|lte|gt|gte} event-id
router {eq|neq} router-instance [regexp]
severity {eq|neq|lt|lte|gt|gte} severity-level
subject {eq|neq} subject [regexp]
Log filter configuration output
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
file-id 1
description "This is our log file."
location cf1:
rollover 600 retention 24
exit
filter 1
default-action drop
description "This is a sample filter."
entry 1
action forward
match
application eq "mirror"
severity eq critical
exit
exit
exit
...
log-id 2
shutdown
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
------------------------------------------
A:ALA-12>config>log#
Configuring an SNMP trap group
The associated log-id does not have to be configured before an snmp-trap-group can be created; however, the snmp-trap-group must exist before the log-id can be configured to use it.
Use the following syntax to configure an SNMP trap group.
config>log
snmp-trap-group log-id
trap-target name [address ip-address] [port port] [snmpv1|snmpv2c| snmpv3] notify-community communityName |snmpv3SecurityName [security-level {no-auth-no-privacy|auth-no-privacy|privacy}]
SNMP trap group configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 2
trap-target 10.10.10.104:5 "snmpv3" notify-community "coummunitystring"
exit
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Configuring SNMP dying gasp
SNMP dying gasp for IPv4 is supported on all 7210 SAS platforms as described in this document, except the 7210 SAS-R6 and 7210 SAS-R12.
SNMP dying gasp for IPv6 is not supported on any of the 7210 SAS platforms.
Use the following syntax to configure SNMP dying gasp.
config>log
no snmp-dying-gasp primary trap-target-group-num trap-target-name [secondary {trap-target-group-num trap-target-name} [tertiary {trap-target-group-num trap-target-name}]]
*A:Dut-A>config>log# snmp-dying-gasp primary 7 server1 secondary 8 server2
*A:Dut-A>config>log# info
----------------------------------------------
snmp-trap-group 7
trap-target "server1" address 10.1.1.1 snmpv2c notify-community "public"
exit
snmp-trap-group 8
trap-target "server2" address 10.135.2.10 snmpv3 notify-
community "snmpv3user" security-level auth-no-privacy
exit
snmp-trap-group 9
trap-target "server3" address 10.2.2.2 snmpv3 notify-
community "snmpv3user" security-level auth-no-privacy
exit
log-id 7
from main
to snmp
exit
log-id 8
from main
to snmp
exit
log-id 9
from main
to snmp
exit
snmp-dying-gasp primary 7 "server1" secondary 8 "server2"
----------------------------------------------
*A:Dut-A>config>log#
Configuration guidelines for SNMP dying gasp trap
The system does not try to resolve the ARP when it needs to send out the SNMP dying-gasp trap, since the amount of time available during power loss event is very less. Instead, the system assumes that ARP entry to the gateway used to reach the SNMP trap server is always available. Nokia recommends that users run a periodic ping query to the SNMP trap server in the background using the cron utility.
The following is a sample configuration output of a cron job which initiates a ping to the server mentioned in the pingscript file every one minute.
*7210-SAS># configure cron
*7210-SAS >config>cron# info
----------------------------------------------
time-range "NO-TIME-RANGE" create
description "NO-TIME-RANGE is the default always-on time-range"
exit
----------------------------------------------
7210SAS>config>cron#
Configuring a syslog target
Log events cannot be sent to a syslog target host until a valid syslog ID exists.
Use the following syntax to configure a syslog file.
config>log
syslog syslog-id
description description-string
address ip-address
log-prefix log-prefix-string
port port
level {emergency|alert|critical|error|warning|notice|info|debug}
facility syslog-facility
Syslog configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
syslog 1
description "This is a syslog file."
address 10.10.10.104
facility user
level warning
exit
...
----------------------------------------------
A:ALA-12>config>log#
Log management tasks
This section describes the logging tasks.
Modifying a log file
Use the following syntax to modify a log file.
config>log
log-id log-id
description description-string
filter filter-id
from {[main] [security] [change] [debug-trace]}
to console
to file file-id
to memory [size]
to session
to snmp [size]
to syslog syslog-id
Current log configuration output
ALA-12>config>log>log-id# info
----------------------------------------------
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
ALA-12>config>log>log-id#
Command usage to modify log file parameters
config# log
config>log# log-id 2
config>log>log-id# description "Chassis log file."
config>log>log-id# filter 2
config>log>log-id# from security
config>log>log-id# exit
Modified log file configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
log-id 2
description "Chassis log file."
filter 2
from security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a log file
The log ID must be shut down first before it can be deleted. In the previous example, "file 1" is associated with "log-id 2".
A:ALA-12>config>log# info
----------------------------------------------
file-id 1
description "LocationTest."
location cf1:
rollover 600 retention 24
exit
...
log-id 2
description "Chassis log file."
filter 2
from security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Use the following syntax to delete a log file.
config>log
no log-id log-id
shutdown
Command usage to delete a log file
config# log
config>log# log-id 2
config>log>log-id# shutdown
config>log>log-id# exit
config>log# no log-id 2
Modifying a file ID
When the file-id location parameter is modified, log files are not written to the new location until a rollover occurs or the log is manually cleared. A rollover can be forced by using the clear>log command. Subsequent log entries are then written to the new location. If a rollover does not occur or the log not cleared, the old location remains in effect.
The location can be CF (cflash-id) or USB (usb-flash-id).
Use the following syntax to modify a log file.
config>log
file-id log-file-id
description description-string
location [cflash-id]
rollover minutes [retention hours]
Current log configuration output
A:ALA-12>config>log# info
------------------------------------------
file-id 1
description "This is a log file."
location cf1:
rollover 600 retention 24
exit
----------------------------------------------
A:ALA-12>config>log#
Command usage to modify log file parameters
config# log
config>log# file-id 1
config>log>file-id# description "LocationTest."
config>log>file-id# rollover 2880 retention 500
config>log>file-id# exit
File modifications
A:ALA-12>config>log# info
----------------------------------------------
...
file-id 1
description "LocationTest."
location cf1:
rollover 2880 retention 500
exit
...
----------------------------------------------
Deleting a file ID
All references to the file ID must be deleted before the file ID can be removed.
Use the following syntax to delete a log ID.
config>log
no file-id log-file-id
Command usage to delete a file ID
config>log# no file-id 1
Modifying a syslog ID
All references to the syslog ID must be deleted before the syslog ID can be removed.
Use the following syntax to modify a syslog ID parameters.
config>log
syslog syslog-id
description description-string
address ip-address
log-prefix log-prefix-string
port port
level {emergency|alert|critical|error|warning|notice|info|debug}
facility syslog-facility
Command usage to modify syslog ID parameters
config# log
config>log# syslog 1
config>log>syslog$description "Test syslog."
config>log>syslog# address 10.10.0.91
config>log>syslog# facility mail
config>log>syslog# level info
Syslog configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
syslog 1
description "Test syslog."
address 10.10.10.91
facility mail
level info
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a syslog
Use the following syntax to delete a syslog file.
config>log
no syslog syslog-id
Command usage to delete a syslog ID
config# log
config>log# no syslog 1
Modifying an SNMP trap group
Use the following syntax to modify an SNMP trap group.
config>log
snmp-trap-group log-id
trap-target name [address ip-address] [port port] [snmpv1|snmpv2c| snmpv3] notify-community communityName |snmpv3SecurityName [security-level {no-auth-no-privacy|auth-no-privacy|privacy}]
Current SNMP trap group configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.10.104:5 "snmpv3" notify-community "coummunitystring"
exit
...
----------------------------------------------
A:ALA-12>config>log#
Command usage to modify an SNMP trap group
config# log
config>log# snmp-trap-group 10
config>log>snmp-trap-group# no trap-target 10.10.10.104:5
config>log>snmp-trap-group# snmp-trap-group# trap-target 10.10.0.91:1 snmpv2c notify-community "com1"
SNMP trap group configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.0.91:1 "snmpv2c" notify-community "com1"
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting an SNMP trap group
Use the following syntax to delete a trap target and SNMP trap group.
config>log
no snmp-trap-group log-id
no trap-target name
SNMP trap group configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.0.91:1 "snmpv2c" notify-community "com1"
exit
...
----------------------------------------------
A:ALA-12>config>log#
Command usage to delete a trap target and SNMP trap group
config>log# snmp-trap-group 10
config>log>snmp-trap-group# no trap-target 10.10.0.91:1
config>log>snmp-trap-group# exit
config>log# no snmp-trap-group 10
Modifying a log filter
Use the following syntax to modify a log filter.
config>log
filter filter-id
default-action {drop|forward}
description description-string
entry entry-id
action {drop|forward}
description description-string
match
application {eq|neq} application-id
number {eq|neq|lt|lte|gt|gte} event-id
router {eq|neq} router-instance [regexp]
severity {eq|neq|lt|lte|gt|gte} severity-level
subject {eq|neq} subject [regexp]
Current log filter configuration output
ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
...
filter 1
default-action drop
description "This is a sample filter."
entry 1
action forward
match
application eq "mirror"
severity eq critical
exit
exit
exit
...
------------------------------------------
ALA-12>config>log#
Command usage to modify the log filter
config# log
config>log# filter 1
config>log>filter# description "This allows <n>."
config>log>filter# default-action forward
config>log>filter# entry 1
config>log>filter>entry$ action drop
config>log>filter>entry# match
config>log>filter>entry>match# application eq user
config>log>filter>entry>match# number eq 2001
config>log>filter>entry>match# no severity
config>log>filter>entry>match# exit
Sample log filter configuration output
A:ALA-12>config>log>filter# info
----------------------------------------
...
filter 1
description "This allows <n>."
entry 1
action drop
match
application eq "user"
number eq 2001
exit
exit
exit
...
----------------------------------------
A:ALA-12>config>log>filter#
Deleting a log filter
Use the following syntax to delete a log filter.
config>log
no filter filter-id
Current log filter configuration output
A:ALA-12>config>log>filter# info
----------------------------------------
...
filter 1
description "This allows <n>."
entry 1
action drop
match
application eq "user"
number eq 2001
exit
exit
exit
...
----------------------------------------
A:ALA-12>config>log>filter#
Command usage to delete a log filter
config>log# no filter 1
Modifying event control parameters
Use the following syntax to modify event control parameters.
config>log
event-control application-id [event-name|event-number] generate [severity-level] [throttle]
event-control application-id [event-name|event-number] suppress
Current event control configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
event-control 2014 generate critical
...
----------------------------------------------
A:ALA-12>config>log#
Command usage to modify event control
config# log
config>log# event-control 2014 suppress
Log filter configuration output
A:ALA-12>config>log# info
----------------------------------------------
...
event-control 2014 suppress
...
----------------------------------------------
A:ALA-12>config>log#
Returning to the default event control configuration
The no form of the event-control command returns modified values back to the default values.
Use the following syntax to modify event control parameters.
config>log
no event-control application-id [event-name |event-nunmber]
Command usage to return to default values
config# log
config>log# no event-control 2001
config>log# no event-control 2002
config>log# no event-control 2014
Configuration output
A:ALA-12>config>log# info detail
----------------------------------------------
#------------------------------------------
echo "Log Configuration"
#------------------------------------------
event-control 2001 generate minor
event-control 2002 generate warning
event-control 2003 generate warning
event-control 2004 generate critical
event-control 2005 generate warning
event-control 2006 generate warning
event-control 2007 generate warning
event-control 2008 generate warning
event-control 2009 generate warning
event-control 2010 generate warning
event-control 2011 generate warning
event-control 2012 generate warning
event-control 2013 generate warning
event-control 2014 generate warning
event-control 2015 generate critical
event-control 2016 generate warning
...
----------------------------------------------
A:ALA-12>config>log#
Log command reference
Command hierarchies
Configuration commands
Event control commands
config
- log
- event-control application-id [event-name | event-number] [generate [severity-level] [throttle]
- event-control application-id [event-name | event-number] suppress
- no event-control application [event-name | event-number]
- route-preference primary {inband | outband} secondary {inband | outband | none}
- no route-preference
- throttle-rate events [interval seconds]
- no throttle-rate
Accounting policy commands
config
- log
- accounting-policy acct-policy-id
- no accounting-policy acct-policy-id
- [no] default
- collection-interval minutes
- [no] collection-interval
- description description-string
- no description
- [no] log-memory
- record record-name
- no record
- [no] shutdown
- [no] to file log-file-id
File ID commands
config
- log
- [no] file-id log-file-id
- description description-string
- no description
- location cflash-id | usb-flash-id [backup-cflash-id]
- no location
- rollover minutes [retention hours]
- no rollover
Event filter commands
config
- log
- [no] filter filter-id
- default-action {drop | forward}
- no default-action
- description description-string
- no description
- [no] entry entry-id
- action {drop | forward}
- no action
- description description-string
- no description
- [no] match
- application {eq | neq} application-id
- no application
- number {eq | neq | lt | lte | gt | gte} event-id
- no number
- router {eq | neq} router-instance [regexp]
- no router
- severity {eq | neq | lt | lte | gt | gte} severity-level
- no severity
- subject {eq | neq} subject [regexp]
- no subject
Log ID commands
config
- log
- [no] log-id log-id
- description description-string
- no description
- filter filter-id
- no filter
- from {[main] [security] [change] [debug-trace]}
- no from
- [no] shutdown
- time-format {local | utc}
- to console
- to file log-file-id
- to memory [size]
- to session
- to snmp [size]
- to syslog syslog-id
SNMP trap group commands
config
- log
- [no] snmp-trap-group log-id
- description description-string
- no description
- trap-target name [address ip-address] [port port] [snmpv1 | snmpv2c | snmpv3] notify-community communityName | snmpv3SecurityName [security-level {no-auth-no-privacy | auth-no-privacy | privacy} [replay]]
- no trap-target name
- [no] snmp-dying-gasp primary trap-target-group-num trap-target-name [secondary {trap-target-group-num trap-target-name} [tertiary {trap-target-group-num trap-target-name}]]
Syslog commands
config
- log
- [no] syslog syslog-id
- address ip-address
- no address
- description description-string
- no description
- facility syslog-facility
- no facility
- level {emergency | alert | critical | error | warning | notice | info | debug}
- no level
- log-prefix log-prefix-string
- no log-prefix
- port port
- no port
Show commands
show
- log
- accounting-policy [acct-policy-id] [access | network]
- accounting-records
- applications
- event-control [application-id [event-name | event-number]]
- file-id [log-file-id]
- filter-id [filter-id]
- log-collector
- log-id [log-id] [severity severity-level] [application application] [sequence from-seq [to-seq]] [count count] [router router-instance [expression]] [subject subject [regexp]] [ascending | descending]
- snmp-trap-group [log-id]
- syslog [syslog-id]
Clear commands
clear
- log log-id
Tools dump commands
tools
- dump
- accounting-policy [id] flash-write-count [clear]
See the 7210 SAS-Mxp, R6, R12, S, Sx, T OAM and Diagnostics Guide for more information about the tools dump accounting-policy command.
Command descriptions
Configuration commands
Generic commands
description
Syntax
description string
no description
Context
config>log
config>log>file-id
config>log>log-id
config>log>filter
config>log>filter>entry
config>log>accounting-policy
config>log>syslog
config>log>snmp-trap-group
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command creates a text description stored in the configuration file for a configuration context. The description command associates a text string with a configuration context to help identify the content in the configuration file.
The no form of this command removes the string from the configuration.
Parameters
- string
Specifies a string of up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>log
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command administratively disables an entity. When disabled, an entity does not change, reset, or remove any configuration settings or statistics. The operational state of the entity is disabled as well as the operational state of any entities contained within. Many objects must be shut down before they may be deleted.
The no form of this command administratively enables an entity.
Default
no shutdown
Special Cases
- log-id
When a log-id is shut down, no events are collected for the entity. This leads to the loss of event data.
- accounting-policy
When an accounting policy is shut down, no accounting data is written to the destination log ID. Counters in the billing data reflect totals, not increments, so when the policy is re-enabled (no shutdown) the counters include the data collected during the period the policy was shut down.
Event control commands
event-control
Syntax
event-control application-id [event-name | event-number] [generate] [severity-level] [throttle]
event-control application-id [event-name | event-number] suppress
no event-control application [event-name | event-number]
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies that a particular event or all events associated with an application are either generated or suppressed.
Events are generated by an application and contain an event number and description of the cause of the event. Each event has a default designation that directs it to be generated or suppressed.
Events are generated with a default severity level that can be modified by using the severity-level option.
Events that are suppressed by default are typically used for debugging purposes. Events are suppressed at the time the application requests the event generation. No event log entry is generated, regardless of the destination. While this feature can save processor resources, there may be a negative effect on the ability to troubleshoot problems if the logging entries are squelched. However, the generation of too many events may cause excessive overhead.
The rate of event generation can be throttled using the throttle parameter.
The no form of this command reverts the parameters to the default setting for events for the application or a specific event within the application. The severity-level, generate, suppress, and throttle options will also be reset to the initial values.
Default
Each event has a set of default settings. To display a list of all events and the current configuration, use the event-control command.
Parameters
- application-id
Specifies the application whose events are affected by this event control filter.
- event-name | event-number
Specifies the event number or short name, which can generate, suppress, or revert to default for a single event. If no event number or name is specified, the command applies to all events in the application. To display a list of all event short names, use the event-control command.
- generate
Specifies that logger event is created when this event occurs. The generate keyword can be used with two optional parameters, severity-level and throttle.
- severity-name
Specifies an ASCII string representing the severity level to associate with the specified generated events.
- throttle
Specifies whether or not events of this type will be throttled. By default, event throttling is on for most event types.
- suppress
Keyword to indicate that the specified events will not be logged. If the suppress keyword is not specified, the events are generated by default.
route-preference
Syntax
route-preference primary {inband | outband} secondary {inband | outband | none}
no route-preference
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the primary and secondary routing preference for traffic generated for SNMP notifications and syslog messages. If the remote destination is not reachable through the routing context specified by primary route preference, the secondary routing preference will be attempted.
The no form of this command reverts to the default values.
Default
no route-preference
Parameters
- primary
Specifies the primary routing preference for traffic generated for SNMP notifications and syslog messages.
- secondary
Specifies the secondary routing preference for traffic generated for SNMP notifications and syslog messages. The routing context specified by the secondary route preference will be attempted if the remote destination was not reachable by the primary routing preference, specified by primary route preference. The value specified for the secondary routing preference must be distinct from the value for primary route preference.
- inband
Specifies that the logging utility will attempt to use the base routing context to send SNMP notifications and syslog messages to remote destinations.
- outband
Specifies that the logging utility will attempt to use the management routing context to send SNMP notifications and syslog messages to remote destinations.
- none
Specifies that no attempt will be made to send SNMP notifications and syslog messages to remote destinations.
Log file commands
file-id
Syntax
[no] file-id log-file-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
Commands in this context configure a file ID template to be used as a destination for an event log or billing file.
This command defines the file location and characteristics to use as the destination for a log event message stream or accounting or billing information. The file defined in this context is subsequently specified in the to command under log-id or accounting-policy to direct specific logging or billing source streams to the file destination.
A file ID can only be assigned to either one log-id or one accounting-policy. It cannot be reused for multiple instances. A file ID and associated file definition must exist for each log and billing file that must be stored in the file system.
A file is created when the file ID defined in this command is selected as the destination type for a specific log or accounting record. Log files are collected in a ‟log” directory. Accounting files are collected in an ‟act” directory.
The system creates the filenames for a log, as summarized in the following table.
| File type | Filename |
|---|---|
Log file |
logllff-timestamp |
Accounting file |
actaaff-timestamp |
where:
ll is the log-id
aa is the accounting policy-id
ff is the file-id
The timestamp is the actual timestamp when the file is created. The format for the timestamp is yyyymmdd-hhmmss where:
-
yyyy is the year (for example, 2016)
-
mm is the month number (for example, 12 for December)
-
dd is the day of the month (for example, 03 for the 3rd of the month)
-
hh is the hour of the day in 24 hour format (for example, 04 for 4 a.m.)
-
mm is the minutes (for example, 30 for 30 minutes past the hour)
-
ss is the number of seconds (for example, 14 for 14 seconds)
-
The accounting file is compressed and has a gz extension.
When initialized, each file will contain:
the log-id description
the time the file was opened
the reason the file was created
the sequence number of the last event stored on the log is recorded, if the event log file was closed properly
If the process of writing to a log file fails (for example, the compact flash card is full) and if a backup location is not specified or fails, the log file will not become operational even if the compact flash card is replaced. Enter either a clear log command or a shutdown or no shutdown command to reinitialize the file.
If the primary location fails (for example, the compact flash card fills up during the write process), a trap is sent and logging continues to the specified backup location. This can result in truncated files in different locations.
The no form of this command removes the file-id from the configuration. A file-id can only be removed from the configuration if the file is not the designated output for a log destination. The actual file remains on the file system.
Parameters
- log-file-id
Specifies the file identification number, expressed as a decimal integer.
location
Syntax
location cflash-id | usb-flash-id [backup-cflash-id]
no location
Context
config>log>file-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the primary location where the log or billing file will be created.
When creating files, the primary location is used as long as there is available space. If no space is available, an attempt is made to delete unnecessary files that are past their retention date.
If sufficient space is not available, an attempt is made to remove the oldest to newest closed log or accounting files. After each file is deleted, the system attempts to create the new file.
A high priority alarm condition is raised if none of the configured compact flash devices for this file ID are present or if there is insufficient space available. If space becomes available, the alarm condition will be cleared.
The no form of this command reverts to default settings.
Default
log files are created on cf1: and accounting files are created on cf1:
Parameters
- cflash-id
Specifies the primary location.
- usb-flash-id
Specifies the USB location.
- backup-cflash-id
Specify the backup location.
rollover
Syntax
rollover minutes [retention hours]
no rollover
Context
config>log>file-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command configures how often an event or accounting log is rolled over or partitioned into a new file.
An event or accounting log is actually composed of multiple, individual files. The system creates a new file for the log based on the rollover time, expressed in minutes.
The retention option, expressed in hours, allows you to modify the default time to keep the file in the system. The retention time is based on the rollover time of the file.
When multiple rollover commands for a file-id are entered, the last command overwrites the previous command.
Default
rollover 1440 retention 12
Parameters
- minutes
Specifies the rollover time, in minutes.
- retention hours
Specifies the retention period in hours, expressed as a decimal integer. The retention time is based on the creation time of the file. The file becomes a candidate for removal when the creation datestamp + rollover time + retention time equals less than the current timestamp.
Log filter commands
filter
Syntax
[no] filter filter-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command enables the context for an event filter. An event filter specifies whether to forward or drop an event or trap based on the match criteria.
Filters are configured in the filter filter-id context and applied to a log in the log-id log-id context. Only events for the configured log source streams destined to the log ID where the filter is applied are filtered.
Changes made to an existing filter using any of the subcommands are immediately applied to the destinations where the filter is applied.
The no form of this command removes the filter association from log IDs, which causes those logs to forward all events.
Parameters
- filter-id
Specifies the filter ID uniquely identifies the filter.
default-action
Syntax
default-action {drop | forward}
no default-action
Context
config>log>filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies the action that is applied to events when no action is specified in the event filter entries or when an event does not match the specified criteria.
When multiple default-action commands are entered, the last command overwrites the previous command.
The no form of this command reverts to the default value.
Default
default-action forward
Parameters
- drop
Keyword to specify that the events that are not explicitly forwarded by an event filter match are dropped.
- forward
Keyword to specify that the events that are not explicitly dropped by an event filter match are forwarded.
Log filter entry commands
action
Syntax
action {drop | forward}
no action
Context
config>log>filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies a drop or forward action associated with the filter entry. If neither drop nor forward is specified, the default-action will be used for traffic that conforms to the match criteria. This could be considered a No-Op filter entry used to explicitly exit a set of filter entries without modifying previous actions.
When multiple action statements are entered, the last action will overwrite the previous actions.
The no form of this command removes the specified action statement.
Default
the action specified by the default-action command
Parameters
- drop
Keyword to specify that packets matching the entry criteria will be dropped.
- forward
Keyword to specify that packets matching the entry criteria will be forwarded.
entry
Syntax
[no] entry entry-id
Context
config>log>filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
Commands in this context create or edit an event filter entry. Multiple entries may be created using unique entry-id numbers. The -TiMOS implementation exits the filter on the first match found and executes the action in accordance with the action command.
Comparisons are performed in an ascending entry ID order. When entries are created, they should be arranged sequentially from the most explicit entry to the least explicit. Matching stops when a packet matches an entry. The entry action is performed on the packet, either drop or forward. To be considered a match, the packet must meet all the conditions defined in the entry.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action for it to be considered complete. Entries without the action keyword will be considered incomplete and are rendered inactive.
The no form of this command removes the specified entry from the event filter. Entries removed from the event filter are immediately removed from all log IDs where the filter is applied.
Parameters
- entry-id
Specifies the entry ID, which uniquely identifies a set of match criteria corresponding action within a filter. Entry ID values should be configured in staggered increments so you can insert a new entry in an existing policy without renumbering the existing entries.
Log filter entry match commands
match
Syntax
[no] match
Context
config>log>filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
Commands in this context create or edit match criteria for a filter entry. When the match criteria is satisfied, the action associated with the entry is executed.
If more than one match parameter (within one match statement) is specified, all criteria must be satisfied and functional before the action associated with the match is executed.
Use the application command to display a list of the valid applications.
Match context can consist of multiple match parameters (application, event-number, severity, subject), but multiple match statements cannot be entered per entry.
The no form of this command removes the match criteria for the entry-id.
application
Syntax
application {eq | neq} application-id
no application
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command adds a 7210 SAS application as an event filter match criterion.
A 7210 SAS application is the software entity that reports the event. Applications include IP, MPLS, OSPF, CLI, services, and others. Only one application can be specified. The latest application command overwrites the previous command.
The no form of this command removes the application as a match criterion.
Default
no application
Parameters
- eq | neq
The operator specifying the type of match. Valid operators are listed in the following table.
Table 6. Valid application operators Operator Notes eq equal to
neq not equal to
- application-id
Specifies the application name string.
number
Syntax
number {eq | neq | lt | lte | gt | gte} event-id
no number
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds a 7210 SAS application event number as a match criterion.
The 7210 SAS event numbers uniquely identify a specific logging event within an application.
Only one number command can be entered per event filter entry. The latest number command overwrites the previous command.
The no form of this command removes the event number as a match criterion.
Default
no event-number
Parameters
- eq | neq | lt | lte | gt | gte
Keyword to configure the operator that specifies the type of match. Valid operators are listed in the following table.
Table 7. Valid operators Operator Notes eq equal to
neq not equal to
lt less than
lte less than or equal to
gt greater than
gte greater than or equal to
- event-id
Specifies the event ID, expressed as a decimal integer.
router
Syntax
router {eq | neq} router-instance [regexp]
no router
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies the log event matches for the router.
Parameters
- eq
Determines if the matching criteria should be equal to the specified value.
- neq
Determines if the matching criteria should not be equal to the specified value.
- router-instance
Specifies a router name up to 32 characters to be used in the match criteria.
- regexp
Keyword to specify the type of string comparison to use to determine whether the log event matches the value of router command parameters. When the regexp keyword is specified, the string in the router command is a regular expression string that will be matched against the subject string in the log event being filtered.
severity
Syntax
severity {eq | neq | lt | lte | gt | gte} severity-level
no severity
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command adds an event severity level as a match criterion. Only one severity command can be entered per event filter entry. The latest severity command overwrites the previous command.
The no form of this command removes the severity match criterion.
Default
no severity
Parameters
- eq | neq | lt | lte | gt | gte
Keyword to configure the operator that specifies the type of match. Valid operators are listed in the following table.
Table 8. Valid operators Operator Notes eq equal to
neq not equal to
lt less than
lte less than or equal to
gt greater than
gte greater than or equal to
- severity-level
Specifies the ITU severity level name. The following table lists severity names and corresponding numbers per ITU standards M.3100 X.733 and X.21 severity levels.
Table 9. Severity levels Severity Number Severity Name 1
cleared
2
indeterminate (info)
3
critical
4
major
5
minor
6
warning
subject
Syntax
subject {eq | neq} subject [regexp]
no subject
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command adds an event subject as a match criterion.
The subject is the entity for which the event is reported, such as a port. In this case, the port-id string would be the subject. Only one subject command can be entered per event filter entry. The latest subject command overwrites the previous command.
The no form of this command removes the subject match criterion.
Default
no subject
Parameters
- eq | neq
Keyword to configure the operator that specifies the type of match. Valid operators are listed in the following table.
Table 10. Valid operators Operator Notes eq equal to
neg not equal to
- subject
Specifies a string used as the subject match criterion.
- regexp
Keyword to specify the type of string comparison to use to determine whether the log event matches the value of subject command parameters. When the regexp keyword is specified, the string in the subject command is a regular expression string that will be matched against the subject string in the log event being filtered.
When regexp keyword is not specified, the subject command string is matched exactly by the event filter.
Syslog commands
syslog
Syntax
[no] syslog syslog-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure a syslog target host that is capable of receiving selected syslog messages from this network element.
A valid syslog-id must have the target syslog host address configured.
A maximum of 10 syslog IDs can be configured.
No log events are sent to a syslog target address until the syslog-id has been configured as the log destination (to) in the log-id node.
Parameters
- syslog-id
Specifies the syslog ID number for the syslog destination, expressed as a decimal integer.
address
Syntax
address ip-address
no address
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds the syslog target host IP address to/from a syslog ID.
This parameter is mandatory. If no address is configured, syslog data cannot be forwarded to the syslog target host.
Only one address can be associated with a syslog-id. If multiple addresses are entered, the last address entered overwrites the previous address.
The same syslog target host can be used by multiple log IDs.
The no form of this command removes the syslog target host IP address.
Default
no address
Parameters
- ip-address
Specifies the IP address of the syslog target host in dotted-decimal notation.
facility
Syntax
facility syslog-facility
no facility
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command configures the facility code for messages sent to the syslog target host.
Multiple syslog IDs can be created with the same target host, but each syslog ID can only have one facility code. If multiple facility codes are entered, the last facility-code entered overwrites the previous facility-code.
If multiple facilities need to be generated for a single syslog target host, multiple log-id entries must be created, each with its own filter criteria to select the events to be sent to the syslog target host with a specific facility code.
The no form of this command reverts to the default value.
Default
facility local7
Parameters
- syslog-facility
Specifies the syslog facility name, which represents a specific numeric facility code. The code should be entered in accordance with the syslog RFC. However, the software does not validate if the facility code configured is appropriate for the event type being sent to the syslog target host.
log-prefix
Syntax
log-prefix log-prefix-string
no log-prefix
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command adds the string prepended to every syslog message sent to the syslog host.
RFC3164, The BSD syslog Protocol, allows a alphanumeric string (tag) to be prepended to the content of every log message sent to the syslog host. This alphanumeric string can, for example, be used to identify the node that generates the log entry. The software appends a colon (:) and a space to the string and it is inserted in the syslog message after the date stamp and before the syslog message content.
Only one string can be entered. If multiple strings are entered, the last string overwrites the previous string. The alphanumeric string can contain lowercase (a-z), uppercase (A-Z), and numeric (0-9) characters.
The no form of this command removes the log prefix string.
Default
no log-prefix
Parameters
- log-prefix-string
Specifies an alphanumeric string up to 32 characters. Spaces and colons cannot be used in the string.
level
Syntax
level syslog-level
no level
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command configures the syslog message severity level threshold. All messages with severity level equal to or higher than the threshold are sent to the syslog target host. Severity levels are shown in Threshold severity levels.
Only a single threshold level can be specified. If multiple levels are entered, the last level entered will overwrite the previously entered commands.
The no form of this command reverts to the default value.
Parameters
- value
The threshold severity level name.
port
Syntax
port port
no port
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the UDP port that will be used to send syslog messages to the syslog target host.
The port configuration is needed if the syslog target host uses a port other than the standard UDP syslog port 514.
Only one port can be configured. If multiple port commands are entered, the last entered port overwrites the previously entered ports.
The no form of this command reverts to default value.
Default
no port
Parameters
- port
Specifies the configured UDP port number used when sending syslog messages.
throttle-rate
Syntax
throttle-rate events [interval seconds]
no throttle-rate
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command configures an event throttling rate.
Parameters
- events
Specifies the number of log events that can be logged within the specified interval for a specific event. When the limit has been reached, any additional events of that type will be dropped, for example, the event drop count will be incremented. At the end of the throttle interval, if any events have been dropped a trap notification will be sent.
- seconds
Specifies the number of seconds that an event throttling interval lasts.
SNMP trap group commands
snmp-trap-group
Syntax
[no] snmp-trap-group log-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure a group of SNMP trap receivers and their operational parameters for a specific log-id.
A group specifies the types of SNMP traps and specifies the log ID that will receive the group of SNMP traps. A trap group must be configured for SNMP traps to be sent.
To suppress the generation of all alarms and traps, see the event-control command. To suppress alarms and traps that are sent to this log-id, see the filter command. When alarms and traps are generated, they can be directed to one or more SNMP trap groups. Logger events that can be forwarded as SNMP traps are always defined on the main event source.
The no form of this command deletes the SNMP trap group.
Parameters
- log-id
Specifies the log ID value of a log configured in the log-id context. Alarms and traps cannot be sent to the trap receivers until a valid log-id exists.
snmp-dying-gasp
Syntax
snmp-dying-gasp primary trap-target-group-num trap-target-name [secondary {trap-target-group-num trap-target-name} [tertiary {trap-target-group-num trap-target-name}]]
no snmp-dying-gasp
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command notifies the SNMP trap server about node power failure. On power failure, the system sends dying gasp traps to the configured SNMP trap servers. Up to three SNMP trap servers can be configured to receive the trap. The traps are sent in the following order:
primary SNMP trap receiver
secondary SNMP trap receiver
tertiary SNMP trap receiver
When this command is enabled, the node does not generate EFM OAM dying gasp messages even if EFM OAM is enabled. That is, the generation of an SNMP dying gasp trap is mutually exclusive to the use of the EFM OAM dying gasp message.
By default, the system generates an EFM OAM dying gasp message to remain compatible with earlier version of the software releases. The user must explicitly configure the system to send an SNMP trap on loss of power to the node using this command.
Typically, SNMP traps are generated only if the user configures a log to direct the system log events to SNMP. For the SNMP dying gasp trap, it is not required to do so. The DSCP value used by an SNMP dying gasp packet is AF (Assured Forwarding class, value 22).
The no form of this command disables the generation of an SNMP trap message. It enables the generation of an EFM OAM dying gasp on access-uplink ports if EFM OAM is enabled on those ports. Generation of a SNMP dying gasp trap is disabled by default.
The system IP address must be configured. The node uses it to generate the dying gasp traps. If It is not configured SNMP dying gasp traps are not generated.
When sending out SNMP dying gasp traps, one of the available routes in either the management routing instance or the base routing instance is used to resolve the next-hop gateway IP address to reach the trap-server destinations configured under primary, secondary, and tertiary trap targets. The route to the destination is always searched first in the management routing instance and, if not found, the routes in the base routing instance are looked up. Configuration of the route preference does not change this behavior (that is, the order of route lookup does not change).
Parameters
- primary trap-target-group-num
Specifies the trap target group number for the primary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap group configurations under config log snmp-trap-group trap-num.
- primary trap-target-name
Specifies the trap target name, up to 28 characters, for the primary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-name must correspond to one of the SNMP trap receiver targets configured under config log snmp-trap-group trap-num trap-target target-name.
- secondary trap-target-group-num
Specifies the trap target group number for the secondary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap group configurations under config log snmp-trap-group trap-num.
- secondary trap-target-name
Specifies the trap target name, up to 28 characters, for the secondary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-name must correspond to one of the SNMP trap receiver targets configured under config log snmp-trap-group trap-num trap-target target-name.
- tertiary trap-target-group-num
Specifies the trap target group number for the tertiary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap group configurations under config log snmp-trap-group trap-num.
- tertiary trap-target-name
Specifies the trap target name, up to 28 characters, for the tertiary SNMP trap receiver to which the system will address the SNMP trap. The trap-target-name must correspond to one of the SNMP trap receiver targets configured under config log snmp-trap-group trap-num trap-target target-name.
trap-target
Syntax
trap-target name [address ip-address] [port port] [snmpv1 | snmpv2c | snmpv3] notify-community communityName | snmpv3SecurityName [security-level {no-auth-no-privacy | auth-no-privacy | privacy}] [replay]
no trap-target name
Context
config>log>snmp-trap-group
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command creates or edits a trap receiver and configures the operational parameters for the trap receiver. A trap reports significant events that occur on a network device such as errors or failures.
Before an SNMP trap can be issued to a trap receiver, the log-id, snmp-trap-group and at least one trap-target must be configured.
The trap-target command is used to add or remove a trap receiver from an snmp-trap-group. The operational parameters specified in the command include the following:
IP address of the trap receiver
UDP port used to send the SNMP trap
SNMP version
SNMP community name for SNMPv1 and SNMPv2c receivers
security name and level for SNMPv3 trap receivers
A single snmp-trap-group log-id can have multiple trap receivers. Each trap receiver can have different operational parameters.
An address can be configured as a trap receiver more than once as long as a different port is used for each instance.
To prevent resource limitations, only configure a maximum of 10 trap receivers.
If the same trap-target name port port parameter value is specified in more than one SNMP trap group, each trap destination should be configured with a different notify-community value. This allows a trap receiving an application, such as NMS, to reconcile a separate event sequence number stream for each 7210 SAS event log when multiple event logs are directed to the same IP address and port destination.
The no form of this command removes the SNMP trap receiver from the SNMP trap group.
Parameters
- name
Specifies the name of the trap target, up to 28 characters.
- ip-address
Specifies the IP address of the trap receiver in dotted-decimal notation. Only one IP address destination can be specified per trap destination group.
- port
The destination UDP port used for sending traps to the destination, expressed as a decimal integer. Only one port can be specified per trap-target statement. If multiple traps need to be issued to the same address, multiple ports must be configured.
- snmpv1 | snmpv2c | snmpv3
Specifies the SNMP version format to use for traps sent to the trap receiver.
The keyword snmpv1 selects the SNMP version 1 format. When specifying snmpv1, the notify-community must be configured for the correct SNMP community string that the trap receiver expects to be present in alarms and traps messages. If the SNMP version is changed from snmpv3 to snmpv1, then the notify-community parameter must be changed to reflect the community string rather than the security-name that is used by snmpv3.
The keyword snmpv2c selects the SNMP version 2c format. When specifying snmpv2c, the notify-community must be configured for the correct SNMP community string that the trap receiver expects to be present in alarms and traps messages. If the SNMP version is changed from snmpv3 to snmpv2c, then the notify-community parameter must be changed to reflect the community string rather than the security-name that is used by snmpv3.
The keyword snmpv3 selects the SNMP version 3 format. When specifying snmpv3, the notify-community must be configured for the SNMP security-name. If the SNMP version is changed from snmpv1 or snmpv2c to snmpv3, then the notify-community parameter must be changed to reflect the security-name rather than the community string used by snmpv1 or snmpv2c.
The following preexisting conditions are checked before the snmpv3SecurityName is accepted.
The username must be configured.
The v3 access group must be configured.
The v3 notification view must be configured.
- notify-community communityName | snmpv3SecurityName
Specifies the community string for snmpv1 or snmpv2c or the snmpv3 security-name. If no notify-community is configured, then no alarms nor traps will be issued for the trap destination. If the SNMP version is modified, the notify-community must be changed to the correct form for the SNMP version.
- community
The community string as required by the snmpv1 or snmpv2c trap receiver. The community string can be an ASCII string up to 31 characters.
- security-name
The security-name as defined in the config>system>security>user context for SNMP v3. The security-name can be an ASCII string up to 31 characters.
- security-level {no-auth-no-privacy | auth-no-privacy | privacy}
Specifies the required authentication and privacy levels required to access the views configured on this node when configuring an snmpv3 trap receiver.
The keyword no-auth-no-privacy specifies no authentication and no privacy (encryption) are required.
The keyword auth-no-privacy specifies authentication is required but no privacy (encryption) is required. When this option is configured the security-name must be configured for authentication.
The keyword privacy specifies both authentication and privacy (encryption) is required. When this option is configured the security-name must be configured for authentication and privacy.
- replay
Enables replay of missed events to target. If replay is applied to an SNMP trap target address, the address is monitored for reachability. Reachability is determined by whether or not there is a route in the routing table by which the target address can be reached. Before sending a trap to a target address, the SNMP module asks the PIP module if there is either an in-band or out-of-band route to the target address. If there is no route to the SNMP target address, the SNMP module saves the sequence-id of the first event that will be missed by the trap target. When the routing table changes again so that there is now a route by which the SNMP target address can be reached, the SNMP module replays (for example, retransmits) all events generated to the SNMP notification log while the target address was removed from the route table.
Note:The route table changes the convergence time, so it is possible that one or more events may be lost at the beginning or end of a replay sequence.
Logging destination commands
filter
Syntax
filter filter-id
no filter
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds an event filter policy with the log destination.
The filter command is optional. If no event filter is configured, all events, alarms, and traps generated by the source stream will be forwarded to the destination.
An event filter policy defines (limits) the events that are forwarded to the destination configured in the log-id. The event filter policy can also be used to select the alarms and traps to be forwarded to a destination snmp-trap-group.
The application of filters for debug messages is limited to application and subject only.
Accounting records cannot be filtered using the filter command.
Only one filter-id can be configured per log destination.
The no form of this command removes the specified event filter from the log-id.
Default
no filter
Parameters
- filter-id
The event filter policy ID is used to associate the filter with the log-id configuration. The event filter policy ID must already be defined in config>log>filter filter-id.
from
Syntax
from {[main] [security] [change] [debug-trace]}
no from
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the source stream to be sent to a log destination.
One or more source streams must be specified. The source of the data stream must be identified using the from command before you can configure the destination using the to command. The from command can identify multiple source streams in a single statement (for example: from main change debug-trace).
Only one from command may be entered for a single log-id. If multiple from commands are configured, then the last command entered overwrites the previous from command.
The no form of this command removes all previously configured source streams.
Parameters
- main
Keyword to instruct all events in the main event stream to be sent to the destination defined in the to command for this destination log-id. The main event stream contains the events that are not explicitly directed to any other event stream. To limit the events forwarded to the destination, configure filters using the filter command.
- security
Keyword to instruct all events in the security event stream to be sent to the destination defined in the to command for this destination log-id. The security stream contains all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access, or attempts to enter a branch of the CLI to which access has not been granted. To limit the events forwarded to the destination, configure filters using the filter command.
- change
Keyword to instructs all events in the user activity stream to be sent to the destination configured in the to command for this destination log-id. The change event stream contains all events that directly affect the configuration or operation of this node. To limit the events forwarded to the change stream destination, configure filters using the filter command.
- debug-trace
Keyword to instruct all debug-trace messages in the debug stream to be sent to the destination configured in the to command for this destination log-id. Filters applied to debug messages are limited to application and subject.
log-id
Syntax
[no] log-id log-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
Commands in this context configure destinations for event streams.
The log-id context is used to direct events, alarms and traps, and debug information to respective destinations.
A maximum of 10 logs can be configured.
Before an event can be associated with this log-id, the from command identifying the source of the event must be configured.
Only one destination can be specified for a log-id. The destination of an event stream can be an in-memory buffer, console, session, snmp-trap-group, syslog, or file.
Use the event-control command to suppress the generation of events, alarms, and traps for all log destinations.
An event filter policy can be applied in the log-id context to limit which events, alarms, and traps are sent to the specified log-id.
Log IDs 99 and 100 are created by the agent. Log ID 99 captures all log messages. Log ID 100 captures log messages with a severity level of major and above.
Log ID 99 provides valuable information for the admin-tech file. Removing or changing the log configuration may hinder debugging capabilities. Nokia strongly recommends not to alter the configuration for Log ID 99.
The no form of this command deletes the log destination ID from the configuration.
Parameters
- log-id
Specifies the log ID number, expressed as a decimal integer.
to console
Syntax
to console
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to the console. If the console is not connected, all entries are dropped.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and re-created.
to file
Syntax
to file log-file-id
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to a specified file.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and re-created.
Parameters
- log-file-id
Specifies to instruct the events selected for the log ID to be directed to the log-file-id. The characteristics of the log-file-id referenced here must have already been defined in the config>log>file log-file-id context.
to memory
Syntax
to memory [size]
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to a memory log. A memory file is a circular buffer. When the file is full, each new entry replaces the oldest entry in the log.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and re-created.
Parameters
- size
Specifies the number of events that can be stored in the memory.
to session
Syntax
to session
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to the current console or Telnet session. This command is only valid for the duration of the session. When the session is terminated, the log ID is removed. A log ID with a session destination is not saved in the configuration file.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and re-created.
to snmp
Syntax
to snmp [size]
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the alarms and traps to be directed to the snmp-trap-group associated with log-id.
A local circular memory log is always maintained for SNMP notifications sent to the specified snmp-trap-group for the log-id.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and recreated.
Parameters
- size
Specifies the number of events stored in this memory log.
to syslog
Syntax
to syslog syslog-id
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the log ID destination. This parameter is mandatory when configuring a log destination.
This command instructs the alarms and traps to be directed to a specified syslog. To remain consistent with the standards governing syslog, messages to syslog are truncated to 1k bytes.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and recreated.
Parameters
- syslog-id
Instructs the events selected for the log ID to be directed to the syslog-id. The characteristics of the syslog-id referenced here must have been defined in the config>log>syslog syslog-id context.
time-format
Syntax
time-format {local | utc}
Context
config>log>log-id
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies whether the time should be displayed in local or Coordinated Universal Time (UTC) format.
Default
utc
Parameters
- local
Keyword to specify that timestamps are written in the system local time.
- utc
Keyword to specify that timestamps are written using the UTC value. This was formerly called Greenwich Mean Time (GMT) and Zulu time.
Accounting policy commands
accounting-policy
Syntax
accounting-policy policy-id
no accounting-policy policy-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables an access or network accounting policy. An accounting policy defines the accounting records that are created.
Access accounting policies are policies that can be applied to one or more SAPs or access ports. Changes made to an existing policy, using any of the subcommands, are applied immediately to all SAPs or access ports where this policy is applied.
If an accounting policy is not specified on a SAP or an access port, then accounting records are produced in accordance with the access policy designated as the default. If a default access policy is not specified, then no accounting records are collected other than the records for the accounting policies that are explicitly configured.
Network accounting policies are policies that can be applied to one or more network ports, network IP interfaces and SDPs. Any changes made to an existing policy, using any of the subcommands, will be applied immediately to all network ports, IP interfaces or SDPs where this policy is applied.
If no accounting policy is defined on a network port, network IP interface and SDP, accounting records will be produced in accordance with the default network policy as designated with the default command. If no network default policy is created, then no accounting records will be collected other than the records for the accounting policies explicitly configured.
On the 7210 SAS, a total of 21 accounting records are available. There are five types of accounting policies:
access
access port
network
network interface
SDP (not supported on platforms operating in access-uplink mode)
When creating accounting policies, one access, one access port, one network, one network interface, and one SDP accounting policy can be defined as default. If statistics collection is enabled on an accounting object and no accounting policy is applied, the respective default accounting policy is used. If no default policy is defined, no statistics are collected unless a specifically defined accounting policy is applied.
The no form of this command deletes the policy from the configuration. The accounting policy cannot be removed unless it is removed from all the SAPs, network ports or channels where the policy is applied.
Parameters
- policy-id
Specifies the policy ID that uniquely identifies the accounting policy, expressed as a decimal integer.
collection-interval
Syntax
collection-interval minutes
no collection-interval
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the accounting collection interval.
Parameters
- minutes
Specifies the interval between collections, in minutes.
default
Syntax
[no] default
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the default accounting policy to be used with all SAPs that do not have an accounting policy.
If no accounting policy is defined on an access or network object, accounting records are produced in accordance with the default access policy. If no default access policy is created, then no accounting records will be collected other than the records for the accounting policies that are explicitly configured.
When creating accounting policies, one access, one access port, one network, one network interface, and one SDP accounting policy can be defined as default.
The record name must be specified before assigning an accounting policy as default.
If a policy is configured as the default policy, then a no default command must be issued before a new default policy can be configured.
The no form of this command removes the default policy designation from the policy ID. The accounting policy will be removed from all access or network object ports that do not have this policy explicitly defined.
record
Syntax
[no] record record-name
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds the accounting record type to the accounting policy to be forwarded to the configured accounting file. A record name can only be used in one accounting policy. To obtain a list of all record types that can be configured, use the show log accounting-records command.
To configure an accounting policy for SAPs, select the access type accounting records such as service-ingress-packets; for access ports, select access port type records, such as access-egress-packets; for network ports select network type records, such as network-egress-packets; for IP interfaces, select network interface type records, such as network-interface-ingress-packets; and for SDP and SDP bindings select SDP type records, such as complete-sdp-ingress-egress.
If the change required modifies the record from one type to another, the old record name must be removed using the no form of this command.
Only one record may be configured in a single accounting policy. For example, if an accounting-policy is configured with an access-egress-octets record, to change it to service-ingress-octets, use the no record command under the accounting policy to remove the old record and then enter the service-ingress-octets record.
Collecting excessive statistics can adversely affect the CPU utilization and take up large amounts of storage space.
The no form of this command removes the record type from the policy.
Parameters
- record-name
Specifies the accounting record name.
Output
The following output is an example of show accounting records for 7210 SAS platforms.
Sample output for 7210 SAS-Sx 10/100GE*A:7210SAS>show>log# accounting-records
===========================================================
Accounting Policy Records
===========================================================
Record # Record Name Def. Interval
-----------------------------------------------------------
1 service-ingress-octets 5
2 service-egress-octets 5
3 service-ingress-packets 5
4 service-egress-packets 5
5 network-ingress-octets 15
6 network-egress-octets 15
7 network-ingress-packets 15
8 network-egress-packets 15
10 combined-service-ingress 5
11 combined-network-ing-egr-octets 15
13 complete-service-ingress-egress 5
14 combined-sdp-ingress-egress 5
15 complete-sdp-ingress-egress 5
32 saa 5
56 complete-pm 5
101 network-interface-ingress-octets 15
102 network-interface-ingress-packets 15
103 combined-network-interface-ingress 15
104 access-egress-packets 5
105 access-egress-octets 5
106 combined-access-egress 5
107 combined-network-egress 15
108 combined-service-egress 5
===========================================================
*A:7210SAS>show>log#
to
Syntax
to file file-id
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command specifies the destination for the accounting records selected for the accounting policy.
Parameters
- file-id
Specifies the destination for the accounting records selected for this destination. The characteristics of the file-id must have already been defined in the config>log>file context. A file-id can only be used once.
The file is generated when the file policy is referenced. This command identifies the type of accounting file to be created. The file definition defines its characteristics.
If the to command is executed while the accounting policy is in operation, it becomes active during the next collection interval.
log-memory
Syntax
log-memory
[no] log-memory
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
If the user specifies use of log-memory, the system allocates some RAM (that is, volatile memory) as a temporary storage to write accounting records every collection-interval. The accounting records are moved from the temporary storage to the accounting file on non-volatile memory (that is, flash), when either the rollover-interval expires or when temporary storage location gets full.
The accounting records held in the temporary storage are lost on a reboot (either due to loss of power or due to user action).
Show commands
accounting-policy
Syntax
accounting-policy [acct-policy-id] [access | network]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays accounting policy information.
Parameters
- policy-id
Specifies the policy ID that uniquely identifies the accounting policy, expressed as a decimal integer.
- access
Specifies to display only access accounting policies.
- network
Specifies to display only network accounting policies.
Output
The following output is an example of accounting policy information, and Output fields: accounting policy describes the output fields.
Sample output*A:7210-SAS>show>log# accounting-policy
===============================
Accounting Policies
===============================================================================
Policy Type Def Admin Oper Intvl File Record Name
Id State State Id
-------------------------------------------------------------------------------
1 access No Down Down 5 1 combined-service-ingress
Description : (Not Specified)
Log-Memory : Yes
Log-Memory Size : 128 KB
Data Loss Count : 0 Data Loss TimeStamp: N/A
-------------------------------------------------------------------------------
This policy is applied to:
Svc :101 SAP:lag-3:101.101 Collect-Stats
Svc :102 SAP:lag-3:102.102 Collect-Stats
Svc :103 SAP:lag-3:103.103 Collect-Stats
....
| Label | Description |
|---|---|
Policy ID |
Displays the identifying value assigned to a specific policy |
Type |
Identifies accounting record type forwarded to the configured accounting file access — Indicates that the policy is an access accounting policy network — Indicates that the policy is a network accounting policy sdp — Indicates that the policy is meant to collect accounting stats for SDPs and spoke SDPs access port — Indicates that the policy is an access port accounting policy which can be used to collect accounting records only for access ports network interface — Indicates that the policy is an network Interface accounting policy which can be used to collect accounting records only for network IP interface none — Indicates no accounting record types assigned |
Def |
Yes — Indicates that the policy is a default access or network policy No — Indicates that the policy is not a default access or network policy |
Admin State |
Displays the administrative state of the policy Up — Indicates that the policy is administratively enabled Down — Indicates that the policy is administratively disabled |
Oper State |
Displays the operational state of the policy Up — Indicates that the policy is operationally up Down — Indicates that the policy is operationally down |
Intvl |
Displays the interval, in minutes, in which statistics are collected and written to their destination The default depends on the record name type |
File ID |
Displays the log destination |
Record Name |
Displays the accounting record name which represents the configured record type |
Log-Memory |
If the values shown is 'Yes', it indicates that temporary volatile memory is in use for this accounting policy If it displays 'No', the temporary volatile memory is not in use for this accounting policy |
Log-Memory Size |
Displays the amount of temporary volatile memory in use for this accounting policy |
This policy is applied to |
Specifies the entity where the accounting policy is applied |
accounting-records
Syntax
accounting-records
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays accounting policy record names.
Output
The following output is an example of accounting record information, and Output fields: accounting records describes the output fields.
Sample output*A:7210-SAS>show>log# accounting-records
==========================================================
Accounting Policy Records
==========================================================
Record # Record Name Def. Interval
----------------------------------------------------------
1 service-ingress-octets 5
2 service-egress-octets 5
3 service-ingress-packets 5
4 service-egress-packets 5
5 network-ingress-octets 15
6 network-egress-octets 15
7 network-ingress-packets 15
8 network-egress-packets 15
10 combined-service-ingress 5
11 combined-network-ing-egr-octets 15
13 complete-service-ingress-egress 5
14 combined-sdp-ingress-egress 5
15 complete-sdp-ingress-egress 5
32 saa 5
33 network-interface-ingress-octets 15
34 network-interface-ingress-packets 15
35 combined-network-interface-ingress 15
36 access-egress-packets 5
37 access-egress-octets 5
38 combined-access-egress 5
39 combined-network-egress 15
40 combined-service-egress 5
==========================================================
*A:7210-SAS>show>log#
| Label | Description |
|---|---|
Record # |
The record ID that uniquely identifies the accounting policy, expressed as a decimal integer |
Record Name |
The accounting record name |
Def. Interval |
The default interval, in minutes, in which statistics are collected and written to their destination |
applications
Syntax
applications
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command displays a list of all application names that can be used in event-control and filter commands.
Output
The following output is an example of application name information.
Sample outputA:ALA-1# show log applications
==================================
Log Event Application Names
==================================
Application Name
----------------------------------
CCAG
CHASSIS
CPMHWFILTER
DHCP
DEBUG
DOT1X
FILTER
IGMP
IGMP_SNOOPING
IP
ISIS
LAG
LDP
LOGGER
MIRROR
MPLS
OAM
OSPF
PORT
PPP
QOS
RIP
ROUTE_POLICY
RSVP
SECURITY
SNMP
STP
SVCMGR
SYSTEM
USER
VRRP
VRTR
==================================
A:ALA-1#
event-control
Syntax
event-control [application-id [event-name | event-number]]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command displays event control settings for events including whether the event is suppressed or generated and the severity level for the event.
If no options are specified, all events, alarms, and traps are listed.
Parameters
- application-id
Displays event control for only the specified application.
- event-name
Displays event control only for the named application event.
- event-number
Displays event control for only the specified application event number.
Output
The following output is an example of event control settings information, and Output fields: event control describes the output fields.
Sample output*A:SAS>show>log# event-control
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
BGP:
2001 bgpEstablished MI gen 0 0
2002 bgpBackwardTransition WA gen 0 0
2003 tBgpMaxPrefix90 WA gen 0 0
2004 tBgpMaxPrefix100 CR gen 0 0
L 2005 sendNotification WA gen 0 0
L 2006 receiveNotification WA gen 0 0
L 2007 bgpInterfaceDown WA gen 0 0
L 2008 bgpConnNoKA WA gen 0 0
L 2009 bgpConnNoOpenRcvd WA gen 0 0
L 2010 bgpRejectConnBadLocAddr WA gen 0 0
L 2011 bgpRemoteEndClosedConn WA gen 0 0
L 2012 bgpPeerNotFound WA gen 0 0
L 2013 bgpConnMgrTerminated WA gen 0 0
L 2014 bgpTerminated WA gen 0 0
L 2015 bgpNoMemoryPeer CR gen 0 0
L 2016 bgpVariableRangeViolation WA gen 0 0
L 2017 bgpCfgViol WA gen 0 0
2018 tBgpPeerGRStatusChange WA gen 0 0
2019 tBgpNgEstablished MI gen 0 0
2020 tBgpNgBackwardTransition WA gen 0 0
2021 tBgpPeerNgHoldTimeInconsistent WA gen 0 0
CHASSIS:
2001 cardFailure MA gen 0 0
2002 cardInserted MI gen 5 0
2003 cardRemoved MI gen 0 0
2004 cardWrong MI gen 0 0
2005 EnvTemperatureTooHigh MA gen 0 0
2006 fanFailure CR gen 0 0
2007 powerSupplyOverTemp CR gen 0 0
2008 powerSupplyAcFailure CR gen 0 0
2009 powerSupplyDcFailure CR gen 0 0
2010 powerSupplyInserted MA gen 1 0
2011 powerSupplyRemoved MA gen 0 0
2012 redPrimaryCPMFail CR gen 0 0
2016 clearNotification MA gen 0 0
2017 syncIfTimingHoldover CR gen 0 0
2018 syncIfTimingHoldoverClear CR gen 0 0
2019 syncIfTimingRef1Alarm MI gen 0 0
2020 syncIfTimingRef1AlarmClear MI gen 0 0
2021 syncIfTimingRef2Alarm MI gen 0 0
2022 syncIfTimingRef2AlarmClear MI gen 0 0
2023 flashDataLoss MA gen 0 0
2024 flashDiskFull MA gen 0 0
2025 softwareMismatch MA gen 0 0
2026 softwareLoadFailed MA gen 0 0
2027 bootloaderMismatch MA gen 1 0
2028 bootromMismatch MA gen 0 0
2029 fpgaMismatch MA gen 0 0
2030 syncIfTimingBITSAlarm MI gen 0 0
2031 syncIfTimingBITSAlarmClear MI gen 0 0
2032 cardUpgraded MA gen 0 0
2033 cardUpgradeInProgress MA gen 0 0
2034 cardUpgradeComplete MA gen 0 0
2050 powerSupplyInputFailure CR gen 0 0
2051 powerSupplyOutputFailure CR gen 0 0
2052 mdaHiBwMulticastAlarm MI gen 0 0
2056 mdaCfgNotCompatible MA gen 0 0
2057 cardSyncFileNotPresent MI gen 0 0
2058 tmnxEqMdaXplError MI sup 0 0
2059 tmnxEqCardPChipError MI sup 0 0
2060 tmnxEqCardSoftResetAlarm MI gen 0 0
2061 tmnxEqMdaSyncENotCompatible MA gen 0 0
2062 tmnxIPsecIsaGrpActiveIsaChgd MI gen 0 0
2063 tmnxEqCardPChipMemoryEvent MI sup 0 0
2064 tmnxIPsecIsaGrpUnableToSwitch MI gen 0 0
2065 tmnxIPsecIsaGrpTnlLowWMark MI gen 0 0
2066 tmnxIPsecIsaGrpTnlHighWMark MI gen 0 0
2067 tmnxIPsecIsaGrpTnlMax MI gen 0 0
2076 tmnxEqCardPChipCamEvent CR gen 0 0
2078 tmnxEqHwEnhancedCapability MA gen 0 0
2068 tmnxEqSyncIfTimingRef1Quality MI gen 0 0
2069 tmnxEqSyncIfTimingRef2Quality MI gen 0 0
2072 tmnxEqSyncIfTimingRefSwitch MI gen 0 0
2077 tmnxEqSyncIfTimingSystemQuality MI gen 1 0
3001 tmnxSasAlarminput1StateChanged MA gen 0 0
3002 tmnxSasAlarminput2StateChanged MA gen 0 0
3003 tmnxSasAlarminput3StateChanged MA gen 0 0
3004 tmnxSasAlarminput4StateChanged MA gen 0 0
3000 EnvTemperatureTooLow MA gen 0 0
DEBUG:
L 2001 traceEvent MI gen 0 0
EFM_OAM:
2001 tmnxDot3OamPeerChanged MI gen 0 0
2002 tmnxDot3OamLoopDetected MI gen 0 0
2003 tmnxDot3OamLoopCleared MI gen 0 0
2008 dot3OamNonThresholdEvent MI gen 0 0
2902 tmnxDyingGasp MI gen 0 0
ETH_CFM:
2001 dot1agCfmFaultAlarm MI gen 0 0
2002 tmnxDot1agCfmMepLbmTestComplete MI gen 0 0
2003 tmnxDot1agCfmMepLtmTestComplete MI gen 0 0
2004 tmnxDot1agCfmMepEthTestComplete MI gen 0 0
2005 tmnxDot1agCfmMepDMTestComplete MI gen 0 0
2006 tmnxDot1agCfmMepAisStateChanged MI gen 0 0
2007 tmnxDot1agCfmMipEvaluation MI gen 0 0
ERING:
2001 tmnxEthRingPathFwdStateChange MI gen 0 0
2002 tmnxEthRingApsPrvsnRaiseAlarm MI gen 0 0
2003 tmnxEthRingApsPrvsnClearAlarm MI gen 0 0
ETUN:
2001 tmnxEthTunnelApsCfgRaiseAlarm MI gen 0 0
2002 tmnxEthTunnelApsCfgClearAlarm MI gen 0 0
2003 tmnxEthTunnelApsPrvsnRaiseAlarm MI gen 0 0
2004 tmnxEthTunnelApsPrvsnClearAlarm MI gen 0 0
2005 tmnxEthTunnelApsNoRspRaiseAlarm MI gen 0 0
2006 tmnxEthTunnelApsNoRspClearAlarm MI gen 0 0
2007 tmnxEthTunnelApsSwitchoverAlarm MI gen 0 0
FILTER:
2001 tIPFilterPBRPacketsDrop WA gen 0 0
2002 tFilterEntryActivationFailed WA gen 0 0
2003 tFilterEntryActivationRestored WA gen 0 0
IGMP_SNOOPING:
2001 sapIgmpSnpgGrpLimitExceeded WA gen 0 0
2002 sapIgmpSnpgMcacPlcyDropped WA gen 0 0
2003 sdpBndIgmpSnpgGrpLimitExceeded WA gen 0 0
2004 sdpBndIgmpSnpgMcacPlcyDropped WA gen 0 0
2005 sapIgmpSnpgMcsFailure WA gen 0 0
2006 sapIgmpSnpgSrcLimitExceeded WA gen 0 0
2007 sdpBndIgmpSnpgSrcLimitExceeded WA gen 0 0
IP:
L 2001 clearRTMError MI gen 0 0
L 2002 ipEtherBroadcast MI gen 0 0
L 2003 ipDuplicateAddress MI gen 0 0
L 2004 ipArpInfoOverwritten MI gen 0 0
L 2005 fibAddFailed MA gen 0 0
L 2006 qosNetworkPolicyMallocFailed MA gen 0 0
L 2007 ipArpBadInterface MI gen 0 0
L 2008 ipArpDuplicateIpAddress MI gen 0 0
L 2009 ipArpDuplicateMacAddress MI gen 0 0
L 2010 ipAnyDuplicateAddress MI gen 0 0
ISIS:
2001 vRtrIsisDatabaseOverload WA gen 0 0
2002 vRtrIsisManualAddressDrops WA gen 0 0
2003 vRtrIsisCorruptedLSPDetected WA gen 0 0
2004 vRtrIsisMaxSeqExceedAttempt WA gen 0 0
2005 vRtrIsisIDLenMismatch WA gen 0 0
2006 vRtrIsisMaxAreaAddrsMismatch WA gen 0 0
2007 vRtrIsisOwnLSPPurge WA gen 0 0
2008 vRtrIsisSequenceNumberSkip WA gen 0 0
2009 vRtrIsisAutTypeFail WA gen 0 0
2010 vRtrIsisAuthFail WA gen 0 0
2011 vRtrIsisVersionSkew WA gen 0 0
2012 vRtrIsisAreaMismatch WA gen 0 0
2013 vRtrIsisRejectedAdjacency WA gen 0 0
2014 vRtrIsisLSPTooLargeToPropagate WA gen 0 0
2015 vRtrIsisOrigLSPBufSizeMismatch WA gen 0 0
2016 vRtrIsisProtoSuppMismatch WA gen 0 0
2017 vRtrIsisAdjacencyChange WA gen 0 0
2018 vRtrIsisCircIdExhausted WA gen 0 0
2019 vRtrIsisAdjRestartStatusChange WA gen 0 0
2020 vRtrIsisLdpSyncTimerStarted WA gen 0 0
2021 vRtrIsisLdpSyncExit WA gen 0 0
LAG:
2001 DynamicCostOn WA gen 0 0
2002 DynamicCostOff WA gen 0 0
2003 LagPortAddFailed WA gen 0 0
2004 LagSubGroupSelected WA gen 0 0
2005 LagPortAddFailureCleared WA gen 0 0
LDP:
2001 vRtrLdpStateChange MI gen 0 0
2002 vRtrLdpInstanceStateChange MI gen 0 0
2003 vRtrLdpIfStateChange MI sup 0 0
2004 vRtrLdpGroupIdMismatch MI gen 0 0
LLDP:
2001 lldpRemTablesChange MI gen 0 0
LOGGER:
L 2001 STARTED MI gen 5 0
2002 tmnxLogTraceError CR gen 0 0
2005 tmnxLogSpaceContention MA gen 0 0
2006 tmnxLogAdminLocFailed MA gen 0 0
2007 tmnxLogBackupLocFailed MA gen 0 0
2008 tmnxLogFileRollover MA gen 0 0
2009 tmnxLogFileDeleted MI gen 0 0
2010 tmnxClear IN gen 0 0
2011 tmnxTestEvent IN gen 0 0
2012 tmnxLogEventThrottled MA gen 0 0
2013 tmnxSysLogTargetProblem MA gen 0 0
2014 tmnxLogAccountingDataLoss MA gen 0 0
2015 tmnxStdEventsReplayed MA gen 0 0
L 2016 tmnxLogOnlyEventThrottled MA gen 0 0
MC_REDUNDANCY:
2001 tmnxMcRedundancyPeerStateChanged WA gen 0 0
2002 tmnxMcRedundancyMismatchDetected WA gen 0 0
2003 tmnxMcRedundancyMismatchResolved WA gen 0 0
2004 tmnxMcPeerSyncStatusChanged WA gen 0 0
2005 tmnxMcSyncClientAlarmRaised WA gen 0 0
2006 tmnxMcSyncClientAlarmCleared WA gen 0 0
2007 tmnxSrrpSubnetMismatch WA gen 0 0
2008 tmnxSrrpSubnetMismatchCleared WA gen 0 0
2009 tmnxSrrpInstanceIdMismatch WA gen 0 0
2010 tmnxSrrpSapMismatch WA gen 0 0
2011 tmnxSrrpSapTagMismatch WA gen 0 0
2012 tmnxSrrpRedIfMismatch WA gen 0 0
2013 tmnxSrrpDualMaster WA gen 0 0
2014 tmnxMcLagInfoLagChanged WA gen 0 0
2015 tmnxSrrpSystemIpNotSet WA gen 0 0
2016 tmnxMcRingOperStateChanged WA gen 0 0
2017 tmnxMcRingInbCtrlOperStateChgd WA gen 0 0
2018 tmnxMcRingNodeLocOperStateChgd WA gen 0 0
2019 tmnxMcSyncClockSkewRaised WA gen 0 0
2020 tmnxMcSyncClockSkewCleared WA gen 0 0
2021 tmnxSrrpDuplicateSubIfAddress WA gen 0 0
2022 tmnxMcPeerRingsOperStateChanged WA gen 0 0
2023 tmnxSrrpTrapNewMaster MI gen 0 0
2024 tmnxSrrpBecameBackup MI gen 0 0
L 2025 srrpPacketDiscarded MI gen 0 0
2026 tmnxSrrpBfdIntfSessStateChgd MI gen 0 0
2027 tmnxMcPeerEPBfdSessionOpen WA gen 0 0
2028 tmnxMcPeerEPBfdSessionClose WA gen 0 0
2029 tmnxMcPeerEPBfdSessionUp WA gen 0 0
2030 tmnxMcPeerEPBfdSessionDown WA gen 0 0
2031 tmnxMcPeerEPOperDown WA gen 0 0
2032 tmnxMcPeerEPOperUp WA gen 0 0
2033 tmnxMCEPSessionPsvModeEnabled WA gen 0 0
2034 tmnxMCEPSessionPsvModeDisabled WA gen 0 0
MIRROR:
2001 sourceEnabled MI gen 0 0
2002 sourceDisabled MI gen 0 0
2003 destinationEnabled MI gen 0 0
2004 destinationDisabled MI gen 0 0
2006 sourceIpFilterChange MI gen 0 0
2007 sourceMacFilterChange MI gen 0 0
2008 sourceSapChange MI gen 0 0
2009 sourceSubscriberChange MI gen 0 0
MPLS:
2001 mplsXCUp WA gen 0 0
2002 mplsXCDown WA gen 0 0
2003 mplsTunnelUp WA gen 0 0
2004 mplsTunnelDown WA gen 0 0
2005 mplsTunnelRerouted WA sup 0 0
2006 mplsTunnelReoptimized WA sup 0 0
2007 vRtrMplsStateChange WA gen 0 0
2008 vRtrMplsIfStateChange WA gen 0 0
2009 vRtrMplsLspUp WA gen 0 0
2010 vRtrMplsLspDown WA gen 0 0
2011 vRtrMplsLspPathUp WA gen 0 0
2012 vRtrMplsLspPathDown WA gen 0 0
2013 vRtrMplsLspPathRerouted WA gen 0 0
2014 vRtrMplsLspPathResignaled WA gen 0 0
2015 vRtrMplsP2mpInstanceUp WA gen 0 0
2016 vRtrMplsP2mpInstanceDown WA gen 0 0
2017 vRtrMplsS2lSubLspUp WA gen 0 0
2018 vRtrMplsS2lSubLspDown WA gen 0 0
2019 vRtrMplsS2lSubLspRerouted WA gen 0 0
2020 vRtrMplsS2lSubLspResignaled WA gen 0 0
2021 vRtrMplsLspPathSoftPreempted WA gen 0 0
2022 vRtrMplsLspPathLstFillReoptElig WA gen 0 0
2023 vRtrMplsP2mpInstanceResignaled WA gen 0 0
2024 vRtrMplsResignalTimerExpired WA gen 0 0
NTP:
2001 tmnxNtpAuthMismatch WA gen 0 0
2002 tmnxNtpNoServersAvail MA gen 0 0
2003 tmnxNtpServersAvail MI gen 0 0
2008 tmnxNtpOperChange WA gen 0 0
2009 tmnxNtpServerChange MI gen 0 0
OAM:
2001 tmnxOamPingProbeFailedV3 MI gen 0 0
2002 tmnxOamPingTestFailedV3 MI gen 0 0
2003 tmnxOamPingTestCompletedV3 MI gen 0 0
2004 tmnxAncpLoopbackTestCompleted WA gen 0 0
L 2005 tmnxAncpLoopbackTestCompletedL WA gen 0 0
2050 tmnxOamTrPathChange MI gen 0 0
2051 tmnxOamTrTestFailed MI gen 0 0
2052 tmnxOamTrTestCompleted MI gen 0 0
L 2053 svcIdInvalid MI gen 0 0
L 2054 svcIdWrongType MI gen 0 0
2055 tmnxOamLdpTtraceAutoDiscState MI gen 0 0
2056 tmnxOamLdpTtraceFecProbeState MI gen 0 0
2057 tmnxOamLdpTtraceFecDisStatus MI gen 0 0
2101 tmnxOamSaaThreshold MI gen 0 0
OSPF:
2001 tmnxOspfVirtIfStateChange WA gen 0 0
2002 tmnxOspfNbrStateChange WA gen 0 0
2003 tmnxOspfVirtNbrStateChange WA gen 0 0
2004 tmnxOspfIfConfigError WA gen 0 0
2005 tmnxOspfVirtIfConfigError WA gen 0 0
2006 tmnxOspfIfAuthFailure WA gen 0 0
2007 tmnxOspfVirtIfAuthFailure WA gen 0 0
2008 tmnxOspfIfRxBadPacket WA gen 0 0
2009 tmnxOspfVirtIfRxBadPacket WA gen 0 0
2010 tmnxOspfTxRetransmit WA sup 0 0
2011 tmnxOspfVirtIfTxRetransmit WA sup 0 0
2012 tmnxOspfAreaOriginateLsa WA sup 0 0
2013 tmnxOspfAreaMaxAgeLsa WA gen 0 0
2014 tmnxOspfLsdbOverflow WA gen 0 0
2015 tmnxOspfLsdbApproachingOverflow WA gen 0 0
2016 tmnxOspfIfStateChange WA gen 0 0
2017 tmnxOspfNssaTranslatorStatusChg WA gen 0 0
2018 tmnxOspfRestartStatusChange WA gen 0 0
2019 tmnxOspfNbrRestartHlprStsChg WA gen 0 0
2020 tmnxOspfVirtNbrRestartHlprStsChg WA gen 0 0
2021 tmnxOspfSpfRunsStopped WA gen 0 0
2022 tmnxOspfSpfRunsRestarted WA gen 0 0
2023 tmnxOspfOverloadEntered WA gen 0 0
2024 tmnxOspfOverloadExited WA gen 0 0
2025 tmnxOspfAsOriginateLsa WA sup 0 0
2026 tmnxOspfAsMaxAgeLsa WA gen 0 0
2027 tmnxOspfLinkOriginateLsa WA sup 0 0
2028 tmnxOspfLinkMaxAgeLsa WA gen 0 0
2029 tmnxOspfLdpSyncTimerStarted WA gen 0 0
2030 tmnxOspfLdpSyncExit WA gen 0 0
2031 tmnxOspfShamIfStateChange WA gen 0 0
2032 tmnxOspfShamNbrStateChange WA gen 0 0
2033 tmnxOspfShamIfConfigError WA gen 0 0
2034 tmnxOspfShamIfAuthFailure WA gen 0 0
2035 tmnxOspfShamIfRxBadPacket WA gen 0 0
2036 tmnxOspfShamIfTxRetransmit WA gen 0 0
2037 tmnxOspfShamNbrRestartHlprStsChg WA gen 0 0
2038 tmnxOspfFailureDisabled WA gen 0 0
PORT:
2001 sonetSDHAlarmSet MI gen 0 0
2002 sonetSDHAlarmClear MI gen 0 0
2003 sonetSDHChannelAlarmSet MI gen 0 0
2004 sonetSDHChannelAlarmClear MI gen 0 0
2005 SFPInserted MI gen 17 0
2006 SFPRemoved MI gen 3 0
2008 SFPStatusFailure MI gen 0 0
2009 portError MI gen 0 0
2010 yellowDiffDelayExceeded MI gen 0 0
2011 redDiffDelayExceeded MA gen 0 0
2012 bndlBadEndPtDiscriminator MI gen 0 0
2013 ds3AlarmSet MI gen 0 0
2014 ds3AlarmClear MI gen 0 0
2015 ds1AlarmSet MI gen 0 0
2016 ds1AlarmClear MI gen 0 0
2017 etherAlarmSet MI gen 5 0
2018 etherAlarmClear MI gen 4 0
2019 ds1LoopbackStart MI gen 0 0
2020 ds1LoopbackStop MI gen 0 0
2021 ds3LoopbackStart MI gen 0 0
2022 ds3LoopbackStop MI gen 0 0
2023 sdhLoopbackStart MI gen 0 0
2024 sdhLoopbackStop MI gen 0 0
2025 etherLoopDetected MI gen 0 0
2026 etherLoopCleared MI gen 0 0
2027 etherSpeedNotCompatible MA gen 0 0
2028 etherDuplexNotCompatible MA gen 0 0
2029 etherIngressRateCfgNotCompatible MA gen 0 0
2030 digitalDiagnosticMonitorFailed MI gen 9 0
2031 SFPStatusDDMCorrupt MI gen 0 0
2032 SFPStatusReadError MI gen 0 0
2033 SFPStatusUnsupported MI gen 0 0
2034 dsxClockSyncStateChange MI gen 0 0
2035 bundleMlfrMemberLoopback MI gen 0 0
2036 tmnxPortUnsupportedFunction WA gen 0 0
2037 otuAlarms MI gen 0 0
ROUTE_POLICY:
L 2001 trigPolicyPrevEval WA gen 0 0
RSVP:
2001 vRtrRsvpStateChange WA gen 0 0
2002 vRtrRsvpIfStateChange WA gen 0 0
2003 vRtrRsvpIfNbrStateUp WA gen 0 0
2004 vRtrRsvpIfNbrStateDown WA gen 0 0
SECURITY:
L 2001 cli_user_login MI gen 3 0
L 2002 cli_user_logout MI gen 2 0
L 2003 cli_user_login_failed MI gen 0 0
L 2004 cli_user_login_max_attempts MI gen 0 0
L 2005 ftp_user_login MI gen 0 0
L 2006 ftp_user_logout MI gen 0 0
L 2007 ftp_user_login_failed MI gen 0 0
L 2008 ftp_user_login_max_attempts MI gen 0 0
L 2009 ssh_user_login MI gen 0 0
L 2010 ssh_user_logout MI gen 0 0
L 2011 ssh_user_login_failed MI gen 0 0
L 2012 ssh_user_login_max_attempts MI gen 0 0
2014 radiusOperStatusChange MI gen 0 0
L 2015 user_disconnect MA gen 0 0
L 2016 radiusSystemIpAddrNotSet MA gen 0 0
2018 tacplusOperStatusChange MI gen 0 0
L 2019 mafEntryMatch MA gen 0 0
L 2020 ftp_transfer_successful MI gen 0 0
L 2021 ftp_transfer_failed MI gen 0 0
L 2022 enable_admin WA gen 0 0
L 2023 host_snmp_attempts WA gen 0 0
2024 SSH_server_preserve_key_fail MI gen 0 0
2025 tacplusInetSrvrOperStatusChange MI gen 0 0
2026 radiusInetServerOperStatusChange MI gen 0 0
2027 tmnxKeyChainAuthFailure MI gen 0 0
2028 tmnxCpmProtViolPort WA gen 0 0
2029 tmnxCpmProtViolPortAgg WA gen 0 0
2030 tmnxCpmProtViolIf WA gen 0 0
2031 tmnxCpmProtViolSap WA gen 0 0
2032 tmnxCpmProtViolMac WA gen 0 0
2033 tmnxCpmProtViolVdoSvcClient WA gen 0 0
2034 tmnxCpmProtViolVdoVrtrClient WA gen 0 0
2206 tmnxConfigModify WA gen 2 0
2207 tmnxConfigCreate WA gen 2 0
2208 tmnxConfigDelete WA gen 0 0
2209 tmnxStateChange WA gen 0 0
SNMP:
2001 coldStart MA gen 1 0
2002 warmStart MA gen 0 0
2003 authenticationFailure MI sup 0 0
2004 linkDown WA gen 5 0
2005 linkUp WA gen 8 0
2101 risingAlarm MA gen 0 0
2102 fallingAlarm MA gen 0 0
2201 snmpdError MA gen 0 0
STP:
2001 topologyChangeSapMajorState WA gen 0 0
2002 newRootSap WA gen 0 0
2003 topologyChangeVcpState WA gen 0 0
2004 newRootVcpState WA gen 0 0
2005 topologyChangeSapState WA gen 0 0
2006 receivedTCN WA gen 0 0
2007 newRootBridge WA gen 0 0
2008 unacknowledgedTCN WA gen 0 0
2009 higherPriorityBridge WA gen 0 0
2011 sapEncapPVST MI gen 0 0
2012 sapEncapDot1d MI gen 0 0
2014 tmnxSvcTopoChgSdpBindMajorState WA gen 0 0
2015 tmnxSvcNewRootSdpBind WA gen 0 0
2016 tmnxSvcTopoChgSdpBindState WA gen 0 0
2017 tmnxSvcSdpBindRcvdTCN WA gen 0 0
2018 tmnxSvcSdpBindRcvdHigherBriPrio WA gen 0 0
2019 tmnxSvcSdpBindEncapPVST MI gen 0 0
2020 tmnxSvcSdpBindEncapDot1d MI gen 0 0
2021 tmnxNewCistRegionalRootBridge WA gen 0 0
2022 tmnxNewMstiRegionalRootBridge WA gen 0 0
2023 tmnxStpRootGuardViolation WA gen 0 0
2024 tmnxStpMeshNotInMstRegion WA gen 0 0
2025 tmnxSapStpExcepCondStateChng WA gen 0 0
2026 tmnxSdpBndStpExcepCondStateChng WA gen 0 0
2050 sapActiveProtocolChange MI gen 0 0
2051 tmnxSvcSdpActiveProtocolChange MI gen 0 0
2052 vcpActiveProtocolChange MI gen 0 0
2053 topologyChangePipMajorState WA gen 0 0
2054 topologyChangePipState WA gen 0 0
2055 tmnxPipStpExcepCondStateChng WA gen 0 0
2056 pipActiveProtocolChange MI gen 0 0
SVCMGR:
2011 svcTlsMacPinningViolation WA gen 0 0
2103 svcStatusChanged MI gen 4 0
2104 svcTlsFdbTableFullAlarmRaised MI gen 0 0
2105 svcTlsFdbTableFullAlarmCleared MI gen 0 0
2108 iesIfStatusChanged MI gen 0 0
2109 tmnxSvcObjTodSuiteApplicFailed WA gen 0 0
2110 tmnxEndPointTxActiveChanged WA gen 0 0
2111 tmnxSvcPEDiscPolServOperStatChg MI gen 0 0
2120 svcTlsMrpAttrRegistrationFailed MI gen 0 0
2125 svcTlsMrpAttrTblFullAlarmRaised MI gen 0 0
2126 svcTlsMrpAttrTblFullAlarmCleared MI gen 0 0
2128 svcEpipePbbOperStatusChanged MI gen 0 0
2203 sapStatusChanged MI gen 2 0
2204 sapTlsMacAddrLimitAlarmRaised MI gen 0 0
2205 sapTlsMacAddrLimitAlarmCleared MI gen 0 0
2206 hostConnectivityLost WA gen 0 0
2207 hostConnectivityRestored WA gen 0 0
2208 sapReceivedProtSrcMac MI gen 0 0
2209 sapTlsMacMoveExceeded MI gen 0 0
2210 sapPortStateChangeProcessed MA gen 0 0
2211 sapCemPacketDefectAlarm MI gen 0 0
2212 sapCemPacketDefectAlarmClear MI gen 0 0
2213 msapStateChanged MI gen 0 0
2214 msapCreationFailure MI gen 0 0
2303 sdpStatusChanged MI gen 0 0
2306 sdpBindStatusChanged MI gen 0 0
L 2307 sdpKeepAliveStarted MI gen 0 0
L 2308 sdpKeepAliveStopped MI gen 0 0
L 2309 sdpKeepAliveProbeFailure MI gen 0 0
L 2310 sdpKeepAliveLateReply MI gen 0 0
2311 sdpTlsMacAddrLimitAlarmRaised MI gen 0 0
2312 sdpTlsMacAddrLimitAlarmCleared MI gen 0 0
2313 sdpBindPwPeerStatusBitsChanged MI gen 0 0
2314 sdpBindTlsMacMoveExceeded MI gen 0 0
2315 sdpBindPwPeerFaultAddrChanged MI gen 0 0
2316 sdpBindSdpStateChangeProcessed MA gen 0 0
2317 sdpBandwidthOverbooked MA gen 0 0
2318 sdpBindInsufficientBandwidth MA gen 0 0
2319 dynamicSdpConfigChanged MA gen 0 0
2320 dynamicSdpBindConfigChanged MA gen 0 0
2321 dynamicSdpCreationFailed MA gen 0 0
2322 dynamicSdpBindCreationFailed MA gen 0 0
2401 svcTlsMfibTableFullAlarmRaised MI gen 0 0
2402 svcTlsMfibTableFullAlarmCleared MI gen 0 0
2500 tmnxSubscriberCreated WA gen 0 0
2501 tmnxSubscriberDeleted WA gen 0 0
2502 tmnxSubscriberRenamed WA gen 0 0
2503 tmnxSubAcctPlcyFailure WA gen 0 0
2504 tmnxSubMcsRelatedProblem WA gen 0 0
2505 tmnxSubAuthPlcyRadSerOperStatChg MI gen 0 0
2506 tmnxSubAcctPlcyRadSerOperStatChg MI gen 0 0
2507 svcEndPointMacLimitAlarmRaised MI gen 0 0
2508 svcEndPointMacLimitAlarmCleared MI gen 0 0
2509 tmnxSubRadSapDisconnectError WA gen 0 0
2510 tmnxSubRadSdpBndDisconnectError WA gen 0 0
2511 tmnxSubRadSapCoAError WA gen 0 0
2512 tmnxSubRadSdpBndCoAError WA gen 0 0
2513 tmnxSubRadSapSubAuthError WA gen 0 0
2514 tmnxSubRadSdpBndSubAuthError WA gen 0 0
2515 svcFdbMimDestTblFullAlrm MI gen 0 0
2516 svcFdbMimDestTblFullAlrmCleared MI gen 0 0
2517 svcPersistencyProblem WA gen 0 0
2520 svcArpHostPopulateErr WA gen 0 0
2522 svcEPMCEPConfigMismatch WA gen 0 0
2523 svcEPMCEPConfigMismatchResolved WA gen 0 0
2524 svcEPMCEPPassiveModeActive WA gen 0 0
2525 svcEPMCEPPassiveModePassive WA gen 0 0
2526 sapHostBGPPeeringSetupFailed MI gen 0 0
2527 tmnxSubUserCategoryOutOfCredit MI gen 0 0
2528 svcRestoreHostProblem WA gen 0 0
2529 tmnxSubUserCategoryRefreshCredit MI gen 0 0
2530 tmnxSubUserCategoryError MI gen 0 0
SYSTEM:
2001 stiDateAndTimeChanged WA gen 0 0
2002 ssiSaveConfigSucceeded MA gen 0 0
2003 ssiSaveConfigFailed CR gen 0 0
2004 sbiBootConfig MA gen 1 0
2005 sbiBootSnmpd MA gen 1 0
2006 tmnxConfigModify WA gen 66 0
2007 tmnxConfigCreate WA gen 11 0
2008 tmnxConfigDelete WA gen 0 0
2009 tmnxStateChange WA gen 7 0
2010 tmnxModuleMallocFailed MA gen 0 0
2011 tmnxTrapDropped MA gen 0 0
2012 ssiSyncConfigOK WA gen 0 0
2013 ssiSyncConfigFailed CR gen 0 0
2014 ssiSyncBootEnvOK WA gen 0 0
2015 ssiSyncBootEnvFailed CR gen 0 0
L 2016 socket_bind_failed CR gen 0 0
L 2017 socket_conn_accept_failed CR gen 0 0
2018 sntpTimeDiffExceedsThreshold MA gen 0 0
2022 tmnxSssiMismatch MA gen 0 0
2023 tmnxSnmpdStateChange MA gen 1 0
2024 tmnxRedStandbySyncing MA gen 0 0
2025 tmnxRedStandbyReady MA gen 0 0
2026 tmnxRedStandbySyncLost CR gen 0 0
2027 tmnxRedSwitchover CR gen 0 0
2028 tmnxRedCpmActive CR gen 0 0
2029 tmnxRedSingleCpm CR gen 0 0
2030 persistencyClosedAlarmRaised MA gen 0 0
2031 persistencyClosedAlarmCleared MA gen 0 0
2032 tmnxSntpOperChange MA gen 0 0
2034 tmnxFtpClientFailure MI gen 0 0
2037 persistencyEventReport WA gen 0 0
2038 sbiBootConfigFailFileError MA gen 0 0
2039 sbiBootConfigOKFileError MA gen 0 0
2101 schedActionFailure MA gen 0 0
2102 smScriptAbort MA gen 0 0
2103 smScriptResult MI sup 0 0
2104 smScriptException MI sup 0 0
USER:
L 2001 cli_user_login MI gen 3 0
L 2002 cli_user_logout MI gen 2 0
L 2003 cli_user_login_failed MI gen 0 0
L 2004 cli_user_login_max_attempts MI gen 0 0
L 2005 ftp_user_login MI gen 0 0
L 2006 ftp_user_logout MI gen 0 0
L 2007 ftp_user_login_failed MI gen 0 0
L 2008 ftp_user_login_max_attempts MI gen 0 0
L 2009 cli_user_io MI sup 0 35
L 2010 snmp_user_set MI sup 0 0
L 2011 cli_config_io MI gen 276 0
VRTR:
2001 tmnxVRtrMidRouteTCA MI gen 0 0
2002 tmnxVRtrHighRouteTCA MI gen 0 0
2003 tmnxVRtrHighRouteCleared MI gen 0 0
2004 tmnxVRtrIllegalLabelTCA MA gen 0 0
2008 tmnxVRtrMaxArpEntriesTCA MA gen 0 0
2009 tmnxVRtrMaxArpEntriesCleared MI gen 0 0
2011 tmnxVRtrMaxRoutes MI gen 0 0
2012 tmnxVRtrBfdSessionDown MA gen 0 0
2013 tmnxVRtrBfdMaxSessionOnSlot MA gen 0 0
2014 tmnxVRtrBfdPortTypeNotSupported MA gen 0 0
2015 tmnxVRtrBfdSessionUp MA gen 0 0
2016 tmnxVRtrIPv6MidRouteTCA MI gen 0 0
2017 tmnxVRtrIPv6HighRouteTCA MI gen 0 0
2018 tmnxVRtrIPv6HighRouteCleared MI gen 0 0
2019 tmnxVRtrStaticRouteCPEStatus MI gen 0 0
2020 tmnxVRtrBfdSessionDeleted MI gen 0 0
2021 tmnxVRtrBfdSessionProtChange MI gen 0 0
2022 tmnxVRtrManagedRouteAddFailed MI gen 0 0
2023 tmnxVRtrFibOccupancyThreshold MI sup 0 0
2024 tmnxVRtrInetAddressAttachFailed MI gen 0 0
2029 tmnxVRtrIfLdpSyncTimerStart WA sup 0 0
2030 tmnxVRtrIfLdpSyncTimerStop WA sup 0 0
=======================================================================
A:ALA-1# show log event-control ospf
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2001 ospfVirtIfStateChange WA gen 0 0
2002 ospfNbrStateChange WA gen 1 0
2003 ospfVirtNbrStateChange WA gen 0 0
2004 ospfIfConfigError WA gen 0 0
2005 ospfVirtIfConfigError WA gen 0 0
2006 ospfIfAuthFailure WA gen 0 0
2007 ospfVirtIfAuthFailure WA gen 0 0
2008 ospfIfRxBadPacket WA gen 0 0
2009 ospfVirtIfRxBadPacket WA gen 0 0
2010 ospfTxRetransmit WA sup 0 0
2011 ospfVirtIfTxRetransmit WA sup 0 0
2012 ospfOriginateLsa WA sup 0 404
2013 ospfMaxAgeLsa WA gen 3 0
2014 ospfLsdbOverflow WA gen 0 0
2015 ospfLsdbApproachingOverflow WA gen 0 0
2016 ospfIfStateChange WA gen 2 0
2017 ospfNssaTranslatorStatusChange WA gen 0 0
2018 vRtrOspfSpfRunsStopped WA gen 0 0
2019 vRtrOspfSpfRunsRestarted WA gen 0 0
2020 vRtrOspfOverloadEntered WA gen 1 0
2021 vRtrOspfOverloadExited WA gen 0 0
2022 ospfRestartStatusChange WA gen 0 0
2023 ospfNbrRestartHelperStatusChange WA gen 0 0
2024 ospfVirtNbrRestartHelperStsChg WA gen 0 0
=======================================================================
A:ALA-1#
A:ALA-1# show log event-control ospf ospfVirtIfStateChange
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2001 ospfVirtIfStateChange WA gen 0 0
=======================================================================
A:ALA-1#
| Label | Description |
|---|---|
Application |
Displays the application name |
ID# |
Displays the event ID number within the application L ID# An ‟L” in front of an ID represents event types that do not generate an associated SNMP notification Most events do generate a notification, only the exceptions are marked with a preceding ‟L” |
Event Name |
Displays the event name |
P |
CL — The event has a cleared severity/priority CR — The event has critical severity/priority IN — The event has indeterminate severity/priority MA — The event has major severity/priority MI — The event has minor severity/priority WA — The event has warning severity/priority |
g/s |
gen — The event will be generated or logged by event control sup — The event will be suppressed or dropped by event control thr — Specifies that throttling is enabled |
Logged |
Displays the number of events logged or generated |
Dropped |
Displays the number of events dropped or suppressed |
file-id
Syntax
file-id [log-file-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays event file log information.
If no command line parameters are specified, a summary output of all event log files is displayed.
Specifying a file ID displays detailed information about the event file log.
Parameters
- log-file-id
Displays detailed information about the specified event file log.
Output
The following output is an example of event file information, and Output fields: log file ID describes the output fields.
Sample output*A:MTUSN945189# show log file-id
=============================================================
File Id List
=============================================================
file-id rollover retention admin backup oper
location location location
-------------------------------------------------------------
1 30 500 cf1: none cf1:
2 30 500 cf1: none cf1:
3 30 500 cf1: none cf1:
4 30 500 cf1: none cf1:
5 30 500 cf1: none cf1:
6 30 500 cf1: none cf1:
7 30 500 cf1: none cf1:
8 30 500 cf1: none cf1:
9 30 500 cf1: none cf1:
10 30 500 cf1: none cf1:
11 30 500 cf1: none cf1:
12 30 500 cf1: none cf1:
13 30 500 cf1: none cf1:
14 30 500 cf1: none cf1:
15 30 500 cf1: none cf1:
16 30 500 cf1: none cf1:
17 30 500 cf1: none cf1:
18 30 500 cf1: none cf1:
=============================================================
*A:MTUSN945189#
A:MTUSN945189# show log file-id 1
=============================================================
File Id List
=============================================================
file-id rollover retention admin backup oper
location location location
-------------------------------------------------------------
1 2800 500 cf1: none cf1:
=============================================================
===============================================================
File Id 1 Location cf1:
===============================================================
file name expired state
---------------------------------------------------------------
cf1:\act\act0101-20010518-085306.xml.gz no complete
=============================================================
*A:MTUSN945189#
| Label | Description |
|---|---|
file-id |
Displays the log file ID |
rollover |
Displays the rollover time for the log file which is how long in between partitioning of the file into a new file |
retention |
Displays the retention time for the file in the system which is how long the file should be retained in the file system |
admin location |
The primary flash device specified for the file location. none — Indicates no specific flash device was specified |
oper location |
Displays the actual flash device on which the log file exists |
file-id |
Displays the log file ID |
rollover |
Displays the rollover time for the log file which is how long in between partitioning of the file into a new file |
retention |
Displays the retention time for the file in the system which is how long the file should be retained in the file system |
file name |
Displays the complete pathname of the file associated with the log ID |
expired |
Indicates whether or not the retention period for this file has passed |
state |
in progress — Indicates the current open log file complete — Indicates the old log file |
filter-id
Syntax
filter-id [filter-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays event log filter policy information.
Parameters
- filter-id
Displays detailed information about the specified event filter policy ID.
Output
The following outputs are examples of event log filter information, and the associated table describe the output fields.
*A:ALA-48>config>log# show log filter-id
=============================================================================
Log Filters
=============================================================================
Filter Applied Default Description
Id Action
-----------------------------------------------------------------------------
1 no forward
5 no forward
10 no forward
1001 yes drop Collect events for Serious Errors Log
=============================================================================
*A:ALA-48>config>log#
| Label | Description |
|---|---|
Filter Id |
Displays the event log filter ID |
Applied |
no — The event log filter is not currently in use by a log ID yes — The event log filter is currently in use by a log ID |
Default Action |
drop — The default action for the event log filter is to drop events not matching filter entries forward — The default action for the event log filter is to forward events not matching filter entries |
Description |
Displays the description string for the filter ID |
*A:ALA-48>config>log# show log filter-id 1001
==========================================================================
Log Filter
==========================================================================
Filter-id : 1001 Applied : yes Default Action: drop
Description : Collect events for Serious Errors Log
--------------------------------------------------------------------------
Log Filter Match Criteria
--------------------------------------------------------------------------
Entry-id : 10 Action : forward
Application : Operator : off
Event Number : 0 Operator : off
Severity : major Operator : greaterThanOrEqual
Subject : Operator : off
Match Type : exact string :
Router : Operator : off
Match Type : exact string :
Description : Collect only events of major severity or higher
--------------------------------------------------------------------------
==========================================================================
*A:ALA-48>config>log#
| Label | Description |
|---|---|
Filter-id |
Displays the event log filter ID |
Applied |
no — The event log filter is not currently in use by a log ID yes — The event log filter is currently in use by a log ID |
Default Action |
drop — The default action for the event log filter is to drop events not matching filter entries forward — The default action for the event log filter is to forward events not matching filter entries |
Description (Filter-id) |
Displays the description string for the filter ID |
Entry-id |
Displays the event log filter entry ID |
Action |
default — There is no explicit action for the event log filter entry and the filter default action is used on matching events drop — The action for the event log filter entry is to drop matching events forward — The action for the event log filter entry is to forward matching events |
Description (Entry-id) |
Displays the description string for the event log filter entry |
Application |
Displays the event log filter entry application match criterion |
Event Number |
Displays the event log filter entry application event ID match criterion |
Severity |
cleared — The log event filter entry application event severity cleared match criterion indeterminate — The log event filter entry application event severity indeterminate match criterion critical — The log event filter entry application event severity critical match criterion major — The log event filter entry application event severity cleared match criterion minor — The log event filter entry application event severity minor match criterion warning — The log event filter entry application event severity warning match criterion |
Subject |
Displays the event log filter entry application event ID subject string match criterion |
Router |
Displays the event log filter entry application event ID router router-instance string match criterion |
Operator |
There is an operator field for each match criteria: application, event number, severity, and subject. equal — Matches when equal to the match criterion GreaterThan — Matches when greater than the match criterion greaterThanOrEqual — Matches when greater than or equal to the match criterion lessThan — Matches when less than the match criterion lessThanOrEqual — Matches when less than or equal to the match criterion notEqual — Matches when not equal to the match criterion off — No operator specified for the match criterion |
log-collector
Syntax
log-collector
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays log collector statistics for the main, security, change and debug log collectors.
Output
The following output is an example of log collector information, and Output fields: log collector describes the output fields.
Sample outputA:ALA-1# show log log-collector
===============================================================================
Log Collectors
===============================================================================
Main Logged : 1224 Dropped : 0
Dest Log Id: 99 Filter Id: 0 Status: enabled Dest Type: memory
Dest Log Id: 100 Filter Id: 1001 Status: enabled Dest Type: memory
Security Logged : 3 Dropped : 0
Change Logged : 3896 Dropped : 0
Debug Logged : 0 Dropped : 0
===============================================================================
A:ALA-1#
| Label | Description |
|---|---|
<Collector Name> |
Main The main event stream contains the events that are not explicitly directed to any other event stream. |
Security The security stream contains all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. |
|
Change The change event stream contains all events that directly affect the configuration or operation of this node. |
|
Debug The debug-trace stream contains all messages in the debug stream. |
|
Dest. Log ID |
Specifies the event log stream destination. |
Filter ID |
The value is the index to the entry which defines the filter to be applied to this log's source event stream to limit the events output to this log's destination. If the value is 0, then all events in the source log are forwarded to the destination. |
Status |
Enabled Logging is enabled. |
Disabled Logging is disabled. |
|
Dest. Type |
Console — A log created with the console type destination displays events to the physical console device Events are displayed to the console screen whether a user is logged in to the console or not A user logged in to the console device or connected to the CLI via a remote telnet or SSH session can also create a log with a destination type of 'session' Events are displayed to the session device until the user logs off When the user logs off, the 'session' type log is deleted Syslog — All selected log events are sent to the syslog address SNMP traps — Events defined as SNMP traps are sent to the configured SNMP trap destinations and are logged in NOTIFICATION-LOG-MIB tables File — All selected log events will be directed to a file on one of the compact flash disks Memory — All selected log events will be directed to an in-memory storage area |
log-id
Syntax
log-id [log-id] [severity severity-level] [application application] [sequence from-seq [to-seq]] [count count] [router router-instance [expression]] [subject subject [regexp]] [ascending | descending]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command displays an event log summary with settings and statistics or the contents of a specific log file, SNMP log, or memory log.
If the command is specified with no command line options, a summary of the defined system logs is displayed. The summary includes log settings and statistics.
If the log ID of a memory, SNMP, or file event log is specified, the command displays the contents of the log. Additional command line options control what and how the contents are displayed.
Contents of logs with console, session, or syslog destinations cannot be displayed. The actual events can only be viewed on the receiving syslog or console device.
Parameters
- log-id
Displays the contents of the specified file log or memory log ID. The log ID must have a destination of an SNMP or file log or a memory log for this parameter to be used.
- severity-level
Displays only events with the specified and higher severity.
- application
Displays only events generated by the specified application.
- expression
Specifies to use a regular expression as match criteria for the router instance string.
- from-seq [to-seq]
Displays the log entry numbers from a particular entry sequence number (from-seq) to another sequence number (to-seq). The to-seq value must be larger than the from-seq value.
If the to-seq number is not provided, the log contents to the end of the log is displayed unless the count parameter is present in which case the number of entries displayed is limited by the count.
- count
Limits the number of log entries displayed to the number specified.
- router-instance
Specifies a router name up to 32 characters to be used in the display criteria.
- subject
Displays only log entries matching the specified text subject string, up to 32 characters. The subject is the object affected by the event. For example the port ID would be the subject for a link-up or link-down event.
- regexp
Specifies to use a regular expression as parameters with the specified subject string.
- ascending | descending
Specifies sort direction. Logs are shown from the newest entry to the oldest in descending sequence number order on the screen. When using the ascending parameter, the log will be shown from the oldest to the newest entry.
Output
The following outputs are examples of event log summary information, and Output fields: log ID describes the output fields.
Sample outputA:ALA-1# show log log-id
=====================================================================
Event Logs
=====================================================================
Log Source Filter Admin Oper Logged Dropped Dest Dest Size
Id Id State State Type Id
--------------------------------------------------------------------
1 none none up down 52 0 file 10 N/A
2 C none up up 41 0 syslog 1 N/A
99 M none up up 2135 0 memory 500
=====================================================================
A:ALA-1#
A:gal171# show log log-id 99
===============================================================================
Event Log 99
===============================================================================
Description : Default System Log
Memory Log contents [size=500 next event=70 (not wrapped)]
69 2007/01/25 18:20:40.00 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
68 2007/01/25 17:48:38.16 UTC WARNING: SYSTEM #2006 Base LOGGER
"New event throttle interval 10, configuration modified"
67 2007/01/25 00:34:53.97 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
66 2007/01/24 22:59:22.00 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
65 2007/01/24 02:08:47.92 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
...
===============================================================================
A:gal171
A:NS061550532>config>log>snmp-trap-group# show log log-id 1
===============================================================================
Event Log 1
===============================================================================
SNMP Log contents [size=100 next event=3 (not wrapped)]
Cannot send to SNMP target address 10.1.1.1.
14 2000/01/05 00:54:09.11 UTC WARNING: MPLS #2007 Base VR 1:
"Instance is in administrative state: inService, operational state: inService"
13 2000/01/05 00:54:09.11 UTC WARNING: MPLS #2008 Base VR 1:
"Interface linkToIxia is in administrative state: inService, operational state: inSe
rvice"
....
===============================================================================
A:NS061550532>config>log>snmp-trap-group#
| Label | Description |
|---|---|
Log Id |
Displays an event log destination |
Source |
no — The event log filter is not currently in use by a log ID yes — The event log filter is currently in use by a log ID |
Filter ID |
Displays the index to the entry that defines the filter to be applied to this log source event stream to limit the events output to this log destination If the value is 0, all events in the source log are forwarded to the destination |
Admin State |
Up — Indicates that the administrative state is up Down — Indicates that the administrative state is down |
Oper State |
Up — Indicates that the operational state is up Down — Indicates that the operational state is down |
Logged |
Displays the number of events that have been sent to the log sources that were forwarded to the log destination |
Dropped |
Displays the number of events sent to the log sources that were not forwarded to the log destination because they were filtered out by the log filter |
Dest. Type |
Console — All selected log events are directed to the system console If the console is not connected, all entries are dropped Syslog — All selected log events are sent to the syslog address SNMP traps — Events defined as SNMP traps are sent to the configured SNMP trap destinations and are logged in NOTIFICATION-LOG-MIB tables File — All selected log events will be directed to a file on one of the compact flash disks Memory — All selected log events will be directed to an in-memory storage area |
Dest ID |
The event log stream destination |
Size |
The allocated memory size for the log |
Time format |
The time format specifies the type of timestamp format for events sent to logs where log ID destination is either syslog or file When the time format is UTC, timestamps are written using the Coordinated Universal Time value When the time format is local, timestamps are written in the system's local time |
snmp-trap-group
Syntax
snmp-trap-group [log-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command displays SNMP trap group configuration information.
Parameters
- log-id
Displays SNMP trap group information only for the specified trap group log ID.
Output
The following output is an example of SNMP trap group information, and Output fields: SNMP trap group describes the output fields.
Sample outputA:SetupCLI>config>log>snmp-trap-group# show log snmp-trap-group 44
===============================================================================
SNMP Trap Group 44
===============================================================================
Description : none
-------------------------------------------------------------------------------
Name : ntt-test
Address : 10.10.10.3
Port : 162
Version : v2c
Community : ntttesting
Sec. Level : none
-------------------------------------------------------------------------------
Name : test2
Address : 10.20.20.5
Port : 162
Version : v2c
Community : ntttesting
Sec. Level : none
===============================================================================
A:SetupCLI>config>log>snmp-trap-group#
| Label | Description |
|---|---|
Log-ID |
The log destination ID for an event stream. |
Address |
The IP address of the trap receiver, |
Port |
The destination UDP port used for sending traps to the destination, expressed as a decimal integer. |
Version |
Specifies the SNMP version format to use for traps sent to the trap receiver. Valid values are snmpv1, snmpv2c, snmpv3. |
Community |
The community string required by snmpv1 or snmpv2c trap receivers. |
Security-Level |
The required authentication and privacy levels required to access the views on this node. |
syslog
Syntax
syslog [syslog-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command displays syslog event log destination summary information or detailed information about a specific syslog destination.
Parameters
- syslog-id
Displays detailed information about the specified syslog event log destination.
Output
The following output is an example of syslog information, and Output fields: syslog describes the output fields.
Sample output*A:ALA-48>config>log# show log syslog
===============================================================================
Syslog Target Hosts
===============================================================================
Id Ip Address Port Sev Level
Below Level Drop Facility Pfx Level
-------------------------------------------------------------------------------
2 unknown 514 info
0 local7 yes
3 unknown 514 info
0 local7 yes
5 unknown 514 info
0 local7 yes
10 unknown 514 info
0 local7 yes
===============================================================================
*A:ALA-48>config>log#
*A:MV-SR>config>log# show log syslog 1
===============================================================================
Syslog Target 1
===============================================================================
IP Address : 192.168.15.22
Port : 514
Log-ids : none
Prefix : Sr12
Facility : local1
Severity Level : info
Prefix Level : yes
Below Level Drop : 0
Description : Linux Station Springsteen
===============================================================================
*A:MV-SR>config>log#
| Label | Description |
|---|---|
Syslog ID |
Displays the syslog ID number for the syslog destination |
IP Address |
Displays the IP address of the syslog target host |
Port |
Displays the configured UDP port number used when sending syslog messages |
Facility |
Displays the facility code for messages sent to the syslog target host |
Severity Level |
Displays the syslog message severity level threshold |
Below Level Dropped |
Displays a count of messages not sent to the syslog collector target because the severity level of the message was above the configured severity The higher the level, the lower the severity |
Prefix Present |
Yes — A log prefix was prepended to the syslog message sent to the syslog host No — A log prefix was not prepended to the syslog message sent to the syslog host |
Description |
Displays a text description stored in the configuration file for a configuration context |
LogPrefix |
Displays the prefix string prepended to the syslog message |
Log-id |
Events are directed to this destination |
Clear commands
log
Syntax
log log-id
Context
clear
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command reinitializes the specified memory or file event log ID. Memory logs are reinitialized and cleared of contents. File logs are manually rolled over by this command.
This command is only applicable to event logs that are directed to file destinations and memory destinations.
SNMP, syslog, and console or session logs are not affected by this command.
Parameters
- log-id
Specifies the event log ID to be initialized or rolled over.