SNMP
This chapter provides information to configure SNMP.
SNMP overview
This section provides an overview of the Simple Network Management Protocol (SNMP).
SNMP architecture
The Service Assurance Manager (SAM) is composed of two elements: managers and agents. The manager is the entity through which network management tasks are facilitated. Agents interface managed objects. Managed devices, such as bridges, hubs, routers, and network servers can contain managed objects. A managed object can be a configuration attribute, performance statistic, or control action that is directly related to the operation of a device.
Managed devices collect and store management information and use Simple Network Management Protocol (SNMP). SNMP is an application-layer protocol that provides a message format to facilitate communication between SNMP managers and agents. SNMP provides a standard framework to monitor and manage devices in a network from a central location.
An SNMP manager controls and monitors the activities of network hosts which use SNMP. An SNMP manager can obtain (get) a value from an SNMP agent or store (set) a value in the agent. The manager uses definitions in the management information base (MIB) to perform operations on the managed device such as retrieving values from variables or blocks of data, replying to requests, and processing traps.
Between the SNMP agent and the SNMP manager the following actions can occur:
The manager can get information from the agent.
The manager can set the value of a MIB object that is controlled by an agent.
The agent can send traps to notify the manager of significant events that occur on the router.
Management information base
An MIB is a formal specifications document with definitions of management information used to remotely monitor, configure, and control a managed device or network system. The agent’s management information consists of a set of network objects that can be managed with SNMP. Object identifiers are unique object names that are organized in a hierarchical tree structure. The main branches are defined by the Internet Engineering Task Force (IETF). When requested, the Internet Assigned Numbers Authority (IANA) assigns a unique branch for use by a private organization or company. The branch assigned to Nokia (TiMetra) is 1.3.6.1.4.1.6527.
The SNMP agent provides management information to support a collection of IETF specified MIBs and a number of MIBs defined to manage device parameters and network data unique to the 7210 SAS.
SNMP protocol operations
Between the SNMP agent and the SNMP manager the following actions can occur:
The manager can get information from the agent.
The manager can set the value of a MIB object that is controlled by an agent.
The agent notifies the manager of significant events that occur on the router.
SNMP versions
The agent supports multiple versions of the SNMP protocol as follows:
SNMP Version 1 (SNMPv1) is the original Internet-standard network management framework.
SNMPv1 uses a community string match for authentication.
The implementation uses SNMPv2c, the community-based administrative framework for SNMPv2. SNMPv2c uses a community string match for authentication.
In SNMP Version 3 (SNMPv3), USM defines the user authentication and encryption features. View Access Control MIB (VACM) defines the user access control features. The SNMP-COMMUNITY-MIB is used to associate SNMPv1/SNMPv2c community strings with SNMPv3 VACM access control.
SNMPv3 uses a username match for authentication.
Management information access control
By default, the implementation of SNMP uses SNMPv3. SNMPv3 incorporates security model and security level features. A security model is the authentication type for the group and the security level is the permitted level of security within a security model. The combination of the security level and security model determines which security mechanism handles an SNMP packet.
To implement SNMPv1 and SNMPv2c configurations, several access groups are predefined. These access groups provide standard read-only, read-write, and read-write-all access groups and views that can be assigned community strings. To implement SNMP with security features, security models, security levels, and USM communities must be explicitly configured. Optionally, additional views which specify more specific OIDs (MIB objects in the subtree) can be configured.
Access to the management information in as SNMPv1/SNMPv2c agent is controlled by the inclusion of a community name string in the SNMP request. The community defines the sub-set of the agent managed objects can be accessed by the requester. It also defines what type of access is allowed: read-only or read-write.
The use of community strings provide minimal security and context checking for both agents and managers that receive requests and initiate trap operations. A community string is a text string that acts like a password to allow access to the agent on the router.
The Nokia implementation of SNMP has defined three levels of community-named access:
Read-Only permission
Grants only read access to objects in the MIB, except security objects.
Read-Write permission
Grants read and write access to all objects in the MIB, except security objects.
Read-Write-All permission
Grants read and write access to all objects in the MIB, including security objects.
User-based security model community strings
User-based security model (USM) community strings associates a community string with an SNMPv3 access group and its view. The access granted with a community string is restricted to the scope of the configured group.
Views
Views control the access to a managed object. The total MIB of a router can be viewed as a hierarchical tree. When a view is created, either the entire tree or a portion of the tree can be specified and made available to a user to manage the objects contained in the subtree. Object identifiers (OIDs) uniquely identify managed objects. A view defines the type of operations for the view such as read, write, or notify.
OIDs are organized in a hierarchical tree with specific values assigned to different organizations. A view defines a subset of the agent’s managed objects controlled by the access rules associated with that view.
Predefined views are available that are particularly useful when configuring SNMPv1 and SNMPv2c.
The Nokia SNMP agent associates SNMPv1 and SNMPv2c community strings with a SNMPv3 view.
Access groups
Access groups associate a user group and a security model to the views the group can access. An access group is defined by a unique combination of a group name, security model (SNMPv1, SNMPv2c, or SNMPv3), and security level (no-authorization-no privacy, authorization-no-privacy, or privacy).
An access group, in essence, is a template which defines a combination of access privileges and views. A group can be associated with one or more network users to control their access privileges and views.
Additional access parameters must be explicitly configured if the preconfigured access groups and views for SNMPv1 and SNMPv2c do not meet your security requirements.
Users
By default, authentication and encryption parameters are not configured. Authentication parameters which a user must use to be validated by the device can be modified. SNMP authentication allows the device to validate the managing node that issued the SNMP message and determine whether the message has been tampered with.
User access and authentication privileges must be explicitly configured. In a user configuration, a user is associated with an access group, which is a collection of users who have common access privileges and views (see Access groups).
Which SNMP version to use?
SNMPv1 and SNMPv2c do not provide security, authentication, or encryption. Without authentication, a non authorized user could perform SNMP network management functions and eavesdrop on management information as it passes from system to system. Many SNMPv1 and SNMPv2c implementations are restricted read-only access, which, in turn, reduces the effectiveness of a network monitor in which network control applications cannot be supported.
To implement SNMPv3, an authentication and encryption method must be assigned to a user to be validated by the device. SNMP authentication allows the router to validate the managing node that issued the SNMP message and determine whether the message was tampered with.
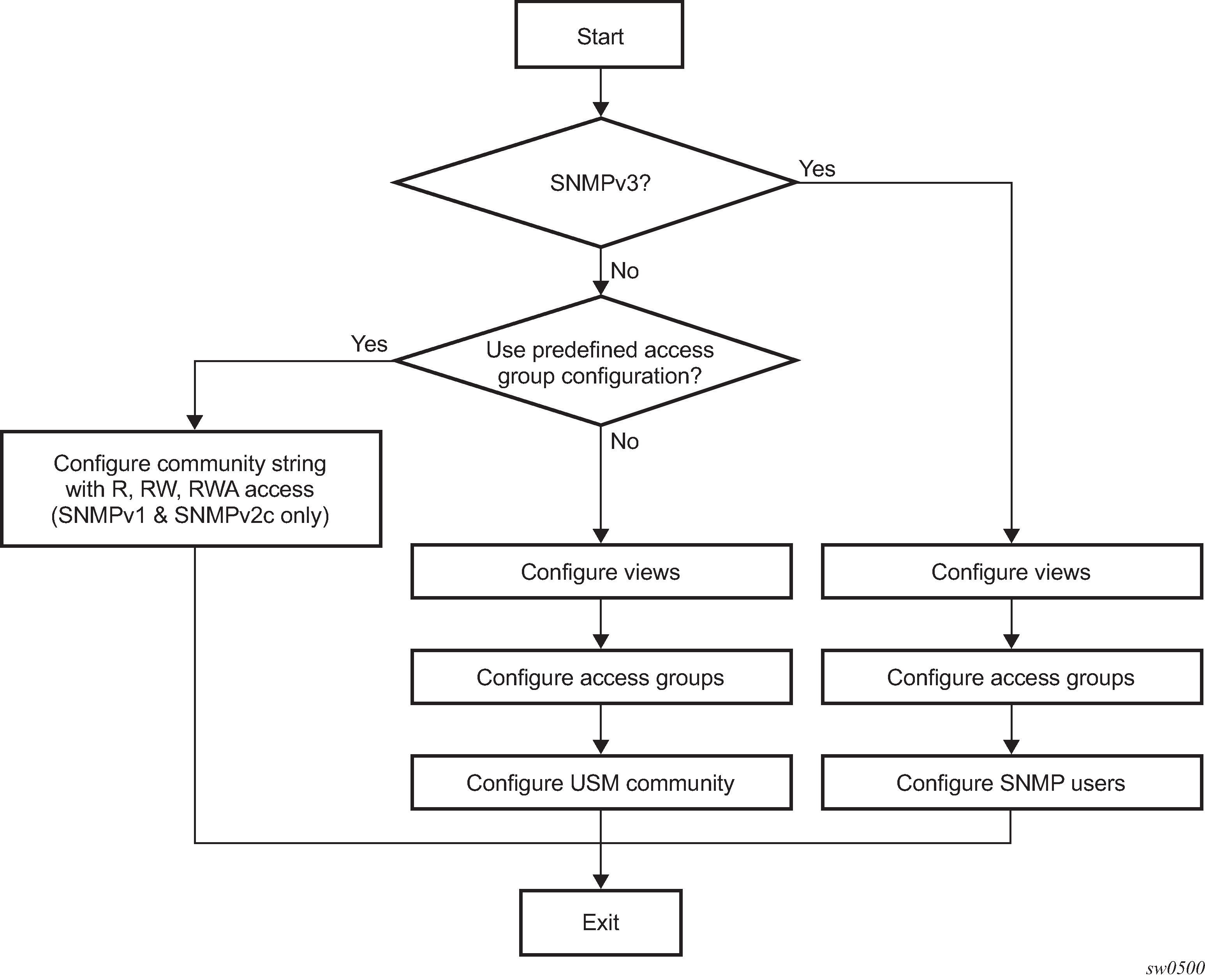
The following figure shows the configuration requirements to implement SNMPv1/SNMPv2c and SNMPv3.
Configuration notes
This section describes SNMP configuration guidelines and restrictions.
General
To avoid management systems attempting to manage a partially booted system, SNMP remains in a shutdown state if the configuration file fails to complete during system startup. While shutdown, SNMP gets and sets are not processed. However, notifications are issued if an SNMP trap group has been configured.
To enable SNMP, the portions of the configuration that failed to load must be initialized properly. Start SNMP with the config>system>snmp>no shutdown CLI command.
Use caution when changing the SNMP engine ID. If the SNMP engine ID is changed in the config>system>snmp> engineID engine-id context, the current configuration must be saved and a reboot must be executed. If not, the previously configured SNMP communities and logger trap-target notify communities are not valid for the new engine ID.
SNMP dying gasp uses system IP to send out packet. Therefore, the system IP must be configured before configuring SNMP dying gasp.
Note:The SNMP dying gasp feature is not supported on the 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p.
Configuring SNMP with CLI
This section provides information about configuring SNMP with CLI.
SNMP configuration overview
This section describes how to configure SNMP components which apply to SNMPv1 and SNMPv2c, and SNMPv3 on the router.
Configuring SNMPv1 and SNMPv2c
Nokia routers are based on SNMPv3. To use the routers with SNMPv1 and/or SNMPv2c, SNMP community strings must be configured. Three predefined access methods are available when SNMPv1 or SNMPv2c access is required. Each access method (r, rw, or rwa) is associated with an SNMPv3 access group that determines the access privileges and the scope of managed objects available. The community command is used to associate a community string with a specific access method and the required SNMP version (SNMPv1 or SNMPv2c). The access methods are:
Read-Only
Grants read only access to the entire management structure with the exception of the security area.
Read-Write
Grants read and write access to the entire management structure with the exception of the security area.
Read-Write-All
Grants read and write access to the entire management structure, including security.
If the predefined access groups do not meet your access requirements, then additional access groups and views can be configured. The usm-community command is used to associate an access group with an SNMPv1 or SNMPv2c community string.
SNMP trap destinations are configured in the config>log>snmp-trap-group context.
Configuring SNMPv3
By default, the 7210 SAS implements SNMPv3. If security features other than the default views are required, the following parameters must be configured:
-
views
-
access groups
-
SNMP users
Basic SNMP security configuration
This section provides information to configure SNMP parameters and provides examples of common configuration tasks. The minimal SNMP parameters are:
For SNMPv1 and SNMPv2: configure community string parameters.
For SNMPv3:
configure view parameters
configure SNMP group
configure access parameters
configure user with SNMP parameters
SNMP default views, access groups, and attempts parameters
A:ALA-1>config>system>security>snmp# info detail
----------------------------------------------
view iso subtree 1
mask ff type included
exit
view no-security subtree 1
mask ff type included
exit
view no-security subtree 1.3.6.1.6.3
mask ff type excluded
exit
view no-security subtree 1.3.6.1.6.3.10.2.1
mask ff type included
exit
view no-security subtree 1.3.6.1.6.3.11.2.1
mask ff type included
exit
view no-security subtree 1.3.6.1.6.3.15.1.1
mask ff type included
exit
access group snmp-ro security-model snmpv1 security-level no-auth-
no-privacy read no-security notify no-security
access group snmp-ro security-model snmpv2c security-level no-auth-
no-privacy read no-security notify no-security
access group snmp-rw security-model snmpv1 security-level no-auth-
no-privacy read no-security write no-security notify no-security
access group snmp-rw security-model snmpv2c security-level no-auth-
no-privacy read no-security write no-security notify no-security
access group snmp-rwa security-model snmpv1 security-level no-auth-
no-privacy read iso write iso notify iso
access group snmp-rwa security-model snmpv2c security-level no-auth-
no-privacy read iso write iso notify iso
access group snmp-trap security-model snmpv1 security-level no-auth-
no-privacy notify iso
access group snmp-trap security-model snmpv2c security-level no-
auth-no-privacy notify iso
attempts 20 time 5 lockout 10
Configuring SNMP components
Use the following syntax to configure the SNMP scenarios.
config>system>security>snmp
access group group-name security-model security-model security-level security-level [context context-name [prefix-match]] [read view-name-1] [write view-name-2] [notify view-name-3]
attempts [count] [time minutes1] [lockout minutes2]
community community-string access-permissions [version SNMP version]
usm-community community-string group group-name
view view-name subtree oid-value
mask mask-value [type {included|excluded}]Configuring a community string
SNMPv1 and SNMPv2c community strings are used to define the relationship between an SNMP manager and agent. The community string acts like a password to allow access to the agent. The access granted with a community string is restricted to the scope of the configured group.
One or more of these characteristics associated with the string can be specified:
Read-only, read-write, and read-write-all permission for the MIB objects accessible to the community.
The SNMP version, SNMPv1 or SNMPv2c.
Default access features are preconfigured by the agent for SNMPv1/SNMPv2c.
Use the following CLI syntax to configure community options:
config>system>security>snmp
community community-string access-permissions [version SNMP-version]SNMP community configuration
*A:cses-A13>config>system>security>snmp# info
----------------------------------------------
community "uTdc9j48PBRkxn5DcSjchk" hash2 rwa version both
community "Lla.RtAyRW2" hash2 r version v2c
community "r0a159kIOfg" hash2 r version both
----------------------------------------------
*A:cses-A13>config>system>security>snmp#
Configuring view options
Use the following CLI syntax to configure view options:
config>system>security>snmp
view view-name subtree oid-value
mask mask-value [type {included|excluded}]View configuration
*A:cses-A13>config>system>security>snmp# info
----------------------------------------------
view "testview" subtree "1"
mask ff
exit
view "testview" subtree "1.3.6.1.2"
mask ff type excluded
exit
community "uTdc9j48PBRkxn5DcSjchk" hash2 rwa version both
community "Lla.RtAyRW2" hash2 r version v2c
community "r0a159kIOfg" hash2 r version both
----------------------------------------------
*A:cses-A13>config>system>security>snmp#Configuring access options
The access command creates an association between a user group, a security model and the views that the user group can access. Access must be configured unless security is limited to the preconfigured access groups and views for SNMPv1 and SNMPv2. An access group is defined by a unique combination of the group name, security model and security level.
Use the following CLI syntax to configure access features:
config>system>security>snmp
access group group-name security-model security-model security-level security-level [context context-name [prefix-match]] [read view-name-1] [write view-name-2] [notify view-name-3]
Access configuration with the view configurations
*A:cses-A13>config>system>security>snmp# info
----------------------------------------------
view "testview" subtree "1"
mask ff
exit
view "testview" subtree "1.3.6.1.2"
mask ff type excluded
exit
access group "test" security-model usm security-level auth-no-pr
ivacy read "testview" write "testview" notify "testview"
community "uTdc9j48PBRkxn5DcSjchk" hash2 rwa version both
community "Lla.RtAyRW2" hash2 r version v2c
community "r0a159kIOfg" hash2 r version both
----------------------------------------------
*A:cses-A13>config>system>security>snmp#Use the following CLI syntax to configure user group and authentication parameters:
config>system>security# user user-name
access [ftp] [snmp] [console]
snmp
authentication [none]|[[hash]{md5 key|sha key} privacy {none|des-key key}]
group group-name
The following displays a user’s SNMP configuration example.
A:ALA-1>config>system>security# info
----------------------------------------------
user "testuser"
access snmp
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy none
group testgroup
exit
exit
...
----------------------------------------------
A:ALA-1>config>system>security#
Configuring USM community options
User-based security model (USM) community strings associate a community string with an SNMPv3 access group and its view. The access granted with a community string is restricted to the scope of the configured group.
By default, the implementation of SNMP uses SNMPv3. However, to implement SNMPv1 and SNMPv2c, USM community strings must be explicitly configured.
Use the following CLI syntax to configure USM community options:
config>system>security>snmp
usm-community community-string group group-nameSNMP community configuration
A:ALA-1>config>system>security>snmp# info
----------------------------------------------
view "testview" subtree "1"
mask ff
exit
view "testview" subtree "1.3.6.1.2"
mask ff type excluded
exit
access group "test" security-model usm security-level auth-no-pr
ivacy read "testview" write "testview" notify "testview"
community "uTdc9j48PBRkxn5DcSjchk" hash2 rwa version both
community "Lla.RtAyRW2" hash2 r version v2c
community "r0a159kIOfg" hash2 r version both
----------------------------------------------
A:ALA-1>config>system>security>snmp#
The group grouptest is configured in the config>system>security>snmp> access CLI context.
Configuring other SNMP parameters
Use the following CLI syntax to modify the system SNMP options:
config>system>snmp
engineID engine-id
general-port port
packet-size bytes
no shutdownSystem SNMP default values
A:ALA-104>config>system>snmp# info detail
----------------------------------------------
shutdown
engineID "0000xxxx000000000xxxxx00"
packet-size 1500
general-port 161
----------------------------------------------
A:ALA-104>config>system>snmp#
SNMP command reference
Command hierarchies
Configuration commands
SNMP system commands
config
- system
- snmp
- engineID engine-id
- no engineID
- general-port port
- no general-port
- packet-size bytes
- no packet-size
- [no] shutdown
SNMP security commands
config
- system
- security
- snmp
- access group group-name security-model security-model security-level security-level [context context-name [prefix-match]] [read view-name-1] [write view-name-2] [notify view-name-3]
- no access group group-name [security-model security-model] [security-level security-level] [context context-name [prefix-match]] [read view-name-1] [write view-name-2] [notify view-name-3
- attempts [count] [time minutes1] [lockout minutes2]
- no attempts
- community community-string [hash | hash2] access-permissions [version SNMP-version]
- no community community-string [hash | hash2]
- usm-community community-string [hash | hash2] group group-name
- no usm-community community-string [hash | hash2]
- view view-name subtree oid-value
- no view view-name [subtree oid-value]
- mask mask-value [type {included | excluded}]
- no mask
The following commands configure user-specific SNMP features. See the Security section for CLI syntax and command descriptions.
config
- system
- security
- [no] users user-name
- [no] snmp
- authentication {[none] | [[hash] {md5 key-1 | sha key-1} privacy {privacy-level key-2}]
- group group-name
- [no] group
Show commands
show
- snmp
- system
- information
- security
- access-group [group-name]
- authentication [statistics]
- keychain [key-chain] [detail]
- management-access-filter
- ip-filter [entry entry-id]
- password-options
- profile [profile-name]
- snmp
- community [community-string]
- ssh
- user [user-id] [detail]
- view [view-name] [detail]
Command descriptions
Configuration commands
SNMP system commands
snmp
Syntax
snmp
Context
config>system
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure SNMP parameters.
engineID
Syntax
[no] engineID engine-id
Context
config>system>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command sets the SNMP engineID to uniquely identify the SNMPv3 node. By default, the engineID is generated using information from the system backplane.
If SNMP engine ID is changed in the config>system>snmp>engineID context, the current configuration must be saved and a reboot must be executed. If not, the previously configured SNMP communities and logger trap-target notify communities are not valid for the new engine ID.
In conformance with IETF standard RFC 2274, User-based Security Model (USM) for version 3 of the Simple Network Management Protocol (SNMPv3), hashing algorithms which generate SNMPv3 MD5 or SHA security digest keys use the engineID. Changing the SNMP engineID invalidates all SNMPv3 MD5 and SHA security digest keys and may render the node unmanageable.
When a chassis is replaced, use the engine ID of the first system and configure it in the new system to preserve SNMPv3 security keys. This allows management stations to use their existing authentication keys for the new system.
Ensure that the engine IDs are not used on multiple systems. A management domain can only have one instance of each engineID.
The no form of this command reverts to the default.
Default
the engine ID is system generated
Parameters
- engine-id
Specifies an identifier from 10 to 64 hexadecimal digits (5 to 32 octet number), uniquely identifying this SNMPv3 node. This string is used to access this node from a remote host with SNMPv3.
general-port
Syntax
general-port port-number
no general-port
Context
config>system>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the port number used by this node to receive SNMP request messages and to send replies. SNMP notifications generated by the agent are sent from the port specified in the config log snmp-trap-group trap-target command.
The no form of this command reverts to the default value.
Default
161
Parameters
- port-number
Specifies the port number used to send SNMP traffic other than traps.
packet-size
Syntax
packet-size bytes
no packet-size
Context
config>system>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the maximum SNMP packet size generated by this node. If the packet size exceeds the MTU size of the egress interface the packet is fragmented.
The no form of this command reverts to the default value.
Default
1500
Parameters
- bytes
Specifies the SNMP packet size, in bytes.
shutdown
Syntax
[no] shutdown
Context
config>system>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively disables SNMP agent operations. System management can then only be performed using the command line interface (CLI). Shutting down SNMP does not remove or change configuration parameters other than the administrative state. This command does not prevent the agent from sending SNMP notifications to any configured SNMP trap destinations. SNMP trap destinations are configured under the config>log>snmp-trap-group context.
This command is automatically invoked in the event of a reboot when the processing of the configuration file fails to complete or when an SNMP persistent index file fails while the bof persist on command is enabled.
The no form of this command administratively enables SNMP.
Default
no shutdown
SNMP security commands
snmp
Syntax
snmp
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure SNMPv1, SNMPv2, and SNMPv3 parameters.
access
Syntax
[no] access group group-name security-model security-model security-level security-level [context context-name [prefix-match]] [read view-name-1] [write view-name-2] [notify view-name-3]
Context
config>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates an association between a user group, a security model, and the views that the user group can access. Access parameters must be configured unless security is limited to the preconfigured access groups and views for SNMPv1 and SNMPv2. An access group is defined by a unique combination of the group name, security model and security level.
Access must be configured unless security is limited to SNMPv1/SNMPv2c with community strings. See the community command for more information.
Default access group configurations cannot be modified or deleted.
Use the no access group group-name command to remove the user group with associated security models and security levels
Use the no access group group-name security-model {snmpv1 | snmpv2c | usm} security-level {no-auth-no-privacy | auth-no-privacy | privacy} command to remove a security model and security level combination from a group.
Parameters
- group-name
Specifies a unique group name, up to 32 characters.
- security-model {snmpv1 | snmpv2c | usm}
Specifies the security model required to access the views configured in this node. A group can have multiple security models. For example, one view may only require SNMPv1/ SNMPv2c access while another view may require USM (SNMPv3) access rights.
- security-level {no-auth-no-priv | auth-no-priv | privacy}
Specifies the required authentication and privacy levels to access the views configured in this node.
- security-level no-auth-no-privacy
Specifies that no authentication and no privacy (encryption) is required. When configuring the user’s authentication, select the none option.
- security-level auth-no-privacy
Specifies that authentication is required but privacy (encryption) is not required. When this option is configured, both the group and the user must be configured for authentication.
- security-level privacy
Specifies that both authentication and privacy (encryption) is required. When this option is configured, both the group and the user must be configured for authentication. The user must also be configured for privacy.
- context context-name
Specifies a set of SNMP objects that are associated with the context-name. The context-name is treated as either a full context-name string or a context name prefix depending on the keyword specified (exact or prefix).
- read view-name
Specifies the keyword and variable of the view to read the MIB objects. This command must be configured for each view to which the group has read access.
- write view-name
Specifies the keyword and variable of the view to configure the contents of the agent, up to 32 characters. This command must be configured for each view to which the group has write access.
- notify view-name
Specifies keyword and variable of the view to send a trap about MIB objects. This command must be configured for each view to which the group has notify access.
attempts
Syntax
attempts [count] [time minutes1] [lockout minutes2]
no attempts
Context
config>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a threshold value of unsuccessful SNMP connection attempts allowed in a specified time frame. The command parameters are used to counter denial of service (DOS) attacks through SNMP.
If the threshold is exceeded, the host is locked out for the lockout time period.
If multiple attempts commands are entered, each command overwrites the previously entered command.
The no form of this command reverts the parameters to the default values.
Default
attempts 20 time 5 lockout 10
Parameters
- count
Specifies the number of unsuccessful SNMP attempts allowed for the specified time.
- time minutes1
Specifies the period of time, in minutes, that a specified number of unsuccessful attempts can be made before the host is locked out.
- lockout minutes2
Specifies the lockout period, in minutes, where the host is not allowed to login.
When the host exceeds the attempted count times in the specified time, that host is locked out from any further login attempts for the configured time period.
community
Syntax
community community-string [hash | hash2] access-permissions [version SNMP-version]
no community community-string]
Context
config>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates SNMP community strings for SNMPv1 and SNMPv2c access. This command is used in combination with the predefined access groups and views. To create custom access groups and views and associate them with SNMPv1 or SNMPv2c access, use the usm-community command.
When configured, community implies a security model for SNMPv1 and SNMPv2c only.
For SNMPv3 security, the access command must be configured.
The no form of this command removes a community string.
Parameters
- community-string
Specifies the SNMPv1 / SNMPv2c community string.
- access-permissions
Specifies the access permissions.
- version {v1 | v2c | both}
Keyword to configure the scope of the community string to be for SNMPv1, SNMPv2c, or both SNMPv1 and SNMPv2c access.
usm-community
Syntax
usm-community community-string [hash | hash2] group group-name
no usm-community community-string [hash | hash2]
Context
config>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command is used to associate a community string with an SNMPv3 access group and its view. The access granted with a community string is restricted to the scope of the configured group.
The Nokia implementation of SNMP uses SNMPv3. To implement SNMPv1 and SNMPv2c configurations, several access groups are predefined. To implement SNMP with security features (Version 3), security models, security levels, and USM communities must be explicitly configured. Optionally, additional views which specify more specific OIDs (MIB objects in the subtree) can be configured.
The no form of this command removes a community string.
Parameters
- community-string
Specifies the SNMPv1/SNMPv2c community string to determine the SNMPv3 access permissions to be used.
- group
Specifies the group that governs the access rights of this community string. This group must be configured first in the config>system>security>snmp>access>group context.
view
Syntax
view view-name subtree oid-value
no view view-name [subtree oid-value]
Context
config>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a view. Views control the accessibility of a MIB object within the configured MIB view and subtree. Object identifiers (OIDs) uniquely identify MIB objects in the subtree. OIDs are organized hierarchically with specific values assigned by different organizations.
After the subtree (OID) is identified, a mask can be created to select the portions of the subtree to be included or excluded for access using this particular view. See the mask command for more information. Views configured with this command can subsequently be used in read, write, and notify commands which are used to assign specific access group permissions to created views and assigned to particular access groups.
Multiple subtrees can be added or removed from a view name to tailor a view to the requirements of the user access group.
The no view view-name command removes a view and all subtrees.
The no view view-name subtree oid-value removes a sub-tree from the view name.
Parameters
- view-name
Specifies a view name, up to 32 characters.
- oid-value
Specifies the object identifier (OID) value for the view-name. This value, for example, 1.3.6.1.6.3.11.2.1, combined with the mask and include and exclude statements, configures the access available in the view.
It is possible to have a view with different subtrees with their own masks and include and exclude statements. This allows for customizing visibility and write capabilities to specific user requirements.
mask
Syntax
mask mask-value [type {included | excluded}]
no mask
Context
config>system>security>snmp>view
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the mask value and the mask type and, along with the oid-value configured in the view command, determines the access of each sub-identifier of an object identifier (MIB subtree) in the view.
Each bit in the mask corresponds to a sub-identifier position. For example, the most significant bit for the first sub-identifier, the next most significant bit for the second sub-identifier, and so on. If the bit position on the sub-identifier is available, it can be included or excluded.
For example, the MIB subtree that represents MIB-II is 1.3.6.1.2.1. The mask that catches all MIB-II would be 0xfc or 0b11111100.
Only a single mask may be configured per view and OID value combination. If more than one entry is configured, each subsequent entry overwrites the previous entry.
Per RFC 2575, View-based Access Control Model (VACM) for the Simple Network Management Protocol (SNMP), each MIB view is defined by two sets of view subtrees, the included view subtrees and the excluded view subtrees. Every such view subtree, both the included and the excluded ones, are defined in this table. To determine whether a particular object instance is in a particular MIB view, compare the object instance’s object identifier (OID) with each of the MIB view’s active entries in this table. If none match, the object instance is not in the MIB view. If one or more match, the object instance is included in, or excluded from, the MIB view according to the value of vacmViewTreeFamilyType in the entry whose value of vacmViewTreeFamilySubtree has the most sub-identifiers.
The no form of this command removes the mask from the configuration.
Parameters
- mask-value
Specifies the mask value associated with the OID value determines whether the sub-identifiers are included or excluded from the view. (Default: all 1s)
The mask can be entered in the following formats:
hexadecimal, for example, 0xfc
binary, for example, 0b11111100
Note:If the number of bits in the bit mask is less than the number of sub-identifiers in the MIB subtree, the mask is extended with ones until the mask length matches the number of sub-identifiers in the MIB subtree.
- type {included | excluded}
Specifies whether to include or exclude MIB subtree objects.
Show commands
information
Syntax
information
Context
show>system
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays the SNMP configuration and statistics.
Output
The following output is an example of SNMP configuration and statistics information, and Output fields: system information describes the output fields.
Sample outputSample output for 7210 SAS D:
*A:SAS-D>show>system# information
===============================================================================
System Information
===============================================================================
System Name : SAS-D
System Type : 7210 SAS-D 6F4T-1
System Version : B-3.0.S66
System Contact :
System Location :
System Coordinates :
System Up Time : 10 days, 01:24:01.43 (hr:min:sec)
SNMP Port : 161
SNMP Engine ID : 0000197f0000003f11abca11
SNMP Max Message Size : 1500
SNMP Admin State : Disabled
SNMP Oper State : Disabled
SNMP Index Boot Status : Not Persistent
SNMP Sync State : N/A
Tel/Tel6/SSH/FTP Admin : Disabled/Disabled/Enabled/Disabled
Tel/Tel6/SSH/FTP Oper : Down/Down/Up/Down
BOF Source : N/A
Image Source : primary
Config Source : N/A
Last Booted Config File: N/A
Last Boot Cfg Version : N/A
Last Boot Config Header: N/A
Last Boot Index Version: N/A
Last Boot Index Header : N/A
Last Saved Config : cf1:\smitha.cfg
Time Last Saved : 1970/01/01 00:04:11
Changes Since Last Save: Yes
User Last Modified : admin
Time Last Modified : 1970/01/11 00:44:21
Max Cfg/BOF Backup Rev : 5
Cfg-OK Script : N/A
Cfg-OK Script Status : not used
Cfg-Fail Script : N/A
Cfg-Fail Script Status : not used
Management IP Addr : 0.0.0.0/0
Primary DNS Server : N/A
Secondary DNS Server : N/A
Tertiary DNS Server : N/A
DNS Domain :
DNS Resolve Preference : ipv4-only
BOF Static Routes : None
===============================================================================
*A:SAS-D>show>system#
Label |
Description |
|---|---|
System Name |
The name configured for the device |
System Contact |
The text string that identifies the contact name for the device |
System Location |
The text string that identifies the location of the device |
System Coordinates |
The text string that identifies the system coordinates for the device location For example, ‟37.390 -122.0550" is read as latitude 37.390 north and longitude 122.0550 west. |
System Up Time |
The time since the last reboot |
SNMP Port |
The port which SNMP sends responses to management requests |
SNMP Engine ID |
The ID for either the local or remote SNMP engine to uniquely identify the SNMPv3 node |
SNMP Max Message Size |
The maximum size SNMP packet generated by this node |
SNMP Admin State |
Enabled — SNMP is administratively enabled Disabled — SNMP is administratively disabled |
SNMP Oper State |
Enabled — SNMP is operationally enabled Disabled — SNMP is operationally disabled |
SNMP Index Boot Status |
Persistent — Persistent indexes at the last system reboot was enabled Disabled — Persistent indexes at the last system reboot was disabled |
SNMP Sync State |
The state when the synchronization of configuration files between the primary and secondary s finish |
Telnet/SSH/FTP Admin |
Displays the administrative state of the Telnet, SSH, and FTP sessions |
Telnet/SSH/FTP Oper |
Displays the operational state of the Telnet, SSH, and FTP sessions |
BOF Source |
The boot location of the BOF |
Image Source |
primary — Specifies whether the image was loaded from the primary location specified in the BOF secondary — Specifies whether the image was loaded from the secondary location specified in the BOF tertiary — Specifies whether the image was loaded from the tertiary location specified in the BOF |
Config Source |
primary — Specifies whether the configuration was loaded from the primary location specified in the BOF secondary — Specifies whether the configuration was loaded from the secondary location specified in the BOF tertiary — Specifies whether the configuration was loaded from the tertiary location specified in the BOF |
Last Booted Config File |
Displays the URL and filename of the configuration file used for the most recent boot |
Last Boot Cfg Version |
Displays the version of the configuration file used for the most recent boot |
Last Boot Config Header |
Displays header information of the configuration file used for the most recent boot |
Last Boot Index Version |
Displays the index version used in the most recent boot |
Last Boot Index Header |
Displays the header information of the index used in the most recent boot |
Last Saved Config |
Displays the filename of the last saved configuration |
Time Last Saved |
Displays the time the configuration was most recently saved |
Changes Since Last Save |
Yes — The configuration changed since the last save No — The configuration has not changed since the last save |
Time Last Modified |
Displays the time of the last modification |
Max Cfg/BOF Backup Rev |
The maximum number of backup revisions maintained for a configuration file This value also applies to the number of revisions maintained for the BOF. |
Cfg-OK Script |
URL — The location and name of the CLI script file executed following successful completion of the boot-up configuration file execution N/A — No CLI script file is executed |
Cfg-OK Script Status |
Successful/Failed — The results from the execution of the CLI script file specified in the Cfg-OK Script location Not used — No CLI script file was executed |
Cfg-Fail Script |
URL — The location and name of the CLI script file executed following a failed boot-up configuration file execution Not used — No CLI script file was executed |
Cfg-Fail Script Status |
Successful/Failed — The results from the execution of the CLI script file specified in the Cfg-Fail Script location Not used — No CLI script file was executed |
Management IP address |
The Management IP address of the node |
DNS Server |
The DNS address of the node |
DNS Domain |
The DNS domain name of the node |
BOF Static Routes |
To — The static route destination Next Hop — The next hop IP address used to reach the destination Metric — Displays the priority of this static route versus other static routes None — No static routes are configured |
access-group
Syntax
access-group group-name
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays access-group information.
Output
The following output is an example of access group information, and Output fields: security access group describes the output fields.
Sample outputA:ALA-1# show system security access-group
===============================================================================
Access Groups
===============================================================================
group name security security read write notify
model level view view view
-------------------------------------------------------------------------------
snmp-ro snmpv1 none no-security no-security
snmp-ro snmpv2c none no-security no-security
snmp-rw snmpv1 none no-security no-security no-security
snmp-rw snmpv2c none no-security no-security no-security
snmp-rwa snmpv1 none iso iso iso
snmp-rwa snmpv2c none iso iso iso
snmp-trap snmpv1 none iso
snmp-trap snmpv2c none iso
-------------------------------------------------------------------------------
No. of Access Groups: 8
===============================================================================
A:ALA-1#
A:ALA-1# show system security access-group detail
===============================================================================
Access Groups
===============================================================================
group name security security read write notify
model level view view view
-------------------------------------------------------------------------------
snmp-ro snmpv1 none no-security no-security
-------------------------------------------------------------------------------
No. of Access Groups:
...
===============================================================================
A:ALA-1#
Label |
Description |
|---|---|
Group name |
The access group name |
Security model |
The security model required to access the views configured in this node |
Security level |
Specifies the required authentication and privacy levels to access the views configured in this node |
Read view |
Specifies the view to read the MIB objects |
Write view |
Specifies the view to configure the contents of the agent |
Notify view |
Specifies the view to send a trap about MIB objects |
No. of access groups |
The total number of configured access groups |
authentication
Syntax
authentication [statistics]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays authentication information.
Output
The following output is an example of authentication information, and Output fields: authentication describes the output fields.
Sample outputA:ALA-49>show>system>security# authentication
===============================================================================
Authentication sequence : radius tacplus local
===============================================================================
server address status type timeout(secs) single connection retry count
-------------------------------------------------------------------------------
10.10.10.103 up radius 5 n/a 5
10.10.0.1 up radius 5 n/a 5
10.10.0.2 up radius 5 n/a 5
10.10.0.3 up radius 5 n/a 5
-------------------------------------------------------------------------------
radius admin status : down
tacplus admin status : up
health check : enabled
-------------------------------------------------------------------------------
No. of Servers: 4
===============================================================================
A:ALA-49>show>system>security#
Label |
Description |
|---|---|
sequence |
The authentication order in which password authentication, authorization, and accounting is attempted among RADIUS, TACACS+, and local passwords |
server address |
The address of the RADIUS, TACACS+, or local server |
status |
The status of the server |
type |
The type of server |
timeout (secs) |
Number of seconds the server waits before timing out |
single connection |
Specifies whether a single connection is established with the server The connection is kept open and is used by all the Telnet/SSH/FTP sessions for AAA operations. |
retry count |
The number of attempts to retry contacting the server |
radius admin status |
The administrative status of the RADIUS protocol operation |
tacplus admin status |
The administrative status of the TACACS+ protocol operation |
health check |
Specifies whether the RADIUS and TACACS+ servers are periodically monitored Each server is contacted every 30 seconds. If in this process a server is found to be unreachable, or a previously unreachable server starts responding, based on the type of the server, a trap is sent. |
No. of Servers |
The total number of servers configured |
keychain
Syntax
keychain [key-chain] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays keychain information.
Parameters
- key-chain
Specifies the keychain name to display.
- detail
Displays detailed keychain information.
Output
The following output is an example of keychain information.
Sample output*A:ALA-A# show system security keychain test
===============================================================================
Key chain:test
===============================================================================
TCP-Option number send : 254 Admin state : Up
TCP-Option number receive : 254 Oper state : Up
===============================================================================
*A:ALA-A#
management-access-filter
Syntax
management-access-filter
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays management access filter information for IP and MAC filters.
ip-filter
Syntax
ip-filter [entry entry-id]
Context
show>system>security>mgmt-access-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays management-access IP filters.
Parameters
- entry-id
Displays information for the specified entry.
Output
The following output is an example of management access IP filter information, and Output fields: IP filter describes the output fields.
Sample output*7210-SAS>show>system>security>management-access-filter# ip-filter entry 1
===============================================================================
IPv4 Management Access Filter
===============================================================================
filter type : ip
Def. Action : permit
Admin Status : enabled (no shutdown)
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Src IP : undefined
Src interface : undefined
Dest port : undefined
Protocol : undefined
Router : undefined
Action : none
Log : disabled
Matches : 0
===============================================================================
*7210-SAS>show>system>security>management-access-filter#
Label |
Description |
|---|---|
Def. action |
Permit — Specifies that packets not matching the configured selection criteria in any of the filter entries are permitted Deny — Specifies that packets not matching the configured selection criteria in any of the filter entries are denied and that a ICMP host unreachable message will be issued Deny-host-unreachable — Specifies that packets not matching the configured selection criteria in the filter entries are denied |
Entry |
The entry ID in a policy or filter table |
Description |
A text string describing the filter |
Src IP |
The source IP address used for management access filter match criteria |
Src Interface |
The interface name for the next-hop to which the packet should be forwarded if it hits this filter entry |
Dest port |
The destination port |
Match |
The number of times a management packet has matched this filter entry |
Protocol |
The IP protocol to match |
Action |
The action to take for packets that match this filter entry |
password-options
Syntax
password-options
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays password options.
Output
The following output is an example of password options, and Output fields: password options describes the output fields.
Sample outputA:ALA-48>show>system>security# password-options
===============================================================================
Password Options
===============================================================================
Password aging in days : 365
Number of invalid attempts permitted per login : 5
Time in minutes per login attempt : 5
Lockout period (when threshold breached) : 20
Authentication order : radius tacplus local
Configured complexity options :
Minimum password length : 8
===============================================================================
A:ALA-48>show>system>security#
Label |
Description |
|---|---|
Password aging in days |
Number of days a user password is valid before the user must change their password |
Number of invalid attempts permitted per login |
Displays the maximum number of unsuccessful login attempts allowed for a user |
Time in minutes per login attempt |
Displays the time in minutes that user is to be locked out |
Lockout period (when threshold breached) |
Displays the number of minutes the user is locked out if the threshold of unsuccessful login attempts has exceeded |
Authentication order |
Displays the most preferred method to authenticate and authorize a user |
Configured complexity options |
Displays the complexity requirements of locally administered passwords, HMAC-MD5-96, HMAC-SHA-96 and DES-keys configured in the authentication section |
Minimum password length |
Displays the minimum number of characters required in the password |
profile
Syntax
profile [profile-name]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays user profiles for CLI command tree permissions.
Parameters
- profile-name
Specifies the profile name to display information about a single user profile. If no profile name is displayed, the entire list of profile names are listed.
Output
The following output is an example of user profile information, and Output fields: profile describes the output fields.
Sample outputA:ALA-48>config>system>snmp# show system security profile
===============================================================================
User Profile
===============================================================================
User Profile : test
Def. Action : none
-------------------------------------------------------------------------------
Entry : 1
Description :
Match Command:
Action : unknown
===============================================================================
User Profile : default
Def. Action : none
-------------------------------------------------------------------------------
Entry : 10
Description :
Match Command: exec
Action : permit
-------------------------------------------------------------------------------
Entry : 20
Description :
Match Command: exit
Action : permit
-------------------------------------------------------------------------------
Entry : 30
Description :
Match Command: help
Action : permit
-------------------------------------------------------------------------------
...
-------------------------------------------------------------------------------
Entry : 80
Description :
Match Command: enable-admin
Action : permit
===============================================================================
User Profile : administrative
Def. Action : permit-all
-------------------------------------------------------------------------------
Entry : 10
Description :
Match Command: configure system security
Action : permit
-------------------------------------------------------------------------------
Entry : 20
Description :
Match Command: show system security
Action : permit
===============================================================================
-------------------------------------------------------------------------------
No. of profiles: 3
===============================================================================
A:ALA-48>config>system>snmp#
Label |
Description |
|---|---|
User Profile |
default — The action to be given to the user profile if none of the entries match the command administrative — Specifies the administrative state for this profile |
Def. Action |
none — No action is given to the user profile when none of the entries match the command permit-all — The action to be taken when an entry matches the command |
Entry |
10 to 80 — Each entry represents the configuration for a system user |
Description |
A text string describing the entry |
Match Command |
administrative — Enables the user to execute all commands configure system security — Enables the user to execute the config system security command enable-admin — Enables the user to enter a special administrative mode by entering the enable-admin command exec — Enables the user to execute (exec) the contents of a text file as if they were CLI commands entered at the console exit — Enables the user to execute the exit command help — Enables the user to execute the help command logout — Enables the user to execute the logout command password — Enables the user to execute the password command show config — Enables the user to execute the show config command show — Enables the user to execute the show command show system security — Enables the user to execute the show system security command |
Action |
permit — Enables the user access to all commands deny-all — Denies the user access to all commands |
snmp
Syntax
snmp
Context
show
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context displays SNMP information.
community
Syntax
community
community community-string
Context
show>system>security>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command lists SNMP communities and characteristics.
Parameters
- community-string
Specifies the community name, up to 32 characters.
Output
The following output is an example of SNMP community information, and Output fields: SNMP community describes the output fields.
Sample outputA:Dut-P# show system security snmp community
==============================================================================
Communities
==============================================================================
community access view version group name
------------------------------------------------------------------------------
cli-readonly r iso v2c cli-readonly
cli-readwrite rw iso v2c cli-readwrite
private rwa iso v1 v2c snmp-rwa
public rwa iso v1 v2c snmp-rwa
------------------------------------------------------------------------------
No. of Communities: 4
==============================================================================
A:Dut-P#
Label |
Description |
|---|---|
Community |
Displays the community string name for SNMPv1 and SNMPv2c access only |
Access |
r — The community string allows read-only access rw — The community string allows read-write access rwa — The community string allows read-write access mgmt — The unique SNMP community string assigned to the management router |
View |
Displays the view name |
Version |
Displays the SNMP version |
Group Name |
Displays the access group name |
No of Communities |
Displays the total number of configured community strings |
ssh
Syntax
ssh
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays all the SSH sessions as well as the SSH status and fingerprint.
Output
The following output is an example of SSH session information, and Output fields: SSH describes the output fields.
Sample outputA:ALA-7# show system security ssh
SSH is enabled
Key fingerprint: 34:00:f4:97:05:71:aa:b1:63:99:dc:17:11:73:43:83
=======================================================
Connection Encryption Username
=======================================================
192.168.5.218 3des admin
-------------------------------------------------------
Number of SSH sessions : 1
=======================================================
A:ALA-7#
A:ALA-49>config>system>security# show system security ssh
SSH is disabled
A:ALA-49>config>system>security#
Label |
Description |
|---|---|
SSH status |
SSH is enabled — Displays that SSH server is enabled |
SSH is disabled — Displays that SSH server is disabled |
|
Key fingerprint |
The key fingerprint is the server identity. Clients trying to connect to the server verify the server fingerprint. If the server fingerprint is not known, the client may not continue with the SSH session because the server might be spoofed. |
Connection |
The IP address of the connected routers (remote client) |
Encryption |
des — Data encryption using a private (secret) key 3des — An encryption method that allows proprietary information to be transmitted over untrusted networks |
Username |
The name of the user |
Number of SSH sessions |
The total number of SSH sessions |
user
Syntax
users [user-id] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays user information.
Output
The following output is an example of user information, and Output fields: security user describes the output fields.
Sample outputA:ALA-1# show system security user
===============================================================================
Users
===============================================================================
user id need user permissions password attempted failed local
new pwd console ftp snmp expires logins logins conf
-------------------------------------------------------------------------------
admin n y n n never 2 0 y
testuser n n n y never 0 0 y
-------------------------------------------------------------------------------
Number of users : 2
===============================================================================
A:ALA-1#
Label |
Description |
|---|---|
User ID |
The name of a system user |
Need New PWD |
Yes — The user must change their password at the next login No — The user is not forced to change their password at the next login |
User Permission |
Console — Specifies whether the user is permitted console/Telnet access FTP — Specifies whether the user is permitted FTP access SNMP — Specifies whether the user is permitted SNMP access |
Password expires |
The date on which the current password expires |
Attempted logins |
The number of times the user has attempted to login irrespective of whether the login succeeded or failed |
Failed logins |
The number of unsuccessful login attempts |
Local Conf. |
Y — Password authentication is based on the local password database N — Password authentication is not based on the local password database |
view
Syntax
view [view-name] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command lists one or all views and permissions in the MIB-OID tree.
Output
The following output is an example of permissions views, and Output fields: security view describes the output fields.
Sample outputA:ALA-1# show system security view
===============================================================================
Views
===============================================================================
view name oid tree mask permission
-------------------------------------------------------------------------------
iso 1 included
no-security 1 included
no-security 1.3.6.1.6.3 excluded
no-security 1.3.6.1.6.3.10.2.1 included
no-security 1.3.6.1.6.3.11.2.1 included
no-security 1.3.6.1.6.3.15.1.1 included
-------------------------------------------------------------------------------
No. of Views: 6
===============================================================================
A:ALA-1#
A:ALA-1# show system security view no-security detail
===============================================================================
Views
===============================================================================
view name oid tree mask permission
-------------------------------------------------------------------------------
no-security 1 included
no-security 1.3.6.1.6.3 excluded
no-security 1.3.6.1.6.3.10.2.1 included
no-security 1.3.6.1.6.3.11.2.1 included
no-security 1.3.6.1.6.3.15.1.1 included
-------------------------------------------------------------------------------
No. of Views: 5
===============================================================================
=======================================
no-security used in
=======================================
group name
---------------------------------------
snmp-ro
snmp-rw
=======================================
A:ALA-1#
Label |
Description |
|---|---|
View name |
The name of the view Views control the accessibility of a MIB object within the configured MIB view and subtree. |
OID tree |
The Object Identifier (OID) value OIDs uniquely identify MIB objects in the subtree. |
Mask |
The mask value and the mask type, along with the oid-value configured in the view command, determines the access of each sub-identifier of an object identifier (MIB subtree) in the view. |
Permission |
Included — Specifies to include MIB subtree objects Excluded — Specifies to exclude MIB subtree objects |
No. of Views |
The total number of configured views |
Group name |
The access group name |