Filter policies
This chapter provides information about filter policies and management.
Filter policy configuration overview
Filter policies, also referred to as Access Control Lists (ACLs), are templates applied to services or network IP interfaces to control network traffic into (ingress) or out of (egress) a service access port (SAP) or network IP interface based on IP and MAC matching criteria. Filters are applied to services to look at packets entering or leaving a SAP. Filters can be used on several interfaces. The same filter can be applied to ingress traffic, egress traffic, or both. Ingress filters affect only inbound traffic destined for the routing complex, and egress filters affect only outbound traffic sent from the routing complex.
Configuring an entity with a filter policy is optional. If an entity such as a service or network IP interface is not configured with filter policies, then all traffic is allowed on the ingress and egress interfaces. By default, there are no filters associated with services or interfaces. They must be explicitly created and associated. When you create a new filter, default values are provided although you must specify a unique filter ID value to each new filter policy as well as each new filter entry and associated actions. The filter entries specify the filter matching criteria and also an action to be taken upon a match.
Available ingress and egress CAM hardware resources can be allocated as per user needs for use with different filter criteria. By default, the system allocates resources to maintain backward compatibility with release 4.0. Users can modify the resource allocation based on their need to scale the number of entries or number of associations (that is, number of SAP/IP interfaces using a filter policy that defines particular match criteria). If no CAM resources are allocated to particular match criteria defined in a filter policy, then the association of that filter policy to a SAP will fail. This is true for both ingress and egress filter policy. Please read the configuration notes section below for more information.
Only one ingress IP or MAC filter policy and one egress IP or MAC filter policy can be applied to a Layer 2 SAP. Both IPv4 and IPv6 ingress and egress filter policy can be used simultaneously with a Layer 2 SAP. Only one ingress IP filter policy and one egress IP filter policy can be applied to a network IP interface. Both IPv4 and IPv6 ingress and egress filter policy can be used simultaneously with an IP interface (For example: network Port IP interface in network mode and IES IP interface in access-uplink mode) for which IPv6 addressing is supported. Network filter policies control the forwarding and dropping of packets based on IP match criteria. Note that non-IP packets are not hitting the IP filter policy, so the default action in the filter policy will not apply to these packets.
Note that non-IP packets are not hitting the IP filter policy, so the default action in the filter policy will not apply to these packets.
Service and network IP interface-based filtering
IP and MAC filter policies specify either a forward or a drop action for packets based on information specified in the match criteria.
Filter entry matching criteria can be as general or specific as you require, but all conditions in the entry must be met in order for the packet to be considered a match and the specified entry action performed. The process stops when the first complete match is found and executes the action defined in the entry, either to drop or forward packets that match the criteria.
Filter policy entities
A filter policy compares the match criteria specified within a filter entry to packets coming through the system, in the order the entries are numbered in the policy. When a packet matches all the parameters specified in the entry, the system takes the specified action to either drop or forward the packet. If a packet does not match the entry parameters, the packet continues through the filter process and is compared to the next filter entry, and so on. If the packet does not match any of the entries, then system executes the default action specified in the filter policy. Each filter policy is assigned a unique filter ID. Each filter policy is defined with:
scope
default action
description
Each filter entry contains:
match criteria
an action
Applying filter policies
The following tables describe support of filter policies on different 7210 platforms.
| Service | IP filter | IPv6 filter | MAC filter |
|---|---|---|---|
Network port IP interface |
Network port IP interface (ingress and egress) |
Network port IP interface (ingress and egress) |
Not available |
Epipe |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
VPLS |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
IES |
IES interface SAP (ingress and egress) |
IES interface SAP (ingress and egress) |
Not available |
VPRN |
VPRN interface SAP (ingress and egress) |
VPRN interface SAP (ingress and egress) |
Not available |
PBB |
Ingress and egress of Epipe I-SAP and I-VPLS I-SAP |
Ingress and egress of Epipe I-SAP, and I-VPLS I-SAP |
Ingress and egress of Epipe I-SAP, I-VPLS I-SAP and B-VPLS B-SAP |
RVPLS (RVPLS SAPs) 1 |
VPLS access (ingress and egress) and network SAPs (ingress and egress) |
Not available |
Not available |
RVPLS (RVPLS IES IP Interface) 1 |
Ingress override filters (ingress) |
Not available |
Not available |
| Service | IP filter | IPv6 filter | MAC filter |
|---|---|---|---|
Epipe |
Epipe access SAP (egress and ingress), Epipe access-uplink SAP (egress and ingress) |
Epipe (egress and ingress), Epipe access-uplink SAP (egress and ingress) |
Epipe (egress and ingress), Epipe access-uplink SAP (egress and ingress) |
VPLS |
VPLS access SAP (ingress and egress), VPLS access-uplink SAP (ingress and egress) |
VPLS access SAP (ingress and egress), VPLS access-uplink SAP (ingress and egress) |
VPLS access SAP (ingress and egress), VPLS access-uplink SAP (ingress and egress) |
|
RVPLS (VPLS SAPs) 1 |
VPLS access (ingress and egress) and access-uplink SAPs (ingress and egress) |
Not available |
Not available |
RVPLS (RVPLS IES IP Interface) 1 |
Ingress override filters (ingress) |
Not available |
Not available |
IES |
IES access SAP, IES access-uplink SAP |
IES access-uplink SAP |
Not available |
| Service | IP filter | IPv6 filter | MAC filter |
|---|---|---|---|
Network port IP interface |
Network port IP interface (ingress and egress) |
Network port IP interface (ingress and egress) |
Not available |
Epipe |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
VPLS |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
IES |
IES interface SAP (ingress and egress) |
IES interface SAP (ingress and egress) |
Not available |
VPRN |
VPRN interface SAP (ingress and egress) |
VPRN interface SAP (ingress and egress) |
Not available |
PBB |
Not supported |
Not supported |
Not supported |
|
RVPLS (VPLS SAPs) 1 |
VPLS access (ingress and egress) and access-uplink SAPs (ingress and egress) |
Available only for 7210 SAS-Mxp Not available for 7210 SAS-R6 and 7210 SAS-R12 |
Available only for 7210 SAS-Mxp Not available for 7210 SAS-R6 and 7210 SAS-R12 |
RVPLS (RVPLS IES and VPRN IP interface) 1 |
Ingress override filters (ingress) |
Available only for 7210 SAS-Mxp Not available for 7210 SAS-R6 and 7210 SAS-R12 |
Not available |
| Service | IP filter | IPv6 filter | MAC filter |
|---|---|---|---|
Network port IP interface |
Network port IP interface (ingress and egress) |
Network port IP interface (ingress and egress) |
Not available |
Epipe |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
Epipe SAP (ingress and egress) |
VPLS |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
VPLS SAP (ingress and egress) |
IES |
IES interface SAP (ingress and egress) |
IES interface SAP (ingress and egress) |
Not available |
VPRN |
VPRN interface SAP (ingress and egress) |
VPRN interface SAP (ingress and egress) |
Not available |
PBB |
Not available |
Not available |
Not available |
|
RVPLS (VPLS SAPs) 1 |
VPLS access (ingress and egress) and access-uplink SAPs (ingress and egress) |
Not available |
Not available |
RVPLS (RVPLS IES and VPRN IP interface) 1 |
Ingress override filters (ingress) |
Not available |
Not available |
ACL on range SAPs
The ACLs on VLAN range SAPs are supported only on ingress (for Epipe and VPLS services). The following tables list the support.
| Platforms/types of filters | 7210 SAS-T (network mode) | 7210 SAS-T (access-uplink mode) |
|---|---|---|
Ingress IP or IPv6 |
Yes |
Yes |
Ingress MAC |
Yes |
Yes |
Egress IP |
No |
No |
Egress MAC |
No |
No |
| Platforms/types of filters | 7210 SAS-R6 and 7210 SAS-R12 | 7210 SAS-Mxp | 7210 SAS-Sx/S 1/10GE | 7210 SAS-Sx 10/100GE |
|---|---|---|---|---|
Ingress IP or IPv6 |
Yes |
Yes |
Yes |
Yes |
Ingress MAC |
Yes |
Yes |
Yes |
Yes |
Egress IP |
No |
No |
No |
No |
Egress MAC |
No |
No |
No |
No |
| Platforms/types of filters | 7210 SAS-T (access-uplink mode) | 7210 SAS-T (network mode) |
|---|---|---|
Ingress IP or IPv6 |
Yes |
No |
Ingress MAC |
Yes |
No |
Egress IP |
No |
No |
Egress MAC |
No |
No |
Filter policies are applied to the following service entities:
SAP ingress
IP and MAC filter policies applied on the SAP ingress define the Service Level Agreement (SLA) enforcement of service packets as they ingress a SAP according to the filter policy match criteria.
SAP egress
Filter policies applied on the SAP egress define the Service Level Agreement (SLA) enforcement for service packets as they egress on the SAP according to the filter policy match criteria.
network ingress
IP filter policies are applied to network ingress IP interfaces.
network egress
IP filter policies are applied to network egress IP interfaces.
Configuration guidelines for Routed VPLS and ACLs
The following information describes Routed VPLS and ACLs configuration guidelines:
MAC filters are supported on R-VPLS SAPs only on the 7210 SAS-Mxp. See the ‟Routed VPLS” section in the 7210 SAS-Mxp, S, Sx, T Services Guide for more information.
IPv6 filters on RVPLS SAP are supported only on the 7210 SAS-Mxp.
IP filters using resources from the pool allocated to IPv4 criteria are supported as override filters on all platforms as described in this document.
IP filters using resources from the pool allocated to IPv4 criteria, and IPv6 filters using resources allocated to IPv6 criteria (both 64-bit and 128-bit resource pools), are supported as override filters only on 7210 SAS-Mxp.
IP filters using IPv6 resources are not supported on RVPLS SAP.
Egress override filters are not supported (under the IES and VPRN interface associated with RVPLS).
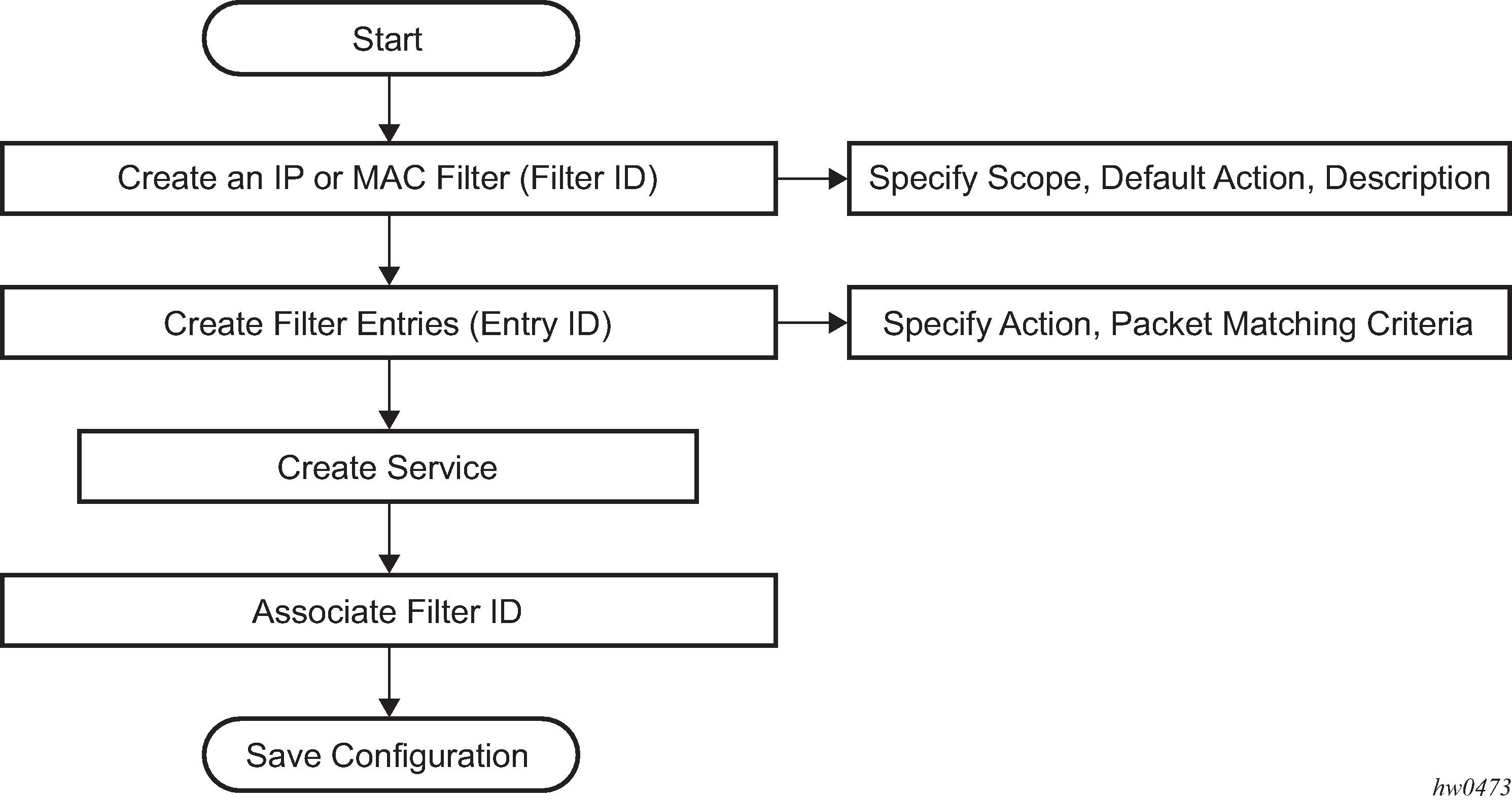
Creating and applying policies
The following figure shows the process to create filter policies and apply them to a service network IP interface.
Packet matching criteria
As few or as many match parameters can be specified as required, but all conditions must be met for the packet to be considered a match and the specified action performed. The process stops when the first complete match is found and then executes the action defined in the entry, either to drop or forward packets that match the criteria.
IP filter policies match criteria that associate traffic with an ingress or egress SAP. Matching criteria to drop or forward IP traffic include:
source IP address and mask
Source IP address and mask values can be entered as search criteria. The IP Version 4 addressing scheme consists of 32 bits expressed in dotted-decimal notation (X.X.X.X).
Address ranges are configured by specifying mask values, the 32-bit combination used to describe the address portion which refers to the subnet and which portion refers to the host. The mask length is expressed as an integer (range 1 to 32).
destination IP address and mask
Destination IP address and mask values can be entered as search criteria. Similar choice as available for source IPv6 addresses is available for destination IPv6 addresses (see above).
protocol
Entering a protocol ID (such as TCP, UDP, and so on) allows the filter to search for the protocol specified in this field.
protocol
For IPv6: entering a next header allows the filter to match the first next header following the IPv6 header.
source port
Entering the source port number allows the filter to search for matching TCP or UDP port values.
destination port
Entering the destination port number allows the filter to search for matching TCP or UDP port.
DSCP marking
Entering a DSCP marking enables the filter to search for the DSCP marking specified in this field. See DSCP name to DSCP value table .
ICMP code
Entering an ICMP code allows the filter to search for matching ICMP code in the ICMP header.
ICMP type
Entering an ICMP type allows the filter to search for matching ICMP types in the ICMP header.
IPv4 filter created in the mode to use IPv6 resource cannot be applied at egress SAP. Similarly IPv4 filter created in the mode to use IPv6 resource fails to match fragment option.
fragmentation
IPv4 only: Enable fragmentation matching. A match occurs if packets have either the MF (more fragment) bit set or have the Fragment Offset field of the IP header set to a non-zero value.
option present
Enabling the option presence allows the filter to search for presence or absence of IP options in the packet. Padding and EOOL are also considered as IP options.
TCP-ACK/SYN flags
Entering a TCP-SYN/TCP-ACK flag allows the filter to search for the TCP flags specified in these fields.
MAC filter policies match criteria that associate traffic with an ingress or egress SAP. Matching criteria to drop or forward MAC traffic include:
source MAC address and mask
Entering the source MAC address range allows the filter to search for matching a source MAC address or range. Enter the source MAC address and mask in the form of xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 00:dc:98:1d:00:00.
destination MAC address and mask
Entering the destination MAC address range allows the filter to search for matching a destination MAC address or range. Enter the destination MAC address and mask in the form of xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 02:dc:98:1d:00:01.
dot1p and mask
Entering an IEEE 802.1p value or range allows the filter to search for matching 802.1p frame. The Dot1p and mask accepts decimal, hex, or binary in the range of 0 to 7.
Ethertype
Entering an Ethernet type II Ethertype value to be used as a filter match criterion. The Ethernet type field is a two-byte field used to identify the protocol carried by the Ethernet frame. The Ethertype accepts decimal, hex, or binary in the range of 1536 to 65535.
DSCP values
The following table lists DSCP values.
| DSCP name | Decimal DSCP value | Hexadecimal DSCP value | Binary DSCP value |
|---|---|---|---|
default |
0 |
* |
|
cp1 |
1 |
||
cp2 |
2 |
||
cp3 |
3 |
||
cp4 |
4 |
||
cp5 |
5 |
||
cp6 |
6 |
||
cp7 |
7 |
* |
|
cs1 |
8 |
||
cp9 |
9 |
||
af11 |
11 |
* |
|
af12 |
12 |
* |
|
cp13 |
13 |
||
cp15 |
15 |
||
cs2 |
16 |
* |
|
cp17 |
17 |
||
af21 |
18 |
* |
|
cp19 |
19 |
||
af22 |
20 |
* |
|
cp21 |
21 |
||
af23 |
22 |
* |
|
cp23 |
23 |
||
cs3 |
24 |
* |
|
cp25 |
25 |
||
af31 |
26 |
* |
|
cp27 |
27 |
||
af32 |
28 |
* |
|
cp29 |
29 |
||
af33 |
30 |
* |
|
cp21 |
31 |
||
cs4 |
32 |
* |
|
cp33 |
33 |
||
af41 |
34 |
* |
|
cp35 |
35 |
||
af42 |
36 |
* |
|
cp37 |
37 |
||
af43 |
38 |
* |
|
cp39 |
39 |
||
cs5 |
40 |
* |
|
cp41 |
41 |
||
cp42 |
42 |
||
cp43 |
43 |
||
cp44 |
44 |
||
cp45 |
45 |
||
ef |
46 |
* |
|
cp47 |
47 |
||
nc1 |
48 |
* |
(cs6) |
cp49 |
49 |
||
cp50 |
50 |
||
cp51 |
51 |
||
cp52 |
52 |
||
cp53 |
53 |
||
cp54 |
54 |
||
cp55 |
55 |
||
cp56 |
56 |
||
cp57 |
57 |
||
nc2 |
58 |
* |
(cs7) |
cp60 |
60 |
||
cp61 |
61 |
||
cp62 |
62 |
Ordering filter entries
When entries are created, they should be arranged sequentially from the most explicit entry to the least explicit. Filter matching ceases when a packet matches an entry. The entry action is performed on the packet. 7210 SAS supports either drop or forward action.To be considered a match, the packet must meet all the conditions defined in the entry.
Packets are compared to entries in a filter policy in an ascending entry ID order. To reorder entries in a filter policy, edit the entry ID value; for example, to reposition entry ID "6" to a more explicit location, change the entry ID "6" value to entry ID "2".
When a filter consists of a single entry, the filter executes actions as follows:
If a packet matches all the entry criteria, the entry specified action is performed (drop or forward).
If a packet does not match all of the entry criteria, the policy default action is performed.
If a filter policy contains two or more entries, packets are compared in ascending entry ID order (1, 2, 3 or 10, 20, 30, and so on):
Packets are compared with the criteria in the first entry ID.
If a packet matches all the properties defined in the entry, the entry specified action is executed.
If a packet does not completely match, the packet continues to the next entry, and then subsequent entries.
If a packet does not completely match any subsequent entries, then the default action is performed.
The following figure shows an example of several packets forwarded upon matching the filter criteria and several packets traversing through the filter entries and then dropped.
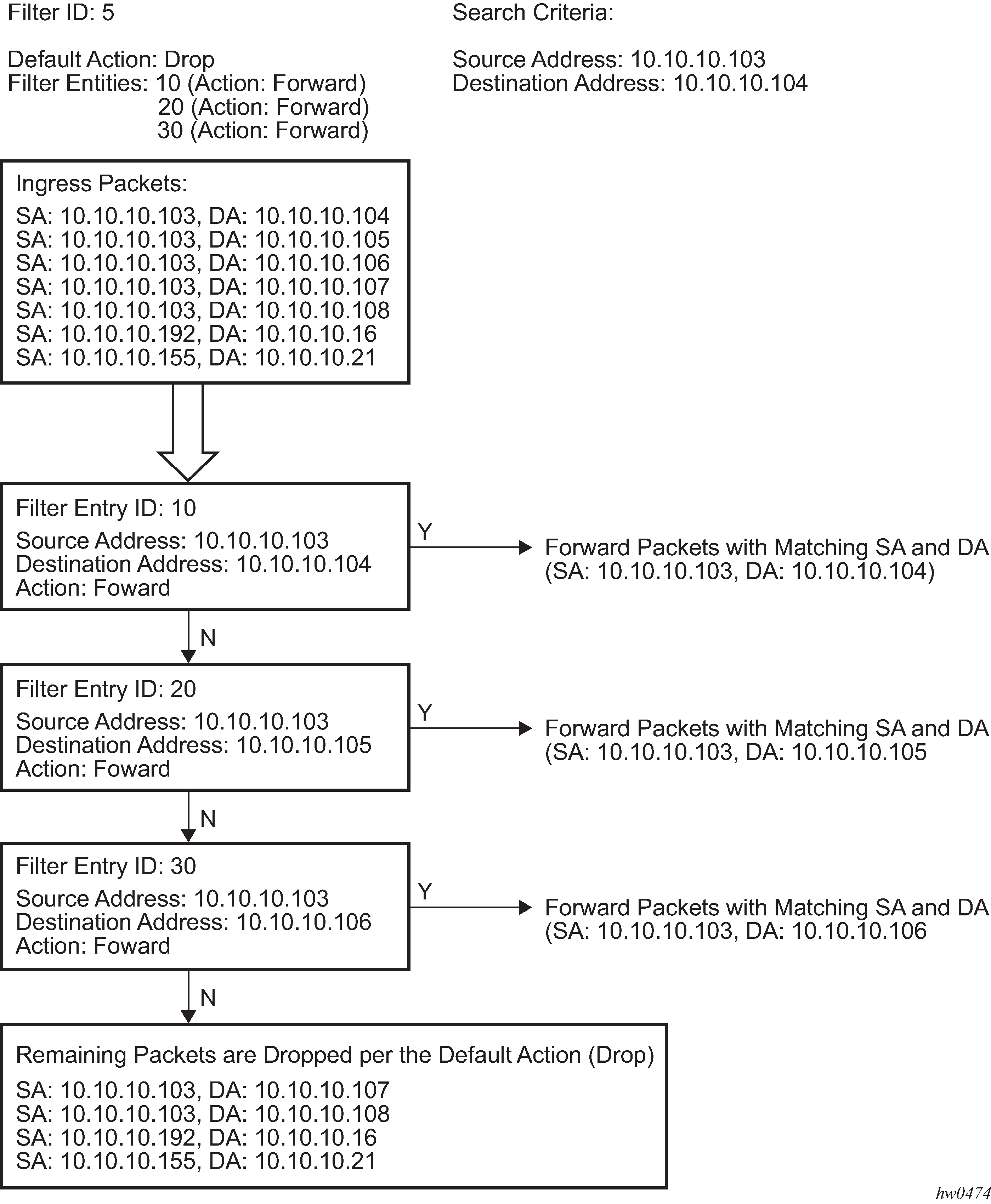
Applying filters
This section provides information about applying filters to entities.
Applying a filter to a SAP
During the SAP creation process, ingress and egress filters are selected from a list of qualifying IP and MAC filters. When ingress filters are applied to a SAP, packets received at the SAP are checked against the matching criteria in the filter entries. If the packet completely matches all criteria in an entry, the checking stops and an entry action is performed. If permitted, the traffic is forwarded according to the specification of the action. If the packets do not match, the default filter action is applied. If permitted, the traffic is forwarded.
When egress filters are applied to a SAP, packets received at the egress SAP are checked against the matching criteria in the filter entries. If the packet completely matches all criteria in an entry, the checking stops. If permitted, the traffic is transmitted. If denied, the traffic is dropped. If the packets do not match, the default filter action is applied.
Filters can be added or changed to an existing SAP configuration by modifying the SAP parameters. Filter policies are not operational until they are applied to a SAP and the service enabled.
Applying a filter to a network IP interface
An IP filter can be applied to a network port IP interface. Packets received on the interface are checked against the matching criteria in the filter entries. If the packet completely matches all criteria in an entry, the checking stops. If permitted, the traffic is forwarded. If the packets do not match, they are discarded or forwarded based on the default action specified in the policy.
Configuration notes
See the 7210 SAS-Mxp, S, Sx, T Services Guide and the 7210 SAS-R6, R12 Services Guide for service-specific ACL support and restrictions.
The following information describes filter implementation guidelines and restrictions:
Creating a filter policy is optional.
Associating a service with a filter policy is optional.
When a filter policy is configured, it should be defined as having either an exclusive scope for one-time use, or a template scope meaning that the filter can be applied to multiple SAPs.
A specific filter must be explicitly associated with a specific service in order for packets to be matched.
A filter policy can consist of zero or more filter entry. Each entry represents a collection of filter match criteria. When packets enter the ingress or egress ports, packets are compared to the criteria specified within the entry or entries.
When a large (complex) filter is configured, it may take a few seconds to load the filter policy configuration and be instantiated.
The action keyword must be entered for the entry to be active. Any filter entry without the action keyword will be considered incomplete and be inactive.
When a filter policy is created with the option ipv6-64bit-address, the entries can only use only the IPv6 src-ip and IPv6 dst-ip fields in the match criteria.
When a filter policy is created with the option ipv6-128bit-address, the entries can use the IPv6 src-ip, IPv6 dst-ip, IPv6 DSCP, TCP/UDP port numbers (source and destination port), ICMP code and type, and TCP flags fields in the match criteria.
The resources must be allocated for use by ingress IPv6 filters, before associating an IPv6 filter policy to a SAP. By default, the software does not enable the use of IPv6 resources. Until resources are allocated for use by IPv6 filters, software fails all attempts to associate a IPv6 filter policy with a SAP.
The available ingress CAM hardware resources can be allocated as per user needs for use with different filter criteria using the commands under config> system>resource-profile>ingress-internal-tcam>acl-sap-ingress. By default, the system allocates resources to maintain backward compatibility with Release 4.0. Users can modify the resource allocation based on their need to scale the number of entries or number of associations (that is, number of SAP/IP interfaces using a filter policy that defines a particular match criterion).
The available egress CAM hardware resources can be allocated as per user needs for use with different filter criteria using the commands under config> system>resource-profile>egress-internal-tcam>acl-sap-egress. By default, the system allocates resources to maintain backward compatibility with Release 4.0. Users can modify the resource allocation based on their needs to scale the number of entries or the number of associations (that is, number of SAP/IP interfaces using a filter policy that defines a particular match criterion).
IPv6 ACLs and MAC QoS policies cannot co-exist on the SAP.
If no CAM resources are allocated to a particular match criterion defined in a filter policy, then the association of that filter policy to a SAP will fail. This is true for both ingress and egress filter policy.
IPv6 ACLs and MAC QoS policies cannot co-exist on the SAP.
For traffic ingressing a B-VPLS SAP and destined to a B-VPLS SAP, the MAC filter matches the B-domain, MAC header fields (that is, B-DA, B-SA, and others). The MAC filter can be used to match customer payload MAC header fields for traffic ingressing a B-VPLS SAP and destined to an I-VPLS SAP.
MAC filters
The following information describes MAC filters:
If a MAC filter policy is created with an entry and entry action specified but the packet matching criteria is not defined, then all packets processed through this filter policy entry will pass and take the action specified. There are no default parameters defined for matching criteria.
MAC filters cannot be applied to network interfaces. On the 7210 SAS-Mxp, they can be applied on an R-VPLS service with IES or VPRN. See Applying filter policies and the 7210 SAS-Mxp, S, Sx, T Services Guide for more information.
Some of the MAC match criteria fields are exclusive to each other, based on the type of Ethernet frame. Use the following table to determine the exclusivity of fields. On the 7210 SAS, the default frame-format is ‟EthernetII”.
Frame format |
Etype |
|---|---|
Ethernet – II |
Yes |
802.3 |
No |
802.3 – snap |
No |
IP filters
The following information describes IP filterSs:
define filter entry packet matching criteria
If a filter policy is created with an entry and entry action specified but the packet matching criteria is not defined, then all packets processed through this filter policy entry will pass and take the action specified. There are no default parameters defined for matching criteria.
action
An action parameter must be specified for the entry to be active. Any filter entry without an action parameter specified will be considered incomplete and be inactive.
IPv6 filters
The following information describes IPv6 filters:
define filter entry packet matching criteria
If a filter policy is created with an entry and entry action specified, but the packet matching criteria is not defined, then all packets processed through this filter policy entry passes and takes the action specified. There are no default parameters defined for matching criteria.
action
An action parameter must be specified for the entry to be active. Any filter entry without an action parameter specified is considered incomplete and inactive.
Resource usage for ingress filter policies
The number of entries per slice/chunk is different for both ingress-internal-tcam resource pool and egress-internal-tcam resource pool for different platforms.
The example below assumes number of entries to be 256 per slice/chunk for ingress-internal-tcam resource pool (for example: 7210 SAS-T). It is valid for other platforms with suitable modification of number of entries per slice.
When the user allocates resources from the ingress CAM resource pool for use by filter policies using the configure> system> resource-profile CLI commands, the system allocates resources in chunks of fixed-size entries (example - 256 entries per chunk on 7210 SAS-T). The usage of these entries by different type of match criteria is described below:
mac-criteria - User needs to allocate resources for mac-criteria from the filter resource pool by using the command config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>mac-match-enable before using ingress ACLs with mac-criteria. Every entry configured in the filter policy using the mac-criteria uses one (1) entry from the chunks allocated for use by mac-criteria in the hardware. For example, assume a filter policy is configured with 50 entries and uses config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>mac-match-enable 1, the user configures one chunk for use by mac-criteria (allowing a total of 256 entries. one reserved for internal use entries for use by SAPs using filter policies that use mac-criteria). In this case, the user can have 5 SAPs using mac-criteria filter policy and consumes 250 entries.
ipv4-criteria - User needs to allocate resources for IPv4 criteria from the filter resource pool by using the command config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv4-match-enable before using ingress ACLs with IPv4 criteria. The resource usage per IPv4 match entry is same as the mac-criteria. Please check the preceding example. When created with use-ipv6-resource, the resource usage is the same as IPv6 filters using ipv6-128-bit-addresses.
-
ipv4-criteria with port range values - Users must allocate resources for the IPv4 criteria using the port-range values from the filter resource pool by using the config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv4-port-range-match-enable command before using ingress ACLs with an IPv4 criteria port range. Every entry configured in the filter policy using the IPv4 criteria port range uses two entries from the chunks allocated for use by the IPv4 criteria port range in the hardware. For example, if a filter policy is configured with 50 entries and includes the config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv4-port-range-match-enable 2 configuration, the user configures one chunk for use by the IPv4 criteria port range values (allowing a total of 256 entries; one entry is reserved for internal use entries for use by SAPs using filter policies that use an IPv4 criteria port range). In this case, the user can have two filter policies using the IPv4 criteria filter policy and consumes 200 entries (each policy requires 100 entries, as each of the 50 entries must have two entries each).
ipv6-criteria using ipv6-64-bit addresses - User needs to allocate resources for IPv6 criteria with 64-bit address match from the filter resource pool by using the command config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv6-64only-match-enable before using ingress ACLs with ipv6-criteria that use only IPv6 64-bit address for source and destination IPv6 addresses. The IPv6 headers fields available for match is limited. Please see the CLI description for filter below for more information. The usage is same as the ipv4 and mac-criteria.
ipv6-criteria using ipv6-128-bit addresses - User needs to allocate resources for IPv6 criteria with 128-bit address match from the filter resource pool by using the command config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv4-ipv6-128-match-enable before using ingress ACLs with ipv6-criteria that use only IPv6 128-bit address for source and destination IPv6 addresses. These resources can be shared by a policy that uses only IPv4 criteria entries. Every entry configured in the filter policy using the ipv6-criteria with 128-bit addresses uses two entries from the chunks allocated for use by IPv6 criteria (128-bit) in the hardware. For example: Assume a filter policy is configured with 50 entries and using config>system>resource-profile>ingress-internal-tcam>acl-sap-ingress>ipv4-ipv6-128-match-enable 1, the user configures one chunk for use by IPv6 criteria with 128-bit addresses (allowing for a total of 128 entries for use by SAPs using filter policies that use this criteria). In this case, user can have five (5) SAPs using this filter policy and consumes 125 entries. Note when a chunk is allocated to IPv6 criteria, software automatically adjusts the number of available entries in that chunk to 128, instead of 256, since two entries are needed to match IPv6 fields.
The users can use the tools>dump>system-resources command to know the current usage and availability. For example: Though chunks are allocated in 256 entries, only 128 entries show up against filters using those of IPv6 128-bit addresses. One or more entries are reserved for system use and is not available for user.
Resource usage for egress filter policies
When the user allocates resources for use by filter policies using the config>system>resource-profile>egress-internal-tcam CLI commands, the system allocates resources in chunks of fixed-size entries (example - 256 entries per slice on 7210 SAS-Mxp) from the egress internal tcam pool in hardware. The usage of these entries by different type of match criteria is described below:
mac-criteria - The user needs to allocate resources for using mac-criteria using the command config>system>resource-profile>egress-internal-tcam>acl-sap-egress>mac-match-enable 2 or config>system>resource-profile>egress-internal-tcam>acl-sap-egress>mac-ipv4-match-enable 2 or config>system> resource-profile>egress-internal-tcam>acl-sap-egress>mac-ipv6-64bit-match-enable 2. In the last two cases, the resources can be shared with SAPs that use IPv4 or IPv6 64-bit filter policies. The first case allocates resources for exclusive use by MAC filter policies. The resource usage varies based how resources have been allocated:
If resources are allocated for use by mac-criteria only (using mac-match-enable), then every entry configured in the filter policy uses one (1) entry from the chunks allocated for use by mac-criteria in the hardware. For example: Assume a filter policy is configured with 25 mac-criteria entries and uses config>system>resource-profile>egress-internal-tcam>acl-sap-egress>mac-match-enable 2, the user configures two chunks (each chunk having 256 entries each) for use by mac-criteria, allowing a total of 512 entries for use by SAPs using filter policies that use mac-criteria. Therefore, the user can have about 10 SAPs using mac-criteria filter policy and consumes 500 entries. With this, SAPs using ipv4 criteria or ipv6 criteria cannot share the resources along with SAPs using mac-criteria.
If the resources are allocated for sharing between mac-criteria and ipv4-criteria, then every entry configured in the filter policy uses 2 (two) entries from the chunks allocated in hardware. For example, assume a filter policy is configured with 25 mac-criteria entries and another filter policy configured with 25 IPv4 criteria entries and, with mac-ipv4-match-enable set to 2, that is, user configures two chunks (each chunk having 256 entries each) for sharing between MAC and IPv4, allowing for a total of 128 entries for use by SAPs that use filter policies using ipv4-criteria or mac-criteria. Therefore, the user can have about 5 SAPs using filter policies, such that 3 SAPs uses mac-criteria and the other 2 SAPs use ipv4-criteria or any combination thereof.
If the resources are allocated for sharing between mac-criteria and ipv6-64bit-criteria, then every entry configured in the filter policy uses 2 (two) entries from the chunks allocated in hardware.
For example, assume a filter policy is configured with 50 mac-criteria entries and another filter policy configured with 50 IPv6 64-bit criteria entries and, with mac-ipv6-64bit-match-enable set to 2, that is, user configures two chunks (with 256 entries each) for sharing between MAC and IPv6-64bit, allowing for a total of 128 entries for use by SAPs that use filter policies using ipv6-64bit-criteria or mac-criteria. Therefore, the user can have about 2 SAPs using filter policies, such that one SAP uses mac-criteria and the other one SAP uses ipv6-64bit-criteria or any combination thereof.
ipv4-criteria - The user need to allocate resources using the command config> system>resource-profile>egress-internal-tcam>acl-sap-egress>mac-ipv4-match-enable. The resource usage is as described previously.
ipv6-criteria using ipv6-64-bit addresses - The user need to allocate resources using the command config>system>resource-profile>egress-internal-tcam>acl-sap-egress> mac-ipv6-64bit-match-enable. The resource usage is as described previously.
ipv6-criteria using ipv6-128-bit addresses - The user need to allocate resources using the command config>system>resource-profile>egress-internal-tcam>acl-sap-egress>ipv6-128bit-match-enable. This command allocates resources for exclusive by IPv6-128bit criteria filter policies and cannot be shared by SAPs using any another criteria. If resources are allocated for use by ipv6-128bit-criteria only, then every entry configured in the filter policy uses two (2) entries from the chunks allocated for use in hardware. For example: Assume a filter policy is configured with 50 ipv6-128bit-criteria entries and user uses config>system>resource-profile>egress-internal-tcam>acl-sap-egress>ipv6-128bit-match-enable 2, to configure two chunks (each chunk having 256 entries each) for use by ipv6-128bit-criteria. This allows for a total of 128 entries for use by SAPs using filter policies that use ipv6-128bit-criteria. Therefore the user can have about 2 SAPs using ipv6-128bit-criteria filter policy and consumes 100 entries.
The user can use the tools>dump>system-resources command to know the current usage and availability.
Configuring filter policies with CLI
This section provides information to configure filter policies using the command line interface.
Basic configuration
The most basic IP and MAC filter policies must have the following:
a filter ID
template scope, either exclusive or template
default action, either drop or forward
at least one filter entry
specified action, either drop or forward
specified matching criteria
allocates the required amount of resources for ingress and egress filter policies
The following is a sample configuration output of allocation of ingress internal CAM resources for ingress policy for 7210 SAS.
*A:7210SAS>config>system>res-prof>ing-internal-tcam>acl-sap-ing# info detail
----------------------------------------------
ipv4-match-enable max
ipv6-64-only-match-enable 1
no ipv4-ipv6-128-match-enable
----------------------------------------------
*A:7210SAS>config>system>res-prof>ing-internal-tcam>acl-sap-ing# back
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-Sx/S 1/10GE.
A:7210SAS>config>system>res-prof>egr-internal-tcam# info detail
----------------------------------------------
acl-sap-egress 2
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
mac-ipv6-64bit-match-enable 0
mac-match-enable 0
exit
----------------------------------------------
*A:7210SAS>config>system>res-prof>egr-internal-tcam# acl-sap-egress
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-Sx 10/100GE.
*A:7210SAS>config>system>res-prof>egr-internal-tcam# info detail
----------------------------------------------
acl-sap-egress 2
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
ipv6-64bit-match-enable 0
mac-match-enable 0
exit
no egress-sap-aggregate-meter
----------------------------------------------
*A:7210SAS>config>system>res-prof>egr-internal-tcam# acl-sap-egress
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-Mxp.
*A:sim_dutc>config>system>res-prof>egr-internal-tcam>acl-sap-egr# info detail
----------------------------------------------
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
mac-ipv6-64bit-match-enable 0
mac-match-enable 0
----------------------------------------------
*A:sim_dutc>config>system>res-prof>egr-internal-tcam>acl-sap-egr#
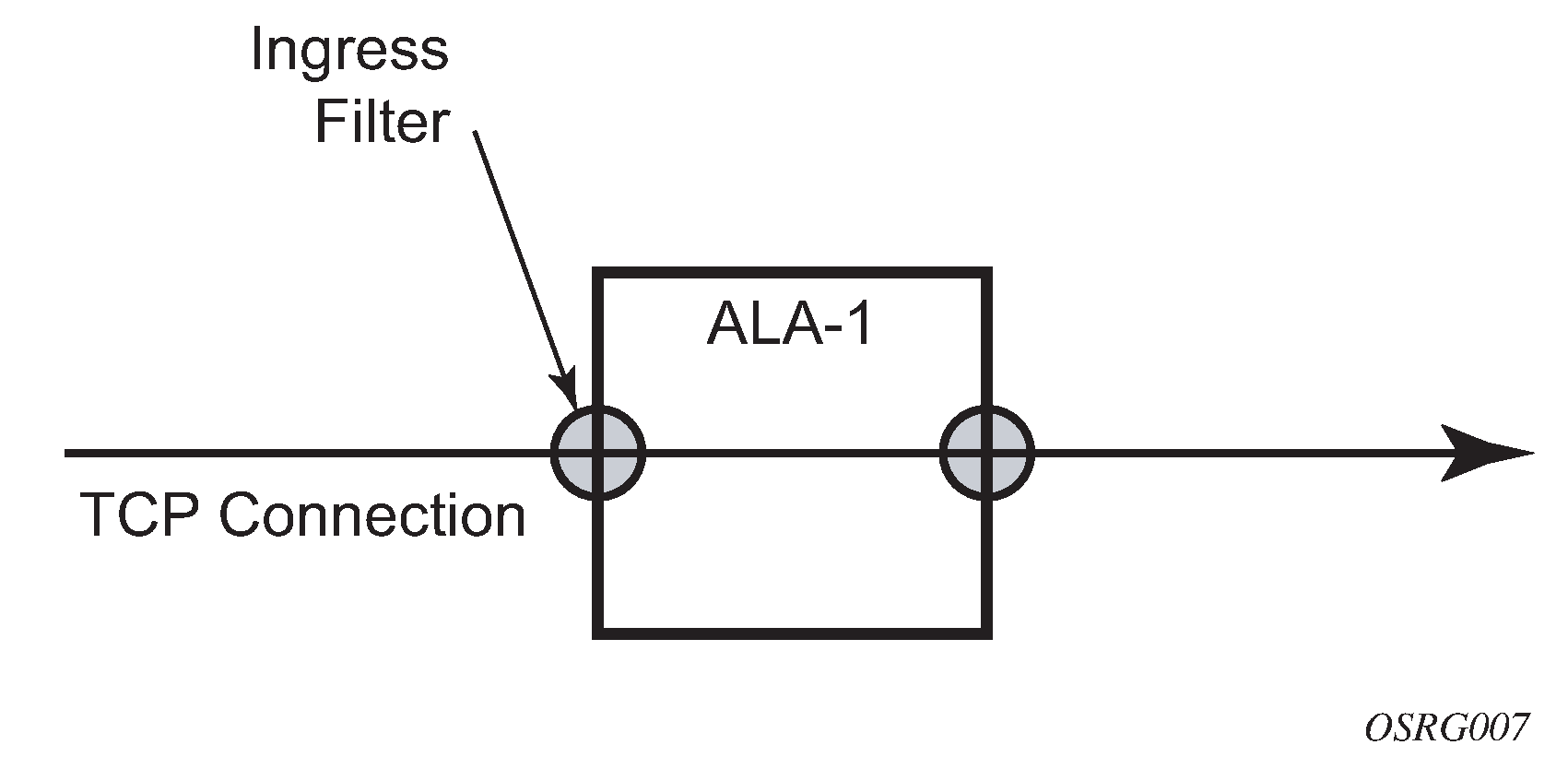
The following is a sample configuration output of an IP filter policy. The configuration blocks all incoming TCP session except Telnet and allows all outgoing TCP sessions from IP net 10.67.132.0/24. CAM resources must be allocated to IPv4 criteria before associating the filter with a SAP. Applying an IP filter to an ingress interface shows the interface to apply the filter.
A:ALA-1>config>filter# info
----------------------------------------------
ip-filter 3 create
entry 10 create
match protocol 6
dst-port eq 23
src-ip 10.67.132.0/24
exit
action
forward
exit
entry 20 create
match protocol 6
tcp-syn true
tcp-ack false
exit
action
drop
exit
exit
----------------------------------------------
A:ALA-1>config>filter#
The following figure shows the IP filter applied to an ingress interface.
Common configuration tasks
This section provides a brief overview of the tasks that must be performed for both IP and MAC filter configurations and provides the CLI commands.
Creating an IP filter policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
the filter type specified (IP)
a filter policy ID
a default action, either drop or forward
filter policy scope specified, either exclusive or template
at least one filter entry with matching criteria specified
configure CAM hardware resource for use by the filter policy match-criteria
IP filter policy
The following is a sample exclusive filter policy configuration output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 12 create
description "IP-filter"
scope exclusive
exit
...
----------------------------------------------
A:ALA-7>config>filter#
IP filter entry
Within a filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded:
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
Use the following syntax to create an IP filter entry.
config>filter# ip-filter filter-id [create]
entry entry-id [time-range time-range-name][create]
description description-string
The following is a sample IP filter entry configuration output.
A:ALA-7>config>filter>ip-filter# info
----------------------------------------------
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
exit
no action
exit
exit
----------------------------------------------
A:ALA-7>config>filter>ip-filter#
IP entry matching criteria
Use the following syntax to configure IP filter matching criteria.
The following is a sample IP filter matching configuration output.
*A:ALA-48>config>filter>ip-filter# info
----------------------------------------------
description "filter-mail"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action
forward
exit
----------------------------------------------
*A:ALA-48>config>filter>ip-filter#
Creating an IPv6 filter policy
Configuring and applying IPv6 filter policies is optional. Each filter policy must have the following:
the IPv6 filter type specified
an IPv6 filter policy ID
a default action, either drop or forward
template scope specified, either exclusive or template
at least one filter entry with matching criteria specified
IPv6 filter policy
Use the following syntax to create an IPv6 filter policy.
To create an IPv6 filter using 64-bit-address, the user can use the command config> filter>ipv6-filter filter-id ipv6-64bit-address create.
By default, the IPv6 filters are configured using 128-bit-address, the output is as follows.
*A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
exit
*A:7210SAS>config>filter>ipv6-filter#
IPv6 filter entry
Within an IPv6 filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded:
Enter an IPv6 filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
The following is a sample IPv6 filter entry configuration output.
*A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
entry 1 create
no description
match next-header none
no dscp
no dst-ip
no dst-port
src-ip 2001:db8::1/128
no src-port
no tcp-syn
no tcp-ack
no icmp-type
no icmp-code
exit
action
forward
exit
*A:7210SAS>config>filter>ipv6-filter#
Creating a MAC filter policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
The filter type specified (MAC).
A filter policy ID.
A default action, either drop or forward
Filter policy scope, either exclusive or template.
At least one filter entry.
Matching criteria specified.
MAC filter policy
The following is a sample MAC filter policy configuration output.
A:ALA-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "filter-west"
scope exclusive
exit
----------------------------------------------
A:ALA-7>config>filter#
MAC filter entry
Within a filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded:
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
The following is a sample MAC filter entry configuration output.
A:sim1>config>filter# info
----------------------------------------------
mac-filter 90 create
entry 1 create
description "allow-104"
match
exit
action
drop
exit
exit
----------------------------------------------
A:sim1>config>filter#
MAC entry matching criteria
The following is a sample filter matching configuration output.
Sample filter matching configuration output
A;ALA-7>config>filter>mac-filter# info
----------------------------------------------
description "filter-west"
scope exclusive
entry 1 create
description "allow-104"
match
src-mac 00:dc:98:1d:00:00 ff:ff:ff:ff:ff:ff
dst-mac 02:dc:98:1d:00:01 ff:ff:ff:ff:ff:ff
exit
action
drop
exit
----------------------------------------------
Apply IP and MAC filter policies
Use the following syntax to apply an IP and a MAC filter policy to an Epipe service.
config>service# epipe service-id
sap sap-id
egress
filter {ip ip-filter-id | mac mac-filter-id}
ingress
filter {ip ip-filter-id | mac mac-filter-id}
The following is a sample of IP and MAC filters assigned to an ingress and egress SAP output.
A:ALA-48>config>service>epipe# info
----------------------------------------------
sap 1/1/1.1.1 create
ingress
filter ip 10
exit
egress
filter mac 92
exit
exit
no shutdown
----------------------------------------------
A:ALA-48>config>service>epipe#
Apply an IPv6 filter policy to VPLS
The following is a sample of IPv6 filters assigned to VPLS service interface output.
*A:7210SAS>config>service#vpls#sap info detail
----------------------------------------------
......
ingress
counter-mode in-out-profile-count
no drop-count-extra-vlan-tag-pkts
exit
exit
ingress
qos 1
no aggregate-meter-rate
filter ipv6 1
exit
egress
no filter
exit
no collect-stats
no accounting-policy
no shutdown
exit
*A:7210SAS>config>service#vpls#sap info detail
Applying filter policies to a network IP interface
IP filter policies can be applied to network IP interfaces. MAC filters cannot be applied to network IP interfaces or to routable IES services.
Applying a filter policy to an IP interface
config>router# interface ip-int-name
The following is a sample IP filter applied to an interface at ingress output.
A:ALA-48>config>router# info
#------------------------------------------
# IP Configuration
#------------------------------------------
...
interface "to-104"
address 10.0.0.103/24
port 1/1/1
ingress
filter ip 10
exit
egress
filter ip 10
exit
exit
...
#------------------------------------------
A:ALA-48>config>router#
Filter management tasks
This section describes the filter policy management tasks.
Renumbering filter policy entries
The system exits the matching process when the first match is found and then executes the actions in accordance with the specified action. Because the ordering of entries is important, the numbering sequence can be rearranged. Entries should be numbered from the most explicit to the least explicit.
Use the following syntax to renumber existing MAC or IP filter entries to re-sequence filter entries.
config>filter
ip-filter filter-id
renum old-entry-numbernew-entry-number
mac-filter filter-id
renum old-entry-numbernew-entry-number
config>filter>ip-filter# renum 10 15
config>filter>ip-filter# renum 20 10
config>filter>ip-filter# renum 40 1
The following is a sample of the original filter entry order output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action forward
exit
entry 20 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action drop
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action forward
exit
entry 40 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action drop
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
The following is a sample of the reordered filter entries output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action drop
exit
entry 10 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action forward
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action forward
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
Modifying an IP filter policy
To access a specific IP filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
config>filter>ip-filter# description "New IP filter info"
config>filter>ip-filter# entry 2 create
config>filter>ip-filter>entry$ description "new entry"
config>filter>ip-filter>entry# action drop
config>filter>ip-filter>entry# match dst-ip 10.10.10.104/32
config>filter>ip-filter>entry# exit
config>filter>ip-filter#
The following is a sample of the modified IP filter output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "New IP filter info"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
description "new entry"
match
dst-ip 10.10.10.104/32
exit
action
drop
exit
entry 10 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action
drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action
forward
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action
forward
exit
exit
..
----------------------------------------------
A:ALA-7>config>filter#
Modifying an IPv6 filter policy
To access a specific IPv6 filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
config>filter# ipv6-filter 11
config>filter>ipv6-filter# description "IPv6 filter for Customer 1"
config>filter>ipv6-filter# scope exclusive
config>filter>ipv6-filter# entry 1
config>filter>ipv6-filter>entry# description "Fwds matching packets"
config>filter>ipv6-filter>entry# action forward
config>filter>ipv6-filter>entry# exit
The following is a sample output of the modified IPv6 filter output.
A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
entry 1 create
description "Test"
match next-header none
no dscp
no dst-ip
no dst-port
src-ip 2001:db8::1/128
no src-port
no tcp-syn
no tcp-ack
no icmp-type
no icmp-code
exit
action
forward
exit
...
A:7210SAS>config>filter>ipv6-filter
Modifying a MAC filter policy
To access a specific MAC filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
— config>filter# mac-filter 90
— config>filter>mac-filter# description "New filter info"
— config>filter>mac-filter# entry 1
— config>filter>mac-filter>entry# description "New entry info"
— config>filter>mac-filter>entry# action forward
— config>filter>mac-filter>entry# exit
— config>filter>mac-filter# entry 2 create
— config>filter>mac-filter>entry$ action drop
— config>filter>mac-filter>entry# match
— config>filter>mac-filter>entry>match# dot1p 7 7
The following is a sample of the modified MAC filter output.
A:ALA-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "New filter info"
scope exclusive
entry 1 create
description "New entry info"
match
src-mac 00:dc:98:1d:00:00 ff:ff:ff:ff:ff:ff
dst-mac 02:dc:98:1d:00:01 ff:ff:ff:ff:ff:ff
exit
action
forward
exit
entry 2 create
match
dot1p 7 7
exit
action
drop
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
Detaching/deleting a filter policy
Before you can delete a filter, you must remove the filter association from the applied ingress and egress SAPs and network interfaces.
From an ingress SAP
The following shows the command usage to remove a filter from an ingress SAP.
config>service# [epipe | vpls] service-id
sap port-id[:encap-val]
ingress
no filter
config>service# epipe 5
config>service>epipe# sap 1/1/2:3
config>service>epipe>sap# ingress
config>service>epipe>sap>ingress# no filter
From an egress SAP
The following shows the command usage to remove a filter from an egress SAP.
config>service# [epipe | vpls] service-id
sap port-id[:encap-val]
egress
no filter
config>service# epipe 5
config>service>epipe# sap 1/1/2:3
config>service>epipe>sap# egress
config>service>epipe>sap>egress# no filter
From a network interface
The following shows the command usage to delete a filter from a network interface.
config>router# interface ip-int-name
ingress
config>router>if>ingress# no filter ip 2
config>router>if>ingress# exit
From the filter configuration
Use the following syntax to delete the filter after you have removed the filter from the SAP.
config>filter# no ip-filter filter-id
config>filter# no mac-filter filter-id
config>filter# no ip-filter 11
config>filter# no mac-filter 13
Copying filter policies
When changes are made to an existing filter policy, they are applied immediately to all services where the policy is applied. If numerous changes are required, the policy can be copied so you can edit the ‟work in progress” version without affecting the filtering process. When the changes are completed, you can overwrite the work in progress version with the original version.
New filter policies can also be created by copying an existing policy and renaming the new filter.
config>filter# copy filter-type src-filter-id [src-entry src-entry-id] to dst-filter-id [dst-entry dst-entry-id][overwrite]
The following shows the command usage to copy an existing IP filter (11) to create a new filter policy (12).
config>filter# copy ip-filter 11 to 12
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "This is new"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
...
ip-filter 12 create
description "This is new"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
...
----------------------------------------------
A:ALA-7>config>filter#
Filter command reference
Command hierarchies
Configuration commands
IP filter policy commands
config
- filter
- [no] ip-filter filter-id [use-ipv6-resource] [create]
- [no] ip-filter filter-id [use-port-range] [create]
- no ip-filter filter-id
- default-action {drop | forward}
- description description-string
- no description
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
- entry entry-id [time-range time-range-name] [create]
- no entry entry-id
- action
- no action
- drop
- forward
- description description-string
- no description
- match [protocol protocol-id]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ip-address/mask | ip-address ipv4-address-mask}
- no dst-ip
- dst-port {eq} dst-port-number
- dst-port range dst-port-number1 dst-port-number2
- no dst-port
- fragment {true | false}
- no fragment
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- option-present {true | false}
- no option-present
- src-ip {ip-address/mask | ip-address ipv4-address-mask}
- no src-ip
- src-port {eq} src-port-number
- src-port range src-port-number1 src-port-number2
- no src-port
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
IPv6 filter policy commands
config
- filter
- ipv6-filter ipv6-filter-id [ipv6-128bit-address | ipv6-64bit-address] [create]
- no ipv6-filter ipv6-filter-id
- default-action {drop | forward}
- description description-string
- no description
- filter-name filter-name
- no filter-name
- entry entry-id [time-range time-range-name] [create]
- no entry entry-id
- action
- no action
- drop
- forward
- description description-string
- no description
- match [next-header next-header]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ipv6-address/prefix-length}
- no dst-ip
- dst-port {eq} dst-port-number
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- dst-ip {ipv6-address/prefix-length}
- no dst-ip
- src-port {eq} src-port-number
- src-port range start end}
- no src-port
- src-ip {ipv6-address/prefix-length}
- no src-ip
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
MAC filter policy commands
config
- filter
- mac-filter filter-id [create]
- no mac-filter filter-id
- default-action {drop | forward}
- description description-string
- no description
- entry entry-id [time-range time-range-name]
- no entry entry-id
- description description-string
- no description
- action [drop]
- action forward
- no action
- match
- no match
- dot1p dot1p-value [dot1p-mask]
- no dot1p
- dst-mac ieee-address [ieee-address-mask]
- no dst-mac
- etype 0x0600..0xffff
- no etype
- src-mac ieee-address [ieee-address-mask]
- no src-mac
- filter-name filter-name
- no filter-name
- renum old-entry-id new-entry-id
- scope {exclusive | template}
- no scope
- type filter-type
Generic filter commands
config
- filter
- copy ip-filter | ipv6-filter| mac-filter src-filter-id [src-entry src-entry-id] to dst-filter-id [dst-entry dst-entry-id] [overwrite]
Show commands
show
- filter
- download-failed
- ip [ip-filter-id [entry entry-id] [association | counters]]
- ipv6 [ipv6-filter-id [entry entry-id] [association | counters]]
- mac {mac-filter-id [entry entry-id] [association | counters]}
Clear commands
Monitor commands
Command descriptions
Configuration commands
Generic commands
description
Syntax
description string
no description
Context
config>filter>ip-filter
config>filter>ip-filter>entry
config>filter>ipv6-filter
config>filter>ipv6-filter>entry
config>filter>mac-filter
config>filter>mac-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates a text description for a configuration context to help identify the content in the configuration file.
The no form of this command removes any description string from the context.
Parameters
- string
Specifies the description character string. Allowed values are any string up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, etc.), the entire string must be enclosed within double quotes.
Global filter commands
ip-filter
Syntax
[no] ip-filter filter-id [use-ipv6-resource] [create]
[no] ip-filter filter-id [use-port-range] [create]
Context
config>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure an IP filter policy.
The IP filter policies specify either a forward or a drop action for packets based on the specified match criteria.
The IP filter policy, sometimes referred to as an access control list (ACL), is a template that can be applied to multiple services or multiple network ports as long as the scope of the policy is template.
Any changes made to the existing policy, using any of the subcommands, will be applied immediately to all services where this policy is applied. For this reason, when many changes are required on an IP filter policy, Nokia recommends that the policy be copied to a work area. That work-in-progress policy can be modified until complete and then written over the original filter policy. Use the config filter copy command to maintain policies in this manner.
By default, when an IPv4 filter policy is associated with a service entity (For example: SAP), the software attempts to allocate resources for the filter policy entries from the IPv4 resource pool. If resources unavailable in the pool, then the software fails to associate and display an error. If the user knows that resources are free in the IPv6 resource pool, then the use-ipv6-resource parameter is used to allow the user to share the entries in the resource chunks allocated for use by IPv6 128-bit resource pool, if available. If this parameter is specified, the resource for this filter policy is always allocated from the IPv6 128-bit filter resource pool.
By default, IPv4 filters are created using IPv4 resources, assuming an unspecified use-ipv6-resource. If such filters are to be created using IPv6 resources, the use-ipv6-resource option needs to be specified. Ahead of the application of such a filter, the user should ensure the number of policies in the newly created policy is within the limit of available resources in the IPv6 128-bit resource pool, by considering the output of the tools>dump>system-resources command.
The no form of this command deletes the IP filter policy. A filter policy cannot be deleted until it is removed from all SAPs or network ports where it is applied.
Parameters
- filter-id
Specifies the IP filter policy ID number.
- create
Specifies that when the context is created, one can navigate into the context without the create keyword. This keyword is required when first creating the configuration context.
- use-ipv6-resource
Specifies that the hardware resources for the entries in this filter policy must be allocated from the IPv6 filter resource pool, if available.
- use-port-range
-
Keyword to indicate that the IP criteria match entries can use the port range for matching L4 port values and to allocate resources for this filter policy from the ipv4-port-range-match-enable pool. This keyword is only available on the 7210 SAS-Mxp.
There are limited amount of unique port range values that can be used (see the tools>dump>system-resources command to know the current usage). The port range entries are shared among QoS and ACLs, along with source and destination port range values.
ipv6-filter
Syntax
[no] ipv6-filter ipv6-filter-id [ipv6-128bit-address | ipv6-64bit-address] [create]
Context
config>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates an IPv6 filter policy. During the 'create', the user must specify if IPv6 addresses, both source and destination IPv6 addresses, specified in the match criteria uses complete 128-bits or uses only the upper 64 bits of the IPv6 addresses.
The no form of this command deletes the IPv6 filter policy. A filter policy cannot be deleted until it is removed from all SAPs or network ports where it is applied.
Default
128-bit addresses
Parameters
- ipv6-filter-id
Specifies the IPv6 filter policy ID number.
- ipv6-128bit-address
Specifies that if the user intends to use complete 128-bit addresses, then the user requires the ipv6-128bit-address CLI parameter with the create command. When this policy is associated with a SAP, software allocates resources for the filter entries from the IPv6 128-bit resource pool for the SAP.
- ipv6-64bit-address
Specifies that if the user intends to use upper most significant bit (MSB) 64-bit addresses, then the user requires the ipv6-64bit-address CLI parameter with the create command. When this policy is associated with a SAP, the software allocates resources for the filter entries from the IPv6 64-bit resource pool for the SAP. All the IP packet fields are not available for match are when using 64-bit addresses. For more information, see Configuration notes, to know the packet header fields available for match when using this option.
- create
Specifies that when the context is created, one can navigate into the context without the create keyword. This keyword is required when first creating the configuration context.
mac-filter
Syntax
[no] mac-filter filter-id [create]
Context
config>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the context for a MAC filter policy.
The mac-filter policy specifies either a forward or a drop action for packets based on the specified match criteria.
The mac-filter policy, sometimes referred to as an access control list, is a template that can be applied to multiple services as long as the scope of the policy is template.
It is not possible to apply a MAC filter policy to a network port network IP interface.
Any changes made to the existing policy, using any of the subcommands, will be applied immediately to all services where this policy is applied. For this reason, when many changes are required on a mac-filter policy, Nokia recommends that the policy be copied to a work area. That work-in-progress policy can be modified until complete and then written over the original filter policy. Use the config filter copy command to maintain policies in this manner.
The no form of this command deletes the mac-filter policy. A filter policy cannot be deleted until it is removed from all SAP where it is applied.
Parameters
- filter-id
Specifies the MAC filter policy ID number.
- create
Specifies that when the context is created, one can navigate into the context without the create keyword. This keyword is required when first creating the configuration context.
Filter policy commands
default-action
Syntax
default-action {drop | forward}
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the action to be applied to packets when the packets do not match the specified criteria in all of the IP filter entries of the filter.
When multiple default-action commands are entered, the last command will overwrite the previous command.
Default
drop
Parameters
- drop
Specifies that all packets will be dropped unless there is a specific filter entry which causes the packet to be forwarded.
- forward
Specifies that all packets will be forwarded unless there is a specific filter entry which causes the packet to be dropped.
scope
Syntax
scope {exclusive | template}
no scope
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the filter policy scope as exclusive or template. If the scope of the policy is template and is applied to one or more services or network interfaces, the scope cannot be changed.
The no form of this command reverts the scope of the policy to the default.
Default
template
Parameters
- exclusive
Specifies that the policy can only be applied to a single entity (SAP or network IP interface). Attempting to assign the policy to a second entity will result in an error message. If the policy is removed from the entity, it will become available for assignment to another entity.
- template
Specifies that the policy can be applied to multiple SAPs or network IP interfaces.
General filter entry commands
entry
Syntax
entry entry-id [time-range time-range-name] [create]
no entry entry-id
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates or edits an IP or MAC filter entry. Multiple entries can be created using unique entry-id numbers within the filter. The implementation exits the filter on the first match found and executes the actions in accordance with the accompanying action command. For this reason, entries must be sequenced correctly from most to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have the action command for it to be considered complete. Entries without the action command will be considered incomplete and therefore will be rendered inactive.
The no form of this command removes the specified entry from the IP or MAC filter. Entries removed from the IP or MAC filter are immediately removed from all services or network ports where that filter is applied.
Parameters
- entry-id
Specifies a match criteria and the corresponding action. Nokia recommends that multiple entries be specified entry-ids in staggered increments. This allows users to insert a new entry in an existing policy without requiring renumbering of all the existing entries.
- time-range time-range-name
Specifies the time range name to be associated with this filter entry up to 32 characters. The time-range name must already exist in the config>cron context.
- create
Specifies that when the context is created, one can navigate into the context without the create keyword. This keyword is required when first creating the configuration context.
IP filter entry commands
action
Syntax
action
no action
Context
config>filter>ip-filter>entry
config>filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the action taken when a packet meets filtering criteria.
The no form of this command removes the currently configured action.
Default
no action
drop
Syntax
drop
Context
config>filter>ip-filter>entry>action
config>filter>ipv6-filter>entry>action
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the filter action to drop packets matching the filter entry.
forward
Syntax
forward
Context
config>filter>ip-filter>entry>action
config>filter>ipv6-filter>entry>action
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the filter action to forward packets matching the filter entry.
match
Syntax
match [protocol] [protocol-id]
no match
Context
config>filter>ip-filter>entry
config>filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enters match criteria for the filter entry. When the match criteria have been satisfied the action associated with the match criteria is executed.
If more than one match criteria (within one match statement) are configured, then all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
The no form of this command removes the match criteria for the entry-id.
Parameters
- protocol-id
-
Specifies the decimal value representing the IP protocol to be used as an IP filter match criterion. Well known protocol numbers include ICMP(1), TCP(6), UDP(17) (see the following table).The values can be expressed in decimal, hexadecimal, or binary.
MAC filter entry commands
action
Syntax
action drop
action forward
no action
Context
config>filter>mac-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the action for a MAC filter entry. The action keyword must be entered for the entry to be active. Any filter entry without the action keyword will be considered incomplete and will be inactive.
If neither drop nor forward is specified, this is considered a No-Op filter entry used to explicitly set a filter entry inactive without modifying match criteria or removing the entry.
Multiple action statements entered will overwrite previous actions parameters when defined. To remove a parameter, use the no form of the action command with the specified parameter.
The no form of this command removes the specified action statement. The filter entry is considered incomplete and therefore rendered inactive without the action command.
Parameters
- drop
Specifies that packets matching the entry criteria will be dropped.
- forward
Specifies that packets matching the entry criteria will be forwarded.
If neither drop nor forward is specified, the filter action is no-op and the filter entry is inactive.
match
Syntax
match [frame-type keyword]
no match
Context
config>filter>mac-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures match criteria for the filter entry and specifies an Ethernet frame type for the entry. When the match criteria have been satisfied the action associated with the match criteria is executed.
If more than one match criteria (within one match statement) are configured then all criteria must be satisfied (AND function) before the action associated with the match will be executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
The no form of this command removes the match criteria for the entry-id.
Parameters
- frame-type keyword
Specifies an Ethernet frame type to be used for the MAC filter match criteria.
IP filter match criteria
dscp
Syntax
dscp dscp-name
no dscp
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a DiffServ Code Point (DSCP) name to be used as an IP filter match criterion.
The no form of this command removes the DSCP match criterion.
Default
no dscp
Parameters
- dscp-name
Specifies a dscp name that has been previously mapped to a value using the dscp-name command. The DiffServ code point may only be specified by its name.
dst-ip
Syntax
dst-ip {ip-address/mask | ip-address ipv4-address-mask}
no dst-ip
Context
config>filter>ip-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a destination IPv4 address range to be used as an IP filter match criterion.
To match on the destination IPv4 address, specify the address and its associated mask, such as 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 may also be used.
The no form of this command removes the destination IPv4 address match criterion.
Default
none
Parameters
- ip-address
Specifies the IPv4 prefix for the IP match criterion in dotted decimal notation.
- mask
Specifies the subnet mask length expressed as a decimal integer.
- ipv4-address-mask
Specifies any mask expressed in dotted quad notation.
dst-ip
Syntax
dst-ip {ipv6-address/prefix-length}
no dst-ip
Context
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a destination IPv6 address range to be used as an IP filter match criterion.
To match on the destination IPv6 address, specify the address and its associated mask.
The no form of this command removes the destination IPv6 address match criterion.
Default
none
Parameters
- ipv6-address
Specifies the IPv6 prefix for the IP match criterion in hex digits.
- prefix-length
Specifies the IPv6 prefix length for the IPv6 address as a decimal integer.
dst-port
Syntax
dst-port {eq} dst-port-number
dst-port range dst-port-number1 dst-port-number2
no dst-port
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a destination TCP or UDP port number for an IP filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, and so on) fragments of a fragmented packet since only the first fragment contains the L4 information.
- One port range hardware entry is required to match a unique combination of port range values configured by the user. Two port range values (for example, port range 1024 to 2048 and port range 3050 to 3055) are considered to be unique if their range 1 and range 2 values do not match. Each unique port range value consumes one entry each in hardware.
- Each unique port range entry requires two entries in the hardware table if it is used for both a source and destination match. In other words, a unique port range value requires one entry for matching a source port and another entry for matching a destination port.
- If one or more QoS or ACL policy use the same unique port range value for either the source port match or destination port match but not both, only a single entry in the hardware table is required. For example, if port range 1000 to 2000 is used in both the access ingress policy and filter policy to match on source port, it requires one entry in the hardware port range table.
- If one or more QoS and or ACL policy use the same unique port range value for both source port match and destination port, two entries in the hardware table are required. For example, if port range 1000 to 2000 is used in both access ingress policy and filter policy to match on both the source port and destination port, it requires two entries in the hardware port range table.
The no form of this command removes the destination port match criterion.
Parameters
- eq
Specifies the operator to use relative to dst-port-number for specifying the port number match criteria. The eq keyword specifies that dst-port-number must be an exact match.
- dst-port-number
Specifies the destination port number to be used as a match criteria expressed as a decimal integer.
- range dst-port-number1
-
Specifies the first destination port number in the range to match a range of ports. This parameter is only available on the 7210 SAS-Mxp.
- range dst-port-number2
-
Specifies the last destination port number in the range to match a range of ports. The second number must be greater than the first number in the range. This parameter is only available on the 7210 SAS-Mxp.
fragment
Syntax
fragment {true | false}
no fragment
Context
config>filter>ip-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures fragmented or non-fragmented IP packets as an IP filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, etc) fragments of a fragmented packet since only the first fragment contains the L4 information.
The no form of this command removes the match criterion.
Default
no fragment
Parameters
- true
Specifies a match on all fragmented IP packets. A match will occur for all packets that have either the MF (more fragment) bit set or have the Fragment Offset field of the IP header set to a non-zero value.
- false
Specifies a match on all non-fragmented IP packets. Non-fragmented IP packets are packets that have the MF bit set to zero and have the Fragment Offset field also set to zero.
icmp-code
Syntax
icmp-code icmp-code
no icmp-code
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures matching on ICMP code field in the ICMP header of an IP packet as a filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, etc) fragments of a fragmented packet since only the first fragment contains the L4 information.
This option is only meaningful if the protocol match criteria specifies ICMP (1).
The no form of this command removes the criterion from the match entry.
Default
no icmp-code
Parameters
- icmp-code
Specifies the ICMP code values that must be present to match.
icmp-type
Syntax
icmp-type icmp-type
no icmp-type
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures matching on the ICMP type field in the ICMP header of an IP or packet as a filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, etc) fragments of a fragmented packet since only the first fragment contains the L4 information.
This option is only meaningful if the protocol match criteria specifies ICMP (1).
The no form of this command removes the criterion from the match entry.
Default
no icmp-type
Parameters
- icmp-type
Specifies the ICMP type values that must be present to match.
option-present
Syntax
option-present {true | false}
no option-present
Context
config>filter>ip-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures matching packets that contain the option field or have an option field of zero in the IP header as an IP filter match criterion.
The no form of this command removes the checking of the option field in the IP header as a match criterion.
Parameters
- true
Specifies matching on all IP packets that contain the option field in the header. A match will occur for all packets that have the option field present. An option field of zero is considered as no option present.
- false
Specifies matching on IP packets that do not have any option field present in the IP header. (an option field of zero). An option field of zero is considered as no option present.
src-ip
Syntax
src-ip {ip-address/mask | ip-address ipv4-address-mask}
no src-ip
Context
config>filter>ip-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a source IPv4 address range to be used as an IP filter match criterion.
To match on the source IPv4 address, specify the address and its associated mask, for example, 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 may also be used.
The no form of this command removes the source IPv4 address match criterion.
Default
no src-ip
Parameters
- ip-address
Specifies the IPv4 prefix for the IP match criterion in dotted decimal notation.
- mask
Specifies the subnet mask length, expressed as a decimal integer.
- ipv4-address-mask
Specifies any mask, expressed in dotted quad notation.
src-ip
Syntax
src-ip {ipv6-address/prefix-length}
no src-ip
Context
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a source IPv6 address range to be used as an IP filter match criterion.
To match on the source IPv6 address, specify the address and its associated mask.
If the filter is created to match 64-bit address, the IPv6 address specified for the match must contain only the first 64-bits (that is, the first four 16-bit groups of the IPv6 address).
The no form of this command removes the source IPv6 address match criterion.
Default
no src-ip
Parameters
- ipv6-address
Specifies the IPv6 prefix for the IP match criterion in hex digits.
- prefix-length
Specifies the IPv6 prefix length for the IPv6 address as a decimal integer.
src-port
Syntax
src-port {eq} src-port-number
src-port range src-port-number1 src-port-number2
no src-port
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a source TCP or UDP port number for an IP filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, etc) fragments of a fragmented packet since only the first fragment contains the L4 information.
- One port range hardware entry is required to match a unique combination of port range values configured by the user. Two port range values (for example, port range 1024 to 2048 and port range 3050 to 3055) are considered to be unique if their range 1 and range 2 values do not match. Each unique port range value consumes one entry each in hardware.
- Each unique port range entry requires two entries in the hardware table if it is used for both a source and destination match. In other words, a unique port range value requires one entry for matching a source port and another entry for matching a destination port.
- If one or more QoS or ACL policy use the same unique port range value for either the source port match or destination port match but not both, only a single entry in the hardware table is required. For example, if port range 1000 to 2000 is used in both the access ingress policy and filter policy to match on source port, it requires one entry in the hardware port range table.
- If one or more QoS and or ACL policy use the same unique port range value for both source port match and destination port, two entries in the hardware table are required. For example, if port range 1000 to 2000 is used in both access ingress policy and filter policy to match on both the source port and destination port, it requires two entries in the hardware port range table.
The no form of this command removes the source port match criterion.
Default
no src-port
Parameters
- eq
Specifies the operator to use relative to src-port-number for specifying the port number match criteria. The eq keyword specifies that src-port-number must be an exact match.
- src-port-number
Specifies the source port number to be used as a match criteria expressed as a decimal integer.
- range src-port-number1
-
Specifies the first source port number in the range to match a range of ports. This parameter is only available on the 7210 SAS-Mxp.
- range src-port-number2
-
Specifies the last source port number in the range to match a range of ports. The second number must be greater than the first number in the range. This parameter is only available on the 7210 SAS-Mxp.
tcp-ack
Syntax
tcp-ack {true | false}
no tcp-ack
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures matching on the ACK bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, etc) fragments of a fragmented packet since only the first fragment contains the L4 information.
The no form of this command removes the criterion from the match entry.
Default
no tcp-ack
Parameters
- true
Specifies matching on IP packets that have the ACK bit set in the control bits of the TCP header of an IP packet.
- false
Specifies matching on IP packets that do not have the ACK bit set in the control bits of the TCP header of the IP packet.
tcp-syn
Syntax
tcp-syn {true | false}
no tcp-syn
Context
config>filter>ip-filter>entry>match
config>filter>ipv6-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures matching on the SYN bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, and so on) fragments of a fragmented packet since only the first fragment contains the L4 information.
The SYN bit is normally set when the source of the packet needs to initiate a TCP session with the specified destination IP address.
The no form of this command removes the criterion from the match entry.
Default
no tcp-syn
Parameters
- true
Specifies matching on IP packets that have the SYN bit set in the control bits of the TCP header.
- false
Specifies matching on IP packets that do not have the SYN bit set in the control bits of the TCP header.
MAC filter match criteria
dot1p
Syntax
dot1p ip-value [mask]
no dot1p
Context
config>filter>mac-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures an IEEE 802.1p value or range to be used as a MAC filter match criterion.
When a frame is missing the 802.1p bits, specifying an dot1p match criterion will fail for the frame and result in a non-match for the MAC filter entry.
The no form of this command removes the criterion from the match entry.
The MAC filter applied on the SAP egress can match the details of the packet-on-the-wire. For example, a QinQ packet came in on a null SAP and egressing on a dot1p-encapsulated port, the packet-on-the-wire will have three tags. Now, the etype=0x8100 and dot1p will equal the outer VLAN tag dot1p. This Etype and dot1p can be configured on the egress filter to match this packet.
Default
no dot1p
Parameters
- ip-value
Specifies the IEEE 802.1p value, in decimal notayion
- mask
Specifies a 3-bit mask.
This 3-bit mask can be specified using the following formats:
Table 11. 3-bit mask format Format style
Format syntax
Example
Decimal
D
4
Hexadecimal
0xH
0x4
Binary
0bBBB
0b100
To select a range from 4 up to 7 specify p-value of 4 and a mask of 0b100 for value and mask.
dst-mac
Syntax
dst-mac ieee-address [mask]
no dst-mac
Context
config>filter>mac-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Configures a destination MAC address or range to be used as a MAC filter match criterion.
The no form of this command removes the destination mac address as the match criterion.
Default
no dst-mac
Parameters
- ieee-address
Specifies the MAC address to be used as a match criterion.
- mask
Specifies a 48-bit mask to match a range of MAC address values.
This 48-bit mask can be configured using the following formats:
Table 12. 48-bit mask format Format style
Format syntax
Example
Decimal
DDDDDDDDDDDDDD
281474959933440
Hexadecimal
0xHHHHHHHHHHHH
0xFFFFFF000000
Binary
0bBBBBBBB...B
0b11110000...B
To configure so that all packets with a source MAC OUI value of 00-03-FA are subject to a match condition, then the entry should be specified as: 0003FA000000 0xFFFFFF000000
etype
Syntax
etype ethernet-type
no etype
Context
config>filter>mac-filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures an Ethernet type II Ethertype value for use as a MAC filter match criterion.
The Ethernet type field is a two-byte field used to identify the protocol carried by the Ethernet frame. For example, 0800 is used to identify the IPv4 packets.
The Ethernet type field is used by the Ethernet version-II frames. IEEE 802.3 Ethernet frames do not use the type field. MAC match criteria exclusivity rules describes fields that are exclusive based on the frame format.
The data plane processes a maximum of two VLAN tags in a received packet. The Ethertype used in the MAC matching criteria for ACLs is the Ethertype that is found in the packet after processing single-tagged frames, double-tagged frames, and no-tag frames
The packet is considered to have no tags if at least one of the following criteria is true.
The packet is a null-tagged frame
The packet is a priority-tagged frame
The outermost Ethertype does not match the default Ethertype (0x8100)
The outermost Ethertype does not match the configured dot1q-etype on Dot1q encapsulated ports
The outermost Ethertype does not match the configured qinq-etype on QinQ encapsulated ports
The packet is considered to have a single tag if at least one of the following criteria is true.
The outermost Ethertype matches the default Ethertype (0x8100)
The outermost Ethertype matches the configured dot1q-etype on Dot1q encapsulated ports
The outermost Ethertype matches the configured qinq-etype on QinQ encapsulated ports
The packet is considered to have double tags if at least one of the following criteria is true.
The outermost Ethertype matches the default Ethernet type (0x8100)
The configured dot1q-etype on Dot1q encapsulated ports and the immediately following Ethertype match the default Ethertype (0x8100)
The configured qinq-etype on QinQ encapsulated ports and the immediately following Ethertype match the default Ethertype (0x8100)
The no form of this command removes the previously entered etype field as the match criteria.
Default
no etype
Parameters
- ethernet-type
Specifies the Ethernet type II frame Ethertype value to be used as a match criterion, expressed in hexadecimal.
src-mac
Syntax
src-mac ieee-address [ieee-address-mask]
no src-mac
Context
config>filter>mac-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a source MAC address or range to be used as a MAC filter match criterion.
The no form of this command removes the source mac as the match criteria.
Default
no src-mac
Parameters
- ieee-address
Specifies the 48-bit IEEE mac address to be used as a match criterion.
- ieee-address-mask
Specifies a 48-bit mask.
This 48-bit mask can be configured using the following formats:
Table 13. 48-bit mask format Format style
Format syntax
Example
Decimal
DDDDDDDDDDDDDD
281474959933440
Hexadecimal
0xHHHHHHHHHHHH
0xFFFFFF000000
Binary
0bBBBBBBB...B
0b11110000...B
To configure so that all packets with a source MAC OUI value of 00-03-FA are subject to a match condition, the entry should be specified as: 003FA000000 0xFFFFFF000000
Policy and entry maintenance commands
copy
Syntax
copy {ip-filter | ipv6-filter | mac-filter} source-filter-id dest-filter-id dest-filter-id [overwrite]
Context
config>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command copies existing filter list entries for a specific filter ID to another filter ID. The copy command is a configuration level maintenance tool to create new filters using existing filters. It also allows bulk modifications to an existing policy with the use of the overwrite keyword. If overwrite is not specified, an error occurs if the destination policy ID exists.
Parameters
- ip-filter
Specifies that the source-filter-id and the dest-filter-id are IP filter IDs.
- ipv6-filter
Specifies that the source-filter-id and the dest-filter-id are IPv6 filter IDs.
- mac-filter
Specifies that the source-filter-id and the dest-filter-id are MAC filter IDs.
- source-filter-id
Specifies the source-filter-id, which identifies the source filter policy from which the copy command will attempt to copy. The filter policy must exist within the context of the preceding keyword (ip-filter or mac-filter).
- dest-filter-id
Specifies the destination filter policy where the copy command attempts to copy. If the overwrite keyword does not follow, the filter policy ID cannot already exist within the system for the filter type the copy command is issued for. If the overwrite keyword is present, the destination policy ID may or may not exist.
- overwrite
Specifies that the destination filter ID may exist. If it does, the existing destination filter ID will be overwritten with the contents of the source filter ID. If the destination filter ID exists, either overwrite must be specified or an error message is returned. If overwrite is specified, the function of copying from source to destination occurs in a ‟break before make” manner, so must be handled with care.
filter-name
Syntax
filter-name filter-name
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures filter-name attribute of a specific filter. filter-name, when configured, can be used instead of filter ID to reference the specific policy in the CLI.
Default
no filter-name
Parameters
- filter-name
Specifies a string of up to 64 characters uniquely identifying this filter policy.
renum
Syntax
renum old-entry-id new-entry-id
Context
config>filter>ip-filter
config>filter>ipv6-filter
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command renumbers existing MAC or IP filter entries to properly sequence filter entries. This may be required in some cases since the OS exits when the first match is found and executes the actions according to the accompanying action command. This requires that entries be sequenced correctly from most to least explicit.
Parameters
- old-entry-id
Specifies the entry number of an existing entry.
- new-entry-id
Specifies the new entry-number to be assigned to the old entry.
type
Syntax
type filter-type
Context
config>filter>mac-filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the type of mac-filter as normal, ISID or VID types.
Default
normal
Parameters
- filter-type
Specifies which type of entries this MAC filter can contain.
Show commands
download-failed
Syntax
download-failed
Context
show>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays all filter entries for which the download has failed.
Output
The following output is an example of failed download information, and Output fields: filter download-failed describes the output fields.
Sample outputA:ALA-48# show filter download-failed
============================================
Filter entries for which download failed
============================================
Filter-type Filter-Id Filter-Entry
--------------------------------------------
ip 1 10
============================================
A:ALA-48#
| Label | Description |
|---|---|
|
Filter-type |
Displays the filter type |
|
Filter-ID |
Displays the ID of the filter |
|
Filter-Entry |
Displays the entry number of the filter |
ip
Syntax
ip ip-filter-id [association | counters]
ip ip-filter-id entry entry-id [counters]
Context
show>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays IP filter information.
Parameters
- ip-filter-id
Displays detailed information for the specified filter ID and its filter entries.
- entry entry-id
Displays information about the specified filter entry ID for the specified filter ID only.
- associations
Displays information about where the filter policy ID is applied to the detailed filter policy ID output.
- counters
Displays counter information for the specified filter ID. Egress counters count the packets without Layer 2 encapsulation. Ingress counters count the packets with Layer 2 encapsulation.
- type entry-type
Displays information about the specified filter ID for the specified entry-type only
Output
The following outputs are examples of IP filter information, and the associated tables describe the output fields.
-
IP Filter: Sample Output , Output fields: filter IP
-
IP Filter with Filter ID Specified: Sample Output , Sample Output on the 7210 SAS-Mxp, Output fields: filter with filter ID specified
-
IP Filter with Time-range Specified: Sample Output
-
IP Filter Associations: Sample Output , Output fields: filter IP associations
-
IP Filter Counters: Output fields: filter counters
A:ALA-49# show filter ip
===============================================================================
IP Filters
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
1 Template Yes
3 Template Yes
6 Template Yes
10 Template No
11 Template No
-------------------------------------------------------------------------------
Num IP filters: 5
===============================================================================
A:ALA-49#
*A:Dut-C>config>filter# show filter ip
===============================================================================
IP Filters Total: 2
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
10001 Template Yes
fSpec-1 Template Yes BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Num IP filters: 2
===============================================================================
*A:Dut-C>config>filter#
| Label | Description |
|---|---|
|
Filter Id |
The IP filter ID. |
|
Scope |
Template The filter policy is of type template. Exclusive The filter policy is of type exclusive. |
|
Applied |
No The filter policy ID has not been applied. Yes The filter policy ID has been applied. |
|
Description |
The IP filter policy description. |
A:ALA-49>config>filter# show filter ip 3
===============================================================================
IP Filter
===============================================================================
Filter Id : 3 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 1
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10
Src. IP : 10.1.1.1/24 Src. Port : None
Dest. IP : 0.0.0.0/0 Dest. Port : None
Protocol : 2 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 0 Egr. Matches : 0
===============================================================================
A:ALA-49>config>filter#
*A:Dut-C>config>filter# show filter ip fSpec-1 associations
===============================================================================
IP Filter
===============================================================================
Filter Id : fSpec-1 Applied : Yes
Scope : Template Def. Action : Forward
Radius Ins Pt: n/a
CrCtl. Ins Pt: n/a
Entries : 2 (insert By Bgp)
Description : BGP FlowSpec filter for the Base router
-------------------------------------------------------------------------------
Filter Association : IP
-------------------------------------------------------------------------------
Service Id : 1 Type : IES
- SAP 1/1/3:1.1 (merged in ip-fltr 10001)
===============================================================================
*A:Dut-C>config>filter#
*A:Dut-C>config>filter# show filter ip 10001
===============================================================================
IP Filter
===============================================================================
Filter Id : 10001 Applied : Yes
Scope : Template Def. Action : Drop
Radius Ins Pt: n/a
CrCtl. Ins Pt: n/a
Entries : 1
BGP Entries : 2
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Log Id : n/a
Src. IP : 0.0.0.0/0 Src. Port : None
Dest. IP : 0.0.0.0/0 Dest. Port : None
Protocol : 6 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Match action : Forward
Next Hop : Not Specified
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : fSpec-1-32767 - inserted by BGP FLowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 0.0.0.0/0 Src. Port : None
Dest. IP : 0.0.0.0/0 Dest. Port : None
Protocol : 6 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : fSpec-1-49151 - inserted by BGP FLowSpec
Description : (Not Specified)
Log Id : n/a
Src. IP : 0.0.0.0/0 Src. Port : None
Dest. IP : 0.0.0.0/0 Dest. Port : None
Protocol : 17 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
Sampling : Off Int. Sampling : On
IP-Option : 0/0 Multiple Option: Off
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
===============================================================================
*A:Dut-C>config>filter#
===============================================================================
IP Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
System filter: Unchained
RadSh. Ins Pt: n/a
PccRl. Ins Pt: n/a
Entries : 16
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1
Description : Entry1
Src. IP : 0.0.0.0/0
Src. Port : 10..15
Dest. IP : 0.0.0.0/0
Dest. Port : 10..15
Protocol : 6 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off
Sampling : Off Int. Sampling : On
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Egress PBR : Disabled
Match action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : 2 (Inactive)
Description : Entry2
Src. IP : 0.0.0.0/0
Src. Port : 20..25
Dest. IP : 0.0.0.0/0
Dest. Port : 20..25
Protocol : 6 Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off
Sampling : Off Int. Sampling : On
TCP-syn : Off TCP-ack : Off
Option-pres : Off
Egress PBR : Disabled
Match action : Drop
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
| Label | Description |
|---|---|
|
Filter Id |
The IP filter policy ID. |
|
Scope |
Template — Indicates the filter policy is of type template. |
|
Exclusive — Indicates the filter policy is of type exclusive. |
|
|
Entries |
The number of entries configured in this filter ID. |
|
Description |
The IP filter policy description. |
|
Applied |
No — Indicates the filter policy ID has not been applied. |
|
Yes — Indicates the filter policy ID has been applied. |
|
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
|
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
|
Filter Match Criteria |
IP — Indicates the filter is an IP filter policy. |
|
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
|
ICMP Type |
The ICMP type match criterion. Undefined indicates no ICMP type specified. |
|
Fragment |
False — Configures a match on all non-fragmented IP packets. |
|
True — Configures a match on all fragmented IP packets. |
|
|
Off — Fragments are not a matching criteria. All fragments and non-fragments implicitly match. |
|
|
TCP-syn |
False — Configures a match on packets with the SYN flag set to false. |
|
True — Configured a match on packets with the SYN flag set to true. |
|
|
Off — The state of the TCP SYN flag is not considered as part of the match criteria. |
|
|
Match action |
Default — The filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates the entry is Inactive, the filter entry is incomplete, no action was specified. |
|
Drop — Drop packets matching the filter entry. |
|
|
Forward — The explicit action to perform is forwarding of the packet. |
|
|
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
|
Src. IP |
The source IP address. |
|
Src. Port |
The source TCP or UDP port number. |
|
Dest. IP |
The destination IP address. |
|
Dest. Port |
The destination TCP or UDP port number. |
|
Dscp |
The DiffServ Code Point (DSCP) name. |
|
ICMP Code |
The ICMP code field in the ICMP header of an IP packet. |
|
Option-present |
Off — Does not search for packets that contain the option field or have an option field of zero. |
|
On — Matches packets that contain the option field or have an option field of zero be used as IP filter match criteria. |
|
|
TCP-ack |
False — Configures a match on packets with the ACK flag set to false. |
|
True — Configures a match on packets with the ACK flag set to true. |
|
|
Off — The state of the TCP ACK flag is not considered as part of the match criteria. |
|
|
Egr. Matches |
The number of egress filter matches or hits for the filter entry. |
A:ALA-49# show filter ip 10
===============================================================================
IP Filter
===============================================================================
Filter Id : 10 Applied : No
Scope : Template Def. Action : Drop
Entries : 2
-------------------------------------------------------------------------------
Filter Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 1010
time-range : day Cur. Status : Inactive
Src. IP : 0.0.0.0/0 Src. Port : None
Dest. IP : 10.10.100.1/24 Dest. Port : None
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
TCP-syn : Off TCP-ack : Off
Match action : Forward
Ing. Matches : 0 Egr. Matches : 0
Entry : 1020
time-range : night Cur. Status : Active
Src. IP : 0.0.0.0/0 Src. Port : None
Dest. IP : 10.10.1.1/16 Dest. Port : None
Protocol : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
Fragment : Off Option-present : Off
TCP-syn : Off TCP-ack : Off
Match action : Forward
Ing. Matches : 0 Egr. Matches : 0
===============================================================================
A:ALA-49#
A:ALA-49# show filter ip 1 associations
===============================================================================
IP Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 1
-------------------------------------------------------------------------------
Filter Association : IP
-------------------------------------------------------------------------------
Service Id : 1001 Type : VPLS
- SAP 1/1/1:1001 (Ingress)
Service Id : 2000 Type : Epipe
- SAP 1/1/1:2000 (Ingress)
===============================================================================
A:ALA-49#
A:ALA-49# show filter ip 160 associations
===============================================================================
IP Filter
===============================================================================
Filter Id : 160 Applied : No
Scope : Template Def. Action : Drop
Entries : 0
-------------------------------------------------------------------------------
Filter Association : IP
-------------------------------------------------------------------------------
Tod-suite "english_suite"
- ingress, time-range "day" (priority 5)
===============================================================================
A:ALA-49#
| Label | Description |
|---|---|
|
Filter Id |
The IP filter policy ID. |
|
Scope |
Template — The filter policy is of type Template. |
|
Exclusive — The filter policy is of type Exclusive. |
|
|
Entries |
The number of entries configured in this filter ID. |
|
Applied |
Yes — The filter policy ID has been applied. |
|
No — The filter policy ID has not been applied. |
|
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Service Id |
The service ID on which the filter policy ID is applied. |
|
SAP |
The Service Access Point on which the filter policy ID is applied. |
|
(Ingress) |
The filter policy ID is applied as an ingress filter policy on the interface. |
|
(Egress) |
The filter policy ID is applied as an egress filter policy on the interface. |
|
Type |
The type of service of the service ID. |
| Label | Description |
|---|---|
|
IP Filter Filter Id |
The IP filter policy ID. |
|
Scope |
Template — The filter policy is of type Template. |
|
Exclusive — The filter policy is of type Exclusive. |
|
|
Applied |
No — The filter policy ID has not been applied. |
|
Yes — The filter policy ID has been applied. |
|
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
|
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
|
Filter Match Criteria |
IP — Indicates the filter is an IP filter policy. |
|
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is Inactive, then the filter entry is incomplete as no action has been specified. |
|
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. Ingress counters count the packets with Layer 2 encapsulation. |
|
Egr. Matches |
The number of egress filter matches or hits for the filter entry. Egress counters count the packets without Layer 2 encapsulation. |
ipv6
Syntax
ipv6 {ipv6-filter-id [entry entry-id] [association | counters]}
Context
show>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays IPv6 filter information.
Parameters
- ipv6-filter-id
Displays detailed information for the specified IPv6 filter ID and filter entries.
- entry entry-id
Displays information about the specified IPv6 filter entry ID for the specified filter ID.
- associations
Displays information about where the IPv6 filter policy ID is applied to the detailed filter policy ID output.
- counters
Displays counter information for the specified IPv6 filter ID.
Egress counters count the packets without Layer 2 encapsulation. Ingress counters count the packets with Layer 2 encapsulation.
Output
The following outputs are examples of IP filter information, and the associated tables describe the output fields.
Sample Output, Output fields: IP filter (no filter-id specified)
Sample Output for IPv6 Filter with Filter ID Specified, Output fields: filter (with filter-id specified)
Sample Output for IPv6 Filter Associations, Output fields: filter associations
Sample Output for IPv6 Filter Counters, Output fields: filter counters
*A:7210SAS>show>filter# ipv6
===============================================================================
IPv6 Filters Total: 1
===============================================================================
Filter-Id Scope Applied Description
-------------------------------------------------------------------------------
1 Template Yes
-------------------------------------------------------------------------------
Num IPv6 filters: 1
===============================================================================
*A:7210SAS>show>filter#
| Label | Description |
|---|---|
Filter Id |
The IP filter ID. |
Scope Template |
The filter policy is of type template. |
Exclusive |
The filter policy is of type exclusive. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Description |
The IP filter policy description. |
*A:7210SAS>show>filter# ipv6 1
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 2
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 1
Description : Test
Src. IP : 2001:db8::1/128 Src. Port : None
Dest. IP : 2001:db8::/0 Dest. Port : None
Next Header : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
TCP-syn : Off TCP-ack : Off
Match action : Forward
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : 2
Description : (Not Specified)
Src. IP : ::/0 Src. Port : None
Dest. IP : 1:2::1AFC/128 Dest. Port : None
Next Header : Undefined Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
TCP-syn : Off TCP-ack : Off
Match action : Drop
Ing. Matches : 819 pkts
Egr. Matches : 0 pkts
===============================================================================
*A:7210SAS>show>filter#
| Label | Description |
|---|---|
Filter Id |
The IP filter policy ID. |
Scope |
Template — The filter policy is of type template. |
Exclusive — The filter policy is of type exclusive. |
|
Entries |
The number of entries configured in this filter ID. |
Description |
The IP filter policy description. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Filter Match Criteria |
IP — Indicates the filter is an IP filter policy. |
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
Src. IP |
The source IP address and mask match criterion. 0.0.0.0/0 indicates no criterion specified for the filter entry. |
Dest. IP |
The destination IP address and mask match criterion. 0.0.0.0/0 indicates no criterion specified for the filter entry. |
ICMP Type |
The ICMP type match criterion. Undefined indicates no ICMP type specified. |
IP-Option |
Specifies matching packets with a specific IP option or a range of IP options in the IP header for IP filter match criteria. |
TCP-syn |
False — Configures a match on packets with the SYN flag set to false. |
True — Configured a match on packets with the SYN flag set to true. |
|
Off — The state of the TCP SYN flag is not considered as part of the match criteria. |
|
Match action |
Default — The filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
Drop — Drop packets matching the filter entry. |
|
Forward — The explicit action to perform is forwarding of the packet. If the action is Forward, then, if configured, the next-hop information should be displayed, including Nexthop: <IP address>, Indirect: <IP address> or Interface: <IP interface name>. |
|
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
Src. Port |
The source TCP or UDP port number or port range. |
Dest. Port |
The destination TCP or UDP port number or port range. |
Dscp |
The DiffServ Code Point (DSCP) name. |
ICMP Code |
The ICMP code field in the ICMP header of an IP packet. |
TCP-ack |
False — Configures a match on packets with the ACK flag set to false. |
True — Configured a match on packets with the ACK flag set to true. |
|
Off — The state of the TCP ACK flag is not considered as part of the match criteria |
|
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
Egr. Matches |
The number of egress filter matches or hits for the filter entry. |
*A:7210SAS>show>filter# ipv6 1 associations
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 2
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Association : IPv6
-------------------------------------------------------------------------------
Service Id : 1 Type : Epipe
- SAP 1/1/1:1 (Ingress)
Service Id : 2 Type : VPLS
- SAP 1/1/1:2 (Ingress)
- SAP 1/1/1:3 (Ingress)
===============================================================================
*A:7210SAS>show>filter#
| Label | Description |
|---|---|
Filter Id |
The IPv6 filter policy ID. |
Scope |
Template — The filter policy is of type Template. |
Exclusive — The filter policy is of type Exclusive. |
|
Entries |
The number of entries configured in this filter ID. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Description |
The IP filter policy description. |
Service Id |
The service ID on which the filter policy ID has been applied. |
SAP |
The Service Access Point on which the filter policy ID is applied. |
Ingress — The filter policy ID is applied as an ingress filter policy on the interface. |
|
Egress — The filter policy ID is applied as an egress filter policy on the interface. |
|
Type |
The type of service of the service ID. |
*A:7210SAS>show>filter# ipv6 1 counters
===============================================================================
IPv6 Filter
===============================================================================
Filter Id : 1 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 2
Description : (Not Specified)
-------------------------------------------------------------------------------
Filter Match Criteria : IPv6
-------------------------------------------------------------------------------
Entry : 1
Ing. Matches : 0 pkts
Egr. Matches : 0 pkts
Entry : 2
Ing. Matches : 819 pkts
Egr. Matches : 0 pkts
===============================================================================
*A:7210SAS>show>filter#
| Label | Description |
|---|---|
Filter Id |
The IPv6 filter policy ID. |
Scope |
Template — The filter policy is of type Template. |
Exclusive — The filter policy is of type Exclusive. |
|
Entries |
The number of entries configured in this filter ID. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Description |
The IP filter policy description. |
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
Egr. Matches |
The number of egress filter matches or hits for the filter entry. Egress counters count the packets without Layer 2 encapsulation. Ingress counters count the packets with Layer 2 encapsulation. |
mac
Syntax
mac [mac-filter-id [associations | counters] [entry entry-id]]
Context
show>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays MAC filter information.
Parameters
- mac-filter-id
Displays detailed information for the specified filter ID and its filter entries.
- associations
Displays information about where the filter policy ID is applied to the detailed filter policy ID output.
- counters
Displays counter information for the specified filter ID.
- entry entry-id
Displays information about the specified filter entry ID for the specified filter ID only.
Output
The following outputs are examples of MAC filter information, and the associated tables describe the output fields.
Sample Output, Sample Detailed Output, Output fields: filter MAC
Sample Output for MAC Filter Associations, Output fields: filter MAC associations
Sample Output for MAC Filter Counters, Output fields: filter MAC counters
===============================================================================
Mac Filter
===============================================================================
Filter Id : 8 Applied : Yes
Scope : Template Def. Action : Forward
Entries : 2
Description : Description for Mac Filter Policy id # 8
-------------------------------------------------------------------------------
Filter Match Criteria : Mac
-------------------------------------------------------------------------------
Entry : 8 FrameType : Ethernet
Ing. Matches: 80 pkts
Egr. Matches: 62 pkts
Entry : 10 FrameType : Ethernet
Ing. Matches: 80 pkts
Egr. Matches: 80 pkts
===============================================================================
Mac Filter : 200
===============================================================================
Filter Id : 200 Applied : No
Scope : Exclusive D. Action : Drop
Description : Forward SERVER sourced packets
-------------------------------------------------------------------------------
Filter Match Criteria : Mac
-------------------------------------------------------------------------------
Entry : 200 FrameType : 802.2SNAP
Description : Not Available
Src Mac : 00:00:5a:00:00:00 ff:ff:ff:00:00:00
Dest Mac : 00:00:00:00:00:00 00:00:00:00:00:00
Dot1p : Undefined Ethertype : 802.2SNAP
Match action : Forward
Ing. Matches : 0 Egr. Matches : 0
Entry : 300 (Inactive) FrameType : Ethernet
Description : Not Available
Src Mac : 00:00:00:00:00:00 00:00:00:00:00:00
Dest Mac : 00:00:00:00:00:00 00:00:00:00:00:00
Dot1p : Undefined Ethertype : Ethernet
Match action : Default
Ing. Matches : 0 Egr. Matches : 0
===============================================================================
| Label | Description |
|---|---|
MAC Filter Filter Id |
The MAC filter policy ID. |
Scope |
Template — The filter policy is of type Template. |
Exclusive — The filter policy is of type Exclusive. |
|
Description |
The IP filter policy description. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Filter Match Criteria |
MAC — Indicates that the filter is an MAC filter policy. |
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
Description |
The filter entry description. |
FrameType |
Ethernet — The entry ID match frame type is Ethernet IEEE 802.3. |
Ethernet II — The entry ID match frame type is Ethernet Type II |
|
Src MAC |
The source MAC address and mask match criterion. When both the MAC address and mask are all zeros, no criterion specified for the filter entry. |
Dest MAC |
The destination MAC address and mask match criterion. When both the MAC address and mask are all zeros, no criterion specified for the filter entry. |
Dot1p |
The IEEE 802.1p value for the match criteria. Undefined indicates no value is specified. |
Ethertype |
The Ethertype value match criterion. |
Match action |
Default — The filter does not have an explicit forward or drop match action specified. If the filter entry ID indicates the entry is Inactive, the filter entry is incomplete, no action was specified. |
Drop — Packets matching the filter entry criteria are dropped. |
|
Forward — Packets matching the filter entry criteria are forwarded. |
|
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
Egr. Matches |
The number of egress filter matches or hits for the filter entry. |
A:ALA-49# show filter mac 3 associations
===============================================================================
Mac Filter
===============================================================================
Filter ID : 3 Applied : Yes
Scope : Template Def. Action : Drop
Entries : 1
-------------------------------------------------------------------------------
Filter Association : Mac
-------------------------------------------------------------------------------
Service Id : 1001 Type : VPLS
- SAP 1/1/1:1001 (Egress)
===============================================================================
A:ALA-49#
| Label | Description |
|---|---|
Filter Association |
Mac — The filter associations displayed are for a MAC filter policy ID. |
Service Id |
The service ID on which the filter policy ID is applied. |
SAP |
The Service Access Point on which the filter policy ID is applied. |
Type |
The type of service of the Service ID. |
(Ingress) |
The filter policy ID is applied as an ingress filter policy on the interface. |
(Egress) |
The filter policy ID is applied as an egress filter policy on the interface. |
A:ALA-49# show filter mac 8 counters
| Label | Description |
|---|---|
Mac Filter Filter Id |
The MAC filter policy ID. |
Scope |
Template — The filter policy is of type Template. |
Exclusive — The filter policy is of type Exclusive. |
|
Description |
The MAC filter policy description. |
Applied |
No — The filter policy ID has not been applied. |
Yes — The filter policy ID has been applied. |
|
Def. Action |
Forward — The default action for the filter ID for packets that do not match the filter entries is to forward. |
Drop — The default action for the filter ID for packets that do not match the filter entries is to drop. |
|
Filter Match Criteria |
Mac — Indicates that the filter is an MAC filter policy. |
Entry |
The filter ID filter entry ID. If the filter entry ID indicates the entry is (Inactive), then the filter entry is incomplete as no action has been specified. |
FrameType |
Ethernet II — The entry ID match frame type is Ethernet Type II. |
Ing. Matches |
The number of ingress filter matches or hits for the filter entry. |
Egr. Matches |
The number of egress filter matches or hits for the filter entry. |
Clear commands
ip
Syntax
ip ip-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command clears the counters associated with the IP filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Parameters
- ip-filter-id
Specifies the IP filter policy ID.
- entry-id
Specifies that only the counters associated with the specified filter policy entry will be cleared.
- ingress
Specifies to only clear the ingress counters.
- egress
Specifies to only clear the egress counters.
ipv6
Syntax
ipv6 ip-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command clears the counters associated with the IPv6 filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Parameters
- ip-filter-id
Specifies the IP filter policy ID.
- entry-id
Specifies that only the counters associated with the specified filter policy entry will be cleared.
- ingress
Specifies to only clear the ingress counters.
- egress
Specifies to only clear the egress counters.
mac
Syntax
mac mac-filter-id [entry entry-id] [ingress | egress]
Context
clear>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command clears the counters associated with the MAC filter policy.
By default, all counters associated with the filter policy entries are reset. The scope of which counters are cleared can be narrowed using the command line parameters.
Parameters
- mac-filter-id
Specifies the MAC filter policy ID.
- entry-id
Specifies that only the counters associated with the specified filter policy entry will be cleared.
- ingress
Specifies to only clear the ingress counters.
- egress
Specifies to only clear the egress counters.
Monitor commands
ip
Syntax
ip ip-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command monitors the counters associated with the IP filter policy.
Parameters
- ip-filter-id
Specifies the IP filter policy ID.
- entry-id
Specifies that only the counters associated with the specified filter policy entry will be monitored.
- interval
Specifies the interval for each display, in seconds.
- repeat repeat
Specifies how many times the command is repeated.
- absolute
Displays raw statistics without processing. No calculations are performed on the delta or rate statistics.
- rate
Displays the rate-per-second for each statistic instead of the delta.
ipv6
Syntax
ipv6 ip-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command monitors the counters associated with the IPv6 filter policy.
Parameters
- ip-filter-id
Specifies the IP filter policy ID.
- entry-id
Specifies that only the counters associated with the specified filter policy entry will be monitored.
- interval seconds
Specifies the interval for each display, in seconds.
- repeat repeat
Specifies how many times the command is repeated.
- absolute
Displays raw statistics without processing. No calculations are performed on the delta or rate statistics.
- rate
Displays the rate-per-second for each statistic instead of the delta.
mac
Syntax
mac mac-filter-id entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command monitors the counters associated with the MAC filter policy.
Parameters
- mac mac-filter-id
Specifies the MAC filter policy ID.
- entry entry-id
Specifies that only the counters associated with the specified filter policy entry will be cleared.
- interval seconds
Specifies the interval for each display, in seconds.
- repeat repeat
Specifies how many times the command is repeated.
- absolute
Displays raw statistics without processing. No calculations are performed on the delta or rate statistics.
- rate
Displays the rate-per-second for each statistic instead of the delta.