Event and accounting logs
This chapter provides information about configuring event and accounting logs on the 7210 SAS.
Logging overview
The two primary types of logging supported on the 7210 SAS are event logging and accounting logs.
Event logging controls the generation, dissemination and recording of system events for monitoring status and troubleshooting faults within the system. The 7210 SAS groups events into four major categories or event sources:
security events
These are events that pertain to attempts to breach system security.
change events
These are events that pertain to the configuration and operation of the node.
main events
These are events that pertain to applications that are not assigned to other event categories/sources.
debug events
These are events that pertain to trace or other debugging information.
The following are events within the 7210 SAS and have the following characteristics:
a time stamp in UTC or local time
the generating application
a unique event ID within the application
the VRF-ID
a subject identifying the affected object
a short text description
Event control assigns the severity for each application event and whether the event should be generated or suppressed. The severity numbers and severity names supported on the 7210 SAS conform to ITU standards M.3100 X.733 and X.21 and are listed in the following table.
Severity number |
Severity name |
|---|---|
1 |
cleared |
2 |
indeterminate (info) |
3 |
critical |
4 |
major |
5 |
minor |
6 |
warning |
Events that are suppressed by event control do not generate event log entries. Event control maintains a count of the number of events generated (logged) and dropped (suppressed) for each application event. The severity of an application event can be configured in event control.
An event log in the 7210 SAS associates the event sources with logging destinations. Examples of logging destinations include, the console session, a specific Telnet or SSH session, memory logs, file destinations, SNMP trap groups and syslog destinations. A log filter policy can be associated with the event log to control which events are logged in the event log based on combinations of application, severity, event ID range, VRF ID, and the subject of the event.
The 7210 SAS accounting logs collect comprehensive accounting statistics to support a variety of billing models. The routers collect accounting data on services and network ports on a per-service class basis. In addition to gathering information critical for service billing, accounting records can be analyzed to provide insight about customer service trends for potential service revenue opportunities. Accounting statistics on network ports can be used to track link utilization and network traffic pattern trends. This information is valuable for traffic engineering and capacity planning within the network core.
Accounting statistics are collected according to the parameters defined within the context of an accounting policy. Accounting policies are applied to access objects (such as access ports and SAPs) or network objects (such as SDPs, network ports, network IP interface). Accounting statistics are collected by counters for individual services defined on the customer’s SAP or by the counters within forwarding class (FC) queues defined on the network ports.
The type of record defined within the accounting policy determines where a policy is applied, what statistics are collected and time interval at which to collect statistics.
The ‟location” field of the file-id allows the user configure the device and store it in any directory. The default value is cf1:, but it can also be uf1: (for devices supporting USB).
Log destinations
Both event logs and accounting logs use a common mechanism for referencing a log destination.
Only a single log destination can be associated with an event log or with an accounting log. An event log can be associated with multiple event sources, but it can only have a single log destination.
A file destination is the only type of log destination that can be configured for an accounting log.
Console
Sending events to a console destination means the message is sent to the system console. The console device can be used as an event log destination.
Session
A session destination is a temporary log destination that directs entries to the active Telnet or SSH session for the duration of the session. When the session is terminated, for example, when the user logs out, the event log is removed. Event logs configured with a session destination are not stored in the configuration file. Event logs can direct log entries to the session destination.
Memory logs
A memory log is a circular buffer. When the log is full, the oldest entry in the log is replaced with the new entry. When a memory log is created, the specific number of entries it can hold can be specified, otherwise it assumes a default size. An event log can send entries to a memory log destination.
Log files
Log files can be used by both event logs and accounting logs and are stored on the compact flash devices (specifically cf1:) in the file system.
A log file is identified with a single log file ID, but a log file is generally composed of a number individual files in the file system. A log file is configured with a rollover parameter, expressed in minutes, which represents the length of time an individual log file should be written to before a new file is created for the relevant log file ID. The rollover time is checked only when an update to the log is performed. Therefore, complying to this rule is subject to the incoming rate of the data being logged. For example, if the rate is very low, the actual rollover time may be longer than the configured value.
The retention time for a log file specifies the amount of time the file should be retained on the system based on the creation date and time of the file.
When a log file is created, only the compact flash device for the log file is specified. Log files are created in specific subdirectories with standardized names depending on the type of information stored in the log file.
Event log files are always created in the \log directory on the specified compact flash device. The naming convention for event log files is:
log eeff-timestamp
where:
ee is the event log ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2007)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14 seconds)
Accounting log files are created in the \act-collect directory on a compact flash device (cf1). The naming convention for accounting log files is nearly the same as for log files except the prefix act is used instead of the prefix log. The naming convention for accounting logs is:
act aaff-timestamp.xml.gz
where:
aa is the accounting policy ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2022)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14 seconds)
Accounting logs are .xml files created in a compressed format and have a .gz extension.
The \act-collect directory is where active accounting logs are written. When an accounting log is rolled over, the active file is closed and archived in the \act directory before a new active accounting log file created in \act-collect.
SNMP trap group
An event log can be configured to send events to SNMP trap receivers by specifying an SNMP trap group destination.
An SNMP trap group can have multiple trap targets. Each trap target can have different operational parameters.
A trap destination has the following properties:
the IP address of the trap receiver
the UDP port used to send the SNMP trap
SNMP version (v1, v2c, or v3) used to format the SNMP notification
SNMP community name for SNMPv1 and SNMPv2c receivers
security name and level for SNMPv3 trap receivers
For SNMP traps that are sent in-band, the source IP address of the trap is the system IP address of the 7210 SAS.
Each trap target destination of a trap group receives the identical sequence of events as defined by the log ID and the associated sources and log filter applied.
Syslog
An event log can be configured to send events to one syslog destination. Syslog destinations have the following properties:
syslog server IP address
UDP port used to send the syslog message
Syslog Facility Code (0 - 23) (default 23 - local 7)
Syslog Severity Threshold (0 - 7)
Events that exceed the configured level are sent
Because syslog uses eight severity levels whereas the 7210 SAS uses six internal severity levels, the severity levels are mapped to syslog severities. The following table lists the severity level mappings to syslog severities.
Severity level |
Numerical severity (highest to lowest) |
Syslog configured severity |
Definition |
|---|---|---|---|
0 |
emergency |
System is unusable |
|
3 |
1 |
alert |
Action must be taken immediately |
4 |
2 |
critical |
Critical conditions |
5 |
3 |
error |
Error conditions |
6 |
4 |
warning |
Warning conditions |
5 |
notice |
Normal but significant condition |
|
1 cleared 2 indeterminate |
6 |
info |
Informational messages |
7 |
debug |
Debug-level messages |
Event logs
Event logs are the means of recording system generated events for later analysis. Events are messages generated by the system by applications or processes within the 7210 SAS.
The following figure shows a function block diagram of event logging.
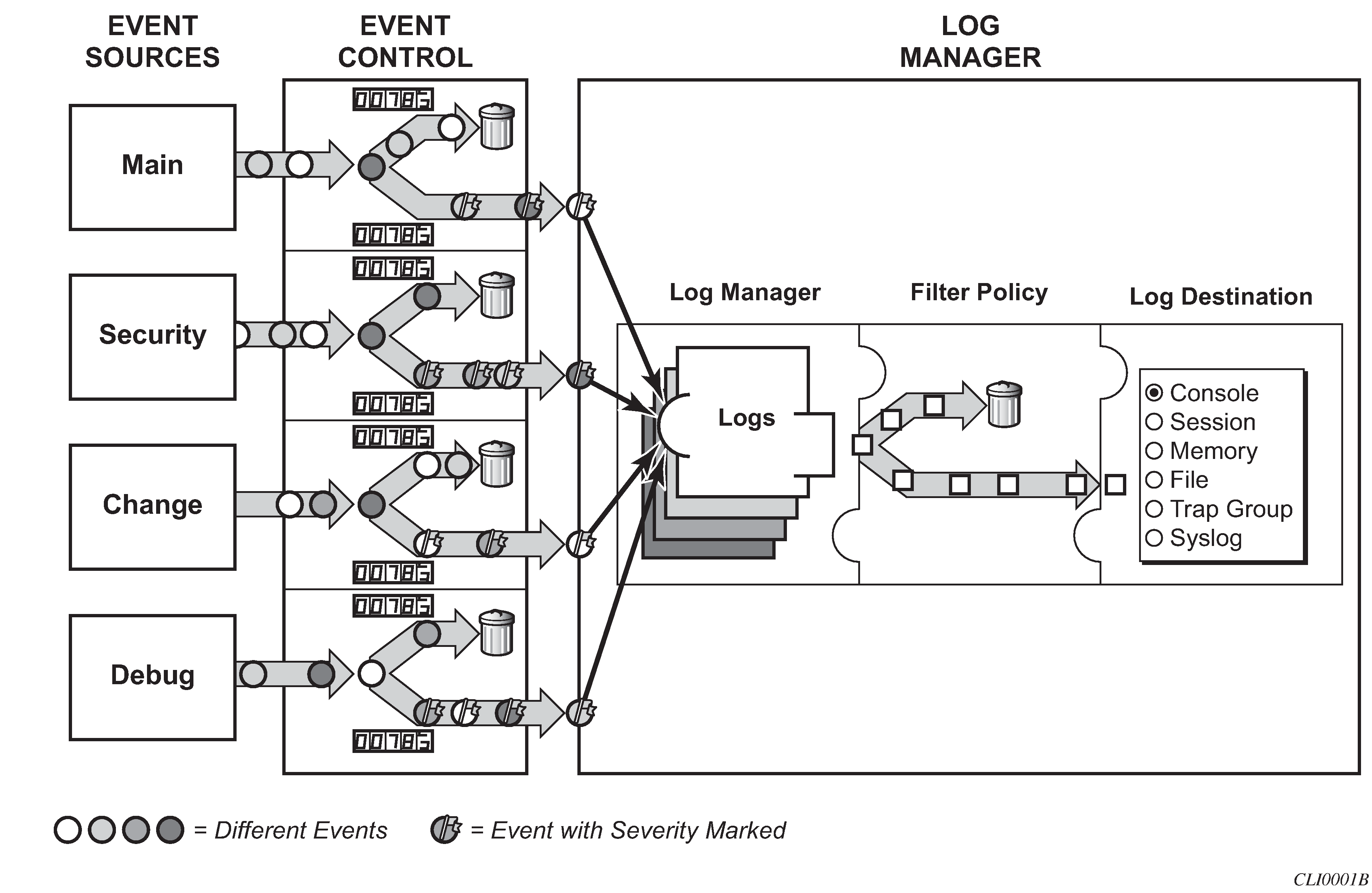
Event sources
In Event logging block diagram, the event sources are the main categories of events that feed the log manager:
security
The security event source is all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. Security events are generated by the SECURITY application and the authenticationFailure event in the SNMP application.
change
The change activity event source is all events that directly affect the configuration or operation of the node. Change events are generated by the USER application. The Change event stream also includes the tmnxConfigModify(#2006), tmnxConfigCreate (#2007), tmnxConfigDelete (#2008) and tmnxStateChange (#2009) change events from the SYSTEM application.
debug
The debug event source is the debugging configuration that has been enabled on the system. Debug events are generated by the DEBUG application.
main
The main event source receives events from all other applications within the 7210 SAS.
Examples of applications within 7210 SAS include IP, MPLS, OSPF, CLI, and services.
The following shows an example of the show log applications command output that displays all applications.
*A:ALU-7210# show log applications
==================================
Log Event Application Names
==================================
Application Name
----------------------------------
CHASSIS
DEBUG
DOT1AG
DOT1X
EFM_OAM
FILTER
IGMP
IP
LAG
LOGGER
MIRROR
NTP
OAM
PORT
QOS
SECURITY
SNMP
STP
SVCMGR
SYSTEM
TIP
TOD
USER
VRTR
==================================
Event control
Event control preprocesses the events generated by applications before the event is passed into the main event stream. Event control assigns a severity to application events and can either forward the event to the main event source or suppress the event. Suppressed events are counted in event control, but these events do not generate log entries because they never reach the log manager.
Simple event throttling is another method of event control and is configured similarly to the generation and suppression options. See Simple logger event throttling.
Events are assigned a default severity level in the system, but the application event severities can be changed by the user.
Application events contain an event number and description that describe why the event is generated. The event number is unique within an application, but the number can be duplicated in other applications.
The following example, generated by querying event control for application generated events, displays a partial list of event numbers and names.
router# show log event-control
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
CHASSIS:
2001 cardFailure MA gen 0 0
2002 cardInserted MI gen 2 0
2003 cardRemoved MI gen 0 0
2004 cardWrong MI gen 0 0
2005 EnvTemperatureTooHigh MA gen 0 0
2006 fanFailure CR gen 0 0
...
EFM_OAM:
2001 tmnxDot3OamPeerChanged MI gen 0 0
2002 tmnxDot3OamLoopDetected MI gen 0 0
2003 tmnxDot3OamLoopCleared MI gen 0 0
FILTER:
2001 tIPFilterPBRPacketsDrop WA gen 0 0
2002 tFilterEntryActivationFailed WA gen 0 0
2003 tFilterEntryActivationRestored WA gen 0 0
IGMP:
2001 vRtrIgmpIfRxQueryVerMismatch WA gen 0 0
2002 vRtrIgmpIfCModeRxQueryMismatch WA gen 0 0
2003 vRtrIgmpMaxGrpsLimitExceeded WA gen 0 0
2004 vRtrIgmpMcacPlcyDropped WA gen 0 0
IP:
L 2001 clearRTMError MI gen 0 0
L 2002 ipEtherBroadcast MI gen 0 0
L 2003 ipDuplicateAddress MI gen 0 0
L 2004 ipArpInfoOverwritten MI gen 0 0
L 2005 fibAddFailed MA gen 0 0
...
SYSTEM:
2001 stiDateAndTimeChanged WA gen 0 0
2002 ssiSaveConfigSucceeded MA gen 1 0
2003 ssiSaveConfigFailed CR gen 1 0
2004 sbiBootConfig MA gen 1 0
2005 sbiBootSnmpd MA gen 1 0
...
VRTR:
2001 tmnxVRtrMidRouteTCA MI gen 0 0
2002 tmnxVRtrHighRouteTCA MI gen 0 0
2003 tmnxVRtrHighRouteCleared MI gen 0 0
...
=======================================================================
router#
Log manager and event logs
Events that are forwarded by event control are sent to the log manager. The log manager manages the event logs in the system and the relationships between the log sources, event logs and log destinations, and log filter policies.
An event log has the following properties:
a unique log ID
the log ID is a short, numeric identifier for the event log (a maximum of ten logs can be configured at a time)
one or more log sources
the source stream or streams to be sent to log destinations can be specified. The source must be identified before the destination can be specified. The events can be from the main event stream, events in the security event stream, or events in the user activity stream
one event log destination
a log can only have a single destination (the destination for the log ID destination can be one of console, session, syslog, snmp-trap-group, memory, or a file on the local file system)
an optional event filter policy
an event filter policy defines whether to forward or drop an event or trap-based on match criteria
Event filter policies
The log manager uses event filter policies to allow fine control over which events are forwarded or dropped based on various criteria. Like other policies with the 7210 SAS, filter policies have a default action. The default actions are either:
Forward
Drop
Filter policies also include a number of filter policy entries that are identified with an entry ID and define specific match criteria and a forward or drop action for the match criteria.
Each entry contains a combination of matching criteria that define the application, event number, router, severity, and subject conditions. The entry’s action determines how the packets should be treated if they have met the match criteria.
Entries are evaluated in order from the lowest to the highest entry ID. The first matching event is subject to the forward or drop action for that entry.
Valid operators are listed in the following table.
Operator |
Description |
|---|---|
eq |
equal to |
neq |
not equal to |
lt |
less than |
lte |
less than or equal to |
gt |
greater than |
gte |
greater than or equal to |
A match criteria entry can include combinations of:
equal to or not equal to a specific system application
equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to an event number within the application
equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to a severity level
equal to or not equal to a router name string or regular expression match
equal to or not equal to an event subject string or regular expression match
Event log entries
Log entries that are forwarded to a destination are formatted in a way appropriate for the specific destination whether it be recorded to a file or sent as an SNMP trap, but log event entries have common elements or properties. All application generated events have the following properties:
a time stamp in UTC or local time
the generating application
a unique event ID within the application
a router name identifying the VRF-ID that generated the event
a subject identifying the affected object
a short text description
The general format for an event in an event log with either a memory, console or file destination is as follows.
nnnn YYYY/MM/DD HH:MM:SS.SS <severity>:<application> # <event_id> <router-
name> <subject> description
The following is an event log example:
475 2006/11/27 00:19:40.38 WARNING: SNMP #2007 Base 1/1/1
"interface 1/1/1 came up"
The specific elements that compose the general format are described in the following table.
Label |
Description |
|---|---|
nnnn |
The log entry sequence number. |
YYYY/MM/DD |
The UTC date stamp for the log entry. YYYY — year MM — month DD — date |
HH:MM:SS.SS |
The UTC time stamp for the event. HH — hours (24 hour format) MM — minutes SS.SS — seconds |
<severity> |
The severity level name of the event. CLEARED — a cleared event (severity number 1) INFO — an indeterminate/informational severity event (severity level 2) CRITICAL — a critical severity event (severity level 3) MAJOR — a major severity event (severity level 4) MINOR — a minor severity event (severity level 5) WARNING — a warning severity event (severity 6) |
<application> |
The application generating the log message. |
<event_id> |
The application’s event ID number for the event. |
<router> |
The router name representing the VRF-ID that generated the event. |
<subject> |
The subject/affected object for the event. |
<description> |
A text description of the event. |
Simple logger event throttling
Simple event throttling provides a mechanism to protect event receivers from being overloaded when a scenario causes many events to be generated in a very short period of time. A throttling rate, # events/# seconds, can be configured. Specific event types can be configured to be throttled. After the throttling event limit is exceeded in a throttling interval, any further events of that type cause the dropped events counter to be incremented. Dropped events counts are displayed by the show>log>event-control context. Events are dropped before being sent to one of the logger event collector tasks. There is no record of the details of the dropped events and therefore no way to retrieve event history data lost by this throttling method.
A specific event type can be generated by multiple managed objects within the system. At the point this throttling method is applied the logger application has no information about the managed object that generated the event and cannot distinguish between events generated by object ‟A” from events generated by object ‟B”. If the events have the same event-id, they are throttled regardless of the managed object that generated them. It also does not know which events may eventually be logged to destination log-id <n> from events that will be logged to destination log-id <m>.
Throttle rate applies commonly to all event types. It is not configurable for a specific event-type. A timer task checks for events dropped by throttling when the throttle interval expires. If any events have been dropped, a TIMETRA-SYSTEM-MIB::tmnxTrapDropped notification is sent.
Default system log
Log 99 is a preconfigured memory-based log that logs events from the main event source (not security, debug, and so on). Log 99 exists by default.
Log 99 configuration
ALA-1>config>log# info detail
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
...
snmp-trap-group 7
exit
...
log-id 99
description "Default system log"
no filter
from main
to memory 500
no shutdown
exit
----------------------------------------------
ALA-1>config>log#
Event handling system
The event handling system (EHS) tool is only supported on the 7210 SAS-Dxp.
The EHS tool allows operator-defined behavior to be configured on the router. EHS adds user-controlled programmatic handling by allowing the execution of a CLI script upon the detection of a log event (the "trigger"). Regular expression type of pattern matching is available for various fields in the log event to give flexibility in the trigger definition.
-
trigger events (typically log events that match some configurable criteria)
-
a set of actions to perform (typically one or more CLI scripts)
EHS makes use of the generic CLI script-control functions for scripts. Any command available in the CLI (with some limited exceptions, such as candidate commands) can be executed in a script as the result of an EHS handler being triggered. The following figure illustrates the relationships between the different configurable objects used by EHS.
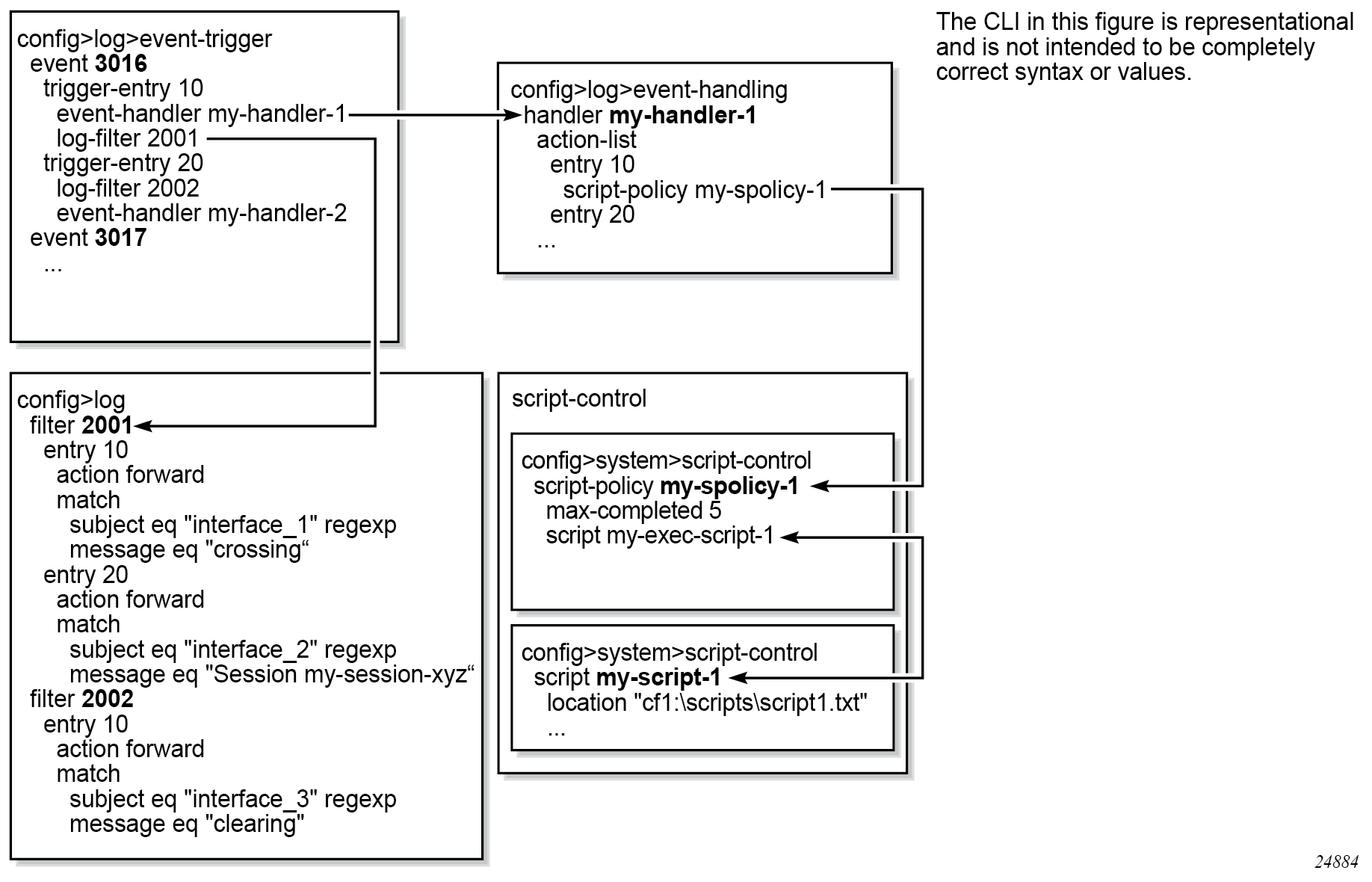
Complex rules can be configured to match on log events as a trigger for an EHS handler.
-
EHS does not trigger on log events that are suppressed through config>log>event-control
-
EHS does not trigger on log events that are throttled by the logger
EHS triggers on log events that are dropped by user-configured log filters assigned to individual logs (config>log>filter). The EHS event trigger logic occurs before the distribution of log event streams into individual logs.
-
the common event parameters appid, name, eventid, severity, subject, and gentime
-
the predefined varbinds in a log event's message
- appid
- eventid
- severity
- subject
- gentime
- event_varbind_1
- event_varbind_2
- event_varbind_N
- The passed in event's gentime is always UTC.
- The event's sequence number is not passed in to the script.
An EHS script has the ability to define local static variables and use basic .if and .set commands in the script. The use of variables with the .if and .set commands within an EHS script adds more logic to EHS scripting and allows the reuse of a single EHS script for more than one trigger or action.
Both imported and local variables can be used within the EHS script, either as part of the CLI commands or as part of the .if or .set commands.
-
Using $X without using single or double quotes, replaces the variable X with its string or integer value.
-
Using “X” with double quotes, means the literal string X.
-
Using “$X” with double quotes, replaces the variable X with its string or integer value.
-
Using 'X' with single quotes, means the literal string X.
-
Using ‘$X’ with single quotes, does not replace the variable X with its value but means the literal string $X.
-
All characters enclosed within single quotes are interpreted as a string character.
-
All characters enclosed within double quotes are interpreted as regular characters except for $, which replaces the variable with its value (for example, shell expansion inside a string).
Supported shell command scenarios and examples
Some supported shell command scenarios are (the following are pseudo commands):
-
.if $string_variable==string_value_or_string_variable {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if ($string_variable==string_value_or_string_variable) {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if $integer_variable==integer_value_or_integer_variable {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if ($integer_variable==integer_value_or_integer_variable) {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if $string_variable!=string_value_or_string_variable {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if ($string_variable!=string_value_or_string_variable) {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if $integer_variable!=integer_value_or_integer_variable {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.if ($integer_variable!=integer_value_or_integer_variable) {
CLI_commands_set1
.} else {
CLI_commands_set2
.} endif
-
.set $string_variable = string_value_or_string_variable
-
.set ($string_variable = string_value_or_string_variable)
-
.set $integer_variable = integer_value_or_integer_variable
-
.set ($integer_variable = integer_value_or_integer_variable)
where:
-
CLI_commands_set1 is a set of one or more CLI commands
-
CLI_commands_set2 is a set of one or more CLI commands
-
string_variable is a local (static) string variable
-
string_value_or_string_variable is a string value/variable
-
integer_variable is a local (static) integer variable
-
integer_value_or_integer_variable is an integer value/variable
-
A limit of 100 local static variables per EHS script is imposed. Exceeding this limit may result in an error and partial execution of the script.
-
When a set statement is used to set a string_variable to a string_value, the string_value can be any non-integer value not enclosed in single or double quotes or it can be enclosed in single or double quotes.
-
A "." preceding a directive (for example, if, set, and so on) is always expected to start a new line.
-
An end of line is always expected after {.
-
A CLI command is always expected to start a new line.
-
Passed-in dynamic variables are always read-only inside an EHS script and cannot be overwritten using a set statement.
-
.if commands support == and != operators only.
-
.if and .set commands support addition, subtraction, multiplication, and division of integers.
-
.if and .set commands support addition, which means concatenation, of strings.
Valid examples:
-
configure service epipe $serviceID
where $serviceID is either a local static integer variable or passed-in (dynamic) integer variable
-
echo srcAddr is $srcAddr
where $srcAddr is a passed-in dynamic string variable
-
.set $ipAddr = "10.0.0.1"
where $ipAddr is a local static string variable
-
.set $ipAddr = $srcAddr
where $srcAddr is a passed-in dynamic string variable
$ipAddr is a local static string variable.
-
.set ($customerID = 50)
where $customerID is a local static integer variable
-
.set ($totalPackets = $numIngrPackets + $numEgrPackets)
where $totalPackets, $numIngrPackets, $numEgrPackets are local (static) integer variables
-
.set ($portDescription = $portName + $portLocation)
where $portDescription, $portName, $portLocation are local (static) string variables
-
if ($srcAddr == "CONSOLE") {
CLI_commands_set1
.else {
CLI_commands_set2
.} endif
where $srcAddr is a passed-in dynamic string variable
CLI_commands_set1 is a set of one or more CLI commands
CLI_commands_set2 is a set of one or more CLI commands
-
.if ($customerId == 10) {
CLI_commands_set1
.else {
CLI_commands_set2
.} endif
where $customerID is a passed-in dynamic integer variable CLI_commands_set1 is a set of one or more CLI commands
CLI_commands_set2 is a set of one or more CLI commands
-
.if ($numIngrPackets == $numEgrPackets) {
CLI_commands_set1
.else {
CLI_commands_set2
.} endif
where $numIngrPackets and $numEgrPackets are local static integer variables
CLI_commands_set1 is a set of one or more CLI commands
CLI_commands_set2 is a set of one or more CLI commands
Invalid examples:
-
.set $srcAddr = "10.0.0.1"
where $srcAddr is a passed-in dynamic string variable
Reason: passed-in variables are read only inside an EHS script.
-
.set ($ipAddr = $numIngrPackets + $numEgrPackets)
where $ipAddr is a local (static) string variable
$numIngrPackets and $numEgrPackets are local static integer variables
Reason: variable types do not match, cannot assign a string to an integer.
-
.set ($numIngrPackets = $ipAddr + $numEgrPackets)
where $ipAddr is a local static string variable
$numIngrPackets and $numEgrPackets are local static integer variables
Reason: variable types do not match, cannot concatenate a string to an integer.
-
.set $ipAddr = "10.0.0.1"100
where $ipAddr is a local static string variable
Reason: when double quotes are used, they have to surround the entire string.
-
.if ($totalPackets == "10.1.1.1") {
.} endif
where $totalPackets is a local static integer variables
Reason: cannot compare an integer variable to a string value.
-
.if ($ipAddr == 10) {
.} endif
where $ipAddr is a local static string variable
Reason: cannot compare a string variable to an integer value.
-
.if ($totalPackets == $ipAddr) {
where $totalPackets is a local static integer variables
$ipAddr is a local static string variable
Reason: cannot compare an integer variable to a string variable.
EHS support on 7210 SAS
On the 7210 SAS, EHS script triggers are limited to these dot1x events. They cannot be used with any other events though it is not blocked in the software.
-
tmnxPortDot1xAuthSuccess - triggered upon successful authentication of user/device using dot1x RADIUS authentication
-
tmnxPortDot1xAuthLost - triggered upon loss of authentication, either because the device disconnected or the device sent an EAP-Logoff message, or because of subsequent unsuccessful authentication when reauthentication is attempted
-
tmnxPortDot1xAuthLostGRvC - triggered when the RADIUS server returns an authentication failure and there is no response from the RADIUS server, or if dot1x authentication is enabled on a port but no EAPOL packets are received from the connected device
-
tmnxPortDot1xAuthLostGRvD - triggered when the previously created SAP in the guest or restricted VLAN service must be deleted because of the successful reauthentication of the connected device, device disconnection, or the device sends an EAP-Logoff message
Users can configure an EHS script to associate an authenticated port or MAC with a service and SAP that is provisioned based on the VLAN-ID provided by the RADIUS server upon a successful authentication. The software invokes the EHS script when the tmnxPortDot1xAuthSuccess event is triggered.
Users can also configure an EHS script to associate the port or MAC with a service and SAP that is provisioned using the config>port>ethernet>dot1x>guest-service service-id [vlan-id vlan-id] and config>port>ethernet>dot1x>restricted-service service-id [vlan-id vlan-id] commands. The software invokes the EHS script when the tmnxPortDot1xAuthLostGRvC event is triggered so that the corresponding port or MAC can be associated with a guest or restricted VLAN service.
EHS script configuration for a SAP in a service
- SAP creation and association with the VPLS service when the dot1x event tmnxPortDot1xAuthSuccess is generated
- SAP deletion after it is shut down when the dot1x event tmnxPortDot1xAuthLost is generated
The VLAN ID returned by the RADIUS server is used as the service-delimiting VLAN tag of the newly created SAP, and also used to identify the VPLS service ID. See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Services Guide for configuration guidelines of a VLAN ID returned by the RADIUS server.
exit all
.if $eventid == 3016 (tmnxPortDot1xAuthSuccess) {
echo $tmnxPortNotifyPortId
echo $tmnxPortDot1xVlanId
.set ($sapStr = $tmnxPortNotifyPortId + ":" + "$tmnxPortDot1xVlanId")
/configure service vpls $tmnxPortDot1xVlanId sap $sapStr create
exit all
.} endif
.if $eventid == 3017 (tmnxPortDot1xAuthLost) {
exit all
echo $tmnxPortNotifyPortId
echo $tmnxPortDot1xVlanId
.set ($sapStr = $tmnxPortNotifyPortId + ":" + "$tmnxPortDot1xVlanId")
/configure service vpls $tmnxPortDot1xVlanId sap $sapStr shutdown
/configure service vpls $tmnxPortDot1xVlanId no sap $sapStr
exit all
.} endif
Node configuration for an EHS script
The dot1x configuration per port is not displayed in the following example.
system
script-control
script <script-name>
location <ehs-script-path>
no shutdown
exit
script-policy <script-policy-name>
results <resuls-path>
script <script-name>
no shutdown
exit
exit
exit
log
filter 11
default-action drop
entry 11
action forward
exit
exit
event-handling
handler <handler-name>
action-list
entry 11
script-policy <script-policy-name> ==> created under system ==> script-control
no shutdown
exit
exit
no shutdown
exit
exit
event-trigger
event "port" 3016
trigger-entry 1
event-handler <handler-name>
log-filter 11
no shutdown
exit
no shutdown
exit
event "port" 3017
trigger-entry 1
event-handler <handler-name>
log-filter 11
no shutdown
exit
no shutdown
exit
exit
exit
Restricted and guest VLAN configuration
The following provides an example of an EHS script used for SAP creation and deletion in a guest or restricted VLAN service.
.if $eventid == 3018 (tmnxPortDot1xAuthLostGRvC){
echo $name
echo $tmnxPortNotifyPortId
echo $tmnxPortDot1xVlanId
echo $tmnxPortDot1xGRSvcId
.set ($sapStr = $tmnxPortNotifyPortId + ":" + "$tmnxPortDot1xVlanId")
echo $sapStr
.if $tmnxPortDot1xGRSvcId == 1 {
/configure service vpls $tmnxPortDot1xGRSvcId sap $sapStr create
/configure service vpls $tmnxPortDot1xGRSvcId sap $sapStr no shutdown
exit all
.} endif
.if $tmnxPortDot1xGRSvcId == 2 {
/configure service epipe $tmnxPortDot1xGRSvcId sap $sapStr create
/configure service epipe $tmnxPortDot1xGRSvcId sap $sapStr no shutdown
exit all
.} endif
.} endif
.if $eventid == 3019 (tmnxPortDot1xAuthLostGRvD){
echo $name
.set ($sapStr = $tmnxPortNotifyPortId + ":" + "$tmnxPortDot1xVlanId")
.if $tmnxPortDot1xGRSvcId == 1 {
/configure service vpls $tmnxPortDot1xGRSvcId sap $sapStr shutdown
/configure service vpls $tmnxPortDot1xGRSvcId no sap $sapStr
.} endif
.if $tmnxPortDot1xGRSvcId == 2 {
/configure service epipe $tmnxPortDot1xGRSvcId sap $sapStr shutdown
/configure service epipe $tmnxPortDot1xGRSvcId no sap $sapStr
.} endif
.} endifAccounting logs
Before an accounting policy can be created, a target log file must be created to collect the accounting records. The files are stored in system memory on compact flash (cf1:) in a compressed (tar) XML format and can be retrieved using FTP or SCP.
A file ID can only be assigned to either one event log ID or one accounting log.
Accounting records
An accounting policy must define a record name and collection interval. Only one record name can be configured per accounting policy. Also, a record name can only be used in one accounting policy.
When creating accounting policies, one service accounting policy and one network accounting policy can be defined as default. If statistics collection is enabled on a SAP, access-uplink, or network port and no accounting policy is applied, then the respective default policy is used. If no default policy is defined, then no statistics are collected unless a specifically defined accounting policy is applied.
The record name, sub-record types, and default collection period for service and network accounting policies are listed in Accounting record names and collection periods for 7210 SAS-D, Accounting record names and collection periods for 7210 SAS-Dxp, Accounting record names and collection periods for 7210 SAS-K 2F1C2T , Accounting record names and collection periods for 7210 SAS-K 2F6C4T, and Accounting record names and collection periods for 7210 SAS-K 3SFP+ 8C.
Accounting record names and collection periods
Record name |
Sub-record types |
Accounting object |
Default collection period (minutes) |
|---|---|---|---|
service-ingress-octets |
sio |
Access SAP |
5 |
service-egress-octets |
seo |
Access SAP |
5 |
service-ingress-packets |
sip |
Access SAP |
5 |
service-egress-packets |
sep |
Access SAP |
5 |
combined-service-ingress |
sip, sio |
Access SAP |
5 |
combined-service-egress |
seo, sep |
Access SAP |
5 |
complete-service-ingress-egress |
sip, sio, seo, sep |
Access SAP |
5 |
access-egress-packets |
aep |
Access-port |
5 |
access-egress-octets |
aeo |
Access-port |
5 |
combined-access-egress |
cmAeo, cmAep |
Access-port |
5 |
network-ingress-octets |
nio |
Access-uplink-port |
15 |
network-ingress-packets |
nip |
Access-uplink-port |
15 |
network-egress-octets |
neo |
Access-uplink-port |
15 |
network-egress-packets |
neo |
Access-uplink-port |
15 |
combined-network-egress |
cmNeo, cmNep |
Access-uplink-port |
15 |
combined-network-ingress-egress-octets |
cmNio, cmNeo |
Access-uplink-port |
15 |
saa |
5 |
Record name |
Sub-record types |
Accounting object |
Default collection period (minutes) |
|---|---|---|---|
service-ingress-octets |
sio |
Access SAP |
5 |
service-egress-octets |
seo |
Access SAP |
5 |
service-ingress-packets |
sip |
Access SAP |
5 |
service-egress-packets |
sep |
Access SAP |
5 |
combined-service-ingress |
sip, sio |
Access SAP |
5 |
combined-service-egress |
seo, sep |
Access SAP |
5 |
complete-service-ingress-egress |
sip, sio, seo, sep |
Access SAP |
5 |
access-egress-packets |
aep |
Access-port |
5 |
access-egress-octets |
aeo |
Access-port |
5 |
combined-access-egress |
cmAeo, cmAep |
Access-port |
5 |
network-ingress-octets |
nio |
Access-uplink-port |
15 |
network-ingress-packets |
nip |
Access-uplink-port |
15 |
network-egress-octets |
neo |
Access-uplink-port |
15 |
network-egress-packets |
nep |
Access-uplink-port |
15 |
combined-network-egress |
cmNeo, cmNep |
Access-uplink-port |
15 |
combined-network-ingress-egress-octets |
cmNio, cmNeo |
Access-uplink-port |
15 |
saa |
5 |
||
complete-pm |
5 |
Record name |
Sub-record types |
Accounting object |
Default collection period (minutes) |
|---|---|---|---|
service-ingress-octets |
sio |
Access SAP |
5 |
service-egress-octets |
seo |
Access SAP |
5 |
service-ingress-packets |
sip |
Access SAP |
5 |
service-egress-packets |
sep |
Access SAP |
5 |
combined-service-ingress |
sip, sio |
Access SAP |
5 |
combined-service-egress |
seo, sep |
Access SAP |
5 |
complete-service-ingress-egress |
sip, sio, seo, sep |
Access SAP |
5 |
network-ingress-octets |
nio |
Access-uplink-port |
15 |
network-ingress-packets |
nip |
Access-uplink-port |
15 |
network-egress-octets |
neo |
Access-uplink-port |
15 |
network-egress-packets |
neo |
Access-uplink-port |
15 |
combined-network-egress |
cmNeo, cmNep |
Access-uplink-port |
15 |
combined-network-ingress-egress-octets |
cmNio, cmNeo |
Access-uplink-port |
15 |
saa |
5 |
||
y1564 |
5 |
||
complete-pm |
5 |
Record name |
Sub-record types |
Accounting object |
Default collection period (minutes) |
|---|---|---|---|
service-ingress-octets |
sio |
Access SAP |
5 |
service-egress-octets |
seo |
Access SAP |
5 |
service-ingress-packets |
sip |
Access SAP |
5 |
service-egress-packets |
sep |
Access SAP |
5 |
combined-service-ingress |
sip, sio |
Access SAP |
5 |
combined-service-egress |
seo, sep |
Access SAP |
5 |
complete-service-ingress-egress |
sip, sio, seo, sep |
Access SAP |
5 |
combined-access-egress |
cmAeo, cmAep |
Access-port |
5 |
network-ingress-octets |
nio |
Access-uplink-port and Network port |
15 |
network-ingress-packets |
nip |
Access-uplink-port and Network port |
15 |
network-egress-octets |
neo |
Access-uplink-port and Network port |
15 |
network-egress-packets |
neo |
Access-uplink-port and Network port |
15 |
combined-network-egress |
cmNeo, cmNep |
Access-uplink-port and Network port |
15 |
combined-network-ingress-egress-octets |
cmNio, cmNeo |
Access-uplink-port and Network port |
15 |
saa |
5 |
||
y1564 |
5 |
||
complete-pm |
5 |
Record name |
Sub-record types |
Accounting object |
Default collection period (minutes) |
|---|---|---|---|
service-ingress-octets |
sio |
Access SAP |
5 |
service-egress-octets |
seo |
Access SAP |
5 |
service-ingress-packets |
sip |
Access SAP |
5 |
service-egress-packets |
sep |
Access SAP |
5 |
combined-service-ingress |
sip, sio |
Access SAP |
5 |
combined-service-egress |
seo, sep |
Access SAP |
5 |
complete-service-ingress-egress |
sip, sio, seo, sep |
Access SAP |
5 |
combined-access-egress |
cmAeo, cmAep |
Access-port |
5 |
network-ingress-octets |
nio |
Access-uplink-port and Network port |
15 |
network-ingress-packets |
nip |
Access-uplink-port and Network port |
15 |
network-egress-octets |
neo |
Access-uplink-port and Network port |
15 |
network-egress-packets |
neo |
Access-uplink-port and Network port |
15 |
combined-network-egress |
cmNeo, cmNep |
Access-uplink-port and Network port |
15 |
combined-network-ingress-egress-octets |
cmNio, cmNeo |
Access-uplink-port and Network port |
15 |
saa |
5 |
||
y1564 |
5 |
||
complete-pm |
5 |
Accounting record details
Each accounting record name is composed of one or more sub-records, which are in turn composed of multiple fields.
See Appendix: accounting record name details for 7210 SAS platforms for more information about accounting records and statistics for the 7210 SAS platforms.
Configuration guidelines
The following information describes configuration guidelines:
On the 7210 SAS-D and 7210 SAS-Dxp, the ingress SAP counter counts both octets and packets simultaneously.
On the 7210 SAS-D, the egress SAP counter is disabled by default.
Ensure that egress SAP counters are enabled on 7210 SAS-D devices before associating accounting records of type service-egress-octets, service-egress-packets, combined-service-egress and complete-service-ingress-egress.
Before modifying the counter mode, disable account log generation. Execute the no collect-stats command. Changing the mode of the counter results in loss of previously collected counts and resets the counter.
Egress SAP statistics are not available on any of the SAPs of a port on which a dot1q SAP and dot1q default SAP configuration are present at the same time.
On the 7210 SAS-D and 7210 SAS-Dxp for VLL and VPLS services, the counter-mode of counters associated with SAP ingress meters/policers can be changed by executing the following command:
For 7210 SAS-D and 7210 SAS-Dxp devices — config>service>epipe/vpls>sap>statistics>ingress>counter-mode {in-out-profile-count | forward-drop-count}
For more information about the counter-mode command, See the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Services Guide.
The statistics collected for the following accounting records vary based on the counter-mode selected:
Service-ingress-octets
Service-ingress-packets
Combined-service-ingress
Complete-service-ingress-egress
Reporting and time-based accounting
Node support for volume and time-based accounting concept provides an extra level of intelligence at the network element level to provide service models such as ‟prepaid access” in a scalable manner. This means that the network element gathers and stores per-subscriber accounting information and compare it with predefined quotas. After a quota is exceeded, the predefined action (such as redirection to a web portal or disconnect) is applied.
Configuration notes
This following information describes logging configuration restrictions:
A file or filter cannot be deleted if it has been applied to a log.
File IDs, syslog IDs, or SNMP trap groups must be configured before they can be applied to a log ID.
A file ID can only be assigned to either one log ID or one accounting policy.
Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
The snmp-trap-id must be the same as the log-id.
Configuring logging with CLI
This section provides information to configure logging using the command line interface.
Log configuration overview
Configure logging parameters to save information in a log file or direct the messages to other devices. Logging does the following:
provides you with logging information for monitoring and troubleshooting
allows you to select the types of logging information to be recorded
allows you to assign a severity to the log messages
allows you to select the source and target of logging information
Log types
Logs can be configured in the following contexts:
Log file
Log files can contain log event message streams or accounting/billing information. Log file IDs are used to direct events, alarms/traps and debug information to their respective targets.
SNMP trap groups
SNMP trap groups contain an IP address and community names which identify targets to send traps following specified events.
Syslog
Information can be sent to a syslog host that is capable of receiving selected syslog messages from a network element.
Event control
Configures a particular event or all events associated with an application to be generated or suppressed.
Event filters
An event filter defines whether to forward or drop an event or trap based on match criteria.
Accounting policies
An accounting policy defines the accounting records that will be created. Accounting policies can be applied to one or more service access points (SAPs), access-uplink (network) ports, and access ports.
Event logs
An event log defines the types of events to be delivered to its associated destination.
Event throttling rate
Defines the rate of throttling events.
Basic event log configuration
The most basic log configuration must have the following:
log ID or accounting policy ID
a log source
a log destination
Log configuration
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
event-control 2001 generate critical
file-id 1
description "This is a test file-id."
location cf1:
exit
file-id 2
description "This is a test log."
location cf1:
exit
snmp-trap-group 7
trap-target 11.22.33.44 "snmpv2c" notify-community "public"
exit
log-id 2
from main
to file 2
exit
----------------------------------------------
A:ALA-12>config>log#Common configuration tasks
The following sections describe basic system tasks that must be performed.
Configuring an event log
A event log file contains information used to direct events, alarms, traps, and debug information to their respective destinations. One or more event sources can be specified. File IDs, SNMP trap groups, or syslog IDs must be configured before they can be applied to an event log ID.
Use the following CLI syntax to configure a log file:
config>log
log-id log-id
description description-string
filter filter-id
from {[main] [security] [change] [debug-trace]}
to console
to file file-id
to memory [size]
to session
to snmp [size]
to syslog syslog-id}
time-format {local|utc}
no shutdownLog file configuration
ALA-12>config>log>log-id# info
----------------------------------------------
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
ALA-12>config>log>log-id#
Configuring a file ID
To create a log file, a file ID is defined, the target CF or USB drive is specified, and the rollover retention interval period for the log file is defined. The rollover interval is defined in minutes and determines how long a file is used before it is closed and a new log file is created. The retention interval determines how long the file is stored on the storage device before it is deleted.
Use the following CLI syntax to configure a log file:
config>log
file-id log-file-id
description description-string
location cflash-id
rollover minutes [retention hours]log file configuration
A:ALA-12>config>log# info
------------------------------------------
file-id 1
description "This is a log file."
location cf1:
rollover 600 retention 24
exit
----------------------------------------------
A:ALA-12>config>log#Configuring an accounting policy
Before an accounting policy can be created a target log file must be created to collect the accounting records. The files are stored in system memory of compact flash (cf1:) in a compressed (tar) XML format and can be retrieved using FTP or SCP. See Configuring an event log and Configuring a file ID.
Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
The default accounting policy statement cannot be applied to LDP nor RSVP statistics collection records.
An accounting policy must define a record type and collection interval. Only one record type can be configured per accounting policy.
policy can be defined as default. If statistics collection is enabled on an accounting object, and no accounting policy is applied, then the respective default accounting policy is used. If no default policy is defined, then no statistics are collected unless a specifically-defined accounting policy is applied.
Use the following CLI syntax to configure an accounting policy:
config>log>
accounting-policy acct-policy-id interval minutes
description description-string
default
record record-name
to file log-file-id
no shutdownAccounting policy configuration
A:ALA-12>config>log# info
----------------------------------------------
accounting-policy 5
description "This is a test accounting policy."
record service-ingress-packets
to file 3
exit
----------------------------------------------
A:ALA-12>config>log#
Configuring event control
Use the following CLI syntax to configure event control. Note that the throttle parameter used in the event-control command syntax enables throttling for a specific event type. The config>log>throttle-rate command configures the number of events and interval length to be applied to all event types that have throttling enabled by this event-control command.
config>log
event-control application-id [event-name|event-number] generate [severity-level] [throttle]
event-control application-id [event-name|event-number] suppress
throttle-rate events [interval seconds]Event control configuration
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration"
#------------------------------------------
throttle-rate 500 interval 10
event-control "oam" 2001 generate throttle
event-control "ospf" 2001 suppress
event-control "ospf" 2003 generate cleared
event-control "ospf" 2014 generate critical
..
----------------------------------------------
A:ALA-12>config>log>filter#
Configuring throttle rate
This command configures the number of events and interval length to be applied to all event types that have throttling enabled by the event-control command.
Use the following CLI syntax to configure the throttle rate.
config>log#
throttle-rate events [interval seconds]
Throttle rate configuration
*A:gal171>config>log# info
---------------------------------------------
throttle-rate 500 interval 10
event-control "aps" 2001 generate throttle
----------------------------------------------
Configuring a log filter
Use the following CLI syntax to configure a log filter:
config>log
filter filter-id
default-action {drop|forward}
description description-string
entry entry-id
action {drop|forward}
description description-string
match
application {eq|neq} application-id
number {eq|neq|lt|lte|gt|gte} event-id
router {eq|neq} router-instance [regexp]
severity {eq|neq|lt|lte|gt|gte} severity-level
subject {eq|neq} subject [regexp]
Log filter configuration
A:ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
file-id 1
description "This is our log file."
location cf1:
rollover 600 retention 24
exit
filter 1
default-action drop
description "This is a sample filter."
entry 1
action forward
match
application eq "mirror"
severity eq critical
exit
exit
exit
...
log-id 2
shutdown
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
------------------------------------------
Configuring an SNMP trap group
The associated log-id does not have to configured before a snmp-trap-group can be created, however, the snmp-trap-group must exist before the log-id can be configured to use it.
Use the following CLI syntax to configure an SNMP trap group:
config>log
snmp-trap-group log-id
trap-target name [address ip-address] [port port] [snmpv1|snmpv2c| snmpv3] notify-community communityName |snmpv3SecurityName [security-level {no-auth-no-privacy|auth-no-privacy|privacy}]
Basic SNMP trap group configuration
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 2
trap-target 10.10.10.104:5 "snmpv3" notify-community "coummunitystring"
exit
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Configuring SNMP dying gasp
Use the following CLI syntax to configure SNMP dying gasp:
config>log
no snmp-dying-gasp primary <trap-target-group-num> < trap-target-name> [secondary {<trap-target-group-num><trap-target-name>} [tertiary {<trap-target-group-num> <trap-target- name>}]]
SNMP dying gasp configuration
*A:Dut-A>config>log# snmp-dying-gasp primary 7 server1 secondary 8 server2
*A:Dut-A>config>log# info
----------------------------------------------
snmp-trap-group 7
trap-target "server1" address 10.1.1.1 snmpv2c notify-community "public"
exit
snmp-trap-group 8
trap-target "server2" address 10.135.2.10 snmpv3 notify
community "snmpv3user" security-level auth-no-privacy
exit
snmp-trap-group 9
trap-target "server3" address 10.2.2.2 snmpv3 notify
community "snmpv3user" security-level auth-no-privacy
exit
log-id 7
from main
to snmp
exit
log-id 8
from main
to snmp
exit
log-id 9
from main
to snmp
exit
snmp-dying-gasp primary 7 "server1" secondary 8 "server2"
----------------------------------------------
*A:Dut-A>config>log# Configuration guidelines for SNMP dying gasp trap
The system does not try to resolve the ARP when it needs to send out the SNMP dying-gasp trap, because the amount of time available during power loss event is very less. Instead, the system assumes that ARP entry to the gateway used to reach the SNMP trap server is always available. It is recommended that user run a periodic ping query to the SNMP trap server in the background using the cron utility.
The following is an example configuration of a cron job that initiates a ping to the server mentioned in the pingscript file every one minute.
*7210-SAS># configure cron
*7210-SAS >config>cron# info
----------------------------------------------
time-range "NO-TIME-RANGE" create
description "NO-TIME-RANGE is the default always-on time-range"
exit
----------------------------------------------
7210SAS>config>cron#
Configuring a syslog target
Log events cannot be sent to a syslog target host until a valid syslog ID exists.
Use the following CLI syntax to configure a syslog file:
config>log
syslog syslog-id
description description-string
address ip-address
log-prefix log-prefix-string
port port
level {emergency|alert|critical|error|warning|notice|info|debug}
facility syslog-facilitySyslog configuration
A:ALA-12>config>log# info
----------------------------------------------
...
syslog 1
description "This is a syslog file."
address 10.10.10.104
facility user
level warning
exit
...
----------------------------------------------
A:ALA-12>config>log#
Log management tasks
This section discusses the logging management tasks.
Modifying a log file
Use the following CLI syntax to modify a log file:
config>log
log-id log-id
description description-string
filter filter-id
from {[main] [security] [change] [debug-trace]}
to console
to file file-id
to memory [size]
to session
to snmp [size]
to syslog syslog-id
Current log configuration
ALA-12>config>log>log-id# info
----------------------------------------------
...
log-id 2
description "This is a test log file."
filter 1
from main security
to file 1
exit
...
----------------------------------------------
ALA-12>config>log>log-id#
Modifying log file parameters
config# log
config>log# log-id 2
config>log>log-id# description "Chassis log file."
config>log>log-id# filter 2
config>log>log-id# from security
config>log>log-id# exit
Modified log file configuration
A:ALA-12>config>log# info
----------------------------------------------
...
log-id 2
description "Chassis log file."
filter 2
from security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a log file
The log ID must be shut down before it can be deleted. In a previous example, file 1 is associated with log-id 2.
A:ALA-12>config>log# info
----------------------------------------------
file-id 1
description "LocationTest."
location cf1:
rollover 600 retention 24
exit
...
log-id 2
description "Chassis log file."
filter 2
from security
to file 1
exit
...
----------------------------------------------
A:ALA-12>config>log#
Use the following CLI syntax to delete a log file.
config>log
no log-id log-id
shutdown
The following shows an example to delete a log file.
config# log
config>log# log-id 2
config>log>log-id# shutdown
config>log>log-id# exit
config>log# no log-id 2
Modifying a file ID
When the file-id location parameter is modified, log files are not written to the new location until a rollover occurs or the log is manually cleared. A rollover can be forced by using the clear>log command. Subsequent log entries are then written to the new location. If a rollover does not occur or the log not cleared, the old location remains in effect.
The location can be CF (cflash-id) or USB (usb-flash-id).
Use the following CLI syntax to modify a log file ID:
config>log
file-id log-file-id
description description-string
location [cflash-id]
rollover minutes [retention hours]
The following displays the current log configuration.
A:ALA-12>config>log# info
------------------------------------------
file-id 1
description "This is a log file."
location cf1:
rollover 600 retention 24
exit
----------------------------------------------
A:ALA-12>config>log#
The following displays an example to modify log file parameters.
config# log
config>log# file-id 1
config>log>file-id# description "LocationTest."
config>log>file-id# rollover 2880 retention 500
config>log>file-id# exit
The following displays the file modifications.
A:ALA-12>config>log# info
----------------------------------------------
...
file-id 1
description "LocationTest."
location cf1:
rollover 2880 retention 500
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a file ID
All references to the file ID must be deleted before the file ID can be removed.
Use the following CLI syntax to delete a file ID:
config>log
no file-id log-file-id
Deleting a file ID
config>log# no file-id 1
Modifying a syslog ID
All references to the syslog ID must be deleted before the syslog ID can be removed.
Use the following CLI syntax to modify a syslog ID parameters:
config>log
syslog syslog-id
description description-string
address ip-address
log-prefix log-prefix-string
port port
level {emergency|alert|critical|error|warning|notice|info|debug}
facility syslog-facilitySyslog ID modifications
config# log
config>log# syslog 1
config>log>syslog$ description "Test syslog."
config>log>syslog# address 10.10.0.91
config>log>syslog# facility mail
config>log>syslog# level info
Syslog configuration
A:ALA-12>config>log# info
----------------------------------------------
...
syslog 1
description "Test syslog."
address 10.10.10.91
facility mail
level info
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a syslog
Use the following CLI syntax to delete a syslog file:
config>log
no syslog syslog-id
Deleting a syslog ID
config# log
config>log# no syslog 1
Modifying an SNMP trap group
Use the following CLI syntax to modify an SNMP trap group:
config>log
snmp-trap-group log-id
trap-target name [address ip-address] [port port] [snmpv1|snmpv2c| snmpv3] notify-community communityName |snmpv3SecurityName [security-level {no-auth-no-privacy|auth-no-privacy|privacy}]
Current SNMP trap group configuration
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.10.104:5 "snmpv3" notify-community "coummunitystring"
exit
...
----------------------------------------------
A:ALA-12>config>log#
Command usage to modify an SNMP trap group
config# log
config>log# snmp-trap-group 10
config>log>snmp-trap-group# no trap-target 10.10.10.104:5
config>log>snmp-trap-group# snmp-trap-group# trap-target 10.10.0.91:1 snmpv2c notify-community "com1"
SNMP trap group configuration
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.0.91:1 "snmpv2c" notify-community "com1”
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting an SNMP trap group
Use the following CLI syntax to delete a trap target and SNMP trap group:
config>log
no snmp-trap-group log-id
no trap-target name
SNMP trap group configuration
A:ALA-12>config>log# info
----------------------------------------------
...
snmp-trap-group 10
trap-target 10.10.0.91:1 "snmpv2c" notify-community "com1"
exit
...
----------------------------------------------
A:ALA-12>config>log#
Deleting a trap target and an SNMP trap group
— config>log# snmp-trap-group 10
— config>log>snmp-trap-group# no trap-target 10.10.0.91:1
— config>log>snmp-trap-group# exit
— config>log# no snmp-trap-group 10
Modifying a log filter
Use the following CLI syntax to modify a log filter:
config>log
filter filter-id
default-action {drop|forward}
description description-string
entry entry-id
action {drop|forward}
description description-string
match
application {eq|neq} application-id
number {eq|neq|lt|lte|gt|gte} event-id
router {eq|neq} router-instance [regexp]
severity {eq|neq|lt|lte|gt|gte} severity-level
subject {eq|neq} subject [regexp]
Current log filter configuration
ALA-12>config>log# info
#------------------------------------------
echo "Log Configuration "
#------------------------------------------
...
filter 1
default-action drop
description "This is a sample filter."
entry 1
action forward
match
application eq "mirror"
severity eq critical
exit
exit
exit
...
------------------------------------------
ALA-12>config>log#
Log filter modifications
config# log
config>log# filter 1
config>log>filter# description "This allows <n>."
config>log>filter# default-action forward
config>log>filter# entry 1
config>log>filter>entry$ action drop
config>log>filter>entry# match
config>log>filter>entry>match# application eq user
config>log>filter>entry>match# number eq 2001
config>log>filter>entry>match# no severity
config>log>filter>entry>match# exit
Log filter configuration
A:ALA-12>config>log>filter# info
----------------------------------------
...
filter 1
description "This allows <n>."
entry 1
action drop
match
application eq "user"
number eq 2001
exit
exit
exit
...
----------------------------------------
A:ALA-12>config>log>filter#
Deleting a log filter
Use the following CLI syntax to delete a log filter:
config>log
no filter filter-id
Current log filter configuration
A:ALA-12>config>log>filter# info
----------------------------------------
...
filter 1
description "This allows <n>."
entry 1
action drop
match
application eq "user"
number eq 2001
exit
exit
exit
...
----------------------------------------
A:ALA-12>config>log>filter#
Command usage to delete a log filter
— config>log# no filter 1
Modifying event control parameters
Use the following CLI syntax to modify event control parameters:
config>log
event-control application-id [event-name|event-number] generate[severity-level] [throttle]
event-control application-id [event-name|event-number] suppress
Current event control configuration
A:ALA-12>config>log# info
----------------------------------------------
...
event-control 2014 generate critical
...
----------------------------------------------
A:ALA-12>config>log#
Event control modification
config# log
config>log# event-control 2014 suppress
Log filter configuration
A:ALA-12>config>log# info
----------------------------------------------
...
event-control 2014 suppress
...
----------------------------------------------
A:ALA-12>config>log#
Returning to the default event control configuration
The no form of the event-control command returns modified values back to the default values.
Use the following CLI syntax to modify event control parameters:
config>log
no event-control application [event-name |event-nunmber]
Command usage to return to the default values
config# log
config>log# no event-control 2001
config>log# no event-control 2002
config>log# no event-control 2014
A:ALA-12>config>log# info detail
----------------------------------------------
#------------------------------------------
echo "Log Configuration"
#------------------------------------------
event-control 2001 generate minor
event-control 2002 generate warning
event-control 2003 generate warning
event-control 2004 generate critical
event-control 2005 generate warning
event-control 2006 generate warning
event-control 2007 generate warning
event-control 2008 generate warning
event-control 2009 generate warning
event-control 2010 generate warning
event-control 2011 generate warning
event-control 2012 generate warning
event-control 2013 generate warning
event-control 2014 generate warning
event-control 2015 generate critical
event-control 2016 generate warning
...
----------------------------------------------
A:ALA-12>config>log#
Log command reference
Command hierarchies
Configuration commands
Event control commands
config
- log
- event-control application-id [event-name | event-number] [generate [severity-level] [throttle]
- event-control application-id [event-name | event-number] suppress
- no event-control application [event-name | event-number]
- route-preference primary {inband | outband} secondary {inband | outband | none}
- no route-preference
- throttle-rate events [interval seconds]
- no throttle-rate
Event handling system commands
config
- log
- event-control
- [no] handler eveny-handler-name
- action-list
- [no] entry entry-id
- description string
- no description
- min-delay [delay]
- no min-delay
- script-policy script-policy-name [owner owner-name]
- no script-policy
- description string
- no description
- [no] shutdown
Event trigger commands
config
- log
- event-control
- [no] handler application-id event-name-id
- description string
- no description
- [no] shutdown
- [no] trigger-entry entry-id
- event-handler event-handler
- no event-handler
- log-filter filter-id
- no log-filter
Accounting policy commands
config
- log
- accounting-policy acct-policy-id
- no accounting-policy acct-policy-id
- align
- no align
- collection-interval minutes
- [no] collection-interval
- [no] default
- description description-string
- no description
- [no] log-memory
- record record-name
- no record
- [no] shutdown
- [no] to file log-file-id
File ID commands
config
- log
- [no] file-id log-file-id
- description description-string
- no description
- location [cflash-id | usb-flash-id]
- rollover minutes [retention hours]
- no rollover
Event filter commands
config
- log
- [no] filter filter-id
- default-action {drop | forward}
- no default-action
- description description-string
- no description
- [no] entry entry-id
- action {drop | forward}
- no action
- description description-string
- no description
- [no] match
- application {eq | neq} application-id
- no application
- number {eq | neq | lt | lte | gt | gte} event-id
- no number
- router {eq | neq} router-instance [regexp]
- no router
- severity {eq | neq | lt | lte | gt | gte} severity-level
- no severity
- subject {eq | neq} subject [regexp]
- no subject
Log ID commands
config
- log
- [no] log-id log-id
- description description-string
- no description
- filter filter-id
- no filter
- from {[main] [security] [change] [debug-trace]}
- no from
- [no] shutdown
- time-format {local | utc}
- to console
- to file log-file-id
- to memory [size]
- to session
- to snmp [size]
- to syslog syslog-id
SNMP trap group commands
config
- log
- [no] snmp-dying-gasp primary trap-target-group-num trap-target-name [secondary {trap-target-group-num trap-target-name} [tertiary {trap-target-group-num trap-target-name}]]
- [no] snmp-trap-group log-id
- description description-string
- no description
- trap-target name [address ip-address] [port port] [snmpv1 | snmpv2c | snmpv3] notify-community communityName | snmpv3SecurityName [security-level {no-auth-no-privacy | auth-no-privacy | privacy} [replay]]
- no trap-target name
Syslog commands
config
- log
- [no] syslog syslog-id
- address ip-address
- no address
- description description-string
- no description
- facility syslog-facility
- no facility
- level syslog-level
- no level
- log-prefix log-prefix-string
- no log-prefix
- port port
- no port
Show commands
show
- log
- accounting-policy [acct-policy-id] [access | network]
- accounting-records
- applications
- event-control [application-id [event-name | event-number]]
- file-id [log-file-id]
- filter-id [filter-id]
- log-collector
- log-id [log-id] [severity severity-level] [application application] [sequence from-seq [to-seq]] [count count] [router router-instance [expression]] [subject subject [regexp]] [ascending | descending]
- snmp-trap-group [log-id]
- syslog [syslog-id]
Clear commands
clear
- log log-id
Tools dump commands
tools
- dump
- accounting-policy [id] flash-write-count [clear]
For more information, see the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C OAM and Diagnostics Guide.
Command descriptions
Configuration commands
Generic commands
description
Syntax
description string
no description
Context
config>log
config>log>event-handling>handler
config>log>event-handling>handler>action-list>entry
config>log>event-trigger>event
config>log>filter
config>log>filter>entry
config>log>accounting-policy
config>log>syslog
config>log>snmp-trap-group
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates a text description stored in the configuration file for a configuration context. The description command associates a text string with a configuration context to help identify the content in the configuration file.
The no form of the command removes the string from the configuration.
Parameters
- string
The description can contain a string of up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>log
config>log>accounting-policy
config>log>event-handling>handler>action-list>entry
config>log>event-trigger>event
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command administratively disables an entity. When disabled, an entity does not change, reset, or remove any configuration settings or statistics. The operational state of the entity is disabled as well as the operational state of any entities contained within. Many objects must be shut down before they may be deleted.
The no form of this command administratively enables an entity.
Default
no shutdown
Special Cases
- log-id
When a log-id is shut down, no events are collected for the entity. This leads to the loss of event data.
- accounting-policy
When an accounting policy is shut down, no accounting data is written to the destination log ID. Counters in the billing data reflect totals, not increments, so when the policy is re-enabled (no shutdown) the counters include the data collected during the period the policy was shut down.
Event control commands
event-control
Syntax
event-control application-id [event-name | event-number] [generate [severity-level] [throttle]
event-control application-id [event-name | event-number] suppress
no event-control application [event-name | event-number]
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies that a particular event or all events associated with an application is either generated or suppressed.
Events are generated by an application and contain an event number and description describing the cause of the event. Each event has a default designation which directs it to be generated or suppressed.
Events are generated with a default severity level that can be modified by using the severity-level option.
Events that are suppressed by default are typically used for debugging purposes. Events are suppressed at the time the application requests the event generation. No event log entry is generated regardless of the destination. While this feature can save processor resources, there may be a negative effect on the ability to troubleshoot problems if the logging entries are squelched. In reverse, indiscriminate application may cause excessive overhead.
The rate of event generation can be throttled by using the throttle parameter.
The no form of the command reverts the parameters to the default setting for events for the application or a specific event within the application. The severity, generate, suppress, and throttle options are also reset to the initial values.
Default
Each event has a set of default settings. To display a list of all events and the current configuration use the event-control command.
Parameters
- application-id
The application whose events are affected by this event control filter.
- event-name | event-number
To generate, suppress, or revert to default for a single event, enter the specific number or event short name. If no event number or name is specified, the command applies to all events in the application. To display a list of all event short names use the event-control command.
- generate
Specifies that logger event is created when this event occurs. The generate keyword can be used with two optional parameters, severity-level and throttle.
- severity-name
An ASCII string representing the severity level to associate with the specified generated events
- throttle
Specifies whether events of this type are throttled. By default, event throttling is on for most event types.
- suppress
Indicates that the specified events are not logged. If this keyword is not specified, the events are generated by default.
route-preference
Syntax
route-preference primary {inband | outband} secondary {inband | outband | none}
no route-preference
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the primary and secondary routing preference for traffic generated for SNMP notifications and syslog messages. If the remote destination is not reachable through the routing context specified by primary route preference, the secondary routing preference is attempted.
The no form of the command reverts to the default values.
Default
no route-preference
Parameters
- primary
Specifies the primary routing preference for traffic generated for SNMP notifications and syslog messages.
- secondary
Specifies the secondary routing preference for traffic generated for SNMP notifications and syslog messages. The routing context specified by the secondary route preference is attempted if the remote destination was not reachable by the primary routing preference, specified by primary route preference. The value specified for the secondary routing preference must be distinct from the value for primary route preference.
- inband
Specifies that the logging utility attempts to use the base routing context to send SNMP notifications and syslog messages to remote destinations.
- outband
Specifies that the logging utility attempts to use the management routing context to send SNMP notifications and syslog messages to remote destinations.
- none
Specifies that no attempt is made to send SNMP notifications and syslog messages to remote destinations.
Event handling system commands
event-handling
Syntax
event-handling
Context
config>log
Platforms
7210 SAS-Dxp
Description
Commands in this context configure event handling within the Event Handler System (EHS).
handler
Syntax
[no] handler event-handler-name
Context
config>log>event-handling
Platforms
7210 SAS-Dxp
Description
This command configures an EHS handler.
The no form of this command removes the specified EHS handler.
Default
no handler
Parameters
- event-handler-name
-
Specifies the name of the EHS handler, up to 32 characters.
action-list
Syntax
action-list
Context
config>log>event-handling>handler
Platforms
7210 SAS-Dxp
Description
Commands in this context configure the EHS handler action list.
entry
Syntax
[no] entry entry-id
Context
config>log>event-handling>handler>action-list
Platforms
7210 SAS-Dxp
Description
This command configures an EHS handler action list entry. A handler can have multiple actions where each action, for example, can request the execution of a different script. When the handler is triggered it walks through the list of configured actions.
The no form of this command removes the specified EHS handler action list entry.
Default
no entry
Parameters
- entry-id
-
Specifies the identifier of the EHS handler entry.
min-delay
Syntax
min-delay [delay]
no min-delay
Context
config>log>event-handling>handler>action-list>entry
Platforms
7210 SAS-Dxp
Description
This command specifies the minimum delay, in seconds, between subsequent executions of the action specified in this entry. This is useful, for example, to ensure that a script does not get triggered too often.
The no form of this command disables the minimum delay.
Default
no min-delay
Parameters
- delay
-
Specifies the minimum delay, in seconds.
script-policy
Syntax
script-policy policy-name [owner policy-owner]
no script-policy
Context
config>log>event-handling>handler>action-list>entry
Platforms
7210 SAS-Dxp
Description
This command configures the script policy parameters to use for the EHS handler action list entry. The associated script is launched when the handler is triggered.
The no form of this command disables the script policy parameters.
Default
no script-policy
Parameters
- policy-name
-
Specifies the script policy name, up to 32 characters.
- owner policy-owner
-
Specifies the script policy owner, up to 32 characters.
Event trigger commands
event-trigger
Syntax
event-trigger
Context
config>log
Platforms
7210 SAS-Dxp
Description
Commands in this context configure log events as triggers for EHS handlers.
event
Syntax
[no] event application-id event-name-id
Context
config>log>event-trigger
Platforms
7210 SAS-Dxp
Description
This command configures a specific log event as a trigger for one or more EHS handlers. Further matching criteria can be applied to only trigger specific handlers with specific instances of the log event.
The no form of this command removes the specified trigger event.
Default
no event
Parameters
- application-id
-
Specifies the type of application that triggers the event.
- event-name-id
-
Specifies the name or numerical identifier of the event.
trigger-entry
Syntax
[no] trigger-entry entry-id
Context
config>log>event-trigger>event
Platforms
7210 SAS-Dxp
Description
This command configures an instance of a trigger for an EHS handler. A trigger entry binds a set of matching criteria for a log event to a specific handler. If the log event occurs in the system and matches the criteria configured in the associated log filter, the handler is executed.
The no form of this command removes the specified trigger entry.
Default
no trigger-entry
Parameters
- entry-id
-
Specifies the identifier of the EHS event trigger entry.
event-handler
Syntax
event-handler event-handler
no event-handler
Context
config>log>event-trigger>event>trigger-entry
Platforms
7210 SAS-Dxp
Description
This command configures the event handler to be used for this trigger entry.
The no form of this command removes the event handler to be used for the trigger entry.
Default
no event-handler
Parameters
- event-handler
-
Specifies the name of the event handler, up to 32 characters.
log-filter
Syntax
log-filter filter-id
no log-filter
Context
config>log>event-trigger>event>trigger-entry
Platforms
7210 SAS-Dxp
Description
This command configures the log filter to be used for this trigger entry. The log filter defines the matching criteria that must be met for the log event to trigger the handler execution. The log filter is applied to the log event and, if the filtering decision results in a "forward" action, the handler is triggered.
It is typically unnecessary to configure match criteria for "application" or "number" in the log filter used for the EHS since the specific filter is only applied for a specific log event application and number, as configured under config>log>event-trigger.
The no form of this command removes the log filter to be used for this trigger entry.
Default
no log-filter
Parameters
- filter-id
-
Specifies the ID of the filter.
Log file commands
file-id
Syntax
[no] file-id file-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure a file ID template to be used as a destination for an event log or billing file.
This command defines the file location and characteristics that are to be used as the destination for a log event message stream or accounting/billing information. The file defined in this context is subsequently specified in the to command under log-id or accounting-policy to direct specific logging or billing source streams to the file destination.
A file ID can only be assigned to either one log-id or one accounting-policy. It cannot be reused for multiple instances. A file ID and associated file definition must exist for each log and billing file that must be stored in the file system.
A file is created when the file ID defined in this command is selected as the destination type for a specific log or accounting record. Log files are collected in a ‟log” directory. Accounting files are collected in an ‟act” directory.
The filenames for a log are created by the system as summarized in the following table.
File type |
File name |
|---|---|
Log File |
log lff-timestamp |
Accounting File |
act aaff-timestamp |
where:
ll is the log-id
aa is the accounting policy-id
ff is the file-id
The timestamp is the actual timestamp when the file is created. The format for the timestamp is yyyymmdd-hhmmss where:
yyyy is the year (for example, 2022)
mm is the month number (for example, 12 for December)
dd is the day of the month (for example, 03 for the 3rd of the month)
hh is the hour of the day in 24 hour format (for example, 04 for 4 a.m.)
mm is the minutes (for example, 30 for 30 minutes past the hour)
ss is the number of seconds (for example, 14 for 14 seconds)
The accounting file is compressed and has a .gz extension.
When initialized, each file contains the following:
the log-id description
the time the file was opened
the reason the file was created
if the event log file was closed properly, the sequence number of the last event stored on the log is recorded
If the process of writing to a log file fails (for example, the compact flash card is full) and a backup location is not specified or fails, the log file does not become operational even if the compact flash card is replaced. Enter either a clear log command or a shutdown/no shutdown command to reinitialize the file.
If the primary location fails (for example, the compact flash card fills up during the write process), a trap is sent and logging continues to the specified backup location. This can result in truncated files in different locations.
The no form of this command removes the file-id from the configuration. A file-id can only be removed from the configuration if the file is not the designated output for a log destination. The actual file remains on the file system.
Parameters
- file-id
The file identification number, expressed as a decimal integer.
location
Syntax
location [cflash-id | usb-flash-id]
no location
Context
config>log>file file-id
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the primary location where the log or billing file is created.
When creating files, the primary location is used as long as there is available space. If no space is available, an attempt is made to delete unnecessary files that are past their retention date.
If sufficient space is not available, an attempt is made to remove the oldest to newest closed log or accounting files. After each file is deleted, the system attempts to create the new file.
A medium severity trap is issued to indicate that a compact flash is either not available or that no space is available on the specified flash and that the backup location is being used.
A high priority alarm condition is raised if none of the configured compact flash devices for this file ID are present or if there is insufficient space available. If space becomes available, the alarm condition is cleared.
The no form of this command reverts to default settings.
Default
Log files are created on cf1: and accounting files are created on cf1:.
Parameters
- cflash-id
Specifies the primary location.
- usb-flash-id
Specifies the USB location.
Note:The usb-flash-id parameter is applicable only to platforms that support USB port and USB storage devices.
rollover
Syntax
rollover minutes [retention hours]
no rollover
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures how often an event or accounting log is rolled over or partitioned into a new file.
An event or accounting log is actually composed of multiple individual files. The system creates a new file for the log based on the rollover time, expressed in minutes.
The retention option, expressed in hours, allows you to modify the default time to keep the file in the system. The retention time is based on the rollover time of the file.
When multiple rollover commands for a file-id are entered, the last command overwrites the previous command.
Default
rollover 1440 retention 12
Parameters
- minutes
Specifies the rollover time, in minutes.
- hours
Specifies the retention, period in hours, expressed as a decimal integer. The retention time is based on the creation time of the file. The file becomes a candidate for removal when the creation datestamp, rollover time, and retention time added together is less than the current timestamp.
Log filter commands
filter
Syntax
[no] filter filter-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configured an event filter. An event filter specifies whether to forward or drop an event or trap based on the match criteria.
Filters are configured in the filter filter-id context and applied to a log in the log-id log-id context. Only events for the configured log source streams destined for the log ID where the filter is applied are filtered.
Any changes made to an existing filter, using any of the sub-commands, are immediately applied to the destinations where the filter is applied.
The no form of the command removes the filter association from log IDs, which causes those logs to forward all events.
Parameters
- filter-id
Specifies the filter ID.
default-action
Syntax
default-action {drop | forward}
no default-action
Context
config>log>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the action that is applied to events when no action is specified in the event filter entries or when an event does not match the specified criteria. When multiple default-action commands are entered, the last command overwrites the previous command.
The no form of this command reverts the default action to the default value.
Default
default-action forward
Parameters
- drop
Specifies that the events that are not explicitly forwarded by an event filter match are dropped.
- forward
Specifies that the events that are not explicitly dropped by an event filter match are forwarded.
Log filter entry commands
action
Syntax
action {drop | forward}
no action
Context
config>log>filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies a drop or forward action associated with the filter entry. If neither drop nor forward is specified, the default-action is used for traffic that conforms to the match criteria. This could be considered a no-op filter entry used to explicitly exit a set of filter entries without modifying previous actions.
Multiple action statements entered overwrite previous actions.
The no form of this command removes the specified action statement.
Default
Action specified by the default-action command applies.
Parameters
- drop
Specifies packets matching the entry criteria are dropped.
- forward
Specifies packets matching the entry criteria are forwarded.
entry
Syntax
[no] entry entry-id
Context
config>log>filter
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates or edits an event filter entry. Multiple entries may be created using unique entry-id numbers. The -TiMOS implementation exits the filter on the first match found and executes the action in accordance with the action command.
Comparisons are performed in an ascending entry ID order. When entries are created, they should be arranged sequentially from the most explicit entry to the least explicit. Matching ceases when a packet matches an entry. The entry action is performed on the packet, either drop or forward. To be considered a match, the packet must meet all the conditions defined in the entry.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action for it to be considered complete. Entries without the action keyword are considered incomplete and rendered inactive.
The no form of this command removes the specified entry from the event filter. Entries removed from the event filter are immediately removed from all log IDs where the filter is applied.
Parameters
- entry-id
The entry ID uniquely identifies a set of match criteria corresponding action within a filter. Entry ID values should be configured in staggered increments so you can insert a new entry in an existing policy without renumbering the existing entries.
Log filter entry match commands
match
Syntax
[no] match
Context
config>log>filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates or edits match criteria for a filter entry. When the match criteria is satisfied, the action associated with the entry is executed.
If more than one match parameter (within one match statement) is specified, all the criteria must be satisfied (and functional) before the action associated with the match is executed.
Use the application command to display a list of the valid applications.
Match context can consist of multiple match parameters (application, event-number, severity, subject), but multiple match statements cannot be entered per entry.
The no form of this command removes the match criteria for the entry-id.
application
Syntax
application {eq | neq} application-id
no application
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds a 7210 SAS application as an event filter match criterion.
A 7210 SAS application is the software entity that reports the event. Applications include IP, MPLS, OSPF, CLI, services, and so on. Only one application can be specified. The latest application command overwrites the previous command.
The no form of the command removes the application as a match criterion.
Default
no application
Parameters
- eq | neq
Specifies the operator specifying the type of match. Valid operators are listed in the following table.
Table 11. Valid operators Operator
Notes
eq
equal to
neq
not equal to
- application-id
Specifies the application name string.
number
Syntax
number {eq | neq | lt | lte | gt | gte} event-id
no number
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds an application event number as a match criterion.
The event numbers uniquely identify a specific logging event within an application.
Only one number command can be entered per event filter entry. The latest number command overwrites the previous command.
The no form of the command removes the event number as a match criterion.
Default
no event-number
Parameters
- eq | neq | lt | lte | gt | gte
This operator specifies the type of match. Valid operators are listed in the following table.
Table 12. Valid operators Operator
Notes
eq
equal to
neq
not equal to
lt
less than
lte
less than or equal to
gt
greater than
gte
greater than or equal to
- event-id
Specifies the event ID, expressed as a decimal integer.
router
Syntax
router {eq | neq} router-instance [regexp]
no router
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the log event matches for the router.
Parameters
- eq
Determines if the matching criteria should be equal to the specified value.
- neq
Determines if the matching criteria should not be equal to the specified value.
- router-instance
Specifies a router name up to 32 characters to be used in the match criteria.
- regexp
Specifies the type of string comparison to use to determine whether the log event matches the value of router command parameters. When the regexp keyword is specified, the string in the router command is a regular expression string that is matched against the subject string in the log event being filtered.
severity
Syntax
severity {eq | neq | lt | lte | gt | gte} severity-level
no severity
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds an event severity level as a match criterion. Only one severity command can be entered per event filter entry. The latest severity command overwrites the previous command.
The no form of this command removes the severity match criterion.
Default
no severity
Parameters
- eq | neq | lt | lte | gt | gte
Specifies the type of match. Valid operators are listed in the following table.
Table 13. Valid operators Operator
Notes
eq
equal to
neq
not equal to
lt
less than
lte
less than or equal to
gt
greater than
gte
greater than or equal to
- severity-level
Specifies the ITU severity level name. The following table lists severity names and corresponding numbers per ITU standards M.3100 X.733 and X.21 severity levels.
Table 14. Severity levels Severity number
Severity name
1
cleared
2
indeterminate (info)
3
critical
4
major
5
minor
6
warning
subject
Syntax
subject {eq|neq} subject [regexp]
no subject
Context
config>log>filter>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds an event subject as a match criterion.
The subject is the entity for which the event is reported, such as a port. In this case the port-id string would be the subject. Only one subject command can be entered per event filter entry. The latest subject command overwrites the previous command.
The no form of this command removes the subject match criterion.
Default
no subject
Parameters
- eq | neq
Specifies the type of match. Valid operators are listed in the following table.
Table 15. Valid operators Operator
Notes
eq
equal to
neg
not equal to
- subject
Specifies a string used as the subject match criterion.
- regexp
Specifies the type of string comparison to use to determine whether the log event matches the value of subject command parameters. When the regexp keyword is specified, the string in the subject command is a regular expression string that is matched against the subject string in the log event being filtered.
When the regexp keyword is not specified, the subject command string is matched exactly by the event filter.
Syslog commands
syslog
Syntax
[no] syslog syslog-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure a syslog target host that is capable of receiving selected syslog messages from this network element.
A valid syslog-id must have the target syslog host address configured. A maximum of 10 syslog IDs can be configured.
No log events are sent to a syslog target address until the syslog-id has been configured as the log destination (to) in the log-id node.
The no form of this command removes the syslog configuration.
Parameters
- syslog-id
Specifies the syslog ID number for the syslog destination, expressed as a decimal integer.
address
Syntax
address ip-address
no address
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds the syslog target host IP address to/from a syslog ID.
This parameter is mandatory. If no address is configured, syslog data cannot be forwarded to the syslog target host.
Only one address can be associated with a syslog-id. If multiple addresses are entered, the last address entered overwrites the previous address.
The same syslog target host can be used by multiple log IDs.
The no form of this command removes the syslog target host IP address.
Default
no address
Parameters
- ip-address
Specifies the IP address of the syslog target host in dotted decimal notation.
facility
Syntax
facility syslog-facility
no facility
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the facility code for messages sent to the syslog target host.
Multiple syslog IDs can be created with the same target host, but each syslog ID can only have one facility code. If multiple facility codes are entered, the last facility code entered overwrites the previous facility code.
If multiple facilities need to be generated for a single syslog target host, multiple log ID entries must be created, each with its own filter criteria to select the events to be sent to the syslog target host with a specific facility code.
The no form of this command reverts to the default value.
Default
facility local7
Parameters
- syslog-facility
Specifies the syslog facility name. The syslog facility name represents a specific numeric facility code. The code should be entered in accordance with the syslog RFC. However, the software does not validate if the facility code configured is appropriate for the event type being sent to the syslog target host.
|
Numerical code |
Facility code |
|---|---|
|
0 |
kernel |
|
1 |
user |
|
2 |
|
|
3 |
systemd |
|
4 |
auth |
|
5 |
syslogd |
|
6 |
printer |
|
7 |
net-news |
|
8 |
uucp |
|
9 |
cron |
|
10 |
auth-priv |
|
11 |
ftp |
|
12 |
ntp |
|
13 |
log-audit |
|
14 |
log-alert |
|
15 |
cron2 |
|
16 |
local0 |
|
17 |
local1 |
|
18 |
local2 |
|
19 |
local3 |
|
20 |
local4 |
|
21 |
local5 |
|
22 |
local6 |
|
23 |
local7 |
log-prefix
Syntax
log-prefix log-prefix-string
no log-prefix
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds the string prepended to every syslog message sent to the syslog host.
RFC 3164, The BSD syslog Protocol, allows an alphanumeric string (tag) to be prepended to the content of every log message sent to the syslog host. This alphanumeric string can, for example, be used to identify the node that generates the log entry. The software appends a colon (:) and a space to the string and it is inserted in the syslog message after the date stamp and before the syslog message content.
Only one string can be entered. If multiple strings are entered, the last string overwrites the previous string. The alphanumeric string can contain lowercase (a-z), uppercase (A-Z), and numeric (0-9) characters.
The no form of this command removes the log prefix string.
Default
no log-prefix
Parameters
- log-prefix-string
Specifies an alphanumeric string, up to 32 characters. Spaces and colons cannot be used in the string.
level
Syntax
level syslog-level
no level
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the syslog message severity level threshold. All messages with a severity level equal to or higher than the threshold are sent to the syslog target host. Severity levels are shown in Syslog message severity levels.
Only a single threshold level can be specified. If multiple levels are entered, the last level entered overwrites the previously entered commands.
The no form of this command reverts to the default value.
Default
level info
Parameters
- syslog-level
Specifies the threshold severity level name.
|
Severity level |
Numerical severity (highest to lowest) |
Configured severity |
Definition |
|---|---|---|---|
|
0 |
emergency |
system is unusable |
|
|
3 |
1 |
alert |
action must be taken immediately |
|
4 |
2 |
critical |
critical condition |
|
5 |
3 |
error |
error condition |
|
6 |
4 |
warning |
warning condition |
|
5 |
notice |
normal but significant condition |
|
|
1 cleared 2 indeterminate |
6 |
info |
informational messages |
|
7 |
debug |
debug-level messages |
port
Syntax
port port
no port
Context
config>log>syslog
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the UDP port that is used to send syslog messages to the syslog target host.
The port configuration is needed if the syslog target host uses a port other than the standard UDP syslog port 514.
Only one port can be configured. If multiple port commands are entered, the last entered port overwrites the previously entered ports.
The no form of this command removes the value from the configuration.
Default
no port
Parameters
- port
Specifies the UDP port number to use when sending syslog messages.
throttle-rate
Syntax
throttle-rate events [interval seconds]
no throttle-rate
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures an event throttling rate.
Parameters
- events
Specifies the number of log events that can be logged within the specified interval for a specific event. When the limit is reached, any additional events of that type are dropped, for example, the event drop count is incremented. At the end of the throttle interval, if any events have been dropped, a trap notification is sent.
- interval seconds
Specifies the number of seconds that an event throttling interval lasts.
SNMP trap group commands
snmp-trap-group
Syntax
[no] snmp-trap-group log-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure a group of SNMP trap receivers and their operational parameters for a specific log-id.
A group specifies the types of SNMP traps and the log ID that will receive the group of SNMP traps. A trap group must be configured for SNMP traps to be sent.
To suppress the generation of all alarms and traps, see the event-control command. To suppress alarms and traps that are sent to this log-id, see the filter command. When alarms and traps are generated, they can be directed to one or more SNMP trap groups. Logger events that can be forwarded as SNMP traps are always defined on the main event source.
The no form of this command deletes the SNMP trap group.
Parameters
- log-id
-
Specifies the log ID value of a log configured in the log-id context. Alarms and traps cannot be sent to the trap receivers until a valid log-id exists.
snmp-dying-gasp
Syntax
snmp-dying-gasp primary trap-target-group-num trap-target-name [secondary {trap-target-group-num trap-target-name} [tertiary {trap-target-group-num trap-target- name}]]
no snmp-dying-gasp
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document, except the 7210 SAS-Dxp 16p and 7210 SAS-Dxp 24p
Description
This command notifies the SNMP trap server about node power failure. On power failure, the system sends dying gasp traps to the configured SNMP trap servers. Up to three SNMP trap servers can be configured to receive the trap. The traps are sent in the following order:
-
primary SNMP trap receiver
-
Secondary SNMP trap receiver
-
tertiary SNMP trap receiver
When this command is enabled, the node does not generate EFM OAM dying gasp message even if EFM OAM is enabled. That is, generation of an SNMP dying gasp trap is mutually exclusive to the use of an EFM OAM dying gasp message.
By default, the system generates an EFM OAM dying gasp message to remain compatible with earlier versions of the software releases. The user must explicitly configure the system to send out an SNMP trap on loss of power to the node using this command.
Typically, SNMP traps are generated only if the user configures a log to direct the system log events to SNMP. For an SNMP dying gasp trap, it is not required to do so. The DSCP value used by a SNMP dying gasp packet is AF (Assured Forwarding class, value 22).
-
The system IP address must be configured. The node uses this address to generate dying gasp traps. If It is not configured, SNMP dying gasp traps are not generated.
-
When sending out SNMP dying gasp traps, one of the available routes in either the management routing instance or the base routing instance is used to resolve the next-hop gateway IP address to reach the trap-server destinations configured under primary, secondary, and tertiary trap targets. The route to the destination is always searched first in the management routing instance and if not found, the routes in the base routing instance is looked up. Configuration of route preference does not change this behavior (that is, the order of route lookup does not change).
The no form of this command disables generation of SNMP trap messages. It enables generation of EFM OAM dying gasp on access-uplink ports, if EFM OAM is enabled on those ports. The generation of SNMP dying gasp traps is disabled by default.
Default
no snmp-dying-gasp
Parameters
- primary trap-target-group-numtrap- target-name
-
Specifies the primary SNMP trap receiver to which the system addresses the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap groups configured in the config>log>snmp-trap-group trap-num command. The trap-target-name must correspond to one of the SNMP trap receiver targets configured under config>log>snmp-trap-group trap-num trap-target target-name.
- secondary trap-target-group-numtrap-target-name
-
Specifies the secondary SNMP trap receiver to which the system addresses the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap groups configured under config>log>snmp-trap-group trap-num. The trap-target-name must correspond to one of the SNMP trap receiver target configured under config>log>snmp-trap-group trap-num trap-target target-name.
- tertiary trap-target-group-numtrap-target- name
-
Specifies the tertiary SNMP trap receiver to which the system addresses the SNMP trap. The trap-target-group-num must correspond to one of the SNMP trap group configuration under config>log>snmp-trap-group trap-num. The trap-target-name must correspond to one of the SNMP trap receiver target configured under config>log>snmp-trap-group trap-num trap-target target-name.
- trap-target-group-num
-
Specifies the trap target group number, expressed as a decimal integer.
- trap-target-name
-
Specifies the trap target name, up to 28 characters.
trap-target
Syntax
trap-target name [address ip-address] [port port] [snmpv1 | snmpv2c | snmpv3] notify-community communityName | snmpv3SecurityName [security-level {no-auth-no-privacy | auth-no-privacy | privacy}] [replay]
no trap-target name
Context
config>log>snmp-trap-group
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds or modifies a trap receiver and configures the operational parameters for the trap receiver. A trap reports significant events that occur on a network device such as errors or failures.
Before an SNMP trap can be issued to a trap receiver, the log-id, snmp-trap-group, and at least one trap-target must be configured.
The trap-target command is used to add or remove a trap receiver from an snmp-trap-group. The operational parameters specified in the command include the following:
-
IP address of the trap receiver
-
UDP port used to send the SNMP trap
-
SNMP version
-
SNMP community name for SNMPv1 and SNMPv2c receivers
-
security name and level for SNMPv3 trap receivers
A single snmp-trap-group log-id can have multiple trap receivers. Each trap receiver can have different operational parameters.
An address can be configured as a trap receiver more than once, as long as a different port is used for each instance.
To prevent resource limitations, only configure a maximum of 10 trap receivers.
If the same trap-target name port port parameter value is specified in more than one SNMP trap group, each trap destination should be configured with a different notify-community value. This allows a trap receiving an application, such as NMS, to reconcile a separate event sequence number stream for each 7210 SAS event log when multiple event logs are directed to the same IP address and port destination.
The no form of this command removes the SNMP trap receiver from the SNMP trap group.
Parameters
- name
-
Specifies the name of the trap target up to 28 characters.
- address ip-address
-
Specifies the IP address of the trap receiver in dotted decimal notation. Only one IP address destination can be specified per trap destination group.
- port
-
Specifies the destination UDP port used to send traps to the destination, expressed as a decimal integer. Only one port can be specified per trap-target statement. If multiple traps must be issued to the same address, multiple ports must be configured.
- snmpv1 | snmpv2c | snmpv3
-
Specifies the SNMP version format to use for traps sent to the trap receiver.
The keyword snmpv1 selects the SNMP version 1 format. When specifying snmpv1, the notify-community must be configured for the correct SNMP community string that the trap receiver expects to be present in alarms and traps messages. If the SNMP version is changed from snmpv3 to snmpv1, the notify-community parameter must be changed to reflect the community string instead of the security-name that is used by snmpv3.
The keyword snmpv2c selects the SNMP version 2c format. When specifying snmpv2c, the notify-community must be configured for the correct SNMP community string that the trap receiver expects to be present in alarms and traps messages. If the SNMP version is changed from snmpv3 to snmpv2c, the notify-community parameter must be changed to reflect the community string instead of the security-name that is used by snmpv3.
The keyword snmpv3 selects the SNMP version 3 format. When specifying snmpv3, the notify-community must be configured for the SNMP security-name. If the SNMP version is changed from snmpv1or snmpv2c to snmpv3, the notify-community parameter must be changed to reflect the security-name instead of the community string used by snmpv1 or snmpv2c.
The following pre-existing conditions are checked before the snmpv3SecurityName is accepted.
-
The username must be configured.
-
The v3 access group must be configured.
-
The v3 notification view must be configured.
-
- notify-community community | security-name
-
Specifies the community string for the snmpv1, snmpv2c, or snmpv3 security-name. If no notify-community is configured, no alarms nor traps are issued for the trap destination. If the SNMP version is modified, the notify-community must be changed to the correct form for the SNMP version.
- community
-
Specifies the community string as required by the snmpv1 or snmpv2c trap receiver. The community string can be an ASCII string up to 31 characters in length.
- security-name
-
Specifies the security-name as defined in the config>system>security>user context for SNMPv3. The security-name can be an ASCII string up to 31 characters.
- security-level {no-auth-no-privacy | auth-no-privacy | privacy}
-
Specifies the required authentication and privacy levels required to access the views configured on this node when configuring an snmpv3 trap receiver.
The keyword no-auth-no-privacy specifies that no authentication and no privacy (encryption) are required.
The keyword auth-no-privacy specifies that authentication is required, but no privacy (encryption) is required. When this option is configured the security-name must be configured for authentication.
The keyword privacy specifies that both authentication and privacy (encryption) is required. When this option is configured the security-name must be configured for authentication and privacy.
- replay
-
Enables replay of missed events to target. If replay is applied to an SNMP trap target address, the address is monitored for reachability. Reachability is determined by whether there is a route in the routing table by which the target address can be reached. Before sending a trap to a target address, the SNMP module asks the PIP module if there is either an in-band or out-of-band route to the target address.
If there is no route to the SNMP target address, the SNMP module saves the sequence ID of the first event that is missed by the trap target. When the routing table changes again so that there is now a route by which the SNMP target address can be reached, the SNMP module replays (for example, retransmits) all events generated to the SNMP notification log while the target address was removed from the route table.
Note:The route table changes the convergence time so it is possible that one or more events may be lost at the beginning or end of a replay sequence.
Logging destination commands
filter
Syntax
filter filter-id
no filter
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds an event filter policy with the log destination.
This command is optional. If no event filter is configured, all events, alarms, and traps generated by the source stream are forwarded to the destination.
An event filter policy defines (limits) the events that are forwarded to the destination configured in the log ID. The event filter policy can also be used to select the alarms and traps to be forwarded to a destination snmp-trap-group.
The application of filters for debug messages is limited to application and subject only.
Accounting records cannot be filtered using the filter command.
Only one filter-id can be configured per log destination.
The no form of the command removes the specified event filter from the log-id.
Default
no filter
Parameters
- filter-id
Specifies the filter with which to associate the log-id configuration. The event filter policy ID must already be defined in config>log>filter filter-id.
from
Syntax
from {[main] [security] [change] [debug-trace]}
no from
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the source stream to be sent to a log destination.
One or more source streams must be specified. The source of the data stream must be identified using the from command before you can configure the destination using the to command. The from command can identify multiple source streams in a single statement (for example, from main change debug-trace).
Only one from command may be entered for a single log-id. If multiple from commands are configured, the last command entered overwrites the previous from command.
The no form of this command removes all previously configured source streams.
Parameters
- main
Instructs all events in the main event stream to be sent to the destination defined in the to command for this destination log-id. The main event stream contains the events that are not explicitly directed to any other event stream. To limit the events forwarded to the destination, configure filters using the filter command.
- security
Instructs all events in the security event stream to be sent to the destination defined in the to command for this destination log-id. The security stream contains all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. To limit the events forwarded to the destination, configure filters using the filter command.
- change
Instructs all events in the user activity stream to be sent to the destination configured in the to command for this destination log-id. The change event stream contains all events that directly affect the configuration or operation of this node. To limit the events forwarded to the change stream destination, configure filters using the filter command.
- debug-trace
Instructs all debug-trace messages in the debug stream to be sent to the destination configured in the to command for this destination log-id. Filters applied to debug messages are limited to application and subject.
log-id
Syntax
[no] log-id log-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure destinations for event streams.
The log-id context is used to direct events, alarms and traps, and debug information to respective destinations.
A maximum of 10 logs can be configured.
Before an event can be associated with this log-id, the from command identifying the source of the event must be configured.
Only one destination can be specified for a log-id. The destination of an event stream can be an in-memory buffer, console, session, snmp-trap-group, syslog, or file.
Use the event-control command to suppress the generation of events, alarms, and traps for all log destinations.
An event filter policy can be applied in the log-id context to limit which events, alarms, and traps are sent to the specified log-id.
Log IDs 99 and 100 are created by the agent. Log ID 99 captures all log messages. Log ID 100 captures log messages with a severity level of major and above.
Log ID 99 provides valuable information for the admin-tech file. Removing or changing the log configuration may hinder debugging capabilities. It is strongly recommended not to alter the configuration for log ID 99.
The no form of this command deletes the log destination ID from the configuration.
Parameters
- log-id
Specifies the log ID number, expressed as a decimal integer.
to console
Syntax
to console
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to the console. If the console is not connected, all entries are dropped.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
to file
Syntax
to file log-file-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to a specified file.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
Parameters
- log-file-id
Instructs the events selected for the log ID to be directed to the log-file-id. The characteristics of the log-file-id referenced here must have already been defined in the config>log>file log-file-id context.
to memory
Syntax
to memory [size]
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies a log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to a memory log. A memory file is a circular buffer. When the file is full, each new entry replaces the oldest entry in the log.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
Parameters
- size
Specifies the number of events that can be stored in the memory.
to session
Syntax
to session
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies a log ID destination and is mandatory when configuring a log destination. This command instructs the events selected for the log ID to be directed to the current console or Telnet session. This command is only valid for the duration of the session. When the session is terminated the log ID is removed. A log ID with a session destination is not saved in the configuration file.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
to snmp
Syntax
to snmp [size]
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the log ID destination. This parameter is mandatory when configuring a log destination. This command instructs the alarms and traps to be directed to the snmp-trap-group associated with log-id.
A local circular memory log is always maintained for SNMP notifications sent to the specified snmp-trap-group for the log-id.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
Parameters
- size
Specifies the number of events stored in this memory log.
to syslog
Syntax
to syslog syslog-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command also specifies the log ID destination. This parameter is mandatory when configuring a log destination.
This command instructs the alarms and traps to be directed to a specified syslog. To remain consistent with the standards governing syslog, messages to syslog are truncated to 1k bytes.
The source of the data stream must be specified in the from command before configuring the destination with the to command.
The to command cannot be modified or re-entered. If the destination or maximum size of an SNMP or memory log needs to be modified, the log ID must be removed and then re-created.
Parameters
- syslog-id
Instructs the events selected for the log ID to be directed to the syslog-id. The characteristics of the syslog-id referenced here must have been defined in the config>log>syslog syslog-id context.
time-format
Syntax
time-format {local | utc}
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies whether the time should be displayed in the local or Coordinated Universal Time (UTC) format.
Default
time-format utc
Parameters
- local
Specifies that timestamps are written in the system’s local time.
- utc
Specifies that timestamps are written using the UTC value. This was formerly called Greenwich Mean Time (GMT) and Zulu time.
Accounting policy commands
accounting-policy
Syntax
accounting-policy policy-id
no accounting-policy policy-id
Context
config>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables an access or network accounting policy. An accounting policy defines the accounting records that are created.
Access accounting policies are policies that can be applied to one or more SAPs or access ports.
Changes made to an existing policy, using any of the sub-commands, are applied immediately to all SAPs or access ports where this policy is applied.
If an accounting policy is not specified on a SAP or an access port, accounting records are produced in accordance with the access policy designated as the default. If a default access policy is not specified, no accounting records are collected other than the records for the accounting policies that are explicitly configured.
Network accounting policies can be applied to one or more network ports. Any changes made to an existing policy, using any of the subcommands, are immediately applied to all network ports where this policy is applied.
If no accounting policy is defined on a network port, accounting records are produced in accordance with the default network policy as designated with the default command. If no network default policy is created, no accounting records are collected other than the records for the accounting policies explicitly configured.
A total of 16 accounting records are available on the 7210 SAS-D. A total of 17 accounting records are available on the 7210 SAS-Dxp.
There are three types of accounting policies:
access
access port
network
When creating accounting policies, one access, access port, and network accounting policy can be defined as default. If statistics collection is enabled on an accounting object, and no accounting policy is applied, the respective default accounting policy is used. If no default policy is defined, no statistics are collected unless a specifically defined accounting policy is applied.
The no form of this command deletes the policy from the configuration. The accounting policy cannot be removed unless it is removed from all the SAPs, network ports, or channels where the policy is applied.
Parameters
- policy-id
Specifies the policy ID that uniquely identifies the accounting policy, expressed as a decimal integer.
align
Syntax
align
no align
Context
config>log>accounting-policy
Platforms
7210 SAS-Dxp
Description
This command aligns statistics collection to the nearest interval within an hour. Enabling this alignment allows statistics to be collected in an accounting file that is synchronized across multiple network nodes in the network.
The no form of this command disables the alignment of statistics collection.
Default
no align
collection-interval
Syntax
collection-interval minutes
no collection-interval
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the accounting collection interval.
Parameters
- minutes
Specifies the interval between collections, in minutes.
default
Syntax
[no] default
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the default accounting policy to be used with all SAPs that do not have an accounting policy.
If no accounting policy is defined on an access or network object, accounting records are produced in accordance with the default access policy. If no default access policy is created, then no accounting records are collected other than the records for the accounting policies that are explicitly configured.
When creating accounting policies, one access, one access port, and one network accounting policy can be defined as default.
The record name must be specified before assigning an accounting policy as default.
If a policy is configured as the default policy, a no default command must be issued before a new default policy can be configured.
The no form of this command removes the default policy designation from the policy ID. The accounting policy is removed from all access or network object ports that do not have this policy explicitly defined.
record
Syntax
[no] record record-name
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command adds the accounting record type to the accounting policy to be forwarded to the configured accounting file. A record name can only be used in one accounting policy. To obtain a list of all record types that can be configured, use the show log accounting-records command.
The following is an output sample for the 7210 SAS-D and 7210 SAS-Dxp.
A:7210-SAS>show>log# accounting-records
==========================================================
Accounting Policy Records
==========================================================
Record # Record Name Def. Interval
----------------------------------------------------------
1 service-ingress-octets 5
2 service-egress-octets 5
3 service-ingress-packets 5
4 service-egress-packets 5
5 network-ingress-octets 15
6 network-egress-octets 15
7 network-ingress-packets 15
8 network-egress-packets 15
10 combined-service-ingress 5
11 combined-network-ing-egr-octets 15
13 complete-service-ingress-egress 5
32 saa 5
36 access-egress-packets 5
37 access-egress-octets 5
38 combined-access-egress 5
39 combined-network-egress 15
40 combined-service-egress 5
==========================================================
A:7210-SAS>show>log#
The following is an output sample for 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, or 7210 SAS-K 3SFP+ 8C.
*A:7210SASk>show>log# accounting-records
===========================================================
Accounting Policy Records
===========================================================
Record # Record Name Def. Interval
-----------------------------------------------------------
1 service-ingress-octets 5
2 service-egress-octets 5
3 service-ingress-packets 5
4 service-egress-packets 5
5 network-ingress-octets 15
6 network-egress-octets 15
7 network-ingress-packets 15
8 network-egress-packets 15
10 combined-service-ingress 5
11 combined-network-ing-egr-octets 15
13 complete-service-ingress-egress 5
32 saa 5
58 combined-network-egress 15
59 combined-service-egress 5
===========================================================
*A:7210SASk>show>log#
To configure an accounting policy for access SAPs, select a service record (for example, service-ingress-octets). To change the record name to another service record, enter the record command with the new record name and it replaces the old record name.
To configure an accounting policy for access ports, select access port type records such as access-egress packets. When changing the record name to another access port record, the record command with the new record name can be entered, and it replaces the old record name.
When configuring an accounting policy for network ports, a network record should be selected. When changing the record name to another network record, the record command with the new record name can be entered and it replaces the old record name.
If the change required modifies the record from one type to another, the old record name must be removed using the no form of this command.
Only one record may be configured in a single accounting policy. For example, if an accounting-policy is configured with an access-egress-packets record, to change it to service-ingress-octets, use the no record command under the accounting-policy to remove the old record and enter the service-ingress-octets record.
Collecting excessive statistics can adversely affect the CPU utilization and take up large amounts of storage space
The no form of this command removes the record type from the policy.
Parameters
- record-name
Specifies the accounting record name.
to
Syntax
to file file-id
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the destination for the accounting records selected for the accounting policy.
Parameters
- file-id
This option specifies the destination for the accounting records selected for this destination. The characteristics of the file-id must have already been defined in the config>log>file context. A file-id can be used only once.
The file is generated when the file policy is referenced. This command identifies the type of accounting file to be created. The file definition defines its characteristics.
If the to command is executed while the accounting policy is in operation, it becomes active during the next collection interval.
log-memory
Syntax
log-memory
[no] log-memory
Context
config>log>accounting-policy
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the system to allocate some RAM (that is, volatile memory) as a temporary storage to write accounting records every collection-interval. The accounting records are moved from the temporary storage to the accounting file on non-volatile memory (that is, flash), when either the rollover-interval expires or the temporary storage location gets full.
The accounting records held in the temporary storage is lost on a reboot (either as a result of loss of power or as a result of user action).
Show commands
accounting-policy
Syntax
accounting-policy [acct-policy-id] [access | network]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays accounting policy information.
Parameters
- policy-id
Displays the policy ID that uniquely identifies the accounting policy, expressed as a decimal integer.
- access
Displays only access accounting policies.
- network
Displays only network accounting policies.
Output
The following output is an example of accounting policy information, and Output fields: accounting policy describes the output fields.
Sample outputA:ALA-1# show log accounting-policy
==============================================================================
Accounting Policies
==============================================================================
Policy Type Def Admin Oper Intvl File Record Name
Id State State Id
------------------------------------------------------------------------------
1 network No Up Up 15 1 network-ingress-packets
2 network Yes Up Up 15 2 network-ingress-octets
==============================================================================
A:ALA-1#
A:ALA-1# show log accounting-policy 10
==============================================================================
Accounting Policies
==============================================================================
Policy Type Def Admin Oper Intvl File Record Name
Id State State Id
------------------------------------------------------------------------------
10 access Yes Up Up 5 3 service-ingress-octets
Description : (Not Specified)
This policy is applied to:
Svc Id: 100 SAP : 1/1/8:0 Collect-Stats
Svc Id: 101 SAP : 1/1/8:1 Collect-Stats
Svc Id: 102 SAP : 1/1/8:2 Collect-Stats
Svc Id: 103 SAP : 1/1/8:3 Collect-Stats
Svc Id: 104 SAP : 1/1/8:4 Collect-Stats
Svc Id: 105 SAP : 1/1/8:5 Collect-Stats
Svc Id: 106 SAP : 1/1/8:6 Collect-Stats
Svc Id: 107 SAP : 1/1/8:7 Collect-Stats
Svc Id: 108 SAP : 1/1/8:8 Collect-Stats
Svc Id: 109 SAP : 1/1/8:9 Collect-Stats
...
==============================================================================
A:ALA-1#
A:ALA-1# show log accounting-policy network
==============================================================================
Accounting Policies
==============================================================================
Policy Type Def Admin Oper Intvl File Record Name
Id State State Id
------------------------------------------------------------------------------
1 network No Up Up 15 1 network-ingress-packets
2 network Yes Up Up 15 2 network-ingress-octets
==============================================================================
A:ALA-1#
A:ALA-1# show log accounting-policy access
==============================================================================
Accounting Policies
==============================================================================
Policy Type Def Admin Oper Intvl File Record Name
Id State State Id
------------------------------------------------------------------------------
10 access Yes Up Up 5 3 service-ingress-octets
==============================================================================
A:ALA-1#
Label |
Description |
|---|---|
Policy ID |
Displays the identifying value assigned to a specific policy |
Type |
Identifies the accounting record type forwarded to the configured accounting file access — Indicates that the policy is an access accounting policy network — Indicates that the policy is a network accounting policy access port — Indicates that the policy is an access port accounting policy which can be used to collect accounting records only for access ports none — Indicates no accounting record types assigned |
Def |
Yes — Indicates that the policy is a default access or network policy No — Indicates that the policy is not a default access or network policy |
Admin State |
Displays the administrative state of the policy Up — Indicates that the policy is administratively enabled Down — Indicates that the policy is administratively disabled |
Oper State |
Displays the operational state of the policy Up — Indicates that the policy is operationally up Down — Indicates that the policy is operationally down |
Intvl |
Displays the interval, in minutes, in which statistics are collected and written to their destination The default depends on the record name type |
File ID |
Displays the log destination |
Record Name |
Displays the accounting record name, which represents the configured record type |
Log-Memory |
Yes — Indicates that temporary volatile memory is in use for this accounting policy No — Indicates that temporary volatile memory is not in use for this accounting policy |
Log-Memory Size |
Displays the amount of temporary volatile memory in use for this accounting policy |
This policy is applied to |
Specifies the entity where the accounting policy is applied |
accounting-records
Syntax
accounting-records
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays accounting policy record names.
Output
The following outputs are examples of accounting record information, and Output fields: accounting records describes the output fields.
Sample output for 7210 SAS-D and 7210 SAS-DxpA:7210-SAS>show>log# accounting-records
==========================================================
Accounting Policy Records
==========================================================
Record # Record Name Def. Interval
----------------------------------------------------------
1 service-ingress-octets 5
2 service-egress-octets 5
3 service-ingress-packets 5
4 service-egress-packets 5
5 network-ingress-octets 15
6 network-egress-octets 15
7 network-ingress-packets 15
8 network-egress-packets 15
10 combined-service-ingress 5
11 combined-network-ing-egr-octets 15
13 complete-service-ingress-egress 5
32 saa 5
36 access-egress-packets 5
37 access-egress-octets 5
38 combined-access-egress 5
39 combined-network-egress 15
40 combined-service-egress 5
==========================================================
A:7210-SAS>show>log#
Label |
Description |
|---|---|
Record # |
Displays the record ID that uniquely identifies the accounting policy, expressed as a decimal integer |
Record Name |
Displays the accounting record name |
Def. Interval |
Displays the default interval, in minutes, in which statistics are collected and written to their destination |
applications
Syntax
applications
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays a list of all application names that can be used in event-control and filter commands.
Output
The following output is an example of log application name information.
Sample outputA:ALA-1# show log applications
==================================
Log Event Application Names
==================================
Application Name
----------------------------------
CCAG
CHASSIS
CPMHWFILTER
DHCP
DEBUG
DOT1X
FILTER
IGMP
IGMP_SNOOPING
IP
ISIS
LAG
LDP
LOGGER
MIRROR
MPLS
OAM
OSPF
PORT
PPP
QOS
RIP
ROUTE_POLICY
RSVP
SECURITY
SNMP
STP
SVCMGR
SYSTEM
USER
VRRP
VRTR
==================================
A:ALA-1#
event-control
Syntax
event-control [application-id [event-name | event-number]]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays event control settings for events including whether the event is suppressed or generated and the severity level for the event.
If no options are specified all events, alarms and traps are listed.
Parameters
- application-id
Only displays event control for the specified application.
- event-name
Only displays event control for the named application event, up to 32 characters.
- event-number
Only displays event control for the specified application event number.
Output
The following output is an example of event control settings information, and Output fields: event control describes the output fields.
Sample outputA:ALA-1# show log event-control ospf
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2001 ospfVirtIfStateChange WA gen 0 0
2002 ospfNbrStateChange WA gen 1 0
2003 ospfVirtNbrStateChange WA gen 0 0
2004 ospfIfConfigError WA gen 0 0
2005 ospfVirtIfConfigError WA gen 0 0
2006 ospfIfAuthFailure WA gen 0 0
2007 ospfVirtIfAuthFailure WA gen 0 0
2008 ospfIfRxBadPacket WA gen 0 0
2009 ospfVirtIfRxBadPacket WA gen 0 0
2010 ospfTxRetransmit WA sup 0 0
2011 ospfVirtIfTxRetransmit WA sup 0 0
2012 ospfOriginateLsa WA sup 0 404
2013 ospfMaxAgeLsa WA gen 3 0
2014 ospfLsdbOverflow WA gen 0 0
2015 ospfLsdbApproachingOverflow WA gen 0 0
2016 ospfIfStateChange WA gen 2 0
2017 ospfNssaTranslatorStatusChange WA gen 0 0
2018 vRtrOspfSpfRunsStopped WA gen 0 0
2019 vRtrOspfSpfRunsRestarted WA gen 0 0
2020 vRtrOspfOverloadEntered WA gen 1 0
2021 vRtrOspfOverloadExited WA gen 0 0
2022 ospfRestartStatusChange WA gen 0 0
2023 ospfNbrRestartHelperStatusChange WA gen 0 0
2024 ospfVirtNbrRestartHelperStsChg WA gen 0 0
=======================================================================
A:ALA-1#
A:ALA-1# show log event-control ospf ospfVirtIfStateChange
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2001 ospfVirtIfStateChange WA gen 0 0
=======================================================================
A:ALA-1#
Label |
Description |
|---|---|
Application |
Displays the application name |
ID# |
Displays the event ID number within the application L ID# An ‟L” in front of an ID represents event types that do not generate an associated SNMP notification Most events do generate a notification, only the exceptions are marked with a preceding ‟L” |
Event Name |
Displays the event name |
P |
CL — The event has a cleared severity/priority CR — The event has critical severity/priority IN — The event has indeterminate severity/priority MA — The event has major severity/priority MI — The event has minor severity/priority WA — The event has warning severity/priority |
g/s |
gen — The event is generated/logged by event control sup — The event is suppressed or dropped by event control thr — Specifies that throttling is enabled |
Logged |
Displays the number of events logged/generated |
Dropped |
Displays the number of events dropped/suppressed |
file-id
Syntax
file-id [log-file-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays event file log information.
If no command line parameters are specified, a summary output of all event log files is displayed.
Specifying a file ID displays detailed information about the event file log.
Parameters
- log-file-id
Displays detailed information about the specified event file log.
Output
The following output is an example of event file log information, and Output fields: file ID describes the output fields.
Sample outputA:ALA-4# show system security access-group
Label |
Description |
|---|---|
file-id |
Displays the log file ID |
rollover |
Displays the rollover time for the log file, which is how long in between partitioning of the file into a new file |
retention |
Displays the retention time for the file in the system, which is how long the file should be retained in the file system |
admin location |
The primary flash device specified for the file location none — indicates no specific flash device was specified |
oper location |
Displays the actual flash device on which the log file exists |
file-id |
Displays the log file ID |
rollover |
Displays the rollover time for the log file, which is how long in between partitioning of the file into a new file |
retention |
Displays the retention time for the file in the system, which is how long the file should be retained in the file system |
file name |
Displays the complete path name of the file associated with the log ID |
expired |
Indicates whether the retention period for this file has passed |
state |
in progress — Indicates the current open log file complete — Indicates the old log file |
filter-id
Syntax
filter-id [filter-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays event log filter policy information.
Parameters
- filter-id
Displays detailed information about the specified event filter policy ID.
Output
The following outputs are examples of log filter policy information, and the associated tables describe the output fields.
Sample output — standard*A:ALA-48>config>log# show log filter-id
=============================================================================
Log Filters
=============================================================================
Filter Applied Default Description
Id Action
-----------------------------------------------------------------------------
1 no forward
5 no forward
10 no forward
1001 yes drop Collect events for Serious Errors Log
=============================================================================
*A:ALA-48>config>log#
Label |
Description |
|---|---|
Filter Id |
Displays the event log filter ID |
Applied |
no — The event log filter is not currently in use by a log ID yes — The event log filter is currently in use by a log ID |
Default Action |
drop — The default action for the event log filter is to drop events not matching filter entries forward — The default action for the event log filter is to forward events not matching filter entries |
Description |
Displays the description string for the filter ID |
*A:ALA-48>config>log# show log filter-id 1001
==========================================================================
Log Filter
==========================================================================
Filter-id : 1001 Applied : yes Default Action: drop
Description : Collect events for Serious Errors Log
--------------------------------------------------------------------------
Log Filter Match Criteria
--------------------------------------------------------------------------
Entry-id : 10 Action : forward
Application : Operator : off
Event Number : 0 Operator : off
Severity : major Operator : greaterThanOrEqual
Subject : Operator : off
Match Type : exact string :
Router : Operator : off
Match Type : exact string :
Description : Collect only events of major severity or higher
--------------------------------------------------------------------------
==========================================================================
*A:ALA-48>config>log#
Label |
Description |
|---|---|
Entry-id |
Displays the event log filter entry ID |
Action |
default — There is no explicit action for the event log filter entry and the filter’s default action is used on matching events drop — The action for the event log filter entry is to drop matching events forward — The action for the event log filter entry is to forward matching events |
Description (Entry-id) |
Displays the description string for the event log filter entry |
Application |
Displays the event log filter entry application match criterion |
Event Number |
Displays the event log filter entry application event ID match criterion |
Severity |
cleared — The log event filter entry application event severity cleared match criterion indeterminate — The log event filter entry application event severity indeterminate match criterion critical — The log event filter entry application event severity critical match criterion major — The log event filter entry application event severity cleared match criterion minor — The log event filter entry application event severity minor match criterion warning — The log event filter entry application event severity warning match criterion |
Subject |
Displays the event log filter entry application event ID subject string match criterion |
Router |
Displays the event log filter entry application event ID router router-instance string match criterion |
Operator |
There is an operator field for each match criteria: application, event number, severity, and subject equal — Matches when equal to the match criterion greaterThanOrEqual — Matches when greater than or equal to the match criterion lessThan — Matches when less than the match criterion lessThanOrEqual — Matches when less than or equal to the match criterion notEqual — Matches when not equal to the match criterion off — No operator specified for the match criterion |
log-collector
Syntax
log-collector
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays log collector statistics for the main, security, change, and debug log collectors.
Output
The following output is an example of log collector information, and Output fields: log collector describes the output fields.
Sample outputA:ALA-1# show log log-collector
===============================================================================
Log Collectors
===============================================================================
Main Logged : 1224 Dropped : 0
Dest Log Id: 99 Filter Id: 0 Status: enabled Dest Type: memory
Dest Log Id: 100 Filter Id: 1001 Status: enabled Dest Type: memory
Security Logged : 3 Dropped : 0
Change Logged : 3896 Dropped : 0
Debug Logged : 0 Dropped : 0
===============================================================================
A:ALA-1#
Label |
Description |
|---|---|
<Collector Name> |
Main — The main event stream contains the events that are not explicitly directed to any other event stream Security — The security stream contains all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted Change — The change event stream contains all events that directly affect the configuration or operation of this node Debug — The debug-trace stream contains all messages in the debug stream |
Dest. Log ID |
Specifies the event log stream destination |
Filter ID |
The value is the index to the entry which defines the filter to be applied to this log's source event stream to limit the events output to this log's destination If the value is 0, then all events in the source log are forwarded to the destination |
Status |
Enabled — Logging is enabled Disabled — Logging is disabled |
Dest. Type |
Console — A log created with the console type destination displays events to the physical console device Events are displayed to the console screen whether a user is logged in to the console or not A user logged in to the console device or connected to the CLI via a remote Telnet or SSH session can also create a log with a destination type of 'session'. Events are displayed to the session device until the user logs off. When the user logs off, the 'session' type log is deleted Syslog — All selected log events are sent to the syslog address SNMP traps — Events defined as SNMP traps are sent to the configured SNMP trap destinations and are logged in NOTIFICATION-LOG-MIB tables File — All selected log events are directed to a file on one of the compact flash disks Memory — All selected log events are directed to an in-memory storage area |
log-id
Syntax
log-id [log-id] [severity severity-level] [application application] [sequence from-seq [to-seq]] [count count] [router router-instance [expression]] [subject subject [regexp]] [ascending | descending]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays an event log summary with settings and statistics or the contents of a specific log file, SNMP log, or memory log.
If the command is specified with no command line options, a summary of the defined system logs is displayed. The summary includes log settings and statistics.
If the log ID of a memory, SNMP, or file event log is specified, the command displays the contents of the log. Additional command line options control what and how the contents are displayed.
Contents of logs with console, session, or syslog destinations cannot be displayed. The actual events can only be viewed on the receiving syslog or console device.
Parameters
- log-id
Displays the contents of the specified file log or memory log ID. The log ID must have a destination of an SNMP or file log or a memory log for this parameter to be used.
- severity-level
Displays only events with the specified and higher severity.
- application
Displays only events generated by the specified application.
- expression
Specifies to use a regular expression as match criteria for the router instance string.
- from-seq [to-seq]
Displays the log entry numbers from a particular entry sequence number (from-seq) to another sequence number (to-seq). The to-seq value must be larger than the from-seq value.
If the to-seq number is not provided, the log contents to the end of the log is displayed unless the count parameter is present in which case the number of entries displayed is limited by the count.
- count
Limits the number of log entries displayed to the number specified.
- router-instance
Specifies a router name up to 32 characters to be used in the display criteria.
- subject
Displays only log entries matching the specified text subject string, up to 32 characters. The subject is the object affected by the event, for example the port-id would be the subject for a link-up or link-down event.
- regexp
Specifies to use a regular expression as parameters with the specified subject string.
- ascending | descending
Specifies sort direction. Logs are normally shown from the newest entry to the oldest in descending sequence number order on the screen. When using the ascending parameter, the log are shown from the oldest to the newest entry.
Output
The following outputs are examples of event log information, and the associated tables describe the output fields.
Sample outputA:ALA-1# show log log-id
=====================================================================
Event Logs
=====================================================================
Log Source Filter Admin Oper Logged Dropped Dest Dest Size
Id Id State State Type Id
--------------------------------------------------------------------
1 none none up down 52 0 file 10 N/A
2 C none up up 41 0 syslog 1 N/A
99 M none up up 2135 0 memory 500
=====================================================================
A:ALA-1#
Label |
Description |
|---|---|
Log Id |
Displays the event log destination |
Source |
no — The event log filter is not currently in use by a log ID yes — The event log filter is currently in use by a log ID |
Filter ID |
Displays the index to the entry which defines the filter to be applied to this log's source event stream to limit the events output to this log's destination. If the value is 0, then all events in the source log are forwarded to the destination. |
Admin State |
Up — Indicates that the administrative state is up Down — Indicates that the administrative state is down |
Oper State |
Up — Indicates that the operational state is up Down — Indicates that the operational state is down |
Logged |
Displays the number of events that have been sent to the log sources that were forwarded to the log destination |
Dropped |
Displays the number of events that have been sent to the log sources that were not forwarded to the log destination because they were filtered out by the log filter |
Dest. Type |
Console — All selected log events are directed to the system console. If the console is not connected, all entries are dropped. Syslog — All selected log events are sent to the syslog address SNMP traps — Events defined as SNMP traps are sent to the configured SNMP trap destinations and are logged in NOTIFICATION-LOG-MIB tables File — All selected log events are directed to a file on one of the compact flash disks Memory — All selected log events are directed to an in-memory storage area |
Dest ID |
Displays the event log stream destination |
Size |
Displays the allocated memory size for the log |
Time format |
Displays the type of timestamp format for events sent to logs where log ID destination is either syslog or file. When the time format is UTC, timestamps are written using the Coordinated Universal Time value. When the time format is local, timestamps are written in the system's local time. |
A:gal171# show log log-id 99
===============================================================================
Event Log 99
===============================================================================
Description : Default System Log
Memory Log contents [size=500 next event=70 (not wrapped)]
69 2007/01/25 18:20:40.00 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
68 2007/01/25 17:48:38.16 UTC WARNING: SYSTEM #2006 Base LOGGER
"New event throttle interval 10, configuration modified"
67 2007/01/25 00:34:53.97 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
66 2007/01/24 22:59:22.00 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
65 2007/01/24 02:08:47.92 UTC CRITICAL: SYSTEM #2029 Base Redundancy
"The active CPM card A is operating in singleton mode. There is no standby CPM card
."
...
===============================================================================
A:gal171
A:NS061550532>config>log>snmp-trap-group# show log log-id 1
===============================================================================
Event Log 1
===============================================================================
SNMP Log contents [size=100 next event=3 (not wrapped)]
Cannot send to SNMP target address 10.1.1.1.
14 2000/01/05 00:54:09.11 UTC WARNING: MPLS #2007 Base VR 1:
"Instance is in administrative state: inService, operational state: inService"
13 2000/01/05 00:54:09.11 UTC WARNING: MPLS #2008 Base VR 1:
"Interface linkToIxia is in administrative state: inService, operational state: inSe
rvice"
....
===============================================================================
A:NS061550532>config>log>snmp-trap-group#
snmp-trap-group
Syntax
snmp-trap-group [log-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays SNMP trap group configuration information.
Parameters
- log-id
Displays only SNMP trap group information for the specified trap group log ID.
Output
The following output is an example of SNMP trap group configuration information, and Output fields: SNMP trap group describes the output fields.
Sample SNMP trap group outputA:SetupCLI>config>log>snmp-trap-group# show log snmp-trap-group 44
===============================================================================
SNMP Trap Group 44
===============================================================================
Description : none
-------------------------------------------------------------------------------
Name : ntt-test
Address : 10.10.10.3
Port : 162
Version : v2c
Community : ntttesting
Sec. Level : none
-------------------------------------------------------------------------------
Name : test2
Address : 10.20.20.5
Port : 162
Version : v2c
Community : ntttesting
Sec. Level : none
===============================================================================
A:SetupCLI>config>log>snmp-trap-group#
Label |
Description |
|---|---|
Log-ID |
Displays the log destination ID for an event stream |
Address |
Displays the IP address of the trap receiver |
Port |
Displays the destination UDP port used for sending traps to the destination, expressed as a decimal integer |
Version |
Specifies the SNMP version format to use for traps sent to the trap receiver. Valid values are snmpv1, snmpv2c, snmpv3. |
Community |
Displays the community string required by snmpv1 or snmpv2c trap receivers |
Security-Level |
Displays the required authentication and privacy levels required to access the views on this node |
syslog
Syntax
syslog [syslog-id]
Context
show>log
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command displays syslog event log destination summary information or detailed information about a specific syslog destination.
Parameters
- syslog-id
Displays detailed information about the specified syslog event log destination.
Output
The following output is an example of syslog event log destination information, and Output fields: syslog describes the output fields.
Sample output*A:ALA-48>config>log# show log syslog
===============================================================================
Syslog Target Hosts
===============================================================================
Id Ip Address Port Sev Level
Below Level Drop Facility Pfx Level
-------------------------------------------------------------------------------
2 unknown 514 info
0 local7 yes
3 unknown 514 info
0 local7 yes
5 unknown 514 info
0 local7 yes
10 unknown 514 info
0 local7 yes
===============================================================================
*A:ALA-48>config>log#
*A:MV-SR>config>log# show log syslog 1
===============================================================================
Syslog Target 1
===============================================================================
IP Address : 192.168.15.22
Port : 514
Log-ids : none
Prefix : Sr12
Facility : local1
Severity Level : info
Prefix Level : yes
Below Level Drop : 0
Description : Linux Station Springsteen
===============================================================================
*A:MV-SR>config>log#
Label |
Description |
|---|---|
Syslog ID |
Displays the syslog ID number for the syslog destination |
IP Address |
Displays the IP address of the syslog target host |
Port |
Displays the configured UDP port number used when sending syslog messages |
Facility |
Displays the facility code for messages sent to the syslog target host |
Severity Level |
Displays the syslog message severity level threshold |
Below Level Dropped |
Displays a count of messages not sent to the syslog collector target because the severity level of the message was above the configured severity The higher the level, the lower the severity |
Prefix Present |
Yes — A log prefix was prepended to the syslog message sent to the syslog host No — A log prefix was not prepended to the syslog message sent to the syslog host |
Description |
Displays a text description stored in the configuration file for a configuration context |
LogPrefix |
Displays the prefix string prepended to the syslog message |
Log-id |
Displays the destination to which events are directed |
Clear commands
log
Syntax
log log-id
Context
clear
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command reinitializes the specified memory/file event log ID. Memory logs are reinitialized and cleared of contents. File logs are manually rolled over by this command.
This command is only applicable to event logs that are directed to file destinations and memory destinations.
SNMP, syslog, and console/session logs are not affected by this command.
Parameters
- log-id
Specifies the event log ID to be initialized/rolled over.