FIPS-140 mode
Starting in Release 24.3.R3, SR OS is in the process of obtaining the FIPS-140-3 certification with the Crypto Module Version (CMV) SRCM 5.0. After the certificate is obtained, all SR OS releases with CMV SRCM 5.0 can be considered to be FIPS-approved. You can use the show system information command to display the CMV.
The system can be configured in FIPS mode using the fips-140 flag in the BOF. See Booting up the system in FIPS mode.
Not all SR OS releases are FIPS certified. The FIPS-certified SR OS CMV is listed on the National Institute of Standards and Technology (NIST) website. The uncertified releases can operate in FIPS-140 mode.
FIPS operating environment
The SR OS FIPS certification extends over multiple minor or major releases. The system software is FIPS certified against an operating kernel (OK) “TiMOS SMP Kernel Version 2.5”, which does not change. The OK contains a Cryptographic Module (also known as Crypto Module) version (CMV).
The CMV contains the FIPS Provider version (FPV) and the Entropy Source version (ESV). The CMV changes when any of its components change. For example, if the FPV changes to 3.1, the CMV changes to 5.1. If the ESV changes, the CMV changes also.
The FIPS certification is valid for a specified OK version and CMV. Software images that do not contain the certified OK and CMV are not officially FIPS certified. The user must check the NIST website to identify the FIPS-certified OK and CMV.
Displaying the OK and the CMV
The OK and the CMV are displayed only on systems that support the FIPS mode and are configured in FIPS mode. The CMV, FPV, and ESV are displayed on systems supporting FIPS when the systems are in FIPS mode. The systems that do not support the FIPS mode do not display all the information.
When the system is in FIPS mode, the show system information command displays the CMV, FPV and ESV.
The following example shows the FIPS operating environment information on a system in FIPS mode.
System in FIPS mode
===================================================================
System Information
===================================================================
System Name : system-1
System Type : <system-type>
Chassis Topology : Standalone
System Version : <system-version>
Kernel Version : TiMOS SMP version 2.5
Crypto Module Version : SRCM 5.0
FIPS-Provider Version: 3.1.5-nokia.1.0
Entropy Source Version: 3.4.1-nokia.1.0
...The following is the corresponding MD-CLI state information.
MD-CLI state information about the FIPS operating environment on a system in FIPS mode
[/state system]
A:admin@node-2# info
...
crypto-module {
crypto-module-version "SRCM 5.0"
fips-provider-version "3.1.5-nokia.1.0"
entropy-source-version "3.4.1-nokia.1.0"
}The following is an example of operating environment information on a system that is not in FIPS mode.
Operating environment information on a system that is not in FIPS mode
===================================================================
System Information
===================================================================
System Name : system-2
System Type : <system-type>
Chassis Topology : Standalone
System Version : <system-version>
Kernel Version : TiMOS SMP version 2.5
Crypto Module Version :
FIPS-Provider Version:
Entropy Source Version: 3.4.1-nokia.1.0
The following is the corresponding MD-CLI state information of the preceding system example.
MD-CLI state information about the operating environment on a system that is not in FIPS mode
[/state system]
A:admin@node-2# info
...
crypto-module {
entropy-source-version "3.4.1-nokia.1.0"
}
Booting up the system in FIPS mode
To start using the system in FIPS mode, perform the following steps:
- Use the following command to configure the fips-140 flag in the
BOF:
- MD-CLI
bof system fips-140 - classic
CLI
bof fips-140
- MD-CLI
- Save the BOF.
- Reboot the system.
- Starting in Release 24.10.R1, a digital signature (DS) validation using SHA256 is performed for upgrades on the image and the .tim files. See FIPS image upgrade validation using a DS.
Supported algorithms in FIPS mode
When the system is configured in FIPS mode, the ciphers and hash algorithms that are not FIPS approved are removed from the SSH and TLS protocols. The FIPS certificate security target on the NIST website provides all the supported ciphers, hash, HMAC, and signature algorithms.
FIPS image upgrade validation using a DS
When upgrading to a new image, the National Information Assurance Partnership's (NIAP) collaborative Network Device Protection Profile (NDcPP) requires the new image be verified using a digital signature (DS). For more information about the SR OS DS environment, see Digital signature.
The NIAP functionality is available when the SR OS is configured in FIPS-140 mode. NIAP testing was performed with the SR OS in FIPS-140 mode. When a node is in the FIPS-140 mode of operation in accordance with the FIPS-140-3 certification requirements, it validates the image using a DS before it uses the image for the upgrade. For more information, see DS verification. If the DS of the image does not validate, the node does not upgrade to the new primary image.
Digital signature
The following figure shows the components of the SR OS digital signature (DS) environment.
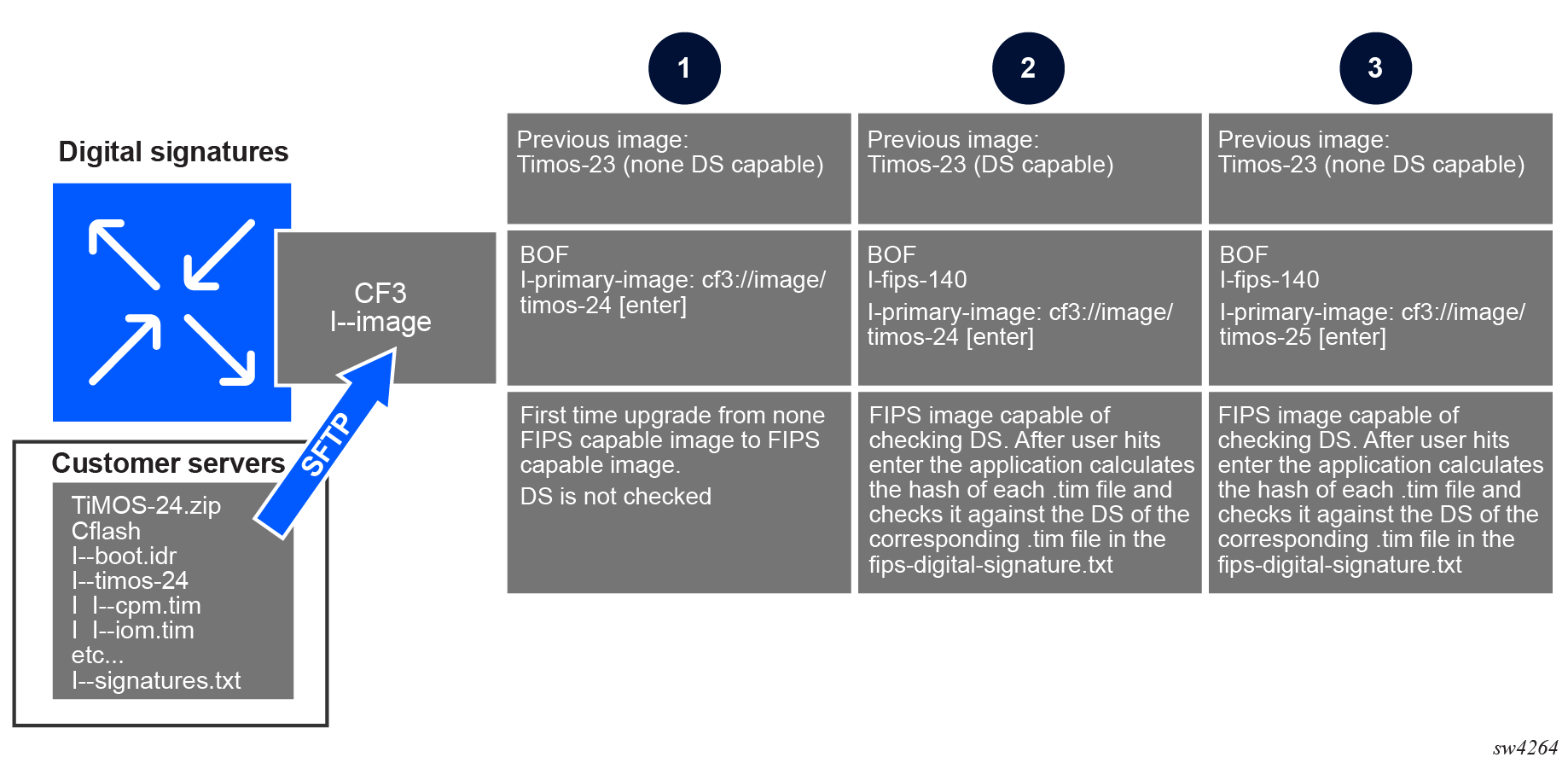
For the FIPS and NIAP validation of new SR OS images, the hash over different .tim files is calculated using SHA256 at Nokia premises. This hash is then encrypted using an RSA key pair (private key) with a key size of 2K. The encrypted hash is known as DS.
The compact flash (CF) image downloaded from the Nokia servers contains a file named signatures.txt, which contains the DSs of selected .tim files and the public key to validate these DSs.
DS verification
The following figure shows the DS verification components.
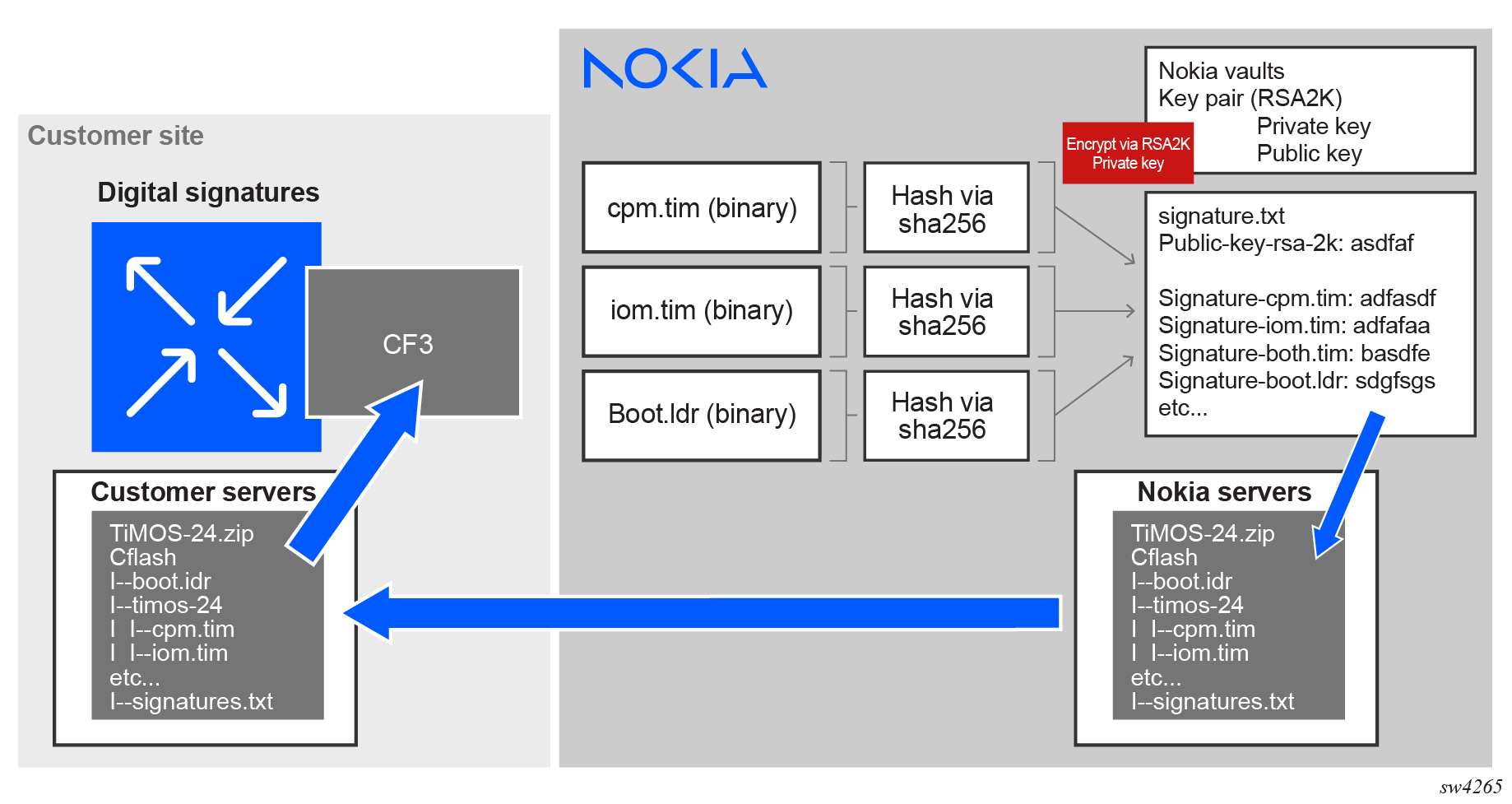
After the TiMOS .zip file with DS capabilities is downloaded from the SR OS servers, the cflash directory must be transferred to the system’s CF. The user should ensure that the transfer is secure.
Nokia does not recommend, nor support upgrading to a new image using FTP. The image must be located on the CF.
After transferring the cflash to the CF, the system must be upgraded to the FIPS-140 image before configuring the fips-140 flag in the BOF. After the upgrade, to use the system in FIPS-140 mode, the user must first run the admin command to validate the image DS. Then, after the DS is validated, the user must enable the FIPS mode by configuring the fips-140 flag in the BOF. If the DS check fails, the system is not allowed to enter the FIPS-140 mode.
After upgrading to the FIPS image and entering the FIPS mode, any time the user wants to upgrade the system again, the DS of the .tim files must be validated first using the corresponding admin command. Use the following command to validate the DS before proceeding with the upgrade:
- MD-CLI
admin system security image-digital-signature validate software-image url - classic
CLI
admin system security image-digital-signature-validate url
The parameter of the preceding command specifies the URL of the software image location. If the DS validation passes, the URL is accepted and the image can be upgraded. If the validation does not pass, the primary image is rejected and the system is not upgraded. The system verifies the DS using SHA256 on the .tim files and compares this hash with the corresponding hash that is stored in the signatures.txt file. The hash in the signatures.txt file is decrypted using the public key. If the two hashes match, the .tim file is validated. This process is repeated for all selected .tim files that must be updated on the system.
DS support for files
- cpm.tim
- both.tim
- iom.tim
- boot.ldr
- support.tim
- kernel.tim
- hypervisor.tim
- isa-aa.tim
DS file directories
The following directories and files must be in the same directory as the .tim image files.
- signatures.txt
-
- cflash directory:
- cflash/TiMOS-SR-version/signatures.txt
- cflash/TiMOS-SR-version/signatures-isa-aa.txt
- cflash directory:
- cflash-nl (No-LI version)
- SAR-Hm
- VSR-VMware, VSR-KVM, VSR-Container, VSIM-VMware, VSIM-KVM
- vm-nl (No-LI VM)
- pysros, PROTOBUF, MIBs, YANG
DS verification when configuring the fips-140 flag in the BOF
When the attempt is made to configure the fips-140 flag in the BOF, the system verifies the DS of the selected .tim files. If the DS verification fails, the flag cannot be configured in the BOF, the system does not enter FIPS-140 mode, and a security log is generated.
To check the DS of the image, use the following command:
- MD-CLI
admin system security image-digital-signature validate software-image - classic
CLI
admin system security image-digital-signature-validate
The command caches the result of the DS verification. While the DS verification is in progress, the fips-140 flag cannot be configured in the BOF. You must wait for the DS verification to be completed on the image. After the verification passes, the fips-140 flag can be configured in the BOF and the system can be rebooted into FIPS mode.
DS verification for ISA-AA
When the system is in FIPS mode, ISA-AA is part of the DS verification. See the mechanism described in DS verification when configuring the fips-140 flag in the BOF.
Checking a file DS
In FIPS mode, you can use the file version url check command to check the DS of the .tim file located at the specified URL. If the DS check fails, a message is displayed.
Upgrade procedure to a FIPS image
Ensure that the signatures.txt file is synchronized between the CPMs. The signatures.txt file and the DS verification are only required in FIPS mode; they are not required in non-FIPS mode.
This procedure describes how to upgrade from a non-FIPS image to a FIPS image with DS for the first time.
- SFTP the context of the software bundle to the active CF3. The signatures.txt file is copied to the active CF3 as part of this transfer.
- Perform an admin redundancy synchronization to ensure all files are synchronized between the active and standby CF3. An image that does not support the signatures.txt file and the DS verification does not synchronize the signatures.txt file to the standby CF3. (Such an image has no understanding that the signatures.txt file is a critical component that must be synchronized between the two CPMs.)
- After upgrading to the FIPS release, the signatures.txt file will not be present on the standby CF3. Before enabling the FIPS-140 mode, perform an admin redundancy synchronization to copy the signatures.txt file to the standby CF3. After this step, both CPMs have the signatures.txt file and you can enable the FIPS-140 mode in the BOF.