L2TPV3 tunnels
L2TPv3 overview
Layer 2 Tunneling Protocol version 3 (L2TPv3) is a mechanism for the tunneling of Ethernet traffic over an IP network. For this application, the ISA functions as a resource module for the system, performing the L2TPv3 encapsulation and decapsulation functions.
L2TPv3 support for IP transport shows L2TPv3 support for the IP transport model. L2TPv3 support for IP transport — tunnel processing steps describes the tunnel processing steps in the figure.
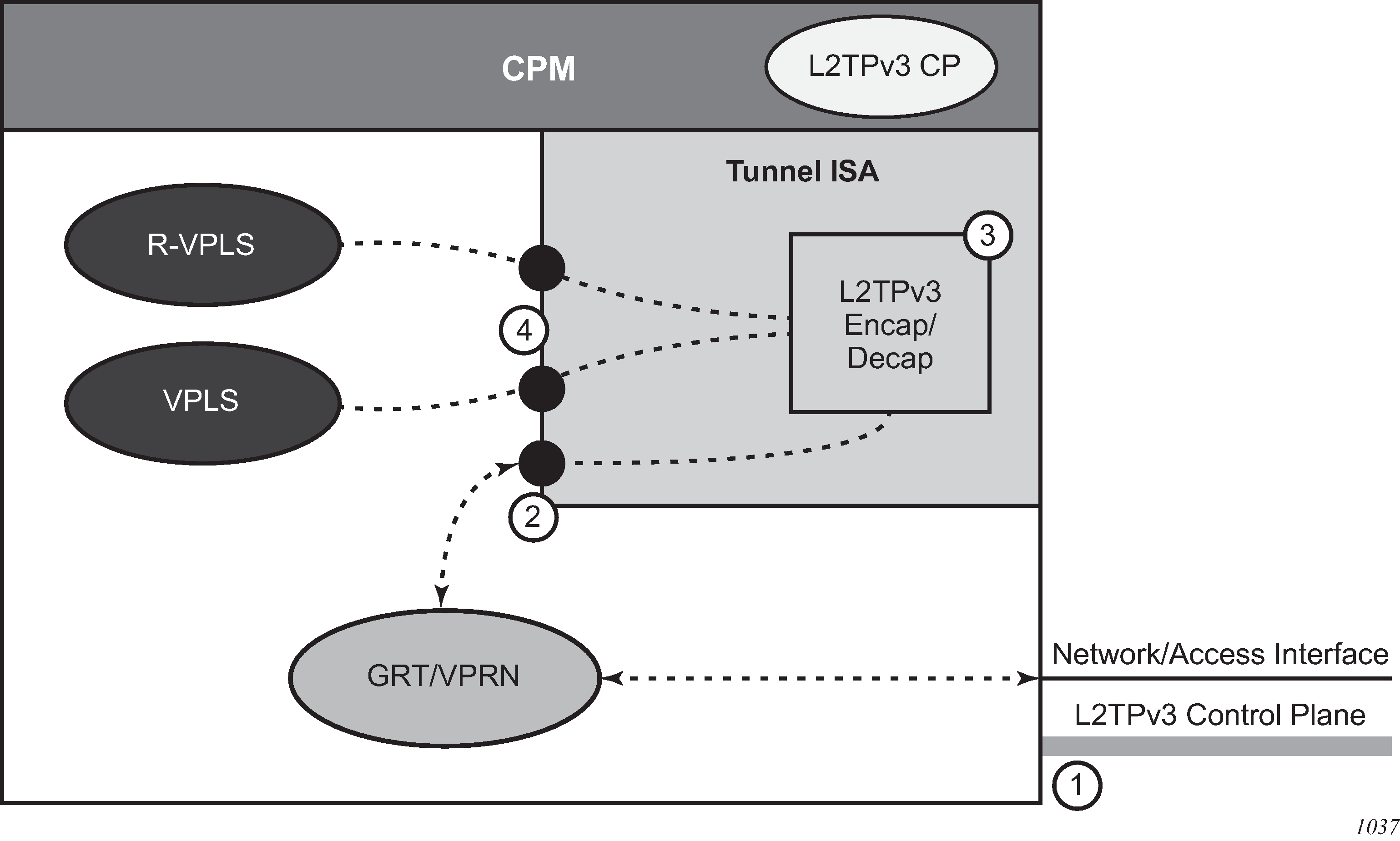
| Step number | Description |
|---|---|
1 |
The L2TPv3 control plane can run within either the base routing or VPRN contexts. |
2 |
L2TPv3 encapsulated packets ingress and egress through the public interface, which can be in either the base routing or VPRN contexts. |
3 |
L2TPv3 encapsulation and decapsulation processing is handled within the tunnel ISA. |
4 |
Unencapsulated packets pass between the tunnel ISA and the associated service via the configured private SAP. |
Control plane
The configuration of the L2TPv3 control plane is similar to that of L2TPv2. A number of the same commands are used for both, but there are new commands specific to L2TPv3. The L2TPv3-specific commands are located in a separate L2TPv3 context in both the general configuration area as well as within the group configuration context.
L2TPv3 control plane command options can be configured at the global level within the configure router l2tp context, which may include some L2TPv3-specific command options. This should be used for command options that are the same for the majority of L2TPv3 tunnels. The same command options can be configured on a per-tunnel group basis. The tunnel group can be configured within either the base router context or a VPRN service context.
The following example displays an L2TPv3 tunnel group configured within the base routing context.
MD-CLI
[ex:/configure router "Base" l2tp]
A:admin@node-2# info
l2tpv3 {
cookie-length 8
digest-type sha1
nonce-length 64
transport-type {
ip true
}
}
group "base l2tpv3 left" {
admin-state enable
protocol v3draft
password "AbkdpF.rY1FgcK4qAYmimsykdmwbAucq hash2"
avp-hiding never
l2tpv3 {
password "rhXAlJTUjuliBn8lVUfKJywztX9cKOEb/rbWUR/e4ow hash2"
pw-cap-list {
ethernet true
ethernet-vlan true
}
}
ethernet-tunnel {
reconnect-timeout 60
}
tunnel "base l2tpv3 tunnel" {
admin-state enable
peer 192.168.0.100
local-address 172.16.0.100
}
}classic CLI
A:node-2>config>router>l2tp# info
----------------------------------------------
l2tpv3
cookie-length 8
digest-type sha1
nonce-length 64
transport-type ip
exit
group "base l2tpv3 left" protocol v3draft create
avp-hiding never
eth-tunnel
reconnect-timeout 60
exit
l2tpv3
pw-cap-list ethernet ethernet-vlan
password "AbkdpF.rY1FgcK4qAYmimsykdmwbAucq" hash2
exit
password "rhXAlJTUjuliBn8lVUfKJywztX9cKOEb/rbWUR/e4ow" hash2
tunnel "base l2tpv3 tunnel" create
local-address 172.16.0.100
peer 192.168.0.100
no shutdown
exit
no shutdown
exit
----------------------------------------------
Public SAP
The public SAP is the access interface to the L2TPv3 tunnel over which encapsulated traffic is sent to or received from the far end. The IP address bound to this SAP is on the same subnet as the local L2TPv3 tunnel endpoint.
The public SAP must be configured in the same routing context as the L2TPv3 tunnel group configuration. As shown in L2TPv3 support for IP transport, the public SAP can be associated with an IES or VPRN service to connect to the outside or public access network.
The following example displays an L2TPv3 public SAP configured within the base routing context.
MD-CLI
[ex:/configure service ies "10"]
A:admin@node-2# info
customer "1"
interface "l2tp-public-interface" {
sap tunnel-1.public:2 {
}
ipv4 {
primary {
address 172.16.0.1
prefix-length 24
}
}
}classic CLI
A:node-2>config>service# info
----------------------------------------------
ies 10
interface "l2tp-public-interface" create
address 172.16.0.1/24
sap tunnel-1.public:2 create
exit
exit
----------------------------------------------
Private SAP
The private SAP is the access interface to the L2TPv3 over which unencapsulated traffic is sent to or received from the far end. The public SAP must be configured within an Ethernet service, such as an Epipe, VPLS, or I-VPLS service.
The private SAP configuration includes the configuration of the following L2TPv3 session command options:
-
VC-ID
-
PW-Type
-
L2TPv3 tunnel group association
The following example displays an L2TPv3 private SAP configured within the base routing context.
MD-CLI
[ex:/configure service vpls "100"]
A:admin@node-2# info
admin-state enable
customer "1"
sap tunnel-1.private:100 {
l2tpv3-session {
admin-state enable
vc-id 100
pseudo-wire {
ethernet
}
router {
group "base l2tpv3 left"
router-instance "2"
}
}
}
classic CLI
A:node-2>config>service>vpls$ info
----------------------------------------------
sap tunnel-1.private:100 create
l2tpv3-session create
router group "base l2tpv3 left" service-name "2"
vc-id 100
pw-type ethernet
no shutdown
exit
no shutdown
exit
no shutdown
----------------------------------------------