RADIUS authentication attributes
Subscriber host identification
Attributes related to subscriber-host configuration included in RADIUS authentication request and response.
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
Refers to the user to be authenticated in the Access-Request. The format for IPoE/PPPoE hosts depends on configuration parameters pppoe-access-method, ppp-user-name, or user-name-form at in the CLI context configure subscriber-mgmt authentication-policy name. The format for ARP-hosts is not configurable and always the host IPv4-address. The format for S11 GTP Sessions is based on the PAP username signaled in the Protocol Configuration Options (PCO) in the GTP Create Session Request message, if no PAP username is present the username is based on the gtp-user-name configuration under configure subscriber-mgmt authentication-policy name. The RADIUS User-Name specified in an Access-Accept or CoA is reflected in the corresponding accounting messages. |
|
2 |
User-Password |
The password of the user to be authenticated, or the user's input following an Access-Challenge. For PPPoE users it indirectly maps to the password provided by a PPPoE PAP user in response to the PAP Authenticate-Request. For IPoE/ARP hosts it indirectly maps to a preconfigured password (configure subscriber-mgmt authentication policy name password password or configure aaa isa-radius-policy name password password). |
|
3 |
CHAP-Password |
Provided by a PPPoE CHAP user in response to the CHAP challenge. The CHAP challenge sent by the NAS to a PPPoE CHAP user is part of the CHAP authentication sequence RFC 1994, PPP Challenge Handshake Authentication Protocol (CHAP), (Challenge, Response, Success, Failure). The user generated CHAP password length is equal to the defined Limits and contains a one byte CHAP-Identifier from the user's CHAP Response followed by the CHAP Response from the user. |
|
4 |
NAS-IP-Address |
The identifying IP Address of the NAS requesting the Authentication. Included when the RADIUS server is reachable using IPv4. The address is determined by the routing instance through which the RADIUS server can be reached: ‟Management” — the active IPv4 address in the Boot Options File (bof address ipv4-address) ‟Base” or ‟VPRN” — the IPv4 address of the system interface (configure router interface system address address) The address can be overwritten with the configured source-address (configure aaa radius-server-policy policy-name servers source‑address ip-address). |
|
5 |
NAS-Port |
The physical access-circuit on the NAS which is used for the Authentication of the user. The format of this attribute is configurable on the NAS as a fixed 32 bit value or a parameterized 32 bit value. The parameters can be a combination of outer and inner vlan ID, slot number, MDA number, port number, lag-id, pw-id, pxc‑id, pxc-subport and fixed bit values (zero or one) but cannot exceed 32 bits. The format can be configured for following applications: configure router l2tp cisco-nas-port, configure service vprn service-id l2tp cisco-nas-port, configure subscriber-mgmt authentication-policy name include-radius-attribute nas-port. |
|
6 |
Service-Type |
The type of service the PPPoE user has requested, or the type of service to be provided for the PPPoE user. Optional in RADIUS-Accept and CoA. Treated as a session setup failure if different from Framed-User. |
|
7 |
Framed-Protocol |
The framing to be used for framed access in case of PPPoE users. Optional in RADIUS-Accept and CoA. Treated as a session setup failure if different from PPP. |
|
8 |
Framed-IP-Address |
The IPv4 address to be configured for the host using DHCPv4 (RADIUS proxy), IPCP (PPPoE), or data-triggered subscriber management.[8] Framed-IP-Address with value 255.255.255.254 is ignored in RADIUS Access-Accept (the NAS should select an address for the user). See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. Attribute is also used in CoA and Disconnect messages (part of the ESM or AA user identification key). |
|
9 |
Framed-IP-Netmask |
The IP netmask to be configured for the user when the user is a router to a network. For DHCPv4 users, the attribute maps to DHCPv4 option [1] Subnet mask and is mandatory for numbered subscriber hosts if [8] Framed-IP-Address is also returned. A subnet mask is autogenerated for unnumbered subscriber hosts when not obtained from authentication. For PPPoE residential access, the attribute should be set to 255.255.255.255 (also the default value if the attribute is omitted). For PPPoE business access, the attribute maps to PPPoE IPCP option [144] Subnet-Mask only when the user requests this option and if the node parameter configure subscriber-mgmt ppp-policy ppp-policy-name ipcp-subnet-negotiation is set. |
|
18 |
Reply-Message |
Text that may be displayed to the user by a PPPoE client as a success, failure or dialog message. It is mapped to the message field from the PAP/CHAP authentication replies to the user. Omitting this attribute results in standard reply messages: login ok and login incorrect for PAP, CHAP authentication success and CHAP authentication failure for CHAP. String length greater than the defined Limits are accepted but truncated at this boundary. |
|
22 |
Framed-Route |
Routing information (IPv4 managed route) to be configured on the NAS for a host (DHCP, PPPoE, ARP, or data-triggered) that operates as a router without NAT (routed subscriber host). The route included in the Framed-Route attribute is accepted as a managed route only if its next-hop points to the hosts ip-address, if the next-hop address equals 0.0.0.0, or if the included route is a valid classful network, in which case the subnet-mask is omitted. If neither is applicable, this specific framed-route attribute is ignored and the host is instantiated without this specific managed route installed. A Framed-Route attribute is also ignored if the SAP does not have anti-spoof configured to nh-mac (the host is installed as a standalone host without a managed route). Any routes above the configured Limits are silently ignored. Optionally, a metric, tag or protocol preference can be specified for the managed route. If the metrics are not specified, specified in a wrong format, or specified with out-of-range values, then the default values are used for all metrics: metric=0, no tag and preference=0. If an identical managed route is associated with different routed subscriber hosts in the context of the same IES/VPRN service up to max-ecmp-routes managed routes are installed in the routing table (configured as ecmp max-ecmp-routes in the routing instance). Candidate ECMP Framed-Routes have identical prefix, equal lowest preference and equal lowest metric. The ‟lowest ip next-hop” is the tie breaker if more candidate ECMP Framed-Routes are available than the configured max-ecmp-routes. Other identical managed routes are shadowed (not installed in the routing table) and an event is logged. An alternative to RADIUS managed routes are managed routes using host dynamic BGP peering. Valid RADIUS learned managed routes can be included in RADIUS accounting messages. |
|
25 |
Class |
Attribute sent by the RADIUS server to the NAS in an Access-Accept or CoA and is sent unmodified by the NAS to the Accounting server as part of the Accounting-Request packet. Strings with a length longer than the defined Limits are accepted but truncated to this boundary. |
|
27 |
Session-Timeout |
Sets the maximum number of seconds of service provided to the user (IPoEv4 host, PPPoE or IPoE session) before termination of the session. The attribute equals [26.6527.160] Alc-Relative-Session-Timeout when received in Access-Accept because the current session time portion is then equal to zero. Value zero sets the session-timeout to infinite (no session-timeout). The attribute is CoA NAK'd if its value is smaller than the current-session time. Simultaneous received [27] Session-Timeout and [26.6527.160] Alc-Relative-Session-Timeout are treated as an error condition (setup failure if received using Access-Accept and NAK’d if received using CoA). With IPoE session disabled for IPoEv4 radius proxy and CoA create-host scenarios, [27] Session-Timeout is interpreted as lease-time instead of session-time if [26.6527.174] Alc-Lease-Time is omitted. For WLAN-GW group interfaces, the interpretation of the Session-Timeout attribute is configured with: configure service ies | vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlangw ipoe-session radius-session-timeout {backwardscompatible | ignore | absolute}. |
|
28 |
Idle-Timeout |
Sets the maximum number of consecutive seconds of idle connection allowed to the user before termination of the session (IPoE/PPPoE) or a connectivity check is triggered (IPoE). Values outside the allowed Limits are accepted but rounded to these boundaries. A value of zero is treated as an infinite idle-timeout. The idle-timeout handling on the node is implemented using category-maps (configure subscriber-mgmt category-map category-map-name and configure subscriber-mgmt sla-profile sla-profile-name category-map category‑map‑name). |
|
30 |
Called-Station-Id |
Allows the NAS to send in an Access Request with respect to the user called. Attribute is omitted in authentication using: configure subscriber-mgmt authentication-policy name include-radius attribute no called-station-id. Supported applications:
|
|
31 |
Calling-Station-Id |
Allows the NAS to send unique information identifying the user who requested the service. This format is driven by configuration (configure subscriber-mgmt authentication-policy name include-radius-attribute calling-station-id <llid | mac | remote-id | sap-id | sap-string>). The LLID (logical link identifier) is the mapping from a physical to logical identification of a subscriber line and supplied by a RADIUS llid-server. The sap-string maps to configure service ies | vprn service-id subscriber-interface ip-int-name group-interface ip-int-name sap sap-id calling-station-id sap-string. A [31] Calling-Station-Id attribute value longer than the allowed maximum is treated as a setup failure. The attribute is omitted in authentication using configure subscriber-mgmt authentication-policy name include-radius-attribute no calling-station-id. |
|
32 |
NAS-Identifier |
A string (configure system name system-name) identifying the NAS originating the Authentication requests and sent when configured: include-radius-attribute nas-identifier in configure subscriber-mgmt authentication-policy |
|
44 |
Acct-Session-Id |
A unique identifier that represents the subscriber host or session that is authenticated. This attribute can be used as CoA or Disconnect Message key to target the host or session and is reflected in the accounting messages for this host or session. The attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute acct-session-id [host | session]. For PPPoE, either the host acct-session-id (default) or the session acct-session-id is included. |
|
60 |
CHAP-Challenge |
The CHAP challenge sent by the NAS to a PPPoE CHAP user as part of the chap authentication sequence RFC 1994 (Challenge, Response, Success, Failure). The generated challenge length for each new pppoe session is by default a random value from 32 to 64 bytes unless configured different under configure subscriber-mgmt ppp-policy ppp-policy-name ppp-chap-challenge-length [8 to 64] or configure service vprn service-id | router l2tp group tunnel-group-name ppp chap-challenge-length [8 to 64] for LNS (the command can also be specified at the tunnel level). The CHAP challenge value is copied into the request-authenticator field of the RADIUS Access-Request message if the minimum and maximum value is configured at exact 16 (RFC 2865, Remote Authentication Dial In User Service (RADIUS), section 2.2, Interoperation with PAP and CHAP). Attribute CHAP-Password is provided by a PPPoE CHAP user in response to the [60] CHAP-challenge. |
|
61 |
NAS-Port-Type |
The type of the physical port of the NAS which is authenticating the user and value automatically determined from subscriber SAP encapsulation. It can be overruled by configuration. Included if include-radius-attribute nas-port-type is configured in: configure subscriber-mgmt authentication-policy . Checked for correctness if returned in CoA. The NAS-Port-Type attribute is always included when the Nas-Port-Id is also included. |
|
85 |
Acct-Interim-Interval |
The interval, in seconds, at which Acct-Interim-Update messages should be generated for the first RADIUS Accounting Policy in the subscriber profile. Overrides the local configured update-interval value in the RADIUS accounting policy. This only takes effect if interim-updates are enabled for one of the accounting modes in the RADIUS Accounting Policy. An attribute value of 0 disables the generation of Acct-Interim-Update messages. Attribute [85] Acct-Interim-Interval takes precedence over [26.6527.232] Alc-Acct-Interim-IvI with tag 1 when both are included. Attribute values outside the allowed limits are accepted but are rounded to the minimum or maximum limit. |
|
87 |
NAS-Port-Id |
A text string which identifies the physical/logical port of the NAS which is authenticating the user. Attribute is also used in CoA and Disconnect Message (part of the user identification-key). See [87] NAS-Port-Id attribute details for a detailed description of the attribute format. The NAS-Port-Id can have an optional prefix-string (max 8 chars) and suffix-string (max 64 chars) added (configure subscriber-mgmt authentication-policy name include-radius-attribute nas-port-id [prefix-string string] [suffix circuit-id | remote-id]). Included only if include-radius-attribute nas-port-id is configured: configure subscriber-mgmt authentication-policy. For a capture-sap, the nas-port-id attribute is always included in authentication requests. |
|
88 |
Framed-Pool |
The name of one address pool or the name of a primary and secondary address pool separated with a one character configurable delimiter (configure router/service vprn service-id dhcp local-dhcp-server server-name use-pool-from-client delimiter delimiter) that should be used to assign an address for the user and maps to either: 1) dhcpv4 option [82] vendor-specific-option [9] sub-option [13] dhcpPool if option is enabled on the node (configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name dhcp option vendor-specific-option pool-name) or 2) used directly as pool-name in the local configured dhcp server when local-address-assignment is used and client-application is ppp-v4 (configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name local-address-assignment). Alternative to [26.2352.36] Ip-Address-Pool-Name and [26.4874.2] ERX-Address-Pool-Name. Framed-Pool names longer than the allowed maximum are treated as host setup failures. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. |
|
95 |
NAS-IPv6-Address |
The identifying IP Address of the NAS requesting the Authentication. Included when the RADIUS server is reachable using IPv6. The address is determined by the routing instance through which the RADIUS server can be reached: ‟Management” — The active IPv6 address in the Boot Options File (bof address ipv6-address). ‟Base” or ‟VPRN” — The IPv6 address of the system interface (configure router interface system ipv6 address ipv6-address). The address can be overwritten with the configured ipv6-source-address (configure aaa radius-server-policy policy-name servers ipv6-source-address ipv6-address). |
|
97 |
Framed-IPv6-Prefix |
The IPv6 prefix or prefix length to be configured using SLAAC (Router Advertisement) to the WAN side of the user. Any non /64 prefix-length for SLAAC host creation is treated as a session setup failure for this host. This attribute is an alternative to [100] Framed-IPv6-Pool and [26.6527.99] Alc-IPv6-Address, which assigns IPv6 addressing to the wan-side of a host using DHCPv6 IA-NA. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. Attribute is also used in CoA and Disconnect Message (part of the ESM or AA user identification-key). |
|
99 |
Framed-IPv6-Route |
Routing information (IPv6 managed route) that is configured on the NAS for an IPv6 WAN host (IPoE or PPPoE) that operates as a router. The functionality is comparable with offering multiple PD prefixes for a single host. The route included in the Framed-IPv6-Route attribute is accepted as a managed route only if its next hop is a WAN host (DHCPv6 IA-NA, SLAAC, or /128 data-triggered). Therefore, Framed-IPv6-Routes with an explicitly configured gateway prefix of a pd-host (DHCPv6 IA-PD) are not installed. A Framed-Route attribute is also ignored if the SAP does not have anti-spoof configured to nh-mac (the host is installed as a standalone host without managed route). Any routes above the configured limits are silently ignored. Optionally, a metric, tag, or protocol preference can be specified for the managed route. If the metrics are not specified, specified in a wrong format, or specified with out-of-range values, then the following default values are used for all metrics: metric=0, no tag, and preference=0. If an identical managed route is associated with different routed subscriber hosts in the context of the same IES or VPRN service, up to max-ecmp-routes managed routes are installed in the routing table (configured as ecmp max-ecmp-routes in the routing instance). Candidate ECMP Framed-IPv6-Routes have an identical prefix, equal lowest preference, and equal lowest metric. The lowest IP next hop is the tie breaker if more candidate ECMP Framed-IPv6-Routes are available than the configured max-ecmp-routes. Other identical managed routes are shadowed (not installed in the routing table) and an event is logged. Valid RADIUS-learned managed routes can be included in RADIUS accounting messages. |
|
100 |
Framed-IPv6-Pool |
The name of an assigned pool that should be used to assign an IPv6 address using DHCPv6 (IA-NA) to the WAN side of the user (IPoE, PPPoE). Maps to DHCPv6 vendor-option [17], sub-option [1] wan-pool. Framed-IPv6-Pool names longer than the allowed maximum are treated as host setup failures. This attribute is an alternative to [97] Framed-IPv6-Prefix and [26.6527.99] Alc-IPv6-Address, that also assigns IPv6 addressing to the WAN side of a host using SLAAC or DHCPv6 IA-NA. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. |
|
101 |
Error-Cause |
The Error-Cause Attribute provides more detail on the cause of the problem if the NAS cannot honor Disconnect-Request or CoA-Request messages for some reason. It may be included within Disconnect-ACK, Disconnect-NAK and CoA-NAK messages. The Error-Causes are divided in 5 blocks. Range [400-499] is used for fatal errors committed by the RADIUS server. Range [500-599] is used for fatal errors occurring on a NAS or RADIUS proxy. Ranges [000-199 reserved], [300-399 reserved] and [200-299 used for successful completion in disconnect-ack/coa-ack] are not implemented. |
|
123 |
Delegated-IPv6-Prefix |
The attribute that carries the prefix (IPv6 prefix or prefix length) to be delegated using DHCPv6 (IA-PD) for the LAN side of the user (IPoE, PPPoE). Maps to DHCPv6 option IA-PD [25] sub-option IA-Prefix [26] Prefix. An exact Delegated-prefix-Length [DPL] match with configure service ies | vprn service-id subscriber-interface ip-int-name ipv6 delegated-prefix-length [48 to 64] is required with the received attribute prefix-length unless a variable DPL is configured (configure service ies | vprn service-id subscriber-interface ip-int-name ipv6 delegated-prefix-length variable). In the latter case, multiple hosts for the same group-interface having different prefix-length [48 to 64] per host are supported. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. Attribute is also used in CoA and Disconnect Message (part of the ESM or AA user identification-key). For data-triggered subscriber host authentication, an Access-Accept message can include this attribute to specify the prefix to create an IPv6 prefix host. |
|
26.2352.1 |
Client-DNS-Pri |
The IPv4 address of the primary DNS server for this subscriber’s connection and maps to PPPoE IPCP option 129 Primary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.4874.4 ERX-Primary-Dns or 26.6527.9 Alc-Primary-Dns. |
|
26.2352.2 |
Client-DNS-Sec |
A IPv4 address of the secondary DNS server for this subscriber’s connection and maps to 'PPPoE IPCP option 131 Secondary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.4874.5 ERX-Secondary-Dns or 26.6527.10 Alc-Secondary-Dns. |
|
26.2352.36 |
Ip-Address-Pool-Name |
The name of an assigned address pool that should be used to assign an address for the user and maps to DHCPv4 option [82] vendor-specific-option [9] sub-option [13] dhcpPool if option is enabled on the node (configure service ies | vprn service-id subscriber-interface ip-int-name group-interface ip-int-name dhcp option vendor-specific-option pool-name). Alternative to [88] Pool-Name and [26.4874.2] ERX-Address-Pool-Name. Pool names longer than the allowed maximum are treated as host setup failures. [8] Framed-IP-Address attribute with value different from 255.255.255.254 has precedence over [26.2352.36] Ip-Address-Pool-Name when both are present in RADIUS Access-Accept. |
|
26.2352.99 |
RB-Client-NBNS-Pri |
The IPv4 address of the primary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 130 Primary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.4874.6 ERX-Primary-Wins or 26.6527.29 Alc-Primary-Nbns. |
|
26.2352.100 |
RB-Client-NBNS-Sec |
The IPv4 address of the secondary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 132 Secondary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.4874.7 ERX-Secondary-Wins or 26.6527.30 Alc-Secondary-Nbns. |
|
26.3561.1 |
Agent-Circuit-Id |
Information describing the subscriber agent circuit identifier corresponding to the logical access loop port of the Access Node or DSLAM from which a subscriber's requests are initiated. Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute circuit-id. For data-triggered subscriber host authentication:
For data-triggered subscriber host authentication, this attribute in the Access-Request message contains the source IPv4 or IPv6 address of the data-trigger. The Access-Accept message can include this attribute to specify the circuit ID of the IPoE session if the configure subscriber-management ipoe-session-policy name circuit-id-from-auth command is configured. |
|
26.3561.2 |
Agent-Remote-Id |
A string that uniquely identifies the subscriber on the associated access loop on the Access Node on which the PPPoE or DHCP client messages are received. Attribute is included with the following configuration: configure subscriber-mgmt authentication-policy name include-radius-attribute remote-id. For PPPoE sessions, its value is the Agent Remote ID sub option of the BBF vendor specific PPPoE access loop identification tag inserted in the PADI/PADR messages of the discovery phase by a PPPoE Intermediate Agent. For IPoE DHCPv4, its value is the Agent Remote ID sub option of the Relay Agent Information Option 82 inserted by a Layer 2 or Layer 3 Relay Agent. For IPoE DHCPv6, its value is the Relay Agent Remote-ID Option 37 inserted by an LDRA or Layer 3 Relay Agent. Note: The Agent Remote ID sub option of the DHCPv4 Relay Agent Information Option 82 only contains a remote ID string, while the DHCPv6 Relay Agent Remote-ID Option 37 has an enterprise number field and a remote-id field. For the authentication of an IPoE DHCPv6 host with IPoE sessions disabled, the first four bytes of the Agent-Remote-Id RADIUS attribute contain the enterprise number field, followed by the remote-id field. With IPoE sessions enabled, the enterprise number field is omitted, and the Agent-Remote-Id RADIUS attribute only contains the remote-id field. |
|
26.3561.129 |
Actual-Data-Rate-Upstream |
The actual upstream train rate of a subscriber's synchronized DSL link and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.130 |
Actual-Data-Rate-Downstream |
Actual downstream train rate of a subscriber's synchronized DSL link and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.131 |
Minimum-Data-Rate-Upstream |
The subscriber's operator-configured minimum upstream data rate and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.132 |
Minimum-Data-Rate-Downstream |
The subscriber's operator-configured minimum downstream data rate and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.133 |
Attainable-Data-Rate-Upstream |
The subscriber's attainable upstream data rate and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.134 |
Attainable-Data-Rate-Downstream |
The subscriber's attainable downstream data rate and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.135 |
Maximum-Data-Rate-Upstream |
The subscriber's maximum upstream data rate, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.136 |
Maximum-Data-Rate-Downstream |
The subscriber's maximum downstream data rate, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.137 |
Minimum-Data-Rate-Upstream-Low-Power |
The subscriber's minimum upstream data rate in low power state, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.138 |
Minimum-Data-Rate-Downstream-Low-Power |
The subscriber's minimum downstream data rate in low power state, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.139 |
Maximum-Interleaving-Delay-Upstream |
The subscriber's maximum one-way upstream interleaving delay, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.140 |
Actual-Interleaving-Delay-Upstream |
The subscriber's actual one-way upstream interleaving delay and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.141 |
Maximum-Interleaving-Delay-Downstream |
The subscriber’s maximum one-way downstream interleaving delay, as configured by the operator and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.142 |
Actual-Interleaving-Delay-Downstream |
The subscriber's actual one-way downstream interleaving delay and maps to values received during PPPoE discovery (tag 0x0105) or DHCP (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.3561.144 |
Access-Loop-Encapsulation |
The last mile encapsulation used by the subscriber on the DSL access loop and maps to values received during PPPoE discovery Tags (tag 0x0105) or DHCP Tags (opt-82). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. Last mile encapsulation information can be used to adjust automatically the egress aggregate rate for this subscriber. Preconfigured encapsulation types are used if PPP or IPoE access loop information (tags) is not available (configure subscriber-mgmt sub-profile subscriber-profile-name egress encap-offset type type or configure subscriber-mgmt local-user-db local-user-db-name ppp host access-loop encap-offset type). [26.6527.133] Alc-Access-Loop-Encap-Offset when returned in Access-Accept is taken into account (overrules received tags and preconfigured encapsulation types) for ALE adjust (last mile aware shaping) but is not reflected in access-loop-options send to RADIUS. Alc-Access-Loop-Encap from ANCP are currently not taken into account for ALE adjust. |
|
26.3561.254 |
IWF-Session |
The presence of this Attribute indicates that the IWF has been performed with respect to the subscriber's session. IWF is used to enable the carriage of PPP over ATM (PPPoA) traffic over PPPoE. The Access Node inserts the PPPoE Tag 0x0105, vendor-id 0x0de9 with sub-option code 0xFE, length field is set to 0x00 into the PPPoE Discovery packets when it is performing an IWF functionality. Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.4874.2 |
ERX-Address-Pool-Name |
The name of an assigned address pool that should be used to assign an address for the user and maps to dhcpv4 option[82] vendor-specific-option [9] sub-option [13] dhcpPool if option is enabled on the node (configure service ies | vprn service-id subscriber-interface ip-int-name group-interface ip-int-name dhcp option vendor-specific-option pool-name). Alternative to [88] Pool-Name and [26.2352.36] Ip-Address-Pool-Name. Pool names longer than the allowed maximum are treated as host setup failures. [8] Framed-IP-Address attribute with value different from 255.255.255.254 has precedence over [26.4874.2] ERX-Address-Pool-Name when both are present in RADIUS Access-Accept. |
|
26.4874.4 |
ERX-Primary-Dns |
The IPv4 address of the primary DNS server for this subscriber’s connection and maps to PPPoE IPCP option 129 Primary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.2352.1 Client-DNS-Pri or 26.6527.9 Alc-Primary-Dns. |
|
26.4874.5 |
ERX-Secondary-Dns |
The IPv4 address of the secondary DNS server for this subscriber’s connection and maps to PPPoE IPCP option 131 Secondary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.2352.2 Client-DNS-Sec or 26.6527.10 Alc-Secondary-Dns. |
|
26.4874.6 |
ERX-Primary-Wins |
The IPv4 address of the primary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 130 Primary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.2352.99 RB-Client-NBNS-Pri or 26.6527.29 Alc-Primary-Nbns. |
|
26.4874.7 |
ERX-Secondary-Wins |
The IPv4 address of the secondary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 132 Secondary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.2352.100 RB-Client-NBNS-Sec or 26.6527.30 Alc-Secondary-Nbns. |
|
26.4874.47 |
ERX-Ipv6-Primary-Dns |
The IPv6 address of the primary DNSv6 server for this subscriber’s connection and maps to DNS Recursive Name Server option 23 (RFC 3646) in DHCPv6. This attribute is an alternative for 26.6527.105 Alc-Ipv6-Primary-Dns. |
|
26.4874.48 |
ERX-Ipv6-Secondary-Dns |
The IPv6 address of the secondary DNSv6 server for this subscriber’s connection and maps to DNS Recursive Name Server option 23 (RFC 3646) in DHCPv6. This attribute is an alternative for 26.6527.106 Alc-Ipv6-Secondary-Dns. |
|
26.6527.9 |
Alc-Primary-Dns |
The IPv4 address of the primary DNS server for this subscriber’s connection and maps to PPPoE IPCP option 129 Primary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.2352.1 Client-DNS-Pri or 26.4874.4 ERX-Primary-Dns. |
|
26.6527.10 |
Alc-Secondary-Dns |
The IPv4 address of the secondary DNS server for this subscriber’s connection and maps to PPPoE IPCP option 131 Secondary DNS Server address or DHCPv4 option 6 Domain Server. This attribute is an alternative for 26.2352.2 Client-DNS-Sec or 26.4874.5 ERX-Secondary-Dns. |
|
26.6527.11 |
Alc-Subsc-ID-Str |
A subscriber is a collection of subscriber-hosts (typically represented by IP-MAC combination) and is uniquely identified by a subscriber string. Subscriber-hosts queues or policers belonging to the same subscriber (residing on the same forwarding complex) can be treated under one aggregate scheduling QoS mechanism. Fallback to preconfigured values if attribute is omitted. Attribute values longer than the allowed string value are treated as setup failures. Can be used as key in CoA and Disconnect Message. |
|
26.6527.12 |
Alc-Subsc-Prof-Str |
The subscriber profile is a template that contains settings (accounting, IGMP, HQoS, and so on) that apply to all hosts belonging to the same subscriber where [26.6527.12] Alc-Subsc-Prof-Str is the string that maps (configure subscriber-mgmt sub-ident-policy sub-ident-policy-name sub-profile-map) to such an subscriber profile (configure subscriber-mgmt sub-profile subscriber-profile-name). Strings longer than the allowed maximum are treated as setup failures. Unreferenced strings (where the string does not map to a policy) are silently ignored and a fallback to preconfigured defaults is done. |
|
26.6527.13 |
Alc-SLA-Prof-Str |
The SLA profile is a template which contains settings (filter, QoS, host-limit, and so on) which are applicable to individual hosts were [26.6527.13] Alc-SLA-Prof-Str is the string that maps (configure subscriber-mgmt sub-ident-policy sub-ident-policy-name sla-profile-map) to such a sla profile (configure subscriber-mgmt sla-profile sla-profile-name). Strings longer than the allowed maximum are treated as setup failures. Unreferenced strings (where the string does not map to a policy) are silently ignored and a fallback to preconfigured defaults is done. |
|
26.6527.14 |
Alc-Force-Renew |
An individual DHCPv4 session is renewed with a CoA with attribute [26.6527.14] Alc-Force-Renew. The NAS initiates the ForceRenew procedure with re-authentication (triggers dhcp Force Renew to client and start re-authentication on dhcp Request received). |
|
26.6527.16 |
Alc-ANCP-Str |
Information describing the subscriber agent circuit identifier corresponding to the logical access loop port of the Access Node or DSLAM from which a subscriber's requests are initiated and used to associate the ANCP Circuit-Id (info received using ANCP Port Up and Port Down) with the PPPoE/IPoE Circuit-Id (info received using [26.6527.16] Alc-ANCP-Str and [26.3561.1] Agent-Circuit-Id). A subscriber is associated with ANCP when both strings are equal. For associated subscribers, the ingress and egress ANCP QoS rules apply (configure subscriber-mgmt ancp ancp-policy policy-name and configure subscriber-mgmt sub-profile ancp ancp-policy policy-name. |
|
26.6527.18 |
Alc-Default-Router |
Maps to an DHCP offer or ACK message option [3] default-router for a DHCPv4 RADIUS proxy scenario and defines the default gateway for the user. This attribute is silently ignored if the NAS is using DHCPv4 relay. In the latter case, the default-router is part of the DHCPv4 server configuration. |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
MAC address from a user that requests a service and included in Authentication (configure subscriber-mgmt authentication-policy name include-radius-attribute mac-address). May be included in CoA as host identification attribute. |
|
26.6527.28 |
Alc-Int-Dest-Id-Str |
A string representing an aggregation point (example, Access Node) and interpreted as the intermediate destination ID. Subscribers connected to the same aggregation point receives the same int-dest-id string assigned. The int-dest-id is used in MC ring access redundancy to identify subscribers behind a ring node (configure redundancy multi-chassis peer ip-address mc-ring ring/l3-ring name ring-node ring-node-name). The int-dest-id can be used in QoS to shape the egress traffic of a group of subscribers to an aggregate rate using Vports (configure port port-id ethernet access egress vport name host-match dest destination-string). For egress policed subscriber traffic, the int-dest-id can be used to select the egress queue-group for forwarding (configure port port-id ethernet access egress queue-group name host-match dest destination-string). Strings longer than the allowed maximum are treated as setup failures. |
|
26.6527.29 |
Alc-Primary-Nbns |
The IPv4 address of the primary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 130 Primary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.2352.99 RB-Client-NBNS-Pri or 26.4874.6 ERX-Primary-Wins. |
|
26.6527.30 |
Alc-Secondary-Nbns |
The IPv4 address of the secondary NetBios Name Server (NBNS) for this subscriber’s connection and maps to PPPoE IPCP option 132 Secondary NBMS Server address or DHCPv4 option44 NETBIOS name server. This attribute is an alternative for 26.2352.100 RB-Client-NBNS-Sec or 26.4874.7 ERX-Secondary-Wins. |
|
26.6527.34 |
Alc-PPPoE-PADO-Delay |
Specifies the number in deciseconds that the PPPoE protocol stack on the NAS waits before sending a PADO packet in response to a PADI request. In dual homed topologies, you may want to designate a primary NAS and a backup NAS for handling a particular service request. In such a scenario, you can configure a delay for the backup NAS to allow sufficient time for the primary NAS to respond to the client with a PADO packet. If the primary NAS does not send the PADO packet within this delay period, then the backup NAS sends the PADO packet after the delay period expires. This attribute is only applicable if RADIUS PADI authentication is used (configure subscriber-mgmt authentication-policy name pppoe-access-method padi). Values above the allowed Limits are truncated at the Limits boundary. There is no PADO delay if the attribute is omitted or if the attribute is received with a value of zero. |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
Maps to PADI field PPPoE tags [0x0101] service-name and is sent in the Access-Request if enabled under configure subscriber-mgmt authentication-policy name include-radius-attribute pppoe-service-name. A PPPoE-Service-Name above the allowed maximum length is handled as a PPPoE session setup failure. |
|
26.6527.36 |
Alc-DHCP-Vendor-Class-Id |
Initiated by DHCP clients using option [60] Vendor Class Identifier and reflected in Authentication. (configure subscriber-mgmt authentication-policy name include-radius-attribute dhcp-vendor-class-id or configure aaa isa-radius-policy name auth-include-attributes dhcp-vendor-class-id). DHCP option [60] Vendor Class Identifier can also be used as username in RADIUS requests. (configure subscriber-mgmt authentication-policy name user-name-format dhcp-client-vendor-opts). |
|
26.6527.45 |
Alc-App-Prof-Str |
Application Assurance for residential, business, or transit-AA subscribers is enabled through the assignment of an application profile as part of either enhanced subscriber management or static configuration. [26.6527.45] Alc-App-Prof-Str is a string that maps (configure subscriber-mgmt sub-ident-policy sub-ident-policy-name app-profile-map) to such an application profile (configure application-assurance group aa-group-id:partition-id policy app-profile app-profile-name). This attribute is used in access-accept to assign an application profile during esm host creation and in CoA to change the application profile of a AA-subscriber or to create transit AA-subscriber. Strings longer than the allowed maximum are treated as setup failures. Unreferenced strings (strings not mapping to an application profile) silently triggers a fallback to preconfigured default values if allowed. If no default value is preconfigured, the subscriber's application profile is silently disabled for esm AA-subscriber; in case of a transit AA-subscriber creation, the CoA is rejected. The change of an application profile to one configured under a different group or partition or the modification of the application profile of a static AA-subscriber is not allowed and is treated as setup failures. |
|
26.6527.98 |
Alc-Force-Nak |
An individual DHCPv4 session is terminated with a CoA with attribute [26.6527.98] Alc-Force-Nak. The NAS initiates the force renew procedure and then answers the clients DHCP request with a DHCP NAK to force the client in the INIT state. The NAS also sends a DHCP release to the DHCP server. |
|
26.6527.99 |
Alc-Ipv6-Address |
The IPv6 address to be configured to the WAN side of the user (IPoE,PPPoE) using DHCPv6 (IA-NA). Maps to DHCPv6 option IA-NA[3] sub-option IA-Address[5] address. This attribute is an alternative to [97] Framed-IPv6-Prefix and [100] Framed-IPv6-Pool, which also assigns IPv6 addressing to the wan-side of a host using SLAAC or DHCPv6 IA-NA. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. Attribute is also used in CoA and Disconnect Message (part of the ESM or AA user identification-key). For data-triggered subscriber host creation in the Enhanced Subscriber Management (ESM) context, the attribute can be included in an Access-Accept message to specify the IPv6 address to create a /128 IPv6 host. For data-triggered authentication of an IPv6 UE in Distributed Subscriber Management (DSM) context, this attribute contains the IPv6 address that triggered the request. Inclusion of this attribute is configured under configure aaa isa-radius-policy policy-name auth-include-attributes ipv6-address. For data-triggered subscriber host creation, an Access-Accept message can contain this attribute to specify the IPv6 address to create an IPv6 /128 host. |
|
26.6527.100 |
Alc-Serv-Id |
Applies to FWA sessions only. This VSA refers to the service where the GTP sessions are terminated (configure service {vprn | ies} service-id). This overrides a potential default configured under configure subscriber-mgmt gtp apn-policy policy-name apn apn defaults group-interface interface-name svc-id service-id. This VSA must be accompanied with a valid Alc-Interface VSA. |
|
26.6527.101 |
Alc-Interface |
Applies to FWA sessions only. This VSA refers to a group-interface of type gtp where the GTP sessions are terminated (configure service {vprn | ies} subscriber-interface ip-int-name group-interface ip-int-name gtp). This overrides a potential default configured under configure subscriber-mgmt gtp apn-policy policy-name apn apn defaults group-interface interface-name svc-id service-id. If neither a default nor a radius-specified interface is provided, session setup fails. |
|
26.6527.102 |
Alc-ToServer-Dhcp-Options |
Send to RADIUS all DHCPv4 options received in a DHCPv4 message triggering authentication. The DHCPv4 options are concatenated in the attribute up to maximum length per attribute. If more space is needed, an additional attribute is included. If the total dhcp options space requires more than the total maximum length, then no attributes are included. Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute dhcp-options. This feature is supported for both DHCP relay and proxy. For DHCP triggered authentication in a Distribute Subscriber Management (DSM) context, this attribute contains the DHCP client options as sent to the WLAN-GW. Inclusion of this attribute is configured using configure aaa isa-radius-policy name auth-include-attributes dhcp-options. |
|
26.6527.103 |
Alc-ToClient-Dhcp-Options |
The value of this attribute represents DHCPv4 options encoded in a hexadecimal format. DHCPv4 options originated by RADIUS are appended to the options already present in the DHCPv4 messages toward the client. Multiple DHCP options can be concatenated in a single VSA. Attributes outside the defined limits result in a setup failure. When more than the supported number of attributes are received from RADIUS, only the supported number of VSAs are appended in the DHCP message, starting with the first attribute received. The remaining attributes are silently ignored. |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
The IPv6 address of the primary DNSv6 server for this subscriber’s connection. Maps to DNS Recursive Name Server option 23 (RFC 3646) in DHCPv6 and Recursive DNS Server Option type 25 (RFC 6106) for SLAAC RA. This attribute is an alternative for [26.4874.47] ERX-Ipv6-Primary-Dns. |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
The IPv6 address of the secondary DNSv6 server for this subscriber’s connection. Maps to DNS Recursive Name Server option 23 (RFC 3646) in DHCPv6 and Recursive DNS Server Option type 25 (RFC 6106) for SLAAC RA. This attribute is an alternative for [26.4874.48] ERX- Ipv6-Secondary-Dns. |
|
26.6527.126 |
Alc-Subscriber-QoS-Override |
Used to override queue or policer parameters (CIR, PIR, CBS, MBS, burst-limit, PIR and CIR parent weights) and HQoS parameters (aggregate rate, scheduler rate or root arbiter rate) configured at sla-profile and sub-profile context. Enables per subscriber or host customization. Each set of Alc-Subscriber-QoS-Override attributes in a RADIUS message replaces the set of Alc-Subscriber-QoS-Override attributes from a previous message. Hence the SLA profile or subscriber profile QoS configuration is always used as the base config. To undo a previously enabled RADIUS QoS-override and return to the base config, send a CoA with at least one Alc-Subscriber-QoS-Override attribute. The value part of each Alc-Subscriber-QoS-Override attribute must be empty (for example, Alc-Subscriber-QoS-Override += i:q:2:). Incorrectly formatted attributes or too many attributes are treated as a setup failure or result in a CoA NAK. |
|
26.6527.131 |
Alc-Delegated-IPv6-Pool |
The name of an assigned pool that should be used to assign an IPv6 prefix using DHCPv6(IA-PD) to the LAN side of the user (IPoE, PPPoE). Maps to DHCPv6 vendor-option[17],sub-option[2] pfx-pool. Alc-Delegated-ipv6-pool names longer than the allowed maximum are treated as host setup failures. Alternative method for [123] Delegated-IPv6-Prefix. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. The length information [DPL] can be supplied using [26.6527.161] Alc-Delegated-IPv6-Prefix-Length along with the pool name. The [26.6527.161] Alc-Delegated-IPv6-Prefix-Length has priority over other possible sources of DPL. (As a fixed [48 to 64] DPL or variable DPL under configure service ies | vprn service-id subscriber-interface ipv6 delegated-prefix-length or on the DHCPv6 server configure router dhcp6 local-dhcp-server server-name pool pool-name delegated-prefix-length). |
|
26.6527.132 |
Alc-Access-Loop-Rate-Down |
The actual downstream rate (coded in kb/s) of a PPPoE subscriber's synchronized DSL link and competes with the value received from alternative sources (dsl-forum tags, LUDB, ANCP). Values outside the limits are treated as setup failures. This attribute is silently ignored for non-MLPPP sessions or IPoE sessions. |
|
26.6527.133 |
Alc-Access-Loop-Encap-Offset |
The last mile encapsulation representing the subscriber’s DSL access loop encapsulation. When returned in RADIUS-Accept (PTA or LAC), it is taken into account for ALE adjust (last mile aware shaping) but not reflected in [26.3561.144] Access-Loop-Encapsulation (access-loop-options) send to Accounting. For LAC, this attributes maps to LTP AVP [3561-144] Access-Loop-Encapsulation. |
|
26.6527.135 |
Alc-PPP-Force-IPv6CP |
Forces IPv6CP negotiation in conditions where no IPv6 related attributes (such as v6 pool, v6 prefix, v6 address, DNSv6) are obtained using authentication (Access Accept, local user database, and so on). Without these IPv6 related attributes, the NAS cannot detect that this is a dual-stack PPPoE user and therefore it does not start IPv6CP negotiation. An attribute value other than 0 (zero) forces IPv6CP negotiation to start when no IPv6 attributes are obtained in authentication. An attribute value of 0 (zero) is treated the same as not sending the attribute. |
|
26.6527.136 |
Alc-Onetime-Http-Redirection-Filter-Id |
The preconfigured IPv4 filter with HTTP redirection rules. using this host- specific filter only the first HTTP request from the host is redirected to a configured URL with specified parameters. There is no HTTP redirection for subsequent HTTP requests which is useful in cases where service providers need to push a web page of advertisement or announcements to broadband users. Note: Filter name ([245.26.6527.7.5]
Alc-Sub-Ipv4-Onetime-Http-Redirect-Filter-Name) and filter
ID ([26.6527.136] Alc-Onetime-Http-Redirection-Filter-Id)
overrides should not be mixed during the lifetime of a
subscriber host or session.
|
|
26.6527.146 |
Alc-Wlan-APN-Name |
This VSA contains the Access Point Name string as signaled in the incoming GTP-C message for FWA sessions. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute apn. |
|
26.6527.147 |
Alc-MsIsdn |
This VSA contains the MSISDN (telephone number) as signaled in the incoming GTP-C message for FWA sessions. If the corresponding GTP-C IE is not present the VSA is not included. Inclusion of this attribute can be configured using configure subscriber-mgmt authentication-policy name include-radius-attribute msisdn. |
|
26.6527.160 |
Alc-Relative-Session-Timeout |
Sets or resets the IPoE or PPPoE session timeout to a relative value (current session time + newly received Alc-Relative-Session-Timeout). Attribute equals to [27] Session-Timeout if received in Access-Accept since the current session time equals zero. A value of zero sets or resets the session-timeout to infinite (no session-timeout). Simultaneous received [27] Session-Timeout and [26.6527.160] Alc-Relative-Session-Timeout are treated as a setup failure (setup failure if received in Access-Accept or CoA rejected (NAK) with error cause = Invalid Request). |
|
26.6527.161 |
Alc-Delegated-IPv6-Prefix-Length |
Defines the IA-PD length information [DPL] and only applicable together with [26.6527.131] Alc-Delegated-IPv6-Pool (silently ignored if received in RADIUS Accept without Alc-Delegated-IPv6-Pool). Maps to DHCPv6 vendor-option[17], sub-option[3] pfx-len. The [26.6527.161] Alc-Delegated-IPv6-Prefix-Length has priority over other possible sources of DPL. (As a fixed [48 to 64] DPL or variable DPL under configure service ies |vprn service-id subscriber-interface ip-int-name ipv6 delegated-prefix-length or on the dhcpv6 server configure router dhcp6 local-dhcp-server server-name pool pool-name delegated-prefix-length). DPL values outside the limits are treated as setup failures. |
|
26.6527.174 |
Alc-Lease-Time |
Defines the lease-time in seconds for RADIUS proxy and create-host-CoA scenarios only. The [27] Session-Timeout is interpreted and used as IPoE lease-time if [26.6527.174] Alc-lease-Time is omitted. Returning attribute [26.6527.174] Alc-Lease-Time in other scenarios than radius-proxy and create-host-CoA are treated as setup failures. |
|
26.6527.175 |
Alc-DSL-Line-State |
Status of the DSL line obtained using ANCP can be one of three value: SHOWTIME (the modem is ready to transfer data), IDLE (line is idle) or SILENT (line is silent). Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.6527.176 |
Alc-DSL-Type |
Type of the DSL line (ADSL1, ADSL2, ADSL2PLUS, VDSL1, VDSL2, SDSL, other) obtained using ANCP. This attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute access-loop-options. |
|
26.6527.177 |
Alc-Portal-Url |
The URL to which traffic matching the host’s IPv4 filter entry with HTTP redirect action is redirected. The URL overrides the configured URL in the redirect filter. RADIUS overrides must explicitly be enabled: configure filter ip-filter filter-id entry entry-id action http-redirect rdr-url-string allow-radius-override. |
|
26.6527.178 |
Alc-Ipv6-Portal-Url |
The URL to which traffic matching the host’s IPv6 filter entry with HTTP redirect action is redirected. The URL overrides the configured URL in the redirect filter. RADIUS overrides must explicitly be enabled: configure filter ipv6-filter filter-id entry entry-id action http-redirect rdr-url-string allow-radius-override. |
|
26.6527.180 |
Alc-SAP-Session-Index |
Per SAP, this is a unique PPPoE or IPoE session index that can be included in RADIUS Access Request messages. The lowest free index is assigned to a new PPPoE or IPoE session. Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute sap-session-index. |
|
26.6527.181 |
Alc-SLAAC-IPv6-Pool |
A pool name that can be used in local address assignment to assign an IPv6 SLAAC prefix using a Router Advertisement to the WAN side of the IPoE or PPPoE user. Alc-SLAAC-IPv6-Pool names longer than the allowed maximum are treated as host setup failures. If local-address-assignment is not enabled on the group-interface for ipv6 client-application ppp-slaac, then the PPP session is terminated. If local-address-assignment is not enabled on the group-interface for ipv6 client-application ipoe-slaac, then the IPoE host is not instantiated. See Address, prefix, and pool attribute details that describes the behavior when both address or prefix and pool attributes are returned for a subscriber session. |
|
26.6527.183 |
Alc-WPP-Error-Code |
This attribute specifies the value of the ErrCode that the system should use in a WPP ACK_AUTH packet. This attribute can only be included in a RADIUS Access-Reject packet. |
|
26.6527.185 |
Alc-Onetime-Http-Redirect-Reactivate |
An indication to reactivate a onetime HTTP redirect filter for the host. When received in a RADIUS CoA message, the filter with the value indicated by [26.6527.136] Alc-Onetime-Http-Redirection-Filter-Id is activated. If [26.6527.136] Alc-Onetime-Http-Redirection-Filter-Id contains the value 0, then the existing onetime http redirect filter ID associated with the host is removed. If no [26.6527.136] Alc-Onetime-Http-Redirection-Filter-Id VSA is provided in the RADIUS CoA message, then the existing onetime http redirect filter ID associated with the host is applied. The value of the [26.6527.185] Alc-Onetime-Http-Redirect-Reactivate VSA is opaque. It is the presence of the VSA in a RADIUS CoA that triggers the action. |
|
26.6527.191 |
Alc-ToServer-Dhcp6-Options |
This attribute contains DHCPv6 client options present in a DHCPv6 Solicit or Request message to be passed to RADIUS in an Access-Request. Multiple attributes are inserted when the length of the DHCPv6 options exceeds the maximum length of a single attribute. No attributes are included if the total length of the DHCPv6 options exceeds the total limit for this attribute. When the DHCPv6 solicit or request message is encapsulated in a Relay-Forward message, only the inner DHCPv6 client options are copied in the Alc-ToServer-Dhcp6-Options attribute. Options inserted by a Relay Agent are ignored. Attribute is included or excluded based on configure subscriber-mgmt authentication-policy name include-radius-attribute dhcp6-options. This feature is supported for both DHCP relay and proxy. For DHCPv6 triggered authentication in a Distribute Subscriber Management (DSM) context, this attribute contains the DHCPv6 client options as sent to the WLAN-GW. Inclusion of this attribute is configured using configure aaa isa-radius-policy policy-name auth-include-attributes dhcp6-options. |
|
26.6527.192 |
Alc-ToClient-Dhcp6-Options |
The value of this attribute represents DHCPv6 options encoded in a hexadecimal format. DHCPv6 options originated by RADIUS are appended to the options already present in the DHCPv6 Advertise and Reply messages toward the client. Attributes outside the defined limits result in a setup failure. When more than the supported number of attributes are received from RADIUS, only the supported number of VSAs are appended in the DHCP message, starting with the first attribute received. The remaining attributes are silently ignored. This feature is supported for both DHCP relay and proxy. |
|
26.6527.200 |
Alc-v6-Preferred-Lifetime |
An IPv6 address or prefix preferred lifetime is the length of time that a valid address or prefix is preferred (for example, the time until deprecation). When the preferred lifetime expires, the address or prefix becomes deprecated (it can still be used in existing communications but should not be used as a source in new communications). This attribute is applicable only when an IPv6 address or prefix is assigned using RADIUS (DHCPv6 proxy). It overrides the dhcp6 proxy-server preferred-lifetime configuration on the group-interface. The attribute value is expressed in seconds. Values outside the allowed range result in a setup failure. If, for the final determined values from the different sources (LUDB, RADIUS, defaults), the following rule is violated: renew timer 7705 SAR-8 rebind timer <= preferred lifetime <= valid lifetime then the default timers are used: renew-timer = 30 min, rebind-timer = 48 min, preferred-lifetime = 1hr, valid-lifetime = 1 day. Note that only a single value can be specified that applies to both IA-NA address and IA-PD prefix. |
|
26.6527.201 |
Alc-v6-Valid-Lifetime |
The IPv6 address or prefix valid lifetime is the length of time an address or prefix remains in the valid state (for example, the time until invalidation). When the valid lifetime expires, the address or prefix becomes invalid and must no longer be used in communications. This attribute is used as the DHCPv6 lease time. This attribute is applicable only when an IPv6 address or prefix is assigned using RADIUS (DHCPv6 proxy). Overrides the dhcp6 proxy-server valid-lifetime configuration on the group-interface. The attribute value is expressed in seconds. Values outside the allowed range result in a setup failure. If, for the final determined values from the different sources (LUDB, RADIUS, defaults), the following rule is violated: renew timer <= rebind timer <= preferred lifetime <= valid lifetime then the default timers are used: renew-timer = 30 min, rebind-timer = 48 min, preferred-lifetime = 1hr, valid-lifetime = 1 day. Note that only a single value can be specified that applies to both IA-NA address and IA-PD prefix. |
|
26.6527.202 |
Alc-Dhcp6-Renew-Time |
The attribute value represents the DHCPv6 lease renew time (T1). T1 is the time at which the client contacts the addressing authority to extend the lifetimes of the DHCPv6 leases (addresses or prefixes). This attribute is applicable only when an IPv6 address or prefix is assigned using RADIUS (DHCPv6 proxy). Overrides the dhcp6 proxy-server renew-timer configuration on the group interface. The attribute value is expressed in seconds. Values outside the allowed range result in a setup failure. If, for the final determined values from the different sources (LUDB, RADIUS, defaults), the following rule is violated: renew timer <= rebind timer <= preferred lifetime <= valid lifetime then the default timers are used: renew-timer = 30 min, rebind-timer = 48 min, preferred-lifetime = 1hr, valid-lifetime = 1 day. Note that only a single value can be specified that applies to both IA-NA address and IA-PD prefix. |
|
26.6527.203 |
Alc-Dhcp6-Rebind-Time |
The attribute value represents the DHCPv6 lease rebind time (T2). T2 is the time at which the client contacts any available addressing authority to extend the lifetimes of DHCPv6 leases. This attribute is applicable only when an IPv6 address or prefix is assigned using RADIUS (DHCPv6 proxy). The attribute overrides the dhcp6 proxy-server rebind-timer configuration on the group interface The attribute value is expressed in seconds. Values outside the allowed range result in a setup failure. If, for the final determined values from the different sources (LUDB, RADIUS, defaults), the following rule is violated: renew timer <= rebind timer <= preferred lifetime <= valid lifetime then the default timers are used: renew-timer = 30 min, rebind-timer = 48 min, preferred-lifetime = 1hr, valid-lifetime = 1 day. Note that only a single value can be specified that applies to both IA-NA address and IA-PD prefix. |
|
26.6527.217 |
Alc-UPnP-Sub-Override-Policy |
Specifies the UPnP policy to use for this L2-Aware subscriber. The policy must be configured in configure service upnp upnp-policy policy-name. Overrides the configured policy in the sub-profile for the subscriber: configure subscriber-mgmt sub-profile name upnp-policy policy-name. The value ‟_tmnx_no_override” removes any existing override and installs the upnp-policy configured in the sub-profile instead. The value ‟_tmnx_disabled” creates a special override that disables UPnP for this subscriber. Specifying a non-existing policy results in a host or session setup failure or in a CoA Reject. All hosts belonging to the subscriber are affected by a UPnP policy override. Changing the UPnP policy clears all existing UPnP mappings. |
|
26.6527.228 |
Alc-Trigger-Acct-Interim |
When included in a CoA message an accounting interim update is generated for all accounting modes that have interim-updates enabled. The Alc-Trigger-Acct-Interim attribute with free formatted string value is echoed in the CoA triggered accounting interim update message. The [26.6527.163] Alc-Acct-Triggered- Reason attribute in the interim update is set to 18 (CoA-Triggered). |
|
26.6527.232 |
Alc-Acct-Interim-IvI |
Tagged Attribute. The interval in seconds at which Acct-Interim-Update messages should be generated. Overrides the local configured update-interval value in the RADIUS accounting policy. Only takes effect if interim-updates are enabled for one of the accounting modes in the RADIUS accounting policy. With attribute value=0, the interim accounting is switched off. The tag value (1 to 5) indicates which RADIUS accounting policy in the subscriber profile is updated. To change the update interval of the first accounting policy, attribute [85] Acct-Interim-Interval takes precedence over [26.6527.232] Alc-Acct-Interim-Ivl with tag 1 when both are included. |
|
26.6527.234 |
Alc-DNAT-Override |
A composite RADIUS attribute used to modify DNAT function for Layer 2–aware NAT subscribers:
After the DNAT configuration is modified using CoA (by enabling or disabling DNAT or changing the DNAT IP address), the existing flows remain active for five more seconds while the new flows are being created in accordance with the new configuration. After a five-second timeout, the stale flows are cleared from the system. If multiple Alc-DNAT-Override attributes with conflicting actions are received in the same CoA or Access-Accept, the last one takes precedence. |
|
26.6527.238 |
Alc-Remove-Override |
This attribute, when included in a CoA, removes the override installed with or deactivates the action triggered by the referenced attribute ID. |
|
26.6527.242 |
Alc-Radius-Py |
A free format attribute reserved for use in combination with a RADIUS Python script. SR OS ignores the attribute when received in an access accept or CoA and does not generate the attribute. The primary purpose for this attribute is to interact with RADIUS servers that do not support RFC 6929 extended and long extended vendor specific attribute types. This attribute can be used between the RADIUS server and the Python script. The Python script should convert the attribute value in an RFC 6929 compliant attribute format. |
|
26.6527.244 |
Alc-Force-DHCP-Relay |
This attribute is only supported for DHCP promotion of data-triggered hosts. When this attribute is included in an Access Accept message at the authentication of a data triggered subscriber hosts IPoE session, then a DHCP relay is performed when the subscriber host in the session is promoted to a DHCP host at renew or rebind. The IP and, or IPv6 address/prefix origin is set to DHCP or DHCP6 for the data triggered subscriber host that is promoted to a DHCP host. The IP address/prefix for all IP stacks of the subscribers IPoE session must also be included in the Access Accept. Attributes with invalid value are ignored. |
|
241.26.6527.16 |
Alc-IPv6-Router-Adv-Policy |
This attribute specifies the Router Advertisement policy to be used for this subscriber host or session. The Router Advertisement policy is configured in configure subscriber-mgmt router-advertisement-policy name. The Router Advertisement policy overrides the default Router Advertisement parameters configured in the ipv6 router-advertisements CLI context at the group interface or subscriber interface (wholesale or retail). Referencing a non-existing policy results in a subscriber host or session setup failure or a CoA reject. |
|
241.26.6527.17 |
Alc-Nat-Outside-IPs |
This attribute allows to specify an outside NAT IP address from AAA instead of allocating an address from the local NAT pools. An IP address can be provided for each policy. |
|
241.26.6527.18 |
Alc-Mld-Import-Policy |
This attribute overrides the subscriber’s current list of dynamic MLD import policies. The order in which the policies were added can be checked with show router [router-instance] mld hosts host ipv6-address detail. Note that the configured MLD import policy (configure subscriber-mgmt mld-policy mld-policy-name import policy-name) cannot be overridden and is always applied as the last policy in the MLD import policies list. As the import policies are evaluated in the applied order using a match and exit, it is good practice to only include a default-action in the configured MLD import policy. Access-Accept fails and CoA is rejected if more than 14 attributes are present. |
|
241.26.6527.19 |
Alc-Bonding-Id |
Attribute description is defined in the Bonding section, see Bonding (description). |
|
241.26.6527.22 |
Alc-Bonding-Reference-Rate |
Attribute description is defined in the Bonding section, see Bonding (description). |
|
241.26.6527.27 |
Alc-IPv6-Sub-If-Prefix |
This attribute installs a subscriber interface IPv6 prefix of type pd, wan-host or both. This is similar to a statically configured IPv6 prefix on a subscriber interface. The prefix is part of the subscriber host or session state. The prefix is removed from the system when the subscriber host or session disconnects. An invalid prefix, such as when overlapping with a static provisioned prefix, results in a subscriber host or session setup failure. |
|
241.26.6527.35 |
Alc-Mld-Import-Policy-Modif |
This attribute modifies the subscriber’s dynamic MLD import policy list. The command can either add or delete an MLD import policy to or from the list. The CoA is rejected if more than the allowed number of attributes are included or if the number of resulting dynamic MLD import policies is more than 14. |
|
241.26.6527.37 |
Alc-VAS-IPv4-Filter |
(Layer 2–aware NAT subscriber only). This VSA enables IPv4 service chaining for a Layer 2–aware NAT subscriber using the named Value Added Services (VAS) filter configured under configure subscriber-mgmt isa-service-chaining vas-filter. |
|
241.26.6527.38 |
Alc-VAS-NSH-IPv4-Opaque-Meta-Data |
(Layer 2–aware NAT subscriber only). For Value Added Services (VAS) enabled sessions this VSA specifies the Network Services Header (NSH) context header data for MD type 1. This value overrides insert-subscriber-id or opaque-data configured under configure subscriber-mgmt isa-service-chaining vas-filter filter-name entry id action {downstream | upstream} insert-nsh meta-data. An NSH header with this context data is only inserted if svc-path is correctly configured under configure subscriber-mgmt isa-service-chaining vas-filter filter-name entry id action {downstream | upstream} insert-nsh. |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
Static port forwards to be installed for Layer 2–aware NAT subscribers using external address assignment. |
|
241.26.6527.40 |
Alc-IPv6-Slaac-Replacement-Prefix |
Override the current host SLAAC prefix with the one specified in the VSA. The host address origin is not changed. Three subsequent Router Advertisements are sent to the SLAAC host respecting the configured advertisement intervals. The Router Advertisements contain both the current and new SLAAC prefixes: the valid and preferred lifetime for the current prefix are set to zero and for the new prefix the values are either specified in the router advertisement policy or the group interface configuration. Because of the prefix change, all traffic send using the old SLAAC prefix as source address is dropped in the BNG when anti-spoof is set to IP + MAC. Note that the prefix change results in a SLAAC host delete and create. |
|
241.26.6527.47 |
Alc-SPI-Sharing-Id |
Sets or overrides the SLA Profile Instance (SPI) sharing method for this subscriber session to SPI sharing per group or to the default SPI sharing method (per SAP or per session) as specified in the SLA profile (configure subscriber-mgmt sla-profile sla-profile-name def-instance-sharing spi-sharing-type). For SPI sharing per group, the group is identified with an integer group identifier (for example, the SPI sharing ID). An SPI is shared by all subscriber sessions with the same subscriber ID, SAP, SLA profile and group ID. Setting this attribute for an IPoE host with IPoE session disabled on the group interface results in a setup failure. Unsupported values result in a subscriber session setup failure. |
|
241.26.6527.57 |
Alc-Gtp-Skip-Ipv4-Alloc-Override |
Applies to FWA sessions only. 3GPP describes the following address management related Protocol Configuration Option (PCO) values.
The FWA-GW honors the PCO Address Management options set by the RG or UE which results in a non-deferred or deferred address allocation. By default, non-deferred address allocation applies when the PCO Address Management options are not set by the RG or UE. The default non-deferred behavior can be overruled to deferred address allocation using the following APN scope parameter: configure subscriber-mgmt gtp apn-policy policy-name apn apn skip-gtp-ipv4-alloc The CLI parameter skip-gtp-ipv4-alloc is only applicable when PCO Address Management options are not set by the RG or UE. The skip-gtp-ipv4-alloc behavior (deferred address allocation) can be overridden to non-deferred address allocation for an individual session using the Alc-Gtp-Skip-Ipv4-Alloc-Override attribute with value 1 (on). The Alc-Gtp-Skip-Ipv4-Alloc-Override attribute is silently ignored when the CLI parameter skip-gtp-ipv4-alloc is not configured. |
|
241.26.6527.58 |
Alc-Change-Reporting-Action |
Applies to FWA sessions only. Controls the change reporting action signaled in GTP. Overrides the value specified under configure subscriber-mgmt gtp peer-profile name change-reporting-action. The specified action only applies if the MME supports change reporting. |
|
241.26.6527.62 |
Alc-Host-DNAT-Override |
Enables or Disables DNAT functionality on a session level. This overrides any value that has been set by the Alc-DNAT-Override attribute. |
|
241.26.6527.71 |
Alc-Host-DNAT-Default-Address-Override |
Overrides the DNAT destination IP address on a per session level. This overrides both the default value configured under configure service nat nat-classifier classifier-name default-dnat-ip-address and the value set by the Alc-DNAT-Override attribute. |
|
241.26.6527.92 |
Alc-PPPoE-LCP-Keepalive-Interval |
Specifies the interval in seconds at which PPPoE LCP Echo-Request messages are sent. Overrides the LCP keepalive interval value configured in subscriber-mgmt ppp-policy for PPPoE PTA sessions or in the base router or VPRN service l2tp group context for L2TP LNS sessions. |
|
241.26.6527.93 |
Alc-PPPoE-LCP-Keepalive-Multiplier |
Specifies the number of PPPoE Echo-Request messages that can be missed before the PPPoE session is terminated. Overrides the LCP keepalive multiplier value configured in subscriber-mgmt ppp-policy for PPPoE PTA sessions or in the base router or VPRN service l2tp group context for L2TP LNS sessions. |
|
245.26.6527.5 |
Alc-Spi-Host-And-Session-Limits |
Used to override host-limits and session-limits configured at the sla-profile context. Enables to dynamically set host and session limits that are enforced per SLA Profile Instance. All subscriber hosts and sessions that belong to the same SLA Profile Instance should get the same dynamic override values. The limits are checked at host or session creation time. When a limit is reached, the host or session creation fails. See [245.26.6527.5] Alc-Spi-Host-And-Session-Limits attribute details for a detailed description of the attribute. |
|
245.26.6527.6 |
Alc-Sub-Host-And-Session-Limits |
Used to override host-limits and session-limits configured at the sub-profile context. Enables to dynamically set host and session limits that are enforced per subscriber. All subscriber hosts and sessions that belong to the same subscriber should get the same dynamic override values. The limits are checked at host or session creation time. When a limit is reached, the host or session creation fails. See [245.26.6527.6] Alc-Sub-Host-And-Session-Limits attribute details for a detailed description of the attribute. |
|
26.10415.1 |
3GPP-IMSI |
Applies to For FWA sessions only. This attribute reflects the IMSI of the session being set up. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute imsi. |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS-Profile |
This VSA contains the QoS values signaled in the incoming GTP-C message for FWA sessions. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute gprs-negotiated-qos-profile. |
|
26.10415.20 |
3GPP-IMEISV |
This VSA contains the International Mobile Equipment Identity and its software version as signaled in the incoming GTP-C message for FWA sessions. If the corresponding GTP-C IE is not present the VSA is not included. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute imei. |
|
26.10415.21 |
3GPP-RAT-Type |
This VSA contains the Radio Access Type as signaled in the incoming GTP-C message for FWA sessions. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute rat-type. |
|
26.10415.22 |
3GPP-User-Location-Info |
This VSA contains the User Location Information as signaled in the incoming GTP-C message for FWA sessions. To include this attribute use the command configure subscriber-mgmt authentication-policy name include-radius-attribute uli. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
253 chars |
Form depends on authentication method and configuration. For example: User-Name user1@domain1.com |
|
2 |
User-Password |
string |
64 bytes |
Encrypted password For example: User-Password 4ec1b7bea6f2892fa466b461c6accc00 |
|
3 |
CHAP-Password |
octets |
16+1 bytes |
Users CHAP identifier 1 followed by the Encrypted password For example: CHAP-Password 01ef8ddc7237f4adcd991ac4c277d312e9 |
|
4 |
NAS-IP-Address |
ipaddr |
4 bytes |
# ipv4 address For example: NAS-IP-Address=192.0.2.1 |
|
5 |
NAS-Port |
integer |
4 bytes |
nas-port <binary-spec> <binary-spec> = <bit-specification> <binary-spec> <bit-specification> = 0 | 1 | <bit-origin> <bit-origin> = *<number-of-bits><origin> <number-of-bits> = [1 to 32] <origin> = s: slot number m: MDA number p: port number, lag-id, pw-id or pxc-id o: outer VLAN ID i: inner VLAN ID c: pxc-subport (a=0, b=1) Only the lower bits of the specified origin are included if the number of bits assigned for that origin is not enough to hold its maximum value. For example, when specifying 10 bits for an outer VLAN ID (*10o), then VLAN 3000 (binary 1011 1011 1000) would be reported as 952 (binary 11 1011 1000) The connector number of a connector port, such as c1 in port 1/2/c1/2 is not encoded in the NAS-Port attribute For ports on an IOM-s in an SR-s chassis, such as 2/x1/1/c4/1, the MDA number is encoded as m=2 for an MDA in position x1/1 and m=3 for an MDA in position x1/2 For example: configured nas-port *12o*10i*3s*2m*5p for SAP 2/2/4:221.7 corresponds to the binary value 000011011101 0000000111 010 10 00100 resulting in NAS-Port = 231742788 |
|
6 |
Service-Type |
integer |
2 (mandatory value) |
PPPoE and PPPoL2TP hosts only For example: Service-Type = Framed-User |
|
7 |
Framed-Protocol |
integer |
1 (fixed value) |
PPPoE and PPPoL2TP hosts only For example: Service-Type = PPP |
|
8 |
Framed-IP-Address |
ipaddr |
4 bytes |
IP address to be assigned to the subscriber host. value 255.255.255.254: indicates that the NAS should select an address for the user (for example, Assigned from a pool of addresses kept by the NAS) For example: # ip-address 10.11.12.13 Framed-IP-Address 0a0b0c0d |
|
9 |
Framed-IP-Netmask |
ipaddr |
4 bytes |
For example: Framed-IP-Netmask = 255.255.255.255 #PPPoE residential Framed-IP-Netmask = 255.255.255.0 #PPPoE Business with IPCP option 144 support Framed-IP-Netmask = 255.255.255.0 # IPoE |
|
18 |
Reply-Message |
string |
253 chars |
For example: Reply-Message MyCustomizedReplyMessage |
|
22 |
Framed-Route |
string |
max 50 Framed-Route attributes |
"<ip-prefix>[/<prefix-length>] <space> <gateway-address> [<space> <metric>] [<space> tag <space> <tag-value>] [<space> pref <space> <preference-value>]" where: <space> is a white space or blank character <ip-prefix>[/prefix-length] is the managed route to be associated with the routed subscriber host. The prefix-length is optional and if not specified, a class-full class A,B or C subnet is assumed. When specified, the prefix-length must be in the range [1..32]. <gateway-address> must be the routed subscriber host IP address. ‟0.0.0.0” is automatically interpreted as the host IPv4 address. [<metric>] (Optional) Installed in the routing table as the metric of the managed route. If not specified, metric zero is used. Value = [0 to 65535] [tag <tag-value>] (Optional) The managed route is tagged for use in routing policies. If not specified or tag-value=0, then the route is not tagged. Value = [0 to 4294967295] [pref <preference-value>] (Optional) Installed in the routing table as protocol preference for this managed route. If not specified, preference zero is used. Value = [0 to 255] For example: Framed-Route = "192.168.1.0/24 0.0.0.0" where 0.0.0.0 is replaced by host address. Default metrics are used (metric=0, preference=0 and no tag) Framed-Route = "192.168.1.0 0.0.0.0" where 192.168.1.0 is a class-C network /24 and 0.0.0.0 is replaced host address. Default metrics are used. Framed-Route = "192.168.1.0/24 192.168.1.1" where 192.168.1.1 is the host address. Default metrics are used. Framed-Route = "192.168.1.0 0.0.0.0 10 tag 3 pref 100" installs a managed route with metric=10, protocol preference = 100 and tagged with tag=3 |
|
25 |
Class |
octets |
Up to 6 attributes. Max. value length for each attribute is 253 chars |
For example: Class += My Class1 Class += MyClass2 |
|
27 |
Session-Timeout |
integer |
[0 to 2147483647] seconds |
0 = infinite (no session-timeout) [0 to 2147483647] in seconds For example: Session-Timeout = 3600 |
|
28 |
Idle-Timeout |
integer |
[60 to 15552000] seconds |
0 = infinite (no idle-timeout) [60 to 15552000] in seconds For example: Idle-Timeout = 3600 |
|
30 |
Called-Station-Id |
string |
64 chars |
LNS: L2TP Called Number AVP21 from LAC For example: Called-Station-Id = 4441212 WLAN Gateway / vRGW: AP-MAC/BRG-MAC and SSID, separated by a colon. Value "00:00:00:00:00:00" is returned when the info is not available or provided in an invalid format. For example: Called-Station-Id = 00:00:01:00:00:01:my_ssid |
|
31 |
Calling-Station-Id |
string |
64 chars |
llid | mac | remote-id | sap-id | sap-string (64 char. string configured at sap-level) For example: include-radius-attribute calling-station-id sap-id Calling-Station-Id = 1/1/2:1.1 |
|
32 |
NAS-Identifier |
string |
64 chars |
For example: NAS-Identifier = PE1-Antwerp |
|
44 |
Acct-Session-Id |
string |
22 bytes |
Internally generated 22 bytes number. For example: Acct-Session-Id = 241AFF0000003250B5F750 |
|
60 |
CHAP-Challenge |
octets |
[8 to 64] bytes |
random length For example: 20 bytes CHAP-Challenge 0xa9710d2386c3e1771b8a3ea3d4e53f2a1c7024fb |
|
61 |
NAS-Port-Type |
integer |
4 bytes Values [0 to 255] |
Values as defined in rfc-2865 and rfc-4603 For LNS, the value is set to virtual (5) For example: NAS-Port-Type = PPPoEoQinQ (34) |
|
85 |
Acct-Interim-Interval |
integer |
0, [300 to 15552000] |
A value of 0 (zero) disables the generation of interim update messages. A value of 1 to 299 is rounded to 300s (minimum CLI value). A value of 300 to 15552000 specifies the Acct-Interim-Update message interval in seconds. A value greater than 15552000 is rounded to 15552000 (maximum CLI value). For example: 1 hour interval for interim updates Acct-Interim-Interval = 3600 |
|
87 |
NAS-Port-Id |
string |
253 bytes in Access-Request messages. 128 bytes in CoA |
See [87] NAS-Port-Id attribute details for a detailed description of the attribute format. For example: NAS-Port-Id = 1/1/4:501.1001 NAS-Port-Id = LNS rtr-2#lip-203.0.113.1#rip-198.51.100.1#ltid-11381#rtid-1285#lsid-30067#rsid-19151#347 |
|
88 |
Framed-Pool |
string |
32 chars per pool name 65 chars in total (primary pool, delimiter, secondary pool) |
For example: Framed-Pool = "MyPoolname" Framed-Pool = "Pool-1#Pool-2" |
|
95 |
NAS-IPv6-Address |
ipv6addr |
16 bytes |
# ipv6 address For example: NAS-IPv6-Address = 2001:db8::1 |
|
97 |
Framed-IPv6-Prefix |
ipv6prefix |
max. 16 bytes for prefix + 1 byte for length |
PPPoE SLAAC wan-host <ipv6-prefix/prefix-length> with prefix-length 64 For example: Framed-IPv6-Prefix 2001:db8:FFF3:1::/64 |
|
99 |
Framed-IPv6-Route |
string |
max. 50 Framed-IPv6-Route attributes |
"<ip-prefix>/<prefix-length> <space> <gateway-address> [<space> <metric>] [<space> tag <space> <tag-value>] [<space> pref <space> <preference-value>]" where: <space> is a white space or blank character <ip-prefix>/<prefix-length> is the managed route to be associated with the routed subscriber host. The prefix-length must be in the range [1..128]. <gateway-address> must be the routed subscriber host IP address. ‟::” and ‟0:0:0:0:0:0:0:0” are automatically interpreted as the wan-host IPv6 address. [<metric>] (Optional) Installed in the routing table as the metric of the managed route. If not specified, metric zero is used. Value = [0 to 65535] [tag <tag-value>] (Optional) The managed route is tagged for use in routing policies. If not specified or tag-value=0, then the route is not tagged. Value = [0 to 4294967295] [pref <preference-value>] (Optional) Installed in the routing table as protocol preference for this managed route. If not specified, preference zero is used. Value = [0 to 255] For example: Framed-IPv6-Route = "2001:db8:1::/48 ::" where :: resolves in the wan-host. Default metrics are used (metric=0, preference=0 and no tag) Framed-IPv6-Route = "2001:db8:2::/48 0:0:0:0:0:0:0:0" where 0:0:0:0:0:0:0:0 resolves in the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:3::/48 0::0" where 0::0 resolves in the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:3::/48 2001:db8:aa:1::1" where 2001:db8:aa:1::1 is the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:1::/48 :: 10 tag 3 pref 100" installs a managed route with metric = 10, protocol preference = 100 and tagged with tag = 3 Framed-IPv6-Route = "2001:db8:1::/48 :: tag 5" installs a managed route with metric = 0 (default), protocol preference = 0 (default) and tagged with tag = 5 |
|
100 |
Framed-IPv6-Pool |
string |
32 chars |
For example: Framed-IPv6-Pool MyWanPoolnameIANA |
|
101 |
Error-Cause |
octets |
4 bytes |
Current supported causes are: Missing Attribute[402], NAS Identification Mismatch[403], Invalid Request[404], Unsupported Service[405], Invalid Attribute Value[407], Administratively Prohibited [501], Session Context Not Found [503], Resources Unavailable[506] For example: Error-Cause = Invalid Request |
|
123 |
Delegated-IPv6-Prefix |
ipv6prefix |
max. 16 bytes for prefix + 1 Byte for length |
<ipv6-prefix/prefix-length> with prefix-length [48 to 64] For example: Delegated-IPv6-Prefix 2001:DB8:173A:100::/56 |
|
26.2352.1 |
Client-DNS-Pri |
ipaddr |
4 bytes |
For example: Client-DNS-Pri = 198.51.100.1 |
|
26.2352.2 |
Client-DNS-Sec |
ipaddr |
4 bytes |
For example: Client-DNS-Sec = 198.51.100.2 |
|
26.2352.36 |
Ip-Address-Pool-Name |
string |
65 chars |
For example: Ip-Address-Pool-Name = Address_Pool_1 |
|
26.2352.99 |
RB-Client-NBNS-Pri |
ipaddr |
4 bytes |
For example: RB-Client-NBNS-Pri = 198.51.100.1 |
|
26.2352.100 |
RB-Client-NBNS-Sec |
ipaddr |
4 bytes |
For example: RB-Client-NBNS-Sec = 198.51.100.2 |
|
26.3561.1 |
Agent-Circuit-Id |
string |
247 chars |
format see also RFC4679 # Ethernet/DSL <Access-Node-Identifier><eth slot/port[:vlan-id]> For example: ethernet dslam1 slot 2 port 1 vlan 100 Agent-Circuit-Id = dslam1 eth 2/1:100 |
|
26.3561.2 |
Agent-Remote-Id |
string |
247 chars |
Format see also RFC 4679 For example: Agent-Remote-Id = MyRemoteId |
|
26.3561.129 |
Actual-Data-Rate-Upstream |
integer |
4294967295 |
For example: Actual-Data-Rate-Upstream = 1000000 |
|
26.3561.130 |
Actual-Data-Rate-Downstream |
integer |
4294967295 |
For example: Actual-Data-Rate-Downstream = 5000000 |
|
26.3561.131 |
Minimum-Data-Rate-Upstream |
integer |
4294967295 |
For example: Minimum-Data-Rate-Upstream = 1000 |
|
26.3561.132 |
Minimum-Data-Rate-Downstream |
integer |
4294967295
|
For example: Minimum-Data-Rate-Downstream = 1000 |
|
26.3561.133 |
Attainable-Data-Rate-Upstream |
integer |
4294967295
|
For example: Attainable-Data-Rate-Downstream = 1000 |
|
26.3561.134 |
Attainable-Data-Rate-Downstream |
integer |
4294967295
|
For example: Minimum-Data-Rate-Upstream = 1000 |
|
26.3561.135 |
Maximum-Data-Rate-Upstream |
integer |
4294967295
|
For example: Maximum-Data-Rate-Upstream = 1000 |
|
26.3561.136 |
Maximum-Data-Rate-Downstream |
integer |
4294967295
|
For example: Maximum-Data-Rate-Downstream = 1000 |
|
26.3561.137 |
Minimum-Data-Rate-Upstream-Low-Power |
integer |
4294967295
|
For example: Minimum-Data-Rate-Upstream-Low-Power = 1000 |
|
26.3561.138 |
Minimum-Data-Rate-Downstream-Low-Power |
integer |
4294967295
|
For example: Minimum-Data-Rate-Downstream-Low-Power = 1000 |
|
26.3561.139 |
Maximum-Interleaving-Delay-Upstream |
integer |
4294967295 |
For example: Maximum-Interleaving-Delay-Upstream = 10 |
|
26.3561.140 |
Actual-Interleaving-Delay-Upstream |
integer |
4294967295 |
For example: Actual-Interleaving-Delay-Upstream = 10 |
|
26.3561.141 |
Maximum-Interleaving-Delay-Downstream |
integer |
4294967295 |
For example: Maximum-Interleaving-Delay-Downstream = 10 |
|
26.3561.142 |
Actual-Interleaving-Delay-Downstream |
integer |
4294967295 |
For example: Actual-Interleaving-Delay-Downstream = 10 |
|
26.3561.144 |
Access-Loop-Encapsulation |
octets |
3 bytes |
<Data Link><Encaps-1><Encaps-2> <Data Link>: AAL5(0), Ethernet(1) <Encaps 1>: NotAvailable(0), Untagged Ethernet(1), Single-Tagged Ethernet(2) <Encaps 2>: Not Available(0), PPPoA LLC(1), PPPoA Null(2), IPoA LLC(3), IPoA Null(4), Ethernet over AAL5 LLC w FCS(5), Ethernet over AAL5 LLC without FCS(6), Ethernet over AAL5 Null w FCS(7), Ethernet over AAL5 Null without FCS(8) For example: Ethernet, Single-Tagged Ethernet, Not Available Access-Loop-Encapsulation = 0x010200 |
|
26.3561.254 |
IWF-Session |
octets |
len 0 |
For example: IWF-Session |
|
26.4874.2 |
ERX-Address-Pool-Name |
string |
65 chars |
For example: ERX-Address-Pool-Name = MyPoolname |
|
26.4874.4 |
ERX-Primary-Dns |
ipaddr |
4 bytes |
For example: ERX-Primary-Dns = 198.51.100.1 |
|
26.4874.5 |
ERX-Secondary-Dns |
ipaddr |
4 bytes |
For example: ERX-Secondary-Dns = 198.51.100.2 |
|
26.4874.6 |
ERX-Primary-Wins |
ipaddr |
4 bytes |
For example: ERX-Primary-Wins = 198.51.100.1 |
|
26.4874.7 |
ERX-Secondary-Wins |
ipaddr |
4 bytes |
For example: ERX-Ipv6-Primary-Dns = 198.51.100.2 |
|
26.4874.47 |
ERX-Ipv6-Primary-Dns |
ipv6addr |
16 bytes |
For example: ERX-Secondary-Wins = 2001:db8:1::1 |
|
26.4874.48 |
ERX-Ipv6-Secondary-Dns |
ipv6addr |
16 bytes |
For example: ERX-Ipv6-Secondary-Dns = 2001:db8:2::1 |
|
26.6527.9 |
Alc-Primary-Dns |
ipaddr |
4 bytes |
For example: Alc-Primary-Dns = 198.51.100.1 |
|
26.6527.10 |
Alc-Secondary-Dns |
ipaddr |
4 bytes |
For example: Alc-Secondary-Dns = 1198.51.100.2 |
|
26.6527.11 |
Alc-Subsc-ID-Str |
string |
64 chars |
For example: Alc-Subsc-ID-Str = MySubscriberId |
|
26.6527.12 |
Alc-Subsc-Prof-Str |
string |
32 chars |
For example: Alc-Subsc-Prof-Str = MySubProfile |
|
26.6527.13 |
Alc-SLA-Prof-Str |
string |
32 chars |
For example: Alc-SLA-Prof-Str = MySlaProfile |
|
26.6527.14 |
Alc-Force-Renew |
string |
no limits |
The attribute value is ignored For example: Alc-Force-Renew = anything Alc-Force-Renew = 1 |
|
26.6527.16 |
Alc-ANCP-Str |
string |
63 chars |
format see also RFC4679 # Ethernet/DSL <Access-Node-Identifier><eth slot/port[:vlan-id]> For example: If [26.3561.1] Agent-Circuit-Id = dslam1 eth 2/1:100 then put Alc-ANCP-Str = dslam1 eth 2/1:100 |
|
26.6527.18 |
Alc-Default-Router |
ipaddr |
4 bytes |
For example: Alc-Default-Router = 10.0.255.254 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
string |
6 bytes |
For example: Alc-Client-Hardware-Addr = 00:00:00:00:00:01 |
|
26.6527.28 |
Alc-Int-Dest-Id-Str |
string |
32 chars |
For example: Alc-Int-Dest-Id-Str= AccessNode1 |
|
26.6527.29 |
Alc-Primary-Nbns |
ipaddr |
4 bytes |
For example: Alc-Primary-Nbns = 198.51.100.1 |
|
26.6527.30 |
Alc-Secondary-Nbns |
ipaddr |
4 bytes |
For example: Alc-Secondary-Nbns = 198.51.100.2 |
|
26.6527.34 |
Alc-PPPoE-PADO-Delay |
integer |
[0 to 30] deci-seconds |
For example: 3 seconds pado-delay Alc-PPPoE-PADO-Delay = 30 |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
string |
247 chars |
For example: Alc-PPPoE-Service-Name = MyServiceName |
|
26.6527.36 |
Alc-DHCP-Vendor-Class-Id |
string |
247 chars |
For example: Alc-DHCP-Vendor-Class-Id = My-DHCP-VendorClassId |
|
26.6527.45 |
Alc-App-Prof-Str |
string |
16 bytes |
For example: Alc-App-Prof-Str = MyAppProfile |
|
26.6527.98 |
Alc-Force-Nak |
string |
no limits |
The attribute value is ignored For example: Alc-Force-Nak = anything Alc-Force-Nak = 1 |
|
26.6527.99 |
Alc-Ipv6-Address |
ipv6addr |
16 bytes |
For example: Alc-Ipv6-Address 2001:db8:FFF5::1 |
|
26.6527.100 |
Alc-Serv-Id |
integer |
2147483647 ID |
For example: Alc-Serv-Id = 100 |
|
26.6527.101 |
Alc-Interface |
string |
32 chars |
For example: Alc-Interface = myGTPgroupinterface |
|
26.6527.102 |
Alc-ToServer-Dhcp-Options |
octets |
5 attributes 247 bytes/ attribute total 1235 bytes (includes 4B magic cookie) DSM: 2 attributes 247 bytes/attribute 494 bytes total |
For example: DHCPv4 Discover , option-60 [Class-identifier-option] = DHCP-VendorClassId ; Agent-Circuit-Id = circuit10;Agent-Remote-Id = remote10 Alc-ToServer-Dhcp-Options = 66313501013c12444843502d56656e646f72436c617373496452150109636972637569743130020872656d6f74653130 Fragmented DHCP packets are not supported. For DHCP packets totaling over 1500 bytes in size, DHCP signaling using in-band interface is recommended. |
|
26.6527.103 |
Alc-ToClient-Dhcp-Options |
octets |
8 attributes 247 bytes/attribute 1729 bytes total (for example, 7 attributes with the maximum length) |
For example: Insert DHCP Option 121, length=7, 16.192.168 10.1.255.254 # Classless Static Route: 192.168.0.0/16 10.1.255.254 Alc-ToClient-Dhcp-Options = 0x790710C0A80A01FFFE Fragmented DHCP packets are not supported. For DHCP packets totaling over 1500 bytes in size, DHCP signaling using in-band interface is recommended. |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
ipv6addr |
16 bytes |
For example: Alc-Ipv6-Primary-Dns = 2001:db8:1::1 |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
ipv6addr |
16 bytes |
For example: Alc-Ipv6-Secondary-Dns = 2001:db8:2::1 |
|
26.6527.126 |
Alc-Subscriber- QoS-Override |
string |
18 attributes |
<direction>:<QoS object>:[<id or name>:][<parameter>=value,...] [iIeE]:[qQ]:<queue-id>:(pir|cir|mbs|cbs|burst_limit|parent_weight|cir_parent_weight) [eE]:[qQ]:<queue-id>:(wrr_weight|class_weight) [iIeE]:[pP]:<policer-id>:(pir|cir|mbs|cbs|parent_weight|cir_parent_weight) [eE]:[rR]:(rate) [eE]:[lL]:(rate) [eE]:[gG]:<wrr-group-id>:(rate|class_weight) [iIeE]:[aA]:root|<intermediate arbiter name>:(rate) [iIeE]:[sS]:<scheduler-name>:(rate|cir) See [26.6527.126] Alc-Subscriber-QoS-Override attribute details for a detailed description of the attribute format. For example: ingress queue 1 pir, cir, mbs, cbs and egress aggregate rate overrides Alc-Subscriber-QoS-Override += i:q:1:pir=40000,cir=20000,mbs=32000,cbs=16 000, Alc-Subscriber-QoS-Override += e:r:rate=800000 |
|
26.6527.131 |
Alc-Delegated-IPv6-Pool |
string |
32 chars |
For example: Alc-Delegated-IPv6-Pool = MyLanPoolnameIAPD |
|
26.6527.132 |
Alc-Access-Loop-Rate-Down |
integer |
[1 to 100000] kb/s |
For example: rate 4M b/s Alc-Access-Loop-Rate-Down = 4000 |
|
26.6527.133 |
Alc-Access-Loop-Encap-Offset |
octets |
3 bytes |
<Data Link><Encaps-1><Encaps-2> <Data Link>: AAL5(0), Ethernet(1) <Encaps 1>: NotAvailable(0), Untagged Ethernet(1), Single-Tagged Ethernet(2) <Encaps 2>: Not Available(0), PPPoA LLC(1), PPPoA Null(2), IPoA LLC(3), IPoA Null(4), Ethernet over AAL5 LLC w FCS(5), Ethernet over AAL5 LLC without FCS(6), Ethernet over AAL5 Null with FCS(7), Ethernet over AAL5 Null without FCS(8) For example: # pppoe-tagged -> 01,02,00 Alc-Access-Loop-Encap-Offset = 0x010200 |
|
26.6527.135 |
Alc-PPP-Force-IPv6CP |
integer |
[0 to 4294967295] |
0 : False - start IPv6CP negotiation only when IPv6 attributes are obtained in authentication >0 : True - also start IPv6CP negotiation when no IPv6 attributes are obtained in authentication For example: Alc-PPP-Force-IPv6CP = 1 |
|
26.6527.136 |
Alc-Onetime-Http-Redirection-Filter-Id |
string |
249 bytes |
‟Ingr-v4:<number>” [1 to 65535] = apply this filter-id as one-time-http-redirect-filter 0 = Remove the current redirection filter and replace it with sla-profile ingress filter For example: Alc-Onetime-Http-Redirection-Filter-Id = Ingr-v4:1000 |
|
26.6527.146 |
Alc-Wlan-APN- Name |
string |
247 bytes |
The APN is directly reflected as present in the incoming GTP-C message. For example: Alc-Wlan-APN-Name = demo.mnc001.mcc001.gprs |
|
26.6527.147 |
Alc-MsIsdn |
string |
9 to 15 digits |
Textual representation of the MSISDN in decimal format. For example: Alc-MsIsdn = 13109976224 |
|
26.6527.160 |
Alc-Relative-Session-Timeout |
integer |
[0 to 2147483647] seconds |
0 = infinite (no session-timeout) [0 to 2147483647] in seconds For example: Alc-Relative-Session-Timeout = 3600 |
|
26.6527.161 |
Alc-Delegated-IPv6-Prefix-Length |
integer |
[48 to 64] DPL length |
For example: Alc-Delegated-IPv6-Prefix-Length = 48 |
|
26.6527.174 |
Alc-Lease-Time |
integer |
[0 to 4294967295] seconds |
0 : fallback to the default lease-time of 7 days. The maximum value 4294967295 corresponds with a lease-time > 9999 days (24855d 03h). [1 to 4294967295] lease-time in seconds For example: Alc-Lease-Time = 3600 |
|
26.6527.175 |
Alc-DSL-Line-State |
integer |
4 bytes |
1=showtime, 2-idle, 3=silent For example: Alc-DSL-Line-State = SHOWTIME |
|
26.6527.176 |
Alc-DSL-Type |
integer |
4 bytes |
0=other, 1=ADSL1, 2=ADSL2, 3=ADSL2PLUS, 4=VDSL1, 5=VDSL2, 6=SDSL For example: Alc-DSL-Type = VDSL2 |
|
26.6527.177 |
Alc-Portal-Url |
string |
247 chars |
URL string. An empty string removes the override. For example: Alc-Portal-Url = ‟http://portal.com/welcome/sub=$SUB” |
|
26.6527.178 |
Alc-Ipv6-Portal-Url |
string |
247 chars |
URL string. An empty string removes the override. For example: Alc-IPv6-Portal-Url = ‟http://portal.com/welcome/sub=$SUB” |
|
26.6527.180 |
Alc-SAP-Session-Index |
integer |
4 bytes |
For example: Alc-SAP-Session-Index = 5 |
|
26.6527.181 |
Alc-SLAAC-IPv6-Pool |
string |
32 chars |
DHCPv6 server pool name. Pool name "_tmnx_auto" indicates that the pool is automatically selected by the system, for example for use with IPv6 firewall. For example: Alc-SLAAC-IPv6-Pool = "MySlaacPoolname" |
|
26.6527.183 |
Alc-WPP-Error-Code |
integer |
4 bytes |
A non-zero unsigned integer. Valid values are 1, 2, or 4 |
|
26.6527.185 |
Alc-Onetime-Http-Redirect-Reactivate |
string |
247 chars |
The value of the attribute is opaque. Its presence in a RADIUS CoA triggers the action. |
|
26.6527.191 |
Alc-ToServer-Dhcp6-Options |
octets |
5 attributes 247 bytes/ attribute 1235 bytes total DSM: 2 attributes 247 bytes/attribute 494 bytes total |
For example, when the DHCPv6 solicit contains following options: Option : ELAPSED_TIME (8), Length : 2 Time : 0 seconds Option : CLIENTID (1), Length : 10 LL : HwTyp=0001,LL=005100000002 00030001005100000002 Option : ORO (6), Length : 4 Requested Option : IA_NA (3) Requested Option : IA_PD (25) Option : IA_NA (3), Length : 12 IAID : 0 Time1: 0 seconds Time2: 0 seconds Option : IA_PD (25), Length : 12 IAID : 1 Time1: 0 seconds Time2: 0 seconds Alc-ToServer-Dhcp6-Options = 0x0008000200000001000a0003000100510000000200060004000300190003000c0000000000000000000000000019000c000000010000000000000000 Fragmented DHCP packets are not supported. For DHCP packets totaling over 1500 bytes in size, DHCP signaling using in-band interface is recommended. |
|
26.6527.192 |
Alc-ToClient-Dhcp6-Options |
octets |
8 attributes 247 bytes/ attribute 1729 bytes total (for example, 7 attributes with the maximum length) |
For example, to insert following option: Option: Simple Network Time Protocol Server (31) Length: 32 Value: SNTP servers address: 2001:db8:cafe:1::1 SNTP servers address: 2001:db8:cafe:2::1 Alc-ToClient-Dhcp6-Options = 0x001F002020010DB8CAFE0001000000000000000120010DB8CAFE00020000000000000001 Fragmented DHCP packets are not supported. For DHCP packets totaling over 1500 bytes in size, DHCP signaling using in-band interface is recommended. |
|
26.6527.200 |
Alc-v6-Preferred-Lifetime |
integer |
[300 to 315446399] seconds |
For example: Alc-v6-Preferred-Lifetime = 3600 |
|
26.6527.201 |
Alc-v6-Valid-Lifetime |
integer |
[300 to 315446399] seconds |
For example: Alc-v6-Valid-Lifetime = 86400 |
|
26.6527.202 |
Alc-Dhcp6-Renew-Time |
integer |
[0 to 604800] seconds |
For example: Alc-Dhcp6-Renew-Time = 1800 |
|
26.6527.203 |
Alc-Dhcp6-Rebind-Time |
integer |
[0 to 1209600] seconds |
For example: Alc-Dhcp6-Rebind-Time = 2880 |
|
26.6527.217 |
Alc-UPnP-Sub-Override-Policy |
string |
32 chars |
UPnP policy name or special values ‟_tmnx_no_override” or ‟_tmnx_disabled”. For example: Alc-UPnP-Sub-Override-Policy = ‟my-UPnP-policy” |
|
26.6527.228 |
Alc-Trigger-Acct-Interim |
string |
247 chars |
Free formatted string that is echoed in the triggered interim update message. For example: Alc-Trigger-Acct-Interim = "CoA - Filter update" |
|
26.6527.232 |
Alc-Acct-Interim-IvI |
integer |
1 VSA per tag per message Max. tag 1- 5 Value [300 to 15552000] |
Tagged attribute A value of 0 (zero) disables the generation of interim update messages. A value [1 to 299] seconds is rounded to 300s (min. CLI value) and a value > 15552000 seconds (max. CLI value) is rounded to the max. CLI value. An untagged attribute or tag value of 0 (zero) and tag values greater than 5 are not supported and result in a host setup failure or CoA Reject. A tag value of [1 to 5] changes the update interval of the corresponding accounting policy specified in the subscriber profile. For example: Alc-Acct-Interim-lvl:1 += 300 Alc-Acct-Interim-lvl:2 += 600 |
|
26.6527.234 |
Alc-DNAT-Override |
string |
247 chars |
{DNAT-state | DNAT-ip-addr}[,nat-policy-name] DNAT state = none | disable
DNAT-ip-addr = IPv4 address in dotted format (a.b.c.d)
DNAT-state and DNAT-ip-addr parameters are mutually exclusive nat-policy-name = name of the nat-policy. This is an optional parameter and if not specified then the default nat-policy is assumed. If two parameters are present simultaneously within the Alc-DNAT-Override attribute, then they are separated by a comma with no white spaces used as delimiter. For example: Alc-DNAT-Override=none This re-enables DNAT functionality in the default nat-policy, assuming that DNAT was previously disabled using the Alc-DNAT-Override=disable attribute submitted either in Access-Accept or in a previous CoA. If the none value was received at the time when the DNAT is already enabled, a CoA ACK is sent back to the originator. This negates any previous DNAT-related override in the default nat-policy. The DNAT functionality is set as originally defined in the default nat-policy. If the DNAT classifier is not present in the default nat-policy when this CoA is received, an error log message is raised. |
|
26.6527.234 |
— |
— |
— |
For example: Alc-DNAT-Override =198.51.100.1, nat-pol-1 This changes the default DNAT IP address to 198.51.100.1 in the specified nat-policy with name nat-pol-1. DNAT is implicitly enabled in case that it was disabled before this CoA was received. For example: Alc-DNAT-Override = none, 198.51.100.1 DNAT-state and DNAT-ip-addr parameters are mutually exclusive within the same Alc-DNAT-Override attribute. A CoA ACK is returned to the RADIUS server and an error event is logged. |
|
26.6527.238 |
Alc-Remove- Override |
string |
Single attribute identifier per attribute Multiple attributes per message |
[<action><space>]<attribute identifier> See [26.6527.238] Alc-Remove-Override attribute details for a detailed description of the attribute format and its possible values For example: To deactivate an ESM L2TP steering profile: Alc-Remove-Override = "deactivate 241.26.6527.25” |
|
26.6527.242 |
Alc-Radius-Py |
octets |
247 bytes |
Free formatted attribute value for use with a corresponding RADIUS Python script. |
|
26.6527.244 |
Alc-Force-DHCP-Relay |
string |
max. 2 attributes fixed values |
Fixed values: ‟relay-ipv4” – sets the lease origin to DHCP ‟relay-ipv6” – sets the lease origin to DHCP6 For example: Alc-Force-DHCP-Relay = ‟relay-ipv4” |
|
241.26.6527.16 |
Alc-IPv6-Router-Adv-Policy |
string |
32 chars |
The Router Advertisement policy name. For example: Alc-IPv6-Router-Adv-Policy = ‟RA-policy-01” |
|
241.26.6527.17 |
Alc-Nat-Outside-IPs |
string |
max. 4 attributes |
<outside IP address>;<NAT policy name> For example: Alc-Nat-Outside-IPs += 192.0.2.1;nat-policy-1 Alc-Nat-Outside-IPs += 198.51.100.1;nat-policy-2 |
|
241.26.6527.18 |
Alc-Mld-Import-Policy |
string |
32 chars Up to 14 attributes |
The MLD import policy name. A subscriber can have a list of up to 14 MLD import policies associated from Radius. Each MLD policy must be included in a separate attribute. For example: Alc-Mld-Import-Policy=”ch-lineup-01” |
|
241.26.6527.19 |
Alc-Bonding-Id |
— |
— |
Attribute limits are defined in the Bonding section, see Bonding (limits). |
|
241.26.6527.22 |
Alc-Bonding-Reference-Rate |
— |
— |
Attribute limits are defined in the Bonding section, see Bonding (limits). |
|
241.26.6527.27 |
Alc-IPv6-Sub-If-Prefix |
string |
127 chars Max. 1 attribute |
<IPv6 prefix>/<prefix length><space><type> Where <type> is either pd, wan-host, or wan-host pd. When not specified, pd is assumed. A maximum of one prefix per subscriber host or session can be specified and up to 24 prefixes per system or per subscriber interface. For example: Alc-IPv6-Sub-If-Prefix = ‟2001:db8::/32 pd” Alc-IPv6-Sub-If-Prefix = ‟2001:db8::/32 wan-host pd” Alc-IPv6-Sub-If-Prefix = ‟2001:db8::/32” |
|
241.26.6527.35 |
Alc-Mld-Import-Policy-Modif |
string |
34 chars Max. 5 attribute |
<action>:<MLD policy name> where <action> is a — Adds the MLD policy to the list of import policies. s – Subtracts (removes) the MLD policy from the list of import policies. For example: Alc-Mld-Import-Policy-Modif=”a:ch-lineup-01” Alc-Mld-Import-Policy-Modif=”s:ch-lineup-02” |
|
241.26.6527.37 |
Alc-VAS-IPv4-Filter |
string |
1..32 characters |
Name of a VAS filter as defined under configure subscriber-mgmt isa-service-chaining vas-filter For example: Alc-VAS-IPv4-Filter="vas_filter_1" |
|
241.26.6527.38 |
Alc-VAS-NSH-IPv4-Opaque-Meta-Data |
octets |
16 bytes |
Opaque data in network order to send in NSH. This is only applicable if insert-nsh is correctly configured and overrides insert-subscriber-id or opaque data configured under configure subscriber-mgmt isa-service-chaining vas-filter filter-name entry id action {downstream | upstream} insert-nsh meta-data. |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
string |
64 SPFs |
See [241.26.6527.39] Alc-Static-Port-Forward attribute details for a detailed description of the attribute format and its possible values For example: Add a Layer 2–aware NAT SPF to open up TCP port 80 (HTTP) on the outside and forward it to port 8080 on ip 10.1.0.1 on the inside: Alc-Static-Port-Forward = "c tcp 10.1.0.1 8080->80" |
|
241.26.6527.40 |
Alc-IPv6-Slaac-Replacement-Prefix |
ipv6prefix |
Max. 16 Bytes for prefix + 1 Byte for length |
<ipv6-prefix/prefix-length> with prefix-length 64 For example: Alc-IPv6-Slaac-Replacement-Prefix = 2001:db8:FFF3:1::/64 |
|
241.26.6527.47 |
Alc-SPI-Sharing-Id |
string |
Max. 247 chars |
To set or override the SLA Profile Instance (SPI) sharing to SPI sharing per group: "group:<group id>" where <group id> is an unsigned integer value in the range [0..65535] For example: Alc-SPI-Sharing-Id = "group:100" To set or override the SLA Profile Instance (SPI) sharing to the default SPI sharing method as specified in the SLA profile def-instance-sharing: "default" For example: Alc-SPI-Sharing-Id = "default" |
|
241.26.6527.57 |
Alc-Gtp-Skip-Ipv4-Alloc-Override |
integer |
[1 | 2] |
1 = on, overrides the CLI parameter skip-gtp-ipv4-alloc for this session. The IPv4 address is assigned using GTP signaling, even if the request does not contain the "IP address allocation using NAS signaling" (0x000a) PCO. 2 = off, do not override the CLI parameter skip-gtp-ipv4-alloc for this session. The effect is the same as not including the attribute. For example: Alc-Gtp-Skip-Ipv4-Alloc-Override = 1 |
|
241.26.6527.58 |
Alc-Change-Reporting-Action |
integer |
[0 | 3 | 4 | 6] |
0 = stop-reporting. Disables change reporting 1 = cgi-sai. Unexpected value 2 = rai. Unexpected value 3 = tai. Enables TAI change reporting 4 = ecgi. Enables ECGI change reporting 5 = cgi-sai-rai. Unexpected value 6 = tai-ecgi. Enables TAI and ECGI change reporting Unexpected values are accepted and reflected in GTP but does not trigger any location reporting by the system. For example: Alc-Change-Reporting-Action = 3 |
|
241.26.6527.62 |
Alc-Host-DNAT-Override |
integer |
[1 | 2] |
1 = enable dnat override 2 = disable dnat override For example: Alc-Host-DNAT-Override = 1 |
|
241.26.6527.71 |
Alc-Host-DNAT-Default-Address-Override |
ipaddr |
4 bytes |
A valid unicast IPv4 address For example: Alc-Host-DNAT-Default-Address-Override = 198.51.100.1 |
|
241.26.6527.92 |
Alc-PPPoE-LCP-Keepalive-Interval |
integer |
[4..300] seconds |
For example: Alc-PPPoE-LCP-Keepalive-Interval 10 |
|
241.26.6527.93 |
Alc-PPPoE-LCP-Keepalive-Multiplier |
integer |
[1..5] |
For example: Alc-PPPoE-LCP-Keepalive-Multiplier 2 |
|
245.26.6527.5 |
Alc-Spi-Host-And-Session-Limits |
tlv |
23 attributes |
See [245.26.6527.5] Alc-Spi-Host-And-Session-Limits attribute details for a detailed description of the attribute format. |
|
245.26.6527.6 |
Alc-Sub-Host-And-Session-Limits |
tlv |
23 attributes |
See [245.26.6527.5] Alc-Spi-Host-And-Session-Limits attribute details for a detailed description of the attribute format. |
|
26.10415.1 |
3GPP-IMSI |
string |
1 to 15 digits |
3GPP vendor specific attribute as defined in 3GPP TS 29.061. For example: 3GPP-IMSI = 001001123456789 |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS- Profile |
string |
length as defined in the 3GPP TS 29.061 |
Specified in TS 29.061 version 8.5.0 Release 8 section 16.4.7.2 For example: 3GPP-GPRS-Negotiated-QoS-Profile = 08-4D020000002710000000138800000001f40000000bb8 |
|
26.10415.20 |
3GPP-IMEISV |
string |
14 to 16 digits |
3GPP vendor specific attribute as defined in TS 29.061 |
|
26.10415.21 |
3GPP-RAT-Type |
octets |
1 octet [0..255] |
Specifies the Radio Access Technology type, see 3GPP 29.061 section 16.4.7.2. for more details For example (E-UTRAN RAT Type): 3GPP-RAT-Type = 0x06 |
|
26.10415.22 |
3GPP-User- Location-Info |
octets |
247 bytes |
3GPP vendor specific attribute as defined in TS 29.061 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
1 |
User-Name |
1 |
0-1 |
0-1 |
|
2 |
User-Password |
0-1 |
0 |
0 |
|
3 |
CHAP-Password |
0-1 |
0 |
0 |
|
4 |
NAS-IP-Address |
0-1 |
0 |
0 |
|
5 |
NAS-Port |
0-1 |
0 |
0 |
|
6 |
Service-Type |
0-1 |
0-1 |
0-1 |
|
7 |
Framed-Protocol |
0-1 |
0-1 |
0-1 |
|
8 |
Framed-IP-Address |
0 |
0-1 |
0-11 |
|
9 |
Framed-IP-Netmask |
0 |
0-1 |
0 |
|
18 |
Reply-Message |
0 |
0-1 |
0 |
|
22 |
Framed-Route |
0 |
0+ |
0 |
|
25 |
Class |
0 |
0+ |
0+ |
|
27 |
Session-Timeout |
0 |
0-1 |
0-1 |
|
28 |
Idle-Timeout |
0 |
0-1 |
0-1 |
|
30 |
Called-Station-Id |
0-1 |
0 |
0-1 |
|
31 |
Calling-Station-Id |
0-1 |
0-1 |
0-1 |
|
32 |
NAS-Identifier |
0-1 |
0 |
0 |
|
44 |
Acct-Session-Id |
0-1 |
0 |
0-11 |
|
60 |
CHAP-Challenge |
0-1 |
0 |
0 |
|
61 |
NAS-Port-Type |
0-1 |
0 |
0-1 |
|
85 |
Acct-Interim-Interval |
0 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
0-1 |
0 |
0-11 |
|
88 |
Framed-Pool |
0 |
0-1 |
0 |
|
95 |
NAS-IPv6-Address |
0-1 |
0 |
0 |
|
97 |
Framed-IPv6-Prefix |
0 |
0-1 |
0-11 |
|
99 |
Framed-IPv6-Route |
0 |
0+ |
0 |
|
100 |
Framed-IPv6-Pool |
0 |
0-1 |
0 |
|
101 |
Error-Cause |
0 |
0 |
0-1 |
|
123 |
Delegated-IPv6-Prefix |
0 |
0-1 |
0-11 |
|
26.2352.1 |
Client-DNS-Pri |
0 |
0-1 |
0-1 |
|
26.2352.2 |
Client-DNS-Sec |
0 |
0-1 |
0-1 |
|
26.2352.36 |
Ip-Address-Pool-Name |
0 |
0-1 |
0 |
|
26.2352.99 |
RB-Client-NBNS-Pri |
0 |
0-1 |
0-1 |
|
26.2352.100 |
RB-Client-NBNS-Sec |
0 |
0-1 |
0-1 |
|
26.3561.1 |
Agent-Circuit-Id |
0-1 |
0-1 |
0 |
|
26.3561.2 |
Agent-Remote-Id |
0-1 |
0 |
0 |
|
26.3561.129 |
Actual-Data-Rate-Upstream |
0-1 |
0 |
0 |
|
26.3561.130 |
Actual-Data-Rate-Downstream |
0-1 |
0 |
0 |
|
26.3561.131 |
Minimum-Data-Rate-Upstream |
0-1 |
0 |
0 |
|
26.3561.132 |
Minimum-Data-Rate-Downstream |
0-1 |
0 |
0 |
|
26.3561.133 |
Attainable-Data-Rate-Upstream |
0-1 |
0 |
0 |
|
26.3561.134 |
Attainable-Data-Rate-Downstream |
0-1 |
0 |
0 |
|
26.3561.135 |
Maximum-Data-Rate-Upstream |
0-1 |
0 |
0 |
|
26.3561.136 |
Maximum-Data-Rate-Downstream |
0-1 |
0 |
0 |
|
26.3561.137 |
Minimum-Data-Rate-Upstream-Low-Power |
0-1 |
0 |
0 |
|
26.3561.138 |
Minimum-Data-Rate-Downstream-Low-Power |
0-1 |
0 |
0 |
|
26.3561.139 |
Maximum-Interleaving-Delay-Upstream |
0-1 |
0 |
0 |
|
26.3561.140 |
Actual-Interleaving-Delay-Upstream |
0-1 |
0 |
0 |
|
26.3561.141 |
Maximum-Interleaving-Delay-Downstream |
0-1 |
0 |
0 |
|
26.3561.142 |
Actual-Interleaving-Delay-Downstream |
0-1 |
0 |
0 |
|
26.3561.144 |
Access-Loop-Encapsulation |
0-1 |
0 |
0 |
|
26.3561.254 |
IWF-Session |
0-1 |
0-1 |
0 |
|
26.4874.2 |
ERX-Address-Pool-Name |
0 |
0-1 |
0 |
|
26.4874.4 |
ERX-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.4874.5 |
ERX-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.4874.6 |
ERX-Primary-Wins |
0 |
0-1 |
0-1 |
|
26.4874.7 |
ERX-Secondary-Wins |
0 |
0-1 |
0-1 |
|
26.4874.47 |
ERX-Ipv6-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.4874.48 |
ERX-Ipv6-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.9 |
Alc-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.10 |
Alc-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.11 |
Alc-Subsc-ID-Str |
0 |
0-1 |
0-11 |
|
26.6527.12 |
Alc-Subsc-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.13 |
Alc-SLA-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.14 |
Alc-Force-Renew |
0 |
0 |
0-1 |
|
26.6527.16 |
Alc-ANCP-Str |
0 |
0-1 |
0-1 |
|
26.6527.18 |
Alc-Default-Router |
0 |
0-1 |
0 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
0-1 |
0-1 |
0-1 |
|
26.6527.28 |
Alc-Int-Dest-Id-Str |
0 |
0-1 |
0-1 |
|
26.6527.29 |
Alc-Primary-Nbns |
0 |
0-1 |
0-1 |
|
26.6527.30 |
Alc-Secondary-Nbns |
0 |
0-1 |
0-1 |
|
26.6527.34 |
Alc-PPPoE-PADO-Delay |
0 |
0-1 |
0 |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
0-1 |
0 |
0 |
|
26.6527.36 |
Alc-DHCP-Vendor-Class-Id |
0-1 |
0 |
0 |
|
26.6527.45 |
Alc-App-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.98 |
Alc-Force-Nak |
0 |
0 |
0-1 |
|
26.6527.99 |
Alc-Ipv6-Address |
0 |
0-1 |
0-11 |
|
26.6527.100 |
Alc-Serv-Id |
0 |
0-1 |
0 |
|
26.6527.101 |
Alc-Interface |
0 |
0-1 |
0 |
|
26.6527.102 |
Alc-ToServer-Dhcp-Options |
0+ |
0 |
0 |
|
26.6527.103 |
Alc-ToClient-Dhcp-Options |
0 |
0+ |
0 |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.126 |
Alc-Subscriber-QoS-Override |
0 |
0-1 |
0-1 |
|
26.6527.131 |
Alc-Delegated-IPv6-Pool |
0 |
0-1 |
0 |
|
26.6527.132 |
Alc-Access-Loop-Rate-Down |
0 |
0-1 |
0-1 |
|
26.6527.133 |
Alc-Access-Loop-Encap-Offset |
0 |
0-1 |
0 |
|
26.6527.135 |
Alc-PPP-Force-IPv6CP |
0 |
0-1 |
0 |
|
26.6527.136 |
Alc-Onetime-Http-Redirection-Filter-Id |
0 |
0-1 |
0-1 |
|
26.6527.146 |
Alc-Wlan-APN-Name |
0-1 |
0 |
0 |
|
26.6527.147 |
Alc-MsIsdn |
0-1 |
0 |
0 |
|
26.6527.160 |
Alc-Relative-Session-Timeout |
0 |
0-1 |
0-1 |
|
26.6527.161 |
Alc-Delegated-IPv6-Prefix-Length |
0 |
0-1 |
0 |
|
26.6527.174 |
Alc-Lease-Time |
0 |
0-1 |
0 |
|
26.6527.175 |
Alc-DSL-Line-State |
0-1 |
0 |
0 |
|
26.6527.176 |
Alc-DSL-Type |
0-1 |
0 |
0 |
|
26.6527.177 |
Alc-Portal-Url |
0 |
0-1 |
0-1 |
|
26.6527.178 |
Alc-Ipv6-Portal-Url |
0 |
0-1 |
0-1 |
|
26.6527.180 |
Alc-SAP-Session-Index |
0-1 |
0 |
0 |
|
26.6527.181 |
Alc-SLAAC-IPv6-Pool |
0 |
0-1 |
0 |
|
26.6527.183 |
Alc-WPP-Error-Code |
0 |
0 (Access-Reject only) |
0 |
|
26.6527.185 |
Alc-Onetime-Http-Redirect-Reactivate |
0 |
0 |
0-1 |
|
26.6527.191 |
Alc-ToServer-Dhcp6-Options |
0+ |
0 |
0 |
|
26.6527.192 |
Alc-ToClient-Dhcp6-Options |
0 |
0+ |
0 |
|
26.6527.200 |
Alc-v6-Preferred-Lifetime |
0 |
0-1 |
0 |
|
26.6527.201 |
Alc-v6-Valid-Lifetime |
0 |
0-1 |
0 |
|
26.6527.202 |
Alc-Dhcp6-Renew-Time |
0 |
0-1 |
0 |
|
26.6527.203 |
Alc-Dhcp6-Rebind-Time |
0 |
0-1 |
0 |
|
26.6527.217 |
Alc-UPnP-Sub-Override-Policy |
0 |
0-1 |
0-1 |
|
26.6527.228 |
Alc-Trigger-Acct-Interim |
0 |
0 |
0-1 |
|
26.6527.232 |
Alc-Acct-Interim-IvI |
0 |
0+ |
0+ |
|
26.6527.234 |
Alc-DNAT-Override |
0 |
0+ |
0+ |
|
26.6527.238 |
Alc-Remove-Override |
0 |
0 |
0+ |
|
26.6527.242 |
Alc-Radius-Py |
0+ |
0+ |
0+ |
|
26.6527.244 |
Alc-Force-DHCP-Relay |
0 |
0+ |
0 |
|
241.26.6527.16 |
Alc-IPv6-Router-Adv-Policy |
0 |
0-1 |
0-1 |
|
241.26.6527.17 |
Alc-Nat-Outside-IPs |
0 |
0+ |
0+ |
|
241.26.6527.18 |
Alc-Mld-Import-Policy |
0 |
0+ |
0+ |
|
241.26.6527.19 |
Alc-Bonding-Id |
0 |
0-1 |
0 |
|
241.26.6527.22 |
Alc-Bonding-Reference-Rate |
0 |
0-1 |
0-1 |
|
241.26.6527.27 |
Alc-IPv6-Sub-If-Prefix |
0 |
0-1 |
0 |
|
241.26.6527.35 |
Alc-Mld-Import-Policy-Modif |
0 |
0 |
0+ |
|
241.26.6527.37 |
Alc-VAS-IPv4-Filter |
0 |
0-1 |
0-1 |
|
241.26.6527.38 |
Alc-VAS-NSH-IPv4-Opaque-Meta-Data |
0 |
0-1 |
0-1 |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
0 |
0+ |
0+ |
|
241.26.6527.40 |
Alc-IPv6-Slaac-Replacement-Prefix |
0 |
0 |
0-1 |
|
241.26.6527.47 |
Alc-SPI-Sharing-Id |
0 |
0-1 |
0-1 |
|
241.26.6527.57 |
Alc-Gtp-Skip-Ipv4-Alloc-Override |
0 |
0-1 |
0 |
|
241.26.6527.58 |
Alc-Change-Reporting-Action |
0 |
0-1 |
0-1 |
|
241.26.6527.62 |
Alc-Host-DNAT-Override |
0 |
0-1 |
0-1 |
|
241.26.6527.71 |
Alc-Host-DNAT-Default-Address-Override |
0 |
0-1 |
0-1 |
|
241.26.6527.92 |
Alc-PPPoE-LCP-Keepalive-Interval |
0 |
0-1 |
0 |
|
241.26.6527.93 |
Alc-PPPoE-LCP-Keepalive-Multiplier |
0 |
0-1 |
0 |
|
245.26.6527.5 |
Alc-Spi-Host-And-Session-Limits |
0 |
0+ |
0+ |
|
245.26.6527.6 |
Alc-Sub-Host-And-Session-Limits |
0 |
0+ |
0+ |
|
26.10415.1 |
3GPP-IMSI |
0-1 |
0 |
0 |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS-Profile |
0-1 |
0-1 |
0 |
|
26.10415.20 |
3GPP-IMEISV |
0-1 |
0 |
0 |
|
26.10415.21 |
3GPP-RAT-Type |
0-1 |
0 |
0 |
|
26.10415.22 |
3GPP-User-Location-Info |
0-1 |
0 |
0 |
[87] NAS-Port-Id attribute details
The [87] NAS-Port-Id attribute identifies a physical or logical port and is formatted as described in NAS-Port-Id attribute details.
| Port type | Format | Example |
|---|---|---|
|
Ethernet port |
[<prefix>] <slot>[/<xiom>] /<mda>[/<connector>]/<port>[:<outer vlan id>[.<inner vlan id>]] [<suffix>] where <prefix> is an optional configured string (8 chars. max) <suffix> is an optional string containing circuit-id or remote-id (64 chars. max) |
1/1/4:501.1001 1/2/c1/2:100 2/x1/1/c4/1:35.2 |
|
LAG |
[<prefix>] lag-<lag-id>[:<outer vlan id>[.<inner vlan id>]] [<suffix>] where <prefix> is an optional configured string (8 chars. max) <suffix> is an optional string containing circuit-id or remote-id (64 chars. max) |
lag-12:1000.20 |
| PseudoWire port2 |
[<prefix>] pw--<pw-port-id>:<outer vlan id>[.<inner vlan id>] [<suffix>] where <prefix> is an optional configured string (8 chars. max) <suffix> is an optional string containing circuit-id or remote-id (64 chars. max) |
pw-2:320.100 |
|
LNS |
LNS rtr-<routing instance> #lip-<tunnel-server-endpoint> #rip-<tunnel-client-endpoint> #ltid-<local-tunnel-id> #rtid-<remote-tunnel-id> #lsid-<local-session-id> #rsid-<remote-session-id> #<call sequence number> |
LNS rtr-2 #lip-3.3.3.3 #rip- 1.1.1.1 #ltid-11381 #rtid-1285 #lsid-30067 #rsid-19151 #347 |
|
WLANGW tunneled access |
<tunnel-type> rtr-<virtual router id> #lip-<local ip address> #rip-<remote ip address> where <tunnel-type> = GRE | L2TP, <virtual router id> is the transport service <local ip address> is the local tunnel end-point <remote ip address> is the remote tunnel end-point |
GRE rtr-11 #lip-50.1.1.1 #rip-201.1.1.2 |
|
WLANGW L2 access |
VLAN svc-<svc-id>[:<outer-vlan>[.<inner-vlan>]] where <svc-id> is the relative identifier of the internal _tmnx_WlanGwL2ApService Epipe service connecting the WLAN-GW group interface SAP to the MS-ISA [:<outer-vlan>[.<inner-vlan>]] is the optional dot1q or QinQ encapsulation identifying the AP |
VLAN svc-1:10 |
|
ESMoGTP |
GTP rtr-<virtual router id> #lip-<local ip address> #rip-<MME ip address> #lteid-<local teid> #rteid-<remote teid> |
GTP rtr-56 #lip-50.50.50.1 #rip-10.207.5.2 #lteid-4284481792 #rteid-1000000 |
|
IPsec |
public SAP ID of IKEv2 remote-access tunnel |
tunnel-1.public:100 |
|
AA sap or spoke-sdp |
SAP or SDP serving the AA-transit subscriber: Parent SAP: <slot>/<mda>/<port>[:<outer vlan id>[.<inner vlan id>]] Parent spoke SDP: <sdp-id>:<vc-id> |
parent SAP: 1/1/4:501.1001 parent spoke SDP: 4:100 |
[26.6527.126] Alc-Subscriber-QoS-Override attribute details
The format for [26.6527.126] Alc-Subscriber-QoS-Override is a string formatted as:
<direction>:<QoS object>:[<id or name>:][<parameter>=value,...]
Alc-Subscriber-QoS-Override attribute details provides details on the respective fields.
Multiple parameters can be combined in a comma separated list.
The direction must be specified as:
-
i or I for ingress
-
e or E for egress
For example:
Alc-Subscriber-QoS-Override = "E:Q:1:pir=2000,cir=1000"
Overrides are always stored as part of the subscriber host or session but are only applied when the override is valid in the active QoS configuration. For example:
-
An egress queue 5 PIR rate override is stored with the subscriber session but not applied when the sap-egress QoS policy has no queue 5 defined
-
An HSQ egress queue wrr-weight override is stored with the subscriber session but not applied when the queue is not attached to a WRR group.
| Direction | QoS object | ID or name |
Parameter=value |
Description |
|---|---|---|---|---|
|
i, I, e or E
|
q or Q
|
queue ID [1..32] ingress [1..8] egress |
pir=<pir-rate> |
Queue PIR value in kilobits per second -1 or "max" : maximum value -2 : no override |
|
cir=<cir-rate> |
Queue CIR value in kilobits per second -1 or "max" : maximum value -2 : no override |
|||
|
mbs=<mbs-size> |
Queue MBS size in bytes -1 reset to default value -2 : no override |
|||
|
cbs=<cbs-size> |
Queue CBS size in bytes -1 reset to default value -2 : no override |
|||
|
burst_limit |
Queue burst limit value in bytes. (explicit shaping burst size -1 reset to default value -2 : no override |
|||
|
parent_weight |
Queue parent weight value [0..100] (relative weight of this queue in comparison to other children and used at the above-CIR priority level) -1 reset to default value -2 : no override |
|||
|
cir_parent_weight |
Queue CIR parent weight value [0..100] (relative CIR weight of this queue in comparison to other children and used at the within-CIR priority level) -1 reset to default value -2 : no override |
|||
|
e or E |
q or Q |
queue ID [1..8] |
class_weight=<weight> |
Class weight [1, 2, 4 or 8] -2 : no override Applies to HSQ hs-class-weight |
|
e or E |
q or Q |
queue ID [1..8] HSQ |
wrr_weight=<weight> |
WRR weight [1..127] for HSQ -2 : no override Applies to HSQ hs-wrr-weight |
|
i, I, e or E
|
p or P
|
policer ID [1..63] |
pir=<pir-rate> |
Policer PIR value in kilobits per second -1 or "max" : maximum value -2 : no override |
|
cir=<cir-rate> |
Policer CIR value in kilobits per second -1 or "max" : maximum value -2 : no override |
|||
|
mbs=<mbs-size> |
Policer MBS size in bytes -1 reset to default value -2 : no override |
|||
|
cbs=<cbs-size> |
Policer CBS size in bytes -1 reset to default value -2 : no override |
|||
|
parent_weight |
Policer parent weight value [0-100] (relative weight of this policer in comparison to other children and used at the above-CIR priority level) -1 reset to default value -2 : no override |
|||
|
cir_parent_weight |
Policer CIR parent weight value [0-100] (relative CIR weight of this policer in comparison to other children and used at the within-CIR priority level) Not applicable to arbiter or root arbiter parents. -1 reset to default value -2 : no override |
|||
|
e or E |
r or R |
not applicable |
rate=<rate> |
Egress aggregate rate in kilobits per second -1 or "max" : maximum value -2 : no override applies to sub-profile agg-rate-limit or HSQ sub-profile hs-agg-rate-limit For HSQ hs-sla-mode single, the applied rate is the minimum between the sla-profile and sub-profile hs-agg-rate-limit The sub-profile egress agg-rate-limit override value is a frame-based rate (on-the-wire bandwidth). |
|
e or E |
l or L |
not applicable |
rate=<rate> |
Egress aggregate rate in kilobits per second -1 or "max" : maximum value -2 : no override applies to HSQ sla-profile hs-agg-rate-limit For HSQ hs-sla-mode single, the applied rate is the minimum between the sla-profile and sub-profile hs-agg-rate-limit |
|
e or E
|
g or G
|
wrr group ID [1..2] |
rate=<rate> |
WRR group PIR value in kilobits per second -1 or "max" : maximum value -2 : no override applies to HSQ hs-wrr-group <group-id> rate |
|
class_weight=<weight> |
WRR groups class weight [1, 2, 4 or 8] -2 : no override applies to HSQ hs-wrr-group <group-id> hs-class-weight |
|||
|
i, I, e or E |
a or A |
root arbiter: fixed name "root" intermediate arbiter: arbiter name (32 chars. max) |
rate=<rate> |
Root or intermediate arbiter rate in kilobits per second -1 or "max" : maximum value -2 : no override |
|
i, I, e or E
|
s or S
|
scheduler-name |
rate=<pir-rate> |
Scheduler PIR rate in kilobits per second. Applies to ingress or egress sub-profile scheduler-policy schedulers only -1 or "max" : maximum value -2 : no override |
|
cir=<cir-rate> |
Scheduler CIR rate in kilobits per second. Applies to ingress or egress sub-profile scheduler-policy schedulers only -1 or "max" : maximum value -2 : no override "sum" : sum of the queue or policer CIRs parented to the scheduler |
[26.6527.238] Alc-Remove-Override attribute details
The format for [26.6527.238] Alc-Remove-Override is a string formatted as:
[<action><space>]<attribute identifier>
where <action> is:
-
deactivate
This command deactivates the function that was activated with the specified VSA.
-
no <action> specified
This removes the override that was installed with the specified VSA.
If the CoA target is:
-
an ESM subscriber host/session or a vRGW session -> BRG level, then the application falls back to the system default for that attribute
-
a vRGW session -> session level, then the application falls back to the BRG level value for that attribute. If there is no BRG level attribute specified, then the application falls back to the system default for that attribute. For some attributes, a BRG level value must be present: fallback to the system default is not possible
-
where <attribute identifier> is a single attribute identifier specified in dotted number notation or alternatively using a "-" (hyphen) as the delimiter.
Alc-Remove-Override attribute - applicable attribute identifiers lists the attribute identifiers that can be specified as value in the Alc-Remove-Override VSA to remove the override from or to deactivate the action triggered by the references attributes.
| Attribute ID | Attribute name | Action | Applicability | |||
|---|---|---|---|---|---|---|
| ESM Session/host |
vRGW session | |||||
| Unspecified -remove override |
Deactivate | BRG level |
Session level |
|||
|
92 |
NAS-Filter-Rule |
✓ |
— |
✓3 | ||
|
26.6527.13 |
Alc-SLA-Prof-Str |
✓ |
— |
✓3 | ||
|
26.6527.45 |
Alc-App-Prof-Str |
✓ |
— |
✓3 | ||
|
26.6527.126 |
Alc-Subscriber-QoS-Override |
✓ |
— |
✓ |
||
|
26.6527.134 |
Alc-Subscriber-Filter |
✓ |
— |
✓3 | ||
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
✓ |
— |
✓3 | ||
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
✓ |
— |
✓3 | ||
|
26.6527.193 |
Alc-AA-App-Service-Options |
✓ |
✓ |
✓ |
||
|
241.26.6527.17 |
Alc-Nat-Outside-IP |
✓ |
✓ |
— |
||
|
241.26.6527.25 |
Alc-Steering-Profile |
✓ |
✓ |
|||
|
241.26.6527.37 |
Alc-VAS-IPv4-Filter |
✓ |
✓ |
✓ |
✓ |
|
|
241.26.6527.39 |
Alc-Static-Port-Forward |
✓ |
✓ |
— |
||
|
241.26.6527.62 |
Alc-Host-DNAT-Override |
✓ |
✓ |
— |
✓ |
|
|
241.26.6527.71 |
Alc-Host-DNAT-Default-Address-Override |
✓ |
✓ |
— |
✓ |
|
[245.26.6527.5] Alc-Spi-Host-And-Session-Limits attribute details
The [245.26.6527.5] Alc-Spi-Host-And-Session-Limits VSA, is an Extended-Vendor-Specific-5 type attribute encoded as a TLV. See Alc-Spi-Host-And-Session-Limits attribute details for a detailed description.
Multiple limits can be encoded in a single VSA. For example, to set the host-limits overall = 2, ipv4-overall=1, ipv6-overall=1 and the session-limit ipoe = 1:
SR OS debug:
VSA [245.26] 28(not frag) Nokia(6527)
SPI HOST AND SESSION LIMITS [5] 28 (tlv)
HOST LIMITS [1] 18 (tlv)
SPI HOST LIMITS IPV4 OVERALL [3] 4 1
SPI HOST LIMITS IPV6 OVERALL [5] 4 1
SPI HOST LIMITS OVERALL [15] 4 2
SESSION LIMITS [2] 6 (tlv)
SPI SESSION LIMITS IPOE [1] 4 1Alternatively, multiple VSA's can be included, each encoding a single or multiple limits. For example, to set the host-limits overall = 2, ipv4-overall=1, ipv6-overall=1 and the session-limit ipoe = 1:
SR OS debug:
VSA [245.26] 8(not frag) Nokia(6527)
SPI HOST AND SESSION LIMITS [5] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SPI HOST LIMITS IPV4 OVERALL [3] 4 1
VSA [245.26] 8(not frag) Nokia(6527)
SPI HOST AND SESSION LIMITS [5] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SPI HOST LIMITS IPV6 OVERALL [5] 4 1
VSA [245.26] 8(not frag) Nokia(6527)
SPI HOST AND SESSION LIMITS [5] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SPI HOST LIMITS OVERALL [15] 4 2
VSA [245.26] 8(not frag) Nokia(6527)
SPI HOST AND SESSION LIMITS [5] 8 (tlv)
SESSION LIMITS [2] 6 (tlv)
SPI SESSION LIMITS IPOE [1] 4 1The host and session limits have following special values:
-
for -2, use the configured value
-
for -1, no limit
| Attribute ID | Attribute name | Type | Description |
|---|---|---|---|
|
245.26.6527.5 |
Alc-Spi-Host-And-Session-Limits |
tlv |
This attribute has no meaning on its own. It allows to send multiple host and session limits per SLA Profile Instance grouped in a single VSA. |
|
245.26.6527.5.1 |
Alc-Spi-Host-Limits |
tlv |
This attribute has no meaning on its own. It groups the host limits per SLA Profile Instance in the VSA. |
|
245.26.6527.5.1.1 |
Alc-Spi-Host-Limits-IPv4-Arp |
integer |
Overrides the ipv4-arp limit configured in the sla-profile host-limits context. Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.2 |
Alc-Spi-Host-Limits-IPv4-Dhcp |
integer |
Overrides the ipv4-dhcp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.3 |
Alc-Spi-Host-Limits-IPv4-Overall |
integer |
Overrides the ipv4-overall limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.4 |
Alc-Spi-Host-Limits-IPv4-Ppp |
integer |
Overrides the ipv4-ppp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.5 |
Alc-Spi-Host-Limits-IPv6-overall |
integer |
Overrides the ipv6-overall limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.6 |
Alc-Spi-Host-Limits-IPv6-Pd-Ipoe-Dhcp |
integer |
Overrides the ipv6-pd-ipoe-dhcp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.7 |
Alc-Spi-Host-Limits-IPv6-Pd-Overall |
integer |
Overrides the ipv6-pd-overall limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.8 |
Alc-Spi-Host-Limits-IPv6-Pd-Ppp-Dhcp |
integer |
Overrides the ipv6-pd-ppp-dhcp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.9 |
Alc-Spi-Host-Limits-IPv6-Wan-Ipoe-Dhcp |
integer |
Overrides the ipv6-wan-ipoe-dhcp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.10 |
Alc-Spi-Host-Limits-IPv6-Wan-Ipoe-Slaac |
integer |
Overrides the ipv6-wan-ipoe-slaac limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.11 |
Alc-Spi-Host-Limits-IPv6-Wan-Overall |
integer |
Overrides the ipv6-wan-overall limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.12 |
Alc-Spi-Host-Limits-IPv6-Wan-Ppp-Dhcp |
integer |
Overrides the ipv6-wan-ppp-dhcp limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.13 |
Alc-Spi-Host-Limits-IPv6-Wan-Ppp-Slaac |
integer |
Overrides the ipv6-wan-ppp-slaac limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.14 |
Alc-Spi-Host-Limits-Lac-Overall |
integer |
Overrides the lac-overall limit configured in the sla-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.1.15 |
Alc-Spi-Host-Limits-Overall |
integer |
Overrides the overall limit configured in the sla-profile host-limits context Range [-2, -1, 1..131071] |
|
245.26.6527.5.2 |
Alc-Spi-Session-Limits |
tlv |
This attribute has no meaning on its own. It groups the session limits per SLA Profile Instance in the VSA. |
|
245.26.6527.5.2.1 |
Alc-Spi-Session-Limits-IPoE |
integer |
Overrides the ipoe limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.2 |
Alc-Spi-Session-Limits-PPPoE-Local |
integer |
Overrides the pppoe-local limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.3 |
Alc-Spi-Session-Limits-PPPoE-Lac |
integer |
Overrides the pppoe-lac limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.4 |
Alc-Spi-Session-Limits-PPPoE-Overall |
integer |
Overrides the pppoe-overall limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.5 |
Alc-Spi-Session-Limits-L2TP-Lns |
integer |
Overrides the l2tp-lns limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.6 |
Alc-Spi-Session-Limits-L2TP-Lts |
integer |
Overrides the l2tp-lts limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.7 |
Alc-Spi-Session-Limits-L2TP-Overall |
integer |
Overrides the l2tp-overall limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.5.2.8 |
Alc-Spi-Session-Limits-Overall |
integer |
Overrides the overall limit configured in the sla-profile session-limits context Range [-2, -1, 0..131071] |
[245.26.6527.6] Alc-Sub-Host-And-Session-Limits attribute details
The [245.26.6527.6] Alc-Sub-Host-And-Session-Limits VSA, is an Extended-Vendor-Specific-5 type attribute encoded as a TLV. See Alc-Sub-Host-And-Session-Limits attribute details for a detailed description.
Multiple limits can be encoded in a single VSA. For example, to set the host-limits ipv4-overall=1, ipv6-overall=1, overall = 2 and the session-limit ipoe = 1:
SR OS debug:
VSA [245.26] 28(not frag) Nokia(6527)
SUB HOST AND SESSION LIMITS [6] 28 (tlv)
HOST LIMITS [1] 18 (tlv)
SUB HOST LIMITS IPV4 OVERALL [3] 4 1
SUB HOST LIMITS IPV6 OVERALL [5] 4 1
SUB HOST LIMITS OVERALL [15] 4 2
SESSION LIMITS [2] 6 (tlv)
SUB SESSION LIMITS IPOE [1] 4 1Alternatively, multiple VSA's can be included, each encoding a single or multiple limits. For example, to set the host-limits ipv4-overall=1, ipv6-overall=1, overall = 2 and the session-limit ipoe = 1:
SR OS debug:
VSA [245.26] 8(not frag) Nokia(6527)
SUB HOST AND SESSION LIMITS [6] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SUB HOST LIMITS IPV4 OVERALL [3] 4 1
VSA [245.26] 8(not frag) Nokia(6527)
SUB HOST AND SESSION LIMITS [6] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SUB HOST LIMITS IPV6 OVERALL [5] 4 1
VSA [245.26] 8(not frag) Nokia(6527)
SUB HOST AND SESSION LIMITS [6] 8 (tlv)
HOST LIMITS [1] 6 (tlv)
SUB HOST LIMITS OVERALL [15] 4 2
VSA [245.26] 8(not frag) Nokia(6527)
SUB HOST AND SESSION LIMITS [6] 8 (tlv)
SESSION LIMITS [2] 6 (tlv)
SUB SESSION LIMITS IPOE [1] 4 1
The host and session limits have following special values:
-
for -2, use the configured value
-
for -1, no limit
| Attribute ID | Attribute name | Type | Description |
|---|---|---|---|
|
245.26.6527.6 |
Alc-Sub-Host-And-Session-Limits |
tlv |
This attribute has no meaning on its own. It allows to send multiple host and session limits per subscriber grouped in a single VSA. |
|
245.26.6527.6.1 |
Alc-Sub-Host-Limits |
tlv |
This attribute has no meaning on its own. It groups the host limits per subscriber in the VSA. |
|
245.26.6527.6.1.1 |
Alc-Sub-Host-Limits-IPv4-Arp |
integer |
Overrides the ipv4-arp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.2 |
Alc-Sub-Host-Limits-IPv4-Dhcp |
integer |
Overrides the ipv4-dhcp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071 |
|
245.26.6527.6.1.3 |
Alc-Sub-Host-Limits-IPv4-Overall |
integer |
Overrides the ipv4-overall limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071 |
|
245.26.6527.6.1.4 |
Alc-Sub-Host-Limits-IPv4-Ppp |
integer |
Overrides the ipv4-ppp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.5 |
Alc-Sub-Host-Limits-IPv6-overall |
integer |
Overrides the ipv6-overall limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.6 |
Alc-Sub-Host-Limits-IPv6-Pd-Ipoe-Dhcp |
integer |
Overrides the ipv6-pd-ipoe-dhcp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.7 |
Alc-Sub-Host-Limits-IPv6-Pd-Overall |
integer |
Overrides the ipv6-pd-overall limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.8 |
Alc-Sub-Host-Limits-IPv6-Pd-Ppp-Dhcp |
integer |
Overrides the ipv6-pd-ppp-dhcp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.9 |
Alc-Sub-Host-Limits-IPv6-Wan-Ipoe-Dhcp |
integer |
Overrides the ipv6-wan-ipoe-dhcp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.10 |
Alc-Sub-Host-Limits-IPv6-Wan-Ipoe-Slaac |
integer |
Overrides the ipv6-wan-ipoe-slaac limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.11 |
Alc-Sub-Host-Limits-IPv6-Wan-Overall |
integer |
Overrides the ipv6-wan-overall limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.12 |
Alc-Sub-Host-Limits-IPv6-Wan-Ppp-Dhcp |
integer |
Overrides the ipv6-wan-ppp-dhcp limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.13 |
Alc-Sub-Host-Limits-IPv6-Wan-Ppp-Slaac |
integer |
Overrides the ipv6-wan-ppp-slaac limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.14 |
Alc-Sub-Host-Limits-Lac-Overall |
integer |
Overrides the lac-overall limit configured in the sub-profile host-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.1.15 |
Alc-Sub-Host-Limits-Overall |
integer |
Overrides the overall limit configured in the sub-profile host-limits context Range [-2, -1, 1..131071] |
|
245.26.6527.6.2 |
Alc-Sub-Session-Limits |
tlv |
This attribute has no meaning on its own. It groups the session limits per subscriber in the VSA. |
|
245.26.6527.6.2.1 |
Alc-Sub-Session-Limits-IPoE |
integer |
Overrides the ipoe limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.2 |
Alc-Sub-Session-Limits-PPPoE-Local |
integer |
Overrides the pppoe-local limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.3 |
Alc-Sub-Session-Limits-PPPoE-Lac |
integer |
Overrides the pppoe-lac limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.4 |
Alc-Sub-Session-Limits-PPPoE-Overall |
integer |
Overrides the pppoe-overall limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.5 |
Alc-Sub-Session-Limits-L2TP-Lns |
integer |
Overrides the l2tp-lns limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.6 |
Alc-Sub-Session-Limits-L2TP-Lts |
integer |
Overrides the l2tp-lts limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.7 |
Alc-Sub-Session-Limits-L2TP-Overall |
integer |
Overrides the l2tp-overall limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
|
245.26.6527.6.2.8 |
Alc-Sub-Session-Limits-Overall |
integer |
Overrides the overall limit configured in the sub-profile session-limits context Range [-2, -1, 0..131071] |
Address, prefix, and pool attribute details
For subscriber session address allocation, an IP address or prefix attribute can be returned for RADIUS proxy deployments. Alternatively, an IP address or prefix pool can be returned for DHCP relay or local address allocation deployments. The following table describes the behavior when both address or prefix and pool attributes are returned for a subscriber session.
|
Simultaneous returned attributes in authentication |
8 Framed-IP-Address 88 Framed-Pool |
26.6527.99 Alc-IPv6-Address 100 Framed-IPv6-Pool |
123 Delegated-IPv6-Prefix 26.6527.131 Alc-Delegated-IPv6-Pool |
97 Framed-IPv6-Prefix 26.6527.181 Alc-SLAAC-IPv6-Pool |
|---|---|---|---|---|
|
PPPoE session |
Framed-IP-Address with value different from 255.255.255.254 is used Framed-IP-Address with value 255.255.255.254 is ignored and Framed-Pool is used instead |
PPPoE session failure: DHCP6 address and pool information combination is not supported |
PPPoE session failure: DHCP6 address and pool information combination is not supported |
PPPoE session failure SLAAC prefix and pool information combination is not supported |
|
IPoE session |
Framed-IP-Address with value different from 255.255.255.254 is used Framed-IP-Address with value 255.255.255.254 is ignored and Framed-Pool is used instead |
Alc-IPv6-Address is used |
Delegated-IPv6-Prefix is used |
Framed-IPv6-Prefix is used |
|
DHCPv4 host (ipoe-session disabled) |
Framed-IP-Address with value different from 255.255.255.254 is used Framed-IP-Address with value 255.255.255.254 is ignored and Framed-Pool is used instead |
N/A |
N/A |
N/A |
|
DHCPv6 IA_NA host (ipoe-session disabled) |
N/A |
Host setup failure: Subscr. Mgmt. Update failed (Authentication returned IPv6 address and pool information) |
N/A |
N/A |
|
DHCPv6 IA_PD host (ipoe-session disabled) |
N/A |
N/A |
Host setup failure: Subscr. Mgmt. Update failed (Authentication returned IPv6 address and pool information) |
N/A |
|
SLAAC host (ipoe-session disabled) |
N/A |
N/A |
N/A |
Host setup failure: Router Solicitation packet dropped (Both IP information and pool information returned) |
Wholesale-retail — local access mode
| Attribute ID | Attribute name | Description |
|---|---|---|
|
26.6527.17 |
Alc-Retail-Serv-Id |
The service ID of the retailer to which this subscriber host belongs. (configure service ies | vprn retail-service-id subscriber-interface retail-interface-name fwd-service wholesale-service-id fwd-subscriber-interface wholesale-interface-name). Returning an IES service ID for an IPoEv4 host is treated as a session setup failure. This attribute must be included together with NAS-Port-Id and an IP address or prefix attribute in a CoA targeting a subscriber host in a retail service. Note: [241.26.6527.89] Alc-Retail-Serv-Name takes precedence over [26.6527.17] Alc-Retail-Serv-Id if
both are specified.
|
|
26.6527.31 |
Alc-MSAP-Serv-Id |
The service ID where Managed SAPs are created. (configure service ies/vprn service-id). If this attribute is omitted, use msap defaults created under ludb or capture VPLS. (configure subscriber-mgmt local-user-db local-user-db-name ppp/ipoe host msap-defaults service service-id or configure service vpls service-id sap sap-id msap-defaults service service-id). This omitted attribute without explicitly created msap-defaults is treated as a setup failure. Note: [241.26.6527.90] Alc-MSAP-Serv-Name takes precedence over [26.6527.31] Alc-MSAP-Serv-Id if
both are specified.
|
|
26.6527.32 |
Alc-MSAP-Policy |
Managed sap policy-name used to create managed SAPs and refers to the CLI context configure subscriber-mgmt msap-policy msap-policy-name). The policy contains similar parameters that would be configured for a regular subscriber SAP. If this attribute is omitted, then the MSAP default configured in ludb or capture-sap is used (configure subscriber-mgmt local-user-db local-user-db ppp/ipoe host host-name msap-defaults policy msap-policy-name or configure service vpls service-id sap sap-id msap-defaults policy msap-policy-name).This omitted attribute without explicitly created MSAP defaults is treated as a setup failure. |
|
26.6527.33 |
Alc-MSAP-Interface |
The group interface name where managed SAPs are created and refers to CLI context configure service ies | vprn service-id subscriber-interface ip-int-name group-interface ip-int-name. If this attribute is omitted, the MSAP defaults configured in the ludb or capture-sap are used. (configure subscriber-mgmt local-user-db local-user-db-name ppp/ipoe host host-name msap-defaults group-interface ip-int-name or configure service vpls service-id sap sap-id msap-defaults group-interface ip-int-name). Strings above the limits and an omitted attribute without explicitly created MSAP defaults are treated as setup failures. |
|
241.26.6527.89 |
Alc-Retail-Serv-Name |
The service name of the retailer to which this subscriber host belongs. (configure service ies | vprn retail-service-id name retail-service-name subscriber-interface retail-interface-name fwd-service wholesale-service-id fwd-subscriber-interface wholesale-interface-name) . Returning an IES service name for an IPoEv4 host is treated as a session setup failure. This attribute must be included together with NAS-Port-Id and an IP address or prefix attribute in a CoA targeting a subscriber host in a retail service. When the host was setup from RADIUS using the Alc-Retail-Serv-Name, the CoA must also use the Alc-Retail-Serv-Name. Note: [241.26.6527.89] Alc-Retail-Serv-Name takes precedence over
[26.6527.17] Alc-Retail-Serv-Id if both are specified.
|
|
241.26.6527.90 |
Alc-MSAP-Serv-Name |
The service name where managed SAPs are created. (configure service ies | vprn service-id name retail-service-name). If this attribute is omitted, use the MSAP defaults created under ludb or capture VPLS. (configure subscriber-mgmt local-user-db local-user-db-name ppp | ipoe host msap-defaults service service-id or configure service vpls service-id sap sap-id msap-defaults service service-id). This omitted attribute without explicitly created msap-defaults is treated as a setup failure. Note: [241.26.6527.90] Alc-MSAP-Serv-Name takes precedence over
[26.6527.31] Alc-MSAP-Serv-Id if both are specified.
|
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
26.6527.17 |
Alc-Retail-Serv-Id |
integer |
2147483647 ID |
For example: Alc-Retail-Serv-Id = 10 |
|
26.6527.31 |
Alc-MSAP-Serv-Id |
integer |
2147483647 ID |
For example: Alc-MSAP-Serv-Id = 20 |
|
26.6527.32 |
Alc-MSAP-Policy |
string |
32 chars |
Policy may start with a letter or number For example: Alc-MSAP-Policy = 1-Policy-business |
|
26.6527.33 |
Alc-MSAP-Interface |
string |
32 chars |
Interface-name must start with a letter For example: Alc-MSAP-Interface = group-1 |
|
241.26.6527.89 |
Alc-Retail-Serv-Name |
string |
64 chars |
For example: Alc-Retail-Serv-Name=Service-1 |
|
241.26.6527.90 |
Alc-MSAP-Serv-Name |
string |
64 chars |
For example: Alc-MSAP-Serv-Name=Service-1 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
26.6527.17 |
Alc-Retail-Serv-Id |
0 |
0-1 |
0-1 |
|
26.6527.31 |
Alc-MSAP-Serv-Id |
0 |
0-1 |
0 |
|
26.6527.32 |
Alc-MSAP-Policy |
0 |
0-1 |
0 |
|
26.6527.33 |
Alc-MSAP-Interface |
0 |
0-1 |
0 |
|
241.26.6527.89 |
Alc-Retail-Serv-Name |
0 |
0-1 |
0-1 |
|
241.26.6527.90 |
Alc-MSAP-Serv-Name |
0 |
0-1 |
0 |
Wholesale-retail — L2TP tunneled access mode
| Attribute ID | Attribute name | Description |
|---|---|---|
|
64 |
Tunnel-Type |
The tunneling protocols to be used (in the case of a tunnel initiator) or the tunneling protocol in use (in the case of a tunnel terminator). This attribute is mandatory on LAC Access-Accept and needs to be L2TP. The same attribute is included on LNS in the Access-Request and Acct-Request if the CLI RADIUS policy include-radius-attribute tunnel-server-attrs is enabled on a 7750 SR LNS. For L2TP Tunnel or Link Accounting, this attribute is always included on LAC and LNS. |
|
65 |
Tunnel-Medium-Type |
The transport medium to use when creating a tunnel for those protocols (such as L2TP) that can operate over multiple transports. This attribute is mandatory on LAC Access-Accept and needs to be IP or IPv4.The same attribute is included on LNS in the Access-Request and Acct-Request if the CLI RADIUS policy include-radius-attribute tunnel-server-attrs is enabled on a 7750 SR LNS. For L2TP Tunnel or Link Accounting, this attribute is always included on LAC and LNS. |
|
66 |
Tunnel-Client-Endpoint |
The dotted-decimal IP address of the initiator end of the tunnel. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp local-address). If omitted in Access Accept on LAC and no local-address configured, then the address is taken from the interface with name system. This attribute is included on LNS in the Access-Request and Acct-Request only if the CLI RADIUS policy include-radius-attribute tunnel-server-attrs is enabled on a 7750 SR LNS. For L2TP Tunnel or Link Accounting, this attribute is always included on LAC and LNS as untagged. |
|
67 |
Tunnel-Server-Endpoint |
The dotted-decimal IP address of the server end of the tunnel is also on the LAC the destination IP for all L2TP packets for that tunnel. To support more than 31 tunnels in a single RADIUS Access-Accept message, multiple Tunnel-Server-Endpoint attributes with the same tag can be inserted. All tunnels specified by Tunnel-Sever-Endpoint attributes with a tag uses the tunnel parameters specified by the other Tunnel attributes having the same tag value. |
|
69 |
Tunnel-Password |
A shared, salt-encrypted secret used for tunnel authentication and AVP-hiding. The usage of tunnel-authentication is indicated by attribute [26.6527.97] Alc-Tunnel-Challenge and the usage of AVP-hiding is indicated by attribute [26.6527.54] Alc-Tunnel-AVP-Hiding. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp password). There is no default password. Received passwords longer than the maximum character limit are truncated at that limit. |
|
81 |
Tunnel-Private-Group-ID |
The group ID for a particular tunneled session. This RADIUS attribute is copied by a 7750 SR LAC in AVP 37 - Private Group ID (ICCN) and is used by the LAC to indicate that this call is to be associated with a particular customer group. The 7750 SR LNS ignores AVP 37 when received from LAC. The value with tag 0 is used as default for the tunnels where the value is not specified. String lengths above the maximum value are treated as setup failures. |
|
82 |
Tunnel-Assignment-ID |
Indicates to the tunnel initiator the particular tunnel to which a session is to be assigned. Some tunneling protocols, such as PPTP and L2TP, allow for sessions between the same two tunnel endpoints to be multiplexed over the same tunnel, and also for a specific session to use its own dedicated tunnel. Tag-0 Tunnel-Assignment-ID:0 string, has a special meaning and the string becomes the tunnel group name that can hold up to maximum 31 tunnels with the name Tunnel-Assignment-ID-[1 to 31] string. A tunnel group with the name default_radius_group is created on the LAC when this attribute with tag-0 is omitted. This attribute is not the same as attribute [26.4874.64] ERX-Tunnel-Group or [26.6527.46] Alc-Tunnel-Group because these attributes both reference a tunnel group name created in CLI context. When not specified, the default value for Tunnel-Assignment-ID-[1 to 31] string is unnamed. String lengths above the limits are treated as a setup failure. |
|
83 |
Tunnel-Preference |
Indicates the relative preference assigned to each tunnel if more than one set of tunneling attributes is returned by the RADIUS server to the tunnel initiator. 0x0 (zero) being the lowest and 0x0FFFFFF(16777215) being the highest numerical value. The tunnel having the numerically lowest value in the Value field of this Attribute is assigned the highest preference. Other tunnel selection criteria are used if preference values from different tunnels are equal. Preference 50 is used when attribute is omitted. Values above the Limits wrap around by Freeradius before send to the NAS (start again from zero until the Limits). |
|
90 |
Tunnel-Client-Auth-ID |
Used during the authentication phase of tunnel establishment and copied by the LAC in L2TP SCCRQ AVP 7 Host Name. Reported in L2TP Tunnel or Link accounting when length is different from zero. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when the attribute is omitted (configure router/service vprn service-id l2tp local-name). The Node system-name is copied in AVP Host Name if this attribute is omitted and no local-name is configured. |
|
91 |
Tunnel-Server-Auth-ID |
Used during the authentication phase of tunnel establishment and reported in L2TP Tunnel or Link accounting when length is different from zero. For authentication the value of this attribute is compared with the value of AVP 7 Host Name from the received LNS SCCRP. Authentication from LAC point of view passes if both attributes are the same. This authentication check is not performed if the RADIUS attribute is omitted. |
|
26.2352.21 |
Tunnel-Max-sessions |
The maximum number of sessions allowed per tunnel group (untagged attribute only). This attribute has the same function as attribute 26.6527.48 Alc-Tunnel-Max-Sessions:0. No sessions are setup above the limits. Preconfigured values configure router/service vprn service-id l2tp session-limit are used when attribute is omitted. |
|
26.4874.33 |
ERX-Tunnel-Maximum-Sessions |
The maximum number of sessions allowed per tunnel group (untagged attribute only). This attribute has the same meaning as attribute 26.6527.48 Alc-Tunnel-Max-Sessions:0. No sessions are setup above the limits. Preconfigured values (configure router/service vprn service-id l2tp session-limit) are used when attribute is omitted. |
|
26.4874.64 |
ERX-Tunnel-Group |
The name of the tunnel group that refers to the CLI-created tunnel-group-name context configure router/service vprn service-id l2tp group tunnel-group-name. Any other RADIUS returned L2TP parameter is ignored and other required info to setup the tunnel should come from the CLI-created context. Strings above the limits are treated as a setup failure. |
|
26.6527.46 |
Alc-Tunnel-Group |
The tunnel-group-name that refers to the CLI-created tunnel-group-name context configure router/service vprn service-id l2tp group tunnel-group-name. Any other RADIUS returned L2TP parameter is ignored and other required info to setup the tunnel should come from the CLI-created context. Strings above the limits are treated as a setup failure. |
|
26.6527.47 |
Alc-Tunnel-Algorithm |
Describes how new sessions are assigned (weighted-access, weighted-random or existing-first) to one of the set of suitable tunnels that are available or could be made available. A preconfigured algorithm (configure router/service vprn service-id l2tp session-assign-method) is used when this attribute is omitted. Attribute value existing-first specifies that the first suitable tunnel is used or set up for the first session and re-used for all subsequent sessions. The weighted-access attribute value (session-assign-method weighted) specifies that the sessions are equally distributed over the available tunnels; new tunnels are set up until the maximum number is reached; the distribution aims at an equal ratio of the actual number of sessions to the maximum number of sessions. When there are multiple tunnels with an equal number of sessions (equal weight), LAC selects the first tunnel from the candidate list. The weighted-random attribute value enhances the weighted-access algorithm such that when there are multiple tunnels with an equal number of sessions (equal weight), LAC randomly selects a tunnel. The maximum number of sessions per tunnel is retrieved using attribute 26.6527.48 Alc-Tunnel-Max-Sessions or set to a preconfigured value if Alc-Tunnel-Max-Sessions is omitted. Values outside the limits are treated as a setup failure. |
|
26.6527.48 |
Alc-Tunnel-Max-Sessions |
The maximum number of sessions allowed per tunnel (if tag is 1 to 31) or per tunnel group (if tag is 0).This attribute has the same meaning as attribute 26.2352.21 Tunnel-Max-sessions and 26.4874.33 ERX-Tunnel-Maximum-Sessions with the only difference that these latter attributes refers to the tunnel group only (untagged attributed). No sessions are setup above the Limits. Preconfigured values (configure router/service vprn service-id l2tp session-limit) are used when attribute is omitted. |
|
26.6527.49 |
Alc-Tunnel-Idle-Timeout |
The period in seconds that an established tunnel with no active sessions (Established-Idle) persists before being disconnected. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp idle-timeout). The tunnel is not disconnected (infinite) without local configured idle-timeout or if the attribute has value -1 (16777215). Values above the Limits are treated as setup failures. |
|
26.6527.50 |
Alc-Tunnel-Hello-Interval |
The time interval in seconds between two consecutive tunnel Hello messages. A value of 0 or -1 (16777215) specifies that the keepalive function is disabled (infinite). The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp hello-interval). Values outside the limits are treated as a setup failure. |
|
26.6527.51 |
Alc-Tunnel-Destruct-Timeout |
The time in seconds that operational data of a disconnected tunnel persists on the node before being removed. Availability of the data after tunnel disconnection allows better troubleshooting. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp destruct-timeout). Values outside the limits are treated as a setup failure. |
|
26.6527.52 |
Alc-Tunnel-Max-Retries-Estab |
The number of retries allowed for established tunnels before their control connection goes down. An exponential back-off mechanism is used for the retransmission interval: the first retransmission occurs after 1 second, the next after 2 seconds, then 4 seconds up to a maximum interval of 8 seconds (1,2,4,8,8,8,8). The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp max-retries-estab). Values outside the limits are treated as a setup failure. |
|
26.6527.53 |
Alc-Tunnel-Max-Retries-Not-Estab |
The number of retries allowed for unestablished tunnels before their control connection goes down. An exponential back-off mechanism is used for the retransmission interval: the first retransmission occurs after 1 second, the next after 2 seconds, then 4 seconds up to a maximum interval of 8 seconds (1,2,4,8,8,8,8). The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp max-retries-not-estab). Values outside the limits are treated as a setup failure. |
|
26.6527.54 |
Alc-Tunnel-AVP-Hiding |
Indicates if data is hidden in the Attribute Value field of an L2TP AVP. The H bit in the header of each L2TP AVP provides a mechanism to indicate to the receiving peer whether the contents of the AVP are hidden or present in cleartext. This feature can be used to hide sensitive control message data such as user passwords or user IDs. All L2TP AVPs are passed in cleartext if the attribute is omitted and corresponds with the nothing value. The sensitive-only value specifies that the H bit is only set for AVPs containing sensitive information. The all value specifies that the H bit is set for all AVPs where it is allowed. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when the attribute is omitted configure router/service vprn service-id l2tp avp-hiding. AVP hiding uses the shared LAC-LNS secret defined in attribute [69] Tunnel-Password or in configuration. If no password is specified, the tunnel setup fails for sensitive-only and all values. Values outside the Limits are treated as a setup failure. |
|
26.6527.97 |
Alc-Tunnel-Challenge |
Indicates whether the tunnel authentication (challenge-response) is to be used. L2TP tunnel-authentication is based on RFC 1994 CHAP authentication and requires the shared-secret defined in attribute [69] Tunnel-Password. The value with tag 0 is used as default for the tunnels where the value is not specified. When the attribute is omitted and no [69] Tunnel-Password attribute is specified, a preconfigured value is used (configure router/service vprn service-id l2tp challenge). When the attribute is omitted and a [69] Tunnel-Password attribute is specified, then the always value is used. When the attribute has the always value, no [69] Tunnel-Password attribute is specified and no preconfigured value exists for the password, then the tunnel setup fails. Values outside the limits are treated as a setup failure. |
|
26.6527.100 |
Alc-Serv-Id |
The service ID on the LNS node where the PPP sessions are established (configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name). Preconfigured values are used if attribute is omitted (configure subscriber-mgmt local-user-db local-user-db-name ppp host host-name interface ip-int-name service-id service-id or configure router/service vprn service-id l2tp group ppp default-group-interface ip-int-name service-id service-id). Values above the limits or unreferenced are treated as a setup failure. Note: [241.26.6527.88] Alc-Serv-Name takes precedence over [26.6527.100] Alc-Serv-Id if both are
specified.
|
|
26.6527.101 |
Alc-Interface |
Refers to the group interface ip-int-name on LNS node only where the PPP sessions are established (configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name lns). Preconfigured values are used if the attribute is omitted (configure subscriber-mgmt local-user-db local-user-db-name ppp host host-name interface ip-int-name service-id service-id or configure router/service vprn service-id l2tp group ppp default-group-interface ip-int-name service-id service-id). Alc-interface names longer than the maximum allowed value are treated as session setup failures. |
|
26.6527.104 |
Alc-Tunnel-Serv-Id |
The service ID from which the tunnel should be established, enables the tunnel origin to be in a VPRN (VRF). The default value equals Base. Values above the limits or unreferenced are treated as a setup failure. Note: [241.26.6527.91] Alc-Tunnel-Serv-Name takes precedence over [26.6527.104] Alc-Tunnel-Serv-Id
if both are specified.
|
|
26.6527.120 |
Alc-Tunnel-Rx-Window-Size |
The initial receive window size being offered to the remote peer. This attribute is copied in the AVP 10 L2TP Receive Window Size. The remote peer may send the specified number of control messages before it must wait for an acknowledgment. The value with tag 0 is used as default for the tunnels where the value is not specified. A preconfigured value is used when the attribute is omitted (configure router/service vprn service-id l2tp receive-window-size). Values outside the allowed limits are treated as a setup failure. |
|
26.6527.144 |
Alc-Tunnel-Acct-Policy |
Refers to a preconfigured L2TP tunnel accounting policy name (configure aaa l2tp-accounting-policy policy-name). L2TP tunnel accounting (RFC 2867) can collect usage data based either on L2TP tunnel and L2TP sessions and send these accounting data to a RADIUS server. Different RADIUS attributes such as [66] Tunnel-Client-Endpoint, [67] Tunnel-Server-Endpoint, [68] Acct-Tunnel-Connection, [82] Tunnel-Assignment-ID can be used to identify the tunnel or session. The value with tag 0 is used as default for the tunnels where the value is not specified. Preconfigured values are used when the attribute is omitted (configure router/service vprn service-id l2tp radius-accounting-policy). Unreferenced policy names or policy names longer than the allowed maximum are treated as host setup failures. |
|
26.6527.204 |
Alc-Tunnel-DF-bit |
This attribute is used on an L2TP LAC only. By default, a LAC does not allow L2TP packet fragmentation by sending L2TP toward the LNS with the Do not Fragment (DF) bit set to 1. This DF bit can be set to 0 to allow downstream routers to fragment the L2TP packets. The LAC itself does not fragment L2TP packets. Packets sent with MTU bigger than the allowed size on the LAC egress port are dropped. This attribute is silently ignored if RADIUS returns an Alc-Tunnel-Group attribute. In that case, the tunnel level, group level, or as last resort, the root level configuration is used instead. |
|
26.6527.214 |
Alc-Tunnel-Recovery-Method |
Sets the L2TP LAC failover recovery method to be used for this tunnel: MCS or recovery tunnel (RFC 4951). Preconfigured values are used when the attribute is omitted (configure router/service vprn service-id l2tp failover recovery-method). When the tunnel recovery method is set to recovery-tunnel but LNS does not support this capability, then the system automatically falls back to mcs. Values outside the limits are treated as a setup failure. |
|
26.6527.215 |
Alc-Tunnel-Recovery-Time |
Only applicable when the L2TP LAC failover recovery-method is set to recovery-tunnel. Sets the L2TP LAC failover recovery-time to be negotiated with LNS using L2TP failover extensions (RFC 4951). It indicates to the LNS how long it needs to extend its protocol retry timeout before declaring the control channel down. Preconfigured values are used when attribute is omitted (configure router/service vprn service-id l2tp failover recovery-time). Values outside the limits are treated as a setup failure. |
|
241.26.6527.25 |
Alc-Steering-Profile |
The steering profile that should be applied to perform traffic steering on L2TP LAC. The steering profile is configured in the following CLI context: configure subscriber-mgmt steering-profile name. An L2TP LAC session is successfully set up when a non-existent steering profile name is referenced in an Access-Accept. A CoA containing a non-existent steering profile is rejected. In both cases, the non-existent steering profile is stored in the L2TP LAC session information and becomes active when the profile is configured at a later stage. To deactivate traffic steering on L2TP LAC, the [26.6527.238] Alc-Remove-Override attribute must be used. |
|
241.26.6527.88 |
Alc-Serv-Name |
The service name on the LNS node where the PPP sessions are established (configure service ies | vprn service-id name service-name subscriber-interface ip-int-name group-interface ip-int-name). Preconfigured values are used if the attribute is omitted (configure subscriber-mgmt local-user-db local-user-db-name ppp host host-name interface ip-int-name service-id service-id or configure router | service vprn service-id l2tp group ppp default-group-interface ip-int-name service-name service-name). Values that exceed the limits or are unreferenced are treated as a setup failure. Note: [241.26.6527.88] Alc-Serv-Name takes precedence over
[26.6527.100] Alc-Serv-Id if both are specified.
|
|
241.26.6527.91 |
Alc-Tunnel-Serv-Name |
The service name from which the tunnel should be established, enables the tunnel origin to be in a VPRN (VRF). The default value equals Base. Values that exceed the limits or are unreferenced are treated as a setup failure. Note: [241.26.6527.91] Alc-Tunnel-Serv-Name takes precedence over
[26.6527.104] Alc-Tunnel-Serv-Id if both are specified.
|
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
64 |
Tunnel-Type |
integer |
3 (mandatory value) |
Mandatory 3=L2TP For example: Tunnel-Type = L2TP |
|
65 |
Tunnel-Medium-Type |
integer |
1 (mandatory value) |
Mandatory 1=IP or IPv4 For example: Tunnel-Medium-Type = IP |
|
66 |
Tunnel-Client-Endpoint |
string |
Max. length = 15 bytes (untagged) or 16 bytes (tagged) |
<tag field><dotted-decimal IP address used on LAC as L2TP src-ip> If the tag field is greater than 0x1F, it is interpreted as the first byte of the following string field For example: # untagged Tunnel-Client-Endpoint = 3139382e35312e3130302e31 Tunnel-Client-Endpoint = 198.51.100.1 # tagged 0 Tunnel-Client-Endpoint = 003139382e35312e3130302e31 Tunnel-Client-Endpoint:0 = 198.51.100.1 # tagged 1 Tunnel-Client-Endpoint = 013139382e35312e3130302e31 Tunnel-Client-Endpoint:1 = 198.51.100.1 |
|
67 |
Tunnel-Server-Endpoint |
string |
Max. length = 15 bytes (untagged) or 16 bytes (tagged) Max. 451 attributes or limited by RADIUS message size |
<tag field><dotted-decimal IP address used on LAC as L2TP dst-ip> If Tag field is greater than 0x1F, it is interpreted as the first byte of the following string field For example: # tagged 1 Tunnel-Server-Endpoint = 013230332e302e3131332e31 Tunnel-Server-Endpoint:1 = 203.0.113.1 |
|
69 |
Tunnel-Password |
string |
64 chars |
For example: Tunnel-Password:1 = password |
|
81 |
Tunnel-Private-Group-ID |
string |
32 chars |
For example: Tunnel-Private-Group-ID:1 = MyPrivateTunnelGroup |
|
82 |
Tunnel-Assignment-ID |
string |
32 chars |
Tag 0x00 tunnel-group Tag 0x01-0x01f individual tunnels within this tunnel-group For example: Tunnel-Assignment-ID:0 += LNS-ALU Tunnel-Assignment-ID:1 += Tunnel-1 Tunnel-Assignment-ID:2 += Tunnel-2 |
|
83 |
Tunnel-Preference |
integer |
16777215 |
Default preference 50 For example: Tunnel 1 and 2 same preference and first selected Tunnel-Preference:1 += 10 Tunnel-Preference:2 += 10 Tunnel-Preference:3 += 20 |
|
90 |
Tunnel-Client-Auth-ID |
string |
64 chars |
For example: Tunnel-Client-Auth-Id:0 = LAC-Antwerp-1 |
|
91 |
Tunnel-Server-Auth-ID |
string |
64 chars |
For example: Tunnel-Server-Auth-ID:0 = LNS-Antwerp-1 |
|
26.2352.21 |
Tunnel-Max-sessions |
integer |
131071 |
max sessions per group with default=131071 default=131071 For example: Tunnel-Max-sessions:0 = 1000 |
|
26.4874.33 |
ERX-Tunnel-Maximum-Sessions |
integer |
131071 |
max sessions per group with default=131071 For example: ERX-Tunnel-Maximum-Sessions:0 = 1000 |
|
26.4874.64 |
ERX-Tunnel-Group |
string |
32 chars |
node preconfigured tunnel-group For example: ERX-Tunnel-Group:0 = MyCliTunnelGroupName |
|
26.6527.46 |
Alc-Tunnel-Group |
string |
32 chars |
node preconfigured tunnel-group For example: Alc-Tunnel-Group = MyCliTunnelGroupName |
|
26.6527.47 |
Alc-Tunnel-Algorithm |
integer |
values [1 to 3] |
1=weighted-access, 2=existing-first, 3=weighted-random default=existing-first For example: Alc-Tunnel-Algorithm:0 = weighted-access |
|
26.6527.48 |
Alc-Tunnel-Max-Sessions |
integer |
250000 |
max sessions per group or tunnel with default=131071 Unlimited cannot be set. The operational value is restricted to the maximum supported on the platform. For example: # 10000 for the group and individual settings per tunnel Alc-Tunnel-Max-Sessions:0 += 10000 Alc-Tunnel-Max-Sessions:1 += 2000 Alc-Tunnel-Max-Sessions:2 += 1000 |
|
26.6527.49 |
Alc-Tunnel-Idle-Timeout |
integer |
[0 to 3600] seconds |
infinite = -1 (16777215) or [0 to 3600] seconds with default= infinite For example: # do not disconnect tunnel1 Alc-Tunnel-Idle-Timeout :1 += 16777215 # disconnect tunnel2 after 1 minute Alc-Tunnel-Idle-Timeout :2 += 60 # disconnect tunnel3 immediately Alc-Tunnel-Idle-Timeout :3 += 0 |
|
26.6527.50 |
Alc-Tunnel-Hello-Interval |
integer |
[10 to 3600] seconds |
no keepalive (infinite) = 0 or -1 (16777215) or keepalive interval = [10 to 3600] seconds with default= 300 seconds For example: # tunnel 1 keepalive 120 seconds Alc-Tunnel-Hello-Interval:1 += 120 |
|
26.6527.51 |
Alc-Tunnel-Destruct-Timeout |
integer |
[60 to 86400] seconds |
[60 to 86400] seconds with default= 60 seconds For example: # tunnel 1 tunnel destruct timer 120 seconds Alc-Tunnel-Destruct-Timeout:1 += 120 |
|
26.6527.52 |
Alc-Tunnel-Max-Retries-Estab |
integer |
[2 to 7] |
default 5 For example: # retry 2 times for all tunnels in tunnel group Alc-Tunnel-Max-Retries-Estab:0 = 2 |
|
26.6527.53 |
Alc-Tunnel-Max-Retries-Not-Estab |
integer |
[2 to 7] |
default 5 For example: # retry 2 times for all tunnels in tunnel group Alc-Tunnel-Max-Retries-Not-Estab:0 = 2 |
|
26.6527.54 |
Alc-Tunnel-AVP-Hiding |
integer |
values [1 to 3] |
1=nothing,2=sensitive-only,3=all; default nothing 1=nothing: all L2TP AVPs in clear text 2=sensitive-only: AVP 11-Challenge, 13-Response, 14-Assigned Session ID, 21-Called-number, 22-Calling-number, 26-Initial Received LCP Confreq, 27-Last Sent LCP Confreq,28-Last Received LCP Confreq, 29-Proxy Authen Type, 30-Proxy Authen Name, 31-Proxy Authen Challenge, 32-Proxy Authen ID, 33-Proxy Authen Response 3=all: all AVPs that, according RFC 2661 can be hidden, are hidden. For example: # Best common practices Alc-Tunnel-AVP-Hiding:0 = sensitive-only |
|
26.6527.97 |
Alc-Tunnel-Challenge |
integer |
values [1 to 2] |
1=never, 2=always; default never For example: Alc-Tunnel-Max-Retries-Estab:0 = always |
|
26.6527.100 |
Alc-Serv-Id |
integer |
2147483647 ID |
For example: Alc-Serv-Id = 100 |
|
26.6527.101 |
Alc-Interface |
string |
32 chars |
For example: Alc-Interface = MyGroupInterface |
|
26.6527.104 |
Alc-Tunnel-Serv-Id |
integer |
2147483647 ID |
default = 'Base' router For example: # vprn service 100 Alc-Tunnel-Serv-Id = 100 |
|
26.6527.120 |
Alc-Tunnel-Rx-Window-Size |
integer |
[4 to 1024] |
Tag 0 = default when not specified (all tunnels) Tag 1 to 31 = specific tunnel default 64 For example: Alc-Tunnel-Rx-Window-Size = 1000 |
|
26.6527.144 |
Alc-Tunnel-Acct-Policy |
string |
32 chars |
For example: Alc-Tunnel-Acct-Policy = MyL2TPTunnelPolicy |
|
26.6527.204 |
Alc-Tunnel-DF-bit |
integer |
values [0 to 1] |
0=clr-lac-data, 1=set-lac-data; default = 1 For example: Alc-Tunnel-DF-bit:0 = clr-lac-data |
|
26.6527.214 |
Alc-Tunnel-Recovery-Method |
integer |
values [0 to 1] |
0=recovery-tunnel, 1=mcs; default = 0 For example: Alc-Tunnel-Recovery-Method:1 = recovery-tunnel |
|
26.6527.215 |
Alc-Tunnel-Recovery-Time |
integer |
[0 to 900] seconds |
[0 to 900] in seconds; default = 0 For example: Alc-Tunnel-Recovery-Time = 180 |
|
241.26.6527.25 |
Alc-Steering-Profile |
string |
32 chars |
Steering profile name For example: Alc-Steering-Profile = ‟steering-profile-1” |
|
241.26.6527.88 |
Alc-Serv-Name |
string |
64 chars |
For example: Alc-Serv-Name=Service-1 |
|
241.26.6527.91 |
Alc-Tunnel-Serv-Name |
string |
64 chars |
For example: Alc-Tunnel-Serv-Name=Service-1 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Encrypted | Tag | Max. tag |
|---|---|---|---|---|---|---|---|
|
64 |
Tunnel-Type |
0-1 |
1 |
0 |
✓ |
31 |
|
|
65 |
Tunnel-Medium-Type |
0-1 |
1 |
0 |
✓ |
31 |
|
|
66 |
Tunnel-Client-Endpoint |
0-1 |
0-1 |
0 |
✓ |
31 |
|
|
67 |
Tunnel-Server-Endpoint |
0-1 |
1 |
0 |
✓ |
31 |
|
|
69 |
Tunnel-Password |
0 |
0-1 |
0 |
✓ |
✓ |
31 |
|
81 |
Tunnel-Private-Group-ID |
0-1 |
0-1 |
0 |
✓ |
31 |
|
|
82 |
Tunnel-Assignment-ID |
0 |
0-1 |
0 |
✓ |
31 |
|
|
83 |
Tunnel-Preference |
0 |
0-1 |
0 |
✓ |
31 |
|
|
90 |
Tunnel-Client-Auth-ID |
0-1 |
0-1 |
0 |
✓ |
31 |
|
|
91 |
Tunnel-Server-Auth-ID |
0-1 |
0-1 |
0 |
✓ |
31 |
|
|
26.2352.21 |
Tunnel-Max-sessions |
0 |
0-1 |
0 |
— |
||
|
26.4874.33 |
ERX-Tunnel-Maximum-Sessions |
0 |
0-1 |
0 |
— |
||
|
26.4874.64 |
ERX-Tunnel-Group |
0 |
0-1 |
0 |
— |
||
|
26.6527.46 |
Alc-Tunnel-Group |
0 |
0-1 |
0 |
— |
||
|
26.6527.47 |
Alc-Tunnel-Algorithm |
0 |
0-1 |
0 |
— |
||
|
26.6527.48 |
Alc-Tunnel-Max-Sessions |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.49 |
Alc-Tunnel-Idle-Timeout |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.50 |
Alc-Tunnel-Hello-Interval |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.51 |
Alc-Tunnel-Destruct-Timeout |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.52 |
Alc-Tunnel-Max-Retries-Estab |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.53 |
Alc-Tunnel-Max-Retries-Not-Estab |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.54 |
Alc-Tunnel-AVP-Hiding |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.97 |
Alc-Tunnel-Challenge |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.100 |
Alc-Serv-Id |
0 |
0-1 |
0 |
— |
||
|
26.6527.101 |
Alc-Interface |
0 |
0-1 |
0 |
— |
||
|
26.6527.104 |
Alc-Tunnel-Serv-Id |
0 |
0-1 |
0 |
— |
||
|
26.6527.120 |
Alc-Tunnel-Rx-Window-Size |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.144 |
Alc-Tunnel-Acct-Policy |
0 |
0-1 |
0 |
✓ |
31 (untag-ged) |
|
|
26.6527.204 |
Alc-Tunnel-DF-bit |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.214 |
Alc-Tunnel-Recovery-Method |
0 |
0-1 |
0 |
✓ |
31 |
|
|
26.6527.215 |
Alc-Tunnel-Recovery-Time |
0 |
0-1 |
0 |
✓ |
31 |
|
|
241.26.6527.25 |
Alc-Steering-Profile |
0 |
0-1 |
0-1 |
— |
||
|
241.26.6527.88 |
Alc-Serv-Name |
0 |
0-1 |
0 |
— |
||
|
241.26.6527.91 |
Alc-Tunnel-Serv-Name |
0 |
0-1 |
0 |
— |
Business service access
| Attribute ID | Attribute name | Description |
|---|---|---|
|
22 |
Framed-Route |
Routing information (IPv4 managed route) to be configured on the NAS for a host (DHCP, PPPoE, ARP) that operates as a router without NAT (so called routed subscriber host). The route included in the Framed-Route attribute is accepted as a managed route only if the next-hop points to the host’s IP address if the next-hop address equals 0.0.0.0, or if the included route is a valid classful network in case the subnet-mask is omitted. If neither is applicable, this specific framed-route attribute is ignored and the host is instantiated without this specific managed route installed. A Framed-Route attribute is also ignored if the SAP does not have anti-spoof configured to NH-MAC (the host is installed as a standalone host without managed route). The number of routes above limits are silently ignored. Optionally, a metric, tag, and protocol preference can be specified for the managed route. If the metrics are not specified, are specified in a wrong format, or specified with out-of-range values, then default values are used for all metrics: metric=0, no tag and preference=0. If an identical managed route is associated with different routed subscriber hosts in the context of the same IES/VPRN service, up to max-ecmp-routes managed routes are installed in the routing table (configured as ecmp max-ecmp-routes in the routing instance). Candidate ECMP Framed-Routes have identical prefix, equal lowest preference, and equal lowest metric. The lowest IP next-hop” is the tie breaker if more candidate ECMP Framed-Routes are available than the configured max-ecmp-routes. Other identical managed routes are shadowed (not installed in the routing table) and an event is logged. An alternative to RADIUS managed routes are managed routes using host dynamic BGP peering. Valid RADIUS-learned managed routes can be included in RADIUS accounting messages. |
|
99 |
Framed-IPv6-Route |
Routing information (IPv6 managed route) to be configured on the NAS for a v6 WAN host (IPoE or PPPoE) that operates as a router. The functionality is comparable with offering multiple PD prefixes for a single host. The route included in the Framed-IPv6-Route attribute is accepted as a managed route only if its next-hop is a WAN host (DHCPv6 IA-NA or SLAAC) or if the next-hop address equals ::. As a consequence, Framed-IPv6-Routes with explicit configured gateway prefix of a pd-host (DHCPv6 IA-PD) are not installed. A Framed-Route attribute is also ignored if the SAP does not have anti-spoof configured to NH-MAC (the host is installed as a standalone host without a managed route). The number of routes above limits are silently ignored. Optionally, a metric, tag, or protocol preference can be specified for the managed route. If the metrics are not specified, specified in a wrong format, or specified with out-of-range values, then default values are used for all metrics: metric=0, no tag and preference=0. If an identical managed route is associated with different routed subscriber hosts in the context of the same IES or VPRN service up to max-ecmp-routes managed routes are installed in the routing table (configured as ecmp max-ecmp-routes in the routing instance). Candidate ECMP Framed-IPv6-Routes have identical prefix, equal lowest preference and equal lowest metric. The lowest IP next-hop is the tie breaker if more candidate ECMP Framed-IPv6-Routes are available than the configured max-ecmp-routes. Other identical managed routes are shadowed (not installed in the routing table) and an event is logged. Valid RADIUS learned managed routes can be included in RADIUS accounting. |
|
26.6527.55 |
Alc-BGP-Policy |
Refers to a preconfigured policy under configure subscriber-mgmt bgp- peering-policy policy-name. Mandatory attribute for dynamic BGPv4 peering. The referenced policy contains all required parameters to setup the dynamic BGPv4 peer. Peer-AS, MD5 key, Authentication-Keychain and import and export policies can be overridden by optional RADIUS attributes. Dynamic BGPv4 peering related attributes are ignored if the session or host does not terminate in a VPRN. Host setup is successful, but without BGPv4 peering if a non-existing policy-name is received or if the SAP anti-spoof type is different from nh-mac. Policy names above the maximum length result in a host setup failure. |
|
26.6527.56 |
Alc-BGP-Auth-Keychain |
Optional attribute for dynamic BGPv4 peering. Refers to the keychain parameters (configure system security keychain keychain-name) used to sign or authenticate the BGP protocol stream using the TCP enhanced authentication option (draft-bonica-tcp-auth). Host setup is successful, but without BGPv4 peering if a non-existing keychain name is received. Keychain names above the maximum length result in a host setup failure. Alternative for [26.6527.57] Alc-BGP-Auth-Key. |
|
26.6527.57 |
Alc-BGP-Auth-Key |
Optional attribute for dynamic BGPv4 peering. Indicates the authentication key used between BGPv4 peers before establishing sessions. Authentication is done using the MD5 message based digest protocol. Authentication keys are truncated at 247 Bytes and are not encrypted. |
|
26.6527.58 |
Alc-BGP-Export-Policy |
Optional attribute for dynamic BGPv4 peering. This refers to a preconfigured BGP export policy (configure router policy-options policy-statement name). The RADIUS received policy is appended to the list of export policies configured in the peering policy (configure subscriber-mgmt bgp-peering-policy policy-name export policy-name) if there are fewer than 15 preconfigured policies or replaces the fifteenth policy. Host setup is successful, but without export policy applied if a non-existing policy-name is received. Policy names above the maximum length result in a host setup failure. |
|
26.6527.59 |
Alc-BGP-Import-Policy |
Optional attribute for dynamic BGPv4 peering. Refers to a preconfigured BGP import policy (configure router policy-options policy-statement name). The RADIUS received policy is appended to the peer (if preconfigured policies for peer are smaller than 15) or replaces the fifteenth policy (if preconfigured policies for peer are exact 15). Host setup is successful but without import policy applied if a non-existing policy-name is received. Policy names above the maximum length result in a host setup failure. |
|
26.6527.60 |
Alc-BGP-PeerAS |
Optional attribute for dynamic BGPv4 peering. Specifies the Autonomous System number for the remote BGPv4 peer. |
|
26.6527.207 |
Alc-RIP-Policy |
Refers to the preconfigured policy under configure subscriber-mgmt rip-policy policy-name and enables the BNG to listen to RIPv1 or RIPv2 messages from the host (master SRRP node only in case of a dual-homed BNG). The referenced policy contains the authentication type and authentication key used to establish a RIP neighbor with this host. Host setup is successful, but the RIP message from the host are ignored if a non-existing policy name is received or if the SAP anti-spoof type is different from NH-MAC. Policy names exceeding the maximum length result in a host setup failure. |
|
26.6527.208 |
Alc-BGP-IPv6-Policy |
Refers to a preconfigured policy under configure subscriber-mgmt bgp-peering-policy policy-name. Mandatory attribute for dynamic BGPv6 peering. The referenced policy contains all required parameters to setup the dynamic BGPv6 peer. Peer-AS, MD5 key, Authentication-Keychain and import or export policies can be overridden by optional RADIUS attributes. Dynamic BGPv6 peering related attributes are ignored if the session or host does not terminate in a VPRN. Host setup is successful, but without BGPv6 peering if a non-existing policy name is received or if the SAP anti-spoof type is different from nh-mac. Policy names above the maximum length result in a host setup failure. For single hop BGPv6, the peering address for the customer premises equipment (CPE) must be an IPv6 address configured on the subscriber interface. For multihop BGPv6, the peering address for the CPE can be any routable IPv6 interface address in the same routing instance as the subscriber host. |
|
26.6527.209 |
Alc-BGP-IPv6-Auth-Keychain |
Optional attribute for dynamic BGPv6 peering. Refers to the keychain parameters (configure system security keychain keychain-name) used to sign or authenticate the BGPv6 protocol stream using the TCP enhanced authentication option (draft-bonica-tcp-auth). Host setup is successful, but without BGPv6 peering if a non-existing keychain name is received. Keychain names above the maximum length result in a host setup failure. Alternative for [26.6527.201] Alc-BGP-IPv6-Auth-Key. |
|
26.6527.210 |
Alc-BGP-IPv6-Auth-Key |
Optional attribute for dynamic BGPv6 peering. Indicates the authentication key used between BGPv6 peers before establishing sessions. Authentication is performed using the MD5 message based digest protocol. Authentication keys are truncated at 247 bytes and are not encrypted. |
|
26.6527.211 |
Alc-BGP-IPv6-Export-Policy |
Optional attribute for dynamic BGPv6 peering. Refers to a preconfigured BGP export policy (configure router policy-options policy-statement name). The RADIUS received policy is appended to the peer (if there are fewer than 15) or replaces the fifteenth policy. Host setup is successful, but without export policy applied if a non-existing policy name is received. Policy names above the maximum length result in a host setup failure. |
|
26.6527.212 |
Alc-BGP-IPv6-Import-Policy |
Optional attribute for dynamic BGPv6 peering. Refers to a preconfigured BGP import policy (configure router policy-options policy-statement name). The RADIUS received policy is appended to the peer (if there are fewer than 15) or if the received policy replaces the fifteenth policy. Host setup is successful, but without import policy applied if a non-existing policy name is received. Policy names above the maximum length result in a host setup failure. |
|
26.6527.213 |
Alc-BGP-IPv6-PeerAS |
Optional attribute for dynamic BGPv6 peering. Specifies the Autonomous System number for the remote BGPv6 peer. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
22 |
Framed-Route |
string |
max. 50 Framed-Route attributes |
"<ip-prefix>[/<prefix-length>] <space> <gateway-address> [<space> <metric>] [<space> tag <space> <tag-value>] [<space> pref <space> <preference-value>]” where: <space> is a white space or blank character <ip-prefix>[/prefix-length] is the managed route to be associated with the routed subscriber host. The prefix-length is optional and if not specified, a class-full class A,B or C subnet is assumed. <gateway-address> must be the routed subscriber host IP address. ‟0.0.0.0” is automatically interpreted as the host IPv4 address. [<metric>] (Optional) Installed in the routing table as the metric of the managed route. If not specified, metric zero is used. Value = [0 to 65535] [tag <tag-value>] (Optional) The managed route is tagged for use in routing policies. If not specified or tag-value=0, then the route is not tagged. Value = [0 to 4294967295] [pref <preference-value>] (Optional) Installed in the routing table as protocol preference for this managed route. If not specified, preference zero is used. Value = [0 to 255] For example: Framed-Route = "192.168.1.0/24 0.0.0.0" where 0.0.0.0 is replaced by host address. Default metrics are used (metric=0, preference=0 and no tag) Framed-Route = "192.168.1.0 0.0.0.0" where 192.168.1.0 is a class-C network /24 and 0.0.0.0 is replaced host address. Default metrics are used. Framed-Route = "192.168.1.0/24 192.168.1.1" where 192.168.1.1 is the host address. Default metrics are used. Framed-Route = "192.168.1.0 0.0.0.0 10 tag 3 pref 100" installs a managed route with metric=10, protocol preference = 100 and tagged with tag=3 Framed-Route = "192.168.1.0 0.0.0.0 tag 5" installs a managed route with metric=0 (default), protocol preference = 0 (default) and tagged with tag=5" |
|
99 |
Framed-IPv6-Route |
string |
max. 50 Framed-IPv6-Route attributes |
<ip-prefix>/<prefix-length> <space> <gateway-address> [<space> <metric>] [<space> tag <space> <tag-value>] [<space> pref <space> <preference-value>]” where: <space> is a white space or blank character <ip-prefix>/<prefix-length> is the managed route to be associated with the routed subscriber host. <gateway-address> must be the routed subscriber host IP address. ‟::” and ‟0:0:0:0:0:0:0:0” are automatically interpreted as the wan-host IPv6 address. [<metric>] (Optional) Installed in the routing table as the metric of the managed route. If not specified, metric zero is used. Value = [0 to 65535] [tag <tag-value>] (Optional) The managed route is tagged for use in routing policies. If not specified or tag-value=0, then the route is not tagged. Value = [0 to 4294967295] [pref <preference-value>] (Optional) Installed in the routing table as protocol preference for this managed route. If not specified, preference zero is used. Value = [0 to 255] For example: Framed-IPv6-Route = "2001:db8:1::/48 ::" where :: resolves in the wan-host. Default metrics are used (metric=0, preference=0 and no tag) Framed-IPv6-Route = "2001:db8:2::/48 0:0:0:0:0:0:0:0" where 0:0:0:0:0:0:0:0 resolves in the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:3::/48 0::0" where 0::0 resolves in the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:3::/48 2001:db8:aa::1" where 2021:1::1 is the wan-host. Default metrics are used. Framed-IPv6-Route = "2001:db8:1::/48 :: 10 tag 3 pref 100" installs a managed route with metric = 10, protocol preference = 100 and tagged with tag = 3 Framed-IPv6-Route = "2001:db8:1::/48 :: tag 5" installs a managed route with metric = 0 (default), protocol preference = 0 (default) and tagged with tag = 5 |
|
26.6527.55 |
Alc-BGP-Policy |
string |
32 chars |
For example: Alc-BGP-Policy = MyBGPPolicy |
|
26.6527.56 |
Alc-BGP-Auth-Keychain |
string |
32 chars |
For example: Alc-BGP-Auth-Keychain = MyKeychainPolicy |
|
26.6527.57 |
Alc-BGP-Auth-Key |
octets |
247 bytes |
For example: Alc-BGP-Auth-Key = "SecuredBGP" |
|
26.6527.58 |
Alc-BGP-Export-Policy |
string |
32 chars |
For example: Alc-BGP-Export-Policy = to_dynamic_bgp_peer |
|
26.6527.59 |
Alc-BGP-Import-Policy |
string |
32 chars |
For example: Alc-BGP-Import-Policy = from_dynamic_bgp_peer |
|
26.6527.60 |
Alc-BGP-PeerAS |
integer |
[1 to 4294967294] |
For example: Alc-BGP-PeerAS = 64500 |
|
26.6527.207 |
Alc-RIP-Policy |
string |
32 chars |
For example: Alc-RIP-Policy = MyRIPPolicy |
|
26.6527.208 |
Alc-BGP-IPv6-Policy |
string |
32 chars |
For example: Alc-BGP-IPv6-Policy = MyBGPPolicy |
|
26.6527.209 |
Alc-BGP-IPv6-Auth-Keychain |
string |
32 chars |
For example: Alc-BGP-IPv6-Auth-Keychain = MyKeychain |
|
26.6527.210 |
Alc-BGP-IPv6-Auth-Key |
octets |
247 bytes |
For example: Alc-BGP-IPv6-Auth-Key = ‟SecuredBGPv6” |
|
26.6527.211 |
Alc-BGP-IPv6-Export-Policy |
string |
32 chars |
For example: Alc-BGP-IPv6-Export-Policy = to_dynamic_bgpv6_peer |
|
26.6527.212 |
Alc-BGP-IPv6-Import-Policy |
string |
32 chars |
For example: Alc-BGP-IPv6-Import-Policy = from_dynamic_bgpv6_peer |
|
26.6527.213 |
Alc-BGP-IPv6-PeerAS |
integer |
[1 to 4294967294] |
For example: Alc-BGP-IPv6-PeerAS = 64500 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
22 |
Framed-Route |
0 |
0+ |
0 |
|
99 |
Framed-IPv6-Route |
0 |
0+ |
0 |
|
26.6527.55 |
Alc-BGP-Policy |
0 |
0-1 |
0 |
|
26.6527.56 |
Alc-BGP-Auth-Keychain |
0 |
0-1 |
0 |
|
26.6527.57 |
Alc-BGP-Auth-Key |
0 |
0-1 |
0 |
|
26.6527.58 |
Alc-BGP-Export-Policy |
0 |
0-1 |
0 |
|
26.6527.59 |
Alc-BGP-Import-Policy |
0 |
0-1 |
0 |
|
26.6527.60 |
Alc-BGP-PeerAS |
0 |
0-1 |
0 |
|
26.6527.207 |
Alc-RIP-Policy |
0 |
0-1 |
0 |
|
26.6527.208 |
Alc-BGP-IPv6-Policy |
0 |
0-1 |
0 |
|
26.6527.209 |
Alc-BGP-IPv6-Auth-Keychain |
0 |
0-1 |
0 |
|
26.6527.210 |
Alc-BGP-IPv6-Auth-Key |
0 |
0-1 |
0 |
|
26.6527.211 |
Alc-BGP-IPv6-Export-Policy |
0 |
0-1 |
0 |
|
26.6527.212 |
Alc-BGP-IPv6-Import-Policy |
0 |
0-1 |
0 |
|
26.6527.213 |
Alc-BGP-IPv6-PeerAS |
0 |
0-1 |
0 |
Accounting on-line charging
| Attribute ID | Attribute name | Description |
|---|---|---|
|
26.6527.95 |
Alc-Credit-Control-CategoryMap |
Refers to a preconfigured category-map (configure subscriber-mgmt category-map category-map-name) that contains credit control information for up to 16 predefined categories The category-map-name can also be assigned using the LUDB, or credit-control-policy if the attribute is omitted. This attribute is ignored if the host has no credit‑control‑policy defined in its SLA profile instance. Strings with lengths above the limits are treated as a setup failure. |
|
26.6527.96 |
Alc-Credit-Control-Quota |
Defines a volume and time quota per category. Either volume or time monitoring is supported and the operational credit-type (volume or time) is taken from the category map, if both the volume and time quota in the attribute are non-zero. The operational credit-type becomes time if the volume quota is zero, and volume if the time quota is zero. The Credit Expired becomes true and the corresponding Out Of Credit action is triggered, if both the time and volume quota are zero in the initial Authentication-Accept or CoA. The value zero for both the time and volume quotas in additional Authentication Accepts (triggered by a credit refresh or re-authentication) is interpreted as no extra credit granted. This does not influence the current available credit, where non-zero values reset the current available credit. For CoA requests, both the Alc-Credit-Control-Category Map and Alc-Credit-Control-Quota attributes must be included. For RADIUS-Access Accepts this is not mandatory and either both or one of the two attributes can come from pre-defined values from the node. Volume quota values outside the defined limits are treated as an error condition. Time quota values above the defined limits are accepted and capped at the maximum value. If more attributes are present than allowed by the limits, it is treated as a setup failure. For Distributed Subscriber Management (DSM), this VSA only supports volume quota. Time quota must always be set to zero. Two predefined categories are supported:
The related attribute Alc-Credit-Control-CategoryMap is not used for DSM. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
26.6527.95 |
Alc-Credit-Control-CategoryMap |
string |
32 chars |
For example: Alc-Credit-Control-CategoryMap = MyCatMap |
|
26.6527.96 |
Alc-Credit-Control-Quota |
string |
(2^64 - 1) volume value (2^32 - 1) time value 16 attributes For DSM: 1B to 1TB volume value 0 (fixed) time value 2 attributes |
volume-value volume-units|time-value time- units|category-name <volume-value>: converted in bytes and stored in 64 bit counter - value '0' = no volume credit - value between 1 Byte and (2^64 - 1 / 18446744073709551615) Bytes <time-value>: converted in seconds and stored in 32 bit counter - value '0' = no time credit - value between 1 second and (2^32 - 1 / 4294967295) seconds <volume-units>: - in byte (B or units omitted), kilobyte (K or KB), megabyte (M or MB), gigabyte (G or GB) - a combination (10GB200MB20KB|) of different volume units is not allowed. <time-units>: - in seconds (s or units omitted), in minutes (m), in hours (h), in days (d) - a combination of different time units is allowed with some restrictions: 15m30s is accepted while 15m60s is not. For example: 500 Mbytes volume credit for category cat1 and 1 day, 2 hours, 3 minutes and 4 seconds time credit for category cat2 Alc-Credit-Control-Quota += 500MB|0|cat1, Alc-Credit-Control-Quota += 0|1d2h3m4s|cat2 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
26.6527.95 |
Alc-Credit-Control-CategoryMap |
0 |
0-1 |
0-1 |
|
26.6527.96 |
Alc-Credit-Control-Quota |
0+ |
0+ |
0+ |
IP and IPv6 filters
| Attribute ID | Attribute name | Description |
|---|---|---|
|
92 |
NAS-Filter-Rule |
Subscriber host specific filter entry. The match criteria are automatically extended with the subscriber host IP or IPv6 address as source (ingress) or destination (egress) IP. They represent a per-host customization of a generic filter policy: only traffic to or from the subscriber host matches against these entries. A range of entries must be reserved for subscriber host specific entries in a filter policy: configure filter ip-filter/ipv6-filter filter-id sub-insert-radius Subscriber host specific filter entries are moved if the subscriber host filter policy is changed (new SLA profile or ip filter policy override) and if the new filter policy contains enough free reserved entries. When the subscriber host session terminates or is disconnected, then the corresponding subscriber host-specific filter entries are also deleted. The function of the attribute is identical to [26.6527.159] Alc-Ascend-Data-Filter-Host-Spec but it has a different format. The format used to specify host specific filter entries (NAS-Filter-Rule format or Alc-Ascend-Data-Filter-Host-Spec format) cannot change during the lifetime of the subscriber host. Mixing formats in a single RADIUS message results in a failure. |
|
26.529.242 |
Ascend-Data-Filter |
A local configured filter policy can be extended with shared dynamic filter entries. A dynamic copy of the base filter (the filter associated with the host using SLA profile or host filter override) is made and extended with the set of filter rules per type (IPv4 or IPv6) and direction (ingress or egress) in the RADIUS message. If a dynamic copy with the same set of rules already exists, no new copy is made, but the existing copy is associated with the host or session. If after host or session disconnection, no hosts or sessions are associated with the dynamic filter copy, then the dynamic copy is removed. Shared filter entries are moved if the subscriber host filter policy is changed (new SLA profile or IP filter policy override) and if the new filter policy contains enough free reserved entries. A range of entries must be reserved for shared entries in a filter policy using the following command: configure filter ip-filter/ipv6 filter filter-id sub-insert-shared-radius. The function of the attribute is identical to [26.6527.158] Alc-Nas-Filter-Rule-Shared but it has a different format. The format used to specify shared filter entries (Alc-Nas-Filter-Rule-Shared format or Ascend-Data-Filter format) cannot change during the lifetime of the subscriber host. Mixing formats in a single RADIUS message results in a failure. Shared filter entries should only be used if many hosts share the same set of filter rules that need to be controlled from RADIUS. |
|
26.6527.134 |
Alc-Subscriber-Filter |
Subscriber host preconfigured IP or IPv6 ingress and egress filters to be used instead of the filters defined in the SLA profile. Non-relevant fields are ignored (for example, IPv4 filters for an IPv6 host). The scope of the local preconfigured filter should be set to template for correct operation (configure filter ip-filter/ipv6-filter filter-id scope template). This is not enforced. For a RADIUS CoA message, if the ingress or egress field is missing in the VSA, there is no change for that direction. For a RADIUS Access-Accept message, if the ingress or egress field is missing in the VSA, then the IP filters as specified in the SLA profile is active for that direction Applicable to all dynamic host types, including L2TP LNS but excluding L2TP LAC. Note: Filter name ([245.26.6527.7.x]
Alc-Sub-…-Filter-Name) and filter ID ([26.6527.134]
Alc-Subscriber-Filter) overrides should not be mixed during the
lifetime of a subscriber host or session.
|
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
A local configured filter policy can be extended with shared dynamic filter entries. A dynamic copy of the base filter (the filter associated with the host using SLA profile or host filter override) is made and extended with the set of filter rules per type (IPv4 or IPv6) and direction (ingress or egress) in the RADIUS message. If a dynamic copy with the same set of rules already exists, no new copy is made, but the existing copy is associated with the host or session. If after host or session disconnection, no hosts or sessions are associated with the dynamic filter copy, then the dynamic copy is removed. Shared filter entries are moved if the subscriber host filter policy is changed (new SLA profile or IP filter policy override) and if the new filter policy contains enough free reserved entries. A range of entries must be reserved for shared entries in a filter policy: configure filter ip-filter|ipv6-filter filter-id sub-insert-shared-radius. The function of the attribute is identical to [26.529.242] Ascend-Data-Filter but it has a different format. The format used to specify shared filter entries (Alc-Nas-Filter-Rule-Shared format or Ascend-Data-Filter format) cannot change during the lifetime of the subscriber host. Mixing formats in a single RADIUS message results in a failure. Shared filter entries should only be used if many hosts share the same set of filter rules that need to be controlled from RADIUS. |
|
26.6527.159 |
Alc-Ascend-Data-Filter-Host-Spec |
Subscriber host specific filter entry. The match criteria is automatically extended with the subscriber host IP address or IPv6 address as source (ingress) or destination (egress) IP. They represent a per host customization of a generic filter policy: only traffic to or from the subscriber host matches against these entries. A range of entries must be reserved for subscriber host specific entries in a filter policy: configure filter ip-filter/ipv6-filter filter-id sub-insert-radius. Subscriber host specific filter entries are moved if the subscriber host filter policy is changed (new SLA profile or IP filter policy override) and if the new filter policy contains enough free reserved entries. When the subscriber host session terminates or is disconnected, then the corresponding subscriber host specific filter entries are also deleted. The function of the attribute is identical to [92] Nas-Filter-Rule but it has a different format. The format used to specify host-specific filter entries (NAS-Filer-Rule format or Alc-Ascend-Data-Filter-Host-Spec format) cannot change during the lifetime of the subscriber host. Mixing formats in a single RADIUS message results in a failure. |
| 245.26.6527.7 | Alc-Subscriber-Filter-Name | Used to override IP and IPv6 ingress and egress filters or the one time HTTP redirection
filter configured in the subscriber-mgmt sla-profile
context. See [245.26.6527.7] Alc-Subscriber-Filter-Name Attribute Details for a
detailed description of the attribute. Note: Filter name ([245.26.6527.7.x]
Alc-Sub-…-Filter-Name) and filter ID ([26.6527.134]
Alc-Subscriber-Filter or [26.6527.136]
Alc-Onetime-Http-Redirection-Filter-Id) overrides should not be
mixed during the lifetime of a subscriber host or
session.
|
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
92 |
NAS-Filter-Rule |
string |
Max. 10 attributes per message (up to 10 host specific filter entries) |
The format of a NAS-Filter-Rule is defined in RFC 3588, Diameter Base Protocol, section-4.3, Derived AVP Data Formats. A single filter rule is a string of format <action> <direction> <protocol> from <source> to <destination> <options> Multiple rules should be separated by a NUL (0x00). A NAS-Filter-Rule attribute may contain a partial rule, one rule, or more than one rule. Filter rules may be continued across attribute boundaries. A RADIUS message with NAS-Filter-Rule attribute value equal to 0x00 or ‟ ‟ (a space) removes all host specific filter entries for that host. See also IP filter attribute details. For example: Nas-Filter-Rule = permit in ip from any to 10.1.1.1/32 |
|
26.529.242 |
Ascend-Data-Filter |
Octets |
Max. 120 attributes per message. Up to 120 shared filter entries: total of IPv4 ingress + IPv4 egress + IPv6 ingress + IPv6 egress Minimum/maximum attribute length:
|
A string of octets with fixed field lengths (type (ipv4/ipv6), direction (ingress or egress), src-ip, dst-ip, and so on. Each attribute represents a single filter entry. See IP filter attribute details for a description of the format. For example: # permit in ip from any to 10.1.1.1/32 Ascend-Data-Filter = 0x01010100000000000a01010100200000000000000000 |
|
26.6527.134 |
Alc-Subscriber-Filter |
string |
Max. 1 VSA. |
Comma separated list of strings: Ingr-v4:<number>, Ingr-v6:<number>,Egr-v4:<number>,Egr-v6:<number> where <number> can be one of: [1 to 65535] = ignore sla-profile filter; apply this filter-id 0 = ignore sla-profile filter; do not assign a new filter (only allowed if no dynamic subscriber host specific rules are present) -1 = No change in filter configuration -2 = Restore sla-profile filter For example: Alc-Subscriber-Filter = Ingr-v4:20,Egr-v4:101 |
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
string |
Max. 120 attributes per message. Up to 120 shared filter entries: total of IPv4 ingress + IPv4 egress + IPv6 ingress + IPv6 egress |
The format is identical to [92] NAS-Filter-Rule and is defined in RFC 3588 section-4.3. A single filter rule is a string of format <action> <direction> <protocol> from <source> to <destination> <options> Multiple rules should be separated by a NUL (0x00). An Alc-Nas-Filter-Rule-Shared attribute may contain a partial rule, one rule, or more than one rule. Filter rules may be continued across attribute boundaries. A RADIUS message with Alc-Nas-Filter-Rule-Shared attribute value equal to 0x00 or ‟ ‟ (a space) removes the shared filter entries for that host. See also IP filter attribute details. For example: Alc-Nas-Filter-Rule-Shared = permit in ip from any to 10.1.1.1/32 |
|
26.6527.159 |
Alc-Ascend-Data-Filter-Host-Spec |
octets |
Max. 10 attributes per message (up to 10 host specific filter entries) minimum/maximum attribute length:
|
A string of octets with fixed field length (type ipv4 or ipv6), direction (ingress or egress), src-ip, dst-ip, and so on). Each attribute represents a single filter entry. See IP filter attribute details for a description of the format. For example: # permit in ip from any to 10.1.1.1/32 Alc-Ascend-Data-Filter-Host-Spec = 0x01010100000000000a01010100200000 000000000000 |
| 245.26.6527.7 | Alc-Subscriber-Filter-Name | tlv | 5 attributes | See [245.26.6527.7] Alc-Subscriber-Filter-Name Attribute Details for a detailed description of the attribute format. |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
92 |
NAS-Filter-Rule |
0 |
0+ |
0+ |
|
26.529.242 |
Ascend-Data-Filter |
0 |
0+ |
0+ |
|
26.6527.134 |
Alc-Subscriber-Filter |
0 |
0-1 |
0-1 |
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
0 |
0+ |
0+ |
|
26.6527.159 |
Alc-Ascend-Data-Filter-Host-Spec |
0 |
0+ |
0+ |
| 245.26.6527.7 | Alc-Subscriber-Filter-Name | 0 | 0+ | 0+ |
IP filter attribute details
[92] Nas-Filter-Rule and [26.6527.158] Alc-Nas-Filter-Rule-Shared
The format for [92] Nas-Filter-Rule and [26.6527.158] Alc-Nas-Filter-Rule-Shared is a string formatted as: action direction protocol from source to destination options. [92] Nas-Filter-Rule attribute format provides details on the respective fields.
| Action or classifier | Value | Corresponding SR OS filter function | |
|---|---|---|---|
|
action |
deny |
action drop |
|
|
permit |
action forward |
||
|
direction |
in |
ingress |
|
|
out |
egress |
||
|
protocol |
ip |
protocol none |
|
|
any number [0 to 255] |
protocol [0 to 255] |
||
|
ip |
next-header none |
||
|
any number [1 to 42] |
next-header [1 to 42] |
||
|
any number [45 to 49] |
next-header [45 to 49] |
||
|
any number [52 to 59] |
next-header [52 to 59] |
||
|
any number [61 to 255] |
next-header [61 to 255] |
||
|
any number 43|44|50|51|60 |
not supported |
||
|
from source |
any |
100 |
ingress: src-ip = host-ip-address; src-port eq 100 egress: src-ip = 0.0.0.0/0 | ::/0; src-port eq 100 |
|
200 to 65535 |
ingress: src-ip = host-ip-address; src-port range 200 65535 egress: src-ip = 0.0.0.0/0 | ::/0; src-port range 200 65535 |
||
|
ip-prefix/length |
100 |
ingress: src-ip = host-ip-address; src-port eq 100 egress: src-ip = ip-prefix/length; src-port eq 100 |
|
|
200 to 65535 |
ingress: src-ip = host-ip-address; src-port range 200 65535 egress: src-ip = ip-prefix/length; src-port range 200 65535 |
||
|
to destination |
any |
100 |
ingress: dst-ip = 0.0.0.0/0 | ::/0; dst-port eq 100 egress: dst-ip = host-ip-address; dst-port eq 100 |
|
200 to 65535 |
ingress: dst-ip = 0.0.0.0/0 | ::/0; dst-port range 200 65535 egress: dst-ip = host-ip-address; dst-port range 200 65535 |
||
|
ip-prefix/length |
100 |
ingress: dst-ip = ip-prefix/length; dst-port eq 100 egress: dst-ip = host-ip-address; dst-port eq 100 |
|
|
200 to 65535 |
ingress: dst-ip = ip-prefix/length; dst-port range 200 65535 egress: dst-ip = host-ip-address; dst-port range 200 65535 |
||
|
options: frag |
frag |
fragment true (IPv4 only) |
|
|
options: ipoptions |
ssrr |
ip-option 9 / ip-mask 255 |
|
|
lsrr |
ip-option 3/ ip-mask 255 |
||
|
rr |
ip-option 7/ ip-mask 255 |
||
|
ts |
ip-option 4/ ip-mask 255 |
||
|
!ssrr |
— |
||
|
!lsrr |
— |
||
|
!rr |
— |
||
|
!ts |
— |
||
|
ssrr,lsrr,rr,ts |
— |
||
|
options: tcpoptions |
mss |
— |
|
|
window |
— |
||
|
sack |
— |
||
|
ts |
— |
||
|
!mss |
— |
||
|
!window |
— |
||
|
!sack |
— |
||
|
!ts |
— |
||
|
mss,window,sack,ts |
— |
||
|
options: established |
established |
— |
|
|
— |
|||
|
— |
|||
|
options: setup |
setup |
tcp-syn true |
|
|
tcp-ack false |
|||
|
protocol tcp |
|||
|
options: tcpflags |
syn |
tcp-syn true |
|
|
!syn |
tcp-syn false |
||
|
ack |
tcp-ack true |
||
|
!ack |
tcp-ack false |
||
|
fin |
— |
||
|
rst |
— |
||
|
psh |
— |
||
|
urg |
— |
||
|
options: icmptypesv4 |
echo reply |
protocol 1 / icmp-type 0 |
|
|
destination unreachable |
protocol 1 / icmp-type 3 |
||
|
source quench |
protocol 1 / icmp-type 4 |
||
|
redirect |
protocol 1 / icmp-type 5 |
||
|
echo request |
protocol 1 / icmp-type 8 |
||
|
router advertisement |
protocol 1 / icmp-type 9 |
||
|
router solicitation |
protocol 1 / icmp-type 10 |
||
|
time-to-live exceeded |
protocol 1 / icmp-type 11 |
||
|
IP header bad |
protocol 1 / icmp-type 12 |
||
|
timestamp request |
protocol 1 / icmp-type 13 |
||
|
timestamp reply |
protocol 1 / icmp-type 14 |
||
|
information request |
protocol 1 / icmp-type 15 |
||
|
information reply |
protocol 1 / icmp-type 16 |
||
|
address mask request |
protocol 1 / icmp-type 17 |
||
|
address mask reply |
protocol 1 / icmp-type 18 |
||
|
— |
protocol 1 / icmp-type [0 to 255] |
||
|
3-9 (range) |
— |
||
|
3,5,8,9 (comma separated) |
— |
||
|
options: icmptypesv6 |
destination unreachable |
icmp-type 1 |
|
|
time-to-live exceeded |
icmp-type 3 |
||
|
IP header bad |
icmp-type 4 |
||
|
echo request |
icmp-type 128 |
||
|
echo reply |
icmp-type129 |
||
|
router solicitation |
icmp-type 133 |
||
|
router advertisement |
icmp-type 134 |
||
|
redirect |
icmp-type 137 |
||
[26.529.242] Ascend-Data-Filter and [26.6527.159] Alc-Ascend-Data-Filter-Host-Spec
The format for [26.529.242] Ascend-Data-Filter and [26.6527.159] Alc-Ascend-Data-Filter-Host-Spec is an octet string with fixed length fields. [26.529.242] Ascend-Data-Filter attribute format displays details on the respective fields.
| Field | Length | Value |
|---|---|---|
|
Type |
1 byte |
1 = IPv4 |
|
3 = IPv6 |
||
|
Filter or forward |
1 byte |
0 = drop |
|
1 = accept |
||
|
Indirection |
1 byte |
0 = egress |
|
1 = ingress |
||
|
Spare |
1 byte |
ignored |
|
Source IP address |
IPv4 = 4 bytes |
IP address of the source interface |
|
IPv6 = 16 bytes |
||
|
Destination IP address |
IPv4 = 4 bytes |
IP address of the destination interface |
|
IPv6 = 16 bytes |
||
|
Source IP prefix |
1 byte |
Number of bits in the network portion |
|
Destination IP prefix |
1 byte |
Number of bits in the network portion |
|
Protocol |
1 byte |
Protocol number. Note - Match the inner most header only for IPv6. |
|
Established |
1 byte |
ignored (not implemented) |
|
Source port |
2 bytes |
Port number of the source port |
|
Destination port |
2 bytes |
Port number of the destination port |
|
Source port qualifier |
1 byte |
0 = no compare |
|
1 = less than |
||
|
2 = equal to |
||
|
3 = greater than |
||
|
4 = not equal to (not supported) |
||
|
Destination port qualifier |
1 byte |
0 = no compare |
|
1 = less than |
||
|
2 = equal to |
||
|
3 = greater than |
||
|
4 = not equal to (not supported) |
||
|
Reserved |
2 bytes |
ignored |
[245.26.6527.7] Alc-Subscriber-Filter-Name Attribute Details
SR OS debug:
VSA [245.26] 74(not frag) Nokia(6527)
SUBSCRIBER FILTER NAMES [7] 74 (tlv)
INGR IPV4 FILTER NAME [1] 17 v4-ingress-filter
EGR IPV4 FILTER NAME [2] 16 v4-egress-filter
INGR IPV6 FILTER NAME [3] 17 v6-ingress-filter
EGR IPV6 FILTER NAME [4] 16 v6-egress-filterSR OS debug:
VSA [245.26] 19(not frag) Nokia(6527)
SUBSCRIBER FILTER NAMES [7] 19 (tlv)
INGR IPV4 FILTER NAME [1] 17 v4-ingress-filter
VSA [245.26] 18(not frag) Nokia(6527)
SUBSCRIBER FILTER NAMES [7] 18 (tlv)
EGR IPV4 FILTER NAME [2] 16 v4-egress-filter
VSA [245.26] 19(not frag) Nokia(6527)
SUBSCRIBER FILTER NAMES [7] 19 (tlv)
INGR IPV6 FILTER NAME [3] 17 v6-ingress-filter
VSA [245.26] 18(not frag) Nokia(6527)
SUBSCRIBER FILTER NAMES [7] 18 (tlv)
EGR IPV6 FILTER NAME [4] 16 v6-egress-filterThe filter name attributes can have the following special values:
- _tmnx_default – install the filter defined in the SLA profile
- _tmnx_delete – do not install any filter; ignore the filter defined in the SLA profile; only allowed when no specific rules for the dynamic subscriber host are present
A filter override specified as a filter name and installed with the Alc-Subscriber-Filter-Name VSA in RADIUS takes precedence over a filter override specified as a filter ID using the Alc-Subscriber-Filter VSA in RADIUS or using the Charging-Rule-Name AVP in Diameter Gx. For example, a CoA with Alc-Subscriber-Filter cannot override a filter that was previously installed as an override specified as a filter name with Alc-Subscriber-Filter-Name. When both filter name and ID are specified in a CoA, the filter name takes precedence.
| Attribute ID | Attribute Name | Description |
|---|---|---|
| 245.26.6527.7 | Alc-Subscriber-Filter-Name |
This attribute has no meaning on its own. It’s a TLV container attribute that enables the sending of multiple filter overrides for a subscriber host or session grouped in a single VSA. Description common for all IPv4 and IPv6 filter override sub-attributes: Non-relevant filter name sub-attributes are ignored (host model) or stored in the session state. For example, Alc-Sub-Ipv4-Ingress-Filter-Name for an IPv6 host. The scope of the local preconfigured filter should be set to template for correct operation (configure filter ip-filter/ipv6-filter filter-id scope template). This is not enforced. For a RADIUS CoA, if the ingress or egress filter name sub-attribute is missing in the CoA, there is no change for that direction. For a RADIUS Access-Accept, if an ingress or egress filter name sub-attribute is missing in the Access-Accept, the IP filter specified in the SLA profile is installed for that direction. Filter overrides are applicable to all dynamic host types, including L2TP LNS but excluding L2TP LAC. |
| 245.26.6527.7.1 | Alc-Sub-Ipv4-Ingress-Filter-Name | Subscriber host preconfigured IP ingress filter to be used instead of the filter defined in the SLA profile. |
| 245.26.6527.7.2 | Alc-Sub-Ipv4-Egress-Filter-Name | Subscriber host preconfigured IP egress filter to be used instead of the filter defined in the SLA profile. |
| 245.26.6527.7.3 | Alc-Sub-Ipv6-Ingress-Filter-Name | Subscriber host preconfigured IPv6 ingress filter to be used instead of the filter defined in the SLA profile. |
| 245.26.6527.7.4 | Alc-Sub-Ipv6-Egress-Filter-Name | Subscriber host preconfigured IPv6 egress filter to be used instead of the filter defined in the SLA profile. |
| 245.26.6527.7.5 | Alc-Sub-Ipv4-Onetime-Http-Redirect-Filter-Name | The preconfigured IPv4 filter with HTTP redirection rules to be used instead of the one-time-http-redirection filter defined in the SLA profile. This host-specific filter is only used to redirect the first HTTP request from the host. There is no HTTP redirection for subsequent HTTP requests which is useful in cases where service providers need to push a web page of advertisement or announcements to broadband users. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
| 245.26.6527.7 | Alc-Subscriber-Filter-Name | tlv | 5 sub-attributes | container attribute for encapsulating filter name sub-attributes |
| 245.26.6527.7.1 | Alc-Sub-Ipv4-Ingress-Filter-Name | string | Max 64 chars | IP filter name, or _tmnx_default: install SLA profile filter _tmnx_delete: install no filter |
| 245.26.6527.7.2 | Alc-Sub-Ipv4-Egress-Filter-Name | string | Max 64 chars | IP filter name, or _tmnx_default: install SLA profile filter _tmnx_delete: install no filter |
| 245.26.6527.7.3 | Alc-Sub-Ipv6-Ingress-Filter-Name | string | Max 64 chars | IP filter name, or _tmnx_default: install SLA profile filter _tmnx_delete: install no filter |
| 245.26.6527.7.4 | Alc-Sub-Ipv6-Egress-Filter-Name | string | Max 64 chars | IP filter name, or _tmnx_default: install SLA profile filter _tmnx_delete: install no filter |
| 245.26.6527.7.5 | Alc-Sub-Ipv4-Onetime-Http-Redirect-Filter-Name | string | Max 64 chars | IP filter name, or _tmnx_default: install SLA profile filter _tmnx_delete: install no filter |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
| 245.26.6527.7 | Alc-Subscriber-Filter-Name | 0 | 0+ | 0+ |
| 245.26.6527.7.1 | Alc-Sub-Ipv4-Ingress-Filter-Name | 0 | 0-1 | 0-1 |
| 245.26.6527.7.2 | Alc-Sub-Ipv4-Egress-Filter-Name | 0 | 0-1 | 0-1 |
| 245.26.6527.7.3 | Alc-Sub-Ipv6-Ingress-Filter-Name | 0 | 0-1 | 0-1 |
| 245.26.6527.7.4 | Alc-Sub-Ipv6-Egress-Filter-Name | 0 | 0-1 | 0-1 |
| 245.26.6527.7.5 | Alc-Sub-Ipv4-Onetime-Http-Redirect-Filter-Name | 0 | 0-1 | 0-1 |
Subscriber host creation
| Attribute ID | Attribute name | Description |
|---|---|---|
|
8 |
Framed-IP-Address |
The IPv4 address to be configured for the host using DHCPv4 (radius proxy), IPCP (PPPoE) or data-triggered subscriber management. Simultaneous returned attributes [88] Framed-Pool and [8] Framed-IP-Address (RADIUS Access-Accept) are handled as host setup failures. This attribute is also used in CoA and Disconnect Message (part of the ESM or AA user identification-key). This attribute is omitted in accounting using configure subscriber-mgmt radius-accounting-policy name include-radius-attribute no framed-ip-addr. |
|
87 |
NAS-Port-Id |
A text string which identifies the physical port of the NAS (SAP ID) where the host is created. |
|
26.6527.15 |
Alc-Create-Host |
Used to create an IPv4 host using CoA. Additional mandatory attributes to create such a host are [8] Framed-IP-Address, [87] NAS-Port-Id and [26.6527.27] Alc-Client-Hardware-Addr |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
MAC address from a user that requests a service and included in CoA, Authentication or Accounting (configure subscriber-mgmt authentication-policy/radius-accounting-policy name include-radius-attribute mac-address) |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
8 |
Framed-IP-Address |
ipaddr |
4 bytes |
For example: # ip-address 10.11.12.13 Framed-IP-Address 0a0b0c0d |
|
87 |
NAS-Port-Id |
string |
253 bytes |
<slot> / <mda> / <port> [ : <qtag1> [. <qtag2>] ] For example: NAS-Port-Id = 1/1/4:501.1001 |
|
26.6527.15 |
Alc-Create-Host |
string |
no limits |
The attribute value is ignored For example: Alc-Create-Host = anything Alc-Create-Host = 1 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
string |
6 bytes |
For example: Alc-Client-Hardware-Addr = 00:00:00:00:00:01 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
8 |
Framed-IP-Address |
0 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
0-1 |
0 |
0-1 |
|
26.6527.15 |
Alc-Create-Host |
0 |
0 |
0-1 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
0-1 |
0-1 |
0 |
Subscriber services
| Attribute ID | Attribute name | Description |
|---|---|---|
|
26.6527.151 |
Alc-Sub-Serv-Activate |
Activate a subscriber service. The attribute typically contains parameters as input for the Python script that populates the subscriber service data structure (sub_svc). The attribute is ignored if not used in Python. The parameters can cross an attribute boundary. The concatenation of all Alc-Sub-Serv-Activate attributes with the same tag in a single message is typically used as a unique subscriber service instance identifier (key). In subscriber service RADIUS accounting messages, the attribute is sent untagged and contains the subscriber service data structure sub_svc.name value used at service activation. Multiple attributes may be present if the total length does not fit a single attribute. |
|
26.6527.152 |
Alc-Sub-Serv-Deactivate |
Deactivate a subscriber service. The attribute typically contains parameters as input for the Python script that populates the subscriber service data structure (sub_svc). The attribute is ignored if not used in Python. The parameters can cross an attribute boundary. The concatenation of all Alc-Sub-Serv-Deactivate attributes with the same tag in a single message is typically used as the unique subscriber service instance identifier (key). |
|
26.6527.153 |
Alc-Sub-Serv-Acct-Stats-Type |
Enable or disable subscriber service accounting and specify the stats type: volume and time or time only. The attribute is used as input for the Python script that populates the subscriber service data structure (sub_svc.acct_stats_type). The attribute is ignored if not used in Python. The subscriber service accounting statistics type cannot be changed for an active subscriber service. |
|
26.6527.154 |
Alc-Sub-Serv-Acct-Interim-Ivl |
The interim accounting interval in seconds at which Acct-Interim-Update messages should be generated for subscriber service accounting. The attribute is used as input for the Python script that populates the subscriber service data structure (sub_svc.acct_interval). The attribute is ignored if not used in Python. sub_svc.acct_interval overrides the local configured update-interval value in the subscriber profile policy. With value = 0, the interim accounting is switched off. The subscriber service accounting interim interval cannot be changed for an active subscriber service. |
|
26.6527.155 |
Alc-Sub-Serv-Internal |
For internal use only. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
26.6527.151 |
Alc-Sub-Serv-Activate |
string |
multiple VSAs per tag per message |
For example: Alc-Sub-Serv-Activate:1 = rate-limit;1000;8000 |
|
26.6527.152 |
Alc-Sub-Serv-Deactivate |
string |
multiple VSAs per tag per message |
For example: Alc-Sub-Serv-Deactivate:1 = rate-limit;1000;8000 |
|
26.6527.153 |
Alc-Sub-Serv-Acct-Stats-Type |
integer |
1 VSA per tag per message |
1=off, 2=volume-time, 3=time For example: Alc-Sub-Serv-Acct-Stats-Type:1 = 2 |
|
26.6527.154 |
Alc-Sub-Serv-Acct-Interim-Ivl |
integer |
1 VSA per tag per message [300 to 15552000] |
A value of 0 (zero) corresponds with no interim update messages. A value [1 to 299] seconds is rounded to 300s (min. CLI value) and a value > 15552000 seconds (max. CLI value) is rounded to the max. CLI value. [300 to 15552000] = override local configured update-interval for this subscriber service For example: Alc-Sub-Serv-Acct-Interim-Ivl:1 = 3600 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Tag | Max. tag |
|---|---|---|---|---|---|---|
|
26.6527.151 |
Alc-Sub-Serv-Activate |
0 |
0+ |
0+ |
Y |
0-31 (untagged) |
|
26.6527.152 |
Alc-Sub-Serv-Deactivate |
0 |
0+ |
0+ |
Y |
0-31 |
|
26.6527.153 |
Alc-Sub-Serv-Acct-Stats-Type |
0 |
0+ |
0+ |
Y |
0-31 |
|
26.6527.154 |
Alc-Sub-Serv-Acct-Interim-Ivl |
0 |
0+ |
0+ |
Y |
0-31 |
GTP uplink
In this section, GTP uplink application specific attributes are detailed. These attributes are applicable to WLAN Gateway as well as ESM scenarios such as Hybrid Access.
| Attribute ID | Attribute name | Description |
|---|---|---|
|
26.6527.145 |
Alc-MGW-Interface-Type |
This contains the interface type that is used to determine the type of GTP-C connection, overrides local configuration. |
|
26.6527.146 |
Alc-Wlan-APN-Name |
Specifies the Access Point Name (APN) for which a GTP-C session is set up. This is signaled in the GTP-C setup and may be used to determine the IP address of the GGSN/P-GW by performing a DNS query if the [26.10415.5] 3GPP-GGSN-Address attribute is not present. This overrides a locally configured APN. |
|
26.6527.147 |
Alc-Mslsdn |
Contains the MSISDN (telephone number) of the UE, and is included in GTP-C signaling. When not present the corresponding GTP-C Information Element is not sent. |
|
26.6527.179 |
Alc-GTP-Local-Breakout |
Specifies if part of the UE traffic can be locally broken out (such as, NATed and routed), subject to matching an IPv4 filter entry with action gtp-local-breakout, associated with the UE. |
|
26.6527.205 |
Alc-GTP-Default-Bearer-Id |
When establishing a GTP connection for a UE, this specifies the bearer ID (GTPv2) or NSAPI (GTPv1) that is used for the data path connection. If not provided, a default value of 5 is used. |
|
26.6527.219 |
Alc-Egress-Report-Rate-Subtract |
This value is subtracted from the base downlink AMBR value calculated using the report-rate mechanism. This attribute is only interpreted if report-rate is enabled in the applicable SLA profile: configure subscriber-mgmt sla-profile sla-profile-name egress report-rate. |
|
26.10415.1 |
3GPP-IMSI |
This is used to identify the host in a GTP-C connection. If not present and a gtp-c connection is requested, the subscriber-id or username in the EAP-SIM message is parsed as an IMSI. This should be provided for any GTP-C user. |
|
26.10415.3 |
3GPP-PDP-Type |
Specifies which address type should be requested from the P- GW: ipv4, ipv6 or ipv4v6. If this attribute is not present, the value under configure router | service vprn service-id gtp uplink pdn-type is used. |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS-Profile |
Used to signal the QOS for default bearer or primary PDP context using GTP "QOS IE" in create-PDP-context and "Bearer QOS" in create-session-request. |
|
26.10415.7 |
3GPP-GGSN-Address |
For 3G, it represents the GGSN IPv4 address that is used by the GTP control plane for the context establishment on the Gn interface. For 4G, it represents the P-GW IPv4 address that is used on the S2a or S2b interface for the GTP session establishment. If not present, the WLAN-GW sends a DNS query based on the APN name derived from [26.6527.146] Alc-Wlan-APN-Name or local configuration. |
|
26.10415.13 |
3GPP-Charging-Characteristics |
Used to signal charging-characteristic IE content. |
|
26.10415.20 |
3GPP-IMEISV |
International Mobile Equipment ID and its Software Version, this is echoed in the GTP-C setup messages. |
|
26.10415.21 |
3GPP-RAT-Type |
Specifies the value that is signaled in the RAT Type IE during GTPv1/GTPv2 setup. If this attribute is not present, the value under configure subscriber-mgmt gtp peer-profile profilename rat-type type is used. |
|
26.10415.22 |
3GPP-User-Location-Info |
This attribute specifies the location information for a specific UE that is echoed in the ULI IE in GTP-C setup messages. The format and radius-to-GTP mapping is specified in 3GPP specification 29.061. If not present, no user location is reflected in GTP. RADIUS servers can use the information from for example, attributes [30] Called-Station-Id, [26.6527.206] Alc-Wlan-SSID-VLAN or [87] NAS-Port-Id to create a corresponding ULI value. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
26.6527.145 |
Alc-MGW-interface-Type |
integer |
values [1 to 3] |
Gn(GTPv1)=1; S2a(GTPv2)=2; S2b(GTPv2)=3 default = s2a For example: Alc-MGW-Interface-Type = 1 |
|
26.6527.146 |
Alc-Wlan-APN-Name |
string |
100 chars if both <NI> and <OI> parts are present. 63 chars if only the <NI> part is present. |
The APN Name attribute must be formatted as <NI>[.mnc<MNC>.mcc<MCC>.gprs]. The Operator-ID (OI) part is optional and is automatically derived from the IMSI if it is not present. The APN FQDN generated for DNS resolution is composed of the Network-ID (<NI>) portion and the Operator-ID (OI) portion (<MCC> and <MNC>) as per 3GPP TS 29.303 and is reformatted as <NI>.apn.epc.mnc<MNC>.mcc<MCC>.3gppnetwork.org For example: Alc-Wlan-APN-Name = wlangw.mnc004.mcc204.gprs |
|
26.6527.147 |
Alc-MsIsdn |
string |
9 to 15 digits |
For example: Alc-MsIsdn = 13109976224 |
|
26.6527.179 |
Alc-GTP-Local-Breakout |
integer |
values [0 to 1] |
values: not-allowed = 0, allowed = 1 For example: Alc-GTP-Local-Breakout = allowed |
|
26.6527.205 |
Alc-GTP-Default-Bearer-Id |
integer |
[5 to 15] |
If outside of the specified range, 5 is used. |
|
26.6527.219 |
Alc-Egress-Report-Rate-Subtract |
integer |
[0 to 2147483647] kb/s |
Example (subtract 500 kb/s): Alc-Egress-Report-Rate-Subtract=500 |
|
26.10415.1 |
3GPP-PDP-Type |
string |
1 to 15 digits |
3GPP vendor specific attribute as defined in 3GPP TS 29.061. For example: 3GPP-IMSI = 204047910000598 |
|
26.10415.3 |
3GPP-PDP-Type |
integer |
[0,2,3] |
0=ipv4, 2 =ipv6, 3 = ipv4v6 For example (Request a dual stack session) 3GPP-PDP-Type=3 |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS- Profile |
string |
length as defined in the 3GPP TS 29.061 |
Specified in TS 29.061 version 8.5.0 Release 8 section 16.4.7.2 For example: 3GPP-GPRS-Negotiated-QoS-Profile = 08-4D020000002710000000138800000001f40000000bb8 |
|
26.10415.7 |
3GPP-GGSN-Address |
ipaddr |
4 bytes |
3GPP vendor specific attribute as defined in TS 29.061. For example: 3GPP-GGSN-Address = 10.43.129.23 |
|
26.10415.13 |
3GPP-Charging-Characteristics |
string |
4 chars |
Specified in TS 29.061 version 8.5.0 Release 8 section 16.4.7.2 For example: 3GPP-Charging-Characteristics = 1A2B |
|
26.10415.20 |
3GPP-IMEISV |
string |
14 to 16 digits |
3GPP vendor specific attribute as defined in TS 29.061. |
|
26.10415.21 |
3GPP-RAT-Type |
octets |
1 octet, [0..255] |
Specifies the Radio Access Technology type, see 3GPP 29.061 section 16.4.7.2. for more details. For example (E-UTRAN RAT Type): 3GPP-RAT-Type = 0x06 |
|
26.10415.22 |
3GPP-User-Location-Info |
octets |
247 bytes |
Specified in TS 29.061 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Acct. messages |
|---|---|---|---|---|---|
|
26.6527.145 |
Alc-MGW-Interface-Type |
0 |
0-1 |
0 |
0 |
|
26.6527.146 |
Alc-Wlan-APN-Name |
0 |
0-1 |
0 |
0 |
|
26.6527.147 |
Alc-Mslsdn |
0 |
0-1 |
0 |
0 |
|
26.6527.179 |
Alc-GTP-Local-Breakout |
0 |
0-1 |
0 |
0-1 |
|
26.6527.205 |
Alc-GTP-Default-Bearer-Id |
0 |
0-1 |
0 |
0 |
|
26.6527.219 |
Alc-Egress-Report-Rate-Subtract |
0 |
0-1 |
0 |
0 |
|
26.10415.1 |
3GPP-IMSI |
0 |
0-1 |
0 |
0 |
|
26.10415.3 |
3GPP-PDP-Type |
0 |
0-1 |
0 |
0 |
|
26.10415.5 |
3GPP-GPRS-Negotiated-QoS-Profile |
0 |
0-1 |
0 |
0 |
|
26.10415.7 |
3GPP-GGSN-Address |
0 |
0-1 |
0 |
0 |
|
26.10415.13 |
3GPP-Charging-Characteristics |
0 |
0-1 |
0 |
0 |
|
26.10415.20 |
3GPP-IMEISV |
0 |
0-1 |
0 |
0 |
|
26.10415.21 |
3GPP-RAT-Type |
0 |
0-1 |
0 |
0 |
|
26.10415.22 |
3GPP-User-Location-Info |
0 |
0-1 |
0 |
0 |
WLAN gateway
In this section, WLAN gateway application specific attributes are detailed, including generic Enhanced Subscriber Management (ESM) attributes that have different semantics when used in WLAN gateway scenarios. Relevant attributes for GTP uplink are documented in a separate GTP uplink section.
| Attribute ID | Attribute name | Description |
|---|---|---|
|
4 |
NAS-IP-Address |
The identifying IP Address of the NAS requesting Authentication or Accounting. Authentication generated from ISA (for a UE in migrant state) can be configured to use the local IP address of the RADIUS client on ISA or the system IP address on CPM: configure aaa isa-radius-policy name nas-ip-address-origin {isa-ip | system-ip} When an ESM host exists for the UE (UE is in authenticated state), then the NAS IP in authentication and accounting is the system IP address. Inclusion of this attribute is configurable: configure aaa isa-radius-policy name auth-include-attributes nas-ip-address |
|
30 |
Called-Station-Id |
If configured for inclusion in authentication and accounting policy (configure aaa isa-radius-policy name auth-include-attributes/acct-include-attributes called-station-id), the called-station-id received from EAP authentication request is transparently forwarded in access-request. If it is contained in the accounting messages received from the APs, it is transparently forwarded in the accounting messages sent from the WLAN-GW. Typically the string contains ‟AP MAC : SSID-name”. |
|
31 |
Calling-Station-Id |
Calling-station-id contains the MAC address of the UE, if it is configured for inclusion in isa-radius-policy (configure aaa isa-radius-policy name auth-include-attributes calling-station-id) for authentication generated from the ISA (for a UE in migrant state), or in authentication and accounting policy for messages generated from the CPM. For CPM generated authentication or accounting, the inclusion of calling-station-id must explicitly specify the format of the calling-station-id as MAC: configure subscriber-mgmt authentication-policy | radius-accounting-policy name include-radius-attribute calling-station-id mac. |
|
87 |
NAS-Port-Id |
A text string with format defined by the aggregation type: GRE, L2TPv3 or VLAN. See [87] NAS-Port-Id attribute details for a detailed description of the attribute format. |
| 95 | NAS-IPv6-Address | The identifying IPv6 address of the NAS requesting Authentication
or Accounting. Authentication generated from ISA can be configured
to use the local IP address of the RADIUS client on ISA or the
system IP address on CPM: configure aaa isa-radius-policy name nas-ip-address-origin {isa-ip | system-ip} Inclusion of this attribute is configurable:configure aaa isa-radius-policy name auth-include-attributes nas-ipv6-address |
|
26.3561.1 |
Agent-Circuit-Id |
Agent-circuit-id is transparently taken from the circuit-id in DHCP option-82. Most WIFI access-points insert information describing the AP and SSID that the UE is associated with. Recommended format is an ASCII string containing APs MAC@, SSID name and SSID type (open or secure), with a delimiter between each, as shown in example: ‟00:00:00:00:00:01;xfinity-wifi;o” |
|
26.6527.148 |
Alc-RSSI |
Received Signal Strength Indication. Used in conjunction with the radius-proxy track-accounting feature. When the radius-proxy receives this attribute in an accounting message, it is copied into the DHCP lease state and echoed by SR OS accounting. |
|
26.6527.149 |
Alc-Num-Attached-Ues |
Number of attached WIFI UEs. The attribute is forwarded by the RADIUS proxy when received in an Access-Request from the AP. For authentication originated by the WLAN gateway, this attribute contains the total number of UEs that are currently attached to this UE’s tunnel. This can be used to detect if this is the first UE on a tunnel (value 1). For non wlan-gw/vRGW UEs this value is 0. Inclusion can be configured by adding the option wifi-num-attached-ues in configure subscriber-mgmt authentication-policy name include-radius-attribute for ESM, and in configure aaa isa-radius-policy name auth-include-attributes for DSM. |
|
26.6527.172 |
Alc-Wlan-Portal-Redirect |
Used when authenticating migrant hosts. When an access-accept contains this attribute, the host stays in the migrant phase, but has limited forwarding capabilities. All filtered (not allowed) http-traffic is redirected to a specified portal URL. This attribute must contain the name of a redirect policy configured under configure subscriber-mgmt http-redirect-policy policy-name which specifies a set of forwarding filters. To force a redirect with the configured policy and URL, send an empty Alc- Wlan-Portal-Redirect VSA. |
|
26.6527.173 |
Alc-Wlan-Portal-Url |
If a migrant host is redirected, specifies the URL it has to be redirected to, takes precedence over the URL configured in the redirect policy under configure subscriber-mgmt http-redirect-policy policy-name. |
|
26.6527.184 |
Alc-Wlan-Ue-Creation-Type |
When promoting a migrant user, this indicates if the UE should be created on CPM/IOM (as an ESM host) or on ISA (as a DSM host). When this attribute is not present during promote, creation-type CPM/IOM is assumed. The attribute can be included in an Access-Accept message for a UE that is auto-signed-in (it does not need web redirect to portal), or in a CoA message triggered to remove web redirect for a UE after successful portal authentication. If Alc-Wlan-Ue-Creation-Type indicates a DSM UE then any IPv6 or GTP related parameters in an Access-Accept or CoA message is ignored, and the UE is created as a DSM host. Alc-WLAN-UE-Creation-Type cannot be changed mid-session for a UE in DSM or ESM state. |
|
26.6527.186 |
Alc-Wlan-Dsm-Ot-Http-Redirect-Url |
If a one-time redirect is enabled for a distributed subscriber management host, then this attribute specifies the redirect URL. This URL overrides the configured URL under configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range start starting-vlan end ending-vlan distributed-sub-mgmt one-time-redirect. This attribute is mutual exclusive with Alc-Wlan-Dsm-Http-Redirect-Url (241.26.6527.65). If both attributes are signaled simultaneously this attribute is ignored, otherwise this value removes the redirect URL override. |
|
26.6527.187 |
Alc-Wlan-Dsm-Ip-Filter |
Specifies the name of a distributed subscriber management (DSM) ip filter configured under configure subscriber-mgmt isa-filter dsm-ip-filter-name. This filter is applied to the DSM UE. This overrides the value configured under configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range start starting-vlan end ending-vlan distributed-sub-mgmt dsm-ip-filter dsm-ip-filter-name. |
|
26.6527.188 |
Alc-Wlan-Dsm-Ingress-Policer |
Specifies the name of a distributed subscriber management (DSM) ingress policer configured under configure subscriber-mgmt isa-policer policer-name. This policer is applied to the DSM UE. This overrides the value configured under configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range start starting-vlan end ending-vlan distributed-sub-mgmt ingress-policer policer-name. |
|
26.6527.189 |
Alc-Wlan-Dsm-Egress-Policer |
Specifies the name of a distributed subscriber management (DSM) egress policer configured under configure subscriber-mgmt isa-policer policer-name. This policer is applied to the DSM UE. This overrides the value configured under configure service ies/vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range start starting-vlan end ending-vlan distributed-sub-mgmt egress-policer policer-name. |
|
26.6527.190 |
Alc-Wlan-Handover-Ip-Address |
IP address provided in RADIUS Access-Accept message to signal handover from LTE or UMTS to WIFI. If this VSA is present, handover indication is set in GTP session creation request to PGW/GGSN. |
|
26.6527.206 |
Alc-Wlan-SSID-VLAN |
The VLAN is transparently taken from the UEs Ethernet layer and can be reflected in both authentication and accounting. This is typically added by the Access Point and uniquely identifies an SSID. This is useful when the SSID is not available in the [30] Called-Station-Id (for example, datatrigger scenarios). When this attribute is configured for inclusion but no VLAN is present in the UE payload, the attribute is not reflected in RADIUS. When this attribute is sent in an Access-Accept message for a RADIUS proxy, the VLAN is used to perform SSID validation. If there is already an active UE and there is a mismatch between both VLANs, the UE is removed. If there is no UE present yet, the VLAN is stored and any subsequent data-plane packets (such as, DHCP Discover) is dropped unless the stored VLAN is matched. |
|
26.6527.216 |
Alc-Datatrig-Lease-Time |
Defines the initial lease-time used for data-triggered DHCP relay hosts. If this attribute is not provided or equal to zero, the used lease-time is 7 days. This lease time is overridden upon the first renew after data-triggered host-creation. |
|
26.6527.218 |
Alc-Wlan-Handover-Ipv6-Address |
Specifies the current IPv6 address of the UE in a 3GPP-to-WLAN handover scenario. In GTPv2 this sets the HI bit and signals the IP in the PDN Address Allocation IE. In GTPv1 this is not supported. |
|
26.6527.233 |
Alc-Tunnel-QoS-Override |
Used to override WLAN gateway tunnel HQoS parameters (aggregate rate and scheduler PIR/CIR), and enables per-tunnel customization. This attribute is included in a per-UE RADIUS message, and the value is applied to the tunnel with which the tunnel is currently associated. To remove an override, an empty value should be signaled. When removing an override, the tunnel QoS reverts to the configured values. It is not possible to revert to a previously applied override. It is also not possible to enable QoS using overrides. Tunnel QoS must be enabled on the WLAN gateway for overrides to function. |
|
241.26.6527.6 |
Alc-Xconnect-Tunnel-Service |
Specifies the service in which the control and data traffic for a x-connect UE is tunneled between visited WLAN-GW and home WLAN-GW. X-connect UE is a roaming UE that requires to be anchored on its home WLAN-GW. |
|
241.26.6527.7 |
Alc-Xconnect-Tunnel-Remote-Ipv6 |
Specifies the IPv6 destination endpoint of the tunnel between visited WLAN-GW and home WLAN-GW for a x-connect UE. |
|
241.26.6527.8 |
Alc-Xconnect-Tunnel-Type |
Specifies the type of tunnel between visited WLAN-GW and home WLAN-GW for a x-connect UE. Supported tunnel types are L2oGRE and L2TPv3 with IPv6 transport. |
|
241.26.6527.49 |
Alc-Xconnect-Tunnel-Local-Ipv6 |
Specifies the IPv6 source used for the tunnel between visited WLAN-GW and home WLAN-GW for a x-connect UE. |
|
241.26.6527.55 |
Alc-Bcast-LL-Mcast-Replication |
Specifies whether traffic destined for any IPv4 subnet-broadcast, IPv4 network-broadcast address, IPv4/IPv6 link-local multicast address, or IPv6 solicited-node multicast address can be received from an ESM host and replicated to other ESM hosts according to the scope of these addresses. This attribute only applies to ESM hosts over soft-GRE tunnels. It applies to both sending and receiving hosts. |
|
241.26.6527.59 |
Alc-Xconnect-Tunnel-Home-Ipv6 |
Specifies the x-connect IPv6 gateway address configured on the home WLAN-GW (H-GW). When the host moves to the visited WLAN-GW (V-GW) the RADIUS server can return the IPv6 address in authentication using the [241.26.6527.7] Alc-Xconnect-Tunnel-Remote-Ipv6 attribute. The V-GW can then setup a x-connect tunnel to this H-GW IPv6 address. Inclusion can be configured by adding the option xconnect-tunnel-home-address in configure subscriber-mgmt authentication-policy name include-radius-attribute for ESM, and in configure aaa isa-radius-policy name auth-include-attributes for DSM. |
|
241.26.6527.65 |
Alc-Wlan-Dsm-Http-Redirect-Url |
Overrides the HTTP redirect URL of an ISA filter action configured under configure subscriber-mgmt isa-filter name entry id action or configure subscriber-mgmt isa-filter name ipv6 entry id action. This attribute is mutually exclusive with Alc-Wlan-Dsm-Ot-Http-Redirect-Url (26.6527.186). If signaled simultaneously, the one-time redirect is ignored, otherwise this value removes the one-time redirect override. |
|
241.26.6527.94 |
Alc-L2-Service-Name |
Specifies the VPLS service name that the UE traffic is forwarded to. The attribute is ignored when the dynamic-service command is not configured in either the IES or VPRN service subscriber-interface group-interface wlan-gw vlan-tag-ranges range context. Additionally, the following command must be configured for the VPLS service: configure service vpls service-id wlan-gw wlan-gw-group If the preceding command is not configured, the promotion of the UE fails. The UE remains in a DCHP/data-triggered or authorized-only state, until it is cleared. |
|
241.26.6527.95 |
Alc-Wlan-Custom-User-Group |
A custom user group name which can be used to selectively query UEs or tunnels for operational state retrieval. |
|
26.25053.2 |
Ruckus-Sta-RSSI |
Received Signal Strength Indication. Used in conjunction with the radius-proxy track-accounting feature. When the radius-proxy receives this attribute in an accounting message, it is copied into the DHCP lease state and echoed by the SR OS accounting. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
4 |
NAS-IP-Address |
ipaddr |
4 bytes |
For example: NAS-IP-Address = 10.1.1.2 |
|
30 |
Called-Station-Id |
string |
64 chars |
For example: Called-Station-Id = ‟0a-0b-0c-00-00-01 : AirportWifi” |
|
31 |
Calling-Station-Id |
string |
64 chars |
For example: Calling-station-id = 00:00:00:00:00:01 |
|
87 |
NAS-Port-Id |
string |
253 chars |
See [87] NAS-Port-Id attribute details for a detailed description of the attribute format. L2TP | GRE: ‟<tunnel-type> rtr-<virtual router id>#lip-<local ip address>#rip-<remote ip address>” VLAN: ‟VLAN svc-<svc-id>[:<vlan>[.<vlan>]]” For example: NAS-Port-Id = ‟GRE rtr-11#lip-192.0.2.1#rip-172.16.1.1” |
| 95 | NAS-IPv6-Address | ipv6addr | 16 bytes | For example: NAS-IPv6-Address = 2001:db8::1 |
|
26.3561.1 |
Agent-Circuit-Id |
string |
247 chars |
String containing information about the AP and the SSID that the UE is associated with. Recommended format is <AP-MAC>;<SSID-Name>;<SSID-Type>. SSID-Type can be open (‛o’), or secure (‛s’) For example: Agent-Circuit-Id = ‟00:00:00:00:00:01;xfinity-wifi;o” |
|
26.6527.148 |
Alc-RSSI |
integer |
32 bit value |
For example: Alc-RSSI = 30 |
|
26.6527.149 |
Alc-Num-Attached-Ues |
integer |
32 bit value |
For example: Alc-Num-Attached-Ues = 3 |
|
26.6527.172 |
Alc-Wlan-Portal-Redirect |
string |
32 chars |
For example: Alc-Wlan-Portal-Redirect = Redirect-policy-1 |
|
26.6527.173 |
Alc-Wlan-Portal-Url |
string |
247 chars |
For example: Alc-Wlan-Portal-Url = http:// welcome.portal.com |
|
26.6527.184 |
Alc-Wlan-Ue-Creation-Type |
integer |
values [0 to 1] |
values: iom = 0, isa = 1 Any other value is invalid and the corresponding RADIUS message is dropped. For example: Alc-Wlan-Ue-Creation-Type = iom |
|
26.6527.186 |
Alc-Wlan-Dsm-Ot-Http-Redirect-Url |
string |
247 chars |
For example: Alc-Wlan-Dsm-Ot-Http-Redirect-Url = ‟http://www.mydomain.com/advertisement?mac=$MAC” |
|
26.6527.187 |
Alc-Wlan-Dsm-Ip-Filter |
string |
32 chars |
If the filter cannot be found, the RADIUS Access-Accept message is dropped or the CoA NAK’d. For example: Alc-Wlan-Dsm-Ip-Filter = drop_non_http |
|
26.6527.188 |
Alc-Wlan-Dsm-Ingress-Policer |
string |
32 chars |
If the policer cannot be found, the RADIUS Access-Accept message is dropped or the CoA NAK’d. For example: Alc-Wlan-Dsm-Ingress-Policer = 1 Mb/s |
|
26.6527.189 |
Alc-Wlan-Dsm-Egress-Policer |
string |
32 chars |
If the policer cannot be found, the RADIUS Access-Accept message is dropped or the CoA NAK’d. For example: Alc-Wlan-Dsm-Egress-Policer = 10 Mb/s-limit |
|
26.6527.190 |
Alc-Wlan-Handover-Ip-Address |
ipaddr |
4 bytes |
For example: Alc-Wlan-Handover-Ip-Address = 10.1.1.1 |
|
26.6527.206 |
Alc-Wlan-SSID-VLAN |
string |
247 chars |
Textual representation of the vlan. If no vlan-tag was present, this attribute is not included. For example: Alc-Wlan-SSID-VLAN = ‟2173” |
|
26.6527.216 |
Alc-Datatrig-Lease-Time |
integer |
[0 to 2147483647] seconds |
0: fallback to the default lease-time of 7 days. [1 to 2147483647] lease-time in seconds For example: Alc- Datatrig-Lease-Time = 3600 |
|
26.6527.218 |
Alc-Wlan-Handover-Ipv6-Address |
ipv6addr |
16 bytes |
# IPv6 address For example: Alc-Wlan-Handover-Ipv6-Address = 2001:db8::1 |
|
26.6527.233 |
Alc-Tunnel-QoS-Override |
string |
Up to 4 attributes |
<direction>:<QoS object>:[<id or name>:][<parameter>=value,...] <direction> = e or E for egress <QoS object> = r or R for egress aggregate-rate overrides <QoS object> = s or S for scheduler overrides <id or name> = identifies the QoS object, for example scheduler-name <parameter>=value,... = a comma-separated list of parameters to override with the corresponding value. All rates and CIRs are in kb/s. [eE]:[rR]:(rate) [eE]:[sS]:<scheduler-name>:(rate|cir) For example: aggregate rate override to 8 Mb/s Alc-Tunnel-QoS-Override += e:r:rate=8000 |
|
241.26.6527.6 |
Alc-Xconnect-Tunnel-Service |
integer |
2147483647 ID |
A valid VPRN or IES service ID For example: Alc-Xconnect-Tunnel-Service = 20 |
|
241.26.6527.7 |
Alc-Xconnect-Tunnel-Remote-Ipv6 |
ipv6addr |
16 bytes |
IPv6 address For example: Alc-Xconnect-Tunnel-IPv6 = 2001:db8::1 |
|
241.26.6527.8 |
Alc-Xconnect-Tunnel-Type |
integer |
Values [0,1] |
0 = l2tpv3 1 = gre For example: Alc-Xconnect-Tunnel-Type = 0 |
|
241.26.6527.49 |
Alc-Xconnect-Tunnel-Local-Ipv6 |
ipv6addr |
16 bytes |
IPv6 address For example: Alc-Xconnect-Tunnel-IPv6 = 2001:db8::1 |
|
241.26.6527.55 |
Alc-Bcast-LL-Mcast-Replication |
integer |
Values [1,2] |
1 = enable 2 = disable For example: Alc-Bcast-LL-Mcast-Replication = enable |
|
241.26.6527.59 |
Alc-Xconnect-Tunnel-Home-Ipv6 |
ipv6addr |
16 bytes |
IPv6 address For example: Alc-Xconnect-Tunnel-Home-Ipv6 = 2001:db8::1 |
|
241.26.6527.65 |
Alc-Wlan-Dsm-Http-Redirect-Url |
string |
247 chars |
The URL to return in the HTTP Location Header Field. The following variables are automatically replaced:
For example: Alc-Wlan-Dsm-Http-Redirect-Url = http://recharge.portal.com?mac=$MAC |
|
241.26.6527.94 |
Alc-L2-Service-Name |
string |
247 chars |
For example: Alc-L2-Service-Name = "1000" |
|
241.26.6527.95 |
Alc-Wlan-Custom-User-Group |
string |
32 chars per attribute, up to 4 attributes |
A user group expressed as text. For example: Assign two custom groups "premium" and "east" Alc-Wlan-Custom-User-Group+="premium" Alc-Wlan-Custom-User-Group+="east" |
|
26.25053.2 |
Ruckus-Sta-RSSI |
integer |
32 bit value |
For example: Ruckus-Sta-RSSI = 28 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Acct. messages |
|---|---|---|---|---|---|
|
4 |
NAS-IP-Address |
1 |
0 |
0 |
1 |
|
30 |
Called-Station-Id |
0-1 |
0 |
0-1 |
0-1 |
|
31 |
Calling-Station-Id |
0-1 |
0 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
0-1 |
0 |
0-1 |
0-1 |
| 95 | NAS-IPv6-Address | 1 | 0 | 0 | 1 |
|
26.3561.1 |
Agent-Circuit-Id |
0-1 |
0 |
0 |
0-1 |
|
26.6527.148 |
Alc-RSSI |
0 |
0 |
0 |
0-1 |
|
26.6527.149 |
Alc-Num-Attached-Ues |
0-1 |
0 |
0 |
0-1 |
|
26.6527.172 |
Alc-Wlan-Portal-Redirect |
0 |
0-1 |
0 |
0 |
|
26.6527.173 |
Alc-Wlan-Portal-Url |
0 |
0-1 |
0 |
0 |
|
26.6527.184 |
Alc-Wlan-Ue-Creation-Type |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.186 |
Alc-Wlan-Dsm-Ot-Http-Redirect-Url |
0 |
0-1 |
0-1 |
0 |
|
26.6527.187 |
Alc-Wlan-Dsm-Ip-Filter |
0 |
0-1 |
0-1 |
0 |
|
26.6527.188 |
Alc-Wlan-Dsm-Ingress-Policer |
0 |
0-1 |
0-1 |
0 |
|
26.6527.189 |
Alc-Wlan-Dsm-Egress-Policer |
0 |
0-1 |
0-1 |
0 |
|
26.6527.190 |
Alc-Wlan-Handover-Ip-Address |
0 |
0-1 |
0 |
0 |
|
26.6527.206 |
Alc-Wlan-SSID-VLAN |
0-1 |
0-1 |
0 |
0-1 |
|
26.6527.216 |
Alc-Datatrig-Lease-Time |
0 |
0-1 |
0 |
0 |
|
26.6527.218 |
Alc-Wlan-Handover-Ipv6-Address |
0 |
0-1 |
0 |
0 |
|
26.6527.233 |
Alc-Tunnel-QoS-Override |
0 |
0-1 |
0-1 |
0 |
|
241.26.6527.6 |
Alc-Xconnect-Tunnel-Service |
0 |
0-1 |
0 |
0-1 |
|
241.26.6527.7 |
Alc-Xconnect-Tunnel-Remote-Ipv6 |
0 |
0-1 |
0 |
0-1 |
|
241.26.6527.8 |
Alc-Xconnect-Tunnel-Type |
0 |
0-1 |
0 |
0-1 |
|
241.26.6527.49 |
Alc-Xconnect-Tunnel-Local-Ipv6 |
0 |
0 |
0 |
0-1 |
|
241.26.6527.55 |
Alc-Bcast-LL-Mcast-Replication |
0 |
0-1 |
0 |
0 |
|
241.26.6527.59 |
Alc-Xconnect-Tunnel-Home-Ipv6 |
0-1 |
0 |
0 |
0-1 |
|
241.26.6527.94 |
Alc-L2-Service-Name |
0 |
0-1 |
0 |
0 |
|
241.26.6527.95 |
Alc-Wlan-Custom-User-Group |
0 |
0+ |
0+ |
0 |
|
26.25053.2 |
Ruckus-Sta-RSSI |
0 |
0 |
0 |
0-1 |
WLAN gateway ISA authentication (applicability) lists the applicability of ISA authentication attributes on WLAN-GW. The following messages are distinguished:
-
Access Request
This message is applicable to any Access Request generated by the ISA. Not applicable to proxied requests.
-
Portal Access Accept
This message is applicable to a UE that must perform portal authentication after RADIUS authentication.
-
DSM Access Accept
This message is applicable to a UE that bypasses portal authentication.
-
CoA
This message is applicable to a CoA received in DSM state or a CoA moving a UE from portal to DSM state.
| Attribute ID | Attribute name | Access Request | Portal Access Accept | DSM accept | CoA |
|---|---|---|---|---|---|
|
1 |
User-Name |
1 |
0 |
0 |
0-14 |
|
2 |
User-Password |
1 |
0 |
0 |
0 |
|
4 |
NAS-IP-Address |
0-1 |
0 |
0 |
0 |
|
5 |
NAS-Port |
0-1 |
0 |
0 |
0 |
|
8 |
Framed-IP-Address |
0-1 |
0 |
0 |
0 |
|
25 |
Class |
0 |
0+ |
0+ |
0+ |
|
27 |
Session-Timeout |
0 |
0-1 |
0-1 |
0-1 |
|
28 |
Idle-Timeout |
0 |
0-1 |
0-1 |
0-1 |
|
30 |
Called-Station-Id |
0-1 |
0 |
0 |
0 |
|
31 |
Calling-Station-Id |
0-1 |
0 |
0 |
0 |
|
32 |
NAS-Identifier |
0-1 |
0 |
0 |
0 |
|
44 |
Acct-Session-Id |
0 |
0 |
0 |
0-14 |
|
61 |
NAS-Port-Type |
0-1 |
0 |
0 |
0 |
|
85 |
Acct-Interim-Interval |
0 |
0 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
0-1 |
0 |
0 |
0 |
| 95 | NAS-IPv6-Address | 0-1 | 0 | 0 | 0 |
|
26.3561.1 |
Agent-Circuit-id |
0-1 |
0 |
0 |
0 |
|
26.3561.2 |
Agent-Remote-id |
0-1 |
0 |
0 |
0 |
|
26.6527.9 |
Alc-Primary-Dns |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.10 |
Alc-Secondary-Dns |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.17 |
Alc-Retail-Serv-id |
0 |
0-1 |
0-1 |
0 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
0-1 |
0 |
0 |
0 |
|
26.6527.36 |
Alc-Dhcp-Vendor-Class-id |
0-1 |
0 |
0 |
0 |
|
26.6527.45 |
Alc-App-Prof-Str |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.96 |
Alc-Credit-Control-Quota |
0 |
0 |
0+ |
0+ |
|
26.6527.99 |
Alc-Ipv6-Address |
0-1 |
0 |
0 |
0 |
|
26.6527.102 |
Alc-ToServer-Dhcp-Options |
0+ |
0 |
0 |
0 |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
0 |
0-1 |
0-1 |
0-1 |
|
26.6527.122 |
Alc-LI-Action |
0 |
0 |
0-1 |
0-1 |
|
26.6527.123 |
Alc-LI-Destination |
0 |
0 |
0-1 |
0-1 |
|
26.6527.138 |
Alc-LI-Intercept-Id |
0 |
0 |
0-1 |
0-1 |
|
26.6527.139 |
Alc-LI-Session-id |
0 |
0 |
0-1 |
0-1 |
|
26.6527.172 |
Alc-Wlan-Portal-Redirect |
0 |
1 |
0 |
0 |
|
26.6527.173 |
Alc-Wlan-Portal-Url |
0 |
0-1 |
0 |
0 |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
0 |
0 |
0-1 |
0-1 |
|
26.6527.184 |
Alc-Wlan-Ue-Creation-Type |
0 |
0 |
1 |
0-1 |
|
26.6527.186 |
Alc-Wlan-Dsm-Ot-Http-Redirect-Url |
0 |
0 |
0-1 |
0-1 |
|
26.6527.187 |
Alc-Wlan-Dsm-Ip-Filter |
0 |
0 |
0-1 |
0-1 |
|
26.6527.188 |
Alc-Wlan-Dsm-Ingress-Policer |
0 |
0 |
0-1 |
0-1 |
|
26.6527.189 |
Alc-Wlan-Dsm-Egress-Policer |
0 |
0 |
0-1 |
0-1 |
|
26.6527.191 |
Alc-ToServer-Dhcp6-Options |
0+ |
0 |
0 |
0 |
|
26.6527.193 |
Alc-AA-App-Service-Options |
0 |
0-8 |
0-8 |
0-8 |
|
26.6527.206 |
Alc-Wlan-SSID-VLAN |
0-1 |
0 |
0-15 |
0 |
|
241.26.6527.59 |
Alc-Xconnect-Tunnel-Home-Ipv6 |
0-1 |
0 |
0 |
0 |
|
241.26.6527.65 |
Alc-Wlan-Dsm-Http-Redirect-Url |
0 |
0 |
0-1 |
0-1 |
Virtual residential gateway
This section describes the attributes that are used in virtual residential gateway (vRGW) authentication. This includes both authentication at the home/BRG (Bridged Residential Gateway) level and authentication at the per device/session level. The terminology used is as follows:
-
vRGW refers to the virtual residential gateway functionality in the SR OS.
-
BRG refers to the physical device in the home. In the context of the vRGW it refers to a single residence.
-
HLE refers to Home LAN Extension functionality in SR OS.
vRGW (description) and vRGW (limits) lists the description and limits for vRGW authentication attributes that are specific to vRGW applications only or that are different from the ESM or WLAN-GW authentication scenarios.
vRGW - BRG level authentication – Access Request (applicability) lists the applicability for BRG level authentication Access Request attributes. This table is only applicable when the vRGW performs authentication on behalf of the BRG.
vRGW - BRG and session level authentication (applicability) lists the applicability for BRG level and session level authentication Access-Accept/CoA attributes of sessions in a vRGW context. Access-Accept and CoA attributes that are not listed or explicitly listed as 0 are not supported.
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
In BRG authentication this is fixed to the Bridged Residential Gateway Identifier (BRG-Id) |
|
2 |
User-Password |
In BRG authentication this maps to a pre-configured password: configure subscriber-mgmt vrgw brg brg-profile profile-name radius-authentication password password The attribute is not included when no password is configured. |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
This VSA indicates the value of the service-name attribute that is included in a PADI sent by the PPPoE client. |
|
26.6527.220 |
Alc-Home-Aware-Pool |
This specifies a basic small-scale IP pool that can be used to allocate addresses to multiple hosts of the same subscriber. This IP allocation mechanism has priority over other mechanisms (IP from RADIUS, IP from LUDB, IP from DHCP server). It is not necessary for a pool to be configured on the NAT inside, but if there is one, this overrides those values. This attribute updates following four parameters:
The attribute can also be used to change the pool for an existing subscriber, resulting in:
If the pool is incorrectly formatted, host setup fails or the CoA is not applied and NAK’d. |
|
26.6527.221 |
Alc-DMZ-Address |
In a vRGW context with home-aware pool management this attribute identifies the IP address to be used for DMZ. This attribute does not trigger the creation of a host with this IP, but if the host specified by this IP is installed, DMZ is enabled in NAT. All incoming traffic not matching an existing NAT flow is forwarded to this host with ports unchanged. |
|
26.6527.222 |
Alc-Standby-lps |
After a stateless redundancy event this attribute can be used to inform the home aware pool of addresses that were in use before failure. The pool sets these addresses aside and does not use them for dynamic allocation. Only devices explicitly requiring this IP, for example using data trigger or DHCP renew, get this IP address assigned. After a configurable time (configure subscriber-mgmt vrgw brg brg-profile profile-name dhcp-pool standby-ip-lifetime) all addresses that are still in standby is returned to the pool and made available for dynamic allocation. This VSA only applies when the pool is initially created any further changes are ignored. |
|
26.6527.223 |
Alc-Reserved-Addresses |
For a subscriber with home-aware pool management this attribute lists a set of MAC-IP combinations that are reserved. IP addresses listed here are only allocated to the host with that specific MAC address. There are three types of reserved addresses:
This is mainly used to simplify configuration of always-on devices in home networks. For example a network printer may have a sticky or private static IP, a light webserver may use private static IP + DMZ or a public static IP. A keyword is used to differentiate between sticky and static addresses. This attribute can be repeated multiple times to specify multiple reserved hosts. The list of reserved addresses can be changed using a CoA as follows:
|
|
26.6527.224 |
Alc-BRG-Profile |
Specifies that this Bridged Residential Gateway (BRG) should use the values configured under configure subscriber-mgmt vrgw brg brg-profile profile-name. |
|
26.6527.225 |
Alc-BRG-Id |
In session authentication, reflects the BRG identifier of the associated BRG (if known) in Access-Request. In BRG authentication, reflects the BRG identifier (if known), in the Access Request. Can also be used as key to target a specific BRG with a CoA/Disconnect message. |
|
26.6527.235 |
Alc-BRG-DHCP-Streaming-Dest |
When specified in authentication, DHCPv4 messages (UDP layer) from all sessions for that BRG are mirrored to this destination. If a valid non 0.0.0.0 value is provided for the destination address, then streaming is enabled for the BRG (for example, for all sessions associated with the BRG). Streaming can be disabled at the BRG level by including this VSA with value 0.0.0.0. |
|
26.6527.236 |
Alc-Host-DHCP-Streaming-Disabled |
(Applies to session level authentication of a session associated with a BRG or CoA targeted to a session in a vRGW context.) This attribute controls the DHCPv4 streaming per session. A value of 1 disables DHCPv4 streaming for the session, and value of 0 enables it. |
|
26.6527.238 |
Alc-Remove-Override |
This VSA refers to another VSA that is about to be removed or explicitly disabled. When the referred VSA is removed, SR OS falls back to behavior as if the VSA was never specified. When removed on session level the BRG level is used (if present). When removed on BRG level the default behavior is used. |
|
26.6527.241 |
Alc-Per-Host-Port-Range |
This attribute is used to enable or disable per-host outside port-range allocation for vRGW. When present, this attribute indicates how many ports should be available in each per host range. A value of zero disables per-host port range allocation. This attribute can only be used if a single block per nat outside IP is provisioned using configure router | service vprn service-id nat outside pool nat-pool-name port-reservation blocks 1. |
|
241.26.6527.1 |
Alc-PPPoE-Client-Service |
This VSA indicates in which L2 service PPPoE traffic is forwarded. |
|
241.26.6527.2 |
Alc-PPPoE-Client-MAC |
This VSA indicates the MAC address used by the PPPoE Client. If this VSA is omitted, then the BRG-ID formatted as MAC address is used instead. The PPPoE session setup fails when the VSA is not included and the BRG-ID is not formatted as a MAC address. |
|
241.26.6527.3 |
Alc-PPPoE-Client-Policy |
This VSA indicates that a BRG PPPoE client needs to be started and which pre-configured policy should be used as input parameters. If this attribute is omitted, all other PPPoE-Client related VSAs are ignored. |
|
241.26.6527.4 |
Alc-PPPoE-Client-Username |
This VSA specifies which username must be used in the PAP authentication phase of the PPPoE Client setup. If it is not provisioned, the BRG-ID is used. |
|
241.26.6527.5 |
Alc-PPPoE-Client-Password |
This VSA specifies which password (PAP) or secret (CHAP) must be used in the authentication phase of the PPPoE Client setup. |
|
241.26.6527.9 |
Alc-Bridge-Id |
This VSA enables a Home LAN Extension (HLE) service for the subscriber: the system creates an HLE service and bridge domain using the attribute value as the bridge domain ID. Not specifying a bridge ID when HLE is enabled on the wlangw group interface for session and BRG level authentication results in a session setup failure. |
|
241.26.6527.10 |
Alc-Vxlan-VNI |
This VSA specifies the VXLAN Network Identifier (VNI) to be used for an egress VXLAN packet of the HLE service. When the VSA is not included, then the system automatically assigns a VNI. |
|
241.26.6527.14 |
Alc-RT |
This VSA specifies the Route Target of the HLE BGP EVPN service. When the VSA is not included, then the system derives the route target as "target:<configured_lanext_as>:<Alc-Bridge-Id>". Where <configured_lanext_as> is the value configured with configure subscriber-mgmt vrgw lanext router-target-as-number as-number. |
|
241.26.6527.15 |
Alc-RD |
This VSA specifies the Route Distinguisher of the HLE BGP EVPN service. When the VSA is not included, then the system derives the route distinguisher as "<configured_lanext_as>:<Alc-Bridge-Id>". Where <configured_lanext_as> is the value configured with configure subscriber-mgmt vrgw lanext router-target-as-number as-number. |
|
241.26.6527.24 |
Alc-IPv6-DMZ-Enabled |
This VSA determines if the corresponding session should be treated as part of a demilitarized zone in an IPv6 firewall or not. This attribute is ignored if the session is not part of a subscriber with firewall enabled. |
|
241.26.6527.30 |
Alc-HLE-Access-Ingress-Policer |
This VSA references the ISA policer (configure subscriber-mgmt isa-policer) to be used to rate limit ingress home traffic per tunnel on the HLE access facing connection of the Bridge Domain. Overrides the policer configured in configure service ies|vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range range vrgw lanext access policer policer-name |
|
241.26.6527.32 |
Alc-HLE-Network-Ingress-Policer |
This VSA references the ISA policer (configure subscriber-mgmt isa-policer) to be used to rate-limit ingress data center traffic per tunnel on the HLE network facing connection of the Bridge Domain. Overrides the policer configured in configure service ies|vprn service-id subscriber-interface ip-int-name group-interface ip-int-name wlan-gw vlan-tag-ranges range range vrgw lanext network policer policer-name |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
This VSA includes any static port forwards for Layer 2–aware NAT and, or IPv6 firewall. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
32 chars |
For example: User-Name = ‟00:01:02:03:04:05” |
|
2 |
User-Password |
string |
64 bytes encrypted password |
For example: User-Password = ‟4ec1b7bea6f2892fa466b461c6accc00” |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
string |
247 chars |
For example: Alc-PPPoE-Service-Name = MyServiceName |
|
26.6527.220 |
Alc-Home-Aware-Pool |
string |
Max. 2048 IP addresses in range |
<gateway-ip>/<prefix-length> <space> <start-address> <dash> <end-address> For example: Alc-Home-Aware-Pool = ‟192.168.1.2/24 192.168.1.50-192.168.1.100” |
|
26.6527.221 |
Alc-DMZ-Address |
ipaddr |
4 bytes |
Must be within the subnet of the home aware pool. 0.0.0.0 disables DMZ. For example: Enable Alc-DMZ-Address = 192.168.1.90 For example: Disable Alc-DMZ-Address = 0.0.0.0 |
|
26.6527.222 |
Alc-Standby-lps |
ipaddr |
4 bytes Up to 128 VSA’s |
This attribute can occur multiple times. For example: Alc-Standby-Ips += 192.168.1.100 Alc-Standby-Ips += 192.168.1.111 Alc-Standby-Ips += 192.168.1.115 |
|
26.6527.223 |
Alc-Reserved-Addresses |
string |
Max. 40 chars Max. 64 attributes |
<static | sticky> <space> <mac-address> <space> <ip-address> Per attribute, a single MAC and IP to specify the reservation and a keyword to specify the type of reservation (sticky or static). To delete all/last host of a specific reservation type, specify the type keyword and a mapping of MAC 00:00:00:00:00:00 to IP 0.0.0.0 For example:
|
|
26.6527.224 |
Alc-BRG-Profile |
string |
16 chars |
For example: Alc-BRG-Profile = ‟default_brg” |
|
26.6527.225 |
Alc-BRG-Id |
string |
64 chars |
For example: Alc-BRG-Id = ‟00:01:02:03:04:05” |
|
26.6527.235 |
Alc-BRG-DHCP-Streaming-Dest |
ipaddr |
4 bytes |
The destination IPv4 address for streaming DHCPv4 messages. IPv4 = 0.0.0.0 disables DHCPv4 streaming at BRG level For example: Alc-BRG-DHCP-Streaming-Dest = 172.30.1.1 Alc-BRG-DHCP-Streaming-Dest = 0.0.0.0 |
|
26.6527.236 |
Alc-Host-DHCP-Streaming-Disabled |
integer |
4 bytes [0 to 1] |
0 = enable DHCPv4 streaming for this session 1 = disable DHCPv4 streaming for this session Controls DHCPv4 streaming on per session level. For example: Alc-Host-DHCP-Streaming-Disabled = 1 |
|
26.6527.238 |
Alc-Remove-Override |
string |
Single attribute identifier per attribute. Multiple attributes per message. |
[<action><space>]<attribute identifier> See [26.6527.238] Alc-Remove-Override attribute details for a detailed description of the attribute format and its possible values. For example: remove overrides for SLA-Profile And NAS-Filter-Rule Alc-Remove-Override += ‟26.6527.13” Alc-Remove-Override += ‟92” |
|
26.6527.241 |
Alc-Per-Host-Port-Range |
integer |
0-64512 |
A value of 0 disables per-host port range allocation. Ports are allocated from the available dynamic ports per IP address. A value of 1 to 64512 specifies the number of ports per host range. This is additionally limited by the number of available dynamic ports per IP address. For example: 1000 ports per host, max. 64 hosts Alc-Per-Host-Port-Range = 1000 |
|
241.26.6527.1 |
Alc-PPPoE-Client-Service |
integer |
2147483647 |
For example: Alc-PPPoE-Client-Service = 2 |
|
241.26.6527.2 |
Alc-PPPoE-Client-MAC |
string |
17 chars |
MAC address in aa: or AA: format. For example: Alc-PPPoE-Client-MAC = "00:00:5E:00:53:01" |
|
241.26.6527.3 |
Alc-PPPoE-Client-Policy |
string |
32 chars |
String referring to a policy configured under configure subscriber-mgmt pppoe-client-policy For example: Alc-PPPoE-Client-Policy = Policy-1 |
|
241.26.6527.4 |
Alc-PPPoE-Client-Username |
string |
247 chars |
For example: Alc-PPPoE-Client-Username = user-1 |
|
241.26.6527.5 |
Alc-PPPoE-Client-Password |
string |
247 chars |
Encrypted Password For example: Alc-PPPoE-Client-Password = password-1 |
|
241.26.6527.9 |
Alc-Bridge-Id |
integer |
1 - 4294967294 |
For example: Alc-Bridge-Id = 200 |
|
241.26.6527.10 |
Alc-Vxlan-VNI |
integer |
1 - 16777214 |
For example: Alc-Vxlan-VNI =250 |
|
241.26.6527.14 |
Alc-RT |
string |
SR OS supported format |
One of the following formats:
For example: Alc-RT = "target: 64496:200" |
|
241.26.6527.15 |
Alc-RD |
string |
SR OS supported format |
One of the following formats:
For example: Alc-RD = "64496:510" |
|
241.26.6527.24 |
Alc-IPv6-DMZ-Enabled |
integer |
[0 to 1] |
0 = DMZ disabled 1 = DMZ enabled For example: DMZ enabled Alc-IPv6-DMZ-Enabled = 1 |
|
241.26.6527.30 |
Alc-HLE-Access-Ingress-Policer |
string |
32 chars |
ISA policer name For example: Alc-HLE-Access-Ingress-Policer = policer-1 |
|
241.26.6527.32 |
Alc-HLE-Network-Ingress-Policer |
string |
32 chars |
ISA policer name For example: Alc-HLE-Network-Ingress-Policer = policer-2 |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
string |
64 SPFs |
See [241.26.6527.39] Alc-Static-Port-Forward attribute details for details on this format. For example: Add an IPv6 firewall SPF to open up TCP port 80 (HTTP) Alc-Static-Port-Forward = "c tcp 2001:db8:1::1 80" Add an IPv6 SPF to open up UDP port 5 but only for traffic coming from IP 2001:db8:2::2 and port 80 Alc-Static-Port-Forward = "c udp 2001:db8:1::1 5 foreign 2001:db8:2::2 80" Add a Layer 2–aware NAT SPF to open up TCP port 80 (HTTP) on the outside and forward it to port 8080 on ip 10.1.1.1 on the inside Alc-Static-Port-Forward = "c tcp 10.1.1.1 80->8080" |
| Attribute ID | Attribute name | Access request |
|---|---|---|
|
1 |
User-Name |
1 |
|
2 |
User-Password |
0-1 |
|
26.6527.225 |
Alc-BRG-Id |
1 |
| Attribute ID | Attribute name | BRG level | Session level | ||
|---|---|---|---|---|---|
| Access Accept | CoA | Access Accept | CoA | ||
|
1 |
User-Name |
— |
— |
0-1 |
0-1 |
|
8 |
Framed-IP-Address |
— |
— |
0-1 |
0-1 |
|
9 |
Framed-IP-Netmask |
— |
— |
0-1 |
0 |
|
22 |
Framed-Route |
— |
— |
0+ |
0 |
|
25 |
Class |
0+ |
0+ |
0+ |
0+ |
|
27 |
Session-Timeout |
0-1 |
0-1 |
0-1 |
0-1 |
|
28 |
Idle-Timeout |
0-1 |
0-1 |
0-1 |
0-1 |
|
44 |
Acct-Session-Id |
— |
— |
0-1 |
0-1 |
|
61 |
NAS-Port-Type |
— |
— |
0-1 |
0-1 |
|
85 |
Acct-Interim-Interval |
0-1 |
0-1 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
— |
— |
0 |
0-1 |
|
92 |
NAS-Filter-Rule |
0+ |
0+ |
0+ |
0+ |
|
97 |
Framed-IPv6-Prefix |
0-1 |
0-1 |
0 |
0-1 |
|
99 |
Framed-IPv6-Route |
— |
— |
0+ |
0 |
|
100 |
Framed-IPv6-Pool |
0-16 | 0-16 |
— |
— |
|
101 |
Error-Cause |
0 |
0-1 |
0 |
0-1 |
|
26.529.242 |
Ascend-Data-Filter |
0+ |
0+ |
0+ |
0+ |
|
26.2352.1 |
Client-DNS-Pri |
0-17 | 0-17 |
0-1 |
0 |
|
26.2352.2 |
Client-DNS-Sec |
0-17 | 0-17 |
0-1 |
0 |
|
26.2352.99 |
RB-Client-NBNS-Pri |
0-17 | 0-17 |
0-1 |
0 |
|
26.2352.100 |
RB-Client-NBNS-Sec |
0-17 | 0-17 |
0-1 |
0 |
|
26.4874.4 |
ERX-Primary-Dns |
0-17 | 0-17 |
0-1 |
0 |
|
26.4874.5 |
ERX-Secondary-Dns |
0-17 | 0-17 |
0-1 |
0 |
|
26.4874.6 |
ERX-Primary-Wins |
0-17 | 0-17 |
0-1 |
0 |
|
26.4874.7 |
ERX-Secondary-Wins |
0-17 | 0-17 |
0-1 |
0 |
|
26.4874.47 |
ERX-Ipv6-Primary-Dns |
0-17 | 0-17 |
0-1 |
0-1 |
|
26.4874.48 |
ERX-Ipv6-Secondary-Dns |
0-17 | 0-17 |
0-1 |
0-1 |
|
26.6527.9 |
Alc-Primary-Dns |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.10 |
Alc-Secondary-Dns |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.11 |
Alc-Subsc-ID-Str |
0-18 |
0 |
0-1 |
0-1 |
|
26.6527.12 |
Alc-Subsc-Prof-Str |
0-1 |
0-1 |
— |
— |
|
26.6527.13 |
Alc-SLA-Prof-Str |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.18 |
Alc-Default-Router |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
— |
— |
0-1 |
0-1 |
|
26.6527.28 |
Alc-Int-Dest-Id-Str |
0-1 |
0-1 |
— |
— |
|
26.6527.29 |
Alc-Primary-Nbns |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.30 |
Alc-Secondary-Nbns |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.31 |
Alc-MSAP-Serv-Id |
— |
— |
0-1 |
0 |
|
26.6527.32 |
Alc-MSAP-Policy |
— |
— |
0-1 |
0 |
|
26.6527.33 |
Alc-MSAP-Interface |
— |
— |
0-1 |
0 |
|
26.6527.35 |
Alc-PPPoE-Service-Name |
0-19 | 0-19 |
— |
— |
|
26.6527.45 |
Alc-App-Prof-Str |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.95 |
Alc-Credit-Control-CategoryMap |
— |
— |
0-1 |
0-1 |
|
26.6527.96 |
Alc-Credit-Control-Quota |
— |
— |
0+ |
0+ |
|
26.6527.99 |
Alc-Ipv6-Address |
— |
— |
0-1 |
0-1 |
|
26.6527.103 |
Alc-ToClient-Dhcp-Options |
0+ |
0+ |
0+ |
0 |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
0-17 | 0-17 |
0-1 |
0-1 |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
0-17 | 0-17 |
0-1 |
0-1 |
|
26.6527.122 |
Alc-Ll-Action (enable/disable) |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.123 |
Alc-Ll-Destination |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.124 |
Alc-LI-FC |
0+ |
0+ |
0+ |
0+ |
|
26.6527.125 |
Alc-LI-Direction |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.126 |
Alc-Subscriber-QoS-Override |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.134 |
Alc-Subscriber-Filter |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.138 |
Alc-Ll-Intercept-Id |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.139 |
Alc-LI-Session-Id |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.151 |
Alc-Sub-Serv-Activate |
— |
— |
0+ |
0+ |
|
26.6527.152 |
Alc-Sub-Serv-Deactivate |
— |
— |
0+ |
0+ |
|
26.6527.153 |
Alc-Sub-Serv-Acct-Stats-Type |
— |
— |
0+ |
0+ |
|
26.6527.154 |
Alc-Sub-Serv-Acct-Interim-lvl |
— |
— |
0+ |
0+ |
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
0+ |
0+ |
0+ |
0+ |
|
26.6527.159 |
Alc-Ascend-Data-Filter-Host-Spec |
0+ |
0+ |
0+ |
0+ |
|
26.6527.160 |
Alc-Relative-Session-Timeout |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.174 |
Alc-Lease-Time |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.177 |
Alc-Portal-Url |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.178 |
Alc-Ipv6-Portal-Url |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.181 |
Alc-SLAAC-IPv6-Pool |
0-16 | 0-16 |
— |
— |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
0-1 |
0-1 |
0-1 |
0-1 |
|
26.6527.192 |
Alc-ToClient-Dhcp6-Options |
0+ |
0+ |
0+ |
0 |
|
26.6527.193 |
Alc-AA-App-Service-Options |
0+ |
0+ |
0-1 |
0-1 |
|
26.6527.200 |
Alc-v6-Preferred-Lifetime |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.201 |
Alc-v6-Valid-Lifetime |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.202 |
Alc-Dhcp6-Renew-Time |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.203 |
Alc-Dhcp6-Rebind-Time |
0-17 | 0-17 |
0-1 |
0 |
|
26.6527.217 |
Alc-UPnP-Sub-Override-Policy |
0-1 |
0-1 |
— |
— |
|
26.6527.220 |
Alc-Home-Aware-Pool |
0-1 |
0-1 |
— |
— |
|
26.6527.221 |
Alc-DMZ-Address |
0-1 |
0-1 |
— |
— |
|
26.6527.222 |
Alc-Standby-Ips |
0+8 |
0 |
— |
— |
|
26.6527.223 |
Alc-Reserved-Addresses |
0+ |
0+ |
— |
— |
|
26.6527.224 |
Alc-BRG-Profile |
0-1 |
0-1 |
— |
— |
|
26.6527.225 |
Alc-BRG-Id |
0-110 | 0-110 |
0-1 |
0 |
|
26.6527.228 |
Alc-Trigger-Acct-Interim |
— |
— |
0 |
0-1 |
|
26.6527.234 |
Alc-DNAT-Override |
0+ |
0+ |
n/a |
— |
|
26.6527.235 |
Alc-BRG-DHCP-Streaming-Dest |
0-1 |
0-1 |
n/a |
— |
|
26.6527.236 |
Alc-Host-DHCP-Streaming-Disabled |
— |
— |
0-1 |
0-1 |
|
26.6527.238 |
Alc-Remove-Override |
0 |
0+ |
0 |
0+ |
|
26.6527.241 |
Alc-Per-Host-Port-Range |
0-1 |
0-1 |
— |
— |
|
241.26.6527.1 |
Alc-PPPoE-Client-Service |
0-18 |
0 |
— |
— |
|
241.26.6527.2 |
Alc-PPPoE-Client-MAC |
0-18 |
0 |
— |
— |
|
241.26.6527.3 |
Alc-PPPoE-Client-Policy |
0-19 | 0-19 |
— |
— |
|
241.26.6527.4 |
Alc-PPPoE-Client-Username |
0-19 | 0-19 |
— |
— |
|
241.26.6527.5 |
Alc-PPPoE-Client-Password |
0-19 |
0 |
— |
— |
|
241.26.6527.9 |
Alc-Bridge-Id |
0-1 |
0 |
0-1 |
0 |
|
241.26.6527.10 |
Alc-Vxlan-VNI |
0-1 |
0 |
— |
— |
|
241.26.6527.14 |
Alc-RT |
0-1 |
0 |
— |
— |
|
241.26.6527.15 |
Alc-RD |
0-1 |
0 |
— |
— |
|
241.26.6527.16 |
Alc-IPv6-Router-Adv-Policy |
0-1 |
0-1 |
0-1 |
0-1 |
|
241.26.6527.17 |
Alc-Nat-Outside-IPs |
0+ |
0+ |
0 |
0 |
|
241.26.6527.24 |
Alc-IPv6-DMZ-Enabled |
— |
— |
0-1 |
0-1 |
|
241.26.6527.26 |
Alc-Aa-Sub-Scope |
0-18 |
0 |
— |
— |
|
241.26.6527.30 |
Alc-HLE-Access-Ingress-Policer |
0-1 |
0 |
— |
— |
|
241.26.6527.32 |
Alc-HLE-Network-Ingress-Policer |
0-1 |
0 |
— |
— |
|
241.26.6527.37 |
Alc-VAS-IPv4-Filter |
0-1 |
0-1 |
0-1 |
0-1 |
|
241.26.6527.38 |
Alc-VAS-NSH-IPv4-Opaque-Meta-Data |
— |
— |
0-1 |
0-1 |
|
241.26.6527.39 |
Alc-Static-Port-Forward |
0+ |
0+ |
0 |
0 |
|
241.26.6527.47 |
Alc-SPI-Sharing-Id |
0-1 |
0-1 |
0-1 |
0-1 |
|
241.26.6527.62 |
Alc-Host-DNAT-Override |
— |
— |
0-1 |
0-1 |
|
241.26.6527.71 |
Alc-Host-DNAT-Default-Address-Override |
— |
— |
0-1 |
0-1 |
|
245.26.6527.5 |
Alc-Spi-Host-And-Session-Limits |
0+ |
0+ |
0+ |
0+ |
|
245.26.6527.6 |
Alc-Sub-Host-And-Session-Limits |
0+ |
0+ |
0+ |
0+ |
[241.26.6527.39] Alc-Static-Port-Forward attribute details
Static port forwards (SPF) for NAT and firewall can be installed using the Alc-Static-Port-Forward Extended VSA. This section describes the format used for each application. Alc-Static-Port-Forward: Format for Layer 2–aware NAT static port forwards illustrates a diagram showing an overview of this syntax.
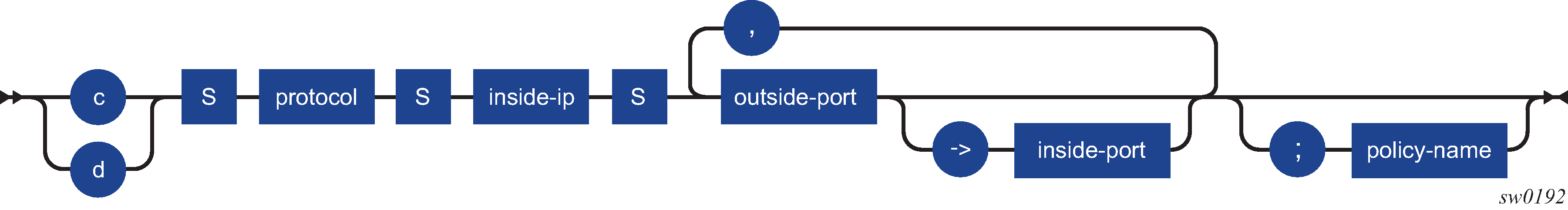
For l2-aware, the format looks as follows:
{c|d}<space>protocol<space>inside-ip<space>outside-port[->insideport][,outside-port[->insideport]]*[;policy-name]
l2-aware field descriptions describes the l2-aware format.
| Field name | Description |
|---|---|
|
c/d |
This field specifies whether the specified SPF needs to be created or deleted. |
|
protocol |
This field specifies the protocol to which this SPF applies. This can be either the literals 'udp' or 'tcp' or the protocol numbers 6 or 17. |
|
inside-ip |
This field specifies the inside IP to which the SPF traffic is forwarded. |
|
outside-port, inside-port |
This field is a list of ports that is opened. If inside-port is not specified, it is chosen the same as outside-port. Each specified (inside,outside) port pair results in a separate installed SPF. |
|
policy-name |
This field is the policy to which this SPF applies. If not provided, the default policy of the subscriber (sub-profile changes) is used. |
Alc-Static-Port-Forward: Format for residential firewall static port forwards illustrates a diagram showing an overview of the residential firewall format.
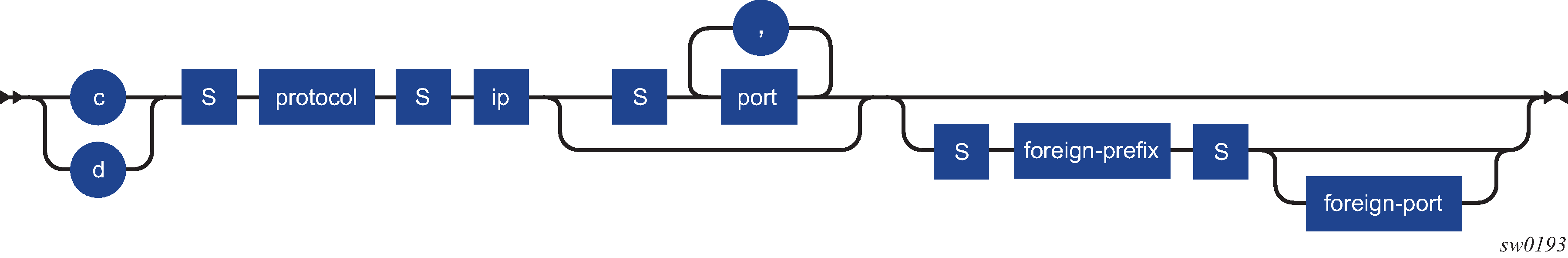
For residential firewall, the format looks as follows:
{c|d}<space>protocol<space>ip[<space>port[,]]*[<space>foreign-prefix[<space>foreign-port]]
Residential firewall field descriptions describes the Residential Firewall format.
| Field name | Description |
|---|---|
|
c/d |
This field specifies whether the specified SPF needs to be created or deleted. |
|
protocol |
This field specifies the protocol to which this SPF applies. For tcp or udp, the literal tcp or udp can be used. Only SPFs for TCP, UDP and supported unknown protocols can be used. SPFs for other protocols (for example, ICMPv6) are not supported. Note - If ICMPv6 is configured as an unknown protocol, a warning is issued. |
|
ip |
This field specifies the IP to which the SPF applies. |
|
port |
This field is a list of ports that are opened. No port may be specified for unknown protocols and at least one port needs to be specified for TCP/UDP. |
|
foreign-prefix |
This field limits the SPF to only allow traffic received from this prefix. |
|
foreign-port |
This field further limits traffic to this specific port. |
Any Static Port Forwards that are syntactically correct, but do not apply (for example, unused NAT policy or nonexistent IP) also count toward the maximum supported port forwards.
Bonding
This section describes attributes applicable to bonding. Bonding (description) and Bonding (limits) give an overview of all authentication attributes specific to bonding. Bonding context (applicability) subsequently gives an overview of the attributes that are applicable for the authentication of a Bonding context.
| Attribute ID | Attribute name | Description |
|---|---|---|
|
241.26.6527.19 |
Alc-Bonding-Id |
When present in authentication of an access session, indicates that the IPoE, PPPoE, or GTP session being authenticated is part of a bonding context with the given ID. The bonding-ID is also used as the subscriber-id for the associated bonding subscriber. |
|
241.26.6527.20 |
Alc-Bonding-Serv-Id |
Indicates the service in which a bonding subscriber is created and must be specified during authentication of the access session together with the attribute [241.26.6527.21] Alc-Bonding-Interface. |
|
241.26.6527.21 |
Alc-Bonding-Interface |
Defines the group-interface where the bonding subscriber is created and must be passed during authentication of the access session. The specified group interface must be of the type bonding. |
|
241.26.6527.22 |
Alc-Bonding-Reference-Rate |
For the preferred access connection in a bonding context this defines which rate is considered to determine if that connection is completely filled. The attribute either specifies an absolute rate or a QoS object from which rate is used. When a QoS object is specified, dynamic overrides are taken into account. The bonding load-balancing mechanism sends traffic over this connection first until the specified rate is reached; then it starts to send traffic over the alternate link too. This mechanism is configured under configure subscriber-mgmt sla-profile sla-profile-name egress bonding-selection. If the attribute is not present, then the bonding selection uses the subscriber aggregate-rate. If there is no aggregate-rate defined then the maximum absolute value is used. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
241.26.6527.19 |
Alc-Bonding-Id |
string |
1-32 chars |
A valid human-readable string, must not start with an underscore (_). For example: Alc-Bonding-Id = home1 |
|
241.26.6527.20 |
Alc-Bonding-Serv-Id |
integer |
2147483647 ID |
A valid VPRN or IES service ID For example: Alc-Bonding-Serv-Id = 5 |
|
241.26.6527.21 |
Alc-Bonding-Interface |
string |
1-32 chars |
The name of a group-interface of type bonding within the service defined by Alc-Bonding-Serv-Id For example: Alc-Bonding-Interface = bonding-group-interface |
|
241.26.6527.22 |
Alc-Bonding-Reference-Rate |
string |
1..4294967295 kb/s or a valid QoS object |
Format must be one of the following (quotes not included): '<value>': absolute rate in kb/s 'r|R': aggregate rate 'a|A:<name>': rate of named arbiter 's|S:<name>': rate of named scheduler For example: Alc-Bonding-Reference-Rate = s:scheduler-1 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
1 |
User-Name |
1 |
0-1 |
0-1 |
|
2 |
User-Password |
0-1 |
0 |
0 |
|
4 |
NAS-IP-Address |
0-1 |
0 |
0 |
|
8 |
Framed-IP-Address |
0 |
0-1 |
0-1 |
|
9 |
Framed-IP-Netmask |
0 |
0-1 |
0 |
|
22 |
Framed-Route |
0 |
0-1 |
0 |
|
25 |
Class |
0 |
0-1 |
0-1 |
|
27 |
Session-Timeout |
0 |
0-1 |
0-1 |
|
32 |
NAS-Identifier |
0-1 |
0 |
0 |
|
44 |
Acct-Session-Id |
0-1 |
0 |
0-1 |
|
61 |
NAS-Port-Type |
0-1 |
0 |
0-1 |
|
85 |
Acct-Interim-Interval |
0 |
0-1 |
0-1 |
|
87 |
NAS-Port-Id |
0-1 |
0 |
0-1 |
|
88 |
Framed-Pool |
0 |
0-1 |
0 |
|
92 |
NAS-Filter-Rule |
0 |
0+ |
0+ |
|
95 |
NAS-IPv6-Address |
0-1 |
0 |
0 |
|
97 |
Framed-IPv6-Prefix |
0 |
0-1 |
0-1 |
|
99 |
Framed-IPv6-Route |
0 |
0-1 |
0 |
|
101 |
Error-Cause |
0 |
0 |
0-1 |
|
26.529.242 |
Ascend-Data-Filter |
0 |
0+ |
0+ |
|
26.2352.1 |
Client-DNS-Pri |
0 |
0-1 |
0 |
|
26.2352.2 |
Client-DNS-Sec |
0 |
0-1 |
0 |
|
26.2352.36 |
Ip-Address-Pool-Name |
0 |
0-1 |
0 |
|
26.2352.99 |
Client-NBNS-Pri |
0 |
0-1 |
0 |
|
26.2352.100 |
Client-NBNS-Sec |
0 |
0-1 |
0 |
|
26.4874.2 |
ERX-Address-Pool-Name |
0 |
0-1 |
0 |
|
26.4874.4 |
ERX-Primary-Dns |
0 |
0-1 |
0 |
|
26.4874.5 |
ERX-Secondary-Dns |
0 |
0-1 |
0 |
|
26.4874.6 |
ERX-Primary-Wins |
0 |
0-1 |
0 |
|
26.4874.7 |
ERX-Secondary-Wins |
0 |
0-1 |
0 |
|
26.4874.47 |
ERX-Ipv6-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.4874.48 |
ERX-Ipv6-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.9 |
Alc-Primary-Dns |
0 |
0-1 |
0 |
|
26.6527.10 |
Alc-Secondary-Dns |
0 |
0-1 |
0 |
|
226.6527.11 |
Alc-Subsc-ID-Str |
0 |
0-1 |
0-1 |
|
26.6527.12 |
Alc-Subsc-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.13 |
Alc-SLA-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.18 |
Alc-Default-Router |
0 |
0-1 |
0 |
|
26.6527.28 |
Alc-Int-Dest-Id-Str |
0 |
0-1 |
0-1 |
|
26.6527.29 |
Alc-Primary-Nbns |
0 |
0-1 |
0 |
|
26.6527.30 |
Alc-Secondary-Nbns |
0 |
0-1 |
0 |
|
26.6527.45 |
Alc-App-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.95 |
Alc-Credit-Control-CategoryMap |
0 |
0-1 |
0-1 |
|
26.6527.96 |
Alc-Credit-Control-Quota |
0-1 |
0-1 |
0-1 |
|
26.6527.105 |
Alc-Ipv6-Primary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.106 |
Alc-Ipv6-Secondary-Dns |
0 |
0-1 |
0-1 |
|
26.6527.122 |
Alc-LI-Action |
0 |
1 |
1 |
|
26.6527.123 |
Alc-LI-Destination |
0 |
1 |
1 |
|
26.6527.124 |
Alc-LI-FC |
0 |
0+ |
0-1 |
|
26.6527.125 |
Alc-LI-Direction |
0 |
0-1 |
0-1 |
|
26.6527.126 |
Alc-Subscriber-QoS-Override |
0 |
0-1 |
0-1 |
|
26.6527.134 |
Alc-Subscriber-Filter |
0 |
0-1 |
0-1 |
|
26.6527.136 |
Alc-Onetime-Http-Redirection-Filter-Id |
0 |
0-1 |
0-1 |
|
26.6527.137 |
Alc-Authentication-Policy-Name |
0 |
0 |
0-1 |
|
26.6527.138 |
Alc-LI-Intercept-Id |
0 |
0-1 |
0-1 |
|
26.6527.139 |
Alc-LI-Session-Id |
0 |
0-1 |
0-1 |
|
26.6527.151 |
Alc-Sub-Serv-Activate |
0 |
0+ |
0+ |
|
26.6527.152 |
Alc-Sub-Serv-Deactivate |
0 |
0+ |
0+ |
|
26.6527.153 |
Alc-Sub-Serv-Acct-Stats-Type |
0 |
0+ |
0+ |
|
26.6527.154 |
Alc-Sub-Serv-Acct-Interim-Ivl |
0 |
0+ |
0+ |
|
26.6527.158 |
Alc-Nas-Filter-Rule-Shared |
0 |
0+ |
0+ |
|
26.6527.159 |
Alc-Ascend-Data-Filter-Host-Spec |
0 |
0+ |
0+ |
|
26.6527.160 |
Alc-Relative-Session-Timeout |
0 |
0-1 |
0-1 |
|
26.6527.177 |
Alc-Portal-Url |
0 |
0-1 |
0-1 |
|
26.6527.178 |
Alc-Ipv6-Portal-Url |
0 |
0-1 |
0-1 |
|
26.6527.180 |
Alc-SAP-Session-Index |
0-1 |
0 |
0 |
|
26.6527.181 |
Alc-SLAAC-IPv6-Pool |
0 |
0-1 |
0 |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
0 |
0-1 |
0-1 |
|
26.6527.185 |
Alc-Onetime-Http-Redirect-Reactivate |
0 |
0 |
0-1 |
|
26.6527.193 |
Alc-AA-App-Service-Options |
0 |
0+ |
0+ |
|
26.6527.200 |
Alc-v6-Preferred-Lifetime |
0 |
0-1 |
0 |
|
26.6527.201 |
Alc-v6-Valid-Lifetime |
0 |
0-1 |
0 |
|
26.6527.217 |
Alc-UPnP-Sub-Override-Policy |
0 |
0-1 |
0-1 |
|
26.6527.228 |
Alc-Trigger-Acct-Interim |
0 |
0 |
0-1 |
|
26.6527.232 |
Alc-Acct-Interim-Ivl |
0 |
0+ |
0+ |
|
26.6527.234 |
Alc-DNAT-Override |
0 |
0-1 |
0-1 |
|
26.6527.238 |
Alc-Remove-Override |
0 |
0 |
0+ |
|
26.6527.242 |
Alc-Radius-Py |
0+ |
0+ |
0+ |
|
241.26.6527.20 |
Alc-Bonding-Serv-Id |
0 |
0-1 |
0 |
|
241.26.6527.21 |
Alc-Bonding-Interface |
0 |
0-1 |
0 |
Dynamic data services
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
This attribute is for RADIUS authentication of data triggered Dynamic Data Services only. The user to be authenticated in the Access-Request. The attribute value is the dynamic service data trigger sap-id. |
|
2 |
User-Password |
This attribute is for RADIUS authentication of data triggered Dynamic Data Services only. The password of the user to be authenticated. The attribute value is preconfigured: configure service dynamic-services dynamic-services-policy dynsvc-policy-name authentication password password |
|
4 |
NAS-IP-Address |
This attribute is for RADIUS authentication of data triggered Dynamic Data Services only. The identifying IP Address of the NAS requesting the Authentication. Included when the RADIUS server is reachable using IPv4. The address is determined by the routing instance through which the RADIUS server can be reached: "Management" — The active IPv4 address in the Boot Options File (bof address ipv4-address) "Base" or "VPRN" — the IPv4 address of the system interface (configure router interface system address address). The address can be overwritten with the configured source-address (configure aaa radius-server-policy policy-name servers source-address ip- address). |
|
8 |
Framed-IP-Address |
This attribute is for RADIUS authentication of data triggered Dynamic Data Services only. The IPv4 source address of an IPv4 data trigger frame that resulted in the authentication. Not included if the data trigger frame is not an IPv4 packet. |
|
32 |
NAS-Identifier |
(RADIUS authentication of data triggered Dynamic Data Services only) A string identifying the NAS originating the Authentication request. The attribute value is the system name of the router: configure system name system-name |
|
44 |
Acct-Session-Id |
(RADIUS authentication of data triggered Dynamic Data Services only) A unique identifier that represents the dynamic service data trigger that is authenticated. This attribute can be used as CoA or Disconnect Message key to target the dynamic service data trigger and is reflected in the accounting messages as attribute [50] Acct-Multi-Session-Id. |
|
87 |
NAS-Port-Id |
(RADIUS authentication of data triggered Dynamic Data Services only) A text string which identifies the physical or logical port of the NAS which is authenticating the user. Attribute is also used in CoA and Disconnect Message as identification key. The attribute value is the dynamic service data trigger sap-id. |
|
95 |
NAS-IPv6-Address |
(RADIUS authentication of data triggered Dynamic Data Services only) The identifying IP Address of the NAS requesting the Authentication or Accounting. Included when the RADIUS server is reachable using IPv6. The address is determined by the routing instance through which the RADIUS server can be reached: "Management" - The active IPv6 address in the Boot Options File (bof address ipv6-address). "Base" or "VPRN" - The IPv6 address of the system interface (configure router interface system ipv6 address ipv6-address). The address can be overwritten with the configured IPv6 source-address (configure aaa radius-server-policy policy-name servers ipv6-source-address ipv6-address). |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
(RADIUS authentication of data triggered Dynamic Data Services only) The MAC address of the dynamic service data trigger frame that resulted in the authentication. The format is fixed: xx:xx:xx:xx:xx:xx |
|
26.6527.99 |
Alc-Ipv6-Address |
(RADIUS authentication of data triggered Dynamic Data Services only) The IPv6 source address of an IPv6 data trigger frame that resulted in the authentication. Not included if the data trigger frame is not an IPv6 packet. |
|
26.6527.164 |
Alc-Dyn-Serv-SAP-Id |
Identifies the dynamic data service SAP. Only Ethernet ports and LAGs are valid. The Dynamic Service SAP-ID uniquely identifies a Dynamic Data Service instance. It can be specified explicitly or relative to the control channel SAP-ID using wildcards. If explicitly specified, the Dynamic Data Service SAP-ID and Control Channel SAP-ID do not have to be on the same port. The setup of the Dynamic Data Service fails if the SAP specified in [26.6527.164] Alc-Dyn-Serv-SAP-Id is not created. The Dynamic Data Service SAP becomes orphaned if the SAP is not deleted with a teardown action. |
|
26.6527.165 |
Alc-Dyn-Serv-Script-Params |
Parameters as input to the Dynamic Data Service Python script. The parameters can cross an attribute boundary. The concatenation of all [26.6527.165] Alc-Dyn-Serv-Script-Params attributes with the same tag in a single message must be formatted as function-key dictionary where function-key specifies which Python functions is called and dictionary contains the actual parameters in a Python dictionary structure format. In dynamic service RADIUS accounting messages, the attribute is sent untagged and contains the last received [26.6527.165] Alc-Dyn-Serv-Script-Params value in an Access-Accept or CoA message for this dynamic service. Multiple attributes may be present if the total length does not fit a single attribute. |
|
26.6527.166 |
Alc-Dyn-Serv-Script-Action |
The action specifies if a dynamic data service should be created (setup), changed (modify) or deleted (teardown). Together with the function-key in the [26.6527.165] Alc-Dyn-Serv-Script-Params, this attribute determines which Python function is called. The attribute is mandatory in a CoA message. The attribute is optional in an Access-Accept message. If included in an Access-Accept and the specified action is different from setup, the dynamic data service action fails. |
|
26.6527.167 |
Alc-Dyn-Serv-Policy |
Specifies which local configured Dynamic Data Service Policy to use for provisioning of this dynamic service. If the attribute is not present, the dynamic services policy with the name default is used. If the default policy does not exist, then the dynamic data service action fails. The [26.6527.167] Alc-Dyn-Serv-Policy attribute is optional in case of modify or teardown actions; the policy specified for the dynamic data service setup is automatically used. If the [26.6527.167] Alc-Dyn-Serv-Policy is specified for modify or teardown actions, it must point to the same dynamic services policy as used during the dynamic data service setup. If a different policy is specified, the action fails. |
|
26.6527.168 |
Alc-Dyn-Serv-Acct-Interim-Ivl-1 |
The number of seconds between each dynamic data service accounting interim update for the primary accounting server. Overrides local configured value in the Dynamic Services policy. With value = 0, the interim accounting to the primary accounting server is switched off. The dynamic data service accounting interim interval cannot be changed for an active service. The attribute is rejected if the script action is different from setup. |
|
26.6527.169 |
Alc-Dyn-Serv-Acct-Interim-Ivl-2 |
The number of seconds between each dynamic data service accounting interim update for the duplicate accounting server. Overrides local configured value in the Dynamic Services policy. With value = 0, the interim accounting to the duplicate accounting server is switched off. The dynamic data service accounting interim interval cannot be changed for an active service. The attribute is rejected if the script action is different from setup. |
|
26.6527.170 |
Alc-Dyn-Serv-Acct-Stats-Type-1 |
Enable or disable dynamic data service accounting to the primary accounting server and specify the stats type: volume and time or time only. Overrides the local configured value in the Dynamic Services Policy. The dynamic data service accounting statistics type cannot be changed for an active service. The attribute is rejected if the script action is different from setup. |
|
26.6527.171 |
Alc-Dyn-Serv-Acct-Stats-Type-2 |
Enable or disable dynamic data service accounting to the secondary accounting server and specify the stats type: volume and time or time only. Overrides the local configured value in the Dynamic Services Policy. The dynamic data service accounting statistics type cannot be changed for an active service. The attribute is rejected if the script action is different from setup. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
253 chars |
Fixed to the sap-id of the dynamic service data trigger packet For example: User-Name = "1/1/1:10.2" |
|
2 |
User-Password |
string |
64 bytes |
Encrypted password For example: User-Password = "6/TcjoaomHgakafcDrpCDk" |
|
4 |
NAS-IP-Address |
ipaddr |
4 bytes |
IPv4 address. For example: NAS-IP-Address = 192.0.2.1 |
|
8 |
Framed-IP-Address |
ipaddr |
4 bytes |
IPv4 address. For example: Framed-IP-Address = 10.1.0.1 |
|
32 |
NAS-Identifier |
string |
64 chars |
For example: NAS-Identifier = "router-1" |
|
44 |
Acct-Session-Id |
string |
22 bytes |
Internal generated 22 byte number. For example: Acct-Session-Id = "144DFF000000CB56A79EC4" |
|
87 |
NAS-Port-Id |
string |
253 chars |
Fixed to the sap-id of the dynamic service data trigger packet For example: User-Name = "1/1/1:10.2" |
|
95 |
NAS-IPv6-Address |
ipv6addr |
16 bytes |
IPv6 address. For example: NAS-IPv6-Address = 2001:db8::1 |
|
26.6527.27 |
Alc-Client-Hardware-Addr |
string |
6 bytes |
Format fixed to xx:xx:xx:xx:xx:xx For example: Alc-Client-Hardware-Addr = 00:51:00:dd:01:01 |
|
26.6527.99 |
Alc-Ipv6-Address |
ipv6addr |
16 bytes |
IPv6 address. For example: Alc-Ipv6-Address = 2001:db8:100::1 |
|
26.6527.164 |
Alc-Dyn-Serv-SAP-Id |
string |
1 VSA per tag per message |
Any valid Ethernet SAP format (null, dot1q or QinQ encaps), including LAGs. A wildcard (#) can be specified for the port field and optionally for one of the tag fields of a QinQ encap. To find the dynamic data service SAP-ID, the wildcard fields are replaced with the corresponding field from the Control Channel SAP-ID. For example: Alc-Dyn-Serv-SAP-Id:1 = 1/2/7:10.201 Alc-Dyn-Serv-SAP-Id:2 = #:#.100 |
|
26.6527.165 |
Alc-Dyn-Serv-Script-Params |
string |
multiple VSAs per tag per message. Max length of concatenated strings per tag = 1000 bytes |
The script parameters may be continued across attribute boundaries. The concatenated string must have following format: function-key <dictionary> where function-key specifies which Python functions are used and <dictionary> contains the actual parameters in a Python dictionary structure format. For example: Alc-Dyn-Serv-Script-Params:1 = data_svc_1 = { 'as_id' : '100', 'comm_id' : '200', 'if_name' : 'itf1', 'ipv4_address': '192.168.1.1', 'egr_ip_filter' : '100' , 'routes' : [{'to' : '172.16.1.0/24', 'next-hop' : '192.168.2.2'}, {'to' : '172.16.2.0/24', 'next-hop' : '192.168.2.2'}]} |
|
26.6527.166 |
Alc-Dyn-Serv-Script-Action |
integer |
1 VSA per tag per message |
1=setup, 2=modify, 3=teardown For example: Alc-Dyn-Serv-Script-Action:1 = 2 |
|
26.6527.167 |
Alc-Dyn-Serv-Policy |
string |
1 VSA per tag per message; max. length: 32 chars |
The name of the local configured Dynamic Service Policy For example: Alc-Dyn-Serv-Policy:1 = dynsvc-policy-1 |
|
26.6527.168 |
Alc-Dyn-Serv-Acct-Interim-Ivl-1 |
integer |
1 VSA per tag per message [300 to 15552000] |
A value of 0 (zero) corresponds with no interim update messages. A value [1 to 299] seconds is rounded to 300s (min. CLI value) and a value > 15552000 seconds (max. CLI value) is rounded to the max. CLI value. Range = 0 | [300 to 15552000] For example: Alc-Dyn-Serv-Acct-Interim-Ivl-1:1 = 3600 |
|
26.6527.169 |
Alc-Dyn-Serv-Acct-Interim-Ivl-2 |
integer |
1 VSA per tag per message [300 to 15552000] |
A value of 0 (zero) corresponds with no interim update messages. A value [1 to 299] seconds is rounded to 300s (min. CLI value) and a value > 15552000 seconds (max. CLI value) is rounded to the max. CLI value. Range = 0 | [300 to 15552000] For example: Alc-Dyn-Serv-Acct-Interim-Ivl-2:1 = 86400 |
|
26.6527.170 |
Alc-Dyn-Serv-Acct-Stats-Type-1 |
integer |
1 VSA per tag per message |
1=off, 2=volume-time, 3=time For example: Alc-Dyn-Serv-Acct-Stats-Type-1:1 = 1 |
|
26.6527.171 |
Alc-Dyn-Serv-Acct-Stats-Type-2 |
integer |
1 VSA per tag per message |
1=off, 2=volume-time, 3=time For example: Alc-Dyn-Serv-Acct-Stats-Type-2:1 = 2 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Tag | Max. tag |
|---|---|---|---|---|---|---|
|
1 |
User-Name |
1 |
0 |
0 |
— |
|
|
2 |
User-Password |
1 |
0 |
0 |
— |
|
|
4 |
NAS-IP-Address |
0-1 |
0 |
0 |
— |
|
|
8 |
Framed-IP-Address |
0-1 |
0 |
0 |
— |
|
|
32 |
NAS-Identifier |
1 |
0 |
0 |
— |
|
|
44 |
Acct-Session-Id |
1 |
0 |
0-1 |
— |
|
|
87 |
NAS-Port-Id |
1 |
0 |
0-1 |
— |
|
|
95 |
NAS-IPv6-Address |
0-1 |
0 |
0 |
— |
|
|
26.6527.27 |
Alc-Client-Hardware-Addr |
1 |
0 |
0 |
— |
|
|
26.6527.99 |
Alc-Ipv6-Address |
0-1 |
0 |
0 |
— |
|
|
26.6527.164 |
Alc-Dyn-Serv-SAP-Id |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.165 |
Alc-Dyn-Serv-Script-Params |
0 |
0+ |
0+ |
✓ |
0-31 (untagged) |
|
26.6527.166 |
Alc-Dyn-Serv-Script-Action |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.167 |
Alc-Dyn-Serv-Policy |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.168 |
Alc-Dyn-Serv-Acct-Interim-Ivl-1 |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.169 |
Alc-Dyn-Serv-Acct-Interim-Ivl-2 |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.170 |
Alc-Dyn-Serv-Acct-Stats-Type-1 |
0 |
0+ |
0+ |
✓ |
0-31 |
|
26.6527.171 |
Alc-Dyn-Serv-Acct-Stats-Type-2 |
0 |
0+ |
0+ |
✓ |
0-31 |
Dynamic data services — control channel CoA attributes lists the mandatory/optional attributes in CoA messages to the control channel.
| Attribute name | Setup | Modify | Teardown | Comment |
|---|---|---|---|---|
|
Acct-Session-Id |
M |
M |
M |
(CoA key) Acct-Session-Id of the Control Channel (or any other valid CoA key for ESM hosts/sessions) |
|
Alc-Dyn-Serv-SAP-Id |
M11 | M11 | M11 |
Identifies the dynamic data service |
|
Alc-Dyn-Serv-Script-Params |
M11 | M11 |
N/A |
For a Modify, the Script Parameters represent the new parameters required for the change. |
|
Alc-Dyn-Serv-Script-Action |
M11 | M11 | M11 | |
|
Alc-Dyn-Serv-Policy |
O |
O |
O |
Default policy used when not specified for Setup action. Must be same as used for setup if specified for Modify or Teardown. |
|
Alc-Dyn-Serv-Acct-Interim-Ivl-1 |
O |
X12 | X12 | |
|
Alc-Dyn-Serv-Acct-Interim-Ivl-2 |
O |
X12 | X12 | |
|
Alc-Dyn-Serv-Acct-Stats-Type-1 |
O |
X12 | X12 | |
|
Alc-Dyn-Serv-Acct-Stats-Type-2 |
O |
X12 | X12 | |
|
M = Mandatory, O = Optional, X = May Not, N/A = Not Applicable (ignored) |
||||
Data triggered dynamic services (CoA Key = Nas-Port-Id or Acct-Session-Id of dynamic data service SAP) - CoA attributes lists the mandatory/optional attributes in CoA messages sent to a dynamic data service associated with a dynamic services data trigger using Nas-Port-Id or Acct-Session-Id of a dynamic data service sap as CoA key.
| Attribute name | Setup | Modify | Teardown | Comment |
|---|---|---|---|---|
|
Nas-Port-Id |
N/S |
M13 | M13 |
(CoA key) Nas-Port-Id of a Dynamic Data Service sap |
|
Alc-Dyn-Serv-SAP-Id |
N/S |
O |
O |
If specified, the sap-id must be the same as the Nas-Port-Id or correspond with the dynamic service sap identified with the Acct-Session-Id. |
|
Alc-Dyn-Serv-Script- Params |
N/S |
M14 |
N/A |
For a Modify, the Script Parameters represent the new parameters required for the change. |
|
Alc-Dyn-Serv-Script- Action |
N/S |
M14 | M14 | |
|
Alc-Dyn-Serv-Policy |
N/S |
O |
O |
Must be same as used for setup if specified for Modify or Teardown. |
|
Alc-Dyn-Serv-Acct- Interim-Ivl-1 |
N/S |
X15 | X15 | |
|
Alc-Dyn-Serv-Acct- Interim-Ivl-2 |
N/S |
X15 | X15 | |
|
Alc-Dyn-Serv-Acct- Stats-Type-1 |
N/S |
X15 | X15 | |
|
Alc-Dyn-Serv-Acct- Stats-Type-2 |
N/S |
X15 | X15 | |
|
M = Mandatory, O = Optional, X = May Not, N/A = Not Applicable (ignored), N/S = Not Supported |
||||
Data triggered dynamic services (CoA Key = Acct-Session-Id of dynamic service data trigger) - CoA attributes lists the mandatory/optional attributes in CoA messages sent to a dynamic services data trigger using the Acct-Session-Id of the data trigger as CoA key.
| Attribute name | Setup | Modify | Teardown | Comment |
|---|---|---|---|---|
|
Acct-Session-Id |
M |
M |
M |
(CoA key) Acct-Session-Id of a dynamic service data trigger. |
|
Alc-Dyn-Serv-SAP-Id |
M16 | M16 | M16 |
Identifies the dynamic data service associated with the dynamic service data trigger. |
|
Alc-Dyn-Serv-Script- Params |
M16 | M16 |
N/A |
For a Modify, the Script Parameters represent the new parameters required for the change. |
|
Alc-Dyn-Serv-Script- Action |
M16 | M16 | M16 | |
|
Alc-Dyn-Serv-Policy |
O |
O |
O |
Default policy used when not specified for Setup action. Must be same as used for setup if specified for Modify or Teardown. |
|
Alc-Dyn-Serv-Acct- Interim-Ivl-1 |
O |
X17 | X17 | |
|
Alc-Dyn-Serv-Acct- Interim-Ivl-2 |
O |
X17 | X17 | |
|
Alc-Dyn-Serv-Acct- Stats-Type-1 |
O |
X17 | X17 | |
|
Alc-Dyn-Serv-Acct- Stats-Type-2 |
O |
X17 | X17 | |
|
M = Mandatory, O = Optional, X = May Not, N/A = Not Applicable (ignored) |
||||
Lawful intercept
| Attribute ID | Attribute name | Description |
|---|---|---|
|
26.6527.122 |
Alc-LI-Action |
Defines the traffic mirroring action start-mirroring 'enable' or stop-mirroring 'disable'. The Alc-LI-Action 'no-action' specifies that the router does not perform any traffic mirroring-related action. This setting can provide additional security by confusing unauthorized users who attempt to access traffic mirroring communication between the router and the RADIUS server. The CoA-only 'clear-dest-service' Alc-LI-Action creates the ability to delete all li-source entries from the mirror service defined using the Alc-LI-Destination service-id. A 'clear-dest-service' action requires an additional [26.6527.137] Alc-Authentication-Policy-Name if the CoA server is configured in the authentication policy. Values outside the Limits are treated as a setup failure. |
|
26.6527.123 |
Alc-LI-Destination |
Defines the LI destination which could be either the mirror destination service ID or the IP destination.
Note - The VSA Alc-LI-Action = 4 (clear-dest-service) can be used to delete the auto-generated mirror destination service identified by three parameters: ip-dst, udp-dst and routing instance. These parameters can be specified in the Alc-LI-Destination VSA. Missing parameters are obtained from the active radius mirror destination template (configure li radius mirror-dest-template name). All mirror destination services with any ip-src, udp-src, and direction-bit are deleted. A LI admin user can also clear the mirror destination service created from Radius with following CLI command: clear li radius mirror-dest svc-id. |
|
26.6527.124 |
Alc-LI-FC |
Defines which Forwarding Classes (FCs) should be mirrored (for example: Alc-LI-FC=ef). Attribute needs to be repeated for each FC that needs to be mirrored. Values above the Limits are treated as a setup failure and all FCs are mirrored if attribute is omitted. Additional attributes above the limits are silently ignored. |
|
26.6527.125 |
Alc-LI-Direction |
Defines if ingress, egress or both traffic directions needs to be mirrored. Both directions are mirrored if Attribute is omitted. Values above the Limits are treated as a setup failure. |
|
26.6527.137 |
Alc-Authentication-Policy-Name |
Used when clearing all RADIUS LI-triggered sources from a mirror destination using CoA ([26.6527.122] Alc-LI-Action = 'clear-dest-service'). The policy defined in this attribute is used to authenticate the CoA and refers to configure subscriber-mgmt authentication-policy name. The attribute is mandatory if the RADIUS CoA server is configured in the authentication policy (configure subscriber-mgmt authentication-policy name radius-authentication-server). The attribute is ignored if the RADIUS CoA server is configured in the radius-server context of the routing instance (configure router | service vprn service-id radius-server). Values above the Limits or unreferenced policies are treated as a setup failure. |
|
26.6527.138 |
Alc-LI-Intercept-Id |
Specifies the intercept-id to be placed in the LI-Shim header and only applicable if the mirror-dest (as specified by the [26.6527.123] Alc-LI-Destination attribute) is configured with routable encap that contains the LI-Shim (configure mirror mirror-dest service-id encap layer-3-encap ip-udp-shim). A zero can be returned in CoA or RADIUS Accept or the value of 0 is used if this VSA is not present at all. The length of the attribute changes if the CLI parameter direction-bit (dir-bit) under the mirror-dest service-id encap layer-3-encap is enabled. |
|
26.6527.139 |
Alc-LI-Session-Id |
Specifies the session-id to be placed in the LI-Shim header and only applicable if the mirror-dest (as specified by the [26.6527.123] Alc-LI-Destination attribute) is configured with routable encap that contains the LI-Shim (configure mirror mirror-dest service-id encap layer-3-encap ip-udp-shim). A zero can be returned in CoA or RADIUS Accept or the value of 0 is used if this VSA is not present at all. |
|
26.6527.243 |
Alc-LI-Use-Outside-Ip |
Defines if Lawful Intercept should be performed before or after NAT on a Layer 2–aware NAT subscriber. If set to true (1), the lawful intercepted traffic contains the subscriber outside public IP address. If set to false (2), the lawful intercepted traffic contains the subscriber inside private IP address. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
26.6527.122 |
Alc-LI-Action |
integer |
[1 to 4] |
1=no-action, 2=enable, 3=disable, 4=clear-dest-service Note - Alc-LI-Action=clear-dest-service together with Alc-Authentication-Policy-Name attribute are only applicable in CoA For example: Alc-LI-Action = enable |
|
26.6527.123 |
Alc-LI-Destination |
string |
32 chars |
|
|
26.6527.124 |
Alc-LI-FC |
integer |
[0 to 7] values 8 attributes |
0=be, 1=l2, 2=af, 3=l1, 4=h2, 5=ef, 6=h1, 7=nc For example: # mirror forwarding class be, af and ef Alc-LI-FC += be Alc-LI-FC += af Alc-LI-FC += ef |
|
26.6527.125 |
Alc-LI-Direction |
integer |
[1 to 2] |
1=ingress, 2=egress For example: Alc-LI-Direction = ingress |
|
26.6527.137 |
Alc-Authentication-Policy-Name |
string |
32 chars |
For example: Alc-Authentication-Policy-Name = MyAuthenticationPolicy |
|
26.6527.138 |
Alc-LI-Intercept-Id |
integer |
29b with dir-bit 30b without dir-bit |
29b = [0 to 536870911] 30b = [0 to 1073741823] For example: Alc-LI-Intercept-Id = 1234 |
|
26.6527.139 |
Alc-LI-Session-Id |
integer |
[0 to 4294967295] ID |
For example: Alc-LI-Session-Id = 8888 |
|
26.6527.243 |
Alc-LI-Use-Outside-Ip |
integer |
[1 to 2] |
1=true, 2=false For example: Alc-LI-User-Outside-IP = 1 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request | Encrypted |
|---|---|---|---|---|---|
|
26.6527.122 |
Alc-LI-Action |
0 |
1 |
1 |
✓ |
|
26.6527.123 |
Alc-LI-Destination |
0 |
1 |
1 |
✓ |
|
26.6527.124 |
Alc-LI-FC |
0 |
0+ |
0+ |
✓ |
|
26.6527.125 |
Alc-LI-Direction |
0 |
0-1 |
0-1 |
✓ |
|
26.6527.137 |
Alc-Authentication-Policy-Name |
0 |
0 |
0-1 |
|
|
26.6527.138 |
Alc-LI-Intercept-Id |
0 |
0-1 |
0-1 |
✓ |
|
26.6527.139 |
Alc-LI-Session-Id |
0 |
0-1 |
0-1 |
✓ |
|
26.6527.243 |
Alc-LI-Use-Outside-Ip |
0 |
0-1 |
0-1 |
✓ |
IPsec
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
For IKEv1 remote-access tunnel, this represents the xauth username. For IKEv2 remote-access tunnel, this represents the identity of the peer; the value of User-Name is the received IDi in IKEv2 message. |
|
2 |
User-Password |
For IKEv1 remote-access tunnel, this represents the xauth password. For IKEv2 remote-access tunnel with pskradius authentication method, this represents the pre-shared-key of the ipsec-gw or ipsec-tunnel: configure service ies/vprn service-id interface ip-int-name sap sap-id ipsec-gw gw-name pre-shared-key or configure service vprn service-id interface ip-int-name sap sap-id ipsec-tunnel tnl-name dynamic-keying pre-shared-key For IKEv2 remote-access tunnel with authentication method other than psk-radius, this represents the password configured in IPsec radius-authentication-policy: configure ipsec radius-authentication-policy name password |
|
4 |
NAS-IP-Address |
The identifying IP Address of the NAS requesting the authentication. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute nas-ip-addr. The address is determined by the routing instance through which the RADIUS server can be reached: "Management" - the active IPv4 address in the Boot Options File (bof address ipv4-address) "Base" or "VPRN" - the IPv4 address of the system interface (configure router interface system address address) The address can be overwritten with the configured source-address (configure aaa radius-server-policy policy-name servers source-address ip-address). |
|
8 |
Framed-IP- Address |
The IPv4 address to be assigned to IKEv1/v2 remote-access tunnel client using configuration payload: INTERNAL_IP4_ADDRESS. |
|
9 |
Framed-IP-Netmask |
The IPv4 netmask to be assigned to IKEv1/v2 remote-access tunnel client using configuration payload: INTERNAL_IP4_NETMASK. |
|
30 |
Called-Station-Id |
The local gateway address of IKEv2 remote-access tunnel. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute called-station-id. |
|
31 |
Calling-Station-Id |
The peer’s address and port of IKEv2 remote-access tunnel. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute calling-station-id. |
|
32 |
NAS-Identifier |
A string (configure system name system-name) identifying the NAS originating the Authentication requests. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute nas-identifier. |
|
44 |
Acct-Session-Id |
A unique identifier representing an IKEv2 remote-access tunnel session that is authenticated. Same Acct-Session-Id is included in both access-request and accounting-request. |
|
79 |
EAP-Message |
This attribute encapsulates the received IKEv2 EAP payload in access-request. |
|
80 |
Message-Authenticator |
This attribute is used in EAP authentication and provides message integrity verification. |
|
87 |
Nas-Port-Id |
The public SAP ID of IKEv2 remote-access tunnel. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute nas-port-id. |
|
88 |
Framed-Pool |
The name of one IPv4 address pool or the name of a primary and secondary IPv4 address pool separated with a one-character configurable delimiter (configure router | service vprn service-id dhcp local-dhcp-server server-name use-pool-from-client delimiter delimiter) that should be used for local address assignment during IKEv2 remote-access tunnel setup. A RADIUS server can include the attribute in an Access-Accept. The value of this attribute overrides the local configured value in the ipsec-gw local-address-assignment ipv4 CLI context of the interface SAP. |
|
97 |
Framed-IPv6-Prefix |
The IPv6 address to be assigned to IKEv2 remote-access tunnel client using IKEv2 configuration payload: INTERNAL_IP6_ADDRESS. The prefix and prefix-length of Framed-IPv6-Prefix are conveyed in the corresponding part of INTERNAL_IP6_ADDRESS. |
|
100 |
Framed-IPv6-Pool |
The name of the IPv6 address pool used for local address assignment during IKEv2 remote-access tunnel setup. The value of this attribute overrides the local configured value in the ipsec-gw>local-address-assignment>ipv6 CLI context of the interface SAP. |
|
26.311.16 |
MS-MPPE-Send-Key |
This attribute along with [26.311.17] MS-MPPE-Recv-Key hold the Master Session Key (MSK) of the EAP authentication. It is expected in access-accept when EAP authentication succeed with specific EAP methods. |
|
26.311.17 |
MS-MPPE-Recv-Key |
This attribute along with [26.311.16] MS-MPPE-Send-Key hold the Master Session Key (MSK) of the EAP authentication. It is expected in access-accept when EAP authentication succeed with specific EAP methods. |
|
26.6527.9 |
Alc-Primary-Dns |
The IPv4 DNS server address to be assigned to an IKEv1/v2 remote-access tunnel client using configuration payload: INTERNAL_IP4_DNS. In case of IKEv2, up to four DNS server addresses can be returned to a client, including Alc-Primary-Dns, Alc-Secondary-Dns, Alc-Ipv6-Primary-Dns and Alc-Ipv6-Secondary-Dns. |
|
26.6527.10 |
Alc-Secondary-Dns |
The IPv4 DNS server address to be assigned to an IKEv2 remote-access tunnel client using IKEv2 configuration payload: INTERNAL_IP4_DNS. Up to four DNS server addresses can be returned to a client, including Alc-Primary-Dns, Alc-Secondary-Dns, Alc-Ipv6-Primary-Dns and Alc-Ipv6-Secondary-Dns. |
|
26.6527.61 |
Alc-IPsec-Serv-Id |
IPsec private service ID, used by IKEv1/v2 remote-access tunnel, referring to the preconfigured VPRN where the IPsec tunnel terminates (configure service vprn service-id). A default private service is used when this attribute is omitted (configure service vprn interface sap ipsec-gw default-secure-service). If the returned service ID does not exist/out-of limits or exists but not a VPRN service, the tunnel setup fails. |
|
26.6527.62 |
Alc-IPsec-Interface |
Private IPsec interface name, used by IKEv1/v2 remote-access tunnel, refers to a preconfigured private ipsec interface the IPsec tunnel terminates (config>service>vprn>interface ip-int-name tunnel). A default private interface is used when this attribute is omitted (config>service>ies/vprn>if>sap>ipsec-gw>default-secure-service service-id interface ip-int-name); the maximum length is 32 bytes; if the returned interface does not exist or exceeds the maximum length or exists but is not a private ipsec interface, the tunnel setup fails. |
|
26.6527.63 |
Alc-IPsec-Tunnel-Template-Id |
IPsec tunnel-template ID, used by IKEv1/v2 remote-access tunnel, refers to a preconfigured ipsec tunnel-template (configure ipsec tunnel-template ipsec template identifier). A default tunnel-template is used when this attribute is omitted (config>service>vprn>if>sap>ipsec-gw>default-tunnel-template template-id). If the returned template does not exist or exceeds the limits, the tunnel setup fails. |
|
26.6527.64 |
Alc-IPsec-SA-Lifetime |
IPsec phase2 SA lifetime in seconds, used by IKEv1/v2 remote-access tunnel. A preconfigured value is used when this attribute is omitted (configure ipsec ike-policy policy-id ipsec-lifetime ipsec-lifetime). Values outside the Limits are treated as a tunnel setup failure. |
|
26.6527.65 |
Alc-IPsec-SA-PFS-Group |
IPsec PFS group ID, used by IKEv1/v2 remote-access tunnel. The PFS group in ike-policy is used when this attribute is omitted (configure ipsec ike-policy policy-id pfs dh-group grp-id); if the returned value is not one of the allowed values, the tunnel setup fails. |
|
26.6527.66 |
Alc-IPsec-SA-Encr-Algorithm |
IPsec phase2 SA Encryption Algorithm, used by IKEv1/v2 remote-access tunnel. The esp-encryption-algorithm in ipsec-transform is used when this attribute is omitted (configure ipsec ipsec-transform transform-id esp-encryption-algorithm algo). This attribute must be used along with Alc-IPsec-SA-Auth-Algorithm, otherwise tunnel setup fails. Values different then the Limits are treated as a setup failure. |
|
26.6527.67 |
Alc-IPsec-SA-Auth-Algorithm |
IPsec phase2 SA Authentication Algorithm, used by IKEv1/v2 remote-access tunnel. The esp-auth-algorithm in ipsec-transform is used when this attribute is omitted (configure ipsec ipsec-transform transform-id esp-auth-algorithm algo). Values different than the Limits are treated as a tunnel setup failure. This attribute must be used along with Alc-IPsec-SA-Encr-Algorithm, otherwise tunnel setup fails. |
|
26.6527.68 |
Alc-IPsec-SA-Replay-Window |
IPsec anti-replay window size, used by IKEv1/v2 remote-access tunnel. The replay-window size in tunnel-template is used when this attribute is omitted (configure ipsec tunnel-template ipsec template identifier replay-window size). Values different than the Limits are treated as a tunnel setup failure. |
|
26.6527.105 |
Alc-Ipv6- Primary-Dns |
The IPv6 DNS server address to be assigned to an IKEv2 remote-access tunnel client using IKEv2 configuration payload: INTERNAL_IP6_DNS. Up to four DNS server addresses can be returned to a client, which could be any combination of Alc-Primary-Dns, Alc-Secondary-Dns, Alc-Ipv6-Primary-Dns and Alc-Ipv6-Secondary-Dns. |
|
26.6527.106 |
Alc-Ipv6- Secondary-Dns |
The IPv6 DNS server address to be assigned to an IKEv2 remote-access tunnel client using IKEv2 configuration payload: INTERNAL_IP6_DNS. Up to four DNS server addresses can be returned to a client, which could be any combination of Alc-Primary-Dns, Alc-Secondary-Dns, Alc-Ipv6-Primary-Dns and Alc-Ipv6-Secondary-Dns. |
|
26.6527.229 |
Alc-IPsec-Ts-Override |
The name of the ts-list to be used during IKEv2 tunnel setup. It overrides the CLI configured value using the CLI command ts-negotiation. |
|
26.6527.237 |
Alc-Subject-Key-Identifier |
The binary value of Subject Key Id in peer's certificate. The attribute can be included or excluded with configure ipsec radius-authentication-policy name include-radius-attribute client-cert-subject-key-id. |
|
241.26.6527.50 |
Alc-IPsec-LAA-IPv4-Svr-Name |
The local DHCPv4 server name that is used for IKEv2 remote-access tunnel local address assignment; The local-dhcp4-svr-name in address-source config is used when this attribute is omitted (configure service ies|vprn service-id interface ip-int-name sap sap-id ipsec-gw name local-address-assignment ipv4 address-source router router-instance dhcp-server local-dhcp4-svr-name pool dhcp4-server-pool [secondary-pool <[32 chars max]>]) |
|
241.26.6527.51 |
Alc-IPsec-LAA-IPv6-Svr-Name |
The local DHCPv6 server name that is used for IKEv2 remote-access tunnel local address assignment; The local-dhcp6-svr-name in address-source config is used when this attribute is omitted (configure service ies|vprn service-id interface ip-int-name sap sap-id ipsec-gw name local-address-assignment ipv6 address-source router router-instance dhcp-server local-dhcp6-svr-name pool dhcp6-server-pool [secondary-pool <[32 chars max]>]) |
|
241.26.6527.52 |
Alc-IPsec-LAA-IPv4-Svc-Name |
The service name where local DHCPv4 server that is used for IKEv2 remote-access tunnel local address assignment resides in; The router-instance in address-source config is used when this attribute is omitted (configure service ies|vprn service-id interface ip-int-name sap sap-id ipsec-gw name local-address-assignment ipv4 address-source router router-instance dhcp-server local-dhcp4-svr-name pool dhcp4-server-pool [secondary-pool <[32 chars max]>]) |
|
241.26.6527.53 |
Alc-IPsec-LAA-IPv6-Svc-Name |
The service name where local DHCPv6 server that is used for IKEv2 remote-access tunnel local address assignment resides in; The router-instance in address-source config is used when this attribute is omitted (configure service ies|vprn service-id interface ip-int-name sap sap-id ipsec-gw name local-address-assignment ipv6 address-source router router-instance dhcp-server local-dhcp6-svr-name pool dhcp6-server-pool [secondary-pool <[32 chars max]>]) |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
253 bytes |
Format depends on IDi format. For example: User-Name = ‟user1@domain1.com” |
|
2 |
User-Password |
string |
64 bytes |
— |
|
4 |
NAS-IP-Address |
ipaddr |
4 bytes |
For example: NAS-IP-Address=192.0.2.1 |
|
8 |
Framed-IP-Address |
ipaddr |
4 bytes |
For example: Framed-IP-Address = 192.168.10.100 |
|
9 |
Framed-IP-Netmask |
ipaddr |
4 bytes |
For example: Framed-IP-Netmask = 255.255.255.0 |
|
30 |
Called-Station-Id |
string |
253 bytes |
local gateway address of IKEv2 remote-access tunnel. For example: Called-Station-Id = ‟172.16.100.1” |
|
31 |
Calling-Station-Id |
string |
253 bytes |
peer-address:port For example: Calling-Station-Id = ‟192.168.5.100:500” |
|
32 |
NAS-Identifier |
string |
64 char |
For example: NAS-Identifier = "pe1" |
|
44 |
Acct-Session-Id |
string |
147 bytes |
local_gw_ip-remote_ip:remote_port-time_stamp For example: Acct-Session-Id = 172.16.100.1-192.168.5.100:500-1365016423 |
|
79 |
EAP-Message |
string |
253 bytes |
Binary string |
|
80 |
Message-Authenticator |
string |
16 bytes |
Binary string |
|
87 |
Nas-Port-Id |
string |
44 bytes |
SAP-ID For example: Nas-Port-Id = ‟tunnel-1.public:100” |
|
88 |
Framed-Pool |
string |
32 chars per pool name |
For example: Framed-Pool = "MyPoolname" |
|
97 |
Framed-IPv6-Prefix |
ipv6prefix |
max. 16 bytes for prefix + 1 byte for length |
For example: Framed-IPv6-Prefix = 2001:DB8:CAFE:1::100/128 |
|
100 |
Framed-IPv6-Pool |
string |
32 chars |
For example: Framed-IPv6-Pool = "MyV6Poolname" |
|
26.311.16 |
MS-MPPE-Send-Key |
string |
254 bytes |
Binary string |
|
26.311.17 |
MS-MPPE-Recv-Key |
string |
254 bytes |
Binary string |
|
26.6527.9 |
Alc-Primary-Dns |
ipaddr |
Up to 4 attributes (4B per attribute) |
For example: Alc-Primary-Dns = 192.168.1.1 |
|
26.6527.10 |
Alc-Secondary-Dns |
ipaddr |
Up to 4 attributes (4B per attribute) |
For example: Alc-Secondary-Dns = 192.168.2.1 |
|
26.6527.61 |
Alc-IPsec-Serv-Id |
integer |
2147483647 ID |
For example: Alc-IPsec-Serv-Id = 100 |
|
26.6527.62 |
Alc-IPsec-Interface |
string |
32 chars |
For example: Alc-IPsec-Interface = IPsec-Priv |
|
26.6527.63 |
Alc-IPsec-Tunnel-Template-Id |
integer |
1 to 2048 |
For example: Alc-IPsec-Tunnel-Template-Id = 200 |
|
26.6527.64 |
Alc-IPsec-SA-Lifetime |
integer |
[1200 to 172800] seconds |
For example: Alc-IPsec-SA-Lifetime = 2400 |
|
26.6527.65 |
Alc-IPsec-SA-PFS-Group |
integer |
[1 | 2 | 5 | 14 | 15 | 19 | 20 | 21] |
1=group1, 2=group2, 5=group5, and so on For example: Alc-IPsec-SA-PFS-Group = 2 |
|
26.6527.66 |
Alc-IPsec-SA-Encr-Algorithm |
integer |
[1 to 18] |
1=null, 2=des, 3=3des, 4=aes128, 5=aes192, 6=aes256, 7=aes128gcm8, 8=aes128gcm12, 9=aes128gcm16, 10=aes192gcm8, 11=aes192gcm12, 12=aes192gcm16, 13=aes256gcm8, 14=aes256gcm12, 15=aes256gcm16, 16=aes128gmac, 17=aes192gmac, 18=aes256gmac For example: Alc-IPsec-SA-Encr-Algorithm = 3 |
|
26.6527.67 |
Alc-IPsec-SA-Auth-Algorithm |
integer |
[1 to 8] |
1=null, 2=md5, 3=sha1, 4=sha256, 5=sha384, 6=sha512, 7=aesXcbc, 8=authencrypt For example: Alc-IPsec-SA-Auth-Algorithm = 3 |
|
26.6527.68 |
Alc-IPsec-SA-Replay-Window |
integer |
32|64|128|256|512 |
For example: Alc-IPsec-SA-Replay-Window = 128 |
|
26.6527.105 |
Alc-Ipv6- Primary-Dns |
ipv6addr |
Up to 4 attributes (16B per attribute) |
For example: Alc-Ipv6-Primary-Dns = 2001:DB8:1::1 |
|
26.6527.106 |
Alc-Ipv6- Secondary-Dns |
ipv6addr |
Up to 4 attributes (16B per attribute) |
For example: Alc-Ipv6-Secondary-Dns = 2001:DB8:2::1 |
|
26.6527.229 |
Alc-IPsec-Ts-Override |
string |
32 bytes |
For example: Alc-IPsec-Ts-Override="ikev2-ts-list-1" |
|
26.6527.237 |
Alc-Subject-Key-Identifier |
integer64 |
8 bytes |
The least significant 247 bytes of the Subject Key Id in peer's certificate. |
|
241.26.6527.50 |
Alc-IPsec-LAA-IPv4-Svr-Name |
string |
32 bytes |
For example: Alc-IPsec-LAA-IPv4-Svr-Name = "dhcpv4-svr-1" |
|
241.26.6527.51 |
Alc-IPsec-LAA-IPv6-Svr-Name |
string |
32 bytes |
For example: Alc-IPsec-LAA-IPv6-Svr-Name = "dhcpv6-svr-1" |
|
241.26.6527.52 |
Alc-IPsec-LAA-IPv4-Svc-Name |
string |
32 bytes |
For example: Alc-IPsec-LAA-IPv4-Svc-Name = "svc-1" |
|
241.26.6527.53 |
Alc-IPsec-LAA-IPv6-Svc-Name |
string |
32 bytes |
For example: Alc-IPsec-LAA-IPv6-Svc-Name = "svc-2" |
| Attribute ID | Attribute name | Access Request | Access Accept | Access challenge |
|---|---|---|---|---|
|
1 |
User-Name |
1 |
0-1 |
0 |
|
2 |
User-Password |
1 |
0 |
0 |
|
4 |
NAS-IP-Address |
0-1 |
0 |
0 |
|
8 |
Framed-IP- Address |
0 |
1 |
0 |
|
9 |
Framed-IP-Netmask |
0 |
0-1 |
0 |
|
30 |
Called-Station-Id |
0-1 |
0 |
0 |
|
31 |
Calling-Station-Id |
0-1 |
0 |
0 |
|
32 |
NAS-Identifier |
0-1 |
0 |
0 |
|
44 |
Acct-Session-Id |
1 |
0 |
0 |
|
79 |
EAP-Message |
0+ |
0+ |
0+ |
|
80 |
Message-Authenticator |
0-1 |
0-1 |
0-1 |
|
87 |
Nas-Port-Id |
0-1 |
0 |
0 |
|
88 |
Framed-Pool |
0 |
0-1 |
0 |
|
97 |
Framed-IPv6-Prefix |
0 |
0-1 |
0 |
|
100 |
Framed-IPv6-Pool |
0 |
0-1 |
0 |
|
26.311.16 |
MS-MPPE-Send-Key |
0 |
0-1 |
0 |
|
26.311.17 |
MS-MPPE-Recv-Key |
0 |
0-1 |
0 |
|
26.6527.9 |
Alc-Primary-Dns |
0 |
0+ |
0 |
|
26.6527.10 |
Alc-Secondary-Dns |
0 |
0+ |
0 |
|
26.6527.61 |
Alc-IPsec-Serv-Id |
0 |
0-1 |
0 |
|
26.6527.62 |
Alc-IPsec-Interface |
0 |
0-1 |
0 |
|
26.6527.63 |
Alc-IPsec-Tunnel-Template-Id |
0 |
0-1 |
0 |
|
26.6527.64 |
Alc-IPsec-SA-Lifetime |
0 |
0-1 |
0 |
|
26.6527.65 |
Alc-IPsec-SA-PFS-Group |
0 |
0-1 |
0 |
|
26.6527.66 |
Alc-IPsec-SA-Encr-Algorithm |
0 |
0-1 |
0 |
|
26.6527.67 |
Alc-IPsec-SA-Auth-Algorithm |
0 |
0-1 |
0 |
|
26.6527.68 |
Alc-IPsec-SA-Replay-Window |
0 |
0-1 |
0 |
|
26.6527.105 |
Alc-Ipv6- Primary-Dns |
0 |
0+ |
0 |
|
26.6527.106 |
Alc-Ipv6- Secondary-Dns |
0 |
0+ |
0 |
|
26.6527.229 |
Alc-IPsec-Ts-Override |
0 |
0-1 |
0 |
|
26.6527.237 |
Alc-Subject-Key-Identifier |
0-1 |
0 |
0 |
|
241.26.6527.50 |
Alc-IPsec-LAA-IPv4-Svr-Name |
0 |
0-1 |
0 |
|
241.26.6527.51 |
Alc-IPsec-LAA-IPv6-Svr-Name |
0 |
0-1 |
0 |
|
241.26.6527.52 |
Alc-IPsec-LAA-IPv4-Svc-Name |
0 |
0-1 |
0 |
|
241.26.6527.53 |
Alc-IPsec-LAA-IPv6-Svc-Name |
0 |
0-1 |
0 |
Application Assurance
| Attribute ID | Attribute name | Description |
|---|---|---|
|
8 |
Framed-IP-Address |
Mandatory IPv4 address attribute to create (CoA), delete (Delete) or audit (CoA) an IPv4 AA-transit subscriber. In case of an IPv4 host creation (CoA), if the host is already configured for another AA-transit subscriber with the same parent SAP, it is removed for this AA-subscriber and added to AA-subscriber, referred by the [26.6527.11] Alc-Subsc-ID-Str, in the CoA message. If the parent SAP, referred by the [87] NAS-Port-Id), is different, the host creation fails. An AA-transit subscriber can have up to 32 hosts (IPv4 or IPv6). A host cannot be added to a AA-transit subscriber if it is already configured for a static AA-transit subscriber with a different subscriber-ID. A Disconnect message sent with the last host of an AA-transit subscriber deletes the AA-transit subscriber. |
|
87 |
NAS-Port-Id |
A text string identifying the physical SAP or SDP serving the AA-transit subscriber (parent SAP or SDP). Mandatory attribute to create (CoA), delete (Disconnect) or audit (CoA) a transit-AA subscriber. |
|
97 |
Framed-IPv6-Prefix |
The IPv6 address for AA-Transit subscriber creation or removal (same use as [8] Framed-Ip-Address). |
|
26.6527.11 |
Alc-Subsc-ID-Str |
A mandatory attribute used in Access-Accept for AA subscriber creation (as in ESM host creation) or application-profile change (CoA) and for AA-transit subscriber creation (CoA), removal (Disconnect) or audit (CoA). Attribute values longer than the allowed string value are treated as setup failures. |
|
26.6527.45 |
Alc-App-Prof-Str |
Application Assurance for residential, business, or transit-AA subscribers is enabled through the assignment of an application profile as part of either enhanced subscriber management or static configuration. [26.6527.45] Alc-App-Prof-Str is a string that maps (configure subscriber-mgmt sub-ident-policy sub-ident-policy-name app-profile-map) to such an application profile (configure application-assurance group aa-group-id:partition-id policy app-profile app-profile-name). This attribute is used in access-accept (to assign an application profile during esm host creation) and CoA (to change the application profile of a AA-subscriber or to create transit AA-subscriber). Strings longer than the allowed maximum are treated as setup failures. Unreferenced strings (strings not mapping to an application profile) silently triggers a fallback to preconfigured default values if allowed. If no default value is preconfigured, the subscriber's application profile is silently disabled for the ESM AA-subscriber; in case of a transit AA-subscriber creation the CoA is rejected. The change of an application profile to one configured under a different group/partition or the modification of the application profile of a static AA-subscriber is not allowed and is treated as setup failures. |
|
26.6527.130 |
Alc-AA-Transit-IP |
Used to create (CoA), modify (CoA), delete (disconnect) or audit (CoA) an Application Assurance transit-ipv4 or v6-subscriber for business AA deployments and allows reporting and policy enforcement at IP address or prefix level within the parent SAP or spoke-SDP. Mandatory attributes to create(c), modify(m), delete(d) or audit(a) an AA-transit-ip-subscriber are: [8] Framed-IP-Address (c/m/d/a) or [97] Framed-IPv6-Prefix(c/m/d/a), [87] NAS-Port-Id(c/m/d/a), [26.6527.11] Alc-Subsc-ID-Str(c/m/d/a), [26.6527.45] Alc-App-Prof-Str(c/m/a) and [26.6527.130] Alc-AA-Transit-IP(c/m/d/a). The value of [26.6527.130] Alc-AA-Transit-IP must be an Integer, the value 1 (host) is used for host creation or deletion, 2 (audit-start) and 3 (audit-end) are used for the audit. |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
Optional text string used to customize the URL used for HTTP In-Browser Notification and automatically appended at the end of the notification script URL as an argument. This text string can also be configured in the http-redirect URL policy using macro substitution. The VSA string typically contains one or more argument names and values; there is no limit in the number of arguments besides the maximum length of the VSA. Each new argument must be preceded by ‟&” so as to be understood properly by a web server, the format for the Alc-AA-Sub-Http-Url-Param string must be for instance: "&arg1=value1" or "&arg1=value1&arg2=value2" This VSA string can be overwritten through CoA. |
|
26.6527.193 |
Alc-AA-App-Service-Options |
Used to apply Application Service Option (ASO) overrides. These attributes can only be applied if an app-profile is also or has previously been associated with the AA-sub (explicitly or by default), or else the override is rejected. An Access-Accept or CoA message can send one or more of these VSAs, with each VSA containing a string with the characteristic name and the value name pair. To provide multiple ASO attributes, the message can include multiple ASO VSAs, in addition to an App-profile VSA. The VSA string contains the characteristic name and the value name. The format for the Alc-AA-App-Service-Options string must be "char=value". An equal sign is used as the delimiter between characteristic string and value string. Each name can have any character including spaces, except ‛=’. Everything before the '=' is interpreted as the character string and everything after the '=' is interpreted as the value string. One ASO char=value pair is supported per VSA, If an ASO char=value pair is not found in a VSA, the message is rejected. If an ASO char=value does not match a provisioned ASO for the group/partition for that subscriber, the message is rejected. An app profile is a defined set of ASO values. App-profiles interact with ASO overrides in this way:
If there are multiple ASO VSAs for the same characteristic in the CoA, the last one takes effect. |
|
241.26.6527.26 |
Alc-Aa-Sub-Scope |
This attribute is used to define the scope of the [26.6527.45] Alc-App-Prof-Str attribute and the related [26.6527.193] Alc-AA-App-Service-Options attributes to affect either the subscriber (all hosts) or to affect only the specific host IP addresses used by a unique MAC address. The absence of this attribute defaults to using subscriber scope. |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
8 |
Framed-IP-Address |
ipaddr |
4 bytes |
# Example: ipv4 transit-AA-subscriber 10.0.200.1 Framed-IP-Address = ‟10.0.200.1” |
|
87 |
NAS-Port-Id |
string |
253 bytes |
# Depends on the parent port type # Example for sap NAS-Port-Id = 1/1/4:501.1001 # Example for spoke-sdp NAS-Port-Id = 4:100 |
|
97 |
Framed-IPv6-Prefix |
ipv6prefix |
max. 16 bytes for prefix + 1 byte for length |
# Example: Framed-IPv6-Prefix = 2001:db8:cafe:1::/64 |
|
26.6527.11 |
Alc-Subsc-ID-Str |
string |
32 chars |
# Example: Alc-Subsc-ID-Str = transit-sub-radius1 |
|
26.6527.45 |
Alc-App-Prof-Str |
string |
16 bytes |
# Example: Alc-App-Prof-Str = MyAppProfile |
|
26.6527.130 |
Alc-AA-Transit-IP |
integer |
4 bytes |
1=host, 2=audit-start, 3=audit-end For example: # CoA create AA transit subscriber on SAP 4/1/1, IP address 10.0.200.1 Alc-AA-Transit-IP = host NAS-Port-ID = 4/1/1 framed-ip-address = 10.0.200.1 Alc-Subsc-ID-Str = transit-sub-radius1 Alc-App-Prof-Str = MyAppProfile |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
string |
247 chars (DSM) 32 chars (ESM) |
# For example: Alc-AA-Sub-Http-Url-Param = "&Provider=ISPname&Location=Station21" |
|
26.6527.193 |
Alc-AA-App-Service-Options |
string |
65 bytes per VSA (char. 32bytes + 1 byte + value 32bytes) 32 VSAs per message |
Format: characteristic=value, # For example: Alc-AA-App- Service-Options = ‟ServiceTier=Bronze” |
|
241.26.6527.26 |
Alc-Aa-Sub-Scope |
integer |
4 bytes |
1=subscriber, 2=mac For example: To set the scope of the application profile to subscriber hosts with the same MAC address: Alc-Aa-Sub-Scope = 2 To set the scope of the application profile to all subscriber hosts belonging to the same ESM subscriber: Alc-Aa-Sub-Scope = 1 |
| Attribute ID | Attribute name | Access Request | Access Accept | CoA request |
|---|---|---|---|---|
|
8 |
Framed-IP-Address |
0 |
0 |
0-1 |
|
87 |
NAS-Port-Id |
0 |
0 |
0-1 |
|
97 |
Framed-IPv6-Prefix |
0 |
0 |
0-1 |
|
26.6527.11 |
Alc-Subsc-ID-Str |
0 |
0-1 |
0-1 |
|
26.6527.45 |
Alc-App-Prof-Str |
0 |
0-1 |
0-1 |
|
26.6527.130 |
Alc-AA-Transit-IP |
0 |
0 |
0-1 |
|
26.6527.182 |
Alc-AA-Sub-Http-Url-Param |
0 |
0-1 |
0-1 |
|
26.6527.193 |
Alc-AA-App-Service-Options |
0 |
0+ |
0+ |
|
241.26.6527.26 |
Alc-Aa-Sub-Scope |
0 |
0-1 |
0-1 |
CLI user authentication and authorization
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
The name of user requesting user-Authentication, Authorization, Accounting (AAA). Usernames longer the allowed maximum limit are treated as an authentication failure. |
|
2 |
User-Password |
The password of user requesting user-Authentication, Authorization, Accounting and always encrypted in a fixed length. |
|
4 |
NAS-IP-Address |
The identifying IP address of the NAS requesting the Authentication or Accounting. Included when the RADIUS server is reachable using IPv4. The address is determined by the routing instance through which the RADIUS server can be reached: ‟Management”— The active IPv4 address in the Boot Options File (bof address ipv4-address). ‟Base” — The IPv4 address of the system interface (configure router interface system address address). The address can be overwritten with the configured source-address (configure system security source-address application radius ip-int-name | ip-address). |
|
18 |
Reply-Message |
The attribute received in the Access-Challenge message for challenge-response interactive authentication. The content of the Reply-Message attribute is displayed to the user. The user is prompted for a response. |
|
24 |
State |
The attribute received in the Access-Challenge message for challenge-response interactive authentication and sent unmodified in the new Access-Request |
|
27 |
Session-Timeout |
The attribute received in the Access-Challenge message for challenge-response interactive authentication. The maximum number of seconds in which the user should provide the response. After this time, the prompt is terminated. |
|
28 |
Idle-Timeout |
The attribute received in the Access-Challenge message for challenge-response interactive authentication. The number of seconds after which the prompt is terminated when no user activity is detected. |
|
31 |
Calling-Station-Id |
The IP address (coded in hex) from the user that requests Authentication, Authorization, Accounting or ‟CONSOLE” when requesting access from the serial port (Console). |
|
44 |
Acct-Session-Id |
A unique, without meaning, generated number per authenticated user reported in all accounting messages and used to correlate users CLI commands (accounting data) from the same user. |
|
61 |
NAS-Port-Type |
Mandatory included as type Virtual (5) for Telnet/SSH or Async (0) for Console. |
|
95 |
NAS-IPv6-Address |
The identifying IP address of the NAS requesting the Authentication or Accounting. Included when the RADIUS server is reachable using IPv6. The address is determined by the routing instance through which the RADIUS server can be reached: ‟Management” — The active IPv6 address in the Boot Options File (bof address ipv6-address) ‟Base” — The IPv6 address of the system interface (configure router interface system ipv6 address ipv6-address). The address can be overwritten with the configured ipv6-source-address (configure system security source-address application6 radius ipv6-address). |
|
26.6527.1 |
Timetra-Access |
Specifies the router management access methods for the user: ftp, console (Bluetooth, console port CLI, SCP/SFTP, SSH CLI, and Telnet CLI), netconf, grpc, scp-sftp, console-port-cli, ssh-cli, telnet-cli, and bluetooth. Multiple access methods can be specified by adding the value of the access methods to allow. |
|
26.6527.2 |
Timetra-Home-Directory |
Specifies the local home directory for the user for console and FTP access and is enforced with attribute [26.6527.3] Timetra-Restrict-To-Home. The home directory is not enforced if [26.6527.3] Timetra-Restrict-To-Home is omitted. The local home directory is entered from the moment when the authenticated user enters the file CLI command. |
|
26.6527.3 |
Timetra-Restrict-To-Home |
When the value is true the user is not allowed to navigate to directories above his home directory for file access. The home-directory is specified in [26.6527.2] Timetra-Home-Directory and is root if [26.6527.2] Timetra-Home-Directory is omitted. |
|
26.6527.4 |
Timetra-Profile |
The user profiles that the user has access to and refers to preconfigured user-profile-name's (configure system security profile user-profile-name). These preconfigured profiles hold a default-action, a match command-string and an action. Unreferenced profiles names are silently ignored. If the maximum number of profile strings is violated, or if a string is too long, processing the input is stopped but authorization continues and too long profile string (and all strings followed by that) are ignored. Each user can have multiple profiles and the order is important. The first user profile has highest precedence, followed by the second and so on. Note that for each authenticated RADIUS user a temporary profile with name [1]User-Name is always created (show system security profile) and executed as last profile. This temporary profile is built from the mandatory attribute [26.6527.5]Timetra-Default-Action and optional attributes [26.6527.6] Timetra-Cmd, [26.6527.7] Timetra-Action. |
|
26.6527.5 |
Timetra-Default-Action |
Specifies the default action (permit-all, deny-all, read-only-all, or none) when the user has entered a command and none of the command-strings in [26.6527.6] Timetra-Cmd resulted in a match condition. The attribute is mandatory and required even if the [36.6527.6] Timetra-Cmd is not used. |
|
26.6527.6 |
Timetra-Cmd |
Command string, subtree command string, or a list of command strings as scope for the match condition for user authorization. Multiple command strings in the same attribute are delimited with the ‟;” character. Additional command strings are encoded in multiple attributes. If the maximum number of command strings is violated, or if a string is too long, processing the input is stopped but authorization continues, therefore, if the RADIUS server is configured to have five command strings of which the third is too long, only the first two entries are used and the rest are ignored. Each [26.6527.6] Timetra-Cmd attribute is followed in sequence by a [26.6527.7] Timetra-Action. (A missing Timetra-Action results in a deny.) Note that for each authenticated RADIUS user, a temporary profile with name [1]User-Name is always created (show system security profile) and executed as last profile. This temporary profile is built from the mandatory attribute [26.6527.5] Timetra-Default-Action and optional attributes [26.6527.6] Timetra-Cmd, [26.6527.7] Timetra-Action. |
|
26.6527.7 |
Timetra-Action |
Action to be used in case a user's command matches the commands specified in [26.6527.6] Timetra-Cmd attribute. Action deny is used if the attribute is omitted and the [26.6527.5] Timetra-Default-Action is used when no match is found. Note the following:
|
|
26.6527.8 |
Timetra-Exec-File |
Specifies the file that is executed whenever the user is successfully authenticated. |
| 26.6527.245 | Timetra-Save-When-Restricted | When the value is true, save configurations even when the user is restricted to home ([26.6527.3] Timetra-Restrict-To-Home = true). When the value is false, the configuration save fails if the target directory is not within the users home directory ([26.6527.2] Timetra-Home-Directory). |
| 26.6527.246 | Timetra-NETCONF-Default-Action |
This VSA specifies the default action (permit-all or deny-all) for NETCONF base operations that are not included in the [26.6527.247] Timetra-NETCONF-BaseOp VSA, or when no [26.6527.247] Timetra-NETCONF-BaseOp VSA is specified. The attribute must be included when [26.6527.247] Timetra-NETCONF-BaseOp is included. If no [26.6527.247] Timetra-NETCONF-BaseOp and [26.6527.246] Timetra-NETCONF-Default-Action VSA is received for a user, the default authorization uses the radius-default template which by default uses profile "default". |
| 26.6527.247 | Timetra-NETCONF-BaseOp |
This VSA specifies a semicolon separated list of NETCONF base operations that are:
|
| 26.6527.248 | Timetra-gRPC-Default-Action |
This VSA specifies the default action (permit-all or deny-all) for gRPC RPCs that are not included in the [26.6527.249] Timetra-gRPC-RPC VSA, or when no [26.6527.249] Timetra-gRPC-RPC VSA is specified. The attribute must be included when [26.6527.249] Timetra-gRPC-RPC is included. If no [26.6527.249] Timetra-gRPC-RPC and [26.6527.248] Timetra-gRPC-Default-Action VSA is received for a user, the default authorization uses the radius-default template which by default uses profile "default". |
| 26.6527.249 | Timetra-gRPC-RPC |
This VSA specifies a semicolon separated list of gRPC RPCs that are:
|
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
32 chars |
For example: User-Name = ‟admin” |
|
2 |
User-Password |
string |
16 chars fixed |
Encrypted password For example: User-Password 4ec1b7bea6f2892fa466b461c6accc00 |
|
4 |
NAS-IP-Address |
ipaddr |
4 bytes |
# ip-address For example: NAS-IP-Address = ‟192.0.2.1” |
|
18 |
Reply-Message |
string |
— |
For example: Reply-Message = ‟Please enter your response for challenge: 4598 2441 ?” |
|
24 |
State |
string |
— |
For example: State = ‟Challenge-Response” |
|
27 |
Session-Timeout |
integer |
— |
For example: Session-Timeout = 180 |
|
28 |
Idle-Timeout |
integer |
— |
For example: Idle-Timeout = 90 |
|
31 |
Calling-Station-Id |
string |
64 bytes |
# users ip address or ‟CONSOLE” For example: Calling-Station-Id = ‟192.0.2.2” or Calling-Station-Id = ‟2001:db8::2” |
|
44 |
Acct-Session-Id |
string |
22 bytes |
For example: Acct-Session-Id = ‟2128463592102512113409” |
|
61 |
NAS-Port-Type |
integer |
4 bytes value 5 fixed |
Fixed set to value Virtual (5) for SSH/Telnet and Async (0) for console. For example: NAS-Port-Type 00000005 |
|
95 |
NAS-IPv6-Address |
ipv6addr |
16 bytes |
# ipv6 address For example: NAS-IPv6-Address = 2001:db8::1 |
|
26.6527.1 |
Timetra-Access |
integer |
1..511 |
The sum of the values of the allowed router management access methods: 1=ftp 2=console (Bluetooth, console port CLI, SCP/SFTP, SSH CLI, and Telnet CLI) 4=netconf 8=grpc 16=scp-sftp 32=console-port-cli 64=ssh-cli 128=telnet-cli 256=bluetooth For example: Allow console port CLI and SSH CLI access: Timetra-Access = 96 Allow console port CLI, SSH CLI and NETCONF access: Timetra-Access = 100 Allow gRPC and NETCONF access (deny CLI access): Timetra-Access = 12 |
|
26.6527.2 |
Timetra-Home-Directory |
string |
190 chars |
For example: Timetra-Home-Directory = cf3:/users/user1/ |
|
26.6527.3 |
Timetra-Restrict-To-Home |
integer |
1,2 (false, true) |
1=true, 2=false For example: Timetra-Restrict-To-Home = true |
|
26.6527.4 |
Timetra-Profile |
string |
16 attributes 32 chars/attribute |
For example: Timetra-Profile += administrative1 Timetra-Profile += administrative2 |
|
26.6527.5 |
Timetra-Default-Action |
integer |
1,2,3,4 |
1=permit-all, 2=deny-all, 3=none, 4=read-only-all For example: Timetra-Default-Action = none |
|
26.6527.6 |
Timetra-Cmd |
string |
25 attributes 247 chars/attribute |
For example: Timetra-Cmd += configure router isis;show subscriber-mgmt sub-profile Timetra-Cmd += show router |
|
26.6527.7 |
Timetra-Action |
integer |
25 attributes |
# 1=permit, 2=deny For example: Timetra-Action = permit |
|
26.6527.8 |
Timetra-Exec-File |
string |
200 chars |
Timetra-Exec-File = <local-url>|<remote-url> # local-url : <cflash-id>/][<file-path> # remote-url : {ftp://|tftp://}<login>:<pswd>@<remote-locn>/<file-path> For example: Timetra-Exec-File = cf3:/users/user1/MyScript Timetra-Exec-File = ftp://login:pswd@192.168.0.10/home/user1/MyScript.cfg |
| 26.6527.245 | Timetra-Save-When-Restricted | integer | 1,2 (false, true) | 1=true, 2=false For example: Timetra-Save-When-Restricted = true |
| 26.6527.246 | Timetra-NETCONF-Default-Action | integer | 1, 2 (permit-all, deny-all) |
1=permit-all, 2=deny-all For example: Timetra-NETCONF-Default-Action = deny-all |
| 26.6527.247 | Timetra-NETCONF-BaseOp | string |
16 attributes 247 chars / attribute |
Semicolon separated list of NETCONF base operations. When multiple attributes are present, the lists are combined. Supported base operations: action; cancel-commit; close-session; commit; copy-config; create-subscription; delete-config; discard-changes; edit-config; get; get-config; get-data; get-schema; kill-session; lock; validate For example: Timetra-NETCONF-BaseOp += “close-session;commit;discard-changes” Timetra-NETCONF-BaseOp += “edit-config;get-config;lock;validate” |
| 26.6527.248 | Timetra-gRPC-Default-Action | integer | 1, 2 (permit-all, deny-all) |
1=permit-all, 2=deny-all For example: Timetra-gRPC-Default-Action = deny-all |
| 26.6527.249 | Timetra-gRPC-RPC | string |
25 attributes 247 chars / attribute |
Semicolon separated list of gRPC RPCs. When multiple attributes are present, the lists are combined. Supported RPCs: gnmi-capabilities; gnmi-get; gnmi-set; gnmi-subscribe; gnoi-cert-mgmt-cangenerate; gnoi-cert-mgmt-getcert; gnoi-cert-mgmt-install; gnoi-cert-mgmt-revoke; gnoi-cert-mgmt-rotate; gnoi-file-get; gnoi-file-put; gnoi-file-remove; gnoi-file-stat; gnoi-file-transfertoremote; gnoi-system-cancelreboot; gnoi-system-ping; gnoi-system-reboot; gnoi-system-rebootstatus; gnoi-system-setpackage; gnoi-system-switchcontrolprocessor; gnoi-system-time; gnoi-system-traceroute; md-cli-session; rib-api-getversion; rib-api-modify For example: Timetra-gRPC-RPC += “gnmi-capabilities;gnmi-get” Timetra-gRPC-RPC += “gnmi-set” |
| Attribute ID | Attribute name | Access Request 1 |
Access-challenge 1 |
Access Request 2 |
Access-Accept 1 or 2 |
|---|---|---|---|---|---|
|
1 |
User-Name |
1 |
0 |
1 |
0 |
|
2 |
User-Password |
1 |
0 |
1 |
0 |
|
4 |
NAS-IP-Address |
0-1 |
0 |
0-1 |
0 |
|
18 |
Reply-Message |
0 |
1+ |
0 |
0 |
|
24 |
State |
0 |
0-1 |
0-1 |
0 |
|
27 |
Session-Timeout |
0 |
0-1 |
0 |
0 |
|
28 |
Idle-Timeout |
0 |
0-1 |
0 |
0 |
|
31 |
Calling-Station-Id |
1 |
0 |
1 |
0 |
|
44 |
Acct-Session-Id |
0 |
0 |
0 |
0 |
|
61 |
NAS-Port-Type |
1 |
0 |
1 |
0 |
|
95 |
NAS-IPv6-Address |
0-1 |
0 |
0-1 |
0 |
|
26.6527.1 |
Timetra-Access |
0 |
0 |
0 |
1 |
|
26.6527.2 |
Timetra-Home-Directory |
0 |
0 |
0 |
1 |
|
26.6527.3 |
Timetra-Restrict-To-Home |
0 |
0 |
0 |
1 |
|
26.6527.4 |
Timetra-Profile |
0 |
0 |
0 |
0+ |
|
26.6527.5 |
Timetra-Default-Action |
0 |
0 |
0 |
1 |
|
26.6527.6 |
Timetra-Cmd |
0 |
0 |
0 |
0+ |
|
26.6527.7 |
Timetra-Action |
0 |
0 |
0 |
0-1 |
|
26.6527.8 |
Timetra-Exec-File |
0 |
0 |
0 |
0-1 |
| 26.6527.245 | Timetra-Save-When-Restricted | 0 | 0 | 0 | 0-1 |
| 26.6527.246 | Timetra-NETCONF-Default-Action | 0 | 0 | 0 | 0-1 |
| 26.6527.247 | Timetra-NETCONF-BaseOp | 0 | 0 | 0 | 0+ |
| 26.6527.248 | Timetra-gRPC-Default-Action | 0 | 0 | 0 | 0-1 |
| 26.6527.249 | Timetra-gRPC-RPC | 0 | 0 | 0 | 0+ |
AAA route downloader
| Attribute ID | Attribute name | Description |
|---|---|---|
|
1 |
User-Name |
Maps to configure aaa route-downloader name base-user-name user-name were the base-user-name sets the prefix for the username that shall be used in access requests. The actual name used is a concatenation of this string, a ‟ -” (hyphen) character and a monotonically increasing integer. Consecutive Access-Requests with incrementing User-Name are repeated until the aaa route download application receives an Access-Reject. Default is system-name. |
|
2 |
User-Password |
Maps to configure aaa route-downloader name password password in the RADIUS-Access request. Default is empty string. |
|
22 |
Framed-Route |
The RADIUS route-download application periodically sends a RADIUS Access-Request message to the RADIUS server to request that IPv4 or IPv6 routes be downloaded. The RADIUS server responds with an Access-Accept message and downloads the configured IPv4/IPv6 routes. When the download operation is complete, the route-download application installs the IPv4 or IPv6 routes in the routing table as black-hole routes with protocol periodic and with fixed preference 255. A default metric (configure aaa route-downloader name default-metric [0 to 254]) is installed when the metric value is omitted in the formatted attribute. A default tag (configure aaa route-downloader name default-tag [0 to 4294967295]) is installed when the tag value is omitted in the formatted attribute. The complete RADIUS Access Accept is ignored (fails to parse the route) if at least one route has the wrong format. Only the individual route is silently ignored (not seen as a process download failure) if the formatted VPRN service or service-name is invalid. Routes no longer present in the download are removed from the routing table and new routes are added. The same routes are not replaced. Routes with different tags or metrics are seen as new routes. If the AAA server responds with an Access-Reject for the first username, then all routes are removed from the routing table (implicit empty route-download table). The route-download application accepts downloaded IPv4 routes in either [22] Framed-Route or [26.9.1] Cisco-AVpair attribute format. |
|
99 |
Framed-IPv6-Route |
See description [22] Framed-Route. The route-download application accepts downloaded IPv6 routes only in [99] Framed-IPv6-Route format. |
|
26.9.1 |
cisco-av-pair |
See description [22] Framed-Route |
| Attribute ID | Attribute name | Type | Limits | SR OS format |
|---|---|---|---|---|
|
1 |
User-Name |
string |
32 chars base-user-name |
For example: # base-user-name download-pool USER NAME [1] 16 download-pool-1 |
|
2 |
User-Password |
string |
max. 32 chars |
Encrypted password For example: User-Password 4ec1b7bea6f2892fa466b461c6accc00 |
|
22 |
Framed-Route |
string |
253 bytes 200.000 attributes |
Format [vrf {vpn-name | vpn-serviceid}] {IP} prefix-mask {null0 | null 0 | black-hole} [metric] [tag tag-value] The vpn-name should not contain blank spaces as this would result in a parsing error and a drop of the corresponding prefix. #The prefix-mask could be in any form as: prefix/length, prefix mask or prefix (the mask is derived from the IP class of the prefix). For example: # A base route 172.16.20.0/24 with different formats, metric and tags Framed-Route = 172.16.20.0/24 black-hole tag 1, Framed-Route = 172.16.20.0 255.255.255.0 null 0 20 tag 1, Framed-Route = 172.16.20.0 null0 22255 tag 33, For example: # A vrf route 172.16.21.0/24 with different formats, metric and tags Framed-Route = vrf 6000 172.16.21.0 null0 254 tag 4, Framed-Route = vrf ws/rt-custmomerx 172.16.21.0 null0 254 tag 5, |
|
99 |
Framed-IPv6-Route |
string |
253 bytes 200.000 attributes |
Format [vrf {vpn-name | vpn-serviceid}] {IP} prefix-mask {null0 | null 0 | black-hole} [metric] [tag tag-value] The vpn-name should not contain blank spaces as this would result in a parsing error and a drop of the corresponding prefix. #The prefix-mask could be in any form as: prefix/length, prefix mask or prefix (the mask is derived from the IP class of the prefix). For example: Framed-IPv6-Route += 2001:db8:0:1::/64 null0, Framed-IPv6-Route += vrf ws/rt-custmomerx 2001:db8:0:0:1::/96 null 0 10 tag 4294967295, Framed-IPv6-Route += vrf 6000 2001:db8:1::/48 black-hole 0 tag 4294967295,t |
|
26.9.1 |
cisco-av-pair |
string |
253 bytes 200.000 attributes |
Format [vrf {vpn-name | vpn-serviceid}] {IP} prefix-mask {null0 | null 0 | black-hole} [metric] [tag tag-value] The vpn-name should not contain blank spaces as this would result in a parsing error and a drop of the corresponding prefix. #The prefix-mask could be in any form as: prefix/length, prefix mask or prefix (the mask is derived from the IP class of the prefix). For example: # A base route 192.168.5.0/24 without metric and tags (use defaults) cisco-avpair += ip:route=192.168.0.0 255.255.255.0 null0, For example: # A vrf route 192.168.1.0/24 with different formats, metric and tags cisco-avpair += ip:route=vrf 6000 192.168.1.0/24 null 0 0 tag 62, cisco-avpair += ip:route=vrf ws/rt-custmomerx 192.168.1.0/24 null 0 200 tag 63 |
| Attribute ID | Attribute name | Access Request | Access Accept |
|---|---|---|---|
|
1 |
User-Name |
1 |
0 |
|
2 |
User-Password |
1 |
0 |
|
22 |
Framed-Route |
0 |
0+ |
|
99 |
Framed-IPv6-Route |
0 |
0+ |
|
26.9.1 |
cisco-av-pair |
0 |
0+ |