ANYsec
Nokia ANYsec uses the IEEE802.1AE (MACsec) encryption engine in the Nokia FP5 chipset to encrypt MPLS payloads, while leaving the MPLS labels in clear and unauthenticated. After the MPLS payload is encrypted, the MPLS packet is switched through an MPLS network and eventually is decrypted using the encryption engine at the terminating FP5-enabled PE. Having the MPLS labels in clear and unauthenticated allows any LSR router to switch the ANYsec packets from the ILER ANYsec PE to the ELER ANYsec PE. Any LSR router, including third-party routers, can manipulate the MPLS header. This includes performing label actions such as label swap, pop, and push.
The following figure shows the ANYsec MPLS encryption and decryption process.
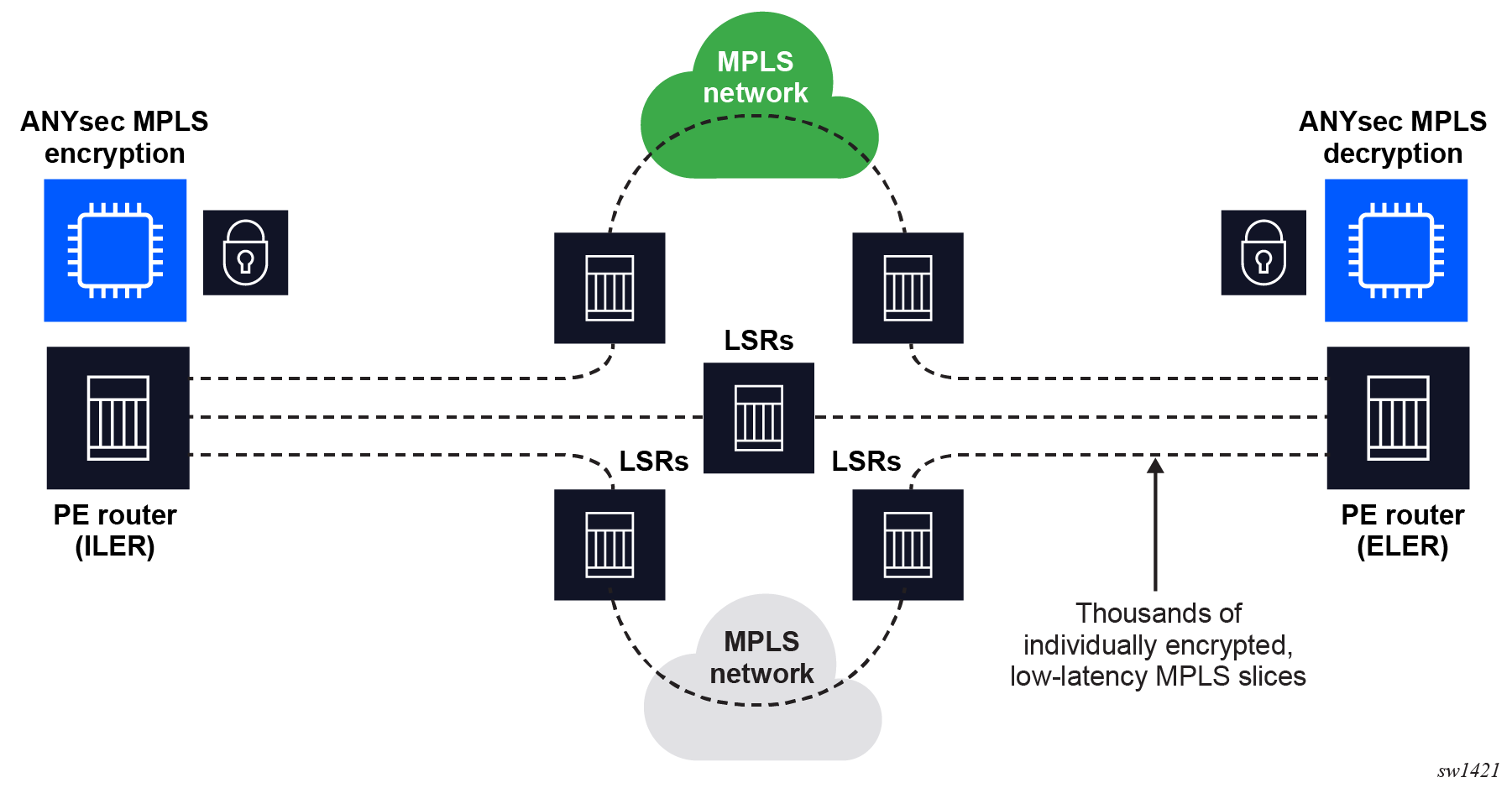
ANYsec overview
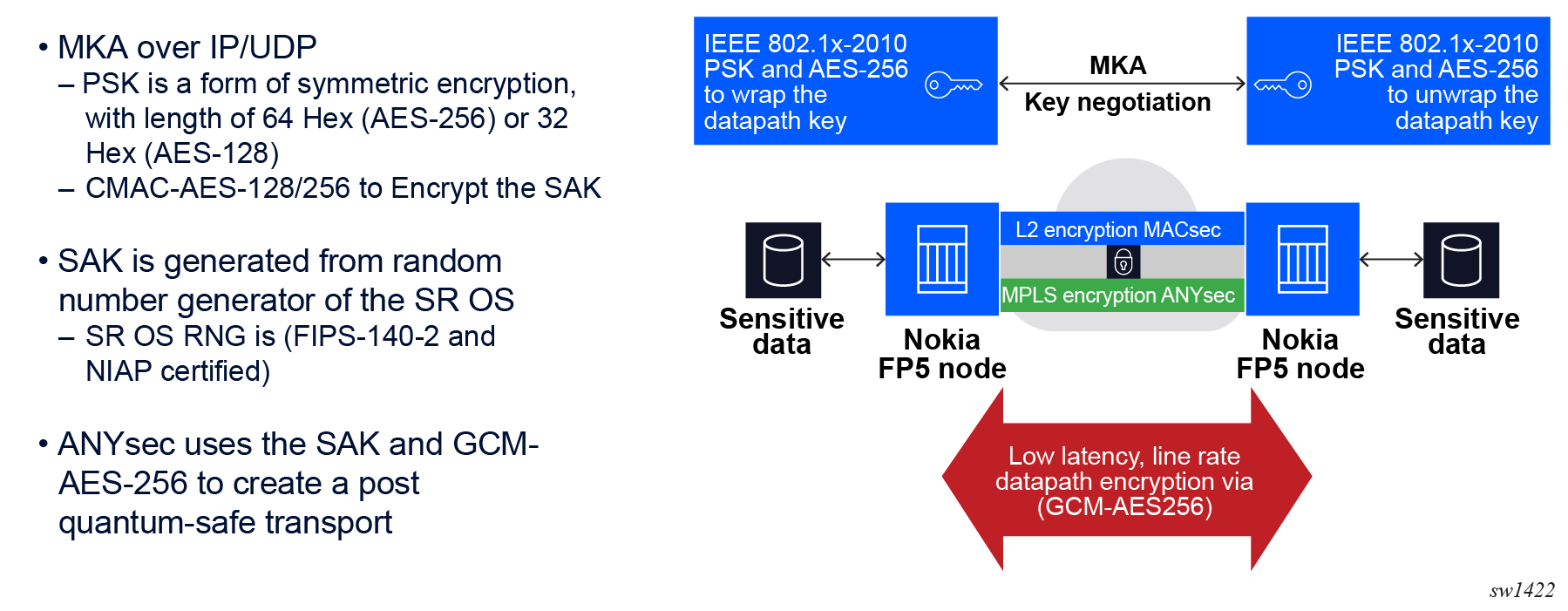
Nokia ANYsec uses IEEE802.1AE (MACsec) as its datapath encryption engine and IEEE802.1x (dot1x/MKA) as its control plane signaling protocol. ANYsec uses the user-configured MACsec connectivity-association (CA) with a set of pre-shared keys (PSKs), the same way MACsec does, to negotiate datapath keys between two or more peers.
The following is the basic high-level overview of the SR OS ANYsec encryption process.
- The user configures the ANYsec-specific CA, which supports the exclusive use of the
CA with ANYsec
encryption.
configure macsec connectivity-association anysec true - The MACsec key agreement (MKA) key server generates the datapath security
association keys (SAKs) locally on the SR OS.
The user configures the key-server selection priority using the following
command.
configure macsec connectivity-association static-cak mka-key-server-priority - The MKA uses CMAC-AES-128/256 to encrypt the SAKs using PSK and distributes the SAKs.
- ANYsec modifies the MKA for transport over IP/UDP (described in more detail in later topics). MKA distributes the SAKs between peers, and ANYsec uses the SAKs to encrypt the MPLS payload via the IEEE802.1AE encryption engine.
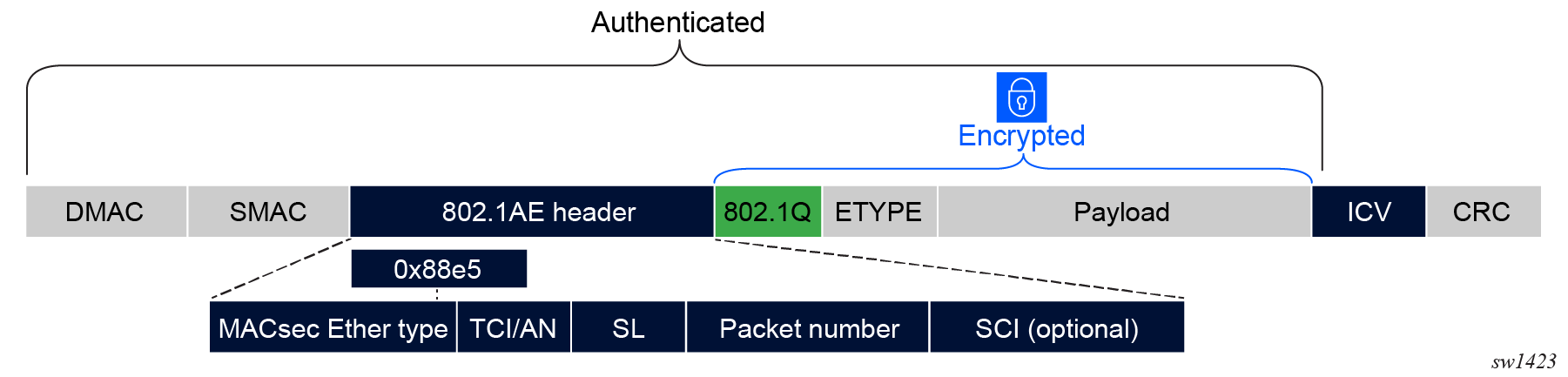
ANYsec packet format
ANYsec MPLS provides packet encryption formats that are different from the MACsec packet formats.
The following figure shows that the MACsec WAN mode leaves the dot1q VLANs in clear and unauthenticated, so the packets can be manipulated by the VLAN switched network.
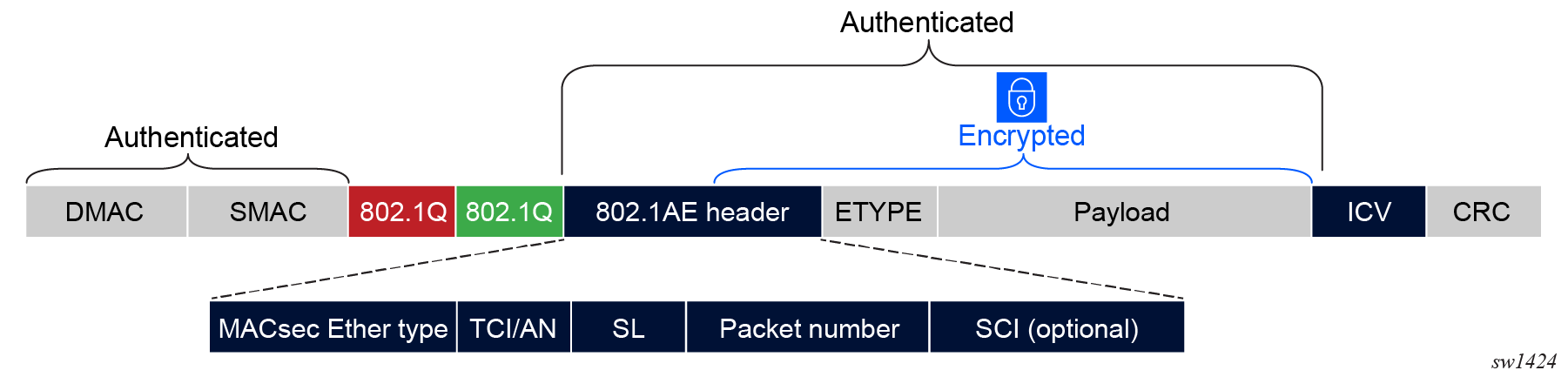
With ANYsec, the entire MPLS label stack is in clear and unauthenticated. This allows the LSR routers to manipulate the MPLS label stack while the system encrypts and authenticates the payload. The following figure shows ANYsec MPLS packet authentication.
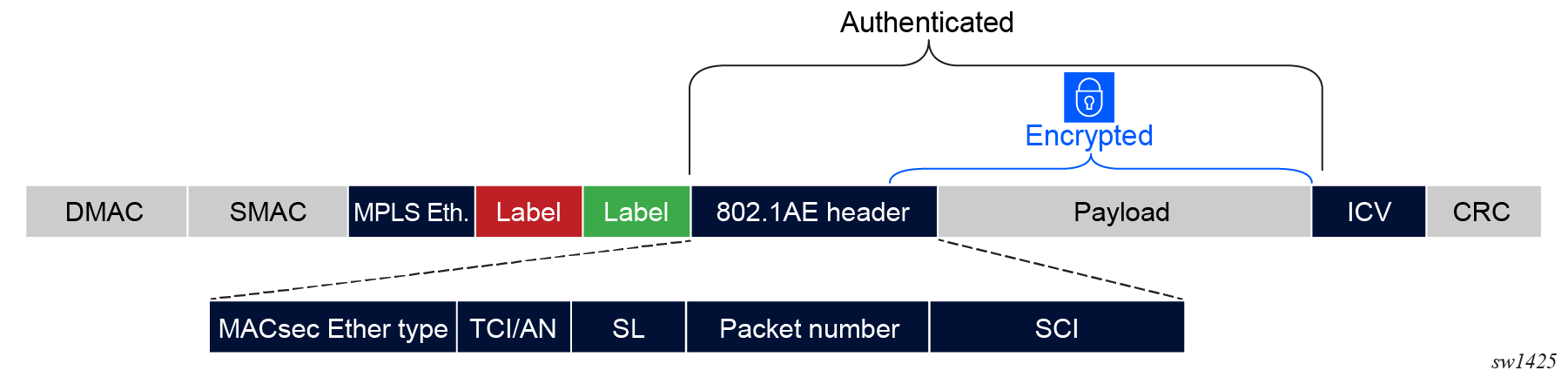
ANYsec encryption
Nokia FP5 ANYsec uses the IEEE802.1AE (MACsec) encryption engine to encrypt multiple layers of OSI. For example, the same encryption engine can encrypt at Layer 2, MACsec, or Layer 2.5 MPLS ANYsec.
ANYsec encryption supports MACsec encryption algorithms, MPLS protocols, and per-flow encryption.
Encryption algorithms
ANYsec uses the MACsec encryption engine and therefore supports all the MACsec encryption algorithms, including the following:
- CMAC-AES-128/AES-256 for pre-shared key encryption used by the MKA protocol
- GCM-AES 128/256 for datapath encryption, using extended packet number (XPN)
MPLS protocol support
ANYsec currently encrypts LSPs that are signaled by the following Segment Routing (SR) protocols:
- SR-ISIS
- SR-OSPF
- SR-OSPF3
Currently ANYsec encrypts the service label, entropy label, and entropy-indication label.
per-flow encryption
configure macsec connectivity-association static-cak mka-key-server-priorityANYsec uses the Layer 3 content addressable memory (CAM) build in the Nokia FP5 chipset to match the MPLS label stack to the appropriate SAK. When a SAK for an LSP is distributed via MKA, ANYsec downloads the LSP's label stack to the Layer 3 CAM and associates it with the corresponding SAK, which it downloads to the SA lookup table.
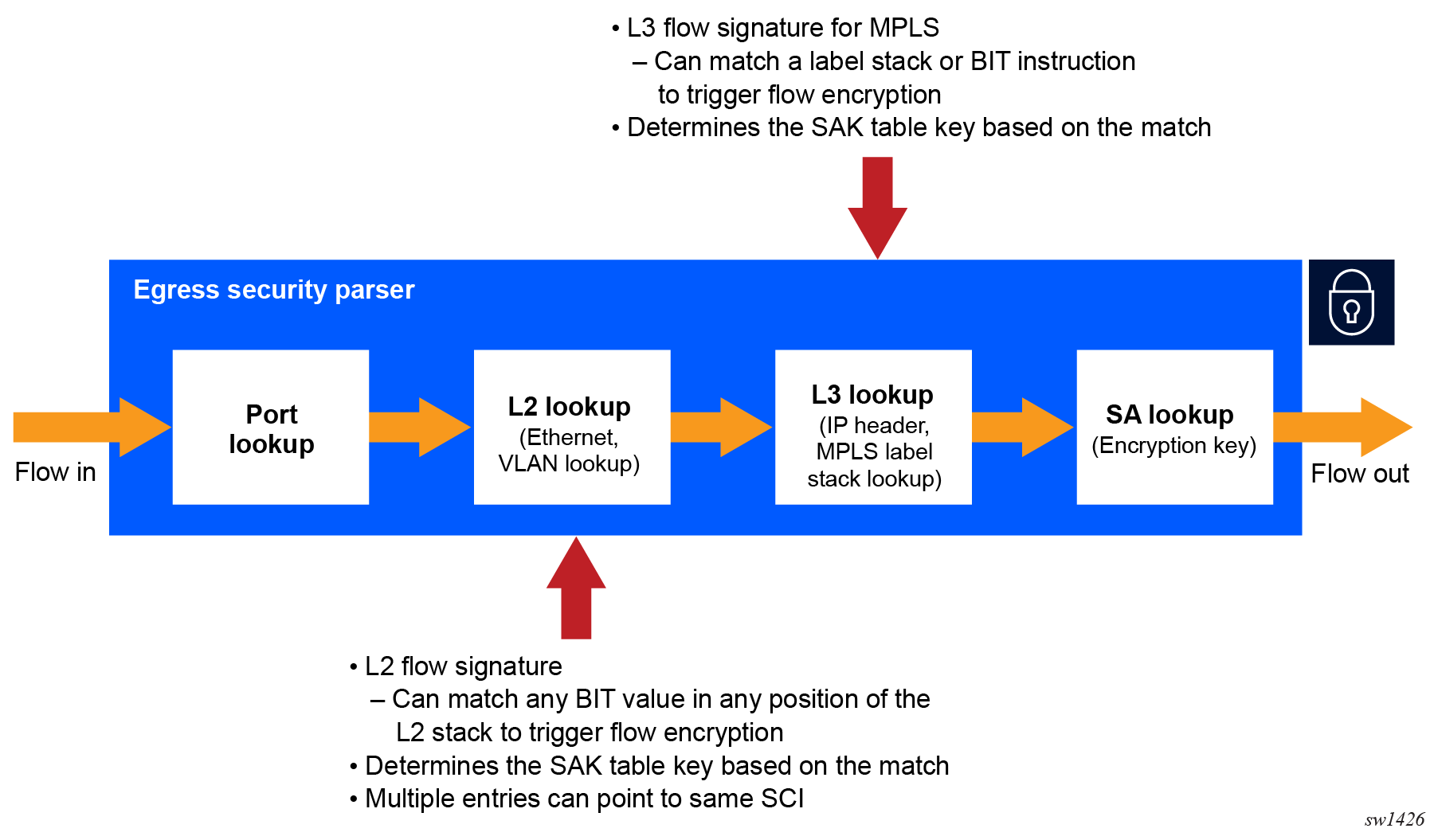
ANYsec and MACsec interaction
If ANYsec is enabled on the network ports, SR OS only supports enabling MACsec on the access ports. If MACsec and ANYsec are on the same IOM and FP5 chipset, MACsec uses scaling resources from ANYsec. For example, if a single MACsec port is configured on the same IOM as ANYsec, the ANYsec scale drops by 1 on that IOM. This is because both MACsec and ANYsec use the same SA lookup table, which has a defined number of entries.
ANYsec and LAG and ECMP interaction
When LSPs are enabled with ANYsec on iLER, the LSPs do not hash their internal flows over multiple ECMP interfaces or over LAG members. Instead, each LSP on iLER maps to a dedicated ECMP interface or LAG member. If an ANYsec LSP is transporting multiple services or IP flows, all the services and IP flows map to a single interface in an ECMP group, or to a single member in a LAG bundle on the iLER. However, if there are multiple ANYsec LSPs on the iLER, each ANYsec LSP and all the flows within the LSP can also hash to a different interface in an ECMP group or a different LAG member in a LAG bundle.
The LSR routers can hash the ANYsec LSPs over an ECMP group interface or a LAG member freely, without any restrictions.
ANYsec behavior when SR-TE is resolved through SR-IGP (ISIS, OSPF, OSPF3)
If an SR-TE or SR policy LSP is resolved through an SR-ISIS, SR-OSPF, or SR-OSPF3 LSP as top SID, the SR-TE or SR policy LSP is encrypted during the segment that it is traversing the SR-ISIS, SR-OSPF, or SR-OSPF3 LSP. At the destination (decrypting node), the packet is decrypted and forwarded to the rest of the segments. Additionally, the encrypting router that has resolved the SR-TE or SR policy top SID through SR-IGP only leaves the SR-IGP and Encryption SID in clear and encrypts the rest of label stack. At the decrypting router, the top SID and the encryption SID are removed and the rest of the label stack and payload is decrypted. At this point, the LSP is forwarded based on the rest of the label stack that is now in clear.
Inter AS and Inter Area solutions
ANYsec LSPs support a single-area solution only. ANYsec does not support inter-AS or inter-AREA option B or option C (for example, seamless MPLS).
ANYsec supports inter-AS or inter-AREA option A with the following conditions:
- The termination of the ANYsec LSP is at the ABR or ASBR router.
- Another ANYsec LSP originates toward the other inter-AS or inter-AREA option A.
In addition, ANYsec does not support tunnels within tunnels. For example, an ANYsec LSP that is encrypted cannot be encapsulated in a second MPLS tunnel such as BGP LU, RSVP-TE, or LDP.
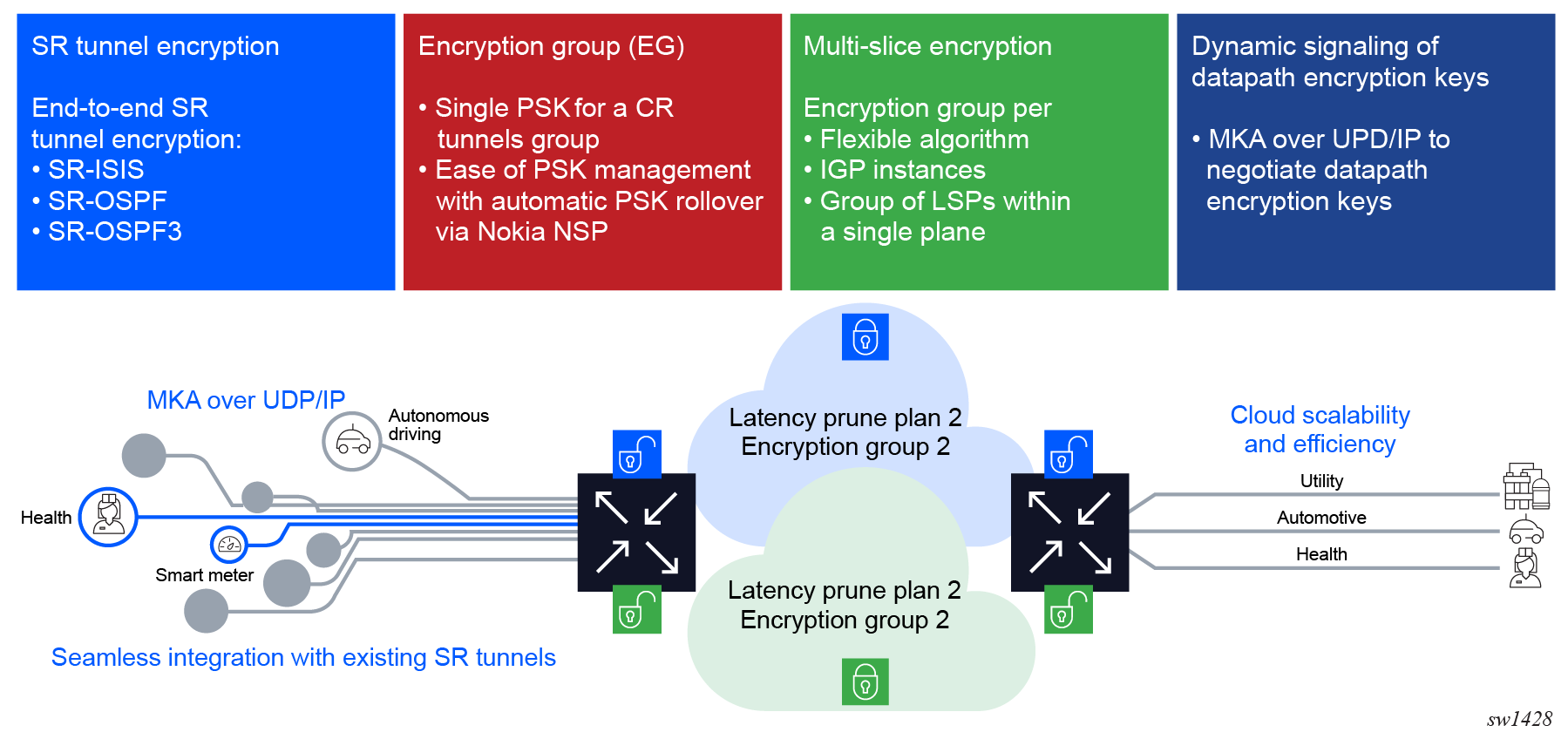
ANYsec implementation design
ANYsec supports the following implementation design:
- At the MKA signaling layer, ANYsec supports assigning the PSKs and the CAs to a group of Segment Routing (SR) tunnels. This assignment is known as Encryption Groups (EG) in ANYsec. EGs support easy management of PSKs for ANYsec tunnels, because multiple tunnels can use the same PSK.
- MKA is established per pair of peers, thereby allowing encryption of each tunnel with its own dedicated SAK. The use of a dedicated SAK per tunnel ensures a high level of security. For ease of management, ANYsec supports using PSKs per group of tunnels. However, for maximum security, the SAK is only supported per pair of peers.
- ANYsec supports tunnel slicing using Flex Algo or multi-instance IGP. Each slice is uniquely identified and a SAK is assigned per slice (per set of peers). ANYsec can also uniquely identify each LSP on each slice, and assign an EG to the LSPs through user configuration.
- ANYsec uses the MKA Layer 2 protocol for signaling, which uses IEEE 802.1x for encapsulation. To transport MKA over IP in a Layer 3 network, ANYsec encapsulates MKA over IP/UDP. The UDP port uniquely identifies the MKA packets to the ANYsec peers. The IP header transports the MKA packet from one ANYsec PE to another ANYsec PE.
The following figure shows the ANYsec design implementation and related requirements.
ANYsec configuration guidelines
These topics describe the basic configuration requirements to implement Nokia ANYsec MPLS encryption.
Configuring ANYsec connectivity association and PSK
ANYsec uses MKA for its control plane and for signaling of SAKs, and therefore ANYsec reuses the MACsec connectivity association (CA) and the PSKs. SR OS supports creation of the CA uniquely for ANYsec. When the anysec command is enabled under the CA, SR OS supports the exclusive use of the CA with ANYsec encryption; this CA cannot be reused for MACsec any longer.
configure macsec connectivity-association anysecANYsec supports the static-cak and the cipher-suite commands for the CA configuration. When a CA is configured for ANYsec, it does not support the following CA configurations:
- clear-tag mode
- delay protection
- encryption offset
- MACsec encryption
- replay-window size
- MAC policy
ANYsec also does not support configuration of a MACsec MAC policy.
The following example displays an ANYsec CA configuration.
MD-CLI
[ex:/configure macsec]
A:admin@node-2# info
connectivity-association "CA-1" {
admin-state enable
cipher-suite gcm-aes-xpn-256
anysec true
static-cak {
mka-hello-interval 2
pre-shared-key 1 {
encryption-type aes-256-cmac
cak "2yzrsjg5sp7MYAnWpod+Nkn4SwXf7OPMEfAMRpNh9Gu/badNTWOoYEG9Qi1NDOBW hash2"
cak-name "11"
}
}
}classic CLI
A:node-2>config>macsec# info
----------------------------------------------
connectivity-association "CA-1" create.
anysec
cipher-suite gcm-aes-xpn-256
static-cak
pre-shared-key 1 encryption-type aes-256-cmac create
cak "2yzrsjg5sp7MYAnWpod+Nkn4SwXf7OPMEfAMRpNh9Gu/badNTWOoYEG9Qi1NDOBW" hash2
ckn "11"
exit
mka-hello-interval 2
exit
no shutdown
exitIdentifying and configuring ANYsec LSP
After configuring the CA as described in Configuring ANYsec connectivity association and PSK, the next step is to identify the LSP to encrypt. The benefit of ANYsec is the ability to easily enable encryption on an LSP at any time, without changing the LSP's service lease agreement (SLA). ANYsec achieves this by doing the following:
- ANYsec uses the MACsec engine to achieve low latency, line rate encryption, with less than 1us and within 100s of ns of introduced encryption and decryption latency.
- ANYsec identifies an LSP to encrypt using a disjoint configuration, and encrypts it independently, allowing creation of MPLS networks with appropriate design and SLA that can be expanded to include encryption on LSPs in the future.
- ANYsec uses bidirectional configuration, even for LSPs that are unidirectional, and therefore the ANYsec configuration has to identify an outgoing LSP to encrypt and an incoming LSP to decrypt, under the same encryption group.
The following example displays a configuration to enable encryption on the egress LSP with the node SID 1.1.216.136, and decryption for the local node SID bound to 1.1.216.100. Both LSPs are on IGP instance ID 11.
MD-CLI
[ex:/configure anysec]
A:admin@node-2# info
reserved-label-block "rlb-1"
mka-over-ip {
mka-udp-port 12345
}
tunnel-encryption {
security-termination-policy "STP-1" {
admin-state enable
local-address 1.1.216.100
igp-instance-id 11
}
security-termination-policy "Sec-Term-Policy" {
}
security-termination-policy "test-policy" {
}
encryption-group "EG-1" {
security-termination-policy "STP-1"
ca-name "CA-1"
peer-tunnel-attributes {
igp-instance-id 11
}
peer 1.1.216.136 {
admin-state enable
}
}
}
classic CLI
A:node-2>config>anysec# info
----------------------------------------------
reserved-label-block "rlb-1"
mka-over-ip
mka-udp-port 12345
exit
tunnel-encryption
security-termination-policy "STP-1" create
igp-instance-id 11
local-address 1.1.216.100 //decrypt the incoming LSP for local node sid
no shutdown
exit
encryption-group "EG-1" create
ca-name "CA-1"
security-termination-policy "STP-1"
peer-tunnel-attributes
igp-instance-id 11
exit
peer 1.1.216.136 create //encrypt the outgoing LSP for remote node sid
no shutdown
exit
no shutdown
exit
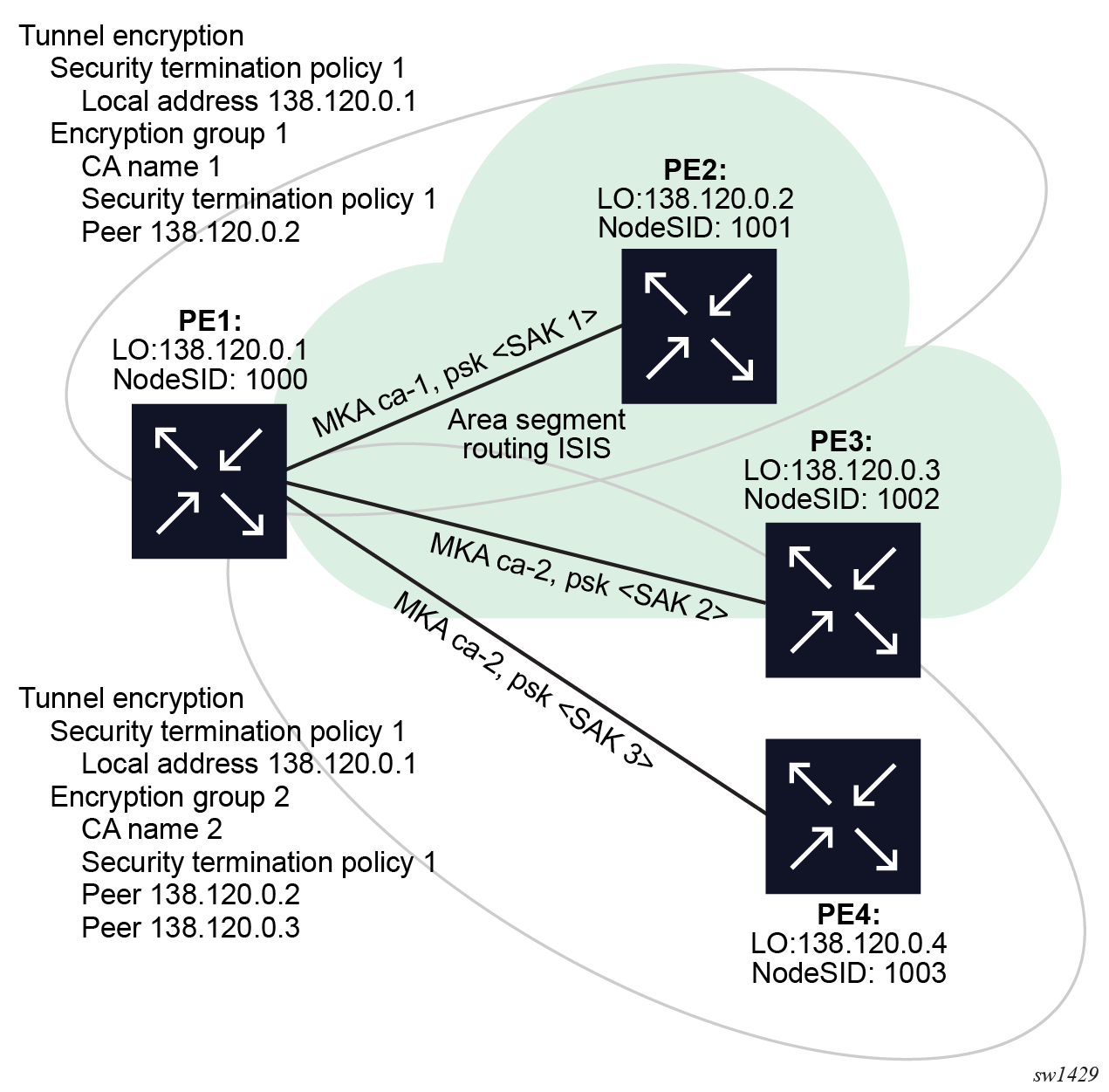
exitThe security-termination policy identifies the decrypting LSP and the node SID on the local router. The decrypting LSPs node SID can arrive from multiple peers, and the SAKs used to decrypt these incoming LSPs are different for each peer.
The encryption group is a group of peers that use the same CA and PSK to secure the SAK over MKA. Each peer node SID and its local node SID use a different SAK to encrypt the datapath, but all these SAKs under the same encryption group are secured and signaled via the same CA and PSK.
A security-termination policy can be part of multiple encryption groups, however, a peer can only be part of a single encryption group. This allows a set of bidirectional LSPs in an encryption group to use the same CA and PSK to secure and signal SAKs between them.
The following figure shows the implementation of ANYsec tunnel encryption using two encryption groups with the same security termination policy, and different CAs and peers.
Configuring ANYsec MKA
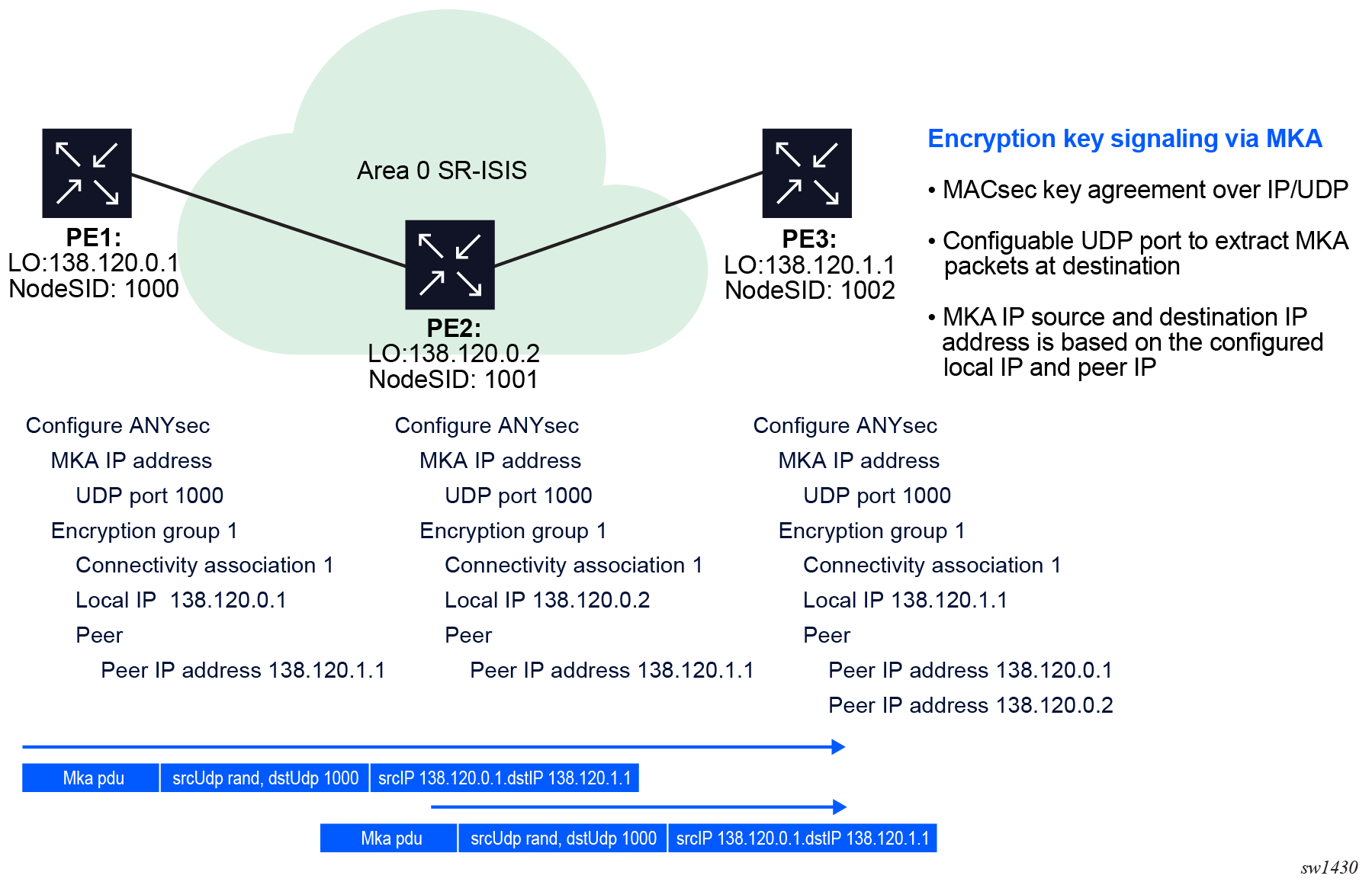
ANYsec uses MKA to distribute SAKs. MKA is part of IEEE802.1x standard and is a Layer 2 protocol without an IP header. As an MPLS Layer 2.5 encryption protocol, ANYsec reuses MKA by encapsulating MKA in IP/UDP to distribute the SAK from one PE to the other.
The user-configurable UDP port identifies the MKA packets on the router. The following configuration guidelines apply:
- Reserve the UDP port for MKA for the entire network.
- Ensure that the UDP port is not in use by any other application.
Use the following command to configure the MKA UDP port.
configure anysec mka-over-ip mka-udp-portThe following figure shows the ANYsec implementation using the MKA UDP port configuration.
Configuring ANYsec encryption SIDs
With ANYsec, the encryption engine locks on a unique label stack and encrypts it with a unique SAK. This label stack needs to be programmed by SR OS in the encryption engine. This creates a problem with double encryption in segment routing technology. In segment routing, all peers wanting to send a packet to a local router, send the packet to the node SID of the local router. As such, the label stack that is pushed on the packet by different routers to switch the packet to the local router may be identical. This means if an encrypting node is also an LSR node for an upstream router, it would encrypt its own local packets to the downstream ANYsec router and would double encrypt the upstream ANYsec router packets that are going through it to the same downstream ANYsec router. For example, in the following figure PE2 would encrypt its own packet destined for PE3 and double encrypt the PE1 packets with same MPLS label stack destined for PE3. This double encryption would mean that PE1 packets are not decrypted correctly at PE3.
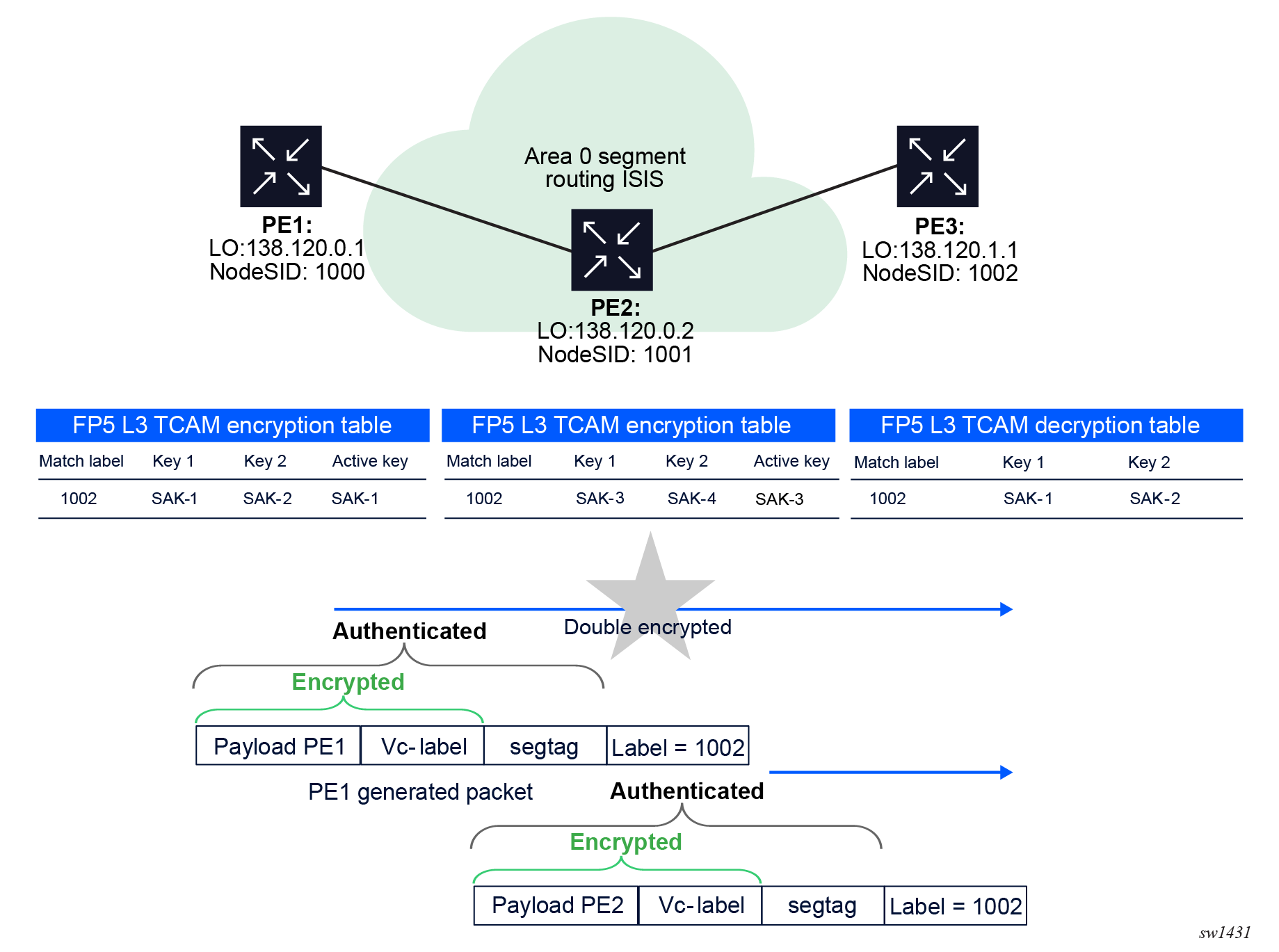
To solve this problem, SR OS introduced the encryption SID concept. The encryption SID uniquely identifies the encrypting router within the network. The encryption SID is pushed by the encrypting router at the bottom of the label stack with S bit set.
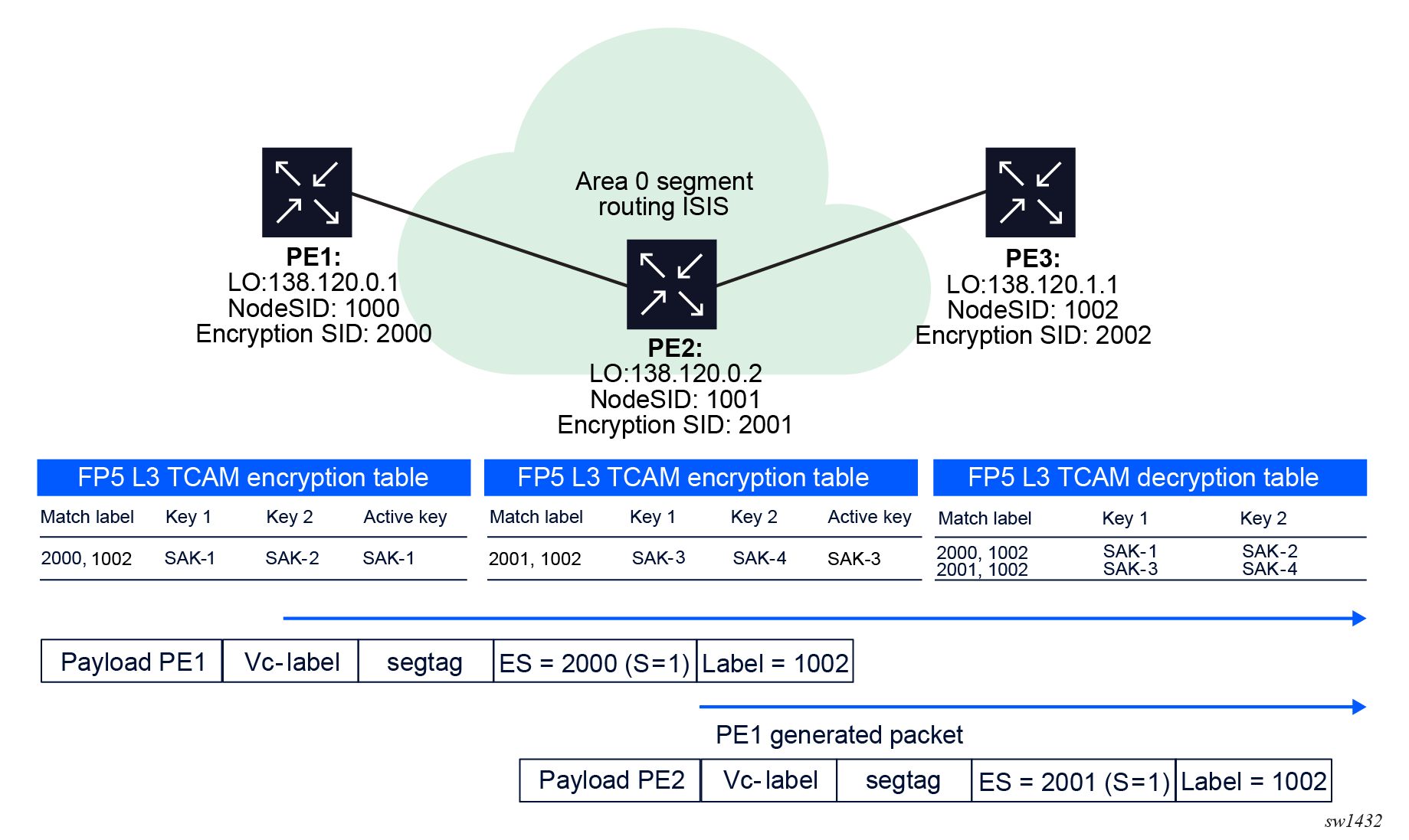
In the following figure, the encryption SID 2000 is assigned to PE1 encrypting node and encryption SID 2001 is assigned to PE2 encrypting node. Both sending packets to PE3.
The encryption SID pushed at the bottom of the label stack ensures that each encrypting node has a unique label stack so double encryption does not occur on the PE2. The PE2 ANYsec CAM is only programmed to encrypt the label stack of <2001(S=1),1002> and does not match the label stack of <2000(S=1),1002> from PE1.
Ensure the following conditions are met for the encryption SID used in the ANYsec configuration:
- The encryption SID for the ANYsec configuration must be uniquely assigned to each encrypting router.
- The encryption SID for the ANYsec configuration must be assigned from a reserved block of labels on SR OS.
The following example displays a configuration of an encryption SID on a encrypting node.
MD-CLI
[ex:/configure router "Base" mpls-labels]
A:admin@node-2# info
sr-labels {
start 60000
end 120000
}
reserved-label-block "r1b-1" {
start-label 50000
end-label 59999
}
[ex:/configure anysec]
A:admin@node-2# info
reserved-label-block "r1b-1"
mka-over-ip {
mka-udp-port 12345
}
tunnel-encryption {
security-termination-policy "STP-1" {
admin-state enable
local-address 1.1.216.100
igp-instance-id 11
}
security-termination-policy "Sec-Term-Policy" {
}
security-termination-policy "test-policy" {
}
encryption-group "EG-1" {
admin-state enable
security-termination-policy "STP-1"
encryption-label 50012
ca-name "CA-1"
peer-tunnel-attributes {
igp-instance-id 11
}
peer 1.1.216.136 {
admin-state enable
}
}
}
classic CLI
A:node-2>config>router>mpls-labels# info
----------------------------------------------
sr-labels start 60000 end 120000
reserved-label-block "rlb-1" //reserved block for encryption sid
start-label 50000 end-label 59999
exit
----------------------------------------------
A:node-2>config>anysec# info
----------------------------------------------
reserved-label-block "rlb-1" //reserve blocked assigned to ANYsec
mka-over-ip
mka-udp-port 12345
exit
tunnel-encryption
security-termination-policy "STP-1" create
igp-instance-id 11
local-address 1.1.216.100
no shutdown
exit
encryption-group "EG-1" create
ca-name "CA-1"
encryption-label 50012 //encryption sid that uniquely identifies this encrypting node and is pushed on the bottom of label stack when the node encrypts the LSP.
security-termination-policy "STP-1"
peer-tunnel-attributes
igp-instance-id 11
exit
peer 1.1.216.136 create
no shutdown
exit
no shutdown
exit
exit
ANYsec OAM MPLS support
OAM support with Segment Routing tunnels
ANYsec supports OAM with following Segment Routing tunnels:
- SR-ISIS
- SR-OSPF
- SR-OSPF3
OAM command support
ANYsec supports OAM tools including P2MP LSP ping and services OAM tools if any services are riding over the ANYsec tunnel. ANYsec supports the use of the following inband OAM commands:
- LSP ping
- SDP ping
- VCCV ping
- Service ping
- ping over a non default service
- L2 service ping
Service encryption
A service can be encrypted using ANYsec and the IEEE 802.1AE encryption engine on the SR OS.
The following figure shows the difference between tunnel encryption and service encryption. With tunnel encryption, all the services traversing the tunnel are encrypted. With service encryption, the user can choose a specific service to be encrypted with its own specific PSK and SAK. The LSP that is carrying the services can serve multiple services that are in cleartext or encrypted.
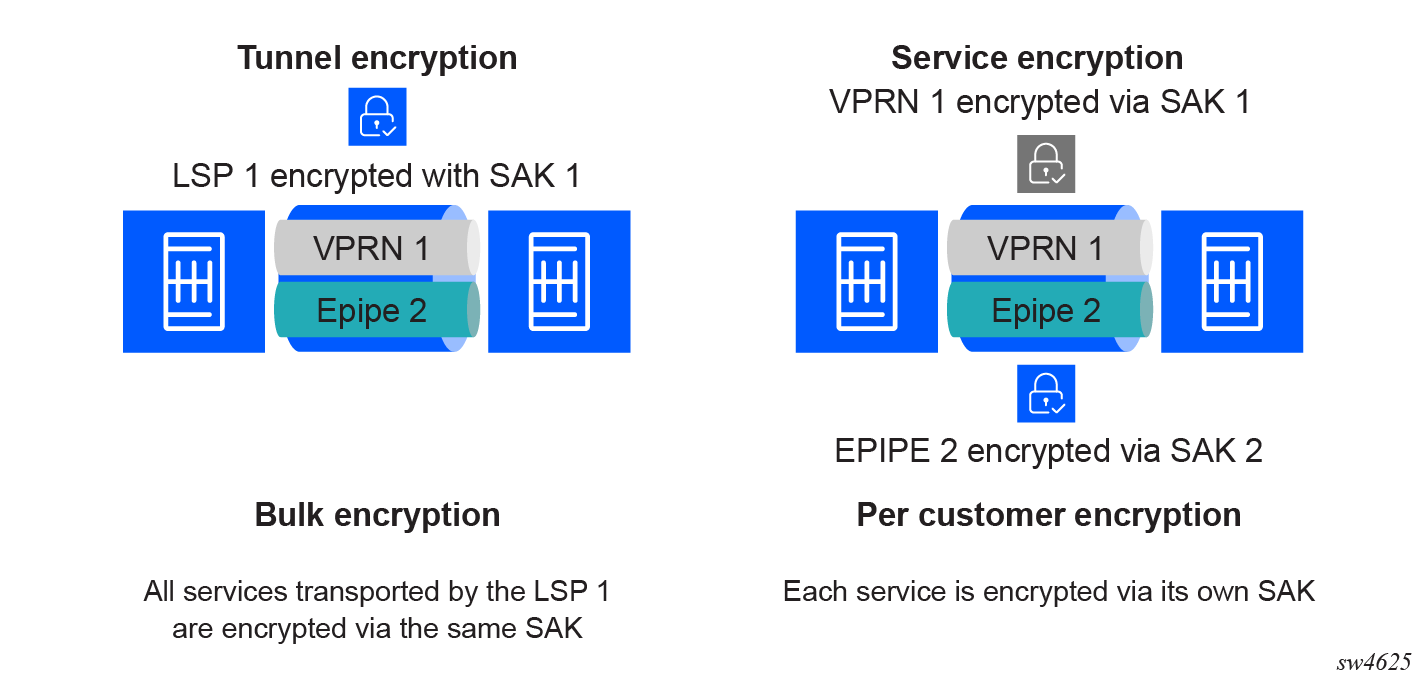
With service encryption, a tunnel can transfer either encrypted or cleartext services. When an encryption group is assigned to a service, that service becomes a secure service and encryption is enabled for it. When encryption is enabled, the service only transmits and accepts encrypted traffic. Any cleartext traffic is rejected and dropped.
The following services support ANYsec encryption:
-
spoke-SDP
VPRN (Layer 3 spoke-SDP interface), IES (Layer 3 spoke-SDP interface), Epipe (including PW-RED and PW-switching)
-
autobind
VPRN BGP-IPVPN or BGP-EVPN route type 5 (IFL)
Encryption on the preceding services is only possible if the underlying protocol is SR-ISIS, SR-OSPF, or SR-OSPF3.
ANYsec service encryption is only supported within a single area; it is not supported with inter-AS or inter-area options B or C. ANYsec service encryption is possible with inter-AS option A, provided that encryption is terminated on the ASBR or ABR, and that encryption on the neighboring ASBR or ABR is restarted by assigning ANYsec to those services.
configure router isis segement-routing prefix-sid-range
configure router ospf segement-routing prefix-sid-rangeEncryption Groups
Encryption Groups (EGs) can be assigned to a service to enable encryption for that service. An EG contains the CA, which contains the PSK used for the MKA to secure the SAK. As with tunnel encryption, the MKA is established for each pair of PEs in a service. The MKA distributes the SAK to each pair of PEs. Each PE pair within a service (such as VPRN) is encrypted with a different SAK, providing additional security. If a pair of PE SAKs is compromised, other PE pairs in the same service remain compromised.
An EG can be assigned to a single service or to multiple services. If assigned to multiple services, the services use the same MKA between peers and the same datapath key (SAK) to encrypt their packets between the peers. This provides scaling benefits for ANYsec, as multiple services are encrypted using the same SAK.
EGs function as follows:
-
The provider can choose to either encrypt a service or multiple services using a single MACsec CA and PSK (and its SAK), or assign each service a unique CA, PSK, and SAK.
As with tunnel encryption, this creates an EG concept.
- An EG can be used for a set of services to be encrypted using a single CA and its
corresponding PSK (CKN, CAK).
- Services using the same EG use the same local encryption SID, which uniquely identifies the source of encrypting.
- Each EG must be configured with a set of PEERs (PEs) that the service is
encrypting traffic toward and receiving encrypted traffic from.
- For service encryptions, these peers must match the peers discovered by dynamic protocols, such as BGP and TLDP, for each service.
- If a service discovers a peer through overlay signaling (BGP or TLDP), and this peer is not configured under the EG for that service, traffic is dropped.
-
Each EG must be configured with its encryption SID (ES) to uniquely identify it as an encrypting source of the service.
The peer's ES is discovered automatically through the MKA SCI field.
- A customer may configure a single EG or multiple EGs for its services, depending on their security needs.
- When the appropriate EGs are configured with their corresponding peers, the EG is
assigned to a service under autobind or within the context of its spoke-SDP. The
following applies:
- When an EG is assigned to an autobind, all LSPs used by that autobind inherit the EG configuration, including the CA, ES, and local address.
- For Epipe PW switching, each spoke-SDP has its own EG. As a result, the encryption terminates on the first spoke and switches to the second spoke, where it is encrypted again.
Shared EG between services
To share a single EG between multiple services, ensure the following rules are not violated:
The following figure shows an example of two encrypted services using the same tunnel and EG.
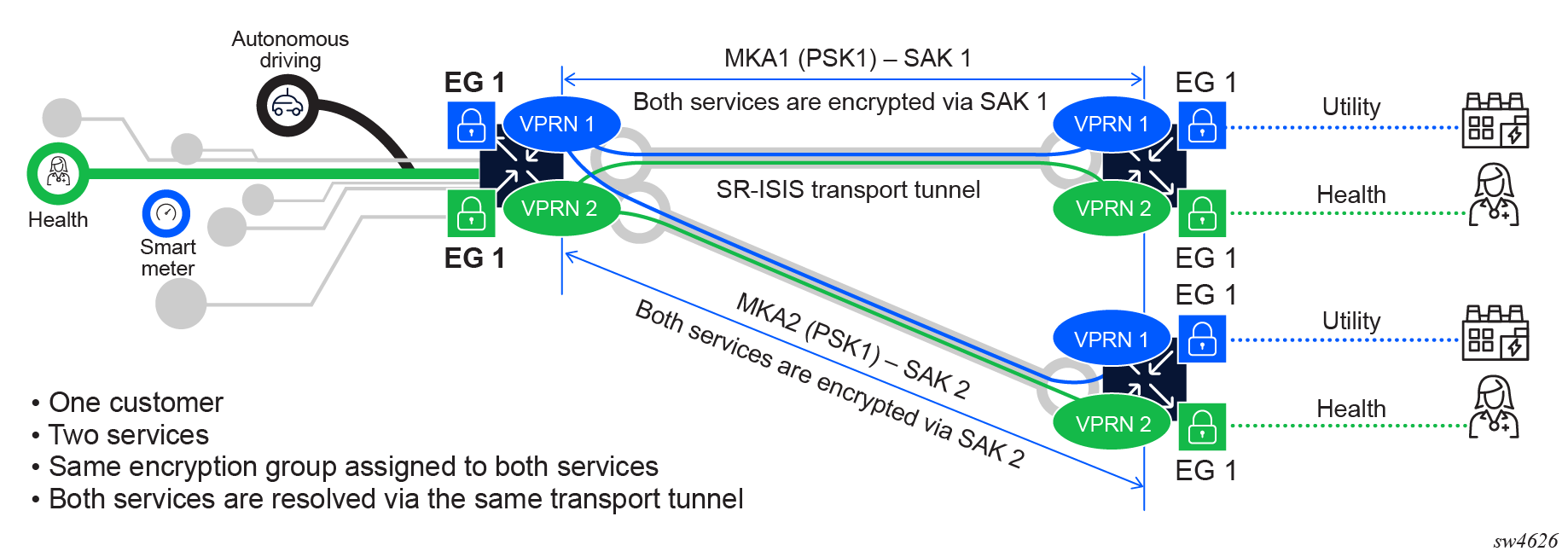
When the EG is shared between multiple services, only a single MKA session is established between the peers. Both services use that MKA session with its PSK to secure the SAK. The MKA session distributes the SAK between the peers, and both services are encrypted with the same SAK.
Unique EG between services
In cases where each service belongs to a unique customer, and each customer has its own security and key management requirements, it is possible to assign an EG per service. Each EG creates a dedicated MKA session with its own PSK securing its unique SAK.
The following figure shows an example of two encrypted services using the same tunnel but different EGs.
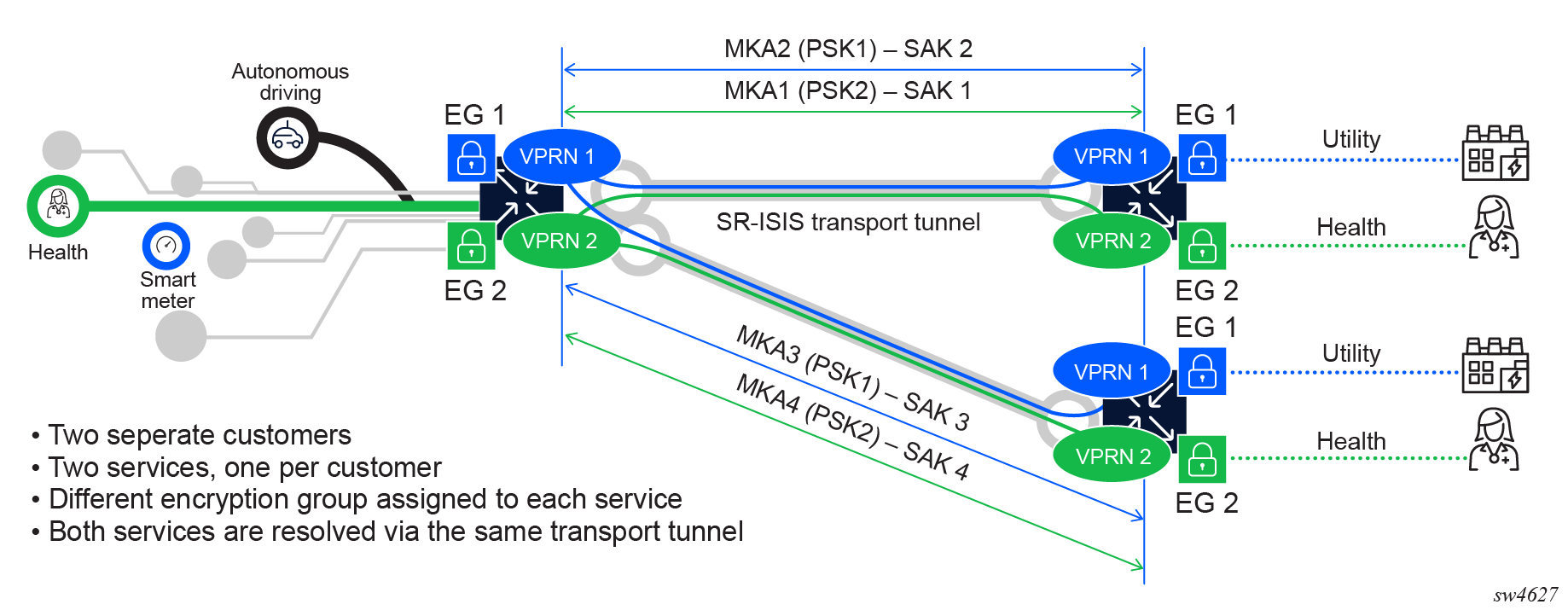
Peer configuration under EG
The peer IP address must be configured under the EG. The IP address should match the BGP neighbor IP address or TLDP far-end IP address.
EG limitations
The following limitations apply for EGs:
- Two services that use two BGP groups with different local addresses to the same peer cannot share the same EG.
- If encrypting two services destined for the same peer through two different tunnels (that is, using the flex algorithm), each service must have a unique EG. That is, the two services cannot share the same EG.
Security termination policy
The security termination policy (secTP), as with tunnel encryption, contains the tunnel-protocol information, IGP instance, and flex algorithm. It also includes the local IP address, which identifies the system IP address or loopback address used to identify the local tunnel. This local IP address must match the BGP source IP address or TLDP source IP address; it is the IP address that identifies the SR tunnel terminating on the router for the service using that secTP.
Multiple EGs can have the same secTP.
Service encryption considerations
The following considerations apply for service encryption:
- When identical EGs are assigned to multiple services or flex algorithms resolving through the same peer (far-end IP address), the resolution must be through the same transport tunnel and resolution filter tunnel type. Additionally, when the same EG is assigned to multiple services or flex algorithms, the same SAK is used to encrypt packets for all services that share the same EG.
- Service encryption only supports service labels per VRF, which is configured using
the following command
option.
configure service vprn label-mode vrf- Service encryption does not support the label-mode next-hop command option, even though it can be configured when the service is encrypted. If next-hop is configured, service encryption does not function correctly.
- Service encryption does not support the advertise-label per-prefix command option in the configure policy-options context.
- If ANYsec enabled, a service can have only a single BGP instance. For example, if ANYsec is enabled under a VPRN service, that service cannot also have an EVPN instance.
-
A transport tunnel cannot be encrypted if it is used for encrypted services.
If the transport tunnel is encrypted and assigned to an encrypted service on egress, traffic is dropped.
- Flex-E is not supported with ANYsec.
-
The security termination policy is a peer and transport tunnel concept. A peer can contain multiple services, some encrypted and others cleartext. As a result, to allow a combination of encrypted and cleartext services to reside on a node, the following command should be set to false in the security termination policy.
configure anysec security-termination-policies policy rx-must-be-encrypted falseNote: When a service is encrypted, it accepts only encrypted traffic; any cleartext traffic is dropped.
Inter-AS and intra-AS solutions
Layer 2 and Layer 3 services can be configured in a single area or across multiple areas or ASs. Most deployments use Option A and Option C, though some also use Option B.
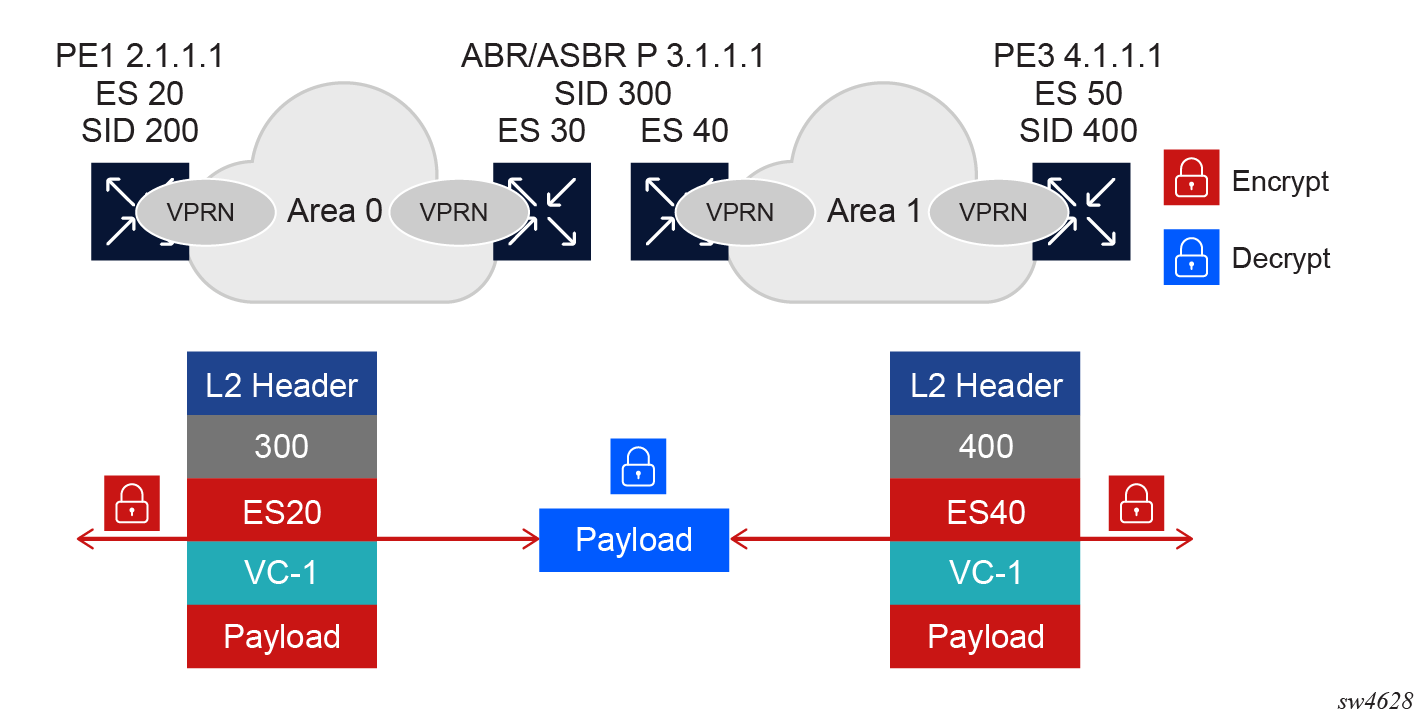
Service encryption supports only Option A. In this scenario, the service is decrypted at the ASBR or ABR PE, after which routes are leaked to the corresponding ASBR or ABR PE in the other domain. Traffic is forwarded in cleartext, and in the second domain the PE can reencrypt the service. The user data is in cleartext between the ASBR and ABR, and between the edge PEs.
The following figure shows an example of an encrypted service with Option A.
Key management
ANYsec uses MKA to distribute datapath keys (SAKs). For ANYsec, the MKA is established for each EG and each peer in the EG.
The MKA is uniquely identified through the source IP address, destination IP address, and SCI. The SCI is made up of the ES and endpoint ID.
The following figure shows an example of the MKA for an encrypted service.
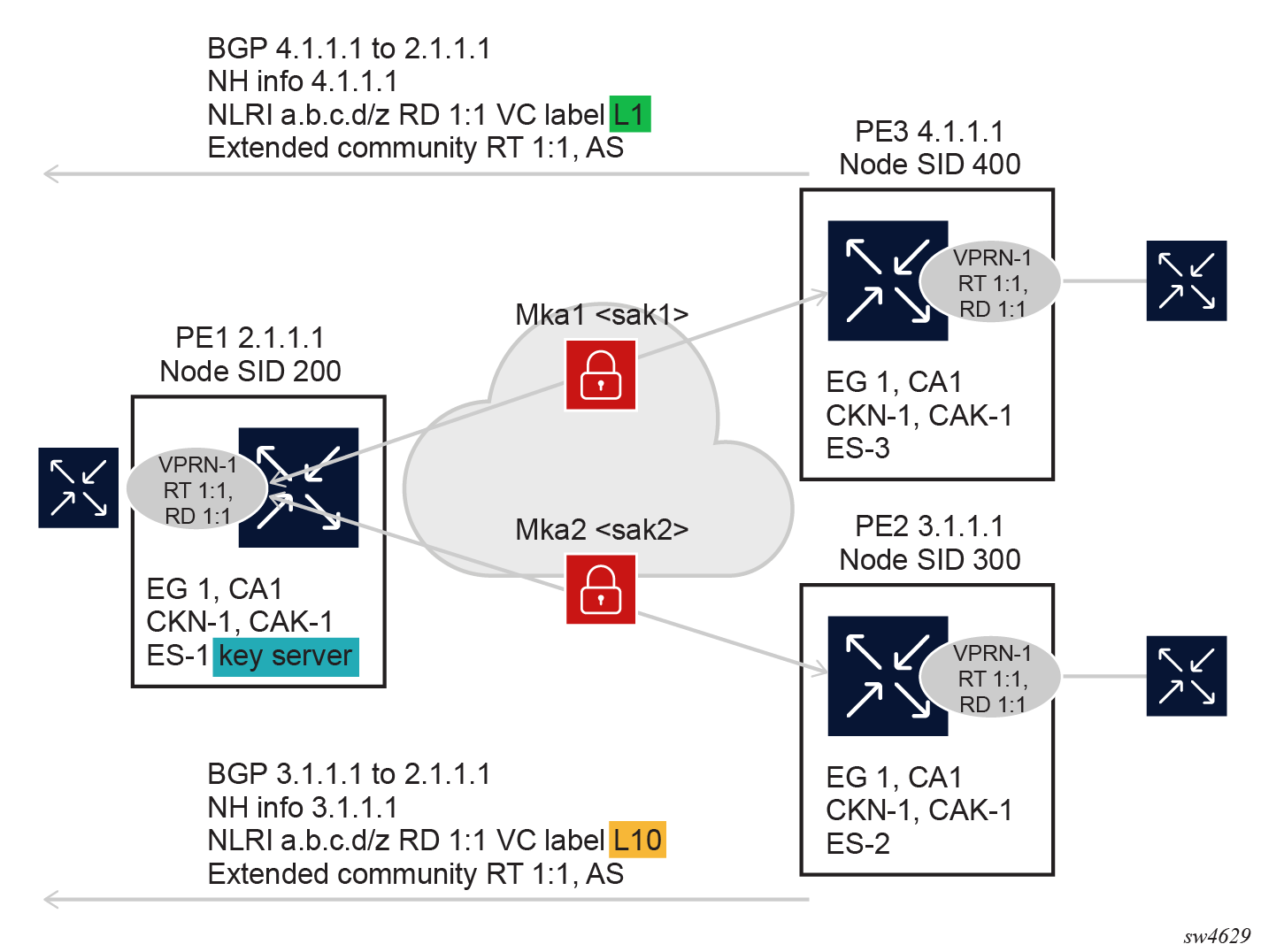
In MKA for encrypted service, if the VPRN on PE1 has two peers (PE3 and PE2) for EG1, two MKA sessions are created: one from PE1 to PE2 and another from PE1 to PE3, both for the same VPRN. The source IP address of the MKA is the local address in the secTP. The destination IP address is the peer IP address in EG1, which has two peers (PE2 and PE3). Each pair of local addresses, peer addresses, and SCIs create an MKA session.
As a result, each EG and PE within that EG is assigned a unique SAK for encryption, as shown in the following figure.
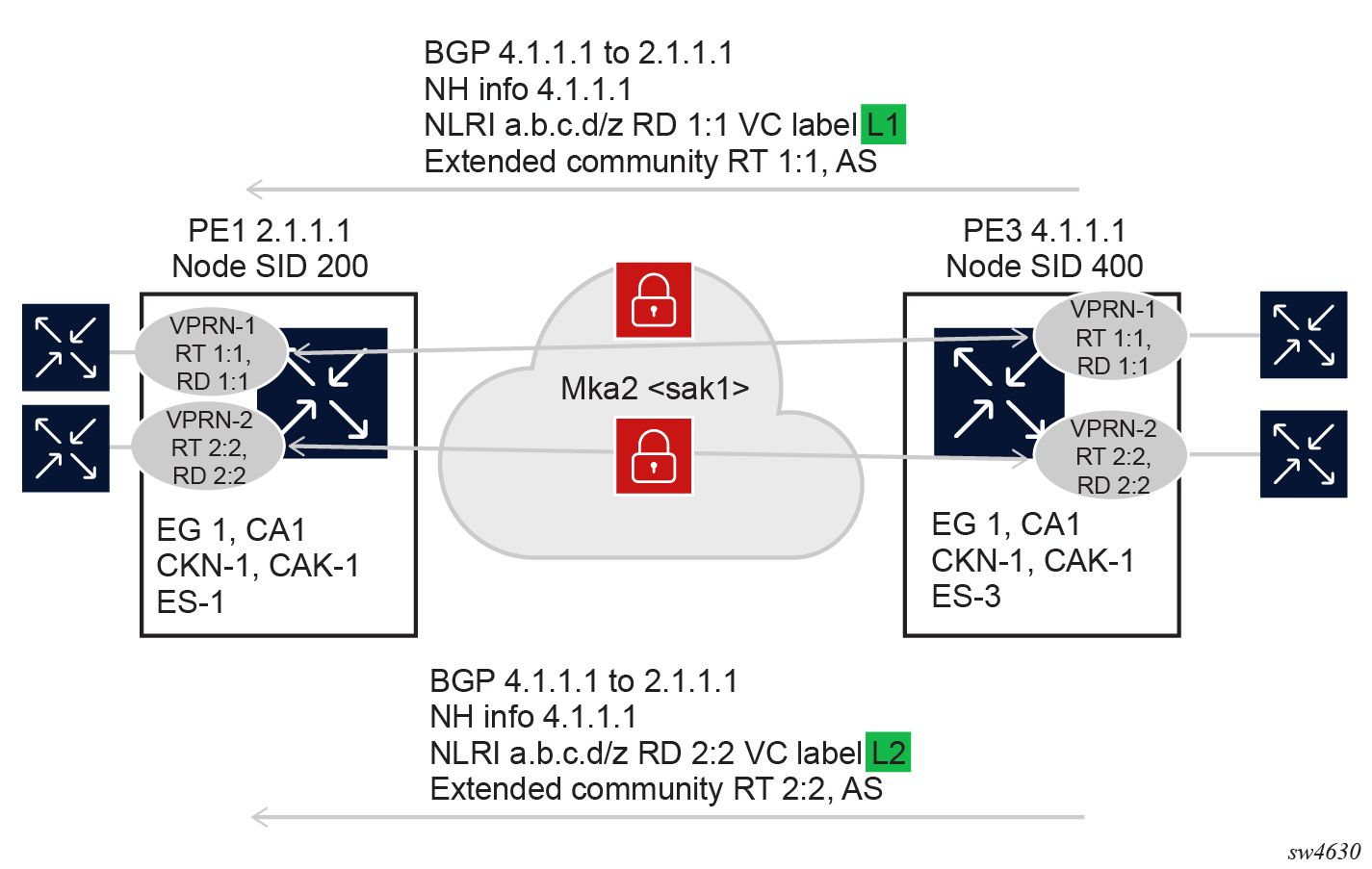
In another example, if two VPRNs between two PEs use the same EG and secTP, only a single MKA session is created. This is because the source IP address of the MKA is the secTP local address, which is common to both VPRNs; the destination IP address is the peer IP address in the EG, which is also common. In addition, the ES is common for both VPRNs. In this case, because one MKA session serves both VPRNs, the same SAK is signaled for both. So user traffic from the two VPRNs is encrypted with the same SAK.
In the preceding example, each VPRN must be configured with a unique EG to have its own MKA and SAK.
Packet format for services
This section provides examples of packet formats for encrypted services in different scenarios.
Example 1: two services using the same EG
In this example, two PEs that have two VPRNs encrypted with the same EG over SR-MPLS.
This scenario occurs when a customer owns both services and wants to manage the CA and PSKs jointly for the two services. The following applies:
- The same EG can be used across multiple services if those services use the same BGP instance.
- If the same EG is configured for two services on the same two PEs, the following
applies:
- A single MKA session runs from the local address of the secTP to the EG peer IP address. That is, the MKA source IP address is the secTP local address assigned to that EG, and the destination IP address is the peer IP address of the same EG used by the two services.
- Because there is a single MKA session between the two services, a single datapath encryption key (SAK) is used to encrypt traffic from both services. If the two services need to use different SAKs, each service must be assigned its own EG.
- The ES is common between the two services because they are encrypted using the same SAK.
- From packets traveling from PE1 to PE3, both services appear identical, as
indicated by the format shown in the following figures.
Figure 19. VPRN1 RT 1:1 service 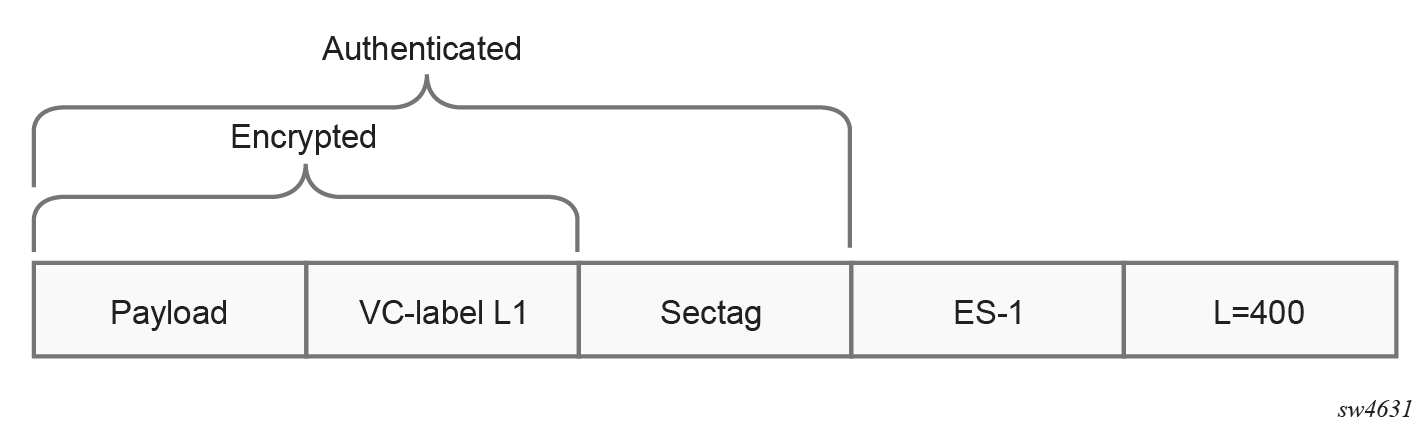
Figure 20. VPRN2 RT 2:2 service 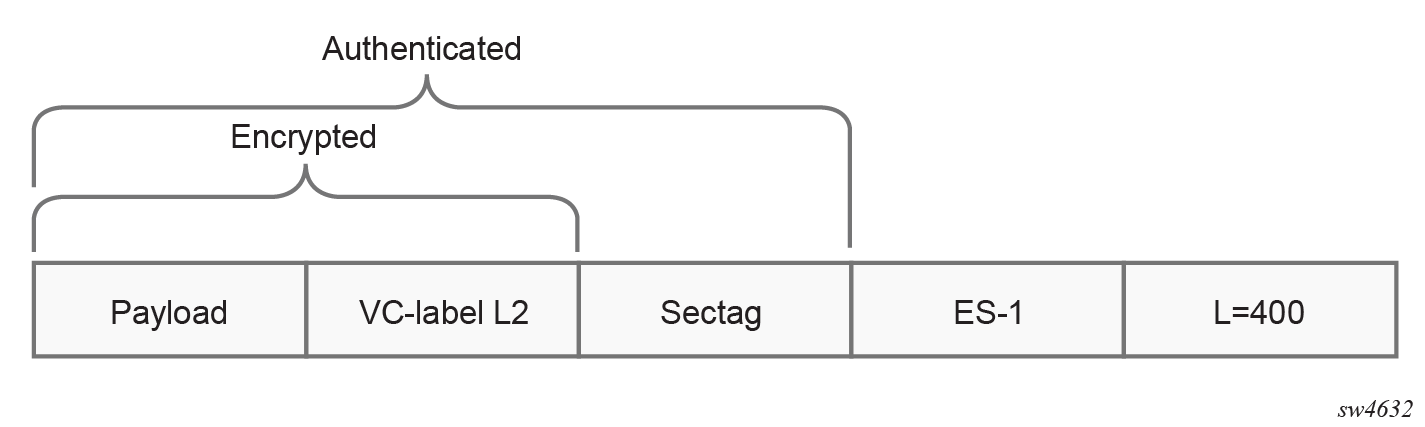
Example 2: Services and SR tunnel with different EGs
The following figure shows an example of two PEs that have two VPRNs encrypted with two different EGs over the same SR MPLS tunnel.
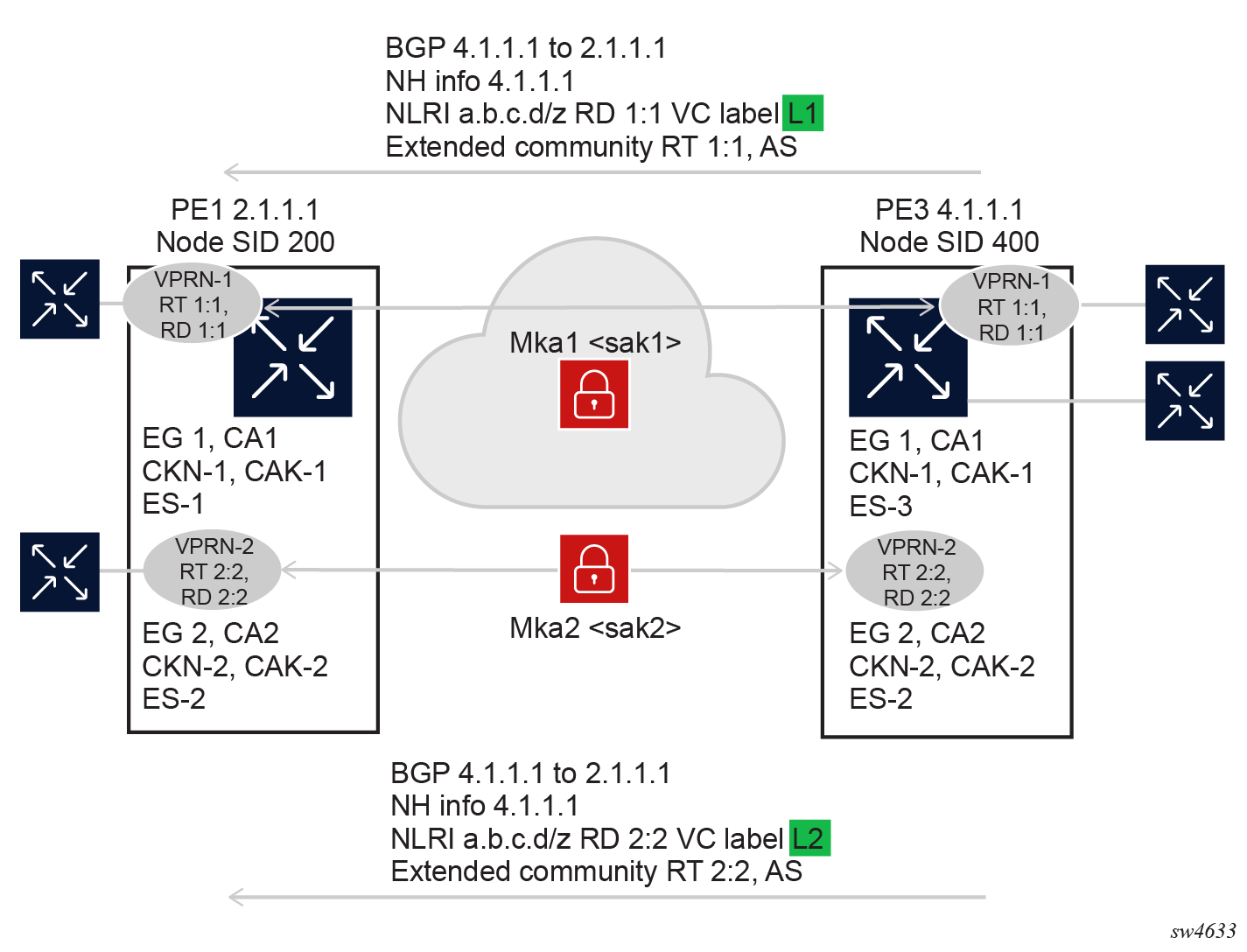
This scenario occurs when the two services are owned by different customers, and they require additional security by having separate CAs, PSKs, and SAKs.
When two separate EGs are configured for two services on the same two PEs, the following applies:
- There are two MKAs from the local address of the secTP of each EG to each EG peer IP address. The MKA source IP address is the local address of the secTP assigned to that EG, and the destination IP address is the peer IP address on the assigned EG for the two services. If the same BGP instance is used for both services, even if the EGs are different, the local address of the secTP and the peer IP address of the EG can still be the same. For example, the same secTP is used for both EGs and the same peer IP address is configured on both EGs. In this case, the unique identifier for the MKA is the SCI because each EG requires a unique ES. As a result, the unique MKA1 identifier is <srcIP= 2.1.1.1, dstIP=4.1.1.1, ES-1>, and MKA2 is < srcIP= 2.1.1.1, dstIP=4.1.1.1, ES-2>.
- Because there is a unique MKA for each service, a unique SAK is used to encrypt service user traffic for each service.
- From online packets going from PE1 to PE3, there are two unique packet signatures,
as shown in the following figures.
Figure 22. VPRN1 RT 1:1 service 
Figure 23. VPRN2 RT 1:1 service 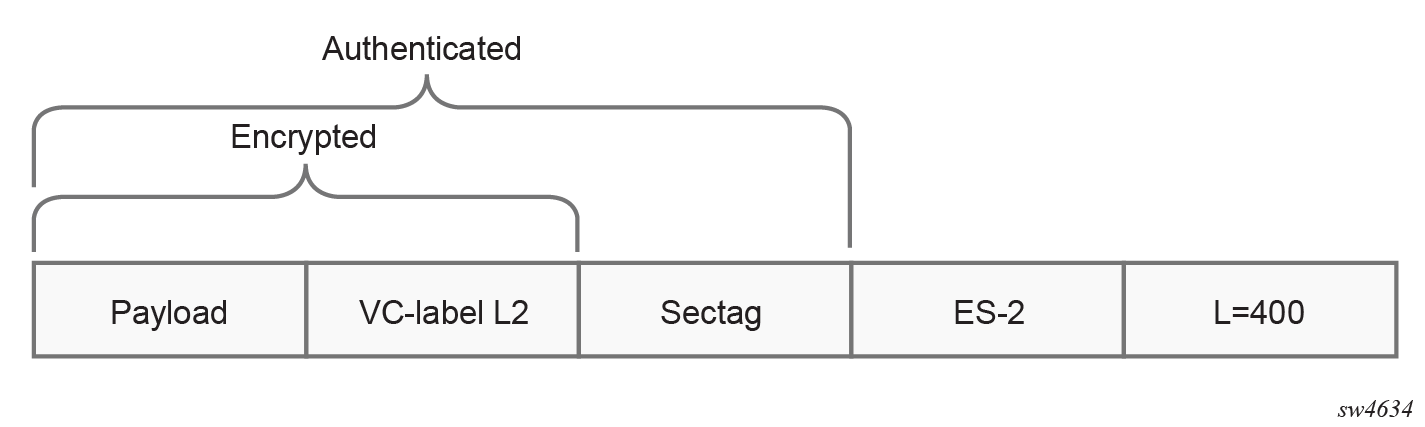
Service encryption and MACsec
Similar to tunnel encryption, ANYsec service encryption can coexist with MACsec. If ANYsec service encryption is enabled, MACsec can be configured on access ports.
Service encryption configuration
This section provides configuration examples for service encryption scenarios.
Two VPRN services with separate CAs and SAKs
Example 2: Encrypted service and SR tunnel with different EGs shows an example of a network where VPRN-1 and VPRN-2 are using BGP to the system IP address.
The following is an example configuration of PE1 from Example 2: Encrypted service and SR tunnel with different EGs.
MD-CLI
[ex:/configure macsec]
A:admin@Dut-PE1# info
connectivity-association "ca1" {
admin-state enable
cipher-suite gcm-aes-xpn-256
anysec true
static-cak {
pre-shared-key 1 {
encryption-type aes-256-cmac
cak "xsMqlX30xmmMVQtpXQIu1Rvx14/2E81okd56kbMjwGTyjQhsUxSJq7uSA7jZEtOW hash2"
cak-name "123456"
}
}
}
connectivity-association "ca2" {
admin-state enable
cipher-suite gcm-aes-xpn-256
anysec true
static-cak {
pre-shared-key 1 {
encryption-type aes-256-cmac
cak "xsMqlX30xmmMVQtpXQIu1Rvx14/2E81okd56kbMjwGTyjQhsUxSJq7uSA7jZEtOW hash2"
cak-name "123456"
}
}
}
classic CLI
DUT-PE1>config>macsec# info
----------------------------------------------
connectivity-association "ca1" create
anysec
cipher-suite gcm-aes-xpn-256
static-cak
pre-shared-key 1 encryption-type aes-256-cmac create
ckn "11"
cak cak-1
exit
exit
no shutdown
exit
connectivity-association "ca2" create
anysec
cipher-suite gcm-aes-xpn-256
static-cak
pre-shared-key 1 encryption-type aes-256-cmac create
ckn “22“
cak cak-2
exit
exit
no shutdown
exit
----------------------------------------------
The following is an example ANYsec configuration for VPRN-1 and VPRN-2 from Example 2: Encrypted service and SR tunnel with different EGs.
MD-CLI
[ex:/configure anysec]
A:admin@Dut-PE1# info
reserved-label-block "es-reserved-block"
mka-over-ip {
mka-udp-port 10000
}
security-termination-policies {
policy "system-ip" {
admin-state enable
local-address 2.1.1.1
protocol sr-isis
}
}
service-encryption {
encryption-group "1" {
security-termination-policy "system-ip"
encryption-label 32000
ca-name "ca1"
peer 4.1.1.1 {
admin-state enable
}
}
encryption-group "2" {
security-termination-policy "system-ip"
encryption-label 32001
ca-name "ca2"
peer 4.1.1.1 {
admin-state enable
}
}
}
classic CLI
Dut-PE1>config>anysec# info
----------------------------------------------
mka-over-ip
udp-port 10000
reserved-label-block “es-reserved-block”
service-encryption
security-termination-policies
policy “system-ip”
protocol sr-isis
local-address 2.1.1.1
no shutdown
exit
encryption-group “1”
security-termination-policy “system-ip”
encryption-label ES-1
ca-name “ca1”
peers
peer 4.1.1.1
no shutdown
exit
encryption-group “2”
security-termination-policy “system-ip”
encryption-label ES-2
ca-name “ca2”
peers
peer 4.1.1.1
no shutdown
exit
exit
----------------------------------------------
The following example shows the EG assignment to the service. In this example, the user creates two MKAs: one for VPRN-1 and another for VPRN-2. Each VPRN service has its own PSK and SAK, and complete encryption separation.
MD-CLI
[ex:/configure service]
A:admin@Dut-PE1# info
vprn "vprn-1" {
bgp-ipvpn {
mpls {
anysec-encryption-group "1"
}
}
}
vprn "vprn-2" {
bgp-ipvpn {
mpls {
anysec-encryption-group "2"
}
}
}
classic CLI
A:Dut-PE1>config>service>vprn# info // vprn-1
……………
bgp-ipvpn
mpls
anysec-encryption-group <1>
auto-bind-tunnel
[no] shutdown
A:Dut-PE1>config>service>vprn# info // vprn-2
……………
bgp-ipvpn
mpls
anysec-encryption-group <2>
auto-bind-tunnel
[no] shutdown
Two VPRN services with same CA and SAK
SAK for encrypted service shows an example of a network where VPRN-1 and VPRN-2 share the same CA and SAK.
The following example shows the configuration of CA1 on PE1 from SAK for encrypted service.
MD-CLI
[ex:/configure macsec]
A:admin@Dut-PE1# info
connectivity-association "ca1" {
admin-state enable
cipher-suite gcm-aes-xpn-256
anysec true
static-cak {
pre-shared-key 1 {
encryption-type aes-256-cmac
cak "xsMqlX30xmmMVQtpXQIu1Rvx14/2E81okd56kbMjwGTyjQhsUxSJq7uSA7jZEtOW hash2"
cak-name "123456"
}
}
}
classic CLI
*A:Dut-PE1>config>macsec# info
----------------------------------------------
connectivity-association "ca1" create
anysec
cipher-suite gcm-aes-xpn-256
static-cak
pre-shared-key 1 encryption-type aes-256-cmac create
ckn "11“
cak cak-1
exit
exit
no shutdown
exit
----------------------------------------------
The following is an example ANYsec configuration for VPRN-1 and VPRN-2 in the preceding figure.
MD-CLI
!*[gl:/configure anysec]
A:admin@Dut-AC# info
reserved-label-block "es-reserved-block"
mka-over-ip {
mka-udp-port 10000
}
security-termination-policies {
policy "system-ip" {
admin-state enable
local-address 2.1.1.1
protocol sr-isis
}
}
service-encryption {
encryption-group "1" {
security-termination-policy "system-ip"
encryption-label 32
ca-name "ca1"
peer 4.1.1.1 {
admin-state enable
}
}
}classic CLI
A:Dut-PE1>config>anysec# info
----------------------------------------------
mka-over-ip
Udp-port 10000
reserved-label-block “es-reserved-block”
service-encryption
security-termination-policies
policy “system-ip”
protocol sr-isis
local-address 2.1.1.1
no shutdown
exit
encryption-group “1”
security-termination-policy “system-ip”
encryption-label ES-1
ca-name “ca1”
peers
peer 4.1.1.1
no shutdown
exit
exit
----------------------------------------------
In the following example, the same EG is assigned to two VPRN services
MD-CLI
[ex:/configure service]
A:admin@Dut-AC# info
vprn "vprn-1" {
bgp-ipvpn {
mpls {
anysec-encryption-group "1"
}
}
}
vprn "vprn-2" {
bgp-ipvpn {
mpls {
anysec-encryption-group "1"
}
}
}
classic CLI
A:Dut-PE1>config>service>vprn# info // vprn-1
……………
bgp-ipvpn
mpls
anysec-encryption-group <1>
auto-bind-tunnel
[no] shutdown
A:Dut-PE1>config>service>vprn# info // vprn-2
……………
bgp-ipvpn
mpls
anysec-encryption-group <1>
auto-bind-tunnel
[no] shutdown