Network Group Encryption Helper
This chapter describes the network group encryption (NGE) helper.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 23.3.R1. Network group encryption (NGE) helpers require use of the VSR-a or the VSR-I and can be deployed with 7750 SR and 7950 XRS.
Overview
The NGE helper enables NGE security for services configured on the 7750 SR or 7950 XRS (hereafter referred to as the router) that require additional confidentiality and integrity.
Multiple NGE helpers can be deployed with a router depending on the encrypted services throughput requirements required by the operator. General architecture using an NGE helper shows the general architecture using an NGE helper.
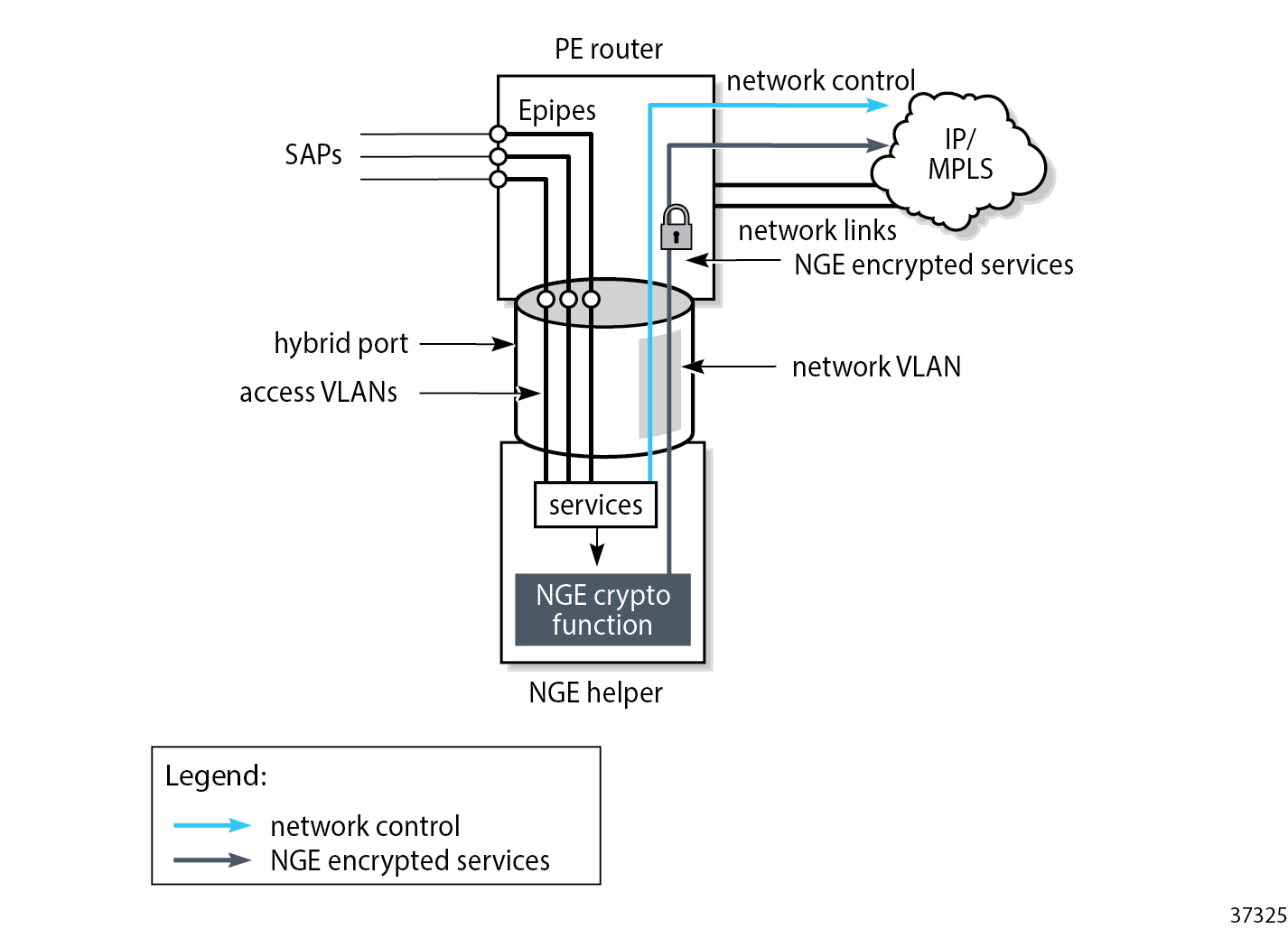
Each NGE helper is connected to the router using an access interface and a network interface, where both interfaces are configured on the NGE helper and on the router. A hybrid port can be used on the router and NGE helper to optimize the deployment, so one physical port is required on the router and NGE helper.
SAPs are configured on the router using an Epipe directed toward the NGE helper access interface. Unencrypted traffic that is received on the SAP interface is sent through the Epipe to the NGE helper which encrypts the traffic before sending it toward the network. The network interface on the NGE helper is enabled with minimal network control plane functions toward the router. The network control plane of the router performs the majority of network level processing and forwarding of NGE encrypted services.
The NGE helper supports services-based encryption, including:
-
VPRN encryption
-
SDP encryption
-
PW-template encryption
Router interface encryption and port-level encryption are not supported by the NGE helper.
Scenarios for encrypting services
The following main services scenarios are supported:
-
VPRN encryption using auto-bind services for both MPLS (LDP or RSVP-TE signaled tunnels) and GRE transport
This scenario uses BGP to advertise the NGE helper IP address to remote NGE helpers. Remote NGE helpers can then send VPRN traffic to other NGE helpers to be processed for the associated destination SAP. This scenario uses VPRN-level NGE.
-
NG-MVPN with VPRN encryption using MLDP tunnels from the NGE helper to the router
This scenario uses a similar setup to VPRN encryption, with the difference that MLDP tunnels are also established between the NGE helper and the router where the point-to-multipoint tree branches from for the NG-MVPN service. This scenario uses VPRN-level NGE.
-
T-LDP signaled Epipe or VPLS services using LDP or RSVP-TE transport tunnels
T-LDP sessions are established from the NGE helper to the remote PEs to establish Epipe or VPLS services. The transport of these services focuses on LDP or LDP with RSVP-TE. Where GRE is possible, GRE support of VPLS or VPWS mainly uses BGP VPLS or BGP VPWS with auto-GRE SDP, because this use case is prevalent with SAR-Hm/Hmc deployments. This scenario uses SDP-level NGE.
-
L2 services using BGP VPLS or BGP VPWS auto-GRE SDP
This scenario is similar to the VPRN auto-bind scenario, except that a BGP session is used to advertise L2 routes to and from the NGE helper where remote PEs can send GRE L2 packets encrypted with the associated NGE configuration under the pw-template context.
Configuration
NGE configuration
NGE configuration is managed by the Network Services Platform Network Functions Manager - Packet (NSP NFM-P). Operators use the NSP NFM-P to configure:
-
global encryption labels
-
key groups
-
VPRN-level encryption – setting the inbound and outbound key groups on VPRN-based services
-
SDP-level encryption – setting the inbound and outbound key groups on selected SDPs
-
PW-template level encryption – setting the inbound and outbound key groups on selected PW templates
Group encryption configuration
In this example, encryption keygroup 1 is configured manually on NGE-1:
# on NGE-1:
configure {
group-encryption {
group-encryption-label 100
encryption-keygroup 1 {
keygroup-name "KG1"
active-outbound-security-association 1
security-association 1 {
authentication-key 0x1111111100000000111111110000000011111111000000001111111100000000
encryption-key 0x11111111000000001111111100000000
}
security-association 2 {
authentication-key 0x2222222200000000222222220000000022222222000000002222222200000000
encryption-key 0x22222222000000002222222200000000
}
security-association 3 {
authentication-key 0x3333333300000000333333330000000033333333000000003333333300000000
encryption-key 0x33333333000000003333333300000000
}
security-association 4 {
authentication-key 0x4444444400000000444444440000000044444444000000004444444400000000
encryption-key 0x44444444000000004444444400000000
}
}The authentication key and the encryption key are configured as cleartext. After configuration, they are never displayed in their cleartext form. The security parameter index (SPI) value in the security association is a node-wide unique value.
PW-template configuration
On NGE-1, PW template 2 is configured with encryption keygroup 1:
# on NGE-1:
service {
pw-template "2" {
auto-gre-sdp true
vc-type vlan
split-horizon-group {
name "SHG"
}
encryption-keygroup {
inbound 1
outbound 1
}
}BGP configuration
BGP must be enabled on the router and the NGE helper for the L2-VPN address family for the following services:
-
BGP VPWS with auto-GRE SDP (where NGE is configured under the pw-template context)
-
BGP VPLS with auto-GRE SDP (where NGE is configured under the pw-template context)
BGP topology for learning BGP label routes shows the BGP topology for learning BGP label routes for those services.
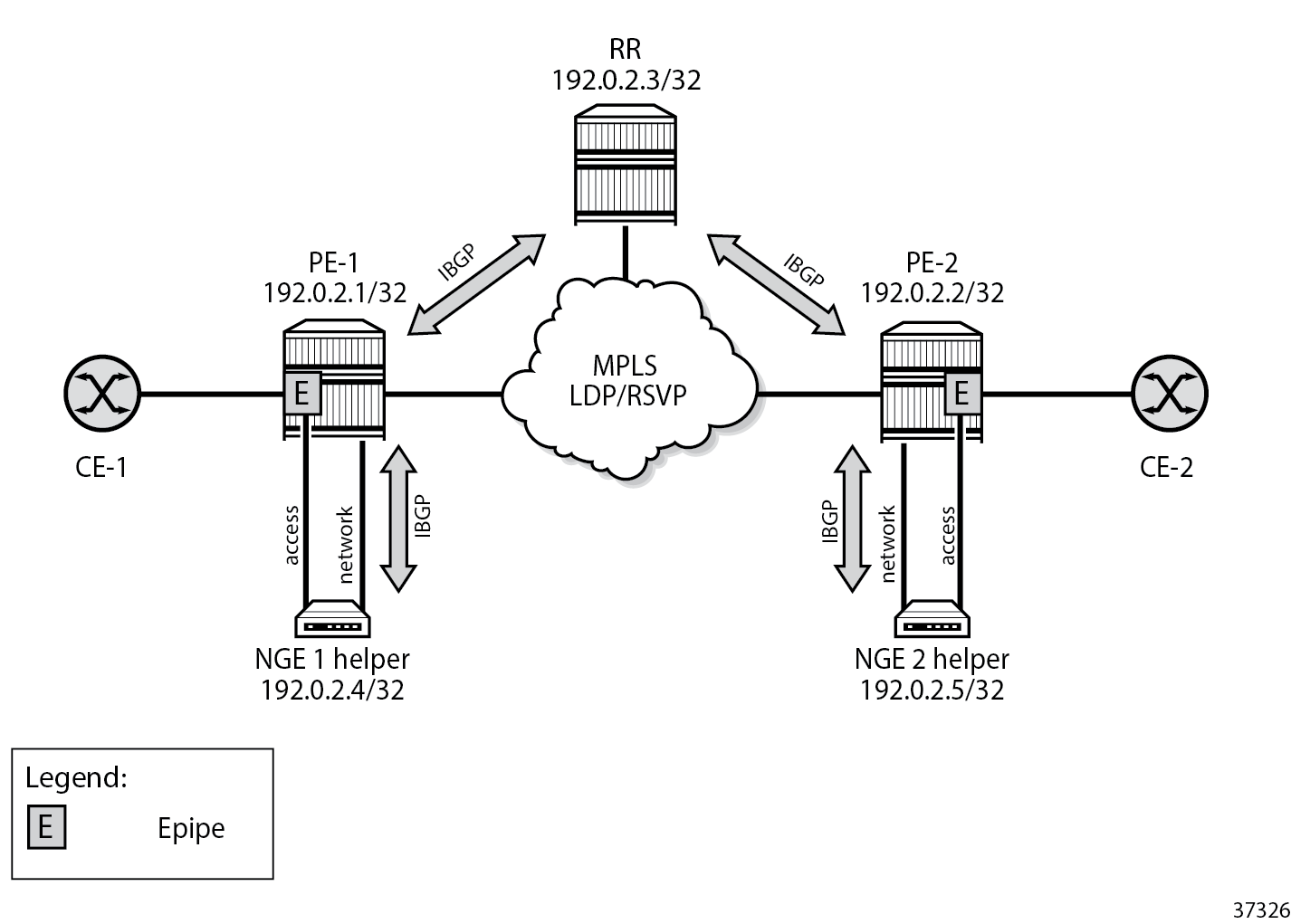
The following configures BGP on PE-1 to support the NGE 1 helper function:
# on PE-1:
configure {
router "Base" {
bgp {
rapid-withdrawal true
group "PE-1-NGE-1-RR" {
peer-as 64496
family {
l2-vpn true
}
cluster {
cluster-id 192.0.2.1
}
}
group "core-RR" {
peer-as 64496
family {
l2-vpn true
}
}
neighbor "192.0.2.3" {
group "core-RR"
}
neighbor "192.0.2.4" {
group "PE-1-NGE-1-RR"
}
} The following configures BGP on PE-2 to support the NGE 2 helper function:
# on PE-2:
configure {
router "Base" {
bgp {
rapid-withdrawal true
group "PE-2-NGE-2-RR" {
peer-as 64496
family {
l2-vpn true
}
cluster {
cluster-id 192.0.2.2
}
}
group "core-RR" {
peer-as 64496
family {
l2-vpn true
}
}
neighbor "192.0.2.3" {
group "core-RR"
}
neighbor "192.0.2.5" {
group "PE-2-NGE-2-RR"
}
}The BGP configuration on the NGE-1 helper is as follows:
# on NGE-1:
configure {
router "Base" {
bgp {
rapid-withdrawal true
group "RR-PE-1" {
peer-as 64496
family {
l2-vpn true
}
}
neighbor "192.0.2.1" {
group "RR-PE-1"
}
}The BGP configuration on the NGE-2 helper is as follows:
# on NGE-2:
configure {
router "Base" {
bgp {
rapid-withdrawal true
group "RR-PE-2" {
peer-as 64496
family {
l2-vpn true
}
}
neighbor "192.0.2.2" {
group "RR-PE-2"
}
}
Services configuration
BGP VPLS or BGP VPWS with auto-GRE SDP
NGE helper for BGP VPLS or BGP VPWS using GRE SDPs with auto-GRE SDP shows the operation of the NGE helper for BGP VPLS and BGP VPWS services that use GRE SDPs when auto-GRE SDP is configured on the associated PW template.
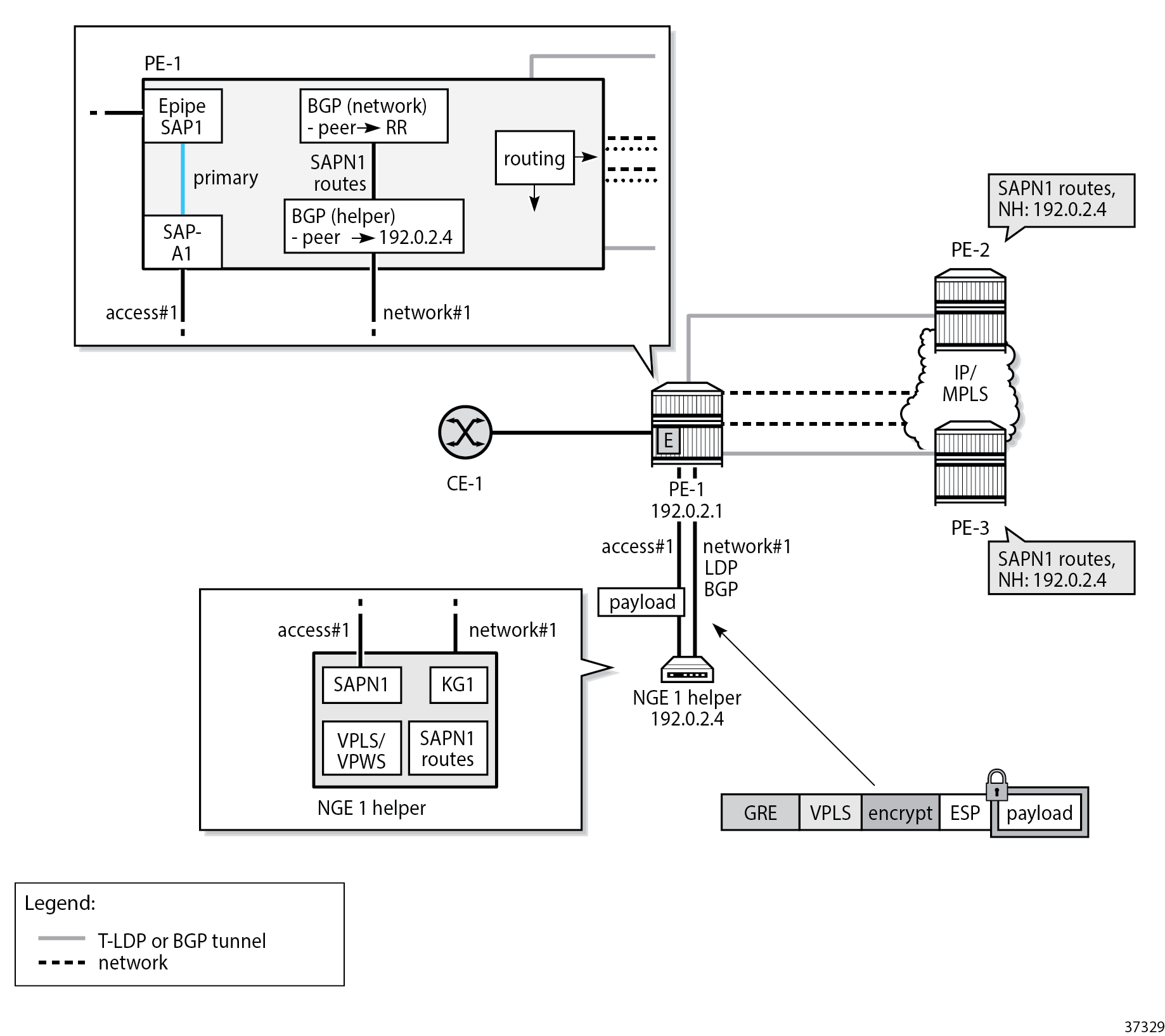
In this scenario, the VPLS or VPWS SAPN1 is configured on the NGE-1 helper. On PE-1, a local Epipe is configured that originates from the customer facing SAP1 and terminates on SAP-A1 connected to the NGE-1 helper. On PE-1, Epipes 100101 and 100201 are configured as follows:
# on PE-1:
configure {
service {
epipe "Epipe-100101" {
admin-state enable
service-id 100101
customer "1"
sap lag-1:101 {
description "toward NGE-1 Epipe 101"
}
sap lag-11:101.1 {
description "toward CE"
}
}
epipe "Epipe-100201" {
admin-state enable
service-id 100201
customer "1"
sap lag-1:201 {
description "toward NGE-1 VPLS 201"
}
sap lag-11:201.1 {
description "toward CE"
}
}On PE-1, the following network configurations are required to support encrypted services from the NGE-1 helper:
-
any routing options that allow GRE packets received from the NGE helper to be routed to remote PEs
-
BGP sessions for the L2-VPN address family, as described in the BGP configuration section
On the NGE-1 helper, the configuration includes:
-
VPLS or VPWS SAPN1
-
BGP session to PE-1 for the L2-VPN address family
-
BGP VPLS or BGP VPWS using PW templates with auto-GRE SDP enabled
-
NGE enabled on the PW templates for encrypting the VPLS or VPWS services using the PW templates
On NGE-1, Epipe 101 is a BGP VPWS with auto-GRE SDP. PW template 2 is configured with encryption keygroup 1. Epipe 101 is configured as follows:
# on NGE-1:
configure {
service {
pw-template "2" {
auto-gre-sdp true
vc-type vlan
split-horizon-group {
name "SHG"
}
encryption-keygroup {
inbound 1
outbound 1
}
}
epipe "Epipe-101" {
admin-state enable
description "BGP VPWS auto-gre SDP_PW template 2"
service-id 101
customer "1"
bgp 1 {
route-distinguisher "101:1"
route-target {
export "target:101:1"
import "target:101:1"
}
pw-template-binding "2" {
}
}
bgp-vpws {
admin-state enable
local-ve {
name "pe-1"
id 1
}
remote-ve "pe-2" {
id 2
}
}
sap lag-1:101 {
}
}
In a similar way, VPLS 201 is a BGP VPLS with auto-GRE SDP. PW template 2 is configured with encryption keygroup 1. VPLS 201 is configured as follows:
# on NGE-1:
configure {
service {
vpls "VPLS-201" {
admin-state enable
description "BGP VPLS auto-gre SDP_PW template 2"
service-id 201
customer "1"
bgp 1 {
route-distinguisher "201:1"
route-target {
export "target:201:1"
import "target:201:1"
}
pw-template-binding "2" {
}
}
bgp-vpls {
admin-state enable
maximum-ve-id 10
ve {
name "pe-1"
id 1
}
}
sap lag-1:201 {
}
}
Verification
The following base information for the services shows that the services are operationally up, as well as their SAPs and SDP bindings:
[/]
A:admin@NGE-1# show service id 101 base
===============================================================================
Service Basic Information
===============================================================================
Service Id : 101 Vpn Id : 0
Service Type : Epipe
MACSec enabled : no
Name : Epipe-101
Description : BGP VPWS auto-gre SDP_PW template 2
Customer Id : 1 Creation Origin : manual
Last Status Change: 03/31/2023 15:44:58
Last Mgmt Change : 03/31/2023 15:44:58
Test Service : No
Admin State : Up Oper State : Up
---snip---
-------------------------------------------------------------------------------
Service Access & Destination Points
-------------------------------------------------------------------------------
Identifier Type AdmMTU OprMTU Adm Opr
-------------------------------------------------------------------------------
sap:lag-1:101 q-tag 8936 8936 Up Up
sdp:32767:4294967295 SB(192.0.2.5) BgpVpws 0 8890 Up Up
===============================================================================
[/]
A:admin@NGE-1# show service id 201 base
===============================================================================
Service Basic Information
===============================================================================
Service Id : 201 Vpn Id : 0
Service Type : VPLS
MACSec enabled : no
Name : VPLS-201
Description : BGP VPLS auto-gre SDP_PW template 2
Customer Id : 1 Creation Origin : manual
Last Status Change: 03/31/2023 15:42:13
Last Mgmt Change : 03/31/2023 15:44:58
Etree Mode : Disabled
Admin State : Up Oper State : Up
MTU : 1514
SAP Count : 1 SDP Bind Count : 1
---snip---
-------------------------------------------------------------------------------
Service Access & Destination Points
-------------------------------------------------------------------------------
Identifier Type AdmMTU OprMTU Adm Opr
-------------------------------------------------------------------------------
sap:lag-1:201 q-tag 8936 8936 Up Up
sdp:32766:4294967294 SB(192.0.2.5) BgpVpls 0 8890 Up Up
===============================================================================
The following command shows the encryption keygroup 1 with the associated SDPs: SDP 32767 is auto-provisioned by BGP-VPWS in Epipe 101, and SDP 32766 by BGP-VPLS in VPLS 201.
[/]
A:admin@NGE-1# show group-encryption encryption-keygroup 1
===============================================================================
Encryption Keygroup Configuration Detail
===============================================================================
Keygroup Id : 1
Keygroup Name : KG1
Description : None
Authentication Algo: sha256
Encryption Algo : aes128
Active Outbound SA : 1
Activation Time : 03/31/2023 15:42:12
-------------------------------------------------------------------------------
Security Associations
-------------------------------------------------------------------------------
Spi : 1
Install Time : 03/31/2023 15:42:12
Key CRC : 0xf57dcffc
Spi : 2
Install Time : 03/31/2023 15:42:12
Key CRC : 0x26134d07
Spi : 3
Install Time : 03/31/2023 15:42:12
Key CRC : 0xde19ce91
Spi : 4
Install Time : 03/31/2023 15:42:12
Key CRC : 0x5bbf4eb0
-------------------------------------------------------------------------------
Encryption Keygroup Forwarded Statistics
-------------------------------------------------------------------------------
Encrypted Pkts : 22 Encrypted Bytes : 2124
Decrypted Pkts : 22 Decrypted Bytes : 2124
-------------------------------------------------------------------------------
Encryption Keygroup Outbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Other : 0
-------------------------------------------------------------------------------
Encryption Keygroup Inbound Discarded Statistics (Pkts)
-------------------------------------------------------------------------------
Total Discard : 0 Invalid Spi : 0
Authentication Failure *: 0 Padding Error : 0
Other : 0
---------------------------------------------------------------
SDP Keygroup Association Table
---------------------------------------------------------------
SDP ID Direction
---------------------------------------------------------------
32766 Inbound Outbound
32767 Inbound Outbound
---------------------------------------------
Inbound Keygroup SDP Association Count: 2
Outbound Keygroup SDP Association Count: 2
---------------------------------------------------------------
-------------------------------------------------------------------------------
VPRN Keygroup Association Table
-------------------------------------------------------------------------------
No entries found
-------------------------------------------------------------------------------
Network Interface Association Table
-------------------------------------------------------------------------------
No entries found
-------------------------------------------------------------------------------
Wlan-GW Keygroup Association Table
-------------------------------------------------------------------------------
No entries found
===============================================================================
* indicates that the corresponding row element may have been truncated.
Conclusion
NGE is a security solution for encrypting traffic flows on a per-service basis. The NGE helper extends the NGE solution to 7750 SR and 7950 XRS platforms where larger core and PE nodes are required to participate with other NGE-capable nodes.