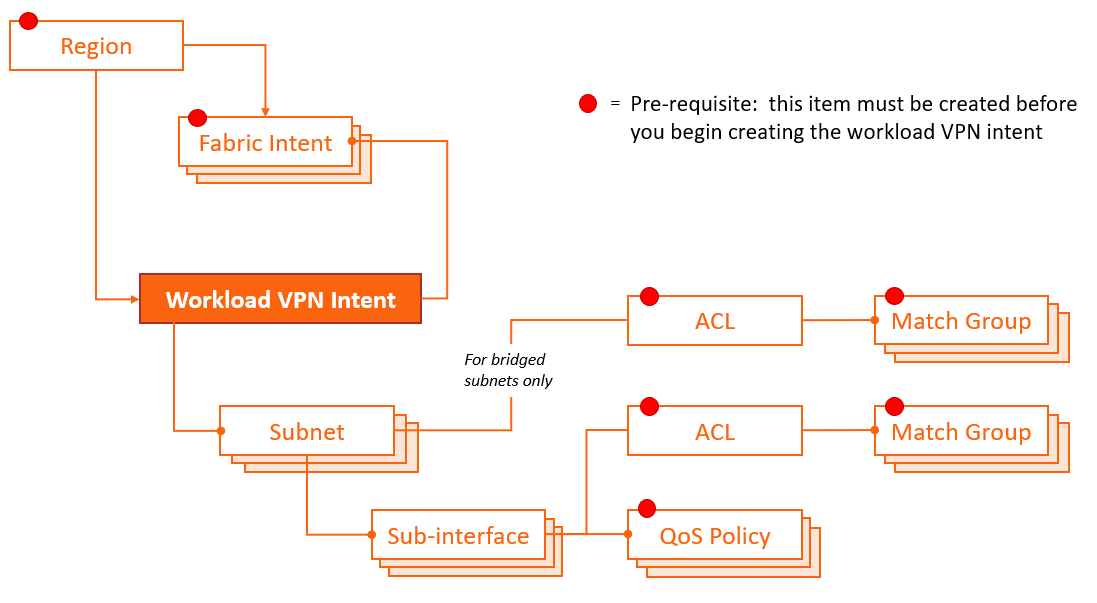
Elements of a workload VPN intent
A workload VPN intent must be associated with specific fabrics within a deployment region (or "region"). The region manages the deployment pipeline, which organizes the sequential deployment of configuration data to the various nodes participating in the intent.
To represent the set of resources available to a workload, a workload VPN intent uses a hierarchical structure consisting of:
- Fabrics: a workload VPN intent can span one or more fabrics that you have already defined in the system.
- Subnets: each subnet defines a subset of the participating fabrics. Subnets can be
either bridged or routed.
A bridged subnet with one or more IP addresses configured can be assigned an access control list (ACL), a set of rules that permit, or reject, any traffic that matches those IP addresses. These rules are applied on the integrated routing and bridging (IRB) interface. The set of IP addresses is stored as a match group; the ACL then assembles a set of match groups, adds further defining properties, and indicates whether to accept or reject the matching packets.
- Sub-interfaces: each sub-interface identifies a set of edge link ports and LAGs
within a particular subnet, and across which the workload traffic can be bridged or
routed.
A sub-interface can be associated with:
- Access Control Lists (ACL): each sub-interface can be assigned a set of rules that permit, or reject, any traffic that matches those IP addresses. The set of IP addresses is stored as a match group; the ACL then assembles a set of match groups, adds further defining properties, and indicates whether to accept or reject the matching packets.
- QoS profiles: each sub-interface can be assigned a set of rules for prioritizing traffic.
Fabrics
Every workload VPN intent allocates resources that belong to one or more fabric intents that already exist in the system.
As part of workload VPN intent design, you must select the participating fabric intent or intents. All traffic managed by the workload VPN intent is confined to these participating fabric intents (and, more specifically, only to the subnets and sub-interfaces you select within those fabric intents).
A single fabric intent can support multiple workload VPN intents.
Subnets
A sub-network, or subnet, is a set of one or more nodes on a selected fabric.
Types of subnets
When creating a workload VPN intent, you identify each subnet as either bridged, routed, or loopback.
- Bridged subnets can be assigned to a network-instance of type
MAC-VRF. They are associated with a MAC-VRF network instance and allow for
configuration of bridge table and VLAN ingress and egress mapping.
When adding a bridged subnet to a workload VPN intent, you associate an IP Anycast Gateway, and can associate an ACL.
With a gateway IP address, a MAC-VRF is attached to the default or ip-vrf network-instance by a single integrated routing and bridging (IRB) interface, which allows routing between different MAC-VRF instances of a particular tenant or group of servers.
Bidirectional forwarding detection (BFD) is supported on bridged subnets; a gateway IP address is required.
If enabled, MAC duplication detection monitors MAC addresses that move between sub-interfaces and between a sub-interface and an EVPN. A MAC address is considered a duplicate when the move count is greater than the number of moves within the configured monitoring window. Upon exceeding the specified number of moves, the system retains the prior local destination of the MAC and executes a specified action. You can enable monitoring for a subnet or for a sub-interface; for a sub-interface, MAC duplication detection must be enabled on the subnet to which the sub-interface belongs).
- Routed subnets can be assigned to a network-instance of type mgmt, default, or ip-vrf. They allow for configuration of IPv4 and IPv6 settings.
- Loopback subnets are assigned to loopback interfaces. Loopback interfaces are virtual interfaces that are always up, providing a stable source or destination from which packets can always be originated or received. When you create a loopback subnet, you must specify /32 (IPV4) or /128 (IPV6) host IP addresses to associate with a loopback interface.
Enabling layer 2 proxy ARP
L2 proxy ARP is applicable to bridged subnets. When proxy ARP is enabled for a MAC-VRF, a table is created that contains entries related to the broadcast domain. The table can include entries that dynamically learned, EVPN-learned, or duplicate entries (if duplicate IP detection is enabled). Static entries are not supported.
You can modify the size of the proxy ARP table; by default, the table can have 250 entries.Enabling layer 3 proxy ARP and layer 3 proxy ARP ND
- a bridged subnet that is configured with a gateway IP address (IRB interface)
- routed subnets
Sub-interfaces
For each subnet, you identify the set of sub-interfaces over which tenant traffic can travel. These sub-interfaces can be physical or logical ports, including link aggregation groups (LAGs).
Each LAG you select as a sub-interface must have been configured previously within the system as part of the fabric intent design. The interfaces participating in a LAG can be located on a single node or on multiple nodes (constituting a multi-home LAG or MH-LAG).
For each sub-interface, you can define quality of service (QoS) profiles that prioritize traffic, and an access control list that identifies the packets to be accepted or rejected.
The Fabric Services system supports MAC duplication detection on sub-interfaces if MAC duplication detection is enabled on the subnet to which the sub-interface belongs.
QoS profiles
The Fabric Services System supports quality of service (QoS) policies for assigning traffic to forwarding classes and remarking traffic at egress before it leaves a router. A QoS profile can be one of the following:
- QoS classifier profile
A QoS classifier profile maps incoming packets to the appropriate forwarding classes.
- QoS rewrite-rule profile
DSCP rewrite-rule policies mark outgoing packets with an appropriate DSCP value based on the forwarding class.
ACL profiles
An access control list (ACL) profile defines a set of packet types that should be either accepted or rejected.
An ACL profile is assembled from one or more match groups. Each match group defines a particular set of properties that could be possessed by packets. The ACL then uses these match groups to specify a set of packet properties, and then includes an instruction to either accept or reject packet that conform to those properties. Match groups thereby provide an easy way to define a set of IP addresses one time, and then re-use that information in multiple ACLs.
When assigned to a bridged subnet or a sub-interface in any type of subnet, the ACL defines the traffic that is permitted on those workload VPN intent resources. When an ACL is applied to a bridged subnet with a gateway configured, the IP filter is applied to the IRB interface.
Routers
A router is a logical object that represents a single EVPN VXLAN IP-VRF instance that can span multiple devices. Routers are responsible for routing between all subnets attached to the router. You can attach subnets and gateways within the subnets to routers. When you create a workload intent and assign IP gateway v4 and v6 addresses, a default router is created. You also can create additional routers objects.
By default, when you create a region, the system provides EVPN Instance (EVI) and Virtual Network Identifier (VNI) pools with a range of values from 1-65535. These range of values can be modified in the region properties of the Fabric Services System.
The VNI and EVI default values are derived from settings in the region properties. You can edit the VNI and specify whether the route targets are automatically derived or you can manually provide route targets.
When the route targets are automatically derived:
- You can set specific VNI and route targets per subnet or router object within a workload VPN intent. These settings are used when there are existing services in the data center (DC) on a DC-GW or other fabric where the existing services (network-instances) need to stretch to the new data center managed by the Fabric Services System. The route targets and VNI used for the network-instance must be specified.
- If you want the Fabric Services System to automatically derive a route target, but need to ensure that the values used do not overlap with existing services in the data center, you can set a specific pool of EVI or VNI from which the Fabric Services System allocates VNI and route targets for an ip-vrf or mac-vrf object within a workload intent.