Security
This chapter provides information to configure security parameters.
Topics in this chapter include:
Authentication, authorization, and accounting
This section describes authentication, authorization, and accounting (AAA) used to monitor and control network access on the 7705 SAR. Network security is based on a multi-step process. The first step, authentication, validates a user’s name and password. The second step is authorization, which allows the user to access and execute commands at various command levels based on profiles assigned to the user.
The third step, accounting, keeps track of the activity of a user who has accessed the network. The type of accounting information recorded can include a history of the commands executed, the amount of time spent in the session, the services accessed, and the data transfer size during the session. The accounting data can then be used to analyze trends, and also for billing and auditing purposes.
You can configure the 7705 SAR to use local, Remote Authentication Dial In User Service (RADIUS), or Terminal Access Controller Access Control System Plus (TACACS+) security to validate users who attempt to access the router by console, Telnet, SSH, SFTP, SCP, or FTP. You can select the authentication order that determines the authentication method to try first, second, and third.
The 7705 SAR supports the following security features:
-
RADIUS can be used for authentication, authorization, and accounting
-
TACACS+ can be used for authentication, authorization, and accounting
-
local security can be implemented for authentication and authorization
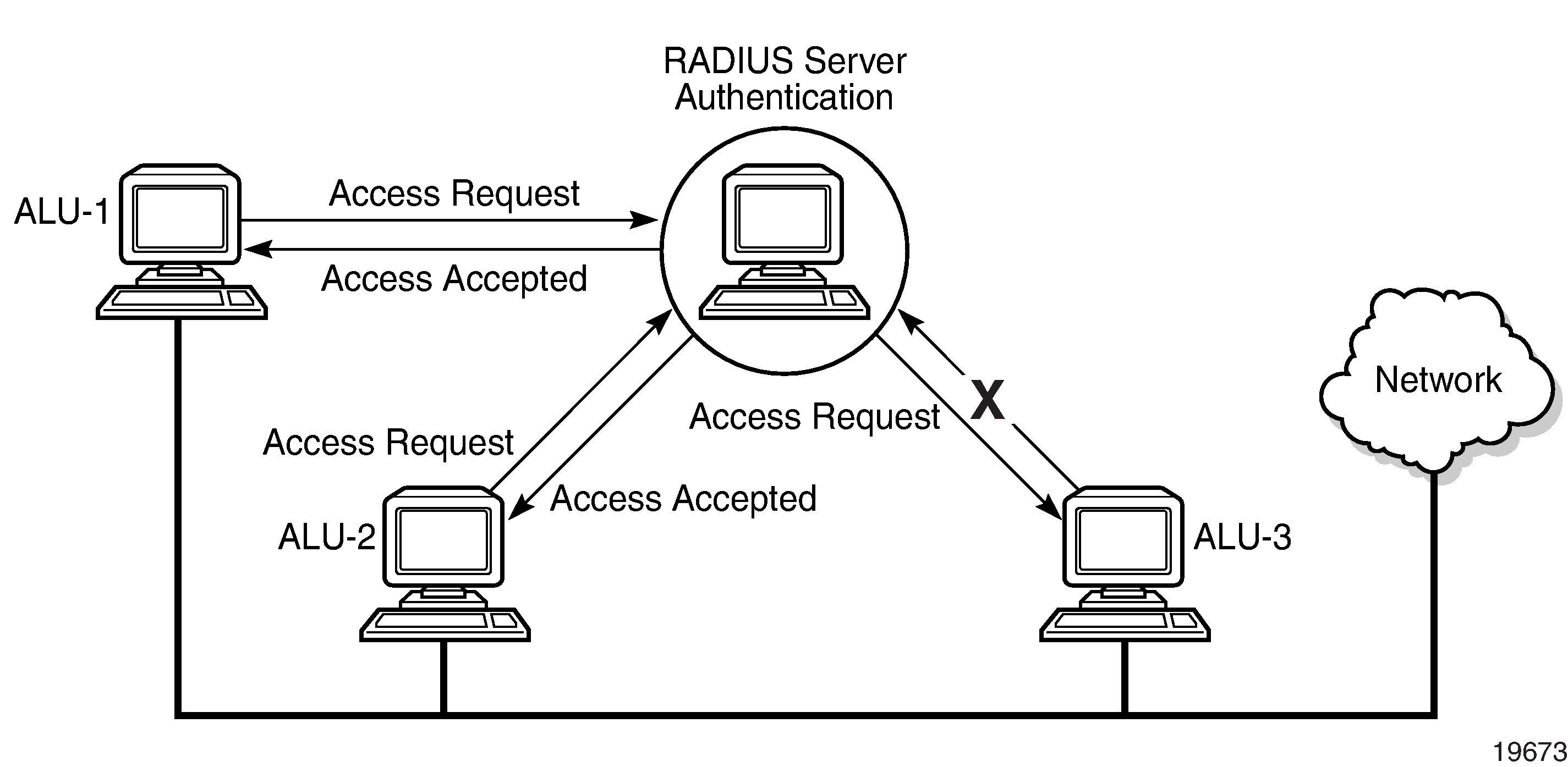
The following figure depicts end-user access requests sent to a RADIUS server. After validating the usernames and passwords, the RADIUS server returns an access accept message to the users on ALU-1 and ALU-2. The username and password from ALU-3 could not be authenticated; therefore, access was denied.
Authentication
Authentication validates a username and password combination when a user attempts to log in.
When a user attempts to log in through the console or through Telnet, SSH, SFTP, SCP, or FTP, the 7705 SAR client sends an access request to a RADIUS, TACACS+, or local database.
Transactions between the client and a RADIUS server are authenticated through the use of a shared secret. The secret is never transmitted over the network. User passwords are sent encrypted between the client and RADIUS server, which prevents someone snooping on an insecure network to learn password information.
If the RADIUS server does not respond within a specified time, the router issues the access request to the next configured servers. Each RADIUS server must be configured identically to guarantee consistent results. Up to five RADIUS servers can be configured.
If a server is unreachable, it is not used again by the RADIUS application until 30 seconds have elapsed, to give the server time to recover from its unreachable state. After 30 seconds, the unreachable server becomes available again for the RADIUS application.
If, within the 30 seconds, the RADIUS server receives a valid response to a previously sent RADIUS packet on that unreachable server, the server immediately becomes available again.
If any RADIUS server rejects the authentication request, it sends an access reject message to the router. In this case, no access request is issued to any other RADIUS servers. However, if other authentication methods such as TACACS+ or local are configured, then these methods are attempted. If no other authentication methods are configured, or all methods reject the authentication request, then access is denied.
The user login is successful when the RADIUS server accepts the authentication request and responds to the router with an access accept message.
Implementing authentication without authorization for the 7705 SAR does not require the configuration of VSAs (vendor-specific attributes) on the RADIUS server. However, users, user access permissions, and command authorization profiles must be configured on each router.
Any combination of these authentication methods can be configured to control network access from a 7705 SAR router:
Local authentication
Local authentication uses PKI or usernames and passwords configured on the router to authenticate login attempts. The usernames and passwords are local to each router, not to user profiles.
By default, local authentication is enabled. When one or more of the other security methods are enabled, local authentication is disabled. Local authentication is restored when the other authentication methods are disabled. Local authentication is attempted if the other authentication methods fail and local is included in the authentication order password parameters.
Remote security servers such as RADIUS or TACACS+ are not enabled.
Password hashing
The 7705 SAR supports two algorithms for user password hashing: bcrypt, which is the default algorithm, and PBKDF2. The PBKDF2 algorithm uses the SHA-2 and SHA-3 sets of cryptographic hash functions for password hashing.
A system administrator can change the default bcrypt password hashing algorithm to the PBKDF2 algorithm using the config>system>security>password>hashing command.
When the password hashing algorithm is changed to PBKDF2 SHA-2 or PBKDF2 SHA-3, users must change their passwords using the /password command to use the new hashing algorithm. The system administrator must then perform an admin>save command to store the new user passwords in the system configuration file.
After a password hashing change, any user logging in to the system who did not update their password to use the new hashing algorithm will be prompted to enter their old password the next time they log in. When the password is entered successfully, the user is prompted to enter a new password that will be hashed using the new algorithm.
RADIUS authentication
Remote Authentication Dial-In User Service (RADIUS) is a client/server security protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize access to the requested system or service.
RADIUS allows administrators to maintain user profiles in a shared central database and provides better security, allowing a company to set up a policy that can be applied at a single administered network point.
RADIUS server selection
Up to five RADIUS servers can be configured. They can be selected to authenticate user requests in two ways, using either the direct method or the round-robin method. The default method is direct.
Direct
In direct mode, the first server, as defined by the server-index command, is the primary server. This server is always used first when authenticating a request.
Round-robin
In round-robin mode, the server used to authenticate a request is the next server in the list, following the last authentication request. For example, if server 1 is used to authenticate the first request, server 2 is used to authenticate the second request, and so on.
TACACS+ authentication
Terminal Access Controller Access Control System, commonly referred to as TACACS, is an authentication protocol that allows a remote access server to forward a user's login password to an authentication server to determine whether access can be allowed to a system. TACACS is an encryption protocol and therefore less secure than the later Terminal Access Controller Access Control System Plus (TACACS+) and RADIUS protocols.
TACACS+ and RADIUS have largely replaced earlier protocols in the newer or recently updated networks. TACACS+ uses Transmission Control Protocol (TCP) and RADIUS uses the User Datagram Protocol (UDP). TACACS+ is popular as TCP is thought to be a more reliable protocol. RADIUS combines authentication and authorization. TACACS+ separates these operations.
Authorization
Authorization operates by applying a profile based on username and password configurations after network access is granted. For RADIUS authorization, the profiles are configured locally on the router or downloaded using VSAs from a RADIUS server. For TACACS+ authorization, local profiles configured on the router can be used or remote profiles configured on the TACACS+ server can be used where each command is sent to the TACACS+ server for authorization. See RADIUS VSAs and TACACS+ services and VSAs.
When using authorization, maintaining a user database on the router is not required. Usernames can be configured on the RADIUS server. Usernames and their associated passwords are temporary and are not saved in the configuration database when the user session terminates.
TACACS+ separates the authentication and authorization functions. RADIUS combines the authentication and authorization functions.
Local authorization
Local authorization uses user profiles and user access information after a user is authenticated. The profiles and user access information specify the actions the user is allowed to perform.
By default, local authorization is enabled. Local authorization is disabled only when a different remote authorization method is configured (RADIUS authorization or TACACS+). Local authorization is restored when RADIUS authorization is disabled.
You must configure profile and user access information locally.
RADIUS authorization
RADIUS authorization grants or denies access permissions for a 7705 SAR router. Permissions include the use of FTP, Telnet, SSH (SCP and SFTP), and console access. When granting Telnet, SSH (SCP and SFTP), and console access to the 7705 SAR router, authorization can be used to limit what CLI commands the user is allowed to issue and which file systems the user is allowed or denied access to.
After a user has been authenticated using RADIUS (or another method), the 7705 SAR router can be configured to perform authorization. The RADIUS server can be used to:
-
download the user profile to the 7705 SAR router
-
send the profile name that the node should apply to the 7705 SAR router
- control file access using VSAs (see RADIUS VSAs)
If RADIUS authentication is successful and no authorization is configured for the user on the RADIUS server, local (router) authorization is attempted if it is configured using the authentication-order command. When authorization is configured and profiles are downloaded to the router from the RADIUS server, the profiles are considered temporary configurations and are not saved when the user session terminates. The temporary profiles are only downloaded if the user authenticates via RADIUS. RADIUS-based authorization is not supported for users who authenticate locally or via TACACS+.
The following table lists the supported authorization configurations.
|
User |
Local authorization |
RADIUS authorization |
|---|---|---|
|
7705 SAR configured user |
✓ |
|
|
RADIUS server configured user |
✓ |
✓ |
|
TACACS+ server configured user |
✓ |
When using authorization, maintaining a user database on the router is not required. Usernames can be configured on the RADIUS server. Usernames are temporary and are not saved in the configuration when the user session terminates. Temporary user login names and their associated passwords are not saved as part of the configuration.
TACACS+ authorization
Like RADIUS authorization, TACACS+ grants or denies access permissions for a 7705 SAR router. The TACACS+ server sends a response based on the username and password.
TACACS+ command authorization operates in the following ways:
- All users who authenticate via TACACS+ can use a single common command authorization profile that is configured locally on the router.
- Every command that a user attempts is sent to the TACACS+ server for authorization.
- The TACACS+ default template can be configured (tacplus_default) and vendor-specific attributes (VSAs) can be used to control file access. The use-default-template command must be enabled to configure all other access parameters locally. See TACACS+ services and VSAs for more information.
To use a single common default command authorization profile to control command authorization for TACACS+ users, enable the TACACS+ default user template and configure the template to point to a valid local profile. The local profile is then used for command authorization. TACACS+ authorization must be disabled.
- CLI syntax:
-
config>system>security tacplus use-default-template no authorization user-template tacplus_default profile user-profile-name
When the tacplus authorization command is enabled, each CLI command that the user issues is sent to the TACACS+ server for authorization. The authorization request contains the first word of the CLI command as the value for the TACACS+ command and all following words as a command argument. Quoted values are expanded so that the quotation marks are stripped off and the enclosed values are seen as one command or command argument.
Accounting
Accounting tracks user activity to a specific host. The 7705 SAR supports RADIUS and TACACS+ accounting.
RADIUS accounting
When enabled, RADIUS accounting sends command line accounting from the 7705 SAR router to the RADIUS server. The router sends accounting records using UDP packets at port 1813 (decimal).
The router issues an accounting request packet for each event requiring the activity to be recorded by the RADIUS server. The RADIUS server acknowledges each accounting request by sending an accounting response after it has processed the accounting request. If no response is received in the time defined in the timeout parameter, the accounting request must be retransmitted until the configured retry count is exhausted. A trap is issued to alert the NMS (or trap receiver) that the server is unresponsive. The router issues the accounting request to the next configured RADIUS server (up to 5).
User passwords and authentication keys of any type are never transmitted as part of the accounting request.
When RADIUS accounting is enabled, the server is responsible for receiving accounting requests and returning a response to the client indicating that it has successfully received the request. Each command issued on the 7705 SAR router generates a record sent to the RADIUS server. The record identifies the user who issued the command and the timestamp.
Accounting can be configured independently from RADIUS authorization and RADIUS authentication.
TACACS+ accounting
The 7705 SAR allows you to configure the type of accounting record packet that is to be sent to the TACACS+ server when specified events occur on the device. The accounting record-type parameter indicates whether TACACS+ accounting start and stop packets will be sent or just stop packets will be sent. A start packet is sent to a TACACS+ server when an authenticated user establishes a Telnet or SSH session and a stop packet is sent when the user logs out.
When a user logs in to request access to the network using Telnet or SSH, or a user enters a command for which accounting parameters are configured, or a system event occurs, such as a reboot or a configuration file reload, the 7705 SAR checks the configuration to see if TACACS+ accounting is required for the particular event.
If TACACS+ accounting is required, then, depending on the accounting record type specified, the device sends a start packet to the TACACS+ accounting server that contains information about the event.
The TACACS+ accounting server acknowledges the start packet and records information about the event. When the event ends, the device sends a stop packet. The stop packet is acknowledged by the TACACS+ accounting server.
Security controls
You can configure the 7705 SAR to use RADIUS, TACACS+, and local authentication to validate users requesting access to the network. The order in which requests are processed among RADIUS, TACACS+ and local methods can be specifically configured. For example, the authentication order can be configured to process authorization using TACACS+ first, then RADIUS, for authentication and accounting. Local access can be specified next in the authentication order if the RADIUS and TACACS+ servers are not operational.
When a server does not respond
A trap is issued if a RADIUS server is unresponsive. An alarm is raised if RADIUS is enabled with at least one RADIUS server and no response is received to either accounting or user access requests from any server.
Periodic checks to determine if the primary server is responsive again are performed. If a server is down, it will not be contacted for 5 minutes. If a login is attempted after 5 minutes, then the server is contacted again. If a server has the health check feature enabled and is unresponsive, the server’s status is checked every 30 seconds. Health check is enabled by default. When a service response is restored from at least one server, the alarm condition is cleared. Alarms are raised and cleared on the Nokia Fault Manager or other third party fault management servers.
The servers are accessed in order from lowest to highest specified index (from 1 to 5) for authentication requests until a response from a server is received. A higher indexed server is only queried if no response is received from a lower indexed server. If a response from the server is received, no other server is queried.
Authentication and authorization request flow
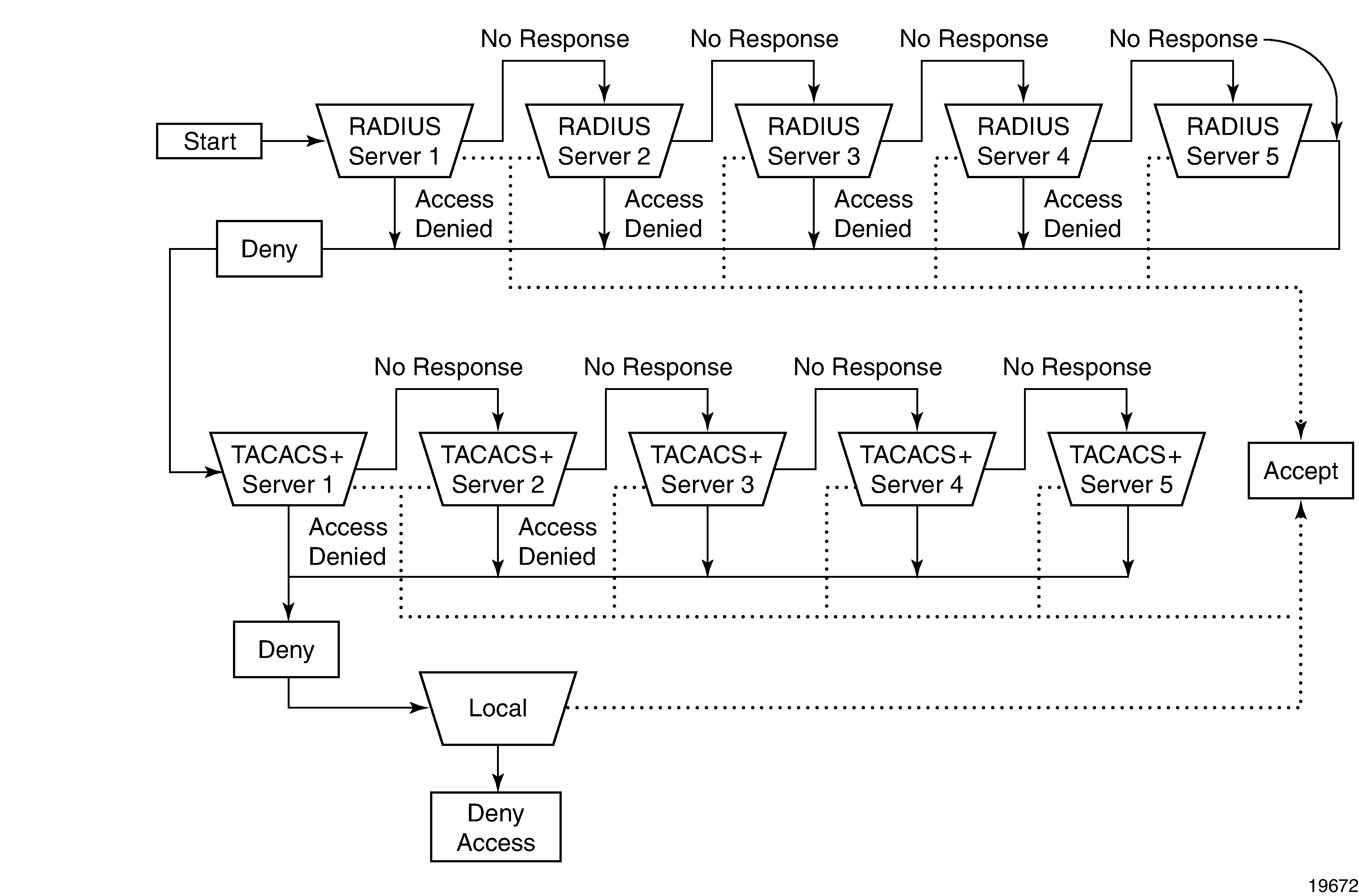
In Security flow, the authentication process is defined in the config>system>security> password context with the authentication-order command. The authentication order is determined by specifying the sequence in which password authentication is attempted among RADIUS, TACACS+, and local servers when exit-on-reject is disabled.
This example uses the authentication order of RADIUS, then TACACS+, and finally, local. A request is sent to RADIUS server 1. If there is no response from the server, the request is passed to the next RADIUS server, and so on, until the last RADIUS server is attempted (RADIUS server 5). If server 5 does not respond, the request is passed to TACACS+ server 1. If there is no response from that server, the request is passed to the next TACACS+ server, and so on.
If a request is sent to an active RADIUS server and the username and password are not recognized, access is denied and the next method is attempted, in this case, the TACACS+ server. The process continues until the request is accepted or denied or each server is queried. Finally, if the request is denied by the active TACACS+ server, the local method is attempted. This is the last chance for the access request to be accepted.
RADIUS VSAs
The 7705 SAR supports the configuration of Nokia-specific RADIUS attributes. These attributes are known as vendor-specific attributes (VSAs) and are defined in RFC 2138. If VSAs are not configured on the RADIUS server, the RADIUS user authenticates with options defined in the RADIUS default template when use-default-template is enabled. If VSAs are used, all mandatory VSAs must be configured for the RADIUS user to authenticate. It is up to the vendor to specify the format of their VSA. The attribute-specific field is dependent on the vendor's definition of that attribute. The Nokia-defined attributes are encapsulated in a RADIUS vendor-specific attribute with the vendor ID field set to 6527. Nokia VSAs are defined in the dictionary-freeradius.txt file in the support folder of the software package.
Nokia supports the following RADIUS VSAs for AAA:
-
Timetra-Access <ftp> <console> <both> <scp-sftp> <console-port-cli> <ssh-cli> <telnet-cli> – specifies the router management access methods a user can access. Multiple access methods can be specified by adding the value of the access methods to allow in the RADIUS server configuration file. This VSA is mandatory when the RADIUS default template is disabled.
For example, to allow console port CLI and SSH CLI access:
RADIUS server configuration
Timetra-Access = 96 # 32 (console-port-cli) + 64 (ssh-cli)or
Timetra-Access = console-port-cli Timetra-Access += ssh-cli -
Timetra-Profile <profile-name> – maps to the user profile, which must be configured on the 7705 SAR router. The following guidelines apply for local and remote authentication:
-
The authentication-order parameters configured on the router must include the local keyword.
-
The username may or may not be configured on the 7705 SAR router.
-
The user must be authenticated by the RADIUS server.
-
Up to eight valid profiles can exist on the router for a user. The sequence in which the profiles are specified is relevant. The most explicit matching criteria must be ordered first. The process stops when the first complete match is found.
If all of the preceding conditions are not met, access to the router is denied and a failed login event or trap is written to the security log.
-
-
Timetra-Action <permit | deny> – specifies the action to be applied when the user has entered a command specified in the Timetable-Cmd VSA
-
Timetra-Default-Action <permit-all | deny-all | read-only-all | none> – specifies the default action when the user has entered a command and no entry configured in the Timetra-Cmd VSA for the user resulted in a match condition. This VSA is mandatory when the RADIUS default template is disabled.
-
Timetra-Cmd <match-string> – configures a command or command subtree as the scope for the match condition. The command and all commands in the subtrees are authorized. If an invalid command is specified, a deny-all profile is installed and the radiusUserProfileInvalid event is logged.
-
Timetra-Home-Directory <home-directory-string> – specifies the home directory. It cannot be used to delete a home directory that is configured in the RADIUS default template.
-
Timetra-Restrict-To-Home <true | false> – specifies if user access is limited to their home directory (and directories and files subordinate to their home directory). If this VSA is not configured, the user is allowed to access the entire file system.
- Timetra-Save-When-Restricted <true | false> – when this VSA is set to true, the user can execute configuration save operations (for example, admin save) in the CLI when Timetra-Restrict-To-Home is set to true.
-
Timetra-Exec-File <login-exec-string> – specifies the login exec file that is executed when the user successfully logs in to a console session. If this VSA is not configured, no login exec file is applied.
RADIUS configuration for file access control using VSAs
- locally with no VSAs (see Configuring users for information about configuring user access parameters locally)
- with VSAs
Example: RADIUS server with VSA configuration for per-user home directories and a locally configured default template for other options
- all users can save the configuration
- on the router: each user has a home directory with restricted file access. The administrator must create the home directory for each user.
- on the RADIUS server: the home directory is configured with a VSA
- on the router: optionally, access to copy files to the router with SCP/SFTP is configured in the RADIUS default template
- on the router: other file access controls are configured in the RADIUS default template
user1
Timetra-Home-Directory = "cf3:\users\user1"
user2
Timetra-Home-Directory = "cf3:\users\user2"
user3
Timetra-Home-Directory = "cf3:\users\user3"
user4
Timetra-Home-Directory = "cf3:\users\user4"A:node-2>config>system>security>user-template# info
----------------------------------------------
restricted-to-home
save-when-restricted
----------------------------------------------Example: RADIUS server with VSA configuration and per-user home directories
This example shows the following configuration:
- all file access controls are configured with VSAs, which is the most flexible way to grant different file access to each user
- on the RADIUS server: each user has a home directory with restricted file access. The administrator must create the home directory for each user.
- on the router: the RADIUS default template is not used for file access
- on the RADIUS server: the administrator can restrict file access to the home directory of the user and allow users to save the configuration based on the VSA value
- on the RADIUS server: access to the router and permission to copy files to the router with SCP/SFTP are configured with VSAs
user1
Timetra-Access = 112 # 16 + (scp-sftp) + 32 (console-port-cli) + 64 (ssh-cli)
# Timetra-Home-Directory is not defined
Timetra-Restrict-To-Home = false
# Timetra-Save-When-Restricted is not defineduser2
Timetra-Access = 112 # 16 + (scp-sftp) + 32 (console-port-cli) + 64 (ssh-cli)
Timetra-Home-Directory = "cf3:\users\user2",
Timetra-Restrict-To-Home = true,
Timetra-Save-When-Restricted = trueuser3
Timetra-Access = 96 # 32 (console-port-cli) + 64 (ssh-cli)
Timetra-Home-Directory = "cf3:\users\user3",
Timetra-Restrict-To-Home = true,
Timetra-Save-When-Restricted = falseuser4
Timetra-Access = 96 # 32 (console-port-cli) + 64 (ssh-cli)
# Timetra-Home-Directory is not defined
Timetra-Restrict-To-Home = true,
Timetra-Save-When-Restricted = falseTACACS+ services and VSAs
The 7705 SAR supports the "nokia-user" service with several VSAs. Administrators can optionally configure the service and VSAs for each user on a TACACS+ server instead of configuring access locally.
When a user authenticates with TACACS+, the router:
- if enabled, requests the "nokia-user" VSA from the server for authorization after authentication succeeds
- uses the values from the VSA if present and values from the TACACS+ default template when a VSA is not present
- discards invalid VSA values and authentication fails
- discards unknown VSAs and authentication succeeds
- discards unknown mandatory VSA values and authentication succeeds
The administrator must ensure that the use-default-template command is enabled so that users can be authenticated. If the default template (tacplus_default) is not enabled, no login access (FTP or console) will be granted because that access can only be configured via the default template (not through VSAs).
| Service name | VSA name | Description | Values |
|---|---|---|---|
| nokia-user | home-directory | Home directory for the user | A string up to 200 characters |
| nokia-user | restricted-to-home | Limits user access to their home directory |
true – prevents the user from accessing files outside their home directory false – allows the user to access all files on the system |
| nokia-user | save-when-restricted | Saves configurations when the user is restricted to home |
true – allows all configuration save operations (for example, admin save) via the CLI even if restricted-to-home is enabled false – prevents the user from performing any configuration save operations outside of their home directory when restricted-to-home is enabled |
TACACS+ configuration for file access control using VSAs
- locally with no VSAs (see Configuring users for information about configuring user access parameters locally)
- locally using the TACACS+ default template (tacplus_default) and some VSAs that are different for each user
- using the file access VSAs to control file access and the TACACS+ default template for other user access controls
(tac_plus.conf) is in quotation marks, you must add a backslash (\)
to escape the backslash (\); otherwise, the TACACS+ server will reject the setting and
fail to start. For example: - home-directory = cf3:\users\user1
- home-directory = "cf3:\\users\\user1"
Example: TACACS+ server with VSA configuration for per-user home directories and a locally configured default template for other options
- all users can save the configuration
- on the router: each user has a home directory with restricted file access. The administrator must create the home directory for each user.
- on the TACACS+ server: the home directory is configured with a VSA
- on the router: use-default-template is enabled under the config>system>security>tacplus context; this configuration is mandatory (see note above)
- on the router: other file access controls are configured in the TACACS+ default template
user = user1 {
service = nokia-user {
home-directory = cf3:\users\user1
}
}
user = user2 {
service = nokia-user {
home-directory = cf3:\users\user2
}
}
user = user3 {
service = nokia-user {
home-directory = cf3:\users\user3
}
}
user = user4 {
service = nokia-user {
home-directory = cf3:\users\user4
}
}A:node-2>config>system>security>user-template# info
----------------------------------------------
restricted-to-home
save-when-restricted
----------------------------------------------Example: TACACS+ server configuration with VSA configuration and per-user home directories
This example shows the following configuration:
- all file access is controlled with VSAs, which is the most flexible way to grant different file access to each user
- on the router: each user has a home directory with restricted file access. The administrator must create the home directory for each user.
- on the router: the TACACS+ default template is not used for file access
- on the TACACS+ server: the administrator can also restrict file access to the home directory of the user and allow users to save the configuration based on the VSA value
user = user1 {
service = nokia-user {
# home-directory is not defined
restricted-to-home = false
# save-when-restricted is not defined
}
}user = user2 {
service = nokia-user {
home-directory = cf3:\users\user2
restricted-to-home = true
save-when-restricted = true
}
}user = user3 {
service = nokia-user {
home-directory = cf3:\users\user3
restricted-to-home = true
save-when-restricted = false
}
}user = user4 {
service = nokia-user {
# home-directory is not defined
restricted-to-home = true
save-when-restricted = false
}
}Other security features
This section contains information about the following topics:
SSH
Secure Shell (SSH) is a protocol that provides a secure, encrypted Telnet-like connection to a router.
A connection is always initiated by the client (the user). Authentication takes place by one of the configured authentication methods (local, RADIUS, or TACACS+). With authentication and encryption, SSH allows for a secure connection over an insecure network.
The 7705 SAR supports Secure Shell version 2 (SSHv2). SSHv2 uses host keys to authenticate systems and is considered a more secure, efficient, and portable version of SSH.
SSH runs on top of a transport layer (like TCP or IP), and provides authentication and encryption capabilities. SSH supports remote login to another computer over a network, remote command execution, and file relocation from one host to another.
The 7705 SAR has a global SSH server process to support inbound SSH, SFTP, and SCP sessions initiated by external SSH or SCP client applications. The SSH server supports SSHv2. This server process is separate from the SSH and SCP client commands on the 7705 SAR, which initiate outbound SSH and SCP sessions.
Inbound SSH, Telnet, and FTP sessions are counted separately and it is possible to set the limit for each session type individually with the config>system>login-control command. However, there is a maximum of 50 sessions for SSH and Telnet together. SCP and SFTP sessions are counted as SSH sessions.
When the SSH server is enabled, an SSH security key is generated. Unless the preserve-key command is enabled, the key is only valid until either the node is restarted or the SSH server is stopped and restarted. The key size is non-configurable and is set to 2048 for SSHv2 RSA and to 1024 for SSHv2 DSA. Only SSHv2 RSA is supported in FIPS-140-2 mode. When the server is enabled, all inbound SSH, SCP, and SFTP sessions are accepted provided the session is properly authenticated.
When the global SSH server process is disabled, no inbound SSH, SCP, or SFTP sessions are accepted.
When using SCP to copy files from an external device to the file system, the 7705 SAR SCP server will accept either forward slash (/) or backslash (\) characters to delimit directory and filenames. Similarly, the 7705 SAR SCP client application can use either slash or backslash characters, but not all SCP clients treat backslash characters as equivalent to slash characters. In particular, UNIX systems will often interpret the backslash character as an ‟escape” character, which does not get transmitted to the 7705 SAR SCP server. For example, a destination directory specified as ‟cf3:\dir1\file1” will be transmitted to the 7705 SAR SCP server as ‟cf3:dir1file1”, where the backslash escape characters are stripped by the SCP client system before transmission. On systems where the client treats the backslash like an ‟escape” character, a double backslash (\\) or the forward slash (/) can typically be used to properly delimit directories and the filename.
The 7705 SAR support for SSH, SCP, and SFTP is the same for both IPv4 and IPv6 addressing, including support for:
SSHv2
in-band and out-of-band management of the 7705 SAR
key management and authentication types
encryption types
simultaneous IPv4 and IPv6 SSH/SCP/SFTP sessions
The 7705 SAR supports configurable lists for the following: cipher, key exchange (KEX) algorithms, and message authentication code (MAC) algorithms. These lists can be configured for an SSH client or an SSH server and are used to negotiate the best compatible cipher, KEX, or MAC algorithm between the client and server. The lists are created and managed under the config>system>security>ssh context. The client list is used when the 7705 SAR is acting as an SSH client and the server list is used when the 7705 SAR is acting as an SSH server.
SSH and Telnet listening ports configurable to a non-default value
For security reasons, the SSH server and Telnet server listening ports are configurable to a non-default port value. This configuration makes it more difficult for unauthorized users to scan the SSH or Telnet ports and launch Denial of Service (DoS) attacks. The 7705 SAR SSH and Telnet clients are capable of initiating an SSH or Telnet connection to a specific non-default SSH or Telnet port.
Ensuring no other application is using the SSH or Telnet port
When a user attempts to configure a new value for the default SSH or Telnet port, the SSH or Telnet application checks whether the port is in use by another protocol. If the port is in use, the configuration is blocked and a warning displays stating: "Port is already in use".
The newly configured port cannot be overwritten by any other protocol even if there is no active SSH or Telnet session. After the port is configured, no other protocol is allowed to reserve the port.
Behavior in base routing and VPRN
The 7705 SAR uses GRT leaking and the allow-management command for VPRN management. If the listening port for SSH or Telnet is changed, the configuration also applies to VPRN GRT leaking.
Known limitations
- SSH is connected to port 22 and the user changes the port to 22000; the change is effective immediately, but the SSH connection to port 22 remains open.
- The port cannot be changed back from 22000 to 22 until all connections to port 22 are closed.
Multichannel SSH
The 7705 SAR supports up to five channels within a single SSH connection, up to a maximum of 15 channels per system. SSH channels can be used when an SSH connection has authenticated a user and a channel is opened for configuration while another channel is required to retrieve state information, such as collecting configurations or show command output. The primary connection authenticates the user through public key authentication (PKI) or keyboard authentication. After the primary connection is authenticated, applications can open multiple channels (sessions) to the server with the same connection.
Opening a new channel inside an existing authenticated SSH connection reduces the additional time and memory requirements for establishing a new SSH session. Reducing the time and memory needed is useful when, for example, multiple RPCs from different network managers to the same device are executed at the same time.
SSH session closing behavior
The SSH connection closes automatically when the last channel (session) opened in the connection is closed.
SSH keepalive intervals are disabled on the 7705 SAR, which results in the following:
- the 7705 SAR SSH server does not close the session when the client SSH keepalive intervals time out
- the client SSH keepalive intervals cannot be used to keep the connection to the 7705 SAR server open
SSH PKI authentication
The SSH server supports public key authentication (also known as PKI) if the server has been previously configured to know the client’s public key.
Using public key authentication can be more secure than the existing username and password method for the following reasons:
A user typically reuses the same password with multiple servers. If the password is compromised, the user must reconfigure the password on all affected servers.
A password is not transmitted between the client and server using PKI. Instead, the sensitive information (the private key) is kept on the client. Therefore, the password is less likely to be compromised.
The 7705 SAR supports server-side SSHv2 public key authentication but does not include a key-generation utility.
Support for PKI should be configured at the system level where one or more public keys may be bound to a username. This configuration will not affect any other system security or login functions.
PKI has preference over password authentication. PKI is supported using local authentication. PKI authentication is not supported on TACACS+ or RADIUS.
User public key generation
Before SSH can be used with PKI, a public/private key pair must be generated. This is typically supported by the SSH client software. For example, PuTTY supports a utility called PuTTYGen that will generate key pairs.
The 7705 SAR currently supports Rivest, Shamir, and Adleman (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA) user public keys. The RSA public key is supported up to 4096 bits and the ECDSA public key is supported up to NIST P-521.
If the client is using PuTTY, they first generate a key pair using PuTTYGen. The user sets the key type to SSH-2 RSA and sets the number of bits to be used for the key. The user can also configure a passphrase that is used to store the key locally in encrypted form. If the passphrase is configured, it acts as a password for the private key and the user must enter the passphrase to use the private key. If a passphrase is not used, the key is stored in plaintext locally.
Next, the public key must be configured for the user on the 7705 SAR with the command config>system>security>user>public-keys. The user can program the public key using the CLI or SNMP.
SSH cipher lists
The 7705 SAR supports configurable cipher client and cipher server lists that are used to negotiate the best compatible cipher between the SSH client and SSH server. Each list contains ciphers and their corresponding index values, where a lower index has a higher preference in the SSH negotiation. The list is ordered by preference from highest to lowest. When the client and server exchange their cipher lists, the first cipher in the client list that is also supported by the server is the cipher that is agreed upon.
See SSHv2 default index values in the Security command reference for the cipher index values and names.
The default list can be changed by manually removing a single index or as many indexes as required using the no cipher index command. The default list can also be customized by first removing an index and then redefining it for each algorithm as required (the 7705 SAR does not support customizing an index without first removing it).
SSH KEX lists
The 7705 SAR supports configurable KEX client and KEX server lists that are used to negotiate the best compatible KEX algorithm between the SSH client and SSH server. Each list contains KEX algorithms and their corresponding index values, where a lower index value has a higher preference in the SSH negotiation. The list is ordered by preference from highest to lowest. When the client and server exchange their KEX lists, the first algorithm in the client list that is also supported by the server is the algorithm that is agreed upon.
The KEX client and KEX server each have a default list that contains all supported algorithms and their corresponding indexes. See Default KEX index values in the Security command reference for the default KEX index values and algorithms.
The default list can be changed by manually removing a single index or as many indexes as required using the no kex index command. The default list can also be customized by first removing an index and then redefining it for each algorithm as required (the 7705 SAR does not support customizing an index without first removing it).
Once a change has been made to the default list, the 7705 SAR uses the changed list moving forward. To go back to using the hard-coded list, the default KEX indexes must be manually re-entered with their corresponding algorithms. If all the entries in a KEX list are removed, the list will be empty and any KEX algorithm brought to the negotiation will be rejected.
SSH key re-exchange without disabling SSH
The 7705 SAR supports periodic rollover (or re-exchange) of the SSH symmetric key without disabling SSH. Symmetric key rollover is important in long SSH sessions. Symmetric key rollover ensures that the encryption channel between the client and server is not jeopardized by an external hacker that is trying to break the encryption via a brute force attack. The feature can be configured on either the SSH client or server.
The following are triggers for symmetric key rollover and negotiation:
the negotiation of the key based on a configured time period
the negotiation of the key based on a configured data transmission size
Key re-exchange is enabled by default. The default values for both the client and server are 60 min and 1024 MB, which is the RFC 4253 recommendation.
Key re-exchange procedure
The key re-exchange procedure is initiated by sending an SSH_MSG_KEXINIT message while not performing a key exchange. When this message is received by a client or server, the client or server must respond with its own SSH_MSG_KEXINIT message, except in cases where the received SSH_MSG_KEXINIT message was already sent as a reply. Either client or server can initiate the re-exchange, but the roles must not be changed (that is, the server must remain the server and the client must remain the client).
Key re-exchange is performed using whatever encryption was in effect when the exchange was initiated. Encryption, compression, and MAC methods are not changed before a new SSH_MSG_NEWKEYS message is sent after the key exchange (as in the initial key exchange). Re-exchange is processed in the same way as the initial key exchange, except that the session identifier remains unchanged. Some or all of the algorithms can be changed during the re-exchange. Host keys can also change. All keys and initialization vectors are recomputed after the exchange. Compression and encryption contexts are reset.
SSH MAC lists
The 7705 SAR supports configurable SSHv2 server MAC and client MAC lists that are used to negotiate the best compatible MAC algorithm between the SSH client and SSH server.
Each list contains MAC algorithms and their corresponding index values, where a lower index value has a higher preference in the SSHv2 negotiation. The list is ordered by preference from highest to lowest. When the client and server exchange their MAC lists, the first algorithm in the client list that is also supported by the server is the algorithm that is agreed upon.
In addition, strong HMAC algorithms can be configured at the top of the MAC list (that is, as the lowest index values in the list) in the order to be negotiated first between the client and server. The first algorithm in the list that is supported by both the client and the server is the one that is agreed upon.
The default list can be changed by manually removing a single index or as many indexes as required using the no mac index command. The default list can also be customized by first removing an index and then redefining it for each algorithm as required (the 7705 SAR does not support customizing an index without first removing it).
SFTP
When an SSH server is enabled on the 7705 SAR, users can connect to the node through SSH File Transfer Protocol (SFTP). SFTP runs on top of SSH and uses the same password and authentication process, and once logged in, SFTP users will appear as regular SSH users. Additionally, all other user management features apply to users logging in to the 7705 SAR with an SFTP client.
Event logs are created to capture both successful and unsuccessful attempts to access the node through SFTP.
CSM filters and CSM security
IP forwarding supports CSM filters that are applied to IP packets extracted to the control plane. CSM filters are used to protect the control plane from DoS attacks, unauthorized access to the node, and similar security breaches.
IP filters scan all traffic and take the appropriate (configured) action against matching packets. Packets that are not filtered by the IP filters and are destined for the 7705 SAR are scanned by the configured CSM filter.
For information about IP filters, see the 7705 SAR Router Configuration Guide.
Both IPv4 and IPv6 CSM filters are supported.
IPv4 CSM filters drop or accept incoming packets based on the following match criteria:
DSCP name
destination IP address
destination port
fragmentation
ICMP code
ICMP type
IP option value
multiple options
option present
source IP address
source port
TCP ACK
TCP SYN
IPv6 CSM filters drop or accept incoming packets based on the following match criteria:
DSCP name
destination IP address
destination port
ICMP code
ICMP type
source IP address
source port
TCP ACK
TCP SYN
To prevent DoS-like attacks from overwhelming the control plane while ensuring that critical control traffic such as signaling is always serviced in a timely manner, the 7705 SAR segregates the incoming control plane traffic into different queues. These queues are used to shape and rate-limit traffic for each protocol or group of protocols, or on a per-flow basis, with the main goal of mitigating DoS attacks and ensuring that the control plane does not end up with more traffic than it can handle.
These queues are fixed use (each queue handles a specific type of traffic, which is not user-configurable) and fixed configuration (each queue is configured for particular rates and buffering capacity and is not user-configurable).
Exponential login backoff
A malicious user can gain CLI access via a dictionary attack: using a script to try ‟admin” with any password.
The 7705 SAR increases the delay between login attempts exponentially to mitigate attacks. It is applied to the console login. SSH and Telnet sessions terminate after four attempts.
File access controls
Files on the 7705 SAR can be accessed locally using the CLI file commands and output modifiers, such as > (file redirect), or remotely via FTP or SCP. The 7705 SAR can control file access to:
- allow users to access all files and save the configuration
- allow users to access only the files in their home directory and save the configuration
- allow users to access only the files in their home directory with no ability to save the configuration
- prevent users from accessing any files or saving the configuration
The file access controls provide different levels of user access. File access controls can also be configured to allow users to save the configuration to a system file that is stored outside their home directory when their file access is restricted to their home directory. A home directory is typically a working space for the user; for example, cf3:\users\user1. Although the home directory can be configured to contain saved configuration files, log files, or other system files, administrators should only do this for users who are intended to have access to those files.
The following commands configure file access controls for local or remote users; these commands can be set via the CLI, RADIUS VSAs, or TACACS+ VSAs:
- restricted-to-home – limits file access to only the files in the home directory of the user
- home-directory – home directory for the user; Nokia recommends that this command not be configured in the RADIUS or TACACS+ default template because each user should have their own home directory
- save-when-restricted – allows the user to save configurations when the user is restricted to their home directory, even if the saved configuration file is outside the home directory of the user
The following table lists the user types and privileges and their corresponding file access control configuration.
| Type of user | File system access | Configuration access | Restricted to home | Home directory | Save when restricted |
|---|---|---|---|---|---|
| High-privilege administrator | Full | Yes | Disabled (false) | Unconfigured | Unconfigured |
| High-privilege user with access to all configuration | Private directory with environment settings and Python applications | Yes | Enabled (true) | cf3:\users\user1 | Enabled (true) |
| Medium-privilege user with access to a subset of configuration using AAA command authorization | Directory of CLI scripts and Python applications | Yes | Enabled (true) |
cf3:\scripts\script-group-a
|
Enabled (true) |
| Medium-privilege user with access to a subset of configuration using AAA command authorization | None | Yes | Enabled (true) | Unconfigured | Enabled (true) |
| Low-privilege operational user | Private directory with environment settings and operational scripts | No | Enabled (true) | cf3:\users\user2 | Unconfigured1 |
| Low-privilege operational user | None | No | Enabled (true) | Unconfigured | Unconfigured1 |
| Low-privilege user for managing XML accounting files | Accounting directory | No | Enabled (true) | cf2:\act | Unconfigured1 |
| Low-privilege user for managing log files | Log directory | No | Enabled (true) | cf2:\log | Unconfigured1 |
Note:
- Configuration save operations (for example, admin save) are controlled by AAA command authorization. Optionally, save-when-restricted can be disabled to explicitly deny configuration save operations for these user types.
The following examples show how to use the CLI to configure different permissions for local users. The administrator must create a home directory for each user.
access to all files and the ability to save the configuration
Use the following configuration for a high-privilege administrator who needs access to all files:
config>system>security
user user1
no restricted-to-homeaccess to home directory files only and the ability to save the configuration
Use the following configuration for a medium-privilege user who can access some parts of the configuration and needs to save the configuration, but is denied access to other parts of the configuration in a AAA profile:
config>system>security
user user2
home-directory "cf3:\users\user2"
restricted-to-home
save-when-restrictedaccess to home directory files only and no ability to save the configuration
Use the following configuration for a low-privilege user who does not have access to any part of the configuration but still requires a working area on the file system for their own files:
config>system>security
user user3
home-directory "cf3:\users\user3"
restricted-to-home
no save-when-restrictedno file access and no ability to save the configuration
Use the following configuration for a low-privilege user who does not have access to any part of the configuration and does not require any file system access:
config>system>security
user user4
restricted-to-home
no save-when-restrictedEncryption
Data Encryption Standard (DES) and Triple DES (3DES) are supported for encryption:
-
DES is a widely used method of data encryption using a private (secret) key. Both the sender and the receiver must know and use the same private key.
-
3DES is a more secure version of the DES protocol.
802.1x network access control
The 7705 SAR supports network access control of client devices (PCs, STBs, and so on) on an Ethernet network using the IEEE 802.1x standard. 802.1x is known as Extensible Authentication Protocol (EAP) over a LAN network or EAPOL.
See the 7705 SAR Interface Configuration Guide for more information about IEEE 802.1x.
TCP enhanced authentication and keychain authentication
The 7705 SAR supports non-keychain MD5 authentication for OSPF, IS-IS, and RSVP-TE and TCP MD5 authentication for BGP and LDP. In previous releases, only a single authentication key or pre-hashed MD5 digest could be defined at a time using the authentication-key command. If this key was changed, the adjacency was reset, causing both the local and remote router to reconverge based on the lost adjacency. When a new key or digest was added, the adjacency was re-established, causing another reconvergence event within the network.
The 7705 SAR also supports the TCP Enhanced Authentication Option, as specified in draft-bonica-tcp-auth-05, Authentication for TCP-based Routing and Management Protocols. The TCP Enhanced Authentication option is a TCP extension that enhances security for BGP, LDP, and other TCP-based protocols. It extends the MD5 authentication option to include the ability to change keys in a BGP or LDP session seamlessly without tearing down the session and allows for stronger authentication algorithms to be used. It is intended for applications where secure administrative access to both endpoints of the TCP connection is normally available.
TCP peers can use this extension to authenticate messages passed between one another. This strategy improves upon the practice described in RFC 2385, Protection of BGP Sessions via the TCP MD5 Signature Option. Using this strategy, TCP peers can update authentication keys during the lifetime of a TCP connection. TCP peers can also use stronger authentication algorithms to authenticate routing messages.
Keychain authentication
TCP enhanced authentication uses keychains that are associated with every protected TCP connection.
The keychain concept supported by BGP and LDP has also been extended to the OSPF, IS-IS, and RSVP-TE protocols.
The keychain mechanism allows for the creation of keys used to authenticate protocol communications. Each keychain entry defines the authentication attributes to be used in authenticating protocol messages from remote peers or neighbors. The keychain must include at least one key entry to be valid. The keychain mechanism also allows authentication keys to be changed without affecting the state of the associated protocol adjacencies.
Each key within a keychain must include the following attributes for the authentication of protocol messages:
key identifier – unique identifier, expressed as a decimal integer
authentication algorithm – see Security algorithm support per protocol
authentication key – used by the authentication algorithm to authenticate packets
direction – packet stream direction in which the key is applied (receive direction, send direction, or both)
begin time – the time at which a new authentication key can be used
Optionally, each key can include the following attributes:
end time – the time at which the authentication key becomes inactive (applies to received packets only)
tolerance – period in which both old and new authentication key values can overlap and both keys are allowed on received packets (applies to received packets only)
For added security, support for the Secure Hash Algorithm (SHA) has been added. The following table lists the security algorithms supported per protocol.
Protocol |
Clear text |
MD5 (message digest) |
HMAC-MD5 |
HMAC-SHA-1-96 |
HMAC-SHA-1 |
HMAC-SHA-256 |
AES-128-CMAC-96 |
|---|---|---|---|---|---|---|---|
OSPF |
✓ |
✓ |
✓ |
✓ |
✓ |
||
IS-IS |
✓ |
✓ |
✓ |
✓ |
|||
RSVP-TE |
✓ |
✓ |
✓ |
✓ |
|||
BGP |
✓ |
✓ |
|||||
LDP |
✓ |
✓ |
Keychain configuration guidelines and behavior
The authentication-key command or the auth-keychain command can be used by the protocols listed in Security algorithm support per protocol, but both cannot be supported at the same time. If both commands are configured, the auth-keychain configuration is applied and the authentication-key command is ignored.
A keychain cannot be referenced by a protocol until it has been configured.
If a keychain is referenced by a protocol, the keychain cannot be deleted.
If multiple keys in a keychain are valid at the same time, the newest key (key with the most current begin-time) is used.
If a protocol sends a packet that is configured to use a keychain, the most current key from that keychain is used.
If a protocol receives a packet that is configured to use a keychain, the current key set is returned to authenticate the received packet:
The key set includes the currently active keys (based on the current system time) and the begin-time or end-time associated with each key in the specified keychain.
If a tolerance value is set for a key, the key is returned as part of the key set if the current time is within the key’s begin-time, plus or minus the tolerance value. For example, if the begin-time is 12:00 p.m. and the tolerance is 600 seconds, the new key is included from 11:55 a.m. and the key to be replaced is included until 12:05 p.m.
The end-time and tolerance parameters apply only to received packets. Transmitted packets always use the newest key, regardless of the tolerance value.
If a keychain exists but there are no active key entries with an authentication type that matches the type supported by the protocol, inbound protocol packets are not authenticated and are discarded and no outbound protocol packets are sent.
If a keychain exists but the last key entry has expired, a log entry is raised indicating that all keychain entries have expired.
The OSPF and RSVP-TE protocols continue to authenticate inbound and outbound traffic using the last valid authentication key.
The IS-IS protocol does not revert to an unauthenticated state and requires that the old key not be used; therefore, when the last key has expired, all traffic will be discarded.
For information about associating keychains with protocols, see the 7705 SAR Routing Protocols Guide (for OSPF, IS-IS, and BGP), the 7705 SAR MPLS Guide (for RSVP-TE and LDP), and the 7705 SAR Services Guide (for OSPF and BGP in a VPRN service).
Key rollover
Use the following commands to configure keychain authentication to roll over to a new key without tearing down the session:
config>system>security
keychain name
direction
uni
receive
entry entry-id
begin-time [date] [hours-minutes] [UTC]
end-time [date] [hours-minutes] [UTC]
send
entry entry-id
begin-time [date] [hours-minutes] [UTC]
bi
entry entry-id
begin-time [date] [hours-minutes] [UTC]The begin-time command specifies when the authentication key starts to authenticate the protocol stream and the end-time command specifies when the authentication key is no longer eligible to authenticate the protocol stream. The system uses the key configured with the most recent begin-time. For more information about configuring keychain authentication, see Configuring keychain authentication.
A user does not have to configure an end-time and can instead choose to configure multiple entries with different begin-time configurations so that the newest key (key with the most current begin-time) is used. The current key pair is replaced to improve security without session loss between two peers.
TLS
Transport Layer Security (TLS) is used for two primary purposes:
- authentication of an end device (client or server) using a digital signature
(DS)
TLS uses PKI for device authentication. DSs are used to authenticate the client or the server. The server typically sends a certificate with a DS to the client.
In specific situations, the server can request a certificate from the client to authenticate it. The client has a certificate (called a trust anchor) from the certificate authority (CA) that is used to authenticate the server certificate and its DS. After the client provides a digitally signed certificate to the server and both parties are authenticated, the encryption PDUs can then be transmitted.
- encryption and authentication of application PDUs
After the client and server have been successfully authenticated, the cipher suite is negotiated between the server and clients, and the PDUs are encrypted based on the agreed cipher protocol.
TLS interaction with applications
TLS is a standalone configuration. The user must configure a TLS client profile with certificates and trust anchors, and then assign the TLS client profile to the appropriate applications. When a TLS client profile is assigned to an application, the application does not send any PDUs until the TLS handshake has been successfully completed and the encryption ciphers have been negotiated between the TLS server and the TLS client.
After successful negotiation and handshake, the application is notified that TLS is operationally up. The application begins transmitting PDUs encrypted using TLS based on the agreed ciphers. If at any point the TLS becomes operationally down, the application will stop transmitting PDUs.
For example, a TLS connection with the PCEP application operates as follows:
- A TLS client is configured under PCEP on the 7705 SAR.
-
PCEP stops sending clear text PDUs because a TLS client profile has been assigned and TLS is not ready to encrypt.
- The TLS client begins the handshake.
- Authentication occurs at the TLS layer.
- The TLS server and TLS client negotiate ciphers.
- Salts are negotiated for the symmetric key. A salt is a seed for creating AES encryption keys.
- When negotiations are successfully completed, the handshake finishes, TLS becomes operationally up, and PCEP is notified.
-
PCEP begins transmitting PDUs that are encrypted using TLS.
Until TLS becomes operationally up, PCEP does not transmit any PDUs.
Application support
The 7705 SAR supports TLS client profiles on the PCC to enable PCEP over TLS (PCEPS). See the "PCEP over TLS" section in the 7705 SAR MPLS Guide for more information.
TLS handshake
The following figure shows the TLS handshake process and the table describes the steps.
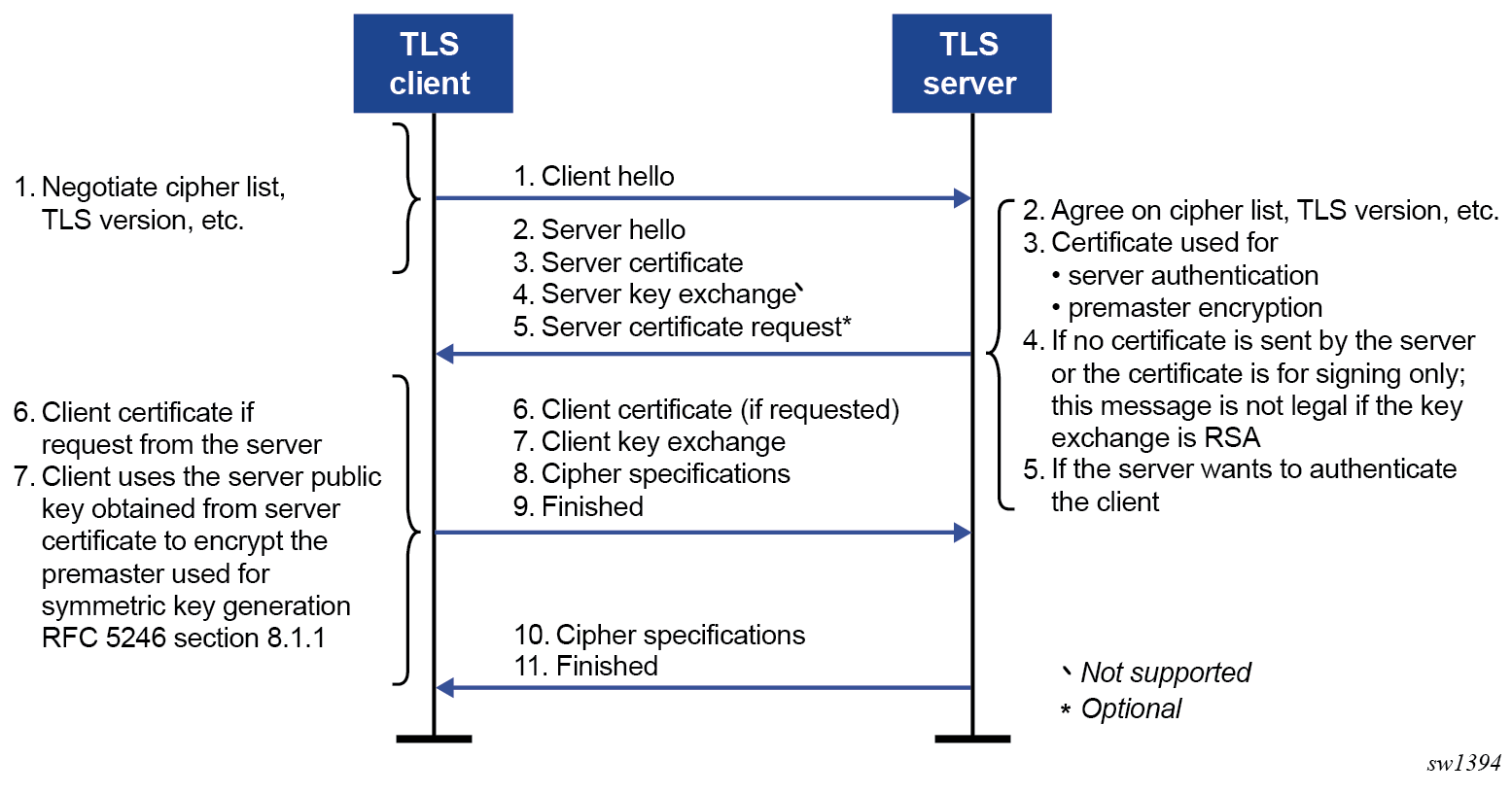
| Step | Description |
|---|---|
| 1 |
The TLS handshake begins with the client Hello message. This message includes the cipher list that the client wants to use and negotiate. |
| 2 |
The TLS server sends back a server Hello message, along with the first common cipher found on both the client cipher list and the server cipher list. This agreed cipher is used for data encryption. |
| 3 |
The TLS server continues by sending a server certificate message, where the server provides a certificate to the client so that the client can authenticate the server identity. The public key of this certificate (RSA key) can also be used for encryption of the symmetric key seed that is used by the client and server to create the symmetric encryption key. This occurs only if PKI is using RSA for asymmetric encryption. |
| 4 |
Server key exchange is not supported by the 7705 SAR. The 7705 SAR only uses RSA keys; Diffie-Hellman key exchange is not supported. |
| 5 |
The server can optionally be configured to request a certificate from the client to authenticate the client. |
| 6 |
If the server requests a certificate, the client must provide a certificate using a client certificate message. If the client does not provide a certificate, the server drops the TLS session. |
| 7 |
The client uses the server public RSA key that was included in the server certificate to encrypt a seed used for creating the symmetric key. This seed is used by the client and server to create the identical symmetric key for encrypting and decrypting the data plane traffic. |
| 8 | The client sends a cipher specification to switch encryption to this symmetric key. |
| 9 | The client successfully finishes the handshake. |
| 10 | The server sends a cipher specification to switch encryption to this symmetric key. |
| 11 | The server successfully finishes the handshake. |
After a successful handshake, TLS is operationally up and can be used for application encryption.
TLS 1.3
TLS 1.3 is required for faster handshakes, stronger encryption, and authentication algorithms.
All 7705 SAR applications that use TLS 1.2 also support TLS 1.3, unless specifically stated otherwise.
The user can configure the node to use TLS 1.2, TLS 1.3, or both for negotiation.
If TLS 1.3 is negotiated with a peer, the node does not negotiate the TLS version down to 1.2 as long as the session is alive.
TLS 1.3 handshake
The TLS 1.3 client handshake is very similar to TLS 1.2 because the client is able to negotiate TLS 1.2 or 1.3 when starting the TLS Hello message to the server. The client includes a "Supported Version" extension in its Hello message. The server responds with its own supported version and agreed ciphers. The server and client must agree on the TLS version to proceed with the connection.
In TLS 1.2 and TLS 1.3, the server can optionally request the client certificate to authenticate the client. If requested, the client must provide its certificate to the server.
TLS 1.3 configuration
The user can configure the TLS 1.3 cipher list independently of TLS 1.2. TLS 1.3 ciphers are configured using the tls13-cipher command. When the user configures a TLS 1.3 cipher list, TLS 1.3 is included as a supported version in the TLS handshake.
TLS 1.3 also introduces group lists and signature lists for the server and client.
In the Hello message sent by the client, the "supported_groups" extension indicates the named groups that the client supports for the key exchange, ordered from most preferred to least preferred. TLS 1.3 supports Elliptic-curve Diffie-Hellman Ephemeral (ECDHE) groups.
TLS 1.3 also allows the selection of signature algorithms. The "signature_algorithms_cert" extension is included to allow implementations that support different sets of algorithms for certificates and in TLS itself to clearly signal their capabilities.
TLS client certificate
The TLS protocol is used for authentication, and therefore the server can ask to authenticate the client via PKI. If the server requests authentication from the client, the client must provide an X.509v3 certificate to the server so that it can be authenticated via the digital signature of its client.
The 7705 SAR supports the configuration of an X.509v3 certificate for TLS clients.
When the server requests a certificate via the server’s Hello message, the client transmits its certificate to the server using a client certificate message.
TLS symmetric key rollover
The 7705 SAR supports key rollover when the TLS server is enabled with a TLS renegotiation timer and sends a HelloRequest message as specified in RFC 5246, section 7.4.1.1.
Supported TLS ciphers
As shown in TLS handshake, TLS negotiates the supported ciphers between the client and the server.
The client sends the supported cipher suites in the client Hello message, and the server compares them with the server cipher list. The top protocol on both lists is chosen and returned from the server in the server Hello message.
The 7705 SAR supports the following ciphers as a TLS 1.2 client:
-
tls-rsa-with3des-ede-cbc-sha
-
tls-rsa-with-aes128-cbc-sha
-
tls-rsa-with-aes256-cbc-sha
-
tls-rsa-with-aes128-cbc-sha256
-
tls-rsa-with-aes256-cbc-sha256
The 7705 SAR supports the following TLS 1.3 ciphers, groups, and signature algorithms as a TLS 1.3 client:
- ciphers:
-
tls-aes128-gcm-sha256
-
tls-aes256-gcm-sha384
-
tls-chacha20-poly1305-sha256
-
tls-aes128-ccm-sha256
-
tls-aes128-ccm8-sha256
-
- groups:
-
tls-ecdhe-256
-
tls-ecdhe-384
-
tls-ecdhe-521
-
tls-x25519
-
tls-x448
-
- signature algorithms:
-
tls-rsa-pkcs1-sha256
-
tls-rsa-pkcs1-sha384
-
tls-rsa-pkcs1-sha512
-
tls-ecdsa-secp256r1-sha256
-
tls-ecdsa-secp384r1-sha384
-
tls-ecdsa-secp521r1-sha512
-
tls-rsa-pss-rsae-sha256
-
tls-rsa-pss-rsae-sha384
-
tls-rsa-pss-rsae-sha512
-
tls-rsa-pss-pss-sha256
-
tls-rsa-pss-pss-sha384
-
tls-rsa-pss-pss-sha512
-
tls-ed25519
-
tls-ed448
-
Certificate management
The 7705 SAR implements a centralized certificate management protocol that can be used by TLS. See the "IPSec" section in the 7705 SAR Services Guide for information about the configuration of the certificates and the corresponding protocols, such as OCSP and CRL.
Certificate profile
The certificate profile is available for the TLS client and is configured with the cert-profile command. The certificate profile contains the certificates that the client sends to the TLS server along with its DS so that the server can authenticate it via the trust-anchor and CA certificate.
Multiple provider certificates can be configured; however, the 7705 SAR currently uses the smallest index as the active provider certificate, and only sends that certificate to the server.
TLS server authentication of the client certificate CN field
If the client provides a certificate, the server checks the common name (CN) field against local CN configurations. The CN is validated via the client IPv4/IPv6 address or FQDN. If the common-name list authentication option is not enabled on the server, it uses certificate signature authentication instead.
Operational guidelines
Server authentication behavior
Following the Hello messages, the server sends its certificate in a certificate message if it is to be authenticated.
The trust-anchor-profile command determines whether the server must be authenticated by the client.
One of the following configurations can be used to establish server connectivity:
-
If trust-anchor-profile is configured under the TLS client-tls-profile context, the server must be authenticated via the trust-anchor-profile command before a trusted connection is established between the server and the client.
-
If there is no trust-anchor-profile under the client-tls-profile context, the trusted connection can be established without server authentication. The RSA key of the certificate is used for public key encryption, requiring basic certificate checks to validate the certificate. These basic checks are as follows:
-
time validity
The certificate is checked to ensure that it is not expired or not yet valid.
-
certificate type
The certificate is not a CA certificate.
-
keyUsage extension
If present, this must contain a digital signature and key encryption.
-
host verification
The IP address or DNS name of the server is looked up, if available, in the common name (cn) or subjectAltName extension. This is to verify that the certificate was issued to that server and not to another.
-
TLS client profile and trust anchor behavior and scale
The 7705 SAR supports the creation of TLS client profiles, which can be assigned to applications such as PCEP to encrypt the application layer.
The client-tls-profile command is used for negotiating and authenticating the server. After the server is authenticated via the trust anchor profile (configured using the trust-anchor-profile command) of a TLS client profile, it negotiates the ciphers and authentication algorithms to be used for encryption of the data.
The TLS client profile must be assigned to an application for it to start encrypting. Up to 16 TLS client profiles can be configured. Because each of these client profiles needs a trust anchor profile to authenticate the server, up to 16 trust anchor profiles can be configured. A trust anchor profile holds up to 8 trust anchors (configured using the trust-anchor command), each of which holds a CA profile (ca-profile).
A CA profile is a container for installing CA certificates. These CA certificates are used to authenticate the server certificate. When the client receives the server certificate, it reads through the trust anchor profile CA certificates and tries to authenticate the server certificate against each CA certificate. The first CA certificate that authenticates the server is used.
Basic TLS configuration
Basic TLS client configuration must have a cipher list created using the config>system>security>tls>client-cipher-list command, and the cipher list must be assigned to the TLS client profile using the config>system>security>tls>client-tls-profile>cipher-list command.
TLS imports the trust anchor certificate for peer certificate authentication and public key retrieval. The following example shows a TLS configuration.
- Example:
-
A:node-2>config>system>security>tls# info ---------------------------------------------- trust-anchor-profile "server-1-ca" create trust-anchor "tls-server-1-ca" exit client-cipher-list "to-active-server" create cipher 1 name tls-rsa-with-aes256-cbc-sha256 cipher 2 name tls-rsa-with-aes128-cbc-sha256 cipher 3 name tls-rsa-with-aes256-cbc-sha exit client-tls-profile "server-1-profile" create cipher-list "to-active-server" trust-anchor-profile ‟server-1-ca‟ no shutdown exit ----------------------------------------------
Common configuration tasks
Configuring a TLS client profile
The following displays the CLI syntax for a TLS client profile:
- CLI syntax:
-
config>system>security>tls client-tls-profile name trust-anchor-profile name
Configuring a TLS client certificate
The following displays the CLI syntax for TLS certificate management:
- CLI syntax:
-
config>system>security>tls cert-profile profile-name entry entry-id cert cert-filename key key-filename send-chain ca-profile name no shutdown client-tls-profile name cert-profile name
Configuring a TLS trust anchor
The following displays the CLI syntax for a TLS trust anchor:
- CLI syntax:
-
config>system>security>tls trust-anchor-profile name client-tls-profile name cipher-list name no shutdown trust-anchor-profile name
The following example shows a TLS trust anchor configuration:
- Example:
-
*A:node-2>config>system>security>tls# info ---------------------------------------------- trust-anchor-profile "server-1-ca" create trust-anchor "tls-server-1-ca" exit client-tls-profile "server-1-profile" create cipher-list "to-active-server" trust-anchor-profile ‟server-1-ca‟ no shutdown exit
Configuration notes
The following are security configuration guidelines and restrictions:
-
If a RADIUS or a TACACS+ server is not configured, password, profiles, and user access information must be configured on each router in the domain.
-
If RADIUS authorization is enabled, VSAs must be configured on the RADIUS server.
Configuring security with CLI
This section provides information to configure security using the command line interface. Topics in this section include:
Setting up security attributes
The following table depicts the capabilities of authentication, authorization, and accounting configurations. For example, authentication can be enabled locally and on RADIUS and TACACS+ servers. Authorization can be executed locally, on a RADIUS server, or on a TACACS+ server. Accounting can be performed on a RADIUS or TACACS+ server.
|
Authentication |
Authorization |
Accounting |
|---|---|---|
|
Local |
Local |
None |
|
RADIUS |
Local and RADIUS |
RADIUS |
|
TACACS+ |
Local and TACACS+ |
TACACS+ |
Configuring authentication
See the following sections to configure authentication:
local authentication
RADIUS authentication (with local authorization)
By default, authentication is enabled locally. Perform the following tasks to configure security on each participating 7705 SAR router:
RADIUS authentication (with RADIUS authorization)
To implement RADIUS authentication with authorization, perform the following tasks on each participating 7705 SAR router:
TACACS+ authentication
To implement TACACS+ authentication, perform the following tasks on each participating 7705 SAR router:
Configuring authorization
See the following sections to configure authorization:
local authorization
For local authorization, configure these tasks on each participating 7705 SAR router:
RADIUS authorization with authentication
For RADIUS authorization with authentication, configure these tasks on each participating 7705 SAR router:
Configuring RADIUS authorization
For RADIUS authorization, VSAs must be configured on the RADIUS server. See RADIUS VSAs.
TACACS+ authorization (only)
For TACACS+ authorization without authentication, perform the task in Configuring TACACS+ authorization for each participating 7705 SAR router:
TACACS+ authorization
For TACACS+ authorization with authentication, configure these tasks on each participating 7705 SAR router:
Configuring accounting
See the following sections to configure accounting.
Local accounting is not implemented. For information about configuring accounting policies, see Configuring logging with CLI.
Security configurations
To implement security features, configure the following components:
-
management access filters
-
CPM (CSM) filters
-
profiles
-
user access parameters
-
password management parameters
-
RADIUS or TACACS+
-
enable one to five RADIUS or TACACS+ (or both) servers
-
configure RADIUS or TACACS+ (or both) parameters
-
The following example displays default values for security parameters.
NOK-1>config>system>security# info detail
----------------------------------------------
no hash-control
telnet-server
no telnet6-server
ftp-server
management-access-filter
ip-filter
no shutdown
exit
ipv6-filter
no shutdown
exit
exit
profile "default"
default-action none
entry 10
no description
match "exec"
action permit
exit
entry 20
no description
match "exit"
action permit
exit
entry 30
no description
match "help"
action permit
exit
entry 40
no description
match "logout"
action permit
exit
entry 50
no description
match "password"
action permit
exit
entry 60
no description
match "show config"
action deny
exit
entry 70
no description
match "show"
action permit
exit
entry 80
no description
match "enable-admin"
action permit
exit
exit
profile "administrative"
default-action permit-all
entry 10
no description
match "configure system security"
action permit
exit
entry 20
no description
match "show system security"
action permit
exit
entry 30
no description
match "tools perform security"
action permit
exit
entry 50
no description
match "admin system security"
action permit
exit
exit
password
authentication-order radius tacplus local
no aging
attempts 3 time 5 lockout 10
health-check interval 30
no admin-password
hashing bcrypt
history-size 0
minimum-age min 10
minimum-change 5
complexity-rules
no allow-user-name
credits lowercase 0 uppercase 0 numeric 0 special-character 0
no minimum-classes
minimum-length 6
no repeated-characters
required lowercase 0 uppercase 0 numeric 0 special-character 0
exit
exit
tech-support
no ts-location
exit
user-template "radius_default"
access console
profile "default"
no home-directory
restricted-to-home
save-when-restricted
console
no login-exec
exit
exit
user-template "tacplus_default"
access console
profile "default"
no home-directory
restricted-to-home
save-when-restricted
console
no login-exec
exit
exit
user "admin"
password "$2y$10$TQrZlpBDra86.qoexZUzQeBXDY1FcdDhGWdD9lLxMuFyPVSm0OGy6"
access console
no home-directory
no restricted-to-home
save-when-restricted
public-keys
ecdsa
exit
rsa
exit
exit
console
no login-exec
no cannot-change-password
no new-password-at-login
member "administrative"
local-lockout
exit
exit
snmp
view "iso" subtree "1"
mask ff type included
exit
...
access group "snmp-ro" security-model snmpv1 security-level no-auth-no-privacy read "no-security" notify "no-security"
access group "snmp-ro" security-model snmpv2c security-level no-auth-no-privacy read "no-security" notify "no-security"
access group "snmp-rw" security-model snmpv1 security-level no-auth-no-privacy read "no-security" write "no-security" notify "no-security"
access group "snmp-rw" security-model snmpv2c security-level no-auth-no-privacy read "no-security" write "no-security" notify "no-security"
access group "snmp-rwa" security-model snmpv1 security-level no-auth-no-privacy read "iso" write "iso" notify "iso"
access group "snmp-rwa" security-model snmpv2c security-level no-auth-no-privacy read "iso" write "iso" notify "iso"
access group "snmp-mgmt" security-model snmpv1 security-level no-auth-no-privacy context "management" exact read "mgmt-view" write "mgmt-view" notify "mgmt-view"
access group "snmp-mgmt" security-model snmpv2c security-level no-auth-no-privacy context "management" exact read "mgmt-view" write "mgmt-view" notify "mgmt-view"
access group "snmp-trap" security-model snmpv1 security-level no-auth-no-privacy notify "iso"
access group "snmp-trap" security-model snmpv2c security-level no-auth-no-privacy notify "iso"
access group "snmp-vprn" security-model snmpv1 security-level no-auth-no-privacy context "vprn" prefix read "vprn-view" write "vprn-view" notify "vprn-view"
access group "snmp-vprn" security-model snmpv2c security-level no-auth-no-privacy context "vprn" prefix read "vprn-view" write "vprn-view" notify "vprn-view"
access group "cli-readonly" security-model snmpv2c security-level no-auth-no-privacy read "iso" notify "iso"
access group "snmp-vprn-ro" security-model snmpv1 security-level no-auth-no-privacy context "vprn" prefix read "vprn-view" notify "vprn-view"
access group "snmp-vprn-ro" security-model snmpv2c security-level no-auth-no-privacy context "vprn" prefix read "vprn-view" notify "vprn-view"
access group "cli-readwrite" security-model snmpv2c security-level no-auth-no-privacy read "iso" write "iso" notify "iso"
access group "snmp-vpls-mgmt" security-model snmpv1 security-level no-auth-no-privacy context "vpls-management" prefix read "mgmt-view" write "mgmt-view" notify "mgmt-view"
access group "snmp-vpls-mgmt" security-model snmpv2c security-level no-auth-no-privacy context "vpls-management" prefix read "mgmt-view" write "mgmt-view" notify "mgmt-view"
access group "cli-vprn-readwrite" security-model snmpv2c security-level no-auth-no-privacy context "vprn" exact read "vprn-view" write "vprn-view" notify "iso"
attempts 20 time 5 lockout 10
community "cV3ISTw2V5pbEWmVEA9jXgB/1EERXQA=" hash2 rwa version both
community "76HzdddhlPpRo1Vql+ZB5spLqccgYQ==" hash2 r version both
exit
ssh
client-cipher-list
cipher 2 name aes256-ctr
cipher 4 name aes192-ctr
cipher 6 name aes128-ctr
cipher 10 name aes128-cbc
cipher 20 name 3des-cbc
cipher 60 name aes192-cbc
cipher 70 name aes256-cbc
exit
server-cipher-list
cipher 2 name aes256-ctr
cipher 4 name aes192-ctr
cipher 6 name aes128-ctr
cipher 10 name aes128-cbc
cipher 20 name 3des-cbc
cipher 60 name aes192-cbc
cipher 70 name aes256-cbc
exit
client-mac-list
mac 200 name hmac-sha2-512
mac 210 name hmac-sha2-256
mac 215 name hmac-sha1
mac 220 name hmac-sha1-96
mac 225 name hmac-md5
mac 240 name hmac-md5-96
exit
server-mac-list
mac 200 name hmac-sha2-512
mac 210 name hmac-sha2-256
mac 215 name hmac-sha1
mac 220 name hmac-sha1-96
mac 225 name hmac-md5
mac 240 name hmac-md5-96
exit
client-kex-list
kex 200 name diffie-hellman-group16-sha512
kex 210 name diffie-hellman-group14-sha256
kex 215 name diffie-hellman-group14-sha1
kex 220 name diffie-hellman-group-exchange-sha1
kex 225 name diffie-hellman-group1-sha1
exit
server-kex-list
kex 200 name diffie-hellman-group16-sha512
kex 210 name diffie-hellman-group14-sha256
kex 215 name diffie-hellman-group14-sha1
kex 220 name diffie-hellman-group-exchange-sha1
kex 225 name diffie-hellman-group1-sha1
exit
key-re-exchange
client
mbytes 1024
minutes 60
no shutdown
exit
server
mbytes 1024
minutes 60
no shutdown
exit
exit
no preserve-key
no server-shutdown
exit
dot1x
shutdown
exit
no vprn-network-exceptions
cli-script
authorization
cron
no cli-user
exit
event-handler
no cli-user
exit
exit
exit
cpm-filter
default-action accept
ip-filter
shutdown
exit
ipv6-filter
shutdown
exit
exit
tls
exitSecurity configuration procedures
Configuring IPv4 or IPv6 management access filters
Creating and implementing management access filters is optional. Management access filters control all traffic going in to the CSM, including all routing protocols. They apply to packets from all ports. The filters can be used to restrict management of the 7705 SAR router by other nodes outside either specific (sub)networks or through designated ports. By default, there are no filters associated with security options. The management access filter and entries must be explicitly created on each router.
Management access filters apply to the management Ethernet port, which supports both IPv4 and IPv6 filters.
The 7705 SAR exits the filter when the first match is found and executes the actions according to the specified action. For this reason, entries must be sequenced correctly from most to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action to be considered complete. Entries without the action keyword are considered incomplete and are rendered inactive.
Use the following CLI commands to configure an IPv4 management access filter.
- CLI syntax:
config>system security management-access-filter ip-filter default-action {permit | deny | deny-host-unreachable} entry entry-id action {permit | deny | deny-host-unreachable} description description-string dst-port port [mask] log protocol protocol-id router router-instance src-ip {ip-prefix[/mask][netmask] | ip-prefix-list ip-prefix-list-name} src-port {port-id | cpm} renum old-entry-number new-entry-number no shutdown
Use the following CLI commands to configure an IPv6 management access filter.
- CLI syntax:
config>system security management-access-filter ipv6-filter default-action {permit | deny | deny-host-unreachable} entry entry-id action {permit | deny | deny-host-unreachable} description description-string dst-port port [mask] flow-label value log next-header next-header router router-instance src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name} src-port {port-id | cpm} renum old-entry-number new-entry-number no shutdown
The following example displays an IPv4 management access filter configuration. This example only accepts packets matching the criteria specified in entries 1 and 2. Non-matching packets are denied.
- Example:
config>system>security# management-access-filter config>system>security>mgmt-access-filter# ip-filter default-action deny config>system>security>mgmt-access-filter# ip-filter entry 1 config>system>security>mgmt-access-filter>ip-filter>entry# src-ip 10.10.10.104/32 config>system>security>mgmt-access-filter>ip-filter>entry# action permit config>system>security>mgmt-access-filter>ip-filter>entry# exit config>system>security>mgmt-access-filter# entry 2 config>system>security>mgmt-access-filter>ip-filter>entry# src-ip 10.10.10.1/32 config>system>security>mgmt-access-filter>ip-filter>entry# action permit config>system>security>mgmt-access-filter>ip-filter>entry# exit
The following example displays the management access filter configuration.
ALU-1>config>system>security# info
----------------------------------------------
management-access-filter
ip-filter
default-action deny
entry 1
action permit
src-ip 10.10.10.104/32
exit
entry 2
action permit
src-ip 10.10.0.1/32
exit
exit
----------------------------------------------
ALU-1>config>system>security#Configuring IPv4 or IPv6 CPM (CSM) filters
CPM filters control all traffic going in to the CSM, including all routing protocols. They apply to packets from all network and access ports, but not to packets from a management Ethernet port. CPM packet filtering is performed by network processor hardware using no resources on the main CPUs.
Use the following CLI commands to configure an IPv4 CPM filter.
- CLI syntax:
config>system>security cpm-filter default-action {accept | drop} ip-filter entry entry-id [create] action {accept | drop} description description-string log log-id match [protocol protocol-id] dscp dscp-name dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name} dst-port [tcp/udp port-number] [mask] fragment {true | false} icmp-code icmp-code icmp-type icmp-type ip-option ip-option-value [ip-option-mask] multiple-option {true | false} option-present {true | false} src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name} src-port src-port-number [mask] tcp-ack {true | false} tcp-syn {true | false} renum old-entry-id new-entry-id
Use the following CLI commands to configure an IPv6 CPM filter.
- CLI syntax:
config>system>security cpm-filter default-action {accept | drop} ipv6-filter entry entry-id [create] action {accept | drop} description description-string log log-id match [next-header next-header] dscp dscp-name dst-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name} dst-port [tcp/udp port-number] [mask] icmp-code icmp-code icmp-type icmp-type src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name} src-port src-port-number [mask] tcp-ack {true | false} tcp-syn {true | false} renum old-entry-id new-entry-id
The following displays an IPv4 CPM filter configuration example:
A:ALU-49>config>sys>sec>cpm>ip-filter# info
----------------------------------------------
entry 10 create
action drop
description "CPM-Filter 10.4.101.2 #101"
log 101
exit
entry 20 create
no action
description "CPM-Filter 10.4.101.2 #201"
log 101
exit
no shutdown
----------------------------------------------
A:ALU-49>config>sys>sec>cpm>ip-filter#Configuring password management parameters
Depending on the authentication requirements, password parameters are configured locally or on the RADIUS or TACACS+ server.
Use the following CLI commands to configure password support:
- CLI syntax:
config>system>security password admin-password password [hash | hash2] aging days attempts count [time minutes1] [lockout minutes2] authentication-order [method-1] [method-2] [method-3] [exit-on-reject] complexity-rules hashing hashing {bcrypt | sha2-pbkdf2 | sha3-pbkdf2} health-check [interval interval] history-size size minimum-age [days days] [hrs hours][min minutes] [sec seconds] minimum-change distance
The following example displays the default password configuration:
*A:Dut-A>config>system>security>password# info detail
----------------------------------------------
authentication-order radius tacplus local
no aging
attempts 3 time 5 lockout 10
health-check interval 30
no admin-password
hashing bcrypt
history-size 0
minimum-age min 10
minimum-change 5
complexity-rules
no allow-user-name
credits lowercase 0 uppercase 0 numeric 0 special-character 0
no disallow-sequence-keys
no minimum-classes
minimum-length 6
no repeated-characters
required lowercase 0 uppercase 0 numeric 0 special-character 0
exit
----------------------------------------------
Managing IPSec certificates
The following is an example of importing a certificate from a pem format:
*A:ALU-A# admin certificate import type cert input cf3:/pre-import/
R10cert.pem output R1-0cert.der format pemThe following is an example of exporting a certificate to a pem format:
*A:ALU-A# admin certificate export type cert input R1-0cert.der output cf3:/
R10cert.pem format pemThe following example displays a profile output:
*A:ALU-A>config>system>security>pki# info
----------------------------------------------
ca-profile "Root" create
description "Root CA"
cert-file "R1-0cert.der"
crl-file "R1-0crl.der"
no shutdown
exit
----------------------------------------------
*A:ALU-A>config>system>security>pki#The following example displays an ike-policy with cert-auth output:
*A:ALU-A>config>ipsec>ike-policy# info
----------------------------------------------
auth-method cert-auth
own-auth-method psk
----------------------------------------------The following example displays a static LAN-to-LAN configuration using cert-auth:
interface "VPRN1" tunnel create
sap tunnel-1.private:1 create
ipsec-tunnel "Sanity-1" create
security-policy 1
local-gateway-address 192.168.0.0 peer 192.168.0.1 delivery-
service 300
dynamic-keying
ike-policy 1
pre-shared-key "Sanity-1"
transform 1
cert
trust-anchor-profile "trustAnchorProfile_1"
cert-profile "certProfile_4"
exit
exit
no shutdown
exitConfiguring profiles
Profiles are used to deny or permit access to a hierarchical branch or specific commands. Profiles are referenced in a user configuration. A maximum of 16 user profiles can be defined. A user can participate in up to 16 profiles. Depending on the authorization requirements, passwords are configured locally or on the RADIUS server.
When configuring profiles, put more specific commands in the lower-numbered entries because the lower-numbered entries take precedence over the higher-numbered entries.
- Example:
-
entry 10 match "show" action permit exit entry 20 match "show system" action deny exit
Use the following CLI commands to configure user profiles:
- CLI syntax:
config>system>security profile user-profile-name default-action {deny-all | permit-all | none} renum old-entry-number new-entry-number entry entry-id description description-string match command-string action {permit | deny}
The following displays an example of the user profile command usage.
- Example:
config>system>security# profile ghost config>system>security>profile$ default-action permit-all config>system>security>profile# entry 1 config>system>security>profile>entry$ action permit config>system>security>profile>entry# match "configure" config>system>security>profile>entry# exit config>system>security>profile# entry 2 config>system>security>profile>entry$ match "show" config>system>security>profile>entry# exit config>system>security>profile# entry 3 config>system>security>profile>entry$ match "exit"
The following example displays the user profile output:
ALU-1>config>system>security# info
----------------------------------------------
...
profile "ghost"
default-action permit-all
entry 1
match "configure"
action permit
exit
entry 2
match "show"
exit
entry 3
match "exit"
exitConfiguring users
Access parameters are configured for individual users. For each user, the login name and, optionally, information that identifies the user is defined. Use the following CLI syntax to configure access parameters for users. The snmp authentication des-key keyword is not available if the 7705 SAR node is running in FIPS-140-2 mode.
- CLI syntax:
config>system>security user user-name access [ftp] [snmp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli] console cannot-change-password local-lockout login-exec url-prefix:source-url member user-profile-name [user-profile-name...(up to 8 max)] new-password-at-login home-directory url-prefix [directory] [directory/directory ..] password [password] restricted-to-home save-when-restricted snmp authentication {[none] | [[hash] {md5 key-1 | sha key-1} privacy {none | des-key key-2 | aes-128-cfb-key key-2}]} group group-name
The following example displays the user configuration, including default values:
NOK-1>config>system>security# info detail
----------------------------------------------
...
user "test"
password "$2y$10$NXW9rLCSdBZiSUZ0fQGI2.mLh4ofLpXKAnay5SPSDVQI5FtKCottq"
access console
no home-directory
restricted-to-home
save-when-restricted
public-keys
ecdsa
exit
rsa
exit
exit
console
no login-exec
no cannot-change-password
no new-password-at-login
member "default"
local-lockout
exit
exit
snmp
view "iso" subtree "1"
mask ff type included
exit
...
--------------------------------------------
NOK-1>config>system>security#Copying and overwriting users and profiles
You can copy a profile or user or overwrite an existing profile or user. The overwrite option must be specified; otherwise, an error occurs if the destination profile or username already exists.
Copying a user
- CLI syntax:
config>system>security# copy {user source-user | profile source-profile} to destination [overwrite]
- Example:
config>system>security# copy user "testuser" to "testuserA" MINOR: CLI User "testuserA" already exists - use overwrite flag. config>system>security# config>system>security# copy user "testuser" to "testuserA" overwrite config>system>security#
The following output displays the copied user configurations:
ALU-12>config>system>security# info
----------------------------------------------
...
user "testuser"
password "$2y$10$siOU8NvWRzFFtJjO5wA1I.7mr.57emDXUC14p6EZtO.pmr0aqL
Sa"
access snmp
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy
none
group "testgroup"
exit
exit
user "testuserA"
password "$2y$10$siOU8NvWRzFFtJjO5wA1I.7mr.57emDXUC14p6EZtO.pmr0aqLW
Sa"
access snmp
console
new-password-at-login
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy
none
group "testgroup"
exit
exit
...
----------------------------------------------
ALU-12>config>system>security# infoALU-12>config>system>security>user# info
----------------------------------------------
password "$2y$10$siOU8NvWRzFFtJjO5wA1I.7mr.57emDXUC14p6EZtO.pmr0aqLWSa"
access snmp
console
cannot-change-password
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy none
group "testgroup"
exit
----------------------------------------------
ALU-12>config>system>security>user# exit
ALU-12>config>system>security# user testuserA
ALU-12>config>system>security>user# info
----------------------------------------------
password "$2y$10$siOU8NvWRzFFtJjO5wA1I.7mr.57emDXUC14p6EZtO.pmr0aqLWSa"
access snmp
console
new-password-at-login
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy none
group "testgroup"
exit
----------------------------------------------
ALU-12>config>system>security>user#Copying a profile
- CLI syntax:
-
config>system>security# copy {user source-user | profile source-profile} to destination [overwrite]
- Example:
-
config>system>security# copy profile default to testuser
The following output displays the copied profiles:
A:ALU-49>config>system>security# info
----------------------------------------------
...
A:ALU-49>config>system>security# info detail
----------------------------------------------
...
profile "default"
default-action none
entry 10
no description
match "exec"
action permit
exit
entry 20
no description
match "exit"
action permit
exit
entry 30
no description
match "help"
action permit
exit
entry 40
no description
match "logout"
action permit
exit
entry 50
no description
match "password"
action permit
exit
entry 60
no description
match "show config"
action deny
exit
entry 70
no description
match "show"
action permit
exit
entry 80
no description
match "enable-admin"
action permit
exit
exit
profile "testuser"
default-action none
entry 10
no description
match "exec"
action permit
exit
entry 20
no description
match "exit"
action permit
exit
entry 30
no description
match "help"
action permit
exit
entry 40
no description
match "logout"
action permit
exit
entry 50
no description
match "password"
action permit
exit
entry 60
no description
match "show config"
action deny
exit
entry 70
no description
match "show"
action permit
exit
entry 80
no description
match "enable-admin"
action permit
exit
exit
profile "administrative"
default-action permit-all exit
...Configuring SSH
Use the ssh command to configure the SSH server. This command should only be enabled or disabled when the SSH server is disabled. This setting cannot be changed while the SSH server is running.
- CLI syntax:
-
config>system>security ssh preserve-key no server-shutdown
- Example:
-
config>system>security# ssh config>system>security>ssh# preserve-key
The following example displays the SSH server configuration using a host-key:
A:ALU-1>config>system>security>ssh# info
----------------------------------------------
preserve-key
----------------------------------------------
A:ALU-1>config>system>security>ssh# Configuring SSH cipher lists
Use the ssh command to configure SSHv2 cipher lists. Client cipher lists are used if the 7705 SAR is acting as an SSH client, and server cipher lists are used if the 7705 SAR is acting as an SSH server.
- CLI syntax:
config>system>security ssh client-cipher-list cipher index name cipher-name server-cipher-list cipher index name cipher-name
- Example:
config>system>security# ssh config>system>security>ssh# client-cipher-list config>system>security>ssh>client-cipher# cipher 2 name aes256-ctr config>system>security>ssh>client-cipher# cipher 4 name aes128-ctr config>system>security>ssh>client-cipher# cipher 6 name aes256-cbc config>system>security>ssh>client-cipher# cipher 10 name aes128-cbc config>system>security>ssh>client-cipher# cipher 20 name 3des-cbc config>system>security>ssh>client-cipher# cipher 60 name aes192-cbc config>system>security>ssh>client-cipher# cipher 70 name aes256-cbc config>system>security>ssh>client-cipher# exit config>system>security>ssh# server-cipher-list config>system>security>ssh>server-cipher# cipher 2 name aes256-ctr config>system>security>ssh>server-cipher# cipher 4 name aes192-ctr config>system>security>ssh>server-cipher# cipher 6 name aes128-ctr config>system>security>ssh>server-cipher# cipher 10 name aes128-cbc config>system>security>ssh>server-cipher# cipher 20 name 3des-cbc config>system>security>ssh>server-cipher# cipher 60 name aes192-cbc config>system>security>ssh>server-cipher# cipher 70 name aes256-cbc config>system>security>ssh>server-cipher# exit config>system>security>ssh# exit
The following example displays SSHv2 client and server cipher list configurations:
A:Sar8 Dut-A>config>system>security>ssh# info detail
----------------------------------------------
client-cipher-list
cipher 2 name aes256-ctr
cipher 4 name aes192-ctr
cipher 6 name aes128-ctr
cipher 10 name aes128-cbc
cipher 20 name 3des-cbc
cipher 60 name aes192-cbc
cipher 70 name aes256-cbc
exit
server-cipher-list
cipher 2 name aes256-ctr
cipher 4 name aes192-ctr
cipher 6 name aes128-ctr
cipher 10 name aes128-cbc
cipher 20 name 3des-cbc
cipher 60 name aes192-cbc
cipher 70 name aes256-cbc
exit
----------------------------------------------
*A:Sar8 Dut-A>config>system>security>ssh#Configuring SSH KEX algorithm lists
Use the ssh command to configure SSHv2 client and server KEX algorithm lists. Client KEX algorithm lists are used if the 7705 SAR is acting as an SSH client, and server KEX algorithm lists are used if the 7705 SAR is acting as an SSH server.
- CLI syntax:
config>system>security ssh client-kex-list kex index name kex-name server-kex-list kex index name kex-name
- Example:
config>system>security# ssh config>system>security>ssh# client-kex-list config>system>security>ssh>client-kex# kex 200 name diffie-hellman-group16-sha512 config>system>security>ssh>client-kex# kex 210 name diffie-hellman-group14-sha256 config>system>security>ssh>client-kex# kex 215 name diffie-hellman-group14-sha1 config>system>security>ssh>client-kex# kex 220 name diffie-hellman-group-exchange-sha1 config>system>security>ssh>client-kex# kex 225 name diffie-hellman-group1-sha1 config>system>security>ssh>client-kex# exit config>system>security>ssh# server-kex-list config>system>security>ssh>server-kex# kex 200 name diffie-hellman-group16-sha512 config>system>security>ssh>server-kex# kex 210 name diffie-hellman-group14-sha256 config>system>security>ssh>server-kex# exit config>system>security>ssh# exit
The following example displays SSHv2 client and server KEX list configurations:
A:Sar8 Dut-A>config>system>security>ssh# info detail
----------------------------------------------
client-kex-list
kex 200 name diffie-hellman-group16-sha512
kex 210 name diffie-hellman-group14-sha256
kex 215 name diffie-hellman-group14-sha1
kex 220 name diffie-hellman-group-exchange-sha1
kex 225 name diffie-hellman-group1-sha1
exit
server-kex-list
kex 200 name diffie-hellman-group16-sha512
kex 210 name diffie-hellman-group14-sha256
kex 215 name diffie-hellman-group14-sha1
kex 220 name diffie-hellman-group-exchange-sha1
kex 225 name diffie-hellman-group1-sha1
exit
----------------------------------------------
*A:Sar8 Dut-A>config>system>security>ssh#Configuring SSH MAC algorithm lists
Use the ssh command to configure SSHv2 client and server MAC algorithm lists. Client MAC algorithm lists are used if the 7705 SAR is acting as an SSH client, and server MAC algorithm lists are used if the 7705 SAR is acting as an SSH server.
-
hmac-sha1-96
- hmac-md5
-
hmac-mda5-96
- CLI syntax:
config>system>security ssh client-mac-list mac index name mac-name server-mac-list mac index name mac-name
- Example:
config>system>security# ssh config>system>security>ssh# client-mac-list config>system>security>ssh>client-mac# mac 200 name hmac-sha2-512 config>system>security>ssh>client-mac# mac 210 name hmac-sha2-256 config>system>security>ssh>client-mac# mac 215 name hmac-sha1 config>system>security>ssh>client-mac# mac 220 name hmac-sha1-96 config>system>security>ssh>client-mac# mac 225 name hmac-md5 config>system>security>ssh>client-mac# mac 240 name hmac-md5-96 config>system>security>ssh>client-mac# exit config>system>security>ssh# server-mac-list config>system>security>ssh>server-mac# mac 200 name hmac-sha2-512 config>system>security>ssh>server-mac# mac 210 name hmac-sha2-256 config>system>security>ssh>server-mac# exit config>system>security>ssh# exit
The following example displays client and server MAC list configurations:
A:Sar8 Dut-A>config>system>security>ssh# info detail
----------------------------------------------
client-mac-list
mac 200 name hmac-sha2-512
mac 210 name hmac-sha2-256
mac 215 name hmac-sha1
mac 220 name hmac-sha1-96
mac 225 name hmac-md5
mac 240 name hmac-md5-96
exit
server-mac-list
mac 200 name hmac-sha2-512
mac 210 name hmac-sha2-256
mac 215 name hmac-sha1
mac 220 name hmac-sha1-96
mac 225 name hmac-md5
mac 240 name hmac-md5-96
exit
exit
----------------------------------------------
*A:Sar8 Dut-A>config>system>security>ssh#Configuring login controls
Use the login-control context to configure parameters for console, FTP, SSH, and Telnet sessions.
- CLI syntax:
-
config>system login-control exponential-backoff ftp inbound-max-sessions value ssh [no] disable-graceful-shutdown inbound-max-sessions value outbound-max-sessions value ttl-security min-ttl-value telnet [no] enable-graceful-shutdown inbound-max-sessions value outbound-max-sessions value ttl-security min-ttl-value idle-timeout {minutes | disable} pre-login-message login-text-string [name] login-banner motd {url url-prefix:source-url | text motd-text-string}
The following example displays the login control configuration:
- Example:
-
config>system>login-control# ftp inbound-max-sessions 5 config>system>login-control# ssh inbound-max-sessions 12 config>system>login-control# ssh outbound-max-sessions 8 config>system>login-control# ssh ttl-security 100 config>system>login-control# telnet enable-graceful-shutdown config>system>login-control# telnet inbound-max-sessions 7 config>system>login-control# telnet outbound-max-sessions 2 config>system>login-control# idle-timeout 1440 config>system>login-control# pre-login-message "Property of Service Routing Inc. Unauthorized access prohibited." config>system>login-control# motd text "Notice to all users: Software upgrade scheduled 3/2 1:00 AM"
The following example displays the login control configuration:
ALU-1>config>system# info
----------------------------------------------
...
login-control
ftp
inbound-max-sessions 5
exit
ssh
no disable-graceful-shutdown
inbound-max-sessions 12
outbound-max-sessions 8
ttl-security 100
telnet
enable-graceful-shutdown
inbound-max-sessions 7
outbound-max-sessions 2
exit
idle-timeout 1440
pre-login-
message "Property of Service Routing Inc. Unauthorized access prohibited."
motd text "Notice to all users: Software upgrade scheduled 3/2 1:00 AM"
exit
no exponential-backoff
...
----------------------------------------------
ALU-1>config>system#Configuring RADIUS parameters
Configuring RADIUS authentication
RADIUS is disabled by default and must be explicitly enabled. The mandatory commands to enable RADIUS on the local router are radius and server server-index address ip-address secret key. The server command adds a RADIUS server and configures the RADIUS server’s IP address, index, and key values. The index determines the sequence in which the servers are queried for authentication requests.
Also, the system IP address must be configured in order for the RADIUS client to work. See ‟Configuring a System Interface” in the 7705 SAR Router Configuration Guide.
The other commands are optional.
On the local router, use the following CLI commands to configure RADIUS authentication:
- CLI syntax:
config>system>security radius port port retry count server server-index address ip-address secret key [hash1 | hash2] timeout seconds no shutdown
The following example displays the CLI syntax usage:
- Example:
config>system>security> security# radius security# no shutdown security>radius# server 1 address A:A:A:A:A:A:A:1 secret test11 security>radius# server 2 address 10.10.0.1 secret test2 security>radius# server 3 address 10.10.0.2 secret test3 security>radius# server 4 address 10.10.0.3 secret test4 security>radius# retry 5 security>radius# timeout 5 config>system>security>radius# exit
The following example displays the RADIUS authentication configuration:
ALU-1>config>system>security# info
----------------------------------------------
retry 5
timeout 5
server 1 address A:A:A:A:A:A:A:1 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
...
----------------------------------------
ALU-1>config>system>security#Configuring RADIUS authorization
In order for RADIUS authorization to function, RADIUS authentication must be enabled first. See Configuring RADIUS authentication.
In addition to the local configuration requirements, VSAs must be configured on the RADIUS server. See RADIUS VSAs.
On the local router, use the following CLI commands to configure RADIUS authorization:
- CLI syntax:
config>system>security radius authorization
The following example displays the CLI syntax usage:
- Example:
config>system>security> config>system>security# radius config>system>security>radius# authorization
The following example displays the RADIUS authorization configuration:
ALU-1>config>system>security# info
----------------------------------------------
...
radius
authorization
retry 5
timeout 5
server 1 address 10.10.10.103 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
exit
...
----------------------------------------------Configuring RADIUS accounting
On the local router, use the following CLI commands to configure RADIUS accounting:
- CLI syntax:
config>system>security radius accounting
The following example displays the CLI syntax usage:
- Example:
config>system>security> config>system>security# radius config>system>security>radius# accounting
The following example displays the RADIUS accounting configuration:
ALU-1>config>system>security# info
----------------------------------------------
...
radius
shutdown
authorization
accounting
retry 5
timeout 5
server 1 address 10.10.10.103 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
exit
...
----------------------------------------------
ALU-1>config>system>security#Configuring 802.1x RADIUS policies
Use the following CLI commands to configure generic authentication parameters for clients using 802.1x EAPOL. Additional parameters are configured on Ethernet ports. See the 7705 SAR Interface Configuration Guide, ‟Configuration Command Reference”, for more information about configuring 802.1x parameters on Ethernet ports.
To configure generic parameters for 802.1x authentication, enter the following CLI syntax:
- CLI syntax:
config>system>security dot1x radius-plcy name [create] retry count server server-index address ip-address secret key [hash | hash2] [auth-port auth-port] [acct-port acct-port] [type server-type] no shutdown source-address ip-address timeout seconds no shutdown
The following example displays the CLI syntax usage:
- Example:
config>system>security> config>system>security# dot1x config>system>security>dot1x# radius-plcy dot1x_plcy create config>system>security>dot1x>radius-plcy# server 1 address 10.10.10.1 secret abc auth-port 65000 config>system>security>dot1x>radius-plcy# server 2 address 10.10.10.3 secret xyz auth-port 862 config>system>security>dot1x>radius-plcy# source-address 10.10.10.255
The following example displays an 802.1x configuration:
*A:7705_custDoc>config>system>security>dot1x# info
----------------------------------------------
radius-plcy "dot1x_plcy" create
server 1 address 10.10.10.1 auth-port 65000 acct-
port 1813 secret "WDoQz6DJf4.0M5dlpwjHbk" hash2 type authorization
server 2 address 10.10.10.3 auth-port 862 acct-port 1813 secret
"WDoQz6DJf4.j1WcCeHZwz." hash2 type authorization
source-address 10.10.10.255
shutdown
exit
...
----------------------------------------------
A:ALU-1>config>system#Configuring TACACS+ parameters
Enabling TACACS+ authentication
To use TACACS+ authentication on the router, configure one or more TACACS+ servers on the network.
Use the following CLI commands to configure TACACS+ authentication:
- CLI syntax:
config>system>security tacplus server server-index address ip-address secret key [hash1 | hash2] timeout seconds no shutdown
The following example is configured in the config>system context:
- Example:
security# tacplus security>tacplus# server 1 address A:A:A:A:A:A:A:1 secret test1 security>tacplus# server 2 address 10.10.0.6 secret test2 security>tacplus# server 3 address 10.10.0.7 secret test3 security>tacplus# server 4 address 10.10.0.8 secret test4 security>tacplus# server 5 address 10.10.0.9 secret test5 config>system>security>tacplus# timeout 5 config>system>security>tacplus# no shutdown
The following example displays the TACACS+ authentication configuration:
ALU-1>config>system>security>tacplus# info
----------------------------------------------
timeout 5
server 1 address A:A:A:A:A:A:A:1 secret "h6.TeL7YPohbmhlvz0gob."
hash2
server 2 address 10.10.0.6 secret "h6.TeL7YPog7WbLsR3QRd." hash2
server 3 address 10.10.0.7 secret "h6.TeL7YPojGJqbYt85LVk" hash2
server 4 address 10.10.0.8 secret "h6.TeL7YPoiCfWKUFHARvk" hash2
server 5 address 10.10.0.9 secret "h6.TeL7YPojuCyTFvTNGBU" hash2Configuring TACACS+ authorization
In order for TACACS+ authorization to function, TACACS+ authentication must be enabled first. See Enabling TACACS+ authentication.
On the local router, use the following CLI commands to configure TACACS+ authorization:
- CLI syntax:
config>system>security tacplus authorization no shutdown
The following example displays the CLI syntax usage:
- Example:
config>system>security> config>system>security# tacplus config>system>security>tacplus# authorization config>system>security>tacplus# no shutdown
The following example displays the TACACS+ authorization configuration:
ALU-1>config>system>security>tacplus# info
----------------------------------------------
authorization
timeout 5
server 1 address 10.10.0.5 secret "h6.TeL7YPohbmhlvz0gob." hash2
server 2 address 10.10.0.6 secret "h6.TeL7YPog7WbLsR3QRd." hash2
server 3 address 10.10.0.7 secret "h6.TeL7YPojGJqbYt85LVk" hash2
server 4 address 10.10.0.8 secret "h6.TeL7YPoiCfWKUFHARvk" hash2
server 5 address 10.10.0.9 secret "h6.TeL7YPojuCyTFvTNGBU" hash2
----------------------------------------------
ALU-1>config>system>security>tacplus# Configuring TACACS+ accounting
On the local router, use the following CLI commands to configure TACACS+ accounting:
- CLI syntax:
config>system>security tacplus accounting
The following example displays the CLI syntax usage:
- Example:
config>system>security> config>system>security# tacplus config>system>security>tacplus# accounting
The following example displays the TACACS+ accounting configuration:
ALU-1>config>system>security>tacplus# info
----------------------------------------------
accounting
authorization
timeout 5
server 1 address 10.10.0.5 secret "h6.TeL7YPohbmhlvz0gob." hash2
server 2 address 10.10.0.6 secret "h6.TeL7YPog7WbLsR3QRd." hash2
server 3 address 10.10.0.7 secret "h6.TeL7YPojGJqbYt85LVk" hash2
server 4 address 10.10.0.8 secret "h6.TeL7YPoiCfWKUFHARvk" hash2
server 5 address 10.10.0.9 secret "h6.TeL7YPojuCyTFvTNGBU" hash2
----------------------------------------------
ALU-1>config>system>security>tacplus#Configuring keychain authentication
The keychain authentication mechanism protects communication between routing protocol neighbors against malicious attacks. Keychain authentication provides the ability to configure authentication keys and update them through key rollover without affecting the state of the routing protocol adjacencies. See Key rollover for more information about begin-time and end-time configuration.
This procedure describes how to set up keychain authentication.
-
Configure the keychain instance using the following command:
Note: A keychain must be configured on the system before it can be applied to a session.
config>system>security>keychain name -
Configure keychain authentication under the keychain
context. The keychain must have at least one valid entry and an authentication
algorithm:
config>system>security>keychain direction bi entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm] begin-time [date] [hours-minutes] [UTC] exit entry entry-id2 [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm] begin-time [date] [hours-minutes] [UTC] exit exit exit no shutdown -
Associate the configured authentication keychain with a protocol; for
example:
Depending on the protocol, authentication keychains can be used for authentication at the global, level, and interface contexts. For IS-IS, Hello authentication keychains can be used for authentication at the interface and interface level contexts.config>router# isis [isis-instance] auth-keychain name level {1 | 2} auth-keychain name
Configuring keychains
The keychain mechanism allows for the creation of keys used to authenticate protocol communications. Each keychain entry defines the authentication attributes to be used in authenticating protocol messages from remote peers or neighbors; the keychain must include at least one key entry to be valid.
Each key within a keychain must include the following attributes for the authentication of protocol messages:
key identifier
authentication algorithm
authentication key
direction
begin time
Optionally, each key can include an end time and tolerance.
Use the following CLI commands to configure a keychain:
- CLI syntax:
config>system>security keychain name description description-string direction bi entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm] begin-time [date] [hours-minutes] [UTC] tolerance {seconds | forever} uni receive entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm] begin-time [date] [hours-minutes] [UTC] tolerance {seconds | forever} send entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm] begin-time [date] [hours-minutes] [UTC]
The following example displays a keychain configuration:
A:ALU-1>config>system>security># info detail
----------------------------------------------
...
keychain "ospf-md5"
description "MD5 keychain for OSPF interfaces"
tcp-option-number
send 254
receive 254
exit
direction
bi
entry 0 key "VyScMGuUfEQw9vxb9YWEG8oEeyRxTrGC.aFwWKzlO1E
" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/01 00:00:00 UTC
no option
exit
entry 1 key "VyScMGuUfEQw9vxb9YWEG6rfIEGa/.sGbxt3BaeWYO.
" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/09 00:00:00 UTC
no option
tolerance 600
exit
exit
exit
no shutdown
exit
keychain "rsvp-md5"
description "MD5 keychain for RSVP interfaces"
tcp-option-number
send 254
receive 254
exit
direction
uni
send
entry 0 key "f4L8216viTz8OMIKEcNfF/0BxU12MaZskrUHlTN
YMwY" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/01 00:00:00 UTC
exit
entry 1 key "f4L8216viTz8OMIKEcNfF0VmwDJEUYqX1ob50zL
E0HY" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/09 00:00:00 UTC
exit
exit
receive
entry 0 key "dE.xAjca3DLqssbdJ8zc8vblBwYsvFXL57dvJEu
RQHE" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/01 00:00:00 UTC
tolerance 600
exit
entry 1 key "dE.xAjca3DLqssbdJ8zc4ty4BxUSFV5xl9ejgfr
YHGG" hash2 algorithm message-digest
no shutdown
begin-time 2016/06/09 00:00:00 UTC
tolerance 600
exit
exit
exit
----------------------------------------------
A:ALU-1>config>system>security#In the above example, two separate keychains are created, ‟ospf-md5” and ‟rsvp-md5”, each with two possible keys.
For ospf-md5:
entry 0 is valid starting at midnight (UTC) on 2016/06/01
entry 1 will become valid at midnight (UTC) on 2016/06/09 and will replace entry 0
there is an overlap (tolerance) period of 600 seconds in which packets with either key (entry 0 or entry 1) will be accepted
For rsvp-md5:
for transmitted packets:
send key entry 0 is valid starting at midnight (UTC) on 2016/06/01
send key entry 1 will become valid at midnight (UTC) on 2016/06/09 and will replace entry 0
for received packets:
receive key entry 0 is valid starting at midnight (UTC) on 2016/06/01
receive key entry 1 will become valid at midnight (UTC) on 2016/06/09 and will replace entry 0
there is an overlap (tolerance) period of 600 seconds in which receive packets with either key (entry 0 or entry 1) will be accepted
Security command reference
Command hierarchies
Admin commands
admin
- system
- security
- system-password admin-password
Configuration commands
Security configuration commands
config
- system
- security
- copy {user source-user | profile source-profile} to destination [overwrite]
- ftp-server
- no ftp-server
- hash-control [read-version {1 | 2 | all}] [write-version {1 | 2}]
- no hash-control
- source-address
- application app [ip-int-name | ip-address]
- no application app
- application6 app ipv6-address
- no application6 app
- telnet
-listening-port port
-no listening-port
- [no] telnet-server
- [no] telnet6-server
- vprn-network-exceptions [number seconds]
- no vprn-network-exceptions
Management access filter commands
config
- system
- security
- [no] management-access-filter
- ip-filter
- default-action {permit | deny | deny-host-unreachable}
- [no] entry entry-id
- action {permit | deny | deny-host-unreachable}
- no action
- description description-string
- no description
- dst-port port [mask]
- no dst-port
- [no] log
- [no] protocol protocol-id
- router router-instance
- router service-name service-name
- no router
- src-ip {ip-prefix [/mask] [netmask] | ip-prefix-list ip-prefix-list-name}
- no src-ip
- src-port {port-id | cpm | lag lag-id}
- no src-port
- renum old-entry-number new-entry-number
- [no] shutdown
IPv6 management access filter commands
config
- system
- security
- [no] management-access-filter
- ipv6-filter
- default-action {permit | deny | deny-host-unreachable}
- [no] entry entry-id
- action {permit | deny | deny-host-unreachable}
- no action
- description description-string
- no description
- dst-port port [mask]
- no dst-port
- flow-label value
- no flow-label
- [no] log
- [no] next-header next-header
- router router-instance
- router service-name service-name
- no router
- src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
- no src-ip
- src-port {port-id | cpm | lag lag-id}
- no src-port
- renum old-entry-number new-entry-number
- [no] shutdown
CPM filter commands
config
- system
- security
- [no] cpm-filter
- default-action {accept | drop}
- ip-filter
- entry entry-id [create]
- no entry entry-id
- action {accept | drop}
- no action
- description description-string
- no description
- log log-id
- no log
- match [protocol protocol-id]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no dst-ip
- dst-port tcp/udp port-number [mask]
- no dst-port
- fragment {true | false}
- no fragment
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- ip-option ip-option-value [ip-option-mask]
- no ip-option
- multiple-option {true | false}
- no multiple-option
- option-present {true | false}
- no option-present
- src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
- no src-ip
- src-port tcp/udp port-number [mask]
- no src-port
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
- renum old-entry-id new-entry-id
- [no] shutdown
IPv6 CPM filter commands
config
- system
- security
- [no] cpm-filter
- default-action {accept | drop}
- ipv6-filter
- entry entry-id [create]
- no entry entry-id
- action {accept | drop}
- no action
- description description-string
- no description
- log log-id
- no log
- match [next-header next-header]
- no match
- dscp dscp-name
- no dscp
- dst-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
- no dst-ip
- dst-port tcp/udp port-number [mask]
- no dst-port
- icmp-code icmp-code
- no icmp-code
- icmp-type icmp-type
- no icmp-type
- src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
- no src-ip
- src-port tcp/udp port-number [mask]
- no src-port
- tcp-ack {true | false}
- no tcp-ack
- tcp-syn {true | false}
- no tcp-syn
- renum old-entry-id new-entry-id
- [no] shutdown
Password commands
config
- system
- security
- password
- admin-password password [hash | hash2]
- no admin-password
- aging days
- no aging
- attempts count [time minutes1] [lockout minutes2]
- no attempts
- authentication-order [method-1] [method-2] [method-3] [exit-on-reject]
- no authentication-order
- complexity-rules
- [no] allow-user-name
- credits [lowercase credits] [uppercase credits] [numeric credits] [special-character credits]
- no credits
- disallow-sequence-keys value
- no disallow-sequence-keys
- minimum-classes minimum
- no minimum-classes
- minimum-length value
- no minimum-length
- repeated-characters count
- no repeated-characters
- required [lowercase count] [uppercase count] [numeric count] [special-character count]
- no required
- hashing hashing {bcrypt | sha2-pbkdf2 | sha3-pbkdf2}
- [no] health-check [interval interval]
- history-size size
- no history-size
- minimum-age [days days] [hrs hours] [min minutes] [sec seconds]
- no minimum-age
- minimum-change length
- no minimum-change
Profile commands
config
- system
- security
- [no] profile user-profile-name
- default-action {deny-all | permit-all | none}
- [no] entry entry-id
- action {permit | deny}
- description description-string
- no description
- match command-string
- no match
- renum old-entry-number new-entry-number
User commands
config
- system
- security
- [no] user user-name
- [no] access [ftp] [snmp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli]
- console
- [no] cannot-change-password
- [no] local-lockout
- login-exec url-prefix:source-url
- no login-exec
- member user-profile-name [user-profile-name…(up to 8 max)]
- no member user-profile-name
- [no] new-password-at-login
- home-directory url-prefix [directory] [directory/directory…]
- no home-directory
- password [password]
- public-keys
- ecdsa
- [no] ecdsa-key key-id [create]
- description description-string
- no description
- key-value public-key-value
- no key-value
- rsa
- [no] rsa-key key-id [create]
- description description-string
- no description
- key-value public-key-value
- no key-value
- [no] restricted-to-home
- [no] save-when-restricted
- snmp
- authentication none
- authentication authentication-protocol authentication-key [privacy none] [hash | hash2]
- authentication authentication-protocol authentication-key privacy privacy-protocol privacy-key [hash | hash2]
- no authentication
- group group-name
- no group
- user-template {tacplus_default | radius_default}
- [no] access [ftp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli]
- console
- login-exec url-prefix:source-url
- no login-exec
- home-directory url-prefix [directory] [directory/directory ..]
- no home-directory
- profile user-profile-name
- no profile
- [no] restricted-to-home
- [no] save-when-restrictedCLI script authorization commands
config
- system
- security
- cli-script
- authorization
- cron
- cli-user user-name
- no cli-user
- event-handler
- cli-user user-name
- no cli-user
RADIUS commands
config
- system
- security
- [no] radius
- access-algorithm {direct | round-robin}
- [no] access-algorithm
- [no] accounting
- accounting-port port
- no accounting-port
- [no] authorization
- port port
- no port
- retry count
- no retry
- server server-index address ip-address secret key [hash | hash2]
- no server server-index
- [no] shutdown
- timeout seconds
- no timeout
- use-default-template
TACACS+ commands
config
- system
- security
- [no] tacplus
- accounting [record-type {start-stop | stop-only}]
- no accounting
- [no] authorization
- server server-index address ip-address secret key [hash | hash2] [port port]
- no server server-index
- timeout seconds
- no timeout
- [no] shutdown
- [no] use-default-template
802.1x commands
config
- system
- security
- [no] dot1x
- [no] radius-plcy name [create]
- retry count
- no retry
- server server-index address ip-address secret key [hash | hash2] [auth-port auth-port] [acct-port acct-port] [type server-type]
- no server server-index
- source-address ip-address
- no source-address
- [no] shutdown
- timeout seconds
- no timeout
- [no] shutdown
SSH commands
config
- system
- security
- ssh
- client-cipher-list
- cipher index name cipher-name
- no cipher index
- client-kex-list
- kex index name kex-name
- no kex index
- client-mac-list
- mac index name mac-name
- no mac index
- key-re-exchange
- client
- mbytes {mbytes | disable}
- no mbytes
- minutes {minutes | disable}
- no minutes
- [no] shutdown
- server
- mbytes {mbytes | disable}
- no mbytes
- minutes {minutes | disable}
- no minutes
- [no] shutdown
- listening-port port
- no listening-port
- [no] preserve-key
- server-cipher-list
- cipher index name cipher-name
- no cipher index
- server-kex-list
- kex index name kex-name
- no kex index
- server-mac-list
- mac index name mac-name
- no mac index
- [no] server-shutdown
TLS commands
config
system
security
tls
cert-profile profile-name [create]
no cert-profile profile-name
entry entry-id [create]
no entry entry-id
cert cert-filename
no cert
key key-filename
no key
[no] send-chain
[no] ca-profile name
[no] shutdown
client-cipher-list name [create]
no client-cipher-list name
cipher index name cipher-suite-code
no cipher index
tls13-cipher index name cipher-suite-code
no tls13-cipher index
client-group-list name [create]
no client-group-list name
tls13-group index name group-suite-code
no tls13-group index
client-signature-list name [create]
no client-signature-list name
tls13-signature index name signature-suite-code
no tls13-signature index
client-tls-profile name [create]
no client-tls-profile name
cert-profile name
no cert-profile
cipher-list name
no cipher-list
group-list name
no group-list
protocol-version TLS version
no protocol-version
[no] shutdown
signature-list name
no signature-list
trust-anchor-profile name
no trust-anchor-profile
trust-anchor-profile name [create]
no trust-anchor-profile name
[no] trust-anchor ca-profile-name
Keychain authentication commands
config
- system
- security
- [no] keychain keychain-name
- description description-string
- no description
- direction
- bi
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entryentry-id
- begin-time date hours-minutes [UTC]
- begin-time {now | forever}
- no begin-time
- option {basic | isis-enhanced}
- no option
- [no] shutdown
- tolerance {seconds | forever}
- no tolerance
- uni
- receive
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entry entry-id
- begin-time date hours-minutes [UTC]
- begin-time {now | forever}
- no begin-time
- end-time date hours-minutes [UTC]
- end-time {now | forever}
- no end-time
- [no] shutdown
- tolerance {seconds | forever}
- no tolerance
- send
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entry entry-id
- begin-time date hours-minutes [UTC]
- begin-time {now | forever}
- no begin-time
- [no] shutdown
- [no] shutdown
- tcp-option-number
- receive option-number
- no receive
- send option-number
- no send
Login control commands
config
- system
- login-control
- [no] exponential-backoff
- ftp
- inbound-max-sessions value
- no inbound-max-sessions
- idle-timeout {minutes | disable}
- no idle-timeout
- [no] login-banner
- motd {url url-prefix: source-url | text motd-text-string}
- no motd
- pre-login-message login-text-string [name]
- no pre-login-message
- ssh
- [no] disable-graceful-shutdown
- inbound-max-sessions value
- no inbound-max-sessions
- outbound-max-sessions value
- no outbound-max-sessions
- ttl-security min-ttl-value
- no ttl-security
- telnet
- [no] enable-graceful-shutdown
- inbound-max-sessions value
- no inbound-max-sessions
- outbound-max-sessions value
- no outbound-max-sessions
- ttl-security min-ttl-value
- no ttl-security
Show commands
Security commands
show
- system
- security
- access-group [group-name]
- authentication [statistics]
- communities
- cpm-filter
- ip-filter [entry entry-id]
- ipv6-filter [entry entry-id]
- keychain [keychain] [detail]
- management-access-filter
- ip-filter [entry entry-id]
- ipv6-filter [entry entry-id]
- password-options
- profile user-profile-name
- source-address
- ssh
- tls
- cert-profile name association
- cert-profile [name]
- cert-profile name entry 1..8
- client-tls-profile [client-tls-profile]
- client-tls-profile client-tls-profile association
- client-tls-profile client-tls-profile [connections]
- trust-anchor-profile trust-anchor-profile association
- trust-anchor-profile [trust-anchor-profile]
- user [user-id] detail
- user [user-id] lockout
- view [view-name] [detail] [capabilities]
Login control commands
show
- users
Clear commands
Admin commands
admin
- clear
- lockout all
- lockout user user-name
- password-history all
- password-history user user-name
Authentication commands
clear
- router
- authentication
- statistics [interface ip-int-name | ip-address]
Monitor commands
monitor
- cpm-filter
- ip entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
- ipv6 entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
- mac entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
- management-access-filter
- ip entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
- ipv6 entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
- mac entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Debug commands
Command descriptions
Admin commands
system-password
Syntax
system-password admin-password
Context
admin>system>security
Description
This operational command changes a local administrative password.
When invoked, the user is prompted to enter the old password, the new password, and then the new password again to verify the correct input. Any subsequent invocation of enable-admin will require this new admin-password.
Parameters
- admin-password
-
specifies to change the administrative password which is requested when a user tries to enable admin mode by running enable-admin to attain administrative privileges
Configuration commands
Generic security commands
description
Syntax
description description-string
no description
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
config>system>security>cpm-filter>ip-filter>entry
config>system>security>cpm-filter>ipv6-filter>entry
config>system>security>keychain
config>system>security>user>public-keys>ecdsa>ecdsa-key
config>system>security>user>public-keys>rsa>rsa-key
Description
This command creates a text description stored in the configuration file for a configuration context.
The no form of the command removes the string.
Default
n/a
Parameters
- description-string
the description character string. Allowed values are any string up to 80 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>system>security>management-access-filter>ip-filter
config>system>security>management-access-filter>ipv6-filter
config>system>security>cpm-filter>ip-filter
config>system>security>cpm-filter>ipv6-filter
config>system>security>keychain
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
config>system>security>radius
config>system>security>tacplus
Description
This command administratively disables the entity. The operational state of the entity is disabled as well as the operational state of any entities contained within. When disabled, an entity does not change, reset, or remove any configuration settings or statistics, other than the administrative state. Many objects must be shut down before they can be deleted.
The no form of the command puts an entity into the administratively enabled state. Many entities must be explicitly enabled using the no shutdown command.
Default
no shutdown
Security commands
security
Syntax
security
Context
config>system
Description
This command enables the context to configure security settings.
Security commands manage user profiles and user membership. Security commands also manage user login registrations.
copy
Syntax
copy {user source-user | profile source-profile} to destination [overwrite]
Context
config>system>security
Description
This command copies the specified user or profile configuration parameters to another (destination) user or profile.
The password is set to the Return key and a new password at login must be selected.
Parameters
- source-user
the user to copy from. The user must already exist.
- source-profile
the profile to copy from. The profile must already exist.
- destination
the destination user or profile
- overwrite
specifies that the destination user or profile configuration will be overwritten with the copied source user or profile configuration. A configuration will not be overwritten if the overwrite command is not specified.
ftp-server
Syntax
[no] ftp-server
Context
config>system>security
Description
This command enables FTP servers running on the system.
FTP servers are disabled by default. At system startup, only SSH servers are enabled.
The no form of the command disables FTP servers running on the system.
Default
no ftp-server
hash-control
Syntax
hash-control [read-version {1 | 2 | all}] [write-version {1 | 2}]
no hash-control
Context
config>system>security
Description
Whenever the user executes a save or info command, the system will encrypt all passwords, keys, and so on for security reasons. At present, two algorithms exist.
The first algorithm is a simple, short key that can be copied and pasted in a different location when the user wants to configure the same password. However, because it is the same password and the hash key is limited to the password/key, it is obvious that it is the same key.
The second algorithm is a more complex key, and cannot be copied and pasted in different locations in the configuration file. In this case, if the same key or password is used repeatedly in different contexts, each encrypted (hashed) version will be different.
Default
all – read-version set to accept both versions 1 and 2
Parameters
- read-version {1 | 2 | all}
when the read-version is configured as ‟all,” both versions 1 and 2 will be accepted by the system. Otherwise, only the selected version will be accepted when reading configuration or exec files. The presence of incorrect hash versions will abort the script/startup.
- write-version {1 | 2}
selects the hash version that will be used the next time the configuration file is saved (or an info command is executed). Be careful to save the read and write version correctly, so that the file can be properly processed after the next reboot or exec.
source-address
Syntax
source-address
Context
config>system>security
Description
This command specifies the source address that should be used in all unsolicited packets sent by the application.
application
Syntax
application app [ip-int-name | ip-address]
no application app
Context
config>system>security>source-address
Description
This command specifies the application to use the source IPv4 address specified by the source-address command.
The no form of the command removes the specified source address from the application, causing the application to use the system IP address as the source address.
Parameters
- app
specifies the application name
- ip-int-name | ip-address
specifies the name of the IP interface or IPv4 address. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
application6
Syntax
application6 app ipv6-address
no application6 app
Context
config>system>security>source-address
Description
This command specifies the application to use the source IPv6 address specified by the source-address command.
The no form of the command removes the specified source address from the application, causing the application to use the system IP address as the source address.
Parameters
- app
specifies the application name
- ipv6-address
specifies the IPv6 address
telnet
Syntax
telnet
Context
config>system>security
Description
This command enables the context to configure Telnet parameters.
listening-port
Syntax
listening-port port
no listening-port
Context
config>system>security>telnet
Description
This command configures the listening TCP port of the Telnet server for incoming Telnet connections via base or management routing. VPRN node management is done via GRT leaking and uses base routing.
The no form of this command resets the listening port to its default of 23.
Default
no listening port
Parameters
- port
-
specifies the port number
telnet-server
Syntax
[no] telnet-server
Context
config>system>security
Description
This command enables Telnet servers running on the system.
Telnet servers are off by default. At system startup, only SSH servers are enabled.
Telnet servers in 7705 SAR networks limit a Telnet client to three retries to log in. The Telnet server disconnects the Telnet client session after three retries.
The no form of the command disables Telnet servers running on the system.
Default
no telnet-server
telnet6-server
Syntax
[no] telnet6-server
Context
config>system>security
Description
This command enables Telnet IPv6 servers running on the system.
Telnet servers are off by default. At system startup, only SSH servers are enabled.
Telnet servers in 7705 SAR networks limit a Telnet client to three retries to log in. The Telnet server disconnects the Telnet client session after three retries.
The no form of the command disables Telnet servers running on the system.
Default
no telnet6-server
vprn-network-exceptions
Syntax
vprn-network-exceptions [number seconds]
no vprn-network-exceptions
Context
config>system>security
Description
This command configures the rate at which the 7705 SAR sends ICMP replies to a source IP address in response to TTL expiry IP packets that have been received for all VPRN instances in the system and from all network IP interfaces. Packets include labeled user packets as well as ping and traceroute packets within a VPRN.
This command does not apply to MPLS packets or service OAM packets such as VPRN ping and trace, LSP ping and trace, and VCC ping and trace.
When the command is issued without any number and seconds parameters specified, the default rate is 100 ICMP reply packets sent per 10 seconds. The no form of the command disables the rate-limiting of ICMP replies.
Default
no vprn-network-exceptions
Parameters
- number
specifies the maximum number of ICMP reply messages that can be sent within the configured number of seconds
- seconds
specifies the time frame in which the configured number of ICMP reply messages can be sent
Management access filter commands
management-access-filter
Syntax
[no] management-access-filter
Context
config>system>security
Description
This command enables the context to edit management access filters and to reset match criteria.
Management access filters control all traffic in and out of the CSM. They can be used to restrict management of the 7705 SAR by other nodes outside either specific (sub)networks or through designated ports.
Management filters, as opposed to other traffic filters, are enforced by system software.
The no form of the command removes management access filters from the configuration.
Default
n/a
ip-filter
Syntax
ip-filter
Context
config>system>security>management-access-filter
Description
This command enables the context to configure IP filter commands.
ipv6-filter
Syntax
ipv6-filter
Context
config>system>security>management-access-filter
Description
This command enables the context to configure IPv6 filter commands.
default-action
Syntax
default-action {permit | deny | deny-host-unreachable}
Context
config>system>security>management-access-filter>ip-filter
config>system>security>management-access-filter>ipv6-filter
Description
This command creates the default action for management access in the absence of a specific management access filter match.
The default-action is applied to a packet that does not satisfy any match criteria in any of the management access filters. Whenever management access filters are configured, the default-action must be defined.
Default
n/a
Parameters
- permit
specifies that packets not matching the configured selection criteria in any of the filter entries will be permitted
- deny
specifies that packets not matching the selection criteria will be denied
- deny-host-unreachable
specifies that packets not matching the selection criteria will be denied and a host unreachable message will be issued
entry
Syntax
[no] entry
Context
config>system>security>management-access-filter>ip-filter
config>system>security>management-access-filter>ipv6-filter
Description
This command is used to create or edit a management access filter entry. Multiple entries can be created with unique entry-id numbers. The 7705 SAR exits the filter upon the first match found and executes the actions according to the respective action command. For this reason, entries must be sequenced correctly from most to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action defined to be considered complete. Entries without the action keyword are considered incomplete and inactive.
The no form of the command removes the specified entry from the management access filter.
Default
n/a
Parameters
- entry-id
an entry ID uniquely identifies a match criteria and the corresponding action. It is recommended that entries be numbered in staggered increments. This allows users to insert a new entry in an existing policy without having to renumber the existing entries.
action
Syntax
action {permit | deny | deny-host-unreachable}
no action
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command creates the action associated with the management access filter match criteria entry.
The action keyword is required. If no action is defined, the filter is ignored. If multiple action statements are configured, the last one overwrites previous configured actions.
If the packet does not meet any of the match criteria, the configured default action is applied.
Default
n/a
Parameters
- permit
specifies that packets matching the configured criteria will be permitted
- deny
specifies that packets not matching the selection criteria will be denied
- deny-host-unreachable
specifies that packets not matching the selection criteria will be denied and a host unreachable message will be issued
dst-port
Syntax
dst-port port [mask]
no dst-port
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command configures a destination TCP or UDP port number or port range for a management access filter match criterion.
The no form of the command removes the destination port match criterion.
Default
n/a
Parameters
- port
the source TCP or UDP port number as match criteria
- mask
mask used to specify a range of destination port numbers as the match criterion
This 16-bit mask can be configured using the formats in the following table.
Table 7. 16-bit mask formats Format style
Format syntax
Example
Decimal
DDDDD
63488
Hexadecimal
0xHHHH
0xF800
Binary
0bBBBBBBBBBBBBBBBB
0b1111100000000000
For example, to select a range from 1024 up to 2047, specify 1024 0xFC00 for value and mask.
flow-label
Syntax
flow-label value
no flow-label
Context
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command configures flow label match conditions for a management access filter match criterion. Flow labeling enables the labeling of packets belonging to particular traffic flows for which the sender requests special handling, such as non-default QoS or real-time service.
This command applies to IPv6 filters only.
Parameters
- value
the flow identifier in an IPv6 packet header that can be used to discriminate traffic flows (see RFC 3595, Textual Conventions for IPv6 Flow Label)
log
Syntax
[no] log
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command enables match logging.
The no form of this command disables match logging.
Default
no log
next-header
Syntax
[no] next-header next-header
Context
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command specifies the next header to match as a management access filter match criterion.
This command applies to IPv6 filters only.
Parameters
- next-header
protocol-number or protocol-name
- protocol-number
the IPv6 next header to match, expressed as a protocol number in decimal, hexadecimal, or binary. This parameter is similar to the protocol parameter used in IPv4 filter match criteria. See IP protocol IDs and descriptions for the protocol IDs and descriptions for the IP protocols.
- protocol-name
the IPv6 next header to match, expressed as a protocol name. This parameter is similar to the protocol parameter used in IPv4 filter match criteria. See IP protocol IDs and descriptions for the protocol IDs and descriptions for the IP protocols.
protocol
Syntax
[no] protocol protocol-id
Context
config>system>security>management-access-filter>ip-filter>entry
Description
This command configures an IP protocol type to be used as a management access filter match criterion.
The protocol type is identified by its respective protocol number. Well-known protocol numbers include ICMP (1), TCP (6), and UDP (17). The following table lists the protocol IDs and descriptions for the IP protocols.
|
Protocol ID |
Protocol |
Description |
|---|---|---|
|
1 |
icmp |
Internet Control Message |
|
2 |
igmp |
Internet Group Management |
|
4 |
ip |
IP in IP (encapsulation) |
|
6 |
tcp |
Transmission Control |
|
8 |
egp |
Exterior Gateway Protocol |
|
9 |
igp |
Any private interior gateway |
|
17 |
udp |
User Datagram |
|
27 |
rdp |
Reliable Data Protocol |
|
41 |
ipv6 |
IPv6 |
|
43 |
ipv6-route |
Routing Header for IPv6 |
|
44 |
ipv6-frag |
Fragment Header for IPv6 |
|
45 |
idrp |
Inter-Domain Routing Protocol |
|
46 |
rsvp |
Reservation Protocol |
|
47 |
gre |
General Routing Encapsulation |
|
58 |
ipv6-icmp |
ICMP for IPv6 |
|
59 |
ipv6-no-nxt |
No Next Header for IPv6 |
|
60 |
ipv6-opts |
Destination Options for IPv6 |
|
80 |
iso-ip |
ISO Internet Protocol |
|
88 |
eigrp |
EIGRP |
|
89 |
ospf-igp |
OSPFIGP |
|
97 |
ether-ip |
Ethernet-within-IP Encapsulation |
|
98 |
encap |
Encapsulation Header |
|
102 |
pnni |
PNNI over IP |
|
103 |
pim |
Protocol Independent Multicast |
|
112 |
vrrp |
Virtual Router Redundancy Protocol |
|
115 |
l2tp |
Layer Two Tunneling Protocol |
|
118 |
stp |
Schedule Transfer Protocol |
|
123 |
ptp |
Performance Transparency Protocol |
|
124 |
isis |
ISIS over IPv4 |
|
126 |
crtp |
Combat Radio Transport Protocol |
|
127 |
crudp |
Combat Radio User Datagram |
|
132 |
sctp |
Stream Control Transmission Protocol |
|
137 |
mpls-in-ip |
MPLS in IP |
This command applies to IPv4 filters only.
The no form of the command removes the protocol from the match criteria.
Default
n/a
Parameters
- protocol-id
protocol-number or protocol-name
- protocol-number
the protocol number for the match criterion, expressed in decimal, hexadecimal, or binary
- protocol-name
the protocol name for the match criterion
router
Syntax
router router-instance
router service-name service-name
no router
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command configures a router name or service ID to be used as a management access filter match criterion.
The no form of the command removes the router name or service ID from the match criteria.
Parameters
- router-instance
specifies one of the following parameters for the router instance:
router-name – specifies a router name up to 32 characters to be used in the match criteria
service-id – specifies an existing service ID to be used in the match criteria
- service-name
specifies the service name of an existing service
src-ip
Syntax
src-ip {ip-prefix[/mask] [/netmask]| ip-prefix-list ip-prefix-list-name}
no src-ip
Context
config>system>security>management-access-filter>ip-filter>entry
Description
This command specifies a source IPv4 address range or specifies an IPv4 prefix list configured under the match-list command to be used as a match criterion for a management access filter. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the source IP address, specify the address and the associated mask (for example, 10.1.0.0/16). The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of the command removes the source IPv4 address or IPv4 prefix list match criterion.
Default
n/a
Parameters
- ip-prefix
the IP prefix for the IP match criterion in dotted-decimal notation
- mask
the subnet mask length expressed as a decimal integer
- netmask
the subnet mask in dotted-decimal notation
- ip-prefix-list-name
the name of the IP prefix list configured with the match-list command
src-ip
Syntax
src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
no src-ip
Context
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command configures a source IPv6 address range or specifies an IPv6 prefix list configured under the match-list command to be used as a match criterion for a management access filter. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the source IP address, specify the address and prefix length; for example, 11::12/128.
The no form of the command removes the source IP address or IPv6 prefix list match criterion.
Default
n/a
Parameters
- ipv6-address/prefix-length
the IPv6 address on the interface
- ipv6-prefix-list-name
the name of the IPv6 prefix list configured with the match-list command
src-port
Syntax
src-port {port-id | cpm | lag lag-id}
no src-port
Context
config>system>security>management-access-filter>ip-filter>entry
config>system>security>management-access-filter>ipv6-filter>entry
Description
This command restricts ingress management traffic to either the CSM Ethernet port or any other logical port (port or channel) on the device.
When the source interface is configured, only management traffic arriving on those ports satisfy the match criteria.
The no form of the command reverts to the default value.
Default
any interface
Parameters
- port-id
the port ID
- cpm
specifies that ingress management traffic is restricted to the CSM Ethernet port
- lag-id
the LAG ID
renum
Syntax
renum old-entry-number new-entry-number
Context
config>system>security>management-access-filter>ip-filter
config>system>security>management-access-filter>ipv6-filter
Description
This command renumbers existing management access filter entries to resequence filter entries.
The 7705 SAR exits on the first match found and executes the actions in accordance with the accompanying action command. This may require some entries to be renumbered from most to least explicit.
Parameters
- old-entry-number
the entry number of the existing entry
- new-entry-number
the new entry number that will replace the old entry number
CPM filter commands
cpm-filter
Syntax
[no] cpm-filter
Context
config>system>security
Description
This command enables the context to configure a CPM (referred to as CSM on the 7705 SAR) filter. A CPM filter is a hardware filter (that is, implemented on the network processor) for the CSM-destined traffic that applies to all the traffic destined for the CSM CPU. It can be used to drop or accept packets, as well as allocate dedicated hardware queues for the traffic. The hardware queues are not user-configurable.
The no form of the command disables the CPM filter.
default-action
Syntax
default-action {accept | drop}
Context
config>system>security>cpm-filter
Description
This command specifies the action to be applied to packets when the packets do not match the specified criteria in all of the IP filter entries of the filter. If there are no filter entries defined, the packets received is either accepted or dropped based on that default action.
Default
accept
Parameters
- accept
packets are accepted unless there is a specific filter entry that causes the packet to be dropped
- drop
packets are dropped unless there is a specific filter entry that causes the packet to be accepted
ip-filter
Syntax
ip-filter
Context
config>system>security>cpm-filter
Description
This command enables the context to configure IPv4 CPM filter parameters.
ipv6-filter
Syntax
ipv6-filter
Context
config>system>security>cpm-filter
Description
This command enables the context to configure IPv6 CPM filter parameters.
entry
Syntax
entry entry-id [create]
no entry entry-id
Context
config>system>security>cpm-filter>ip-filter
config>system>security>cpm-filter>ipv6-filter
Description
This command specifies a particular CPM filter match entry. Every CPM filter must have at least one filter match entry. A filter entry with no match criteria set matches every packet, and the entry action is taken.
The create keyword must be used with every new entry configured. After the entry has been created, you can navigate to the entry context without using the create keyword.
All IPv4 filter entries can specify one or more matching criteria. There are no range-based restrictions on any IPv4 filter entries.
For IPv6 filters, the combined number of fields for all entries in a filter must not exceed 16 fields (or 256 bits), where a field contains the bit representation of the matching criteria.
Parameters
- entry-id
identifies a CPM filter entry as configured on this system.
action
Syntax
action {accept | drop}
no action
Context
config>system>security>cpm-filter>ip-filter>entry
config>system>security>cpm-filter>ipv6-filter>entry
Description
This command specifies the action to take for packets that match this filter entry.
Default
drop
Parameters
- accept
packets matching the entry criteria are forwarded
- drop
packets matching the entry criteria are dropped
log
Syntax
log log-id
no log
Context
config>system>security>cpm-filter>ip-filter>entry
config>system>security>cpm-filter>ipv6-filter>entry
Description
This command specifies the log in which packets matching this entry should be entered. The value 0 indicates that logging is disabled.
The no form of the command deletes the log ID.
Parameters
- log-id
the log ID where packets matching this entry should be entered
match
Syntax
match [protocol protocol-id]
no match
Context
config>system>security>cpm-filter>ip-filter>entry
Description
This command enables the context to enter match criteria for the IPv4 filter entry. When the match criteria have been satisfied, the action associated with the match criteria is executed.
If more than one match criterion (within one match statement) is configured, all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
This command also optionally specifies the IP protocol to be used as an IP filter match criterion. See IP protocol IDs and descriptions .
The no form of the command removes the match criteria for the entry-id.
Parameters
- protocol-id
protocol-number or protocol-name
- protocol-number
the protocol number in decimal, hexadecimal, or binary, to be used as an IP filter match criterion
- protocol-name
the protocol name to be used as an IP filter match criterion
match
Syntax
match [next-header next-header]
no match
Context
config>system>security>cpm-filter>ipv6-filter>entry
Description
This command enables the context to enter match criteria for the IPv6 filter entry. When the match criteria have been satisfied, the action associated with the match criteria is executed.
If more than one match criterion (within one match statement) is configured, all criteria must be satisfied (AND function) before the action associated with the match is executed.
A match context may consist of multiple match criteria, but multiple match statements cannot be entered per entry.
This command also optionally specifies the IPv6 next header (protocol number or protocol name) to be used as an IPv6 match criterion. See IP protocol IDs and descriptions .
The no form of the command removes the match criteria for the entry-id.
Parameters
- next-header
protocol-number or protocol-name
- protocol-number
the IPv6 next header to match, expressed as a protocol number in decimal, hexadecimal, or binary. This parameter is similar to the protocol parameter used in IPv4 filter match criteria.
- protocol-name
the IPv6 next header to match, expressed as a protocol name. This parameter is similar to the protocol parameter used in IPv4 filter match criteria.
dscp
Syntax
dscp dscp-name
no dscp
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures a DiffServ Code Point (DSCP) name to be used as an IP filter match criterion.
The no form of the command removes the DSCP match criterion.
Default
no dscp
Parameters
- dscp-name
a DSCP name that has been previously mapped to a value using the dscp-name command. The DiffServ Code Point can only be specified by its name.
dst-ip
Syntax
dst-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
no dst-ip
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command configures a destination IPv4 address range or specifies an IPv4 prefix list configured under the match-list command to be used as an IP filter match criterion. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the destination IP address, specify the address and its associated mask; for example, 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of the command removes the destination IPv4 address or IPv4 prefix list match criterion.
Default
no dst-ip
Parameters
- ip-address
the IP prefix for the IP match criterion in dotted-decimal notation
- mask
the subnet mask length expressed as a decimal integer
- ipv4-address-mask
the dotted-decimal equivalent of the mask length
- prefix-list-name
the name of the IPv4 prefix list configured with the match-list command
dst-ip
Syntax
dst-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
no dst-ip
Context
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures a destination IPv6 address range or specifies an IPv6 prefix list configured under the match-list command to be used as an IP filter match criterion. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the destination IP address, specify the address and prefix length; for example, 11::12/128.
The no form of the command removes the destination IPv6 address or IPv6 prefix list match criterion.
Default
n/a
Parameters
- ipv6-address/prefix-length
the IPv6 address on the interface
- ipv6-prefix-list-name
the name of the IPv6 prefix list configured with the match-list command
dst-port
Syntax
dst-port tcp/udp port-number [mask]
no dst-port
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command specifies the TCP/UDP port to match the destination port of the packet.
The no form of the command removes the destination port match criterion.
The TCP or UDP protocol must be configured using the match command before this filter can be configured.
Parameters
- tcp/udp port-number
the destination port number to be used as a match criterion
- mask
the 16-bit mask to be applied when matching the destination port
fragment
Syntax
fragment {true | false}
no fragment
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command configures fragmented or non-fragmented IP packets as an IP filter match criterion.
The no form of the command removes the match criterion.
This command applies to IPv4 filters only.
Default
false
Parameters
- true
configures a match on all fragmented IP packets. A match occurs for all packets that have either the MF (more fragment) bit set or have the Fragment Offset field of the IP header set to a non-zero value.
- false
configures a match on all non-fragmented IP packets. Non-fragmented IP packets are packets that have the MF bit set to zero and have the Fragment Offset field also set to zero.
icmp-code
Syntax
icmp-code icmp-code
no icmp-code
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures matching on an ICMP code field in the ICMP header of an IP packet as an IP filter match criterion.
The ICMP protocol must be configured using the match command before this filter can be configured.
The no form of the command removes the criterion from the match entry.
Default
no icmp-code
Parameters
- icmp-code
icmp-code-number or icmp-code-keyword
- icmp-code-number
the ICMP code number in decimal, hexadecimal, or binary, to be used as a filter match criterion
- icmp-code-keyword
the ICMP code keyword to be used as a filter match criterion
icmp-type
Syntax
icmp-type icmp-type
no icmp-type
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures matching on an ICMP type field in the ICMP header of an IP packet as an IP filter match criterion.
The ICMP protocol must be configured using the match command before this filter can be configured.
The no form of the command removes the criterion from the match entry.
Default
no icmp-type
Parameters
- icmp-type
icmp-type-number or icmp-type-keyword
- icmp-type-number
the ICMP type number in decimal, hexadecimal, or binary, to be used as a match criterion
- icmp-type-keyword
the ICMP type keyword to be used as a match criterion
ip-option
Syntax
ip-option ip-option-value [ip-option-mask]
no ip-option
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command configures matching packets with a specific IP option or a range of IP options in the IP header as an IP filter match criterion.
The option type octet contains 3 fields:
1 bit copied flag (copy options in all fragments)
2 bits option class
5 bits option number
The no form of the command removes the match criterion.
This command applies to IPv4 filters only.
Default
no ip-option
Parameters
- ip-option-value
the 8-bit option type (can be entered using decimal, hexadecimal, or binary formats). The mask is applied as an AND to the option byte and the result is compared with the option value.
The decimal value entered for the match should be a combined value of the 8-bit option type field and not just the option number. Therefore, to match on IP packets that contain the Router Alert option (option number = 20), enter the option type of 148 (10010100).
- ip-option-mask
specifies a range of option numbers to use as the match criteria
This 8-bit mask can be entered using decimal, hexadecimal, or binary formats as shown in the following table.
Table 9. IP option formats Format style
Format syntax
Example
Decimal
DDD
20
Hexadecimal
0xHH
0x14
Binary
0bBBBBBBBB
0b0010100
multiple-option
Syntax
multiple-option {true | false}
no multiple-option
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command configures matching packets that contain more than one option field in the IP header as an IP filter match criterion.
The no form of the command removes the checking of the number of option fields in the IP header as a match criterion.
This command applies to IPv4 filters only.
Default
no multiple-option
Parameters
- true
specifies matching on IP packets that contain more than one option field in the header
- false
specifies matching on IP packets that do not contain multiple option fields in the header
option-present
Syntax
option-present {true | false}
no option-present
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command configures matching packets that contain the option field or have an option field of 0 in the IP header as an IP filter match criterion.
The no form of the command removes the checking of the option field in the IP header as a match criterion.
This command applies to IPv4 filters only.
Parameters
- true
specifies matching on all IP packets that contain the option field in the header. A match occurs for all packets that have the option field present. An option field of 0 is considered as no option present.
- false
specifies matching on IP packets that do not have any option field present in the IP header (an option field of 0)
src-ip
Syntax
src-ip {ip-address/mask | ip-address ipv4-address-mask | ip-prefix-list prefix-list-name}
no src-ip
Context
config>system>security>cpm-filter>ip-filter>entry>match
Description
This command specifies the IPv4 address or specifies an IPv4 prefix list configured under the match-list command to be used as a match criterion for an IP filter. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the source IPv4 address, specify the address and its associated mask; for example, 10.1.0.0/16. The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of the command removes the source IPv4 address or IPv4 prefix list match criterion.
Default
no src-ip
Parameters
- ip-address
the IP prefix for the IP match criterion in dotted-decimal notation
- mask
the subnet mask length expressed as a decimal integer
- ipv4-address-mask
the dotted-decimal equivalent of the mask length
- prefix-list-name
the name of the IPv4 prefix list configured with the match-list command
src-ip
Syntax
src-ip {ipv6-address/prefix-length | ipv6-prefix-list ipv6-prefix-list-name}
no src-ip
Context
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures a source IPv6 address range or specifies an IPv6 prefix list configured under the match-list command to be used as a match criterion for an IP filter. See the 7705 SAR Router Configuration Guide for information about the match-list command.
To match on the source IP address, specify the address and prefix length; for example, 11::12/128.
The no form of the command removes the source IP address match criterion.
Default
n/a
Parameters
- ipv6-address/prefix-length
the IPv6 address on the interface
- ipv6-prefix-list-name
the name of the IPv6 prefix list configured with the match-list command
src-port
Syntax
src-port tcp/udp port-number [mask]
no src-port
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command specifies the TCP/UDP port to match the source port of the packet.
Default
no src-port
Parameters
- tcp/udp port-number
the source port number to be used as a match criterion
- mask
the 16-bit mask to be applied when matching the source port
tcp-ack
Syntax
tcp-ack {true | false}
no tcp-ack
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures matching on the ACK bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion.
The no form of the command removes the criterion from the match entry.
Default
no tcp-ack
Parameters
- true
specifies matching on IP packets that have the ACK bit set in the control bits of the TCP header of an IP packet
- false
specifies matching on IP packets that do not have the ACK bit set in the control bits of the TCP header of the IP packet
tcp-syn
Syntax
tcp-syn {true | false}
no tcp-syn
Context
config>system>security>cpm-filter>ip-filter>entry>match
config>system>security>cpm-filter>ipv6-filter>entry>match
Description
This command configures matching on the SYN bit being set or reset in the control bits of the TCP header of an IP packet as an IP filter match criterion.
The SYN bit is normally set when the source of the packet wants to initiate a TCP session with the specified destination IP address.
The no form of the command removes the criterion from the match entry.
Default
no tcp-syn
Parameters
- true
specifies matching on IP packets that have the SYN bit set in the control bits of the TCP header
- false
specifies matching on IP packets that do not have the SYN bit set in the control bits of the TCP header
renum
Syntax
renum old-entry-id new-entry-id
Context
config>system>security>cpm-filter>ip-filter
config>system>security>cpm-filter>ipv6-filter
Description
This command renumbers existing IP filter entries to resequence filter entries.
Resequencing may be required in some cases because the process is exited when the first match is found and the actions are executed according to the accompanying action command. This requires that entries be sequenced correctly from most to least explicit.
Parameters
- old-entry-id
the entry number of an existing entry
- new-entry-id
the new entry number to be assigned to the old entry
Global password commands
enable-admin
Syntax
enable-admin
Context
<global>
Description
The enable-admin command is in the default profile. By default, all users have access to this command.
After the enable-admin command is entered, the user is prompted for a password. If the password matches, the user receives unrestricted access to all the commands.
There are two ways to verify that a user is in enable-admin mode:
enter the show users command – the administrator can see which users are in enable-admin mode, indicated by the "A" on the same line as that username
enter the enable-admin command again at the root prompt and an error message is returned
The # sign indicates the current session.
A:7705:Dut-C# show users
===============================================================================
Username Type
From
Router instance
Connection ID Login time
Session ID SSH Channel ID Idle time
===============================================================================
Console
--
--
6 --
6 -- 0d 00:03:20 --
-------------------------------------------------------------------------------
admin Telnet
192.168.192.37
management
8 03OCT2023 14:06:52
8 -- 0d 00:01:04 --
-------------------------------------------------------------------------------
bla Telnet
192.168.192.37
management
9 03OCT2023 14:08:42
9 -- 0d 00:00:09 A-
-------------------------------------------------------------------------------
admin SSHv2
192.168.192.37
management
7 03OCT2023 14:06:24
#7 0 0d 00:00:00 --
-------------------------------------------------------------------------------
Number of users: 3
Number of sessions: 3
'#' indicates the current active session
'A' indicates user is in admin mode
===============================================================================
*A:7705:Dut-C#
Password commands
password
Syntax
password
Context
config>system>security
Description
This command enables the context to configure password management parameters.
admin-password
Syntax
admin-password password [hash | hash2]
no admin-password
Context
config>system>security>password
Description
This command allows a user (with admin permissions) to configure a password which enables a user to become an administrator for one session. When enabled, no authorization to TACACS+ or RADIUS is performed and the user is locally regarded as an admin user.
The minimum length of the password is determined by the minimum-length command. The complexity requirements for the password are determined by the complexity command.
For example:
file copy ftp://test:secret@192.0.2.0/test/srcfile cf3:\destfile
In this example, the username ‟test” and password ‟secret” are not sent to the AAA servers (or to any logs). They are replaced with ‟****”.
The no form of the command removes the admin password from the configuration.
Default
no admin-password
Parameters
- password
configures the password that enables a user to become a system administrator. The maximum length is as follows:
56 characters if in unhashed plaintext
The unhashed plaintext form must meet all the requirements that are defined within the complexity-rules command context.
60 characters if hashed with bcrypt
from 87 to 92 characters if hashed with PBKDF2 SHA-2
from 131 to 136 characters if hashed with PBKDF2 SHA-3
32 characters if the hash keyword is specified
54 characters if the hash2 keyword is specified
- hash
specifies that the key is entered and stored on the node in encrypted form
- hash2
specifies that the key is entered and stored on the node in a more complex encrypted form
Note: If neither the hash nor hash2 keyword is specified, the key is entered in clear text. However, for security purposes, the key is stored on the node using bcrypt or PBKDF2 hash encryption.
aging
Syntax
aging days
no aging
Context
config>system>security>password
Description
This command configures the number of days a user password is valid before the user must change their password.
The no form of the command reverts to the default value.
Default
no aging is enforced
Parameters
- days
the maximum number of days the password is valid
attempts
Syntax
attempts count [time minutes1] [lockout minutes2]
no attempts
Context
config>system>security>password
Description
This command configures a threshold value of unsuccessful login attempts allowed in a specified time frame.
If the threshold is exceeded, the user is locked out for a specified time period.
If multiple attempts commands are entered, each command overwrites the previously entered command.
The no attempts command resets all values to the default.
Default
count: 3 minutes1: 5 minutes2: 10
Parameters
- count
the number of unsuccessful login attempts allowed for the specified time. This is a mandatory value that must be explicitly entered.
- minutes1
the period of time, in minutes, that a specified number of unsuccessful attempts can be made before the user is locked out
- minutes2
the lockout period, in minutes, where the user is not allowed to log in
authentication-order
Syntax
authentication-order [method-1] [method-2] [method-3] [exit-on-reject]
no authentication-order
Context
config>system>security>password
Description
This command configures the sequence in which password authentication and authorization is attempted among RADIUS, TACACS+, and local servers.
The order should be from the most preferred authentication method to the least preferred. The presence of all methods in the command line does not guarantee that they are all operational. Specifying options that are not available delays user authentication.
If all (operational) methods are attempted and no authentication for a particular login has been granted, then an entry in the security log registers the failed attempt. Both the attempted login identification and originating IP address are logged with a timestamp.
The no form of the command reverts to the default authentication sequence.
Default
authentication-order radius tacplus local
Parameters
- method-1
the first password authentication method to attempt
- method-2
the second password authentication method to attempt
- method-3
the third password authentication method to attempt
- radius
RADIUS authentication
- tacplus
TACACS+ authentication
- local
password authentication based on the local password database
- exit-on-reject
when enabled, and if one of the AAA methods configured in the authentication order sends a reject, then the next method in the order are not tried. If the exit-on-reject keyword is not specified and one AAA method sends a reject, the next AAA method is attempted. If in this process all the AAA methods are exhausted, it is considered a reject.
A rejection is distinct from an unreachable authentication server. When the exit-on-reject keyword is specified, authorization and accounting only use the method that provided an affirmation authentication; only if that method is no longer readable or is removed from the configuration other configured methods are attempted. If the local keyword is the first authentication and:
exit-on-reject is configured and the user does not exist, the user is not authenticated
the user is authenticated locally, then other methods, if configured, is used for authorization and accounting
the user is configured locally but without console access, login is denied
complexity-rules
Syntax
complexity-rules
Context
config>system>security>password
Description
This command enables the context to configure security password complexity rules.
allow-user-name
Syntax
[no] allow-user-name
Context
config>system>security>password>complexity-rules
Description
This command allows a login name to be included as part of the password.
The no form of this command prevents a login name from being included as part of the password.
credits
Syntax
credits [lowercase credits] [uppercase credits] [numeric credits] [special-character credits]
no credits
Context
config>system>security>password>complexity-rules
Description
This command configures a credit value for each of the different character classes in a local password. When a password is created, credits are assigned for each character in a character class, up to the assigned credits limit. The credits each count as one additional character toward the minimum length of the password. This allows a trade-off between a very long, simple password and a short, complex one.
For example, if the password minimum length is seven and lowercase credits is set to 3, a password with four lowercase letters, such as ‟srty”, is accepted. The first three lowercase letters are each given a credit worth one extra character. Combined with the four characters in the password, the total reaches the minimum length. If lowercase credits is set to 2 instead of 3, only the first two lowercase letters are given credit. In this case, the ‟srty” password is worth only six characters (four characters plus two extra characters from credits) and would fail to reach the seven character minimum length.
The no form of this command removes all credit values.
Default
no credits
Parameters
- credits
the number of credits allowed for each character class
disallow-sequence-keys
Syntax
disallow-sequence-keys value
no disallow-sequence-keys
Context
config>system>security>password>complexity-rules
Description
This command configures the number of consecutive characters that are not allowed to be entered as part of the password on a U.S. English or Korean keyboard. These characters can be lowercase or uppercase letters, or numbers. Special characters are not taken into account. These consecutive characters can be horizontal (left to right or right to left), diagonal (top to bottom or bottom to top), or wrapped (for example, "dsalkj" is a sequence of 6 characters). If the number of consecutive characters is equal to or larger than the configured value, the password is disallowed.
For example, if the user attempts to use the password "dsalkjhgfdsa" with this command configured to 8 (meaning any sequence of 8 or more characters fails), the system rejects the password because the substring “lkjhgfdsa” is a sequence of 9 letters and therefore does not pass the check. If the user attempts to use the password “9lkjhgfd5c”, the system accepts the password because the substring “lkjhgfd” is a sequence of 7 characters, which passes the check.
The no form of this command removes the restriction on the number of characters.
Default
no disallow-sequence-keys
Parameters
- value
- specifies the number of disallowed sequential characters in the password
minimum-classes
Syntax
minimum-classes minimum
no minimum-classes
Context
config>system>security>password>complexity-rules
Description
This command enforces a minimum number of different character classes to be used in the password. The possible character classes are lowercase letters, uppercase letters, numbers, and special characters.
The no form of this command removes the minimum character class requirement.
Default
no minimum-classes
Parameters
- minimum
the minimum number of character classes required in a password
minimum-length
Syntax
minimum-length value
no minimum-length
Context
config>system>security>password>complexity-rules
Description
This command configures the minimum number of characters required for passwords.
If multiple minimum-length commands are entered, each command overwrites the previously entered command.
The no form of the command reverts to the default value.
Default
6
Parameters
- value
the minimum number of characters required for a password
repeated-characters
Syntax
repeated-characters count
no repeated-characters
Context
config>system>security>password>complexity-rules
Description
This command configures the maximum number of times a character can be repeated consecutively in a password.
The no form of the command resets to the default value, which removes the restriction on repeated characters in passwords.
Default
no repeated-characters
Parameters
- count
the maximum number of consecutive repeated characters allowed in the password
required
Syntax
required [lowercase count] [uppercase count] [numeric count] [special-character count]
no required
Context
config>system>security>password>complexity-rules
Description
This command configures the minimum number of characters from each character class that are required for a password to be valid.
The no form of the command removes the minimum required characters from each character class.
Default
no required
Parameters
- count
the minimum number of characters required from the character class
hashing
Syntax
hashing {bcrypt | sha2-pbkdf2 | sha3-pbkdf2}
Context
config>system>security>password
Description
This command configures the password hashing algorithm.
Default
bcrypt
Parameters
- bcrypt
sets the password hashing algorithm to bcrypt
- sha2-pbkdf2
sets the password hashing algorithm to PBKDF2 with SHA-2 hashing
- sha3-pbkdf2
sets the password hashing algorithm to PBKDF2 with SHA-3 hashing
health-check
Syntax
[no] health-check [interval interval]
Context
config>system>security>password
Description
This command specifies that RADIUS and TACACS+ servers are monitored for 3 s each during every polling interval. Servers that are not configured have 3 s of idle time. If a server is found to be unreachable, or a previously unreachable server starts responding, depending on the type of server, a trap is sent.
The no form of the command disables the periodic monitoring of the RADIUS and TACACS+ servers. In this case, the operational status for the active server is up if the last access was successful.
Default
30
Parameters
- interval
the polling interval for RADIUS and TACACS+ servers, in seconds
history-size
Syntax
history-size size
no history-size
Context
config>system>security>password
Description
This command configures the number of previous passwords to save in the system. A new password is matched against every old password and is rejected if it is identical to a password in the history.
The no form of the command prevents password history matching.
Default
no history-size
Parameters
- size
specifies how many previous passwords are stored in the history
minimum-age
Syntax
minimum-age [days days] [hrs hours] [min minutes] [sec seconds]
no minimum-age
Context
config>system>security>password
Description
This command configures the minimum required age of a password before it can be changed again.
The no form of this command removes the minimum password age requirement.
Default
no minimum-age
Parameters
- days
the minimum number of days before a password can be changed again
- hours
the minimum number of hours before a password can be changed again
- minutes
the minimum number of minutes before a password can be changed again
- seconds
the minimum number of seconds before a password can be changed again
minimum-change
Syntax
minimum-change length
no minimum-change
Context
config>system>security>password
Description
This command configures the minimum number of characters in a new password that must be unique from the previous password.
The no form of the command removes the unique character requirement.
Default
no minimum-change
Parameters
- length
the minimum number of characters in a new password that must be unique from a previous password
Profile management commands
profile
Syntax
[no] profile user-profile-name
Context
config>system>security
Description
This command creates a context to create user profiles for CLI command tree permissions.
Profiles are used to either deny or allow user console access to a hierarchical branch or to specific commands.
After the profiles are created, the user command assigns users to one or more profiles. You can define up to 16 user profiles, but a maximum of 8 profiles can be assigned to a user.
The no form of the command deletes a user profile.
Default
user-profile default
Parameters
- user-profile-name
the user profile name entered as a character string. The string is case-sensitive and limited to 32 ASCII 7-bit printable characters with no spaces.
default-action
Syntax
default-action {deny-all | permit-all | none}
Context
config>system>security>profile
Description
This command specifies the default action to be applied when no match conditions are met.
Default
none
Parameters
- deny-all
sets the default of the profile to deny access to all commands
- permit-all
sets the default of the profile to allow access to all commands
Note: The permit-all parameter does not change access to security commands. Security commands are only and always available to members of the admin-user profile.
- none
sets the default of the profile to no-action. This option is useful to assign multiple profiles to a user.
For example, if a user is a member of two profiles and the default action of the first profile is permit-all, then the second profile will never be evaluated because permit-all is executed first. If the first profile default action is set to none and if no match conditions are met in the first profile, then the second profile will be evaluated. If the default action of the last profile is none and no explicit match is found, then the default-action deny-all takes effect.
entry
Syntax
[no] entry entry-id
Context
config>system>security>profile
Description
This command is used to create a user profile entry.
More than one entry can be created with unique entry-id numbers. The 7705 SAR exits when the first match is found and executes the actions according to the accompanying action command. Entries should be sequenced from most explicit to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action for it to be considered complete.
The no form of the command removes the specified entry from the user profile.
Default
no entry IDs are defined
Parameters
- entry-id
an entry ID uniquely identifies a user profile command match criteria and a corresponding action. If more than one entry is configured, the entry-ids should be numbered in staggered increments to allow users to insert a new entry without requiring renumbering of the existing entries.
action
Syntax
action {deny | permit}
Context
config>system>security>profile>entry
Description
This command configures the action associated with the profile entry.
Parameters
- deny
specifies that commands matching the entry command match criteria will be denied
- permit
specifies that commands matching the entry command match criteria will be permitted
match
Syntax
match command-string
no match
Context
config>system>security>profile>entry
Description
This command configures a command or command subtree.
Because the 7705 SAR exits when the first match is found, subordinate levels cannot be modified with subsequent action commands. More specific action commands should be entered with a lower entry number or in a profile that is evaluated prior to this profile.
All commands below the hierarchy level of the matched command are denied.
The no form of this command removes a match condition.
Default
no match command string is specified
Parameters
- command-string
the CLI command or CLI tree level that is the scope of the profile entry
renum
Syntax
renum old-entry-number new-entry-number
Context
config>system>security>profile
Description
This command renumbers profile entries to resequence the entries.
Because the 7705 SAR exits when the first match is found and executes the actions according to the accompanying action command, renumbering is useful to rearrange the entries from most explicit to least explicit.
Parameters
- old-entry-number
the entry number of an existing entry
- new-entry-number
the new entry number
User management commands
user
Syntax
[no] user user-name
Context
config>system>security
Description
This command creates a local user and a context to edit the user configuration.
If a new user-name is entered, the user is created. When an existing user-name is specified, the user parameters can be edited.
When a new user is created and the info command is entered, the system displays a password with hash2 encryption in the output screen. However, when using that username, there is no password required. The user can log in to the system by entering their username and then pressing ↵ at the password prompt.
Unless an administrator explicitly changes the password, it is null. The hashed value displayed uses the username and null password field, so when the username is changed, the displayed hashed value changes.
The no form of the command deletes the user and all configuration data. Users cannot delete themselves.
Default
n/a
Parameters
- user-name
the name of the user, up to 32 characters
user-template
Syntax
user-template {tacplus_default | radius_default}
Context
config>system>security
Description
This command configures default security user template parameters.
Parameters
- tacplus_default
specifies that the TACACS+ default template is used for the configuration
- radius_default
specifies that the RADIUS default template is used for the configuration
access
Syntax
[no] access [ftp] [snmp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli]
[no] access [ftp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli]
Context
config>system>security>user
config>system>security>user-template
Description
This command specifies user permissions for one or more methods of management access.
If a user requires access to more than one method, multiple methods can be specified in a single command. Multiple commands are treated sequentially.
The no form of the command removes access for a specific method.
The no access command denies permission for all management access methods. To deny a single access method, enter the no form of the command followed by the method to be denied; for example, no access ftp denies FTP access.
Default
no access
Parameters
- ftp
specifies FTP access permission
- snmp
specifies SNMP access permission. This keyword is only configurable in the config>system>security>user context.
- console
-
specifies SCP/SFTP, Telnet, SSH, and console port CLI access permissions
- scp-sftp
specifies SCP/SFTP access permissions
- console-port-cli
-
specifies console port CLI access permission
- ssh-cli
-
specifies SSH CLI access permission
- telnet-cli
-
specifies Telnet CLI access permission
console
Syntax
console
Context
config>system>security>user
config>system>security>user-template
Description
This command enables the context to configure user profile membership for the console.
cannot-change-password
Syntax
[no] cannot-change-password
Context
config>system>security>user>console
Description
This command allows a user to change their password for both FTP and console login.
To disable a user’s privilege to change their password, use the cannot-change-password form of the command.
The cannot-change-password flag is not replicated when a user copy is performed. A new-password-at-login flag is created instead.
Default
no cannot-change-password
local-lockout
Syntax
[no] local-lockout
Context
config>system>security>user>console
Description
This command prevents console or local serial access if a user is locked out remotely.
The no version of this command allows locked-out users to log in only for console or local serial access.
Default
local-lockout
login-exec
Syntax
[no] login-exec url-prefix:source-url
Context
config>system>security>user>console
config>system>security>user-template>console
Description
This command configures a user’s login exec file, which executes whenever the user successfully logs in to a console session.
Only one exec file can be configured. If multiple login-exec commands are entered for the same user, each subsequent entry overwrites the previous entry.
The no form of the command disables the login exec file for the user.
Default
no login exec file is defined
Parameters
- url-prefix: source-url
enter either a local or remote URL, up to 200 characters in length, that identifies the exec file that is executed after the user successfully logs in
member
Syntax
member user-profile-name [user-profile-name…]
no member user-profile-name
Context
config>system>security>user>console
Description
This command allows the user access to a profile.
A user can participate in up to eight profiles.
The no form of this command deletes access user access to a profile.
Default
default
Parameters
- user-profile-name
the user profile name
new-password-at-login
Syntax
[no] new-password-at-login
Context
config>system>security>user>console
Description
This command forces the user to change passwords at the next console or FTP login.
If the user is limited to FTP access, the administrator must create the new password.
The no form of the command does not force the user to change passwords.
Default
no new-password-at-login
home-directory
Syntax
home-directory url-prefix [directory] [directory/directory…]
no home-directory
Context
config>system>security>user
config>system>security>user-template
Description
This command configures the local home directory for the user for file access. Files on the 7705 SAR can be accessed locally using the CLI file commands and output modifiers, such as > (file redirect), or remotely via FTP or SCP.
If the URL or the specified URL/directory structure is not present, a warning message is issued and the default is assumed.
The no form of the command removes the configured home directory.
Default
no home-directory
Parameters
- url-prefix [directory] [directory/directory…]
the user’s local home directory URL prefix and directory structure, up to 190 characters in length
password
Syntax
password [password]
Context
config>system>security>user
Description
This command configures the user password for console and FTP access.
Passwords must be enclosed in double quotes (‟ ”) at the time of password creation if they contain any special characters (such as #, $, or spaces). The double quote character (‟) is not accepted inside a password. It is interpreted as the start or stop delimiter of a string.
The question mark character (?) cannot be directly inserted as input during a Telnet connection because the character is bound to the help command during a normal Telnet/console connection. To insert # or ? characters, they must be entered inside a notepad or clipboard program and then cut and pasted into the Telnet session in the password field that is encased in double quotes as delimiters for the password.
If a password is entered without any parameters, a password length of zero is implied (return key).
The password is stored in an encrypted format in the configuration file when specified.
Parameters
- password
the password that must be entered by this user during the login procedure. The minimum length of the password is determined by the minimum-length command. The maximum length is as follows:
56 characters if in unhashed plaintext
The unhashed plaintext form must meet all the requirements that are defined within the complexity-rules command context.
60 characters if hashed with bcrypt
from 87 to 92 characters if hashed with PBKDF2 SHA-2
from 131 to 136 characters if hashed with PBKDF2 SHA-3
profile
Syntax
profile user-profile-name
no profile
Context
config>system>security>user-template
Description
This command specifies the user profile to associate with the user template. The profile must already be configured with the profile command under the config>system>security context.
The no form of this command removes the profile.
Default
profile "default"
Parameters
- user-profile-name
-
an existing user profile name
public-keys
Syntax
public-keys
Context
config>system>security>user
Description
This command enables the context to configure public keys for SSH.
ecdsa
Syntax
ecdsa
Context
config>system>security>user>public-keys
Description
This command enables the context to configure ECDSA public keys.
ecdsa-key
Syntax
ecdsa-key key-id [create]
no ecdsa-key key-id
Context
config>system>security>user>public-keys>ecdsa
Description
This command creates an ECDSA public key and associates it with the specified user. Multiple public keys can be associated with the user. The key ID is used to identify these keys for the user.
Default
n/a
Parameters
- key-id
the key identifier
- create
keyword required when first creating the ECDSA key. When the key is created, you can navigate into the context without the create keyword.
key-value
Syntax
key-value public-key-value
no key-value
Context
config>system>security>user>public-keys>ecdsa>ecdsa-key
config>system>security>user>public-keys>rsa>rsa-key
Description
This command configures a value for the ECDSA or RSA public key. The public key must be enclosed in quotation marks. For ECDSA, the key is between 1 and 1024 bits. For RSA, the key is between 768 and 4096 bits.
Default
no key-value
Parameters
- public-key-value
the value for the ECDSA or RSA key
rsa
Syntax
rsa
Context
config>system>security>user>public-keys
Description
This command enables the context to configure RSA public keys.
rsa-key
Syntax
rsa-key key-id [create]
no rsa-key key-id
Context
config>system>security>user>public-keys>rsa
Description
This command creates an RSA public key and associates it with the specified user. Multiple public keys can be associated with the user. The key ID is used to identify these keys for the user.
Parameters
- key-id
the key identifier
- create
keyword required when first creating the RSA key. When the key is created, you can navigate into the context without the create keyword.
restricted-to-home
Syntax
[no] restricted-to-home
Context
config>system>security>user
config>system>security>user-template
Description
This command prevents users from navigating above their home directories for file access. A user is not allowed to navigate to a directory higher in the directory tree on the home directory device. The user is allowed to create and access subdirectories below their home directory.
If a home directory is not configured or the home directory is not available, the user has no file access.
The no form of the command allows the user access to navigate to directories above their home directory.
Default
restricted-to-home
save-when-restricted
Syntax
[no] save-when-restricted
Context
config>system>security>user
config>system>security>user-template
Description
This command specifies whether the system allows all configuration save operations (for example, admin save) via the CLI even if restricted-to-home is enabled.
The home directory does not need to be configured.
The no form of the command prevents the user from performing any configuration save operations outside of their home directory when restricted-to-home is enabled.
Default
save-when-restricted
snmp
Syntax
snmp
Context
config>system>security>user
Description
This command enables the context to configure SNMP group membership for a specific user and defines encryption and authentication parameters.
All SNMPv3 users must be configured with the commands available in this CLI context.
The 7705 SAR always uses the configured SNMPv3 username as the security username.
authentication
Syntax
authentication none
authentication authentication-protocol authentication-key [privacy none] [hash | hash2]
authentication authentication-protocol authentication-key privacy privacy-protocol privacy-key [hash | hash2]
no authentication
Context
config>system>security>user>snmp
Description
This command configures the SNMPv3 authentication and privacy protocols for the user to communicate with the router. The keys are stored in an encrypted format in the configuration.
The keys configured with these commands must be localized keys, which are a hash of the SNMP engine ID and a password. The password is not entered directly in this command. Use the generate-key command under the tools>perform>system>management-interface >snmp context to generate localized authentication and privacy keys. See the 7705 SAR OAM and Diagnostics Guide, ‟Tools perform commands” for information about this command.
If authentication none is configured, only the username is required to allow and authenticate SNMPv3 operations.
The no form of the command prevents the username used to configure the command from getting recognized by SNMP, and the same user cannot be used for any SNMP operations.
Default
authentication none – no authentication protocol is configured and privacy cannot be configured
Parameters
- none
specifies that no authentication protocol is used
- authentication-protocol authentication-key
specifies the SNMPv3 authentication protocol and localized authentication key
- privacy-protocol privacy-key
specifies the SNMPv3 privacy protocol and localized privacy key
- privacy none
specifies that a privacy protocol is not used in the communication
- hash
specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
group
Syntax
group group-name
no group
Context
config>system>security>user>snmp
Description
This command associates (or links) a user to a group name. The access command links the group with one or more views, security models, security levels, and read, write, and notify permissions.
Default
no group name is associated with a user
Parameters
- group-name
enter the group name (between 1 and 32 alphanumeric characters) that is associated with this user. A user can be associated with one group name per security model.
CLI script authorization commands
cli-script
Syntax
cli-script
Context
config>system>security
Description
This command enables the context to configure CLI script security.
authorization
Syntax
authorization
Context
config>system>security>cli-script
Description
This command enables the context to authorize CLI script execution for CRON and Event Handling System (EHS) scripts.
cron
Syntax
cron
Context
config>system>security>cli-script>authorization
Description
This command enables the context to configure authorization for the CRON scheduler.
cli-user
Syntax
cli-user user-name
no cli-user
Context
config>system>security>cli-script>authorization>cron
config>system>security>cli-script>authorization>event-handler
Description
This command defines the user context under which CRON and EHS CLI scripts must execute in order to authorize the script commands. The user must be a local user; TACACS+ and RADIUS users and authorization are not permitted for cli-script authorization.
Two unique users can be defined: one to authorize CLI commands for CRON scripts and one to authorize CLI commands for EHS scripts.
The no form of this command configures scripts to execute with no restrictions and without performing authorization.
Default
no cli-user
Parameters
- user-name
the name of a user in the local node database. TACACS+ or RADIUS users cannot be used. The user configuration must reference a valid local profile for authorization.
event-handler
Syntax
event-handler
Context
config>system>security>cli-script>authorization
Description
This command enables the context to configure authorization for EHS. EHS is a tool that enables operator-defined behavior to be configured on the 7705 SAR. The operator can define a CLI script that the router executes in response to a log event.
RADIUS client commands
radius
Syntax
[no] radius
Context
config>system>security
Description
This command enables the context to configure RADIUS authentication on the 7705 SAR.
For redundancy, multiple server addresses can be configured for each 7705 SAR.
The no form of the command removes the RADIUS configuration.
access-algorithm
Syntax
access-algorithm {direct | round-robin}
[no] access-algorithm
Context
config>system>security>radius
Description
This command configures the algorithm used to access the set of RADIUS servers. Up to five servers can be configured.
In direct mode, the first server, as defined by the server command, is the primary server. This server is always used first when authenticating a request. In round-robin mode, the server used to authenticate a request is the next server in the list, following the last authentication request. For example, if server 1 is used to authenticate the first request, server 2 is used to authenticate the second request, and so on.
Default
direct
Parameters
- direct
first server is always used to authenticate a request
- round-robin
server used to authenticate a request is the next server in the list, following the last authentication request
accounting
Syntax
[no] accounting
Context
config>system>security>radius
Description
This command enables RADIUS accounting. The no form of this command disables RADIUS accounting.
Default
no accounting
accounting-port
Syntax
accounting-port port
no accounting-port
Context
config>system>security>radius
Description
This command specifies a UDP port number on which to contact the RADIUS server for accounting requests.
Parameters
- port
specifies the UDP port number
authorization
Syntax
[no] authorization
Context
config>system>security>radius
Description
This command configures RADIUS authorization parameters for the system.
The no form of this command disables RADIUS authorization for the system.
Default
no authorization
port
Syntax
port port
no port
Context
config>system>security>radius
Description
This command configures the TCP port number to contact the RADIUS server.
The no form of the command reverts to the default value.
Default
1812 (as specified in RFC 2865, Remote Authentication Dial In User Service (RADIUS))
Parameters
- port
the TCP port number to contact the RADIUS server
retry
Syntax
retry count
no retry
Context
config>system>security>radius
Description
This command configures the number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server.
The no form of the command reverts to the default value.
Default
3
Parameters
- count
the retry count
server
Syntax
server server-index address ip-address secret key [hash | hash2]
no server server-index
Context
config>system>security>radius
Description
This command adds a RADIUS server and configures the RADIUS server IP address, index, and key values.
Up to five RADIUS servers can be configured at any one time. RADIUS servers are accessed in order from lowest to highest index for authentication requests until a response from a server is received. A higher-indexed server is only queried if no response is received from a lower-indexed server (which implies that the server is not available). If a response from a server is received, no other RADIUS servers are queried. It is assumed that there are multiple identical servers configured as backups and that the servers do not have redundant data.
The no form of the command removes the server from the configuration.
Default
no RADIUS servers are configured
Parameters
- index
the index for the RADIUS server. The index determines the sequence in which the servers are queried for authentication requests. Servers are queried in order from lowest to highest index.
- ip-address
the IP address of the RADIUS server. Two RADIUS servers cannot have the same IP address. An error message is generated if the server address is a duplicate.
- key
the secret key to access the RADIUS server. This secret key must match the password on the RADIUS server.
- hash
specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security>radius
Description
This command configures the number of seconds the router waits for a response from a RADIUS server.
The no form of the command reverts to the default value.
Default
3
Parameters
- seconds
the number of seconds the router waits for a response from a RADIUS server, expressed as a decimal integer
use-default-template
Syntax
[no] use-default-template
Context
config>system>security>radius
Description
This command specifies whether the user template defined by this entry is to be actively applied to the RADIUS user.
Default
no use-default-template
TACACS+ client commands
tacplus
Syntax
[no] tacplus
Context
config>system>security
Description
This command enables the context to configure TACACS+ authentication on the 7705 SAR.
For redundancy, multiple server addresses can be configured for each 7705 SAR.
The no form of the command removes the TACACS+ configuration.
accounting
Syntax
accounting [record-type {start-stop | stop-only}]
no accounting
Context
config>system>security>tacplus
Description
This command enables TACACS+ accounting and configures the type of accounting record packet that is to be sent to the TACACS+ server. The record-type parameter indicates whether TACACS+ accounting start and stop packets will be sent or just stop packets will be sent.
Default
record-type stop-only
Parameters
- record-type start-stop
specifies that a TACACS+ start packet is sent whenever the user executes a command and a stop packet is sent when the command is complete
- record-type stop-only
specifies that a stop packet is sent when the command execution is complete
authorization
Syntax
[no] authorization
Context
config>system>security>tacplus
Description
This command configures TACACS+ authorization parameters for the system.
Default
no authorization
server
Syntax
server index address ip-address secret key [hash | hash2] [port port]
no server index
Context
config>system>security>tacplus
Description
This command adds a TACACS+ server and configures the TACACS+ server IP address, index, and key values.
Up to five TACACS+ servers can be configured at any one time. TACACS+ servers are accessed in order from the lowest index to the highest index for authentication requests.
The no form of the command removes the server from the configuration.
Default
no TACACS+ servers are configured
Parameters
- index
the index for the TACACS+ server. The index determines the sequence in which the servers are queried for authentication requests. Servers are queried in order from the lowest index to the highest index.
- ip-address
the IP address of the TACACS+ server. Two TACACS+ servers cannot have the same IP address. An error message is generated if the server address is a duplicate.
- key
the secret key to access the RADIUS server. This secret key must match the password on the TACACS+ server.
- hash
specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
- port
the port ID
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security>tacplus
Description
This command configures the number of seconds the router waits for a response from a TACACS+ server.
The no form of the command reverts to the default value.
Default
3
Parameters
- seconds
the number of seconds the router waits for a response from a TACACS+ server, expressed as a decimal integer
use-default-template
Syntax
[no] use-default-template
Context
config>system>security>tacplus
Description
This command specifies whether the user template defined by this entry is to be actively applied to the TACACS+ user.
802.1x commands
dot1x
Syntax
[no] dot1x
Context
config>system>security
Description
This command enables the context to configure 802.1x network access control on the 7705 SAR.
The no form of the command removes the 802.1x configuration.
radius-plcy
Syntax
[no] radius-plcy name [create]
Context
config>system>security>dot1x
Description
This command enables the context to configure RADIUS server parameters for 802.1x network access control on the 7705 SAR.
The RADIUS server configured under the config>system>security>dot1x>radius-plcy context authenticates clients who get access to the data plane of the 7705 SAR. This configuration differs from the RADIUS server configured under the config>system>security>radius context that authenticates CLI login users who get access to the management plane of the 7705 SAR.
The no form of the command removes the RADIUS server configuration for 802.1x.
Parameters
- name
the RADIUS policy name, up to 32 characters
- create
keyword required when first creating the configuration context. When the context is created, you can navigate into the context without the create keyword.
retry
Syntax
retry count
no retry
Context
config>system>security>dot1x
Description
This command configures the number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server.
The no form of the command reverts to the default value.
Default
3
Parameters
- count
the retry count
server
Syntax
server server-index address ip-address secret key [hash | hash2] [auth-port auth-port]
[acct-port acct-port] [type server-type]
no server server-index
Context
config>system>security>dot1x>radius-plcy
Description
This command adds an 802.1x server and configures the IP address, index, and key values.
Up to five 802.1x servers can be configured at any one time. These servers are accessed in order from lowest to highest index for authentication requests until a response from a server is received. A higher- indexed server is only queried if no response is received from a lower-indexed server (which implies that the server is not available). If a response from a server is received, no other 802.1x servers are queried. It is assumed that there are multiple identical servers configured as backups and that the servers do not have redundant data.
The no form of the command removes the server from the configuration.
Default
n/a
Parameters
- server-index
the index for the 802.1x server
- ip-address
the IP address of the 802.1x server. Each 802.1x server must have a unique IP address. An error message is generated if the server address is a duplicate.
- key
the secret key to access the 802.1x server. This secret key must match the password on the 802.1x server.
- hash
specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
specifies that the key is entered in a more complex encrypted form that involves more variables than the key value alone. This means that the hash2 encrypted variable cannot be copied and pasted. If the hash or hash2 parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- auth-port
the UDP port number used to contact the RADIUS server for authentication
- acct-port
the UDP port number used to contact the RADIUS server for accounting requests
- server-type
the server type
source-address
Syntax
source-address ip-address
no source-address
Context
config>system>security>dot1x>radius-plcy
Description
This command configures the NAS IP address to be sent in the RADIUS packet.
The no form of the command reverts to the default value.
Default
system IP address
Parameters
- ip-address
the source address of the RADIUS packet in dotted-decimal notation
shutdown
Syntax
[no] shutdown
Context
config>system>security>dot1x
config>system>security>dot1x>radius-plcy
Description
This command administratively disables the 802.1x protocol operation. Shutting down the protocol does not remove or change the configuration other than the administrative state.
The operational state of the entity is disabled as well as the operational state of any entities contained within.
The no form of the command administratively enables the protocol.
Default
shutdown
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security>dot1x>radius-plcy
Description
This command configures the number of seconds the router waits for a response from a RADIUS server.
The no form of the command reverts to the default value.
Default
5
Parameters
- seconds
the number of seconds the router waits for a response from a RADIUS server, expressed as a decimal integer
SSH commands
ssh
Syntax
ssh
Context
config>system>security
Description
This command enables the context to configure the SSH server parameters on the system.
Quitting SSH while in the process of authentication is accomplished by either executing a ctrl-c or ‟~.” (tilde and dot), assuming the ‟~” is the default escape character for the SSH session.
Default
n/a
client-cipher-list
Syntax
client-cipher-list
Context
config>system>security>ssh
Description
This command enables the context to configure the list of allowed ciphers on the SSH client.
Default
n/a
cipher
Syntax
cipher index name cipher-name
no cipher index
Context
config>system>security>ssh>client-cipher-list
config>system>security>ssh>server-cipher-list
Description
This command configures the allowed SSHv2 ciphers that are available on the SSH client or server. Client cipher and server cipher lists are used to negotiate the best compatible cipher between the SSH client and SSH server. Client ciphers are used when the 7705 SAR node is acting as an SSH client; server ciphers are used when the 7705 SAR node is acting as an SSH server.
Each list contains ciphers and their corresponding index values, where a lower index has a higher preference in the SSH negotiation. The list is ordered by preference from highest to lowest.
The following table lists the default index values used for SSHv2, in order of preference.
|
Cipher index value |
Cipher name |
|---|---|
|
2 |
aes256-ctr |
|
4 |
aes192-ctr |
|
6 |
aes128-ctr |
|
10 |
aes128-cbc |
|
20 |
3des-cbc |
|
60 |
aes192-cbc |
|
70 |
aes256-cbc |
The no form of this command deletes the specified cipher index.
Default
n/a
Parameters
- index
the index of the cipher in the list
- cipher-name
the allowed cipher name
client-kex-list
Syntax
client-kex-list
Context
config>system>security>ssh
Description
This command enables the context to configure a list of preferred KEX algorithms to be used by an SSHv2 client.
Default
n/a
kex
Syntax
kex index name kex-name
no kex index
Context
config>system>security>ssh>client-kex-list
config>system>security>ssh>server-kex-list
Description
This command configures the list of preferred KEX algorithms that are negotiated by the client and server using an SSHv2 phase one handshake.
By default, a KEX client and KEX server each have a hard-coded list that contains the default indexes and their corresponding algorithms. The following table lists the default index values and algorithms, in order of preference.
KEX index value |
KEX algorithm name |
|---|---|
200 |
diffie-hellman-group16-sha512 |
210 |
diffie-hellman-group14-sha256 |
215 |
diffie-hellman-group14-sha1 |
220 |
diffie-hellman-group-exchange-sha1 |
225 |
diffie-hellman-group1-sha1 |
The default list can be changed by manually removing a single index or as many indexes as required using the no kex index command. The default list can also be customized by first removing an index and then redefining it for each algorithm as required. To go back to using the original hard-coded list, the default KEX indexes must be manually re-entered with their corresponding algorithms.
In a KEX list, the algorithm with the lowest index value has the highest preference in the SSH negotiation. The list is ordered by preference from highest to lowest. When the client and server exchange their KEX lists, the first algorithm in the client list that is also supported by the server is the algorithm that is agreed upon.
The no form of this command removes the specified KEX index. Removing all the indexes from a client or server list results in an empty list, and any KEX algorithm the client or server brings to the SSHv2 negotiation will be rejected.
Default
no kex
Parameters
- index
the index of the KEX algorithm in the list. The list is ordered from highest to lowest.
- kex-name
the KEX algorithm for computing the shared secret key
client-mac-list
Syntax
client-mac-list
Context
config>system>security>ssh
Description
This command enables the context to configure a list of preferred MAC algorithms to be used by an SSHv2 client.
Default
n/a
mac
Syntax
mac index name mac-name
no mac index
Context
config>system>security>ssh>client-mac-list
config>system>security>ssh>server-mac-list
Description
This command configures the list of preferred MAC algorithms that are negotiated by an SSHv2 server or client.
Each algorithm in the list has a corresponding index value, where a lower index has a higher preference in the SSH negotiation. The list is ordered by preference from highest to lowest.
The following table lists the default client and server MAC index values used for SSHv2.
|
MAC index value |
MAC algorithm name |
|---|---|
|
200 |
hmac-sha2-512 |
|
210 |
hmac-sha2-256 |
|
215 |
hmac-sha1 |
|
220 |
hmac-sha1-96 |
|
225 |
hmac-md5 |
|
240 |
hmac-md5-96 |
The no form of this command removes the specified MAC index from the list.
Default
no mac
Parameters
- index
the index of the MAC algorithm in the list
- mac-name
the algorithm for calculating the message authentication code
key-re-exchange
Syntax
key-re-exchange
Context
config>system>security>ssh
Description
This command enables the context to configure key re-exchange parameters for an SSH client or server.
client
Syntax
client
Context
config>system>security>ssh>key-re-exchange
Description
This command enables the context to configure key re-exchange parameters for an SSH client.
mbytes
Syntax
mbytes {mbytes| disable}
no mbytes
Context
config>system>security>ssh>key-re-exchange>client
config>system>security>ssh>key-re-exchange>server
Description
This command configures the maximum number of megabytes that can be transmitted during an SSH session before an SSH client or server initiates the key re-exchange procedure.
If both the mbytes and minutes key re-exchange parameters are configured, the key re-exchange will occur at whatever limit is reached first.
The no form of this command returns the setting to the default value.
Default
1024
Parameters
- mbytes
specifies the number of megabytes that can be transmitted during an SSH session before the key re-exchange occurs
- disable
specifies that a session will never time out
minutes
Syntax
minutes {minutes | disable}
no minutes
Context
config>system>security>ssh>key-re-exchange>client
config>system>security>ssh>key-re-exchange>server
Description
This command configures the maximum time that an SSH session can be up before an SSH client or server initiates the key re-exchange procedure.
If both the mbytes and minutes key re-exchange parameters are configured, the key re-exchange will occur at whatever limit is reached first.
The no form of this command returns the setting to the default value.
Default
60
Parameters
- minutes
specifies the number of minutes before an SSH client or server initiates the key re-exchange
- disable
specifies that a session will never time out
shutdown
Syntax
[no] shutdown
Context
config>system>security>ssh>key-re-exchange>client
config>system>security>ssh>key-re-exchange>server
Description
This command enables or disables initiating of the key re-exchange procedure when the configured thresholds are reached.
Default
no shutdown
server
Syntax
server
Context
config>system>security>ssh>key-re-exchange
Description
This command enables the context to configure key re-exchange parameters for an SSH server.
listening-port
Syntax
listening-port port
no listening-port
Context
config>system>security>ssh
Description
This command configures the listening TCP port of the SSH server for incoming SSH connections via base or management routing. VPRN node management is done via GRT leaking and uses base routing.
The no form of this command resets the listening port to its default of 22.
Default
no listening port
Parameters
- port
-
specifies the port number
preserve-key
Syntax
[no] preserve-key
Context
config>system>security>ssh
Description
This command specifies the persistence of the SSH server host key. When enabled, the host key will be saved by the server and restored following a system reboot. This command can only be enabled or disabled when no SSH session is running.
The no form of the command specifies that the host key will be held in memory by the SSH server and not be restored following a system reboot.
Default
no preserve-key
server-cipher-list
Syntax
server-cipher-list
Context
config>system>security>ssh
Description
This command enables the context to configure the list of allowed ciphers on the SSH server.
Default
n/a
server-kex-list
Syntax
server-kex-list
Context
config>system>security>ssh
Description
This command enables the context to configure a list of preferred KEX algorithms to be used by an SSHv2 server.
Default
n/a
server-mac-list
Syntax
server-mac-list
Context
config>system>security>ssh
Description
This command enables the context to configure a list of preferred MAC algorithms to be used by an SSHv2 server.
Default
n/a
server-shutdown
Syntax
[no] server-shutdown
Context
config>system>security>ssh
Description
This command disables the SSH server running on the system. The no version of the command enables the SSH server.
When the no server-shutdown command is executed, an SSH security key is generated. Unless the preserve-key command is enabled, this key is valid until either the node is restarted or the SSH server is stopped with the server-shutdown command and restarted. The key size is non-configurable and is set to 2048 for SSHv2 RSA and to 1024 for SSHv2 DSA. Only SSHv2 RSA is supported in FIPS-140-2 mode.
Default
no server-shutdown
Security TLS commands
tls
Syntax
tls
Context
config>system>security
Description
This command enables the context to configure TLS parameters.
Default
n/a
cert-profile
Syntax
cert-profile profile-name [create]
no cert-profile profile-name
Context
config>system>security>tls
Description
This command creates a new TLS certificate profile or specifies an existing certificate profile. The certificate profile contains the certificates that are sent to the TLS peer to authenticate itself. The TLS server must send this information. The TLS client can optionally send this information upon request from the TLS server.
The no form of the command deletes the specified TLS certificate profile.
Default
n/a
Parameters
- profile-name
-
the name of the TLS certificate profile, up to 32 characters in length
- create
- keyword is mandatory when creating a new certificate profile
entry
Syntax
entry entry-id [create]
no entry entry-id
Context
config>system>security>tls>cert-profile
Description
This command configures an entry for the TLS certificate profile. A certificate profile can have up to eight entries. Currently, TLS uses the entry with the lowest ID number when responding to server requests.
The no form of the command deletes the specified entry.
Default
n/a
Parameters
- entry-id
-
the identification number of the TLS certificate profile entry
- create
- keyword is mandatory when creating a new certificate profile
cert
Syntax
cert cert-filename
no cert
Context
config>system>security>tls>cert-profile>entry
Description
This command specifies the filename of an imported certificate for the cert-profile entry.
The no form of the command removes the certificate.
Default
no cert
Parameters
- cert-filename
-
the filename of the TLS certificate, up to 95 characters in length
key
Syntax
key key-filename
no key
Context
config>system>security>tls>cert-profile>entry
Description
This command specifies the filename of an imported key for the cert-profile entry.
The no form of the command removes the key.
Default
no key
Parameters
- key-filename
-
the filename of the key, up to 95 characters in length
send-chain
Syntax
[no] send-chain
Context
config>system>security>tls>cert-profile>entry
Description
This command enables the sending of certificate authority (CA) certificates and enables the context to configure send-chain information.
By default, the system only sends the TLS client certificate specified by the cert command. This command allows the system to send additional CA certificates to the peer. The certificates must be in the chain of certificates specified by the config>system>security>pki>ca-profile command. The specification of the send-chain is not necessary for a working TLS profile if the TLS peer has the CA certificate used to sign the client certificate in its own trust anchor.
For example, with a TLS client running on the 7705 SAR, the ROOT CA certificate resides on the TLS server, but the subsequent SUB-CA certificate needed to complete the chain resides within the 7705 SAR. The send-chain command allows these SUB-CA certificates to be sent from the 7705 SAR to the peer to be authenticated using the ROOT CA certificate that resides on the peer.
The no form of the command disables the send-chain.
Default
no send-chain
ca-profile
Syntax
[no] ca-profile name
Context
config>system>security>tls>cert-profile>entry>send-chain
Description
This command specifies that a CA certificate in the specified ca-profile is to be sent to the peer.
Up to seven configurations of this command are allowed in the same entry.
The no form of the command disables the transmission of a CA certificate from the specified CA profile.
Default
n/a
Parameters
- name
-
the name of an existing CA
shutdown
Syntax
[no] shutdown
Context
config>system>security>tls>cert-profile
Description
This command disables the certificate profile. When the certificate profile is disabled, it will not be sent to the TLS server.
The no form of the command enables the certificate profile and allows it to be sent to the TLS server.
Default
shutdown
client-cipher-list
Syntax
client-cipher-list name [create]
no client-cipher-list name
Context
config>system>security>tls
Description
This command creates a cipher list or specifies an existing list that the client sends to the server in the client Hello message. The list contains ciphers that are supported and preferred by the 7705 SAR to be used in the TLS session. The server matches this list against the server cipher list. The most preferred cipher found in both lists is chosen.
The no form of the command deletes the specified cipher list.
Default
n/a
Parameters
- name
-
the name of the client cipher list, up to 32 characters in length
- create
- keyword is mandatory when creating a new certificate profile
cipher
Syntax
cipher index name cipher-suite-code
no cipher index
Context
config>system>security>tls>client-cipher-list
Description
This command configures the TLS cipher suite code to be negotiated by the server and client.
The no form of the command removes the cipher suite code.
Default
n/a
Parameters
- index
-
the index number of the cipher suite code, which indicates the position of the code in the negotiation list (the lower the index number, the higher the priority of the code)
- cipher-suite-code
- specifies the cipher suite code
tls13-cipher
Syntax
tls13-cipher index name cipher-suite-code
no tls13-cipher index
Context
config>system>security>tls>client-cipher-list
Description
This command configures the TLS 1.3 supported ciphers that are used by the client and server.
The no form of the command removes the cipher suite code.
Default
n/a
Parameters
- index
-
the index number of the TLS 1.3 cipher suite code, which indicates the position of the code in the negotiation list (the lower the index number, the higher the priority of the code)
- cipher-suite-code
-
specifies the cipher suite code
client-group-list
Syntax
client-group-list name [create]
no client-group-list name
Context
config>system>security>tls
Description
This command creates a client group list or specifies an existing group list that the client sends in a client Hello message. The list contains group suite codes configured with the tls13-group command.
The no form of the command removes the client group list.
Default
n/a
Parameters
- name
-
the name of the client group list, up to 32 characters
- create
- keyword is mandatory when creating a new certificate profile
tls13-group
Syntax
tls13-group index name group-suite-code
no tls13-group index
Context
config>system>security>tls>client-group-list
Description
This command configures the TLS 1.3 supported group suite codes sent by the client in the Hello message.
The 7705 SAR supports the use of Elliptic-curve Diffie-Hellman Ephemeral (ECDHE) groups.
The no form of the command removes the group suite code.
Default
n/a
Parameters
- index
-
the index number of the group suite code, which indicates the position of the code in the negotiation list (the lower the index number, the higher the priority of the code)
- group-suite-code
-
specifies the group suite code
client-signature-list
Syntax
client-signature-list name [create]
no client-signature-list name
Context
config>system>security>tls
Description
This command creates a client signature list or specifies an existing signature list that the client sends in a client Hello message.
The no form of the command removes the client signature list.
Default
n/a
Parameters
- name
-
the name of the client signature list, up to 32 characters
- create
- keyword is mandatory when creating a new certificate profile
tls13-signature
Syntax
tls13-signature index name signature-suite-code
no tls13-signature index
Context
config>system>security>tls>client-signature-list
Description
This command configures the TLS 1.3 supported signature suite codes sent in the client Hello message.
The no form of the command removes the signature suite code.
Default
n/a
Parameters
- index
-
the index number of the TLS 1.3 signature suite code, which indicates the position of the code in the negotiation list (the lower the index number, the higher the priority of the code)
- signature-suite-code
-
specifies the signature suite code
client-tls-profile
Syntax
client-tls-profile name [create]
no client-tls-profile name
Context
config>system>security>tls
Description
This command creates a TLS client profile or specifies an existing client profile to be assigned to applications for encryption. Up to 16 TLS client profiles can be configured.
The no form of the command deletes the TLS client profile.
Default
n/a
Parameters
- name
-
the name of the TLS client profile, up to 32 characters in length
- create
- keyword is mandatory when creating a new certificate profile
cert-profile
Syntax
cert-profile name
no cert-profile
Context
config>system>security>tls>client-tls-profile
Description
This command assigns an existing TLS certificate profile to be used by the TLS client profile. This certificate is sent to the server for authentication of the client and public key.
The no form of the command removes the TLS certificate profile assignment.
Default
no cert-profile
Parameters
- name
-
the name of the TLS certificate profile
cipher-list
Syntax
cipher-list name
no cipher-list
Context
config>system>security>tls>client-tls-profile
Description
This command assigns an existing cipher list to be used by the TLS client profile for negotiation in the client Hello message.
Default
no cipher-list
Parameters
- name
-
the name of the cipher list
group-list
Syntax
group-list name
no group-list
Context
config>system>security>tls>client-tls-profile
Description
This command assigns an existing TLS 1.3 group list to the TLS client profile.
The no form of the command removes the group list from the client profile.
Default
no group-list
Parameters
- name
-
the name of the group list
protocol-version
Syntax
protocol-version TLS version
no protocol-version
Context
config>system>security>tls>client-tls-profile
Description
This command configures the TLS version to be negotiated between the client and server.
When configured, the client adds the specified version as a supported version in its Hello message to the server. If tls-version-all is specified, the client adds both TLS 1.2 and TLS 1.3 as supported versions in its Hello message.
The no form of the command reverts to the default TLS version.
Default
tls-version12
Parameters
- TLS version
-
specifies the TLS version to include in the client Hello message
shutdown
Syntax
[no] shutdown
Context
config>system>security>tls>client-tls-profile
Description
This command disables the client TLS profile.
The no form of the command enables the client TLS profile.
Default
shutdown
signature-list
Syntax
signature-list name
no signature-list
Context
config>system>security>tls>client-tls-profile
Description
This command assigns an existing TLS 1.3 signature list to the TLS client profile.
The no form of the command removes the signature list from the client profile.
Default
no signature-list
Parameters
- name
-
the name of the signature list
trust-anchor-profile
Syntax
trust-anchor-profile name
no trust-anchor-profile
Context
config>system>security>tls>client-tls-profile
Description
This command assigns an existing trust anchor profile to be used by this TLS client profile to authenticate the server.
The no form of the command removes the trust anchor profile from the client profile.
Default
no trust-anchor-profile
Parameters
- name
-
the name of the trust anchor profile
trust-anchor-profile
Syntax
trust-anchor-profile name [create]
no trust-anchor-profile name
Context
config>system>security>tls
Description
This command creates a trust anchor profile or specifies an existing trust anchor profile to be used in the TLS client profile. The trust anchor is used for authentication of the server certificate. Up to 16 trust anchor profiles can be configured, with up to 8 trust anchors in each profile.
Default
n/a
Parameters
- name
-
the name of the trust anchor profile, up to 32 characters
- create
- keyword is mandatory when creating a new certificate profile
trust-anchor
Syntax
[no] trust-anchor ca-profile-name
Context
config>system>security>tls>trust-anchor-profile
Description
This command configures a trust anchor with a CA profile used by the TLS profile. Up to eight trust anchors can be configured under the TLS profile.
Default
n/a
Parameters
- ca-profile-name
-
the name of the TLS trust anchor
Keychain authentication commands
keychain
Syntax
[no] keychain keychain-name
Context
config>system>security
Description
This command enables the context to configure keychain parameters that are used to authenticate protocol communications. A keychain must be configured on the system before it can be applied to a protocol session.
The keychain must include at least one key entry to be valid.
The no form of the command removes the keychain and all commands configured in the keychain context. If the keychain is associated with a protocol when the no keychain command is entered, the command will be rejected and an error indicating that the keychain is in use will be displayed.
Default
n/a
Parameters
- keychain-name
the keychain name, up to 32 characters
direction
Syntax
direction
Context
config>system>security>keychain
Description
This command specifies the stream direction on which the keys will be applied.
Default
n/a
bi
Syntax
bi
Context
config>system>security>keychain>direction
Description
This command configures keys for both send and receive stream directions.
Default
n/a
entry
Syntax
entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
no entry entry-id
Context
config>system>security>keychain>direction>bi
config>system>security>keychain>direction>uni>receive
config>system>security>keychain>direction>uni>send
Description
This command defines a key in the keychain. A keychain must have at least one key entry to be valid.
The key and algorithm keywords are mandatory when the entry is first created.
The no form of the command removes the entry from the keychain. If the key is the active key for sending, this command will cause a new active key to be selected (if one is available). If the key is the only possible send key, the command will be rejected and an error indicating that the configured key is the only available send key will be displayed. If the key is one of the eligible keys for receiving, it will be removed. If the key is the only eligible key for receiving, the command will be rejected and an error indicating that this is the only eligible key will be displayed.
Default
n/a
Parameters
- entry-id
the ID of the key entry
- key
the authentication key ID that is used along with keychain-name and direction to uniquely identify this particular key entry
- authentication-key
the authentication key that will be used by the encryption algorithm, up to 20 characters in any combination of letters and numbers. The key is used to sign and authenticate a protocol packet.
- hash-key | hash2-key
the hash key. The key can be any combination of ASCII characters up to 33 for the hash-key and up to 96 for the hash2-key (encrypted). If spaces are used in the string, the entire string must be enclosed in double quotes.
This parameter is useful when a user must configure the parameter, but for security purposes, the actual unencrypted key value is not provided.
- hash
specifies that the key is entered in an encrypted form. If the hash or hash2 parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 parameter specified.
- hash2
specifies that the key is entered in a more complex encrypted form that involves more variables than the key value alone, meaning that the hash2 encrypted variable cannot be copied and pasted. If the hash or hash2 parameter is not used, the key is assumed to be in an unencrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 parameter specified.
- algorithm
the encryption algorithm to be used by the key defined in the keychain
begin-time
Syntax
begin-time date hours-minutes [UTC]
begin-time {now | forever}
no begin-time
Context
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
Description
This command specifies the calendar date and time after which the key specified by the keychain authentication key entry is used to sign and authenticate the protocol stream.
Each entry within a bidirectional keychain or for a keychain direction (if unidirectional keys are used) must have a unique begin time.
If no date and time is set, the begin-time is represented by a date and time string with all NULLs and the key is not valid.
Default
forever
Parameters
- date hours-minutes
the date (in YYYY/MM/DD format) and time (in hh:mm[:ss] format) at which the key becomes active
- UTC
specifies that the date and time should be in UTC time rather than local time
- now
specifies that the key should become active immediately (current system time)
- forever
specifies that the key is always inactive
option
Syntax
option {basic | isis-enhanced}
no option
Context
config>system>security>keychain>direction>bi>entry
Description
This command enables options to be associated with the authentication key for IS-IS. The command is only applicable for IS-IS and will be ignored by other protocols associated with the keychain.
Default
no option
Parameters
- basic
specifies that IS-IS should use RFC 5304 encoding of the authentication information
- isis-enhanced
specifies that IS-IS should use RFC 5310 encoding of the authentication information
tolerance
Syntax
tolerance {seconds | forever}
no tolerance
Context
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
Description
This command configures the amount of time that an eligible receive key overlaps with the currently active key. During that time, packets with either key will be accepted. Tolerance only applies to received packets. Transmitted packets always use the newest key, regardless of the tolerance value.
If a tolerance value is set for a key, the key is returned as part of the key set if the current time is within the key’s begin time, plus or minus the tolerance value. For example, if the begin time is 12:00 p.m. and the tolerance is 600 seconds, the new key should be included from 11:55 a.m. and the key to be replaced should be included until 12:05 p.m.
Default
300
Parameters
- seconds
specifies the length of time that an eligible receive key overlaps with the active key
- forever
specifies that an eligible receive key will overlap with the active key forever
uni
Syntax
uni
Context
config>system>security>keychain>direction
Description
This command configures keys for send or receive stream directions.
Default
n/a
receive
Syntax
receive
Context
config>system>security>keychain>direction>uni
Description
This command enables the receive context. Entries defined under this context are used to authenticate packets that are received by the router.
Default
n/a
end-time
Syntax
end-time date hours-minutes [UTC]
end-time {now | forever}
no end-time
Context
config>system>security>keychain>direction>uni>receive>entry
Description
This command specifies the calendar date and time after which the key specified by the authentication key is no longer eligible to authenticate the protocol stream.
Default
forever
Parameters
- date hours minutes
the date (in YYYY/MM/DD format) and time (in hh:mm[:ss] format) after which the key is no longer eligible to sign and authenticate the protocol stream. If no year is specified, the system assumes the current year.
- UTC
specifies that the date and time should be in UTC time rather than local time
- now
specifies that the key should become inactive immediately (current system time)
- forever
specifies that the key is always active
send
Syntax
send
Context
config>system>security>keychain>direction>uni
Description
This command enables the send context. Entries defined under this context are used to sign packets that are being sent by the router to another device.
Default
n/a
tcp-option-number
Syntax
tcp-option-number
Context
config>system>security>keychain
Description
This command enables the context to configure the TCP option number to be placed in the TCP packet header.
receive
Syntax
receive option-number
no receive
Context
config>system>security>keychain>tcp-option-number
Description
This command configures the TCP option number that will be accepted in the header of received TCP packets.
Default
254
Parameters
- option-number
the TCP option number to be used in the TCP header
send
Syntax
send option-number
no send
Context
config>system>security>keychain>tcp-option-number
Description
This command configures the TCP option number that will be inserted in the header of sent TCP packets.
Default
254
Parameters
- option-number
the TCP option number to be used in the TCP header
Login control commands
login-control
Syntax
login-control
Context
config>system
Description
This command enables the context to configure the session control for console, FTP, SSH, and Telnet sessions.
exponential-backoff
Syntax
[no] exponential-backoff
Context
config>system>login-control
Description
This command enables the exponential backoff of the login prompt. The exponential-backoff command is used to deter dictionary attacks, when a malicious user can gain access to the CLI by using a script to try admin with any conceivable password.
The no form of the command disables exponential-backoff.
Default
no exponential-backoff
ftp
Syntax
ftp
Context
config>system>login-control
Description
This command enables the context to configure FTP login control parameters.
inbound-max-sessions
Syntax
inbound-max-sessions value
no inbound-max-sessions
Context
config>system>login-control>ftp
Description
This command configures the maximum number of concurrent inbound FTP sessions.
This value is the combined total of inbound and outbound sessions.
The no form of the command reverts to the default value.
Default
3
Parameters
- value
the maximum number of concurrent FTP sessions on the node
idle-timeout
Syntax
idle-timeout {minutes | disable}
no idle-timeout
Context
config>system>login-control
Description
This command configures the idle timeout for FTP, console, SSH, and Telnet sessions before the session is terminated by the system.
By default, each idle FTP, console, SSH, or Telnet session times out after 30 minutes of inactivity.
The no form of the command reverts to the default value.
Default
30
Parameters
- minutes
the idle timeout in minutes
- disable
when the disable option is specified, a session will never time out. To re-enable idle timeout, enter the command without the disable option.
login-banner
Syntax
[no] login-banner
Context
config>system>login-control
Description
This command enables or disables the display of a login banner. The login banner contains the 7705 SAR copyright and build date information for a console login attempt.
The no form of the command causes only the configured pre-login-message and a generic login prompt to display.
motd
Syntax
motd {url url-prefix:source-url | text motd-text-string}
no motd
Context
config>system>login-control
Description
This command creates the message of the day that is displayed after a successful console login. Only one message can be configured.
The no form of the command removes the message.
Default
no motd
Parameters
- url-prefix: source-url
when the message of the day is present as a text file, provide both the url-prefix and the source-url of the file containing the message of the day. The URL prefix can be local or remote.
- motd-text-string
the text of the message of the day, up to 900 characters long. The motd-text-string must be enclosed in double quotes. Multiple text strings are not appended to one another.
Some special characters can be used to format the message text. The ‟\n” character creates multi-line MOTDs and the ‟\r” character restarts at the beginning of the new line. For example, entering ‟\n\r” will start the string at the beginning of the new line, while entering ‟\n” will start the second line below the last character from the first line.
pre-login-message
Syntax
pre-login-message login-text-string [name]
no pre-login-message
Context
config>system>login-control
Description
This command creates a message displayed prior to console login attempts on the console via Telnet.
Only one message can be configured. If multiple pre-login messages are configured, the last message entered overwrites the previous entry.
The system name can be added to an existing message without affecting the current pre-login message.
The no form of the command removes the message.
Default
no pre-login-message
Parameters
- login-text-string
a text string, up to 900 characters. Any printable, 7-bit ASCII characters can be used. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
- name
when the keyword name is defined, the configured system name is always displayed first in the login message. To remove the name from the login message, the message must be cleared and a new message entered without the name.
ssh
Syntax
ssh
Context
config>system>login-control
Description
This command enables the context to configure SSH login control parameters.
disable-graceful-shutdown
Syntax
[no] disable-graceful-shutdown
Context
config>system>login-control>ssh
Description
This command disables graceful shutdown of SSH sessions.
By default, SSH always performs a graceful shutdown on a TCP connection. When graceful shutdown is disabled, SSH sends a FIN message and then immediately terminates the connection.
The no form of the command enables graceful shutdown of SSH sessions.
Default
no disable-graceful-shutdown
inbound-max-sessions
Syntax
inbound-max-sessions value
no inbound-max-sessions
Context
config>system>login-control>ssh
Description
This command limits the number of inbound SSH sessions (channels). Each 7705 SAR router is limited to a total of 15 inbound SSH sessions (IPv4 and IPv6).
The no form of the command reverts to the default value.
Default
5
Parameters
- value
the maximum number of concurrent inbound SSH sessions, expressed as an integer
outbound-max-sessions
Syntax
outbound-max-sessions value
no outbound-max-sessions
Context
config>system>login-control>ssh
Description
This command limits the number of outbound SSH sessions (channels). Each 7705 SAR router is limited to a total of 15 outbound SSH sessions (IPv4 and IPv6).
The no form of the command reverts to the default value.
Default
5
Parameters
- value
the maximum number of concurrent outbound SSH sessions, expressed as an integer
telnet
Syntax
telnet
Context
config>system>login-control
Description
This command enables the context to configure the Telnet login control parameters.
enable-graceful-shutdown
Syntax
[no] enable-graceful-shutdown
Context
config>system>login-control>telnet
Description
This command enables graceful shutdown of Telnet sessions.
When graceful shutdown is enabled, Telnet sends a FIN message and waits for an acknowledgment before terminating the TCP connection.
The no form of the command disables graceful shutdown of Telnet sessions.
Default
no enable-graceful-shutdown
inbound-max-sessions
Syntax
inbound-max-sessions value
no inbound-max-sessions
Context
config>system>login-control>telnet
Description
This command limits the number of inbound Telnet sessions. Each 7705 SAR router is limited to a total of 15 inbound Telnet sessions (IPv4 and IPv6).
The no form of the command reverts to the default value.
Default
5
Parameters
- value
the maximum number of concurrent inbound Telnet sessions, expressed as an integer
outbound-max-sessions
Syntax
outbound-max-sessions value
no outbound-max-sessions
Context
config>system>login-control>telnet
Description
This command limits the number of outbound Telnet sessions. Each 7705 SAR router is limited to a total of 15 outbound Telnet sessions (IPv4 and IPv6).
The no form of the command reverts to the default value.
Default
5
Parameters
- value
the maximum number of concurrent outbound Telnet sessions, expressed as an integer
ttl-security
Syntax
ttl-security min-ttl-value
no ttl-security
Context
config>system>login-control>telnet
config>system>login-control>ssh
Description
This command configures TTL security parameters for incoming packets. When the feature is enabled, SSH or Telnet connections will accept incoming IP packets from a peer only if the TTL value in the packet is greater than or equal to the minimum TTL value configured for that peer.
The no form of the command disables TTL security.
Default
no ttl-security
Parameters
- min-ttl-value
specifies the minimum TTL value for an incoming packet
Show commands
Security show commands
access-group
Syntax
access-group [group-name]
Context
show>system>security
Description
This command displays SNMP access group information.
Parameters
- group-name
displays information for the specified access group
Output
The following output is an example of system security access group information, and System security access group field descriptions describes the fields.
Output exampleA:ALU-4# show system security access-group
===============================================================================
Access Groups
===============================================================================
group name security security read write notify
model level view view view
-------------------------------------------------------------------------------
snmp-ro snmpv1 none no-security no-security
snmp-ro snmpv2c none no-security no-security
snmp-rw snmpv1 none no-security no-security no-security
snmp-rw snmpv2c none no-security no-security no-security
snmp-rwa snmpv1 none iso iso iso
snmp-rwa snmpv2c none iso iso iso
snmp-trap snmpv1 none iso
snmp-trap snmpv2c none iso
===============================================================================
A:ALU-7#
|
Label |
Description |
|---|---|
|
Group name |
The access group name |
|
Security model |
The security model required to access the views configured in this node |
|
Security level |
Specifies the required authentication and privacy levels to access the views configured in this node |
|
Read view |
Specifies the variable of the view to read the MIB objects |
|
Write view |
Specifies the variable of the view to configure the contents of the agent |
|
Notify view |
Specifies the variable of the view to send a trap about MIB objects |
authentication
Syntax
authentication [statistics]
Context
show>system>security
Description
This command displays system login authentication configuration and statistics.
Parameters
- statistics
appends login and accounting statistics to the display
Output
The following output is an example of system security authentication information, and System security authentication field descriptions describes the fields.
Output exampleA:ALU-4# show system security authentication
===============================================================================
Authentication sequence : radius tacplus local
===============================================================================
type status timeout retry
server address (secs) count
-------------------------------------------------------------------------------
radius
10.10.10.103 up 5 5
radius
10.10.0.1 up 5 5
radius
10.10.0.2 up 5 5
tacplus
10.10.0.9(49) down 5 n/a
-------------------------------------------------------------------------------
radius admin status : up
tacplus admin status : down
health check : enabled (interval 30)
-------------------------------------------------------------------------------
No. of Servers: 4
===============================================================================
A:ALU-4#
A:ALU-7>show>system>security# authentication statistics
===============================================================================
Authentication sequence : radius tacplus local
===============================================================================
type status timeout retry
server address (secs) count
-------------------------------------------------------------------------------
radius
10.10.10.103 up 5 5
radius
10.10.0.1 up 5 5
radius
10.10.0.2 up 5 5
tacplus
10.10.0.9(49) down 5 n/a
-------------------------------------------------------------------------------
radius admin status : up
tacplus admin status : down
health check : enabled (interval 30)
-------------------------------------------------------------------------------
No. of Servers: 4
===============================================================================
Login Statistics
===============================================================================
server address conn accepted rejected
errors logins logins
-------------------------------------------------------------------------------
10.10.10.103 0 0 0
10.10.0.1 0 0 0
10.10.0.2 0 0 0
10.10.0.9 0 0 0
local n/a 1 0
===============================================================================
Authorization Statistics (TACACS+)
===============================================================================
server address conn sent rejected
errors pkts pkts
-------------------------------------------------------------------------------
10.10.0.9 0 0 0
===============================================================================
Accounting Statistics
===============================================================================
server address conn sent rejected
errors pkts pkts
-------------------------------------------------------------------------------
10.10.10.103 0 0 0
10.10.0.1 0 0 0
10.10.0.2 0 0 0
===============================================================================
A:ALU-7#
Label |
Description |
|---|---|
Sequence |
The sequence in which authentication is processed |
Server address |
The IP address of the RADIUS server |
Status |
The current status of the RADIUS server |
Type |
The authentication type |
Timeout (secs) |
The number of seconds the router waits for a response from a RADIUS server |
Retry count |
The number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server |
Connection errors |
The number of times a user has attempted to log in irrespective of whether the login succeeded or failed |
Accepted logins |
The number of times the user has successfully logged in |
Rejected logins |
The number of unsuccessful login attempts |
Sent packets |
The number of packets sent |
Rejected packets |
The number of packets rejected |
communities
Syntax
communities
Context
show>system>security
Description
This command displays SNMP communities and characteristics.
Output
The following output is an example of community information, and Communities field descriptions describes the fields.
Output exampleA:ALU-48# show system security communities
=============================================================================
Communities
=============================================================================
community access view version group name
-----------------------------------------------------------------------------
cli-readonly r iso v2c cli-readonly
cli-readwrite rw iso v2c cli-readwrite
public r no-security v1 v2c snmp-ro
-----------------------------------------------------------------------------
No. of Communities: 3
=============================================================================
A:ALU-48#
Label |
Description |
|---|---|
Community |
The community string name for SNMPv1 and SNMPv2c access only |
Access |
r: The community string allows read-only access |
rw: The community string allows read-write access |
|
rwa: The community string allows read-write access |
|
mgmt: The unique SNMP community string assigned to the management router |
|
View |
The view name |
Version |
The SNMP version |
Group Name |
The access group name |
No of Communities |
The total number of configured community strings |
cpm-filter
Syntax
cpm-filter ip-filter [entry entry-id]
cpm-filter ipv6-filter [entry entry-id]
Context
show>system>security
Description
This command displays information for CPM (CSM) filters.
If an entry number is not specified, all entries are displayed.
Parameters
- entry-id
displays information for the specified CPM filter entry
Output
The following output is an example of CPM filter information, and CPM filter field descriptions describes the fields.
Output exampleA:ALU-35# show system security cpm-filter ip-filter
===============================================================================
CPM IP Filters
===============================================================================
Entry-Id Dropped Forwarded Description
-------------------------------------------------------------------------------
2 0 0 CPM filter #2
3 25880 0 CPM filter #3
4 25880 0 CPM filter #4
5 25882 0 CPM filter #5
6 25926 0 CPM filter #6
7 25926 0 CPM filter #7
8 25944 0 CPM filter #8
9 25950 0 CPM filter #9
10 25968 0 CPM filter #10
11 25984 0 CPM filter #11
12 26000 0 CPM filter #12
13 26018 0 CPM filter #13
14 26034 0 CPM filter #14
15 26050 0 CPM filter #15
===============================================================================
A:ALU-35#
A:ALU-35# show system security cpm-filter ip-filter entry 2
===============================================================================
CPM IP Filter Entry
===============================================================================
Entry Id : 2
Description : CPM filter #2
-------------------------------------------------------------------------------
Filter Entry Match Criteria :
-------------------------------------------------------------------------------
Log Id : 101
Src. IP : 10.4.101.2/32 Src. Port : 0
Dest. IP : 10.4.101.1/32 Dest. Port : 0
Protocol : tcp Dscp : ef
ICMP Type : Undefined ICMP Code : Undefined
Fragment : True Option-present : Off
IP-Option : n/a Multiple Option : True
TCP-syn : Off TCP-ack : True
Match action : Drop
Dropped pkts : 0 Forwarded pkts : 0
===============================================================================
A:ALU-35#
A:ALU-35# show system security cpm-filter ipv6-filter entry 101
===============================================================================
CPM IPv6 Filter Entry
===============================================================================
Entry Id : 1
Description : CPM-Filter 11::101:2 #101
-------------------------------------------------------------------------------
Filter Entry Match Criteria :
-------------------------------------------------------------------------------
Log Id : n/a
Src. IP : 11::101:2 Src. Port : 0
Dest. IP : 11::101:1 Dest. Port : 0
next-header : none Dscp : Undefined
ICMP Type : Undefined ICMP Code : Undefined
TCP-syn : Off TCP-ack : Off
Match action : Drop
Dropped pkts : 25880 Forwarded pkts : 0
===============================================================================
Label |
Description |
|---|---|
CPM IP (or IPv6) Filter Entry |
|
Entry-id |
Displays information for the specified CPM filter entry |
Dropped |
The number of dropped events |
Forwarded |
The number of forwarded events |
Description |
The CPM filter description |
Filter Entry Match Criteria |
|
Log Id |
The log ID where matched packets will be logged |
Src. IP |
The source IP address |
Dest. IP |
The destination IP address |
Protocol |
The Protocol field in the IP header (IPv4 filters only) |
next-header |
The next header ID. Undefined indicates no next header is specified. (IPv6 filters only) |
ICMP Type |
The ICMP type field in the ICMP header |
Fragment |
The 3-bit fragment flags or 13-bit fragment offset field (IPv4 filters only) |
IP-Option |
The IP option setting (IPv4 filters only) |
TCP-syn |
The SYN flag in the TCP header |
Match action |
When the criteria matches, displays drop or forward packet |
Dropped pkts |
The number of matched dropped packets |
Src. Port |
The source port number (range) |
Dest. Port |
The destination port number (range) |
Dscp |
The DSCP field in the IP header |
ICMP Code |
The ICMP code field in the ICMP header |
Option-present |
The option present setting (IPv4 filters only) |
Multiple Option |
The multiple option setting (IPv4 filters only) |
TCP-ack |
The ACK flag in the TCP header |
Match action |
When the criteria matches, displays drop or forward packet |
Next Hop |
If match action is forward, indicates destination of the matched packet |
Forwarded pkts |
Indicates number of matched forwarded packets |
keychain
Syntax
keychain [keychain] [detail]
Context
show>system>security
Description
This command displays information about keychains.
If a keychain name is not specified, all keychains are displayed.
Parameters
- keychain
displays information for the specified keychain
- detail
displays detailed keychain information
Output
The following output is an example of keychain information, and Keychain field descriptions describes the fields.
Output example===============================================================================
Key chain:ospf-md5
===============================================================================
Description : MD5 keychain for OSPF interfaces
TCP-Option number send : 254 Admin state : Up
TCP-Option number receive : 254 Oper state : Up
Used by : None
Expired : No
===============================================================================
*A:ALU-35#
A:ALU-35# show system security keychain ospf-md5 detail
===============================================================================
Key entries for key chain: ospf-md5
===============================================================================
Id : 0 Direction : send-receive
Algorithm : message-digest Option : none
Admin State : Up RX Valid : No
TX Active : No Tolerance : 300
Begin Time : 2016/06/01 01:01:00 Begin Time (UTC) : 2016/06/01 01:01:00
End Time : 2016/09/01 01:01:00 End Time (UTC) : 2016/09/01 01:01:00
===============================================================================
Id : 1 Direction : send-receive
Algorithm : message-digest Option : none
Admin State : Up RX Valid : Yes
TX Active : Yes Tolerance : 600
Begin Time : 2016/09/01 01:01:00 Begin Time (UTC) : 2016/09/01 01:01:00
End Time : Forever End Time (UTC) : Forever
===============================================================================
*A:Sar18 Dut-B#
Label |
Description |
|---|---|
Key chain: name |
|
Description |
The text string description for the keychain |
TCP-Option number send |
The TCP option number to be inserted in the header of sent TCP packets |
Admin state |
The administrative state of the keychain: up or down |
TCP-Option number receive |
The TCP option number that will be accepted in the header of received TCP packets |
Oper state |
The operational state of the keychain: up or down |
Used by |
The protocols associated with this keychain |
Expired |
Indicates whether the keychain has expired |
Key entries for key chain: name |
|
Id |
The ID of the key entry |
Direction |
The stream direction on which keys will be applied for this entry: send, receive, or send-receive |
Algorithm |
The encryption algorithm to be used by this key entry |
Option |
Indicates the configured IS-IS encoding standard (indicates ‟none” if the associated protocol is not IS-IS) |
Admin State |
The administrative state of the key entry: up or down |
RX Valid |
Indicates if the receive key is valid |
TX Active |
Indicates if the transmit (sent) key is active |
Tolerance |
The tolerance time configured for support of both currently active and new keys |
Begin Time |
The time at which the new key is used to sign and/or authenticate protocol packets |
Begin Time (UTC) |
The begin time in UTC time |
End Time |
The time at which the key is no longer eligible to authenticate protocol packets |
End Time (UTC) |
The end time in UTC time |
management-access-filter
Syntax
management-access-filter ip-filter [entry entry-id]
management-access-filter ipv6-filter [entry entry-id]
Context
show>system>security
Description
This command displays management access control filter information.
If no specific entry number is specified, all entries are displayed.
Parameters
- entry-id
displays information for the specified management access filter entry
Output
The following output is an example of management access filter information, and Management access filter field descriptions describes the fields.
Output exampleA:ALU-7# show system security management-access-filter ip-filter entry 1
=============================================================================
IPv4 Management Access Filters
=============================================================================
filter type: : ip
Def. Action : permit
Admin Status : enabled (no shutdown)
-----------------------------------------------------------------------------
Entry : 1
Description : test description
Src IP : 10.10.10.104
Src interface : undefined
Dest port : 10.10.10.103
Protocol : 6
Router : undefined
Action : permit
Log : disabled
Matches : 0
=============================================================================
A:ALU-7#
A:ALU-7# show system security management-access-filter ipv6-filter entry 2
=============================================================================
IPv6 Management Access Filter
=============================================================================
filter type : ipv6
Def. Action : permit
Admin Status : enabled (no shutdown)
-----------------------------------------------------------------------------
Entry : 1
Src IP : 2001::1/128
Flow label : undefined
Src interface : undefined
Dest port : undefined
Next-header : undefined
Router : undefined
Action : permit
Log : enabled
Matches : 0
=============================================================================
A:ALU-7#
Label |
Description |
|---|---|
IPv4 (or IPv6) Management Access Filters |
|
filter type |
The management access filter type |
Def. Action |
Permit: Specifies that packets not matching the configured selection criteria in any of the filter entries are permitted |
Deny: Specifies that packets not matching the configured selection criteria in any of the filter entries are denied and that a ICMP host unreachable message will be issued |
|
Deny-host-unreachable: Specifies that packets not matching the configured selection criteria in the filter entries are denied |
|
Admin Status |
Up: indicates that the management access filter is administratively enabled |
Down: indicates that the management access filter is administratively disabled |
|
Entry |
The entry ID in a policy or filter table |
Description |
A text string describing the filter |
Src IP |
The source IP address used for management access filter match criteria |
Flow label |
The flow label to match (IPv6 filters only) |
Src interface |
The interface name for the next hop to which the packet should be forwarded if it hits this filter entry |
Dest port |
The destination port |
Next-header |
The next header ID to match. Undefined indicates no next header is specified. (IPv6 filters only) |
Protocol |
The IP protocol to match (IPv4 filters only) |
Action |
The action to take for packets that match this filter entry |
Matches |
The number of times a management packet has matched this filter entry |
password-options
Syntax
password-options
Context
show>system>security
Description
This command displays configured password options.
Output
The following output is an example of password options information, and Password options field descriptions describes the fields.
Output exampleA:7705:Dut-A# show system security password-options
===============================================================================
Password Options
===============================================================================
Password aging in days : none
Time required between password changes : 0d 00:10:00
Number of invalid attempts permitted per login : 3
Time in minutes per login attempt : 5
Lockout period (when threshold breached) : 10
Authentication order : radius tacplus local
User password history length : disabled
Password hashing : bcrypt
Accepted password length : 6..56 characters
Credits for each character class : none
Number of required characters per class : none
Minimum number of required character classes : 0
Required distance with previous password : 5
Allow consecutively repeating a character : always
Allow passwords containing username : no
Palindrome allowed : no
===============================================================================
A:7705:Dut-A#
Label |
Description |
|---|---|
Password aging in days |
The number of days a user password is valid before the user must change their password |
Time required between password changes |
The time interval required before a password can be changed |
Number of invalid attempts permitted per login |
The number of unsuccessful login attempts allowed for the specified time |
Time in minutes per login attempt |
The period of time, in minutes, that a specified number of unsuccessful attempts can be made before the user is locked out |
Lockout period (when threshold breached) |
The lockout period, in minutes, during which the user is not allowed to log in |
Authentication order |
The sequence in which password authentication is attempted among RADIUS, TACACS+, and local passwords |
User password history length |
The number of recent passwords stored in the history file to compare against new passwords. If a new password matches any of the passwords in the history file, it is rejected |
Password hashing |
The password hashing type, either bcrypt, sha2-pbkdf2, or sha3-pbkdf2 |
Accepted password length |
The minimum and maximum password length |
Credits for each character class |
The maximum number of credits given for each character class |
Number of required characters per class |
The minimum number of characters for each character classes that is required in a password: uppercase, lowercase, numeric, or special character |
Minimum number of required character classes |
The number of different character classes that is required in a password: uppercase, lowercase, numeric, or special character |
Required distance with previous password |
The minimum number of characters required to be different in the new password from the old password. |
Allow consecutively repeating a character |
The number of times the same character is allowed to be repeated consecutively in a new command |
Allow passwords containing username |
Displays whether the username is allowed as part of the password |
Palindrome allowed |
Displays whether palindromes are allowed as part of the password |
profile
Syntax
profile user-profile-name
Context
show>system>security
Description
This command displays user profile information.
If the user-profile-name is not specified, then information for all profiles is displayed.
Parameters
- user-profile-name
displays information for the specified user profile
Output
The following output is an example of user profile information, and User profile field descriptions describes the fields.
Output exampleA:ALU-7# show system security profile administrative
===============================================================================
User Profile
===============================================================================
User Profile : administrative
Def. Action : permit-all
LI : no
-------------------------------------------------------------------------------
Entry : 10
Description :
Match Command: configure system security
Action : permit
-------------------------------------------------------------------------------
Entry : 20
Description :
Match Command: show system security
Action : permit
-------------------------------------------------------------------------------
No. of profiles: 1
===============================================================================
A:ALU-7#
Label |
Description |
|---|---|
User Profile |
The profile name used to deny or permit user console access to a hierarchical branch or to specific commands |
Def. action |
Permit all: Permits access to all commands |
Deny: Denies access to all commands |
|
None: No action is taken |
|
Entry |
The entry ID in a policy or filter table |
Description |
Displays the text string describing the entry |
Match Command |
Displays the command or subtree commands in subordinate command levels |
Action |
Permit all: Commands matching the entry command match criteria are permitted |
Deny: Commands not matching the entry command match criteria are not permitted |
|
No. of profiles |
The total number of profiles listed |
source-address
Syntax
source-address
Context
show>system>security
Description
This command displays the source address configured for applications.
Output
The following output is an example of source address information, and Source address field descriptions describes the fields.
Output exampleA:ALU-1# show system security source-address
===============================================================================
Source-Address applications
===============================================================================
Application IP address/Interface Name Oper status
-------------------------------------------------------------------------------
telnet 10.20.1.7 Up
radius loopback1 Up
===============================================================================
A:ALU-1#
|
Label |
Description |
|---|---|
|
Application |
The source-address application |
|
IP address: Interface Name |
The source address IP address or interface name |
|
Oper status |
Up: The source address is operationally up |
|
Down: The source address is operationally down |
ssh
Syntax
ssh
Context
show>system>security
Description
This command displays all the SSH sessions as well as the SSH status and fingerprint. The type of SSH application (CLI, SCP, or SFTP) is indicated for each SSH connection.
Output
The following output is an example of SSH information for an SSH server, and SSH field descriptions describes the fields.
Output example*A:7705:Dut-C# show system security ssh
===============================================================================
SSH Server
===============================================================================
Administrative State : Enabled
Operational State : Up
Preserve Key : Disabled
Key-re-exchange : 60 minutes / 1024 MB
SSH Protocol Version 2 : Enabled
DSA Host Key Fingerprint : MD5:0a:89:df:09:d8:8c:c4:0d:6c:dc:42:28:79:f9:a1:cf
SHA256:VY42oECtkK3Qy+H+FMKShDzjqGKFlo/cxCdfemVNfwE
RSA Host Key Fingerprint : MD5:8f:cf:0e:5e:48:1b:5d:ce:1a:fb:f6:15:57:1b:82:ac
SHA256:DEf9VOKmUz0rxRxhxoCmWs2E+Ny9ryVCADdornzCk/I
-------------------------------------------------------------------------------
Connection ConnectionID
Username ConnectionStatus
RouterInstance Key-re-exchange
Version KEX
Cipher
MAC
SessionID ChannelID ServerName ChannelStatus
-------------------------------------------------------------------------------
192.168.192.29 14
admin connected
management 60 minutes / 1024 MB
SSHv2 diffie-hellman-group-exchange-sha1
aes128-ctr
hmac-sha1
16 0 cli connected
17 1 cli connected
18 2 cli connected
-------------------------------------------------------------------------------
192.168.192.29 17
admin connected
management 60 minutes / 1024 MB
SSHv2 diffie-hellman-group-exchange-sha1
aes128-ctr
hmac-sha1
21 0 sftp connected
-------------------------------------------------------------------------------
Number of SSH connections : 2
Number of SSH sessions : 4
===============================================================================
*A:7705
|
Label |
Description |
|---|---|
|
Administrative State |
The administrative state of the SSH server: enabled or disabled |
|
Operational State |
The operational state of the SSH server: up or down |
|
Preserve Key |
The preserve-key configuration: enabled or disabled |
|
Key-re-exchange |
The maximum number of minutes elapsed or maximum number of megabytes transmitted before a key re-exchange is initiated |
|
SSH Protocol Version 2 |
The SSHv2 configuration: enabled or disabled |
|
DSA Host Key Fingerprint RSA Host Key Fingerprint |
The key fingerprint is the digital signal algorithm (DSA) or Rivest, Shamir, and Adleman (RSA) host server’s identity. Clients trying to connect to the server verify the server fingerprint. If the server fingerprint is not known, the client will get a warning message that the server may be spoofed and they will not be allowed to log in until the administrator fixes the issue. The MD5 and SHA 256 versions of the keys are supported. |
|
Connection |
The IP address of the connected routers (remote client) |
| ConnectionID | The SSH connection identifier |
| Username | The name of the user |
| ConnectionStatus | The status of the SSH connection: connected or disconnected |
| RouterInstance | The router instance used to establish the connection, either management or base |
| Key-re-exchange |
The number of minutes or the number of megabytes transmitted after which a key re-exchange should occur for this connection |
|
Version |
SSHv2 |
|
KEX |
The KEX algorithm used by the SSH session |
|
Cipher |
The cipher used by the SSH session |
|
MAC |
The MAC algorithm used by the SSH session |
| SessionID | The identifier for the session |
| ChannelID | The identifier for the channel |
| ServerName | The name of the server. For an SSH session, the value is cli. For an SFTP session, the value is sftp. |
|
ChannelStatus |
The status of the channel: connected or disconnected |
|
Number of SSH connections |
The total number of SSH connections |
| Number of SSH sessions | The total number of SSH sessions |
cert-profile
Syntax
cert-profile name association
cert-profile [name]
cert-profile name entry 1..8
Context
show>system>security>tls
Description
This command displays information about TLS certificate profiles.
Parameters
- name
-
the name of a certificate profile for which to display information
- association
- displays TLS client profiles that are associated with the certificate profile
- 1..8
-
- Values
-
1 to 8
Output
The following outputs are examples of client certificate profile information.
Output example*A:7705# show system security tls cert-profile
===============================================================================
Certificate Profile
===============================================================================
Certificate Profile Name AdminState OperState OperFlags
-------------------------------------------------------------------------------
certProfile1 up up
===============================================================================
A:7705# show system security tls cert-profile "certProfile1"
===============================================================================
Certificate Profile Entry "certProfile1"
===============================================================================
Id Certificate File Name Key File Name Status Flags
-------------------------------------------------------------------------------
1 sarcert1 sarkey1
===============================================================================
*A:7705# show system security tls cert-profile "certProfile1" entry 1
===============================================================================
TLS Certificate Profile: "certProfile1" Entry: 1 Detail
===============================================================================
Certificate File : sarcert1
Key File : sarkey1
Status Flags : (Not Specified)
===============================================================================
*A:7705# show system security tls cert-profile "certProfile1" association
===============================================================================
TLS Client Profiles using cert-profile "certProfile1"
===============================================================================
TLS Client Profile Name
-------------------------------------------------------------------------------
tlsClientProfile
-------------------------------------------------------------------------------
Number of TLS Client Profile entries: 1
===============================================================================
client-tls-profile
Syntax
client-tls-profile [client-tls-profile]
client-tls-profile client-tls-profile association
client-tls-profile client-tls-profile [connections]
Context
show>system>security>tls
Description
This command displays TLS client profile information.
Parameters
- client-tls-profile
-
the name of the client TLS profile
- association
- displays TLS certificate profiles that are associated with the TLS client profile
- connections
- displays active TLS connections using the TLS client profile
Output
The following outputs are examples of TLS client profile information.
Output example*A:7705# show system security tls client-tls-profile "tlsClientProfile"
===============================================================================
Client Profile Entry "tlsClientProfile"
===============================================================================
Cipher List Name : tlsClientCipherList
Certificate Profile Name : certProfile1
Trust Anchor Profile Name : trustAnchorProfile1
===============================================================================
A:7705:Dut-A# show system security tls client-tls-profile "tlsClientProfile" connections
===============================================================================
Active TLS connections using client-tls-profile "tlsClientProfile"
===============================================================================
Cipher Client Signature Server Signature
Matched Trust Anchor Server IP
-------------------------------------------------------------------------------
Pcep
1 AES_128_CCM_8_SHA256 RSASSA-PSS-SHA256 RSASSA-PSS-SHA256
rootCA 10.20.1.4:4189
-------------------------------------------------------------------------------
Number of TLS connections: 1
===============================================================================
trust-anchor-profile
Syntax
trust-anchor-profile trust-anchor-profile association
trust-anchor-profile [trust-anchor-profile]
Context
show>system>security>tls
Description
This command displays information about TLS client profiles that are using the specified TLS trust anchor profile.
Parameters
- trust-anchor-profile
-
specifies the trust anchor profile, up to 32 characters
- association
-
displays TLS profiles that are associated with the trust anchor profile
Output
The following outputs are examples of trust anchor profile information.
Output example*A:7705# show system security tls trust-anchor-profile
===============================================================================
Trust Anchor Profile Information
===============================================================================
Name CA Profiles Down
-------------------------------------------------------------------------------
trustAnchorProfile1 0
===============================================================================*A:7705# show system security tls trust-anchor-profile "trustAnchorProfile1"
===============================================================================
CA-profile List for Trust Anchor "trustAnchorProfile1"
===============================================================================
CA Profile Name AdminState OperState
-------------------------------------------------------------------------------
rootCA up up
===============================================================================
*A:7705:Dut-A# show system security tls trust-anchor-profile "trustAnchorProfile1" association
===============================================================================
TLS Client Profiles using trust-anchor-profile trustAnchorProfile1
===============================================================================
TLS Client Profile Name
-------------------------------------------------------------------------------
tlsClientProfile
-------------------------------------------------------------------------------
Number of TLS Client Profile entries: 1
===============================================================================user
Syntax
user [user-id] [detail]
user [user-id] lockout
Context
show>system>security
Description
This command displays user registration and security information. You can clear lockouts for users with the lockout command.
If no command line options are specified, summary information for all users displays.
Parameters
- user-id
displays information for the specified user
- detail
displays detailed user information to the summary output
- lockout
displays information about users that are currently locked out for too many failed login attempts
Output
The following output is an example of user information, and User field descriptions describes the fields.
*A:7705:Dut-C>config>system>security# show system security user "test" detail
===============================================================================
Users
===============================================================================
User ID New Access Password Login Failed Local
Pwd Permissions Expires Attempt Logins Conf
-------------------------------------------------------------------------------
test n -- -- -- -- -- -- -- -- sc -- never 0 0 y
-------------------------------------------------------------------------------
Number of users : 1
Permissions: (bt) Bluetooth, (cc) Console port CLI, (fp) FTP, (gc) gRPC,
(li) LI, (nc) NETCONF, (sp) SCP/SFTP, (sn) SNMP, (sc) SSH CLI,
(tc) Telnet CLI
===============================================================================
===============================================================================
User Configuration Detail
===============================================================================
===============================================================================
user id : test
-------------------------------------------------------------------------------
console parameters
-------------------------------------------------------------------------------
new pw required : no cannot change pw : no
home directory :
restricted to home : yes
save when restrict*: yes
login exec file :
profile : default
locked-out : no
-------------------------------------------------------------------------------
snmp parameters
-------------------------------------------------------------------------------
===============================================================================
* indicates that the corresponding row element may have been truncated.
*A:7705:Dut-C>config>system>security#ALU-7# show system security user lockout
===============================================================================
Currently Failed Login Attempts
===============================================================================
User ID Remaining Login attempts Remaining Lockout Time (min:sec)
-------------------------------------------------------------------------------
jason123 N/A 9:56
-------------------------------------------------------------------------------
Number of users : 1
===============================================================================
|
Label |
Description |
|---|---|
|
Users |
|
|
User ID |
The name of a system user |
|
New Pwd |
Indicates whether the user must change their password at the next login: y or n |
|
Access Permissions |
bt Indicates whether the user is authorized for Bluetooth access (not supported on the 7705 SAR and always displays "--") |
|
cc Indicates whether the user is authorized for console port CLI access |
|
|
fp Indicates whether the user is authorized for FTP access |
|
|
gc Indicates whether the user is authorized for gRPC access (not supported on the 7705 SAR and always displays "--") |
|
|
li Indicates whether the user is authorized for lawful intercept (LI) access (not supported on the 7705 SAR and always displays "--") |
|
|
nc Indicates whether the user is authorized for NETCONF access (not supported on the 7705 SAR and always displays "--") |
|
|
sp Indicates whether the user is authorized for SCP/SFTP access |
|
|
sn Indicates whether the user is authorized for SNMP access |
|
|
sc Indicates whether the user is authorized for SSH CLI access |
|
|
tc Indicates whether the user is authorized for Telnet CLI access |
|
|
Password Expires |
The number of days the user has left before they must change their login password |
|
Login Attempt |
The number of times the user has attempted to log in regardless of whether the login succeeded or failed |
|
Failed Logins |
The number of unsuccessful login attempts |
|
Local Conf |
Indicates whether password authentication is based on the local password database: y or n |
|
Number of users |
The total number of listed users |
|
User Configuration Detail |
|
|
console parameters |
|
|
new pw required |
Indicates whether the user must change their password at the next login: yes or no |
|
cannot change pw |
Indicates whether the user is prevented from changing their password: yes or no |
|
home directory |
The local home directory for the user for both console and FTP access |
|
restricted to home |
Indicates whether the user is restricted from navigating to a directory higher in the directory tree on the home directory device: yes or no |
| save when restricted | Indicates whether configuration save operations are allowed when the user is restricted to home: yes or no |
|
login exec file |
The user’s login exec file, which executes whenever the user successfully logs in to a console session |
|
profile |
The security profiles associated with the user |
|
locked-out |
Indicates whether the user is locked out, and if they are locked out, how much time remains before the user can attempt to log in to the node again |
|
snmp parameters |
|
|
auth protocol |
The SNMPv3 authentication protocol |
|
auth key |
The SNMPv3 authentication key |
|
privacy protocol |
The SNMPv3 privacy protocol |
|
privacy key |
The SNMPv3 privacy key |
|
group |
The group to which the protocols apply |
|
Currently Failed Login Attempts |
|
|
Remaining Login attempts |
The number of login attempts remaining before the user is locked out |
|
Remaining Lockout Time (min:sec) |
The time remaining before the lockout time expires and the user can attempt another login |
With the support of PKI on the 7705 SAR as an SSH server, the authentication process can be done via PKI or password. SSH clients usually authenticate via PKI and password if PKI is configured on the client. In this case, PKI takes precedence over password authentication in most clients.
All client authentications are logged and displayed in the show>system>security>user detail output. The following table shows the rules where pass and fail attempts are logged.
|
Authentication order |
Client (for example, PuTTY) |
Server (for example, 7705 SAR) |
CLI show system security attempts |
||
|---|---|---|---|---|---|
|
Private key programmed |
Public key configured |
Password configured |
Login attempts |
Failed logins |
|
|
1. Public key 2. Password |
Yes |
Yes |
N/A |
Increment |
— |
|
Yes |
Yes (if no match between client and server, go to password) |
Yes |
Increment |
— |
|
|
Yes |
No |
Yes |
Increment |
— |
|
|
No |
N/A |
Yes |
Increment |
— |
|
|
No |
N/A |
No |
— |
Increment |
|
|
1. Public key (only) |
Yes |
Yes |
N/A |
Increment |
— |
|
Yes |
Yes (if no match between client and server, go to password) |
N/A |
— |
Increment |
|
|
Yes |
No |
N/A |
— |
Increment |
|
|
No |
N/A |
N/A |
— |
Increment |
|
view
Syntax
view [view-name] [detail] [capabilities]
Context
show>system>security
Description
This command displays one or all views and permissions in the MIB-OID tree.
Parameters
- view-name
specifies the name of the view to display. If no view name is specified, the complete list of views displays.
- detail
displays detailed view information
Output
The following output is an example of view information, and View field descriptions describes the fields.
Output exampleA:ALU-48# show system security view
===============================================================================
Views
===============================================================================
view name oid tree mask permission
-------------------------------------------------------------------------------
iso 1 included
read1 1.1.1.1 11111111 included
write1 2.2.2.2 11111111 included
testview 1 11111111 included
testview 1.3.6.1.2 11111111 excluded
mgmt-view 1.3.6.1.2.1.2 included
mgmt-view 1.3.6.1.2.1.4 included
mgmt-view 1.3.6.1.2.1.5 included
mgmt-view 1.3.6.1.2.1.6 included
mgmt-view 1.3.6.1.2.1.31 included
mgmt-view 1.3.6.1.2.1.77 included
mgmt-view 1.3.6.1.4.1.6527.3.1.2.3.7 included
mgmt-view 1.3.6.1.4.1.6527.3.1.2.3.11 included
vprn-view 1.3.6.1.2.1.2 included
vprn-view 1.3.6.1.2.1.4 included
vprn-view 1.3.6.1.2.1.5 included
vprn-view 1.3.6.1.2.1.6 included
vprn-view 1.3.6.1.2.1.7 included
vprn-view 1.3.6.1.2.1.23 included
vprn-view 1.3.6.1.2.1.31 included
vprn-view 1.3.6.1.2.1.77 included
vprn-view 1.3.6.1.4.1.6527.3.1.2.3.7 included
vprn-view 1.3.6.1.4.1.6527.3.1.2.3.11 included
vprn-view 1.3.6.1.4.1.6527.3.1.2.20.1 included
no-security 1 included
no-security 1.3.6.1.6.3 excluded
no-security 1.3.6.1.6.3.10.2.1 included
no-security 1.3.6.1.6.3.11.2.1 included
no-security 1.3.6.1.6.3.15.1.1 included
on-security 2 00000000 included
-------------------------------------------------------------------------------
No. of Views: 30
===============================================================================
A:ALU-48#
Label |
Description |
|---|---|
view name |
The name of the view. Views control the accessibility of a MIB object within the configured MIB view and subtree |
oid tree |
The object identifier of the ASN.1 subtree |
mask |
The bit mask that defines a family of view subtrees |
permission |
Indicates whether each view is included or excluded |
No. of Views |
The total number of views |
Login control show commands
users
Syntax
users
Context
show
Description
This command displays console user login and connection information.
Output
The following output is an example of user login information, and Users field descriptions describes the fields.
Output example*A:7705:Dut-C# show users
===============================================================================
Username Type
From
Router instance
Connection ID Login time
Session ID SSH Channel ID Idle time
===============================================================================
Console
--
--
6 --
6 -- 0d 07:11:00 --
-------------------------------------------------------------------------------
admin Telnet
192.168.192.29
management
16 28SEP2023 21:03:11
#20 -- 0d 00:00:00 --
-------------------------------------------------------------------------------
admin Telnet
192.168.192.30
management
12 28SEP2023 16:58:33
14 -- 0d 04:40:43 --
-------------------------------------------------------------------------------
admin SSHv2
192.168.192.29
management
14 28SEP2023 20:29:54
16 0 0d 00:00:25 --
17 1 0d 00:17:59 --
18 2 0d 01:17:08 --
-------------------------------------------------------------------------------
admin SSHv2
192.168.192.29
management
17 --
21 0 0d 00:11:18 --
-------------------------------------------------------------------------------
admin FTP
192.168.192.29
management
18 28SEP2023 21:46:59
22 -- 0d 00:00:04 --
-------------------------------------------------------------------------------
Number of users: 5
Number of sessions: 7
'#' indicates the current active session
===============================================================================
*A:7705:Dut-C#
|
Label |
Description |
|---|---|
|
Username |
The name of the user |
|
Type |
The type of connection: console, Telnet, FTP, SFTP, SSH, or MCT The console session is always displayed but does not count against the number of sessions unless a user is logged in at the console. If no one is logged in at the console, the Username field is blank. |
|
From |
The originating IP address |
| Router instance | The routing instance used to establish the connection, either management or base |
| Connection ID | The identifier for the connection |
|
Login time |
The time the user logged in |
| Session ID | The identifier for the session |
| SSH Channel ID | The SSH channel identifier |
|
Idle time |
The amount of idle time for a specific login |
|
Number of users |
The total number of users logged in |
| Number of sessions | The total number of sessions across all FTP, SFTP, SSH, Telnet, and MCT connections |
Clear commands
lockout
Syntax
lockout all
lockout user user-name
Context
admin>clear
Description
This command clears a security lockout for a specific user, or for all users, after they have been locked out for failing too many login attempts.
Parameters
- all
-
clears lockouts for all users
- name
-
specifies a username
password-history
Syntax
password-history all
password-history user user-name
Context
admin>clear
Description
This command clears old passwords for a specific user or for all users.
Parameters
- all
-
clears password history for all users
- name
-
specifies a username
statistics
Syntax
statistics [interface ip-int-name | ip-address]
Context
clear>router>authentication
Description
This command clears authentication statistics.
Parameters
- ip-int-name
-
clears the authentication statistics for the specified interface name. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
- ip-address
-
clears the authentication statistics for the specified IP address
Monitor commands
cpm-filter
Syntax
cpm-filter
Context
monitor
Description
This command displays monitor command output for CPM filters.
management-access-filter
Syntax
management-access-filter
Context
monitor
Description
This command enables the context to monitor management access filters.
ip
Syntax
ip entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>cpm-filter
monitor>management-access-filter
Description
This command enables IP filter monitoring. The statistical information for the specified IP filter entry is displayed at the configured interval until the configured count is reached.
The first screen displays the current statistics related to the specified IP filter. The subsequent statistical information listed for each interval is displayed as a delta to the previous screen output.
When the keyword rate is specified, the rate per second for each statistic is displayed instead of the delta.
Monitor commands are similar to show commands, but only statistical information is displayed. Monitor commands display the selected statistics according to the configured number of times at the interval specified.
Parameters
- entry-id
displays information for the specified filter entry ID
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
displays raw statistics, without processing. No calculations are performed on the delta or rate statistics.
- rate
displays the rate per second for each statistic instead of the delta
ipv6
Syntax
ipv6 entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>cpm-filter
monitor>management-access-filter
Description
This command enables IPv6 filter monitoring. The statistical information for the specified IPv6 filter entry is displayed at the configured interval until the configured count is reached.
The first screen displays the current statistics related to the specified IPv6 filter. The subsequent statistical information listed for each interval is displayed as a delta to the previous screen output.
When the keyword rate is specified, the rate per second for each statistic is displayed instead of the delta.
Monitor commands are similar to show commands, but only statistical information is displayed. Monitor commands display the selected statistics according to the configured number of times at the interval specified.
Parameters
- entry-id
displays information for the specified filter entry ID
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
displays raw statistics, without processing. No calculations are performed on the delta or rate statistics.
- rate
displays the rate per second for each statistic instead of the delta
mac
Syntax
mac entry entry-id [interval seconds] [repeat repeat] [absolute | rate]
Context
monitor>cpm-filter
monitor>management-access-filter
Description
This command enables MAC filter monitoring. The statistical information for the specified MAC filter entry is displayed at the configured interval until the configured count is reached.
The first screen displays the current statistics related to the specified MAC filter. The subsequent statistical information listed for each interval is displayed as a delta to the previous screen output.
When the keyword rate is specified, the rate per second for each statistic is displayed instead of the delta.
Monitor commands are similar to show commands, but only statistical information is displayed. Monitor commands display the selected statistics according to the configured number of times at the interval specified.
Parameters
- entry-id
displays information for the specified filter entry ID
- seconds
configures the interval for each display in seconds
- repeat
configures how many times the command is repeated
- absolute
displays raw statistics, without processing. No calculations are performed on the delta or rate statistics.
- rate
displays the rate per second for each statistic instead of the delta
Debug commands
radius
Syntax
radius [detail] [hex]
no radius
Context
debug
Description
This command enables debugging for RADIUS connections.
The no form of the command disables the debugging.
Parameters
- detail
-
displays detailed output
- hex
-
displays the packet dump in hexadecimal format