Security
This chapter provides information to configure security parameters.
Authentication, authorization, and accounting
This chapter describes authentication, authorization, and accounting (AAA) used to monitor and control network access on 7210 SAS routers. Network security is based on a multi-step process. The first step, authentication, validates a username and password. The second step is authorization, which allows the user to access and execute commands at various command levels based on profiles assigned to the user.
Another step, accounting, keeps track of the activity of a user who has accessed the network. The type of accounting information recorded can include a history of the commands executed, the amount of time spent in the session, the services accessed, and the data transfer size during the session. The accounting data can then be used to analyze trends, and also for billing and auditing purposes.
You can configure 7210 SAS routers to use local, Remote Authentication Dial In User Service (RADIUS), or Terminal Access Controller Access Control System Plus (TACACS+) security to validate users who attempt to access the router by console, Telnet, or FTP. You can select the authentication order which determines the authentication method to try first, second, and third.
The 7210 SAS supports the following security features:
RADIUS can be used for authentication, authorization, and accounting.
TACACS+ can be used for authentication, authorization, and accounting.
Local security can be implemented for authentication and authorization.
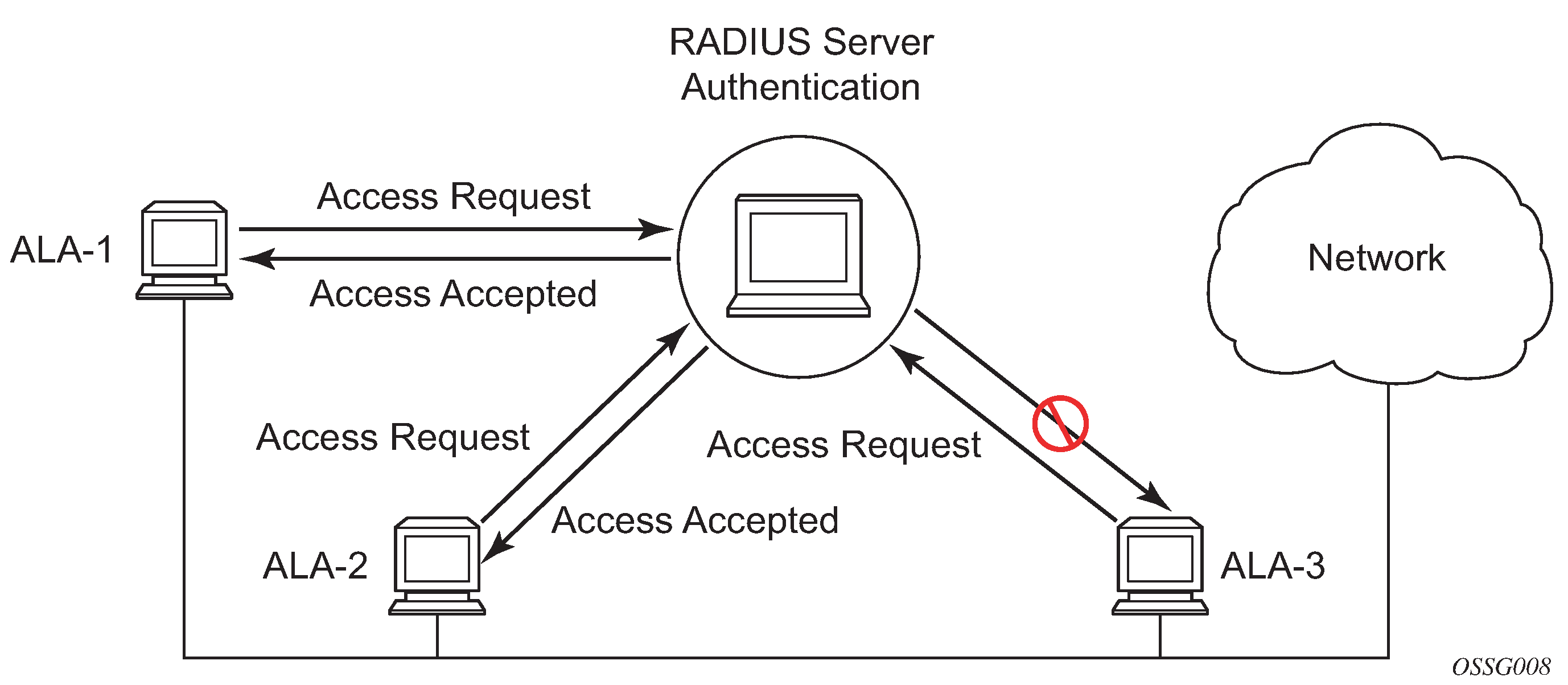
The following figure shows how end user access-requests are sent to a RADIUS server. After validating the usernames and passwords, the RADIUS server returns an access-accept message to the users on ALA-1 and ALA-2. The username and password from ALA-3 could not be authenticated, therefore access was denied.
Authentication
Authentication validates a username and password combination when a user attempts to log in.
When a user attempts to log in through the console, Telnet, SSH, SCP, or FTP, the 7210 SAS client sends an access request to a RADIUS, TACACS+, or local database.
Transactions between the client and a RADIUS server are authenticated through the use of a shared secret. The secret is never transmitted over the network. User passwords are sent encrypted between the client and RADIUS server which prevents someone snooping on an insecure network to learn password information.
If the RADIUS server does not respond within a specified time, the router issues the access request to the next configured servers. Each RADIUS server must be configured identically to guarantee consistent results.
If any RADIUS server rejects the authentication request, it sends an access reject message to the router. In this case, no access request is issued to any other RADIUS servers. However, if other authentication methods such as TACACS+ and/or local are configured, then these methods are attempted. If no other authentication methods are configured, or all methods reject the authentication request, then access is denied.
For the RADIUS server selection, round-robin is used if multiple RADIUS servers are configured. Although, if the first alive server in the list cannot find a user-name, the router does not query the next server in the RADIUS server list and denies the access request. It may get authenticated on the next login attempt if the next selected RADIUS server has the appropriate user-name. Nokia recommends that the same user databases be maintained for RADIUS servers to avoid inconsistent behavior.
The user login is successful when the RADIUS server accepts the authentication request and responds to the router with an access accept message.
Implementing authentication without authorization for the 7210 SAS-Series routers does not require the configuration of VSAs (Vendor Specific Attributes) on the RADIUS server. However, users, user access permissions, and command authorization profiles must be configured on each router.
Any combination of the following authentication methods can be configured to control network access from a 7210 SAS-Series router.
Local authentication
Local authentication uses usernames and passwords to authenticate login attempts. The usernames and passwords are local to each router not to user profiles.
By default, local authentication is enabled. When one or more of the other security methods are enabled, local authentication is disabled. Local authentication is restored when the other authentication methods are disabled. Local authentication is attempted if the other authentication methods fail and local is included in the authentication order password parameters.
Locally, you can configure usernames and password management information. This is referred to as local authentication. Remote security servers such as RADIUS or TACACS+, are not enabled.
RADIUS authentication
Remote Authentication Dial-In User Service (RADIUS) is a client/server security protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize access to the requested system or service.
RADIUS allows you to maintain user profiles in a shared central database and provides better security, allowing a company to set up a policy that can be applied at a single administered network point.
RADIUS server selection
The RADIUS server selection algorithm is used by different applications:
RADIUS operator management
RADIUS authentication for Enhanced Subscriber Management
RADIUS accounting for Enhanced Subscriber Management
RADIUS PE-discovery
Up to 5 RADIUS servers pools (per RADIUS policy, if used) can be configured.
The RADIUS server selection algorithm works in Direct mode.
Direct mode
The first server is used as the primary server. If this server is unreachable, the next server, based on the server index, of the server pool is used. This continues until either all servers in the pool have been tried or an answer is received.
If a server is unreachable, it will not be used again by the RADIUS application for the next 30 seconds to allow the server to recover from its unreachable state. After 30 seconds the unreachable server is available again for the RADIUS application. If in these 30 seconds the RADIUS application receives a valid response for a previously sent RADIUS packet on that unreachable server, the server will be available for the RADIUS application again, immediately after reception of that response.
Server reachability detection
A server is reachable, when the operational state UP, when a valid response is received within a timeout period which is configurable by the retry parameter on the RADIUS policy level.
A server is treated as not-reachable, when the operational state down, when the following occurs:
a timeout
If a number of consecutive timeouts are encountered for a specific server. This number is configurable by the retry parameter on RADIUS policy level.
a send failed
If a packet cannot be sent to the RADIUS server because the forwarding path toward the RADIUS server is broken (for example, the route is not available, the is interface shutdown, and so on), no retry mechanism is invoked and immediately, the next server in line is used.
A server that is down can only be used again by the RADIUS algorithm after 30 seconds, unless, during these 30 seconds a valid RADIUS reply is received for that server. Then, the server is immediately marked UP again.
The operational state of a server can also be ‟unknown” if the RADIUS application is not aware of the state of the RADIUS server (for example, if the server was previously down but no requests had been sent to the server, therefore, it is not certain yet whether the server is actually reachable).
Application-specific behavior
-
Operator Management
The server access mode is fixed to Round-Robin (Direct cannot be configured for operator management). A health-check function is available for operator management, which can optionally be disabled. The health-check polls the server once every 10 seconds with an improbable username. If the server does not respond to this health-check, it will be marked down.
If the first server in the list cannot find a user, the next server in the RADIUS server list is not queried and access is denied. If multiple RADIUS servers are used, it is assumed they all have the same user database.
-
RADIUS Authentication
If the first server in the list cannot find a user, the next server in the RADIUS server list is not queried and access is denied. If multiple RADIUS servers are used, it is assumed they all have the same user database.
-
RADIUS Accounting
The RADIUS accounting application will try to send all the concerned packets of a subscriber host to the same server. If that server is down, then the packet is sent to the next server and, from that moment on, the RADIUS application uses that server to send its packets for that subscriber host.
-
RADIUS PE-Discovery
If the first server in the list cannot find a user, the next server in the RADIUS server list is not queried and access is denied. If multiple RADIUS servers are used, it is assumed they all have the same user database.
The RADIUS PE-discovery application makes use of a 10 second time period instead of the generic 30 seconds and uses a fixed consecutive timeout value of 2 (see Server reachability detection).
As long as the Session-Timeout (attribute in the RADIUS user file) is specified, it is used for the polling interval. Otherwise, the configured polling interval will be used (60 seconds by default).
TACACS+ authentication
Terminal Access Controller Access Control System, commonly referred to as TACACS is an authentication protocol that allows a remote access server to forward a user's log on password to an authentication server to determine whether access can be allowed to a specific system. TACACS is an encryption protocol and therefore less secure than the later Terminal Access Controller Access Control System Plus (TACACS+) and RADIUS protocols.
TACACS+ and RADIUS have largely replaced earlier protocols in the newer or recently updated networks. TACACS+ uses Transmission Control Protocol (TCP) and RADIUS uses the User Datagram Protocol (UDP). TACACS+ is popular as TCP is thought to be a more reliable protocol. RADIUS combines authentication and authorization. TACACS+ separates these operations.
Password hashing
The 7210 SAS supports two algorithms for user password hashing: bcrypt, which is the default algorithm, and PBKDF2. The PBKDF2 algorithm can use SHA2 (SHA-256) for hashing.
The password hashing algorithm can be configured using the configure system security password hashing command. The configured algorithm hashes all user passwords.
When password hashing is configured, the following sequence of steps occurs at login:
The node checks the stored password and notes its hash algorithm.
The password entered by the user is hashed with the noted algorithm, and the node compares the hash with the stored user password hash.
If the entered and stored passwords are the same, and if the hash algorithm of the stored user password is different than the hash algorithm of the system password, the user is prompted to enter a new password two times to ensure password match. The node stores this new password in the RAM (not in the system configuration file).
To store the new password in the configuration file, an admin user must perform the admin save command. If the admin save command is not executed, on the next reboot the hash algorithm of the stored user password may be different than the system hash, and the user must go through this process again from step 2.
After an upgrade to a software load that supports PBKDF2, the default password continues to be stored using the bcrypt algorithm. The following example describes the procedure to change the algorithm. In this example, the algorithm is changed to PBKDF2, and ‟User_name” can be any user.
User_name logs in and runs the hashing command to change the algorithm.
To save the algorithm change, an admin user performs an admin save command.
To store User_name’s password using PBKDF2, the admin user changes User_name’s password.
From this point onward, any new user passwords or changes to existing user passwords are stored using PBKDF2.
Local user profiles
Administrators can configure local user profiles for command authorization and assign the least privileges for different types of network operators. Profiles provide all users with separate user accounts and different levels of command authorization based on user requirements. Profiles typically map to organization support levels.
Local user profile with read-only command authorization
A:node-2>config>system>security# info
----------------------------------------------
profile "read-only"
default-action deny-all
entry 10
match "back"
action permit
exit
entry 20
match "exit"
action permit
exit
entry 30
match "help"
action permit
exit
entry 40
match "history"
action permit
exit
entry 50
match "logout"
action permit
exit
entry 60
match "ping"
action permit
exit
entry 70
match "traceroute"
action permit
exit
entry 80
match "monitor"
action permit
exit
entry 90
match "show"
action permit
exit
entry 100
match "clear port <*> statistics"
action permit
exit
exit
----------------------------------------------User templates
User templates should be configured to control management access methods like the CLI and management protocols, and to assign least privileges for different types of network operators. All users should be provided different levels of access based on their requirements. Templates are applied to local users, and to remote users using the default template or with vendor-specific attributes (VSAs).
Template with access to the CLI on the console port and over SSH
Users configured with this template cannot copy files to the router or access management protocols.
A:node-2>config>system>security>user# info
access console-port-cli ssh-cliAuthorization
The OS support local, RADIUS, and TACACS+ authorization to control the actions of specific users by applying a profile based on username and password configurations when network access is granted. The profiles are configured locally as well as VSAs on the RADIUS server. See Vendor-specific attributes (VSAs).
When a user has been authenticated using RADIUS (or another method), the router can be configured to perform authorization. The RADIUS server can be used to:
download the user profile to the router
send the profile name that the node should apply to the router
Profiles consist of a suite of commands that the user is allowed or not allowed to execute. When a user issues a command, the authorization server looks at the command and the user information and compares it with the commands in the profile. If the user is authorized to issue the command, the command is executed. If the user is not authorized to issue the command, then the command is not executed.
Profiles must be created on each router and should be identical for consistent results. If the profile is not present, then access is denied.
Supported authorization configurations describes the following scenarios:
Remote (RADIUS) authorization cannot be performed if authentication is done locally (on the router).
The reverse scenario is supported if RADIUS authentication is successful and no authorization is configured for the user on the RADIUS server, then local (router) authorization is attempted, if configured in the authorization order.
When authorization is configured and profiles are downloaded to the router from the RADIUS server, the profiles are considered temporary configurations and are not saved when the user session terminates.
| User type | RADIUS supplied profile |
|---|---|
Configured user |
Not Supported |
RADIUS server configured user |
Supported |
TACACS+ server configured user |
Not Supported |
When using authorization, maintaining a user database on the router is not required. Usernames can be configured on the RADIUS server. Usernames are temporary and are not saved in the configuration when the user session terminates. Temporary user login names and their associated passwords are not saved as part of the configuration.
Local authorization
Local authorization uses user profiles and user access information after a user is authenticated. The profiles and user access information specifies the actions the user can and cannot perform.
By default, local authorization is enabled. Local authorization is disabled only when a different remote authorization method is configured (RADIUS authorization). Local authorization is restored when RADIUS authorization is disabled.
You must configure profile and user access information locally.
RADIUS authorization
RADIUS authorization grants or denies access permissions for a router. Permissions include the use of FTP, Telnet, SSH (SCP), and console access. When granting Telnet, SSH (SCP) and console access to the router, authorization can be used to limit what CLI commands the user is allowed to issue and which file systems the user is allowed or denied access.
TACACS+ authorization
Like RADIUS authorization, TACACS+ grants or denies access permissions for a router. The TACACS+ server sends a response based on the username and password.
TACACS+ separates the authentication, authorization, and accounting function. RADIUS combines the authentication and authorization functions.
Accounting
When enabled, RADIUS accounting sends command line accounting from the router to the RADIUS server. The router sends accounting records using UDP packets at port 1813 (decimal).
The router issues an accounting request packet for each event requiring the activity to be recorded by the RADIUS server. The RADIUS server acknowledges each accounting request by sending an accounting response after it has processed the accounting request. If no response is received in the time defined in the timeout parameter, the accounting request must be retransmitted until the configured retry count is exhausted. A trap is issued to alert the NMS (or trap receiver) that the server is unresponsive. The router issues the accounting request to the next configured RADIUS server (up to 5).
User passwords and authentication keys of any type are never transmitted as part of the accounting request.
RADIUS accounting
Accounting tracks user activity to a specified host. When RADIUS accounting is enabled, the server is responsible for receiving accounting requests and returning a response to the client indicating that it has successfully received the request. Each command issued on the router generates a record sent to the RADIUS server. The record identifies the user who issued the command and the timestamp.
Accounting can be configured independently from RADIUS authorization and RADIUS authentication.
TACACS+ accounting
The OS allows you to configure the type of accounting record packet that is to be sent to the TACACS+ server when specified events occur on the device. The accounting record-type parameter indicates whether TACACS+ accounting start and stop packets be sent or just stop packets be sent. Start/stop messages are only sent for individual commands, not for the session.
When a user logs in to request access to the network using Telnet or SSH, or a user enters a command for which accounting parameters are configured, or a system event occurs, such as a reboot or a configuration file reload, the router checks the configuration to see if TACACS+ accounting is required for the particular event.
If TACACS+ accounting is required, then, depending on the accounting record type specified, sends a start packet to the TACACS+ accounting server which contains information about the event.
The TACACS+ accounting server acknowledges the start packet and records information about the event. When the event ends, the device sends a stop packet. The stop packet is acknowledged by the TACACS+ accounting server.
Security controls
You can configure routers to use RADIUS, TACACS+, and local authentication to validate users requesting access to the network. The order in which password authentication is processed among RADIUS, TACACS+ and local passwords can be specifically configured. That is, the authentication order can be configured to process authorization through TACACS+ first, then RADIUS for authentication and accounting. Local access can be specified next in the authentication order in the event that the RADIUS and TACACS+ servers are not operational.
The following table lists the types of security supported by each protocol.
| Method | Authentication | Authorization | Accounting 1 |
|---|---|---|---|
Local |
Y |
Y |
N |
TACACS+ |
Y |
Y |
Y |
RADIUS |
Y |
Y |
Y |
When a server does not respond
A trap is issued if a RADIUS + server is unresponsive. An alarm is raised if RADIUS is enabled with at least one RADIUS server and no response is received to either accounting or user access requests from any server.
Periodic checks to determine whether the primary server is responsive again are not performed. If a server is down, it will not be contacted for 5 minutes. If a login is attempted after 5 minutes, then the server is contacted again. When a server does not respond with the health check feature enabled, the server status is checked every 30 seconds. Health check is enabled by default. When a service response is restored from at least one server, the alarm condition is cleared. Alarms are raised and cleared on the Nokia Fault Manager or other third party fault management servers.
The servers are accessed in order from lowest to highest specified index (from 1 to 5) for authentication requests until a response from a server is received. A higher indexed server is only queried if no response is received, implying a lower indexed server is not available. If a response from the server is received, no other server is queried.
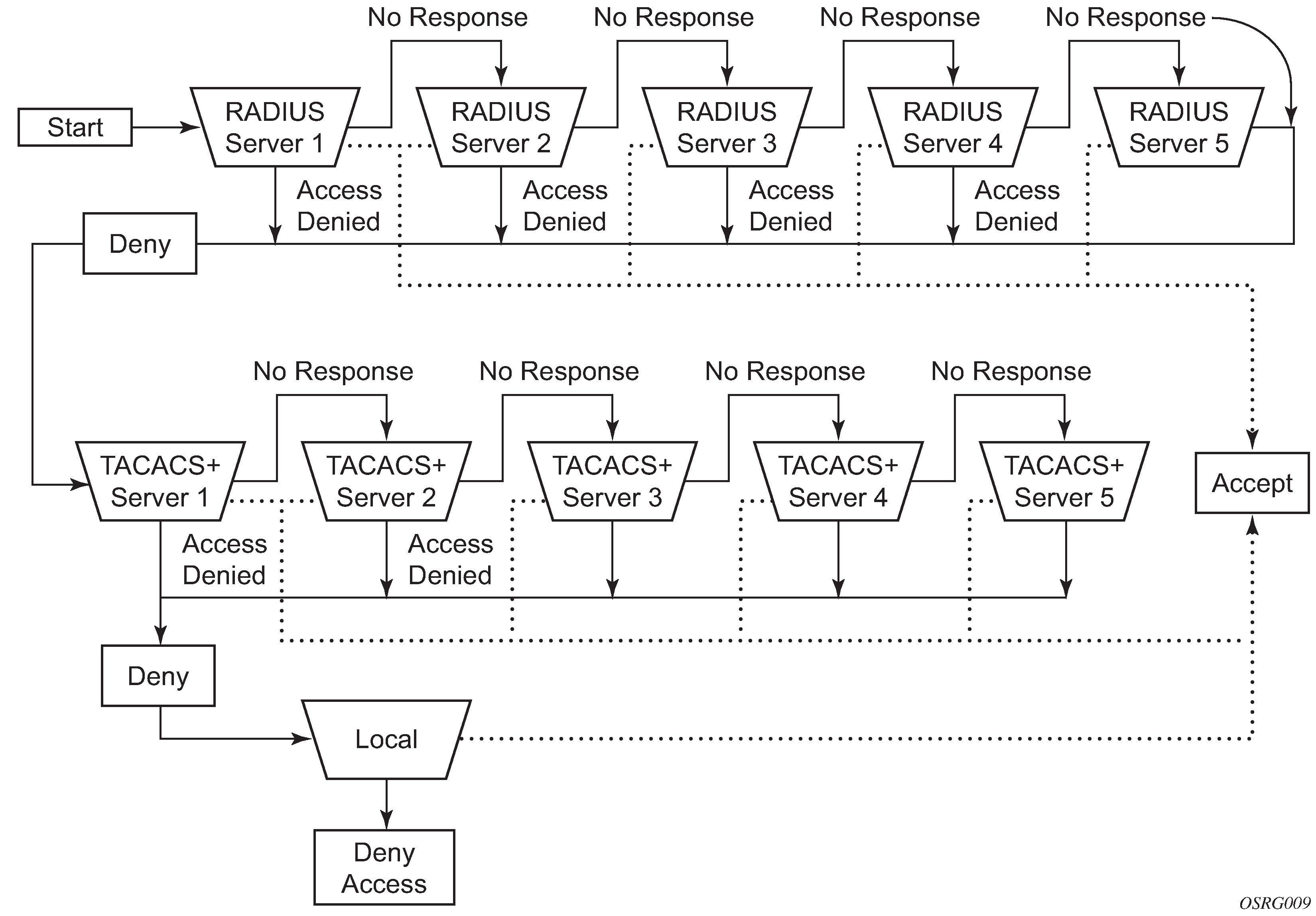
Access request flow
In Security flow, the authentication process is defined in the config>system>security> password context. The authentication order is determined by specifying the sequence in which password authentication is attempted among RADIUS, TACACS+, and local passwords. This example uses the authentication order of RADIUS, then TACACS+, and finally, local. An access request is sent to RADIUS server 1. One of two scenarios can occur. If there is no response from the server, the request is passed to the next RADIUS server with the next lowest index (RADIUS server 2) and so on, until the last RADIUS server is attempted (RADIUS server 5). If server 5 does not respond, the request is passed to the TACACS+ server 1. If there is no response from that server, the request is passed to the next TACACS+ server with the next lowest index (TACACS+ server 2) and so on.
If a request is sent to an active RADIUS server and the username and password is not recognized, access is denied and passed on to the next authentication option, in this case, the TACACS+ server. The process continues until the request is either accepted, denied, or each server is queried. Finally, if the request is denied by the active TACACS+ server, the local parameters are checked for username and password verification. This is the last chance for the access request to be accepted.
Control and management traffic protection
7210 SAS platforms support an extensive set of configurable mechanisms to protect the CPU from being flooded with control or management traffic.
These protection mechanisms are a set of configurable hardware-based filters, classification, queuing, and rate-limiting functions that drop unwanted traffic before it reaches the control processor:
In-band traffic extracted from line cards to the control processing module (CPM) on chassis-based systems, or extracted from front-panel ports on fixed form-factor devices:
Line card or fixed form-factor platform features:
ACLs filters: IPv4, IPv6, and MAC
Distributed CPU protection (supported only on the 7210 SAS-R6 and 7210 SAS-R12)
CPM features:
Centralized CPU protection
Out-band and in-band traffic: management access filters
CPM Management Access Filters
CPM traffic is extracted from the data plane and sent to the CPM for processing. Packets from all network and access ports can be filtered using management access filters, which use CPU resources. Packets originating from a management Ethernet port can also be filtered using management access filters.
CPM protocols and ports
Nokia recommends using a strict CPM management access filter policy allowing traffic from trusted IP subnets for protocols and ports actively used in the router and to explicitly drop other traffic.
The following table identifies the protocols and TCP/UDP ports used per application on 7210 SAS platforms. The source port and destination port reflect the CPM management access filter entry configuration for traffic ingressing the router and sent to the CPM.
| TCP/UDP port number | IP protocol | Application description | Protocols and ports available for in-band and out-of-band management on 7210 SAS platforms | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Source | Destination | SAS-T (network mode) | SAS-T (access-uplink mode) | SAS-MXP | SAS-R6 and SAS-R12 | SAS-Sx/S 1/10GE | SAS-Sx 10/100GE | ||||||||
| In-band | Out-of-band | In-band | Out-of-band | In-band | Out-of-band | In-band | Out-of-band | In-band | Out-of-band | In-band | Out-of-band | ||||
| BFD application | |||||||||||||||
3784 |
UDP |
BFD control 1 hop BFD |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
3785 |
UDP |
BFD echo |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
4784 |
UDP |
BFD control multi-hop |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
6784 |
UDP |
Micro-BFD |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
| BGP application | |||||||||||||||
179 |
TCP |
BGP: server terminated TCP sessions |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
179 |
TCP |
BGP: client responses for initiated TCP session |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
Cflowd application |
|||||||||||||||
1025 to 65535 |
UDP |
✓ |
✓ |
✓2 |
✓2 |
✓ |
✓ |
||||||||
| DHCPv4 application | |||||||||||||||
67 |
67 |
UDP |
DHCPv4: relay agent to server; server to relay agent; relay agent to relay agent |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||
68 |
67 |
UDP |
DHCPv4: client to relay agent; client to server |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||
67 |
68 |
UDP |
DHCPv4: relay agent to server; relay agent to client |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||
| DHCPv6 application | |||||||||||||||
546 |
547 |
UDP |
DHCPv6: client to server; client to relay agent |
✓ |
|||||||||||
547 |
546 |
UDP |
DHCPv6: server to relay agent; relay agent to server; relay agent to relay agent |
✓ |
|||||||||||
| DNS application | |||||||||||||||
53 |
UDP |
DNS Client |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| FTP application | |||||||||||||||
20 |
TCP |
FTP server data and active FTP client |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
21 |
TCP |
FTP server control |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
20 |
TCP |
FTP client data |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
21 |
TCP |
FTP client control |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| GRE application | |||||||||||||||
N/A |
N/A |
GRE |
GRE |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| ICMP application | |||||||||||||||
N/A |
N/A |
ICMP |
ICMP |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
| IGMP application | |||||||||||||||
N/A |
N/A |
IGMP |
IGMP |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||
| LDP application | |||||||||||||||
646 |
UDP |
LDP hello adjacency |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
646 |
TCP |
LDP/T-LDP: terminated TCP sessions |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
646 |
TCP |
LDP/T-LDP: responses for initiated TCP sessions |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
| MC-APS application | |||||||||||||||
1025 |
UDP |
Multi-chassis LAG |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| MCS application | |||||||||||||||
45067 |
TCP |
Multi-chassis synchronization: terminated TCP session |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
45067 |
TCP |
Multi-chassis synchronization: responses for initiated TCP session |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| NETCONF application | |||||||||||||||
830 |
TCP |
NETCONF |
✓ |
||||||||||||
| NTP application | |||||||||||||||
123 |
UDP |
NTP server |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
123 |
UDP |
NTP client |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| OAM application | |||||||||||||||
3503 |
UDP |
LSP ping |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
33408 to 33535 |
UDP |
OAM traceroute |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
| OSPF application | |||||||||||||||
N/A |
N/A |
OSPF |
OSPF |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| PCEP application | |||||||||||||||
4189 |
TCP |
Path Computation Element Protocol (PCEP) |
✓ |
✓ |
✓ |
✓ |
|||||||||
| PIM application | |||||||||||||||
3232 |
UDP |
PIM MDT |
✓ |
✓ |
✓ |
✓ |
✓ |
||||||||
N/A |
N/A |
PIM |
PIM |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| PTP application | |||||||||||||||
319 |
UDP |
1588 PTP event |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
320 |
UDP |
1588 PTP general |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| RADIUS application | |||||||||||||||
1812 |
UDP |
Radius authentication |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
1813 |
UDP |
Radius accounting |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| RIP application | |||||||||||||||
520 |
UDP |
RIP (only on SAS-Mxp) |
✓ |
||||||||||||
| RSVP application | |||||||||||||||
N/A |
N/A |
RSVP |
RSVP |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| SSH application | |||||||||||||||
22 |
TCP |
SSH server and terminated TCP session |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
22 |
TCP |
SSH client and responses for initiated TCP sessions |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| SNMP application | |||||||||||||||
161 |
UDP |
SNMP server; SET and GET commands |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| TACACS application | |||||||||||||||
49 |
TCP |
TACACS client and responses for initiated TCP sessions |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| TELNET application | |||||||||||||||
23 |
TCP |
TELNET server |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|
| TWAMP application | |||||||||||||||
862 |
TCP |
TWAMP control: terminated TCP session |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
Any |
UDP |
TWAMP test |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
1 to 65535 |
UDP |
TWAMP light (per router instance) |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
| VRRP application | |||||||||||||||
N/A |
N/A |
VRRP |
VRRP |
✓ |
✓ |
✓ |
✓ |
✓ |
|||||||
Management Access Filter
Management Access Filters (MAF) are software-based filters used to restrict traffic extracted from the data plane and restrict traffic from the management port to the CPU.
MAF packet match
Two different management-access-filter policies can be configured: ip-filter and ipv6-filter.
The following are the MAF packet match rules:
Each MAF policy is an ordered list of entries; therefore, entries must be sequenced correctly from the most to the least explicit.
If multiple match criteria are specified in a single MAF policy entry, all criteria must be met for the packet to be considered a match against that policy entry (logical AND).
Any match criteria not explicitly defined is ignored during a match.
A MAF filter policy entry defined without a match criteria is inactive.
A MAF filter policy entry with match criteria defined but no action configured inherits the default action defined at the management-access-filter level.
The management-access-filter default-action applies individually per IPv4 or IPv6 filter policies that are in a no shutdown state.
MAF IPv4/IPv6 filter entry match criteria
The following table lists the supported IPv4 and IPv6 match criteria.
Criteria |
Description |
|---|---|
dst-port |
Matches the specified port value against the destination port number of the UDP or TCP packet header. |
flow-label |
Matches the IPv6 flow label. |
fragment |
Matches fragmented or non-fragmented IP packet. |
next-header |
Matches the specified upper-layer protocol (such as TCP, UDP, or IGMPv6) against the next-header field of the IPv6 packet header. "*" can be used to specify a TCP or UDP upper-layer protocol match (logical OR). Next-header matching also allows matching on presence of a subset of IPv6 extension headers. See Management Access Filter commands for details about which extension header match is supported. |
l4-source-port |
Matches the specified port value against the L4 source port number of the UDP or TCP packet header. |
protocol |
Matches the specified protocol against the Protocol field in the IPv4 packet header (for example, TCP, UDP, or IGMP) of the outer IPv4. "*" can be used to specify TCP or UDP upper-layer protocol match (logical OR). |
router |
Matches the router instance that packets are ingressing from for this filter entry. |
src-ip |
Matches the specified source IPv4 or IPv6 address prefix and mask against the source IPv4 or IPv6 address field in the IP packet header. |
src-port |
Matches packets that are ingressing from this port. |
MAF policy action
MAFs allow actions to permit or deny (or use the deny-host-unreachable response for IP filters) traffic.
MAF policy statistics and logging
The management access filter match count can be displayed using show commands. Logging is recorded in the system security logs.
CPU protection modes
The 7210 SAS provides several rate limiting mechanisms to protect the CPM/CFM processing resources of the router:
Centralized CPU Protection: a centralized rate-limiting function that operates on the CPM to limit traffic destined to the CPUs. The CPU protection mechanism is not user-configurable. It is supported on all 7210 SAS platforms.
For historical reasons, the term ‟centralized CPU protection” is called ‟CPU protection” in this user guide.
Distributed CPU Protection (DCP): a control traffic rate-limiting protection mechanism for the CPM and CFM that operates on line cards. See DCP for more information about the DCP mechanism.
Centralized CPU protection
The CPU protection mechanism protects the CPU from a DoS attack by limiting the amount of ingress port traffic destined for the CPM to be processed by its CPU. On the 7210 SAS, a set of dedicated policers are used to limit the amount of traffic to the software-defined rate (the rate is not user-configurable) before the packets are queued to the CPU queues. A strict policy scheduler schedules packets from the CPU queues. A CPU queue traffic shaper, configured to a predefined rate by software, is used to limit the amount of traffic for a protocol or group of protocols using the CPU queue.
In most cases, access interfaces and network uplinks do not share the policers and CPU queues used to manage the amount of traffic sent to the CPM. Access interfaces (typically used to deliver customer services) use a dedicated set of policers and CPU queues; a separate set is used for network facing ports (that is, network ports, hybrid ports, and access-uplink ports). The policer rate and CPU queue rates used for CPU protection are not user-configurable.
DCP
DCP provides a powerful per-protocol-per-object rate-limiting function for control protocol traffic that is extracted from the datapath and sent to the CPM. See DCP applicability for a list of applicable objects. The DCP function is implemented on the router for granular control.
DCP provides the enforcement policers to configure policies that are applied to objects (for example, SAPs). An enforcement policer is an instance of a policer that is policing a flow of packets composed of a single protocol arriving on a single object (for example, SAP). Enforcement policers perform a configurable action, such as a discard, on packets that exceed the configured rate parameters. Static policers are the one type of enforcement policer supported on the 7210 SAS-R6 and 7210 SAS-R12, which are always instantiated if configured.
The following figure shows per-SAP per-protocol static rate limiting with DCP.
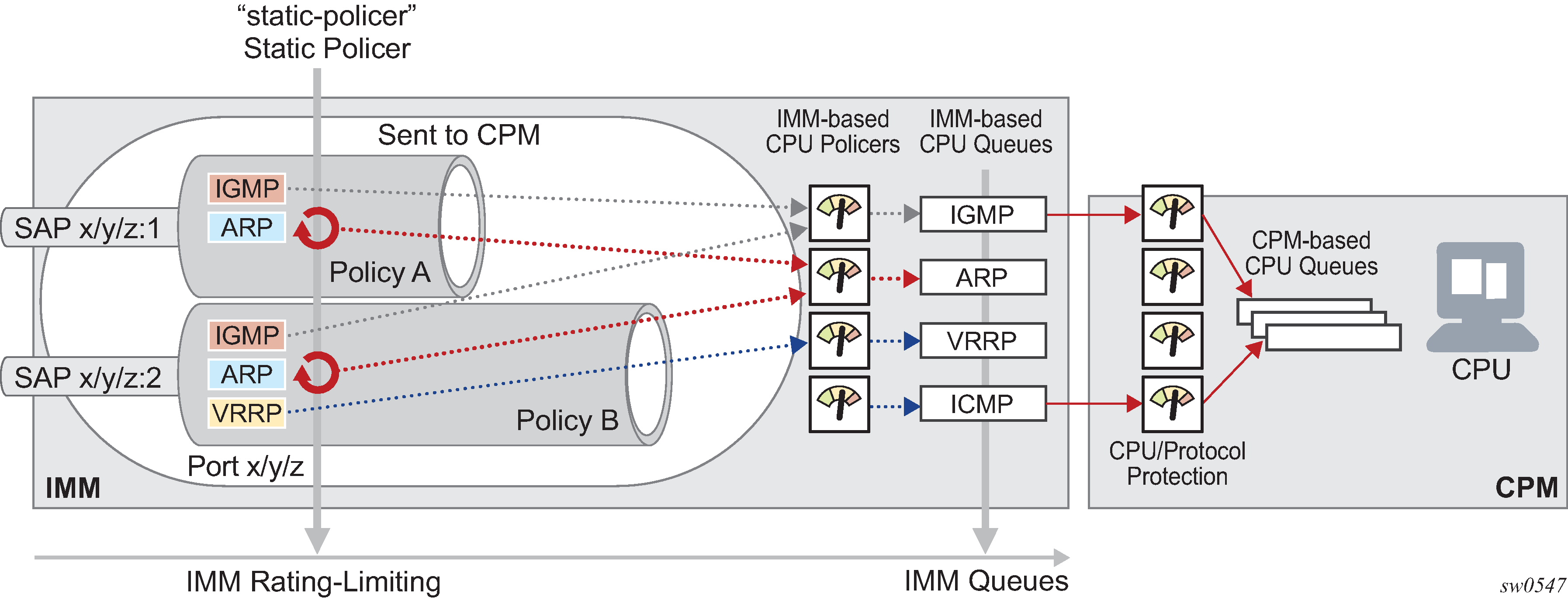
CPU policers and CPU queues on CPM and IMM are shown only for some protocols. on the 7210 SAS, all control traffic to the CPU is rate-limited using a policer per protocol or group of protocols. The CPU queues are further shaped to the system-defined rate. There are different policers and queues used for access ports and network ports to ensure that customer traffic does not affect critical network traffic. The rates for these CPU policers and queues are not configurable by the user.
DCP applicability
By default, the system does not associate a DCP policy with a SAP. The user must configure an explicit policy to enable DCP for a SAP for a supported protocol. Allocate resources for the DCP policy from the ingress internal TCAM resource pool by using the configure>system>resource-profile>ingress-internal-tcam>cpu-protection command. See the 7210 SAS-Mxp, R6, R12, S, Sx, T Basic System Configuration Guide for more information about this command.
The DCP functionality is not enabled on the service objects by default. Use the dist-cpu-protection command in the config>service context to enable the DCP functionality on service objects. The no form of the command disables the DCP functionality on service objects.
DCP policies can be applied to the following types of objects:
IES SAP
VPRN SAP
RVPLS SAP
For RVPLS, DCP rate-limits the packets arriving at the CPU, but for flooded traffic, ingress QoS or ACLs must be used.
Control packets that are extracted in an IES or a VPRN service, where the packets arrived into the node over a VPLS SAP (that is, R-VPLS scenario), will use the DCP policy and policer instances associated with the VPLS SAP. In this case, a DCP policy created for VPLS SAPs, for VPLSs that have a Layer 3 interface bound to them (R-VPLS), may have protocols such as ARP configured in the policy.
Log events, statistics, status and SNMP support
Log events are supported for DCP to warn against potential attacks or misconfigurations, and to tune DCP settings. DCP throttles the rate of DCP events to avoid event floods when multiple parallel attacks or problems occur in the system.
Most DCP log events can be enabled or disabled both individually at the DCP policy level (in the DCP policy configuration), and globally in the system (in log event control).
In the case where the DCP log event indicates a SAP that is an MSAP, the operator can identify the subscribers on a specific MSAP by using the show service active-subscriber command and filtering (‟| match”) on the MSAP string.
The DCP statistics and status is available via the following:
SNMP
For detailed information, see the tables and NOTIFICATION-TYPE objects in the following MIBs where ‟Dcp” or ‟DCpuProt” occurs in the applicable object name:
TIMETRA-CHASSIS-MIB
TIMETRA-SAP-MIB
TIMETRA-VRTR-MIB
TIMETRA-SECURITY-MIB
CLI
Use the show log event-control | match Dcp command to display the log events in the CLI.
In the case where the DCP log event indicates a SAP that is an MSAP, the operator can identify the subscribers on a specific MSAP by using the show service active-subscriber command and filtering (‟| match”) on the MSAP string.
DCP policer resource management
CAM and meter resources from the CPU protection pool are allocated for the DCP policer by using the configure>system>resource-profile>ingress-internal-tcam>cpu-protection command. Resources from this pool (also called a slice) are also used to identify protocol packets that need to be rate-limited and have used a policer or meter to the configured rate before being queued to the CPU queues. Two CAM entries with a single policer is used for every protocol configured in the DCP policy. The 7210 SAS does not support sharing of a policer among protocols. All protocols configured to use a policer are allocated an independent instance of the policer and are policed to the configured rate. See the 7210 SAS-Mxp, R6, R12, S, Sx, T Basic System Configuration Guide for information about resource allocation using the cpu-protection CLI command.
Operational guidelines
This section describes the operational guidelines to leverage distributed CPU protection:
To completely block a set of specific protocols on a specific SAP, create a single static policer with a rate of 0 and map the protocols to that policer.
During normal operation, Nokia recommends that log events for state policers should be configured using the log-events command without the optional verbose keyword. Use the verbose keyword selectively during debugging, testing, tuning, and investigation.
Every protocol configured to use a policer is allocated an independent policer instance to rate-limit that protocol. A single policer cannot be shared across multiple protocols. For example, if a single policer is configured in the service and there are four protocols configured to use it, four policer instances are allocated (that is, eight CAM entries are used for identifying the protocol and four meters are allocated).
The rates enforced by centralized CPU protection are also enforced for protocols configured for DCP. That is, DCP allows users to enforce rates per service object to be below the system-defined rate of the centralized CPU protection. Therefore, it prevents customer traffic from affecting other customer traffic.
Vendor-specific attributes (VSAs)
The 7210 SAS supports the configuration of Nokia-specific RADIUS attributes. These attributes are known as vendor-specific attributes (VSAs) and are described in RFC 2138. VSAs must be configured when RADIUS authorization is enabled. It is up to the vendor to specify the format of their VSA. The attribute-specific field is dependent on the vendor's definition of that attribute. The Nokia defined attributes are encapsulated in a RADIUS vendor-specific attribute with the vendor ID field set to 6527, the vendor ID number.
The PE-record entry is required to support the RADIUS Discovery for Layer 2 VPN feature. A PE-record is only relevant if the RADIUS Discovery feature is used, not for the standard RADIUS setup.
The following RADIUS vendor-specific attributes (VSAs) are supported by Nokia:
-
timetra-access ftp console netconf scp-sftp console-port-cli ssh-cli telnet-cli
This is a mandatory VSA that specifies the router management access methods a user can access. Multiple access methods can be specified by adding the value of the access methods to allow in the RADIUS server configuration file. For example, to allow console port CLI, SSH CLI access: Timetra-Access = 100 (100 is obtained as a sum of the individual values of the options; for example, 100 = 32 (the value for console-port-cli) + 64 (the value for ssh-cli)).
timetra-profile profile-name
When configuring this VSA for a user, it is assumed that the user profiles are configured on the local router and the following applies for local and remote authentication:
The authentication-order parameters configured on the router must include the local keyword.
The username may or may not be configured on the router.
The user must be authenticated by the RADIUS server
Up to 8 valid profiles can exist on the router for a user. The sequence in which the profiles are specified is relevant. The most explicit matching criteria must be ordered first. The process stops when the first complete match is found.
If all the preceding conditions are not met, then access to the router is denied and a failed login event/trap is written to the security log:
timetra-default-action permit-all | deny-all| none
This is a mandatory command that must be configured even if the timetra-cmd VSA is not used. This command specifies the default action when the user has entered a command and no entry configured in the timetra-cmd VSA for the user resulted in a match condition.
timetra-cmd match-string>
Configures a command or command subtree as the scope for the match condition.
The command and all subordinate commands in subordinate command levels are specified.
Configure from most specific to least specific. The system exits on the first match; subordinate levels cannot be modified with subsequent action commands. Subordinate level VSAs must be entered before this entry to be effective.
All commands at and below the hierarchy level of the matched command are subject to the timetra-action VSA.
Multiple match-strings can be entered in a single timetra-cmd VSA. Match strings must be semicolon (;) separated (maximum string length is 254 characters).
One or more timetra-cmd VSAs can be entered followed by a single timetra-action VSA:
timetra-action deny | permit
Causes the permit or deny action to be applied to all match strings specified since the last timetra-action VSA.
timetra-home-directory home-directory string
Specifies the home directory that applies for the FTP and CLI user. If this VSA is not configured, the home directory is Compact Flash slot 1 (cf1:).
timetra-restrict-to-home-directory true | false
Specifies if user access is limited to their home directory (and directories and files subordinate to their home directory). If this VSA is not configured the user is allowed to access the entire file system.
timetra-login-exec login-exec-string
Specifies the login exec file that is executed when the user login is successful. If this VSA is not configured no login exec file is applied.
If no VSAs are configured for a user, then the following applies:
The password authentication-order command on the router must include local.
The username must be configured on the router.
The user must be successfully be authenticated by the RADIUS server
A valid profile must exist on the router for this user.
If all of the preceding conditions are not met, then access to the router is denied and a failed login event/trap is written to the security log.
The complete list of TiMetra VSAs is available on a file included on the compact flash shipped with the image.
Sample user (VSA) configuration
The following example displays a user-specific VSA configuration. This configuration shows attributes for users named "ruser1" and "ruser2".
The following example shows that user "ruser1" is granted console access. The "ruser1" home directory is in compact flash slot 3 and is limited to the home directory. The default action permits all packets when matching conditions are not met. The timetra-cmd parameters allow or deny the user to use the tools;telnet;configure system security commands. Matching strings specified in the timetra-action command are denied for this user since the timetra-action is deny.
The user "ruser2" is granted FTP access.The default action denies all packets when matching conditions are not met. The timetra-cmd parameters allow the user to use the configure, show, and debug commands. Matching strings specified in the timetra-action command are permitted for this user.
users.timetra
ruser1 Auth-Type := System, Password == "ruser1"
Service-Type = Login-User,
Idle-Timeout = 600,
Timetra-Access = console,
Timetra-Home-Directory = cf1:
Timetra-Restrict-To-Home = true
Timetra-Default-Action = permit-all,
Timetra-Cmd = "tools;telnet;configure system security",
Timetra-Action = deny
ruser2 Auth-Type := System, Password == "ruser2"
Service-Type = Login-User,
Idle-Timeout = 600,
Timetra-Access = ftp
Timetra-Default-Action = deny-all,
Timetra-Cmd = "configure",
Timetra-Cmd = "show",
Timetra-Action = permit,
Timetra-Cmd = "debug",
Timetra-Action = permit,
TACACS+ services and VSAs
The 7210 SAS supports the "nokia-user" service with several VSAs. Administrators can optionally configure the service and VSAs for each user on a TACACS+ server instead of configuring access controls locally. TACACS+ VSAs describes the supported TACACS+ VSAs.
When TACACS+ services and VSAs are used, the router:
- requests "nokia-user" service VSAs after authentication succeeds
- uses the values from the TACACS+ default template when a VSA is not present
- discards invalid VSA values and authentication fails
- discards unknown mandatory VSAs and authentication succeeds
- discards unknown optional VSAs and authentication succeeds
The following table describes the supported services and VSAs.
| Service Name | VSA Name | Description | Values |
|---|---|---|---|
| nokia-user | home-directory | Home directory for the user | A string up to 200 characters |
| nokia-user | restricted-to-home | Restrict file access to the home directory of the user |
true – denies the user from accessing files outside their home directory false – permits the user to access all files on the system |
| nokia-user | save-when-restricted | Save configurations when the user is restricted to home |
true – allows configuration save operations for all configuration regions, for example, bof, debug, configure, or li via any management interface such as, CLI and NETCONF even if restricted-to-home is enabled false – denies saving the configuration when restricted-to-home is enabled |
TACACS+ configuration for file access control using VSAs
Configure file access control in one of the following ways depending on the file access requirements of users:
- locally with no VSAs
- locally using the TACACS+ default template and some VSAs that are different for each user
- using the file access VSAs to control file access, and the TACACS+ default template for other user access controls
File access is denied when the restricted-to-home command is configured unless the home-directory command is configured and the directory is created by an administrator.
Some TACACS+ servers require the backslash character (\) to escape the backslash (\)
character in quoted strings in the server configuration file
(tac_plus.conf); for example:
- home-directory = cf3:\users\user1
- home-directory = "cf3:\\users\\user1"
TACACS+ server with VSA configuration for per-user home directories, and a locally configured default template for other options
This example shows the following configurations:
- Each user has a home directory with restricted file access. The administrator must create the home directory for each user.
- The home directory is configured with a VSA.
- Other file access controls are configured in the TACACS+ default template.
- All users can save the configuration.
TACACS+ server configuration
A:node-2>config>system>security>user-template# info
----------------------------------------------
restricted-to-home
save-when-restricted
----------------------------------------------TACACS+ server with VSA configuration and per-user home directories
This example shows the following configurations:
- All file access is controlled with VSAs, which is the most flexible option to grant different file access to each user.
- The TACACS+ default template is not used for file access.
- Each user has a home directory. The administrator must create a home directory for each user.
- The administrator can also restrict file access to the home directory of the user and allow users to save the configuration based on the VSA value.
The user1 profile has access to all files and user1 can save the configuration.
user = user1 {
service = nokia-user {
# home-directory is not defined
restricted-to-home = false
# save-when-restricted is not defined
}
}The user2 profile has home directory access and user2 can save the configuration.
user = user2 {
service = nokia-user {
home-directory = cf3:\users\user2
restricted-to-home = true
save-when-restricted = true
}
}The user3 profile has home directory access but user3 cannot save the configuration.
user = user3 {
service = nokia-user {
home-directory = cf3:\users\user3
restricted-to-home = true
save-when-restricted = false
}
}The user4 profile has no file access and user4 cannot save the configuration.
user = user4 {
service = nokia-user {
# home-directory is not defined
restricted-to-home = true
save-when-restricted = false
}
}Other security features
This sections describes security features supported on the 7210 SAS.
Security algorithms
The following table lists the security algorithms supported per protocol.
| Protocol | Clear text | MD5 | HMAC-MD5 | HMAC-SHA1-96 | HMAC-SHA1 | HMAC-SHA256 | AES-128-CMAC-96 |
|---|---|---|---|---|---|---|---|
OSPF |
✓ |
✓ |
✓ |
✓ |
✓ |
||
IS-IS |
✓ |
✓ |
✓ |
✓ |
|||
RSVP |
✓ |
✓ |
✓ |
||||
BGP |
✓ |
✓ |
|||||
LDP |
✓ |
✓ |
✓ |
Secure Shell (SSH)
Secure Shell (SSH) is a protocol that provides a secure, encrypted Telnet-like connection to a router. A connection is always initiated by the client (the user). Authentication takes places by one of the configured authentication methods (local, RADIUS, or TACACS+). With authentication and encryption, SSH allows for a secure connection over an insecure network.
The 7210 SAS allows a user to configure SSH version 2 (SSHv2). SSHv1 and SSHv2 are different protocols and encrypt at different parts of the packets. SSH1 uses server as well as host keys to authenticate systems whereas SSHv2 only uses host keys. SSHv2 does not use the same networking implementation that SSHv1 does and is considered a more secure, efficient, and portable version of SSH.
SSH runs on top of a transport layer (like TCP or IP), and provides authentication and encryption capabilities.
The 7210 SAS has a global SSH server process to support inbound SSH and SCP sessions initiated by external SSH or SCP client applications. The SSH server supports SSHv1. Note that this server process is separate from the SSH and SCP client commands on the routers which initiate outbound SSH and SCP sessions.
Inbound SSH sessions are counted as inbound Telnet sessions for the purposes of the maximum number of inbound sessions specified by Login Control. Inbound SCP sessions are counted as inbound FTP sessions by Login Control.
When the SSH server is enabled, an SSH security key is generated. Unless the perserve-key command option is configured for SSH, the security key is only valid until the node is restarted or the SSH server is stopped and restarted. The key size is non-configurable and set to 2048 for SSHv2 RSA, and to 1024 for SSHv2 DSA and SSHv1 RSA. When the server is enabled, both inbound SSH and SCP sessions are accepted, as long as the session is properly authenticated.
When the global SSH server process is disabled, no inbound SSH or SCP sessions are accepted.
When using SCP to copy files from an external device to the file system, the SCP server will accept either forward slash (‟/”) or backslash (‟\”) characters to delimit directory and/or filenames. Similarly, the SCP client application can use either slash or backslash characters, but not all SCP clients treat backslash characters as equivalent to slash characters. In particular, UNIX systems will often interpret the backslash character as an ‟escape” character, which is not transmitted to the SCP server. For example, a destination directory specified as ‟cf1:\dir1\file1” will be transmitted to the SCP server as ‟cf1:dir1file1” where the backslash escape characters are stripped by the SCP client system before transmission. On systems where the client treats the backslash like an ‟escape” character, a double backslash ‟\\” or the forward slash ‟/” can be used to properly delimit directories and the filename.
SSH PKI authentication
The SSH server supports a public key authentication provided that the server has been previously configured to know the client's public key.
Using public key authentication, also known as Public Key Infrastructure (PKI), can be more secure than the existing username and password method because of the following:
A user typically reuses the same password with multiple servers. If the password is compromised, the user must reconfigure the password on all affected servers.
A password is not transmitted between the client and server using PKI. Instead the sensitive information (the private key) is kept on the client. Consequently, the password is less likely to be compromised.
The 7210 SAS supports server-side SSHv2 public key authentication, but does not include a key-generation utility.
PKI should be configured in the system-level configuration where one or more public keys may be bound to a username. This configuration does not affect any other system security or login functions.
PKI has preference over password or keyboard authentication. PKI is supported using only local authentication. PKI authentication is not supported on TACACS+ or RADIUS.
User public key generation
Before SSH can be used with PKI, the client must generate a public/private key pair. This is typically supported by the SSH client software. For example, PuTTY supports a utility called PuTTYGen that generates key pairs.
The 7210 SAS currently supports only Rivest, Shamir, and Adleman (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA) user public keys.
If the SSH client software uses PuTTY, it must first generate a key pair using PuTTYGen. The client sets the key type to SSH-2 RSA and configures the number of bits to be used for the key. The client can also configure a passphrase to store the key locally in encrypted form. If the passphrase is configured, it acts as a password that the client must enter to use the private key. If a passphrase is not configured, the private key is stored in plain text locally.
Next, use the config>system>security>user>public-keys command to configure the public key for the client (the public key is obtained as part of the key pair). On the 7210 SAS, the user can program the public key using CLI commands (accessed through Telnet/SSH) or SNMP.
The preceding process to generate a key pair is an example only. This process is not executed on a 7210 SAS node, but on a third-party node acting as the SSH client or any other node.
MAC client and server list
The 7210 SAS supports a configurable client and server MAC list for SSHv2, which allows the user to add or remove Message Authentication Code (MAC) algorithms from the list. The user can program the strong Hashed Message Authentication Code (HMAC) algorithms on top of the configurable MAC list (for example, lowest index in the list) to be negotiated first between the client and server. The first algorithm in the list that is supported by both the client and the server is the one that is agreed upon.
There are two configurable MAC lists:
client list
server list
The default client and server MAC list includes all supported algorithms in the following preference order:
-
mac 200 name hmac-sha2-512
-
mac 210 name hmac-sha2-256
-
mac 215 name hmac-sha1
-
mac 220 name hmac-sha1-96
-
mac 225 name hmac-md5
-
mac 240 name hmac-md5-96
The configurable MAC list is only supported for SSHv2 and not for SSHv1. SSHv1 only supports 32-bit CRC.
Cipher client and server list
The 7210 SAS supports cipher client and server lists. The user can add or remove the desired SSH cipher client and server algorithms to be negotiated. The list is an index list with the lower index having higher preference in the SSH negotiation. The lowest index algorithm in the list is negotiated first in SSH connections and is on top of the negotiation list to the peer.
The default server and client lists for SSHv2 include all supported algorithms in the following preference order:
-
cipher 190 name aes256-ctr
-
cipher 192 name aes192-ctr
-
cipher 194 name aes128-ctr
-
cipher 200 name aes128-cbc
-
cipher 205 name 3des-cbc
-
cipher 225 name aes192-cbc
-
cipher 230 name aes256-cbc
Use the following CLI syntax to configure the client and server cipher list.
*A:Dut-C# configure system security ssh client-cipher-list
- client-cipher-list
[no] cipher - Configure a cipher
*A:Dut-C# configure system security ssh client-cipher-list cipher
- cipher <index> name <cipher-name>
- no cipher <index>
<index> : [1..255]
<cipher-name> : aes128-ctr|aes192-ctr|aes256-ctr|3des-cbc|aes128-cbc|
aes192-cbc|aes256-cbc
*A:Dut-C# configure system security ssh server-cipher-list
- server-cipher-list
[no] cipher - Configure a cipher
*A:Dut-C# configure system security ssh server-cipher-list cipher
- cipher <index> name <cipher-name>
- no cipher <index>
<index> : [1..255]
<cipher-name> : aes128-ctr|aes192-ctr|aes256-ctr|3des-cbc|aes128-cbc|
aes192-cbc|aes256-cbcKEX client and server list
The 7210 SAS supports key exchange (KEX) client and server lists. The user can add or remove the KEX client or server algorithms that the SSH application negotiates using an SSHv2 phase one handshake. The KEX list is an index list with the lower index having higher preference in the SSH negotiation. The lowest indexed algorithm in the list is negotiated first in SSH and is at the top of the negotiation list to the peer.
By default, the KEX list is empty and a hard-coded list that includes all supported algorithms in the following preference order is used:
kex 200 name diffie-hellman-group16-sha512
kex 210 name diffie-hellman-group14-sha256
kex 215 name diffie-hellman-group14-sha1
kex 220 name diffie-hellman-group-exchange-sha1
kex 225 name diffie-hellman-group1-sha1
As soon as the user configures the KEX list, the 7210 SAS starts using the algorithms from the user-defined KEX list instead of the hard-coded list. To revert to the hard-coded list, the user must remove all configured KEX indexes until the list is empty.
Use the following CLI to configure the cipher or MAC server and client lists.
configure system security ssh server-kex-list kex
kex <index> name <kex-name>
no kex <index>
configure system security ssh client-kex-list kex
kex <index> name <kex-name>
no kex <index>
<index> : [1..255]
<kex-name> : diffie-hellman-group14-sha1| diffie-hellman-group14-sha256|
diffie-hellman-group16-sha512|diffie-hellman-group-exchange-
sha1| diffie-hellman-group1-sha1
Exponential login backoff
A malicious user may attempt to gain CLI access by means of a dictionary attack, in which a script is used to attempt automatic logins as an ‟admin” user and a dictionary list is used to test all possible passwords. By using the exponential-backoff feature in the config>system>login-control context, the 7210 SAS increases the delay between login attempts exponentially to mitigate attacks.
When a user attempts to log into a router using a Telnet or an SSH session, the system allows a limited number of attempts to enter the correct password. The interval between the unsuccessful attempts change after each try (1, 2, and 4 seconds). If user lockout is configured on the system, the user will be locked out when the number of unsuccessful attempts is exceeded.
However, if lockout is not configured, three password entry attempts are allowed in the first session after the first failure, at fixed 1, 2 and 4 second intervals, and then the session terminates. Users do not have an unlimited number of login attempts per session. After each failed password attempt, the wait period becomes longer until the maximum number of attempts is reached.
The 7210 SAS terminates after four unsuccessful attempts. A wait period is never longer than 4 seconds. The periods are fixed and restart in subsequent sessions.
The config system login-control [no] exponential-backoff command works in conjunction with the config system security password attempts command, which is also a system wide configuration.
*A:ALA-48>config>system# security password attempts
- attempts <count> [time <minutes1>] [lockout <minutes2>]
- no attempts
<count> : [1..64]
<minutes1> : [0..60]
<minutes2> : [0..1440]
Exponential backoff applies to any user and by any login method such as console, SSH and Telnet.
See Configuring login controls. The commands are described in Login, Telnet, SSH and FTP commands.
User lockout
When a user exceeds the maximum number of attempts allowed (the default is 3 attempts) during a specific period of time (the default is 5 minutes) the account used during those attempts will be locked out for a preconfigured lock-out period (the default is 10 minutes).
An security event log will be generated as soon as a user account has exceeded the number of allowed attempts and the show>system>security>user command can be used to display the total number of failed attempts per user.
The account will be automatically re-enabled as soon as the lock-out period has expired.
Encryption
Data Encryption Standard (DES) and Triple DES (3DES) are supported for encryption:
DES is a widely-used method of data encryption using a private (secret) key. Both the sender and the receiver must know and use the same private key.
3DES is a more secure version of the DES protocol.
802.1x network access control
The 7210 SAS supports network access control of client devices (PCs, STBs, and so on) on an Ethernet network using the IEEE. 802.1x standard. 802.1x is known as Extensible Authentication Protocol (EAP) over a LAN network or EAPOL.
TCP Enhanced Authentication Option
The TCP Enhanced Authentication Option, currently covered in draft-bonica-tcp-auth-05.txt, Authentication for TCP-based Routing and Management Protocols, extends the previous MD5 authentication option to include the ability to change keys without tearing down the session, and allows for stronger authentication algorithms to be used.
The TCP Enhanced Authentication Option is a TCP extension that enhances security for BGP, LDP and other TCP-based protocols. This includes the ability to change keys in a BGP or LDP session seamlessly without tearing down the session. It is intended for applications where secure administrative access to both the end-points of the TCP connection is available.
TCP peers can use this extension to authenticate messages passed between one another. This strategy improves upon current practice, which is described in RFC 2385, Protection of BGP Sessions via the TCP MD5 Signature Option. Using this new strategy, TCP peers can update authentication keys during the lifetime of a TCP connection. TCP peers can also use stronger authentication algorithms to authenticate routing messages.
Packet formats
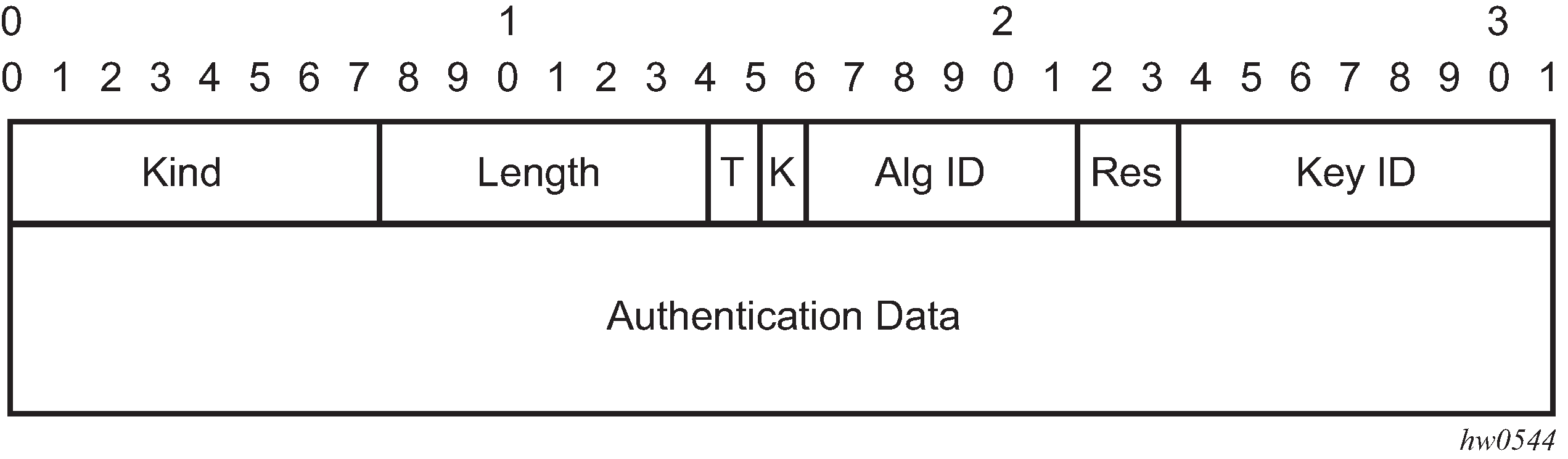
The following figure shows the packet format for the Enhanced Authentication Option.
Option Syntax:
Kind: 8 bits
The Kind field identifies the TCP Enhanced Authentication Option. This value will be assigned by IANA.
Length: 8 bits
The Length field specifies the length of the TCP Enhanced Authentication Option, in octets. This count includes two octets representing the Kind and Length fields.
The valid range for this field is from 4 to 40 octets, inclusive.
For all algorithms specified in this memo the value will be 16 octets.
T-Bit: 1 bit
The T-bit specifies whether TCP Options were omitted from the TCP header for the purpose of MAC calculation. A value of 1 indicates that all TCP options other than the Extended Authentication Option were omitted. A value of 0 indicates that TCP options were included.
The default value is 0.
K-Bit: 1 bit
This bit is reserved for future enhancement. Its value MUST be equal to zero.
Alg ID: 6 bits
The Alg ID field identifies the MAC algorithm.
Res: 2 bits
These bits are reserved. They MUST be set to zero.
Key ID: 6 bits
The Key ID field identifies the key that was used to generate the message digest.
Authentication Data: Variable length
The Authentication Data field contains data that is used to authenticate the TCP segment. This data includes, but need not be restricted to, a MAC. The length and format of the Authentication Data Field can be derived from the Alg ID.
The Authentication for TCP-based Routing and Management Protocols draft provides and overview of the TCP Enhanced Authentication Option. The details of this feature are described in draft-bonica-tcp-auth-04.txt.
Keychain
A keychain is a set of up to 64 keys, where each key is {A[i], K[i], V[i], S[i], T[i], S'[i], T'[i]} as described in draft-bonica-tcp-auth-05.txt, Authentication for TCP-based Routing and Management Protocols. They keys can be assigned to both sides of a LDP peer.The individual keys in a keychain have a begin- and end-time indicating when to use this key.
These fields map to the CLI tree as described in the following table.
| Field | Definition | CLI |
|---|---|---|
i |
The key identifier expressed as an integer (0...63) |
config>system>security>keychain>direction>bi>entry config>system>security>keychain>direction>uni>receive> entry config>system>security>keychain>direction>uni>send>entry |
A[i] |
Authentication algorithm to use with key[i] |
config>system>security>keychain>direction>bi>entry with algorithm algorithm parameter. config>system>security>keychain>direction>uni>receive> entry with algorithm algorithm parameter. config>system>security>keychain>direction>uni>send>entry with algorithm algorithm parameter. |
K[i] |
Shared secret to use with key[i]. |
config>system>security>keychain>direction>uni>receive> entry with shared secret parameter config>system>security>keychain>direction>uni>send>entry with shared secret parameter config>system>security>keychain>direction>bi>entry with shared secret parameter |
V[i] |
A vector that determines whether the key[i] is to be used to generate MACs for inbound segments, outbound segments, or both. |
config>system>security>keychain>direction |
S[i] |
Start time from which key[i] can be used by sending TCPs. |
config>system>security>keychain>direction>bi>entry>begin-time config>system>security>keychain>direction>uni>send>entry >begin-time |
T[i] |
End time after which key[i] cannot be used by sending TCPs. |
Inferred by the begin-time of the next key (youngest key rule). |
S'[i] |
Start time from which key[i] can be used by receiving TCPs. |
config>system>security>keychain>direction>bi>entry>begin-time config>system>security>keychain>direction>bi>entry> tolerance config>system>security>keychain>direction>uni>receive> entry>begin-time config>system>security>keychain>direction>uni>receive> entry>tolerance |
T'[i] |
End time after which key[i] cannot be used by receiving TCPs |
config>system>security>keychain>direction>uni>receive> entry>end-time |
Configuration notes
This section describes security configuration guidelines and caveats.
General
If a RADIUS or a TACACS+ server is not configured, then password, profiles, and user access information must be configured on each router in the domain.
If a RADIUS authorization is enabled, then VSAs must be configured on the RADIUS server.
Configuring security with CLI
This section provides information to configure security using the command line interface.
Setting up security attributes
This section provides a brief overview of the tasks that must be performed to configure security and provides the CLI commands. The following table describes the capabilities of authentication, authorization, and accounting configurations. For example, authentication can be enabled locally and on RADIUS and TACACS+ servers. Authorization can be executed locally, on a RADIUS server, or on a TACACS+ server. Accounting can be performed on a RADIUS or TACACS+ server.
| Authentication | Authorization | Accounting |
|---|---|---|
Local |
Local |
None |
RADIUS |
Local and RADIUS |
RADIUS |
TACACS+ |
Local |
TACACS+ |
Configuring authentication
See the following sections to configure authentication:
Local authentication
RADIUS authentication (only)
By default, authentication is enabled locally. Perform the following tasks to configure security on each participating router:
RADIUS authentication
To implement only RADIUS authentication, with authorization, perform the following tasks on each participating router:
TACACS+ authentication
To implement only TACACS+ authentication, perform the following tasks on each participating router:
Configuring authorization
See the following sections to configure authorization:
Local authorization
For local authorization, configure these tasks on each participating router:
RADIUS authorization (only)
For RADIUS authorization (without authentication), configure these tasks on each participating router:
For RADIUS authorization, VSAs must be configured on the RADIUS server. See Vendor-specific attributes (VSAs).
RADIUS authorization
For RADIUS authorization (with authentication), configure these tasks on each participating router:
Configuring RADIUS authorization For RADIUS authorization, VSAs must be configured on the RADIUS server. See Vendor-specific attributes (VSAs).
TACACS+ authorization (only)
For TACACS+ authorization (without authentication), configure these tasks on each participating router:
TACACS+ authorization
For TACACS+ authorization (with authentication), configure these tasks on each participating router:
Configuring accounting
The following sections provide information about configuring accounting.
Security configurations
This section provides information to configure security and configuration examples of configuration tasks.
To implement security features, configure the following components:
management access filters
profiles
user access parameters
password management parameters
enable RADIUS and/or TACACS+:
one to five RADIUS and/or TACACS+ servers
RADIUS and/or TACACS+ parameters
The following are sample default values for security parameters.
A:ALA-1>config>system>security# info detail
----------------------------------------------
no hash-control
telnet-server
no telnet6-server
no ftp-server
management-access-filter
exit
profile "default"
default-action none
no li
entry 10
no description
match ‟exec”
action permit
...
password
authentication-order radius tacplus local
no aging
minimum-length 6
attempts 3 time 5 lockout 10
complexity
exit
user "admin"
password "./3kQWERTYn0Q6w" hash
access console
no home-directory
no restricted-to-home
console
no login-exec
no cannot-change-password
no new-password-at-login
member "administrative"
exit
exit
snmp
view iso subtree 1
mask ff type included
exit
...
access group snmp-ro security-model snmpv1 security-level no-auth-no
privacy read no-security notify no-security
access group snmp-ro security-model snmpv2c security-level no-auth-no
privacy read no-security notify no-security
access group snmp-rw security-model snmpv1 security-level no-auth-no
privacy read no-security write no-security notify no-security
access group snmp-rw security-model snmpv2c security-level no-auth-no
privacy read no-security write no-security notify no-security
access group snmp-rwa security-model snmpv1 security-level no-auth-no
privacy read iso write iso notify iso
access group snmp-rwa security-model snmpv2c security-level no auth-no
privacy read iso write iso notify iso
access group snmp-trap security-model snmpv1 security-level no-auth-no
privacy notify iso
access group snmp-trap security-model snmpv2c security-level no-auth-no
privacy notify iso
access group cli-readonly security-model snmpv2c security-level
no-auth-no-privacy read iso notify iso
access group cli-readwrite security-model snmpv2c security-level
no-auth-no-privacy read iso write iso notify iso
attempts 20 time 5 lockout 10
exit
no ssh
Security configuration procedures
The following sections provide information about configuring security components.
Configuring Management Access Filters
Creating and implementing management access filters is optional. Management access filters control all traffic going in to the CPM, including all routing protocols. They apply to packets from all ports. The filters can be used to restrict management of the 7210 SAS router by other nodes outside either specific (sub)networks or through designated ports. By default, there are no filters associated with security options. The management access filter and entries must be explicitly created on each router. These filters also apply to the management Ethernet port.
The 7210 SAS implementation exits the filter when the first match is found and execute the actions according to the specified action. For this reason, entries must be sequenced correctly from most to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword CPM to be considered complete. Entries without the action keyword are considered incomplete and will be rendered inactive.
Use the following syntax to configure a management access filter. This example only accepts packets matching the criteria specified in entries 1 and 2. Non-matching packets are denied.
config>system
security
management-access-filter
ip-filter
ipv6-filter
default-action {permit|deny|deny-host-unreachable}
renum old-entry-number new-entry-number
no shutdown
entry entry-id
description description-string
src-port {port-id cpm|laglag-id}
src-ip {ip-prefix/mask | ip-prefix netmask}
protocol protocol-id
dst-port port [mask]
action {permit|deny|deny-host-unreachable}
log
Configuring password management parameters
Password management parameters consists of defining aging, the authentication order and authentication methods, password length and complexity, as well as the number of attempts a user can enter a password.
Depending on the your authentication requirements, password parameters are configured locally.
Use the following syntax to configure password support.
config>system>security
password
admin-password password [hash|hash2]
aging days
attempts count [time minutes1] [lockout minutes2]
authentication-order [method-1] [method-2] [method-3] [exit-on-reject]
complexity-rules
allow-user-name
credits [lowercase credits] [uppercase credits] [numeric credits] [special-character credits]
minimum-classes minimum
minimum-length length
repeated-characters count
required [lowercase count] [uppercase count] [numeric count] [special-character count]
hashing {bcrypt|sha2-pbkdf2}
health-check [interval interval]
history-size size
minimum-age [days days] [hrs hours] [min minutes] [sec seconds]
minimum-change distance
Password configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
password
authentication-order radius tacplus local
aging 365
minimum-length 8
attempts 5 time 5 lockout 20
exit
----------------------------------------------
A:ALA-1>config>system>security#
Configuring profiles
Profiles are used to deny or permit access to a hierarchical branch or specific commands. Profiles are referenced in a user configuration. A maximum of sixteen user profiles can be defined. A user can participate in up to sixteen profiles. Depending on the the authorization requirements, passwords are configured locally or on the RADIUS server.
Use the following syntax to configure user profiles.
config>system>security
profile user-profile-name
default-action {deny-all|permit-all|none}
renum old-entry-number new-entry-number
entry entry-id
description description-string
match command-string
action {permit|deny}
User profile configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
...
profile "ghost"
default-action permit-all
entry 1
match "configure"
action permit
exit
entry 2
match "show"
exit
entry 3
match "exit"
exit
exit
...
----------------------------------------------
A:ALA-1>config>system>security#
Configuring users
Configure access parameters for individual users. For user, define the login name for the user and, optionally, information that identifies the user. Use the following syntax to configure RADIUS support.
config>system>security
user-template template-name
user user-name
access [ftp] [snmp] [console]
console
cannot-change-password
login-exec url-prefix:source-url
member user-profile-name [user-profile-name...(up to 8 max)]
new-password-at-login
home-directory url-prefix [directory][directory/directory ..]
password [password] [hash|hash2]
restricted-to-home
snmp
authentication {[none]|[[hash] {md5 key-1|sha key-1} privacy {none|des-key key-2}]}
group group-name
User configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
...
user "49ers"
password "qQbnuzLd7H/VxGdUqdh7bE" hash2
access console ftp snmp
restricted-to-home
console
member "default"
member "ghost"
exit
exit
...
--------------------------------------------
A:ALA-1>config>system>security#
Configuring keychains
Keychain configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
...
keychain "abc"
direction
bi
entry 1 key "ZcvSElJzJx/wBZ9biCtOVQJ9YZQvVU.S" hash2 alg
orithm aes-128-cmac-96
begin-time 2006/12/18 22:55:20
exit
exit
exit
exit
keychain "basasd"
direction
uni
receive
entry 1 key "Ee7xdKlYO2DOm7v3IJv/84LIu96R2fZh" hash2
algorithm aes-128-cmac-96
tolerance forever
exit
exit
exit
exit
exit
...
----------------------------------------------
A:ALA-1>config>system>security#
Copying and overwriting users and profiles
You can copy a profile or user. You can copy a profile or user or overwrite an existing profile or user. The overwrite option must be specified or an error occurs if the destination profile or username already exists.
User
Use the following CLI syntax to copy a user.
config>system>security# copy {user source-user | profile source-profile} to destination [overwrite]
Command usage
config>system>security# copy user testuser to testuserA
MINOR: CLI User "testuserA" already exists - use overwrite flag.
config>system>security#
config>system>security# copy user testuser to testuserA overwrite
config>system>security#
Copied user configuration output
A:ALA-12>config>system>security# info
----------------------------------------------
...
user "testuser"
password "F6XjryaATzM" hash
access snmp
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy
none
group "testgroup"
exit
exit
user "testuserA"
password "" hash2
access snmp
console
new-password-at-login
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy
none
group "testgroup"
exit
exit
...
----------------------------------------------
A:ALA-12>config>system>security# info
The cannot-change-password flag is not replicated when a copy user command is performed. A new-password-at-login flag is created instead.
A:ALA-12>config>system>security>user# info
----------------------------------------------
password "F6XjryaATzM" hash
access snmp
console
cannot-change-password
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy none
group "testgroup"
exit
----------------------------------------------
A:ALA-12>config>system>security>user# exit
A:ALA-12>config>system>security# user testuserA
A:ALA-12>config>system>security>user# info
----------------------------------------------
password "" hash2
access snmp
console
new-password-at-login
exit
snmp
authentication hash md5 e14672e71d3e96e7a1e19472527ee969 privacy none
group "testgroup"
exit
----------------------------------------------
A:ALA-12>config>system>security>user#
Profile
Use the following CLI syntax to copy a profile.
config>system>security# copy {user source-user | profile source-profile} to destination [overwrite]
Command usage
config>system>security# copy profile default to testuser
Copied profiles configuration output
A:ALA-49>config>system>security# info
----------------------------------------------
...
A:ALA-49>config>system>security# info detail
----------------------------------------------
...
profile "default"
default-action none
entry 10
no description
match "exec"
action permit
exit
entry 20
no description
match "exit"
action permit
exit
entry 30
no description
match "help"
action permit
exit
entry 40
no description
match "logout"
action permit
exit
entry 50
no description
match "password"
action permit
exit
entry 60
no description
match "show config"
action deny
exit
entry 70
no description
match "show"
action permit
exit
entry 80
no description
match "enable-admin"
action permit
exit
exit
profile "testuser"
default-action none
entry 10
no description
match "exec"
action permit
exit
entry 20
no description
match "exit"
action permit
exit
entry 30
no description
match "help"
action permit
exit
entry 40
no description
match "logout"
action permit
exit
entry 50
no description
match "password"
action permit
exit
entry 60
no description
match "show config"
action deny
exit
entry 70
no description
match "show"
action permit
exit
entry 80
no description
match "enable-admin"
action permit
exit
exit
profile "administrative"
default-action permit-all exit
...
----------------------------------------------
A:ALA-12>config>system>security#
Enabling SSH
Use the SSH command to configure the SSH server as SSH1, SSH2 or both. The default is SSH2 (SSH version 2). This command should only be enabled or disabled when the SSH server is disabled. This setting should not be changed while the SSH server is running since the actual change only takes place after SSH is disabled or enabled.
config>system>security
ssh
preserve-key
no server-shutdown
version ssh-version
The following is a sample SSH server configuration output as both SSH and SSH2 using a host-key.
A:sim1>config>system>security>ssh# info
----------------------------------------------
preserve-key
version 1-2
----------------------------------------------
A:sim1>config>system>security>ssh#
RADIUS configurations
The following sections provide information about configuring RADIUS functionality.
Configuring RADIUS authentication
RADIUS is disabled by default and must be explicitly enabled. The mandatory commands to enable RADIUS on the local router are radius and server server-index address ip-address secret key.
The system IP address must be configured in order for the RADIUS client to work.
The other commands are optional. The server command adds a RADIUS server and configures the RADIUS server IP address, index, and key values. The index determines the sequence in which the servers are queried for authentication requests.
On the local router, use the following syntax to configure RADIUS authentication.
config>system>security
radius
port port
retry count
server server-index address ip-address secret key
timeout seconds
no shutdown
RADIUS authentication configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
retry 5
timeout 5
server 1 address 10.10.10.103 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
...
----------------------------------------
A:ALA-1>config>system>security#
Configuring RADIUS authorization
In order for RADIUS authorization to function, RADIUS authentication must be enabled first. See Configuring RADIUS authentication.
In addition to the local configuration requirements, VSAs must be configured on the RADIUS server. See Vendor-specific attributes (VSAs).
On the local router, use the following syntax to configure RADIUS authorization.
config>system>security
radius
authorization
RADIUS authorization configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
...
radius
authorization
retry 5
timeout 5
server 1 address 10.10.10.103 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
exit
...
----------------------------------------------
A:ALA-1>config>system>security#
Configuring RADIUS accounting
Use the following syntax to configure RADIUS accounting on a local router.
config>system>security
radius
accounting
RADIUS accounting configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
...
radius
shutdown
authorization
accounting
retry 5
timeout 5
server 1 address 10.10.10.103 secret "test1"
server 2 address 10.10.0.1 secret "test2"
server 3 address 10.10.0.2 secret "test3"
server 4 address 10.10.0.3 secret "test4"
exit
...
----------------------------------------------
A:ALA-1>config>system>security#
Configuring 802.1x RADIUS policies
Use the following CLI commands to configure generic authentication parameters for clients using 802.1x EAPOL. Additional parameters are configured per Ethernet port. See the 7210 SAS-Mxp, R6, R12, S, Sx, T Interface Configuration Guide.
To configure generic parameters for 802.1x authentication, enter the following CLI syntax.
config>system>security
dot1x
radius-plcy policy-name
server server-index address ip-address secret key [port port]
source-address ip-address
no shutdown
802.1x configuration output
A:ALA-1>config>system>security# info
----------------------------------------------
dot1x
radius-plcy "dot1x_plcy" create
server 1 address 10.1.1.1 port 65535 secret "a"
server 2 address 10.1.1.2 port 6555 secret "a"
source-address 10.1.1.255
no shutdown
...
----------------------------------------------
A:ALA-1>config>system#
TACACS+ configurations
Enabling TACACS+ authentication
To use TACACS+ authentication on the router, configure one or more TACACS+ servers on the network.
Use the following syntax to configure profiles.
config>system>security
tacplus
server server-index address ip-address secret key
timeout seconds
no shutdown
TACACS+ authentication configuration output
A:ALA-1>config>system>security>tacplus# info
----------------------------------------------
timeout 5
server 1 address 10.10.0.5 secret "test1"
server 2 address 10.10.0.6 secret "test2"
server 3 address 10.10.0.7 secret "test3"
server 4 address 10.10.0.8 secret "test4"
server 5 address 10.10.0.9 secret "test5"
----------------------------------------------
A:ALA-1>config>system>security>tacplus#
Configuring TACACS+ authorization
In order for TACACS+ authorization to function, TACACS+ authentication must be enabled first. See Enabling TACACS+ authentication.
Use the following syntax to configure RADIUS authorization on the local router.
config>system>security
tacplus
authorization
no shutdown
TACACS+ authorization configuration output
A:ALA-1>config>system>security>tacplus# info
----------------------------------------------
authorization
timeout 5
server 1 address 10.10.0.5 secret "test1"
server 2 address 10.10.0.6 secret "test2"
server 3 address 10.10.0.7 secret "test3"
server 4 address 10.10.0.8 secret "test4"
server 5 address 10.10.0.9 secret "test5"
----------------------------------------------
A:ALA-1>config>system>security>tacplus#
Configuring TACACS+ accounting
Use the following syntax to configure TACACS+ accounting on a local router.
config>system>security
tacplus
accounting
TACACS+ accounting configuration output
A:ALA-1>config>system>security>tacplus# info
----------------------------------------------
accounting
authorization
timeout 5
server 1 address 10.10.0.5 secret "test1"
server 2 address 10.10.0.6 secret "test2"
server 3 address 10.10.0.7 secret "test3"
server 4 address 10.10.0.8 secret "test4"
server 5 address 10.10.0.9 secret "test5"
----------------------------------------------
A:ALA-1>config>system>security>tacplus#
Configuring login controls
Configure login control parameters for console, Telnet, and FTP sessions.
Use the following syntax to configure login controls.
config>system
login-control
exponential-backoff
ftp
inbound-max-sessions value
telnet
inbound-max-sessions value
outbound-max-sessions value
idle-timeout {minutes |disable}
pre-login-message login-text-string [name]
login-banner
motd {url url-prefix: source-url|text motd-text-string}
Login control configuration output
A:ALA-1>config>system# info
----------------------------------------------
...
login-control
ftp
inbound-max-sessions 5
exit
telnet
inbound-max-sessions 7
outbound-max-sessions 2
exit
idle-timeout 1440
pre-login-
message "Property of Service Routing Inc. Unauthorized access prohibited."
motd text "Notice to all users: Software upgrade scheduled 3/2 1:00 AM"
exit
no exponential-backoff
...
----------------------------------------------
A:ALA-1>config>system#
Security command reference
Command hierarchies
Configuration commands
Security commands
config
- system
- security
- copy {user source-user | profile source-profile} to destination [overwrite]
- dot1x
- [no] ftp-server
- hash-control [read-version {1 | 2 | all}] [write-version {1 | 2}]
- no hash-control
- [no] keychain keychain-name
- management-access-filter
- password
- [no] profile user-profile-name
- [no] radius
- snmp
- source-address
- application app [ip-int-name|ip-address]
- no application app
- application6 app [ipv6-address]
- no application6 app
- [no] telnet-server
- ssh
- [no] tacplus
- [no] users user-name
- user-template {tacplus_default | radius_default}
Management Access Filter commands
config
- system
- security
- [no] management-access-filter
- [no] ip-filter
- default-action {permit | deny | deny-host-unreachable}
- [no] entry entry-id
- action {permit | deny | deny-host-unreachable}
- no action
- description description-string
- no description
- dst-port port [mask]
- no dst-port
- fragment {true | false}
- no fragment
- l4-src-port port [mask]
- no l4-src-port
- [no] log
- protocol protocol-id
- no protocol
- router router-instance
- no router
- src-ip {ip-prefix/mask | ip-prefix netmask}
- no src-ip
- src-port {port-id | lag lag-id}
- no src-port
- [no]ipv6-filter
- default-action {permit | deny | deny-host-unreachable}
- [no] entry entry-id
- action {permit | deny | deny-host-unreachable}
- no action
- description description-string
- no description
- dst-port port [mask]
- no dst-port
- flow-label value
- no flow-label
- l4-src-port port [mask]
- no l4-src-port
- [no] log
- next-header next-header
- no next-header
- router router-instance
- no router
- src-ip {ip-prefix/prefix-length | ip-prefix netmask}
- no src-ip
- src-port {port-id | lag lag-id}
- no src-port
- renum old-entry-number new-entry-number
- [no] shutdown
Distributed CPU protection commands
config
- system
- security
- dist-cpu-protection
- policy policy-name [create]
- no policy policy-name
- description description-string
- no description
- protocol name [create]
- no protocol name
- enforcement {static policer-name}
- static-policer policer-name [create]
- no static-policer policer-name
- description description-string
- no description
- exceed-action {discard | none}
- log-events [verbose]
- no log-events
- rate {kbps {kilobits-per-second | max} {[mbs size] [bytes | kilobytes]}
- no rate
Security password commands
config
- system
- security
- password
- admin-password password [hash | hash2]
- no admin-password
- aging days
- no aging
- attempts count [time minutes1] [lockout minutes2]
- no attempts
- authentication-order [method-1] [method-2] [method-3] [exit-on-reject]
- no authentication-order
- complexity-rules
- [no] allow-user-name
- credits [lowercase credits] [uppercase credits] [numeric credits] [special-character credits]
- no credits
- minimum-classes minimum
- no minimum-classes
- minimum-length length
- no minimum-length
- repeated-characters count
- no repeated-characters
- required [lowercase count] [uppercase count] [numeric count] [special-character count]
- no required
- hashing {bcrypt | sha2-pbkdf2}
- [no] health-check [interval interval]
- history size
- no history
- minimum-age [days days] [hrs hours] [min minutes] [sec seconds]
- no minimum-age
- minimum-change distance
- no minimum-change
Profile commands
config
- system
- security
- [no] profile user-profile-name
- default-action {deny-all | permit-all | none}
- [no] entry entry-id
- action {deny | permit}
- description description-string
- no description
- match command-string
- no match
- renum old-entry-number new-entry-number
RADIUS commands
config
- system
- security
- [no] radius
- [no] accounting
- accounting-port port
- no accounting-port
- [no] authorization
- port port
- no port
- retry count
- no retry
- server server-index address ip-address secret key [hash | hash2]
- no server server-index
- [no] shutdown
- timeout seconds
- no timeout
- [no] use-default-template
SSH commands
config
- system
- security
- ssh
- client-cipher-list protocol-version version
- cipher index name cipher-name
- no cipher index
- client-mac-list
- mac index name mac-name
- no mac index
- client-kex-list
- kex index name kex-name
- no kex index
- [no] permit-empty-passwords
- [no] preserve-key
- server-cipher-list protocol-version version
- cipher index name cipher-name
- no cipher index
- server-mac-list
- mac index name mac-name
- no mac index
- server-kex-list
- kex index name kex-name
- no kex index
- [no] server-shutdown
- [no] version ssh-version
TACPLUS commands
config
- system
- security
- [no] tacplus
- accounting [record-type {start-stop | stop-only}]
- no accounting
- [no] authorization
- server server-index address ip-address secret key [hash | hash2] [port port]
- no server server-index
- [no] shutdown
- timeout seconds
- no timeout
- [no] use-default-template
User commands
config
- system
- security
- [no] user user-name
- [no] access [ftp] [snmp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli] [netconf]
- console
- [no] cannot-change-password
- login-exec url-prefix:source-url
- no login-exec
- [no] member user-profile-name [user-profile-name…(up to 8 max)]
- [no] new-password-at-login
- home-directory url-prefix [directory] [directory/directory…]
- no home-directory
- password [password] [hash | hash2]
- public-keys
- ecdsa
- ecdsa-key ecdsa-public-key-id [create]
- no ecdsa-key ecdsa-public-key-id
- description description-string
- no description
- key-value ecdsa-public-key-value
- no key-value
- rsa
- rsa-key rsa-public-key-id [create]
- no rsa-key rsa-public-key-id
- description description-string
- no description
- key-value rsa-public-key-value
- no key-value
- [no] restricted-to-home
- [no] save-when-restricted
- snmp
- authentication none
- authentication authentication authentication-protocol key-1 [privacy none] [hash | hash2]
- authentication authentication authentication-protocol key-1 privacy privacy-protocol key-2 [hash | hash2]
- no authentication
- group group-name
- no group
User template commands
config
- system
- security
- user-template {tacplus_default | radius_default}
- [no] access [ftp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli]
- console
- login-exec url-prefix:source-url
- no login-exec
- home-directory url-prefix [directory][directory/directory..]
- no home-directory
- profile user-profile-name
- no profile
- [no] restricted-to-home
- [no] save-when-restricted
Dot1x commands
config
- system
- security
- dot1x
- radius-plcy name [create]
- retry count
- no retry
- server server-index address ip-address secret key [hash|hash2] [auth-port auth-port] [acct-port acct-port] [type server-type]
- source-address ip-address
- [no] shutdown
- timeout seconds
- no timeout
- [no] shutdown
Keychain commands
config
- system
- security
- [no] keychain keychain-name
- description description-string
- no description
- direction {uni | bi}
- bi
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entry entry-id
- begin-time date hours-minutes [UTC]
- begin-time {now| forever}
- no begin-time
- [no] shutdown
- tolerance [seconds | forever]
- uni
- receive
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entry entry-id
- begin-time date hours-minutes [UTC]
- begin-time {now| forever}
- no begin-time
- end-time date hours-minutes [UTC]
- end-time {now| forever}
- no end-time
- [no] shutdown
- tolerance [seconds | forever]
- send
- entry entry-id [key authentication-key | hash-key | hash2-key [hash | hash2] algorithm algorithm]
- no entry entry-id
- begin-time date hours-minutes [UTC]
- begin-time {now| forever}
- no begin-time
- [no] shutdown
- [no] shutdown
- tcp-option-number
- receive option-number
- send option-number
Login control commands
config
- system
- login-control
- [no] exponential-backoff
- ftp
- inbound-max-sessions value
- no inbound-max-sessions
- idle-timeout {minutes | disable}
- no idle-timeout
- [no] login-banner
- motd {url url-prefix: source-url | text motd-text-string}
- no motd
- pre-login-message login-text-string [name]
- no pre-login-message
- ssh
- disable-graceful-shutdown
- inbound-max-sessions
- outbound-max-sessions
- telnet
- enable-graceful-shutdown
- inbound-max-sessions value
- no inbound-max-sessions
- outbound-max-sessions value
- no outbound-max-sessions
IPsec commands
config
- ipsec
- static-sa sa-name
- no static-sa
- authentication auth-algorithm ascii-key ascii-string
- authentication auth-algorithm hex-key hex-string [hash | hash2]
- no authentication
- description description-string
- no description
- direction ipsec-direction
- no direction
- protocol ipsec-protocol
- no protocol
- spi spi
- no spi
Show commands
Security
show
- system
- security
- access-group [group-name]
- authentication [statistics]
- dist-cpu-protection
- policy [name] [association | detail]
- keychain [key-chain] [detail]
- management-access-filter
- ip-filter [entry entry-id]
- ipv6-filter [entry entry-id]
- password-options
- profile [user-profile-name]
- source-address
- ssh
- user [user-name] [detail]
- view [view-name] [detail]
Login control
show
- users
Clear commands
Debug commands
debug
- router
- radius
- no radius
- detail-level {low | medium | high}
- no detail-level
- packet-type [authentication] [accounting] [coa]
- no packet-type
- radius-attr type attribute-type [transaction]
- radius-attr type attribute-type [transaction] {address | hex | integer | string} value attribute-value
- radius-attr vendor vendor-id type attribute-type [transaction] [encoding encoding-type]
- radius-attr vendor vendor-id type attribute-type [transaction] [encoding encoding-type] {address | hex | integer | string} value attribute-value
- no radius-attr type attribute-type
- no radius-attr type attribute-type {address | hex | integer | string} value attribute-value
- no radius-attr vendor vendor-id type attribute-type
- no radius-attr vendor vendor-id type attribute-type {address | hex | integer | string} value attribute-value
- server-address ip-address
- no server-address ip-address
Command descriptions
Configuration commands
General security commands
description
Syntax
description description-string
no description
Context
config>system>security>mgmt-access-filter>ip-filter>entry config>system>security>mgmt-access-filter>ipv6-filter>entry
config>sys>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
config>system>security>user>public-keys>ecdsa>ecdsa-key
config>system>security>user>public-keys>rsa>rsa-key
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode
Description
This command creates a text description stored in the configuration file for a configuration context.
This command associates a text string with a configuration context to help identify the context in the configuration file.
The no form of this command removes the string.
Parameters
- string
The description character string. Allowed values are any string up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
shutdown
Syntax
[no] shutdown
Context
config>system>security>mgmt-access-filter
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command administratively disables the entity. When disabled, an entity does not change, reset, or remove any configuration settings or statistics. Many entities must be explicitly enabled using the no shutdown command. The operational state of the entity is disabled as well as the operational state of any entities contained within. Many objects must be shut down before they may be deleted.
The no form of this command puts an entity into the administratively enabled state.
Default
no shutdown
security
Syntax
security
Context
config>system
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure security settings.
Security commands manage user profiles and user membership. Security commands also manage user login registrations.
ftp-server
Syntax
[no] ftp-server
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables FTP servers running on the system.
FTP servers are disabled by default. At system startup, only SSH server are enabled.
The no form of this command disables FTP servers running on the system.
Default
no ftp-server
hash-control
Syntax
hash-control [read-version {1 | 2 | all}] [write-version {1 | 2}]
no hash-control
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the system to encrypt all passwords, MD5 keys, and so on using specific algorithms.
Whenever the user executes a save or info command, the system will encrypt all passwords, MD5 keys, and so on for security reasons. At present, two algorithms exist.
The first algorithm is a simple, short key that can be copied and pasted in a different location when the user needs to configure the same password. However, because it is the same password and the hash key is limited to the password/key, even the casual observer will notice that it is the same key.
The second algorithm is a more complex key, and cannot be copied and pasted in different locations in the configuration file. In this case, if the same key or password is used repeatedly in different contexts, each encrypted (hashed) version will be different.
Default
all
Parameters
- read-version {1 | 2 | all}
Both versions 1 and 2 will be accepted by the system. Otherwise, only the selected version will be accepted when reading configuration or exec files. The presence of incorrect hash versions will abort the script/startup.
- write-version {1 | 2}
Select the hash version that will be used the next time the configuration file is saved (or an info command is executed). Be careful to save the read and write version correctly, so that the file can be properly processed after the next reboot or exec.
source-address
Syntax
source-address
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context specify the source address that should be used in all unsolicited packets sent by the application.
This feature only applies on in-band interfaces and does not apply on the out-band management interface. Packets going out the management interface will keep using that as the source IP address. That is, when the RADIUS server is reachable through both the management interface and a network interface, the management interface is used despite whatever is configured under the source-address statement.
application
Syntax
application app [ip-int-name | ip-address]
no application app
Context
config>system>security>source-address
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the application to use the source IPv4 address specified by the source-address command.
Parameters
- app
Specifies the application name.
- ip-int-name | ip-address
Specifies the name of the IP interface and IP address. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
application6
Syntax
application6 app [ipv6-address]
no application6 app
Context
config>system>security>source-address
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the application to use the source IPv6 address specified by the source address.
Parameters
- app
Specifies the application name.
- ipv6-address
Specifies the name of the IPv6 address.
telnet-server
Syntax
[no] telnet-server
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables Telnet servers running on the system.
Telnet servers are off by default. At system startup, only SSH servers are enabled.
Telnet servers in networks limit a Telnet client to three login attempts. The Telnet server disconnects the Telnet client session after the third attempt.
The no form of this command disables Telnet servers running on the system.
Login, Telnet, SSH and FTP commands
exponential-backoff
Syntax
[no] exponential-backoff
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the exponential backoff of the login prompt. The exponential-backoff command is used to deter dictionary attacks, when a malicious user can gain access to the CLI by using a script to try admin with any conceivable password.
The no form of this command disables exponential backoff.
Default
no exponential-backoff
ftp
Syntax
ftp
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure FTP login control parameters.
idle-timeout
Syntax
idle-timeout {minutes | disable}
no idle-timeout
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the idle timeout for FTP, console, or Telnet sessions before the session is terminated by the system.
By default, an idle FTP, console, SSH, or Telnet session times out after 30 minutes of inactivity. This timer can be set per session.
The no form of this command reverts to the default value.
Default
idle-timeout 30
Parameters
- minutes
Specifies the idle timeout in minutes. Allowed values are 1 to 1440. A value of 0 implies that the sessions never timeout.
- disable
Keyword to specify that a session will never timeout. To re-enable idle timeout, enter the command without the disable option.
inbound-max-sessions
Syntax
inbound-max-sessions value
no inbound-max-sessions
Context
config>system>login-control>ftp
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the maximum number of concurrent inbound FTP sessions.
This value is the combined total of inbound and outbound sessions.
The no form of this command reverts to the default value.
Default
3
Parameters
- value
Specifies the maximum number of concurrent FTP sessions on the node.
inbound-max-sessions
Syntax
inbound-max-sessions value
no inbound-max-sessions
Context
config>system>login-control>telnet
config>system>login-control>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This parameter limits the number of inbound Telnet and SSH sessions. A maximum of 15 Telnet and SSH connections can be established to the router. The local serial port cannot be disabled.
The no form of this command reverts to the default value.
Default
5
Parameters
- value
Specifies the maximum number of concurrent inbound Telnet sessions, expressed as an integer.
login-banner
Syntax
[no] login-banner
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables or disables the display of a login banner. The login banner contains the 7210 SAS copyright and build date information for a console login attempt.
The no form of this command causes only the configured pre-login message and a generic login prompt to display.
login-control
Syntax
login-control
Context
config>system
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure the session control for the console, Telnet, and FTP.
motd
Syntax
motd {url url-prefix: source-url | text motd-text-string}
no motd
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates the message of the day displayed after a successful console login. Only one message can be configured.
The no form of this command removes the message.
Parameters
- url url-prefix: source-url
When the message of the day is present as a text file, provide both url-prefix and the source-url of the file containing the message of the day. The URL prefix can be local or remote.
- text motd-text-string
Specifies the text of the message of the day. The motd-text-string must be enclosed in double quotes. Multiple text strings are not appended to one another.
Some special characters can be used to format the message text. The ‟\n” character creates multi-line MOTDs and the ‟\r” character restarts at the beginning of the new line. For example, entering ‟\n\r” will start the string at the beginning of the new line, while entering ‟\n” will start the second line below the last character from the first line.
outbound-max-sessions
Syntax
outbound-max-sessions value
no outbound-max-sessions
Context
config>system>login-control>telnet
config>system>login-control>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This parameter limits the number of outbound Telnet and SSH sessions. A maximum of 15 Telnet and SSH connections can be established from the router. The local serial port cannot be disabled.
The no form of this command reverts to the default value.
Default
outbound-max-sessions 5
Parameters
- value
Specifies the maximum number of concurrent outbound Telnet sessions, expressed as an integer.
pre-login-message
Syntax
pre-login-message login-text-string [name]
no pre-login-message
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates a message displayed before console login attempts on the console via Telnet.
Only one message can be configured. If multiple pre-login-messages are configured, the last message entered overwrites the previous entry.
It is possible to add the name parameter to an existing message without affecting the current pre-login-message.
The no form of this command removes the message.
Parameters
- login-text-string
The string can be up to 900 characters. Any printable, 7-bit ASCII characters can be used. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
- name
Keyword to always display the configured system name first in the login message. To remove the name from the login message, the message must be cleared and a new message entered without the name.
ssh
Syntax
ssh
Context
config>system>security
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure the SSH parameters.
disable-graceful-shutdown
Syntax
[no] disable-graceful-shutdown
Context
config>system>login-control>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables graceful shutdown of SSH sessions.
The no form of this command disables graceful shutdown of SSH sessions.
client-cipher-list
Syntax
client-cipher-list protocol-version version
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the configuration of a list of allowed ciphers by the SSH client.
Parameters
- version
Specifies the SSH version.
cipher
Syntax
cipher index name cipher-name
no cipher index
Context
config>system>security>ssh>client-cipher-list
config>system>security>ssh>server-cipher-list
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the configuration of a cipher. Client-ciphers are used when the 7210 SAS is acting as an SSH client. Server ciphers are used when the 7210 SAS is acting as an SSH server.
The no form of this command removes the index and cipher name from the configuration.
Default
no cipher index
Parameters
- index
Specifies the index of the cipher in the list.
- cipher-name
Specifies the algorithm used when performing encryption or decryption.
client-mac-list
Syntax
client-mac-list
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure SSH MAC algorithms for the 7210 SAS acting as a client.
mac
Syntax
mac index name mac-name
no mac index
Context
config>system>security>ssh>client-mac-list
config>system>security>ssh>server-mac-list
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command allows the user to configure SSH MAC algorithms for the 7210 SAS acting as an SSH server or an SSH client.
The no form of this command removes the specified mac index.
Default
no mac index
Parameters
- index
Specifies the index of the algorithm in the list.
- mac-name
Specifies the algorithm for calculating the message authentication code.
client-kex-list
Syntax
client-kex-list
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure SSH KEX algorithms for the 7210 SAS in the client role.
By default, the SSH advertises a KEX list that contains the following algorithms:
diffie-hellman-group16-sha512
diffie-hellman-group14-sha256
diffie-hellman-group14-sha1
diffie-hellman-group-exchange-sha1
diffie-hellman-group1-sha1
kex
Syntax
kex index name kex-name
no kex index
Context
config>system>security>ssh>client-kex-list
config>system>security>ssh>server-kex-list
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures phase 1 SSHv2 KEX algorithms for the 7210 SAS in the SSH server or client role.
The no form of this command removes the specified KEX index. If all KEX indexes are removed, the default list is used.
Parameters
- index
Specifies the index of the algorithm in the list. The lowest KEX index is negotiated first and the highest index, which is at the bottom of the KEX list, is negotiated last in the SSH negotiation.
- kex-name
Specifies the KEX algorithm for computing the shared secret key.
permit-empty-passwords
Syntax
[no] permit-empty-passwords
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures permissions that allows users with empty password strings to log in to the system.
The no form of this command prevents users with empty password strings from logging in.
Default
permit-empty-passwords
preserve-key
Syntax
[no] preserve-key
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the server to save private keys, public keys, and host key files. It is restored following a system reboot or an SSH server restart.
The no form of this command specifies that the keys will be held in memory by the SSH server and is not restored following a system reboot.
Default
no preserve-key
server-cipher-list
Syntax
server-cipher-list protocol-version version
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables the configuration of the list of allowed ciphers by the SSH server.
Parameters
- version
Specifies the SSH version.
server-kex-list
Syntax
server-kex-list
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure SSH KEX algorithms for the 7210 SAS in the SSH server role.
By default, the SSH advertises a KEX list that contains the following algorithms:
diffie-hellman-group16-sha512
diffie-hellman-group14-sha256
diffie-hellman-group14-sha1
diffie-hellman-group-exchange-sha1
diffie-hellman-group1-sha1
server-mac-list
Syntax
server-mac-list
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command allows the user to configure SSH MAC algorithms for the 7210 SAS acting as an SSH server.
server-shutdown
Syntax
[no] server-shutdown
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the SSH servers running on the system. At system startup, only the SSH server is enabled.
version
Syntax
version ssh-version
no version
Context
config>system>security>ssh
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the SSH protocol version that will be supported by the SSH server.
Default
version 2
Parameters
- ssh-version
Specifies the SSH version.
telnet
Syntax
telnet
Context
config>system>login-control
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure the Telnet login control parameters.
enable-graceful-shutdown
Syntax
[no] enable-graceful-shutdown
Context
config>system>login-control>telnet
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables graceful shutdown of Telnet sessions.
The no form of this command disables graceful shutdown of Telnet sessions.
Management Access Filter commands
management-access-filter
Syntax
[no] management-access-filter
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context edit management access filters and to reset match criteria.
Management access filters control all traffic in and out. They can be used to restrict management of the router by other nodes outside either specific networks or subnetworks or through designated ports.
Management filters, as opposed to other traffic filters, are enforced by system software.
The no form of this command removes management access filters from the configuration.
ip-filter
Syntax
[no] ip-filter
Context
config>system>security>mgmt-access-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure management access IP filter parameters.
ipv6-filter
Syntax
[no] ipv6-filter
Context
config>system>security>mgmt-access-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure management access IPv6 filter parameters.
default-action
Syntax
default-action {permit | deny | deny-host-unreachable}
Context
config>system>security>mgmt-access-filter>ip-filter
config>system>security>mgmt-access-filter>ipv6-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the default action for management access in the absence of a specific management access filter match.
The default-action is applied to a packet that does not satisfy any match criteria in any of the management access filters. Whenever management access filters are configured, the default-action must be defined.
Parameters
- permit
Specifies that packets not matching the configured selection criteria in any of the filter entries will be permitted.
- deny
Specifies that packets not matching the selection criteria be denied and that an ICMP host unreachable message will not be issued.
- deny-host-unreachable
Specifies that packets not matching the selection criteria be denied and a host unreachable message will be issued.
entry
Syntax
[no] entry entry-id
Context
config>system>security>mgmt-access-filter>ip-filter
config>system>security>mgmt-access-filter>ipv6-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a management access filter entry. Multiple entries can be created with unique entry-id numbers. The 7210 SAS OS exits the filter upon the first match found and executes the actions according to the respective action command. For this reason, entries must be sequenced correctly from most to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action defined to be considered complete. Entries without the action keyword are considered incomplete and inactive.
The no form of this command removes the specified entry from the management access filter.
Parameters
- entry-id
An entry ID uniquely identifies a match criteria and the corresponding action. Nokia recommends that entries be numbered in staggered increments. This allows users to insert a new entry in an existing policy without having to renumber the existing entries.
action
Syntax
action {permit | deny | deny-host-unreachable}
no action
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the action associated with the management access filter match criteria entry.
The action keyword is required. If no action is defined, the filter is ignored. If multiple action statements are configured, the last one overwrites previous configured actions.
If the packet does not meet any of the match criteria the configured default action is applied.
Parameters
- permit
Specifies that packets matching the configured criteria will be permitted.
- deny
Specifies that packets matching the configured selection criteria will be denied and that a ICMP host unreachable message will not be issued.
- deny-host-unreachable
Specifies that packets matching the configured selection criteria will be denied and that a host unreachable message will not be issued.
dst-port
Syntax
[no] dst-port port [mask]
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a source TCP or UDP port number or port range for a management access filter match criterion.
The no form of this command removes the source port match criterion.
Parameters
- port
Specifies the source TCP or UDP port number as match criteria.
- mask
Specifies mask used to specify a range of source port numbers as the match criterion.
This 16-bit mask can be configured using the formats listed in the following table.
Table 12. 16-bit mask configurations Format style Format syntax Example Decimal
DDDDD
63488
Hexadecimal
0xHHHH
0xF800
Binary
0bBBBBBBBBBBBBBBBB
0b1111100000000000
To select a range from 1024 up to 2047, specify 1024 0xFC00 for value and mask.
fragment
Syntax
[no] fragment {true | false}
Context
config>system>security>mgmt-access-filter>ip-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies fragmented or non-fragmented IP packets as an IP filter match criterion.
An entry containing Layer 4 match criteria will not match non-initial (2nd, 3rd, and so on) fragments of a fragmented packet because only the first fragment contains the Layer 4 information.
The no form of this command removes the match criterion.
Default
no fragment
Parameters
- true
Specifies to match on all fragmented IP packets. A match will occur for all packets that have either the MF (more fragment) bit set or have the Fragment Offset field of the IP header set to a non-zero value.
- false
Specifies to match on all non-fragmented IP packets. Non-fragmented IP packets are packets that have the MF bit set to zero and have the Fragment Offset field also set to zero.
l4-src-port
Syntax
[no] l4-src-port port [mask]
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a source TCP or UDP port number for an IP filter match criterion.
an entry containing L4 match criteria will not match non-initial (2nd, 3rd, and so on) fragments of a fragmented packet because only the first fragment contains the L4 information.
The no form of this command removes the source port match criterion.
Default
no l4-src-port
Parameters
- port
Specifies the source port number to be used as a match criteria expressed as a decimal integer.
- mask
Specifies the mask in dotted-decimal notation
flow-label
Syntax
flow-label value
no flow-label
Context
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures flow label match conditions. Flow labeling enables the labeling of packets belonging to particular traffic flows for which the sender requests special handling, such as non default quality of service or real-time service.
Parameters
- value
Specifies the flow identifier in an IPv6 packet header that can be used to discriminate traffic flows, in accordance with RFC 3595, Textual Conventions for IPv6 Flow Label.
log
Syntax
[no] log
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables match logging. When enabled, matches on this entry will cause the security event mafEntryMatch to be raised.
Default
no log
next-header
Syntax
next-header next-header
no next-header
Context
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the next header to match. The protocol type, such as TCP, UDP, or OSPF, is identified by its respective protocol number. Well-known protocol numbers include ICMP(1), TCP(6), and UDP(17).
Parameters
- next-header
Specifies the IP protocol field for IPv4 Management Access Filter (MAF), and the next header type to be used in the match criteria for this MAF entry for IPv6.
protocol
Syntax
[no] protocol protocol-id
Context
config>system>security>mgmt-access-filter>ip-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures an IP protocol type to be used as a management access filter match criterion.
The protocol type, such as TCP, UDP, and OSPF, is identified by its respective protocol number. Well-known protocol numbers include ICMP (1), TCP (6), and UDP (17).
The no form this command removes the protocol from the match criteria.
Parameters
- protocol
Specifies the protocol number for the match criterion.
router
Syntax
router {router-instance}
no router
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a router name or service ID to be used as a management access filter match criterion.
The no form of this command removes the router name or service ID from the match criteria.
Default
base
Parameters
- router-instance
Specifies the router name.
renum
Syntax
renum old-entry-number new-entry-number
Context
config>system>security>mgmt-access-filter>ip-filter
config>system>security>mgmt-access-filter>ipv6-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command renumbers existing management access filter entries to re-sequence filter entries.
The system exits on the first match found and executes the actions in accordance with the accompanying action command. This may require some entries to be renumbered differently from most to least explicit.
Parameters
- old-entry-number
Specifies the entry number of the existing entry.
- new-entry-number
Specifies the new entry number that will replace the old entry number.
src-port
Syntax
src-port {port-id | lag lag-id}
no src-port
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command restricts ingress management traffic to either the CPM Ethernet port or any other logical port (LAG or port) on the device.
When the source interface is configured, only management traffic arriving on those ports satisfy the match criteria.
The no form of this command reverts to the default value.
Default
any interface
Parameters
- port-id
Specifies the port ID in the following format: slot[/mda]/port.
Syntax: port-id: slot/mda/port
src-ip
Syntax
[no] src-ip {ip-prefix/prefix-length | ip-prefix> netmask}
Context
config>system>security>mgmt-access-filter>ip-filter>entry
config>system>security>mgmt-access-filter>ipv6-filter>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a source IP address range to be used as a management access filter match criterion.
To match on the source IP address, specify the address and the associated mask (that is, 10.1.0.0/16). The conventional notation of 10.1.0.0 255.255.0.0 can also be used.
The no form of this command removes the source IP address match criterion.
Parameters
- ip-prefix/prefix-length
Specifies the IP prefix used for IP match criteria in dotted-decimal notation. It can be IPv4 or an IPv6 prefix.
- netmask
Specifies the subnet mask in dotted-decimal notation.
Distributed CPU protection commands
dist-cpu-protection
Syntax
dist-cpu-protection
Context
config>system>security
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
Commands in this context configure distributed CPU protection.
policy
Syntax
policy policy-name [create]
no policy policy-name
Context
config>sys>security>dist-cpu-protection
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command configures one of the maximum 16 distributed CPU protection policies. These policies can be applied to objects such as SAPs.
Parameters
- policy-name
Specifies the policy name, up to 32 characters.
- create
Creates a new policy instance.
description
Syntax
description description-string
no description
Context
config>system>security>dist-cpu-protection>policy
config>system>security>dist-cpu-protection>policy>static-policer
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command creates a text description stored in the configuration file for a configuration context.
This command associates a text string with a configuration context to help identify the context in the configuration file.
The no form of this command removes the string.
Default
no description
Parameters
- string
Specifies the description character string. Allowed values are any string up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
protocol
Syntax
protocol name [create]
no protocol name
Context
config>sys>security>dist-cpu-protection>policy
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command creates the protocol for control in the policy.
For RVPLS, DCP rate-limits the packets arriving at the CPU, but for flooded traffic, ingress QoS or ACLs must be used.
When the no form of this command is used, the packets of the specified protocol are not enforced on the objects to which this DCP policy is assigned.
Parameters
- names
Specifies the protocol name.
- create
Creates a new protocol instance.
enforcement
Syntax
enforcement {static policer-name}
Context
config>sys>security>dist-cpu-protection>policy>protocol
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command configures the enforcement method for the protocol. When the static keyword is used, the protocol is always enforced using a static policer. Multiple protocols can reference the same static policer. When multiple protocols are configured to reference the same policer, each protocol is assigned an independent instance of the policer. The policer is not shared among the multiple protocols that are referencing it.
Default
enforcement dynamic local-mon-bypass
Parameters
- static
Specifies that the protocol is always enforced using a static policer.
- policer-name
Specifies the name of the static policer, up to 32 characters.
static-policer
Syntax
static-policer policer-name [create]
static-policer policer-name
Context
config>sys>security>dist-cpu-protection>policy
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command configures a static enforcement policer that can be referenced by one or more protocols in the policy. When the policer name is referenced by a protocol, this policer is instantiated for each protocol and each object (for example, SAP) that is created and references this policy. If there is no policer resource available, the object is blocked from being created. Multiple protocols can use the same static policer. When multiple protocols reference the same policer, each protocol gets an independent instance of the policer. The policer is not shared among the multiple protocols that are referencing it.
Parameters
- policer-name
Specifies the name of the policer, up to 32 characters.
- create
Keyword to create a new static-policer instance.
exceed-action
Syntax
exceed-action {discard | none}
Context
config>sys>security>dist-cpu-protection>policy>static-policer
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command controls the action performed upon the extracted control packets when the configured policer rates are exceeded.
Default
exceed-action none
Parameters
- discard
Keyword to discards packets that are non-conformant.
- none
Keyword to send packets to the CPU instead of discarding them.
log-events
Syntax
log-events [verbose]
no log-events
Context
config>sys>security>dist-cpu-protection>policy>static-policer
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command controls the creation of log events related to static policer status and activity.
Default
log-events
Parameters
- verbose
Keyword to send the same events as just log events. The optional keyword verbose includes events used during debugging, tuning, and investigation.
rate
Syntax
rate {kbps kilobits-per-second | max} {[mbs size] [bytes | kilobytes]}
no rate
Context
config>sys>security>dist-cpu-protection>policy>static-policer
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command configures the rate and burst tolerance for the policer in either a packet rate or a bit rate.
The hardware may not be able to rate limit to the exact configured parameters. In this case, the
configured parameters are adapted to the closest supported rate. The actual (operational)
parameters can be seen in CLI, for example, show service id 33 sap 1/1/3:33
dist-cpu-protection detail.
Default
rate kbps max mbs default
Parameters
- kilobits-per-second
Specifies the kilobits per second.
- size
Specifies the tolerance for the kbps rate.
- bytes | kilobytes
Specifies that the units of the mbs size parameter are either in bytes or kilobytes.
Password commands
admin-password
Syntax
admin-password password [hash | hash2]
no admin-password
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the context (with administrative permissions) to configure a password that enables a user to become an administrator.
This password is valid only for one session. When enabled, no authorization to TACACS+ or RADIUS is performed and the user is locally regarded as an administrative user.
This functionality can be enabled in two contexts:
config>system>security>password>admin-password
<global> enable-admin
See the description for the enable-admin command. If the admin-password command is configured in the config>system>security>password context, any user can enter the special administrative mode by entering the enable-admin command.
The enable-admin command is in the default profile. By default, all users are given access to this command.
When the enable-admin command is entered, the user is prompted for a password. If the password is correct, the user is given unrestricted access to all commands.
The minimum length of the password is determined by the minimum-length command. The complexity requirements for this password are determined by the configuration in the complexity-rules context.
The password argument of this command is not sent to the servers. This is consistent with other commands that configure secrets.
Usernames and passwords in the FTP and TFTP URLs will not be sent to the authorization or accounting servers when the file>copy source-url dest-url command is executed.
For example:
file copy ftp://test:secret@131.12.31.79/test/srcfile cf1:\destfile
In this example, the username 'test' and password 'secret' will not be sent to the AAA servers (or to any logs). They will be replaced with '****'.
The configure system security password hashing command affects the maximum number of characters that can be used to configure the password parameter.
The no form of this command removes the administrative password from the configuration.
Default
no admin-password
Parameters
- password
Specifies the password, which enables a user to become a system administrator. The maximum length can be up to 56 characters if unhashed, 32 characters if the hash keyword is specified, and 54 characters if the hash2 keyword is specified, 60 characters if hashed with bcrypt, or 87 to 92 characters if hashed with sha2-pbkdf2.
- hash
Specifies that the key is entered in an encrypted form. If the hash keyword is not configured, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form.
- hash2
Specifies the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
enable-admin
Syntax
enable-admin
Context
<global>
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command is in the default profile. By default, all users are given access to this command.
See the description for the admin-password command. If the admin-password command is configured in the config>system>security>password context, then any user can enter the special administrative mode by entering the enable-admin command.
When the enable-admin command is entered, the user is prompted for a password. If the password is correct, the user is given unrestricted access to all commands.
The minimum length of the password is determined by the minimum-length command. The complexity requirements for the password is determined by the configuration in the complexity-rules context.
There are two ways to verify that a user is in the enable-admin mode.
An administrator can enter the show users command know which users are in this mode.
Enter the enable-admin command again at the root prompt and an error message will be returned.
Output
The following output shows an example of an error message when the enable-admin command is entered at the prompt again and the user is already in the enable-admin mode.
Sample output
A:ALA-1# show users
===============================================================================
User Type From Login time Idle time
===============================================================================
admin Console -- 10AUG2006 13:55:24 0d 19:42:22
admin Telnet 10.20.30.93 09AUG2006 08:35:23 0d 00:00:00 A
-------------------------------------------------------------------------------
Number of users : 2
'A' indicates user is in admin mode
===============================================================================
A:ALA-1#
A:ALA-1# enable-admin
MINOR: CLI Already in admin mode.
A:ALA-1#
aging
Syntax
aging days
no aging
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of days a user password is valid before the user must change their password. This parameter can be used to force the user to change the password at the configured interval.
The no form of this command reverts to the default value.
Parameters
- days
Specifies the maximum number of days the password is valid.
attempts
Syntax
attempts count [time minutes1 [lockout minutes2]
no attempts
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a threshold value of unsuccessful login attempts allowed in a specified time frame. The threshold for the number of login attempts can be configured by using the CLI parameter count. An SNMP trap is generated by the device when the number of login attempts exceeds the configured threshold. Generation of the trap can be suppressed using the config>log>event-control command.
By default, the device generates a trap when the login attempts exceed the configured threshold. The trap carries information about the user ID used for the login attempt. An SNMP trap will not be sent for every failed attempt.
If the threshold is exceeded, the user is locked out for a specified time period.
If multiple attempts commands are entered, each command overwrites the previously entered command.
The no form of this command reverts to the default values.
Default
attempts 3 time 5 lockout 10
Parameters
- count
Specifies the number of unsuccessful login attempts allowed for the specified time. This is a mandatory value that must be explicitly entered.
- time minutes
Specifies the period of time, in minutes, that a specified number of unsuccessful attempts can be made before the user is locked out.
- lockout minutes
Specifies the lockout period, in minutes, where the user is not allowed to login. Allowed values are decimal integers.
authentication-order
Syntax
authentication-order [method-1] [method-2] [method-3] [exit-on-reject]
no authentication-order
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the sequence in which password authentication, authorization, and accounting is attempted among RADIUS, TACACS+, and local passwords.
The order should be from the most preferred authentication method to the least preferred. The presence of all methods in the command line does not guarantee that they are all operational. Specifying options that are not available delays user authentication.
If all (operational) methods are attempted and no authentication for a particular login has been granted, an entry in the security log registers the failed attempt. The attempted login identification and originating IP address are logged with the a timestamp.
The no form of this command reverts to the default authentication sequence.
Default
authentication-order radius tacplus local
Parameters
- method-1
Specifies the first password authentication method to attempt.
- method-2
Specifies the second password authentication method to attempt.
- method-3
Specifies the third password authentication method to attempt.
- radius
Specifies the RADIUS authentication.
- tacplus
Specifies the TACACS+ authentication.
- local
Specifies the password authentication based on the local password database.
- exit-on-reject
When enabled and if one of the AAA methods configured in the authentication order sends a reject, the next method in the order will not be tried. If the exit-on-reject keyword is not specified and one AAA method sends a reject, the next AAA method will be attempted. If in this process, all the AAA methods are exhausted, it will be considered as a reject.
A rejection is distinct from an unreachable authentication server. When the exit-on-reject keyword is specified, authorization and accounting will only use the method that provided an affirmation authentication; only if that method is no longer readable or is removed from the configuration will other configured methods be attempted. If the local keyword is the first authentication, exit-on-reject is configured, and the user does not exist, the user will not be authenticated.
The user is authenticated locally, then other methods, if configured, will be used for authorization and accounting.
If the user is configured locally but without console access, login will be denied.
complexity-rules
Syntax
complexity-rules
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context define a list of rules for configurable password options.
allow-user-name
Syntax
[no] allow-user-name
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the username to be used as part of the password.
The no form of this command does not allow the username to be used as part of the password.
credits
Syntax
credits [lowercase credits] [uppercase credits] [numeric credits] [special-character credits]
no credits
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
The maximum credits given for usage of the different character classes in the local passwords.
The no form of this command reverts to the default value.
Default
no credits
Parameters
- credits
Specifies the number of credits that can be used for each characters class.
minimum-classes
Syntax
minimum-classes minimum
no minimum-classes
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command forces the use of at least the specified number of different character classes.
The no form of this command reverts to the default value.
Default
no minimum-classes
Parameters
- minmum
Specifies the minimum number of classes to be configured.
health-check
Syntax
[no] health-check [interval interval]
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies that RADIUS, TACACS+, and LDAP servers are monitored for 3 seconds each at 30 second intervals. Servers that are not configured will have 3 seconds of idle time. If in this process a server is found to be unreachable, or a previously unreachable server starts responding, a trap will be sent based on the server type.
The no form of this command disables the periodic monitoring of the RADIUS, TACACS+, and LDAP servers. In this case, the operational status for the active server will be up if the last access was successful.
Parameters
- interval
Specifies the polling interval for RADIUS, TACACS+, and LDAP servers.
history
Syntax
history size
no history
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures how many previous passwords a new password is matched against.
Default
no history
Parameters
- size
Specifies how many previous passwords a new password is matched against.
minimum-age
Syntax
minimum-age [days days] [hrs hours] [min minutes] [sec seconds]
no minimum-age
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the minimum required age of a password before it can be changed again.
The no form of this command removes the minimum password age requirement.
Default
no minimum-age
Parameters
- days
Specifies the minimum number of days before a password can be changed again.
- hours
Specifies the minimum number of hours before a password can be changed again.
- minutes
Specifies the minimum number of minutes before a password can be changed again.
- seconds
Specifies the minimum number of seconds before a password can be changed again.
minimum-change
Syntax
minimum-change length
no minimum-change
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the minimum number of characters required to be different in the new password from a previous password.
The no form of this command removes the unique character requirement.
Default
no min-change
Parameters
- length
Specifies how many characters must be different in the new password from the old password.
minimum-length
Syntax
minimum-length length
no minimum-length
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the minimum number of characters required for locally administered passwords and keys used with SNMPv3 user authentication and encryption. See the configure system security user snmp authentication command for more information about the use of keys with SNMPv3-based authentication and encryption algorithms.
If multiple minimum-length commands are entered, each new command overwrites the previously configured password length.
The no form of this command reverts to default value.
Default
minimum-length 6
Parameters
- value
Specifies the minimum number of characters required for a locally administered password.
repeated-characters
Syntax
repeated-characters count
no repeated-characters
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of times a character can be repeated consecutively.
The no form of this command reverts to the default value.
Default
no repeated-characters
Parameters
- count
Specifies the minimum count of consecutively repeated characters.
required
Syntax
required [lowercase count] [uppercase count] [numeric count] [special-character count]
no required
Context
config>system>security>password>complexity-rules
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the minimum number of different character classes required.
The no form of this command reverts to the default value.
Default
no required
Parameters
- count
Specifies the minimum count of characters classes.
hashing
Syntax
hashing {bcrypt | sha2-pbkdf2}
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the password hashing algorithm.
Parameters
- bcrypt
Keyword to configure the bcrypt algorithm.
- sha2-pbkdf2
Keyword to configure the PBKDF2 algorithm.
health-check
Syntax
[no] health-check [interval interval]
Context
config>system>security>password
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies that RADIUS and TACACS+ servers are monitored for 3 seconds each at 30 second intervals. Servers that are not configured will have 3 seconds of idle time. If in this process a server is found to be unreachable, or a previously unreachable server starts responding, a trap will be sent based on the type of the server.
The no form of this command disables the periodic monitoring of the RADIUS and TACACS+ servers. In this case, the operational status for the active server will be up if the last access was successful.
Default
health-check
Parameters
- interval
Specifies the interval of the health check, in seconds.
password
Syntax
password
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure password management parameters.
public-keys
Syntax
public-keys
Context
config>system>security>user
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure public keys for SSH.
ecdsa
Syntax
ecdsa
Context
config>system>security>user>public-keys
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure ECDSA public keys.
ecdsa-key
Syntax
ecdsa-key ecdsa-public-key-id [create]
no ecdsa-key ecdsa-public-key-id
Context
config>system>security>user>public-keys>ecdsa
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates an ECDSA public key and associates it with the username. Multiple public keys can be associated with the user. The key ID is used to identify these keys for the user.
The no form of this command removes the configured ECDSA public keys.
Default
no ecdsa-key
Parameters
- create
Keyword to create an ECDSA key. The create keyword requirement can be enabled or disabled in the environment>create context.
- key-id
Specifies the key identifier.
key-value
Syntax
key-value public-key-value
no key-value
Context
config>system>security>user>public-keys>ecdsa>ecdsa-key
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a value for the ECDSA public key. The public key must be enclosed in quotation marks. The key is between 1 and 1024 bits.
The no form of this command removes the configured ECDSA public key value.
Default
no key-value
Parameters
- ecdsa-public-key-value
Specifies the public key value, up to 255 characters.
rsa
Syntax
rsa
Context
config>system>security>user>public-keys
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
Commands in this context configure RSA public keys.
rsa-key
Syntax
rsa-key rsa-public-key-id [create]
no rsa-key rsa-public-key-id
Context
config>system>security>user>public-keys>rsa
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command creates an RSA public key and associates it with the username. Multiple public keys can be associated with the user. The key ID is used to identify these keys for the user.
The no form of this command removes the configured RSA public keys.
Default
no rsa-key
Parameters
- create
Keyword to create the RSA key. The create keyword requirement can be enabled or disabled in the environment>create context.
- key-id
Specifies the key identifier.
key-value
Syntax
key-value rsa-public-key-value
no key-value
Context
config>system>security>user>public-keys>rsa>rsa-key
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures a value for the RSA public key. The public key must be enclosed in quotation marks. The key is between 768 and 4096 bits.
The no form of this command removes the configured public key value.
Default
no key-value
Parameters
- public-key-value
Specifies the public key value, up to 800 characters.
Profile management commands
action
Syntax
action {deny | permit}
Context
config>system>security>profile>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the action associated with the profile entry.
Parameters
- deny
Specifies that commands matching the entry command match criteria are denied.
- permit
Specifies that commands matching the entry command match criteria are permitted.
match
Syntax
match command-string
no match
Context
config>system>security>profile>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a command or command subtree.
Because the system exits when the first match is found, subordinate levels cannot be modified with subsequent action commands. More specific action commands should be entered with a lower entry number or in a profile that is evaluated before this profile.
All commands below the hierarchy level of the matched command are denied.
The no form of this command removes a match condition.
Parameters
- command-string
Specifies the CLI command or CLI tree level that is the scope of the profile entry.
copy
Syntax
copy {user source-user | profile source-profile} to destination [overwrite]
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command copies a profile or user from a source profile to a destination profile.
Parameters
- source-user
Specifies the user, up to 32 characters, to copy from. The user must already exist.
- source-profile
Specifies the profile, up to 32 characters, to copy from. The profile must already exist.
- destination
Specifies the destination profile, up to 32 characters, to which the profile is copied.
- overwrite
Specifies that the destination profile configuration will be overwritten with the copied source profile configuration. A profile will not be overwritten if the overwrite command is not specified.
default-action
Syntax
default-action {deny-all | permit-all | none}
Context
config>system>security>profile
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the default action to be applied when no match conditions are met.
Parameters
- deny-all
Sets the default of the profile to deny access to all commands.
- permit-all
Sets the default of the profile to permit access to all commands.
Note:The permit-all keyword does not change access to security commands. Security commands are only and always available to members of the super-user profile.
- none
Sets the default of the profile to no-action. This option is useful to assign multiple profiles to a user.
For example, if a user is a member of two profiles and the default action of the first profile is permit-all, the second profile will never be evaluated because the permit-all is executed first. Set the first profile default action to none and if no match conditions are met in the first profile, the second profile will be evaluated. If the default action of the last profile is none and no explicit match is found, the default deny-all takes effect.
description
Syntax
description description-string
no description
Context
config>system>security>profile>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates a text description stored in the configuration file for a configuration context.
The description command associates a text string with a configuration context to help identify the context in the configuration file.
The no form of this command removes the string from the context.
Parameters
- description-string
Specifies the description character string. Allowed values are any string up to 80 characters composed of printable, 7-bit ASCII characters. If the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed within double quotes.
entry
Syntax
[no] entry entry-id
Context
config>system>security>profile
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command is used to create a user profile entry.
More than one entry can be created with unique entry-id numbers. The 7210 SAS exits when the first match is found and executes the actions according to the accompanying action command. Entries should be sequenced from most explicit to least explicit.
An entry may not have any match criteria defined (in which case, everything matches) but must have at least the keyword action for it to be considered complete.
The no form of this command removes the specified entry from the user profile.
Parameters
- entry-id
Specifies the entry ID. An entry ID uniquely identifies a user profile command match criteria and a corresponding action. If more than one entry is configured, the entry IDs should be numbered in staggered increments to allow users to insert a new entry without requiring renumbering of the existing entries.
profile
Syntax
[no] profile user-profile-name
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates user profiles for CLI command tree permissions.
Profiles are used to either deny or permit user console access to a hierarchical branch or to specific commands.
When the profiles are created, the users command assigns users to one or more profiles. You can define up to 16 user profiles but a maximum of 8 profiles can be assigned to a user. The user-profile-name can consist of up to 32 alphanumeric characters.
The no form of this command deletes a user profile.
Default
user-profile default
Parameters
- user-profile-name
Specifies the user profile name entered as a character string. The string is case sensitive and limited to 32 ASCII 7-bit printable characters with no spaces.
renum
Syntax
renum old-entry-number new-entry-number
Context
config>system>security>profile
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command renumbers profile entries to resequence the entries.
Because the 7210 SAS exits when the first match is found and executes the actions according to the accompanying action command, renumbering is useful to rearrange the entries from most explicit to least explicit.
Parameters
- old-entry-number
Specifies the entry number of an existing entry.
- new-entry-number
Specifies the new entry number.
User management commands
access
Syntax
[no] access [ftp] [snmp] [console] [scp-sftp] [console-port-cli] [ssh-cli] [telnet-cli] [netconf]
Context
config>system>security>user
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command grants user permission for FTP, SNMP, console, or lawful intercept (LI) access.
If a user requires access to more than one application, multiple applications can be specified in a single command. Multiple commands are treated additively.
The no access command denies permission for all management access methods. To deny a single access method, enter the no form of the command followed by the method to be denied, for example, no access ftp denies FTP access.
Parameters
- ftp
Keyword that specifies FTP permission.
- snmp
-
Keyword that specifies SNMP permission. This keyword is only configurable in the config>system>security>user context.
- console
Keyword that specifies console access (serial port or Telnet) permission.
- scp-sftp
-
Keyword that specifies SCP/SFTP access permission.
- console-port-cli
-
Keyword that specifies console port CLI access permission.
- ssh-cli
-
Keyword that specifies SSH CLI access permission.
- telnet-cli
-
Keyword that specifies Telnet CLI access permission.
- netconf
-
Keyword that specifies NETCONF access permission. This keyword is only supported for local users on the 7210 SAS-Mxp and 7210 SAS-Sx/S 1/10GE.
.
authentication
Syntax
authentication none
authentication authentication-protocol key-1 [privacy none] [hash | hash2]
authentication authentication-protocol key-1 privacy privacy-protocol key-2 [hash | hash2]
no authentication
Context
config>system>security>user>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the authentication and encryption method that the device uses to validate the user. The SNMP authentication allows the device to validate the managing node that issues the SNMP message and detect message tampering.
The no form of this command reverts to the default value.
Default
authentication none
Parameters
- authentication-protocol
Specifies the SNMP authentication protocol.
- privacy-protocol
Specifies the SNMP privacy protocol.
- hash
-
Keyword to indicate the encryption mechanism used to store the authentication and privacy keys in an encrypted format in the configuration file. When hash is not specified, non-encrypted characters can be entered. When hash is specified, the key is expected to be decrypted using the hash mechanism. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 keyword specified.
- hash2
-
Keyword to indicate the encryption mechanism used to store all specified keys in an encrypted format in the configuration file. For example, the hash2 encrypted variable cannot be copied and pasted to a different node. If the hash2 keyword is not specified, the key is assumed to be unencrypted in cleartext form. The hash2 keyword is the default mechanism used if hash is not specified. Therefore, the user does not need to specify hash2 explicitly while entering the key. For security, all keys are stored in encrypted form in the configuration file with the hash or hash2 keyword specified.
- key-1
-
Specifies the key-1 value for SNMP packet encryption.
- key-2
-
Specifies the key-2 value for SNMP packet encryption.
group
Syntax
group group-name
no group
Context
config>system>security>user>snmp
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command associates (or links) a user to a group name. The group name must be configured with the config>system>security>user>snmp>group command. The access command links the group with one or more views, security models, security levels, and read, write, and notify permissions
Parameters
- group-name
Specifies the group name, up to 32 alphanumeric characters, that is associated with this user. A user can be associated with one group name per security model.
cannot-change-password
Syntax
[no] cannot-change-password
Context
config>system>security>user>console
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command allows a user to change their password for FTP and console login.
To disable a user password change privilege, use the cannot-change-password form of this command.
The cannot-change-password flag is not replicated when a user copy is performed. A new-password-at-login flag is created instead.
Default
no cannot-change-password
console
Syntax
console
Context
config>system>security>user
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure user profile membership for the console (either Telnet or serial port user).
copy
Syntax
copy {user source-user | profile source-profile} to destination [overwrite]
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command copies a specific user configuration parameter to another (destination) user.
The password is set to a carriage return and a new password at login must be selected.
Parameters
- source-user
Specifies the user, up to 32 characters, to copy. The user must already exist.
- destination
Specifies the destination user or profile, up to 32 characters.
- overwrite
Specifies that the destination user configuration will be overwritten with the copied source user configuration. A configuration will not be overwritten if the overwrite command is not specified.
home-directory
Syntax
home-directory url-prefix [directory] [directory/directory ..]
no home-directory
Context
config>system>security>user
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the home directory of the user for file access. Use the CLI file commands and output modifiers such as > (file redirect) to access files locally, or remotely via the FTP and SCP. If the home directory does not exist, a warning message is displayed when the user logs in.
When restricted-to-home is configured, file access is denied unless the home-directory command is configured and the directory is created by an administrator.
The no form of this command removes the configured home directory of the user. The directory must be also removed by the administrator.
Default
no home-directory
Parameters
- url-prefix [directory] [directory/directory ..]
-
Specifies the local home directory URL prefix of the user and directory structure, up to 190 characters.
profile
Syntax
profile user-profile-name
no profile
Context
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the profile for the user based on this template.
Parameters
- user-profile-name
Specifies the user profile name entered as a character string. The string is case sensitive and limited to 32 ASCII 7-bit printable characters with no spaces.
login-exec
Syntax
[no] login-exec url-prefix: source-url
Context
config>system>security>user>console
config>system>security>user-template>console
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a user login exec file, which executes whenever the user successfully logs in to a console session.
Only one exec file can be configured. If multiple login-exec commands are entered for the same user, each subsequent entry overwrites the previous entry.
The no form of this command disables the login exec file for the user.
Parameters
- url-prefix:source-url
Specifies either a local or remote URL, up to 200 characters, that identifies the exec file that will be executed after the user successfully logs in.
member
Syntax
member user-profile-name [user-profile-name…up to 8max]
no member user-profile-name
Context
config>system>security>user>console
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command gives the user access to a profile.
A user can participate in up to eight profiles.
The no form of this command deletes user access to a profile.
Default
default
Parameters
- user-profile-name
Specifies the user profile name, up to 32 characters.
new-password-at-login
Syntax
[no] new-password-at-login
Context
config>system>security>user>console
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command forces the user to change a password at the next console login. The new password applies to FTP but the change can be enforced only by the console, SSH, or Telnet login.
The no form of this command does not force the user to change passwords.
Default
no new-password-at-login
password
Syntax
password [password] [hash | hash2]
Context
config>system>security>user
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the user password for console and FTP access.
The use of the hash keyword sets the initial password when the user is created or modifies the password of an existing user and specifies that the specific password was hashed using hashing algorithm version 1.
The password is stored in an encrypted format in the configuration file when specified. Passwords should be encased in double quotes (" ") at the time of the password creation. The double quote character (") is not accepted inside a password. It is interpreted as the start or stop delimiter of a string.
The use of the hash2 keyword specifies that the specific password is already hashed using hashing algorithm version 2. A semantic check is performed on the specific password field to verify if it is a valid hash 2 key to store in the database.
For example:
config>system>security# user testuser1
config>system>security>user$ password "zx/Uhcn6ReMOZ3BVrWcvk." hash2
config>system>security>user# exit
config>system>security# info
-------------------------------------
...
user "testuser1"
password "zx/Uhcn6ReMOZ3BVrWcvk." hash2
exit
...
-------------------------------------
config>system>security#
Parameters
- password
This is the password for the user that must be entered by this user during the login procedure. The minimum length of the password is determined by the minimum-length command. The maximum length is up to 20 characters if unhashed, 32 characters if hashed.
All password special characters (#, $, spaces, and so on) must be enclosed within double quotes.
For example:config>system>security>user# password ‟south#bay?”The question mark character (?) cannot be directly inserted as input during a telnet connection because the character is bound to the help command during a normal Telnet/console connection.
To insert a # or ? character, enter them inside a notepad or clipboard program, and cut and pasted them into the Telnet session in the password field that is encased in the double quotes as delimiters for the password.
If a password is entered without any parameters, a password length of zero is implied: (carriage return).
- hash
Specifies that the specific password is already hashed using hashing algorithm version 1. A semantic check is performed on the specific password field to verify if it is a valid hash 1 key to store in the database.
- hash2
Specifies that the specific password is already hashed using hashing algorithm version 2. A semantic check is performed on the specific password field to verify if it is a valid hash 2 key to store in the database.
restricted-to-home
Syntax
[no] restricted-to-home
Context
config>system>security>user
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command denies user access to files outside their home directory. Files can be accessed locally by CLI file commands and output modifiers such as > (file redirect), or remotely via FTP and SCP.
When enabled, the system denies all configuration save operations (such as admin save) via any management interface (such as CLI and NETCONF) unless save-when-restricted is enabled.
When restricted-to-home is configured, file access is denied unless the home-directory is configured and the directory is created by an administrator.
The no form of this command permits the user to access all files on the system.
Default
no restricted-to-home (for administrators)
restricted-to-home (for all other users)
save-when-restricted
Syntax
[no] save-when-restricted
Context
config>system>security>user
config>system>security>user-template
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies whether the system permits configuration save operations for all configuration regions (bof, debug, configure) via any management interface (such as CLI and NETCONF) even if restricted-to-home is enabled.
The configuration for a region can be saved with CLI commands such as bof save, admin debug-save, or admin save.
The no form of this command denies saving the configuration when restricted-to-home is enabled.
Default
save-when-restricted true (for all local users and administrators)
snmp
Syntax
snmp
Context
config>system>security>user
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates the context to configure SNMP group membership for a specific user and defines encryption and authentication parameters.
All SNMPv3 users must be configured with the commands available in this CLI node.
The 7210 SAS always uses the configured SNMPv3 username as the security username.
user-template
Syntax
user-template {tacplus_default | radius_default}
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures default security user template parameters.
Parameters
- tacplus_default
Specifies that the default TACACS+ user template is actively applied to the TACACS+ user.
- radius_default
Specifies that the default RADIUS user template is actively applied to the RADIUS user if no VSAs are returned with the auth-accept from the RADIUS server.
users
Syntax
users
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the context to edit the user configuration.
When creating a new user and entering the info command, the system displays a password in the output. This is expected behavior in the hash2 scenario. However, when using that username, there will be no password required. The user can login to the system and <ENTER> at the password prompt; the user will be logged in.
Unless an administrator explicitly changes the password, it will be null. The hashed value displayed uses the username and null password field, so when the username is changed, the displayed hashed value will change.
user
Syntax
user user-name
Context
admin
config>system>security>user
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context edit the user configuration.
If a new user-name is entered, the user is created. When an existing user-name is specified, the user parameters can be edited.
When the info command is entered for a newly created user, the system displays a password in the output. This is expected behavior in the hash2 scenario. However, no password is required when that username is used. To log in to the system, the user can press <ENTER> at the password prompt and be logged in.
Unless an administrator explicitly changes the password, it is null. The displayed hashed value uses the username and null password field. Consequently, when the username is changed, the displayed hashed value also changes.
The no form of this command deletes the user and all configuration data. Users cannot delete themselves.
Parameters
- user-name
Specifies the name of the user, up to 32 characters.
RADIUS client commands
accounting
Syntax
[no] accounting
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables RADIUS accounting.
The no form of this command disables RADIUS accounting.
Default
no accounting
accounting-port
Syntax
accounting-port port
no accounting-port
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies a UDP port number on which to contact the RADIUS server for accounting requests.
The no form of this command reverts to the default value.
Parameters
- port
Specifies the UDP port number.
authorization
Syntax
[no] authorization
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures RADIUS authorization parameters for the system.
Default
no authorization
port
Syntax
port port
no port
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the TCP port number to contact the RADIUS server.
The no form of this command reverts to the default value.
Default
port 1812
Parameters
- port
The TCP port number to contact the RADIUS server.
radius
Syntax
[no] radius
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure RADIUS authentication on the router.
Implement redundancy by configuring multiple server addresses for each router.
The no form of this command removes the RADIUS configuration.
retry
Syntax
retry count
no retry
Context
config>system>security>radius
config>system>security>dot1x>radius-plcy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server.
The no form of this command reverts to the default value.
Default
retry 3
Parameters
- count
Specifies the retry count.
server
Syntax
server index address ip-address secret key [hash|hash2] [auth-port auth-port] [acct-port acct-port] [type server-type]
no server index
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures a RADIUS server and its IP address, index, and key values.
Up to five RADIUS servers can be configured at any one time. RADIUS servers are accessed in order from lowest to highest index for authentication requests until a response from a server is received. A higher indexed server is only queried if no response is received from a lower indexed server (which implies that the server is not available). If a response from a server is received, no other RADIUS servers are queried. It is assumed that there are multiple identical servers configured as backups and that the servers do not have redundant data.
The no form of this command removes the server from the configuration.
Parameters
- index
Specifies the index for the RADIUS server. The index determines the sequence in which the servers are queried for authentication requests. Servers are queried in order from lowest to highest index.
- address ip-address
Specifies the IP address of the RADIUS server. Two RADIUS servers cannot have the same IP address. An error message is generated if the server address is a duplicate.
- secret key
Specifies the secret key to access the RADIUS server. This secret key must match the password on the RADIUS server.
- hash
Specifies that the key is entered in an encrypted form. If the hash keyword is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
Specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
shutdown
Syntax
[no] shutdown
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command administratively disables the RADIUS protocol operation. Shutting down the protocol does not remove or change the configuration other than the administrative state.
The operational state of the entity is disabled as well as the operational state of any entities contained within. Many objects must be shut down before they may be deleted.
The no form of this command administratively enables the protocol, which is the default state.
Default
no shutdown
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of seconds the router waits for a response from a RADIUS server.
The no form of this command reverts to the default value.
Default
3 seconds
Parameters
- seconds
Specifies the number of seconds the router waits for a response from a RADIUS server, expressed as a decimal integer.
use-default-template
Syntax
[no] use-default-template
Context
config>system>security>radius
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies whether the RADIUS user template is actively applied to the RADIUS user if no VSAs are returned with the auth-accept from the RADIUS server. When enabled, the RADIUS user template is actively applied if no VSAs are returned with the auth-accept from the RADIUS server.
The no form of this command disables the command.
TACACS+ client commands
server
Syntax
server index address ip-address secret key [hash | hash2] [port port]
no server index
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds a TACACS+ server and configures the TACACS+ server IP address, index, and key values.
Up to five TACACS+ servers can be configured at any one time. TACACS+ servers are accessed in order from lowest index to the highest index for authentication requests.
The no form of this command removes the server from the configuration.
Parameters
- index
Specifies the index for the TACACS+ server. The index determines the sequence in which the servers are queried for authentication requests. Servers are queried in order from the lowest index to the highest index.
- address ip-address
Specifies the IP address of the TACACS+ server. Two TACACS+ servers cannot have the same IP address. An error message is generated if the server address is a duplicate.
- secret key
Specifies the secret key to access the RADIUS server, up to 128 characters. This secret key must match the password on the RADIUS server.
- hash
Specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
Specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
tacplus
Syntax
[no] tacplus
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates the context to configure TACACS+ authentication on the router.
Configure multiple server addresses for each router for redundancy.
The no form of this command removes the TACACS+ configuration.
accounting
Syntax
accounting [record-type {start-stop | stop-only}]
no accounting
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the type of accounting record packet to be sent to the TACACS+ server. The record-type parameter indicates whether TACACS+ accounting start and stop packets be sent or just stop packets be sent.
Default
record-type stop-only
Parameters
- record-type start-stop
Specifies that a TACACS+ start packet is sent whenever the user executes a command.
- record-type stop-only
Specifies that a stop packet is sent whenever the command execution is complete.
authorization
Syntax
[no] authorization
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures TACACS+ authorization parameters for the system.
Default
no authorization
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of seconds the router waits for a response from a TACACS+ server.
The no form of this command reverts to the default value.
Default
timeout 3
Parameters
- seconds
Specifies the number of seconds the router waits for a response from a TACACS+ server, expressed as a decimal integer.
shutdown
Syntax
[no] shutdown
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command administratively disables the TACACS+ protocol operation. Shutting down the protocol does not remove or change the configuration other than the administrative state.
The operational state of the entity is disabled as well as the operational state of any entities contained within. Many objects must be shut down before they may be deleted.
The no form of this command administratively enables the protocol which is the default state.
Default
no shutdown
use-default-template
Syntax
[no] use-default-template
Context
config>system>security>tacplus
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies whether or not the user template defined by this entry is to be actively applied to the TACACS+ user.
Generic 802.1x commands
dot1x
Syntax
[no] dot1x
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command creates the context to configure 802.1x network access control on the 7210 SAS.
The no form of this command removes the 802.1x configuration.
radius-plcy
Syntax
[no] radius-plcy name [create]
Context
config>system>security> dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure RADIUS server parameters for 802.1x network access control on the 7210 SAS.
The RADIUS server configured under the config>system>security>dot1x>radius-plcy context authenticates clients who get access to the data plane of the 7210 SAS as opposed to the RADIUS server configured under the config>system>radius context, which authenticates CLI login users who get access to the management plane of the 7210 SAS.
The no form of this command removes the RADIUS server configuration for 802.1x.
Parameters
- name
Specifies the name of the RADIUS policy, up to 32 characters.
- create
This keyword is mandatory to create a RADIUS policy.
retry
Syntax
retry count
no retry
Context
config>system>security> dot1x
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server.
The no form of this command reverts to the default value.
Default
retry 3
Parameters
- count
Specifies the retry count.
server
Syntax
server server-index address ip-address secret key [hash | hash2] [auth-port auth-port] [acct-port acct-port] [type server-type]
no server index
Context
config>system>security> dot1x>radius-plcy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command adds a Dot1x server and configures the Dot1x server IP address, index, and key values.
Up to five Dot1x servers can be configured at any one time. Dot1x servers are accessed in order from lowest to highest index for authentication requests until a response from a server is received. A higher indexed server is only queried if no response is received from a lower indexed server (which implies that the server is not available). If a response from a server is received, no other Dot1x servers are queried. It is assumed that there are multiple identical servers configured as backups and that the servers do not have redundant data.
The no form of this command removes the server from the configuration.
Parameters
- server-index
Specifies the index for the Dot1x server. The index determines the sequence in which the servers are queried for authentication requests. Servers are queried in order from lowest to highest index.
- address ip-address
Specifies the IP address of the Dot1x server. Two Dot1x servers cannot have the same IP address. An error message is generated if the server address is a duplicate.
- secret key
Specifies the secret key to access the Dot1x server. This secret key must match the password on the Dot1x server.
- hash
Specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
Specifies that the key is entered in a more complex encrypted form. If the hash2 parameter is not used, the less encrypted hash form is assumed.
- acct-port acct-port
Specifies the UDP port number on which to contact the RADIUS server for accounting requests.
- auth-port auth-port
Specifies a UDP port number to be used as a match criteria.
- type server-type
Specifies the server type.
source-address
Syntax
source-address ip-address
no source-address
Context
config>system>security> dot1x>radius-plcy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the NAS IP address to be sent in the RADIUS packet.
The no form of this command reverts to the default value.
Default
By default the system IP address is used in the NAS field.
Parameters
- ip-address
Specifies the IP prefix for the IP match criterion in dotted-decimal notation.
shutdown
Syntax
[no] shutdown
Context
config>system>security>dot1x
config>system>security>dot1x>radius-plcy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command administratively disables the 802.1x protocol operation. Shutting down the protocol does not remove or change the configuration other than the administrative state.
The operational state of the entity is disabled as well as the operational state of any entities contained within.
The no form of this command administratively enables the protocol, which is the default state.
Default
shutdown
timeout
Syntax
timeout seconds
no timeout
Context
config>system>security> dot1x>radius-plcy
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the number of seconds the router waits for a response from a RADIUS server.
The no form of this command reverts to the default value.
Default
timeout 3
Parameters
- seconds
Specifies the number of seconds the router waits for a response from a RADIUS server, expressed as a decimal integer.
TCP Enhanced Authentication commands
keychain
Syntax
[no] keychain keychain-name
Context
config>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure keychain parameters. A keychain must be configured on the system before it can be applied to a session.
The no form of this command removes the keychain nodal context and everything under it from the configuration. If the keychain to be removed is in use when the no keychain command is entered, the command will not be accepted and an error indicating that the keychain is in use will be printed.
Parameters
- keychain-name
Specifies a keychain name, up to 32 characters, which identifies this particular keychain entry.
direction
Syntax
direction
Context
config>system>security>keychain
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the context to specify the data type that indicates the TCP stream direction to apply the keychain.
bi
Syntax
bi
Context
config>system>security>keychain>direction
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures keys for both send and receive stream directions.
uni
Syntax
uni
Context
config>system>security>keychain>direction
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures keys for send or receive stream directions.
receive
Syntax
receive
Context
config>system>security>keychain>direction>uni
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command enables the receive nodal context. Entries defined under this context are used to authenticate TCP segments that are being received by the router.
send
Syntax
send
Context
config>system>security>keychain>direction>uni
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the send nodal context to sign TCP segments that are being sent by the router to another device.
entry
Syntax
entry entry-id [key authentication-key | hash-key | hash2-key] [hash | hash2] algorithm algorithm
no entry entry-id
Context
config>system>security>keychain>direction>bi
config>system>security>keychain>direction>uni>receive
config>system>security>keychain>direction>uni>send
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command defines a particular key in the keychain. Entries are defined by an entry-id. A keychain must have valid entries for the TCP Enhanced Authentication mechanism to work.
The no form of this command removes the entry from the keychain. If the entry is the active entry for sending, this will cause a new active key to be selected (if one is available using the youngest key rule). If it is the only possible send key, the system will reject the command with an error indicating that the configured key is the only available send key.
If the key is one of the eligible keys for receiving, it will be removed. If the key is the only possible eligible key, the command will not be accepted, and an error message indicating that this is the only eligible key will be generated.
The no form of this command deletes the entry.
Parameters
- entry-id
Specifies an entry that represents a key configuration to be applied to a keychain.
- key
Specifies a key ID which is used along with keychain-name and direction to uniquely identify this particular key entry.
- authentication-key
Specifies the authentication-key that will be used by the encryption algorithm. The key is used to sign and authenticate a protocol packet.
The authentication-key can be any combination of letters or numbers.
- algorithm algorithm
Specifies an enumerated integer that indicates the encryption algorithm to be used by the key defined in the keychain.
- hash-key | hash2-key
Specifies the hash key. The key can be any combination of ASCII characters up to 33 for the hash-key and 96 characters for the hash2-key in length (encrypted). If spaces are used in the string, enclose the entire string in quotation marks (‟ ”).
This is useful when a user must configure the parameter, but, for security purposes, the actual unencrypted key value is not provided.
- hash
Specifies that the key is entered in an encrypted form. If the hash parameter is not used, the key is assumed to be in a non-encrypted, clear text form. For security, all keys are stored in encrypted form in the configuration file with the hash parameter specified.
- hash2
Specifies that the key is entered in a more complex encrypted form.
begin-time
Syntax
begin-time [date] [hours-minutes] [UTC] [now] [forever]
Context
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the calendar date and time after which the key specified by the keychain authentication key is used to sign and authenticate the protocol stream.
If no date and time is set, the begin-time is represented by a date and time string with all nulls and the key is not valid by default.
Parameters
- date hours-minutes
Specifies the date and time for the key to become active.
- UTC
Specifies that the date and time should be in UTC time rather than local time.
- now
Specifies that the key should become active immediately.
- forever
Specifies that the key should always be active.
end-time
Syntax
end-time [date] [hours-minutes] [UTC] [now] [forever]
Context
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the calendar date and time after which the key specified by the authentication key is no longer eligible to sign and/or authenticate the protocol stream.
Default
forever
Parameters
- date
Specifies the calendar date after which the key specified by the authentication key is no longer eligible to sign and/or authenticate the protocol stream in the YYYY/MM/DD format. When no year is specified the system assumes the current year.
- hours-minutes
Specifies the time after which the key specified by the authentication key is no longer eligible to sign and/or authenticate the protocol stream in the hh:mm[:ss] format. Seconds are optional, and if not included, assumed to be 0.
- UTC
Indicates that time is given with reference to Coordinated Universal Time in the input.
- now
Specifies a time equal to the current system time.
- forever
Specifies a time beyond the current epoch.
tolerance
Syntax
tolerance [seconds | forever]
Context
config>system>security>keychain>direction>bi>entry
config>system>security>keychain>direction>uni>receive>entry
config>system>security>keychain>direction>uni>send>entry
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the amount of time that an eligible receive key should overlap with the active send key or to never expire.
Parameters
- seconds
Specifies the duration that an eligible receive key overlaps with the active send key, in seconds.
- forever
Specifies that an eligible receive key overlaps with the active send key forever.
tcp-option-number
Syntax
tcp-option-number
Context
config>system>security>keychain
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
Commands in this context configure the TCP option number to be placed in the TCP packet header.
receive
Syntax
receive option-number
Context
config>system>security>keychain>tcp-option-number
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the TCP option number accepted in received TCP packets.
Default
receive 254
Parameters
- option-number
Specifies an enumerated integer that indicates the TCP option number to be used in the TCP header.
send
Syntax
send option-number
Context
config>system>security>keychain>tcp-option-number
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command configures the TCP option number accepted in TCP packets sent.
Default
send 254
Parameters
- option-number
Specifies an enumerated integer that indicates the TCP option number to be used in the TCP header.
dst-port
Syntax
dst-port [tcp/udp port-number] [mask]
no dst-port
Context
config>sys>sec>cpm>entry>match
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command specifies the TCP/UDP port to match the destination port of the packet. An entry containing L4 match criteria will not match non-initial (2nd, 3rd, and so on) fragments of a fragmented packet since only the first fragment contains the L4 information.
The no form of this command removes the destination port match criterion.
Parameters
- dst-port-number
Specifies the destination port number to be used as a match criteria expressed as a decimal integer.
- mask
Specifies the 16 bit mask to be applied when matching the destination port.
lockout
Syntax
lockout all
lockout user user-name
Context
admin>clear
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command is used to clear a lockout for a specific user.
Parameters
- user-name
Specifies the locked user name, up to 32 characters.
- all
Clears lockouts for all users.
IPsec commands
ipsec
Syntax
ipsec
Context
config
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
Commands in this context configure Internet Protocol security (IPsec) parameters. IPsec is a structure of open standards that uses cryptographic security services to ensure private, secure communications over IP networks.
static-sa
Syntax
static-sa sa-name [create]
no static-sa
Context
config>ipsec
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command configures an IPsec static security association (SA).
The no form of this command removes the configuration.
Parameters
- sa-name
Specifies the SA name, up to 32 characters.
- create
Mandatory keyword to create an SA instance.
authentication
Syntax
authentication auth-algorithm ascii-key ascii-string
authentication auth-algorithm hex-key hex-string [hash | hash2]
no authentication
Context
config>ipsec>static-sa
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command configures the authentication algorithm to use for an IPsec manual SA.
The no form of this command removes the configuration.
Default
no authentication
Parameters
- auth-algorithm
Specifies the authentication algorithm.
- ascii-string
Specifies the ASCII key, up to 16 characters for md5 and 20 characters for sha1.
The authentication key is stored an encrypted format. The minimum key length is configured using the config>system>security>password>minimum-length command.
The complexity of the key is configured using the commands in the config>system>security>password>complexity-rules context.
- hex-string
Specifies the hexadecimal key, up to 32 hexadecimal nibbles for md5 and up to 40 hexadecimal nibbles for sha1.
- hash
Keyword that stores all specified keys in encrypted format in the configuration file. The password must be entered in encrypted form when this keyword is configured. If this keyword is not configured, the key is assumed to be in a non-encrypted form.
- hash2
Keyword to store the key in a more complex encrypted form. If this keyword is not used, the less encrypted hash form is assumed.
description
Syntax
description description-string
no description
Context
config>ipsec>static-sa
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command creates a text description, which is stored in the configuration file, to help identify the content of the entity.
The no form of this command removes the string from the configuration.
Parameters
- description-string
Specifies the description character string. Allowed values are any string up to 80 characters composed of printable, 7-bit ASCII characters. It the string contains special characters (#, $, spaces, and so on), the entire string must be enclosed in double quotes.
direction
Syntax
direction ipsec-direction
no direction
Context
config>ipsec>static-sa
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command configures the direction for an IPsec manual SA.
The no form of this command reverts to the default value.
Default
direction bidirectional
Parameters
- ipsec-direction
Specifies the direction.
protocol
Syntax
protocol ipsec-protocol
no protocol
Context
config>ipsec>static-sa
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command configures the security protocol to use for an IPsec manual SA.
The no form of this command reverts to the default value.
Default
protocol esp
Parameters
- ipsec-protocol
Specifies the security protocol.
spi
Syntax
spi spi
no spi
Context
config>ipsec>static-sa
Platforms
Supported on all 7210 SAS platforms as described in this document, except those operating in access-uplink mode
Description
This command configures the security parameter index (SPI) key value for an IPsec manual SA.
The no form of this command removes the configured SPI key value.
Parameters
- spi
Specifies the SPI value.
Show commands
Security commands
access-group
Syntax
access-group [group-name]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays SNMP access group information.
Parameters
- group-name
Displays information for the specified access group name, up to 32 characters.
Output
The following output is an example of SNMP access group information, and Output fields: access group describes the output fields.
Sample outputA:ALA-4# show system security access-group
===============================================================================
Access Groups
===============================================================================
group name security security read write notify
model level view view view
-------------------------------------------------------------------------------
snmp-ro snmpv1 none no-security no-security
snmp-ro snmpv2c none no-security no-security
snmp-rw snmpv1 none no-security no-security no-security
snmp-rw snmpv2c none no-security no-security no-security
snmp-rwa snmpv1 none iso iso iso
snmp-rwa snmpv2c none iso iso iso
snmp-trap snmpv1 none iso
snmp-trap snmpv2c none iso
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
Group name |
Displays the access group name |
Security model |
Displays the security model required to access the views configured in this node |
Security level |
Specifies the required authentication and privacy levels to access the views configured in this node |
Read view |
Specifies the variable of the view to read the MIB objects |
Write view |
Specifies the variable of the view to configure the contents of the agent |
Notify view |
Specifies the variable of the view to send a trap about MIB objects |
authentication
Syntax
authentication [statistics]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays system login authentication configuration and statistics.
Parameters
- statistics
Appends login and accounting statistics to the display.
Output
The following output is an example of system login authentication information, and Output fields: security authentication describes the output fields.
Sample outputA:ALA-4# show system security authentication
===============================================================================
Authentication sequence : radius tacplus local
===============================================================================
server address status type timeout(secs) single connection retry count
-------------------------------------------------------------------------------
10.10.10.103 up radius 5 n/a 5
10.10.0.1 up radius 5 n/a 5
10.10.0.2 up radius 5 n/a 5
10.10.0.3 up radius 5 n/a 5
-------------------------------------------------------------------------------
radius admin status : down
tacplus admin status : up
health check : enabled
-------------------------------------------------------------------------------
No. of Servers: 4
===============================================================================
A:ALA-4#
A:ALA-7>show>system>security# authentication statistics
===============================================================================
Authentication sequence : radius tacplus local
===============================================================================
server address status type timeout(secs) single connection retry count
-------------------------------------------------------------------------------
10.10.10.103 up radius 5 n/a 5
10.10.0.1 up radius 5 n/a 5
10.10.0.2 up radius 5 n/a 5
10.10.0.3 up radius 5 n/a 5
-------------------------------------------------------------------------------
radius admin status : down
tacplus admin status : up
health check : enabled
-------------------------------------------------------------------------------
No. of Servers: 4
===============================================================================
Login Statistics
===============================================================================
server address connection errors accepted logins rejected logins
-------------------------------------------------------------------------------
10.10.10.103 0 0 0
10.10.0.1 0 0 0
10.10.0.2 0 0 0
10.10.0.3 0 0 0
local n/a 1 0
===============================================================================
Authorization Statistics (TACACS+)
===============================================================================
server address connection errors sent packets rejected packets
-------------------------------------------------------------------------------
===============================================================================
Accounting Statistics
===============================================================================
server address connection errors sent packets rejected packets
-------------------------------------------------------------------------------
10.10.10.103 0 0 0
10.10.0.1 0 0 0
10.10.0.2 0 0 0
10.10.0.3 0 0 0
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
Sequence |
Displays the sequence in which authentication is processed |
Server address |
Displays the IP address of the RADIUS server |
Status |
Displays the current status of the RADIUS server |
Type |
Displays the authentication type |
Timeout (secs) |
Displays the number of seconds the router waits for a response from a RADIUS server |
Single connection |
Enabled — Specifies a single connection to the TACACS+ server and validates everything via that connection Disabled — The TACACS+ protocol operation is disabled |
Retry count |
Displays the number of times the router attempts to contact the RADIUS server for authentication if there are problems communicating with the server |
Connection errors |
Displays the number of times a user has attempted to login irrespective of whether the login succeeded or failed |
Accepted logins |
Displays the number of times the user has successfully logged in |
Rejected logins |
Displays the number of unsuccessful login attempts |
Sent packets |
Displays the number of packets sent |
Rejected packets |
Displays the number of packets rejected |
dist-cpu-protection
Syntax
cpu-protection
Context
show>system>security
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
Commands in this context display distributed CPU protection information.
policy
Syntax
policy [name] [association | detail]
Context
show>system>security>dist-cpu-protection
Platforms
7210 SAS-R6 and 7210 SAS-R12
Description
This command displays distributed CPU protection policy information.
Parameters
- name
Displays distributed CPU protection policy information for the specified policy name, up to 32 characters.
- association
Displays associations for the specified policy name.
- detail
Displays detailed information for the specified policy name.
keychain
Syntax
keychain [key-chain] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays keychain information.
Parameters
- key-chain
Specifies the keychain name to display.
- detail
Displays detailed keychain information.
Output
The following output is an example of keychain information, and Output fields: keychain describes the output fields.
Sample output*A:ALA-A# show system security keychain test
===============================================================================
Key chain:test
===============================================================================
TCP-Option number send : 254 Admin state : Up
TCP-Option number receive : 254 Oper state : Up
===============================================================================
*A:ALA-A#
*A:ALA-A# show system security keychain test detail
===============================================================================
Key chain:test
===============================================================================
TCP-Option number send : 254 Admin state : Up
TCP-Option number receive : 254 Oper state : Up
===============================================================================
Key entries for key chain: test
===============================================================================
Id : 0
Direction : send-receive Algorithm : hmac-sha-1-96
Admin State : Up Valid : Yes
Active : Yes Tolerance : 300
Begin Time : 2007/02/15 18:28:37 Begin Time (UTC) : 2007/02/15 17:28:37
End Time : N/A End Time (UTC) : N/A
===============================================================================
Id : 1
Direction : send-receive Algorithm : aes-128-cmac-96
Admin State : Up Valid : Yes
Active : No Tolerance : 300
Begin Time : 2007/02/15 18:27:57 Begin Time (UTC) : 2007/02/15 17:27:57
End Time : 2007/02/15 18:28:13 End Time (UTC) : 2007/02/15 17:28:13
===============================================================================
Id : 2
Direction : send-receive Algorithm : aes-128-cmac-96
Admin State : Up Valid : Yes
Active : No Tolerance : 500
Begin Time : 2007/02/15 18:28:13 Begin Time (UTC) : 2007/02/15 17:28:13
End Time : 2007/02/15 18:28:37 End Time (UTC) : 2007/02/15 17:28:37
===============================================================================
*A:ALA-A#
| Label | Description |
|---|---|
TCP-Option number send |
Displays the TCP option number to be inserted in the header of sent TCP packets |
Admin state |
Displays the administrative state of the keychain: up or down |
TCP-Option number receive |
Displays the TCP option number that will be accepted in the header of received TCP packets |
Oper state |
Displays the operational state of the keychain: up or down |
Key entries for key chain: test |
|
Id |
Displays the ID of the key entry |
Direction |
Displays the stream direction on which keys will be applied for this entry: send, receive, or send-receive |
Algorithm |
Displays the encryption algorithm to be used by this key entry |
Option |
Indicates the configured IS-IS encoding standard (indicates ‟none” if the associated protocol is not IS-IS) |
Admin State |
Displays the administrative state of the key entry: up or down |
Valid |
Indicates if the receive key is valid |
Active |
Indicates if the transmit (sent) key is active |
Tolerance |
Displays the tolerance time configured for support of both currently active and new keys |
Begin Time |
Displays the time at which the new key is used to sign and/or authenticate protocol packets |
Begin Time (UTC) |
Displays the begin time in UTC time |
End Time |
Displays the time at which the key is no longer eligible to authenticate protocol packets |
End Time (UTC) |
Displays the end time in UTC time |
management-access-filter
Syntax
management-access-filter
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays management access filter information for IP filters.
ip-filter
Syntax
ip-filter [entry entry-id]
Context
show>system>security>mgmt-access-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays management access IP filters.
Parameters
- entry-id
Displays information for the specified entry.
Output
The following output is an example of management access IP filter information, and Output fields: IP filter describes the output fields.
Sample output*7210-SAS>show>system>security>management-access-filter# ip-filter entry 1
===============================================================================
IPv4 Management Access Filter
===============================================================================
filter type : ip
Def. Action : permit
Admin Status : enabled (no shutdown)
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Src IP : undefined
Src interface : undefined
Dest port : undefined
L4 Src port : undefined
Fragment : off
Protocol : undefined
Router : undefined
Action : none
Log : disabled
Matches : 0
===============================================================================
*7210-SAS>show>system>security>management-access-filter#
| Label | Description |
|---|---|
Def. action |
Permit — Specifies that packets not matching the configured selection criteria in any of the filter entries are permitted Deny — Specifies that packets not matching the configured selection criteria in any of the filter entries are denied and that a ICMP host unreachable message will be issued Deny-host-unreachble — Specifies that packets not matching the configured selection criteria in the filter entries are denied. |
Entry |
Displays the entry ID in a policy or filter table |
Description |
Displays a text string describing the filter |
Src IP |
Displays the source IP address used for management access filter match criteria |
Src Interface |
Displays the interface name for the next-hop to which the packet should be forwarded if it hits this filter entry |
Dest port |
Displays the destination port |
Match |
Displays the number of times a management packet has matched this filter entry |
Protocol |
Displays the IP protocol to match |
Action |
Displays the action to take for packets that match this filter entry |
Flow label |
Displays the flow label value to match |
Next-header |
Displays the IPv6 next header value to match |
L4 Src port |
Displays the TCP/UDP source port number to match |
Fragment |
Indicates if the entry should match a fragment or not |
Router |
Displays the router Instance ID to match |
Log |
Indicates if packet matching this entry must be logged or not On 7210 SAS platforms, logging is not supported |
ipv6-filter
Syntax
ipv6-filter [entry entry-id]
Context
show>system>security>mgmt-access-filter
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays management access IPv6 filters.
Parameters
- entry-id
Displays information for the specified entry.
Output
The following output is an example of management access IPv6 filter information, and Output fields: IPv6 filter describes the output fields.
Sample outputA:7210SAS# show system security management-access-filter ipv6-filter
===============================================================================
IPv6 Management Access Filter
===============================================================================
filter type : ipv6
Def. Action : permit
Admin Status : enabled (no shutdown)
-------------------------------------------------------------------------------
Entry : 1
Description : (Not Specified)
Src IP : undefined
Flow label : undefined
Src interface : 1/1/1
Dest port : undefined
L4 Src port : undefined
Next-header : undefined
Router : undefined
Action : permit
Log : disabled
Matches : 0
===============================================================================
*A:7210SAS#
| Label | Description |
|---|---|
Def. action |
Permit — Specifies that packets not matching the configured selection criteria in any of the filter entries are permitted Deny — Specifies that packets not matching the configured selection criteria in any of the filter entries are denied and that a ICMP host unreachable message will be issued Deny-host-unreachble — Specifies that packets not matching the configured selection criteria in the filter entries are denied |
Entry |
Displays the entry ID in a policy or filter table |
Description |
Displays a text string describing the filter |
Src IP |
Displays the source IPv6 address used for management access filter match criteria |
Src Interface |
Displays the interface name for the next-hop to which the packet should be forwarded if it hits this filter entry |
Dest port |
Displays the destination port |
Flow label |
Displays the flow label value to match |
Protocol |
Displays the IPv6 protocol to match |
Action |
Displays the action to take for packets that match this filter entry |
Next-header |
Displays the IPv6 next header value to match |
L4 Src port |
Displays the TCP/UDP source port number to match |
Router |
Displays the router Instance ID to match |
Log |
Indicates if packet matching this entry must be logged or not On 7210 SAS platforms, logging is not supported |
password-options
Syntax
password-options
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays configured password options.
Output
The following output is an example of password option information, and Output fields: password options describes the output fields.
Sample outputA:ALA-7# show system security password-options
===============================================================================
Password Options
===============================================================================
Password aging in days : none
Number of invalid attempts permitted per login : 3
Time in minutes per login attempt : 5
Lockout period (when threshold breached) : 10
Authentication order : radius tacplus local
Configured complexity options :
Minimum password length : 6
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
Password aging in days |
Displays the number of days a user password is valid before the user must change their password |
Number of invalid attempts permitted per login |
Displays the number of unsuccessful login attempts allowed for the specified time |
Time in minutes per login attempt |
Displays the period of time, in minutes, that a specified number of unsuccessful attempts can be made before the user is locked out |
Lockout period (when threshold breached) |
Displays the lockout period in minutes where the user is not allowed to login |
Authentication order |
Displays the sequence in which password authentication is attempted among RADIUS, TACACS+, and local passwords |
Configured complexity options |
Displays the complexity requirements of locally administered passwords, HMAC-MD5-96, HMAC-SHA-96 and DES-keys configured in the authentication section |
Minimum password length |
Displays the minimum number of characters required for locally administered passwords, HMAC-MD5-96, HMAC-SHA-96, and DES-keys configured in the system security section |
profile
Syntax
profile [user-profile-name]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays user profile information.
If the user-profile-name is not specified, information for all profiles are displayed.
Parameters
- user-profile-name
Displays information for the specified user profile name, up to 32 characters.
Output
The following output is an example of user profile information, and Output fields: profile describes the output fields.
Sample outputA:ALA-7# show system security profile administrative
===============================================================================
User Profile
===============================================================================
User Profile : administrative
Def. Action : permit-all
-------------------------------------------------------------------------------
Entry : 10
Description :
Match Command: configure system security
Action : permit
-------------------------------------------------------------------------------
Entry : 20
Description :
Match Command: show system security
Action : permit
-------------------------------------------------------------------------------
No. of profiles:
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
User Profile |
Displays the profile name used to deny or permit user console access to a hierarchical branch or to specific commands |
Def. action |
Permit all — Permits access to all commands Deny — Denies access to all commands None — No action is taken |
Entry |
Displays the entry ID in a policy or filter table |
Description |
Displays the text string describing the entry |
Match Command |
Displays the command or subtree commands in subordinate command levels |
Action |
Permit all — Commands matching the entry command match criteria are permitted Deny — Commands not matching the entry command match criteria are not permitted. |
No. of profiles |
Displays the total number of profiles listed |
source-address
Syntax
source-address
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays source addresses configured for applications.
Output
The following output is an example of source address information, and Output fields: source access describes the output fields.
Sample outputA:SR-7# show system security source-address
===============================================================================
Source-Address applications
===============================================================================
Application IP address/Interface Name Oper status
-------------------------------------------------------------------------------
telnet 10.20.1.7 Up
radius loopback1 Up
===============================================================================
A:SR-7#
| Label | Description |
|---|---|
Application |
Displays the source-address application |
IP address Interface Name |
Displays the source address IP address or interface name |
Oper status |
Up — The source address is operationally up Down — The source address is operationally down |
ssh
Syntax
ssh
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays all the SSH sessions as well as the SSH status and fingerprint.
Output
The following output is an example of SSH session information, and Output fields: SSH describes the output fields.
Sample outputALA-7# show system security ssh
SSH is enabled
SSH preserve key: Enabled
SSH protocol version 1: Enabled
RSA host key finger print:c6:a9:57:cb:ee:ec:df:33:1a:cd:d2:ef:3f:b5:46:34
SSH protocol version 2: Enabled
DSA host key finger print:ab:ed:43:6a:75:90:d3:fc:42:59:17:8a:80:10:41:79
=======================================================
Connection Encryption Username
=======================================================
192.168.5.218 3des admin
-------------------------------------------------------
Number of SSH sessions : 1
=======================================================
ALA-7#
A:ALA-49>config>system>security# show system security ssh
SSH is disabled
A:ALA-49>config>system>security#
| Label | Description |
|---|---|
SSH status |
SSH is enabled — Displays that SSH server is enabled SSH is disabled — Displays that SSH server is disabled. |
SSH Preserve Key |
Enabled — Displays that preserve-key is enabled. Disabled — Displays that preserve-key is disabled. |
SSH protocol version 1 |
Enabled — Displays that SSH1 is enabled. Disabled — Displays that SSH1 is disabled. |
SSH protocol version 2 |
Enabled — Displays that SSH2 is enabled. Disabled — Displays that SSH2 is disabled. |
Key fingerprint |
The key fingerprint is the server identity Clients trying to connect to the server verify the server fingerprint If the server fingerprint is not known, the client may not continue with the SSH session since the server might be spoofed |
Connection |
Displays the IP address of the connected routers (remote client) |
Encryption |
des — Data encryption using a private (secret) key 3des — An encryption method that allows proprietary information to be transmitted over untrusted networks |
Username |
Displays the name of the user |
Number of SSH sessions |
Displays the total number of SSH sessions |
user
Syntax
user [user-name] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays user registration information.
If no command line options are specified, summary information for all users is displayed.
Parameters
- user-name
Displays information for the specified user name, up to 32 characters.
- detail
Displays detailed user information to the summary output.
Output
The following output is an example of user registration information, and Output fields: security user describes the output fields.
Sample outputA:ALA-7# show system security user
===============================================================================
Users
===============================================================================
user id need user permissions password attempted failed local
new pwd console ftp snmp expires logins logins conf
-------------------------------------------------------------------------------
admin n y n n never 21 0 y
===============================================================================
A:ALA-7#
A:
ALA-7# show system security user detail
===============================================================================
Users
===============================================================================
user id need user permissions password attempted failed local
new pwd console ftp snmp expires logins logins conf
-------------------------------------------------------------------------------
admin n y n n never 21 0 y
===============================================================================
===============================================================================
User Configuration Detail
===============================================================================
user id : admin
-------------------------------------------------------------------------------
console parameters
-------------------------------------------------------------------------------
new pw required : no cannot change pw : no
home directory : cf1:\
restricted to home : no
login exec file :
profile : administrative
-------------------------------------------------------------------------------
snmp parameters
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
User ID |
Displays the name of a system user |
Need new pwd |
Y — The user must change their password at the next login N — The user is not forced to change their password at the next login |
Cannot change pw |
Y — The user has the ability to change the login password N — The user does not have the ability to change the login password |
User permissions |
Console Y — The user is authorized for console access. N — The user is not authorized for console access. FTP Y — The user is authorized for FTP access. N — The user is not authorized for FTP access. SNMP Y — The user is authorized for SNMP access. N — The user is not authorized for SNMP access. |
Password expires |
Displays the number of days in which the user must change their login password |
Attempted logins |
Displays the number of times the user has attempted to login irrespective of whether the login succeeded or failed |
Failed logins |
Displays the number of unsuccessful login attempts |
Local conf |
Y — Password authentication is based on the local password database N — Password authentication is not based on the local password database |
Home directory |
Specifies the local home directory for the user for both console and FTP access |
Restricted to home |
Yes — The user is not allowed to navigate to a directory higher in the directory tree on the home directory device No — The user is allowed to navigate to a directory higher in the directory tree on the home directory device |
Login exec file |
Displays the user login exec file which executes whenever the user successfully logs in to a console session |
view
Syntax
view [view-name] [detail]
Context
show>system>security
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays the SNMP MIB views.
Parameters
- view-name
Specifies the name of the view to display output, up to 32 characters. If no view name is specified, the complete list of views is displayed.
- detail
Displays detailed view information.
Output
The following output is an example of SNMP MIB view information, and Output fields: security view describes the output fields.
Sample outputA:ALA-48# show system security view
===============================================================================
Views
===============================================================================
view name oid tree mask permission
-------------------------------------------------------------------------------
iso 1 included
read1 1.1.1.1 11111111 included
write1 2.2.2.2 11111111 included
testview 1 11111111 included
testview 1.3.6.1.2 11111111 excluded
mgmt-view 1.3.6.1.2.1.2 included
mgmt-view 1.3.6.1.2.1.4 included
mgmt-view 1.3.6.1.2.1.5 included
mgmt-view 1.3.6.1.2.1.6 included
mgmt-view 1.3.6.1.2.1.7 included
mgmt-view 1.3.6.1.2.1.31 included
mgmt-view 1.3.6.1.2.1.77 included
mgmt-view 1.3.6.1.4.1.6527.3.1.2.3.7 included
mgmt-view 1.3.6.1.4.1.6527.3.1.2.3.11 included
no-security 1 included
no-security 1.3.6.1.6.3 excluded
no-security 1.3.6.1.6.3.10.2.1 included
no-security 1.3.6.1.6.3.11.2.1 included
no-security 1.3.6.1.6.3.15.1.1 included
on-security 2 00000000 included
-------------------------------------------------------------------------------
No. of Views:
===============================================================================
A:ALA-48#
| Label | Description |
|---|---|
view name |
Displays the name of the view Views control the accessibility of a MIB object within the configured MIB view and subtree |
oid tree |
Displays the object identifier of the ASN.1 subtree |
mask |
Displays the bit mask that defines a family of view subtrees |
permission |
Indicates whether each view is included or excluded |
No. of Views |
Displays the total number of views |
Login control
users
Syntax
users
Context
show
Platforms
Supported on all 7210 SAS platforms as described in this document, including those configured in the access-uplink operating mode.
Description
This command displays console user login and connection information.
Output
The following output is an example of console user login and connection information, and Output fields: users describes the output fields.
Sample console users outputA:ALA-7# show users
===============================================================================
User Type From Login time Idle time
===============================================================================
testuser Console -- 21FEB2007 04:58:55 0d 00:00:00 A
-------------------------------------------------------------------------------
Number of users : 1
'A' indicates user is in admin mode
===============================================================================
A:ALA-7#
| Label | Description |
|---|---|
User |
Displays the username |
Type |
Displays the user is authorized this access type |
From |
Displays the originating IP address |
Login time |
Displays the time the user logged in |
Idle time |
Displays the amount of idle time for a specific login |
Number of users |
Displays the total number of users logged in |
Debug commands
radius
Syntax
radius
no radius
Context
debug>router
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command enables debugging for RADIUS connections.
The no form of this command disables RADIUS debugging.
Default
no radius
detail-level
Syntax
detail-level {low | medium | high}
no detail-level
Context
debug>router>radius
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command configures the RADIUS debugging output detail level.
The no form of this command reverts to the default values.
Default
detail-level medium
Parameters
- low
Specifies that the output include the packet type, server address, length, and RADIUS server policy name.
- medium
Specifies that the output include the RADIUS attributes in the packets, in addition to all information included in low detail output.
- high
Specifies that the output include hexadecimal packet dumps, in addition to all information included in medium and low detail output.
packet-type
Syntax
packet-type [authentication] [accounting] [coa]
no packet-type
Context
debug>router>radius
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the RADIUS packet types to include in the RADIUS debugging output.
The no form of this command reverts to the default values.
Default
packet-type authentication accounting coa
Parameters
- authentication
Specifies that RADIUS authentication packets should be included.
- accounting
Specifies that RADIUS accounting packets should be included.
- coa
Specifies that RADIUS change-of-authorization packets should be included.
radius-attr
Syntax
radius-attr type attribute-type [transaction]
radius-attr type attribute-type [transaction] {address | hex | integer | string} value attribute-value
radius-attr vendor vendor-id type attribute-type [transaction] [encoding encoding-type]
radius-attr vendor vendor-id type attribute-type [transaction] [encoding encoding-type] {address | hex | integer | string} value attribute-value
no radius-attr type attribute-type
no radius-attr type attribute-type {address | hex | integer | string} value attribute-value
no radius-attr vendor vendor-id type attribute-type
no radius-attr vendor vendor-id type attribute-type {address | hex | integer | string} value attribute-value
Context
debug>router>radius
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the RADIUS attributes to include in medium or high detail RADIUS debugging output.
The no form of this command disables the inclusion of the specified attributes.
Parameters
- address
Specifies that the attribute-value is an IPv4 or IPv6 address, prefix, or subnet.
- attribute-type
Specifies the RADIUS attribute type.
- attribute-value
Specifies the value of the RADIUS attribute.
- encoding-type
Specifies the size of the vendor-type and vendor-length in bytes. The information is configured in the format "xy", where "x" is the size of the vendor-type and "y" is the size of the vendor-length.
- hex
Specifies that the attribute-value is a binary string in hexadecimal format.
- integer
Specifies that the attribute-value is an integer.
- string
Specifies that the attribute-value is an ASCII string.
- transaction
Specifies that the system outputs both request and response packets in the same session, even if the response packet does not include the filtered attributes.
- vendor-id
Specifies the vendor ID for the vendor-specific attributes.
server-address
Syntax
server-address ip-address
no server-address ip-address
Context
debug>router>radius
Platforms
Supported on all 7210 SAS platforms as described in this document
Description
This command specifies the RADIUS server information to include in the RADIUS debugging output.
The no form of this command removes the specified RADIUS server from the RADIUS debugging output.
Parameters
- ip-address
Specifies the IPv4 or IPv6 address of the RADIUS server.