Virtual private LAN service
VPLS service overview
VPLS as described in RFC 4905, Encapsulation methods for transport of layer 2 frames over MPLS, is a class of virtual private network service that allows the connection of multiple sites in a single bridged domain over a provider-managed IP/MPLS network. The customer sites in a VPLS instance appear to be on the same LAN, regardless of their location. VPLS uses an Ethernet interface on the customer-facing (access) side, which simplifies the LAN/WAN boundary and allows for rapid and flexible service provisioning.
VPLS offers a balance between point-to-point Frame Relay service and outsourced routed services (VPRN). VPLS enables each customer to maintain control of their own routing strategies. All customer routers in the VPLS service are part of the same subnet (LAN), which simplifies the IP addressing plan, especially when compared to a mesh constructed from many separate point-to-point connections. The VPLS service management is simplified because the service is not aware of nor participates in the IP addressing and routing.
A VPLS service provides connectivity between two or more SAPs on one (which is considered a local service) or more (which is considered a distributed service) service routers. The connection appears to be a bridged domain to the customer sites so protocols, including routing protocols, can traverse the VPLS service.
Other VPLS advantages include:
VPLS is a transparent, protocol-independent service.
There is no Layer 2 protocol conversion between LAN and WAN technologies.
There is no need to design, manage, configure, and maintain separate WAN access equipment, which eliminates the need to train personnel on WAN technologies.
VPLS packet walkthrough
This section provides an example of VPLS processing of a customer packet sent across the network from site A, which is connected to PE Router A, to site B, which is connected to PE Router C (see VPLS service architecture).

PE Router A (see Access port ingress packet format and lookup)
Service packets arriving at PE Router A are associated with a VPLS service instance based on the combination of the physical port and the IEEE 802.1Q tag (VLAN ID) in the packet.
Figure 2. Access port ingress packet format and lookup 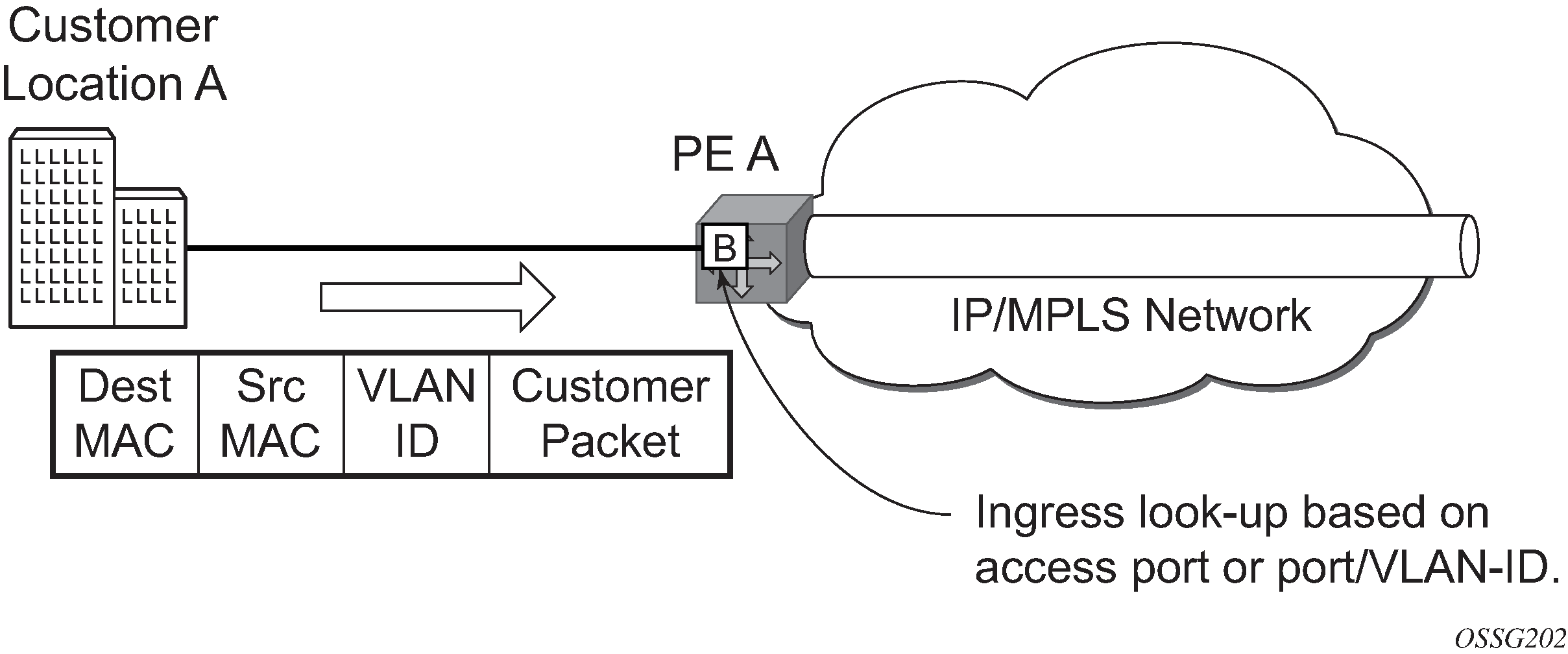
PE Router A learns the source MAC address in the packet and creates an entry in the FDB table that associates the MAC address with the service access point (SAP) on which it was received.
The destination MAC address in the packet is looked up in the FDB table for the VPLS instance. There are two possibilities: either the destination MAC address has already been learned (known MAC address) or the destination MAC address is not yet learned (unknown MAC address).
For a known MAC address, see Network port egress packet format and flooding and proceed to 1.d.
For an unknown MAC address, see Network port egress packet format and flooding and proceed to 1.f.
If the destination MAC address has already been learned by PE Router A, an existing entry in the FDB table identifies the far-end PE router and the service VC-label (inner label) to be used before sending the packet to far-end PE Router C.
-
PE Router A chooses a transport LSP to send the customer packets to PE Router C. The customer packet is sent on this LSP after the IEEE 802.1Q tag is stripped and the service VC-label (inner label) and the transport label (outer label) are added to the packet.
-
If the destination MAC address has not been learned, PE Router A floods the packet to both PE Router B and PE Router C that are participating in the service by using the VC-labels that each PE Router previously added for the VPLS instance. The packet is not sent to PE Router D because this VPLS service does not exist on that PE router.
Figure 3. Network port egress packet format and flooding 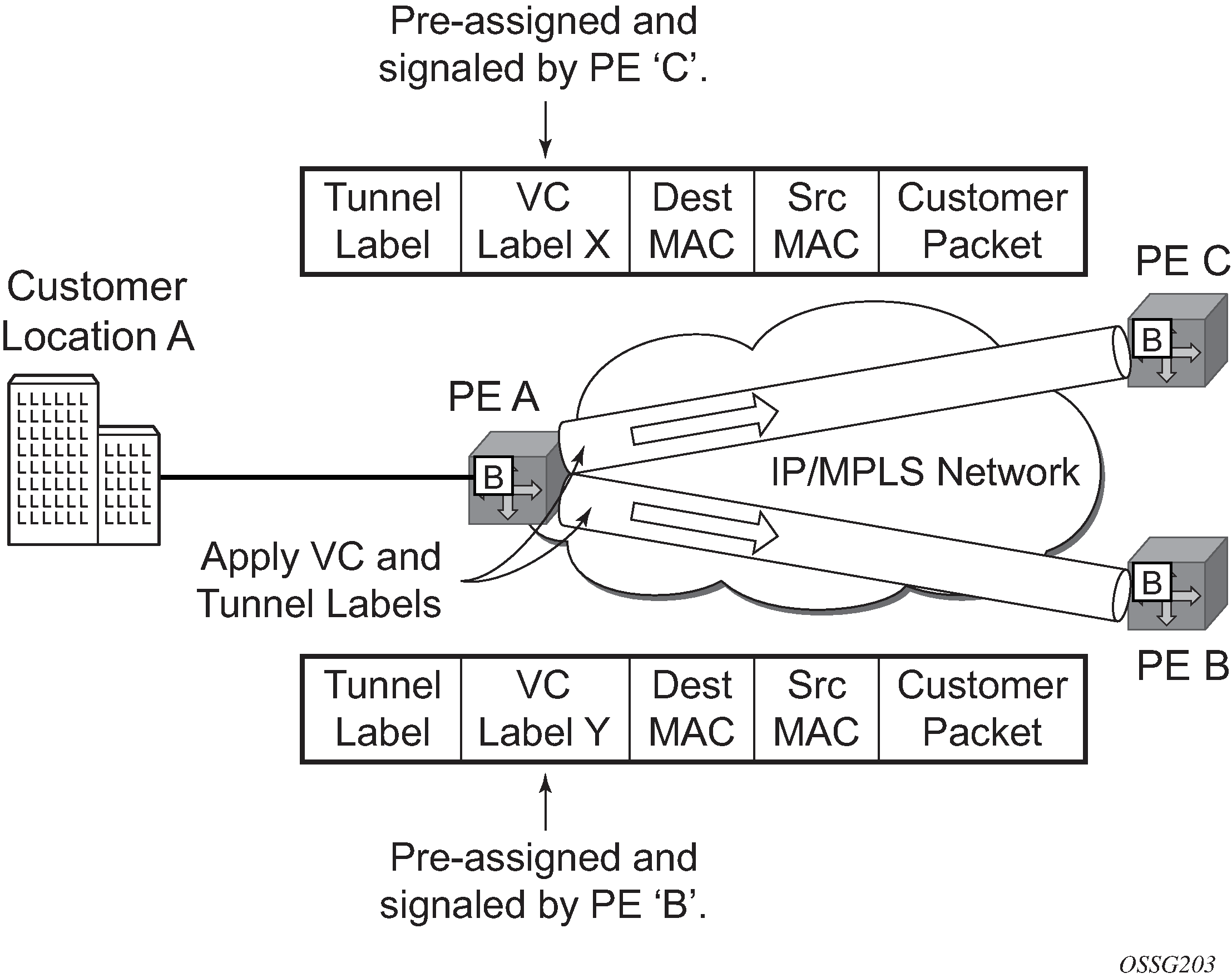
Core Router Switching
All the core routers (‟P” routers in IETF nomenclature) between PE Router A and PE Router B and PE Router C are Label Switch Routers (LSRs) that switch the packet based on the transport (outer) label of the packet until the packet arrives at the far-end PE Router. All core routers are unaware that this traffic is associated with a VPLS service.
PE router C
PE Router C strips the transport label of the received packet to reveal the inner VC-label. The VC-label identifies the VPLS service instance to which the packet belongs.
PE Router C learns the source MAC address in the packet and creates an entry in the FDB table that associates the MAC address with PE Router A, and the VC-label that PE Router A added for the VPLS service on which the packet was received.
The destination MAC address in the packet is looked up in the FDB table for the VPLS instance. Again, there are two possibilities: either the destination MAC address has already been learned (known MAC address) or the destination MAC address has not been learned on the access side of PE Router C (unknown MAC address).
For a known MAC address see Access port egress packet format and lookup.
If the destination MAC address has been learned by PE Router C, an existing entry in the FDB table identifies the local access port and the IEEE 802.1Q tag to be added before sending the packet to customer Location C. The egress Q tag may be different than the ingress Q tag.

VPLS features
This section provides information about VPLS features.
VPLS enhancements
Nokia's VPLS implementation includes several enhancements beyond basic VPN connectivity. The following VPLS features can be configured individually for each VPLS service instance:
Extensive MAC and IP filter support (up to Layer 4). Filters can be applied on a per-SAP basis.
Forwarding Database (FDB) management features on a per service-level basis including:
Configurable FDB size limit. On the 7450 ESS, it can be configured on a per-VPLS, per-SAP, and per spoke-SDP basis.
FDB size alarms. On the 7450 ESS, it can be configured on a per-VPLS basis.
MAC learning disable. On the 7450 ESS, it can be configured on a per-VPLS, per-SAP, and per spoke-SDP basis.
Discard unknown. On the 7450 ESS, it can be configured on a per-VPLS basis.
Separate aging timers for locally and remotely learned MAC addresses.
Ingress rate limiting for broadcast, multicast, and unknown destination flooding on a per-SAP basis.
Implementation of STP parameters on a per-VPLS, per-SAP, and per spoke-SDP basis.
A split horizon group on a per-SAP and per spoke-SDP basis.
DHCP snooping and anti-spoofing on a per-SAP and per-SDP basis for the 7450 ESS or 7750 SR.
IGMP snooping on a per-SAP and per-SDP basis.
Optional SAP and, or spoke-SDP redundancy to protect against node failure.
VPLS over MPLS
The VPLS architecture proposed in RFC 4762, Virtual Private LAN Services Using LDP Signaling specifies the use of provider equipment (PE) that is capable of learning, bridging, and replication on a per-VPLS basis. The PE routers that participate in the service are connected using MPLS Label Switched Path (LSP) tunnels in a full-mesh composed of mesh SDPs or based on an LSP hierarchy (Hierarchical VPLS (H-VPLS)) composed of mesh SDPs and spoke-SDPs.
Multiple VPLS services can be offered over the same set of LSP tunnels. Signaling specified in RFC 4905, Encapsulation methods for transport of layer 2 frames over MPLS is used to negotiate a set of ingress and egress VC labels on a per-service basis. The VC labels are used by the PE routers for demultiplexing traffic arriving from different VPLS services over the same set of LSP tunnels.
VPLS is provided over MPLS by:
connecting bridging-capable provider edge routers with a full mesh of MPLS LSP tunnels
negotiating per-service VC labels using Draft-Martini encapsulation
replicating unknown and broadcast traffic in a service domain
enabling MAC learning over tunnel and access ports (see VPLS MAC learning and packet forwarding)
using a separate FDB per VPLS service
VPLS service pseudowire VLAN tag processing
VPLS services can be connected using pseudowires that can be provisioned statically or dynamically and are represented in the system as either a mesh or a spoke-SDP. The mesh and spoke-SDP can be configured to process zero, one, or two VLAN tags as traffic is transmitted and received. In the transmit direction, VLAN tags are added to the frame being sent, and in the received direction, VLAN tags are removed from the frame being received. This is analogous to the SAP operations on a null, dot1q, and QinQ SAP.
The system expects a symmetrical configuration with its peer; specifically, it expects to remove the same number of VLAN tags from received traffic as it adds to transmitted traffic. When removing VLAN tags from a mesh or spoke-SDP, the system attempts to remove the configured number of VLAN tags (see the following configuration information); if fewer tags are found, the system removes the VLAN tags found and forwards the resulting packet. As some of the related configuration parameters are local and not communicated in the signaling plane, an asymmetrical behavior cannot always be detected and so cannot be blocked. With an asymmetrical behavior, protocol extractions do not necessarily function as they would with a symmetrical configuration, resulting in an unexpected operation.
The VLAN tag processing is configured as follows on a mesh or spoke-SDP in a VPLS service:
zero VLAN tags processed
VPLS Service Pseudowire VLAN Tag Processing. This requires the configuration of vc-type ether under the mesh-SDP or spoke-SDP, or in the related PW template.
one VLAN tag processed
This requires one of the following configurations:
vc-type vlan under the mesh-SDP or spoke-SDP, or in the related PW template
vc-type ether and force-vlan-vc-forwarding under the mesh-SDP or spoke-SDP, or in the related PW template
two VLAN tags processed
This requires the configuration of force-qinq-vc-forwarding [c-tag-c-tag | s-tag-c-tag] under the mesh-SDP or spoke-SDP, or in the related PW template.
The PW template configuration provides support for BGP VPLS services and LDP VPLS services using BGP Auto-Discovery.
The following restrictions apply to VLAN tag processing:
The configuration of vc-type vlan and force-vlan-vc-forwarding is mutually exclusive.
BGP VPLS services operate in a mode equivalent to vc-type ether; consequently, the configuration of vc-type vlan in a PW template for a BGP VPLS service is ignored.
force-qinq-vc-forwarding [c-tag-c-tag | s-tag-c-tag] can be configured with the mesh-SDP or spoke-SDP signaled as either vc-type ether or vc-type vlan.
The following are not supported with force-qinq-vc-forwarding [c-tag-c-tag | s-tag-c-tag] configured under the mesh-SDP or spoke-SDP, or in the related PW template:
Routed, E-Tree, or PBB VPLS services (including B-VPLS and I-VPLS)
L2PT termination on QinQ mesh-SDP or spoke-SDPs
IGMP/MLD/PIM snooping within the VPLS service
force-vlan-vc-forwarding under the same spoke-SDP or PW template
Eth-CFM LM tests
VPLS mesh and spoke-SDP VLAN tag processing: ingress and VPLS mesh and spoke-SDP VLAN tag processing: egress describe the VLAN tag processing with respect to the zero, one, and two VLAN tag configuration described for the VLAN identifiers, Ethertype, ingress QoS classification (dot1p/DE), and QoS propagation to the egress (which can be used for egress classification and, or to set the QoS information in the innermost egress VLAN tag).
| Ingress (received on mesh or spoke-SDP) | Zero VLAN tags | One VLAN tag | Two VLAN Tags (enabled by force-qinq-vc-forwarding [c-tag-c-tag | s-tag-c-tag] |
|---|---|---|---|
VLAN identifiers |
— |
Ignored |
Both inner and outer ignored |
Ethertype (to determine the presence of a VLAN tag) |
— |
0x8100 or value configured under sdp vlan-vc-etype |
Both inner and outer VLAN tags: 0x8100, or outer VLAN tag value configured under sdp vlan-vc-etype (inner VLAN tag value must be 0x8100) |
Ingress QoS (dot1p/DE) classification |
— |
Ignored |
Both inner and outer ignored |
QoS (dot1p/DE) propagation to egress |
Dot1p/DE=0 |
Dot1p/DE taken from received VLAN tag |
Dot1p/DE taken as follows:
|
| Egress (sent on mesh or spoke-SDP) | Zero VLAN tags | One VLAN tag | Two VLAN Tags (enabled by force-qinq-vc-forwarding [c-tag-c-tag | s-tag-c-tag] |
|---|---|---|---|
VLAN identifiers (set in VLAN tags) |
— |
For one VLAN tag, one of the following applies:
|
The inner and outer VLAN tags are derived from one of the following:
|
|
|||
Ethertype (set in VLAN tags) |
— |
0x8100 or value configured under sdp vlan-vc-etype |
Both inner and outer VLAN tags: 0x8100, or outer VLAN tag value configured under sdp vlan-vc-etype (inner VLAN tag value is 0x8100) |
Egress QoS (dot1p/DE) (set in VLAN tags) |
— |
Taken from the innermost ingress service delimiting tag, one of the following applies:
|
Inner and outer dot1p/DE: If c-tag-c-tag is configured, the inner and outer dot1p/DE bits are both taken from the innermost ingress service delimiting tag. It can be one of the following:
|
Egress QoS (dot1p/DE) (set in VLAN tags) |
— |
0 if there is no service delimiting VLAN tag at the ingress SAP or mesh/spoke-SDP Note that neither the inner nor outer dot1p/DE values can be explicitly set. |
0 if there is no service delimiting VLAN tag at the ingress SAP or mesh/spoke-SDP If s-tag-c-tag is configured, the inner and outer dot1p/DE bits are taken from the inner and outer ingress service delimiting tag (respectively). They can be:
|
Any non-service delimiting VLAN tags are forwarded transparently through the VPLS service. SAP egress classification is possible on the outermost customer VLAN tag received on a mesh or spoke-SDP using the ethernet-ctag parameter in the associated SAP egress QoS policy.
VPLS MAC learning and packet forwarding
The 7950 XRS, 7750 SR, and 7450 ESS perform the packet replication required for broadcast and multicast traffic across the bridged domain. MAC address learning is performed by the router to reduce the amount of unknown destination MAC address flooding.
The 7450 ESS, 7750 SR, and 7950 XRS routers learn the source MAC addresses of the traffic arriving on their access and network ports.
Each router maintains an FDB for each VPLS service instance and learned MAC addresses are populated in the FDB table of the service. All traffic is switched based on MAC addresses and forwarded between all objects in the VPLS service. Unknown destination packets (for example, the destination MAC address has not been learned) are forwarded on all objects to all participating nodes for that service until the target station responds and the MAC address is learned by the routers associated with that service.
MAC learning protection
In a Layer 2 environment, subscribers or customers connected to SAPs A or B can create a denial of service attack by sending packets sourcing the gateway MAC address. This moves the learned gateway MAC from the uplink SDP/SAP to the subscriber’s or customer’s SAP causing all communication to the gateway to be disrupted. If local content is attached to the same VPLS (D), a similar attack can be launched against it. Communication between subscribers or customers is also disallowed but split horizon is not sufficient in the topology shown in MAC learning protection.

The 7450 ESS, 7750 SR, and 7950 XRS routers enable MAC learning protection capability for SAPs and SDPs. With this mechanism, forwarding and learning rules apply to the non-protected SAPs. Assume hosts H1, H2, and H3 (MAC learning protection) are non-protected while IES interfaces G and H are protected. When a frame arrives at a protected SAP/SDP, the MAC is learned as usual. When a frame arrives from a non-protected SAP or SDP, the frame must be dropped if the source MAC address is protected and the MAC address is not relearned. The system allows only packets with a protected MAC destination address.
The system can be configured statically. The addresses of all protected MACs are configured. Only the IP address can be included and use a dynamic mechanism to resolve the MAC address (cpe-ping). All protected MACs in all VPLS instances in the network must be configured.
To eliminate the ability of a subscriber or customer to cause a DoS attack, the node restricts the learning of protected MAC addresses based on a statically defined list. Also, the destination MAC address is checked against the protected MAC list to verify that a packet entering a restricted SAP has a protected MAC as a destination.
DEI in IEEE 802.1ad
The IEEE 802.1ad-2005 standard allows drop eligibility to be conveyed separately from priority in Service VLAN TAGs (S-TAGs) so that all of the previously introduced traffic types can be marked as drop eligible. The S-TAG has a new format where the priority and discard eligibility parameters are conveyed in the 3-bit Priority Code Point (PCP) field and, respectively, in the DE bit (DE bit in the 802.1ad S-TAG).
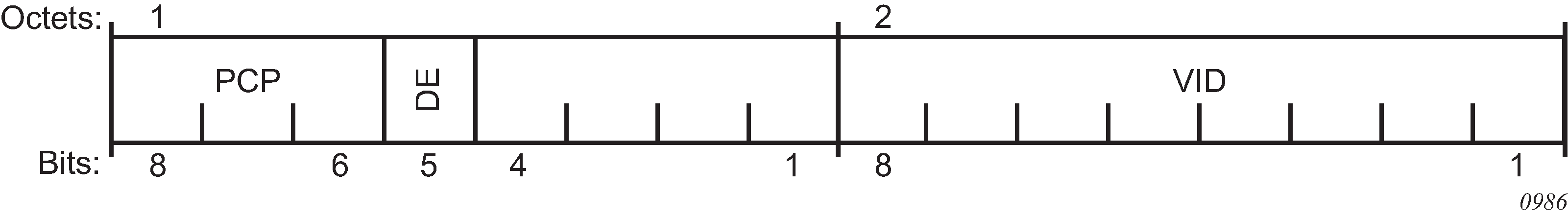
The DE bit allows the S-TAG to convey eight forwarding classes/distinct emission priorities, each with a drop eligible indication.
When the DE bit is set to 0 (DE=FALSE), the related packet is not discarded eligible. This is the case for the packets that are within the CIR limits and must be prioritized in case of congestion. If the DEI is not used or backwards compliance is required, the DE bit should be set to zero on transmission and ignored on reception.
When the DE bit is set to 1 (DE=TRUE), the related packet is discarded eligible. This is the case for the packets that are sent above the CIR limit (but below the PIR). In case of congestion, these packets are the first ones to be dropped.
VPLS using G.8031 protected Ethernet tunnels
The use of MPLS tunnels provides a way to scale the core while offering fast failover times using MPLS FRR. In environments where Ethernet services are deployed using native Ethernet backbones, Ethernet tunnels are provided to achieve the same fast failover times as in the MPLS FRR case. There are still service provider environments where Ethernet services are deployed using native Ethernet backbones.
The Nokia VPLS implementation offers the capability to use core Ethernet tunnels compliant with ITU-T G.8031 specification to achieve 50 ms resiliency for backbone failures. This is required to comply with the stringent SLAs provided by service providers in the current competitive environment. The implementation also allows a LAG-emulating Ethernet tunnel providing a complimentary native Ethernet E-LAN capability. The LAG-emulating Ethernet tunnels and G.8031 protected Ethernet tunnels operate independently. For more information, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide, "LAG Emulation using Ethernet Tunnels".
When using Ethernet tunnels, the Ethernet tunnel logical interface is created first. The Ethernet tunnel has member ports that are the physical ports supporting the links. The Ethernet tunnel controls SAPs that carry G.8031 and 802.1ag control traffic and user data traffic. Ethernet Service SAPs are configured on the Ethernet tunnel. Optionally, when tunnels follow the same paths, end-to-end services are configured with same-fate Ethernet tunnel SAPs, which carry only user data traffic, and share the fate of the Ethernet tunnel port (if properly configured).
When configuring VPLS and B-VPLS using Ethernet tunnels, the services are very similar.
For examples, see the IEEE 802.1ah PBB Guide.
Pseudowire control word
The control-word command enables the use of the control word individually on each mesh SDP or spoke-SDP. By default, the control word is disabled. When the control word is enabled, all VPLS packets, including the BPDU frames, are encapsulated with the control word. The Targeted LDP (T-LDP) control plane behavior is the same as the control word for VLL services. The configuration for the two directions of the Ethernet pseudowire should match.
Table management
The following sections describe VPLS features related to management of the FDB.
Selective MAC address learning
Source MAC addresses are learned in a VPLS service by default with an entry allocated in the FDB for each address on all line cards. Therefore, all MAC addresses are considered to be global. This operation can be modified so that the line card allocation of some MAC addresses is selective, based on where the service has a configured object.
An example of the advantage of selective MAC address learning is for services to benefit from the higher MAC address scale of some line cards (particularly for network interfaces used by mesh or spoke-SDPs, EVPN-VXLAN tunnels, and EVPN-MPLS destinations) while using lower MAC address scale cards for the SAPs.
Selective MAC addresses are those learned locally and dynamically in the data path (displayed in the show output with type ‟L”) or by EVPN (displayed in the show output with type ‟Evpn”, excluding those with the sticky bit set, which are displayed with type ‟EvpnS”). An exception is when a MAC address configured as a conditional static MAC address is learned dynamically on an object other than its monitored object; this can be displayed with type ‟L” or ‟Evpn” but is learned as global because of the conditional static MAC configuration.
Selective MAC addresses have FDB entries allocated on line cards where the service has a configured object. When a MAC address is learned, it is allocated an FDB entry on all line cards on which the service has a SAP configured (for LAG or Ethernet tunnel SAPs, the MAC address is allocated an FDB entry on all line cards on which that LAG or Ethernet tunnel has configured ports) and on all line cards that have a network interface port if the service is configured with VXLAN, EVPN-MPLS, or a mesh or spoke-SDP.
When using selective learning in an I-VPLS service, the learned C-MACs are allocated FDB entries on all the line cards where the I-VPLS service has a configured object and on the line cards on which the associated B-VPLS has a configured object. When using selective learning in a VPLS service with allow-ip-intf-bind configured (for it to become an R-VPLS), FDB entries are allocated on all line cards on which there is an IES or VPRN interface.
If a new configured object is added to a service and there are sufficient MAC FDB resources available on the new line cards, the selective MAC addresses present in the service are allocated on the new line cards. Otherwise, if any of the selective MAC addresses currently learned in the service cannot be allocated an FDB entry on the new line cards, those MAC addresses are deleted from all line cards. Such a deletion increments the FailedMacCmplxMapUpdts statistic displayed in the tools dump service vpls-fdb-stats output.
When the set of configured objects changes for a service using selective learning, the system must reallocate its FDB entries accordingly, which can cause FDB entry ‟allocate” or ‟free” operations to become pending temporarily. The pending operations can be displayed using the tools dump service id fdb command.
When a global MAC address is to be learned, there must be a free FDB entry in the service and system FDBs and on all line cards in the system for it to be accepted. When a selective MAC address is to be learned, there must be a free FDB entry in the service and system FDBs and on all line cards where the service has a configured object for it to be accepted.
To demonstrate the selective MAC address learning logic, consider the following:
a system has three line cards: 1, 2, and 3
two VPLS services are configured on the system:
VPLS 1 having learned MAC addresses M1, M2, and M3 and has configured SAPs 1/1/1 and 2/1/1
VPLS 2 having learned MAC addresses M4, M5, and M6 and has configured SAPs 2/1/2 and 3/1/1
This is shown in MAC address learning logic example .
| Learned MAC addresses | Configured SAPs | |
|---|---|---|
VPLS1 |
M1, M2, M3 |
SAP 1/1/1 SAP 2/1/1 |
VPLS2 |
M4, M5, M6 |
SAP 2/1/2 SAP 3/1/1 |
MAC FDB entry allocation: global versus selective shows the FDB entry allocation when the MAC addresses are global and when they are selective. Notice that in the selective case, all MAC addresses are allocated FDB entries on line card 2, but line card 1 and 3 only have FDB entries allocated for services VPLS 1 and VPLS 2, respectively.
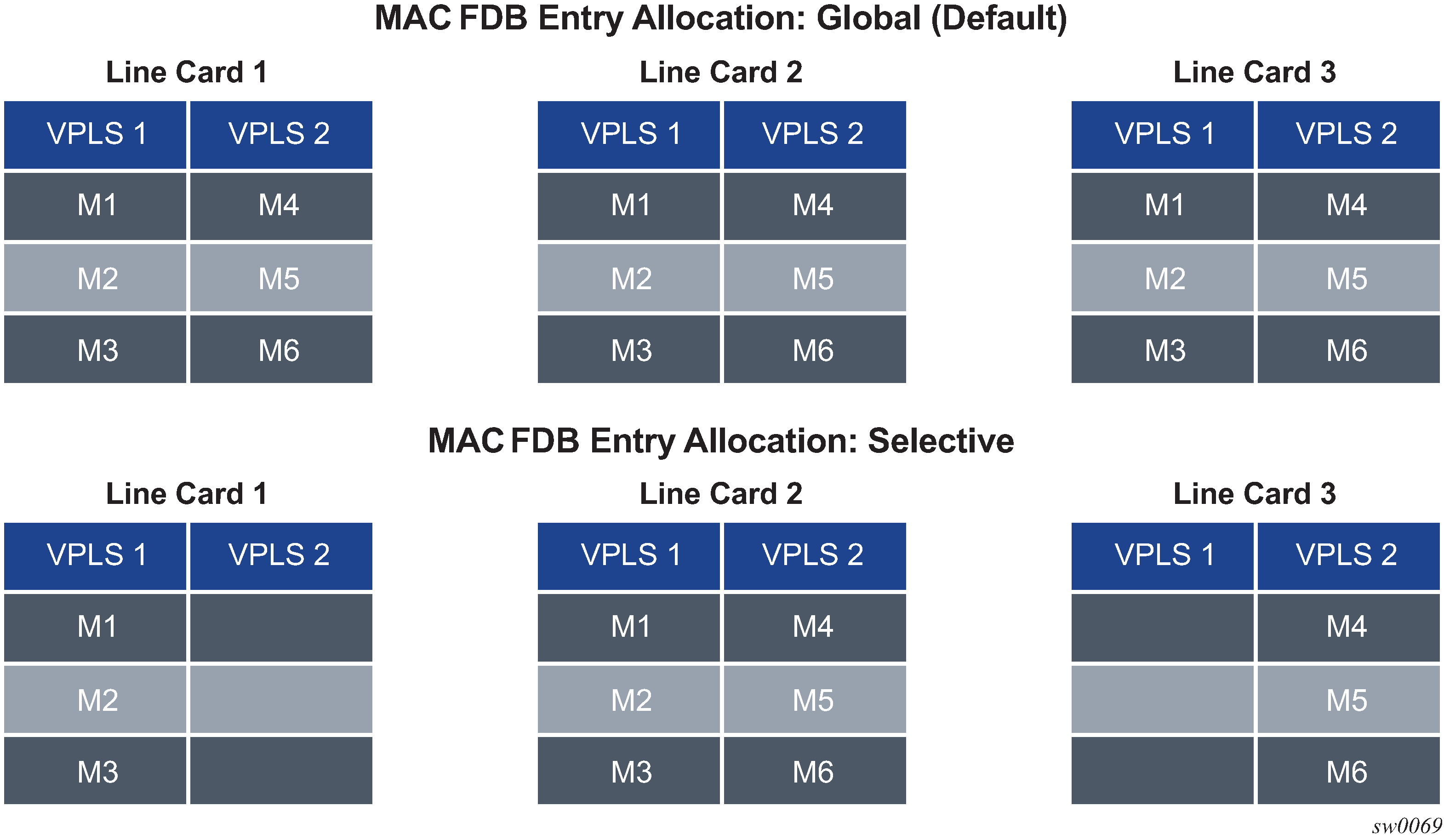
Selective MAC address learning can be enabled as follows within any VPLS service, except for B-VPLS and R-VPLS services:
configure
service
vpls <service-id> create
[no] selective-learned-fdb
Enabling selective MAC address learning has no effect on single line card systems.
When selective learning is enabled or disabled in a VPLS service, the system may need to reallocate FDB entries; this can cause temporary pending FDB entry allocate or free operations. The pending operations can be displayed using the tools dump service id fdb command.
Example operational information
The show and tools dump command output can display the global and selective MAC addresses along with the MAC address limits and the number of allocated and free MAC-address FDB entries. The show output displays the system and card FDB usage, while the tools output displays the FDB per service with respect to MAC addresses and cards.
The configuration for the following output is similar to the simple example above:
the system has three line cards: 1, 2, and 5
the system has two VPLS services:
VPLS 1 is an EVPN-MPLS service with a SAP on 5/1/1:1 and uses a network interface on 5/1/5.
VPLS 2 has two SAPs on 2/1/1:2 and 2/1/2:2.
The first output shows the default where all MAC addresses are global. The second enables selective learning in the two VPLS services.
Global MAC address learning only (default)
By default, VPLS 1 and 2 are not configured for selective learning, so all MAC addresses are global:
*A:PE1# show service id [1,2] fdb | match expression ", Service|Sel Learned FDB"
Forwarding Database, Service 1
Sel Learned FDB : Disabled
Forwarding Database, Service 2
Sel Learned FDB : Disabled
*A:PE1#
Traffic is sent into the services, resulting in the following MAC addresses being learned:
*A:PE1# show service fdb-mac
===============================================================================
Service Forwarding Database
===============================================================================
ServId MAC Source-Identifier Type Last Change
Age
-------------------------------------------------------------------------------
1 00:00:00:00:01:01 sap:5/1/1:1 L/0 01/31/17 08:44:37
1 00:00:00:00:01:02 sap:5/1/1:1 L/0 01/31/17 08:44:37
1 00:00:00:00:01:03 eMpls: EvpnS 01/31/17 08:41:38
P
10.251.72.58:262142
1 00:00:00:00:01:04 eMpls: EvpnS 01/31/17 08:41:38
P
10.251.72.58:262142
2 00:00:00:00:02:01 sap:2/1/2:2 L/0 01/31/17 08:44:37
2 00:00:00:00:02:02 sap:2/1/2:2 L/0 01/31/17 08:44:37
2 00:00:00:02:02:03 sap:2/1/1:2 L/0 01/31/17 08:44:37
2 00:00:00:02:02:04 sap:2/1/1:2 L/0 01/31/17 08:44:37
-------------------------------------------------------------------------------
No. of Entries: 8
-------------------------------------------------------------------------------
Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static Lf=Leaf
===============================================================================
*A:PE1#
A total of eight MAC addresses are learned. There are two MAC addresses learned locally on SAP 5/1/1:1 in service VPLS 1 (type ‟L”), and another two MAC addresses learned using EVPN with the sticky bit set, also in service VPLS 1 (type ‟EvpnS”). A further two sets of two MAC addresses are learned on SAP 2/1/1:2 and 2/1/2:2 in service VPLS 2 (type ‟L”).
The system and line card FDB usage is shown as follows:
*A:PE1# show service system fdb-usage
===============================================================================
FDB Usage
===============================================================================
System
-------------------------------------------------------------------------------
Limit: 511999
Allocated: 8
Free: 511991
Global: 8
-------------------------------------------------------------------------------
Line Cards
-------------------------------------------------------------------------------
Card Selective Allocated Limit Free
-------------------------------------------------------------------------------
1 0 8 511999 511991
2 0 8 511999 511991
5 0 8 511999 511991
-------------------------------------------------------------------------------
===============================================================================
*A:PE1#
The system MAC address limit is 511999, of which eight are allocated, and the rest are free. All eight MAC addresses are global and are allocated on cards 1, 2, and 5. There are no selective MAC addresses. This output can be reduced to specific line cards by specifying the card’s slot ID as a parameter to the command.
To see the MAC address information per service, tools dump commands can be used, as follows for VPLS 1. The following output displays the card status:
*A:PE1# tools dump service id 1 fdb card-status
===============================================================================
VPLS FDB Card Status at 01/31/2017 08:44:38
===============================================================================
Card Allocated PendAlloc PendFree
-------------------------------------------------------------------------------
1 4 0 0
2 4 0 0
5 4 0 0
===============================================================================
*A:PE1#
All of the line cards have four FDB entries allocated in VPLS 1. The ‟PendAlloc” and ‟PendFree” columns show the number of pending MAC address allocate and free operations, which are all zero.
The following output displays the MAC address status for VPLS 1:
*A:PE1# tools dump service id 1 fdb mac-status
===============================================================================
VPLS FDB MAC status at 01/31/2017 08:44:38
===============================================================================
MAC Address Type Status : Card list
-------------------------------------------------------------------------------
00:00:00:00:01:01 Global Allocated : All
00:00:00:00:01:02 Global Allocated : All
00:00:00:00:01:03 Global Allocated : All
00:00:00:00:01:04 Global Allocated : All
===============================================================================
*A:PE1#
The type and card list for each MAC address in VPLS 1 is displayed. VPLS 1 has learned four MAC addresses: the two local MAC addresses on SAP 5/1/1:1 and the two EvpnS MAC addresses. Each MAC address has an FDB entry allocated on all line cards. This output can be further reduced by optionally including a specified MAC address, a specific card, and the operational pending state.
Selective and global MAC address learning
Selective MAC address learning is now enabled in VPLS 1 and VPLS 2, as follows:
*A:PE1# show service id [1,2] fdb | match expression ", Service|Sel Learned FDB"
Forwarding Database, Service 1
Sel Learned FDB : Enabled
Forwarding Database, Service 2
Sel Learned FDB : Enabled
*A:PE1#
The MAC addresses learned are the same, with the same traffic being sent; however, there are now selective MAC addresses that are allocated FDB entries on different line cards.
The system and line card FDB usage is as follows:
*A:PE1# show service system fdb-usage
===============================================================================
FDB Usage
===============================================================================
System
-------------------------------------------------------------------------------
Limit: 511999
Allocated: 8
Free: 511991
Global: 2
-------------------------------------------------------------------------------
Line Cards
-------------------------------------------------------------------------------
Card Selective Allocated Limit Free
-------------------------------------------------------------------------------
1 0 2 511999 511997
2 4 6 511999 511993
5 2 4 511999 511995
-------------------------------------------------------------------------------
===============================================================================
*A:PE1#
The system MAC address limit and allocated numbers have not changed but now there are only two global MAC addresses; these are the two EvpnS MAC addresses.
There are two FDB entries allocated on card 1, which are the global MAC addresses; there are no services or network interfaces configured on card 1, so the FDB entries allocated are for the global MAC addresses.
Card 2 has six FDB entries allocated in total: two for the global MAC addresses plus four for the selective MAC addresses in VPLS 2 (these are the two sets of two local MAC addresses in VPLS 2 on SAP 2/1/1:2 and 2/1/2:2).
Card 5 has four FDB entries allocated in total: two for the global MAC addresses plus two for the selective MAC addresses in VPLS 1 (these are the two local MAC addresses in VPLS 1 on SAP 5/1/1:1).
This output can be reduced to specific line cards by specifying the card’s slot ID as a parameter to the command.
To see the MAC address information per service, tools dump commands can be used for VPLS 1.
The following output displays the card status:
*A:PE1# tools dump service id 1 fdb card-status
===============================================================================
VPLS FDB Card Status at 01/31/2017 08:44:39
===============================================================================
Card Allocated PendAlloc PendFree
-------------------------------------------------------------------------------
1 2 0 0
2 2 0 0
5 4 0 0
===============================================================================
*A:PE1#
There are two FDB entries allocated on line card 1, two on line card 2, and four on line card 5. The ‟PendAlloc” and ‟PendFree” columns are all zeros.
The following output displays the MAC address status for VPLS 1:
*A:PE1# tools dump service id 1 fdb mac-status
===============================================================================
VPLS FDB MAC status at 01/31/2017 08:44:39
===============================================================================
MAC Address Type Status : Card list
-------------------------------------------------------------------------------
00:00:00:00:01:01 Select Allocated : 5
00:00:00:00:01:02 Select Allocated : 5
00:00:00:00:01:03 Global Allocated : All
00:00:00:00:01:04 Global Allocated : All
===============================================================================
*A:PE1#
The type and card list for each MAC address in VPLS 1 is displayed. VPLS 1 has learned four MAC addresses: the two local MAC addresses on SAP 5/1/1:1 and the two EvpnS MAC addresses. The local MAC addresses are selective and have FDB entries allocated only on card 5. The global MAC addresses are allocated on all line cards. This output can be further reduced by optionally including a specified MAC address, a specific card, and the operational pending state.
System FDB size
The system FDB table size is configurable as follows:
configure
service
system
fdb-table-size table-size
where table-size can have values in the range from 255999 to 2047999 (2000k).
The default, minimum, and maximum values for the table size are dependent on the chassis type. To support more than 500k MAC addresses, the CPMs provisioned in the system must have at least 16 GB memory. The maximum system FDB table size also limits the maximum FDB table size of any card within the system.
The actual achievable maximum number of MAC addresses depends on the MAC address scale supported by the active cards and whether selective learning is enabled.
If an attempt is made to configure the system FDB table size such that:
the new size is greater than or equal to the current number of allocated FDB entries, the command succeeds and the new system FDB table size is used
the new size is less than the number of allocated FDB entries, the command fails with an error message. In this case, the user is expected to reduce the current FDB usage (for example, by deleting statically configured MAC addresses, shutting down EVPN, clearing learned MACs, and so on) to lower the number of allocated MAC addresses in the FDB so that it does not exceed the system FDB table size being configured.
The logic when attempting a rollback is similar; however, when rolling back to a configuration where the system FDB table size is smaller than the current system FDB table size, the system flushes all learned MAC addresses (by performing a shutdown then no shutdown in all VPLS services) to allow the rollback to continue.
The system FDB table size can be larger than some of the line card FDB sizes, resulting in the possibility that the current number of allocated global MAC addresses is larger than the maximum FDB size supported on some line cards. When a new line card is provisioned, the system checks whether the line card's FDB can accommodate all of the currently allocated global MAC addresses. If it can, then the provisioning succeeds; if it cannot, then the provisioning fails and an error is reported. If the provisioning fails, the number of global MACs allocated must be reduced in the system to a number that the new line card can accommodate, then the card-type must be reprovisioned.
Per-VPLS service FDB size
The following MAC table management features are available for each instance of a SAP or spoke-SDP within a particular VPLS service instance.
-
When the limit is reached on a SAP or spoke-SDP, packets with unknown source MAC addresses are still forwarded (this default behavior can be changed by configuration). By default, if the destination MAC address is known, it is forwarded based on the FDB, and if the destination MAC address is unknown, it is flooded. Alternatively, if discard unknown is enabled at the VPLS service level, any packets from unknown source MAC addresses are discarded at the SAP.
-
The log event SAP MAC Limit Reached is generated when the limit is reached. When the condition is cleared, the log event SAP MAC Limit Reached Condition Cleared is generated.
-
Disable learning allows users to disable the dynamic learning function on a SAP or a spoke-SDP of a VPLS service instance.
-
Disable aging allows users to turn off aging for learned MAC addresses on a SAP or a spoke-SDP of a VPLS service instance.
System FDB size alarms
High and low watermark alarms give warning when the system MAC FDB usage is high. An alarm is generated when the number of FDB entries allocated in the system FDB reaches 95% of the total system FDB table size and is cleared when it reduces to 90% of the system FDB table size. These percentages are not configurable.
Line card FDB size alarms
High and low watermark alarms give warning when a line card's MAC FDB usage is high. An alarm is generated when the number of FDB entries allocated in a line card FDB reaches 95% of its maximum FDB table size and is cleared when it reduces to 90% of its maximum FDB table size. These percentages are not configurable.
Per VPLS FDB size alarms
The size of the VPLS FDB can be configured with a low watermark and a high watermark, expressed as a percentage of the total FDB size limit. If the actual FDB size grows above the configured high watermark percentage, an alarm is generated. If the FDB size falls below the configured low watermark percentage, the alarm is cleared by the system.
Local and remote aging timers
Like a Layer 2 switch, learned MACs within a VPLS instance can be aged out if no packets are sourced from the MAC address for a specified period of time (the aging time). In each VPLS service instance, there are independent aging timers for locally learned MAC and remotely learned MAC entries in the FDB. A local MAC address is a MAC address associated with a SAP because it ingressed on a SAP. A remote MAC address is a MAC address received by an SDP from another router for the VPLS instance. The local-age timer for the VPLS instance specifies the aging time for locally learned MAC addresses, and the remote-age timer specifies the aging time for remotely learned MAC addresses.
In general, the remote-age timer is set to a longer period than the local-age timer to reduce the amount of flooding required for unknown destination MAC addresses. The aging mechanism is considered a low priority process. In most situations, the aging out of MAC addresses happens within tens of seconds beyond the age time. However, it, can take up to two times their respective age timer to be aged out.
Disable MAC aging
The MAC aging timers can be disabled, which prevents any learned MAC entries from being aged out of the FDB. When aging is disabled, it is still possible to manually delete or flush learned MAC entries. Aging can be disabled for learned MAC addresses on a SAP or a spoke-SDP of a VPLS service instance.
Disable MAC learning
When MAC learning is disabled for a service, new source MAC addresses are not entered in the VPLS FDB, whether the MAC address is local or remote. MAC learning can be disabled for individual SAPs or spoke-SDPs.
Unknown MAC discard
Unknown MAC discard is a feature that discards all packets that ingress the service where the destination MAC address is not in the FDB. The normal behavior is to flood these packets to all endpoints in the service.
Unknown MAC discard can be used with the disable MAC learning and disable MAC aging options to create a fixed set of MAC addresses allowed to ingress and traverse the service.
VPLS and rate limiting
Traffic that is normally flooded throughout the VPLS can be rate limited on SAP ingress through the use of service ingress QoS policies. In a service ingress QoS policy, individual queues can be defined per forwarding class to provide shaping of broadcast traffic, MAC multicast traffic, and unknown destination MAC traffic.
MAC move
The MAC move feature is useful to protect against undetected loops in a VPLS topology as well as the presence of duplicate MACs in a VPLS service.
If two clients in the VPLS have the same MAC address, the VPLS experiences a high relearn rate for the MAC. When MAC move is enabled, the 7450 ESS, 7750 SR, or 7950 XRS shuts down the SAP or spoke-SDP and creates an alarm event when the threshold is exceeded.
MAC move allows sequential order port blocking. By configuration, some VPLS ports can be configured as ‟non-blockable”, which allows a simple level of control of which ports are being blocked during loop occurrence. There are two sophisticated control mechanisms that allow blocking of ports in a sequential order:
Configuration capabilities to group VPLS ports and to define the order in which they should be blocked
Criteria defining when individual groups should be blocked
For the first control mechanism, configuration CLI is extended by definition of ‟primary” and ‟secondary” ports. Per default, all VPLS ports are considered ‟tertiary” ports unless they are explicitly declared primary or secondary. The order of blocking always follows a strict order starting from tertiary to secondary, and then primary.
The definition of criteria for the second control mechanism is the number of periods during which the specified relearn rate has been exceeded. The mechanism is based on the cumulative factor for every group of ports. Tertiary VPLS ports are blocked if the relearn rate exceeds the configured threshold during one period, while secondary ports are blocked only when relearn rates are exceeded during two consecutive periods, and primary ports when exceeded during three consecutive periods. The retry timeout period must be larger than the period before blocking the highest priority port so that the retry timeout sufficiently spans across the period required to block all ports in sequence. The period before blocking the highest priority port is the cumulative factor of the highest configured port multiplied by 5 seconds (the retry timeout can be configured through the CLI).
Auto-learn MAC protect
This section provides information about auto-learn-mac-protect and restrict-protected-src discard-frame features.
VPLS solutions usually involve learning MAC addresses in order for traffic to be forwarded to the correct SAP/SDP. If a MAC address is learned on the wrong SAP/SDP, traffic would be redirected away from its intended destination. This could occur through a misconfiguration, a problem in the network, or by a malicious source creating a DoS attack, and is applicable to any type of VPLS network; for example, mobile backhaul or residential service delivery networks. The auto-learn-mac-protect feature can be used to safeguard against the possibility of MAC addresses being learned on the wrong SAP/SDP.
This feature provides the ability to automatically protect source MAC addresses that have been learned on a SAP or a spoke/mesh SDP and prevent frames with the same protected source MAC address from entering into a different SAP/spoke or mesh SDP.
This is a complementary solution to features such as mac-move and mac-pinning, but has the advantage that MAC moves are not seen and it has a low operational complexity. If a MAC is initially learned on the wrong SAP/SDP, the operator can clear the MAC from the MAC FDB in order for it to be relearned on the correct SAP/SDP.
Two separate commands are used, which provide the configuration flexibility of separating the identification (learning) function from the application of the restriction (discard).
The auto-learn-mac-protect and restrict-protected-src commands allow the following functions:
the ability to enable the automatic protection of a learned MAC using the auto-learn-mac-protect command under a SAP/spoke or mesh SDP/SHG context
the ability to discard frames associated with automatically protected MACs instead of shutting down the entire SAP/SDP as with the restrict-protected-src feature. This is enabled using a restrict-protected-src discard-frame command in the SAP/spoke or mesh SDP/SHG context. An optimized alarm mechanism is used to generate alarms related to these discards. The frequency of alarm generation is fixed to be, at most, one alarm per MAC address per forwarding complex per 10 minutes in a VPLS service.
If the auto-learn-mac-protect or restrict-protected-src discard-frame feature is configured under an SHG, the operation applies only to SAPs in the SHG, not to spoke-SDPs in the SHG. If required, these parameters can also be enabled explicitly under specific SAPs/spoke-SDPs within the SHG.
Applying or removing auto-learn-mac-protect or restrict-protected-src discard-frame to/from a SAP, spoke or mesh SDP, or SHG, clears the MACs on the related objects (for the SHG, this results in clearing the MACs only on the SAPs within the SHG).
The use of restrict-protected-src discard-frame and both the restrict-protected-src [alarm-only] command and with the configuration of manually protected MAC addresses, using the mac-protect command, within a specified VPLS are mutually exclusive.
The following rules govern the changes to the state of protected MACs:
Automatically learned protected MACs are subject to normal removal, aging (unless disabled), and flushing, at which time the associated entries are removed from the FDB.
Automatically learned protected MACs can only move from their learned SAP/spoke or mesh SDP if they enter a SAP/spoke or mesh SDP without restrict-protected-src enabled.
If a MAC address does legitimately move between SAPs/spoke or mesh SDPs after it has been automatically protected on a specified SAP/spoke or mesh SDP (thereby causing discards when received on the new SAP/spoke or mesh SDP), the operator must manually clear the MAC from the FDB for it to be learned in the new/correct location.
MAC addresses that are manually created (using static-mac, static-host with a MAC address specified, or oam mac-populate) are not protected even if they are configured on a SAP/spoke or mesh SDP that has auto-learn-mac-protect enabled on it. Also, the MAC address associated with an R-VPLS IP interface is protected within its VPLS service such that frames received with this MAC address as the source address are discarded (this is not based on the auto-learn MAC protect function). However, VRRP MAC addresses associated with an R-VPLS IP interface are not protected either in this way or using the auto-learn MAC protect function.
MAC addresses that are dynamically created (learned, using static-host with no MAC address specified, or lease-populate) are protected when the MAC address is learned on a SAP/spoke or mesh SDP that has auto-learn-mac-protect enabled on it.
The actions of the following features are performed in the order listed.
Restrict-protected-src
MAC-pinning
MAC-move
Operation
Auto-learn-mac-protect operation shows a specific configuration using auto-learn-mac-protect and restrict-protected-src discard-frame to describe their operation for the 7750 SR, 7450 ESS, or 7950 XRS.
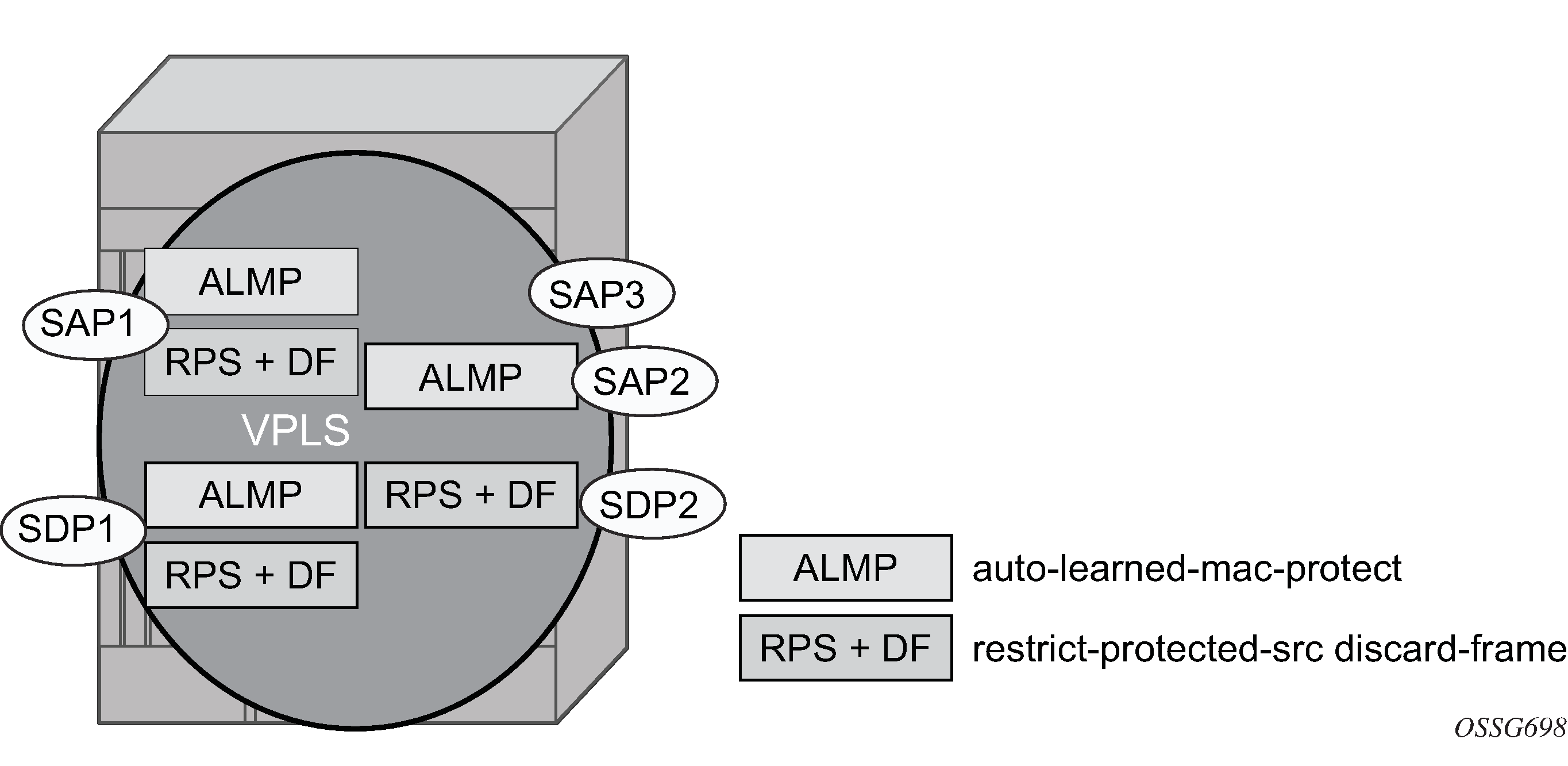
A VPLS service is configured with SAP1 and SDP1 connecting to access devices and SAP2, SAP3, and SDP2 connecting to the core of the network. The auto-learn-mac-protect feature is enabled on SAP1, SAP3, and SDP1, and restrict-protected-src discard-frame is enabled on SAP1, SDP1, and SDP2. The following series of events describes the details of the functionality:
Assume that the FDB is empty at the start of each sequence.
Sequence 1:
A frame with source MAC A enters SAP1, MAC A is learned on SAP1, and MAC-A/SAP1 is protected because of the presence of the auto-learn-mac-protect on SAP1.
All subsequent frames with source MAC A entering SAP1 are forwarded into the VPLS.
Frames with source MAC A enter either SDP1 or SDP2, these frames are discarded, and an alarm indicating MAC A and SDP1/SDP2 is initiated because of the presence of the restrict-protected-src discard-frame on SDP1/SDP2.
The above continues, with MAC-A/SAP1 protected in the FDB until MAC A on SAP1 is removed from the FDB.
Sequence 2:
A frame with source MAC A enters SAP1, MAC A is learned on SAP1, and MAC-A/SAP1 is protected because of the presence of the auto-learn-mac-protect on SAP1.
A frame with source MAC A enters SAP2. As restrict-protected-src is not enabled on SAP2, MAC A is relearned on SAP2 (but not protected), replacing the MAC-A/SAP1 entry in the FDB.
All subsequent frames with source MAC A entering SAP2 are forwarded into the VPLS. This is because restrict-protected-src is not enabled SAP2 and auto-learn-mac-protect is not enabled on SAP2, so the FDB is not changed.
A frame with source MAC A enters SAP1, MAC A is relearned on SAP1, and MAC-A/SAP1 is protected because of the presence of the auto-learn-mac-protect on SAP1.
Sequence 3:
A frame with source MAC A enters SDP2, MAC A is learned on SDP2, but is not protected as auto-learn-mac-protect is not enabled on SDP2.
A frame with source MAC A enters SDP1, and MAC A is relearned on SDP1 because previously it was not protected. Consequently, MAC-A/SDP1 is protected because of the presence of the auto-learn-mac-protect on SDP1.
Sequence 4:
A frame with source MAC A enters SAP1, MAC A is learned on SAP1, and MAC-A/SAP1 is protected because of the presence of the auto-learn-mac-protect on SAP1.
A frame with source MAC A enters SAP3. As restrict-protected-src is not enabled on SAP3, MAC A is relearned on SAP3 and the MAC-A/SAP1 entry is removed from the FDB with MAC-A/SAP3 being added as protected to the FDB (because auto-learn-mac-protect is enabled on SAP3).
All subsequent frames with source MAC A entering SAP3 are forwarded into the VPLS.
A frame with source MAC A enters SAP1, these frames are discarded, and an alarm indicating MAC A and SAP1 is initiated because of the presence of the restrict-protected-src discard-frame on SAP1.
Example use
Auto-learn-mac-protect example shows a possible configuration using auto-learn-mac-protect and restrict-protected-src discard-frame in a mobile backhaul network, with the focus on PE1 for the 7750 SR or 7950 XRS.
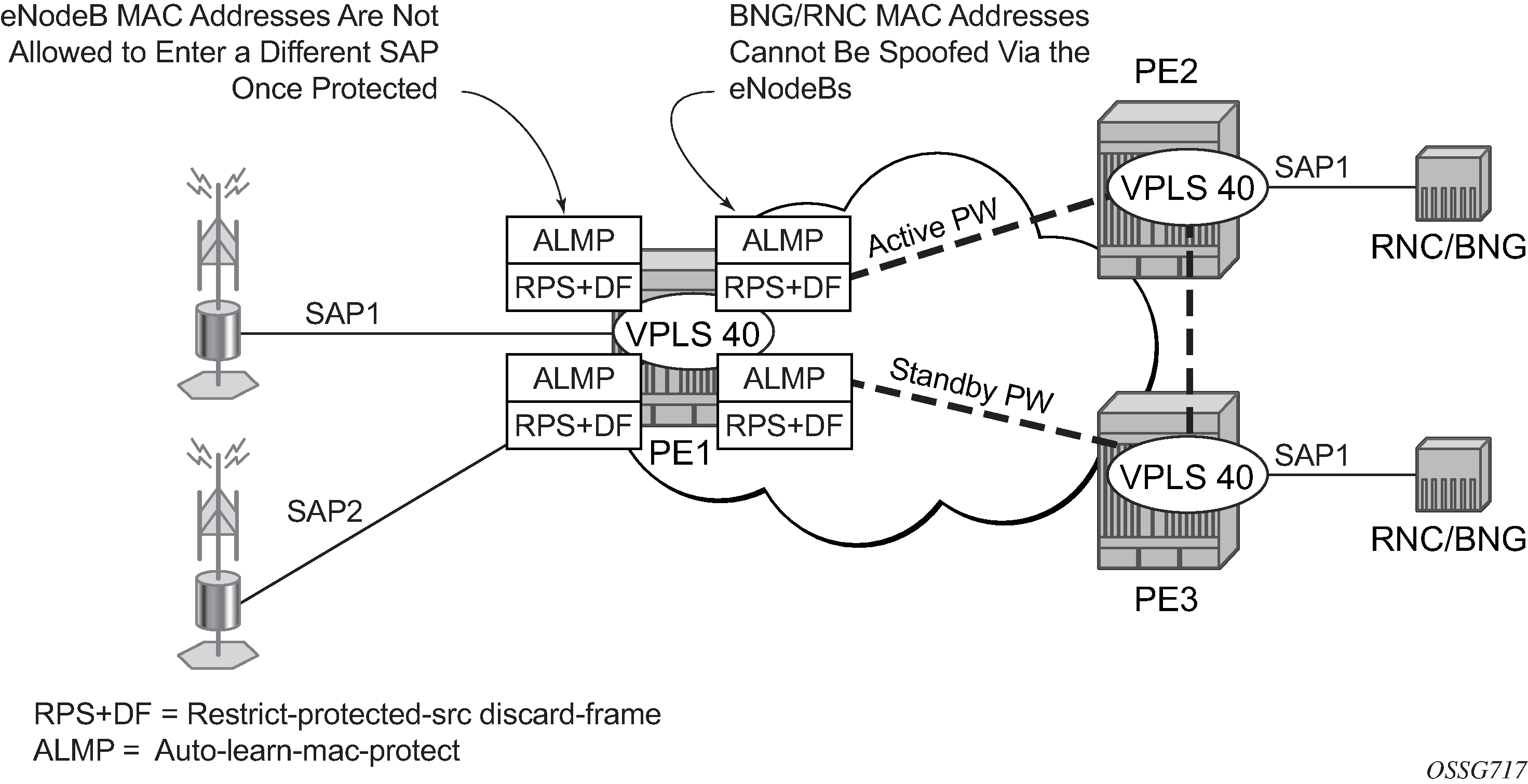
To protect the MAC addresses of the BNG/RNCs on PE1, the auto-learn-mac-protect command is enabled on the pseudowires connecting PE1 to PE2 and PE3. Enabling the restrict-protected-src discard-frame command on the SAPs toward the eNodeBs prevents frames with the source MAC addresses of the BNG/RNCs from entering PE1 from the eNodeBs.
The MAC addresses of the eNodeBs are protected in two ways. In addition to the above commands, enabling the auto-learn-mac-protect command on the SAPs toward the eNodeBs prevents the MAC addresses of the eNodeBs being learned on the wrong eNodeB SAP. Enabling the restrict-protected-src discard-frame command on the pseudowires connecting PE1 to PE2 and PE3 protects the eNodeB MAC addresses from being learned on the pseudowires. This may happen if their MAC addresses are incorrectly injected into VPLS 40 on PE2/PE3 from another eNodeB aggregation PE.
The above configuration is equally applicable to other Layer 2 VPLS-based aggregation networks; for example, to business or residential service networks.
Split horizon SAP groups and split horizon spoke SDP groups
Within the context of VPLS services, a loop-free topology within a fully meshed VPLS core is achieved by applying a split horizon forwarding concept that packets received from a mesh SDP are never forwarded to other mesh SDPs within the same service. The advantage of this approach is that no protocol is required to detect loops within the VPLS core network.
In applications such as DSL aggregation, it is useful to extend this split horizon concept also to groups of SAPs and, or spoke-SDPs. This extension is referred to as a split horizon SAP group or residential bridging.
Traffic arriving on an SAP or a spoke-SDP within a split horizon group is not copied to other SAPs and spoke-SDPs in the same split horizon group (but is copied to SAPs/spoke-SDPs in other split horizon groups if these exist within the same VPLS).
VPLS and spanning tree protocol
Nokia's VPLS service provides a bridged or switched Ethernet Layer 2 network. Equipment connected to SAPs forward Ethernet packets into the VPLS service. The 7450 ESS, 7750 SR, or 7950 XRS participating in the service learns where the customer MAC addresses reside, on ingress SAPs or ingress SDPs.
Unknown destinations, broadcasts, and multicasts are flooded to all other SAPs in the service. If SAPs are connected together, either through misconfiguration or for redundancy purposes, loops can form and flooded packets can keep flowing through the network. The Nokia implementation of the STP is designed to remove these loops from the VPLS topology. This is done by putting one or several SAPs and, or spoke-SDPs in the discarding state.
Nokia's implementation of STP incorporates some modifications to make the operational characteristics of VPLS more effective.
The STP instance parameters allow the balancing between resiliency and speed of convergence extremes. Modifying particular parameters can affect the behavior. For information about command usage, descriptions, and CLI syntax, see Configuring a VPLS service with CLI.
Spanning tree operating modes
Per VPLS instance, a preferred STP variant can be configured. The STP variants supported are:
- rstp
- Rapid Spanning Tree Protocol (RSTP) compliant with IEEE 802.1D-2004 - default mode
- dot1w
- compliant with IEEE 802.1w
- comp-dot1w
- operation as in RSTP but backwards compatible with IEEE 802.1w (this mode allows interoperability with some MTU types)
- mstp
- compliant with the Multiple Spanning Tree Protocol specified in IEEE 802.1Q-REV/D5.0-09/2005. This mode of operation is only supported in a Management VPLS (M-VPLS).
While the 7450 ESS, 7750 SR, or 7950 XRS initially use the mode configured for the VPLS, it dynamically falls back (on a per-SAP basis) to STP (IEEE 802.1D-1998) based on the detection of a BPDU of a different format. A trap or log entry is generated for every change in spanning tree variant.
Some older 802.1w compliant RSTP implementations may have problems with some of the features added in the 802.1D-2004 standard. Interworking with these older systems is improved with the comp-dot1w mode. The differences between the RSTP mode and the comp-dot1w mode are:
The RSTP mode implements the improved convergence over shared media feature; for example, RSTP transitions from discarding to forwarding in 4 seconds when operating over shared media. The comp-dot1w mode does not implement this 802.1D-2004 improvement and transitions conform to 802.1w in 30 seconds (both modes implement fast convergence over point-to-point links).
In the RSTP mode, the transmitted BPDUs contain the port's designated priority vector (DPV) (conforms to 802.1D-2004). Older implementations may be confused by the DPV in a BPDU and may fail to recognize an agreement BPDU correctly. This would result in a slow transition to a forwarding state (30 seconds). For this reason, in the comp-dot1w mode, these BPDUs contain the port's port priority vector (conforms to 802.1w).
The 7450 ESS, 7750 SR, and 7950 XRS support two BPDU encapsulation formats, and can dynamically switch between the following supported formats (on a per-SAP basis):
IEEE 802.1D STP
Cisco PVST
Multiple spanning tree
The Multiple Spanning Tree Protocol (MSTP) extends the concept of IEEE 802.1w RSTP by allowing grouping and associating VLANs to Multiple Spanning Tree Instances (MSTI). Each MSTI can have its own topology, which provides architecture enabling load balancing by providing multiple forwarding paths. At the same time, the number of STP instances running in the network is significantly reduced as compared to Per VLAN STP (PVST) mode of operation. Network fault tolerance is also improved because a failure in one instance (forwarding path) does not affect other instances.
The Nokia implementation of M-VPLS is used to group different VPLS instances under a single RSTP instance. Introducing MSTP into the M-VPLS allows interoperating with traditional Layer 2 switches in an access network and provides an effective solution for dual homing of many business Layer 2 VPNs into a provider network.
Redundancy access to VPLS
The GigE MAN portion of the network is implemented with traditional switches. Using MSTP running on individual switches facilitates redundancy in this part of the network. To provide dual homing of all VPLS services accessing from this part of the network, the VPLS PEs must participate in MSTP.
This can be achieved by configuring M-VPLS on VPLS-PEs (only PEs directly connected to the GigE MAN network), then assigning different managed-VLAN ranges to different MSTP instances. Typically, the M-VPLS would have SAPs with null encapsulations (to receive, send, and transmit MSTP BPDUs) and a mesh SDP to interconnect a pair of VPLS PEs.
Different access scenarios are displayed in Access resiliency as an example of network diagrams dually connected to the PBB PEs:
- Access Type B
- One QinQ switch connected by QinQ/801ad SAPs
- Access Type A
- Source devices connected by null or dot1q SAPs
- Access Type C
- Two or more ES devices connected by QinQ/802.1ad SAPs
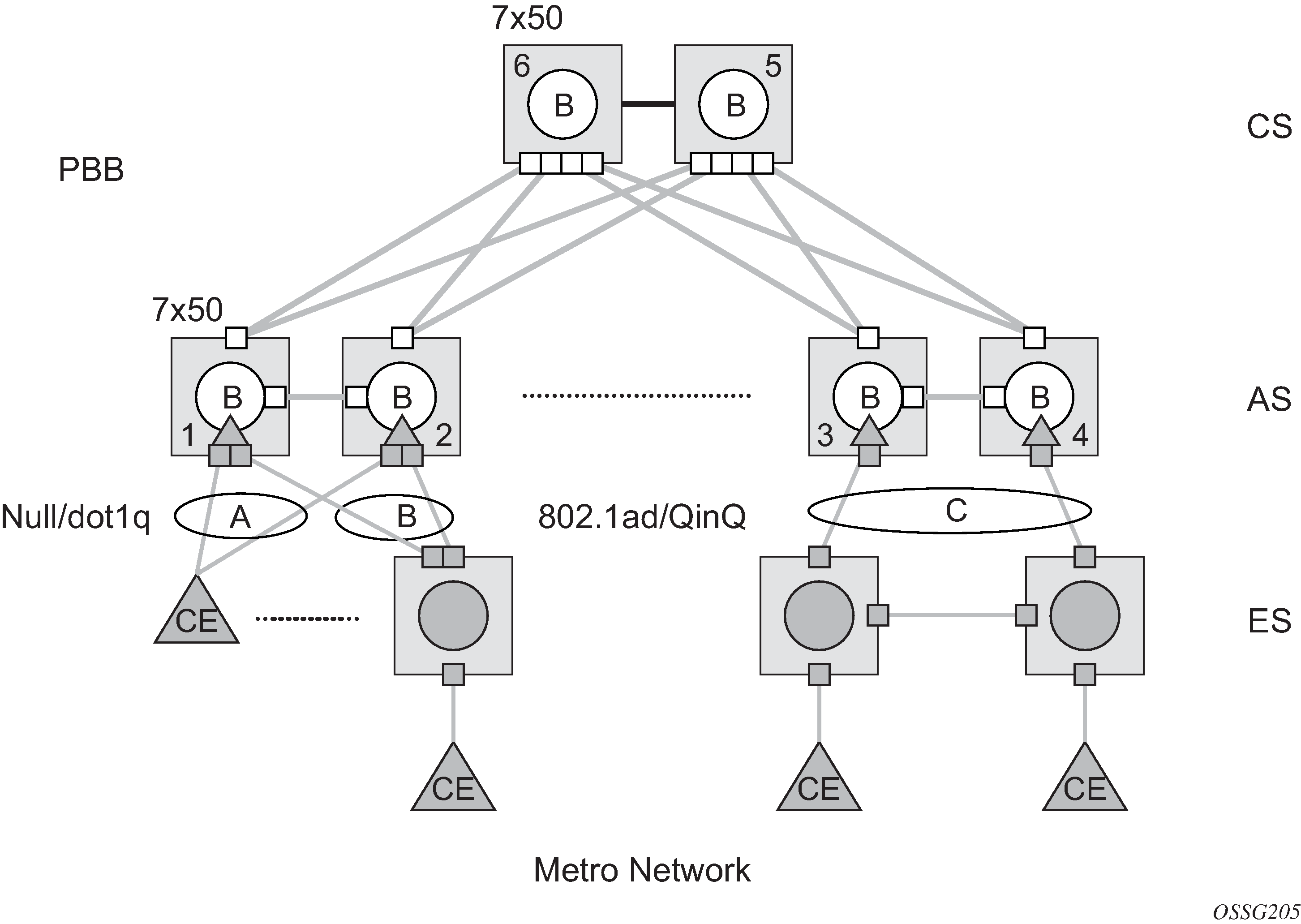
The following mechanisms are supported for the I-VPLS:
STP/RSTP can be used for all access types.
M-VPLS with MSTP can be used as is just for access type A. MSTP is required for access type B and C.
LAG and MC-LAG can be used for access type A and B.
Split-horizon-group does not require residential.
PBB I-VPLS inherits current STP configurations from the regular VPLS and M-VPLS.
MSTP for QinQ SAPs
MSTP runs in a M-VPLS context and can control SAPs from source VPLS instances. QinQ SAPs are supported. The outer tag is considered by MSTP as part of VLAN range control.
Provider MSTP
Provider MSTP is specified in IEEE-802.1ad-2005. It uses a provider bridge group address instead of a regular bridge group address used by STP, RSTP, and MSTP BPDUs. This allows for implicit separation of source and provider control planes.
The 802.1ad access network sends PBB PE P-MSTP BPDUs using the specified MAC address and also works over QinQ interfaces. P-MSTP mode is used in PBBN for core resiliency and loop avoidance.
Similar to regular MSTP, the STP mode (for example, PMSTP) is only supported in VPLS services where the m-VPLS flag is configured.
MSTP general principles
MSTP represents a modification of RSTP that allows the grouping of different VLANs into multiple MSTIs. To enable different devices to participate in MSTIs, they must be consistently configured. A collection of interconnected devices that have the same MST configuration (region-name, revision, and VLAN-to-instance assignment) comprises an MST region.
There is no limit to the number of regions in the network, but every region can support a maximum of 16 MSTIs. Instance 0 is a special instance for a region, known as the Internal Spanning Tree (IST) instance. All other instances are numbered from 1 to 4094. IST is the only spanning-tree instance that sends and receives BPDUs (typically, BPDUs are untagged). All other spanning-tree instance information is included in MSTP records (M-records), which are encapsulated within MSTP BPDUs. This means that a single BPDU carries information for multiple MSTIs, which reduces overhead of the protocol.
Any MSTI is local to an MSTP region and completely independent from an MSTI in other MST regions. Two redundantly connected MST regions use only a single path for all traffic flows (no load balancing between MST regions or between MST and SST region).
Traditional Layer 2 switches running MSTP protocol assign all VLANs to the IST instance per default. The operator may then ‟re-assign” individual VLANs to a specified MSTI by configuring per VLAN assignment. This means that an SR-series PE can be considered as a part of the same MST region only if the VLAN assignment to IST and MSTIs is identical to the one of Layer 2 switches in the access network.
MSTP in the SR-series platform
The SR-series platform uses a concept of M-VPLS to group different SAPs under a single STP instance. The VLAN range covering SAPs to be managed by a specified M-VPLS is declared under a specific M-VPLS SAP definition. MSTP mode-of-operation is only supported in an M-VPLS.
When running MSTP, by default, all VLANs are mapped to the CIST. At the VPLS level, VLANs can be assigned to specific MSTIs. When running RSTP, the operator must explicitly indicate, per SAP, which VLANs are managed by that SAP.
Enhancements to the spanning tree protocol
To interconnect PE devices across the backbone, service tunnels (SDPs) are used. These service tunnels are shared among multiple VPLS instances. The Nokia implementation of the STP incorporates some enhancements to make the operational characteristics of VPLS more effective. The implementation of STP on the router is modified to guarantee that service tunnels are not blocked in any circumstance without imposing artificial restrictions on the placement of the root bridge within the network. The modifications introduced are fully compliant with the 802.1D-2004 STP specification.
When running MSTP, spoke-SDPs cannot be configured. Also, ensure that all bridges connected by mesh SDPs are in the same region. If not, the mesh is prevented from becoming active (trap is generated).
To achieve this, all mesh SDPs are dynamically configured as either root ports or designated ports. The PE devices participating in each VPLS mesh determine (using the root path cost learned as part of the normal protocol exchange) which of the 7450 ESS, 7750 SR, or 7950 XRS devices is closest to the root of the network. This PE device is internally designated as the primary bridge for the VPLS mesh. As a result of this, all network ports on the primary bridges are assigned the designated port role and therefore remain in the forwarding state.
The second part of the solution ensures that the remaining PE devices participating in the STP instance see the SDP ports as a lower-cost path to the root than a path that is external to the mesh. Internal to the PE nodes participating in the mesh, the SDPs are treated as zero-cost paths toward the primary bridge. As a consequence, the path through the mesh is seen as lower cost than any alternative and the PE node designates the network port as the root port. This approach ensures that network ports always remain in forwarding state.
In combination, these two features ensure that network ports are never blocked and maintain interoperability with bridges external to the mesh that are running STP instances.
L2PT termination
L2PT is used to transparently transport protocol data units (PDUs) of Layer 2 protocols such as STP, CDP, VTP, PAGP, and UDLD. This allows running these protocols between customer CPEs without involving backbone infrastructure.
The 7450 ESS, 7750 SR, and 7950 XRS routers allow transparent tunneling of PDUs across the VPLS core. However, in some network designs, the VPLS PE is connected to CPEs through a legacy Layer 2 network, and it does not have direct connections. In such environments, termination of tunnels through such infrastructure is required.
L2PT tunnels PDUs by overwriting MAC destination addresses at the ingress of the tunnel to a proprietary MAC address such as 01-00-0c-cd-cd-d0. At the egress of the tunnel, this MAC address is then overwritten back to the MAC address of the respective Layer 2 protocol.
The 7450 ESS, 7750 SR, and 7950 XRS routers support L2PT termination for STP BPDUs. More specifically:
At ingress of every SAP/spoke-SDP that is configured as L2PT termination, all PDUs with a MAC destination address of 01-00-0c-cd-cd-d0 are intercepted and their MAC destination address is overwritten to the MAC destination address used for the corresponding protocol (PVST, STP, RSTP). The type of the STP protocol can be derived from LLC and SNAP encapsulation.
In the egress direction, all STP PDUs received on all VPLS ports are intercepted and L2PT encapsulation is performed for SAP/spoke-SDPs configured as L2PT termination points. Because of implementation reasons, PDU interception and redirection to CPM can be performed only at ingress. Therefore, to comply with the above requirement, as soon as at least one port of a specified VPLS service is configured as L2PT termination port, redirection of PDUs to CPM is set on all other ports (SAPs, spoke-SDPs, and mesh SDPs) of the VPLS service.
L2PT termination can be enabled only if STP is disabled in a context of the specified VPLS service.
BPDU translation
VPLS networks are typically used to interconnect different customer sites using different access technologies such as Ethernet and bridged-encapsulated ATM PVCs. Typically, different Layer 2 devices can support different types of STP, even if they are from the same vendor. In some cases, it is necessary to provide BPDU translation to provide an interoperable e2e solution.
To address these network designs, BPDU format translation is supported on 7450 ESS, 7750 SR, and 7950 XRS devices. If enabled on a specified SAP or spoke-SDP, the system intercepts all BPDUs destined for that interface and perform required format translation such as STP-to-PVST or the other way around.
Similarly, BPDU interception and redirection to the CPM is performed only at ingress, meaning that as soon as at least one port within a specified VPLS service has BPDU translation enabled, all BPDUs received on any of the VPLS ports are redirected to the CPM.
BPDU translation requires all encapsulation actions that the data path would perform for a specified outgoing port (such as adding VLAN tags depending on the outer SAP and the SDP encapsulation type) and adding or removing all the required VLAN information in a BPDU payload.
This feature can be enabled on a SAP only if STP is disabled in the context of the specified VPLS service.
L2PT and BPDU translation
Cisco Discovery Protocol (CDP), Digital Trunking Protocol (DTP), Port Aggregation Protocol (PAGP), Uni-directional Link Detection (UDLD), and Virtual Trunk Protocol (VTP) are supported. These protocols automatically pass the other protocols tunneled by L2PT toward the CPM and all carry the same specific Cisco MAC.
The existing L2PT limitations apply.
The protocols apply only to VPLS.
The protocols and running STP on the same VPLS as soon as one SAP has L2PT enabled are mutually exclusive.
Forwarding occurs on the CPM.
VPLS redundancy
The VPLS standard (RFC 4762, Virtual Private LAN Services Using LDP Signaling) includes provisions for hierarchical VPLS, using point-to-point spoke-SDPs. Two applications have been identified for spoke-SDPs:
to connect Multi-Tenant Units (MTUs) to PEs in a metro area network
to interconnect the VPLS nodes of two metro networks
In both applications, the spoke-SDPs serve to improve the scalability of VPLS. While node redundancy is implicit in non-hierarchical VPLS services (using a full mesh of SDPs between PEs), node redundancy for spoke-SDPs needs to be provided separately.
Nokia routers have implemented special features for improving the resilience of hierarchical VPLS instances, in both MTU and inter-metro applications.
Spoke SDP redundancy for metro interconnection
When two or more meshed VPLS instances are interconnected by redundant spoke-SDPs (as shown in HVPLS with spoke redundancy), a loop in the topology results. To remove such a loop from the topology, STP can be run over the SDPs (links) that form the loop, such that one of the SDPs is blocked. As running STP in each and every VPLS in this topology is not efficient, the node includes functionality that can associate a number of VPLSs to a single STP instance running over the redundant SDPs. Therefore, node redundancy is achieved by running STP in one VPLS and applying the conclusions of this STP to the other VPLS services. The VPLS instance running STP is referred to as the ‟management VPLS” or M-VPLS.
If the active node fails, STP on the management VPLS in the standby node changes the link states from disabled to active. The standby node then broadcasts a MAC flush LDP control message in each of the protected VPLS instances, so that the address of the newly active node can be relearned by all PEs in the VPLS.
It is possible to configure two management VPLS services, where both VPLS services have different active spokes (this is achieved by changing the path cost in STP). By associating different user VPLSs with the two management VPLS services, load balancing across the spokes can be achieved.
Spoke SDP based redundant access
This feature provides the ability to have a node deployed as MTUs (Multi-Tenant Units) to be multihomed for VPLS to multiple routers deployed as PEs without requiring the use of M-VPLS.
In the configuration example shown in HVPLS with spoke redundancy, the MTUs have spoke-SDPs to two PE devices. One is designated as the primary and one as the secondary spoke-SDP. This is based on a precedence value associated with each spoke.
The secondary spoke is in a blocking state (both on receive and transmit) as long as the primary spoke is available. When the primary spoke becomes unavailable (because of the link failure, PEs failure, and so on), the MTUs immediately switch traffic to the backup spoke and start receiving traffic from the standby spoke. Optional revertive operation (with configurable switch-back delay) is supported. Forced manual switchover is also supported.
To speed up the convergence time during a switchover, MAC flush is configured. The MTUs generate a MAC flush message over the newly unblocked spoke when a spoke change occurs. As a result, the PEs receiving the MAC flush, flush all MACs associated with the impacted VPLS service instance and forward the MAC flush to the other PEs in the VPLS network if propagate-mac-flush is enabled.
Inter-domain VPLS resiliency using multi-chassis endpoints
Inter-domain VPLS refers to a VPLS deployment where sites may be located in different domains. An example of inter-domain deployment can be where different metro domains are interconnected over a Wide Area Network (Metro1-WAN-Metro2) or where sites are located in different autonomous systems (AS1-ASBRs-AS2).
Multi-chassis endpoint (MC-EP) provides an alternate solution that does not require RSTP at the gateway VPLS PEs while still using pseudowires to interconnect the VPLS instances located in the two domains. It is supported in both VPLS and PBB-VPLS on the B-VPLS side.
MC-EP expands the single chassis endpoint based on active-standby pseudowires for VPLS, shown in HVPLS resiliency based on AS pseudowires.

The active-standby pseudowire solution is appropriate for the scenario when only one VPLS PE (MTUs) needs to be dual-homed to two core PEs (PE1 and PE2). When multiple VPLS domains need to be interconnected, the above solution provides a single point of failure at the MTU-s. The example shown in Multi-chassis pseudowire endpoint for VPLS can be used.
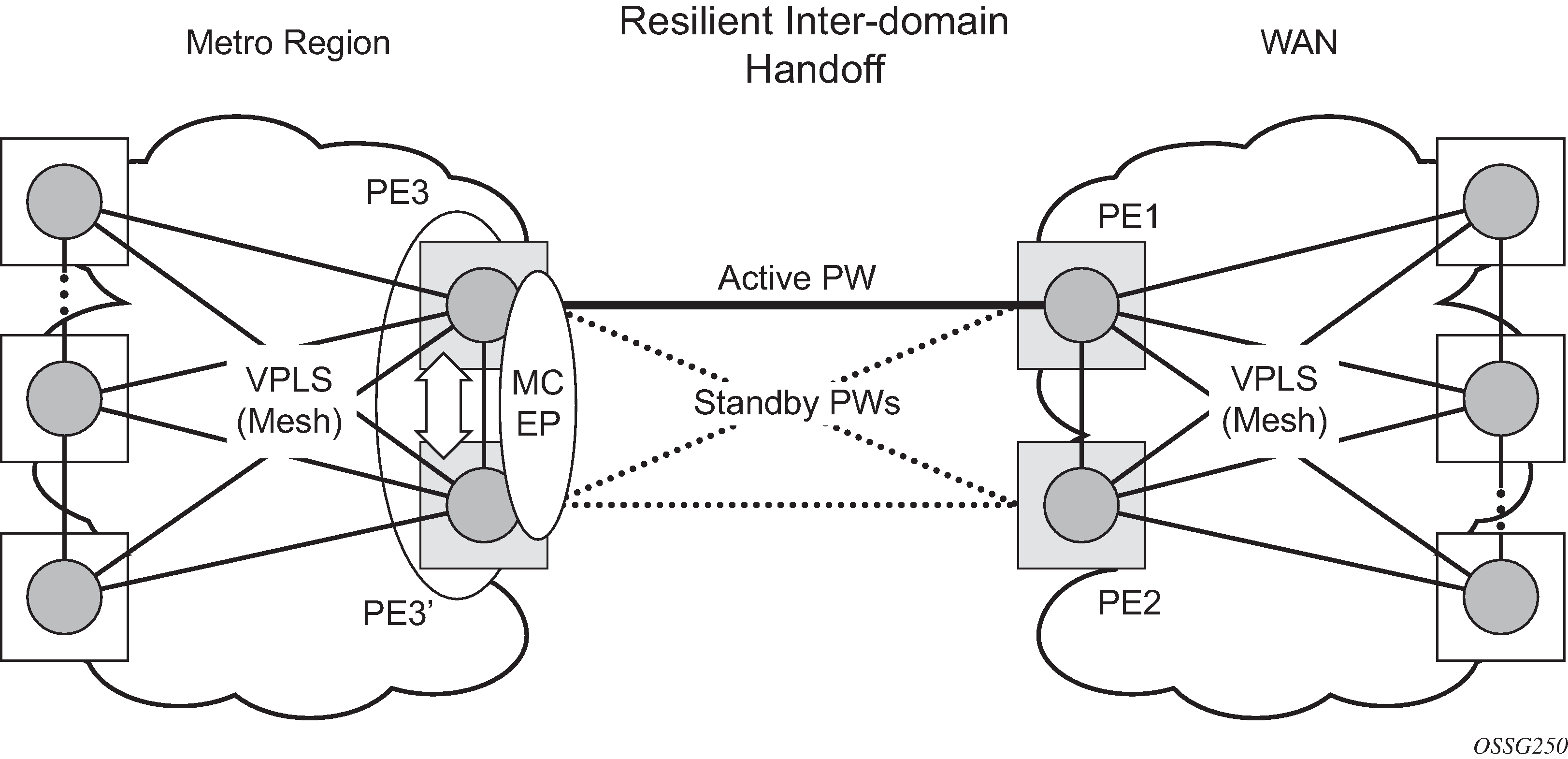
The two gateway pairs, PE3-PE3’ and PE1-PE2, are interconnected using a full mesh of four pseudowires out of which only one pseudowire is active at any time.
The concept of pseudowire endpoint for VPLS provides multi-chassis resiliency controlled by the MC-EP pair, PE3-PE3’ in this example. This scenario, referred to as multi-chassis pseudowire endpoint for VPLS, provides a way to group pseudowires distributed between PE3 and PE3 chassis in a virtual endpoint that can be mapped to a VPLS instance.
The MC-EP inter-chassis protocol is used to ensure configuration and status synchronization of the pseudowires that belong to the same MC-EP group on PE3 and PE3. Based on the information received from the peer shelf and the local configuration, the master shelf decides on which pseudowire becomes active.
The MC-EP solution is built around the following components:
Multi-chassis protocol used to perform the following functions:
Selection of master chassis.
Synchronization of the pseudowire configuration and status.
Fast detection of peer failure or communication loss between MC-EP peers using either centralized BFD, if configured, or its own keep-alive mechanism.
-
T-LDP signaling of pseudowire status informs the remote PEs about the choices made by the MC-EP pair.
Pseudowire data plane is represented by the four pseudowires inter-connecting the gateway PEs.
Only one of the pseudowires is activated based on the primary/secondary, preference configuration, and pseudowire status. In case of a tie, the pseudowire located on the master chassis is chosen.
The rest of the pseudowires are blocked locally on the MC-EP pair and on the remote PEs as long as they implement the pseudowire active/standby status.
Fast detection of peer failure using BFD
Although the MC-EP protocol has its own keep-alive mechanisms, sharing a common mechanism for failure detection with other protocols (for example, BGP, RSVP-TE) scales better. MC-EP can be configured to use the centralized BFD mechanism.
Similar to other protocols, MC-EP registers with BFD if the bfd-enable command is active under the config>redundancy>multi-chassis>peer>mc-ep context. As soon as the MC-EP application is activated using no shutdown, it tries to open a new BFD session or register automatically with an existing one. The source-ip configuration under redundancy multi-chassis peer-ip is used to determine the local interface while the peer-ip is used as the destination IP for the BFD session. After MC-EP registers with an active BFD session, it uses it for fast detection of MC-EP peer failure. If BFD registration or BFD initialization fails, the MC-EP keeps using its own keep-alive mechanism and it sends a trap to the NMS signaling the failure to register with/open a BFD session.
To minimize operational mistakes and wrong peer interpretation for the loss of BFD session, the following additional rules are enforced when the MC-EP is registering with a BFD session:
Only the centralized BFD sessions using system or loopback IP interfaces (source-ip parameter) are accepted in order for MC-EP to minimize the false indication of peer loss.
If the BFD session associated with MC-EP protocol is using a system/loopback interface, the following actions are not allowed under the interface: IP address change, ‟shutdown”, ‟no bfd” commands. If one of these actions is required under the interface, the operator needs to disable BFD using one the following procedures:
- The no bfd-enable command in the
config>redundancy>multi-chassis>peer>mc-ep
context. Note: This is the recommended procedure.
The shutdown command in the config>redundancy>multi-chassis>peer>mc-ep or from under config>redundancy>multi-chassis>peer contexts.
- The no bfd-enable command in the
config>redundancy>multi-chassis>peer>mc-ep
context.
MC-EP keep-alives are still exchanged for the following reasons:
As a backup; if the BFD session does not come up or is disabled, the MC-EP protocol uses its own keep-alives for failure detection.
To ensure the database is cleared if the remote MC-EP peer is shut down or misconfigured (each x seconds; one second suggested as default).
If MC-EP de-registers with BFD using the no bfd-enable command, the following processing steps occur:
-
The local peer indicates to the MC-EP peer that the local BFD is being disabled using the MC-EP peer-config-TLV fields ([BFD local: BFD remote]). This is done to avoid the wrong interpretation of the BFD session loss.
-
The remote peer acknowledges reception indicating through the same peer-config-TLV fields that it is de-registering with the BFD session.
-
Both MC-EP peers de-register and use only keep-alives for failure detection.
Traps are sent when the status of the monitoring of the MC-EP session through BFD changes in the following instances:
When red/mc/peer is no shutdown and BFD is not enabled, a notification is sent indicating BFD is not monitoring the MC-EP peering session.
When BFD changes to open, a notification is sent indicating BFD is monitoring the MC-EP peering session.
When BFD changes to down/close, a notification is sent indicating BFD is not monitoring the MC-EP peering session.
MC-EP passive mode
The MC-EP mechanisms are built to minimize the possibility of loops. It is possible that human error could create loops through the VPLS service. One way to prevent loops is to enable the MAC move feature in the gateway PEs (PE3, PE3', PE1, and PE2).
An MC-EP passive mode can also be used on the second PE pair, PE1 and PE2, as a second layer of protection to prevent any loops from occurring if the operator introduces operational errors on the MC-EP PE3, PE3 pair. An example is shown in MC-EP in passive mode.
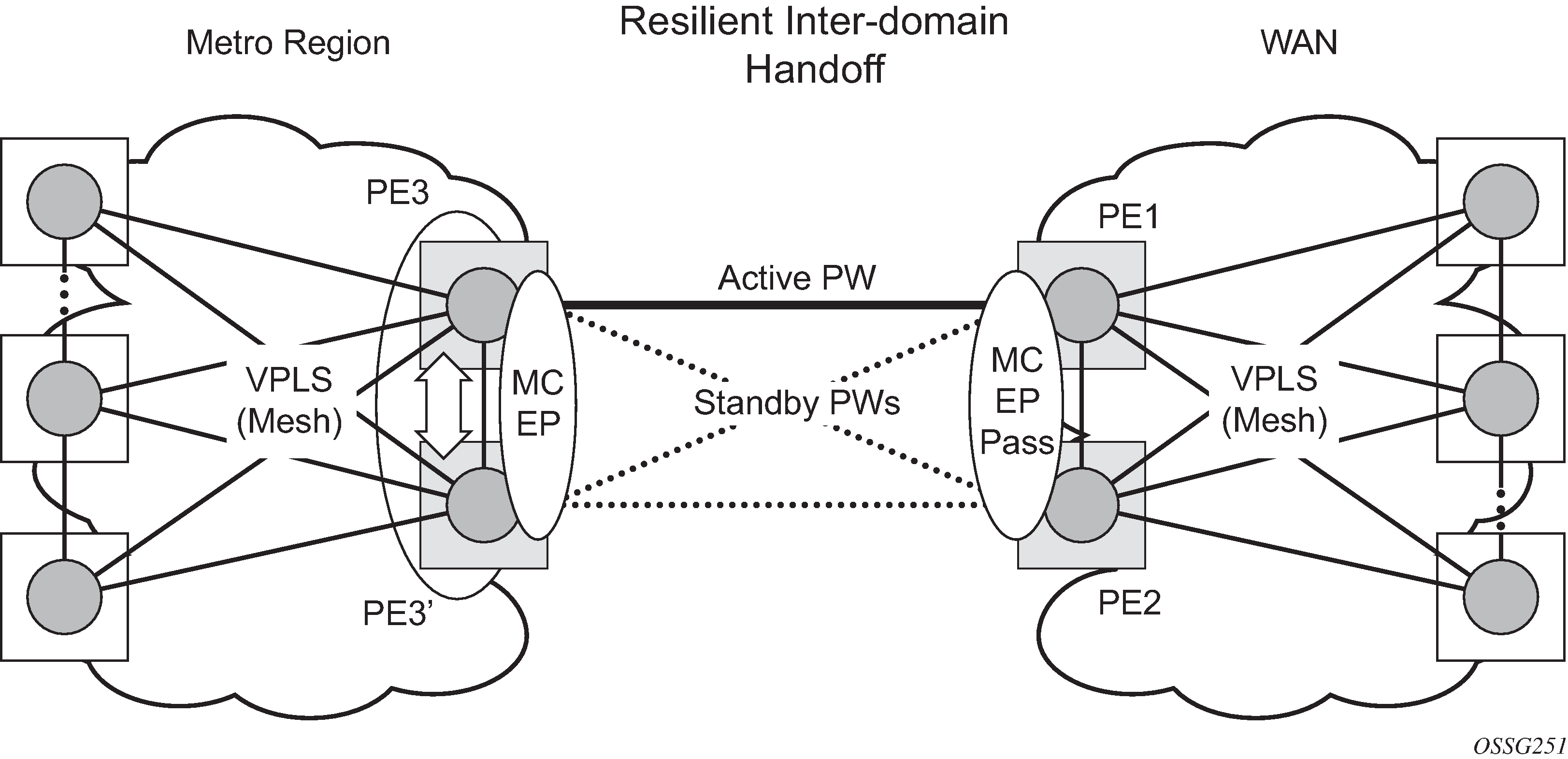
When in passive mode, the MC-EP peers stay dormant as long as one active pseudowire is signaled from the remote end. If more than one pseudowire belonging to the passive MC-EP becomes active, the PE1 and PE2 pair applies the MC-EP selection algorithm to select the best choice and blocks all others. No signaling is sent to the remote pair to avoid flip-flop behavior. A trap is generated each time MC-EP in passive mode activates. Every occurrence of this kind of trap should be analyzed by the operator as it is an indication of possible misconfiguration on the remote (active) MC-EP peering.
For the MC-EP passive mode to work, the pseudowire status signaling for active/standby pseudowires should be enabled. This requires the following CLI configurations:
For the remote MC-EP PE3, PE3 pair:
config>service>vpls>endpoint# no suppress-standby-signaling
When MC-EP passive mode is enabled on the PE1 and PE2 pair, the following command is always enabled internally, regardless of the actual configuration:
config>service>vpls>endpoint no ignore-standby-signaling
Support for single chassis endpoint mechanisms
In cases of SC-EP, there is a consistency check to ensure that the configuration of the member pseudowires is the same. For example, mac-pining, mac-limit, and ignore standby signaling must be the same. In the MC-EP case, there is no consistency check between the member endpoints located on different chassis. The operator must carefully verify the configuration of the two endpoints to ensure consistency.
The following rules apply for suppress-standby-signaling and ignore-standby parameters:
Regular MC-EP mode (non-passive) follows the suppress-standby-signaling and ignore-standby settings from the related endpoint configuration.
For MC-EP configured in passive mode, the following settings are used, regardless of previous configuration: suppress-standby-sig and no ignore-standby-sig. It is expected that when passive mode is used at one side, the regular MC-EP side activates signaling with no suppress-stdby-sig.
When passive mode is configured in just one of the nodes in the MC-EP peering, the other node is forced to change to passive mode. A trap is sent to the operator to signal the wrong configuration.
This section also describes how the main mechanisms used for single chassis endpoint are adapted for the MC-EP solution.
MAC flush support in MC-EP
In an MC-EP scenario, failure of a pseudowire or gateway PE determines activation of one of the next best pseudowires in the MC-EP group. This section describes the MAC flush procedures that can be applied to ensure blackhole avoidance.
MAC flush in the MC-EP solution shows a pair of PE gateways (PE3 and PE3) running MC-EP toward PE1 and PE2 where F1 and F2 are used to indicate the possible direction of the MAC flush, signaled using T-LDP MAC withdraw message. PE1 and PE2 can only use regular VPLS pseudowires and do not have to use an MC-EP or a regular pseudowire endpoint.
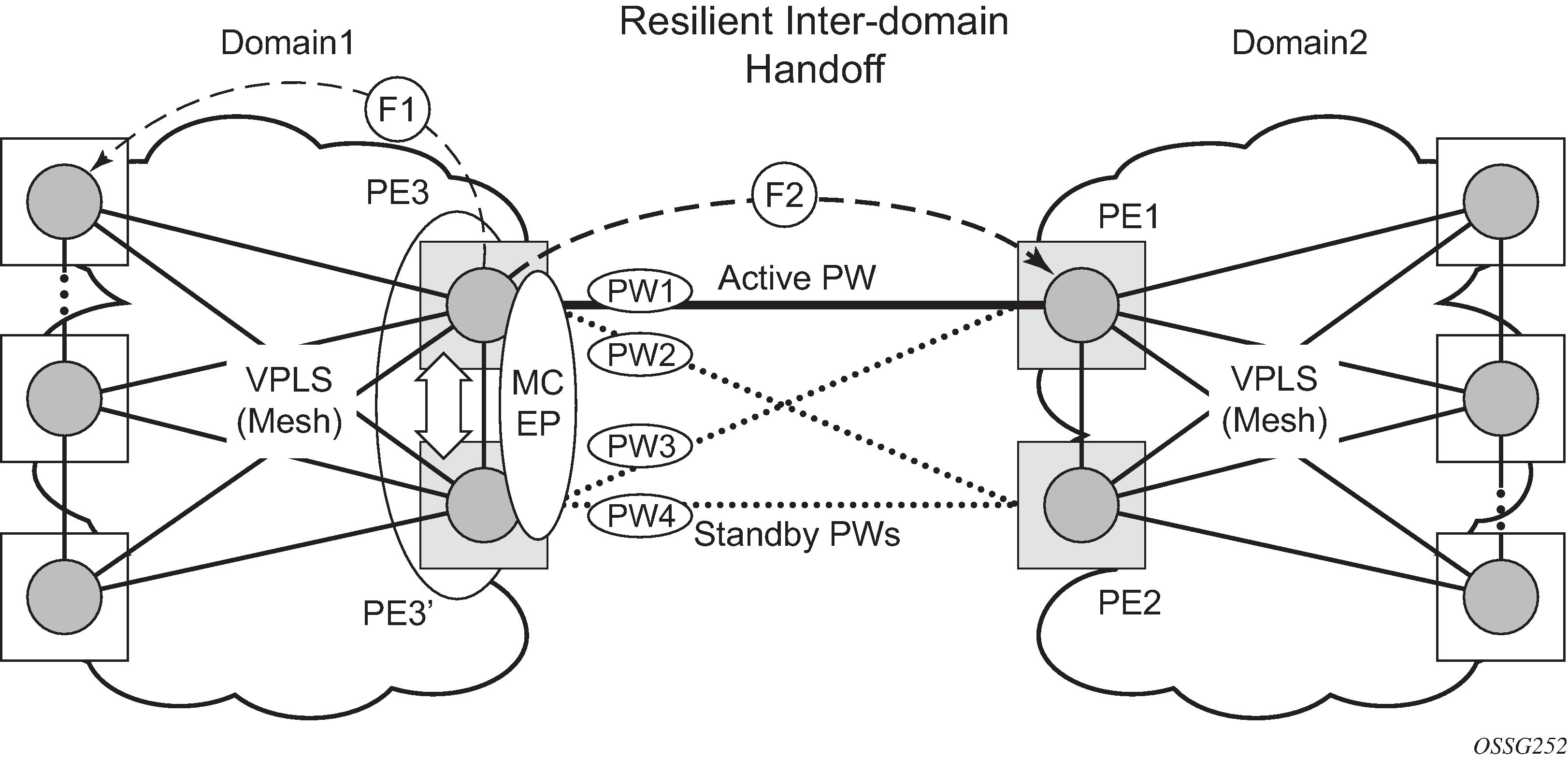
Regular MAC flush behavior applies for the LDP MAC withdraw sent over the T-LDP sessions associated with the active pseudowire in the MC-EP; for example, PE3 to PE1. That includes any Topology Change Notification (TCN) events or failures associated with SAPs or pseudowires not associated with the MC-EP.
The following MAC flush behaviors apply to changes in the MC-EP pseudowire selection:
If the local PW2 becomes active on PE3:
On PE3, the MACs mapped to PW1 are moved to PW2.
A T-LDP flush-all-but-mine message is sent toward PE2 in the F2 direction and is propagated by PE2 in the local VPLS mesh.
No MAC flush is sent in the F1 direction from PE3.
If one of the pseudowires on the pair PE3 becomes active; for example, PW4:
On PE3, the MACs mapped to PW1 are flushed, the same as for a regular endpoint.
PE3 must be configured with send-flush-on-failure to send a T-LDP flush-all-from-me message toward VPLS mesh in the F1 direction.
PE3 sends a T-LDP flush-all-but-mine message toward PE2 in the F2 direction, which is propagated by PE2 in the local VPLS mesh. When MC-EP is in passive mode and the first spoke becomes active, a no MAC flush-all-but-mine message is generated.
Block-on-mesh-failure support in MC-EP scenario
The following rules describe how the block-on-mesh-failure operates with the MC-EP solution (see MAC flush in the MC-EP solution):
If PE3 does not have any forwarding path toward Domain1 mesh, it should block both PW1 and PW2 and inform PE3 so one of its pseudowires can be activated.
To allow the use of block-on-mesh-failure for MC-EP, a block-on-mesh-failure parameter can be specified in the config>service>vpls>endpoint context with the following rules:
The default is no block-on-mesh-failure to allow for easy migration.
For a spoke-SDP to be added under an endpoint, the setting for its block-on-mesh-failure parameter must be in synchronization with the endpoint parameter.
After the spoke-SDP is added to an endpoint, the configuration of its block-on-mesh-failure parameter is disabled. A change in endpoint configuration for the block-on-mesh-failure parameter is propagated to the individual spoke-SDP configuration.
When a spoke-SDP is removed from the endpoint group, it inherits the last configuration from the endpoint parameter.
Adding an MC-EP under the related endpoint configuration does not affect the above behavior.
Before Release 7.0, the block-on-mesh-failure command could not be enabled under config>service>vpls>endpoint context. For a spoke-SDP to be added to an (single-chassis) endpoint, its block-on-mesh-failure had to be disabled (config>service>vpls>spoke-sdp>no block-on-mesh-failure). Then, the configuration of block-on-mesh-failure under a spoke-SDP is blocked.
If block-on-mesh-failure is enabled on PE1 and PE2, these PEs signal pseudowire standby status toward the MC-EP PE pair. PE3 and PE3 should consider the pseudowire status signaling from remote PE1 and PE2 when making the selection of the active pseudowire.
Support for force spoke SDP in MC-EP
In a regular (single chassis) endpoint scenario, the following command can be used to force a specific SDP binding (pseudowire) to become active:
tools perform service id service-id endpoint endpoint-name force
In the MC-EP case, this command has a similar effect when there is a single forced SDP binding in an MC-EP. The forced SDP binding (pseudowire) is selected as active.
However, when the command is run at the same time as both MC-EP PEs, when the endpoints belong to the same MC-EP, the regular MC-EP selection algorithm (for example, the operational status ⇒ precedence value) is applied to determine the winner.
Revertive behavior for primary pseudowires in an MC-EP
For a single-chassis endpoint, a revert-time command is provided under the VPLS endpoint.
In a regular endpoint, the revert-time setting affects just the pseudowire defined as primary (precedence 0). For a failure of the primary pseudowire followed by restoration, the revert-timer is started. After it expires, the primary pseudowire takes the active role in the endpoint. This behavior does not apply for the case when both pseudowires are defined as secondary; that is, if the active secondary pseudowire fails and is restored, it stays in standby until a configuration change or a force command occurs.
In the MC-EP case, the revertive behavior is supported for pseudowire defined as primary (precedence 0). The following rules apply:
The revert-time setting under each individual endpoint control the behavior of the local primary pseudowire if one is configured under the local endpoint.
The secondary pseudowires behave as in the regular endpoint case.
Using B-VPLS for increased scalability and reduced convergence times
The PBB-VPLS solution can be used to improve scalability of the solution and to reduce convergence time. If PBB-VPLS is deployed starting at the edge PEs, the gateway PEs contain only B-VPLS instances. The MC-EP procedures described for regular VPLS apply.
PBB-VPLS can also be enabled just on the gateway MC-EP PEs, as shown in MC-EP with B-VPLS.

Multiple I-VPLS instances may be used to represent in the gateway PEs the customer VPLS instances using the PBB-VPLS M:1 model described in the PBB section. A backbone VPLS (B-VPLS) is used in this example to administer the resiliency for all customer VPLS instances at the domain borders. Just one MC-EP is required to be configured in the B-VPLS to address hundreds or even thousands of customer VPLS instances. If load balancing is required, multiple B-VPLS instances may be used to ensure even distribution of the customers across all the pseudowires interconnecting the two domains. In this example, four B-VPLSs are able to load share the customers across all four possible pseudowire paths.
The use of MC-EP with B-VPLS is strictly limited to cases where VPLS mesh exists on both sides of a B-VPLS. For example, active/standby pseudowires resiliency in the I-VPLS context where PE3 and PE3’ are PE-rs cannot be used because there is no way to synchronize the active/standby selection between the two domains.
For a similar reason, MC-LAG resiliency in the I-VPLS context on the gateway PEs participating in the MC-EP (PE3 and PE3’) should not be used.
For the PBB topology in MC-EP with B-VPLS, block-on-mesh-failure in the I-VPLS domain does not have any effect on the B-VPLS MC-EP side. That is because mesh failure in one I-VPLS should not affect other I-VPLSs sharing the same B-VPLS.
MAC flush additions for PBB VPLS
The scenario shown in MC-EP with B-VPLS failure scenario is used to define the blackholing problem in PBB-VPLS using MC-EP.
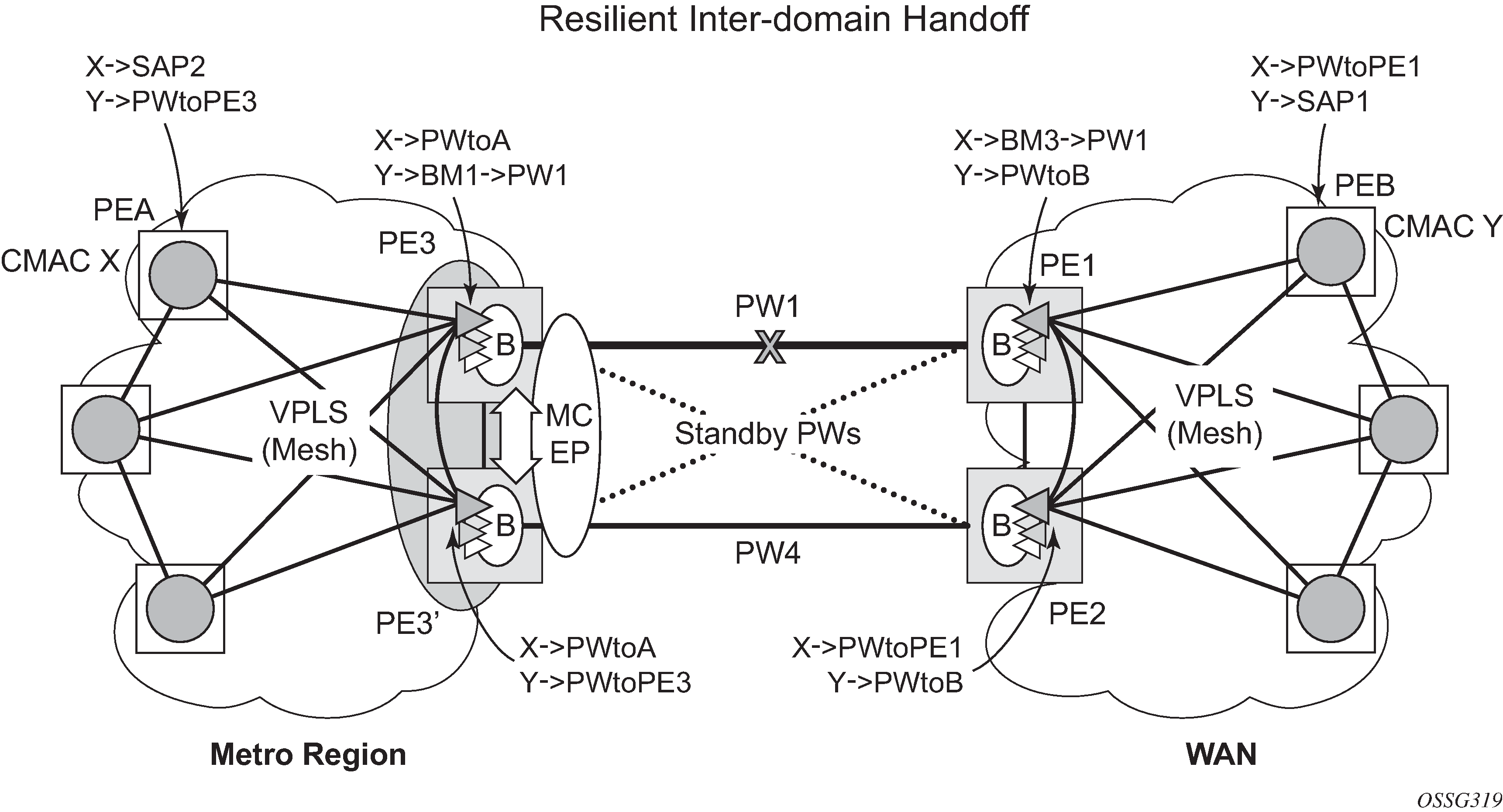
In the topology shown in MC-EP with B-VPLS failure scenario, PEA and PEB are regular VPLS PEs participating in the VPLS mesh deployed in the metro and WAN region, respectively. As the traffic flows between CEs with C-MAC X and C-MAC Y, the FDB entries in PEA, PE3, PE1 and PEB are installed. An LDP flush-all-but-mine message is sent from PE3 to PE2 to clear the B-VPLS FDBs. The traffic between C-MAC X and C-MAC Y is blackholed as long as the entries from the VPLS and I-VPLS FDBs along the path are not removed. This may take as long as 300 seconds, the usual aging timer used for MAC entries in a VPLS FDB.
A MAC flush is required in the I-VPLS space from PBB PEs to PEA and PEB to avoid blackholing in the regular VPLS space.
In the case of a regular VPLS, the following procedure is used:
-
PE3 sends a flush-all-from-me message toward its local blue I-VPLS mesh to PE3 and PEA when its MC-EP becomes disabled.
-
PE3 sends a flush-all-but-mine message on the active PW4 to PE2, which is then propagated by PE2 (propagate-mac-flush must be on) to PEB in the WAN I-VPLS mesh.
For consistency, a similar procedure is used for the B-VPLS case as shown in MC-EP with B-VPLS MAC flush solution.
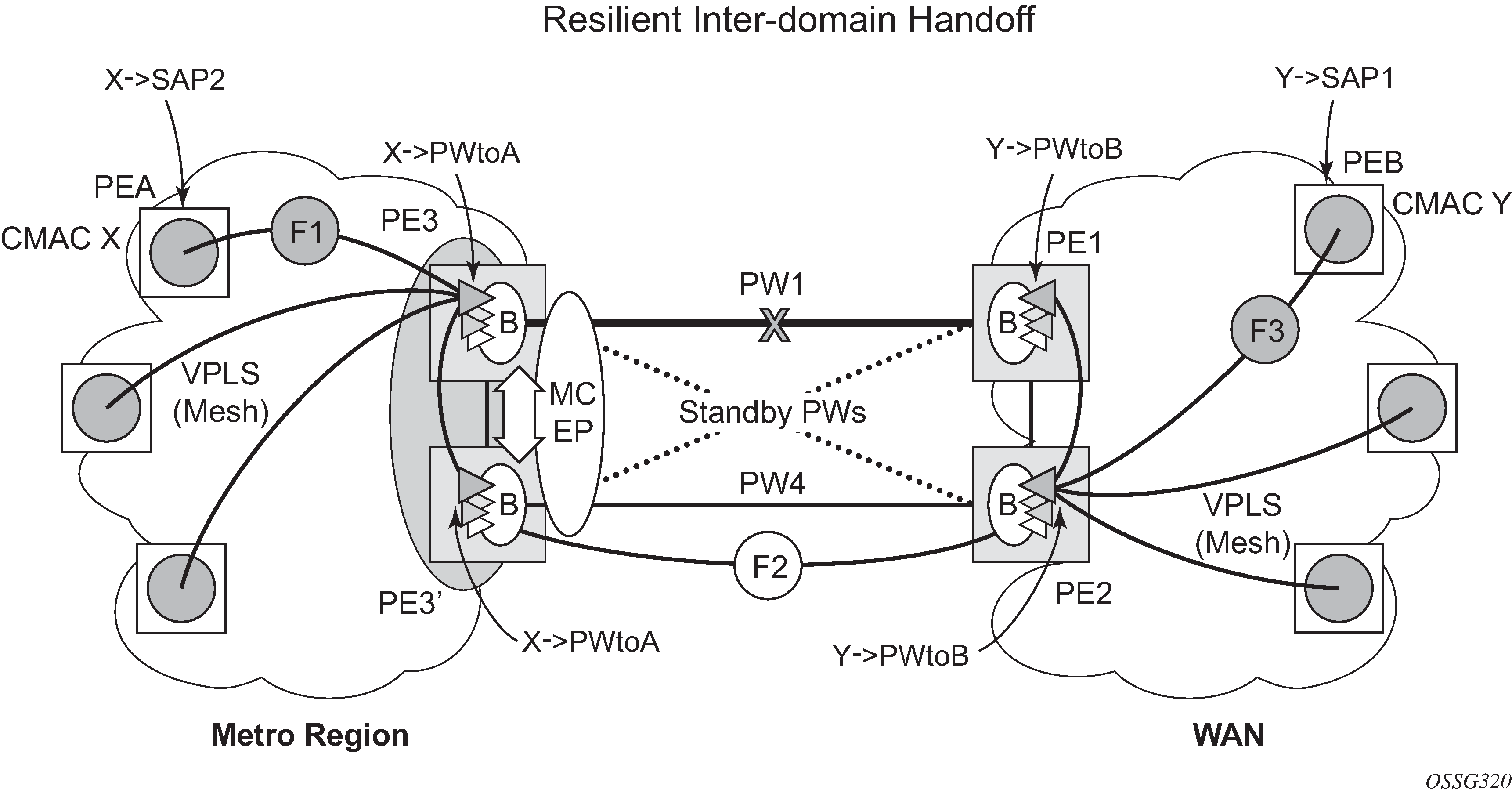
In this example, the MC-EP activates B-VPLS PW4 because of either a link/node failure or because of an MC-EP selection re-run that affected the previously active PW1. As a result, the endpoint on PE3 containing PW1 goes down.
The following steps apply:
-
PE3 sends, in the local I-VPLS context, an LDP flush-all-from-me message (marked with F1) to PEA and to the other regular VPLS PEs, including PE3. The following command enables this behavior on a per I-VPLS basis: config>service>vpls ivpls>send-flush-on-bvpls-failure.
As a result, PEA, PE3, and the other local VPLS PEs in the metro clear the VPLS FDB entries associated with PW to PE3.
-
PE3 clears the entries associated with PW1 and sends, in the B-VPLS context, an LDP flush-all-but-mine message (marked with F2) toward PE2 on the active PW4.
As a result, PE2 clears the B-VPLS FDB entries not associated with PW4.
-
PE2 propagates the MAC flush-all-but-mine (marked with F3) from B-VPLS in the related I-VPLS contexts toward all participating VPLS PEs; for example, in the blue I-VPLS to PEB, PE1. It also clears all the C-MAC entries associated with I-VPLS pseudowires.
The following command enables this behavior on a per I-VPLS basis:
config>service>vpls ivpls>propagate-mac-flush-from-bvpls
As a result, PEB, PE1, and the other local VPLS PEs in the WAN clear the VPLS FDB entries associated with PW to PE2.
Note: This command does not control the propagation in the related I-VPLS of the B-VPLS LDP MAC flush containing a PBB TLV (B-MAC and ISID list).
Similar to regular VPLS, LDP signaling of the MAC flush follows the active topology; for example, no MAC flush is generated on standby pseudowires.
Other failure scenarios are addressed using the same or a subset of the above steps:
If the pseudowire (PW2) in the same endpoint with PW1 becomes active instead of PW4, there is no MAC flush of F1 type.
If the pseudowire (PW3) in the same endpoint becomes active instead of PW4, the same procedure applies.
For an SC/MC endpoint configured in a B-VPLS, failure/deactivation of the active pseudowire member always generates a local MAC flush of all the B-MAC associated with the pseudowire. It never generates a MAC move to the newly active pseudowire even if the endpoint stays up. That is because in SC-EP/MC-EP topology, the remote PE may be the terminating PBB PE and may not be able to reach the B-MAC of the other remote PE. Therefore, connectivity between them exists only over the regular VPLS mesh.
For the same reasons, Nokia recommends that static B-MAC not be used on SC/MC endpoints.
VPLS access redundancy
A second application of hierarchical VPLS is using MTUs that are not MPLS-enabled that must have Ethernet links to the closest PE node. To protect against failure of the PE node, an MTU can be dual-homed and have two SAPs on two PE nodes.
There are several mechanisms that can be used to resolve a loop in an access circuit; however, from an operations perspective, they can be subdivided into two groups:
STP-based access, with or without M-VPLS.
Non-STP based access using mechanisms such as MC-LAG, MC-APS, MC-Ring.
STP-based redundant access to VPLS

In the configuration shown in Dual-homed MTUs in two-tier hierarchy H-VPLS, STP is activated on the MTU and two PEs to resolve a potential loop. STP only needs to run in a single VPLS instance, and the results of the STP calculations are applied to all VPLSs on the link.
In this configuration, the scope of the STP domain is limited to MTU and PEs, while any topology change needs to be propagated in the whole VPLS domain including mesh SDPs. This is done by using so-called MAC-flush messages defined by RFC 4762. In the case of STP as an loop resolution mechanism, every TCN received in the context of an STP instance is translated into an LDP-MAC address withdrawal message (also referred to as a MAC-flush message) requesting to clear all FDB entries except the ones learned from the originating PE. Such messages are sent to all PE peers connected through SDPs (mesh and spoke) in the context of VPLS services, which are managed by the specified STP instance.
Redundant access to VPLS without STP
The Nokia implementation also includes alternative methods for providing a redundant access to Layer 2 services, such as MC-LAG, MC-APS, or MC-Ring. Also in this case, the topology change event needs to be propagated into the VPLS topology to provide fast convergence. The topology change propagation and its corresponding MAC flush processing in a VPLS service without STP is described in Dual homing to a VPLS service.
Object grouping and state monitoring
This feature introduces a generic operational group object that associates different service endpoints (pseudowires, SAPs, IP interfaces) located in the same or in different service instances.
The operational group status is derived from the status of the individual components using specific rules specific to the application using the feature. A number of other service entities, the monitoring objects, can be configured to monitor the operational group status and to perform specific actions as a result of status transitions. For example, if the operational group goes down, the monitoring objects are brought down.
VPLS applicability — block on VPLS a failure
This feature is used in VPLS to enhance the existing BGP MH solution by providing a block-on-group failure function similar to the block-on-mesh failure feature implemented for LDP VPLS. On the PE selected as the Designated Forwarder (DF), if the rest of the VPLS endpoints fail (pseudowire spokes/pseudowire mesh and, or SAPs), there is no path forward for the frames sent to the MH site selected as DF. The status of the VPLS endpoints, other than the MH site, is reflected by bringing down/up the objects associated with the MH site.
Support for the feature is provided initially in VPLS and B-VPLS instance types for LDP VPLS, with or without BGP-AD and for BGP VPLS. The following objects may be placed as components of an operational group: BGP VPLS pseudowires, SAPs, spoke-pseudowire, BGP-AD pseudowires. The following objects are supported as monitoring objects: BGP MH site, individual SAP, spoke-pseudowire.
The following rules apply:
An object can only belong to one group at a time.
An object that is part of a group cannot monitor the status of any group.
An object that monitors the status of a group cannot be part of any group.
An operational group may contain any combination of member types: SAP, spoke-pseudowire, BGP-AD or BGP VPLS pseudowires.
An operational group may contain members from different VPLS service instances.
Objects from different services may monitor the operational group.
The operational group feature may coexist in parallel with the block-on-mesh failure feature as long as they are running in different VPLS instances.
There are two steps involved in enabling the block-on-mesh failure feature in a VPLS scenario:
Identify a set of objects whose forwarding state should be considered as a whole group, then group them under an operational group using the oper-group CLI command.
Associate other existing objects (clients) with the oper-group command using the monitor-group CLI command; its forwarding state is derived from the related operational group state.
The status of the operational group (oper-group) is dictated by the status of one or more members according to the following rule:
The oper-group goes down if all the objects in the oper-group go down; the oper-group comes up if at least one of the components is up.
An object in the oper-group is considered down if it is not forwarding traffic in at least one direction. That could be because the operational state is down or the direction is blocked through some resiliency mechanisms.
If an oper-group is configured but no members are specified yet, its status is considered up. As soon as the first object is configured, the status of the oper-group is dictated by the status of the provisioned members.
For BGP-AD or BGP VPLS pseudowires associated with the oper-group (under the config>service-vpls>bgp>pw-template-binding context), the status of the oper-group is down as long as the pseudowire members are not instantiated (auto-discovered and signaled).
A simple configuration example is described for the case of a BGP VPLS mesh used to interconnect different customer locations. If we assume a customer edge (CE) device is dual-homed to two PEs using BGP MH, the following configuration steps apply:
-
The oper-group bgp-vpls-mesh is created.
-
The BGP VPLS mesh is added to the bgp-vpls-mesh group through the pseudowire template used to create the BGP VPLS mesh.
-
The BGP MH site defined for the access endpoint is associated with the bgp-vpls-mesh group; its status from now on is influenced by the status of the BGP VPLS mesh.
Below is a simple configuration example:
service>oper-group bgp-vpls-mesh-1 create
service>vpls>bgp>pw-template-binding> oper-group bgp-vpls-mesh-1
service>vpls>site> monitor-group bgp-vpls-mesh-1
MAC flush message processing
The previous sections described operating principles of several redundancy mechanisms available in the context of VPLS service. All of them rely on MAC flush messages as a tool to propagate topology change in a context of the specified VPLS. This section summarizes basic rules for generation and processing of these messages.
As described in respective sections, the 7450 ESS, 7750 SR, and 7950 XRS support two types of MAC flush message: flush-all-but-mine and flush-mine. The main difference between these messages is the type of action they signal. Flush-all-but-mine messages request clearing of all FDB entries that were learned from all other LDP peers except the originating PE. This type is also defined by RFC 4762 as an LDP MAC address withdrawal with an empty MAC address list.
Flush-all-mine messages request clearing all FDB entries learned from the originating PE. This means that this message has the opposite effect of the flush-all-but-mine message. This type is not included in the RFC 4762 definition and it is implemented using vendor-specific TLV.
The advantages and disadvantages of the individual types should be apparent from examples in the previous section. The description here summarizes actions taken on reception and the conditions under which individual messages are generated.
Upon reception of MAC flush messages (regardless of the type), an SR-series PE takes the following actions:
-
Clears FDB entries of all indicated VPLS services conforming to the definition.
-
Propagates the message (preserving the type) to all LDP peers, if the propagate-mac-flush flag is enabled at the corresponding VPLS level.
The flush-all-but-mine message is generated under the following conditions:
The flush-all-but-mine message is received from the LDP peer and the propagate-mac-flush flag is enabled. The message is sent to all LDP peers in the context of the VPLS service it was received.
The TCN message in a context of STP instance is received. The flush-all-but-mine message is sent to all LDP peers connected with spoke and mesh SDPs in a context of VPLS service controlled by the specified STP instance (based on M-VPLS definition). If all LDP peers are in the STP domain, that is, the M-VPLS and the uVPLS (user VPLS) both have the same topology, the router does not send any flush-all-but-mine message. If the router has uVPLS LDP peers outside the STP domain, the router sends flush-all-but-mine messages to all its uVPLS peers.
Note: The 7750 SR does not send a withdrawal if the M-VPLS does not contain a mesh SDP. A mesh SDP must be configured in the M-VPLS to send withdrawals.The flush-all-but-mine message is generated when switchover between spoke-SDPs of the same endpoint occurs. The message is sent to the LDP peer connected through the newly active spoke-SDP.
The flush-mine message is generated under the following conditions:
The flush-mine message is received from the LDP peer and the propagate-mac-flush flag is enabled. The message is sent to all LDP peers in the context of the VPLS service it was received.
The flush-mine message is generated when a SAP or SDP transitions from operationally up to an operationally down state and the send-flush-on-failure flag is enabled in the context of the specified VPLS service. The message is sent to all LDP peers connected in the context of the specified VPLS service. The send-flush-on-failure flag is blocked in M-VPLS and is only allowed to be configured in a VPLS service managed by M-VPLS. This is to prevent both messages being sent at the same time.
The flush-mine message is generated when an MC-LAG SAP or MC-APS SAP transitions from an operationally up state to an operationally down state. The message is sent to all LDP peers connected in the context of the specified VPLS service.
The flush-mine message is generated when an MC-Ring SAP transitions from operationally up to an operationally down state or when MC-Ring SAP transitions to slave state. The message is sent to all LDP peers connected in the context of the specified VPLS service.
Dual homing to a VPLS service
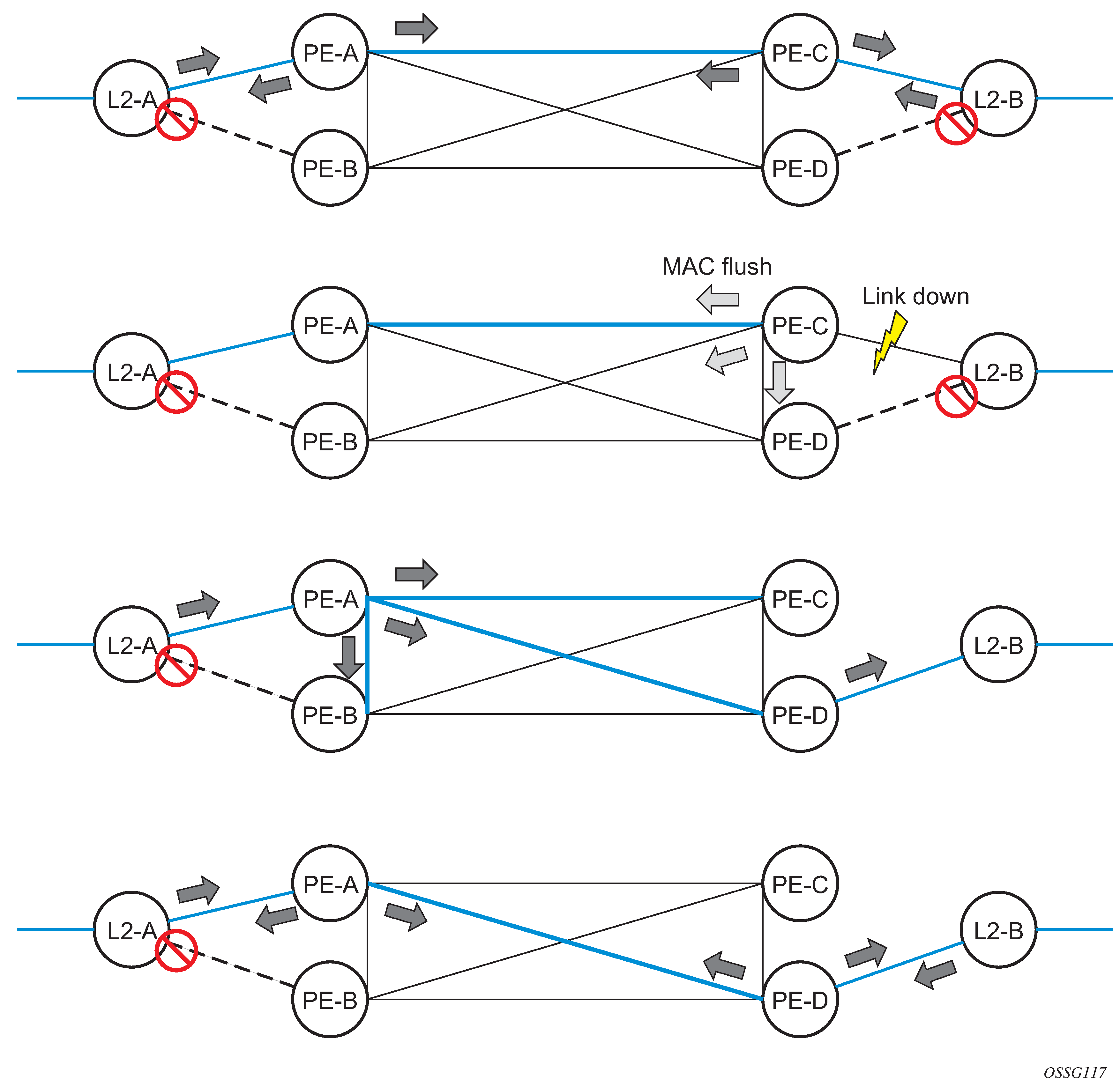
Dual-homed CE connection to VPLS shows a dual-homed connection to VPLS service (PE-A, PE-B, PE-C, PE-D) and operation in case of link failure (between PE-C and L2-B). Upon detection of a link failure, PE-C sends MAC-address-withdraw messages, which indicates to all LDP peers that they should flush all MAC addresses learned from PE-C. This leads to a broadcasting of packets addressing affected hosts and relearning in case an alternative route exists.
The message described here is different than the message described in RFC 4762, Virtual Private LAN Services Using LDP Signaling. The difference is in the interpretation and action performed in the receiving PE. According to the standard definition, upon receipt of a MAC withdraw message, all MAC addresses, except the ones learned from the source PE, are flushed. This section specifies that all MAC addresses learned from the source are flushed. This message has been implemented as an LDP address withdraw message with vendor-specific type, length, and value (TLV), and is called the flush-all-from-me message.
The RFC 4762 compliant message is used in VPLS services for recovering from failures in STP (Spanning Tree Protocol) topologies. The mechanism described in this section represents an alternative solution.
The advantage of this approach (as compared to STP-based methods) is that only the affected MAC addresses are flushed and not the full forwarding database. While this method does not provide a mechanism to secure alternative loop-free topology, the convergence time depends on the speed that the specified CE device opens an alternative link (L2-B switch in Dual-homed CE connection to VPLS) as well as on the speed that PE routers flush their FDB.
In addition, this mechanism is effective only if PE and CE are directly connected (no hub or bridge) as the mechanism reacts to the physical failure of the link.
MC-Ring and VPLS
The use of multi-chassis ring control in a combination with the plain VPLS SAP is supported by the FDB in individual ring nodes, in case the link (or ring node) failure cannot be cleared on the 7750 SR or 7950 XRS.
This combination is not easily blocked in the CLI. If configured, the combination may be functional but the switchover times are proportional to MAC aging in individual ring nodes and, or to the relearning rate because of the downstream traffic.
Redundant plain VPLS access in ring configurations, therefore, exclude corresponding SAPs from the multi-chassis ring operation. Configurations such as M-VPLS can be applied.
ACL next-hop for VPLS
The ACL next-hop for VPLS feature enables an ACL that has a forward to a SAP or SDP action specified to be used in a VPLS service to direct traffic with specific match criteria to a SAP or SDP. This allows traffic destined for the same gateway to be split and forwarded differently based on the ACL.
Policy routing is a popular tool used to direct traffic in Layer 3 networks. As Layer 2 VPNs become more popular, especially in network aggregation, policy forwarding is required. Many providers are using methods such as DPI servers, transparent firewalls, or Intrusion Detection/Prevention Systems (IDS/IPS). Because these devices are bandwidth limited, providers want to limit traffic forwarded through them. In the setup shown in Application 1 diagram, a mechanism is required to direct some traffic coming from a SAP to the DPI without learning, and other traffic coming from the same SAP directly to the gateway uplink-based learning.
This feature allows the provider to create a filter that forwards packets to a specific SAP or SDP. The packets are then forwarded to the destination SAP regardless of learned destination. The SAP can either terminate a Layer 2 firewall, perform deep packet inspection (DPI) directly, or may be configured to be part of a cross-connect bridge into another service. This is useful when running the DPI remotely using VLLs. If an SDP is used, the provider can terminate it in a remote VPLS or VLL service where the firewall is connected. The filter can be configured under a SAP or SDP in a VPLS service. All packets (unicast, multicast, broadcast, and unknown) can be delivered to the destination SAP/SDP.
The filter may be associated with SAPs/SDPs belonging to a VPLS service only if all actions in the ACL forward to SAPs/SDPs that are within the context of that VPLS. Other services do not support this feature. An ACL that contains this feature is allowed, but the system drops any packet that matches an entry with this action.
SDP statistics for VPLS and VLL services
The simple three-node network in SDP statistics for VPLS and VLL services shows two MPLS SDPs and one GRE SDP defined between the nodes. These SDPs connect VPLS1 and VPLS2 instances that are defined in the three nodes. With this feature, the operator has local CLI-based as well as SNMP-based statistics collection for each VC used in the SDPs. This allows for traffic management of tunnel usage by the different services and with aggregation of the total tunnel usage.

SDP statistics allow providers to bill customers on a per-SDP per-byte basis. This destination-based billing model can be used by providers with a variety of circuit types and have different costs associated with the circuits. An accounting file allows the collection of statistics in bulk.
BGP auto-discovery for LDP VPLS
BGP Auto-Discovery (BGP AD) for LDP VPLS is a framework for automatically discovering the endpoints of a Layer 2 VPN, offering an operational model similar to that of an IP VPN. This allows carriers to leverage existing network elements and functions, including but not limited to, route reflectors and BGP policies to control the VPLS topology.
BGP AD complements an already established and well-deployed Layer 2 VPN signaling mechanism target LDP, providing one-touch provisioning for LDP VPLS, where all the related PEs are discovered automatically. The service provider may make use of existing BGP policies to regulate the exchanges between PEs in the same, or in different, autonomous system (AS) domains. The addition of BGP AD procedures does not require carriers to uproot their existing VPLS deployments nor to change the signaling protocol.
BGP AD overview
The BGP protocol establishes neighbor relationships between configured peers. An open message is sent after the completion of the three-way TCP handshake. This open message contains information about the BGP peer sending the message. This message contains Autonomous System Number (ASN), BGP version, timer information, and operational parameters, including capabilities. The capabilities of a peer are exchanged using two numerical values: the Address Family Identifier (AFI) and Subsequent Address Family Identifier (SAFI). These numbers are allocated by the Internet Assigned Numbers Authority (IANA). BGP AD uses AFI 65 (L2VPN) and SAFI 25 (BGP VPLS). For a complete list of allocations, see http://www.iana.org/assignments/address-family-numbers and SAFI http://www.iana.org/assignments/safi-namespace.
Information model
Following the establishment of the peer relationship, the discovery process begins as soon as a new VPLS service instance is provisioned on the PE.
Two VPLS identifiers are used to indicate the VPLS membership and the individual VPLS instance:
VPLS-ID
Membership information, and unique network-wide identifier; the same value is assigned for all VPLS switch instances (VSIs) belonging to the same VPLS. VPLS-ID is encodable and carried as a BGP extended community in one of the following formats:
A two-octet AS-specific extended community
An IPv4 address-specific extended community
VSI-ID
This is the unique identifier for each individual VSI, built by concatenating a route distinguisher (RD) with a 4-byte identifier (usually the system IP of the VPLS PE), encoded and carried in the corresponding BGP NLRI.
To advertise this information, BGP AD employs a simplified version of the BGP VPLS NLRI where just the RD and the next four bytes are used to identify the VPLS instance. There is no need for Label Block and Label Size fields as T-LDP signals the service labels later on.
The format of the BGP AD NLRI is very similar to the one used for IP VPN, as shown in BGP AD NLRI versus IP VPN NLRI. The system IP may be used for the last four bytes of the VSI ID, further simplifying the addressing and the provisioning process.
Network Layer Reachability Information (NLRI) is exchanged between BGP peers indicating how to reach prefixes. The NLRI is used in the Layer 2 VPN case to tell PE peers how to reach the VSI, instead of specific prefixes. The advertisement includes the BGP next hop and a route target (RT). The BGP next hop indicates the VSI location and is used in the next step to determine which signaling session is used for pseudowire signaling. The RT, also coded as an extended community, can be used to build a VPLS full mesh or an HVPLS hierarchy through the use of BGP import/export policies.
BGP is only used to discover VPN endpoints and the corresponding far-end PEs. It is not used to signal the pseudowire labels. This task remains the responsibility of targeted-LDP (T-LDP).
FEC element for T-LDP signaling
Two LDP FEC elements are defined in RFC 4447, PW Setup & Maintenance Using LDP. The original pseudowire-ID FEC element 128 (0x80) employs a 32-bit field to identify the virtual circuit ID and was used extensively in the initial VPWS and VPLS deployments. The simple format is easy to understand but does not provide the required information model for BGP auto-discovery function. To support BGP AD and other new applications, a new Layer 2 FEC element, the generalized FEC (0x81), is required.
The generalized pseudowire-ID FEC element has been designed for auto-discovery applications. It provides a field, the address group identifier (AGI), that is used to signal the membership information from the VPLS-ID. Separate address fields are provided for the source and target address associated with the VPLS endpoints, called the Source Attachment Individual Identifier (SAII) and Target Attachment Individual Identifier (TAII), respectively. These fields carry the VSI ID values for the two instances that are to be connected through the signaled pseudowire.
The detailed format for FEC 129 is shown in Generalized pseudowire-ID FEC element.
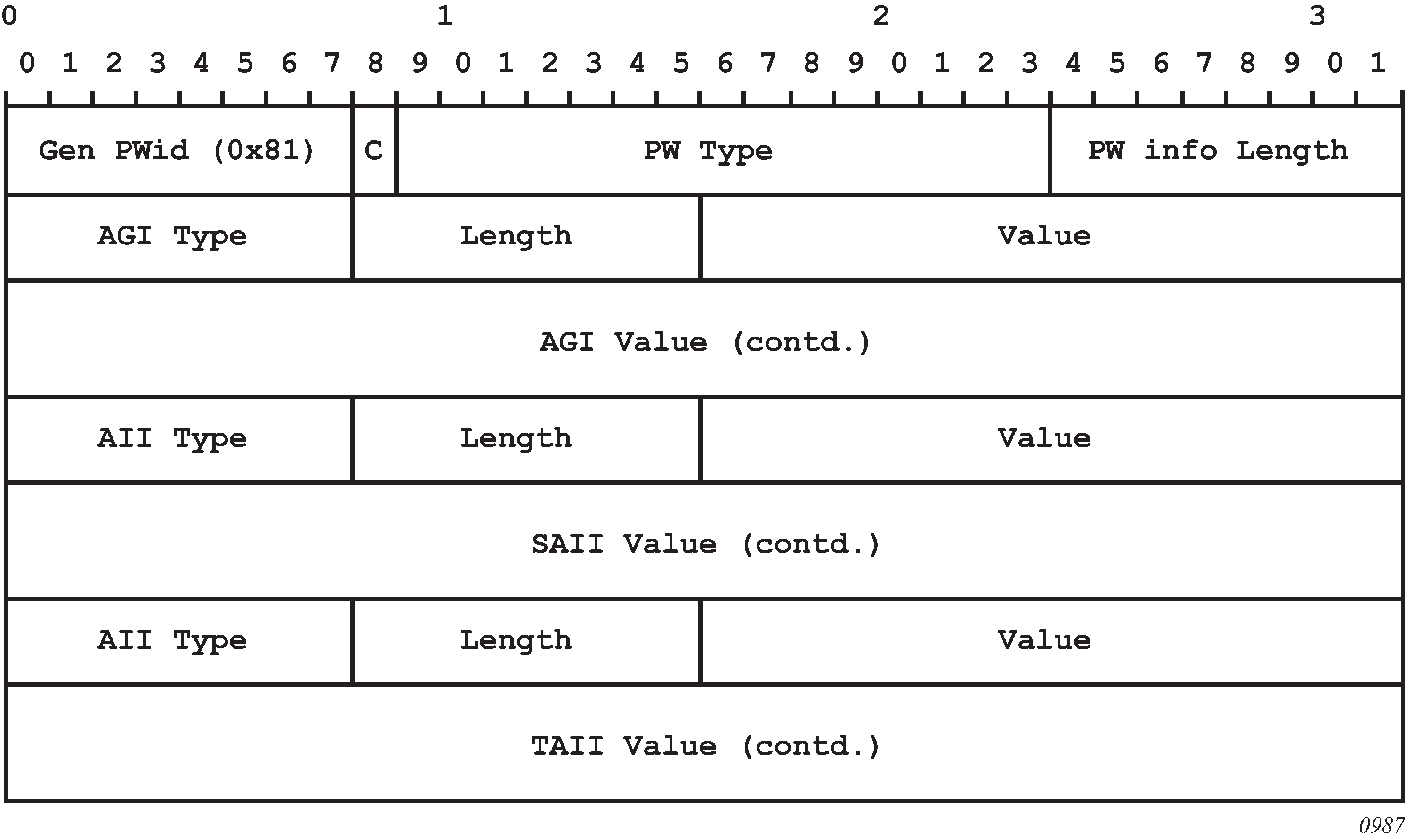
Each of the FEC fields are designed as a sub-TLV equipped with its own type and length, providing support for new applications. To accommodate the BGP AD information model, the following FEC formats are used:
AGI (type 1) is identical in format and content to the BGP extended community attribute used to carry the VPLS-ID value.
Source AII (type 1) is a 4-byte value to carry the local VSI-ID (outgoing NLRI minus the RD).
Target AII (type 1) is a 4-byte value to carry the remote VSI-ID (incoming NLRI minus the RD).
BGP-AD and target LDP (T-LDP) interaction
BGP is responsible for discovering the location of VSIs that share the same VPLS membership. LDP protocol is responsible for setting up the pseudowire infrastructure between the related VSIs by exchanging service-specific labels between them.
After the local VPLS information is provisioned in the local PE, the related PEs participating in the same VPLS are identified through BGP AD exchanges. A list of far-end PEs is generated and triggers the creation, if required, of the necessary T-LDP sessions to these PEs and the exchange of the service-specific VPN labels. The steps for the BGP AD discovery process and LDP session establishment and label exchange are shown in BGP-AD and T-LDP interaction.
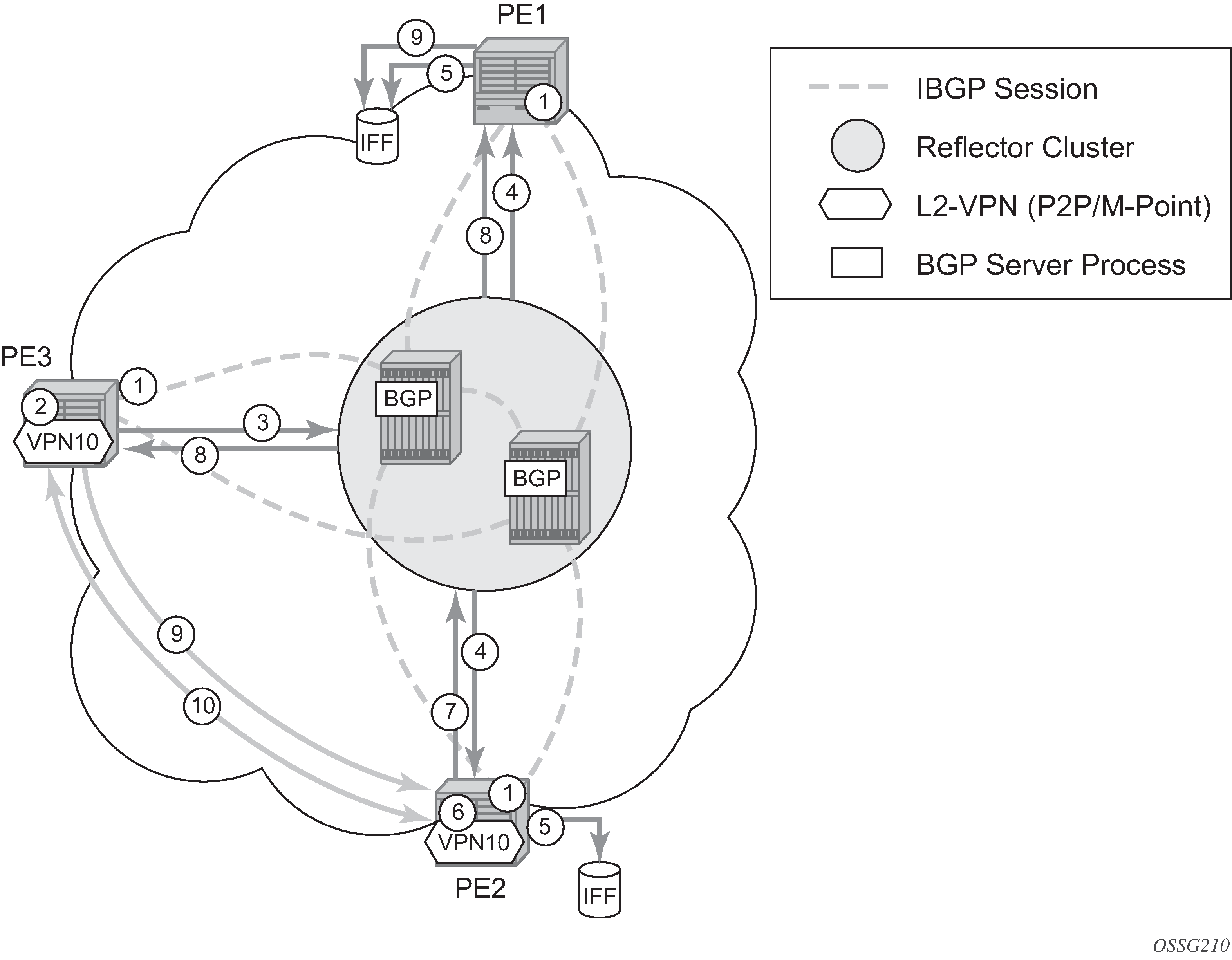
The following corresponds with the actions in BGP-AD and T-LDP interaction:
Establish IBGP connectivity RR.
Configure VPN (10) on edge node (PE3).
Announce VPN to RR using BGP-AD.
Send membership update to each client of the cluster.
LDP exchange or inbound FEC filtering (IFF) of non-match or VPLS down.
Configure VPN (10) on edge node (PE2).
Announce VPN to RR using BGP-AD.
Send membership update to each client of the cluster.
LDP exchange or inbound FEC filtering (IFF) of non-match or VPLS down.
Complete LDP bidirectional pseudowire establishment FEC 129.
SDP usage
Service Access Points (SAPs) are linked to transport tunnels using Service Distribution Points (SDPs). The service architecture allows services to be abstracted from the transport network.
MPLS transport tunnels are signaled using the Resource Reservation Protocol (RSVP-TE) or by the Label Distribution Protocol (LDP). The capability to automatically create an SDP only exists for LDP-based transport tunnels. Using a manually provisioned SDP is available for both RSVP-TE and LDP transport tunnels. For more information about MPLS, LDP and RSVP, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR MPLS Guide.
GRE transport tunnels use GRE encapsulation and can be used with manually provisioned or auto created SDPs.
Automatic creation of SDPs
When BGP AD is used for LDP VPLS, with an LDP or GRE transport tunnel, there is no requirement to manually create an SDP. The LDP or GRE SDP can be automatically instantiated using the information advertised by BGP AD. This simplifies the configuration on the service node.
The use of an automatically created GRE tunnel is enabled by creating the PW template used within the service with the parameter auto-gre-sdp. The GRE SDP and SDP binding is created after a matching BGP route has been received.
Enabling LDP on the IP interfaces connecting all nodes between the ingress and the egress builds transport tunnels based on the best IGP path. LDP bindings are automatically built and stored in the hardware. These entries contain an MPLS label pointing to the best next hop along the best path toward the destination.
When two endpoints need to connect and no SDP exists, a new SDP is automatically constructed. New services added between two endpoints that already have an automatically created SDP are immediately used; no new SDP is constructed. The far-end information is learned from the BGP next hop information in the NLRI. When services are withdrawn with a BGP_Unreach-NLRI, the automatically established SDP remains up while at least one service is connected between those endpoints. An automatically created SDP is removed and the resources are released when the only or last service is removed.
The service provider has the option of associating the auto-discovered SDP with a split horizon group using the pw-template-binding option, to control the forwarding between pseudowires and to prevent Layer 2 service loops.
An auto-discovered SDP using a pw-template-binding without a split horizon group configured has similar traffic flooding behavior as a spoke-SDP.
Manually provisioned SDP
The carrier is required to manually provision the SDP if they create transport tunnels using RSVP-TE. Operators have the option to choose a manually configured SDP if they use LDP as the tunnel signaling protocol. The functionality is the same regardless of the signaling protocol.
Creating a BGP AD-enabled VPLS service on an ingress node with the manually provisioned SDP option causes the tunnel manager to search for an existing SDP that connects to the far-end PE. The far-end IP information is learned from the BGP next hop information in the NLRI. If a single SDP exists to that PE, it is used. If no SDP is established between the two endpoints, the service remains down until a manually configured SDP becomes active.
When multiple SDPs exist between two endpoints, the tunnel manager selects the appropriate SDP. The algorithm prefers SDPs with the best (lower) metric. If there are multiple SDPs with equal metrics, the operational state of the SDPs with the best metric is considered. If the operational state is the same, the SDP with the higher SDP-ID is used. If an SDP with a preferred metric is found with an operational state that is not active, the tunnel manager flags it as ineligible and restarts the algorithm.
Automatic instantiation of pseudowires (SDP bindings)
The choice of manual or auto-provisioned SDPs has limited impact on the amount of required provisioning. Most of the savings are achieved through the automatic instantiation of the pseudowire infrastructure (SDP bindings). This is achieved for every auto-discovered VSI through the use of the pseudowire template concept. Each VPLS service that uses BGP AD contains the pw-template-binding option defining specific Layer 2 VPN parameters. This command references a PW template, which defines the pseudowire parameters. The same PW template may be referenced by multiple VPLS services. As a result, changes to these pseudowire templates have to be treated with caution as they may impact many customers simultaneously.
The Nokia implementation provides for safe handling of pseudowire templates. Changes to the pseudowire templates are not automatically propagated. Tools are provided to evaluate and distribute the changes. The following command is used to distribute changes to a PW template at the service level to one or all services that use that template:
PERs-4# tools perform service id 300 eval-pw-template 1 allow-service-impact
If the service ID is omitted, all services are updated. The type of change made to the PW template influences how the service is impacted:
-
Adding or removing a split-horizon-group causes the router to destroy the original object and re-create it using the new value.
-
Changing parameters in the vc-type {ether | vlan} command requires LDP to re-signal the labels.
Both of these changes are service affecting. Other changes are not service affecting.
Mixing statically configured and auto-discovered pseudowires in a VPLS
The services implementation allows for manually provisioned and auto-discovered pseudowire (SDP bindings) to coexist in the same VPLS instance (for example, both FEC128 and FEC 129 are supported). This allows for gradual introduction of auto-discovery into an existing VPLS deployment.
As FEC 128 and 129 represent different addressing schemes, it is important to ensure that only one is used at any time between the same two VPLS instances. Otherwise, both pseudowires may become active causing a loop that may adversely impact the correct functioning of the service. It is recommended that FEC128 pseudowire be disabled as soon as the FEC129 addressing scheme is introduced in a portion of the network. Alternatively, RSTP may be used during the migration as a safety mechanism to provide additional protection against operational errors.
Resiliency schemes
The use of BGP AD on the network side, or in the backbone, does not affect the different resiliency schemes Nokia has developed in the access network. This means that both Multi-Chassis Link Aggregation (MC-LAG) and Management-VPLS (M-VPLS) can still be used.
BGP AD may coexist with Hierarchical-VPLS (H-VPLS) resiliency schemes (for example, dual-homed MTUs devices to different PE-rs nodes) using existing methods (M-VPLS and statically configured active/standby pseudowire endpoint).
If provisioned SDPs are used by BGP AD, M-VPLS may be employed to provide loop avoidance. However, it is currently not possible to auto-discover active/standby pseudowires and to instantiate the related endpoint.
BGP VPLS
The Nokia BGP VPLS solution, compliant with RFC 4761, Virtual Private LAN Service (VPLS) Using BGP for Auto-Discovery and Signaling, is described in this section.

BGP VPLS solution shows the service representation for BGP VPLS mesh. The major BGP VPLS components and the deltas from LDP VPLS with BGP AD are as follows:
Data plane is identical with the LDP VPLS solution; for example, VPLS instances interconnected by pseudowire mesh. Split horizon groups may be used for loop avoidance between pseudowires.
Addressing is based on a 2-byte VE-ID assigned to the VPLS instance.
BGP-AD for LDP VPLS: 4-byte VSI-ID (system IP) identifies the VPLS instance.
The target VPLS instance is identified by the Route Target (RT) contained in the MP-BGP advertisement (extended community attribute).
BGP-AD: a new MP-BGP extended community is used to identify the VPLS. RT is used for topology control.
Auto-discovery is MP-BGP based; the same AFI, SAFI is used as for LDP VPLS BGP-AD.
The BGP VPLS updates are distinguished from the BGP-AD updates based on the value of the NLRI prefix length: 17 bytes for BGP VPLS, 12 bytes for BGP-AD.
BGP-AD NLRI is shorter because there is no need to carry pseudowire label information as T-LDP does the pseudowire signaling for LDP VPLS.
Pseudowire label signaling is MP-BGP based. Therefore, the BGP NLRI content also includes label-related information; for example, block offset, block size, and label base.
LDP VPLS: target LDP (T-LDP) is used for signaling the pseudowire service label.
The Layer 2 extended community proposed in RFC 4761 is used to signal pseudowire characteristics; for example, VPLS status, control word, and sequencing.
Pseudowire signaling details
The pseudowire is set up using the following NLRI fields:
VE Block offset (VBO)
This is used to define each VE-ID set for which the NLRI is targeted.
VBO = n*VBS+1; for VBS = 8, this results in 1, 9, 17, 25, …
Targeted Remote VE-IDs are from VBO to (VBO + VBS - 1)
-
VE Block size (VBS)
Defines how many contiguous pseudowire labels are reserved, starting with the Label Base; Nokia implementation always uses a value of eight (8).
Label Base (LB)
This is the local allocated label base. The next eight consecutive labels available are allocated for remote PEs.
This BGP update is telling the other PEs that accept the RT: reach me (VE-ID = x), use a pseudowire label of LB + VE-ID – VBO using the BGP NLRI for which VBO =< local VE-ID < VBO + VBS.
Following is an example of how this algorithm works, assuming PE1 has VE-ID 7 configured:
-
PE1 allocates a label block of eight consecutive labels available, starting with LB = 1000.
-
PE1 starts sending a BGP update with pseudowire information of VBO = 1, VBS = 8, LB = 1000 in the NLRI.
-
This pseudowire information is accepted by all participating PEs with VE-IDs from 1 to 8.
-
Each of the receiving PEs uses the pseudowire label = LB + VE-ID - VBO to send traffic back to the originator PE. For example, VE-ID 2 uses pseudowire label 1001.
Assuming that VE-ID = 10 is configured in another PE4, the following procedure applies:
-
PE4 sends a BGP update with the new VE-ID in the network that is received by all the other participating PEs, including PE1.
-
Upon reception, PE1 generates another label block of 8 labels for the VBO = 9. For example, the initial PE creates new pseudowire signaling information of VBO = 9, VBS = 8, LB = 3000, and insert it in a new NLRI and BGP update that is sent in the network.
-
This new NLRI is used by the VE-IDs from 9 to 16 to establish pseudowires back to the originator PE1. For example, PE4 with VE-ID 10 uses pseudowire label 3001 to send VPLS traffic back to PE1.
-
The PEs owning the set of VE-IDs from 1 to 8 ignore this NLRI.
In addition to the pseudowire label information, the "Layer2 Info Extended Community" attribute must be included in the BGP update for BGP VPLS to signal the attributes of all the pseudowires that converge toward the originator VPLS PE.
The format is as follows.
The meaning of the fields are as follows:
extended community type
This is the value allocated by IANA for this attribute is 0x800A.
encaps type
Encapsulation type identifies the type of pseudowire encapsulation. The only value used by BGP VPLS is 19 (13 in HEX). This value identifies the encapsulation to be used for pseudowire instantiated through BGP signaling, which is the same as the one used for Ethernet pseudowire type in regular VPLS. There is no support for an equivalent Ethernet VLAN pseudowire in BGP VPLS in BGP signaling.
control flags
This field is control information concerning the pseudowires (see BGP VPLS solution).
Layer 2 MTU
This is the Maximum Transmission Unit to be used on the pseudowires
reserved
This field is reserved and must be set to zero and ignored on reception except where it is used for VPLS preference.
For inter-AS, the preference information must be propagated between autonomous systems. Consequently, as the VPLS preference in a BGP-VPLS or BGP multihoming update extended community is zero, the local preference is copied by the egress ASBR into the VPLS preference field before sending the update to the EBGP peer. The adjacent ingress ASBR then copies the received VPLS preference into the local preference to prevent the update being considered malformed.
Control flag bit vector format shows the detailed format for the control flags bit vector.
The following bits in the control flags are defined as follows:
- S
- sequenced delivery of frames that must or must not be used when sending VPLS packets to this PE, depending on whether S is 1 or 0, respectively
- C
- a Control word that must or must not be present when sending VPLS packets to this PE, depending on whether C is 1 or 0, respectively. By default, Nokia implementation uses value 0
- MBZ
- Must Be Zero bits, set to zero when sending and ignored when receiving
- D
- indicates the status of the whole VPLS instance (VSI); D = 0 if Admin and Operational status are up, D = 1 otherwise
Following are the events that set the D-bit to 1 to indicate VSI down status in the BGP update message sent out from a PE:
Local VSI is shut down administratively using the config service vpls shutdown command.
All the related endpoints (SAPs or LDP pseudowires) are down.
There are no related endpoints (SAPs or LDP pseudowires) configured yet in the VSI.
The intent is to save the core bandwidth by not establishing the BGP pseudowires to an empty VSI.
Upon reception of a BGP update message with D-bit set to 1, all the receiving VPLS PEs must mark related pseudowires as down.
The following events do not set the D-bit to 1:
The local VSI is deleted; a BGP update with UNREACH-NLRI is sent out. Upon reception, all remote VPLS PEs must remove the related pseudowires and BGP routes.
If the local SDP goes down, only the BGP pseudowires mapped to that SDP go down. There is no BGP update sent.
The adv-service-mtu command can be used to override the MTU value used in BGP signaling to the far-end of the pseudowire. This value is also used to validate the value signaled by the far-end PE unless ignore-l2vpn-mtu-mismatch is also configured.
If the ignore-l2vpn-mtu-mismatch command is configured, the router does not check the value of the "Layer 2 MTU" in the "Layer2 Info Extended Community" received in a BGP update message against the local service MTU, or against the MTU value signaled by this router. The router brings up the BGP-VPLS service regardless of any MTU mismatch.
Supported VPLS features
BGP VPLS includes support for a new type of pseudowire signaling based on MP-BGP, based on the existing VPLS instance; therefore, it inherits all the existing Ethernet switching functions.
The use of an automatically created GRE tunnel is enabled by creating the PW template used within the service with the parameter auto-gre-sdp. The GRE SDP and SDP binding is created after a matching BGP route has been received.
Following are some of the most important VPLS features ported to BGP VPLS:
VPLS data plane features: for example, FDB management, SAPs, LAG access, and BUM rate limiting
MPLS tunneling: LDP, LDP over RSVP-TE, RSVP-TE, GRE, and MP-BGP based on RFC 8277 (Inter-AS option C solution)
Note: Pre-provisioned SDPs must be configured when RSVP-signaled transport tunnels are used.HVPLS topologies, hub and spoke traffic distribution
Coexists with LDP VPLS (with or without BGP-AD) in the same VPLS instance:
LDP and BGP-signaling should operate in disjoint domains to simplify loop avoidance.
Coexists with BGP-based multihoming
BGP VPLS is supported as the control plane for B-VPLS
Supports IGMP/PIM snooping for IPv4
Support for High Availability is provided
Ethernet Service OAM toolset is supported: IEEE 802.1ag, Y.1731.
Not supported OAM features: CPE Ping, MAC trace/ping/populate/purge
Support for RSVP and LSP P2MP LSP for VPLS/B-VPLS BUM
VCCV BFD support for VPLS services
The SR OS supports RFC 5885, which specifies a method for carrying BFD in a pseudowire associated channel. For general information about VCCV BFD, limitations, and configuring, see the VLL Services chapter.
VCCV BFD is supported on the following VPLS services:
T-LDP spoke-SDP termination on VPLS (including I-VPLS, B-VPLS, and R-VPLS)
H-VPLS spoke-SDP
BGP VPLS
VPLS with BGP auto-discovery
To configure VCCV BFD for H-VPLS (where the pseudowire template does not apply), configure the BFD template using the configure service vpls spoke-sdp bfd-template name command, then enable it using the configure service vpls spoke-sdp bfd-enable command.
For BGP VPLS, a BFD template is referenced from the pseudowire template binding context. To configure VCCV BFD for BGP VPLS, use the configure service vpls bgp pw-template-binding bfd-template name command and enable it using the configure service vpls bgp pw-template-binding bfd-enable command.
For BGP-AD VPLS, a BFD template is referenced from the pseudowire template context. To configure VCCV BFD for BGP-AD, use the configure service vpls bgp-ad pw-template-binding bfd-template name command, and enable it using the configure service vpls bgp-ad pw-template-binding bfd-enable command.
BGP multihoming for VPLS
This section describes BGP-based procedures for electing a designated forwarder among the set of PEs that are multihomed to a customer site. Only the local PEs are actively participating in the selection algorithm. The PEs remote from the dual-homed CE are not required to participate in the designated forwarding election for a remote dual-homed CE.
The main components of the BGP-based multihoming solution for VPLS are:
Provisioning model
MP-BGP procedures
Designated Forwarder Election
Blackhole avoidance, indicating the designated forwarder change toward the core PEs and access PEs or CEs
The interaction with pseudowire signaling (BGP/LDP)
Figure 29. BGP multihoming for VPLS 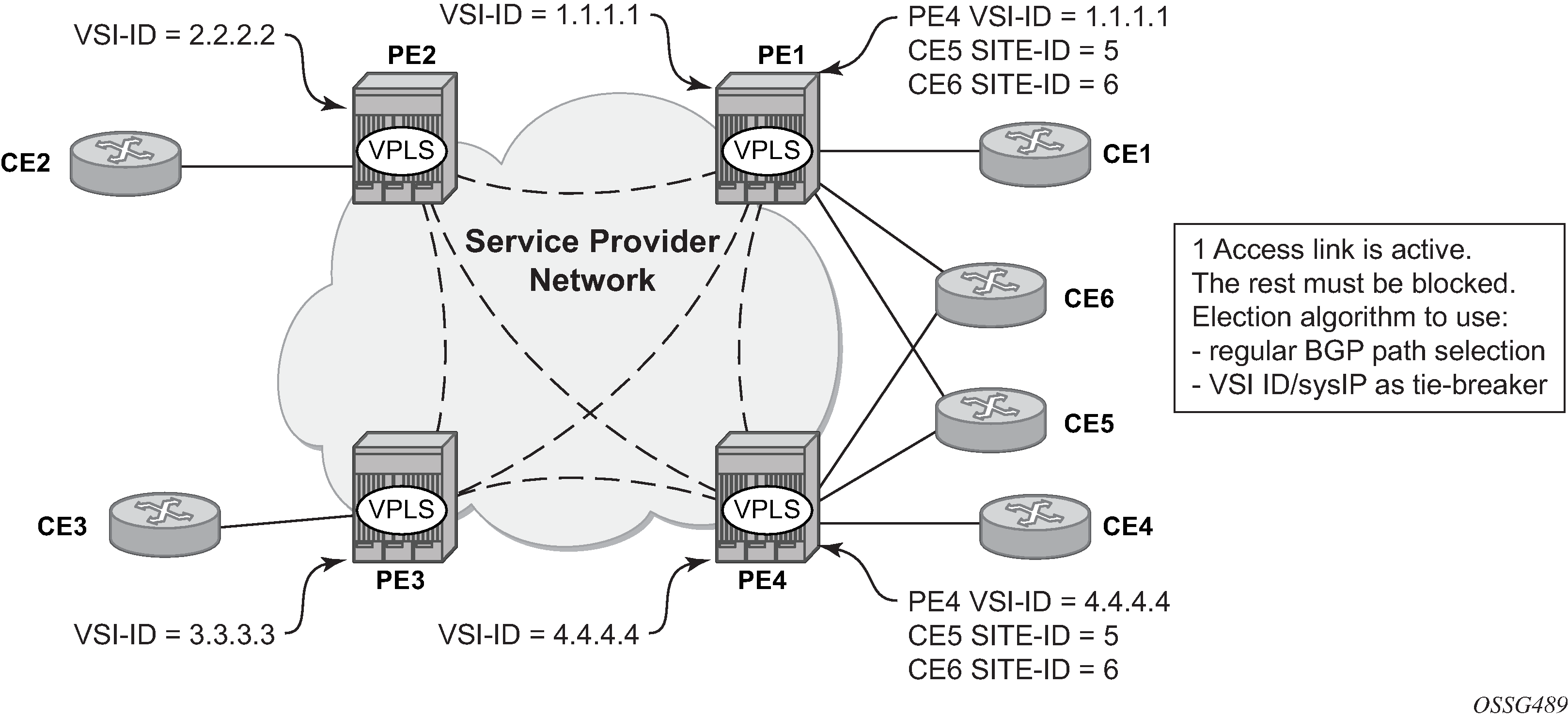
BGP multihoming for VPLS shows the VPLS using BGP multihoming for the case of multihomed CEs. Although the figure shows the case of a pseudowire infrastructure signaled with LDP for an LDP VPLS using BGP-AD for discovery, the procedures are identical for BGP VPLS or for a mix of BGP- and LDP-signaled pseudowires.
Information model and required extensions to L2VPN NLRI
VPLS Multihoming using BGP-MP expands on the BGP AD and BGP VPLS provisioning model. The addressing for the multihomed site is still independent from the addressing for the base VSI (VSI-ID or, respectively, VE-ID). Every multihomed CE is represented in the VPLS context through a site-ID, which is the same on the local PEs. The site-ID is unique within the scope of a VPLS. It serves to differentiate between the multihomed CEs connected to the same VPLS Instance (VSI). For example, in BGP MH-NLRI for VPLS multihoming, CE5 is assigned the same site-ID on both PE1 and PE4. For the same VPLS instance, different site-IDs are assigned for multihomed CE5 and CE6; for example, site-ID 5 is assigned for CE5 and site-ID 6 is assigned for CE6. The single-homed CEs (CE1, 2, 3, and 4) do not require allocation of a multihomed site-ID. They are associated with the addressing for the base VSI, either VSI-ID or VE-ID.
The new information model required changes to the BGP usage of the NLRI for VPLS. The extended MH NLRI for Multi-Homed VPLS is compared with the BGP AD and BGP VPLS NLRIs in BGP MH-NLRI for VPLS multihoming.

The BGP VPLS NLRI described in RFC 4761 is used to carry a 2-byte site-ID that identifies the MH site. The last seven bytes of the BGP VPLS NLRI used to instantiate the pseudowire are not used for BGP-MH and are zeroed out. This NLRI format translates into the following processing path in the receiving VPLS PE:
BGP VPLS PE: no label information means there is no need to set up a BGP pseudowire.
BGP AD for LDP VPLS: length =17 indicates a BGP VPLS NLRI that does not require any pseudowire LDP signaling.
The processing procedures described in this section start from the above identification of the BGP update as not destined for pseudowire signaling.
The RD ensures that the NLRIs associated with a specific site-ID on different PEs are seen as different by any of the intermediate BGP nodes (RRs) on the path between the multihomed PEs. That is, different RDs must be used on the MH PEs every time an RR or an ASBR is involved to guarantee the MH NLRIs reach the PEs involved in VPLS MH.
The L2-Info extended community from RFC 4761 is used in the BGP update for MH NLRI to initiate a MAC flush for blackhole avoidance, to indicate the operational and admin status for the MH site or the DF election status.
After the pseudowire infrastructure between VSIs is built using either RFC 4762, Virtual Private LAN Service (VPLS) Using Label Distribution Protocol (LDP) Signaling, or RFC 4761 procedures, or a mix of pseudowire signaling procedures, on activation of a multihomed site, an election algorithm must be run on the local and remote PEs to determine which site is the designated forwarder (DF). The end result is that all the related MH sites in a VPLS are placed in standby except for the site selected as DF. Nokia BGP-based multihoming solution uses the DF election procedure described in the IETF working group document draft-ietf-bess-vpls-multihoming-01. The implementation allows the use of BGP local preference and the received VPLS preference but does not support setting the VPLS preference to a non-zero value.
Supported services and multihoming objects
This feature is supported for the following services:
LDP VPLS with or without BGP-AD
BGP VPLS (BGP multihoming for inter-AS BGP-VPLS services is not supported)
mix of the above
PBB B-VPLS on BCB
PBB I-VPLS (see IEEE 802.1ah Provider Backbone Bridging for more information)
The following access objects can be associated with MH Site:
SAPs
SDP bindings (pseudowire object), both mesh-SDP and spoke-SDP
Split Horizon Group
Under the SHG we can associate either one or multiple of the following objects: SAPs, pseudowires (BGP VPLS, BGP-AD, provisioned and LDP-signaled spoke-SDP and mesh-SDP)
Blackhole avoidance
Blackholing refers to the forwarding of frames to a PE that is no longer carrying the designated forwarder. This could happen for traffic from:
Core PE participating in the main VPLS
Customer Edge devices (CEs)
Access PEs (pseudowires between them and the MH PEs are associated with MH sites)
Changes in DF election results or MH site status must be detected by all of the above network elements to provide for Blackhole Avoidance.
MAC flush to the core PEs
Assuming that there is a transition of the existing DF to non-DF status, the PE that owns the MH site experiencing this transition generates a MAC flush-all-from-me (negative MAC flush) toward the related core PEs. Upon reception, the remote PEs flush all the MACs learned from the MH PE.
MAC flush-all-from-me indication message is sent using the following core mechanisms:
For LDP VPLS running between core PEs, existing LDP MAC flush is used.
For pseudowire signaled with BGP VPLS, MAC flush is provided implicitly using the L2-Info Extended community to indicate a transition of the active MH site; for example, the attached objects going down or more generically, the entire site going from Designated Forwarder (DF) to non-DF.
Double flushing does not happen as it is expected that between any pair of PEs, there exists only one type of pseudowires, either BGP or LDP pseudowire, but not both.
Indicating non-DF status toward the access PE or CE
For the CEs or access PEs, support is provided for indicating the blocking of the MH site using the following procedures:
For MH Access PE running LDP pseudowires, the LDP standby-status is sent to all LDP pseudowires.
For MH CEs, site deactivation is linked to a CCM failure on a SAP that has a down MEP configured.
BGP multihoming for VPLS inter-domain resiliency
BGP MH for VPLS can be used to provide resiliency between different VPLS domains. An example of a multihoming topology is shown in BGP MH used in an HVPLS topology.

LDP VPLS domains are interconnected using a core VPLS domain, either BGP VPLS or LDP VPLS. The gateway PEs, for example PE2 and PE3, are running BGP multihoming where one MH site is assigned to each of the pseudowires connecting the access PE, PE7, and PE8 in this example.
Alternatively, the MH site can be associated with multiple access pseudowires using an access SHG. The configure service vpls site failed-threshold command can be used to indicate the number of pseudowire failures that are required for the MH site to be declared down.
Multicast-aware VPLS
VPLS is a Layer 2 service; therefore, multicast and broadcast frames are normally flooded in a VPLS. Broadcast frames are targeted to all receivers. However, for IP multicast, normally for a multicast group, only some receivers in the VPLS are interested. Flooding to all sites can cause wasted network bandwidth and unnecessary replication on the ingress PE router.
To avoid this condition, VPLS is IP multicast-aware; therefore, it forwards IP multicast traffic based on multicast states to the object on which the IP multicast traffic is requested. This is achieved by enabling the following related IP multicast protocol snooping:
IGMP snooping
MLD snooping
PIM snooping
IGMP snooping for VPLS
When IGMP snooping is enabled in a VPLS service, IGMP messages received on SAPs and SDPs are snooped to determine the scope of the flooding for a specified stream or (S,G). IGMP snooping operates in a proxy mode, where the system summarizes upstream IGMP reports and responds to downstream queries. For a description of IGMP snooping, see the 7450 ESS, 7750 SR, and VSR Triple Play Service Delivery Architecture Guide, "IGMP Snooping".
Streams are sent to all SAPs and SDPs on which there is a multicast router (either discovered dynamically from received query messages or configured statically using the mrouter-port command) and on which an active join for that stream has been received. The Mrouter port configuration adds a (*,*) entry into the MFIB, which causes all groups (and IGMP messages) to be sent out of the respective object and causes IGMP messages received on that object to be discarded.
Directly-connected multicast sources are supported when IGMP snooping is enabled.
IGMP snooping is enabled at the service level.
IGMP is not supported in the following:
B-VPLS, routed I-VPLS, PBB-VPLS services
a router configured with enable-inter-as-vpn or enable-rr-vpn-forwarding
the following forms of default SAP:
*
*.null
*.*
a VPLS service configured with a connection profile VLAN SAP
MLD snooping for VPLS
MLD snooping is an IPv6 version of IGMP snooping. The guidelines and procedures are similar to IGMP snooping as previously described. However, MLD snooping uses MAC-based forwarding. See MAC-based IPv6 multicast forwarding for more information. Directly connected multicast sources are supported when MLD snooping is enabled.
MLD snooping is enabled at the service level and is not supported in the following services:
B-VPLS
-
Routed I-VPLS
-
EVPN-MPLS services
-
PBB-EVPN services
MLD snooping is not supported under the following forms of default SAP:
*
*.null
*.*
MLD snooping is not supported in a VPLS service configured with a connection profile VLAN SAP.
PIM snooping for VPLS
PIM snooping for VPLS allows a VPLS PE router to build multicast states by snooping PIM protocol packets that are sent over the VPLS. The VPLS PE then forwards multicast traffic based on the multicast states. When all receivers in a VPLS are IP multicast routers running PIM, multicast forwarding in the VPLS is efficient when PIM snooping for VPLS is enabled.
Because of PIM join/prune suppression, to make PIM snooping operate over VPLS pseudowires, two options are available: plain PIM snooping and PIM proxy. PIM proxy is the default behavior when PIM snooping is enabled for a VPLS.
PIM snooping is supported for both IPv4 and IPv6 multicast by default and can be configured to use SG-based forwarding (see IPv6 multicast forwarding for more information).
Directly connected multicast sources are supported when PIM snooping is enabled.
The following restrictions apply to PIM snooping:
PIM snooping for IPv4 and IPv6 is not supported:
in the following services:
PBB B-VPLS
R-VPLS (including I-VPLS and BGP EVPN)
PBB-EVPN B-VPLS
EVPN-VXLAN R-VPLS
-
on a router configured with enable-inter-as-vpn or enable-rr-vpn-forwarding
-
under the following forms of default SAP:
-
*
-
*.null
-
*.*
-
-
in a VPLS service configured with a connection profile VLAN SAP
-
with connected SR OSs configured with improved-assert
-
with subscriber management in the VPLS service
-
as a mechanism to drive MCAC
-
PIM snooping for IPv6 is not supported:
-
in the following services:
-
PBB I-VPLS
-
BGP-VPLS
-
BGP EVPN (including PBB-EVPN)
-
VPLS E-Tree
-
Management VPLS
-
-
with the configuration of MLD snooping
-
Plain PIM snooping
In a plain PIM snooping configuration, VPLS PE routers only snoop; PIM messages are generated on their own. Join/prune suppression must be disabled on CE routers.
When plain PIM snooping is configured, if a VPLS PE router detects a condition where join/prune suppression is not disabled on one or more CE routers, the PE router puts PIM snooping into the PIM proxy state. A trap is generated that reports the condition to the operator and is logged to the syslog. If the condition changes, for example, join/prune suppression is disabled on CE routers, the PE reverts to the plain PIM snooping state. A trap is generated and is logged to the syslog.
PIM proxy
For PIM proxy configurations, VPLS PE routers perform the following:
snoop hellos and flood hellos in the fast data path
consume join/prune messages from CE routers
generate join/prune messages upstream using the IP address of one of the downstream CE routers
run an upstream PIM state machine to determine whether a join/prune message should be sent upstream
Join/prune suppression is not required to be disabled on CE routers, but it requires all PEs in the VPLS to have PIM proxy enabled. Otherwise, CEs behind the PEs that do not have PIM proxy enabled may not be able to get multicast traffic that they are interested in if they have join/prune suppression enabled.
When PIM proxy is enabled, if a VPLS PE router detects a condition where join/prune suppression is disabled on all CE routers, the PE router puts PIM proxy into a plain PIM snooping state to improve efficiency. A trap is generated to report the scenario to the operator and is logged to the syslog. If the condition changes, for example, join/prune suppression is enabled on a CE router, PIM proxy is placed back into the operational state. Again, a trap is generated to report the condition to the operator and is logged to the syslog.
IPv6 multicast forwarding
When MLD snooping or PIM snooping for IPv6 is enabled, the forwarding of IPv6 multicast traffic is MAC-based; see MAC-based IPv6 multicast forwarding for more information.
The operation with PIM snooping for IPv6 can be changed to SG-based forwarding; see SG-based IPv6 multicast forwarding for more information.
The following command configures the IPv6 multicast forwarding mode with the default being mac-based:
configure service vpls mcast-ipv6-snooping-scope {sg-based | mac-based}
The forwarding mode can only be changed when PIM snooping for IPv6 is disabled.
MAC-based IPv6 multicast forwarding
This section describes IPv6 multicast address to MAC address mapping and IPv6 multicast forwarding entries.
For IPv6 multicast address to MAC address mapping, Ethernet MAC addresses in the range of 33-33-00-00-00-00 to 33-33-FF-FF-FF-FF are reserved for IPv6 multicast. To map an IPv6 multicast address to a MAC-layer multicast address, the low-order 32 bits of the IPv6 multicast address are mapped directly to the low-order 32 bits in the MAC-layer multicast address.
For IPv6 multicast forwarding entries, IPv6 multicast snooping forwarding entries are based on MAC addresses, while native IPv6 multicast forwarding entries are based on IPv6 addresses. When both MLD snooping or PIM snooping for IPv6 and native IPv6 multicast are enabled on the same device, both types of forwarding entries are supported on the same forward plane, although they are used for different services.
The following output shows a service with PIM snooping for IPv6 that has received joins for two multicast groups from different sources. As the forwarding mode is MAC-based, there is a single MFIB entry created to forward these two groups.
*A:PE# show service id 1 pim-snooping group ipv6
===============================================================================
PIM Snooping Groups ipv6
===============================================================================
Group Address Source Address Type Incoming Num
Intf Oifs
-------------------------------------------------------------------------------
ff0e:db8:1000::1 2001:db8:1000::1 (S,G) SAP:1/1/1 2
ff0e:db8:1001::1 2001:db8:1001::1 (S,G) SAP:1/1/1 2
-------------------------------------------------------------------------------
Groups : 2
===============================================================================
*A:PE#
*A:PE# show service id 1 all | match "Mcast IPv6 scope"
Mcast IPv6 scope : mac-based
*A:PE#
*A:PE# show service id 1 mfib
===============================================================================
Multicast FIB, Service 1
===============================================================================
Source Address Group Address Port Id Svc Id Fwd
Blk
-------------------------------------------------------------------------------
* 33:33:00:00:00:01 sap:1/1/1 Local Fwd
sap:1/1/2 Local Fwd
-------------------------------------------------------------------------------
Number of entries: 1
===============================================================================
*A:PE#
SG-based IPv6 multicast forwarding
When PIM snooping for IPv6 is configured, SG-based forwarding can be enabled, which causes the IPv6 multicast forwarding to be based on both the source (if specified) and destination IPv6 address in the received join.
Enabling SG-based forwarding increases the MFIB usage if the source IPv6 address or higher 96 bits of the destination IPv6 address varies in the received joins compared to using MAC-based forwarding.
The following output shows a service with PIM snooping for IPv6 that has received joins for two multicast groups from different sources. As the forwarding mode is SG-based, there are two MFIB entries, one for each of the two groups.
*A:PE# show service id 1 pim-snooping group ipv6
===============================================================================
PIM Snooping Groups ipv6
===============================================================================
Group Address Source Address Type Incoming Num
Intf Oifs
-------------------------------------------------------------------------------
ff0e:db8:1000::1 2001:db8:1000::1 (S,G) SAP:1/1/1 2
ff0e:db8:1001::1 2001:db8:1001::1 (S,G) SAP:1/1/1 2
-------------------------------------------------------------------------------
Groups : 2
===============================================================================
*A:PE#
*A:PE# show service id 1 all | match "Mcast IPv6 scope"
Mcast IPv6 scope : sg-based
*A:PE#
*A:PE# show service id 1 mfib
===============================================================================
Multicast FIB, Service 1
===============================================================================
Source Address Group Address Port Id Svc Id Fwd
Blk
-------------------------------------------------------------------------------
2001:db8:1000:* ff0e:db8:1000::1 sap:1/1/1 Local Fwd
sap:1/1/2 Local Fwd
2001:db8:1001:* ff0e:db8:1001::1 sap:1/1/1 Local Fwd
sap:1/1/2 Local Fwd
-------------------------------------------------------------------------------
Number of entries: 2
===============================================================================
*A:PE#
SG-based IPv6 multicast forwarding is supported when both plain PIM snooping and PIM proxy are supported.
SG-based forwarding is only supported on FP3- or higher-based line cards. It is supported in all services in which PIM snooping for IPv6 is supported, with the same restrictions.
It is not supported in the following services:
PBB B-VPLS
PBB I-VPLS
Routed-VPLS (including with I-VPLS and BGP-EVPN)
BGP-EVPN-MPLS (including PBB-EVPN)
VPLS E-Tree
Management VPLS
In any specific service, SG-based forwarding and MLD snooping are mutually exclusive. Consequently, MLD snooping uses MAC-based forwarding.
It is not supported in services with:
subscriber management
multicast VLAN Registration
video interface
It is not supported on connected SR OS routers configured with improved-assert.
It is not supported with the following forms of default SAP:
*
*.null
*.*
PIM and IGMP/MLD snooping interaction
When both PIM snooping for IPv4 and IGMP snooping are enabled in the same VPLS service, multicast traffic is forwarded based on the combined multicast forwarding table. When PIM snooping is enabled, IGMP queries are forwarded but not snooped, consequently the IGMP querier needs to be seen either as a PIM neighbor in the VPLS service or the SAP toward it configured as an IGMP Mrouter port.
There is no interaction between PIM snooping for IPv6 and PIM snooping for IPv4/IGMP snooping when all are enabled within the same VPLS service. The configurations of PIM snooping for IPv6 and MLD snooping are mutually exclusive.
When PIM snooping is enabled within a VPLS service, all IP multicast traffic and flooded PIM messages (these include all PIM snooped messages when not in PIM proxy mode and PIM hellos when in PIM proxy mode) are sent to any SAP or SDP binding configured with an IGMP-snooping Mrouter port. This occurs even without IGMP-snooping enabled but is not supported in a BGP-VPLS or M-VPLS service.
Multi-chassis synchronization for Layer 2 snooping states
To achieve a faster failover in scenarios with redundant active/standby routers performing Layer 2 multicast snooping, it is possible to synchronize the snooping state from the active router to the standby router, so that if a failure occurs the standby router has the Layer 2 multicast snooped states and is able to forward the multicast traffic immediately. Without this capability, there would be a longer delay in re-establishing the multicast traffic path because it would wait for the Layer 2 states to be snooped.
Multi-chassis synchronization (MCS) is enabled per peer router and uses a sync-tag, which is configured on the objects requiring synchronization on both of the routers. This allows MCS to map the state of a set of objects on one router to a set of objects on the other router. Specifically, objects relating to a sync-tag on one router are backed up by, or are backing up, the objects using the same sync-tag on the other router (the state is synchronized from the active object on one router to its backup objects on the standby router).
The object type must be the same on both routers; otherwise, a mismatch error is reported. The same sync-tag value can be reused for multiple peer/object combinations, where each combination represents a different set of synchronized objects; however, a sync-tag cannot be configured on the same object to more than one peer.
The sync-tag is configured per port and can relate to a specific set of dot1q or QinQ VLANs on that port, as follows.
CLI syntax:
configure
redundancy
multi-chassis
peer ip-address [create]
sync
port port-id [sync-tag sync-tag] [create]
range encap-range sync-tag sync-tag
For IGMP snooping and PIM snooping for IPv4 to work correctly with MCS on QinQ ports using x.* SAPs, one of the following must be true:
MCS is configured with a sync-tag for the entire port.
The IGMP snooping SAP and the MCS sync-tag must be provisioned with the same Q-tag values when using the range parameter.
IGMP snooping synchronization
MCS for IGMP snooping synchronizes the join/prune state information from IGMP messages received on the related port/VLANs corresponding to their associated sync-tag. It is enabled as follows.
CLI syntax:
configure
redundancy
multi-chassis
peer ip-address [create]
sync
igmp-snooping
IGMP snooping synchronization is supported wherever IGMP snooping is supported (except in EVPN for VXLAN). See IGMP snooping for VPLS for more information. IGMP snooping synchronization is also only supported for the following active/standby redundancy mechanisms:
MC-LAG
MC-Ring
Single-Active Multihoming (EVPN-MPLS and PBB-EVPN I-VPLS)
Single-Active Multihoming (EVPN-MPLS VPRN and IES routed VPLS)
Configuring an Mrouter port under an object that has the synchronization of IGMP snooping states enabled is not recommended. The Mrouter port configuration adds a (*,*) entry into the MFIB, which causes all groups (and IGMP messages) to be sent out of the respective object. In addition, the mrouter-port command causes all IGMP messages on that object to be discarded. However, the (*,*) entry is not synchronized by MCS. Consequently, the Mrouter port could cause the two MCS peers to be forwarding different sets of multicast streams out of the related object when each is active.
MLD snooping synchronization
MCS for MLD snooping is not supported. The command is not blocked for backward-compatibility reasons but has no effect on the system if configured.
PIM snooping for IPv4 synchronization
MCS for PIM snooping for IPv4 synchronizes the neighbor information from PIM hellos and join/prune state information from PIM for IPv4 messages received on the related SAPs and spoke-SDPs corresponding to the sync-tag associated with the related ports and SDPs, respectively. Use the following CLI syntax to enable MCS for PIM snooping for IPv4 synchronization.
CLI syntax:
configure
redundancy
multi-chassis
peer ip-address [create]
sync
pim-snooping [saps] [spoke-sdps]
Any PIM hello state information received over the MCS connection from the peer router takes precedence over locally snooped hello information. This ensures that any PIM hello messages received on the active router that are then flooded, for example through the network backbone, and received over a local SAP or SDP on the standby router are not inadvertently used in the standby router’s VPLS service.
The synchronization of PIM snooping state is only supported for manually configured spoke-SDPs. It is not supported for spoke-SDPs configured within an endpoint.
When synchronizing the PIM state between two spoke-SDPs, if both spoke-SDPs go down, the PIM state is maintained on both until one becomes active to ensure that the PIM state is preserved when a spoke-SDP recovers.
Appropriate actions based on the expiration of PIM-related timers on the standby router are only taken after it has become the active peer for the related object (after a failover).
PIM snooping for IPv4 synchronization is supported wherever PIM snooping for IPv4 is supported, excluding the following services:
BGP-VPLS
VPLS E-Tree
management VPLS
See PIM snooping for VPLS for more details.
PIM snooping for IPv4 synchronization is also only supported for the following active/standby redundancy mechanisms on dual-homed systems:
MC-LAG
BGP multihoming
active/standby pseudowires
single-active multihoming (EVPN-MPLS and PBB-EVPN I-VPLS)
Configuring an Mrouter port under an object that has the synchronization of PIM snooping for IPv4 states enabled is not recommended. The Mrouter port configuration adds a (*,*) entry into the MFIB, which causes all groups (and PIM messages) to be sent out of the respective object. In addition, the mrouter-port command causes all PIM messages on that object to be discarded. However, the (*,*) entry is not synchronized by MCS. Consequently, the Mrouter port could cause the two MCS peers to be forwarding different sets of multicast streams out of the related object when each is active.
VPLS multicast-aware high availability features
The following features are High Availability capable:
Configuration redundancy (all the VPLS multicast-aware configurations can be synchronized to the standby CPM)
Local snooping states as well as states distributed by LDP can be synchronized to the standby CPM.
Operational states can also be synchronized; for example, the operational state of PIM proxy.
RSVP and LDP P2MP LSP for forwarding VPLS/B-VPLS BUM and IP multicast packets
This feature enables the use of a P2MP LSP as the default tree for forwarding Broadcast, Unicast unknown, and Multicast (BUM) packets of a VPLS or B-VPLS instance. The P2MP LSP is referred to in this case as the Inclusive Provider Multicast Service Interface (I-PMSI).
When enabled, this feature relies on BGP Auto-Discovery (BGP-AD) or BGP-VPLS to discover the PE nodes participating in a specified VPLS/B-VPLS instance. The BGP route contains the information required to signal both the point-to-point (P2P) PWs used for forwarding unicast known Ethernet frames and the RSVP P2MP LSP used to forward the BUM frames. The root node signals the P2MP LSP based on an LSP template associated with the I-PMSI at configuration time. The leaf node automatically joins the P2MP LSP that matches the I-PMSI tunnel information discovered via BGP.
If IGMP or PIM snooping are configured on the VPLS instance, multicast packets matching an L2 multicast Forwarding Information Base (FIB) record are also forwarded over the P2MP LSP.
The user enables the use of an RSVP P2MP LSP as the I-PMSI for forwarding Ethernet BUM and IP multicast packets in a VPLS/B-VPLS instance using the following context:
config>service>vpls [b-vpls]>provider-tunnel>inclusive>rsvp>lsp-template p2mp-lsp-template-name
The user enables the use of an LDP P2MP LSP as the I-PMSI for forwarding Ethernet BUM and IP multicast packets in a VPLS instance using the following context:
config>service>vpls [b-vpls]>provider-tunnel>inclusive>mldp
After the user performs a no shutdown under the context of the inclusive node and the expiration of a delay timer, BUM packets are forwarded over an automatically signaled mLDP P2MP LSP or over an automatically signaled instance of the RSVP P2MP LSP specified in the LSP template.
The user can specify that the node is both root and leaf in the VPLS instance:
config>service>vpls [b-vpls]>provider-tunnel>inclusive>root-and-leaf
The root-and-leaf command is required; otherwise, this node behaves as a leaf-only node by default. When the node is leaf only for the I-PMSI of type P2MP RSVP LSP, no PMSI Tunnel Attribute is included in BGP-AD route update messages and, therefore, no RSVP P2MP LSP is signaled, but the node can join an RSVP P2MP LSP rooted at other PE nodes participating in this VPLS/B-VPLS service. The user must still configure an LSP template even if the node is a leaf only. For the I-PMSI of type mLDP, the leaf-only node joins I-PMSI rooted at other nodes it discovered but does not include a PMSI Tunnel Attribute in BGP route update messages. This way, a leaf-only node forwards packets to other nodes in the VPLS/B-VPLS using the point-to-point spoke-SDPs.
BGP-AD (or BGP-VPLS) must have been enabled in this VPLS/B-VPLS instance or the execution of the no shutdown command under the context of the inclusive node is failed and the I-PMSI does not come up.
Any change to the parameters of the I-PMSI, such as disabling the P2MP LSP type or changing the LSP template, requires that the inclusive node be first shut down. The LSP template is configured in MPLS.
If the P2MP LSP instance goes down, VPLS/B-VPLS immediately reverts the forwarding of BUM packets to the P2P PWs. However, the user can restore at any time the forwarding of BUM packets over the P2P PWs by performing a shutdown under the context of the inclusive node.
This feature is supported with VPLS, H-VPLS, B-VPLS, and BGP-VPLS. It is not supported with I-VPLS and R-VPLS.
MPLS entropy label and hash label
The router supports the MPLS entropy label (RFC 6790) and the Flow Aware Transport label (known as the hash label) (RFC 6391). These labels allow LSR nodes in a network to load-balance labeled packets in a much more granular fashion than allowed by simply hashing on the standard label stack. See the 7450 ESS, 7750 SR, 7950 XRS, and VSR MPLS Guide for more information.
The entropy label is supported for LDP VPLS and BGP-AD VPLS, as well as Epipe and Ipipe spoke-SDP termination on VPLS services. To configure insertion of the entropy label on a spoke-SDP or mesh-SDP of a specific service, use the entropy-label command in the spoke-sdp, mesh-sdp, or pw-template contexts. Note that the entropy label is only inserted if the far end of the MPLS tunnel is also entropy-label-capable.
configure service epipe spoke-sdp hash-labelconfigure service ipipe spoke-sdp hash-labelconfigure service pw-template hash-labelconfigure service vpls mesh-sdp hash-labelconfigure service vpls spoke-sdp hash-labelEither the hash label or the entropy label can be configured on one object, but not both.
Routed VPLS and I-VPLS
This section provides information about Routed VPLS (R-VPLS) and I-VPLS. R-VPLS and I-VPLS apply to the 7450 ESS and 7750 SR.
IES or VPRN IP interface binding
For the remainder of this section, R-VPLS and Routed I-VPLS both re described as a VPLS service, and differences are pointed out where applicable.
A standard IP interface within an existing IES or VPRN service context may be bound to a service name. Subscriber and group IP interfaces are not allowed to bind to a VPLS or I-VPLS service context or I-VPLS. A VPLS service only supports binding for a single IP interface.
While an IP interface may only be bound to a single VPLS service, the routing context containing the IP interface (IES or VPRN) may have other IP interfaces bound to other VPLS service contexts of the same type (all VPLS or all I-VPLS). That is, R-VPLS allows the binding of IP interfaces in IES or VPRN services to be bound to VPLS services and Routed I-VPLS allows of IP interfaces in IES or VPRN services to be bound to I-VPLS services.
Assigning a service name to a VPLS service
When a service name is applied to any service context, the name and service ID association is registered with the system. A service name cannot be assigned to more than one service ID.
Special consideration is provided to a service name that is assigned to a VPLS service that has the configure service vpls allow-ip-int-bind command enabled. If a name is applied to the VPLS service while the flag is set, the system scans the existing IES and VPRN services for an IP interface that is bound to the specified service name. If an IP interface is found, the IP interface is attached to the VPLS service associated with the name. Only one interface can be bound to the specified name.
If the allow-ip-int-bind command is not enabled on the VPLS service, the system does not attempt to resolve the VPLS service name to an IP interface. The corresponding IP interface is bound and becomes operational up as soon as the allow-ip-int-bind flag is configured on the VPLS. There is no need to toggle the shutdown/no shutdown command.
If an IP interface is not currently bound to the service name used by the VPLS service, no action is taken at the time of the service name assignment.
Service binding requirements
If the defined service ID is created on the system, the system checks to ensure that the service type is VPLS. If the service type is not VPLS or I-VPLS, service creation is not allowed and the service ID remains undefined within the system.
If the created service type is VPLS, the IP interface is eligible to enter the operationally up state.
Bound service name assignment
If a bound service name is assigned to a service within the system, the system first checks to ensure the service type is VPLS or I-VPLS. Secondly, the system ensures that the service is not already bound to another IP interface through the service ID. If the service type is not VPLS or I-VPLS or the service is already bound to another IP interface through the service ID, the service name assignment fails.
If a single VPLS service ID and service name is assigned to two separate IP interfaces, the VPLS service is not allowed to enter the operationally up state.
Binding a service name to an IP interface
An IP interface within an IES or VPRN service context may be bound to a service name at any time. Only one interface can be bound to a service.
When an IP interface is bound to a service name and the IP interface is administratively up, the system scans for a VPLS service context using the name and takes one of the following actions:
If the name is not currently in use by a service, the IP interface is placed in an operationally down: non-existent service name or inappropriate service type state.
If the name is currently in use by a non-VPLS service or the wrong type of VPLS service, the IP interface is placed in the operationally down: non-existent service name or inappropriate service type state.
If the name is currently in use by a VPLS service without the allow-ip-int-bind flag set, the IP interface is placed in the operationally down: VPLS service allow-ip-int-bind flag not set state. There is no need to toggle the shutdown/no shutdown command.
If the name is currently in use by a valid VPLS service and the allow-ip-int-bind flag is set, the IP interface is eligible to be placed in the operationally up state depending on other operational criteria being met.
Bound service deletion or service name removal
If a VPLS service is deleted while bound to an IP interface, the IP interface enters the Down: non-existent svc-ID operational state. If the IP interface was bound to the VPLS service name, the IP interface enters the Down: non-existent svc-name operational state. No console warning is generated.
If the created service type is VPLS, the IP interface is eligible to enter the operationally up state.
IP interface attached VPLS service constraints
When a VPLS service has been bound to an IP interface through its service name, the service name assigned to the service cannot be removed or changed unless the IP interface is first unbound from the VPLS service name.
A VPLS service that is currently attached to an IP interface cannot be deleted from the system unless the IP interface is unbound from the VPLS service name.
The allow-ip-int-bind flag within an IP interface attached VPLS service cannot be reset. The IP interface must first be unbound from the VPLS service name to reset the flag.
IP interface and VPLS operational state coordination
When the IP interface is successfully attached to a VPLS service, the operational state of the IP interface is dependent upon the operational state of the VPLS service.
The VPLS service remains down until at least one virtual port (SAP, spoke-SDP, or mesh SDP) is operational.
IP interface MTU and fragmentation
The VPLS service is affected by two MTU values: port MTUs and the VPLS service MTU. The MTU on each physical port defines the largest Layer 2 packet (including all DLC headers) that may be transmitted out a port. The VPLS has a service level MTU that defines the largest packet supported by the service. This MTU does not include the local encapsulation overhead for each port (QinQ, Dot1Q, TopQ, or SDP service delineation fields and headers) but does include the remainder of the packet.
As virtual ports are created in the system, the virtual port cannot become operational unless the configured port MTU minus the virtual port service delineation overhead is greater than or equal to the configured VPLS service MTU. Therefore, an operational virtual port is ensured to support the largest packet traversing the VPLS service. The service delineation overhead on each Layer 2 packet is removed before forwarding into a VPLS service. VPLS services do not support fragmentation and must discard any Layer 2 packet larger than the service MTU after the service delineation overhead is removed.
When an IP interface is associated with a VPLS service, the IP-MTU is based on either the administrative value configured for the IP interface or an operational value derived from VPLS service MTU. The operational IP-MTU cannot be greater than the VPLS service MTU minus 14 bytes.
If the configured (administrative) IP-MTU is configured for a value greater than the normalized IP-MTU, based on the VPLS service-MTU, then the operational IP-MTU is reset to equal the normalized IP-MTU value (VPLS service MTU – 14 bytes).
If the configured (administrative) IP-MTU is configured for a value less than or equal to the normalized IP-MTU, based on the VPLS service-MTU, then the operational IP-MTU is set to equal the configured (administrative) IP-MTU value.
Unicast IP routing into a VPLS service
The VPLS service MTU and the IP interface MTU parameters may be changed at any time.
ARP and VPLS FDB interactions
Two address-oriented table entries are used when routing into a VPLS service. An ARP entry is used on the routing side to determine the destination MAC address used by an IP next-hop. In the case where the destination IP address in the routed packet is a host on the local subnet represented by the VPLS instance, the destination IP address is used as the next-hop IP address in the ARP cache lookup. If the destination IP address is in a remote subnet that is reached by another router attached to the VPLS service, the routing lookup returns the local IP address on the VPLS service of the remote router. If the next-hop is not currently in the ARP cache, the system generates an ARP request to determine the destination MAC address associated with the next-hop IP address.
IP routing to all destination hosts associated with the next-hop IP address stops until the ARP cache is populated with an entry for the next-hop. The ARP cache may be populated with a static ARP entry for the next-hop IP address. While dynamically populated ARP entries age out according to the ARP aging timer, static ARP entries never age out.
The second address table entry that affects VPLS routed packets is the MAC destination lookup in the VPLS service context. The MAC associated with the ARP table entry for the IP next-hop may or may not currently be populated in the VPLS Layer 2 FDB table. While the destination MAC is unknown (not populated in the VPLS FDB), the system floods all packets destined for that MAC (routed or bridged) to all virtual ports within the VPLS service context. When the MAC is known (populated in the VPLS FDB), all packets destined for the MAC (routed or bridged) are targeted to the specific virtual port where the MAC has been learned.
As with ARP entries, static MAC entries may be created in the VPLS FDB. Dynamically learned MAC addresses are allowed to age out or be flushed from the VPLS FDB, while static MAC entries always remain associated with a specific virtual port. Dynamic MACs may also be relearned on another VPLS virtual port than the current virtual port in the FDB. In this case, the system automatically moves the MAC FDB entry to the new VPLS virtual port.
The MAC address associated with the R-VPLS IP interface is protected within its VPLS service such that frames received with this MAC address as the source address are discarded. VRRP MAC addresses are not protected in this way.
R-VPLS specific ARP cache behavior
In typical routing behavior, the system uses the IP route table to select the egress interface, and then at the egress forwarding engine, an ARP entry is used to forward the packet to the appropriate Ethernet MAC. With R-VPLS, the egress IP interface may be represented by a multiple egress forwarding engine (wherever the VPLS service virtual ports exist).
To optimize routing performance, the ingress forwarding engine processing has been augmented to perform an ingress ARP lookup to resolve which VPLS MAC address the IP frame must be routed toward. This MAC address may be currently known or unknown within the VPLS FDB. If the MAC is unknown, the packet is flooded by the ingress forwarding engine to all egress forwarding engines where the VPLS service exists. When the MAC is known on a virtual port, the ingress forwarding engine forwards the packet to the correct egress forwarding engine. Ingress routed to VPLS next-hop behavior describes how the ARP cache and MAC FDB entry states interact at ingress and Egress R-VPLS next-hop behavior describes the corresponding egress behavior.
| Next-hop ARP cache entry | Next-hop MAC FDB entry | Ingress behavior |
|---|---|---|
ARP Cache Miss (No Entry) |
Known or Unknown |
Flood to all egress forwarding engines associated with the VPLS or I-VPLS context. |
Unknown |
Flood to all egress forwarding engines associated with the VPLS or I-VPLS context. |
|
Unknown |
Flood to all egress forwarding engines associated with the VPLS for forwarding to all VPLS or I-VPLS virtual ports. |
| Next-hop ARP Cache entry |
Next-hop MAC FDB entry |
Egress behavior |
|---|---|---|
ARP Cache Miss (No Entry) |
Known |
No ARP entry. The MAC address is unknown and the ARP request is flooded out of all virtual ports of the VPLS or I-VPLS instance. |
Unknown |
Request control engine processing the ARP request to transmit out of all virtual ports associated with the VPLS or I-VPLS service. Only the first egress forwarding engine ARP processing request triggers an egress ARP request. |
|
ARP Cache Hit |
Known |
Forward out of specific egress VPLS or I-VPLS virtual ports where MAC has been learned. |
Unknown |
Flood to all egress VPLS or I-VPLS virtual ports on forwarding engine. |
The allow-ip-int-bind VPLS flag
The allow-ip-int-bind flag on a VPLS service context is used to inform the system that the VPLS service is enabled for routing support. The system uses the setting of the flag as a key to determine the types of ports and forwarding planes the VPLS service may span.
The system also uses the flag state to define which VPLS features are configurable on the VPLS service to prevent enabling a feature that is not supported when routing support is enabled.
R-VPLS SAPs only supported on standard Ethernet ports
The allow-ip-int-bind flag is set (routing support enabled) on a VPLS/I-VPLS service. SAPs within the service can be created on standard Ethernet, and CCAG ports. POS is not supported.
LAG port membership constraints
If a LAG has a non-supported port type as a member, a SAP for the routing-enabled VPLS service cannot be created on the LAG. When one or more routing enabled VPLS SAPs are associated with a LAG, a non-supported Ethernet port type cannot be added to the LAG membership.
R-VPLS feature restrictions
When the allow-ip-int-bind flag is set on a VPLS service, the following restrictions apply. The flag also cannot be enabled while any of these features are applied to the VPLS service:
SDPs used in spoke or mesh SDP bindings cannot be configured as GRE.
The VPLS service type cannot be B-VPLS or M-VPLS.
MVR from R-VPLS and to another SAP is not supported.
Enhanced and Basic Subscriber Management (BSM) features cannot be enabled.
Network domain on SDP bindings cannot be enabled.
Per-service hashing is not supported.
BGP-VPLS is not supported.
Ingress queuing for split horizon groups is not supported.
Multiple virtual routers are not supported.
Routed I-VPLS feature restrictions
The following restrictions apply to routed I-VPLS.
Multicast is not supported.
The VC-VLANs are not supported on SDPs.
The force-qtag-forwarding command is not supported.
Control words are not supported on B-VPLS SDPs.
The hash label is not supported on B-VPLS SDPs.
The provider-tunnel is not supported on routed I-VPLS services.
IPv4 and IPv6 multicast routing support
IPv4 and IPv6 multicast routing is supported in a R-VPLS service through its IP interface when the source of the multicast stream is on one side of its IP interface and the receivers are on either side of the IP interface. For example, the source for multicast stream G1 could be on the IP side sending to receivers on both other regular IP interfaces and the VPLS of the R-VPLS service, while the source for group G2 could be on the VPLS side sending to receivers on both the VPLS and IP side of the R-VPLS service.
IPv4 and IPv6 multicast routing is not supported with Multicast VLAN Registration functions or the configuration of a video interface within the associated VPLS service. It is also not supported in a routed I-VPLS service, or for IPv6 multicast in BGP EVPN-MPLS routed VPLS services. Forwarding IPv4 or IPv6 multicast traffic from the R-VPLS IP interface into its VPLS service on a P2MP LSP is not supported.
The IP interface of a R-VPLS supports the configuration of both PIM and IGMP for IPv4 multicast and for both PIM and MLD for IPv6 multicast.
To forward IPv4/IPv6 multicast traffic from the VPLS side of the R-VPLS service to the IP side, the forward-ipv4-multicast-to-ip-int and/or forward-ipv6-multicast-to-ip-int commands must be configured as follows:
configure
service
vpls <service-id>
allow-ip-int-bind
forward-ipv4-multicast-to-ip-int
forward-ipv6-multicast-to-ip-int
exit
exit
exit
exit
Enabling IGMP snooping or MLD snooping in the VPLS service is optional, where supported. If IGMP/MLD snooping is enabled, IGMP/MLD must be enabled on the R-VPLS IP interface in order for multicast traffic to be sent into, or received from, the VPLS service. IPv6 multicast uses MAC-based forwarding; see MAC-based IPv6 multicast forwarding for more information.
If both IGMP/MLD and PIM for IPv4/IPv6 are configured on the R-VPLS IP interface in a redundant PE topology, the associated IP interface on one of the PEs must be configured as both the PIM designated router and the IGMP/MLD querier. This ensures that the multicast traffic is sent into the VPLS service, as IGMP/MLD joins are only propagated to the IP interface if it is the IGMP/MLD querier. An alternative to this is to configure the R-VPLS IP interface in the VPLS service as an Mrouter port, as follows:
configure
service
vpls <service-id>
allow-ip-int-bind
igmp-snooping
mrouter-port
mld-snooping
mrouter-port
exit
exit
exit
exit
This configuration achieves a faster failover in scenarios with redundant routers where multicast traffic is sent to systems on the VPLS side of their R-VPLS services and IGMP/MLD snooping is enabled in the VPLS service. If the active router fails, the remaining router does not have to wait until it sends an IGMP/MLD query into the VPLS service before it starts receiving IGMP/MLD joins and starts sending the multicast traffic into the VPLS service. When the Mrouter port is configured as above, all IGMP/MLD joins (and multicast traffic) are sent to the VPLS service IP interface.
IGMP/MLD snooping should only be enabled when systems, as opposed to PIM routers, are connected to the VPLS service. If IGMP/MLD snooping is enabled when the VPLS service is used for transit traffic for connected PIM routers, the IGMP/MLD snooping would prevent multicast traffic being forwarded between the PIM routers (as PIM snooping is not supported). A workaround would be to configure the VPLS SAPs and spoke-SDPs (and the R-VPLS IP interface) to which the PIM routers are connected as Mrouter ports.
If IMPM is enabled on an FP on which there is a R-VPLS service with forward-ipv4-multicast-to-ip-int or forward-ipv6-multicast-to-ip-int configured, the IPv4/IPv6 multicast traffic received in the VPLS service that is forwarded through the IP interface is IMPM-managed even without IGMP/MLD snooping being enabled. This does not apply to traffic that is only flooded within the VPLS service.
When IPv4/IPv6 multicast traffic is forwarded from a VPLS SAP through the R-VPLS IP interface, the packet count is doubled in the following statistics to represent both the VPLS and IP replication (this reflects the capacity used for this traffic on the ingress queues, which is subject to any configured rates and IMPM capacity management):
Offered queue statistics
IMPM managed statistics
IMPM unmanaged statistics for policed traffic
IPv4 or IPv6 multicast traffic entering the IP side of the R-VPLS service and exiting over a multi-port LAG on the VPLS side of the service is sent on a single link of that egress LAG, specifically the link used for all broadcast, unknown, and multicast traffic.
An example of IPv4/IPv6 multicast in a R-VPLS service is shown in IPv4/IPv6 multicast with a router VPLS service. There are two R-VPLS IP interfaces connected to an IES service with the upper interface connected to a VPLS service in which there is a PIM router and the lower interface connected to a VPLS service in which there is a system using IGMP/MLD.
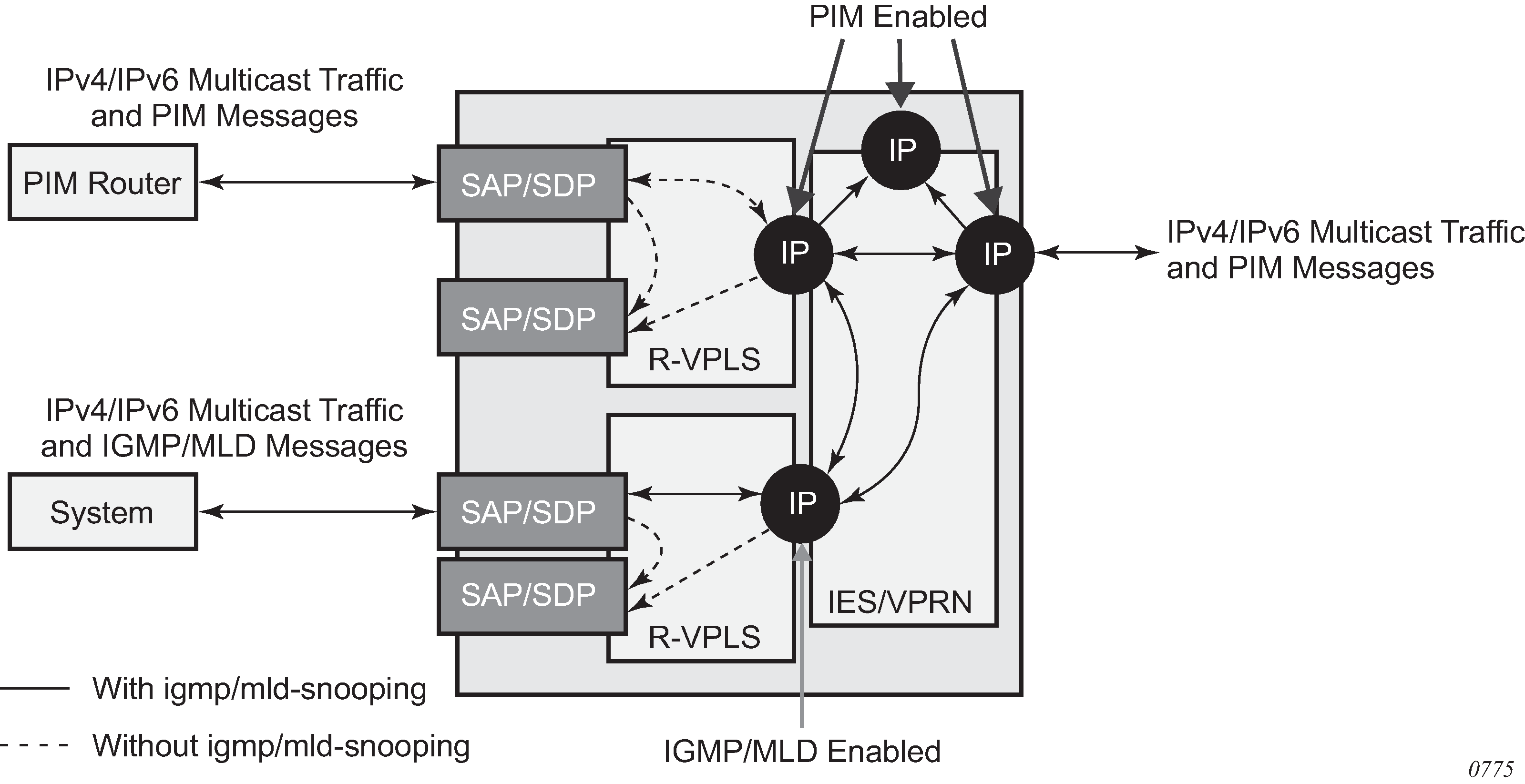
The IPv4/IPv6 multicast traffic entering the IES/VPRN service through the regular IP interface is replicated to both the other regular IP interface and the two R-VPLS interfaces if PIM/IGMP/MLD joins have been received on the respective IP interfaces. This traffic is flooded into both VPLS services unless IGMP/MLD snooping is enabled in the lower VPLS service, in which case it is only sent to the system originating the IGMP/MLD join.
The IPv4/IPv6 multicast traffic entering the upper VPLS service from the connected PIM router is flooded in that VPLS service and, if related joins have been received, forwarded to the regular IP interfaces in the IES/VPRN. It is also be forwarded to the lower VPLS service if an IGMP/MLD join is received on its IP interface, and is flooded in that VPLS service unless IGMP/MLD snooping is enabled.
The IPv4/IPv6 multicast traffic entering the lower VPLS service from the connected system is flooded in that VPLS service, unless IGMP/MLD snooping is enabled, in which case it is only forwarded to SAPs, spoke-SDPs, or the R-VPLS IP interface if joins have been received on them. It is forwarded to the regular IP interfaces in the IES/VPRN service if related joins have been received on those interfaces, and it is also forwarded to the upper VPLS service if a PIM IPv4/IPv6 join is received on its IP interface, this being flooded in that VPLS service.
BGP-AD for R-VPLS support
BGP Auto-Discovery (BGP-AD) for R-VPLS is supported. BGP-AD for LDP VPLS is an already supported framework for automatically discovering the endpoints of a Layer 2 VPN offering an operational model similar to that of an IP VPN.
R-VPLS restrictions
VPLS SAP ingress IP filter override
When an IP Interface is attached to a VPLS or an I-VPLS service context, the VPLS SAP provisioned IP filter for ingress routed packets may be optionally overridden to provide special ingress filtering for routed packets. This allows different filtering for routed packets and non-routed packets. The filter override is defined on the IP interface bound to the VPLS service name. A separate override filter may be specified for IPv4 and IPv6 packet types.
If a filter for a specified packet type (IPv4 or IPv6) is not overridden, the SAP specified filter is applied to the packet (if defined).
IP interface defined egress QoS reclassification
The SAP egress QoS policy defined forwarding class and profile reclassification rules are not applied to egress routed packets. To allow for egress reclassification, a SAP egress QoS policy ID may be optionally defined on the IP interface that is applied to routed packets that egress the SAPs on the VPLS or I-VPLS service associated with the IP interface. Both unicast directed and MAC unknown flooded traffic apply to this rule. Only the reclassification portion of the QoS policy is applied, which includes IP precedence or DSCP classification rules and any defined IP match criteria and their associated actions.
The policers and queues defined within the QoS policy applied to the IP interface are not created on the egress SAPs of the VPLS service. Instead, the QoS policy applied to the egress SAPs defines the egress policers and queues used by both routed and non-routed egress packets. The forwarding class mappings defined in the egress SAP’s QoS policy also defines which policer or queue handles each forwarding class for both routed and non-routed packets.
Remarking for VPLS and routed packets
The remarking of packets to and from an IP interface in an R-VPLS service corresponds to that supported on IP interface, even though the packets ingress or egress a SAP in the VPLS service bound to the IP service. Specifically, this results in the ability to remark the DSCP/prec for these packets.
Packets that ingress and egress SAPs in the VPLS service (not routed through the IP interface) support the regular VPLS QoS and, therefore, the DSCP/prec cannot be remarked.
IPv4 multicast routing
When using IPv4 multicast routing, the following are not supported:
The multicast VLAN registration functions within the associated VPLS service.
The configuration of a video ISA within the associated VPLS service.
The configuration of MFIB-allowed MDA destinations under spoke/mesh SDPs within the associated VPLS service.
The IPv4 multicast routing is not supported in Routed I-VPLS.
The RFC 6037 multicast tunnel termination (including when the system is a bud node) is not supported on the R-VPLS IP interface for multicast traffic received in the VPLS service.
Forwarding of multicast traffic from the VPLS side of the service to the IP interface side of the service is not supported for R-VPLS services that have egress VXLAN VTEPs configured.
R-VPLS supported routing-related protocols
The following protocols are supported on IP interfaces bound to a VPLS service:
BGP
OSPF
ISIS
PIM
IGMP
BFD
VRRP
ARP
DHCP Relay
Spanning tree and split horizon
A R-VPLS context supports all spanning tree and split horizon capabilities that a non-R-VPLS service supports.
VPLS service considerations
This section describes the 7450 ESS, 7750 SR, and 7950 XRS service features and any special capabilities or considerations as they relate to VPLS services.
SAP encapsulations
VPLS services are designed to carry Ethernet frame payloads, so the services can provide connectivity between any SAPs and SDPs that pass Ethernet frames. The following SAP encapsulations are supported on the 7450 ESS, 7750 SR, and 7950 XRS VPLS services:
Ethernet null
Ethernet dot1q
Ethernet QinQ
SONET/SDH BCP-null
SONET/SDH BCP-dot1q
VLAN processing
The SAP encapsulation definition on Ethernet ingress ports defines which VLAN tags are used to determine the service to which the packet belongs:
-
null encapsulation defined on ingress
Any VLAN tags are ignored and the packet goes to a default service for the SAP.
-
dot1q encapsulation defined on ingress
Only the first label is considered.
-
QinQ encapsulation defined on ingress
Both labels are considered. The SAP can be defined with a wildcard for the inner label (for example, ‟100:100.*”). In this situation, all packets with an outer label of 100 are treated as belonging to the SAP. If on the same physical link, there is also an SAP defined with a QinQ encapsulation of 100:100.1, then traffic with 100:1 goes to that SAP and all other traffic with 100 as the first label goes to the SAP with the 100:100.* definition.
In the last two situations above, traffic encapsulated with tags for which there is no definition are discarded.
Ingress VLAN swapping
This feature is supported on VPLS and VLL service where the end-to-end solution is built using two node solutions (requiring SDP connections between the nodes).
In VLAN swapping, only the VLAN ID value is copied to the inner VLAN position. Ethertype of the inner tag is preserved and all consecutive nodes work with that value. Similarly, the dot1p bits value of the outer tag is not preserved.

Ingress VLAN swapping describes the network where, at user access side (DSLAM facing SAPs), every subscriber is represented by several QinQ SAPs with inner-tag encoding service and outer-tag encoding subscriber (DSL line). The aggregation side (BRAS or PE-facing SAPs) is represented by a DSL line number (inner VLAN tag) and DSLAM (outer VLAN tag). The effective operation on the VLAN tag is to drop the inner tag at the access side and push another tag at the aggregation side.
Service auto-discovery using MVRP
IEEE 802.1ak Multiple VLAN Registration Protocol (MVRP) is used to advertise throughout a native Ethernet switching domain one or multiple VLAN IDs to automatically build native Ethernet connectivity for multiple services. These VLAN IDs can be either Customer VLAN IDs (CVID) in an enterprise switching environment, Stacked VLAN IDs (SVID) in a Provider Bridging, QinQ Domain (see the IEEE 802.1ad), or Backbone VLAN IDs (BVID) in a Provider Backbone Bridging (PBB) domain (see the IEEE 802.1ah).
The initial focus of Nokia MVRP implementation is a Service Provider QinQ domain with or without a PBB core. The QinQ access into a PBB core example is used throughout this section to describe the MVRP implementation. With the exception of end-station components, a similar solution can be used to address a QinQ only or enterprise environments.
The components involved in the MVRP control plane are shown in Infrastructure for MVRP exchanges.

All the devices involved are QinQ switches with the exception of the PBB BEB which delimits the QinQ domain and ensures the transition to the PBB core. The circles represent Management VPLS instances interconnected by SAPs to build a native Ethernet switching domain used for MVRP control plane exchanges.
The following high-level steps are involved in auto-discovery of VLAN connectivity in a native Ethernet domain using MVRP:
-
Configure the MVRP infrastructure
-
This requires the configuration of a Management VPLS (M-VPLS) context.
-
MSTP may be used in M-VPLS to provide the loop-free topology over which the MVRP exchanges take place.
-
-
Instantiate related VLAN FDB, trunks in the MVRP, M-VPLS scope
-
The VLAN FDBs (VPLS instances) and associated trunks (SAPs) are instantiated in the same Ethernet switches and on the same ‟trunk ports” as the M-VPLS.
-
There is no need to instantiate data VPLS instances in the BEB. I-VPLS instances and related downward-facing SAPs are provisioned manually because the ISID-to-VLAN association must be configured.
-
-
MVRP activation of service connectivity
When the first two customer UNI and, or PBB end-station SAPs are configured on different Ethernet switches in a specific service context, the MVRP exchanges activate service connectivity.
Configure the MVRP infrastructure using an M-VPLS context
The following provisioning steps apply.
-
Configure the M-VPLS instances in the switches that participate in MVRP control plane.
-
Configure under the M-VPLS the untagged SAPs to be used for MVRP exchanges; only dot1q or qinq ports are accepted for MVRP enabled M-VPLS.
-
Configure the MVRP parameters at M-VPLS instance or SAP level.
Instantiate related VLAN FDBs and trunks in MVRP scope
This requires the configuration in the M-VPLS, under vpls-group, of the following attributes: VLAN ranges, vpls-template and vpls-sap-template bindings. As soon as the VPLS group is enabled, the configured attributes are used to auto-instantiate, on a per-VLAN basis, a VPLS FDB and related SAPs in the switches and on the ‟trunk ports” specified in the M-VPLS context. The trunk ports are ports associated with an M-VPLS SAP not configured as an end-station.
The following procedure is used:
The vpls-template binding is used to instantiate the VPLS instance where the service ID is derived from the VLAN value as per service-range configuration.
The vpls-sap-template binding is used to create dot1q SAPs by deriving from the VLAN value the service delimiter as per service-range configuration.
The above procedure may be used outside of the MVRP context to pre-provision a large number of VPLS contexts that share the same infrastructure and attributes.
The MVRP control of the auto-instantiated services can be enabled using the mvrp-control command under the vpls-group.
If mvrp-control is disabled, the auto-created VPLS instances and related SAPs are ready to forward.
If mvrp-control is enabled, the auto-created VPLS instances are instantiated initially with an empty flooding domain. According to the operator configuration the MVRP exchanges gradually enable service connectivity – between configured SAPs in the data VPLS context.
This also provides protection against operational mistakes that may generate flooding throughout the auto-instantiated VLAN FDBs.
From an MVRP perspective, these SAPs can be either ‟full MVRP” or ‟end-station” interfaces.
A full MVRP interface is a full participant in the local M-VPLS scope as described below.
VLAN attributes received in an MVRP registration on this MVRP interface are declared on all the other full MVRP SAPs in the control VPLS.
VLAN attributes received in an MVRP registration on other full MVRP interfaces in the local M-VPLS context are declared on this MVRP interface.
In an MVRP end-station interface, the attributes registered on that interface have local significance, as described below.
VLAN attributes received in an MVRP registration on this interface are not declared on any other MVRP SAPs in the control VPLS. The attributes are registered only on the local port.
Only locally active VLAN attributes are declared on the end-station interface; VLAN attributes registered on any other MVRP interfaces are not declared on end-station interfaces.
Also defining an M-VPLS SAP as an end-station does not instantiate any objects on the local switch; the command is used just to define which SAP needs to be monitored by MVRP to declare the related VLAN value.
The following example describes the M-VPLS configuration required to auto-instantiate the VLAN FDBs and related trunks in non-PBB switches.
mrp
— no shutdown
— mmrp
— shutdown
— mvrp
— no shutdown
sap 1/1/1:0
— mrp mvrp
— no shutdown
sap 2/1/2:0
— mrp mvrp
— no shutdown
sap 3/1/10:0
— mrp mvrp
— no shutdown
vpls-group 1
— service-range 100-2000
— vpls-template-binding Autovpls1
— sap-template-binding Autosap1
— mvrp-control
— no shutdown
A similar M-VPLS configuration may be used to auto-instantiate the VLAN FDBs and related trunks in PBB switches. The vpls-group command is replaced by the end-station command under the downward-facing SAPs as in the following example.
config>service>vpls control-mvrp m-vpls create customer 1
— [..]
— sap 1/1/1:0
— mvrp mvrp
— endstation-vid-group 1 vlan-id 100-2000
— no shutdown
MVRP activation of service connectivity
As new Ethernet services are activated, UNI SAPs need to be configured and associated with the VLAN IDs (VPLS instances) auto-created using the procedures described in the previous sections. These UNI SAPs may be located in the same VLAN domain or over a PBB backbone. When UNI SAPs are located in different VLAN domains, an intermediate service translation point must be used at the PBB BEB, which maps the local VLAN ID through an I-VPLS SAP to a PBB ISID. This BEB SAP is playing the role of an end-station from an MVRP perspective for the local VLAN domain.
This section discusses how MVRP is used to activate service connectivity between a BEB SAP and a UNI SAP located on one of the switches in the local domain. A similar procedure is used in the case of UNI SAPs configured on two switches located in the same access domain. No end-station configuration is required on the PBB BEB if all the UNI SAPs in a service are located in the same VLAN domain.
The service connectivity instantiation through MVRP is shown in Service instantiation with MVRP - QinQ to PBB example.
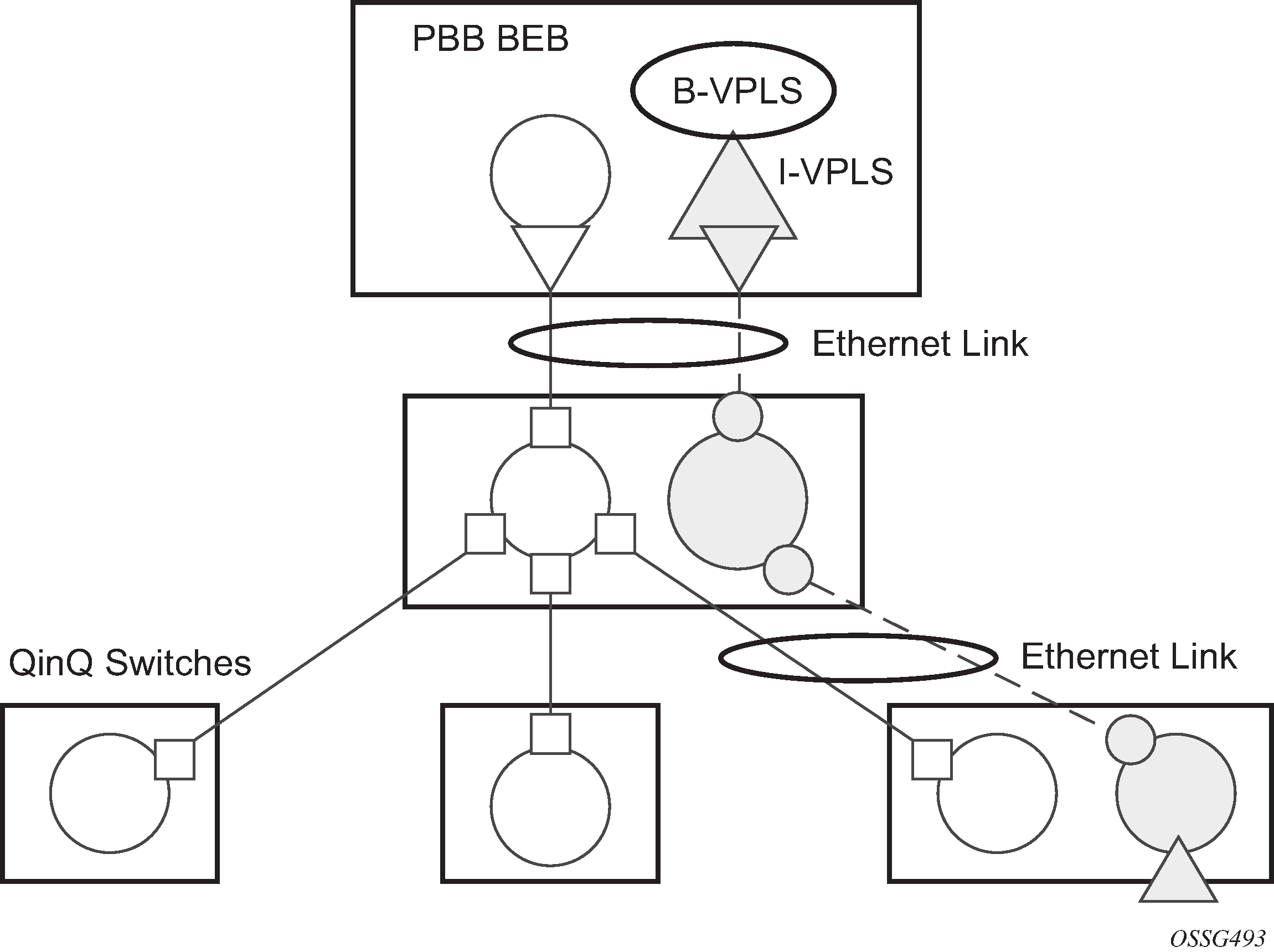
In this example, the UNI and service translation SAPs are configured in the data VPLS represented by the gray circles. This instance and associated trunk SAPs were instantiated using the procedures described in the previous sections. The following are configuration rules:
on the BEB, an I-VPLS SAP must be configured toward the local switching domain (see yellow triangle facing downward in Service instantiation with MVRP - QinQ to PBB example).
on the UNI facing the customer, a ‟customer” SAP is configured on the lower left switch (see yellow triangle facing upward in Service instantiation with MVRP - QinQ to PBB example).
As soon as the first UNI SAP becomes active in the data VPLS on the ES, the associated VLAN value is advertised by MVRP throughout the related M-VPLS context. As soon as the second UNI SAP becomes available on a different switch, or in our example on the PBB BEB, the MVRP proceeds to advertise the associated VLAN value throughout the same M-VPLS. The trunks that experience MVRP declaration and registration in both directions become active, instantiating service connectivity as represented by the big and small yellow circles shown in the figure.
A hold-time parameter (config>service>vpls>mrp>mvrp>hold-time) is provided in the M-VPLS configuration to control when the end-station or last UNI SAP is considered active from an MVRP perspective. The hold-time controls the amount of MVRP advertisements generated on fast transitions of the end-station or UNI SAPs.
If the no hold-time setting is used, the following rules apply:
MVRP stops declaring the VLAN only when the last provisioned UNI SAP associated locally with the service is deleted.
MVRP starts declaring the VLAN as soon as the first provisioned SAP is created in the associated VPLS instance, regardless of the operational state of the SAP.
If a non-zero ‟hold-time” setting is used, the following rules apply:
When a SAP in down state is added, MVRP does not declare the associated VLAN attribute. The attribute is declared immediately when the SAP comes up.
When the SAP goes down, the MVRP waits until ‟hold-time” expiry before withdrawing the declaration.
For QinQ end-station SAPs, only no hold-time setting is allowed.
Only the following PBB Epipe and I-VPLS SAP types are eligible to activate MVRP declarations:
dot1q: for example, 1/1/2:100
qinq or qinq default: for example, 1/1/1:100.1 and respectively 1/1/1:100.*, respectively; the outer VLAN 100 is used as MVRP attribute as long as it belongs to the MVRP range configured for the port
null port and dot1q default cannot be used
Examples of steps required to activate service connectivity for VLAN 100 using MVRP follows.
In the data VPLS instance (VLAN 100) controlled by MVRP, on the QinQ switch, example:
config>service>vpls 100
— sap 9/1/1:10 //UNI sap using CVID 10 as service delimiter
— no shutdown
In I-VPLS on PBB BEB, example:
config>service>vpls 1000 i-vpls
— sap 8/1/2:100 //sap (using MVRP VLAN 100 on endstation port in M-VPLS
— no shutdown
MVRP control plane
MVRP is based on the IEEE 802.1ak MRP specification where STP is the supported method to be used for loop avoidance in a native Ethernet environment. M-VPLS and the associated MSTP (or P-MSTP) control plane provides the loop avoidance component in the Nokia implementation. Nokia MVRP may also be used in a non-MSTP, loop-free topology.
STP-MVRP interaction
MSTP and MVRP interaction table shows the expected interaction between STP (MSTP or P-MSTP) and MVRP.
| Item | M-VPLS service xSTP |
M-VPLS SAP STP | Register/declare data VPLS VLAN on M-VPLS SAP | DSFS (Data SAP Forwarding State) controlled by | Data path forwarding with MVRP enabled controlled by |
|---|---|---|---|---|---|
1 |
(p)MSTP |
Enabled |
Based on M-VPLS SAP’s MSTP forwarding state |
MSTP only |
DSFS and MVRP |
2 |
(p)MSTP |
Disabled |
Based on M-VPLS SAP’s operating state |
— |
MVRP |
3 |
Disabled |
Enabled or Disabled |
Based on M-VPLS SAP’s operating state |
— |
MVRP |
- Running STP in data VPLS instances controlled by MVRP is not allowed.
- Running STP on MVRP-controlled end-station SAPs is not allowed.
Interaction between MVRP and instantiated SAP status
This section describes how MVRP reacts to changes in the instantiated SAP status.
There are a number of mechanisms that may generate operational or admin down status for the SAPs and VPLS instances controlled by MVRP:
Port down
MAC move
Port MTU too small
Service MTU too small
The shutdown of the whole instantiated VPLS or instantiated SAPs is disabled in both VPLS and VPLS SAP templates. The no shutdown option is automatically configured.
In the port down case, the MVRP is also operationally down on the port so no VLAN declaration occurs.
When MAC move is enabled in a data VPLS controlled by MVRP, in case a MAC move happens, one of the instantiated SAPs controlled by MVRP may be blocked. The SAP blocking by MAC move is not reported though to the MVRP control plane. As a result, MVRP keeps declaring and registering the related VLAN value on the control SAPs, including the one that shares the same port with the instantiate SAP blocked by MAC move, as long as MVRP conditions are met. For MVRP, an active control SAP is one that has MVRP enabled and MSTP is not blocking it for the VLAN value on the port. Also in the related data VPLS, one of the two conditions must be met for the declaration of the VLAN value: there must be either a local user SAP or at least one MVRP registration received on one of the control SAPs for that VLAN.
In the last two cases, VLAN attributes get declared or registered even when the instantiated SAP is operationally down, also with the MAC move case.
Using temporary flooding to optimize failover times
MVRP advertisements use the active topology, which may be controlled through loop avoidance mechanisms like MSTP. When the active topology changes as a result of network failures, the time it takes for MVRP to bring up the optimal service connectivity may be added on top of the regular MSTP convergence time. Full connectivity also depends on the time it takes for the system to complete flushing of bad MAC entries.
To minimize the effects of MAC flushing and MVRP convergence, a temporary flooding behavior is implemented. When enabled, the temporary flooding eliminates the time it takes to flush the MAC tables. In the initial implementation, the temporary flooding is initiated only on reception of an STP TCN.
While temporary flooding is active, all the frames received in the extended data VPLS context are flooded while the MAC flush and MVRP convergence take place. The extended data VPLS context comprises all instantiated trunk SAPs regardless of the MVRP activation status. A timer option is also available to configure a fixed period of time, in seconds, during which all traffic is flooded (BUM or known unicast). When the flood-time expires, traffic is delivered according to the regular FDB content. The timer value should be configured to allow auxiliary processes like MAC flush and MVRP to converge. The temporary flooding behavior applies to all VPLS types. MAC learning continues during temporary flooding. Temporary flooding behavior is enabled using the temp-flooding command under config>service>vpls or config>service>template>vpls-template contexts and is supported in VPLS regardless of whether MVRP is enabled.
For temporary flooding in VPLS, the following rules apply:
If discard-unknown is enabled, there is no temporary flooding.
Temporary flooding while active applies also to static MAC entries; after the MAC FDB is flushed it reverts back to the static MAC entries.
If MAC learning is disabled, fast or temporary flooding is still enabled.
Temporary flooding is not supported in B-VPLS context when MMRP is enabled. The use of a flood-time procedure provides a better procedure for this kind of environment.
VPLS E-Tree services
This section describes VPLS E-Tree services.
VPLS E-Tree services overview
The VPLS E-Tree service offers a VPLS service with Root and Leaf designated access SAPs and SDP bindings, which prevent any traffic flow from leaf to leaf directly. With a VPLS E-Tree, the split horizon group capability is inherent for leaf SAPs (or SDP bindings) and extends to all the remote PEs that are part of the same VPLS E-Tree service. This feature is based on IETF Draft draft-ietf-l2vpn-vpls-pe-etree.
A VPLS E-Tree service may support an arbitrary number of leaf access (leaf-ac) interfaces, root access (root-ac) interfaces, and root-leaf tagged (root-leaf-tag) interfaces. Leaf-ac interfaces are supported on SAPs and SDP binds and can only communicate with root-ac interfaces (also supported on SAPs and SDP binds). Leaf-ac to leaf-ac communication is not allowed. Root-leaf-tag interfaces (supported on SAPs and SDP bindings) are tagged with root and leaf VIDs to allow remote VPLS instances to enforce the E-Tree forwarding.
E-Tree service shows a network with two root-ac interfaces and several leaf-ac SAPs (also could be SDPs). The figure indicates two VIDs in use to each service within the service with no restrictions on the AC interfaces. The service guarantees no leaf-ac to leaf-ac traffic.
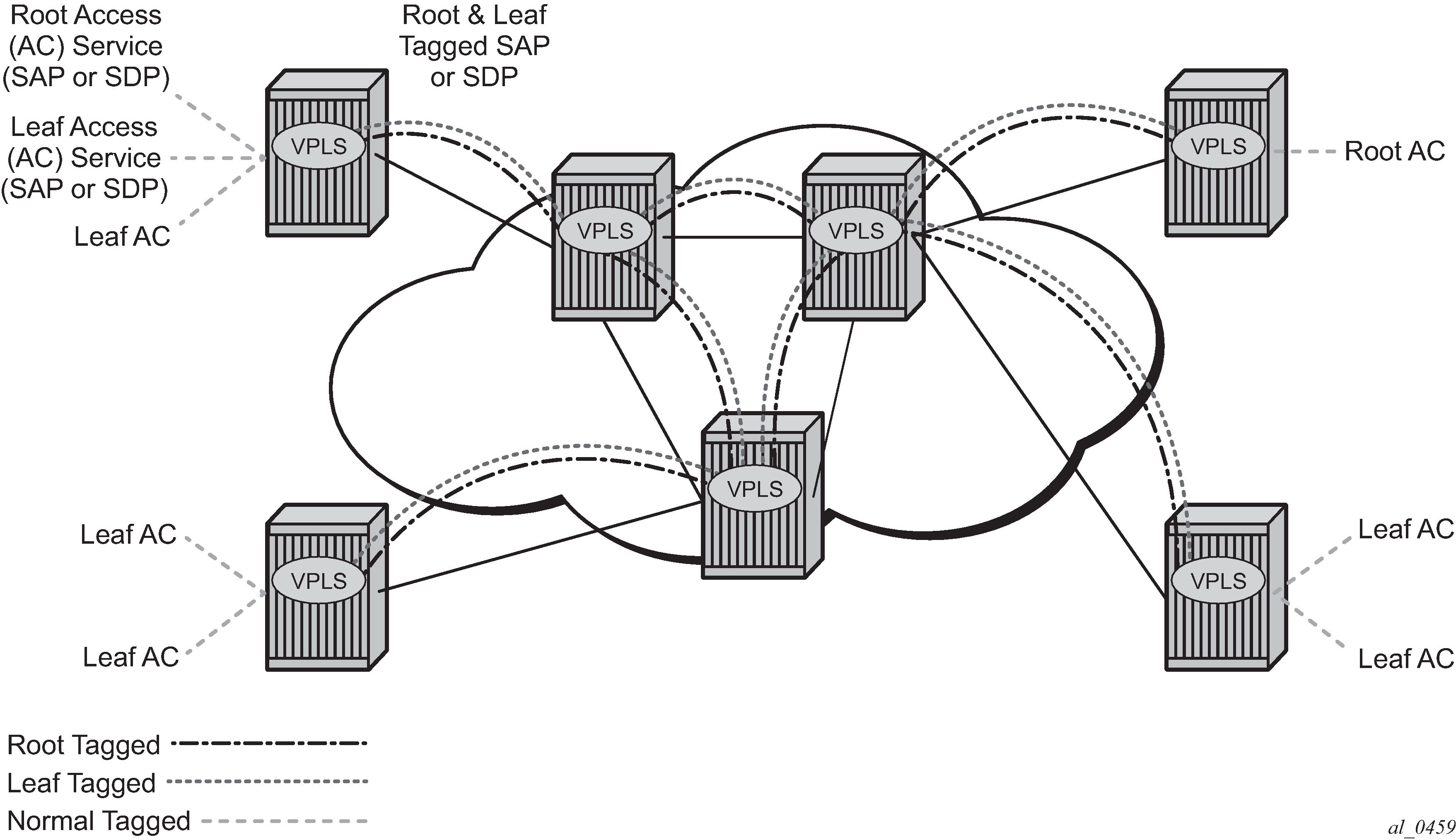
Leaf-ac and root-ac SAPs
Mapping PE model to VPLS service shows the terminology used for E-Tree in IETF Draft draft-ietf-l2vpn-vpls-pe-etree and a mapping to SR OS terms.
An Ethernet service access SAP is characterized as either a leaf-ac or a root-ac for a VPLS E-Tree service. As far as SR OS is concerned, these are normal SAPs with either no tag (Null), priority tag, or dot1q or QinQ encapsulation on the frame. Functionally, a root-ac is a normal SAP and does not need to be differentiated from the regular SAPs except that it is associated with a root behavior in a VPLS E-Tree.
Leaf-ac SAPs have restrictions; for example, a SAP configured for a leaf-ac can never send frames to another leaf-ac directly (local) or through a remote node. Leaf-ac SAPs on the same VPLS instance behave as if they are part of a split horizon group (SHG) locally. Leaf-ac SAPs that are on other nodes need to have the traffic marked as originating ‟from a Leaf” in the context of the VPLS service when carried on PWs and SAPs with tags (VLANs).
Root-ac SAPs on the same VPLS can talk to any root-ac or leaf-ac.

Leaf-ac and root-ac SDP binds
Untagged SDP binds for access can also be designated as root-ac or leaf-ac. This type of E-Tree interface is required for devices that do not support E-Tree, such as the 7210 SAS, to enable them to be connected with pseudowires. Such devices are root or leaf only and do not require having a tagged frame with a root or leaf indication.
Root-leaf-tag SAPs
Support on root-leaf-tag SAPs requires that the outer VID is overloaded to indicate root and leaf. To support the SR service model for a SAP, the ability to send and receive two different tags on a single SAP has been added. Leaf and root tagging dot1q shows the behavior when a root-ac and leaf-ac exchange traffic over a root-leaf-tag SAP. Although the figure shows two SAPs connecting VPLS instances 1 and 2, the CLI shows a single SAP with the format:
sap 2/1/1:25 root-leaf-tag leaf-tag 26 create

The root-leaf-tag SAP performs all of the operations for egress and ingress traffic for both tags (root and leaf):
When receiving a frame, the outer tag VID is compared against the configured root or leaf VIDs and the frame forwarded accordingly.
When transmitting, the system adds a root VLAN (in the outer tag) on frames with an internal indication of Root, and a leaf VLAN on frames with an internal indication of Leaf.
Root-leaf-tag SDP binds
Typically, in a VPLS environment over MPLS, mesh and spoke-SDP binds interconnect the local VPLS instances to remote PEs. To support VPLS E-Tree, the root and leaf traffic is sent over the SDP bind using a fixed VLAN tag value. The SR OS implementation uses a fixed VLAN ID 1 for root and fixed VLAN ID 2 for leaf. The root and leaf tags are considered a global value and signaling is not supported. The vc-type on root-leaf-tag SDP binds must be VLAN. The vlan-vc-tag command is blocked in root-leaf-tag SDP-binds.
Leaf and root tagging PW shows the behavior when leaf-ac or root-ac interfaces exchange traffic over a root-leaf-tag SDP-binding.

Interaction between VPLS E-Tree services and other features
As a general rule, any CPM-generated traffic is always root traffic (STP, OAM, and so on) and any received control plane frame is marked with a root/leaf indication based on which E-Tree interface it arrived at. Some other particular feature interactions are as follows:
ETH-CFM and E-Tree have limited conjunctive uses. ETH-CFM allows the operator to verify connectivity between the various endpoints of the service as well as execute troubleshooting and performance gathering functions. Continuity Checking, ETH-CC, is a method by which endpoints are configured and messages are passed between them at regular configured intervals. When CCM-enabled MEPs are configured, all MEPs in the same maintenance association, the grouping typically along the service lines, must know about every other endpoint in the service. This is the main principle behind continuity verification (all endpoints in communication).
Although the maintenance points configured within the E-Tree service adhere to the forwarding rules of the Leaf and the Root, local population of the MEP database used by the ETH-CFM function may make it appear that the forwarding plane is broken when it is not. All MEPs that are locally configured within a service are automatically added to the local MEP database. However, because of the Leaf and Root forwarding rules, not all of these MEPs can receive the required peer CCM-message to avoid CCM Defect conditions. It is suggested, when deploying CCM enabled MEPs in an E-Tree configuration, these CCM-enabled MEPs are configured on Root entities. If Leaf access requires CCM verification, then down MEPs in separate maintenance associations should be configured. This consideration is only for operators who need to deploy CCM in E-Tree environments. No other ETH-CFM tools query or use this database.
Legacy OAM commands (cpe-ping, mac-ping, mac-trace, mac-populate, and mac-purge) are not supported in E-Tree service contexts. Although some configuration may result in normal behavior for some commands, not all commands or configurations yield the expected results. Standards-based ETH-CFM tools should be used in place of the proprietary legacy OAM command set.
IGMP and PIM snooping for IPv4 work on VPLS E-Tree services. Routers should use root-ac interfaces so the multicast traffic can be delivered properly.
xSTP is supported in VPLS E-Tree services; however, when configuring STP in VPLS E-Tree services, the following considerations apply:
STP must be carefully used so that STP does not block needless objects.
xSTP is not aware of the leaf-to-leaf topology; for example, for leaf-to-leaf traffic, even if there is no loop in the forwarding plane, xSTP may block leaf-ac SAPs or SDP binds.
Because xSTP is not aware of the root-leaf topology either, root ports may end up blocked before leaf interfaces.
When xSTP is used as an access redundancy mechanism, Nokia recommends connecting the dual-homed device to the same type of E-Tree AC, to avoid unexpected forwarding behaviors when xSTP converges.
Redundancy mechanisms such as MC-LAG, SDP bind end-points, or BGP-MH are fully supported on VPLS E-Tree services. However, eth-tunnel SAPs or eth-ring control SAPs are not supported on VPLS E-Tree services.
Configuring a VPLS service with CLI
This section provides information to configure a VPLS service using the command line interface.
Basic configuration
The following fields require specific input (there are no defaults) to configure a basic VPLS service:
Customer ID (for more information see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide)
For a local service, configure two SAPs, specifying local access ports and encapsulation values.
For a distributed service, configure a SAP and an SDP for each far-end node.
The following example shows a configuration of a local VPLS service on ALA-1.
*A:ALA-1>config>service>vpls# info
----------------------------------------------
...
vpls 9001 customer 6 create
description "Local VPLS"
stp
shutdown
exit
sap 1/2/2:0 create
description "SAP for local service"
exit
sap 1/1/5:0 create
description "SAP for local service"
exit
no shutdown
----------------------------------------------
*A:ALA-1>config>service>vpls#
The following example shows a configuration of a distributed VPLS service between ALA-1, ALA-2, and ALA-3.
*A:ALA-1>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
shutdown
description "This is a distributed VPLS."
exit
...
----------------------------------------------
*A:ALA-1>config>service#
*A:ALA-2>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
sap 1/1/5:16 create
description "VPLS SAP"
exit
spoke-sdp 2:22 create
exit
mesh-sdp 8:750 create
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-2>config>service#
*A:ALA-3>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
sap 1/1/3:33 create
description "VPLS SAP"
exit
spoke-sdp 2:22 create
exit
mesh-sdp 8:750 create
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-3>config>service#
Common configuration tasks
This task provides a brief overview of the actions that must be performed to configure both local and distributed VPLS services and provides the CLI commands.
For VPLS services the procedure to be followed is presented below:
- Associate VPLS service with a customer ID.
-
Define SAPs:
-
Select nodes and ports
-
Optionally, select the following:
-
QoS policies other than the default (configured in config>qos context)
-
filter policies (configured in config>filter context)
-
accounting policy (configured in config>log context)
-
-
- Associate SDPs for (distributed services).
- Modify STP default parameters (optional) (see VPLS and spanning tree protocol)
- Enable the service.
Configuring VPLS components
Use the CLI syntax displayed in the following sections to configure VPLS components.
Creating a VPLS service
Use the following CLI syntax to create a VPLS service.
CLI syntax:
config>service# vpls service-id [customer customer-id] [vpn vpn-id] [m-vpls] [b-vpls | i-vpls] [create]
description description-string
no shutdown
The following example shows a VPLS configuration:
*A:ALA-1>config>service>vpls# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
exit
...
----------------------------------------------
*A:ALA-1>config>service>vpls#
Enabling MMRP
When the Multiple MAC Registration Protocol (MMRP) is enabled in the B-VPLS, it advertises the presence of the I-VPLS instances associated with this B-VPLS.
The following example shows a configuration with MMRP enabled.
*A:PE-B>config>service# info
----------------------------------------------
vpls 11 customer 1 vpn 11 i-vpls create
backbone-vpls 100:11
exit
stp
shutdown
exit
sap 1/5/1:11 create
exit
sap 1/5/1:12 create
exit
no shutdown
exit
vpls 100 customer 1 vpn 100 b-vpls create
service-mtu 2000
stp
shutdown
exit
mrp
flood-time 10
no shutdown
exit
sap 1/5/1:100 create
exit
spoke-sdp 3101:100 create
exit
spoke-sdp 3201:100 create
exit
no shutdown
exit
----------------------------------------------
*A:PE-B>config>service#
Because I-VPLS 11 is associated with B-VPLS 100, MMRP advertises the group B-MAC 01:1e:83:00:00:0b) associated with I-VPLS 11 through a declaration on all the B-SAPs and B-SDPs. If the remote node also declares an I-VPLS 11 associated with its B-VPLS 10, then this results in a registration for the group B-MAC. This also creates the MMRP multicast tree (MFIB entries). In this case, sdp 3201:100 is connected to a remote node that declares the group B-MAC.
The following show commands display the current MMRP information for this scenario:
*A:PE-C# show service id 100 mrp
-------------------------------------------------------------------------------
MRP Information
-------------------------------------------------------------------------------
Admin State : Up Failed Register Cnt: 0
Max Attributes : 1023 Attribute Count : 1
Attr High Watermark: 95% Attr Low Watermark : 90%
Flood Time : 10
-------------------------------------------------------------------------------
*A:PE-C# show service id 100 mmrp mac
-------------------------------------------------------------------------------
SAP/SDP MAC Address Registered Declared
-------------------------------------------------------------------------------
sap:1/5/1:100 01:1e:83:00:00:0b No Yes
sdp:3101:100 01:1e:83:00:00:0b No Yes
sdp:3201:100 01:1e:83:00:00:0b Yes Yes
-------------------------------------------------------------------------------
*A:PE-C# show service id 100 sdp 3201:100 mrp
-------------------------------------------------------------------------------
Sdp Id 3201:100 MRP Information
-------------------------------------------------------------------------------
Join Time : 0.2 secs Leave Time : 3.0 secs
Leave All Time : 10.0 secs Periodic Time : 1.0 secs
Periodic Enabled : false
Rx Pdus : 7 Tx Pdus : 23
Dropped Pdus : 0
Rx New Event : 0 Rx Join-In Event : 6
Rx In Event : 0 Rx Join Empty Evt : 1
Rx Empty Event : 0 Rx Leave Event : 0
Tx New Event : 0 Tx Join-In Event : 4
Tx In Event : 0 Tx Join Empty Evt : 19
Tx Empty Event : 0 Tx Leave Event : 0
-------------------------------------------------------------------------------
SDP MMRP Information
-------------------------------------------------------------------------------
MAC Address Registered Declared
-------------------------------------------------------------------------------
01:1e:83:00:00:0b Yes Yes
-------------------------------------------------------------------------------
Number of MACs=1 Registered=1 Declared=1
-------------------------------------------------------------------------------
*A:PE-C#
*A:PE-C# show service id 100 mfib
===============================================================================
Multicast FIB, Service 100
===============================================================================
Source Address Group Address Sap/Sdp Id Svc Id Fwd/Blk
-------------------------------------------------------------------------------
* 01:1E:83:00:00:0B sdp:3201:100 Local Fwd
-------------------------------------------------------------------------------
Number of entries: 1
===============================================================================
*A:PE-C#
Enabling MAC move
The mac-move feature is useful to protect against undetected loops in your VPLS topology as well as the presence of duplicate MACs in a VPLS service. For example, if two clients in the VPLS have the same MAC address, the VPLS experiences a high re-learn rate for the MAC and shuts down the SAP or spoke-SDP when the threshold is exceeded.
Use the following CLI syntax to configure mac-move parameters.
CLI syntax:
config>service# vpls service-id [customer customer-id] [vpn vpn-id] [m-vpls]
— mac-move
— primary-ports
— spoke-sdp
— cumulative-factor
— exit
— secondary-ports
— spoke-sdp
— sap
— exit
— move-frequency frequency
— retry-timeout timeout
— no shutdown
The following example shows a mac-move configuration:
*A:ALA-2009>config>service>vpls>mac-move# show service id 500 mac-move
===============================================================================
Service Mac Move Information
===============================================================================
Service Id : 500 Mac Move : Enabled
Primary Factor : 4 Secondary Factor : 2
Mac Move Rate : 2 Mac Move Timeout : 10
Mac Move Retries : 3
-------------------------------------------------------------------------------
SAP Mac Move Information: 2/1/3:501
-------------------------------------------------------------------------------
Admin State : Up Oper State : Down
Flags : RelearnLimitExceeded
Time to come up : 1 seconds Retries Left : 1
Mac Move : Blockable Blockable Level : Tertiary
-------------------------------------------------------------------------------
SAP Mac Move Information: 2/1/3:502
-------------------------------------------------------------------------------
Admin State : Up Oper State : Up
Flags : None
Time to RetryReset: 267 seconds Retries Left : none
Mac Move : Blockable Blockable Level : Tertiary
-------------------------------------------------------------------------------
SDP Mac Move Information: 21:501
-------------------------------------------------------------------------------
Admin State : Up Oper State : Up
Flags : None
Time to RetryReset: never Retries Left : 3
Mac Move : Blockable Blockable Level : Secondary
-------------------------------------------------------------------------------
SDP Mac Move Information: 21:502
-------------------------------------------------------------------------------
Admin State : Up Oper State : Down
Flags : RelearnLimitExceeded
Time to come up : never Retries Left : none
Mac Move : Blockable Blockable Level : Tertiary
===============================================================================
*A:*A:ALA-2009>config>service>vpls>mac-move#
Configuring STP bridge parameters in a VPLS
Modifying some of the Spanning Tree Protocol parameters allows the operator to balance STP between resiliency and speed of convergence extremes. Modifying particular parameters, as follows, must be done in the constraints of the following two formulas:
2 x (Bridge_Forward_Delay - 1.0 seconds) ≥ Bridge_Max_Age Bridge_Max_Age ≥ 2 x (Bridge_Hello0_Time + 1.0 seconds)
The following STP parameters can be modified at VPLS level:
STP always uses the locally configured values for the first three parameters (Admin State, Mode, and Priority).
For the parameters Max Age, Forward Delay, Hello Time, and Hold Count, the locally configured values are only used when this bridge has been elected root bridge in the STP domain; otherwise, the values received from the root bridge are used. The exception to this rule is: when STP is running in RSTP mode, the Hello Time is always taken from the locally configured parameter. The other parameters are only used when running mode MSTP.
Bridge STP admin state
The administrative state of STP at the VPLS level is controlled by the shutdown command.
When STP on the VPLS is administratively disabled, any BPDUs are forwarded transparently through the 7450 ESS, 7750 SR, or 7950 XRS. When STP on the VPLS is administratively enabled, but the administrative state of a SAP or spoke-SDP is down, BPDUs received on such a SAP or spoke-SDP are discarded.
CLI syntax:
config>service>vpls service-id# stp
no shutdown
Mode
To be compatible with the different iterations of the IEEE 802.1D standard, the 7450 ESS, 7750 SR, and 7950 XRS support several variants of the Spanning Tree protocol:
- rstp
- Rapid Spanning Tree Protocol (RSTP) compliant with IEEE 802.1D-2004 - default mode.
- dot1w
- compliant with IEEE 802.1w
- comp-dot1w
- operation as in RSTP but backwards compatible with IEEE 802.1w (this mode was introduced for interoperability with some MTU types)
- mstp
- compliant with the Multiple Spanning Tree Protocol specified in IEEE 802.1Q REV/D5.0-09/2005. This mode of operation is only supported in an M-VPLS
- pmstp
- compliant with the Multiple Spanning Tree Protocol specified in IEEE 802.1Q REV/D3.0-04/2005 but with some changes to make it backwards compatible to 802.1Q 2003 edition and IEEE 802.1w
See section Spanning tree operating modes for more information about these modes.
CLI syntax:
config>service>vpls service-id# stp
mode {rstp | comp-dot1w | dot1w | mstp}
The default variant of the Spanning Tree protocol is rstp.
Bridge priority
The bridge-priority command is used to populate the priority portion of the bridge ID field within outbound BPDUs (the most significant 4 bits of the bridge ID). It is also used as part of the decision process when determining the best BPDU between messages received and sent. When running MSTP, this is the bridge priority used for the CIST.
All values are truncated to multiples of 4096, conforming with IEEE 802.1t and 802.1D-2004.
CLI syntax:
config>service>vpls service-id# stp
priority bridge-priority
- Range
- 1 to 65535
- Default
- 32768
- Restore Default
- no priority
Max age
The max-age command indicates how many hops a BPDU can traverse the network starting from the root bridge. The message age field in a BPDU transmitted by the root bridge is initialized to 0. Each other bridge takes the message_age value from BPDUs received on their root port and increment this value by 1. Therefore, the message_age reflects the distance from the root bridge. BPDUs with a message age exceeding max-age are ignored.
STP uses the max-age value configured in the root bridge. This value is propagated to the other bridges by the BPDUs. The default value of max-age is 20. This parameter can be modified within a range of 6 to 40, limited by the standard STP parameter interaction formulas.
CLI syntax:
config>service>vpls service-id# stp
max-age max-info-age
- Range
- 6 to 40 seconds
- Default
- 20 seconds
- Restore Default
- no max-age
Forward delay
RSTP, as defined in the IEEE 802.1D-2004 standards, normally transitions to the forwarding state by a handshaking mechanism (rapid transition), without any waiting times. If handshaking fails (for example, on shared links, as follows), the system falls back to the timer-based mechanism defined in the original STP (802.1D-1998) standard.
A shared link is a link with more than two Ethernet bridges (for example, a shared 10/100BaseT segment). The port-type command is used to configure a link as point-to-point or shared (see section SAP link type).
For timer-based transitions, the 802.1D-2004 standard defines an internal variable forward-delay, which is used in calculating the default number of seconds that a SAP or spoke-SDP spends in the discarding and learning states when transitioning to the forwarding state. The value of the forward-delay variable depends on the STP operating mode of the VPLS instance:
In RSTP mode, but only when the SAP or spoke-SDP has not fallen back to legacy STP operation, the value configured by the hello-time command is used.
In all other situations, the value configured by the forward-delay command is used.
CLI syntax:
config>service>vpls service-id# stp
forward-delay seconds
- Range
- 4 to 30 seconds
- Default
- 15 seconds
- Restore Default
- no forward-delay
Hello time
The hello-time command configures the Spanning Tree Protocol (STP) hello time for the Virtual Private LAN Service (VPLS) STP instance.
The seconds parameter defines the default timer value that controls the sending interval between BPDU configuration messages by this bridge, on ports where this bridge assumes the designated role.
The active hello time for the spanning tree is determined by the root bridge (except when the STP is running in RSTP mode, then the hello time is always taken from the locally configured parameter).
The configured hello-time value can also be used to calculate the bridge forward delay; see Forward delay.
CLI syntax:
config>service>vpls service-id# stp
hello-time hello-time
- Range
- 1 to 10 seconds
- Default
- 2 seconds
- Restore Default
- no hello-time
Hold count
The hold-count command configures the peak number of BPDUs that can be transmitted in a period of one second.
CLI syntax:
config>service>vpls service-id# stp
hold-count count-value
- Range
- 1 to 10
- Default
- 6
- Restore Default
- no hold-count
MST instances
You can create up to 15 mst-instances. They can range from 1 to 4094. By changing path-cost and priorities, you can ensure that each instance forms its own tree within the region, therefore ensure that different VLANs follow different paths.
You can assign non-overlapping VLAN ranges to each instance. VLANs that are not assigned to an instance are implicitly assumed to be in instance 0, which is also called the CIST. This CIST cannot be deleted or created.
The parameters that can be defined per instance are mst-priority and vlan-range.
- mst-priority
- the bridge-priority for this specific mst-instance. It follows the same rules as bridge-priority. For the CIST, the bridge-priority is used.
- vlan-range
- the VLANs are mapped to this specific mst-instance. If no VLAN-ranges are defined in any mst-instances, then all VLANs are mapped to the CIST.
MST max hops
The mst-max-hops command defines the maximum number of hops the BPDU can traverse inside the region. Outside the region, max-age is used.
MST name
The MST name defines the name that the operator gives to a region. Together with MST revision and the VLAN to mst-instance mapping, it forms the MST configuration identifier. Two bridges that have the same MST configuration identifier form a region if they exchange BPDUs.
MST revision
The MST revision together with MST-name and VLAN to MST-instance mapping define the MST configuration identifier. Two bridges that have the same MST configuration identifier form a region if they exchange BPDUs.
Configuring GSMP parameters
The following parameters must be configured in order for GSMP to function:
One or more GSMP sessions
One or more ANCP policies
For basic subscriber management only, ANCP static maps
For enhanced subscriber management only, associate subscriber profiles with ANCP policies
Use the following CLI syntax to configure GSMP parameters.
CLI syntax:
config>service>vpls# gsmp
— group name [create]
— ancp
— dynamic-topology-discover
— oam
— description description-string
— hold-multiplier multiplier
— keepalive seconds
— neighbor ip-address [create]
— description v
— local-address ip-address
— priority-marking dscp dscp-name
— priority-marking prec ip-prec-value
— [no] shutdown
— [no] shutdown
— [no] shutdown
This example shows a GSMP group configuration.
A:ALA-48>config>service>vpls>gsmp# info
----------------------------------------------
group "group1" create
description "test group config"
neighbor 10.10.10.104 create
description "neighbor1 config"
local-address 10.10.10.103
no shutdown
exit
no shutdown
exit
no shutdown
----------------------------------------------
A:ALA-48>config>service>vpls>gsmp#
Configuring a VPLS SAP
A default QoS policy is applied to each ingress and egress SAP. Additional QoS policies can be configured in the config>qos context. There are no default filter policies. Filter policies are configured in the config>filter context and must be explicitly applied to a SAP. Use the following CLI syntax to create:
Local VPLS SAPs
To configure a local VPLS service, enter the sap sap-id command twice with different port IDs in the same service configuration.
The following example shows a local VPLS configuration:
*A:ALA-1>config>service# info
----------------------------------------------
...
vpls 90001 customer 6 create
description "Local VPLS"
stp
shutdown
exit
sap 1/2/2:0 create
description "SAP for local service"
exit
sap 1/1/5:0 create
description "SAP for local service"
exit
no shutdown
exit
----------------------------------------------
*A:ALA-1>config>service#
*A:ALA-1>config>service# info
----------------------------------------------
vpls 1150 customer 1 create
fdb-table-size 1000
fdb-table-low-wmark 5
fdb-table-high-wmark 80
local-age 60
stp
shutdown
exit
sap 1/1/1:1155 create
exit
sap 1/1/2:1150 create
exit
no shutdown
exit
----------------------------------------------
*A:ALA-1>config>service#
Distributed VPLS SAPs
To configure a distributed VPLS service, you must configure service entities on originating and far-end nodes. You must use the same service ID on all ends (for example, create a VPLS service ID 9000 on ALA-1, ALA-2, and ALA-3). A distributed VPLS consists of a SAP on each participating node and an SDP bound to each participating node.
For SDP configuration information, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide. For SDP binding information, see Configuring SDP bindings.
The following example shows a configuration of VPLS SAPs configured for ALA-1, ALA-2, and ALA-3.
*A:ALA-1>config>service# info
--------------------------------------------
...
vpls 9000 customer 6 vpn 750 create
description "Distributed VPLS services."
stp
shutdown
exit
sap 1/2/5:0 create
description "VPLS SAP"
multi-service-site "West"
exit
exit
...
--------------------------------------------
*A:ALA-1>config>service#
*A:ALA-2>config>service# info
--------------------------------------------
...
vpls 9000 customer 6 vpn 750 create
description "Distributed VPLS services."
stp
shutdown
exit
sap 1/1/2:22 create
description "VPLS SAP"
multi-service-site "West"
exit
exit
...
--------------------------------------------
*A:ALA-2>config>service#
*A:ALA-3>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 vpn 750 create
description "Distributed VPLS services."
stp
shutdown
exit
sap 1/1/3:33 create
description "VPLS SAP"
multi-service-site "West"
exit
exit
...
----------------------------------------------
*A:ALA-3>config>service#
Configuring SAP-specific STP parameters
When a VPLS has STP enabled, each SAP within the VPLS has STP enabled by default. Subsequent sections describe SAP-specific STP parameters in detail.
SAP STP administrative state
The administrative state of STP within a SAP controls how BPDUs are transmitted and handled when received. The allowable states are:
SAP admin up
The default administrative state is up for STP on a SAP. BPDUs are handled in the normal STP manner on a SAP that is administratively up.
SAP admin down
An administratively down state allows a service provider to prevent a SAP from becoming operationally blocked. BPDUs do not originate out the SAP toward the customer.
If STP is enabled on VPLS level, but disabled on the SAP, received BPDUs are discarded. Discarding the incoming BPDUs allows STP to continue to operate normally within the VPLS service while ignoring the down SAP. The specified SAP is always in an operationally forwarding state.
Note: The administratively down state allows a loop to form within the VPLS.
CLI syntax:
config>service>vpls>sap>stp#
[no] shutdown
- Range
- shutdown or no shutdown
- Default
- no shutdown (SAP admin up)
SAP virtual port number
The virtual port number uniquely identifies a SAP within configuration BPDUs. The internal representation of a SAP is unique to a system and has a reference space much bigger than the 12 bits definable in a configuration BPDU. STP takes the internal representation value of a SAP and identifies it with its own virtual port number that is unique to every other SAP defined on the VPLS. The virtual port number is assigned at the time that the SAP is added to the VPLS.
Because the order in which SAPs are added to the VPLS is not preserved between reboots of the system, the virtual port number may change between restarts of the STP instance. To achieve consistency after a reboot, the virtual port number can be specified explicitly.
CLI syntax:
config>service>vpls>sap# stp
port-num number
- Range
- 1 to 2047
- Default
- (automatically generated)
- Restore Default
- no port-num
SAP priority
SAP priority allows a configurable tie-breaking parameter to be associated with a SAP. When configuration BPDUs are being received, the configured SAP priority is used in some circumstances to determine whether a SAP is designated or blocked. These are the values used for CIST when running MSTP for the 7450 ESS or 7750 SR.
In traditional STP implementations (802.1D-1998), this field is called the port priority and has a value of 0 to 255. This field is coupled with the port number (0 to 255 also) to create a 16-bit value. In the latest STP standard (802.1D-2004), only the upper 4 bits of the port priority field are used to encode the SAP priority. The remaining 4 bits are used to extend the port ID field into a 12-bit virtual port number field. The virtual port number uniquely references a SAP within the STP instance. See SAP virtual port number for more information about the virtual port number.
STP computes the actual SAP priority by taking the configured priority value and masking out the lower four bits. The result is the value that is stored in the SAP priority parameter. For example, if a value of 0 was entered, masking out the lower 4 bits would result in a parameter value of 0. If a value of 255 was entered, the result would be 240.
The default value for SAP priority is 128. This parameter can be modified within a range of 0 to 255; 0 being the highest priority. Masking causes the values actually stored and displayed to be 0 to 240, in increments of 16.
CLI syntax:
config>service>vpls>sap>stp#
priority stp-priority
- Range
- 0 to 255 (240 largest value, in increments of 16)
- Default
- 128
- Restore Default
- no priority
SAP path cost
The SAP path cost is used by STP to calculate the path cost to the root bridge. The path cost in BPDUs received on the root port is incremented with the configured path cost for that SAP. When BPDUs are sent out of other egress SAPs, the newly calculated root path cost is used. These are the values used for CIST when running MSTP.
STP suggests that the path cost is defined as a function of the link bandwidth. Because SAPs are controlled by complex queuing dynamics, in the 7450 ESS, 7750 SR, and 7950 XRS the STP path cost is a purely static configuration.
The default value for SAP path cost is 10. This parameter can be modified within a range of 1 to 65535; 1 being the lowest cost.
CLI syntax:
config>service>vpls>sap>stp#
path-cost sap-path-cost
- Range
- 1 to 200000000
- Default
- 10
- Restore Default
- no path-cost
SAP edge port
The SAP edge-port command is used to reduce the time it takes a SAP to reach the forwarding state when the SAP is on the edge of the network, and therefore has no further STP bridge to handshake with.
The edge-port command is used to initialize the internal OPER_EDGE variable. At any time, when OPER_EDGE is false on a SAP, the normal mechanisms are used to transition to the forwarding state (see Forward delay). When OPER_EDGE is true, STP assumes that the remote end agrees to transition to the forwarding state without actually receiving a BPDU with an agreement flag set.
The OPER_EDGE variable is dynamically set to false if the SAP receives BPDUs (the configured edge-port value does not change). The OPER_EDGE variable is dynamically set to true if auto-edge is enabled and STP concludes there is no bridge behind the SAP.
When STP on the SAP is administratively disabled, and re-enabled, the OPER_EDGE is re-initialized to the value configured for edge-port.
Valid values for SAP edge-port are enabled and disabled, with disabled being the default.
CLI syntax:
config>service>vpls>sap>stp#
[no] edge-port
- Default
- no edge-port
SAP auto edge
The SAP edge-port command is used to instruct STP to dynamically decide whether the SAP is connected to another bridge.
If auto-edge is enabled, and STP concludes there is no bridge behind the SAP, the OPER_EDGE variable is dynamically set to true. If auto-edge is enabled, and a BPDU is received, the OPER_EDGE variable is dynamically set to true (see SAP edge port).
Valid values for SAP auto-edge are enabled and disabled with enabled being the default.
CLI syntax:
config>service>vpls>sap>stp#
[no] auto-edge
- Default
- auto-edge
SAP link type
The SAP link-type parameter instructs STP on the maximum number of bridges behind this SAP. If there is only a single bridge, transitioning to forwarding state is based on handshaking (fast transitions). If more than two bridges are connected by a shared media, their SAPs should all be configured as shared, and timer-based transitions are used.
Valid values for SAP link-type are shared and pt-pt with pt-pt, being the default.
CLI syntax:
config>service>vpls>sap>stp#
link-type {pt-pt | shared}
- Default
- link-type pt-pt
- Restore Default
- no link-type
STP SAP operational states
The operational state of STP within a SAP controls how BPDUs are transmitted and handled when received. Subsequent sections describe STP SAP operational states.
Operationally disabled
Operationally disabled is the normal operational state for STP on a SAP in a VPLS that has any of the following conditions:
VPLS state administratively down
SAP state administratively down
SAP state operationally down
If the SAP enters the operationally up state with the STP administratively up and the SAP STP state is up, the SAP transitions to the STP SAP discarding state.
When, during normal operation, the router detects a downstream loop behind a SAP or spoke-SDP, BPDUs can be received at a very high rate. To recover from this situation, STP transitions the SAP to disabled state for the configured forward-delay duration.
Operationally discarding
A SAP in the discarding state only receives and sends BPDUs, building the local correct STP state for each SAP while not forwarding actual user traffic. The duration of the discarding state is described in section Forward delay.
Operationally learning
The learning state allows population of the MAC forwarding table before entering the forwarding state. In this state, no user traffic is forwarded.
Operationally forwarding
Configuration BPDUs are sent out of a SAP in the forwarding state. Layer 2 frames received on the SAP are source learned and destination forwarded according to the FDB. Layer 2 frames received on other forwarding interfaces and destined for the SAP are also forwarded.
SAP BPDU encapsulation state
IEEE 802.1d (referred as Dot1d) and Cisco’s per VLAN Spanning Tree (PVST) BPDU encapsulations are supported on a per-SAP basis for the 7450 ESS and 7750 SR. STP is associated with a VPLS service like PVST is associated per VLAN. The main difference resides in the Ethernet and LLC framing and a type-length-value (TLV) field trailing the BPDU.
Spoke SDP BPDU encapsulation states shows differences between Dot1d and PVST Ethernet BPDU encapsulations based on the interface encap-type field.
Each SAP has a Read-Only operational state that shows which BPDU encapsulation is currently active on the SAP. The states are:
dot1d
This state specifies that the switch is currently sending IEEE 802.1d standard BPDUs. The BPDUs are tagged or non-tagged based on the encapsulation type of the egress interface and the encapsulation value defined in the SAP. A SAP defined on an interface with encapsulation type dot1q continues in the dot1d BPDU encapsulation state until a PVST encapsulated BPDU is received, in which case, the SAP converts to the PVST encapsulation state. Each received BPDU must be properly IEEE 802.1q tagged if the interface encapsulation type is defined as dot1q. PVST BPDUs is silently discarded if received when the SAP is on an interface defined with a null encapsulation type.
PVST
This state specifies that the switch is currently sending proprietary encapsulated BPDUs. PVST BPDUs are only supported on Ethernet interfaces with the encapsulation type set to dot1q. The SAP continues in the PVST BPDU encapsulation state until a dot1d encapsulated BPDU is received, in which case, the SAP reverts to the dot1d encapsulation state. Each received BPDU must be properly IEEE 802.1q tagged with the encapsulation value defined for the SAP. PVST BPDUs are silently discarded if received when the SAP is on an interface defined with a null encapsulation type.
Dot1d is the initial and only SAP BPDU encapsulation state for SAPs defined on Ethernet interface with encapsulation type set to null.
Each transition between encapsulation types optionally generates an alarm that can be logged and optionally transmitted as an SNMP trap on the 7450 ESS or 7750 SR.
Configuring VPLS SAPs with split horizon
To configure a VPLS service with a split horizon group, add the split-horizon-group parameter when creating the SAP. Traffic arriving on a SAP within a split horizon group is not copied to other SAPs in the same split horizon group.
The following example shows a VPLS configuration with split horizon enabled:
*A:ALA-1>config>service# info
----------------------------------------------
...
vpls 800 customer 6001 vpn 700 create
description "VPLS with split horizon for DSL"
stp
shutdown
exit
sap 1/1/3:100 split-horizon-group DSL-group1 create
description "SAP for residential bridging"
exit
sap 1/1/3:200 split-horizon-group DSL-group1 create
description "SAP for residential bridging"
exit
split-horizon-group DSL-group1
description "Split horizon group for DSL"
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-1>config>service#
Configuring MAC learning protection
To configure MAC learning protection, configure split horizon, MAC protection, and SAP parameters on the 7450 ESS or 7750 SR.
The following example shows a VPLS configuration with split horizon enabled:
A:ALA-48>config>service>vpls# info
----------------------------------------------
description "IMA VPLS"
split-horizon-group "DSL-group1" create
restrict-protected-src
restrict-unprotected-dst
exit
mac-protect
mac ff:ff:ff:ff:ff:ff
exit
sap 1/1/9:0 create
ingress
scheduler-policy "SLA1"
qos 100 shared-queuing
exit
egress
scheduler-policy "SLA1"
filter ip 10
exit
restrict-protected-src
arp-reply-agent
host-connectivity-verify source-ip 10.144.145.1
exit
...
----------------------------------------------
A:ALA-48>config>service>vpls#
Configuring SAP subscriber management parameters
Use the following CLI syntax to configure subscriber management parameters on a VPLS service SAP on the 7450 ESS and 7750 SR. The policies and profiles that are referenced in the def-sla-profile, def-sub-profile, non-sub-traffic, and sub-ident-policy commands must already be configured in the config>subscr-mgmt context.
CLI syntax:
config>service>vpls service-id
— sap sap-id [split-horizon-group group-name]
— sub-sla-mgmt
— def-sla-profile default-sla-profile-name
— def-sub-profile default-subscriber-profile-name
— mac-da-hashing
— multi-sub-sap [number-of-sub]
— no shutdown
— single-sub-parameters
— non-sub-traffic sub-profile sub-profile-name sla-profile sla-profile-name [subscriber sub-ident-string]
— profiled-traffic-only
— sub-ident-policy sub-ident-policy-name
The following example shows a subscriber management configuration:
A:ALA-48>config>service>vpls#
----------------------------------------------
description "Local VPLS"
stp
shutdown
exit
sap 1/2/2:0 create
description "SAP for local service"
sub-sla-mgmt
def-sla-profile "sla-profile1"
sub-ident-policy "SubIdent1"
exit
exit
sap 1/1/5:0 create
description "SAP for local service"
exit
no shutdown
----------------------------------------------
A:ALA-48>config>service>vpls#
MSTP control over Ethernet tunnels
When MSTP is used to control VLANs, a range of VLAN IDs is normally used to specify the VLANs to be controlled on the 7450 ESS and 7750 SR.
If an Ethernet tunnel SAP is to be controlled by MSTP, the Ethernet tunnel SAP ID needs to be within the VLAN range specified under the mst-instance.
vpls 400 customer 1 m-vpls create
stp
mode mstp
mst-instance 111 create
vlan-range 1-100
exit
mst-name "abc"
mst-revision 1
no shutdown
exit
sap 1/1/1:0 create // untagged
exit
sap eth-tunnel-1 create
exit
no shutdown
exit
vpls 401 customer 1 create
stp
shutdown
exit
sap 1/1/1:12 create
exit
sap eth-tunnel-1:12 create
// Ethernet tunnel SAP ID 12 falls within the VLAN
// range for mst-instance 111
eth-tunnel
path 1 tag 1000
path 8 tag 2000
exit
exit
no shutdown
exit
Configuring SDP bindings
VPLS provides scaling and operational advantages. A hierarchical configuration eliminates the need for a full mesh of VCs between participating devices. Hierarchy is achieved by enhancing the base VPLS core mesh of VCs with access VCs (spoke) to form two tiers. Spoke SDPs are generally created between Layer 2 switches and placed at the Multi-Tenant Unit (MTU). The PE routers are placed at the service provider's Point of Presence (POP). Signaling and replication overhead on all devices is considerably reduced.
A spoke SDP is treated like the equivalent of a traditional bridge port where flooded traffic received on the spoke-SDP is replicated on all other ‟ports” (other spoke and mesh SDPs or SAPs) and not transmitted on the port it was received (unless a split horizon group was defined on the spoke-SDP; see section Configuring VPLS spoke SDPs with split horizon).
A spoke SDP connects a VPLS service between two sites and, in its simplest form, could be a single tunnel LSP. A set of ingress and egress VC labels are exchanged for each VPLS service instance to be transported over this LSP. The PE routers at each end treat this as a virtual spoke connection for the VPLS service in the same way as the PE-MTU connections. This architecture minimizes the signaling overhead and avoids a full mesh of VCs and LSPs between the two metro networks.
A mesh SDP bound to a service is logically treated like a single bridge ‟port” for flooded traffic where flooded traffic received on any mesh SDP on the service is replicated to other ‟ports” (spoke SDPs and SAPs) and not transmitted on any mesh SDPs.
A VC-ID can be specified with the SDP-ID. The VC-ID is used instead of a label to identify a virtual circuit. The VC-ID is significant between peer SRs on the same hierarchical level. The value of a VC-ID is conceptually independent from the value of the label or any other datalink specific information of the VC.
SDPs — unidirectional tunnels shows an example of a distributed VPLS service configuration of spoke and mesh SDPs (unidirectional tunnels) between routers and MTUs.
Configuring overrides on service SAPs
The following output shows a service SAP queue override configuration example:
*A:ALA-48>config>service>vpls>sap# info
----------------------------------------------
...
exit
ingress
scheduler-policy "SLA1"
scheduler-override
scheduler "sched1" create
parent weight 3 cir-weight 3
exit
exit
policer-control-policy "SLA1-p"
policer-control-override create
max-rate 50000
exit
qos 100 multipoint-shared
queue-override
queue 1 create
rate 1500000 cir 2000
exit
exit
policer-override
policer 1 create
rate 10000
exit
exit
exit
egress
scheduler-policy "SLA1"
policer-control-policy "SLA1-p"
policer-control-override create
max-rate 60000
exit
qos 100
queue-override
queue 1 create
adaptation-rule pir max cir max
exit
exit
policer-override
policer 1 create
mbs 2000 kilobytes
exit
exit
filter ip 10
exit
----------------------------------------------
*A:ALA-48>config>service>vpls>sap#
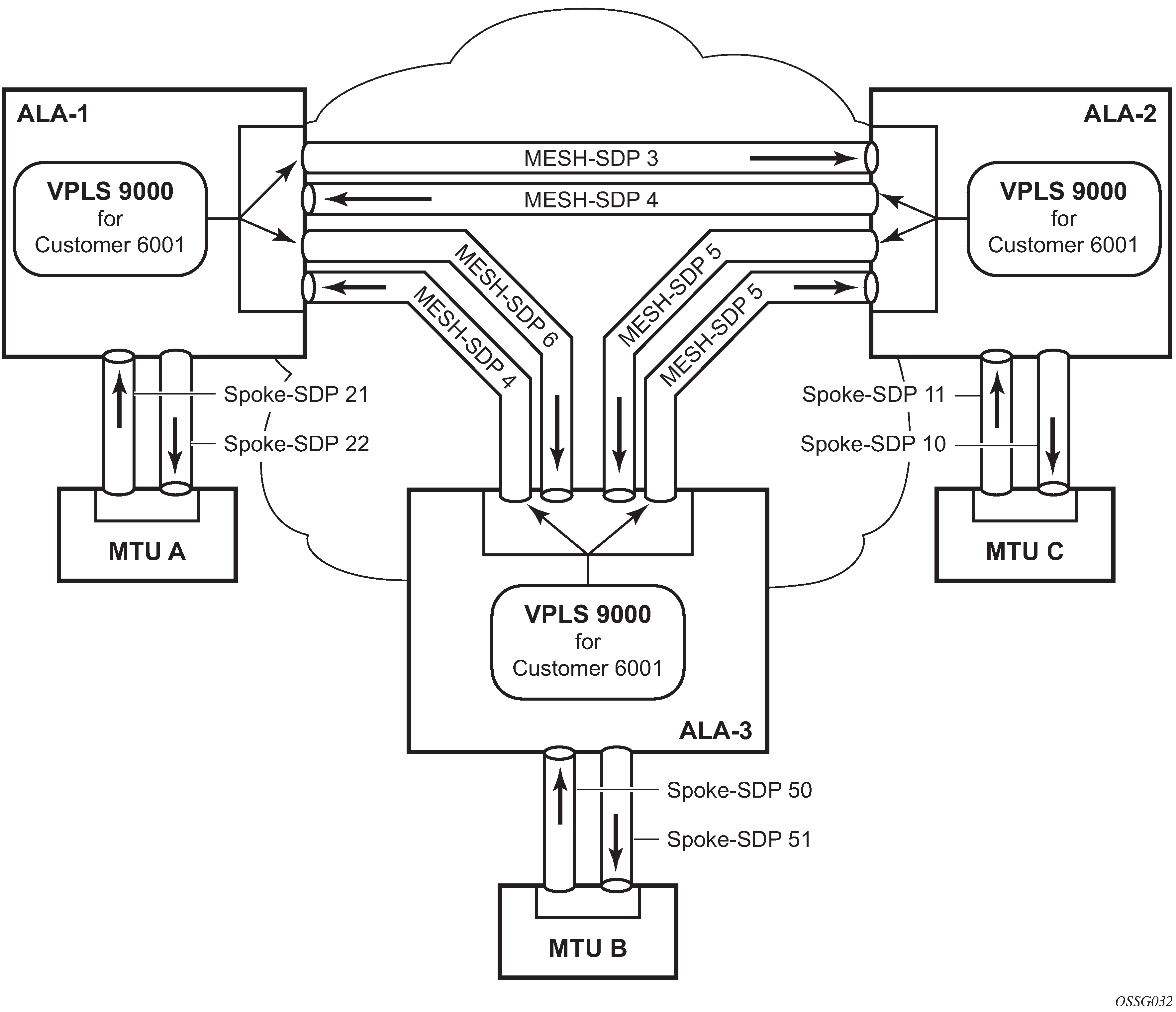
Use the following CLI syntax to create mesh or spoke-SDP bindings with a distributed VPLS service. SDPs must be configured before binding. For information about creating SDPs, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide.
Use the following CLI syntax to configure mesh SDP bindings.
CLI syntax:
config>service# vpls service-id
— mesh-sdp sdp-id[:vc-id] [vc-type {ether | vlan}]
— egress
— filter {ip ip-filter-id|mac mac-filter-id}
— mfib-allowed-mda-destinations
— mda mda-id
— vc-label egress-vc-label
— ingress
— filter {ip ip-filter-id|mac mac-filter-id}
— vc-label ingress-vc-label
— no shutdown
— static-mac ieee-address
— vlan-vc-tag 0..4094
Use the following CLI syntax to configure spoke-SDP bindings.
CLI syntax:
config>service# vpls service-id
— spoke-sdp sdp-id:vc-id [vc-type {ether | vlan}] [split-horizon-group group-name]
— egress
— filter {ip ip-filter-id|mac mac-filter-id}
— vc-label egress-vc-label
— ingress
— filter {ip ip-filter-id|mac mac-filter-id}
— vc-label ingress-vc-label
— limit-mac-move[non-blockable]
— vlan-vc-tag 0..4094
— no shutdown
— static-mac ieee-address
— stp
— path-cost stp-path-cost
— priority stp-priority
— no shutdown
— vlan-vc-tag [0..4094]
The following examples show SDP binding configurations for ALA-1, ALA-2, and ALA-3 for VPLS service ID 9000 for customer 6:
*A:ALA-1>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
sap 1/2/5:0 create
exit
spoke-sdp 2:22 create
exit
mesh-sdp 5:750 create
exit
mesh-sdp 7:750 create
exit
no shutdown
exit
----------------------------------------------
*A:ALA-1>config>service#
*A:ALA-2>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
sap 1/1/2:22 create
exit
spoke-sdp 2:22 create
exit
mesh-sdp 5:750 create
exit
mesh-sdp 7:750 create
exit
no shutdown
exit
----------------------------------------------
*A:ALA-3>config>service# info
----------------------------------------------
...
vpls 9000 customer 6 create
description "This is a distributed VPLS."
stp
shutdown
exit
sap 1/1/3:33 create
exit
spoke-sdp 2:22 create
exit
mesh-sdp 5:750 create
exit
mesh-sdp 7:750 create
exit
no shutdown
exit
----------------------------------------------
*A:ALA-3>config>service#
Configuring spoke-SDP specific STP parameters
When a VPLS has STP enabled, each spoke-SDP within the VPLS has STP enabled by default. Subsequent sections describe spoke-SDP specific STP parameters in detail.
Spoke SDP STP administrative state
The administrative state of STP within a spoke SDP controls how BPDUs are transmitted and handled when received. The allowable states are:
spoke-sdp admin up
The default administrative state is up for STP on a spoke SDP. BPDUs are handled in the normal STP manner on a spoke SDP that is administratively up.
spoke-sdp admin down
An administratively down state allows a service provider to prevent a spoke SDP from becoming operationally blocked. BPDUs do not originate out the spoke SDP toward the customer.
If STP is enabled on VPLS level, but disabled on the spoke SDP, received BPDUs are discarded. Discarding the incoming BPDUs allows STP to continue to operate normally within the VPLS service while ignoring the down spoke SDP. The specified spoke SDP is always in an operationally forwarding state.
Note: The administratively down state allows a loop to form within the VPLS.
CLI syntax:
config>service>vpls>spoke-sdp>stp#
[no] shutdown
- Range
- shutdown or no shutdown
- Default
- no shutdown (spoke-SDP admin up)
Spoke SDP virtual port number
The virtual port number uniquely identifies a spoke SDP within configuration BPDUs. The internal representation of a spoke SDP is unique to a system and has a reference space much bigger than the 12 bits definable in a configuration BPDU. STP takes the internal representation value of a spoke SDP and identifies it with its own virtual port number that is unique to every other spoke-SDP defined on the VPLS. The virtual port number is assigned at the time that the spoke SDP is added to the VPLS.
Because the order in which spoke SDPs are added to the VPLS is not preserved between reboots of the system, the virtual port number may change between restarts of the STP instance. To achieve consistency after a reboot, the virtual port number can be specified explicitly.
CLI syntax:
config>service>vpls>spoke-sdp# stp
port-num number
- Range
- 1 to 2047
- Default
- automatically generated
- Restore Default
- no port-num
Spoke SDP priority
Spoke SDP priority allows a configurable tiebreaking parameter to be associated with a spoke SDP. When configuration BPDUs are being received, the configured spoke-SDP priority is used in some circumstances to determine whether a spoke SDP is designated or blocked.
In traditional STP implementations (802.1D-1998), this field is called the port priority and has a value of 0 to 255. This field is coupled with the port number (0 to 255 also) to create a 16-bit value. In the latest STP standard (802.1D-2004), only the upper 4 bits of the port priority field are used to encode the spoke SDP priority. The remaining 4 bits are used to extend the port ID field into a 12-bit virtual port number field. The virtual port number uniquely references a spoke SDP within the STP instance. See Spoke SDP virtual port number for more information about the virtual port number.
STP computes the actual spoke SDP priority by taking the configured priority value and masking out the lower four bits. The result is the value that is stored in the spoke SDP priority parameter. For instance, if a value of 0 was entered, masking out the lower 4 bits would result in a parameter value of 0. If a value of 255 was entered, the result would be 240.
The default value for spoke SDP priority is 128. This parameter can be modified within a range of 0 to 255; 0 being the highest priority. Masking causes the values actually stored and displayed to be 0 to 240, in increments of 16.
CLI syntax:
config>service>vpls>spoke-sdp>stp#
priority stp-priority
- Range
- 0 to 255 (240 largest value, in increments of 16)
- Default
- 128
- Restore Default
- no priority
Spoke SDP path cost
The spoke SDP path cost is used by STP to calculate the path cost to the root bridge. The path cost in BPDUs received on the root port is incremented with the configured path cost for that spoke-SDP. When BPDUs are sent out of other egress spoke SDPs, the newly calculated root path cost is used.
STP suggests that the path cost is defined as a function of the link bandwidth. Because spoke SDPs are controlled by complex queuing dynamics, the STP path cost is a purely static configuration.
The default value for spoke SDP path cost is 10. This parameter can be modified within a range of 1 to 200000000 (1 is the lowest cost).
CLI syntax:
config>service>vpls>spoke-sdp>stp#
path-cost stp-path-cost
- Range
- 1 to 200000000
- Default
- 10
- Restore Default
- no path-cost
Spoke SDP edge port
The spoke SDP edge-port command is used to reduce the time it takes a spoke-SDP to reach the forwarding state when the spoke-SDP is on the edge of the network, and therefore has no further STP bridge to handshake with.
The edge-port command is used to initialize the internal OPER_EDGE variable. At any time, when OPER_EDGE is false on a spoke-SDP, the normal mechanisms are used to transition to the forwarding state (see Forward delay). When OPER_EDGE is true, STP assumes that the remote end agrees to transition to the forwarding state without actually receiving a BPDU with an agreement flag set.
The OPER_EDGE variable is dynamically set to false if the spoke SDP receives BPDUs (the configured edge-port value does not change). The OPER_EDGE variable is dynamically set to true if auto-edge is enabled and STP concludes there is no bridge behind the spoke SDP.
When STP on the spoke SDP is administratively disabled and re-enabled, the OPER_EDGE is re-initialized to the spoke-SDP configured for edge-port.
Valid values for spoke SDP edge-port are enabled and disabled, with disabled being the default.
CLI syntax:
config>service>vpls>spoke-sdp>stp#
[no] edge-port
- Default
- no edge-port
Spoke SDP auto edge
The spoke SDP edge-port command is used to instruct STP to dynamically decide whether the spoke SDP is connected to another bridge.
If auto-edge is enabled, and STP concludes there is no bridge behind the spoke SDP, the OPER_EDGE variable is dynamically set to true. If auto-edge is enabled, and a BPDU is received, the OPER_EDGE variable is dynamically set to true (see Spoke SDP edge port).
Valid values for spoke SDP auto-edge are enabled and disabled, with enabled being the default.
CLI syntax:
config>service>vpls>spoke-sdp>stp#
[no] auto-edge
- Default
- auto-edge
Spoke SDP link type
The spoke SDP link-type command instructs STP on the maximum number of bridges behind this spoke SDP. If there is only a single bridge, transitioning to forwarding state is based on handshaking (fast transitions). If more than two bridges are connected by a shared media, their spoke SDPs should all be configured as shared, and timer-based transitions are used.
Valid values for spoke SDP link-type are shared and pt-pt, with pt-pt being the default.
CLI syntax:
config>service>vpls>spoke-sdp>stp#
link-type {pt-pt|shared}
- Default
- link-type pt-pt
- Restore Default
- no link-type
Spoke SDP STP operational states
The operational state of STP within a spoke SDP controls how BPDUs are transmitted and handled when received. Subsequent sections describe spoke SDP operational states.
Operationally disabled
Operationally disabled is the normal operational state for STP on a spoke SDP in a VPLS that has any of the following conditions:
VPLS state administratively down
Spoke SDP state administratively down
Spoke SDP state operationally down
If the spoke SDP enters the operationally up state with the STP administratively up and the spoke SDP STP state is up, the spoke-SDP transitions to the STP spoke SDP discarding state.
When, during normal operation, the router detects a downstream loop behind a spoke SDP, BPDUs can be received at a very high rate. To recover from this situation, STP transitions the spoke SDP to a disabled state for the configured forward-delay duration.
Operationally discarding
A spoke-SDP in the discarding state only receives and sends BPDUs, building the local correct STP state for each spoke-SDP while not forwarding actual user traffic. The duration of the discarding state is described in section Forward delay.
Operationally learning
The learning state allows population of the MAC forwarding table before entering the forwarding state. In this state, no user traffic is forwarded.
Operationally forwarding
Configuration BPDUs are sent out of a spoke-SDP in the forwarding state. Layer 2 frames received on the spoke-SDP are source learned and destination forwarded according to the FDB. Layer 2 frames received on other forwarding interfaces and destined for the spoke-SDP are also forwarded.
Spoke SDP BPDU encapsulation states
IEEE 802.1D (referred as dot1d) and Cisco’s per VLAN Spanning Tree (PVST) BPDU encapsulations are supported on a per spoke SDP basis. STP is associated with a VPLS service like PVST is per VLAN. The main difference resides in the Ethernet and LLC framing and a type-length-value (TLV) field trailing the BPDU.
Spoke SDP BPDU encapsulation states shows differences between dot1D and PVST Ethernet BPDU encapsulations based on the interface encap-type field.
| Field | dot1d encap-type null |
dot1d encap-type dot1q |
PVST encap-type null |
PVST encap-type dot1q |
|---|---|---|---|---|
Destination MAC |
01:80:c2:00:00:00 |
01:80:c2:00:00:00 |
N/A |
01:00:0c:cc:cc:cd |
Source MAC |
Sending Port MAC |
Sending Port MAC |
N/A |
Sending Port MAC |
EtherType |
N/A |
0x81 00 |
N/A |
0x81 00 |
Dot1p and DEI |
N/A |
0xe |
N/A |
0xe |
Dot1q |
N/A |
VPLS spoke-SDP ID |
N/A |
VPLS spoke-SDP encap value |
Length |
LLC Length |
LLC Length |
N/A |
LLC Length |
LLC DSAP SSAP |
0x4242 |
0x4242 |
N/A |
0xaaaa (SNAP) |
LLC CNTL |
0x03 |
0x03 |
N/A |
0x03 |
SNAP OUI |
N/A |
N/A |
N/A |
00 00 0c (Cisco OUI) |
SNAP PID |
N/A |
N/A |
N/A |
01 0b |
CONFIG or TCN BPDU |
Standard 802.1d |
Standard 802.1d |
N/A |
Standard 802.1d |
TLV: Type and Len |
N/A |
N/A |
N/A |
58 00 00 00 02 |
TLV: VLAN |
N/A |
N/A |
N/A |
VPLS spoke-SDP encap value |
Padding |
As Required |
As Required |
N/A |
As Required |
Each spoke SDP has a Read Only operational state that shows which BPDU encapsulation is currently active on the spoke SDP. The following states apply:
-
dot1d
Specifies that the switch is currently sending IEEE 802.1D standard BPDUs. The BPDUs are tagged or non-tagged based on the encapsulation type of the egress interface and the encapsulation value defined in the spoke-SDP. A spoke SDP defined on an interface with encapsulation type dot1q continues in the dot1d BPDU encapsulation state until a PVST encapsulated BPDU is received, after which the spoke-SDP converts to the PVST encapsulation state. Each received BPDU must be properly IEEE 802.1q tagged if the interface encapsulation type is defined as dot1q.
-
PVST
Specifies that the switch is currently sending proprietary encapsulated BPDUs. PVST BPDUs are only supported on Ethernet interfaces with the encapsulation type set to dot1q. The spoke SDP continues in the PVST BPDU encapsulation state until a dot1d encapsulated BPDU is received, in which case the spoke SDP reverts to the dot1d encapsulation state. Each received BPDU must be properly IEEE 802.1q tagged with the encapsulation value defined for the spoke SDP.
Dot1d is the initial and only spoke-SDP BPDU encapsulation state for spoke SDPs defined on an Ethernet interface with encapsulation type set to null.
Each transition between encapsulation types optionally generates an alarm that can be logged and optionally transmitted as an SNMP trap.
Configuring VPLS spoke SDPs with split horizon
To configure spoke SDPs with a split horizon group, add the split-horizon-group parameter when creating the spoke SDP. Traffic arriving on an SAP or spoke-SDP within a split horizon group is not copied to other SAPs or spoke SDPs in the same split horizon group.
The following example shows a VPLS configuration with split horizon enabled:
----------------------------------------------
*A:ALA-1>config>service# *A:ALA-1>config>service# info
----------------------------------------------
...
vpls 800 customer 6001 vpn 700 create
description "VPLS with split horizon for DSL"
stp
shutdown
exit
spoke-sdp 51:15 split-horizon-group DSL-group1 create
exit
split-horizon-group DSL-group1
description "Split horizon group for DSL"
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-1>config>service#
Configuring VPLS redundancy
This section discusses VPLS redundancy service management tasks.
Creating a management VPLS for SAP protection
This section provides a brief overview of the tasks that must be performed to configure a management VPLS for SAP protection and provides the CLI commands; see Example configuration for protected VPLS SAP. The following tasks should be performed on both nodes providing the protected VPLS service.
Before configuring a management VPLS, see VPLS redundancy for an introduction to the concept of management VPLS and SAP redundancy.
Create an SDP to the peer node.
Create a management VPLS.
Define a SAP in the M-VPLS on the port toward the MTU. The port must be dot1q or qinq tagged. The SAP corresponds to the (stacked) VLAN on the MTU in which STP is active.
Optionally, modify STP parameters for load balancing.
Create a mesh SDP in the M-VPLS using the SDP defined in Step 1. Ensure that this mesh SDP runs over a protected LSP (see the following note).
Enable the management VPLS service and verify that it is operationally up.
Create a list of VLANs on the port that are to be managed by this management VPLS.
Create one or more user VPLS services with SAPs on VLANs in the range defined by Step 6.
Note: The mesh SDP should be protected by a backup LSP or Fast Reroute. If the mesh SDP went down, STP on both nodes would go to forwarding state and a loop would occur.
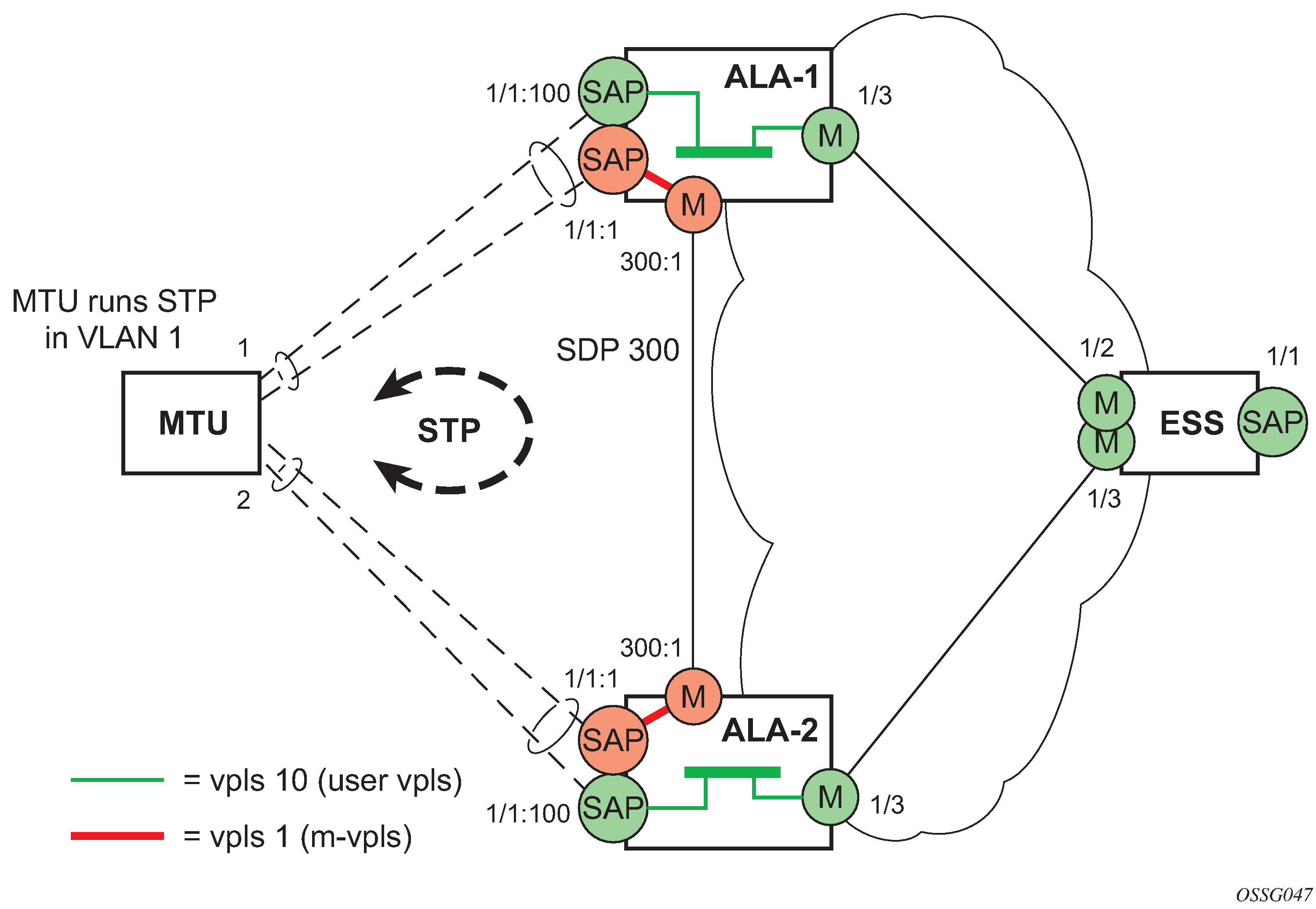
Use the following CLI syntax to create a management VPLS on the 7450 ESS or 7750 SR.
CLI syntax:
config>service# sdp sdp-id mpls create
— far-end ip-address
— lsp lsp-name
— no shutdown
CLI syntax:
vpls service-id customer customer-id [m-vpls] create
— description description-string
— sap sap-id create
— managed-vlan-list
— range vlan-range
— mesh-sdp sdp-id:vc-id create
— stp
— no shutdown
The following example shows a VPLS configuration:
*A:ALA-1>config>service# info
----------------------------------------------
...
sdp 300 mpls create
far-end 10.0.0.20
lsp "toALA-A2"
no shutdown
exit
vpls 1 customer 1 m-vpls create
sap 1/1/1:1 create
managed-vlan-list
range 100-1000
exit
exit
mesh-sdp 300:1 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-1>config>service#
Creating a management VPLS for spoke-SDP protection
This section provides a brief overview of the tasks that must be performed to configure a management VPLS for spoke-SDP protection and provides the CLI commands; see Example configuration for protected VPLS spoke-SDP. The following tasks should be performed on all four nodes providing the protected VPLS service. Before configuring a management VPLS, see Configuring a VPLS SAP for an introduction to the concept of management VPLS and spoke-SDP redundancy.
Create an SDP to the local peer node (node ALA-A2 in the following example).
Create an SDP to the remote peer node (node ALA-B1 in the following example).
Create a management VPLS.
Create a spoke-SDP in the M-VPLS using the SDP defined in Step 1. Ensure that this mesh SDP runs over a protected LSP (see note below).
Enable the management VPLS service and verify that it is operationally up.
Create a spoke-SDP in the M-VPLS using the SDP defined in Step 2. Optionally, modify STP parameters for load balancing (see Configuring load balancing with management VPLS).
Create one or more user VPLS services with spoke-SDPs on the tunnel SDP defined by Step 2.
As long as the user spoke-SDPs created in step 7 are in this same tunnel SDP with the management spoke-SDP created in step 6, the management VPLS protects them.
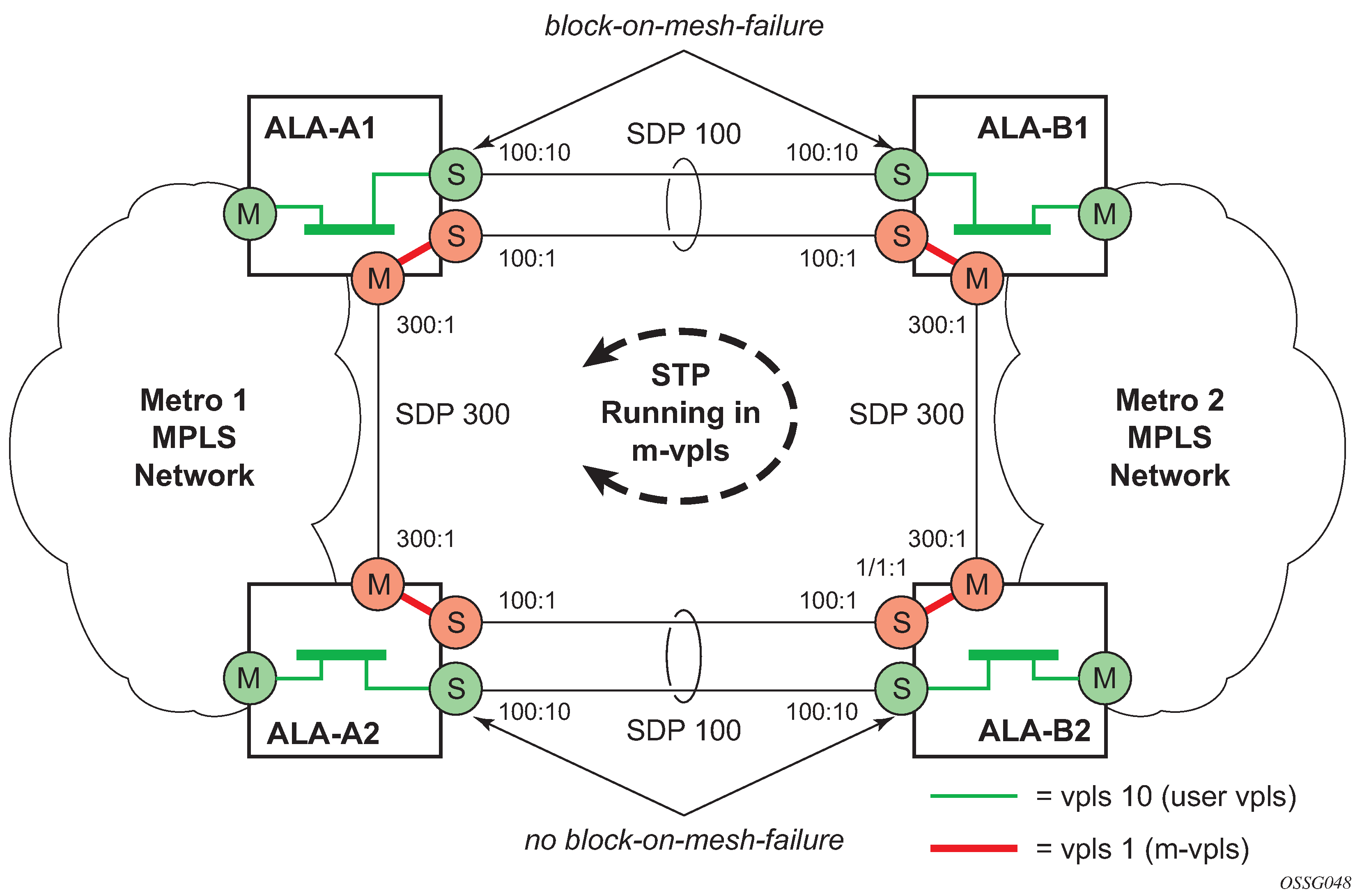
Use the following CLI syntax to create a management VPLS for spoke-SDP protection.
CLI syntax:
config>service# sdp sdp-id mpls create
— far-end ip-address
— lsp lsp-name
— no shutdown
CLI syntax:
vpls service-id customer customer-id [m-vpls] create
— description description-string
— mesh-sdp sdp-id:vc-id create
— spoke-sdp sdp-id:vc-id create
— stp
— no shutdown
The following example shows a VPLS configuration:
*A:ALA-A1>config>service# info
----------------------------------------------
...
sdp 100 mpls create
far-end 10.0.0.30
lsp "toALA-B1"
no shutdown
exit
sdp 300 mpls create
far-end 10.0.0.20
lsp "toALA-A2"
no shutdown
exit
vpls 101 customer 1 m-vpls create
spoke-sdp 100:1 create
exit
meshspoke-sdp 300:1 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-A1>config>service#
Configuring load balancing with management VPLS
With the concept of management VPLS, it is possible to load balance the user VPLS services across the two protecting nodes. This is done by creating two management VPLS instances, where both instances have different active QinQ spokes (by changing the STP path-cost). When user VPLS services are associated with either of the two management VPLS services, the traffic is split across the two QinQ spokes. Load balancing can be achieved in both the SAP protection and spoke-SDP protection scenarios.
Example configuration for load balancing across two protected VPLS spoke-SDPs shows an example configuration for load balancing across two protected VPLS spoke-SDPs.

Use the following CLI syntax to create load balancing across two management VPLS instances.
CLI syntax:
config>service# sdp sdp-id mpls create
far-end ip-address
lsp lsp-name
no shutdown
CLI syntax:
vpls service-id customer customer-id [m-vpls] create
— description description-string
— mesh-sdp sdp-id:vc-id create
— spoke-sdp sdp-id:vc-id create
— stp
— path-cost
— stp
— no shutdown
The following example shows the VPLS configuration on ALA-A1 (upper left, IP address 10.0.0.10):
*A:ALA-A1>config>service# info
----------------------------------------------
...
sdp 101 mpls create
far-end 10.0.0.30
lsp "1toALA-B1"
no shutdown
exit
sdp 102 mpls create
far-end 10.0.0.30
lsp "2toALA-B1"
no shutdown
exit
...
vpls 101 customer 1 m-vpls create
spoke-sdp 101:1 create
stp
path-cost 1
exit
exit
mesh-sdp 300:1 create
exit
stp
exit
no shutdown
exit
vpls 102 customer 1 m-vpls create
spoke-sdp 102:2 create
stp
path-cost 1000
exit
exit
mesh-sdp 300:2 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-A1>config>service#
The following example shows the VPLS configuration on ALA-A2 (lower left, IP address 10.0.0.20):
*A:ALA-A2>config>service# info
----------------------------------------------
...
sdp 101 mpls create
far-end 10.0.0.40
lsp "1toALA-B2"
no shutdown
exit
sdp 102 mpls create
far-end 10.0.0.40
lsp "2toALA-B2"
no shutdown
exit
...
vpls 101 customer 1 m-vpls create
spoke-sdp 101:1 create
stp
path-cost 1000
exit
exit
mesh-sdp 300:1 create
exit
stp
exit
no shutdown
exit
vpls 102 customer 1 m-vpls create
spoke-sdp 102:2 create
stp
path-cost 1
exit
exit
mesh-sdp 300:2 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-A2>config>service#
The following example shows the VPLS configuration on ALA-A3 (upper right, IP address 10.0.0.30):
*A:ALA-A1>config>service# info
----------------------------------------------
...
sdp 101 mpls create
far-end 10.0.0.10
lsp "1toALA-A1"
no shutdown
exit
sdp 102 mpls create
far-end 10.0.0.10
lsp "2toALA-A1"
no shutdown
exit
...
vpls 101 customer 1 m-vpls create
spoke-sdp 101:1 create
stp
path-cost 1
exit
exit
mesh-sdp 300:1 create
exit
stp
exit
no shutdown
exit
vpls 102 customer 1 m-vpls create
spoke-sdp 102:2 create
stp
path-cost 1000
exit
exit
mesh-sdp 300:2 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-A1>config>service#
The following example shows the VPLS configuration on ALA-A4 (lower right, IP address 10.0.0.40):
*A:ALA-A2>config>service# info
----------------------------------------------
...
sdp 101 mpls create
far-end 10.0.0.20
lsp "1toALA-B2"
no shutdown
exit
sdp 102 mpls create
far-end 10.0.0.20
lsp "2toALA-B2"
no shutdown
exit
...
vpls 101 customer 1 m-vpls create
spoke-sdp 101:1 create
stp
path-cost 1000
exit
exit
mesh-sdp 300:1 create
exit
stp
exit
no shutdown
exit
vpls 102 customer 1 m-vpls create
spoke-sdp 102:2 create
stp
path-cost 1
exit
exit
mesh-sdp 300:2 create
exit
stp
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-A2>config>service#
Configuring selective MAC flush
Use the following CLI syntax to enable selective MAC flush in a VPLS.
CLI syntax:
config>service# vpls service-id
send-flush-on-failure
Use the following CLI syntax to disable selective MAC flush in a VPLS.
CLI syntax:
config>service# vpls service-id
no send-flush-on-failure
Configuring multi-chassis endpoints
The following output shows configuration examples of multi-chassis redundancy and the VPLS configuration. The configurations in the graphics depicted in Inter-domain VPLS resiliency using multi-chassis endpoints are represented in this output.
Node mapping to the following examples in this section:
PE3 = Dut-B
PE3' = Dut-C
PE1 = Dut-D
PE2 = Dut-E
PE3 Dut-B
*A:Dut-B>config>redundancy>multi-chassis# info
----------------------------------------------
peer 10.1.1.3 create
peer-name "Dut-C"
description "mcep-basic-tests"
source-address 10.1.1.2
mc-endpoint
no shutdown
bfd-enable
system-priority 50
exit
no shutdown
exit
----------------------------------------------
*A:Dut-B>config>redundancy>multi-chassis#
*A:Dut-B>config>service>vpls# info
----------------------------------------------
fdb-table-size 20000
send-flush-on-failure
stp
shutdown
exit
endpoint "mcep-t1" create
no suppress-standby-signaling
block-on-mesh-failure
mc-endpoint 1
mc-ep-peer Dut-C
exit
exit
mesh-sdp 201:1 vc-type vlan create
exit
mesh-sdp 211:1 vc-type vlan create
exit
spoke-sdp 221:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 1
exit
spoke-sdp 231:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 2
exit
no shutdown
----------------------------------------------
*A:Dut-B>config>service>vpls#
PE3' Dut-C
:Dut-C>config>redundancy>multi-chassis# info
----------------------------------------------
peer 10.1.1.2 create
peer-name "Dut-B"
description "mcep-basic-tests"
source-address 10.1.1.3
mc-endpoint
no shutdown
bfd-enable
system-priority 21
exit
no shutdown
exit
----------------------------------------------
*A:Dut-C>config>redundancy>multi-chassis#
*A:Dut-C>config>service>vpls# info
----------------------------------------------
fdb-table-size 20000
send-flush-on-failure
stp
shutdown
exit
endpoint "mcep-t1" create
no suppress-standby-signaling
block-on-mesh-failure
mc-endpoint 1
mc-ep-peer Dut-B
exit
exit
mesh-sdp 301:1 vc-type vlan create
exit
mesh-sdp 311:1 vc-type vlan create
exit
spoke-sdp 321:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 3
exit
spoke-sdp 331:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
exit
no shutdown
----------------------------------------------
*A:Dut-C>config>service>vpls#
PE1 Dut-D
*A:Dut-D>config>redundancy>multi-chassis# info
----------------------------------------------
peer 10.1.1.5 create
peer-name "Dut-E"
description "mcep-basic-tests"
source-address 10.1.1.4
mc-endpoint
no shutdown
bfd-enable
system-priority 50
passive-mode
exit
no shutdown
exit
----------------------------------------------
*A:Dut-D>config>redundancy>multi-chassis#
*A:Dut-D>config>service>vpls# info
----------------------------------------------
fdb-table-size 20000
propagate-mac-flush
stp
shutdown
exit
endpoint "mcep-t1" create
block-on-mesh-failure
mc-endpoint 1
mc-ep-peer Dut-E
exit
exit
mesh-sdp 401:1 vc-type vlan create
exit
spoke-sdp 411:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 2
exit
spoke-sdp 421:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 1
exit
mesh-sdp 431:1 vc-type vlan create
exit
no shutdown
----------------------------------------------
*A:Dut-D>config>service>vpls#
PE2 Dut-E
*A:Dut-E>config>redundancy>multi-chassis# info
----------------------------------------------
peer 10.1.1.4 create
peer-name "Dut-D"
description "mcep-basic-tests"
source-address 10.1.1.5
mc-endpoint
no shutdown
bfd-enable
system-priority 22
passive-mode
exit
no shutdown
exit
----------------------------------------------
*A:Dut-E>config>redundancy>multi-chassis#
*A:Dut-E>config>service>vpls# info
----------------------------------------------
fdb-table-size 20000
propagate-mac-flush
stp
shutdown
exit
endpoint "mcep-t1" create
block-on-mesh-failure
mc-endpoint 1
mc-ep-peer Dut-D
exit
exit
spoke-sdp 501:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
precedence 3
exit
spoke-sdp 511:1 vc-type vlan endpoint "mcep-t1" create
stp
shutdown
exit
block-on-mesh-failure
exit
mesh-sdp 521:1 vc-type vlan create
exit
mesh-sdp 531:1 vc-type vlan create
exit
no shutdown
----------------------------------------------
*A:Dut-E>config>service>vpls#
ATM/Frame Relay PVC access and termination on a VPLS service
The application as shown in ATM/Frame Relay PVC access and termination on a VPLS example provides access to a VPLS service to Frame Relay and ATM users connected either directly or through an ATM access network to a PE node. The 7750 SR supports a Frame Relay or an ATM VC-delimited Service Access Point (SAP) terminating on a VPLS service.

RFC 2427-encapsulated or RFC 2684-encapsulated untagged Ethernet/802.3 frames (with or without Frame Check Sequence (FCS)) or BPDUs from a customer’s bridge device are received on a specified SAP over an ATM or Frame Relay interface on the 7750 SR. The Frame Relay or ATM-related encapsulation is stripped and the frames (without FCS) are forwarded toward destination SAPs either locally, or using SDPs associated with the VPLS service (as required by destination MAC address VPLS processing). In the egress direction, the received untagged frames are encapsulated into RFC 2427 or RFC 2684 (no Q-tags are added, no FCS in the forwarded frame) and sent over ATM or a FR VC toward the customer CPE.
When AAL5 RFC 2427/2684-encapsulated tagged frames are received from the customer’s bridge on an FR/ATM SAP, the tags are transparent and the frames are processed as described above with the exception that the frames forwarded toward the destinations have the received tags preserved. Similarly in the egress direction, the received tagged Ethernet frames are encapsulated as is (that is, Q-tags are again transparent and preserved) into RFC 2427/2684 and sent over the FR/ATM PVC toward the customer CPE. Because the tagging is transparent, the 7750 SR performs unqualified MAC learning (for example, MAC addresses are learned without reference to VLANs they are associated with). Because of that, MAC addresses used must be unique across all the VLANs used by the customer for a specified VPLS service instance. If a customer wants a per-VLAN separation, the VLAN traffic that needs to be separated must come on different VCs (different SAPs) associated with different VPLS service instances.
All VPLS functionality available on the 7750 SR is applicable to FR and ATM-delimited VPLS SAPs. For example, bridged PDUs received over ATM SAP can be tunneled through or dropped, all FIB functionality applies, packet level QoS and MAC filtering applies, and so on. Also, split horizon groups are applicable to ATM SAPs terminating on VPLS. That is, frame forwarding between ATM SAPs, also referred to as VCI-to- VCI forwarding, within the same group is disabled.
The Ethernet pseudowire is established using Targeted LDP (TLDP) signaling and uses the ether, vlan, or vpls VC type on the SDP. The SDP can be an MPLS or a GRE type.
Configuring BGP auto-discovery
This section provides important information to describe the different configuration options used to populate the required BGP AD and generate the LDP generalized pseudowire-ID FEC fields. There are a large number of configuration options that are available with this feature. Not all these configuration options are required to start using BGP AD. At the end of this section, it will be apparent that a simple configuration will automatically generate the required values used by BGP and LDP. In most cases, deployments provide full mesh connectivity between all nodes across a VPLS instance. However, capabilities are available to influence the topology and build hierarchies or hub and spoke models.
Configuration steps
Using BGP AD configuration example, assume PE6 was previously configured with VPLS 100 as indicated by the configurations code in the upper right. The BGP AD process commences after PE134 is configured with the VPLS 100 instance, as shown in the upper left. This shows a basic BGP AD configuration. The minimum requirement for enabling BGP AD on a VPLS instance is configuring the VPLS-ID and pointing to a pseudowire template.
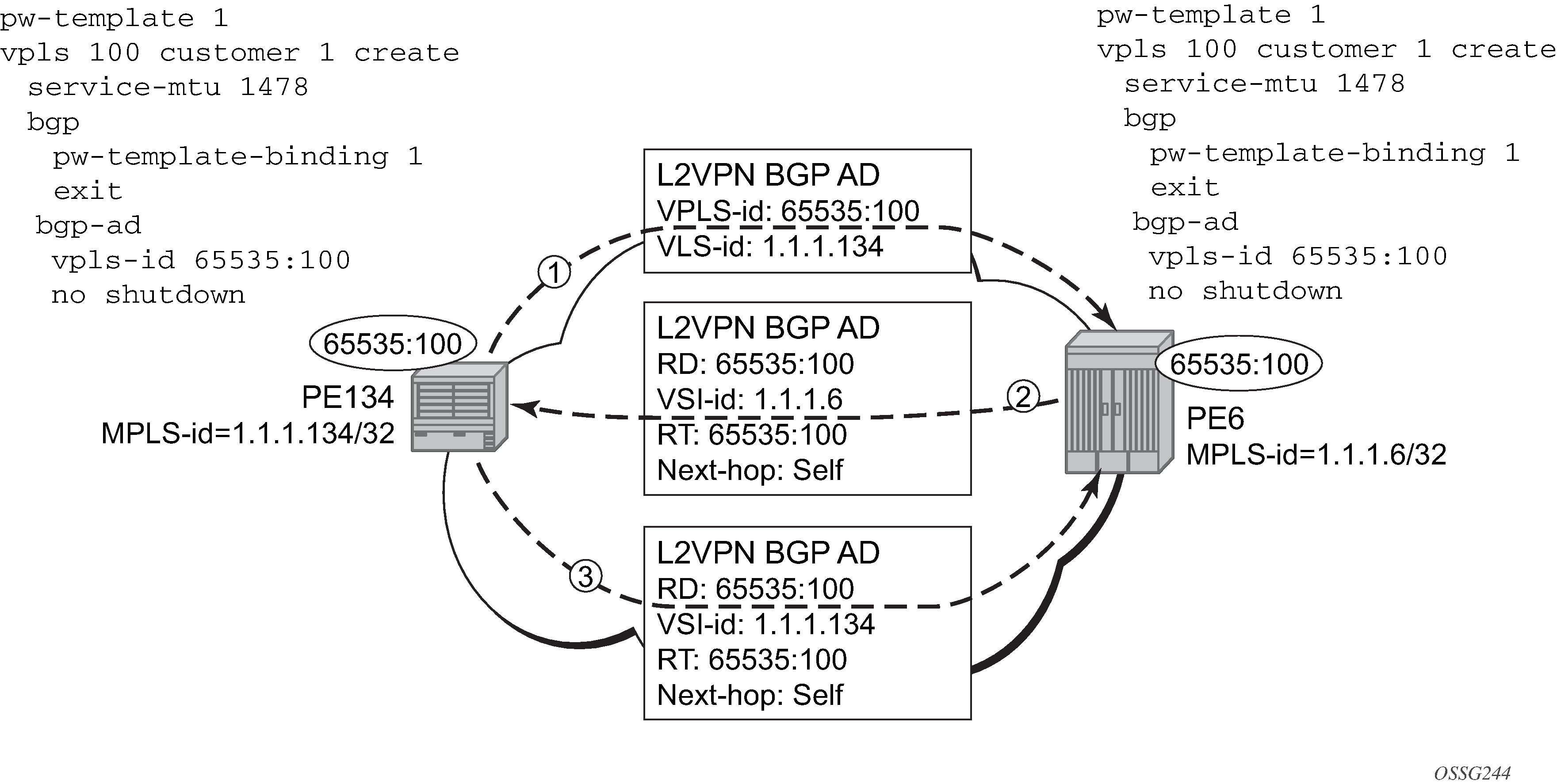
In many cases, VPLS connectivity is based on a pseudowire mesh. To reduce the configuration requirement, the BGP values can be automatically generated using the VPLS-ID and the MPLS router-ID. By default, the lower six bytes of the VPLS-ID are used to generate the RD and the RT values. The VSI-ID value is generated from the MPLS router-ID. All of these parameters are configurable and can be coded to suit requirements and build different topologies.
PE134>config>service>vpls>bgp-ad#
[no] shutdown - Administratively enable/disable BGP auto-discovery
vpls-id - Configure VPLS-ID
vsi-id + Configure VSI-id
The show service command shows the service information, the BGP parameters, and the SDP bindings in use. When the discovery process is completed successfully, each endpoint has an entry for the service.
PE134># show service l2-route-table
=======================================================================
Services: L2 Route Information - Summary Service
=======================================================================
Svc Id L2-Routes (RD-Prefix) Next Hop Origin
Sdp Bind Id
-----------------------------------------------------------------------
100 65535:100-1.1.1.6 1.1.1.6 BGP-L2
17406:4294967295
-----------------------------------------------------------------------
No. of L2 Route Entries: 1
=======================================================================
PERs6>#
PERs6># show service l2-route-table
=======================================================================
Services: L2 Route Information - Summary Service
=======================================================================
Svc Id L2-Routes (RD-Prefix) Next Hop Origin
Sdp Bind Id
-----------------------------------------------------------------------
100 65535:100-1.1.1.134 1.1.1.134 BGP-L2
17406:4294967295
-----------------------------------------------------------------------
No. of L2 Route Entries: 1
=======================================================================
PERs6>#
When only one of the endpoints has an entry for the service in the l2-routing-table, it is most likely a problem with the RT values used for import and export. This would most likely happen when different import and export RT values are configured using a router policy or the route-target command.
Service-specific commands continue to be available to show service-specific information, including status:
PERs6# show service sdp-using
===============================================================================
SDP Using
===============================================================================
SvcId SdpId Type Far End Opr S* I.Label E.Label
-------------------------------------------------------------------------------
100 17406:4294967295 BgpAd 10.1.1.134 Up 131063 131067
-------------------------------------------------------------------------------
Number of SDPs : 1
===============================================================================
* indicates that the corresponding row element may have been truncated.
BGP AD advertises the VPLS-ID in the extended community attribute, VSI-ID in the NLRI, and the local PE ID in the BGP next hop. At the receiving PE, the VPLS-ID is compared against locally provisioned information to determine whether the two PEs share a common VPLS. If they do, the BGP information is used in the signaling phase (see Configuring BGP VPLS).
LDP signaling
T-LDP is triggered when the VPN endpoints have been discovered using BGP. The T-LDP session between the PEs is established when a session does not exist. The far-end IP address required for the T-LDP identification is learned from the BGP AD next hop information. The pw-template and pw-template-binding configuration statements are used to establish the automatic SDP or to map to the appropriate SDP. The FEC129 content is built using the following values:
AGI from the locally configured VPLS-ID
SAII from the locally configured VSI-ID
TAII from the VSI-ID contained in the last 4 bytes of the received BGP NLRI
BGP AD triggering LDP functions shows the different detailed phases of the LDP signaling path, post BGP AD completion. It also indicates how some fields can be auto-generated when they are not specified in the configuration.

The following command shows the LDP peering relationships that have been established (see Show router LDP session output). The type of adjacency is displayed in the ‟Adj Type” column. In this case, the type is ‟Both” meaning link and targeted sessions have been successfully established.

The following command shows the specific LDP service label information broken up per FEC element type: 128 or 129, basis (see Show router LDP bindings FEC-type services). The information for FEC element 129 includes the AGI, SAII, and the TAII.

Pseudowire template
The pseudowire template is defined under the top-level service command (config>service>pw-template) and specifies whether to use an automatically generated SDP or manually configured SDP. It also provides the set of parameters required for establishing the pseudowire (SDP binding) as follows:
PERs6>config>service# pw-template 1 create
-[no] pw-template <policy-id> [use-provisioned-sdp | prefer-provisioned-sdp]
<policy-id> : [1..2147483647]
<use-provisioned-s*> : keyword
<prefer-provisioned*> : keyword
[no] accounting-pol* - Configure accounting-policy to be used
[no] auto-learn-mac* - Enable/Disable automatic update of MAC protect list
[no] block-on-peer-* - Enable/Disable block traffic on peer fault
[no] collect-stats - Enable/disable statistics collection
[no] control word - Enable/Disable the use of Control Word
[no] disable-aging - Enable/disable aging of MAC addresses
[no] disable-learni* - Enable/disable learning of new MAC addresses
[no] discard-unknow* - Enable/disable discarding of frames with unknown source
MAC address
egress + Spoke SDP binding egress configuration
[no] force-qinq-vc-* - Forces qinq-vc-type forwarding in the data-path
[no] force-vlan-vc-* - Forces vlan-vc-type forwarding in the data-path
[no] hash-label - Enable/disable use of hash-label
igmp-snooping + Configure IGMP snooping parameters
in gr ess + Spoke SDP binding ingress configuration
[no] l2pt-terminati* - Configure L2PT termination on this spoke SDP
[no] limit-mac-move - Configure mac move
[no] mac-pinning - Enable/disable MAC address pinning on this spoke SDP
[no] max-nbr-mac-ad* - Configure the maximum number of MAC entries in the FDB
from this SDP
[no] restrict-prote* - Enable/disable protected src MAC restriction
[no] sdp-exclude - Configure excluded SDP group
[no] sdp-include - Configure included SDP group
[no] split-horizon-* + Configure a split horizon group
stp + Configure STP parameters
vc-type - Configure VC type
[no] vlan-vc-tag - Configure VLAN VC tag
A pw-template-binding command configured within the VPLS service under the bgp-ad sub-command is a pointer to the pw-template that should be used. If a VPLS service does not specify an import-rt list, then that binding applies to all route targets accepted by that VPLS. The pw-template-bind command can select a different template on a per import-rt basis. It is also possible to specify specific pw-templates for some route targets with a VPLS service and use the single pw-template-binding command to address all unspecified but accepted imported targets.
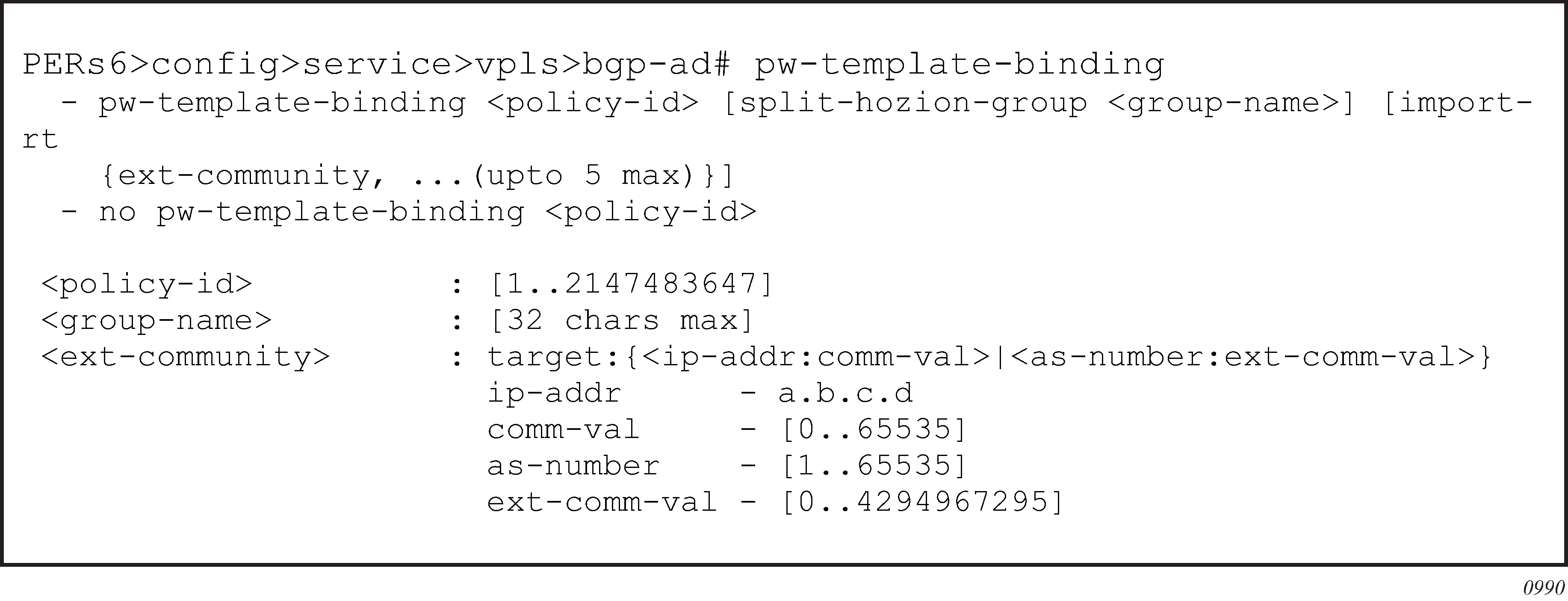
It is important to understand the significance of the split horizon group used by the pw-template. Traditionally, when a VPLS instance was manually created using mesh-SDP bindings, these were automatically placed in a common split horizon group to prevent forwarding between the pseudowire in the VPLS instances. This prevents loops that would have otherwise occurred in the Layer 2 service. When automatically discovering VPLS service using BGP AD, the service provider has the option of associating the auto-discovered pseudowire with a split horizon group to control the forwarding between pseudowires.
Configuring BGP VPLS
This section provides a configuration example required to bring up BGP VPLS in the VPLS PEs depicted in BGP VPLS example.
The red BGP VPLS is configured in the PE24, PE25, and PE26 using the commands shown in the following CLI examples:
*A:PE24>config>service>vpls# info
----------------------------------------------
bgp
route-distinguisher 65024:600
route-target export target:65019:600 import target:65019:600
pw-template-binding 1
exit
bgp-vpls
max-ve-id 100
ve-name 24
ve-id 24
exit
no shutdown
exit
sap 1/1/20:600.* create
exit
no shutdown
----------------------------------------------
*A:PE24>config>service>vpls#
*A:PE25>config>service>vpls# info
----------------------------------------------
bgp
route-distinguisher 65025:600
route-target export target:65019:600 import target:65019:600
pw-template-binding 1
exit
bgp-vpls
max-ve-id 100
ve-name 25
ve-id 25
exit
no shutdown
exit
sap 1/1/19:600.* create
exit
no shutdown
----------------------------------------------
*A:PE25>config>service>vpls#
*A:PE26>config>service>vpls# info
----------------------------------------------
bgp
route-distinguisher 65026:600
route-target export target:65019:600 import target:65019:600
pw-template-binding 1
exit
bgp-vpls
max-ve-id 100
ve-name 26
ve-id 26
exit
no shutdown
exit
sap 5/2/20:600.* create
exit
no shutdown
----------------------------------------------
*A:PE26>config>service>vpls#
Configuring a VPLS management interface
Use the following CLI syntax to create a VPLS management interface:
CLI syntax:
config>service>vpls# interface ip-int-name
address ip-address[/mask] [netmask]
arp-timeout seconds
description description-string
mac ieee-address
no shutdown
static-arp ip-address ieee-address
The following example shows the configuration.
A:ALA-49>config>service>vpls>interface# info detail
---------------------------------------------
no description
mac 14:31:ff:00:00:00
address 10.231.10.10/24
no arp-timeout
no shutdown
---------------------------------------------
A:ALA-49>config>service>vpls>interface#
Configuring policy-based forwarding for DPI in VPLS
The purpose of policy-based forwarding is to capture traffic from a customer and perform a deep packet inspection (DPI) and forward traffic, if allowed, by the DPI on the 7450 ESS or 7750 SR.
In the following example, the split horizon groups are used to prevent flooding of traffic. Traffic from customers enter at SAP 1/1/5:5. Because of the mac-filter 100 that is applied on ingress, all traffic with dot1p 07 marking is forwarded to SAP 1/1/22:1, which is the DPI.
DPI performs packet inspection/modification and either drops the traffic or forwards the traffic back into the box through SAP 1/1/21:1. Traffic is then sent to spoke-SDP 3:5.
SAP 1/1/23:5 is configured to determine whether the VPLS service is flooding all the traffic. If flooding is performed by the router, traffic would also be sent to SAP 1/1/23:5 (which it should not).
Policy-based forwarding for deep packet inspection shows an example to configure policy-based forwarding for deep packet inspection on a VPLS service. For information about configuring filter policies, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Router Configuration Guide.
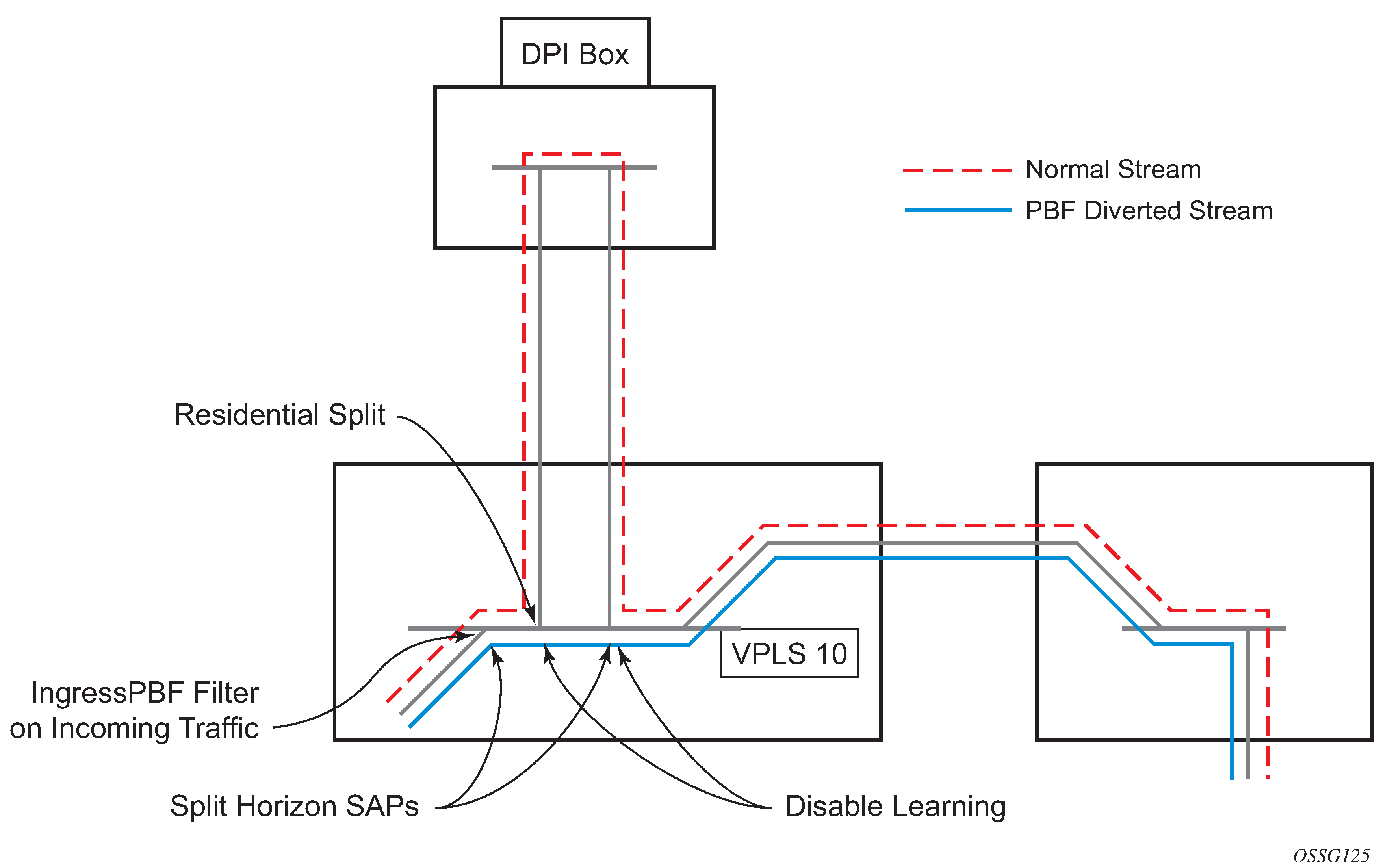
The following example shows the service configuration:
*A:ALA-48>config>service# info
----------------------------------------------
...
vpls 10 customer 1 create
service-mtu 1400
split-horizon-group "dpi" residential-group create
exit
split-horizon-group "split" create
exit
stp
shutdown
exit
igmp-host-tracking
expiry-time 65535
no shutdown
exit
sap 1/1/21:1 split-horizon-group "split" create
disable-learning
static-mac 00:00:00:31:11:01 create
exit
sap 1/1/22:1 split-horizon-group "dpi" create
disable-learning
static-mac 00:00:00:31:12:01 create
exit
sap 1/1/23:5 create
static-mac 00:00:00:31:13:05 create
exit
no shutdown
exit
...
----------------------------------------------
*A:ALA-48>config>service#
The following example shows the MAC filter configuration:
*A:ALA-48>config>filter# info
----------------------------------------------
...
mac-filter 100 create
default-action forward
entry 10 create
match
dot1p 7 7
exit
log 101
action forward sap 1/1/22:1
exit
exit
...
----------------------------------------------
*A:ALA-48>config>filter#
The following example shows the service configuration with a MAC filter:
*A:ALA-48>config>service# info
----------------------------------------------
...
vpls 10 customer 1 create
service-mtu 1400
split-horizon-group "dpi" residential-group create
exit
split-horizon-group "split" create
exit
stp
shutdown
exit
igmp-host-tracking
expiry-time 65535
no shutdown
exit
sap 1/1/5:5 split-horizon-group "split" create
ingress
filter mac 100
exit
static-mac 00:00:00:31:15:05 create
exit
sap 1/1/21:1 split-horizon-group "split" create
disable-learning
static-mac 00:00:00:31:11:01 create
exit
sap 1/1/22:1 split-horizon-group "dpi" create
disable-learning
static-mac 00:00:00:31:12:01 create
exit
sap 1/1/23:5 create
static-mac 00:00:00:31:13:05 create
exit
spoke-sdp 3:5 create
exit
no shutdown
exit
....
----------------------------------------------
*A:ALA-48>config>service#
Configuring VPLS E-Tree services
When configuring a VPLS E-Tree service, the etree keyword must be specified when the VPLS service is created. This is the first operation required before any SAPs or SDPs are added to the service, because the E-Tree service type affects the operations of the SAPs and SDP bindings.
When configuring AC SAPs, the configuration model is very similar to normal SAPs. Because the VPLS service must be designated as an E-Tree, the default AC SAP is a root-ac SAP. An E-Tree service with all root-ac behaves just as a regular VPLS service. A leaf-ac SAP must be configured for leaf behavior.
For root-leaf-tag SAPs, the SAP is created with both root and leaf VIDs. The 1/1/1:x.* or 1/1/1:x would be the typical format, where x designates the root tag. A leaf-tag is configured at SAP creation and replaces the x with a leaf-tag VID. Combined statistics for root and leaf SAPs are reported under the SAP. There are no individual statistics shown for root and leaf.
The following example illustrates the configuration of a VPLS E-Tree service with root-ac (default configuration for SAPs and SDP binds) and leaf-ac interfaces, as well as a root leaf tag SAP and SDP bind.
In the example, the SAP 1/1/7:2006.200 is configured using the root-leaf-tag parameter, where the outer VID 2006 is used for root traffic and the outer VID 2007 is used for leaf traffic.
*A:ALA-48>config>service# info
----------------------------------------------
...
service vpls 2005 etree customer 1 create
sap 1/1/1:2005 leaf-ac create
exit
sap 1/1/7:2006.200 root-leaf-tag leaf-tag 2007 create
exit
sap 1/1/7:0.* create
exit
spoke-sdp 12:2005 vc-type vlan root-leaf-tag create
no shutdown
exit
spoke-sdp 12:2006 leaf-ac create
no shutdown
exit
no shutdown
exit
....
*A:ALA-48>config>service# info
----------------------------------------------
Service management tasks
This section describes VPLS service management tasks.
Modifying VPLS service parameters
You can change existing service parameters. The changes are applied immediately. To display a list of services, use the show service service-using vpls command. Enter the parameter such as description, SAP, SDP, and, or service-MTU command syntax, then enter the new information.
The following shows a modified VPLS configuration:
*A:ALA-1>config>service>vpls# info
----------------------------------------------
description "This is a different description."
disable-learning
disable-aging
discard-unknown
local-age 500
remote-age 1000
stp
shutdown
exit
sap 1/1/5:22 create
description "VPLS SAP"
exit
spoke-sdp 2:22 create
exit
no shutdown
----------------------------------------------
*A:ALA-1>config>service>vpls#
Modifying management VPLS parameters
To modify the range of VLANs on an access port that are to be managed by an existing management VPLS, the new range should be defined, then the old range is removed. If the old range is removed before a new range is defined, all customer VPLS services in the old range become unprotected and may be disabled.
CLI syntax:
config>service# vpls service-id
sap sap-id
managed-vlan-list
[no] range vlan-range
Deleting a management VPLS
As with normal VPLS service, a management VPLS cannot be deleted until SAPs and SDPs are unbound (deleted), interfaces are shut down, and the service is shut down on the service level.
Use the following CLI syntax to delete a management VPLS service.
CLI syntax:
config>service
[no] vpls service-id
shutdown
[no] spoke-sdp sdp-id
[no] mesh-sdp sdp-id
shutdown
[no] sap sap-id
shutdown
Disabling a management VPLS
You can shut down a management VPLS without deleting the service parameters.
When a management VPLS is disabled, all associated user VPLS services are also disabled (to prevent loops). If this is not needed, un-manage the user’s VPLS service by removing them from the managed-vlan-list or moving the spoke-SDPs to another tunnel SDP.
CLI syntax:
config>service
vpls service-id
shutdown
Example:
config>service# vpls 1
config>service>vpls# shutdown
config>service>vpls# exit
Deleting a VPLS service
A VPLS service cannot be deleted until SAPs and SDPs are unbound (deleted), interfaces are shut down, and the service is shut down on the service level.
Use the following CLI syntax to delete a VPLS service.
CLI syntax:
config>service
[no] vpls service-id
shutdown
[no] mesh-sdp sdp-id
shutdown
sap sap-id [split-horizon-group group-name]
no sap sap-id
shutdown
Disabling a VPLS service
You can shut down a VPLS service without deleting the service parameters.
CLI syntax:
config>service> vpls service-id
[no] shutdown
Example:
config>service# vpls 1
config>service>vpls# shutdown
config>service>vpls# exit
Re-enabling a VPLS service
Use the following CLI syntax to re-enable a VPLS service that was shut down.
CLI syntax:
config>service> vpls service-id
[no] shutdown
Example:
config>service# vpls 1
config>service>vpls# no shutdown
config>service>vpls# exit