Secure boot
SR OS Secure Boot ensures that the software executed by the system is trusted and originated from Nokia IP routing.
At every boot of the control card, each step in the boot process verifies the digital signature of the next software element to boot for integrity and authenticity up to the SR OS operating system images. This boot sequence forms the chain of trust for Secure Boot. Software image signatures use RSA-4096 keys and SHA-384 hashes.
The Secure Boot chain is rooted in the platform CPM firmware based on UEFI specifications. As such, Nokia Platform Key, Key Exchange Key, allowed and disallowed databases are provisioned in the system when Secure Boot is activated to perform the required signature verification.
Firmware updates are also digitally signed and verified using the same principle. The signature verification of a firmware update is performed at boot time by the existing firmware before the firmware update can proceed.
Secure Boot chain
The Secure Boot chain of trust for SR OS platforms can be visualized with the following diagram.
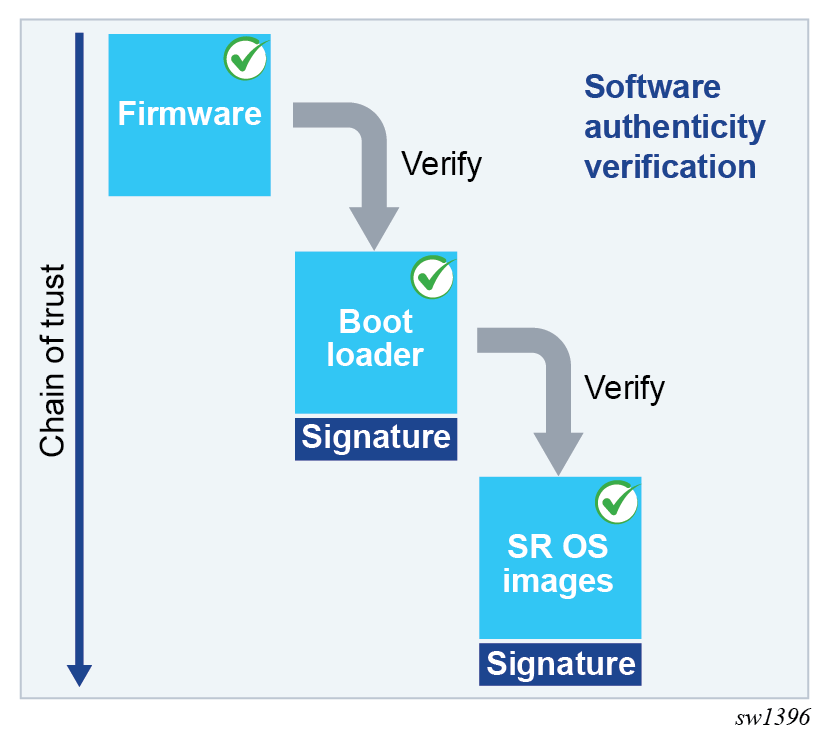
The software images part of the Secure Boot chain varies among SR OS platforms. This list of software images per platform is described in Storage card content and includes the Boot Loader, boot.ldr or ∕EFI∕BOOT∕ and installer images, and the SR OS *.tim software images.
Activate Secure Boot
Secure Boot is enabled, per CPM card, by providing the card slot, card serial number, and confirmation code command options.
Use the following command to activate Secure Boot.
admin system security secure-boot activate card "A" serial-number NS123456789 confirmation-code secure-boot-permanentThe following example shows the warning messages and a prompt for proceeding with Secure Boot activation.
WARNING: CLI This operation will permanently activate secure boot on card A and cannot be reversed.
WARNING: CLI After activation, the system will only accept digitally signed software and will not boot using un-signed software.
WARNING: CLI This operation will immediately reset card A.
WARNING: CLI Configuration and/or Boot options may have changed since the last save.
Are you sure you want to continue (y/n)?
The card serial number and Secure Boot confirmation code are required to avoid activating Secure Boot by mistake in the network. The confirmation code is secure-boot-permanent.
The Secure Boot activate command verifies that the BOF primary image uses the same software release as the currently running software and automatically reboots the designated CPM card if the software release matches. Otherwise, an error is generated in the CLI.
Operational commands and logs
This section describes the following:
- Secure Boot state
- Software update process
- Update Secure Boot variables
Secure Boot state
Secure Boot and UEFI variables Secure Boot keys status is available per CPM.
Use the following command to display Secure Boot state information.
show card A detailHardware Data
Secure boot status : enabled
UEFI variables status : ok
where
- Secure Boot status — indicates if Secure Boot is enabled or disabled
- UEFI variables status — indicates if Secure Boot variables need updating
The system records at every boot in the security log if Secure Boot is enabled or disabled per CPM. The following is an example of such a log message.
24 2023/05/17 06:09:03.140 EDT MAJOR: SECURITY #2241 Base Card A
"CPM A has booted with a secure-boot status of enabled"
Secure Boot UEFI variables can be obtained per CPM card using the following command:
- MD-CLI and
NETCONF
perform system security secure-boot show uefi-variables card - classic
CLI
tools dump system security secure-boot uefi-var card
The command displays the following x509 certificates and SHA-256 hash UEFI variables:
- Platform Key (PK)
- Key Exchange Key (KEK)
- Allowed Database (DB)
- Disallowed Database (DBx)
Software update
After Secure Boot is enabled, and before upgrading to a new software release, the user should validate that the new software image is properly signed. The main reason for this additional verification on systems with Secure Boot enabled is because the system only boots Nokia-signed software images and will not boot unsigned or improperly signed images.
Use the following command to validate the signature of the TiMOS *.tim images contained in the software-image url location referenced in the command. This verification includes cpm.tim, iom.tim, support.tim both.tim, kernel.tim, as well as the boot.ldr if present in CF3: directory.
admin system security secure-boot validate software-image urlUpdate Secure Boot variables
The system supports Secure Boot UEFI key updates and revocation using the following commands.
admin system security secure-boot update-key
admin system security secure-boot revoke-key