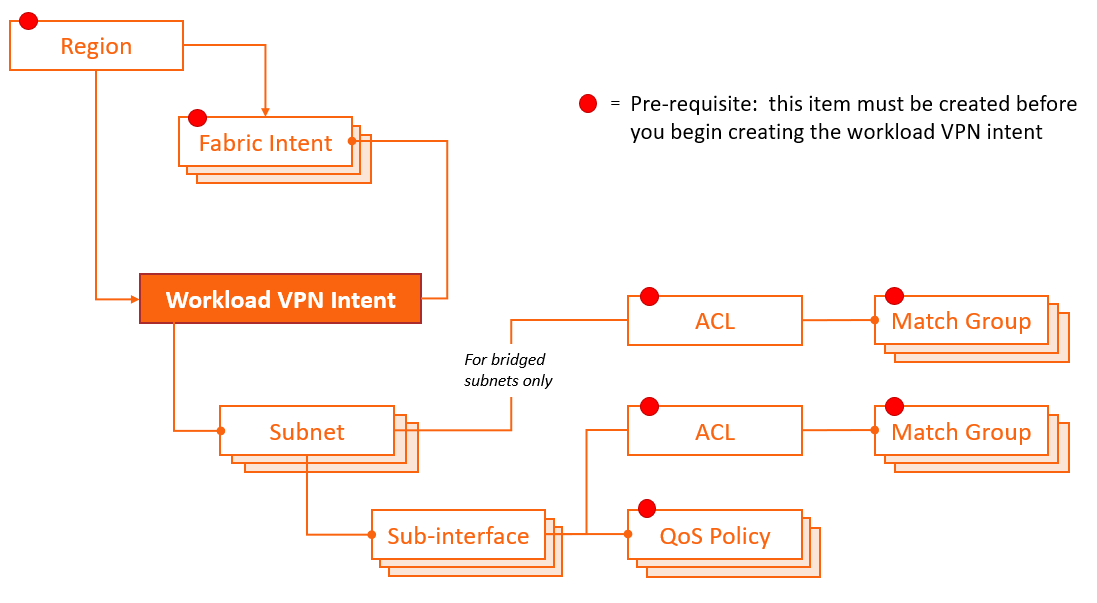
Elements of a workload intent
A workload VPN intent must be associated with specific fabrics within a deployment region (or "region"). The region manages the deployment pipeline, which organizes the sequential deployment of configuration data to the various nodes participating in the intent. For more information about regions, see Deployment regions.
To represent the set of resources available to a workload, a workload intent uses a hierarchical structure consisting of:
- Fabrics: a workload intent can span one or more fabrics that you have already defined in the system.
- Subnets: each subnet defines a subset of the participating fabrics. Subnets can be
either bridged or routed.
A bridged subnet with one or more IP addresses configured can be assigned an Access Control Lists (ACL); a set of rules that permit, or reject, any traffic that matches those IP addresses. These rules are applied on the IRB interface. The set of IP addresses is stored as a Match Group; the ACL then assembles a set of match groups, adds further defining properties, and indicates whether to accept or reject the matching packets.
- Sub-interfaces: each sub-interface identifies a set of edge link ports and LAGs
within a particular subnet, and across which the workload traffic can be bridged or
routed.
A sub-interface can be associated with:
- Access Control Lists (ACL): each sub-interface can be assigned a set of rules that permit, or reject, any traffic that matches those IP addresses. The set of IP addresses is stored as a Match Group; the ACL then assembles a set of match groups, adds further defining properties, and indicates whether to accept or reject the matching packets.
- QoS profiles: each sub-interface can be assigned a set of rules for prioritizing traffic.
Fabrics
Every workload intent allocates resources that belong to one or more fabric intents that already exist in the system.
As part of workload intent design, you must select the participating fabric intent or intents. All traffic managed by the workload intent is confined to these participating fabric intents (and, more specifically, only to the subnets and sub-interfaces you select within those fabric intents).
A single fabric intent can support multiple workload intents.
Subnets
A sub-network, or subnet, is a set of one or more nodes on a selected fabric.
When creating a workload intent, you identify each subnet as either bridged or routed.
- Bridged subnets can be assigned to a network-instance of type MAC-VRF. They are
associated with a MAC-VRF network instance, and allow for configuration of bridge
table and VLAN ingress/egress mapping.
When adding a bridged subnet to a workload VPN intent, you associate an IP Anycast Gateway, and can associate an ACL.
With Gateway IP, a MAC-VRF is attached to the default or ip-vrf network-instance by a single Integrated Routing and Bridging (IRB) interface. This allows routing between different MAC-VRF instances of a particular tenant or group of servers.
- Routed subnets can be assigned to a network-instance of type mgmt, default, or ip-vrf. They allow for configuration of IPv4 and IPv6 settings.
Sub-interfaces
For each subnet, you identify the set of sub-interfaces over which tenant traffic can travel. These sub-interfaces can be physical or logical ports, including Link Aggregation Groups (LAGs).
Each LAG you select as a sub-interface must have been configured previously within the system as part of the Fabric Intent design, and the interfaces participating in a LAG can be located on a single node, or on multiple nodes (constituting a multi-home LAG or MH-LAG).
For each sub-interface, you can define Quality of Service (QoS) profiles that prioritize traffic, and an Access Control List that identifies the packets to be accepted or rejected.
QoS profiles
The Fabric Services System supports Quality of Service (QoS) policies for assigning traffic to forwarding classes and remarking traffic at egress before it leaves a router. DSCP classifier policies map incoming packets to the appropriate forwarding classes, and DSCP rewrite-rule policies mark outgoing packets with an appropriate DSCP value based on the forwarding class.
After you have defined one or more QoS policies, you can assign them to workload intents to help manage the traffic associated with that workload.
For the procedure to create a QoS profile, see Creating a QoS profile.
For the steps to apply a QoS profile within a workload intent, see the "Create a sub-interface" section of the procedure Creating a workload VPN intent.
ACL profiles
An Access Control List (ACL) profile defines a set of packet types that should be either accepted or rejected. When assigned to a subnet (for bridged subnets) or sub-interface (routed or bridged), the ACL defines the traffic that is permitted on those workload intent resources.
An ACL profile is assembled from one or more match groups. Each match group defines a particular set of properties that could be possessed by packets. The ACL then uses these match groups to specify a set of packet properties, and then includes an instruction to either accept or reject packet that conform to those properties.
Match groups thereby provide an easy way to define a set of IP addresses once, and then re-use that information in multiple ACLs.
For the procedure to create a match group, see Creating a match group.
For the procedure to create an ACL profile, see Creating an ACL profile.
For the steps to apply an ACL profile within a workload intent, see the procedures Adding subnets to the workload intent (for bridged subnets) and Adding sub-interfaces to the workload intent (for routed subnets).