Route Policies
This chapter provides information about configuring route policies.
Topics in this chapter include:
Configuring Route Policies
This section contains information on the following topics:
Route policies are used to manage the label database for MPLS and to control entries to the routing table for dynamic routing (see Routing Policy and MPLS).
For routing, the 7705 SAR supports two databases to store routes. The routing database (RIB) is composed of the routing information learned by the routing protocols, including static routes. The forwarding database (FIB) is composed of the routes actually used to forward traffic through a router. In addition, link-state databases are maintained by interior gateway protocols (IGPs) such as OSPF and IS-IS. Refer to the 7705 SAR Routing Protocols Guide for information on OSPF, IS-IS, and other routing protocols.
Routing protocols calculate the best route to each destination and place these routes in the forwarding table. The routes in the forwarding table are used to forward IP packets to neighbors.
As an example, operators can configure a routing policy that will not place routes associated with a specific origin in the routing table. These routes will not be used to forward data packets and these routes are not advertised by the routing protocol to neighbors.
Routing policies control the size and content of the routing tables, the routes that are advertised, and the best route to take to reach a destination. Careful planning is essential to implement route policies that can affect the flow of routing information throughout the network. Before configuring and applying a route policy, operators should develop an overall plan and strategy to accomplish their intended routing actions.
There are no default route policies. Each policy must be created explicitly and applied. Policy parameters are modifiable.
Routing Policy and MPLS
Route policies can be used to manage the MPLS label database.
When used to manage the label database, route policies can be configured to determine which labels should be learned or advertised; for example, labels from a specified neighbor can be added to the label information base (LIB), while labels advertised by certain other neighbors can be discarded. Label learning of MPLS packets and, as a result, how the MPLS packets are forwarded, are based on the defined policies, if there are any. If no route policies are defined, all advertised labels received from neighbors are learned and placed in the LIB.
See the ‟Label Distribution Protocol” section in the 7705 SAR MPLS Guide for more information about how routing policies can be used as LDP import or export policies to control the label bindings that an LSR accepts from, or advertises to, its peers.
Policy Statements
Route policies contain policy statements containing ordered entries that contain match conditions and actions that the user specifies. The entries should be sequenced from the most explicit to the least explicit. Packet forwarding and routing can be implemented according to defined policies. Policy-based routing allows the user to dictate where traffic can be routed, through specific paths, or whether to forward or drop the traffic. Route policies can match a given route policy entry and continue searching for other matches within either the same route policy or the next route policy.
The process can stop when the first complete match is found and the router executes the action defined in the entry, either to accept or reject packets that match the criteria or proceed to the next entry or the next policy. Matching criteria can be based on source, destination, or particular properties of a route. Route policies can be constructed to support multiple stages to the evaluation and setting various route attributes.
Other matching conditions can be provided by specifying criteria such as:
autonomous system (AS) path policy options — a combination of AS numbers and regular expression operators
community list — a group sharing a common property
prefix list — a named list of prefixes
to and from criteria — a route’s destination and source
Default Action Behavior
The default action of a policy applies to a route when the route does not match any of the entries of the policy. If a policy does not have any match entries, all routes are subject to the default action. If no default action is specified and the policy is the last one in a chain of policies, the default action is determined by the protocol that called the policy.
If a default action is defined for one or more of the configured route policies, the default action is handled as follows:
The default action can be set to all available action states, including accept, reject, next-entry, and next-policy.
If the action states accept or reject, the policy evaluation terminates and the appropriate result is returned.
If a default action is defined and no matches occurred with the entries in the policy, the default action is used.
If a default action is defined and one or more matches occurred with the entries of the policy, the default action is not used.
Denied IP Prefixes
The following IP address prefixes are not allowed by the routing protocols and the Route Table Manager and are not populated within the forwarding table:
0.0.0.0/8 or longer
127.0.0.0/8 or longer
224.0.0.0/4 or longer
240.0.0.0/4 or longer
Any other prefixes that need to be filtered can be filtered explicitly using route policies.
Controlling Route Flapping
Route flapping is defined as recurring changes of an advertised route between nodes. That is, the advertised route alternates (flaps) back and forth between two paths. This is typically caused by network problems that cause intermittent route failures. Route flap is defined in RFC 2439.
Route damping is a controlled acceptance of unstable routes from BGP peers so that any ripple effect caused by route flapping across BGP AS border routers is minimized. The rationale is to delay the use of unstable routes (flapping routes) to forward data and advertisements until the route stabilizes.
The Nokia implementation of route damping is based on the following parameters:
Figure of Merit — a route is assigned a Figure of Merit (FoM), which is proportional to the frequency of flaps. The FoM algorithm can characterize a route’s behavior over a period of time. See Damping for more information about FoM and damping.
route flap — a route flap is not limited to the withdrawn route. It also applies to any change in the AS path or the next hop of a reachable route. A change in AS path or next hop indicates that the intermediate AS or the route-advertising peer is not suppressing flapping routes at the source or during the propagation. Even if the route is accepted as a stable route, the data packets destined for the route could experience unstable routing due to the unstable AS path or next hop.
suppress threshold — when the configured suppress threshold is exceeded, the route is suppressed and not advertised to other peers. The state of the route is considered to be down from the perspective of the routing protocol.
reuse threshold — when the FoM value falls below the configured reuse threshold and the route is still reachable, the route is advertised to other peers. The FoM value decays exponentially after a route is suppressed.
The two events that could trigger the route flapping algorithm are:
route flapping — if a route flap is detected within a configured maximum route flap history time, the route’s FoM is initialized and the route is marked as a potentially unstable route. Every time a route flaps, the FoM is increased and the route is suppressed if the FoM crosses the suppress threshold.
route reuse timer trigger — a suppressed route’s FoM decays exponentially. When it crosses the reuse threshold, the route is eligible for advertisement if it is still reachable.
If the route continues to flap, the FoM, with respect to time scale, looks like a sawtooth waveform with the exponential rise and decay of FoM. To control flapping, the following parameters can be configured:
half-life — the half-life value is the time, expressed in minutes, required for a route to remain stable in order for one half of the FoM value to be reduced. For example, if the half-life value is 6 (min) and the route remains stable for 6 min, then the new FoM value is 3. After another 6 min passes and the route remains stable, the new FoM value is 1.5.
max-suppress — the maximum suppression time, expressed in minutes, is the maximum amount of time that a route can remain suppressed
suppress — if the FoM value exceeds the configured integer value, the route is suppressed for use or inclusion in advertisements
reuse — if the FoM value falls below the configured reuse value, then the route can be reused
Regular Expressions
The ability to perform a filter match in the AS-PATH is supported. This feature allows customers to configure match criteria for specific sequences within the AS path so that they can be filtered out before cluttering the service provider’s routing information base (RIB).
The 7705 SAR uses regular expression strings to specify match criteria for:
an AS path string; for example, ‟100 200 300”, where 100, 200, and 300 are AS numbers
a community string; for example, ‟100:200”, where 100 is the AS number and 200 is the community value
A regular expression is expressed as a combination of Terms and Operators. Regular expressions should always be enclosed in quotes.
The 7705 SAR also supports community expressions that allow the use of AND, OR, and NOT logical operators. For more information, see Community Expressions.
Terms
A term for an AS path regular expression is:
-
an elementary term; for example, an AS number ‟200”
-
a range term composed of two elementary terms separated by the ‟-” character, such as ‟200-300”
-
the ‟.” dot wildcard character, which matches any elementary term
-
a regular expression enclosed in parentheses ‟( )”
-
a regular expression enclosed in square brackets used to specify a set of choices of elementary or range terms; for example, [100-300 400] matches any AS number between 100 and 300 or the AS number 400
A term for a community string regular expression is a string that is evaluated character by character and is composed of:
-
an elementary term, which for a community string is any single digit, such as ‟4”
-
a range term composed of two elementary terms separated by the ‟-” character, such as ‟2-3”
-
a colon ‟:” to delimit the AS number from the community value
-
the ‟.” dot wildcard character, which matches any elementary term or ‟:”
-
a regular expression enclosed in parentheses ‟( )”
-
a regular expression enclosed in square brackets, which is used to specify a set of choices of elementary or range terms; for example, [1-3 7] matches any single digit between 1 and 3 or the digit 7
Operators
The regular expression operators are listed in Regular Expression Operators.
Operator |
Description |
|---|---|
| |
Matches the term on alternate sides of the pipe |
. |
Matches any elementary term or ‟:” community string |
* |
Matches multiple occurrences of the term |
? |
Matches 0 or 1 occurrence of the term |
+ |
Matches 1 or more occurrence of the term |
( ) |
Used to parenthesize so a regular expression is considered as one term |
[ ] |
Used to demarcate a set of elementary or range terms |
- |
Used between the start and end of a range |
{m,n} |
Matches at least m and at most n repetitions of the term |
{m} |
Matches exactly m repetitions of the term |
{m,} |
Matches m or more repetitions of the term |
: |
Delimits the AS number from the community value — only allowed for communities |
^ |
Matches the beginning of the string — only allowed for communities |
$ |
Matches the end of the string — only allowed for communities |
\ |
An escape character to indicate that the following character is a match criteria and not a grouping delimiter |
Examples of AS path and community string regular expressions are listed in AS Path and Community Regular Expression Examples.
AS Path to Match Criteria |
Regular Expression |
Examples of Matches |
|---|---|---|
Null AS path |
null 1 |
Null AS path |
AS path is 11 |
11 |
11 |
AS path is 11 22 33 |
11 22 33 |
11 22 33 |
Zero or more occurrences of AS number 11 |
11* |
Null AS path 11 11 11 11 11 11 11 … 11 |
Path of any length that begins with AS numbers 11, 22, 33 |
11 22 33 .* |
11 22 33 11 22 33 400 500 600 |
Path of any length that ends with AS numbers 44, 55, 66 |
.* 44 55 66 |
44 55 66 100 44 55 66 100 200 44 55 66 100 200 300 44 55 66 100 200 300 … 44 55 66 |
One occurrence of the AS numbers 100 and 200, followed by one or more occurrences of the number 33 |
100 200 33+ |
100 200 33 100 200 33 33 100 200 33 33 33 100 200 33 33 33 … 33 |
One occurrence of the AS number 11, followed by one or more occurrences of AS number 22, followed by one or more occurrences of AS number 33 |
11+ 22+ 33+ |
11 22 33 11 11 22 33 11 11 22 22 33 11 11 22 22 33 33 11 ... 11 22 ... 22 33 ... 33 |
Path whose second AS number must be 11 or 22 |
(. 11) | (. 22) .* or . (11 | 22) .* |
100 11 200 22 300 400 … |
Path of length one or two whose second AS number might be 11 or 22 |
. (11 | 22)? |
100 200 11 300 22 |
Path whose first AS number is 100 and second AS number is either 11 or 22 |
100 (11 | 22) .* |
100 11 100 22 200 300 |
AS path 11, 22, or 33 |
[11 22 33] |
11 22 33 |
Range of AS numbers to match a single AS number |
10-14 |
Null AS path 10 or 11 or 12 |
[10-12]* |
Null AS path 10 or 11 or 12 10 10 or 10 11 or 10 12 11 10 or 11 11 or 11 12 12 10 or 12 11 or 12 12 … |
|
Zero or one occurrence of AS number 11 |
11? or 11{0,1} |
Null AS path 11 |
One through four occurrences of AS number 11 |
11{1,4} |
11 11 11 11 11 11 11 11 11 11 |
One through four occurrences of AS number 11 followed by one occurrence of AS number 22 |
11{1,4} 22 |
11 22 11 11 22 11 11 11 22 11 11 11 11 22 |
Path of any length, except nonexistent, whose second AS number can be anything, including nonexistent |
. .* or . .{0,} |
100 100 200 11 22 33 44 55 |
AS number is 100 and community value is 200 |
^100:200$ |
100:200 |
AS number is 11 or 22 and community value is any number |
^((11)|(22)):(.*)$ |
11:100 22:100 11:200 … |
AS number is 11 and community value is any number that starts with 1 |
^11:(1.*)$ |
11:1 11:100 11:1100 |
AS number is any number and community value is any number that ends with 1, 2, or 3 |
^(.*):(.*[1-3])$ |
11:1 100:2002 333:55553 … |
AS number is 11 or 22 and community value is any number that starts with 3 and ends with 4, 5 or 9 |
^((11)|(22)):(3.*[459])$ |
11:34 22:3335 11:3777779 … |
AS number is 11 or 22 and community value ends in 33 or 44 |
[^((11|22)):(.*((33)|(44)))$ |
11:33 22:99944 22:555533 … |
Note:
The null keyword matches an empty AS path.
Community Expressions
A community expression is a collection of community IDs separated by AND, OR, and NOT operations. A community expression is not the same as a regular expression. A community expression must be enclosed within quotes (‟expression”) and may include parentheses to group expressions. An example of a community expression CLI command is:
config>router>policy-option>community "comm-name" expression "(2:2 AND 3:3) AND 4:4 AND NOT(1:1)"
For more information, see the community command description.
BGP and OSPF Route Policy Support
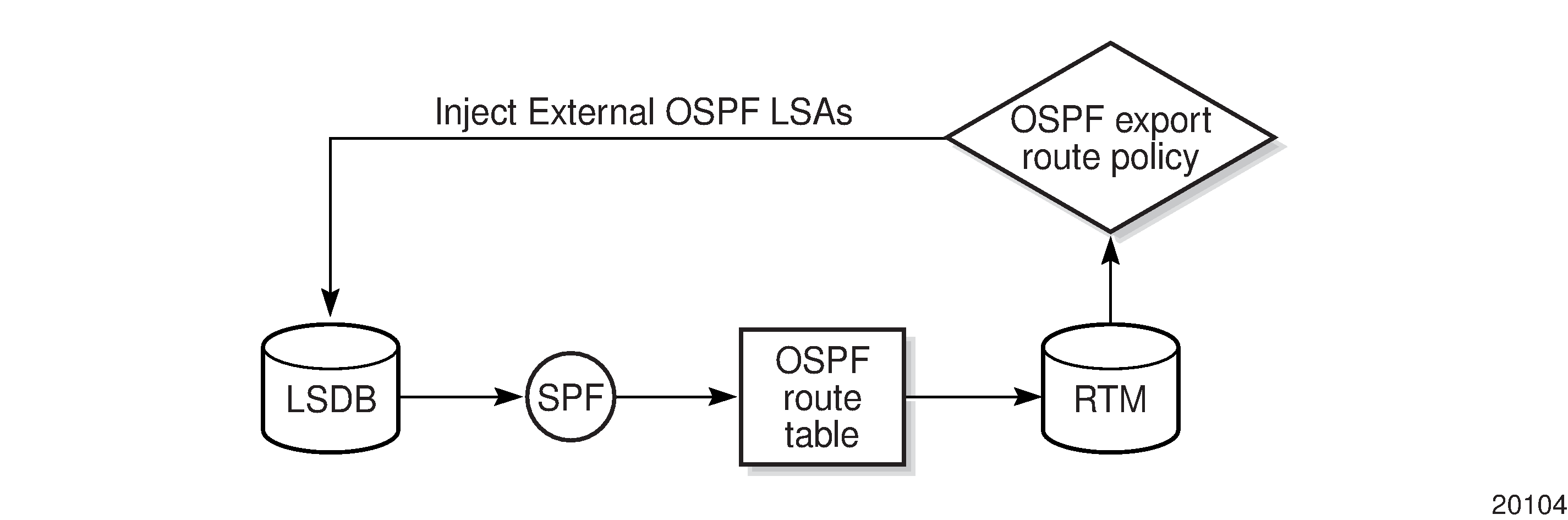
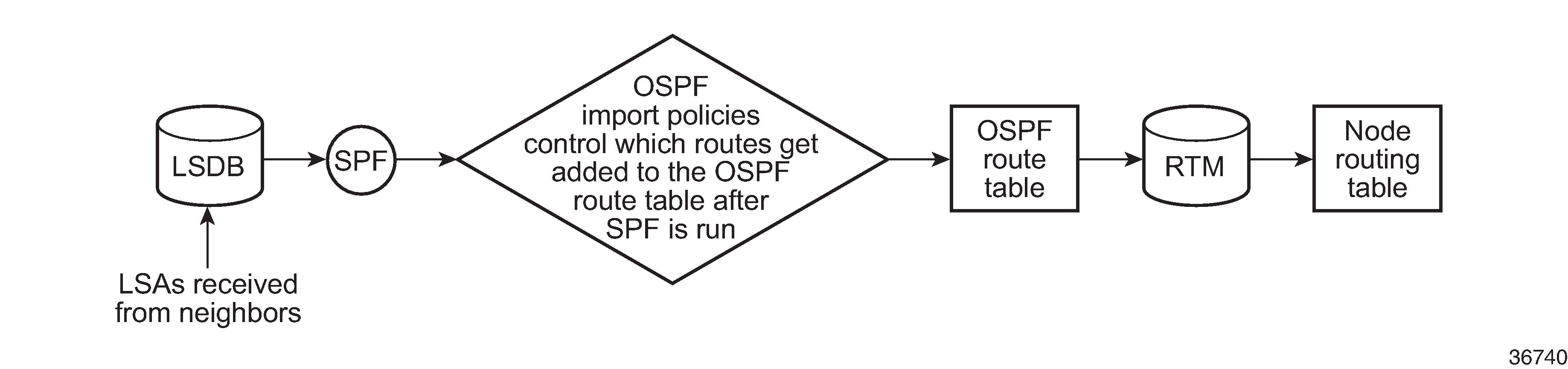
BGP and OSPF require route policy support. BGP Route Policy Diagram , OSPF Export Route Policy Diagram , and OSPF Import Route Policy Diagram show how route policies are evaluated in each protocol. BGP Route Policy Diagram shows BGP support, which applies a route policy as an internal part of the BGP route selection process. OSPF Export Route Policy Diagram shows OSPF support for export policies, which applies routing policies at the edge of the protocol in order to control only the routes that are announced to or accepted from the Routing Table Manager (RTM). OSPF Import Route Policy Diagram shows OSPF support for import policies, which applies import routing policies to control which routes are added to the OSPF route table after SPF is run.
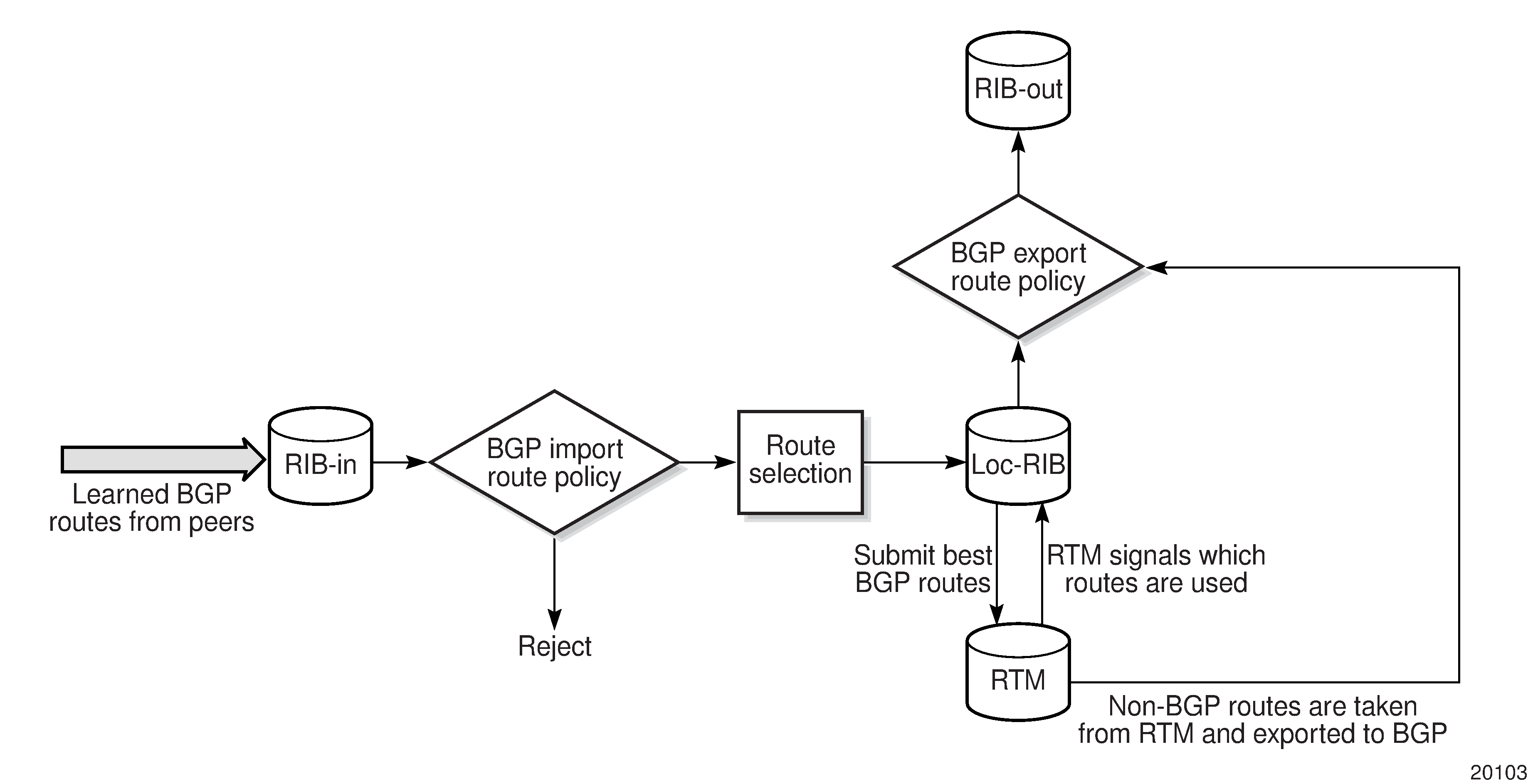
BGP Route Policies
The Nokia implementation of BGP uses route policies extensively. The implied or default route policies can be overridden by customized route policies. The default BGP properties, with no route policies configured, function as follows:
accept all BGP routes into the RTM for consideration
announce all used BGP learned routes to other BGP peers
announce none of the IGP, static, or local routes to BGP peers
Readvertised Route Policies
Occasionally, within the network and as applicable to the VPRN service, BGP routes may be readvertised from BGP into OSPF and IS-IS. OSPF export policies (policies control which routes are exported to OSPF) are not handled by the main OSPF task but are handled by a separate task or an RTM task that filters the routes before they are presented to the main OSPF task.
Route Policies for BGP Next-Hop Resolution and Peer Tracking
The 7705 SAR can attach a route policy to the BGP next-hop resolution process and can allow a route policy to be associated with the optional BGP peer-tracking function. These two features are supported for BGP and VPRN BGP services.
BGP Next-Hop Resolution Policy Overview
BGP next-hop resolution is a fundamental part of BGP protocol operation. It determines the best matching route (or tunnel) for the BGP next-hop address and uses information about this resolving route when running the best-path selection algorithm and programming the forwarding table. Attaching a policy to BGP next-hop resolution provides additional control over which IP routes in the routing table can become resolving routes.
See Route Policy Support for BGP Next-Hop Resolution for details.
BGP Peer Tracking Policy Overview
Peer tracking is a BGP feature that triggers teardown of a BGP session if there is no IP reachability to the neighbor address or if the best matching IP route is rejected by the peer-tracking policy. This feature is configurable down to the peer level and is disabled by default. Peer tracking accelerates routing reconvergence when a failure leads to hold-timer expiry on the BGP session. BFD for BGP sessions has a similar function and is often used instead of peer tracking.
In the BGP implementation, an IPv4 or IPv6 neighbor address is considered reachable by the peer-tracking algorithm if there is any active and eligible IP route that matches the neighbor address. Policy support for peer tracking is useful so that the network administrator can restrict the set of eligible routes used to determine the reachability of an IPv4 or IPv6 BGP neighbor address when peer tracking is enabled.
See Route Policy Support for BGP Peer Tracking for details.
Route Policy Support for BGP Next-Hop Resolution
A route policy can be used for BGP next-hop resolution through the use of the policy command in the config>router>bgp>next-hop-resolution and config>service>vprn>bgp>next-hop-resolution contexts. The policy command specifies the route policy to be used.
If the BGP configuration references a next-hop resolution policy (for example, policy1) and BGP has an unlabeled unicast IPv4 or IPv6 route with IPv4 or IPv6 next-hop address nh1 that is resolvable by an IP route from the RTM, BGP determines the resolving route for nh1 as follows.
BGP looks for the most specific IP route in the candidate set that matches nh1 (call this route R1). If there is no matching, route the BGP route is unresolved and the process is exited.
If R1 is rejected by an entry or the default-action of policy1, the route is unresolved and the process is exited.
If R1 is accepted by an entry or the default-action of policy1, R1 is the resolving route.
All policy actions are supported in a next-hop resolution policy; however, the following points should be noted:
next-policy is ignored and matching routes are handled as per the default-action. Chaining multiple policies is not supported by this feature.
next-entry is supported and causes evaluation of the policy to continue on to the next entry or the default-action is applied if this is the last entry
no route attributes are modified as part of an accept action. The route is accepted but no modification of the AIGP metric, AS path, community, damping parameters, local preference, MED, next-hop, origin, and so on, occurs.
When no default-action is explicitly configured by the user, the implicit default-action is accept.
All from match conditions are supported in a next-hop resolution policy except as noted below:
family is ignored. When resolving an IPv4 BGP route, only IPv4 routes are eligible for resolving the next hop and when resolving an IPv6 BGP route, only IPv6 routes are eligible for resolving the next hop. This logic cannot be changed by policy.
group-address, host-ip, and source-address are ignored because they pertain only to multicast routes
The default next-hop resolution policy, used when the configuration has no policy, is equivalent to a user-configured policy with no entries and a default-action of accept.
It is possible to add, remove, or change the next-hop resolution policy at any time, without requiring BGP to first be shut down. The new policy is processed immediately and any indirect next-hop resolution changes that result from the new policy are immediately pushed down to the datapath.
Route Policy Support for BGP Peer Tracking
A route policy can be used for BGP peer tracking through the use of the peer-tracking-policy command in the config>router>bgp and config>service>vprn>bgp contexts. The policy command specifies the route policy to be used.
If the command references a policy (for example, policy1) and peer tracking is enabled with a BGP neighbor A having IPv4 or IPv6 address p1, the route BGP uses to determine the reachability of p1 is determined as follows.
BGP initializes the set of candidate IP routes to all active routes installed in the forwarding table, excluding aggregate routes.
BGP looks for the most specific IP route in the candidate set that matches p1 (call this route R1). If there is no matching route, the peer is unreachable and the process is exited.
If R1 is a BGP route or R1 is rejected by an entry or the default-action of policy1, the peer is unreachable and the process is exited.
If R1 is accepted by an entry or the default-action of policy1, the peer is reachable via R1.
If the above algorithm determines that the peer is unreachable, the BGP session with A is closed after a 1-second delay to dampen route flaps and stays closed until there is a route R1 that is accepted (that is, meets the step 4 condition). Reachability is evaluated before a new session is established, whenever the most specific route that matches the neighbor address changes, and whenever there is a change to the peer-tracking policy.
All policy actions are supported in a peer-tracking policy; however, the following points should be noted:
next-policy is ignored and matching routes are handled per the default-action. Chaining multiple policies is not supported by this feature.
next-entry is supported and causes evaluation of the policy to continue on to the next entry or the default-action is applied if this is the last entry
no route attributes are modified as part of an accept action. The route is accepted but no modification of the AIGP metric, AS path, community, damping parameters, local preference, MED, next-hop, origin, and so on, occurs.
When no default-action is explicitly configured by the user, the implicit default-action is accept.
All from match conditions are supported in a peer-tracking policy except as noted below:
family is ignored. When determining the reachability of an IPv4 peer address, only IPv4 routes are eligible and when determining the reachability of an IPv6 peer address, only IPv6 routes are eligible. This logic cannot be changed by policy.
group-address, host-ip, and source-address are ignored because they pertain only to multicast routes
The default peer-tracking policy, used when the configuration has no peer-tracking policy, is equivalent to a user-configured policy with no entries and a default-action of accept.
It is possible to add, remove, or change the peer-tracking policy at any time, without requiring BGP to first be shut down. The new policy is processed immediately and this may trigger one or more sessions to be torn down.
When to Use Route Policies
The following are examples of when to configure and apply unique route policies:
to control the protocol to allow all routes to be imported into the routing table. This enables the routing table to learn about particular routes to enable packet forwarding and redistributing of routes into other routing protocols.
to control the export of a protocol’s learned active routes
to enable the MP-BGP routing protocol to announce active routes learned from another routing protocol (that is, the static routes configured in the 7705 SAR). This function is sometimes called route redistribution.
to allow unique behaviors to control route characteristics; for example, change the route preference, AS path, or community values to manipulate or control the route selection
to control BGP route flapping by use of route flap damping
Troubleshooting the FIB
Adapter cards that are installed in a 7705 SAR-8 Shelf V2 or 7705 SAR-18 chassis may have different hardware limitations with respect to IPv4 and IPv6 FIB routing. Alarms may be generated on the node when IPv4 or IPv6 routing faults related to scaling, capability, or a datapath route lookup problem are detected on an adapter card. FIB Alarms lists the applicable alarms.
Alarm |
Description |
|---|---|
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV6_UNSUPPORTED_SUBNET_MASK Error Detected!” |
A /65 to /127 IPv6 route was downloaded to an adapter card without hardware support |
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV4_SCALE_EXCEEDED Error Detected!” |
The total number of IPv4 routes in the FIB exceeds the adapter card hardware capability |
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV4_VRF_SCALE_EXCEEDED Error Detected!” |
The total number of IPv4 routing instances in the FIB (for example, number of VPRNs) exceeds the adapter card hardware capability |
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV6_SCALE_EXCEEDED Error Detected!” |
The total number of IPv6 routes in the FIB exceeds the adapter card hardware capability |
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV6_VRF_SCALE_EXCEEDED Error Detected!” |
The total number of IPv6 routing instances in the FIB (for example, number of VPRNs) exceeds the adapter card hardware capability |
‟Class MDA Module : runtime event, details: Fatal FIB_STATUS_IPV4_DP_LOOKUP_FAULT Error Detected!” |
The software has detected faults with datapath IPv4 route lookups |
If any of the alarms in FIB Alarms are generated, the IPv4 or IPv6 datapath on the adapter card operates in a random way. For example, traffic may continue to flow as expected in some cases, but in other cases, traffic could be blackholed or misrouted.
The show router fib 1 ipv4 summary and show router fib 1 ipv6 summary commands can be used to confirm that the FIB limits are exceeded.
For example:
# show router fib 1 ipv4 summary
===============================================================================
FIB Summary
===============================================================================
Active
-------------------------------------------------------------------------------
Static 0
Direct 142
HOST 0
BGP 0
BGP VPN 38569
OSPF 234
ISIS 486
RIP 0
Aggregate 0
Sub Mgmt 0
-------------------------------------------------------------------------------
Total Installed 39431
-------------------------------------------------------------------------------
Current Occupancy 120%
Overflow Count 0
Suppressed by Selective FIB 0
Occupancy Threshold Alerts
Alert Raised 1 Times; Last Alert 11/30/2016 07:50:46
===============================================================================
To restore a FIB that is in a failed state, the user must do the following.
If possible, resolve the condition that led to the alarm being generated. For example, for scaling alarms, reduce the size of the routing table below the maximum for the affected adapter card.
Execute the tools perform mda-table-refresh command to restore the FIB. Refer to the 7705 SAR OAM and Diagnostics Guide, ‟Tools Perform Commands” for a command description.
Wait a few minutes to ensure that no new alarm is raised; if there are no new alarms, the fault has been successfully resolved.
If a new alarm is raised, this indicates that the adapter card must be replaced.
Alternatively, when an alarm is generated, replace the card with a new adapter card that supports the higher scaling limit (for scaling alarms) or replace the card to resolve persistent datapath lookup faults.
Route Policy Configuration Process Overview
Route Policy Configuration and Implementation Flow displays the process to provision basic route policy parameters.
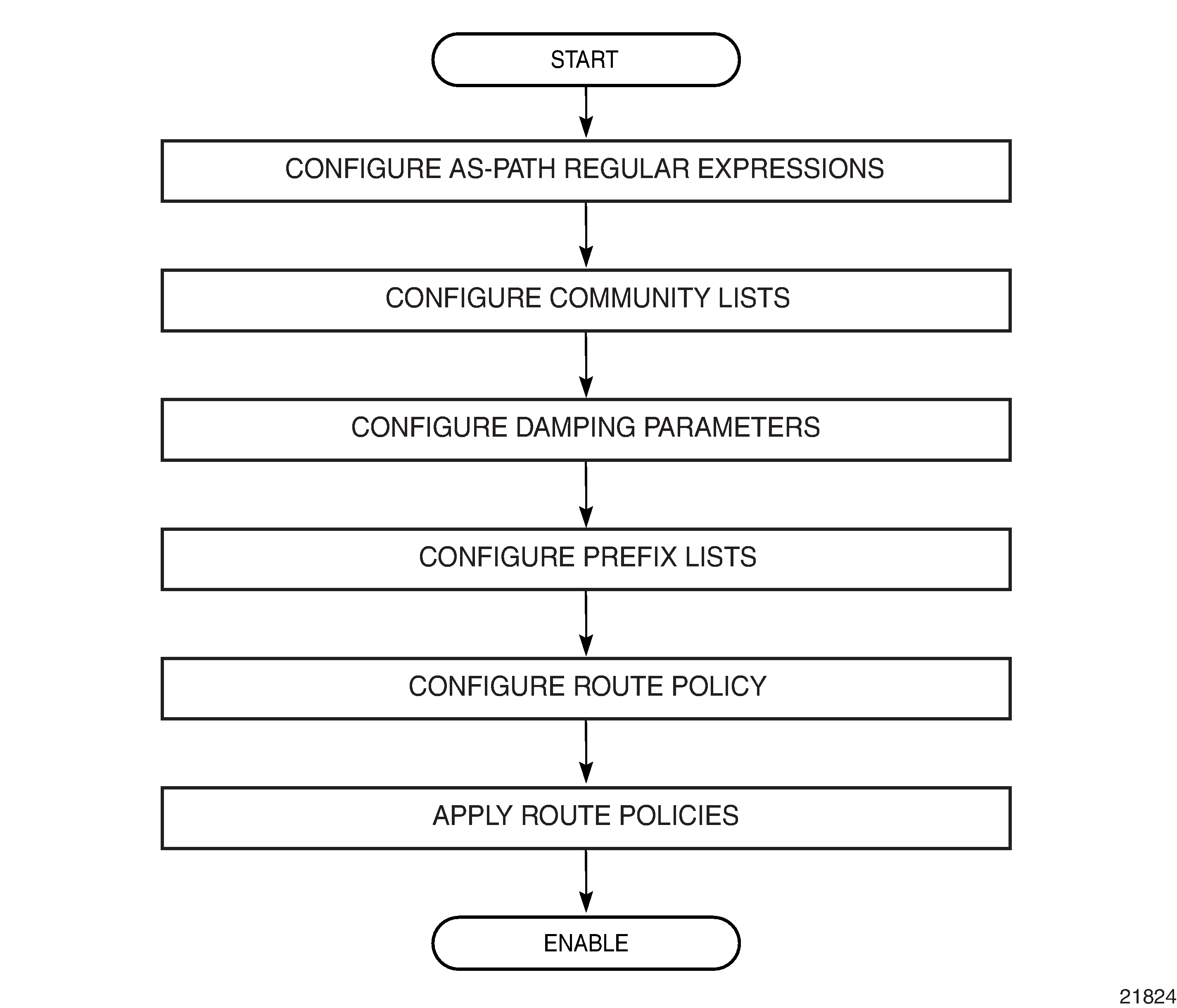
Configuration Notes
When configuring policy statements, the policy statement name must be unique.
Configuring Route Policies with CLI
This section provides information to configure route policies using the command line interface.
Topics in this section include:
Route Policy Configuration Overview
Route policies allow you to configure routing according to specifically defined policies. You can create policies and entries to allow or deny paths based on parameters such as source address, destination address, protocol, and community list.
Policies can be as simple or complex as required. A simple policy can block routes for a specific location or IP address. More complex policies can be configured using numerous policy statement entries containing matching conditions to specify whether to accept or reject the route, control how a series of policies are evaluated, and manipulate the characteristics associated with a route.
When to Create Routing Policies
Route policies are created in the config>router context. There are no default route policies. Each route policy must be explicitly created and applied. Applying route policies can introduce more efficiency as well as more complexity to the capabilities of the 7705 SAR.
Route policies are used to control which MPLS labels should be learned or advertised. Based on the configured routing policy, MPLS labels from certain neighbors can be discarded.
Route policies are also used to control the size and content of the BGP, OSPF, and IS-IS routing tables, the routes that are advertised, and the best route to take to reach a destination.
Route policies can be created to control:
a protocol to export all the active routes learned by that protocol
route characteristics to control which route is selected to act as the active route to reach a destination and advertise the route to neighbors
the protocol to import all routes into the routing table. A routing table must learn about particular routes to be able to forward packets and redistribute to other routing protocols.
damping
Before a route policy is applied, analyze the policy’s purpose and be aware of the results (and consequences) when packets match the specified criteria and the associated actions and default actions, if specified, are executed. Membership reports can be filtered based on a specific source address.
Default Route Policy Actions
Routing protocols have default behaviors for the import and export of routing information.
For BGP, OSPF, and IS-IS, the default route policy actions are as follows:
BGP
import – all routes from BGP peers are accepted and passed to the BGP route selection process
export (internal routes) – all active BGP routes are advertised to BGP peers
export (external routes) – all non-BGP learned routes are not advertised to BGP peers
OSPF
import – all OSPF routes are accepted from OSPF neighbors
export (internal routes) – all OSPF routes are automatically advertised to all neighbors
export (external routes) – all non-OSPF learned routes are not advertised to OSPF neighbors
IS-IS
import – not applicable; all IS-IS routes are accepted from IS-IS neighbors and cannot be controlled by route policies
export (internal routes) – all IS-IS routes are automatically advertised to all neighbors
export (external routes) – all non-IS-IS learned routes are not advertised to IS-IS neighbors
Policy Evaluation
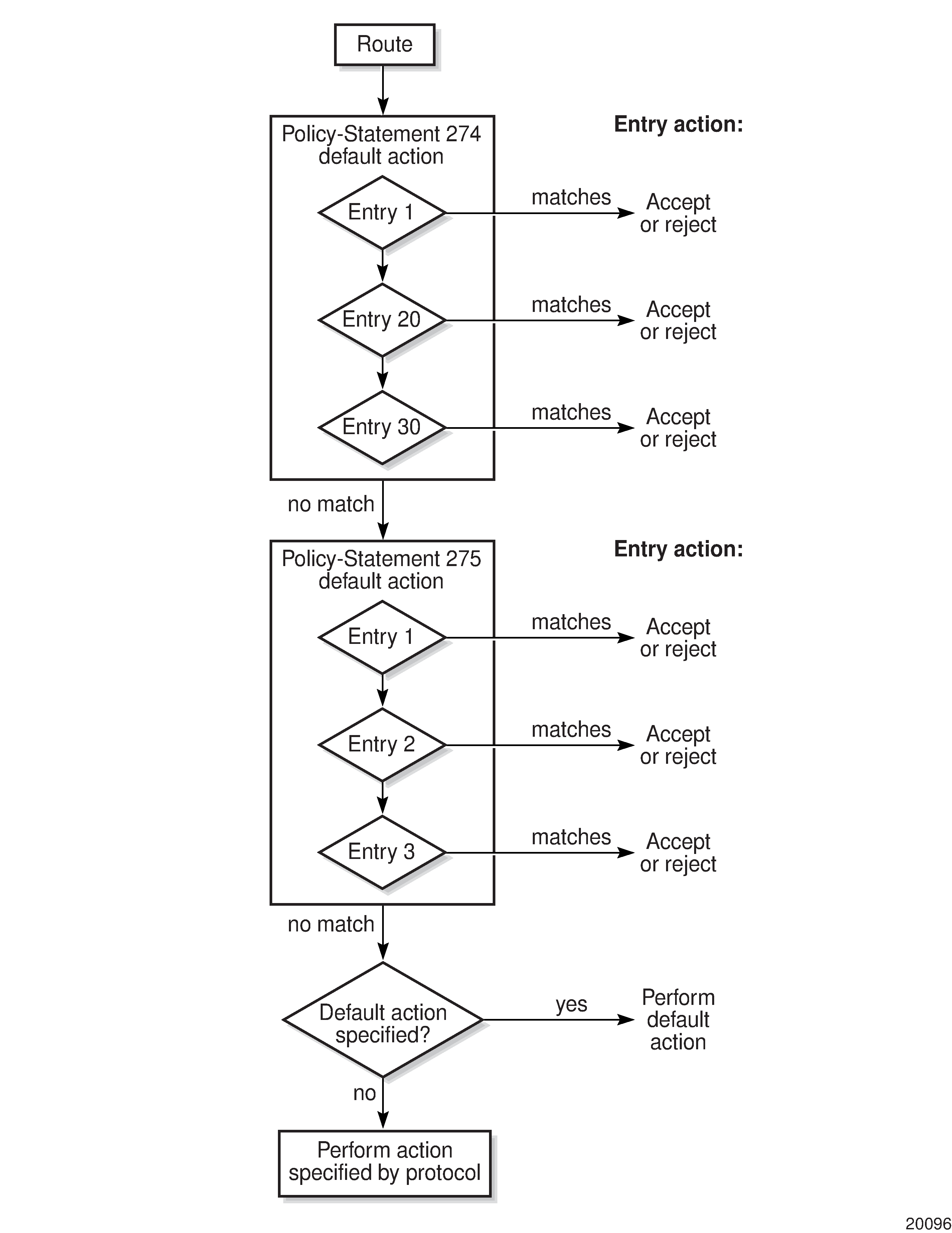
Routing policy statements can consist of one or several entries. The entries specify the matching criteria. A label is compared to the first entry in the policy statement. If it matches, the specified entry action is taken, either accepted or rejected. If the action is to accept or reject the label, that action is taken and the evaluation of the label ends.
If the label does not match the first entry, the label is compared to the next entry (if more than one is configured) in the policy statement. If there is a match with the second entry, the specified action is taken. If the action is to accept or reject the label, that action is taken and the evaluation of the label ends, and so on.
Each route policy statement can have a default-action clause defined. If a default action is defined for one or more of the configured route policies, the default action should be handled in the following ways.
The process stops when the first complete match is found and executes the action defined in the entry.
If the packet does not match any of the entries, the system executes the default action specified in the policy statement.
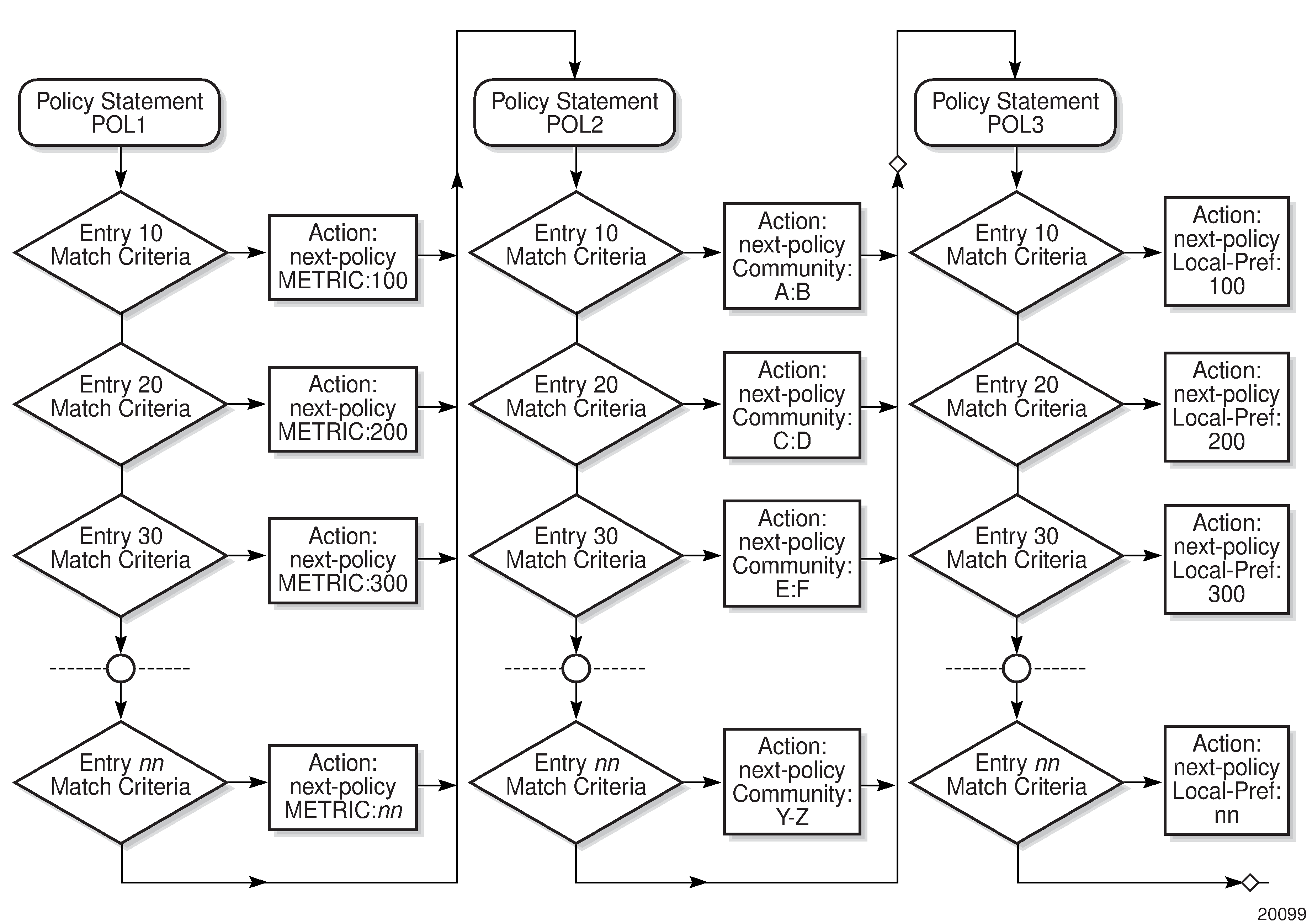
Route policies can also match a given route policy entry and continue to search for other entries within either the same route policy or the next route policy by specifying the next-entry or next-policy option in the entry’s action command. Policies can be constructed to support multiple states to the evaluation and setting of various route attributes.
Route Policy Process Example shows an example of the route policy process.
Next Entry and Next Policy Logic Example shows the next-entry and next-policy route policy processes. The next-entry logic is that for each policy statement, the process checks each entry until the first match is hit, at which point the appropriate action is taken, which could be next-policy.
Damping
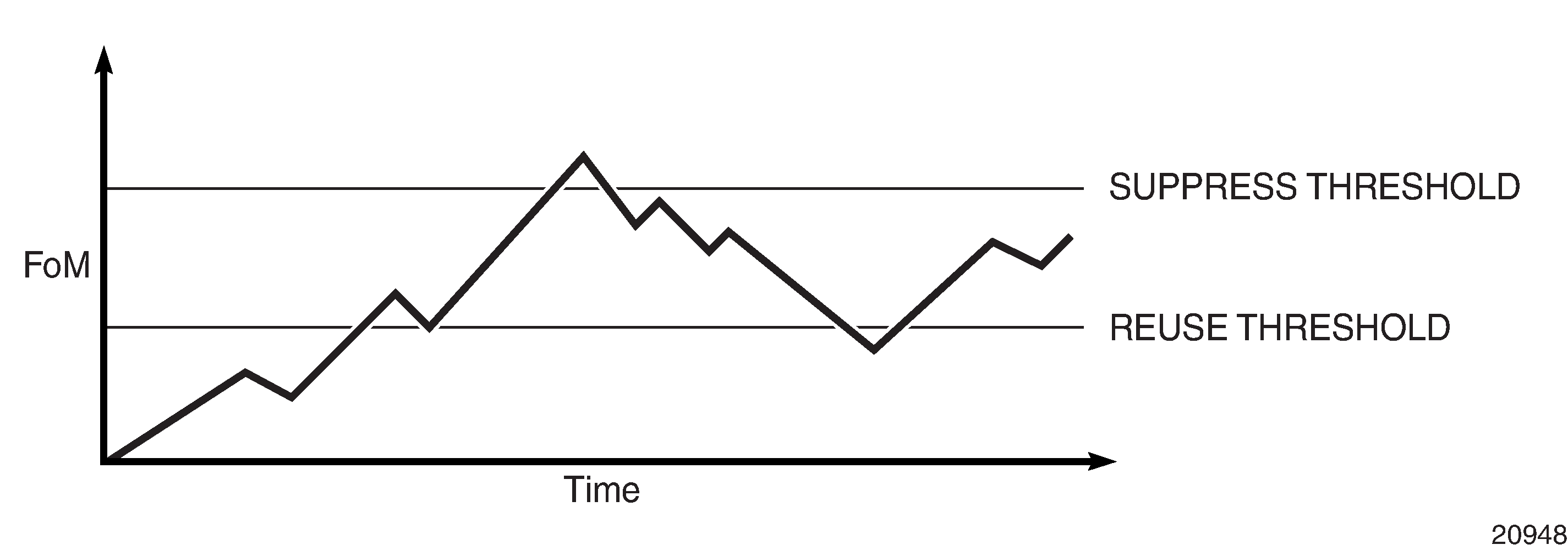
Damping initiates controls when routes flap. Route flapping can occur when an advertised route between nodes alternates (flaps) back and forth between two paths due to network problems that cause intermittent route failures. To limit processing requirements, the amount of routing state change updates propagated must be reduced. Thus, when a route flaps beyond a configured value (the suppress value), then that route is removed from the routing table and routing protocols until the value falls below the reuse value.
A route can be suppressed according to the Figure of Merit (FoM) value. The FoM is a value that is added to a route each time it flaps. A new route begins with an FoM value of 0.
Damping is optional. If damping is configured, the following parameter values must be explicitly specified because there are no default values:
suppress
half-life
reuse
max-suppress
When a route’s FoM value exceeds the suppress value, the route is removed from the routing table. The route is considered to be stable when the FoM drops below the reuse value by means of the specified half-life parameter. The route is then returned to the routing tables. When routes have higher FoM and half-life values, they are suppressed for longer periods of time. Damping Example depicts an example of a flapping route, the suppress threshold, the half-life decay (time), and reuse threshold. The peaks represent route flaps, and the slopes represent half-life decay.
Basic Route Policy Configuration
This section provides information about configuring route policies and shows configuration examples of common tasks.
The minimum route policy parameters that need to be configured are:
policy statement with the following parameters specified:
at least one entry
entry action
The following is an example of route policy configuration, including examples for defining community members, community expressions, and the as-path regular expressions.
A:ALU-B>config>router>policy-options# info
----------------------------------------------
community "all-types" members "5000:[1-6][1-9][0-9]"
community "all-normal" members "5000:[1-5][1-9][0-9]"
community "comm-expression-1" expression "target:1234:111 OR target:1234:222"
community "comm-expression-2" expression "target:555:100 AND target:555:600"
. . .
as-path "Outside madeup paths" expression ".* 5001 .*"
as-path "Outside Internet paths" expression ".* 5002 .*"
policy-statement "RejectOutsideASPaths"
entry 1
from
protocol bgp
as-path "Outside madeup paths"
exit
action reject
exit
exit
entry 2
from
protocol bgp
as-path "Outside Internet paths"
exit
action reject
exit
exit
entry 3
from
protocol ospf
exit
to
protocol bgp
exit
action reject
exit
exit
entry 4
from
protocol isis
exit
to
protocol bgp
exit
action reject
exit
exit
default-action accept
exit
exit
policy-statement "aggregate-customer-peer-only"
entry 1
from
community "all-customer-announce"
exit
action accept
exit
exit
default-action reject
exit
exit
----------------------------------------------
A:ALU-B>config>router>policy-options#
Configuring Route Policy Components
Use the CLI syntax displayed below to configure the following:
- CLI Syntax:
config>router>policy-optionsbegincommitabortprefix-list nameprefix ip-prefix/mask [exact | longer | through length | prefix-length-range length1-length2]policy-statement namedescription textdefault-action {accept | next-entry | next-policy | reject}entry entry-iddescription textaction {accept | next-entry |next-policy | reject}fromneighbor {ip_address | prefix-list name}prefix-list name [name...up to 5 max]
Beginning the Policy Statement
Use the following CLI syntax to begin a policy statement configuration. In order for a policy statement to be complete, an entry must be specified (see Configuring an Entry).
- CLI Syntax:
config>router>policy-optionsbeginpolicy-statement namedescription text
The following error message displays if you try to enter a policy options command without entering begin first.
A:ALU-B>config>router>policy-options# policy-statement ‟allow all”
MINOR: CLI The policy-options must be in edit mode by calling begin before any
changes can be made.
The following example displays policy statement configuration command usage. These commands are configured in the config>router context.
- Example:
config>router# policy-optionspolicy-options# begin
There are no default policy statement options. All parameters must be explicitly configured.
Creating a Route Policy
To enter the mode to create or edit route policies, you must enter the begin keyword at the config>router>policy-options prompt. Other editing commands include:
the commit command, which saves changes made to route policies during a session
the abort command, which discards changes that have been made to route policies during a session
Use the following CLI syntax to enter edit mode:
- CLI Syntax:
config>router>policy-optionsbegin
The following example displays some commands to configure a policy statement. Policy option commands are configured in the config>router context. Use the commit command to save the changes.
- Example:
config>router>policy-options# beginpolicy-options# policy-statement "allow all"policy-options>policy-statement$ description "General Policy"policy-options>policy-statement>default# entry 1policy-options>policy-statement>entry$ action acceptpolicy-options>policy-statement>entry# exitpolicy-options>policy-statement# exitpolicy-options# commit
The following error message displays if you try to modify a policy option without entering begin first.
A:ALU-B>config>router>policy-options# policy-statement ‟allow all”
MINOR: CLI The policy-options must be in edit mode by calling begin before any
changes can be made.
A:ALU-B>config>router>policy-options# info
#------------------------------------------
# Policy
#------------------------------------------
policy-options
begin
policy-statement "allow all"
description "General Policy"
...
exit
exit
----------------------------------------------
A:ALU-B>config>router>policy-options#
Configuring a Default Action
Specifying a default action is optional. The default action controls those packets not matching any policy statement entries. The default action is applied only to those routes that do not match any policy entries.
If no default action is specified and there is no match, the packets are accepted.
A policy statement must include at least one entry (see Configuring an Entry).
To enter the mode to create or edit route policies, you must enter the begin keyword at the config>router>policy-options prompt. Other editing commands include:
the commit command, which saves changes made to route policies during a session
the abort command, which discards changes made to route policies during a session
- CLI Syntax:
config>router>policy-optionsbegincommitabortpolicy-statement namedefault-action {accept |next-entry | next-policy | reject}aigp-metric metricaigp-metric metric addaigp-metric igpas-path {add | replace}nameas-path-prepend as-path [repeat]community {add | remove | replace}name[name...(up to 28 max)]damping {name | none}local-preference local-preferencemetric {add | subtract} metricmetric set {igp | metric}next-hop ip-addressnext-hop-selforigin {igp | egp |incomplete}preferencepreferencetag tagtype type
The following example displays default action configuration command usage. These commands are configured in the config>router>policy-options context.
- Example:
config>router>policy-options# policy-statement "1"policy-statement$ default-actionaccept
The following example displays the default action configuration:
A:ALU-B>config>router>policy-options# info
----------------------------------------------
policy-statement "1"
default-action accept
as-path add "saratoga"
community add "365"
damping "flaptest"
metric igp
next-hop 10.10.10.104
exit
type 1
exit
----------------------------------------------
A:ALU-B>config>router>policy-options#
Configuring an Entry
An entry action must be specified. The other parameters in the entry>action context are optional.
The from>community and from>community expression commands are mutually exclusive for a specific entry. The last community command entered overwrites any previous community command.
- CLI Syntax:
config>router>policy-optionsbegincommitabortpolicy-statement nameentry entry-idaction {accept | next-entry | next-policy | reject}aigp-metric metricaigp-metric metric addaigp-metric igpas-path {add | replace}nameas-path-prepend as-path [repeat]community {add | remove | replace}name[name...(up to 28 max)]damping {name | none}local-preference local-preferencemetric {add | subtract} metricmetric set {igp | metric}next-hop ip-addressnext-hop-selforigin {igp | egp |incomplete}preferencepreferencetag tagtype typedescription description-stringfromarea area-idas-path {add | replace} namecommunity comm-namecommunity expression expressionexternalfamily [ipv4] [vpn-ipv4]group-address prefix-list-nameinterface interface-namelevel {1 | 2}neighbor {ip-address | prefix-list name}origin {igp | egp | incomplete | any}prefix-list name [name...(up to 5 max)]protocol protocol [all | instance instance]source-address ip-addresstag tagtype typetolevel {1 | 2}neighbor {ip-address | prefix-list name}prefix-list name [name...(up to 5 max)]protocol protocol [all | instance instance]
The following example displays entry command usage. These commands are configured in the config>router>policy-options context.
- Example:
config>router>policy-options# policy-statement "1"policy-statement# entry 1policy-statement>entry$ topolicy-statement>entry>to# protocol bgppolicy-statement>entry>to# neighbor 10.10.10.104policy-statement>entry>to# exitpolicy-statement>entry# action acceptpolicy-statement>entry>action# exitpolicy-statement>entry# exitpolicy-statement# entry 2policy-statement>entry$ frompolicy-statement>entry>from# protocol ospfpolicy-statement>entry>from# exitpolicy-statement>entry$ topolicy-statement>entry>to# protocol ospfpolicy-statement>entry>to# neighbor 10.10.0.91policy-statement>entry>to# exitpolicy-statement>entry# action acceptpolicy-statement>entry>action# exit
The following example displays entry parameters and includes the default action parameters that were displayed in the previous section.
A:ALU-B>config>router>policy-options# info
----------------------------------------------
policy-statement "1"
entry 1
to
protocol bgp
neighbor 10.10.10.104
exit
action accept
exit
exit
entry 2
from
protocol ospf
exit
to
protocol ospf
neighbor 10.10.0.91
exit
action accept
exit
exit
default-action accept
. . .
exit
exit
----------------------------------------------
Configuring an AS Path (policy-option)
An AS path is defined by a regular expression in the config>router>policy-options context. Once defined, it can be added, removed, or replaced in a policy statement as part of a default action, an entry action, or an entry from (source) definition. See Configuring a Default Action and Configuring an Entry.
The following example displays as-path command usage.
A:ALU-B>config>router># info
----------------------------------------------
. . .
as-path "Outside madeup paths" expression ".* 5001 .*"
as-path "Outside Internet paths" expression ".* 5002 .*"
. . .
----------------------------------------------
A:ALU-B>config>router>#
Configuring a Community List or Expression
Community lists are composed of a group of destinations that share a common property. Community lists allow you to administer actions on a configured group instead of having to execute identical commands for each member.
Community expressions are logical expressions composed of community lists (community IDs) separated by AND, OR, and NOT operations. Community expressions provide flexible matching of communities.
Community lists and expressions must be enclosed within quotes.
The following example displays community list and community expression configurations:
A:ALU-B>config>router>policy-options# info
----------------------------------------------
community "eastern" members "100:200"
community "western" members "100:300"
community "northern" members "100:400"
community "southern" members "100:500"
community "headquarters" members "100:1000"
community "manor" expression "target:100:111"
community "manor2" expression "target:100:111 AND target:100:555"
policy-statement "1"
entry 1
to
protocol bgp
neighbor 10.10.10.104
exit
entry 10
from
community expression "NOT ([eastern] OR [western])"
exit
action accept
....
----------------------------------------------
Configuring Damping
Observe the following when configuring damping.
For each damping profile, all parameters must be configured.
The suppress value must be greater than the reuse value (see Damping Example).
Damping is enabled in the config>router>bgp context at the BGP global, group, and neighbor levels. If damping is enabled but route policy does not specify a damping profile, the default damping profile is used. This default profile is always present and consists of the following parameters:
half-life: 15 min
max-suppress: 60 min
reuse: 750
suppress: 3000
Use the following CLI syntax to configure damping:
- CLI Syntax:
config>router>policy-optionsdamping namehalf-life minutesmax-suppress minutesreuse integersuppress integer
The following example displays damping configuration command usage.
- Example:
config>router>policy-options#config>router>policy-options#damping damptest123config>router>policy-options#damping# max-suppress 60config>router>policy-options#damping# half-life 15config>router>policy-options#damping# re-use 750config>router>policy-options#damping# suppress 1000config>router>policy-options#damping# exitconfig>router>policy-options#
The following example displays a damping configuration:
A:ALU-B>config>router>policy-options# info
----------------------------------------------
damping "damptest123"
half-life 15
max-suppress 60
reuse 750
suppress 1000
exit
----------------------------------------------
A:ALU-B>config>router>policy-options#
Configuring a Prefix List
Use the following CLI syntax to configure a prefix list:
- CLI Syntax:
config>router>policy-optionsprefix-list nameprefix ip-prefix/prefix-length [exact |longer | through length | prefix-length-range length1-length2]
The following example displays prefix list configuration command usage. These commands are configured in the config>router context.
- Example:
config>router>policy-options# prefix-listpolicy-options# prefix-listwesternpolicy-options>prefix-list# prefix10.10.0.1/8policy-options>prefix-list# prefix10.10.0.2/8policy-options>prefix-list# prefix10.10.0.3/8policy-options>prefix-list# prefix10.10.0.4/8
The following example displays the prefix list configuration.
A:ALU-B>config>router>policy-options# info
----------------------------------------------
prefix-list "western"
prefix 10.10.0.1/8 exact
prefix 10.10.0.2/8 exact
prefix 10.10.0.3/8 exact
prefix 10.10.0.4/8 exact
exit
----------------------------------------------
A:ALU-B>config>router>policy-options>#
Configuring PIM Join/Register Policies
Join policies are used in Protocol Independent Multicast (PIM) configurations to prevent the transport of multicast traffic across a network and the dropping of packets at a router at the edge of the network. PIM Join filters reduce the potential for denial of service (DoS) attacks and PIM state explosion—large numbers of Join messages forwarded to each router on the RPT, resulting in memory consumption.
Register policies are used to prevent any unwanted sources from transmitting multicast streams. You can apply register policies at the RP, or at the edge so that register data does not travel unnecessarily over the network towards the RP.
For information on importing a Join/Register policy into a PIM configuration, see the ‟PIM-SM Routing Policies” and ‟Importing PIM Join/Register Policies” sections in the 7705 SAR Routing Protocols Guide.
Configuring a PIM join or register policy follows the same process as that for any other policy. However, when configuring an entry, include the entry>from>group-address and entry>from>source-address commands. See Configuring an Entry for the CLI syntax.
The (*,G) or (S,G) information is used to forward unicast or multicast packets.
group-address matches the group in join/prune messages
group-address 239.255.50.208/16 exactsource-address matches the source in join/prune messages
source-address 239.255.150.208/16 longerinterface matches any join message received on the specified interface
interface port 1/1/1neighbor matches any join message received from the specified neighbor
neighbor 10.10.10.10
The following example displays the command usage for a PIM join policy named ‟pim_join”. The policy does not allow Join messages for group 239.50.50.208/32 and source 239.255.150.208/16, but does allow other Join messages. These commands are configured in the config>router context.
- Example:
policy-options# beginpolicy-options# policy-statement pim_joinpolicy-options>policy-statement$ entry 10policy-options>policy-statement>entry$ frompolicy-options>policy-statement>entry>from$ group-address 239.255.50.208/16policy-options>policy-statement>entry>from$ source-address 239.255.150.208/16policy-options>policy-statement>entry>from$ exitpolicy-options>policy-statement>entry# action rejectpolicy-options>policy-statement>entry#
The following example displays a PIM register policy that allows registration for (*,239,255.0.0/8). These commands are configured in the config>router context.
- Example:
policy-options# policy-statement reg_polpolicy-options>policy-statement$ entry 10policy-options>policy-statement>entry$ frompolicy-options>policy-statement>entry>from$ group-address 239.255.0.0/8policy-options>policy-statement>entry# action acceptpolicy-options>policy-statement>entry>action# exitpolicy-options>policy-statement>entry# exitpolicy-options>policy-statement# exit
The following example displays the PIM join and register policy configurations:
A:ALA-B>config>router>policy-options# info
----------------------------------------------
...
policy-statement "pim_join"
entry 10
from
group-address "239.50.50.208/32"
source-address 239.255.150.208
exit
action reject
exit
exit
policy-statement "reg_pol"
entry 10
from
group-address "239.255.0.0/8"
exit
action accept
exit
exit
...
----------------------------------------------
Configuring Bootstrap Message Import and Export Policies
Bootstrap import and export policies are used to control the flow of bootstrap messages to and from the rendezvous point (RP).
The following configuration example specifies that there should be no BSR messages received or sent out of interface port 1/1/1. These commands are configured in the config>router context.
- Example:
policy-options# policy-statement pim_import_policypolicy-options>policy-statement$ entry 10policy-options>policy-statement>entry$ frompolicy-options>policy-statement>entry>from$ interface port 1/1/1policy-options>policy-statement>entry>from$ exitpolicy-options>policy-statement>entry# action rejectpolicy-options>policy-statement>entry# exitpolicy-options>policy-statement# exit
- Example:
policy-options# policy-statement pim_export_policypolicy-options>policy-statement$ entry 10policy-options>policy-statement>entry$ topolicy-options>policy-statement>entry>to$ interface port 1/1/1policy-options>policy-statement>entry# action rejectpolicy-options>policy-statement>entry# exitpolicy-options>policy-statement# exit
The following configuration example illustrates the application of the policies to PIM. Up to five import and five export policies can be specified.
- Example:
config>router>pim>rp# bootstrap-import pim_import_policyconfig>router>pim>rp# bootstrap-export pim_export_policy
Configuring LDP-to-Segment Routing Stitching Policies
Use the following CLI syntax to configure route policy options to support LDP-to-Segment Routing (SR) stitching.
- CLI Syntax:
config>router>policy-optionsbeginprefix-list nameprefix ip-prefix/prefix-length [exact | longer | through length | prefix-length-range length1-length2]policy-statement nameentry entry-idfromprotocol isisprefix-list nametoprotocol ldpaction {accept | next-entry | next-policy | reject}
The following is an example of LDP-to-SR stitching route policy options configuration.
- Example:
config>router>policy-options# beginconfig>router>policy-options# prefix-list "prefixes"config>router>policy-options>prefix-list$ prefix 198.51.100.0/24 longerconfig>router>policy-options>prefix-list# exitconfig>router>policy-options# policy-statement "export-SR"config>router>policy-options>policy-statement# entry 10config>router>policy-options>policy-statement>entry# from protocol isisconfig>router>policy-options>policy-statement>entry# from prefix-list "prefixes"config>router>policy-options>policy-statement>entry>from# exitconfig>router>policy-options>policy-statement>entry# to protocol ldpconfig>router>policy-options>policy-statement>entry> to# exitconfig>router>policy-options>policy-statement>entry# action acceptconfig>router>policy-options>policy-statement>entry>action# exitconfig>router>policy-options>policy-statement>entry# exitconfig>router>policy-options# commitconfig>router>policy-options# exit
The following example displays the LDP-to-SR stitching route policy options configuration.
A:NOK-1 Dut-B>config>router>policy-options# info
----------------------------------------------
...
prefix-list "prefixes"
prefix 198.51.100.0/24 longer
exit
policy-statement "export-SR"
entry 10
from
protocol isis
prefix-list "prefixes"
exit
to
protocol ldp
exit
action accept
exit
exit
exit
----------------------------------------------
A:NOK-1 Dut-B>config>router>policy-options#
Route Policy Configuration Management Tasks
This section describes the following route policy configuration management tasks:
Editing Policy Statements and Parameters
Route policy statements can be edited to modify, add, or delete parameters. To enter edit mode, you must enter the begin keyword at the config>router>policy-options prompt. Other editing commands include:
the commit command, which saves changes made to route policies during a session
the abort command, which discards changes that have been made to route policies during a session
The following example displays some commands to configure a policy statement. These commands are configured in the config>router>policy-options context.
- Example:
config>router>policy-options# beginpolicy-options# policy-statement "1"policy-statement# description "Level 1"policy-statement#entry 4policy-statement>entry$ description ‟new entry”policy-statement>entry# frompolicy-statement>entry>from$ prefix-list ‟from hq”policy-statement>entry>from# exitpolicy-statement>entry# action rejectpolicy-statement>entry# commitpolicy-statement>entry# exit
The following example displays the changed configuration.
A:ALU-B>config>router>policy-options>policy-statement# info
----------------------------------------------
description "Level 1"
entry 1
from
neighbor 10.10.10.104
exit
action accept
exit
exit
entry 2
from
prefix-list list1
exit
from
neighbor 10.10.0.91
exit
action accept
exit
exit
entry 4
description "new entry"
from
prefix-list ‟from hq”
exit
action reject
exit
default-action accept
exit
----------------------------------------------
A:ALU-B>config>router>policy-options>policy-statement#
Deleting an Entry
Use the following CLI syntax to delete a policy statement entry:
- CLI Syntax:
config>router>policy-optionsbegincommitabortpolicy-statement nameno entry entry-id
The following example displays the commands required to delete a policy statement entry.
- Example:
config>router>policy-options# beginpolicy-options# policy-statement "1"policy-options>policy-statement# no entry4policy-options>policy-statement# commit
Deleting a Policy Statement
Use the following CLI syntax to delete a policy statement:
- CLI Syntax:
-
config>router>policy-optionsbegincommitabortno policy-statement name
The following example displays the commands required to delete a policy statement.
- Example:
-
config>router>policy-options# beginpolicy-options#no policy-statement 1policy-options# commit
Route Policy Command Reference
Command Hierarchies
Route Policy Configuration Commands
config
- [no] router
- [no] policy-options
- abort
- as-path name expression regular-expression
- no as-path name
- begin
- commit
- community name members comm-id [comm-id … (up to 15 max)]
- community name expression expression [exact]
- no community name [members comm-id]
- [no] damping name
- half-life minutes
- no half-life
- max-suppress minutes
- no max-suppress
- reuse integer
- no reuse
- suppress integer
- no suppress
- [no] policy-statement name
- default-action {accept | next-entry | next-policy | reject}
- no default-action
- aigp-metric metric
- aigp-metric metric add
- aigp-metric igp
- no aigp-metric
- as-path {add | replace} name
- no as-path
- as-path-prepend as-number [repeat]
- no as-path-prepend
- community add name [name...(up to 28 max)]
- community remove name [name...(up to 28 max)]
- community replace name [name...(up to 28 max)]
- no community
- damping {name | none}
- no damping
- local-preference local-preference
- no local-preference
- metric {add | subtract} metric
- metric set {igp | metric}
- no metric
- next-hop ip-address
- no next-hop
- [no] next-hop-self
- origin {igp | egp | incomplete}
- no origin
- preference preference
- no preference
- tag tag
- no tag
- type type
- no type
- description description-string
- no description
- entry entry-id
- no entry
- action {accept | next-entry | next-policy | reject}
- no action
- aigp-metric metric
- aigp-metric metric add
- aigp-metric igp
- no aigp-metric
- as-path {add | replace} name
- no as-path
- as-path-prepend as-number [repeat]
- no as-path-prepend
- community {add name | remove name | replace name} [name...(up to 28 max)]
- no community
- damping {name | none}
- no damping
- local-preference local-preference
- no local-preference
- metric {add | subtract} metric
- metric set {igp | metric}
- no metric
- next-hop ip-address
- no next-hop
- [no] next-hop-self
- origin {igp | egp | incomplete}
- no origin
- preference preference
- no preference
- tag tag
- no tag
- type type
- no type
- description description-string
- no description
- [no] from
- area area-id
- no area
- as-path name
- no as-path
- community comm-name
- community expression expression
- no community
- [no] external
- family [ipv4] [vpn-ipv4] [ipv6] [vpn-ipv6] [mvpn-ipv4] [route-target] [evpn] [label-ipv4] [label-ipv6] [bgp-ls]
- no family
- group-address prefix-list-name
- no group-address
- interface interface-name
- no interface
- level {1 | 2}
- no level
- neighbor {ip-address | prefix-list name}
- no neighbor
- origin {igp | egp | incomplete | any}
- no origin
- prefix-list name [name...(up to 5 max)]
- no prefix-list
- protocol protocol [all | {instance instance}]
- protocol bgp bgp-label
- no protocol
- source-address ip-address
- no source-address
- tag tag
- no tag
- type type
- no type
- [no] to
- level {1 | 2}
- no level
- neighbor {ip-address | prefix-list name}
- no neighbor
- prefix-list name [name...(up to 5 max)]
- no prefix-list
- protocol protocol [all | {instance instance}]
- protocol bgp bgp-label
- no protocol
- [no] prefix-list name
- [no] prefix ip-prefix/prefix-length [exact | longer | through length | prefix-length-range length1-length2]
- [no] triggered-policy
Show Commands
show
- router router-name
- policy [name | damping name | prefix-list name | as-path name | community name | admin]
Command Descriptions
Configuration Commands
Generic Commands
abort
Syntax
abort
Context
config>router>policy-options
Description
This command discards changes made to a route policy.
Default
n/a
begin
Syntax
begin
Context
config>router>policy-options
Description
This command enters the mode to create or edit route policies.
Default
n/a
commit
Syntax
commit
Context
config>router>policy-options
Description
This command saves changes made to a route policy.
Default
n/a
description
Syntax
description description-string
no description
Context
config>router>policy-options>policy-statement
config>router>policy-options>policy-statement>entry
Description
This command creates a text description that is stored in the configuration file to help identify the contents of the entity.
The no form of the command removes the string from the configuration.
Default
n/a
Parameters
- description-string
the description character string. Allowed values are any string up to 80 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
Route Policy Options
as-path
Syntax
as-path name expression regular-expression
no as-path name
Context
config>router>policy-options
Description
This command creates a route policy AS path regular expression statement to use in route policy entries. See Regular Expressions for information.
The no form of the command deletes the AS path regular expression statement.
Default
no as-path
Parameters
- name
the AS path regular expression name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
- regular-expression
the AS path regular expression (any string or null)
community
Syntax
community name members comm-id [comm-id...(up to 15 max)]
community name expression expression [exact]
no community name [members comm-id]
Context
config>router>policy-options
Description
This command creates a route policy community list to use in route policy entries.
The community name expression form of the command extends the community name members form by allowing the community list structure to support AND, OR, and NOT operators.
When the community name members command is used, community lists operate with implicit AND support only, and all communities must match to provide a positive match, as shown in the following example, where the only routes that match include all three communities:
community ‟north” members ‟target:1234:111” ‟target:1234:222” ‟target:1234:333”
Using the community name expression command allows for configuration of a community expression using Boolean operators to provide flexible matching of communities. The AND operator provides functionality equivalent to the community name members command; the OR operator allows an OR match of communities; and the NOT operator allows inverted matches. If required, operators may be chained (for example, AND NOT) or enclosed within parentheses. The entire expression must be enclosed within quotation marks.
community ‟north2” expression ‟target:1234:111 AND target:1234:222 AND target: 1234:333”
community ‟south” expression ‟target:1234:111 OR target:1234:222”
community ‟east” expression ‟target:1234:1.1 AND NOT target:1234:191”
community ‟west” expression ‟[community list A] OR ([community list B] AND [community list C])”
The first example above demonstrates the implementation of AND operators, which is equivalent to the members syntax (that is, ‟north” and ‟north2” are equivalent). The second example shows the OR operator, which matches a route that has target:1234:111 or target:1234:222. The third example shows the combined AND NOT operators, which matches a route that matches the regular expression for target:1234:1.1 except for target:1234.191, where ‟1.1” means any match of 111, 121, 131, 141, 151, 161, 171, 181, or 191. The fourth example shows the grouping of lists B and C through the use of parentheses.
The no form of the command deletes the community list or the provided community ID.
Default
no community
Parameters
- name
the community list or expression name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
- comm-id
the community ID. Up to 15 community ID strings can be specified with a total maximum of 72 characters. A community ID can be specified in four different forms:
2byte-asnumber:comm-val
reg-ex
ext-comm
well-known-comm
- expression
a logical community expression containing terms and operators. It can contain sub-expressions enclosed in parentheses. Allowed values are any string up to 900 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
- exact
the community expression only matches the route with the specified expression. Without the exact keyword, a community expression evaluates to be true if any member is present.
policy-options
Syntax
[no] policy-options
Context
config>router
Description
This command enables the context to configure route policies. Route policies are applied to the routing protocol.
The no form of the command deletes the route policy configuration.
Default
n/a
policy-statement
Syntax
[no] policy-statement name
Context
config>router>policy-options
Description
This command enables the context to configure a route policy statement.
Route policy statements control the flow of routing information from a specific protocol or protocols.
The policy-statement is a logical grouping of match and action criteria. A single policy-statement can affect routing in one or more protocols and/or one or more protocols’ peers/neighbors. A single policy-statement can also affect the export of routing information.
The no form of the command deletes the policy statement.
Default
no policy-statement
Parameters
- name
the route policy statement name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
triggered-policy
Syntax
[no] triggered-policy
Context
config>router
Description
This command triggers route policy re-evaluation.
By default, when a change is made to a policy in the config router policy-options context and then committed, the change is effective immediately. However, there may be circumstances where the changes should or must be delayed; for example, when a policy change is implemented that would affect every BGP peer on a 7705 SAR. It is more effective to control changes on a peer-by-peer basis.
If the triggered-policy command is enabled and a given peer is established, and you want the peer to remain up, then, in order for a change to a route policy to take effect, a clear command with the soft or soft-inbound option must be used. In other words, when a triggered-policy is enabled, any routine policy change or policy assignment change within the protocol will not take effect until the protocol is reset or a clear command is issued to re-evaluate route policies; for example, clear router bgp neighbor x.x.x.x soft. This keeps the peer up, and the change made to a route policy is applied only to that peer, or group of peers.
Default
disabled — dynamic route policy is enabled; policy-option configuration changes take effect immediately
Route Policy Damping Commands
damping
Syntax
[no] damping name
Context
config>router>policy-options
Description
This command creates a context to configure a route damping profile to use in route policy entries.
If damping is enabled and the route policy does not specify a damping profile, the default damping profile is used. This default profile is always present and consists of the following parameters:
Half-life: 15 m
Max-suppress: 60 m
Suppress-threshold: 3000
Reuse-threshold: 750
The no form of the command deletes the named route damping profile and uses the default damping profile.
Default
no damping
Parameters
- name
the damping profile name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
half-life
Syntax
half-life minutes
no half-life
Context
config>router>policy-options>damping
Description
This command configures the half-life value for the route damping profile.
The half-life value is the time, expressed in minutes, required for a route to remain stable in order for the Figure of Merit (FoM) value to be reduced by one half; for example, if the half-life value is 6 and the route remains stable for 6 min, then the new FoM value is 3. After another 3 min pass and the route remains stable, the new FoM value is 1.5.
When the FoM value falls below the reuse threshold, the route is once again considered valid and can be reused or included in route advertisements.
The no form of the command removes the half-life parameter from the damping profile and uses the value from the default profile.
Default
no half-life
Parameters
- minutes
the half-life in minutes, expressed as a decimal integer
max-suppress
Syntax
max-suppress minutes
no max-suppress
Context
config>router>policy-options>damping
Description
This command configures the maximum suppression value for the route damping profile.
This value indicates the maximum time, expressed in minutes, that a route can remain suppressed.
The no form of the command removes the maximum suppression parameter from the damping profile and uses the value from the default profile.
Default
no max-suppress
Parameters
- minutes
the maximum suppression time, in minutes, expressed as a decimal integer
reuse
Syntax
reuse integer
no reuse
Context
config>router>policy-options>damping
Description
This command configures the reuse value for the route damping profile. This value must be less than the suppress value.
When the Figure of Merit (FoM) value falls below the reuse threshold, the route is once again considered valid and can be reused or included in route advertisements.
The no form of the command removes the reuse parameter from the damping profile and uses the value from the default profile.
Default
no reuse
Parameters
- integer
the reuse value, expressed as a decimal integer
suppress
Syntax
suppress integer
no suppress
Context
config>router>policy-options>damping
Description
This command configures the suppression value for the route policy damping profile. This value must be greater than the reuse value
A route is suppressed when it has flapped frequently enough to increase the Figure of Merit (FoM) value so that it exceeds the suppress threshold limit. When the FoM value exceeds the suppress threshold limit, the route is removed from the route table or inclusion in advertisements.
The no form of the command removes the suppress parameter from the damping profile and uses the value from the default profile.
Default
no suppress
Parameters
- integer
the suppress value expressed as a decimal integer
Route Policy Prefix Commands
prefix-list
Syntax
[no] prefix-list name
Context
config>router>policy-options
Description
This command creates a context to configure a prefix list to use in route policy entries.
An empty prefix list can be configured for preprovisioning. This empty prefix list does find a match when referred to by a policy. When removing member prefixes from a prefix list, the prefix list does not automatically get removed when the last member is removed. If required, an empty prefix list must be explicitly removed using the no form of the command.
The no form of the command deletes the named prefix list.
Default
n/a
Parameters
- name
the prefix list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
prefix
Syntax
[no] prefix ip-prefix/prefix-length [exact | longer | through length | prefix-length-range length1-length2]
Context
config>router>policy-options>prefix-list
Description
This command creates a prefix entry in the route policy prefix list.
The no form of the command deletes the prefix entry from the prefix list.
Parameters
- ip-prefix/prefix-length
the IPv4 or IPv6 prefix for the prefix list entry
- exact
the prefix list entry only matches the route with the specified ip-prefix and prefix-length values
- longer
the prefix list entry matches any route that matches the specified ip-prefix and has a prefix-length value greater than the specified prefix-length
- length
the prefix list entry matches any route that matches the specified ip-prefix and has a prefix-length value within the specified length values
- length1 - length2
a route must match the most significant bits and have a prefix-length value within the given range
Route Policy Entry Match Commands
entry
Syntax
entry entry-id
no entry
Context
config>router>policy-options>policy-statement
Description
This command enables the context to edit route policy entries within the route policy statement.
Multiple entries can be created using unique entries. The 7705 SAR exits the filter when the first match is found and executes the action specified. For this reason, entries must be sequenced correctly from most to least explicit.
An entry does not require matching criteria defined (in which case, everything matches) but must have an action defined in order to be considered complete. Entries without an action are considered incomplete and will be rendered inactive.
The no form of the command removes the specified entry from the route policy statement.
Default
n/a
Parameters
- entry-id
the entry ID expressed as a decimal integer. An entry-id uniquely identifies match criteria and the corresponding action. It is recommended that multiple entries be given entry-ids in staggered increments. This allows users to insert a new entry in an existing policy without requiring renumbering of all the existing entries.
from
Syntax
[no] from
Context
config>router>policy-options>policy-statement>entry
Description
This command enables the context to configure policy match criteria based on a route’s source or the protocol from which the route is received.
If no condition is specified, all route sources are considered to match.
The no form of the command deletes the source match criteria for the route policy statement entry.
to
Syntax
[no] to
Context
config>router>policy-options>policy-statement>entry
Description
This command enables the context to configure export policy match criteria based on a route’s destination or the protocol into which the route is being advertised.
If no condition is specified, all route destinations are considered to match.
The to command context only applies to export policies. If it is used for an import policy, match criteria is ignored.
The no form of the command deletes export match criteria for the route policy statement entry.
area
Syntax
area area-id
no area
Context
config>router>policy-options>policy-statement>entry>from
Description
This command configures an OSPF area as a route policy match criterion.
This match criterion is only used in export policies.
All OSPF routes (internal and external) are matched using this criterion if the best path for the route is by the specified area.
The no form of the command removes the OSPF area match criterion.
Default
n/a
Parameters
- area-id
the OSPF area ID expressed in dotted-decimal notation or as a 32-bit decimal integer
as-path
Syntax
as-path name
no as-path
Context
config>router>policy-options>policy-statement>entry>from
Description
This command configures an AS path regular expression statement as a match criterion for the route policy entry. If no AS path criterion is specified, any AS path is considered to match. AS path regular expression statements are configured at the global route policy level (config>router>policy-options>as-path name).
The no form of the command removes the AS path regular expression statement as a match criterion.
Default
no as-path
Parameters
- name
the AS path regular expression name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
The name specified must already be defined.
community
Syntax
community comm-name
community expression expression
no community
Context
config>router>policy-options>policy-statement>entry>from
Description
This command configures a community list or expression as a match criterion for the route policy entry. If no community list or expression is specified, any community is considered a match.
The no form of the command removes the community list or expression match criterion.
Default
no community
Parameters
- comm-name
the community list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
The comm-name specified must already have its members defined using the config>router>policy-options>community name members command.
- expression
the community expression. Allowed values are any expression up to 900 characters long composed of one or more expressions separated by AND, OR, and NOT operators. Operators may be combined (for example, OR NOT).
An expression can also be a community name enclosed in square brackets.
If the expression contains special characters (such as #, $, or spaces), the entire string must be enclosed in double quotes.
The expression specified must already be defined using the config>router>policy-options>community name expression command.
external
Syntax
[no] external
Context
config>router>policy-options>policy-statement>entry>from
Description
This command specifies the external IS-IS route matching criteria for the entry.
Default
no external
family
Syntax
family [ipv4] [vpn-ipv4] [ipv6] [vpn-ipv6] [mvpn-ipv4] [route-target] [evpn] [label-ipv4] [label-ipv6] [bgp-ls]
no family
Context
config>router>policy-options>policy-statement>entry>from
Description
This command specifies address families as matching conditions.
Parameters
- ipv4
specifies IPv4 routing information
- vpn-ipv4
-
specifies VPN-IPv4 routing information
- ipv6
-
specifies IPv6 routing information
- vpn-ipv6
-
specifies VPN-IPv6 routing information
- mvpn-ipv4
-
specifies MVPN-IPv6 routing information
- evpn
-
specifies EVPN routing information
- route-target
-
specifies RTC routing information
- label-ipv4
specifies labeled IPv4 routing information
- label-ipv6
-
specifies labeled IPv6 routing information
- bgp-ls
specifies BGP-LS routing information
group-address
Syntax
group-address prefix-list-name
no group-address
Context
config>router>policy-options>policy-statement>entry>from
Description
This command specifies the multicast group address prefix list containing multicast group addresses that are embedded in the join or prune packet as a filter criterion. The prefix list must be configured prior to entering this command. Prefix lists are configured in the config>router>policy-options>prefix-list context.
The no form of the command removes the criterion from the configuration.
Default
no group-address
Parameters
- prefix-list-name
the prefix-list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes. The prefix-list-name is defined in the config>router>policy-options>prefix-list context.
interface
Syntax
interface interface-name
no interface
Context
config>router>policy-options>policy-statement>entry>from
Description
This command specifies the router interface, specified either by name or address, as a filter criterion.
The no form of the command removes the criterion from the configuration.
Default
no interface
Parameters
- interface-name
the name of the interface used as a match criterion for this entry. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
level
Syntax
level {1 | 2}
no level
Context
config>router>policy-options>policy-statement>entry>from
config>router>policy-options>policy-statement>entry>to
Description
This command specifies the IS-IS route level as a match criterion for the entry.
Default
no level
Parameters
- 1 | 2
matches the IS-IS route learned from level 1 or level 2
neighbor
Syntax
neighbor {ip-address | prefix-list name}
no neighbor
Context
config>router>policy-options>policy-statement>entry>from
config>router>policy-options>policy-statement>entry>to
Description
This command specifies the neighbor address as found in the source address of the actual join and prune message as a filter criterion. If no neighbor is specified, any neighbor is considered a match.
The no form of the command removes the neighbor IP match criterion from the configuration.
Default
no neighbor
Parameters
- ip-address
the neighbor IPv4 or IPv6 address
- name
the prefix list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
The name specified must already be defined.
origin
Syntax
origin {igp | egp | incomplete | any}
no origin
Context
config>router>policy-options>policy-statement>entry>from
Description
This command configures a BGP origin attribute as a match criterion for a route policy statement entry. If no origin attribute is specified, any BGP origin attribute is considered a match.
The no form of the command removes the BGP origin attribute match criterion.
Default
no origin
Parameters
- igp
configures matching path information originating within the local AS
- egp
configures matching path information originating in another AS
- incomplete
configures matching path information learned by another method
- any
ignores this criteria
prefix-list
Syntax
prefix-list name [name...(up to 5 max)]
no prefix-list
Context
config>router>policy-options>policy-statement>entry>from
config>router>policy-options>policy-statement>entry>to
Description
This command configures a prefix list as a match criterion for a route policy statement entry.
If no prefix list is specified, any network prefix is considered a match.
An empty prefix list evaluates as if no match was found.
The prefix list specifies the network prefix (this includes the prefix and length) that a specific policy entry applies to.
Up to five prefix list names can be specified.
The no form of the command removes the prefix list match criterion.
Default
no prefix-list
Parameters
- name
the prefix list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
protocol
Syntax
protocol protocol [all | {instance instance}]
protocol bgp bgp-label
no protocol
Context
config>router>policy-options>policy-statement>entry>from
config>router>policy-options>policy-statement>entry>to
Description
This command configures a routing protocol as a match criterion for a route policy statement entry. This command is used for both import and export policies depending on how it is used.
If no protocol criterion is specified, any protocol is considered a match.
The no form of the command removes all instances of the protocol from the match criterion.
Default
no protocol
Parameters
- protocol
the protocol name to match. The list of protocols supported under from differs from the list supported under to.
- all
specifies that all instances of the protocol are used as match criteria (only applies to IS-IS
- instance
the instance ID of the specified protocol (only applies to IS-IS). If no instance is specified, instance 0 is used.
source-address
Syntax
source-address ip-address
no source-address
Context
config>router>policy-options>policy-statement>entry>from
Description
This command specifies a multicast data source address or prefix list as a match criterion for this entry.
The no form of the command removes the criterion from the configuration.
Default
n/a
Parameters
- ip-address
the source IPv4 or IPv6 address
tag
Syntax
tag tag
no tag
Context
config>router>policy-options>policy-statement>entry>from
Description
This command adds an integer tag to the static or IGP routes. These tags are then matched to control route redistribution. A decimal or hexadecimal value can be entered. Values entered in hexadecimal are converted to decimal in the CLI.
The no form of the command removes the tag field match criterion.
Default
no tag
Parameters
- tag
matches a specific external LSA tag field (can be hexadecimal or decimal)
type
Syntax
type type
no type
Context
config>router>policy-options>policy-statement>entry>from
Description
This command configures an OSPF type metric as a match criterion in the route policy statement entry.
If no type is specified, any OSPF type is considered a match.
The no form of the command removes the OSPF type match criterion.
Parameters
- type
the OSPF type metric
Route Policy Action Commands
default-action
Syntax
default-action {accept | next-entry | next-policy | reject}
no default-action
Context
config>router>policy-options>policy-statement
Description
This command enables the context to configure actions for routes that do not match any route policy statement entries when the accept parameter is specified.
The default action clause can be set to all available action states, including accept, reject, next-entry, and next-policy. If the action states accept or reject, the policy evaluation terminates and the appropriate result is returned.
If a default action is defined and no matches occurred with the entries in the policy, the default action clause is used.
If a default action is defined and one or more matches occurred with the entries of the policy, the default action is not used.
The no form of the command deletes the default-action context for the policy statement.
Default
no default-action
Parameters
- accept
routes matching the entry match criteria are accepted and propagated
- next-entry
the actions specified are made to the route attributes and then policy evaluation continues with the next policy entry (if any others are specified)
- next-policy
the actions specified are made to the route attributes and then policy evaluation continues with the next route policy (if any others are specified)
- reject
routes matching the entry match criteria are rejected
action
Syntax
action {accept | next-entry | next-policy | reject}
no action
Context
config>router>policy-options>policy-statement>entry
Description
This command enables the context to configure actions to take for routes matching a route policy statement entry.
This command is required and must be entered for the entry to be active.
Any route policy entry without the action command is considered incomplete and is made inactive.
The no form of the command deletes the action context from the entry.
Default
no action
Parameters
- accept
specifies that routes matching the entry match criteria are accepted and propagated
- next-entry
the actions specified are made to the route attributes and then policy evaluation continues with the next policy entry (if any others are specified)
- next-policy
the actions specified are made to the route attributes and then policy evaluation continues with the next route policy (if any others are specified)
- reject
routes matching the entry match criteria are rejected
aigp-metric
Syntax
aigp-metric metric
aigp-metric metric add
aigp-metric igp
no aigp-metric
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns a BGP AIGP metric to routes matching the entry. The effect of this command on a route that is matched and accepted by a route policy entry depends on how the policy is applied (whether it is a BGP import policy or BGP export policy), the type of route, and the specific form of the command.
In a BGP import policy, this command is used to:
associate an AIGP metric with an IBGP route received with an empty AS path and no AIGP attribute
associate an AIGP metric with an EBGP route received without an AIGP attribute that has an AS path containing only AS numbers belonging to the local AIGP administrative domain
modify the received AIGP metric value prior to BGP path selection
In a BGP export policy, this command is used to:
add the AIGP attribute and set the AIGP metric value in a BGP route originated by exporting a direct, static, or IGP route from the routing table
remove the AIGP attribute from a route advertisement to a particular peer
modify the AIGP metric value in a route advertisement to a particular peer
The no form of the command removes the AIGP metric from the routes.
Default
no aigp-metric
Parameters
- metric
the administratively defined metric
- metric add
adds a configured metric value to the current AIGP metric value
- igp
sets the AIGP metric value to the IGP metric value
as-path
Syntax
as-path {add | replace} name
no as-path
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns a BGP AS path list to routes matching the route policy statement entry. If no AS path list is specified, the AS path attribute is not changed.
The no form of the command disables the AS path list editing action from the route policy entry.
Default
no as-path
Parameters
- add
the AS path list is to be prepended to an existing AS list
- replace
the AS path list replaces any existing AS path attribute
- name
the AS path list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes. The name specified must already be defined.
as-path-prepend
Syntax
as-path-prepend as-number [repeat]
no as-path-prepend
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command prepends a BGP AS number once or numerous times to the AS path attribute of routes matching the route policy statement entry. If an AS number is not configured, the AS path is not changed.
If the optional number is specified, then the AS number is prepended as many times as indicated by the number.
The no form of the command disables the AS path prepend action from the route policy entry.
Default
no as-path-prepend
Parameters
- as-number
the AS number to prepend expressed as a decimal integer
- repeat
the number of times to prepend the specified AS number expressed as a decimal integer
community
Syntax
community add name [name...(up to 28 max)]
community remove name [name...(up to 28 max)]
community replace name [name...(up to 28 max)]
no community
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command adds, removes, or replaces a BGP community list or expression to or from routes matching the route policy statement entry. If no community list or expression is specified, the community path attribute is not changed. Up to 28 community list or expression names can be used in one add, remove, or replace command.
The community list or expression changes the community path attribute according to the add, remove or replace keywords. If more than one of the keywords is used in a single command, first add is applied, then remove is applied. However, replace overwrites any add or remove.
The no form of the command disables the action to edit the community path attribute for the route policy entry.
Default
no community
Parameters
- add
the specified community list or expression is added to any existing list of communities
- remove
the specified community list or expression is removed from the existing list of communities
- replace
the specified community list or expression replaces any existing community attribute
- name
the community list name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes.
damping
Syntax
damping {name | none}
no damping
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command configures a damping profile used for routes matching the route policy statement entry. If no damping criteria is specified, the default damping profile is used.
The no form of the command removes the damping profile associated with the route policy entry.
Default
no damping
Parameters
- name
the damping profile name. Allowed values are any string up to 32 characters long composed of printable, 7-bit ASCII characters. If the string contains special characters (such as #, $, or spaces), the entire string must be enclosed within double quotes. The name specified must already be defined.
- none
disables route damping for the route policy
local-preference
Syntax
local-preference local-preference
no local-preference
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns a BGP local preference to routes matching a route policy statement entry. If no local preference is specified, the BGP configured local preference is used.
The no form of the command disables assigning a local preference in the route policy entry.
Default
no local-preference
Parameters
- local-preference
the local preference expressed as a decimal integer
metric
Syntax
metric {add | subtract} metric
metric set {igp | metric}
no metric
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
In a BGP import or export policy, this command assigns a Multi-Exit Discriminator (MED) value to routes matched by the policy statement entry. The MED value may be set to a fixed value (overriding the received value), set to the routing table cost of the route that is used to resolve the next hop of the BGP route (the metric set igp command), or modified by adding or subtracting a fixed value offset (the metric add | subtract command).
When used in a BGP export policy, the metric set igp command has the same effect as the med-out igp-cost command (see the 7705 SAR Routing Protocols Guide, ‟BGP Command Reference”) except that it applies only to the routes matched by the policy entry. The effect of the metric set igp command depends on the BGP policy type and the route type as summarized in Effect of Setting the metric set igp Command.
BGP Policy Type |
Matched Route Type |
Effect of metric set igp Command |
|---|---|---|
Export |
Non-BGP route (for example, static, OSPF, or IS-IS) |
Adds the MED attribute and sets it to the metric of the non-BGP route in the routing table manager (RTM) |
Export |
BGP route without MED |
Adds the MED attribute and sets it to the metric of the route or tunnel used to resolve the BGP next hop |
Export |
BGP route with MED assigned |
Overwrites the MED value with the metric of the route or tunnel used to resolve the BGP next hop |
The no form of the command removes the MED value from the route policy statement. If a MED value is configured for a BGP peer using the med-out command, that value is used (see the 7705 SAR Routing Protocols Guide, ‟BGP Command Reference”). If no MED is configured, no MED value is advertised.
Default
no metric
Parameters
- add
the specified metric is added to any existing metric. If the result of the addition results in a number greater than 4294967295, the value 4294967295 is used.
- subtract
the specified metric is subtracted from any existing metric. If the result of the subtraction results in a number less than 0, the value of 0 is used.
- set
the specified metric replaces any existing metric
- igp
sets the MED value to the routing table cost of the route that is used to resolve the next hop of the BGP route
- metric
the metric modifier expressed as a decimal integer
next-hop
Syntax
next-hop ip-address
no next-hop
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns the specified next-hop IP address to routes matching the policy statement entry. If a next-hop IP address is not specified, the next-hop attribute is not changed.
The no form of the command disables assigning a next-hop address in the route policy entry.
Default
no next-hop
Parameters
- ip-address
the next-hop IP address
next-hop-self
Syntax
[no] next-hop-self
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command advertises a next-hop IP address belonging to this router even if a third-party next hop is available to routes matching the policy statement entry.
The no form of the command disables advertising the next-hop-self option for the route policy entry.
Default
no next-hop-self
origin
Syntax
origin {igp | egp | incomplete}
no origin
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command sets the BGP origin assigned to routes exported into BGP.
If the routes are exported into protocols other than BGP, this option is ignored.
The no form of the command disables setting the BGP origin for the route policy entry.
Default
no origin
Parameters
- igp
sets the path information as originating within the local AS
- egp
sets the path information as originating in another AS
- incomplete
sets the path information as learned by some other means
preference
Syntax
preference preference
no preference
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns a route preference to routes matching the route policy statement entry.
If no preference is specified, the default route table manager (RTM) preference for the protocol is used.
The no form of the command disables setting an RTM preference in the route policy entry.
Default
no preference
Parameters
- preference
the route preference expressed as a decimal integer
tag
Syntax
tag tag
no tag
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns an OSPF, IS-IS, or RIP tag to routes that do not match any entry (for default action) or that match the entry (for action). A decimal or hexadecimal value can be entered. Values entered in hexadecimal are converted to decimal in the CLI.
The no form of the command removes the tag.
Default
no tag
Parameters
- tag
assigns an OSPF, IS-IS, or RIP tag (decimal or hexadecimal values)
type
Syntax
type type
no type
Context
config>router>policy-options>policy-statement>default-action
config>router>policy-options>policy-statement>entry>action
Description
This command assigns an OSPF type metric to routes that do not match any entry (for default action) or that match the entry (for action). The no form of the command disables assigning an OSPF type in the route policy entry.
Default
no type
Parameters
- type
specifies the OSPF type metric
Show Commands
policy
Syntax
policy [name | damping name | prefix-list name |as-path name | community name | admin]
Context
show>router
Description
This command displays configured policy statement information.
Parameters
- name
if a name is provided, the matching policy statement is shown. If no statement name is specified, a list of all policies statements and descriptions are shown.
- damping
displays the damping profile for use in the route policy
- prefix-list
displays the prefix lists configured in the route policy
- as-path
displays AS path regular expression statements used in the route policy
- community
displays community lists used in the route policy
- admin
if this keyword is included, the entire policy option configuration is shown, including any uncommitted configuration changes. This command is similar to the info command.
Output
The following outputs are examples of route policy information, and Route Policy Field Descriptions describes the fields.
A:ALU-1# show router policy
===============================================================================
Route Policies
===============================================================================
Policy Description
-------------------------------------------------------------------------------
BGP To OSPF Policy Statement For 'BGP To OSPF'
Direct And Aggregate Policy Statement ABC
-------------------------------------------------------------------------------
Policies : 3
===============================================================================
A:ALU-1#
A:ALU-1# show router policy admin
prefix-list "All-Routes"
prefix 0.0.0.0/0 longer
prefix 2.0.0.0/8 longer
prefix 3.0.0.0/8 longer
prefix 4.0.0.0/8 longer
prefix 5.0.0.0/8 longer
prefix 6.0.0.0/8 exact
prefix 224.0.0.0/24 longer
exit
community "65206" members "no-export" "no-export-subconfed"
community "AS65000" members "701:65000"
as-path "test" "14001 701"
as-path "test1" "1234{1,6} (56|47) (45001|2000|1534)* 9+"
damping "TEST-LOW"
half-life 22
max-suppress 720
reuse 10000
suppress 15000
exit
damping "TEST-HIGH"
half-life 22
max-suppress 720
reuse 1000
suppress 5000
exit
damping "TEST-MEDIUM"
half-life 22
max-suppress 720
reuse 5000
suppress 11000
exit
policy-statement "BGP To OSPF"
description "Policy Statement For 'BGP To OSPF'"
entry 10
description "Entry For Policy 'BGP To OSPF"
from
protocol bgp
exit
to
protocol rip
exit
action accept
metric set 1
next-hop 10.0.18.200
tag 134250805
exit
exit
default-action reject
exit
policy-statement "Direct And Aggregate"
entry 10
from
protocol direct
exit
to
protocol bgp
exit
action accept
exit
exit
entry 20
from
protocol aggregate
exit
to
protocol bgp
exit
action accept
exit
exit
exit
...
A:ALU-1#
description "Policy Statement For 'BGP To OSPF'"
entry 10
description "Entry For Policy 'BGP To OSPF"
from
protocol bgp
exit
to
protocol rip
exit
action accept
metric set 1
next-hop 10.0.18.200
tag 134250805
exit
exit
default-action reject
A:ALU-1#
A:ALU-1# show router policy damping
=============================================
Route Damping Profiles
=============================================
damping "TEST-LOW"
half-life 22
max-suppress 720
reuse 10000
suppress 15000
exit
damping "TEST-HIGH"
half-life 22
max-suppress 720
reuse 1000
suppress 5000
exit
damping "TEST-MEDIUM"
half-life 22
max-suppress 720
reuse 5000
suppress 11000
exit
=============================================
A:ALU-1#
A:ALU-1# show router policy prefix-list
==================================
Prefix Lists
==================================
Prefix List Name
----------------------------------
All-Routes
==================================
A:ALU-1#
A:ALU-1# show router policy prefix-list All-Routes
prefix 0.0.0.0/0 longer
prefix 2.0.0.0/8 longer
prefix 3.0.0.0/8 longer
prefix 4.0.0.0/8 longer
prefix 5.0.0.0/8 longer
prefix 6.0.0.0/8 exact
prefix 224.0.0.0/24 longer
A:ALU-1#
A:ALU-1# show router policy as-path
==================================
AS Paths
==================================
AS Path Name
----------------------------------
test
test1
----------------------------------
AS Paths : 2
==================================
A:ALU-1#
A:ALU-1# show router policy as-path test
as-path "test" "14001 701"
A:ALU-1# show router policy community
==================================
Communities
==================================
Community Name
----------------------------------
65206
AS701
AS65000
----------------------------------
Communities : 3
==================================
A:ALU-1#
A:ALU-1# show router policy community 65206
community "65206" members "no-export" "no-export-subconfed"
A:ALU-1#
|
Label |
Description |
|---|---|
|
Policy |
The list of route policy names |
|
Description |
The description of each route policy |
|
Policies |
The total number of policies configured |
|
Damping Name |
The damping profile name |
|
half-life |
The half-life parameter for the route damping profile |
|
max-suppress |
The maximum suppression value configured for the route damping profile |
|
reuse |
The reuse value configured for the route damping profile |
|
suppress |
The suppression value configured for the route damping profile |
|
Prefix List Name |
The prefix list name and IP address/mask and whether the prefix list entry only matches (exact) the route with the specified ip-prefix and prefix mask (length) values or values greater (longer) than the specified mask |
|
AS Path Name |
The list of AS path names |
|
AS Paths |
The total number of AS paths configured |
|
Community Name |
The list of community names |
|
Communities |
The total number of communities configured |