Configuring ANYsec encryption SIDs
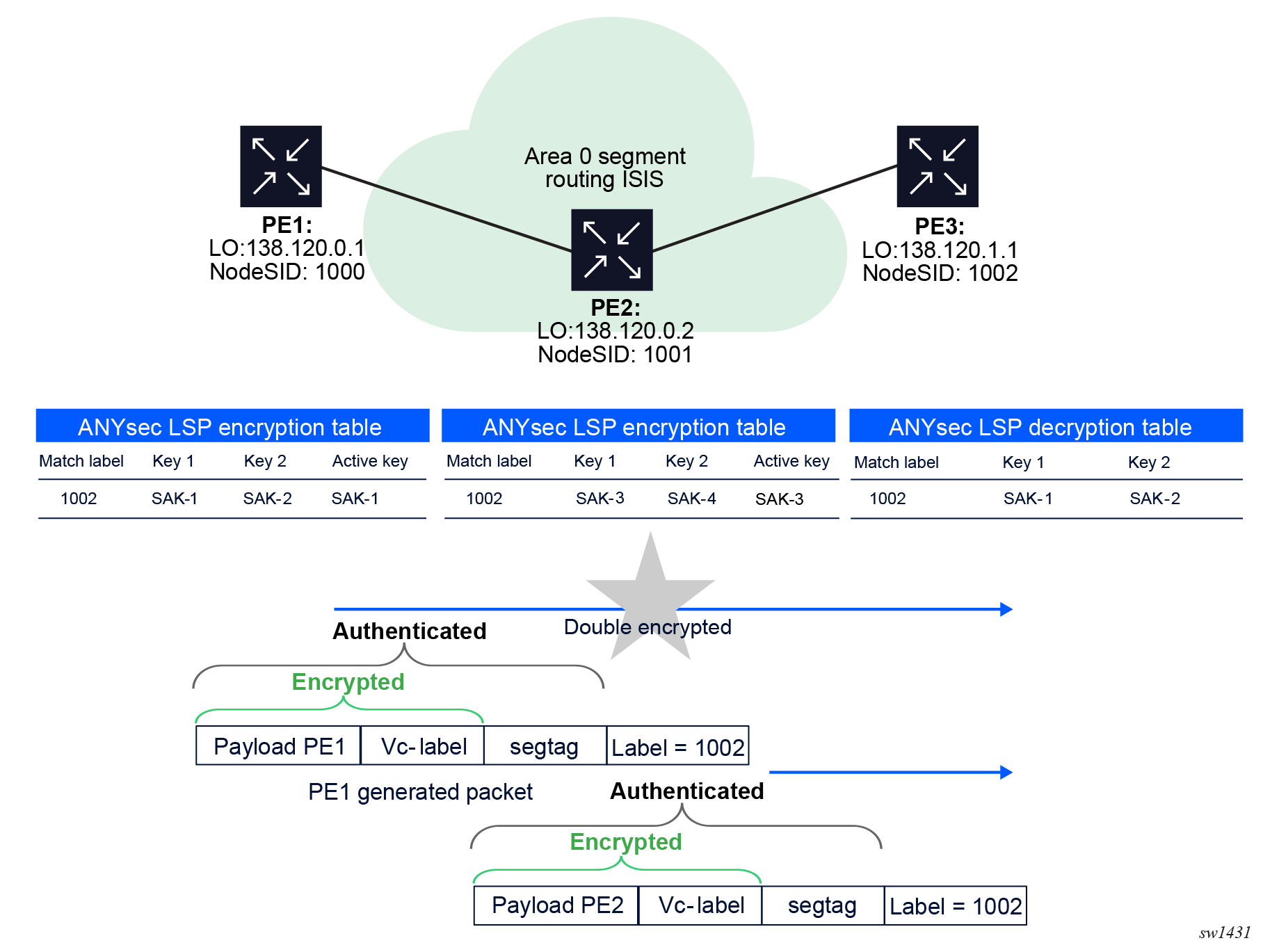
With ANYsec, each affected SR LSP is encrypted with a unique SAK. In segment routing, all peers wanting to send a packet to a local router, send the packet to the node SID of the local router. As such, the label stack that is pushed on the packet by different routers to switch the packet to the local router may be identical. This means if an encrypting node is also an LSR node for an upstream router, it would encrypt its own local packets to the downstream ANYsec router and would double encrypt the upstream ANYsec router packets that are going through it to the same downstream ANYsec router. For example, in the following figure PE2 would encrypt its own packet destined for PE3 and double encrypt the PE1 packets with same MPLS label stack destined for PE3. This double encryption means that PE1 packets are not decrypted correctly at PE3.
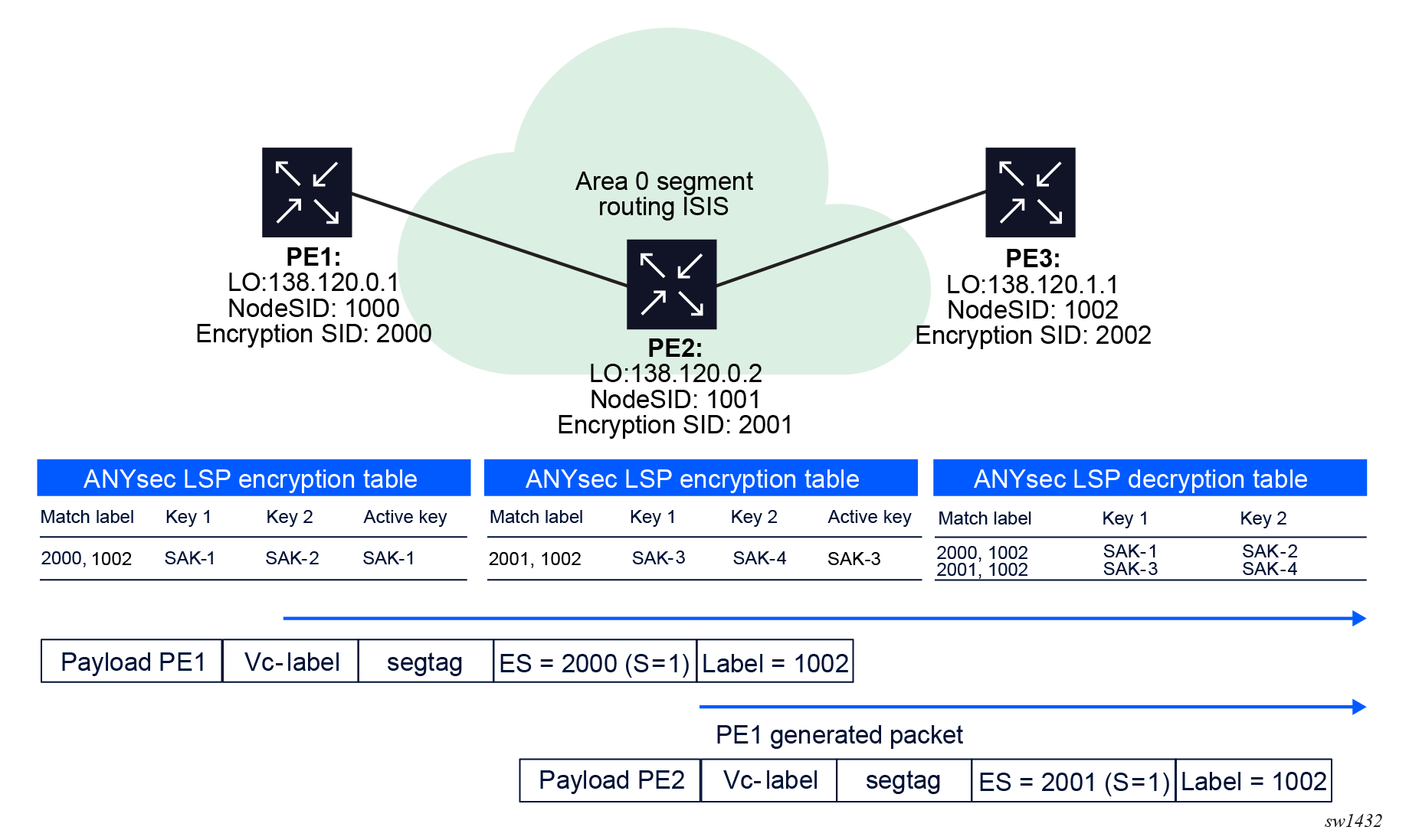
To solve this problem, Nokia introduced the encryption SID, which uniquely identifies the encrypting router within the network. The encryption SID is pushed by the encrypting router at the bottom of the label stack with S bit set if there is no entropy label present. If the entropy label is present, it will be at the bottom of the label stack and the S bit will be set on the entropy label instead of the encryption SID.
In the following figure, the encryption SID 2000 is assigned to PE1 encrypting node and encryption SID 2001 is assigned to PE2 encrypting node. Both PE1 and PE2 are sending packets to PE3.
The encryption SID pushed at the bottom of the label stack ensures that each encrypting node has a unique label stack and double encryption does not occur on PE2. The PE2 ANYsec Encryption Engine and datapath is programmed to only encrypt packets sourced at PE2. It will never encrypt packet coming from upstream routes.
Ensure the following conditions are met for the encryption SID used in the ANYsec configuration:
- The encryption SID for the ANYsec configuration must be uniquely assigned to each encrypting router.
- The encryption SID for the ANYsec configuration must be assigned from a reserved block of labels on the 7705 SAR.
The following example displays a configuration of an encryption SID on an encrypting node.
A:node-2>config>router>mpls-labels# info
----------------------------------------------
sr-labels start 60000 end 120000
reserved-label-block "rlb-1" //reserved block for encryption sid
start-label 50000 end-label 59999
exit
----------------------------------------------
A:node-2>config>anysec# info
----------------------------------------------
reserved-label-block "rlb-1" //reserve blocked assigned to ANYsec
mka-over-ip
mka-udp-port 12345
exit
security-termination-policies
policy "STP-1" create
local-address 1.1.216.100
igp-instance-id 11
no shutdown
exit
exit
tunnel-encryption
encryption-group "EG-1" create
ca-name "CA-1"
encryption-label 50012
security-termination-policy "STP-1"
peer-tunnel-attributes
igp-instance-id 11
exit
peer 1.1.216.136 create
no shutdown
exit
no shutdown
exit
exit