Identifying and configuring ANYsec LSP
After configuring the CA as described in Configuring ANYsec connectivity association and PSK, the next step is to identify the LSP to encrypt. The benefit of ANYsec is the ability to easily enable encryption on an LSP at any time, without changing the LSP's service lease agreement (SLA). ANYsec achieves this by doing the following:
- ANYsec identifies an LSP to encrypt using a disjoint configuration, and encrypts it independently, allowing creation of MPLS networks with appropriate design and SLA that can be expanded to include encryption on LSPs in the future.
- ANYsec uses bidirectional configuration, even for LSPs that are unidirectional, and therefore the ANYsec configuration has to identify an outgoing LSP to encrypt and an incoming LSP to decrypt, under the same encryption group.
The following example displays a configuration to enable encryption on the egress LSP with the node SID 10.20.1.3, and decryption for the local node SID bound to 10.20.1.6. Both LSPs are on IGP instance ID 11.
Example:
*A:7705:Dut-F>config>anysec# info
----------------------------------------------
reserved-label-block "Anysec"
mka-over-ip
mka-udp-port 10000
exit
security-termination-policies
policy "ospfPolicy" create
local-address 10.20.1.6
protocol sr-ospf
rx-must-be-encrypted
no shutdown
exit
exit
tunnel-encryption
encryption-group "ospfEncrGroup" create
ca-name "ospfCA"
encryption-label 52006
security-termination-policy "ospfPolicy"
peer-tunnel-attributes
protocol sr-ospf
exit
peer 10.20.1.3 create
no shutdown
exit
no shutdown
exit
exit
----------------------------------------------
*A:7705:Dut-F>config>anysec#The security-termination policy identifies the decrypting LSP and the node SID on the local router. The decrypting LSPs node SID can arrive from multiple peers, and the SAKs used to decrypt these incoming LSPs are different for each peer.
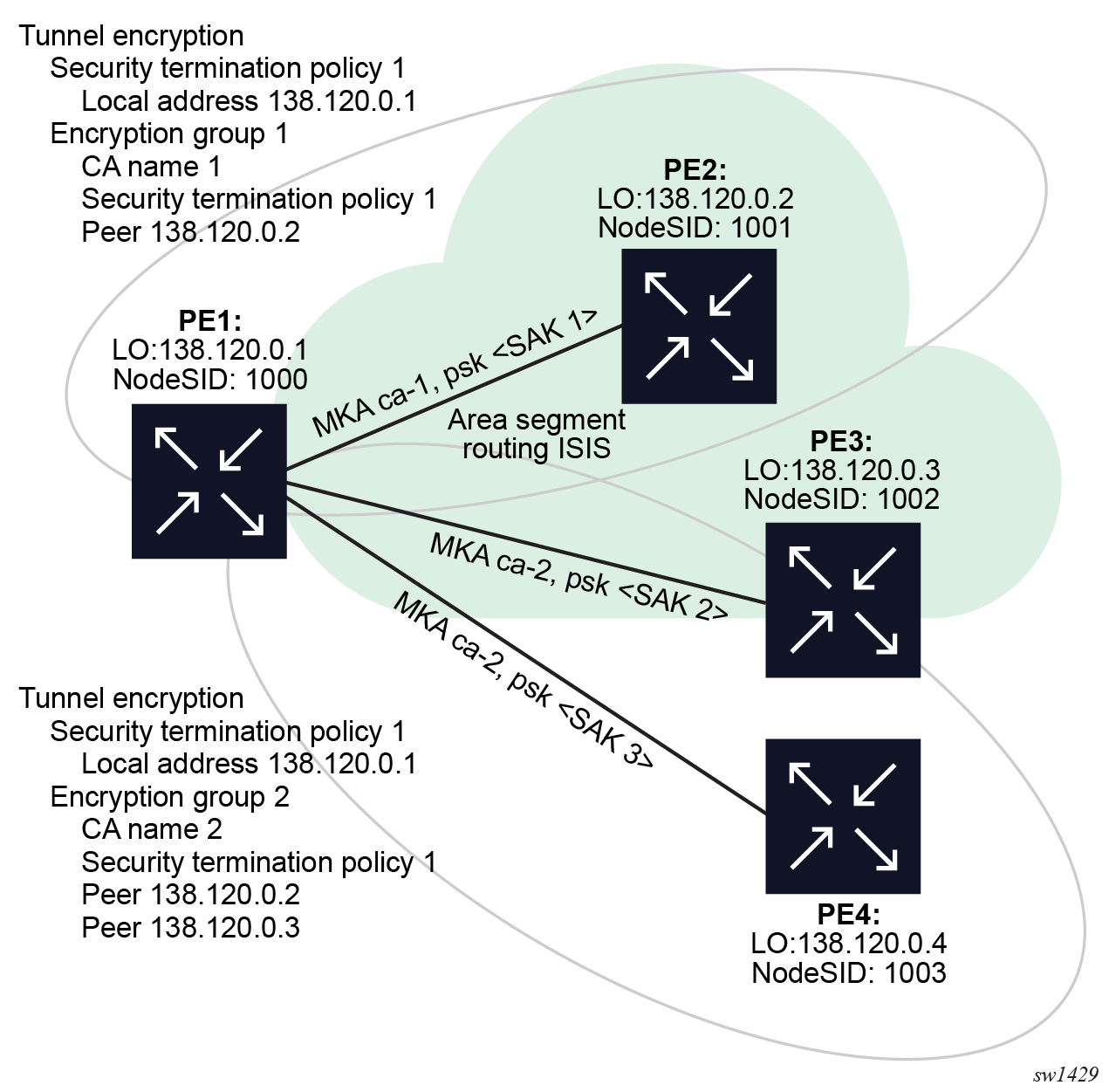
The encryption group is a group of peers that use the same CA and PSK to secure the SAK over MKA. Each peer node SID and its local node SID use a different SAK to encrypt the datapath, but all these SAKs under the same encryption group are secured and signaled via the same CA and PSK.
A security termination policy can be part of multiple encryption groups, however, a peer can only be part of a single encryption group. This allows a set of bidirectional LSPs in an encryption group to use the same CA and PSK to secure and signal SAKs between them.
The following figure shows the implementation of ANYsec tunnel encryption using two encryption groups with the same security termination policy, and different CAs and peers.