Layer 2 services infrastructure
This chapter describes the components of Layer 2 services on SR Linux. It contains the following topics:
MAC-VRF network instance
The network-instance type MAC-VRF functions as a broadcast domain. Each MAC-VRF network instance builds a bridge table composed of MAC addresses that can be learned via the data path on network instance interfaces or via static configuration. You can configure the size of the bridge table for each MAC-VRF network instance, as well as the aging for dynamically learned MAC addresses and other parameters related to the bridge table.
The MAC-VRF network-instance type features a MAC duplication mechanism that monitors MAC address moves across network-instance interfaces and across interfaces.
MAC selection
Each MAC-VRF network instance builds a bridge table to forward Layer 2 frames based on a MAC address lookup. SR Linux selects the MAC addresses to be sent for installation to the line card (XDP), based on the following priority:
local application MACs (for example, IRB interface MACs)
local static MACs
EVPN static MACs
local duplicate MACs
learned and EVPN-learned MACs
MAC duplication detection and actions
MAC duplication is the mechanism used by SR Linux for loop prevention. MAC duplication monitors MAC addresses that move between subinterfaces. It consists of detection, actions, and process restart.
MAC duplication detection
Detection of duplicate MAC addresses is necessary when extending broadcast domains to multiple leaf nodes. SR Linux supports a MAC duplication mechanism that monitors MAC address moves across network-instance interfaces and across interfaces and EVPN.
A MAC address is considered a duplicate when its number of detected moves is greater than a configured threshold within a configured time frame where the moves are observed. When the threshold is exceeded, the system holds on to the prior local destination of the MAC and executes an action.
MAC duplication actions
The action taken on detecting one or more MAC addresses as duplicate on a subinterface can be configured for the MAC-VRF network instance or for the subinterface. The following are the configurable actions:
-
oper-down
When one or more duplicate MAC addresses are detected on the subinterface, the subinterface is brought operationally down.
-
blackhole
On detection of a duplicate mac on the subinterface, the mac is blackholed.
-
stop learning
On detection of a duplicate mac on the subinterface, the MAC address is no longer relearned on this or any subinterface. This is the default action for a MAC-VRF network instance.
-
use-network-instance-action
(Only available for subinterfaces) Use the action specified for the MAC-VRF network instance. This is the default action for a subinterface.
MAC duplication process restarts
When at least one duplicate MAC address is detected, the duplicate MAC addresses are visible in the state datastore and can be displayed with the info from state mac-duplication duplicate-entries CLI command. See Displaying bridge table information.
Configurable hold-down time
The info from state mac-duplication duplicate-entries command also displays the hold-down time for each duplicate MAC address. After the hold-down time expires for all of the duplicate MAC addresses for the subinterface, the oper-down or stop-learning action is cleared, and the subinterface is brought operationally up or starts learning again.
The hold-down time is configurable, ranging from 2 and 60 minutes. You can optionally specify indefinite for the hold-down time, which prevents the oper-down or stop-learning action from being cleared after a duplicate MAC address is detected; in this case, you can manually clear the oper-down or stop-learning action by changing the mac-duplication configuration or using the tools network-instance bridge-table mac-duplication command.
Bridge table configuration
The bridge table, its MAC address limit, and maximum number of entries can be configured on a per mac-vrf or per-subinterface basis.
When the size of the bridge table exceeds its maximum number of entries, the MAC addresses are removed in reverse order of the priority listed in MAC selection.
You can also configure aging for dynamically learned MAC addresses and other parameters related to the bridge table.
Interface extensions for Layer 2 services
To accommodate the Layer 2 services infrastructure, SR Linux interfaces support the following features:
traffic classification and ingress or egress mapping actions
subinterfaces of types routed and bridged
Traffic classification and ingress/egress mapping actions
On MAC-VRF network instances, traffic can be classified based on VLAN tagging. Interfaces where VLAN tagging is set to false or true can be used with MAC-VRF network instances.
A default subinterface can be specified, which captures untagged and non-explicitly configured VLAN-tagged frames in tagged subinterfaces.
Within a tagged interface, a default subinterface (where the vlan-id value is set to optional) and an untagged subinterface can be configured. This type of configuration behaves as follows:
-
the vlan-id optional subinterface captures untagged and non-explicitly configured VLAN-tagged frames
-
the untagged subinterface captures untagged and packets with tag 0 as the outermost tag
When vlan-id optional and untagged subinterfaces are configured on the same tagged interface, packets for unconfigured VLANs go to the vlan-id optional subinterface and tag 0 or untagged packets go to the untagged subinterface.
Classification is based on the following:
-
all traffic, for interfaces where VLAN tagging is set to false, regardless of existing VLAN tags
-
single outermost tag for tagged interfaces where VLAN tagging is set to true. By default, only Ethertype 0x8100 is considered for tags; other Ethertypes are treated as payload. The default Ethertype used for classification can be modified by the command tpid [TPID_0X8100|TPID_0X88A8|TPID_0X9100|TPID_0X9200|TPID_ANY].
The following ingress and egress VLAN mapping actions are supported by default:
-
at ingress, pop the single outermost tag (tagged interfaces) or perform no user-visible action (untagged interfaces)
-
at egress, push a specified tag at the top of the stack (tagged interfaces) or perform no user-visible action (untagged interfaces)
-
if the vlan-id value is set to optional or the subinterface uses an untagged configuration, no tag is popped at ingress or pushed at egress
There is one exception: on a subinterface that uses an untagged configuration, if a received packet has tag 0 as its outermost tag, the subinterface pops tag 0.
For more information on subinterface VLAN configuration, Dot1q tagged bridged subinterfaces, and QinQ bridged subinterfaces, see the Interfaces guide.
Routed and bridged subinterfaces
SR Linux subinterfaces can be specified as type routed or bridged:
routed subinterfaces can be assigned to a network instance of type mgmt, default, or ip-vrf
bridged subinterfaces can be assigned to a network instance of type mac-vrf
Routed subinterfaces allow for configuration of IPv4 and IPv6 settings, and bridged subinterfaces allow for configuration of bridge table and VLAN ingress or egress mapping.
Bridged subinterfaces do not have MTU checks other than the interface-level MTU (port MTU) or the value set with the l2-mtu command. The IP MTU is only configurable on routed subinterfaces.
IRB interfaces
IRB interfaces enable inter-subnet forwarding. Network instances of type mac-vrf are associated with a network instance of type ip-vrf via an IRB interface. See MAC-VRF, IRB interface, and IP-VRF for an illustration of the relationship between MAC-VRF and IP-VRF network instances.
On SR Linux, IRB interfaces are named irbN, where
N is an integer in the range of 0 to 255. Up to 4095
subinterfaces can be defined under an IRB interface. An IP-VRF network instance can have
multiple IRB subinterfaces, while a MAC-VRF network instance can reference only one IRB
subinterface.
IRB subinterfaces are type routed. They cannot be configured as type bridged.
IRB subinterfaces operate in the same way as other routed subinterfaces, including support for the following:
-
IPv4 and IPv6 access control lists (ACLs)
-
static routes and BGP (IPv4 and IPv6 families)
-
IP MTU (with the same range of valid values as Ethernet subinterfaces)
-
all settings in the subinterface/ipv4 and subinterface/ipv6 containers; for IPv6, the IRB subinterface also gets an IPv6 link local address
-
BFD
-
subinterface statistics
| Platform | IRB QoS support |
|---|---|
| 7220 IXR-Dx |
Support for DSCP-based QoS (input and output classifiers and rewrite rules). |
| 7250 IXR 6/10/6e/10/X1b/X3b |
No support. |
| 7730 SXR |
No support. |
| 7215 IXS-A1 |
No support. |
| 7220 IXR-Hx |
No support. |
IRB interfaces do not support sFlow, VLAN tagging, or interface statistics.
Using ACLs with IRB interfaces and Layer 2 subinterfaces
The following items apply when using access control lists (ACLs) with an IRB interface or Layer 2 subinterface:
Input ACLs associated with Layer 2 subinterfaces match all the traffic entering the subinterface, including Layer 2 switched traffic or Layer 3 traffic forwarded to the IRB.
Input ACLs associated with IRB subinterfaces only match Layer 3 traffic, that is, traffic with a MAC destination address (DA) matching the IRB MAC address.
The same ACL can be attached to a Layer 2 subinterface and an IRB subinterface in the same service. In this case, there are two ACL instances: one for the IRB with higher priority and another one for the bridged traffic. Routed traffic matches the higher priority instance entries of the ACL.
The same ACL can be attached to IRB subinterfaces and Layer 2 subinterfaces if both subinterface types belong to different services.
On 7220 IXR-D1, D2, and D3 systems, egress ACLs, unlike ingress ACLs, cannot match both routed and switched traffic when a Layer 2 IP ACL is attached.
Received traffic on a MAC-VRF is automatically discarded if the MAC source address (SA) matches the IRB MAC address, unless the MAC is an anycast gateway MAC.
Packet capture filters show the Layer 2 subinterface for switched traffic and the IRB interface for routed traffic.
Layer 2 services configuration
The examples in this section show how to configure a MAC-VRF network instance, bridged interface, and IRB interface.
MAC-VRF network instance configuration example
The following example configures a MAC-VRF network instance and settings for the bridge table. The bridge table is set to a maximum of 500 entries. Learned MAC addresses are aged out of the bridge table after 600 seconds.
MAC duplication detection is configured so that a MAC address is considered a duplicate when its number of detected moves across network-instance interfaces is greater than three over a 5-minute interval. In this example, the MAC address is blackholed. After the hold-down time of 3 minutes, the MAC address is flushed from the bridge table, and the monitoring process for the MAC address is restarted.
The example includes configuration for a static MAC address in the bridge table.
The MAC-VRF network instance is associated with a bridged interface and an IRB interface.
--{ candidate shared default }--[ ]--
# info network-instance mac-vrf-1
network-instance mac-vrf-1 {
type mac-vrf
admin-state enable
description "Sample mac-vrf network instance"
interface ethernet-1/1.1 {
}
interface irb1.1 {
}
bridge-table {
mac-learning {
admin-state enable
aging {
admin-state enable
age-time 600
}
}
mac-duplication {
admin-state enable
monitoring-window 5
num-moves 3
hold-down-time 3
action blackhole
}
mac-limit {
maximum-entries 500
}
static-mac {
mac 00:00:5E:00:53:FF {
}
}
}
}Bridged subinterface configuration example
The following example configures the bridged subinterface that is associated with the MAC-VRF in the previous example.
--{ candidate shared default }--[ ]--
# info interface ethernet-1/1
interface ethernet-1/1 {
admin-state enable
subinterface 1 {
type bridged
admin-state enable
vlan {
encap {
single-tagged {
vlan-id 10
}
}
}
}
}The vlan-id value can be configured as a specific valid number or with the keyword optional, which means any frame that does not hit the vlan-id configured in other subinterfaces of the same interface is classified in this subinterface.
In the following example, the vlan encap untagged setting is enabled for subinterface 1. This setting allows untagged frames to be captured on tagged interfaces.
For subinterface 2, the vlan encap single-tagged vlan-id optional setting allows non-configured VLAN IDs and untagged traffic to be classified to this subinterface.
With the vlan encap untagged setting on one subinterface, and the vlan encap single-tagged vlan-id optional setting on the other subinterface, traffic enters the appropriate subinterface; that is, traffic for unconfigured VLANs goes to subinterface 2, and tag0 or untagged traffic goes to subinterface 1.
--{ candidate shared default }--[ ]--
# info interface ethernet-1/2
interface ethernet-1/2 {
vlan-tagging true
subinterface 1 {
type bridged
vlan {
encap {
untagged {
}
}
}
}
subinterface 2 {
type bridged
vlan {
encap {
single-tagged {
vlan-id optional
}
}
}
}
}--{ * candidate shared default }--[ ]--
A:srl1# info interface ethernet-1/2
interface ethernet-1/2 {
vlan-tagging true
subinterface 1 {
type bridged
vlan {
encap {
untagged {
}
}
}
}
subinterface 2 {
type bridged
vlan {
encap {
single-tagged {
vlan-id optional
}
}
}
}
subinterface 3 {
type bridged
vlan {
encap {
double-tagged {
inner-vlan-id 10
outer-vlan-id 30
}
}
}
}
}For more information on subinterface VLAN configuration, see the Interfaces guide.
IRB interface configuration example
The following example configures an IRB interface. The IRB interface is operationally up when its admin-state is enabled, and its IRB subinterfaces are operationally up when associated with MAC-VRF and IP-VRF network instances. At least one IPv4 or IPv6 address must be configured for the IRB subinterface to be operationally up.
--{ candidate shared default }--[ ]--
# info interface irb1
interface irb1 {
description IRB_Interface
admin-state enable
subinterface 1 {
admin-state enable
ipv4 {
admin-state enable
address 192.168.1.1/24 {
}
}
}
}Displaying bridge table information
You can display information from the bridge table of a MAC-VRF network instance using show commands and the info from state command.
Display summary information for MAC-VRF network instances
To display a summary of the bridge table contents for the MAC-VRF network instances configured on the system:
# show network-instance * bridge-table mac-table summary
-------------------------------------------------------------------
Network-Instance Bridge table summary
-------------------------------------------------------------------
-------------------------------------------------------------------
Name : mac-vrf-1
Irb mac : 1 Total 1 Active
Static macs : 19 Total 19 Active
Duplicate macs : 10 Total 10 Active
Learnt macs : 15 Total 14 Active
Total macs : 45 Total 44 Active
Maximum-Entries : 200
Warning Threshold Percentage : 95% (190)
Clear Warning : 90% (180)
-------------------------------------------------------------------
Name : mac-vrf-2
Irb mac : 1 Total 1 Active
Static macs : 1 Total 1 Active
Duplicate macs : 10 Total 10 Active
Learnt macs : 15 Total 14 Active
Total macs : 27 Total 26 Active
Maximum-Entries : 200
Warning Threshold Percentage : 95% (190)
Clear Warning : 90% (180)
-------------------------------------------------------------------
-------------------------------------------------------------------
Total Irb macs : 2 Total 2 Active
Total Static macs : 29 Total 29 Active
Total Duplicate macs : 20 Total 20 Active
Total Learnt macs : 30 Total 29 Active
Total Macs : 81 Total 80 Active
-------------------------------------------------------------------
Display bridge table for a MAC-VRF network instance
To list the contents of the bridge table for a MAC-VRF network instance:
# show network-instance mac-vrf-1 bridge-table mac-table all
--------------------------------------------------------------------------------------
Mac-table of network instance mac-vrf-1
--------------------------------------------------------------------------------------
+------------------+--------------+----------+---------+------+-----+----------------+
| Mac |Destination |Dest-Index|Type |Active|Aging|Last-update |
+==================+==============+==========+=========+======+=====+================+
| 00:00:00:00:00:01|ethernet-1/1.1|65 |Learnt |True |256 |2020-2-3T3:37:26|
| 00:00:00:00:00:02| irb1.1| 0 |Irb |True |N/A |2019-2-1T3:37:26|
| 00:00:00:00:00:03| blackhole| 0 |Duplicate|True |N/A |2019-2-1T3:37:26|
| 00:00:00:00:00:04|ethernet-1/1.2|66 |Learnt |True |256 |2019-2-1T3:37:26|
--------------------------------------------------------------------------------------
Total Irb macs : 2 Total 2 Active
Total Static macs : 0 Total 0 Active
Total Duplicate macs : 1 Total 1 Active
Total Learnt macs : 3 Total 3 Active
Total Macs : 6 Total 6 Active
--------------------------------------------------------------------------------------
Display information about a MAC address
To display information about a specific MAC address in the bridge table:
# show network-instance * bridge-table mac-table mac 00:00:00:00:00:01
------------------------------------------------------------------------------------
Mac-table of network instance mac-vrf-1
------------------------------------------------------------------------------------
Mac : 00:00:00:00:00:01
Destination : ethernet-1/1.1
Destination Index : 65
Type : Learnt
Programming status : Success | Failed | Pending
Aging : 250 seconds
Last update : 2019-12-13T23:37:26.000
Duplicate Detect Time : N/A
Hold-down-time-remaining: N/A
------------------------------------------------------------------------------------
Display duplicate MAC addresses
To display the duplicate MAC address entries in the bridge table:
# show network-instance * bridge-table mac-duplication duplicate-entries
------------------------------------------------------------------------------------------
Mac-duplication in network instance mac-vrf-1
------------------------------------------------------------------------------------------
Admin-state : Enabled
Monitoring window : 3 minutes
Number of moves allowed : 5
Hold-down-time : 10 seconds
Action : Stop Learning
------------------------------------------------------------------------------------------
Duplicate entries in network instance mac-vrf-1
------------------------------------------------------------------------------------------
+------------------+----------------+----------+------------------------+----------------+
| Duplicate mac | Destination |Dest-Index| Detect-Time | Hold down |
| | | | | time remaining |
+==================+================+==========+========================+=================
| 00:00:00:00:00:01|ethernet-1/1.1 |65 |2019-12-13T23:37:26.000 | 6
| 00:00:00:00:00:02|ethernet-1/1.1 |65 |2019-12-13T23:37:26.000 | 6
| 00:00:00:00:00:03|ethernet-1/1.1 |65 |2019-12-13T23:37:26.000 | 6
------------------------------------------------------------------------------------------
Total Duplicate macs : 3 Total 3 Active
------------------------------------------------------------------------------------------
Use info from state command to display MAC address entries
You can display the duplicate, learned, or static MAC address entries in the bridge table using info from state commands. For example, the following command displays the duplicate MAC entries:
# info from state network-instance * bridge-table mac-duplication duplicate-entries mac * | as
table
+--------------------+---------------------+---------+------------------------+---------------+
| Network-instance | Duplicate-mac | Dest-idx| Detect-time | Hold-down-time|
| | | | | remaining |
+====================+=====================+=========+========================+===============+
| red | 00:00:00:00:00:01 | 1 | 2019-12-13T23:37:26.000| 10 |
| red | 00:00:00:00:00:02 | 2 | 2019-12-13T23:37:26.000| 20 |
| red | 00:00:00:00:00:03 | 3 | 2019-12-13T23:37:26.000| 90 |
| blue | 00:00:00:00:00:04 | 4 | 2019-12-13T23:37:26.000| 90 |
| blue | 00:00:00:00:00:05 | 0 | 2019-12-13T23:37:26.000| 90 |
+--------------------+---------------------+---------+------------------------+---------------+
Display learned MAC addresses
The following command displays the learned MAC entries in the table:
# info from state network-instance * bridge-table mac-learning learnt-entries mac * | as table
+------------------+------------------+--------------+---------+------------------------+
| Network-instance | Learnt-mac | Dest | Aging | Last-update |
+==================+==================+==============+=========+========================+
| red | 00:00:00:00:00:01|ethernet-1/1.1| 300 | 2019-12-13T23:37:26.000|
| red | 00:00:00:00:00:02|ethernet-1/1.1| 212 | 2019-12-13T23:37:26.000|
| red | 00:00:00:00:00:03|ethernet-1/1.2| 10 | 2019-12-13T23:37:26.000|
| blue | 00:00:00:00:00:04|ethernet-1/1.3| 10 | 2019-12-13T23:37:26.000|
| blue | 00:00:00:00:00:05|ethernet-1/1.4| 20 | 2019-12-13T23:37:26.000|
+------------------+------------------+--------------+---------+------------------------+
Display static MAC entries
The following command displays the static MAC entries in the table:
# info from state network-instance * bridge-table static-mac mac * | as table
+------------------+------------------+--------------+
| Network-instance | Static-mac | Dest |
+==================+==================+==============+
| red | 00:00:00:00:00:01|ethernet-1/1.1|
| red | 00:00:00:00:00:02| irb1.1|
| red | 00:00:00:00:00:03| blackhole|
| blue | 00:00:00:00:00:04|ethernet-1/1.3|
| blue | 00:00:00:00:00:05|ethernet-1/1.4|
+------------------+------------------+--------------+
Deleting entries from the bridge table
The SR Linux includes commands for deleting duplicate or learned MAC entries from the bridge table. For a MAC-VRF or subinterface, you can delete all MAC entries, MAC entries with a blackhole destination, or a specific MAC entry.
Clear blackhole MAC entries
The following example clears MAC entries in the bridge table for a MAC-VRF network instance that have a blackhole destination:
--{ candidate shared default }--[ ]--
# tools network-instance mac-vrf-1 bridge-table mac-duplication delete-blackhole-macs
Delete a learned MAC address
The following example deletes a specified learned MAC address from the bridge table for a MAC-VRF network instance:
--{ candidate shared default }--[ ]--
# tools network-instance mac-vrf-1 bridge-table mac-learning delete-mac 00:00:00:00:00:04
Clear duplicate MAC entries
The following example clears all duplicate MAC entries in the bridge table for a subinterface:
--{ candidate shared default }--[ ]--
# tools interface ethernet-1/1.1 bridge-table mac-duplication delete-all-macs
Storm control on bridged subinterfaces
Storm control allows you to rate limit broadcast, unknown unicast, and multicast (BUM) traffic on bridged subinterfaces. This feature measures the rate for the individual types of BUM traffic, and performs rate limiting based on thresholds configured for each traffic type.
Storm control is configured as an interface-level policer. You set thresholds for each type of BUM traffic. You can configure the threshold as a percentage of interface bandwidth or as a rate in kb/s.
If kbps is specified as the unit type, the rate can be configured as a
multiple of 64; for example, 64, 128, 192, and so on. If the rate is configured as any value
in the 1 to 127 kb/s range, the effective rate is 64 kb/s, which is shown as the
operational-rate in info from state output. Similarly, if the rate is
configured as any value in the 128 to 191 kb/s range, the operational rate is 128 kb/s, and so
on.
The default threshold is 100% of the interface bandwidth for the three traffic types. Specifying a threshold of 0 for a traffic type blocks all traffic of that type on the interface. When a storm control policer is set to 0, the first packet of a flow affected by the policer is forwarded, but subsequent packets are dropped.
Storm control policers can be configured for Ethernet interfaces only. The Ethernet interfaces can be members of a LAG, but storm control must be configured on each interface individually; aggregate rate limiting for the LAG is not supported.
Statistics are not collected for the storm control policers. However, it is possible to check discarded packets at the subinterface level. For example, if storm control for broadcast traffic is configured on interface ethernet-1/1 at a rate of 50%, and broadcast traffic on the ethernet-1/1.1 subinterface exceeds 50% of the port capacity, statistics for the ethernet-1/1.1 subinterface show ingress drops.
Storm control on 7220 IXR-D1/D2/D3/D4/D5 platforms
-
disable-interface
This action brings down the interface if traffic exceeds the rate in any of the policers. The interface oper-down-reason shows storm-control-action. In order to bring the interface back up, the admin-state must be toggled (first disable, then enable).
-
trigger-event
This action creates an event when a configured rate is exceeded. The event indicates that at least one of the configured storm control rates has been exceeded, but it does not indicate which one.
-
none
This is the default action.
Storm control on 7215 IXS-A1 platforms
The implementation of storm control on 7215 IXS-A1 platforms differs compared to other platforms.
The configured storm control rates are Layer 1 rates, as opposed to Layer 2 rates. The configured storm control rates include frame preamble and inter-frame gap (IFG) bytes.
For example, on the 7215 IXS-A1, 64-byte frames and a broadcast rate set to 1 000 000 kb/s corresponds to 761 904 kb/s of actual Layer 2 rate: (1 000 000 * 64) / (64+20) = 761 904 kb/s.
If storm control is enabled, the in-discarded-packets statistics on the interface are increased when packets are dropped due to the storm control policer. However, the subinterface statistics are not modified.
The interface storm control policers are never applied to TCP SYN packets whether their destination MAC is broadcast, multicast, or unknown unicast.
Configuring storm control for an interface
To configure storm
control,
set thresholds for each type of BUM traffic, either as a percentage of interface
bandwidth or as a rate in kbps.
Configure storm control for an interface
The following example configures storm control for an
interface on
7220 IXR-D1/D2/D3/D4/D5 and 7215 IXS-A1 platforms. The unit type
is specified as kbps. Individual thresholds are set for each
traffic type.
--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1
interface ethernet-1/1 {
admin-state enable
ethernet {
storm-control {
units kbps
broadcast-rate 128
multicast-rate 192
unknown-unicast-rate 225
}
}
}Configure storm control with an action
The following example configures storm control with an action on 7220 IXR-D1/D2/D3/D4/D5 platforms. When the amount of broadcast traffic in the interface exceeds 40% of the interface capacity, the interface is disabled.
--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1
interface ethernet-1/1 {
admin-state enable
ethernet {
storm-control {
units percentage
broadcast-rate 40
rising-threshold-action disable-interface
}
}
}Displaying storm control information
Display the configured rates for an interface using info from state and show interface commands.
Display configured rates using info from state command
--{ * candidate shared default }--[ ]--
# info from state interface ethernet-1/1 ethernet storm-control
interface ethernet-1/1 {
ethernet {
storm-control {
units kbps
broadcast-rate 128
multicast-rate 172
unknown-unicast-rate 225
operational broadcast-rate 128
operational multicast-rate 192
operational unknown-unicast-rate 192
}
}
}Display configured rates using show interface command
--{ * candidate shared default }--[ ]--
# show interface ethernet-1/1 detail
========================================================================
Interface: ethernet-1/1
------------------------------------------------------------------------
Description : dut2
Oper state : up
Down reason : N/A
Last change : 9h21m16s ago, 1 flaps since last clear
Speed : 100G
Flow control : Rx is disabled, Tx is disabled
Loopback mode : false
MTU : 9232
VLAN tagging : true
Queues : 8 output queues supported, 0 used since the last clear
MAC address : 00:00:5e:00:53:00
Last stats clear: never
...
-------------------------------------------------------------------------
Storm control for ethernet-1/1
-------------------------------------------------------------------------
Broadcast Rate (kbps) : 128
Multicast Rate (kbps) : 172
Unknown Unicast (kbps) : 225
Operational Broadcast Rate (kbps) : 128
Operational Multicast Rate (kbps) : 192
Operational Unknown Unicast Rate (kbps) : 192L2CP transparency
Layer 2 Control Protocol (L2CP) transparency refers to the ability to control whether L2CP frames are tunneled across a carrier Ethernet network. Tunneling in this context means injecting the L2CP frames into the regular Layer 2 datapath, as opposed to trapping them to the CPU or discarding them.
By default, SR Linux handles L2CP frames according to the default transparency action listed in the following table.
| Layer 2 control protocol | L2CP destination address | Protocol identifier | Default transparency action (7220 IXR-Dx) | Default transparency action (7730 SXR) |
|---|---|---|---|---|
|
LLDP |
01-80-c2-00-00-0e Only the above MAC address is identified as LLDP; other LLDP destination MAC addresses are not. |
Ethertype: 0x88cc |
Trap to CPU only if untagged, drop otherwise |
Tunnel if tagged, trap to CPU if untagged |
|
LACP |
01-80-c2-00-00-02 |
Ethertype: 0x8809 Subtype: 0x01 |
Trap to CPU only if untagged, drop otherwise |
Tunnel if tagged, trap to CPU if untagged |
|
xSTP (STP/RSTP/MSTP) |
01-80-c2-00-00-00 |
Ethertype: any |
Drop |
Tunnel if tagged, drop if untagged |
|
PAUSE |
01-80-c2-00-00-01 |
Ethertype: 0x8808 |
Drop |
Drop |
|
dot1x |
01-80-c2-00-00-03 |
Ethertype: 0x888e |
Trap to CPU only if untagged, drop otherwise |
Tunnel if tagged, trap to CPU if untagged |
|
PTP |
01-80-c2-00-00-0e |
Ethertype: 0x88f7 |
Drop |
Trap to CPU only if untagged, drop otherwise (sync platforms) Tunnel if tagged, drop if untagged (non-sync platforms) |
|
E-LMI |
01-80-c2-00-00-07 |
Ethertype: 0x88ee |
Drop |
Tunnel if tagged, drop if untagged |
| EFM-OAM | 01-80-c2-00-00-02 |
Ethertype: 0x8809 Subtype: 0x03 |
Tunnel if tagged, drop if untagged |
|
|
LACP Marker-Protocol/Link OAM 802.3ah/ESMC |
01-80-c2-00-00-02 |
Ethertype: 0x8809 Subtype: 0x0a |
Drop |
Tunnel if tagged, trap to CPU if untagged (sync platforms) Tunnel if tagged, drop if untagged (non-sync platforms) |
The L2CP transparency feature allows you to configure SR Linux to tunnel the following types of L2CP frames instead of performing the default transparency action, or you can configure SR Linux to tunnel all L2CP frames.
- LLDP
- LACP
- xSTP (STP/RSTP/MSTP)
- dot1x
- PTP
- EFM-OAM (7730 SXR only)
- E-LMI (7730 SXR only)
- ESMC (7730 SXR only)
When tunneling is enabled, the following take place:
- Tagged and untagged L2CP frames are classified into a bridged subinterface based on their dot1q tag VLAN ID. If the L2CP frames are classified for forwarding into a MAC-VRF, they are flooded based on their MAC DA. If no bridged subinterface matches the incoming untagged or VLAN-ID tagged frames, they are discarded.
- L2CP transparency is supported on Ethernet interfaces only, with the processing and tunneling possible on bridged subinterfaces of a MAC-VRF. The system does not apply L2CP transparency rules to VXLAN tunnel interfaces, however it does apply them to Layer 3 subinterfaces in the default network instance.
- When an L2CP PDU is tunneled, the source MAC is learned. When the PDU is dropped, the source MAC is not learned.
On 7220 IXR Dx platforms, to tunnel L2CP frames end-to-end between two EVPN-VXLAN leaf nodes, you must enable L2CP transparency on the ingress Layer 3 subinterfaces of the default network instance on the egress leaf node. Otherwise, even if L2CP transparency for a protocol is configured on the bridged subinterfaces of the ingress leaf, the system discards the L2CP frames at the ingress VXLAN tunnel of the egress leaf.
L2CP transparency is supported in configurations where tunneling for LLDP frames is used in the overlay (between PE and CE devices), and LLDP is used in the underlay (between spine and leaf nodes).
L2CP transparency is not supported on interfaces configured in breakout mode. For LAG interfaces, you must configure L2CP transparency on all member interfaces.
Configuring L2CP transparency
You can enable tunneling for all L2CP protocol types listed in Default L2CP PDU actions for tagged and untagged frames or you can enable tunneling individually for the following L2CP protocol types: LLDP, LACP xSTP (STP/RSTP/MSTP), dot1x, and PTP.
Enable tunneling for all L2CP protocols
--{ candidate shared default }--[ ]--
# info interface ethernet-1/1 ethernet l2cp-transparency
interface ethernet-1/1 {
ethernet {
l2cp-transparency {
tunnel-all-l2cp true
}
}
}When tunnel-all-l2cp true is configured, all L2CP frames coming into the interface, identified by MAC DA = 01:80:c2:00:00:0x or MAC DA = 01:80:c2:00:00:2x where x is any hex value, are tunneled.
The tunnel-all-l2cp command is not supported on interfaces where LLDP or LACP are enabled.
Disable tunneling for all L2CP protocols
--{ candidate shared default }--[ ]--
# info interface ethernet-1/1 ethernet l2cp-transparency
interface ethernet-1/1 {
ethernet {
l2cp-transparency {
tunnel-all-l2cp false
}
}
}When tunnel-all-l2cp false is configured, all L2CP frames not specifically enabled for tunneling are discarded.
Enable tunneling for individual protocol types
You can enable tunneling individually for LLDP, LACP xSTP (STP/RSTP/MSTP), dot1x, and PTP L2CP protocol types. These L2CP frames are identified by the destination MAC address, Ethertype and sometimes slow-protocol subtype; see Default L2CP PDU actions for tagged and untagged frames.
The following example enables tunneling for LLDP frames:
# info interface ethernet-1/1 ethernet l2cp-transparency
interface ethernet-1/1 {
ethernet {
l2cp-transparency {
lldp {
tunnel true
}
}
}
}By default, all the tunnel commands are set to false, so all L2CP protocols are discarded, except for LLDP and LACP, for which a copy is trapped to the CPU (if untagged) and another copy is discarded.
Tunneling for LLDP frames is not supported on an interface where LLDP is enabled.
Tunneling for LACP frames is not supported on an interface where aggregate-id is
configured or the interface is a member of a LAG where LACP is enabled.
Displaying L2CP transparency information
Each of the L2CP protocols that can be tunneled is associated with an L2CP transparency rule
(oper-rule) that indicates the state of the actual rule
installed in the datapath. This rule can be any of the following:
trap-to-cpu-untaggedThis rule is used for LLDP and LACP frames if they are not configured to be tunneled.
On 7220 Dx platforms, untagged frames are trapped to the CPU; that is, a copy is trapped and sent to the CPM, while another copy is discarded. Tagged frames are discarded and not trapped. On 7730 SXR platforms, tagged frames are tunneled, with the exception of PAUSE frames, which are dropped.
drop-tagged-and-untaggedThis rule is used for xSTP, dot1x, and PTP frames if they are not configured for tunneling.
tunnel-tagged-and-untaggedThis rule is used for any of the L2CP protocols when they are configured to be tunneled.
tunnel-tagged-drop-untaggedThis rule is used on 7730 SXR platforms for some of the L2CP protocols when they are configured to not be tunneled.
tunnel-tagged-trap-to-cpu-untaggedThis rule is used on 7730 SXR platforms for some of the L2CP protocols when they are not configured to be tunneled.
You can display the L2CP transparency configuration and oper-rule
for each L2CP protocol that can be tunneled.
Display tunneling configuration and oper-rule for an interface on 7220 IXR Dx platforms
Use the info from state command for an interface to display its
tunnelling configuration and oper-rule for each protocol. For
example:
--{ candidate shared default }--[ ]--
# info from state interface ethernet-1/1 ethernet l2cp-transparency
interface ethernet-1/1 {
ethernet {
l2cp-transparency {
tunnel-all-l2cp false
lldp {
tunnel false
oper-rule trap-to-cpu-untagged
}
lacp {
tunnel false
oper-rule trap-to-cpu-untagged
}
xstp {
tunnel false
oper-rule drop-tagged-and-untagged
}
dot1x {
tunnel false
oper-rule drop-tagged-and-untagged
}
ptp {
tunnel false
oper-rule drop-tagged-and-untagged
}
}
}
}Display the oper-rule for each protocol type on 7220 IXR Dx platforms
Use the show interface detail command to display the L2CP transparency rule
(oper-rule) for each protocol type; for example:
--{ candidate shared default }--[ ]--
# show interface ethernet-1/1 detail
=============================================================================
Interface: ethernet-1/1
-----------------------------------------------------------------------------
Description : <None>
Oper state : up
Down reason : N/A
Last change : 2d22h27m45s ago, 1 flaps since last clear
Speed : 10G
Flow control : Rx is disabled, Tx is disabled
MTU : 9232
VLAN tagging : false
Queues : 8 output queues supported, 2 used since the last clear
MAC address : 00:01:01:FF:00:01
Last stats clear: never
Breakout mode : false
-----------------------------------------------------------------------------
L2cp transparency rules for ethernet-1/1
-----------------------------------------------------------------------------
Lldp : trap-to-cpu-untagged
Lacp : trap-to-cpu-untagged
xStp : drop-tagged-and-untagged
Dot1x : drop-tagged-and-untagged
Ptp : tunnel-tagged-and-untagged
Non-specified L2cp : drop-tagged-and-untagged
-----------------------------------------------------------------------------Displaying L2CP transparency statistics
To display L2CP transparency statistics, use the info from state command in candidate or running mode, or the info command in state mode.
Statistics are displayed for the following:
- total number of L2CP packets of any L2CP protocol on all interfaces, as well as the total number of discarded and tunneled L2CP packets
- total number of ingress tunneled and trapped-to-CPU packets per L2CP protocol at the system
level. Individual statistics are displayed for LLDP, LACP, xSTP, dot1x, and PTP
protocols if
tunnel-all-l2cp falseis configured
Display L2CP transparency statistics for 7220 IXR Dx platforms
--{ candidate shared default }--[ ]--
# info from state system l2cp-transparency l2cp-statistics
system {
l2cp-transparency {
l2cp-statistics {
total-in-packets 0
total-in-discarded-packets 0
total-in-tunneled-packets 0
total-in-trap-to-cpu-packets 0
last-clear "a day ago"
lldp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
lacp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
xstp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
dot1x {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
ptp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
}
}
}Display L2CP transparency statistics for 7730 SXR platforms
--{ candidate shared default }--[ ]--
# info from state system l2cp-transparency l2cp-statistics--{ candidate shared default }--[ ]--
system {
l2cp-transparency {
l2cp-statistics {
total-in-packets 4558
total-in-discarded-packets 0
total-in-tunneled-packets 0
total-in-trap-to-cpu-packets 4558
lldp {
in-tunneled-packets 0
in-trap-to-cpu-packets 4558
}
lacp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
xstp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
dot1x {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
ptp {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
esmc {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
elmi {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
efm-oam {
in-tunneled-packets 0
in-trap-to-cpu-packets 0
}
}
}
}- Discarded L2CP frames are counted as
in-discarded-packetsin interface-level statistics. They are not counted in subinterface statistics. - Tunneled L2CP frames are counted in interface and subinterface statistics for outgoing interfaces in the appropriate counters.
- If tunnel-all-l2cp true is configured, all L2CP frames
(including LLDP, LACP, xSTP, dot1x, and PTP) are counted only in
l2cp-statistics/total-in-tunneled-packetsregardless of protocol-specific configuration. In this case, the protocol-specific statistics are displayed as 0.
Clearing L2CP transparency statistics
You can use a tools command to clear the total counters and the per-protocol counters for L2CP transparency statistics.
Clear statistics counters for all L2CP protocols
--{ running }--[ ]--
# tools system l2cp-transparency l2cp-total-statistics clearClear statistics counters for a specific L2CP protocol type
--{ running }--[ ]--
# tools system l2cp-transparency ptp clearSplit horizon groups on MAC-VRF
By default, in a MAC-VRF network instance, all EVPN destinations are considered part of the same split horizon group (SHG) and every interface and pseudowire is part of a different SHG. With that default configuration, traffic from a subinterface or pseudowire can be forwarded to other subinterfaces or pseudowires and EVPN destinations of the same MAC-VRF. However, traffic from EVPN destinations can only be forwarded to subinterfaces and pseudowires, but not to other EVPN destinations.
The explicit configuration of SHGs in a MAC-VRF network instance modifies this default behavior. SHGs can be configured and associated with bridged subinterfaces, BGP-EVPN instances, and pseudowires.
SHGs are typically used to prevent client-to-client communication while allowing client-to-server communication. SHGs are also used for the seamless integration of pseudowires and EVPN (RFC 8560). See EVPN-MPLS and VPLS seamless integration (RFC 8560) and MPLS transport for EVPN services.
With explicit SHGs, traffic (unicast and BUM) cannot be forwarded between objects that are part of the same SHG.
For control plane traffic, incoming traffic on object A cannot be reinjected by the CPM on object B, if both object A and B are configured with the same SHG. An example of this behavior is proxy-ARP and two Layer 2 subinterfaces configured with the same SHG and attached to the same MAC-VRF. An ARP request received on one of the two subinterfaces cannot be reinjected into the other subinterface if the proxy-ARP lookup fails to find a successful entry.
Configuring split horizon groups
Before you can reference them in any object, you must first manually create SHGs using the following command: network-instance bridge-table split-horizon-group name
When created, SHGs are only used in the context of the MAC-VRF.
network instance interfaces
network-instance interface bridge-table split-horizon-group nameBGP-EVPN MPLS
network-instance protocols bgp-evpn bgp-instance mpls bridge-table split-horizon-group nameconnection points
network-instance connection-point bridge-table split-horizon-group name
Split horizon group configuration example
The following example illustrates the use of SHGs.
Interfaces ethernet-1/1.2 and ethernet-1/1.3 cannot forward traffic between each other, but can send traffic to the other interfaces and EVPN destinations.
Interfaces ethernet-1/2.1 and ethernet-1/2.2 cannot forward traffic between each other, but can send traffic to the other interfaces and EVPN destinations.
Interface ethernet-1/2.3 can forward traffic normally to any other interface or EVPN destination.
Configuring split horizon groups
--{ * candidate shared default }--[ network-instance * ]--
A:leaf1# info
network-instance MAC-VRF-2 {
interface ethernet-1/1.2 {
bridge-table {
split-horizon-group SHG-1
}
}
interface ethernet-1/1.3 {
bridge-table {
split-horizon-group SHG-1
}
}
interface ethernet-1/2.1 {
bridge-table {
split-horizon-group SHG-2
}
}
interface ethernet-1/2.2 {
bridge-table {
split-horizon-group SHG-2
}
}
interface ethernet-1/2.3 {
}
vxlan-interface vxlan0.1 {
}
protocols {
bgp-evpn {
bgp-instance 1 {
admin-state enable
encapsulation-type vxlan
vxlan-interface vxlan0.1
evi 2
}
}
bgp-vpn {
bgp-instance 1 {
}
}
}
bridge-table {
split-horizon-group SHG-1 {
}
split-horizon-group SHG-2 {
}
}
}Platform specifications for split horizon groups
SHGs are supported on 7730 SXR, 7220 IXR-Dx, and 7215 IXS-A1 platforms.
The following limitations apply depending on the platform.
7220 IXR-D1/D2/D2L/D3/D3L platform support
Six SHGs per MAC-VRF are supported on 7220 IXR-D1/D2/D2L/D3/D3L platforms. When used with EVPN in the same MAC-VRF, five SHGs can be configured.
7220 IXR-D4/D5 platform support
Two SHGs per MAC-VRF are supported on 7220 IXR-D4/D5 platforms.
7215 IXS-A1 platform support
For expected SHG behavior, all bridged subinterfaces in a MAC-VRF are assigned to the SHG. A bridged subinterface in an SHG drops (at egress) all packets coming from another bridged subinterface, whether or not the origin is a subinterface in the same SHG.
- In MAC-VRFs without IRB, if all subinterfaces are applied to an SHG there is no connectivity among them. If not all subinterfaces are associated with the SHG, traffic from SHG subinterfaces to non-SHG subinterfaces is forwarded, but traffic from non-SHG subinterfaces to SHG subinterfaces is dropped.
- In MAC-VRFs with IRB, all subinterfaces of the MAC-VRF must be configured on the SHG. Traffic among subinterfaces is dropped, but traffic to and from IRB is forwarded correctly.
Pseudowires
Static and Targeted Label Distribution Protocol (T-LDP) based pseudowires (PWs) are supported on SR Linux. Pseudowires can be used to establish Layer 2 point-to-point services between two PEs (RFC 4448), stretch broadcast domains in an MPLS network, or set up Virtual Private LAN Services (VPLS), as per RFC 4762. Pseudowires can also be seamlessly integrated with EVPN-MPLS (RFC 8560). All these use cases are described in the following sections.
Pseudowires in MAC-VRF network instances
-
Pseudowires are supported in the same MAC-VRF where bridged subinterfaces and EVPN-MPLS are configured.
-
Pseudowires use MPLS tunnels for transport, where the binding between the pseudowire and the transport tunnel is completed by configuring of the pw-tunnel under the pseudowire. The pw-tunnel uses the MPLS tunnels in the tunnel table, unless the type is filtered by the allowed-tunnel-types command.
-
The forwarding rules for pseudowires depend on the association of split-horizon-groups to those pseudowires and the rest of the objects in the network instance. For example, to emulate an RFC 4762 compliant VPLS service, all the connection-points in the MAC-VRF must be associated with the same split-horizon-group.
-
Pseudowires support all bridge table parameters that are also applicable to bridged subinterfaces, including mac-duplication, mac-limit, mac-learning and other parameters.
-
The generation of TLDP MAC withdraw messages to flush MAC addresses on the remote nodes is controlled by the bridge-table tldp-mac-flush send-flush-on-failure command. When enabled, a fault on a subinterface, another pseudowire, or EVPN will trigger a flush-all-from-me message. A flush-all-from-me message is a TLDP-based MAC Withdraw message, by which a PE requests a remote PE to remove all MAC addresses associated with the PE transmitting the message.
Pseudowire configuration characteristics
admin-disablednetwork-instance-oper-downno-ingress-vc-labelno-egress-vc-labelnetwork-instance-mtu-mismatchpseudowire-remote-system-fault-status-bitstransport-tunnel-oper-downno-destination-idevpn-route-conflictNote: Theevpn-route-conflictflag is used for EVPN-VPLS seamless integration to handle conflicts when there is a pseudowire and an EVPN Inclusive Multicast Ethernet Tag (IMET) route to the same far end IP address (RFC 8560).
Virtual circuit type configuration, with ethernet or vlan options determines the vc-type signaling for the pseudowire. The VLAN tag value that is pushed on the frames depends on the VLAN configuration on the ingress subinterface and the type does not push any extra VLAN tag on pseudowires.
Control word configuration determines whether control word support is signaled in the
control plane. If the peer signals control word support too, the pseudowire is
established,
and the control word is pushed on all frames. If there is a mismatch between the
local router and the peer, the pseudowire will
remain
operationally down. The router will show a control-word-mismatch
oper-down reason at the ldp service-fecs fec128
level. A change in the control word configuration that causes a mismatch will
trigger the TLDP withdraw and
re-advertisement
with the control word set. It does not cause a label release locally, but the
pseudowire will bounce.
Flow label configuration determines whether the Flow Aware Transport (FAT) label is used on pseudowires. FAT labels allow for granular load balancing without deep packet inspection, improving the efficiency of traffic flow management. The capability to use the FAT label is signaled in TLDP. Contrary to the control word, discrepancies in the signaling of the FAT label capability between two TLDP peers do not bring down the pseudowire, but they determine whether the flow label is sent on the wire.
pseudowire-forwardingpseudowire-not-forwardinglocal-attachment-circuit-ingress-faultlocal-attachment-circuit-egress-faultprovider-service-network-ingress-faultprovider-service-network-egress-faultpseudowire-forwarding-standbypseudowire-request-switchover
Pseudowires do not have a specific Layer 2 MTU value that can be configured, and the data path layer does not enforce MTU or MRU values other than subinterface mpls-mtu in the default network instance. However, TLDP signals the Layer 2 MTU as follows:
The default value signaled for a pseudowire by TLDP is taken from the oper-mac-vrf-mtu. This default value can be overridden by the value configured with the command advertise-l2-mtu. In case there is a mismatch with the MTU signaled by the peer, the pseudowire will go operationally down with the reason network-instance-mtu-mismatch, unless ignore-mtu-mismatch true is configured.
The oper-mac-vrf-mtu, signaled by TLDP, is computed as the minimum value among all Layer 2 MTU of all the subinterfaces in the MAC-VRF (irrespective of their operational state), with a default value of the system mtu default-l2-mtu in case there are no subinterfaces in the MAC-VRF.
Configuring pseudowires in MAC-VRF network instances
The following examples show a MAC-VRF configuration with a subinterface and three pseudowires.
Assigning a label block
--{ candidate shared default }--[ system mpls services network-instance ]--
A:srl-pe4# info
dynamic-label-block range-5-servicesConfiguring pseudowire tunnels to each PE
A pw-tunnel to each remote PE is then configured. The pw-tunnel requires the configuration of a remote-system IP address and the selection of the tunnel types that are used at the transport level, via the allowed-tunnel-types command. If there are multiple tunnels (of the allowed type) that can resolve the remote system IP address, the best tunnel in the tunnel table is selected (based on preference and metrics). The configuration of a pw-tunnel automatically creates a TLDP session to the remote system IP address for the setup of the pseudowire.
--{ candidate shared default }--[ tunnel pseudowire-tunnel ]--
A:srl-pe4# info
tunnel to-pe1 {
remote-system 10.0.0.1
allowed-tunnel-types [
ldp
]
}
tunnel to-pe2 {
remote-system 10.0.0.2
allowed-tunnel-types [
bgp
ldp
sr-isis
]
}
tunnel to-pe3 {
remote-system 10.0.0.3
allowed-tunnel-types [
ldp
]
}
--{ candidate shared default }--[ tunnel pseudowire-tunnel ]--
A:srl-pe4# info from state tunnel to-pe*
tunnel to-pe1 {
remote-system 10.0.0.1
operational-tunnel-type ldp
operational-tunnel-id 65539
allowed-tunnel-types [
ldp
]
}
tunnel to-pe2 {
remote-system 10.0.0.2
operational-tunnel-type ldp
operational-tunnel-id 65541
allowed-tunnel-types [
bgp
ldp
sr-isis
]
}
tunnel to-pe3 {
remote-system 10.0.0.3
operational-tunnel-type ldp
operational-tunnel-id 65543
allowed-tunnel-types [
ldp
]
}Configuring pseudowires in the MAC-VRF
The pseudowires are then configured in the MAC-VRF. Each pseudowire is configured under a different connection-point. A connection-point is a logical structure that can contain multiple objects, but only one is active. Only one pseudowire can be configured per connection-point.
The association of connection-point and split-horizon-group determines how forwarding is carried out between objects in the MAC-VRF. The following example illustrates a typical RFC 4762 VPLS configuration, where all the pseudowires of the MAC-VRF belong to the same "mesh" or split-horizon-group. This configuration ensures that traffic from a pseudowire can never be forwarded to another pseudowire in the MAC-VRF and only to the subinterface. Should you want traffic to be forwarded between two pseudowires (typical RFC 4762 H-VPLS architectures), those two pseudowires must be part of different split horizon groups.
--{ candidate shared default }--[ network-instance mac-vrf-5 ]--
A:srl-pe4# info
type mac-vrf
interface ethernet-1/1.5 {
}
bridge-table {
split-horizon-group shg-1 {
}
}
connection-point A {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-3 {
admin-state enable
pw-tunnel to-pe3
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}
connection-point B {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-1 {
admin-state enable
pw-tunnel to-pe1
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}
connection-point C {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-2 {
admin-state enable
pw-tunnel to-pe2
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}Displaying pseudowire state information
--{ candidate shared default }--[ network-instance mac-vrf-5 connection-point A pseudowire pw-to-3 ]--
A:srl-pe4# info from state
admin-state enable
oper-state up
index 1
destination-index 373975667326
pw-tunnel to-pe3
control-word false
flow-label false
flow-label-oper-state down
signaling {
virtual-circuit-identifier 5
tldp {
virtual-circuit-type ethernet
ignore-mtu-mismatch false
}
}
local {
operational-ingress-vc-label 1007
}
remote {
operational-egress-vc-label 1009
}Displaying fec-128 bindings state information
--{ candidate shared default }--[ network-instance mac-vrf-5 connection-point A pseudowire pw-to-3 ]--
A:srl-pe4# info from state /network-instance default protocols ldp ipv4 bindings service-fec128 ethernet virtual-circuit-identifier 5 peer-lsr-id 10.0.0.3
binding-oper-state up
advertised {
label 1007
l2-mtu 1500
control-word false
flow-aware-transport-label-transmit-capability false
flow-aware-transport-label-receive-capability false
pw-status true
withdraw-reason none
label-status [
in-use-pop
]
signaling-status [
pseudowire-forwarding
]
}
received {
label 1009
l2-mtu 1500
control-word false
flow-aware-transport-label-transmit-capability false
flow-aware-transport-label-receive-capability false
pw-status true
label-status [
in-use-push
]
signaling-status [
pseudowire-forwarding
]
}EVPN-MPLS and VPLS seamless integration (RFC 8560)
MAC-VRF network instances support seamless integration of pseudowires, interfaces, and EVPN-MPLS destinations by configuring manual split-horizon-group objects.
-
Any traffic among the three objects is discarded.
-
Any MAC addresses learned on ethernet-1/1.1 are not advertised by EVPN.
-
Any MAC addresses learned on connection-point conn-point-1 are not advertised by EVPN.
-
If the pseudowire that belongs to connection-point conn-point-1 and an EVPN multicast destination have the same far-end IP address, the pseudowire will be oper-state down with oper-down-reason evpn-conflict.
--{ candidate shared default }--[ network-instance mac-vrf-5 ]--
A:srl-pe4# info
type mac-vrf
interface ethernet-1/1.5 {
}
protocols {
bgp-evpn {
bgp-instance 1 {
encapsulation-type mpls
evi 5
mpls {
bridge-table {
split-horizon-group shg-1
}
next-hop-resolution {
allowed-tunnel-types [
bgp
ldp
sr-isis
]
}
}
}
}
bgp-vpn {
bgp-instance 1 {
}
}
}
bridge-table {
split-horizon-group shg-1 {
}
}
connection-point A {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-3 {
admin-state enable
pw-tunnel to-pe3
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}
connection-point B {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-1 {
admin-state enable
pw-tunnel to-pe1
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}
connection-point C {
bridge-table {
split-horizon-group shg-1
}
pseudowire pw-to-2 {
admin-state enable
pw-tunnel to-pe2
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}By configuring all connection points and BGP-EVPN with the same split-horizon-group, traffic from a pseudowire is not forwarded to EVPN, and vice versa. Also, MACs learned over one of those pseudowires will not be advertised in EVPN to avoid duplication. A pseudowire is brought down if its remote system IP matches a received IMET route's next hop, to avoid BUM duplication between hybrid PEs.
Pseudowires in VPWS network instances
Virtual Private Wire Service (VPWS) is a type of network instance used for Layer 2 point-to-point connectivity. VPWS network instances support two connection points, where each connection point contains a single object.
-
EVPN-MPLS and a subinterface
-
Two subinterfaces
-
A pseudowire and a subinterface
-
The pseudowire can be added to a VPWS connection-point, where a bridge subinterface exists in the other connection-point.
-
The configuration and state model for the pseudowire in a VPWS network instance follows the model described in Pseudowires in MAC-VRF network instances except for the bridge-table context, which is not supported when the connection-point is added to a VPWS network instance.
Configuring pseudowires in VPWS network instances
-
Configure the pw-tunnel with the same support as for pseudowires in MAC-VRF.
-
At the network instance type vpws level, configure the connection-point (without bridge table aspects).
-
Configure the pseudowire (with signaling static or TLDP) under the configured connection-point.
--{ * candidate shared default }--[ network-instance VPWS-1 ]--
A:srl# info
type vpws
description "VPWS-1 pw and subinterface example"
interface ethernet-1/5.1 {
connection-point A
}
connection-point A {
}
connection-point B {
pseudowire pw-to-4 {
admin-state enable
pw-tunnel to-pe4
signaling {
virtual-circuit-identifier 5
tldp {
}
}
}
}The pseudowires configured in VPWS network instances support the same characteristics as in the case of MAC-VRFs, with the following differences:
- The evpn-route-conflict oper-down-reason does not apply to pseudowires in VPWS services.
- The reception of pw-status bits signaling an error does not bring down the pseudowire. Therefore, some of the pseudowire oper-down-reason options are not applicable to pseudowires in VPWS services.
- The Layer 2 MTU is handled the same way as in MAC-VRFs, with the only difference being that oper-vpws-mtu is used instead of oper-mac-vrf-mtu.
- A mismatch in the signaled mtu, vc-type, flow-label, or control-word is handled similarly to the MAC-VRFs.
- MAC-flush behavior is not applicable to pseudowires in VPWS services. The same applies to other interactions with MAC-VRF bridge table specific features.
In VPWS network instances, the following objects have their own operational state:
- network-instance
- bgp-evpn bgp-instance
- connection-point
- sub-interface
The network-instance oper-state is always up as long as the network instance admin-state enable is configured. The connection-point oper-state is up as long as at least one object in the connection-point is operationally up. This object can be a subinterface oper-state up or a pseudowire.
The following figure shows a case where PE1 is attached to a VPWS service with a subinterface and a pseudowire.
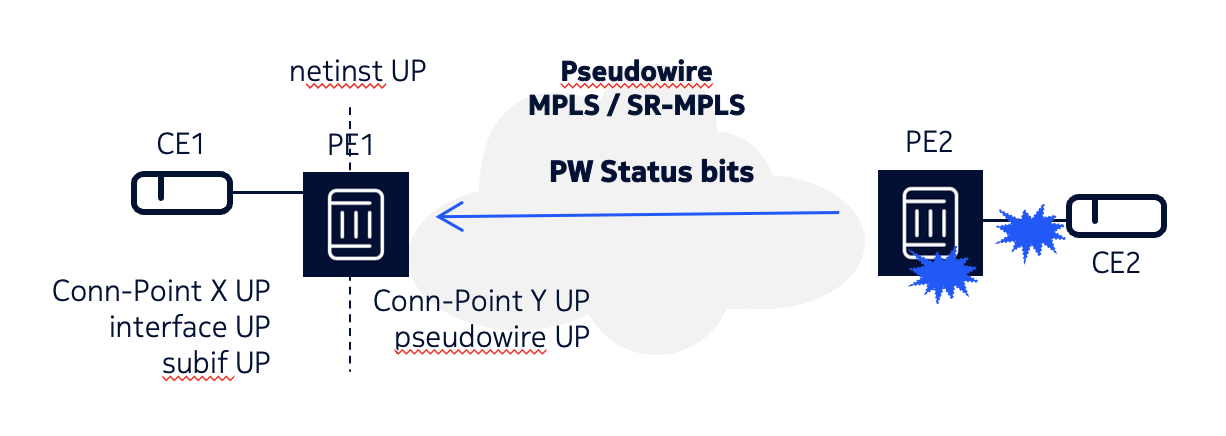
-
PE2 signals the corresponding pw-status bits local-attachment-circuit-ingress/egress-fault.
- Upon reception of the pw-status bits from PE2, PE1 does not bring down the pseudowire or connection point. This is different from the case of MAC-VRFs.
- If the VPWS network instance goes oper-state down, PE2 releases the label allocated to the VPWS network instance and signals the withdrawal of the label to PE1. This will bring down the pseudowire.
Link Loss Forwarding in VPWS network instances
Link Loss Forwarding is supported in cases where the VPWS network instance contains a pseudowire and a subinterface.
The Link Loss Forwarding feature is enabled by the interface ethernet
link-loss-forwarding true command on the interface connected to the CE
over which the fault signaling is propagated. In addition, the command
standby-signaling[=power-off|lacp] must be configured on the
same interface so that ch_mgr can trigger the relevant standby
signaling to the CE.
In the case where VPWS contains a pseudowire and a subinterface, the reception of pw-status bits notifying the remote fault triggers the link loss forwarding procedures to propagate the fault.
-
If PE2 signals a remote fault, PE1 brings down the interface to CE1 due to link loss forwarding, and connection point X goes operationally down.
-
Subsequently, the pseudowire receives an event that connection point X is down, but
pw_mgrwill not react to this (it will not signal any fault in the pw-status bits) because connection point X is down due to link loss forwarding.
Server aggregation configuration example
Server aggregation example shows an example of using MAC-VRF network instances to aggregate servers into the same subnet.
In this example, Leaf-1 and Leaf-2 are configured with MAC-VRF instances that aggregate a group of servers. These servers are assigned IP addresses in the same subnet and are connected to the leaf default network instance by a single IRB subinterface. The servers use a PE-CE BGP session with the IRB IP address to exchange reachability.
Using the MAC-VRF with an IRB subinterface saves routed subinterfaces on the default network instance; only one routed subinterface is needed, as opposed to one per server.
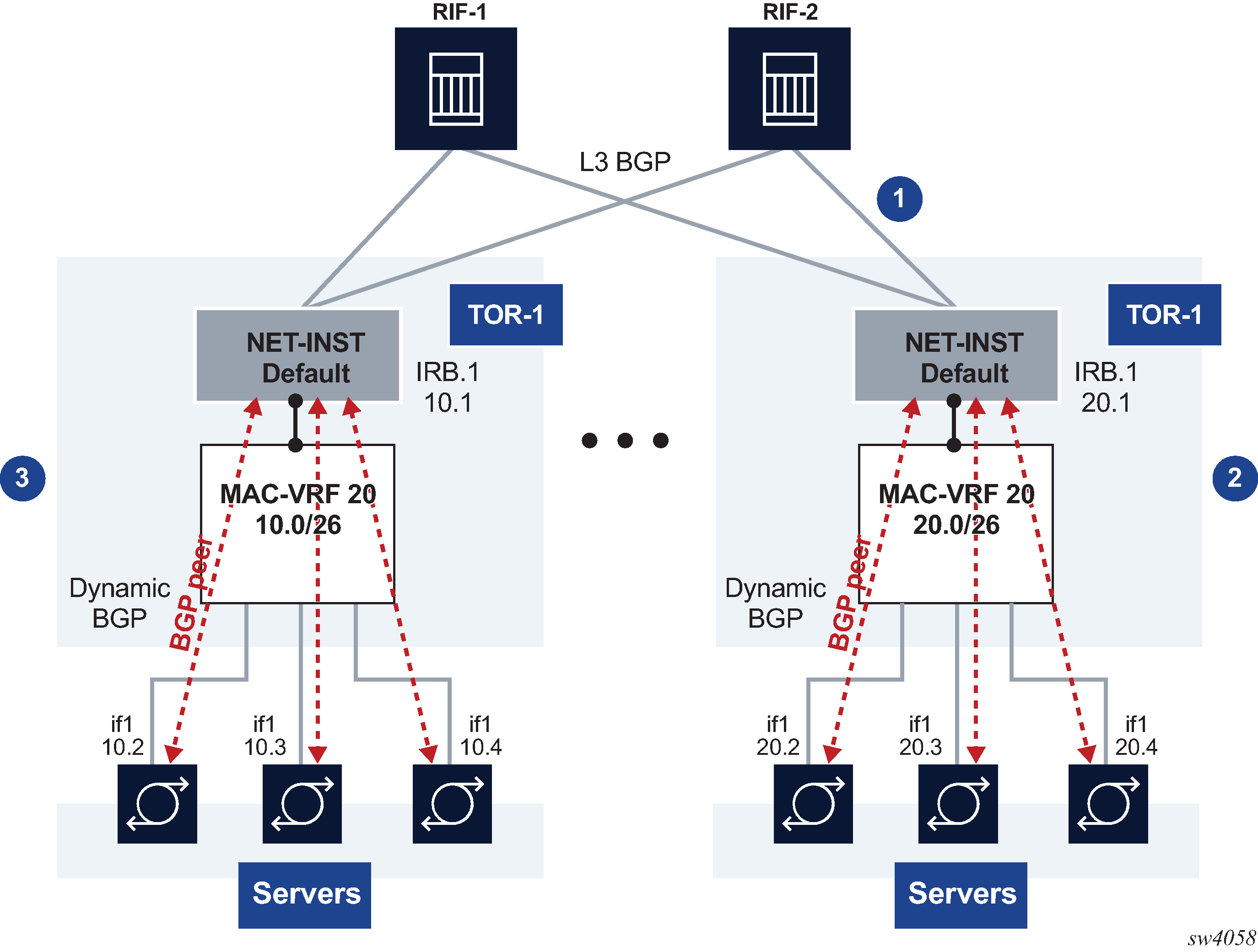
In this example:
TORs peer (eBGP) to two or four RIFs.
MAC-VRF 20 is defined in TORs with an IRB interface with IPv4/IPv6 addresses. DHCP relay is supported on IRB subinterfaces.
The following Layer 2 features are implemented or loop and MAC duplication protection:
MAC duplication with oper-down or blackhole actions configured on the bridged subinterfaces
storm control for BUM traffic on bridged subinterfaces
This example uses the following features:
MAC-VRF with bridge subinterfaces and IRB subinterfaces to the default network instance
PE-CE BGP sessions for IPv4 and IPv6 address families
MAC duplication with oper-down or blackhole actions configured on the bridged subinterfaces
storm control for BUM traffic on bridged subinterfaces
Configuration for server aggregation example
The following shows the configuration of Leaf-1 in Server aggregation example and its BGP session via IRB to server 1. Similar configuration is used for other servers and other TORs.
--{ [FACTORY] + candidate shared default }--[ interface * ]--
A:Leaf-1# info
interface ethernet-1/1 {
description tor1-server1
vlan-tagging true
subinterface 1 {
type bridged
vlan {
encap {
single-tagged {
vlan-id 100
}
}
}
}
}
// Configure an IRB interface and sub-interface that will connect
the MAC-VRF to the existing default network-instance.
--{ [FACTORY] + candidate shared default }--[ interface irb* ]--
A:Leaf-1# info
interface irb1 {
subinterface 1 {
ipv4 {
admin-state enable
address 10.0.0.2/24 {
}
}
ipv6 {
admin-state enable
address 2001:db8::2/64 {
}
}
}
}
// Configure the network-instance type mac-vrf
and associate the bridged and irb interfaces to it.
--{ [FACTORY] + candidate shared default }--[ network-instance MAC-VRF-1 ]--
A:Leaf-1# info
type mac-vrf
admin-state enable
interface ethernet-1/1.1 {
}
interface irb1.1 {
}
// Associate the same IRB interface to the network-
instance default and configure the BGP IPv4 and IPv6 neighbors to DUT1 and DUT3.
--{ [FACTORY] + candidate shared default }--[ network-instance default ]--
A:Leaf-1# info
type default
admin-state enable
router-id 2.2.2.2
interface irb1.1 {
}
protocols {
bgp {
admin-state enable
afi-safi ipv4-unicast {
admin-state enable
}
autonomous-system 64502
router-id 10.0.0.2
ebgp-default-policy {
import-reject-all false
}
failure-detection {
enable-bfd true
fast-failover true
}
group leaf {
admin-state enable
export-policy pass-all
afi-safi ipv4-unicast {
admin-state enable
}
afi-safi ipv6-unicast {
admin-state enable
}
local-as as-number 64502 {
}
timers {
minimum-advertisement-interval 1
}
}
afi-safi ipv4-unicast {
admin-state enable
}
afi-safi ipv6-unicast {
admin-state enable
}
neighbor 10.0.0.1 {
peer-as 64501
peer-group leaf
transport {
local-address 10.0.0.2
}
}
neighbor 2001:db8::1 {
peer-as 64501
peer-group leaf
transport {
local-address 2001:db8::2
}
}
}
}