Route internal tags (tag-sets in routing policies)
Route tags are pieces of information or identifiers attached to individual routes. They can be either external (protocol) tags or internal tags:
- External (protocol) tags are sent on the wire and are typically part of a routing protocol; for example, IS-IS route tags and OSPF route tags.
- Internal tags are not sent on the wire, and they have meaning only within an individual system. Internal tags are assigned to routes by policies or specific commands, and are used by policies to match on a group of routes. Internal tags are typically used to facilitate the matching of multiple routes at the same time or propagate route attributes between different routing protocols.
This chapter describes SR Linux support for internal tags and how to configure them.
About internal tags
In SR Linux, route internal tags are data structures that are attached to IP routes in the FIB or EVPN-specific routes. Internal tags are useful for carrying protocol information such as communities, area-id, as-path, and so on, from one routing protocol context to another. For example, BGP can push its attribute fields, such as local preference, into the FIB as an internal tag. On export, the internal tag associated with the route can be matched by export policies to map the tag into any other metric for a routing protocol.
Every FIB route can be associated with an array of tags. The number of array elements is limited to a maximum of 2 in the current release.
To define internal tags in SR Linux, you configure tag-sets at the
routing-policy level, and refer to the tag-sets by name at
other configuration levels. See Configuring route internal tags.
SR Linux applications that support internal tags
The following SR Linux applications can write internal tags:
- EVPN and Layer 2 proxy-ARP/ND
EVPN and Layer 2 proxy-ARP/ND support writing internal tags for all MAC/IP advertisement routes generated out of the active MACs in the mac-table or IP-to-MAC bindings in the proxy-ARP/ND tables, respectively.
- Layer 3 ARP/ND
SR Linux supports writing internal tags into ARP/ND entries that generate an EVPN MAC/IP advertisement route and also into the ARP/ND entries that generate an arp-nd host route into the route-table.
- Layer 3 routes
In SR Linux, BGP can write internal tags into the route-table entries for a routed network-instance. In this case, all routes to be exported as prefix routes are assigned the configured internal tag.
The route-table includes a state leaf-list with the allocated
internal-tagstag values that indicate whether a specific route entry is associated with an internal tag.
Routing policies and internal tags
An import or export policy can write an internal tag as a configured
action or default-action. These actions are
supported on BGP policies applied to the supported families; that is,
ipv4-unicast, ipv6-unicast, and
evpn.
When internal tags are used in BGP import policies, the policies can be applied at the default network-instance level (including global, per-group, or per-peer policies), MAC-VRF network-instance level, or IP-VRF network-instance level.
When internal tags are used in BGP export policies, the policies can be applied at the MAC-VRF or IP-VRF network-instance level, or IP-VRF/default network-instance level for inter-instance policies.
When an import policy matches an IPv4 BGP route, IPv6 BGP route, or EVPN IP prefix
route (route type 5) and adds a tag-set, the corresponding route created in the
route-table contains the internal tag and is exposed in the route-table entry
internal-tags.
When the import policy matches an EVPN MAC/IP advertisement route (route type 2) and adds a tag-set as an action, the corresponding created MAC and/or ARP/ND entry is associated with the internal tag. Matching on any other EVPN route type and adding an internal tag has no effect, since the rest of the EVPN route types do not create entries into the MAC table, ARP/ND table, or route table.
A MAC/IP VRF export policy can add a tag-set as an action in the following cases
- On a MAC-VRF, the
bgp-vpn.bgp-instance.export-policycan match EVPN MAC/IP routes (with or without IP address) generated for dynamic or static entries in the mac-table or proxy-ARP/ND table; that is, basically for any entry that generates a MAC/IP advertisement route in the context of the MAC-VRF. In those policies, a tag-set can be added. The same tag-set can be matched on peer/group-level export policies in the default network-instance. - On an IP-VRF, the
bgp-vpn.bgp-instance.export-policycan match any route-table entry that generates an EVPN IP prefix route in the context of the IP-VRF. In these policies, a tag-set can be added as an action, and the same tag-set can be matched by a peer/group-level export policy in the default network-instance. - On an IP-VRF or default network-instance, the
inter-instance-policies.export-policycan match any route-table entry and make those entries available for leaking. The internal tag can be used by aninter-instance-policies.import-policyto match the routes that are actually leaked into the destination Layer 3 network-instance.
Insertion points for internal tags
The following diagram shows the SR Linux applications that can write an internal tag, insertion points for the internal tags, and the policy points where internal tag matching can take place.
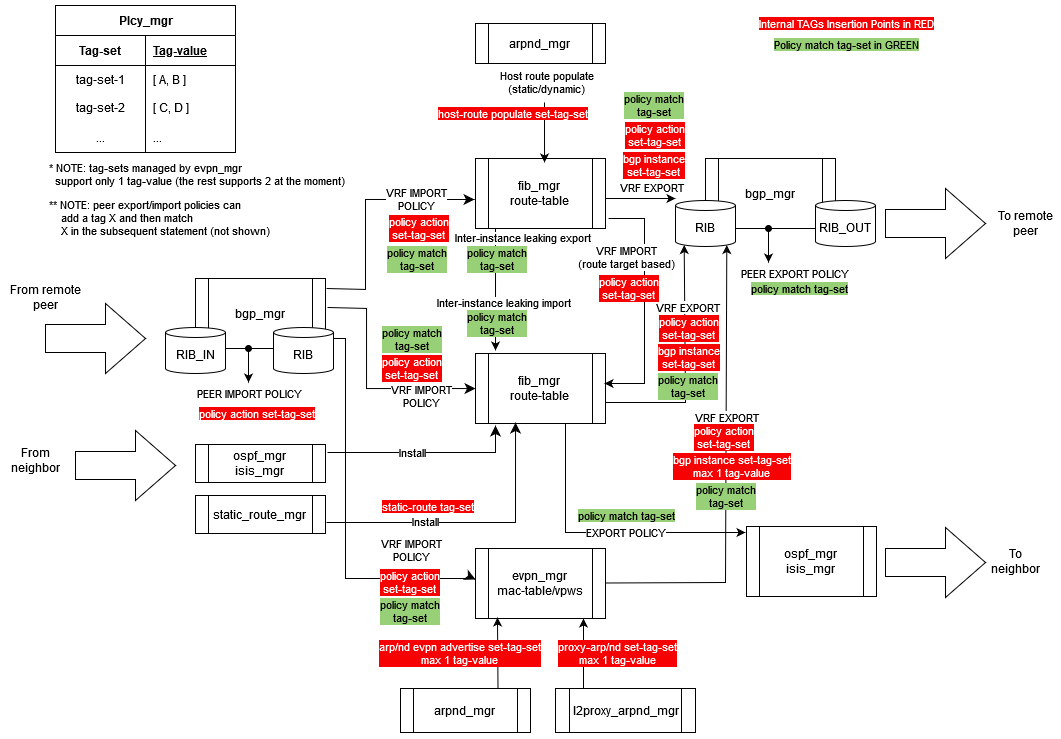
Order of precedence when multiple applications write internal tags
As described in the previous section, multiple SR Linux applications can write internal
tags for a route. For example, a newly created ARP-ND host 10.0.0.1/32 route can be
associated with tag-set TAG-1, and at the same time an export policy
applied on IP-VRF-1, where 10.0.0.1/32 is installed, may have an action to write tag-set
TAG-2 or the same route.
In this case, SR Linux applies precedence rules to determine the tag-set that gets applied to the route. The following sections describe the precedence rules applied when multiple applications attempt to write an internal tag on the same route.
Writing a tag for MAC/IP routes generated for a MAC-VRF
The order in which the internal tag is applied is as follows:
(proxy-arp/nd tag (mac-vrf) + vrf-export-policy tag (mac-vrf level)) > (bgp-evpn.bgp-instance tag (mac-vrf) +vrf-export-policy tag (mac-vrf level))
That is, up to two tag-values can be written. However, if the route already has a tag-value, then the bgp-evpn.bgp-instance tag is not used. The vrf-export-policy tag action always appends to the route's tag (if already present on the route), or the default tag (under the bgp-instance) if configured.
Writing a tag for MAC/IP routes generated for a MAC-VRF with IRB
(arp/nd evpn tag (irb) + vrf-export-policy tag (mac-vrf level)) > (bgp-evpn.bgp-instance tag (mac-vrf) +vrf-export-policy tag (mac-vrf level))
In the same way as proxy-arp/nd tags, up to two tag-values can be written, and if the route already has a tag-value, then the bgp-evpn.bgp-instance tag is not used. The vrf-export-policy tag action always appends to the route's tag (if already present on the route), or the default tag (under the bgp-instance) if configured.
Writing a tag for ARP-ND host routes in an IP-VRF
Tags are appended until a maximum of two is reached, so the vrf-export policy action does not overwrite the tag if that is already present. The default tag of the instance is used when arpnd does not add a tag.
A peer-export policy uses this precedence:
(arp/nd host-route tag (irb) + vrf-export policy tag) > (bgp-evpn.bgp-instance tag (ip-vrf) + vrf-export policy tag)
Writing a tag for IP routes in an IP-VRF (irrespective of the owner)
Tag-values are appended until a maximum of two is reached, so the vrf-export policy action does not overwrite the import-policy tag if that is already present. The default tag of the instance is used when import-policy does not add a tag.
A peer-export policy uses this precedence:
(peer-import-policy-tag + vrf-export policy tag) > (bgp-evpn.bgp-instance tag (ip-vrf) + vrf-export policy tag)
In cases where the routes are static routes, IS-IS routes, OSPF routes, and so on, when exported into EVPN IP prefix routes, there is no peer-import-policy.
In cases where there are BGP PE-CE routes that are imported into the IP-VRF route-table and readvertised as EVPN IP prefix routes, there are peer-import-policies, and the preference is as above.
Writing a tag for MAC/IP routes in MAC-VRF or routes in IP-VRF via multiple import policies
If multiple import-policies match the same route and try to write a tag, writing is allowed until a maximum of two tag-values is reached. Note that applying "multiple import-policies" refers to policy chaining at the peer-import level.
Writing a tag for routes via vrf-import and peer import policies
If both vrf-import and peer-import policies apply to a route, and each step inserts a tag-set, then the tag-set applied as a result of the vrf-import policy takes precedence.
Writing a tag for BGP routes in an ECMP set
If BGP creates an ECMP set for a prefix, when installing such a prefix in the FIB, BGP copies the tag-set of the best route into fib_mgr. This is what other protocols would see when importing the prefix from fib_mgr.
This also applies to BGP VPN routes that are received with different RDs and combined in an ECMP set.
Configuring route internal tags
To configure route internal tags, you configure a tag-set and configure one or more applications to write the tag-set to routes.
Configure a tag-set
--{ * candidate shared default }--[ ]--
# info routing-policy
routing-policy {
tag-set ts1 {
tag-value [
1
2
]
}
}Match a tag-set in a routing policy
--{ +* candidate shared default }--[ ]--
# info routing-policy policy match_tag_1
routing-policy {
policy match_tag_1 {
statement 1 {
match {
internal-tags {
tag-set [
ts1
]
}
}
}
}
}Write a tag-set as an action in a routing policy
--{ * candidate shared default }--[ ]--
# info routing-policy policy d1
routing-policy {
policy t1 {
default-action {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}Write internal tags for MAC/IP advertisement routes generated out of the active MACs in the MAC table
--{ * candidate shared default }--[ ]--
# info network-instance vrf1
network-instance vrf1 {
type mac-vrf
protocols {
bgp-evpn {
bgp-instance 1 {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}Write internal tags for IP-to-MAC bindings in proxy-ARP/ND tables
--{ * candidate shared default }--[ ]--
# info network-instance vrf1 bridge-table proxy-arp evpn
network-instance vrf1 {
bridge-table {
proxy-arp {
evpn {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}--{ * candidate shared default }--[ ]--
# info network-instance vrf1 bridge-table proxy-nd evpn
network-instance vrf1 {
bridge-table {
proxy-nd {
evpn {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}Write internal tags into ARP/ND entries that generate an EVPN MAC/IP advertisement route
--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1 subinterface 1 ipv4 arp evpn
interface ethernet-1/1 {
subinterface 1 {
ipv4 {
arp {
evpn {
advertise dynamic {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}
}
}--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1 subinterface 1 ipv6 neighbor-discovery
interface ethernet-1/1 {
subinterface 1 {
ipv6 {
neighbor-discovery {
evpn {
advertise dynamic {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}
}
}Write internal tags into ARP/ND entries that generate an ARP/ND host route into the route table
--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1 subinterface 1 ipv4 arp
interface ethernet-1/1 {
subinterface 1 {
ipv4 {
arp {
host-route {
populate evpn {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}
}
}--{ * candidate shared default }--[ ]--
# info interface ethernet-1/1 subinterface 1 ipv6 neighbor-discovery
interface ethernet-1/1 {
subinterface 1 {
ipv6 {
neighbor-discovery {
host-route {
populate evpn {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}
}
}
Write internal tag into routes to be exported as EVPN IP prefix routes
--{ * candidate shared default }--[ ]--
# info network-instance ip-vrf-1 protocols bgp-evpn bgp-instance 1
network-instance ip-vrf-1 {
protocols {
bgp-evpn {
bgp-instance 1 {
internal-tags {
set-tag-set [
ts1
]
}
}
}
}
}