sFlow
sFlow is used to monitor data traffic flows traversing different points in a network. The sFlow functionality uses an sFlow agent and an sFlow collector. The agent is software that runs on a network element and samples and reports flow headers and statistics. The collector is software that typically runs on a remote server and receives the flow headers and statistics from one or more sFlow agents.
Sampling and reporting are accomplished as the sFlow agent running on a network element takes periodic samples of ingress traffic and reports the data to one or more collectors. The network element does not need to maintain a local flow cache. Instead, the sampled header information is immediately sent to the collector without additional processing.
- DSCP configuration is supported only on 7250 IXR systems.
- Frame sample sizes of 256 or 512 bytes are supported only on 7250 IXR systems.
- IPv6 sFlow collector configuration is supported only on 7250 IXR systems.
sFlow sampling
sFlow works by sampling flow data and reporting the samples to the configured sFlow collectors. Based on the configured system sampling rate, the forwarding plane samples ingress packet flows and sends the sampled headers to the sFlow agent in the control plane.
- 7220 IXR systems – samples include the top 256 bytes of the sampled packet, starting at the outer Ethernet header
- 7250 IXR systems – samples include the top 256 or 512 bytes of the sampled packet, starting at the outer Ethernet header
For sampled IPv4 packets, the IPv4 header data fields are sent with the raw data. For sampled IPv6 packets, the IPv6 header data fields are sent with the raw data.
sFlow collector reporting
sFlow reports sampled headers and statistics to the configured collectors using IP/UDP datagrams. UDP port 6343 is the default destination port, but you can optionally configure a different port. Sampled packets are sent as soon as the samples are taken, and interface statistics are sent at 10 second intervals. SR Linux supports up to eight remote IPv4 sFlow collectors or one remote IPv6 sFlow collector. IPv6 sFlow collector configuration is supported only on 7250 IXR systems. IPv4 and IPv6 sFlow collectors are mutually exclusive and cannot be configured simultaneously. Each collector can only have one IPv4 or IPv6 address. The flow and counter samples are aggregated in an sFlow datagram packet in software implementation.
sFlow DSCP settings
On 7220 IXR systems, flow and counter samples are assigned a non-configurable default DSCP value of 0.
- Flow samples are also assigned a default DSCP value of 0, but you can optionally assign a different DSCP value for flow samples that applies to all collectors.
- Counter samples are assigned a default DSCP value of 34, which cannot be modified.
sFlow counter samples
Another aspect of the sFlow agent is streaming of interface statistics to configured sFlow collectors. Statistics are only sent to a collector if sFlow has been enabled on an interface. Interface statistics are sent based on a default poll-interval of 10 seconds with a separate timer for each interface. When the interval expires. the current value of each associated statistics are sent to the configured collectors.
The interface counter sample contains:
Interface index
Interface type
Interface speed
Oper and admin status
Input octets
Input packets
Input broadcast packets
Input discards packets
Output errors
Output octets
Output packets
Output broadcast packets
Output discards packets
Configuring the sFlow agent
To configure the sFlow agent on the system, you enable sFlow, and optionally configure the sampling rate (by default, 1 out of every 10 000 packets) and sample size (by default, 256 bytes are sampled from each packet).
Configuring the sFlow agent
The following example enables sFlow on the system and configures the system sampling rate and sample size. The polling interval is not configurable. The following sample size options apply:
-
7220 IXR-D2, D3, D4, D5, and 7220 IXR-H systems: 256 bytes
-
7250 IXR 6/10: 256 or 512 bytes
--{ * candidate shared default }--[ ]--
# info
system {
sflow {
admin-state enable
sample-rate 50000
sample-size 512
}
}Configuring sFlow collectors
The sFlow agent sends sampled packets to sFlow collectors. You can configure up to eight IPv4 sFlow collectors or one IPv6 sFlow collector to receive the data. IPv6 sFlow collector configuration is supported only on 7250 IXR systems. IPv4 and IPv6 sFlow collectors are mutually exclusive and cannot be configured simultaneously. To configure an sFlow collector, you specify its IP address, associated network instance, and IP address to be used as the source IP address in sFlow packets sent from SR Linux to the collector. You can optionally specify a destination port (by default, this is UDP port 6343).
Configuring a network-instance is mandatory. Also, a collector cannot be reached using the mgmt network-instance.
Configuring IPv4 sFlow collectors
The following example configures two IPv4 sFlow collectors. The IP address for each collector is configured, as well as its network instance and source IP address. Each collector receives all samples. The collector DSCP value for flow samples is also configured (applicable only on 7250 IXR systems). If no value is specified, the default DSCP value of 0 applies.
--{ * candidate shared }--[ ]--
#info system sflow
system {
sflow {
dscp 14
collector 1 {
collector-address 10.50.4.1
source-address 192.0.2.1
network-instance default
}
collector 2 {
collector-address 10.50.4.2
source-address 10.1.5.2
network-instance default
port 4310
}
}
}
Configuring an IPv6 sFlow collector
--{ * candidate shared default }--[ ]--
# info system sflow
system {
sflow {
collector 1 {
collector-address 2001:db8::1
network-instance default
source-address 2001:db8::2
}
}
}Configuring sFlow for an interface
When sFlow is configured for an interface, the ingress packets are taken for sampling according to the sample-rate.
Configuring sFlow for an interface
The following example enables sFlow on an interface.
--{ * candidate shared }--[ ]--
interface ethernet-1/1 {
sflow {
admin-state enable
}
}
Displaying the state of the sFlow agent
To display the system-wide state of the sFlow agent, including any sFlow parameters, collector configuration, and general statistics, use the info from state command in candidate or running mode, or the info command in state mode.
Info from state command
# info from state system sflow
system {
sflow {
admin-state enable
sample-rate 1000
sample-size 256
collector 1 {
collector-address 10.1.1.24
network-instance default
source-address 10.0.0.1
port 6343
next-hop 172.24.71.65
}
statistics {
total-samples-taken 5457
total-sent-packets 26800
}
}
}
Displaying the status of the sFlow agent
Use the show system sflow status command in show mode to display the general status of the sFlow agent:
Show system sflow status command
--{ running }--[ ]--
# enter show
# show system sflow status
-------------------------------------
Admin State : enable
Sample Rate : 10000
Sample Size : 256
DSCP : 0
Total Samples : 0
Total Collector Packets: 3269158
-------------------------------------
collector-id : 8
collector-address: 172.10.10.10
network-instance : default
source-address : 10.0.0.1
port : 6343
next-hop : 172.24.71.65
-------------------------------------
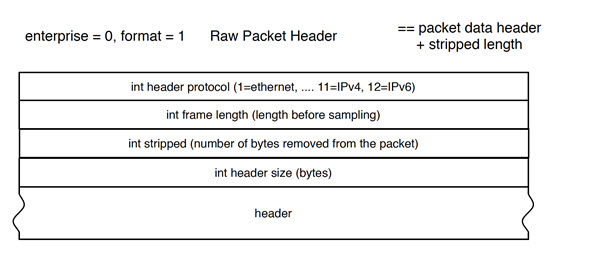
sFlow formats
Raw packet header shows an example of a raw packet header for an sFlow format.
Sampled data and counter examples
The following is an example of IPv4 flow sample data:
IPv4 flow sample data
InMon sFlow
Datagram version: 5
Agent address type: IPv4 (1)
Agent address: 10.0.0.1
Sub-agent ID: 2
Sequence number: 0
SysUptime: 0
NumSamples: 1
Flow sample, seq 0
0000 0000 0000 0000 0000 .... .... .... = Enterprise: standard sFlow (0)
.... .... .... .... .... 0000 0000 0001 = sFlow sample type: Flow sample (1)
Sample length (byte): 141
Sequence number: 0
0000 0000 .... .... .... .... .... .... = Source ID class: 0
.... .... 0000 0000 0000 0000 0011 0110 = Index: 54
Sampling rate: 1 out of 5 packets
Sample pool: 0 total packets
Dropped packets: 0
Input interface (ifIndex): 54
.000 0000 0000 0000 0000 0000 0011 0110 = Output interface (ifIndex): 54
Flow record: 1
Raw packet header
0000 0000 0000 0000 0000 .... .... .... = Enterprise: standard sFlow (0)
Format: Raw packet header (1)
Flow data length (byte): 101
Header protocol: Ethernet (1)
Frame Length: 98
Payload removed: 0
Original packet length: 85
Header of sampled packet:
000c00020000000000111111080045000052000000004006...
Ethernet II, Src: 00:00:00_11:11:11 (00:00:00:11:11:11),
Dst: BebIndus_02:00:00 (00:0c:00:02:00:00)
Destination: BebIndus_02:00:00 (00:0c:00:02:00:00)
Source: 00:00:00_11:11:11 (00:00:00:11:11:11)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.100.1.2, Dst: 10.1.1.2
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 82
Identification: 0x0000 (0)
Flags: 0x00
Fragment offset: 0
Time to live: 64
Protocol: TCP (6)
Header checksum: 0x35a1 [validation disabled]
[Header checksum status: Unverified]
Source: 10.100.1.2
Destination: 10.1.1.254
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
Transmission Control Protocol, Src Port: 0, Dst Port: 0, Seq: 0
LBT-TCP Protocol
LBMC Protocol
[Unreassembled Packet: LBT-TCP]
The following is an example of IPv6 flow sample data:
IPv6 flow sample data
InMon sFlow
Datagram version: 5
Agent address: 3000::2 (3000::2)
Sub-agent ID: 24
Sequence number: 1011
SysUptime: 63684188
NumSamples: 1
Flow sample, seq 2368
Enterprise: standard sFlow (0)
sFlow sample type: Flow sample (1)
Sample length (byte): 568
Sequence number: 2368
Source ID class: 0 index: 704510
Sampling rate: 1 out of 1 packets
Sample pool: 0 total packets
Dropped packets: 0
Input interface: ifIndex 134922238
Output interface: ifIndex 0
Flow record: 1
Raw packet header
Enterprise: standard sFlow (0)
Format: Raw packet header (1)
Flow data length (byte): 528
Header protocol: Ethernet (1)
Frame Length: 125 bytes
Payload removed: 0 bytes
Header of sampled packet: 01005e000002000103ff02018100c064080045c0006b3005...
Ethernet II, Src: 3com_ff:02:01 (00:01:03:ff:02:01), Dst:
IPv4mcast_00:00:02 (01:00:5e:00:00:02)
802.1Q Virtual LAN, PRI: 6, CFI: 0, ID: 100
Internet Protocol Version 4, Src: 192.35.1.1 (192.35.1.1),
Dst: 224.0.0.2 (224.0.0.2)
User Datagram Protocol, Src Port: ldp (646), Dst Port: ldp (646)
Label Distribution Protocol
Version: 1
PDU Length: 75
LSR ID: 3.3.3.1 (3.3.3.1)
Label Space ID: 0
Hello Message
The following is a counter sample example:
Counters sample
InMon sFlow
Datagram version: 5
Agent address: 10.0.0.1 (10.0.0.1)
Sub-agent ID: 0
Sequence number: 8
SysUptime: 6548000
NumSamples: 1
Counters sample, seq 1
Enterprise: standard sFlow (0)
sFlow sample type: Counters sample (2)
Sample length (byte): 108
Sequence number: 1
Source ID type: 64
Source ID index: 49150
Counters records: 1
Generic interface counters
Enterprise: standard sFlow (0)
Format: Generic interface counters (1)
Flow data length (byte): 88
Interface index: 1073790974
Interface Type: 6
Interface Speed: 25600
IfDirection: Full-Duplex
IfAdminStatus: Up
IfOperStatus: Up
Input Octets: 0
Input Packets: 0
Input Multicast Packets: 0
Input Broadcast Packets: 0
Input Discarded Packets: 0
Input Errors: 0
Input Unknown Protocol
Packets: 0
Output Octets: 0
Output Packets: 0
Output Multicast Packets: 0
Output Broadcast Packets: 0
Output Discarded Packets: 0
Output Errors: 0
Promiscuous Mode: 0