Multi-Chassis IPSec Redundancy
This chapter provides information about multi-chassis IPSec redundancy configurations.
Topics in this chapter include:
Applicability
This initial version of this chapter was based on SR OS Release 10.0.R8, but the CLI in the current edition corresponds to SR OS Release 22.10.R2.
Overview
Multi-Chassis IPSec redundancy (MC-IPSec) is a stateful inter-chassis IPSec failover mechanism. IPSec tunnel states are synchronized between the primary and standby chassis. A tunnel group failure on the primary chassis or a primary chassis failure could trigger MC-IPSec failover to the standby chassis.
The following are some highlights of this feature:
Internet Key Exchange version 2 (IKEv2) only
Multi-active tunnel group only
The granularity of failover is tunnel group, which means a specific tunnel group could failover to the standby chassis independent of other tunnel groups on the primary chassis
Both static and dynamic LAN-to-LAN tunnels are supported
This feature has the following building blocks:
Primary chassis election: MC-IPSec mastership protocol (MIMP) runs between the chassis to elect a primary chassis with independent MIMP runs for each tunnel group
Synchronization: multi-chassis synchronization (MCS) synchronizes the IPSec states between chassis
Routing:
MC-IPSec-aware routing attracts traffic to the primary chassis
Shunting support
MC-IPSec-aware virtual router redundancy protocol (VRRP)
MC-IPSec architecture shows two redundant IPSec chassis in the middle: a primary chassis and a standby chassis.
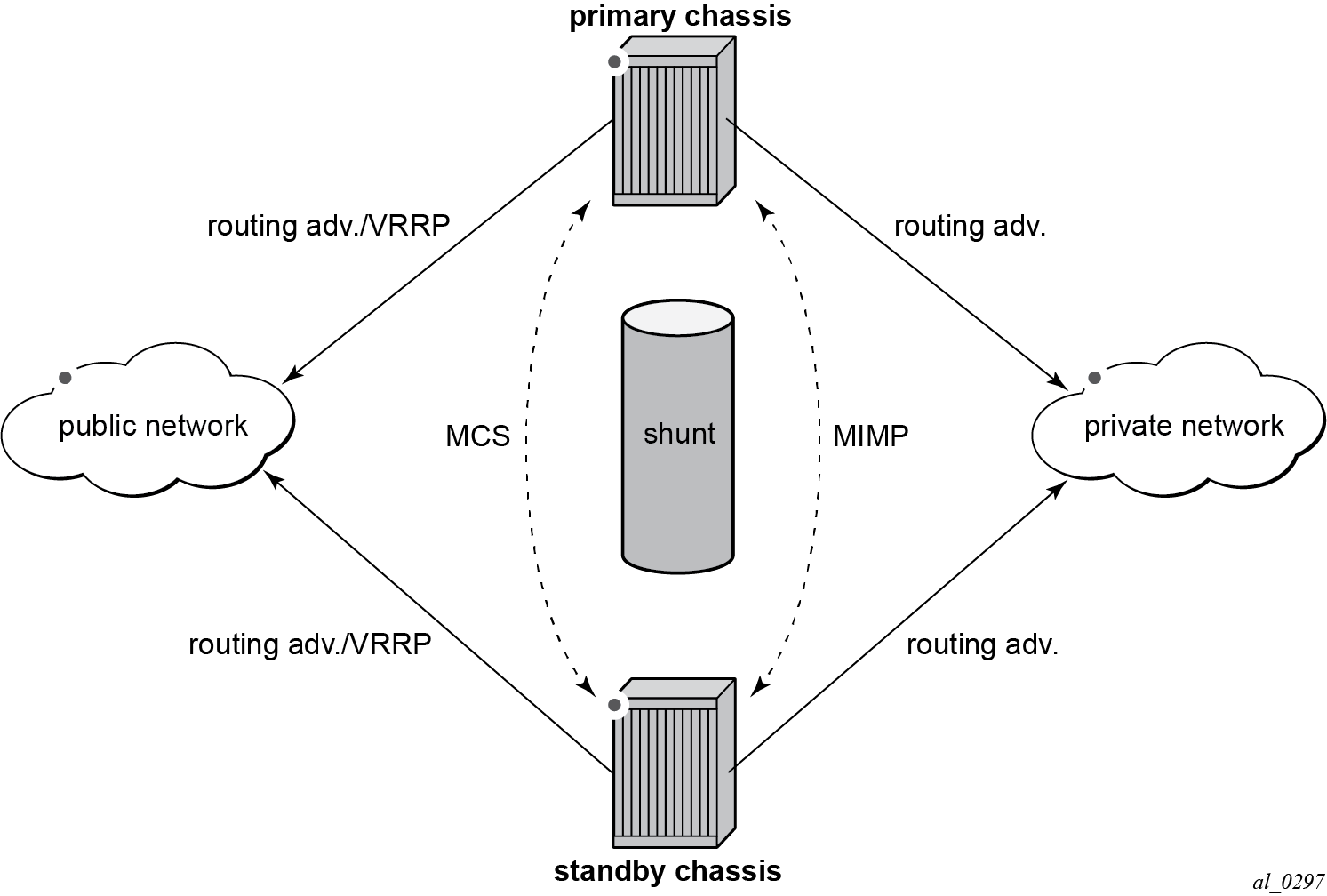
The fundamentals of MC-IPSec are:
Only the primary chassis processes encapsulating security payload (ESP) and IKE traffic. If the standby chassis receives traffic, it shunts it to the primary chassis, if possible. The traffic is discarded if the standby chassis fails to shunt the traffic.
The same local gateway address must be provisioned on both chassis.
MC-IPSec does not synchronize configurations.
MC-IPSec-aware routing attracts traffic to the primary chassis for both public and private services, which is achieved by exporting the corresponding IPSec routes to the routing protocol using a route policy and setting a different routing metric according to the MC-IPSec state.
In case of a Layer 2 public network, MC-IPSec-aware VRRP can be used to trigger VRRP switchover upon MC-IPSec switchover.
MCS synchronizes IPSec states between chassis so that existing IPSec tunnels do not need to be re-established upon switchover.
MIMP elects mastership between two chassis, and it can also detect chassis failure and tunnel group failure; a central BFD session can be associated with MIMP to achieve fast chassis failure detection.
Configuration
The example topology is shown in Example topology.
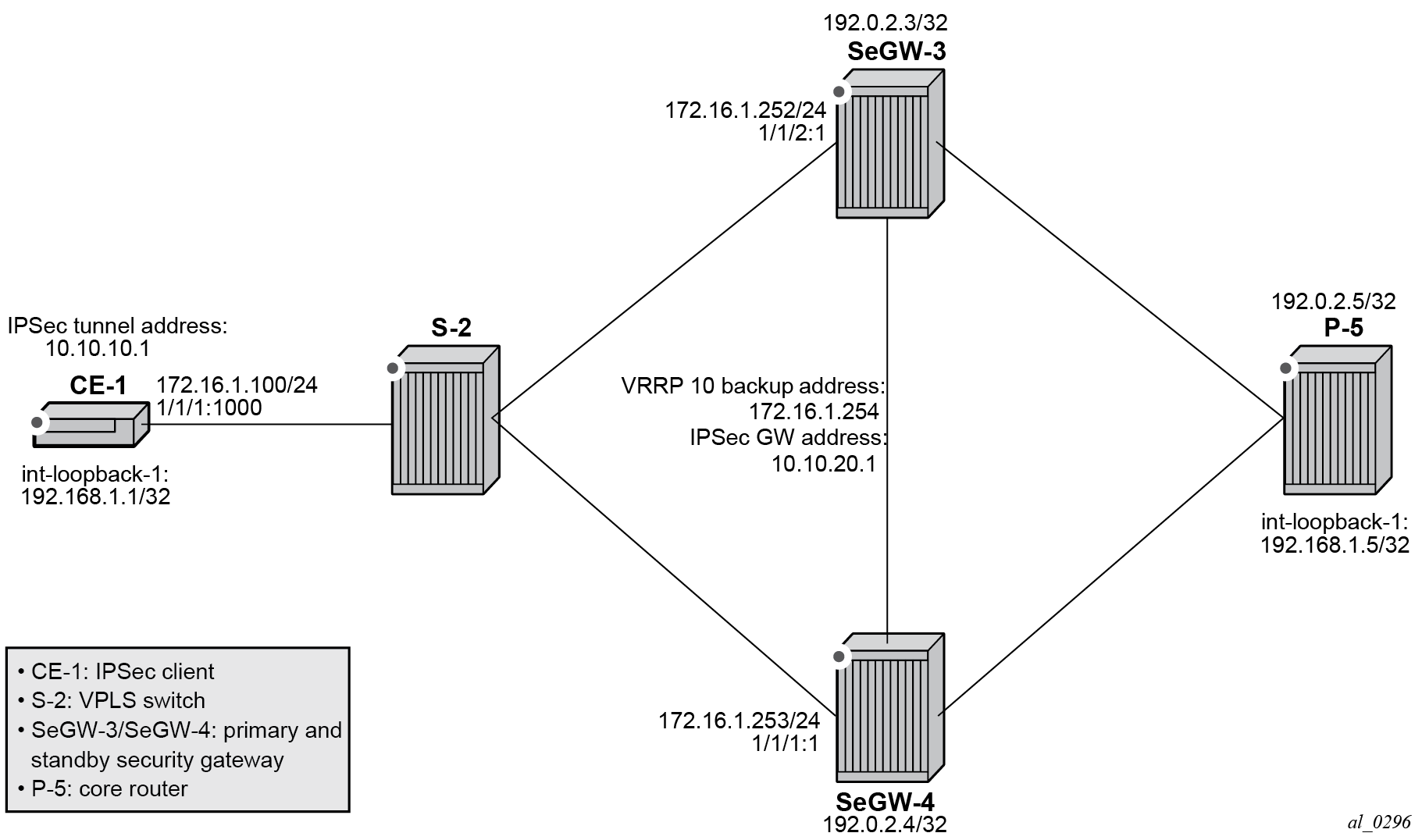
The example setup includes:
-
an IPSec tunnel initiated by CE-1 and terminated on the primary chassis of the two SeGWs.
-
a public IES service "IES-1" and a private VPRN service "VPRN-2" configured on CE-1, SeGW-3, and SeGW-4.
-
VPRN 2 (also) configured on P-5.
-
a static LAN-to-LAN tunnel with pre-shared key.
-
a local VPLS service "VPLS-3" on S-2 to simulate a Layer 2 switch.
-
VRRP 10 between SeGW-3 and SeGW-4 to provide a backup address 192.168.1.254, which is the default next hop for CE-1.
-
VRRP policy 1 bound to VRRP 10 on the primary chassis SeGW-3 to change the in-use priority upon MC-IPSec switchover.
-
OSPF as IGP running in the base routing instance between SeGW-3, SeGW-4, and P-5.
-
MP-BGP running between SeGW-3, SeGW-4, and P-5 for the VPN-IPv4 address family.
A ping in VPRN 2 between loopback interface address 192.168.1.1 on CE-1 and 192.168.1.5 on P-5 is used to verify the connectivity over the IPSec tunnel.
The MC-IPSec configuration commands are shown below.
config>redundancy>multi-chassis>
peer <ip-address> [create]
sync
ipsec
tunnel-group <tunnel-group-id> sync-tag <tag-name> [create]
mc-ipsec
bfd-enable
discovery-interval <interval-1> [boot <interval-2>]
hold-on-neighbor-failure <multiplier>
keep-alive-interval <interval>
tunnel-group <tunnel-group-id> [create]
peer-group <tunnel-group-id>
priority <priority>
shutdown
config>router>policy-options>policy-statement>entry>from>
state ipsec-master-with-peer|ipsec-non-master|ipsec-master-without-peer
protocol ipsec
config>service>ies>if>
config>service>vprn>if>
static-tunnel-redundant-next-hop <ip-address>
dynamic-tunnel-redundant-next-hop <ip-address>
config>isa>tunnel-grp>
ipsec-responder-only
config>vrrp>policy>priority-event>
mc-ipsec-non-forwarding <tunnel-grp-id>
hold-clear <seconds>
hold-set <seconds>
priority <priority-level> explicit
The parameters are the following:
- in the configure redundancy multi-chassis
context:
-
peer <ip-address> [create] — This command creates or enters a multi-chassis peer. The peer address is by default the system address. This can be changed on the peer using the configure redundancy multi-chassis peer source-address command.
-
sync — This command enters the sync configuration context.
-
ipsec — This command enables MCS to synchronize IPSec states.
-
tunnel-group <tunnel-group-id> sync-tag <tag-name>[create] — This command enables MCS to synchronize the IPSec states of the specified tunnel group. The sync-tag parameter is used to match the tunnel group of the peer. The tunnel group states with the same sync-tag on both chassis will be synchronized.
-
-
mc-ipsec — This command enters the multi-chassis IPSec configuration context.
-
bfd-enable — This command enables tracking a central BFD session; if the BFD session goes down, then the system considers the peer as down and changes the MC-IPSec status of the configured tunnel group accordingly.
The BFD session uses the source address of MCS as its source address and the MCS peer address as the destination address. Other BFD parameters are configured with the bfd command on the interface that the MCS source address resides on.
The configuration of BFD is optional for MC-IPSec.
-
discovery-interval <interval-1> [boot <interval-2>] — This command specifies the time interval that the tunnel group stays in discovery state. Interval 1 is used as discovery interval when a new tunnel group is added to multi-chassis redundancy (mp-ipsec); interval 2 is used as discovery interval after system boot-up. Interval 2 is optional, and when it is not specified, the value for interval 1 is used. Both intervals have a default value of 300 seconds.
-
hold-on-neighbor-failure <2..25> — This command specifies the number of keep-alive failures before considering the peer to be down. The default value is 3.
-
keep-alive-interval <5..500> — This command specifies the time interval of the mastership election protocol keep-alive packets in deciseconds. The default value is 10 deciseconds (1 s).
-
tunnel-group <tunnel-group-id> [create] — This command enables multi-chassis redundancy for the specified tunnel group, or enters an already configured tunnel group context. The configured tunnel groups can failover independently.
-
peer-group <tunnel-group-id> — This command specifies the corresponding tunnel group ID on the peer node. The peer tunnel group ID is not necessarily equal to local tunnel group ID.
-
priority <priority> — This command specifies the local priority of the tunnel group, this is used to elect a primary chassis, where the higher number prevails. If the priorities are the same, then the peer which has more active ISAs wins; if the priority and the number of active ISAs are same, then the peer with higher IP address wins. The range is from 0 to 255 and the default value is 100.
-
-
-
-
-
in a from statement of a route policy entry:
-
state ipsec-master-with-peer | ipsec-non-master | ipsec-master-without-peer — These commands specify the MC-IPSec state in a from statement of a route policy entry:
-
ipsec-master-with-peer: The tunnel group is the primary chassis with a peer reachable.
-
ipsec-master-without-peer: The tunnel group is the primary chassis with peer unreachable.
-
ipsec-non-master: The tunnel group is not the primary chassis.
-
-
protocol ipsec — This command specifies IPSec as protocol in a from statement of a route policy entry. protocol ipsec refers to the /32 local gateway routes (of both static and dynamic tunnels) and reverse route of dynamic tunnel.
-
-
on a public or private IPSec interface in an IES or VPRN service:
-
static-tunnel-redundant-next-hop <ip-address> and dynamic-tunnel-redundant-next-hop <ip-address> — These commands specify the redundant next hop address on a public or private IPSec interface (with public or private tunnel SAP) for a static and dynamic IPSec tunnel respectively. The specified next hop address is used by the standby chassis to shunt traffic to the primary chassis in case it receives any traffic. The next hop address is resolved in the routing table of the corresponding service.
Note:-
Shunting is supported over:
-
directly connected SAPs
-
spoke SDP terminated IP interfaces
-
-
Shunting over auto-bind tunnel is not supported.
-
Shunting does not work if the tunnel group is down.
-
-
-
in the isa tunnel-group <id> context:
-
ipsec-responder-only — With this command enabled, the system only acts as IKE responder except for the automatic CHILD_SA rekey upon MC-IPSec switchover.
This command is required for MC-IPSec support of static LAN-to-LAN tunnels.
-
-
in the vrrp policy <id> priority-event context:
-
mc-ipsec-non-forwarding <tunnel-grp-id> — This command creates a VRRP policy priority event: mc-ipsec-non-forwarding, which is triggered whenever the specified tunnel group enters the non-forwarding state.
-
hold-clear <seconds> — This command configures the hold time before clearing the event. The range is from 0 to 86400 seconds and the default value is 0 s.
-
hold-set <seconds> — This command configures the hold time before setting the event. The range is from 0 to 86400 seconds and the default value is 0 s.
-
priority <priority-level> explicit — This command sets the VRRP in-use priority to the configured value upon the event. The range is from 0 to 254 and the default value is 0.
-
-
The initial configuration must include the following:
-
The system time of SeGW-3 and SeGW-4 must be the same for the feature to work. Nokia recommends to use a time synchronization protocol such as NTP or SNTP.
-
SeGW-3 and SeGW-4 must be IP reachable in the base routing instance because both MCS and MIMP run in the base routing instance.
Configuration of MC-IPSec
In this section, the following steps are described:
- configure CE-1
- configure S-2
- configure P-5
- configure IPSec tunnel on SeGW-3
- enable MC-IPSec for tunnel group on SeGW-3
- configure MC-IPSec-aware routing on SeGW-3
- configure MC-IPSec-aware VRRP on SeGW-3
- configure SeGW-4
Configure CE-1
On CE-1, the following is configured:
-
a public IES service "IES-1" and a private VPRN service "VPRN-2".
-
a static default route pointing to the VRRP backup address 172.16.1.254.
-
a static IPSec tunnel "tunnel-1" with local address 10.10.10.1 and remote address 10.10.20.1.
-
a loopback interface in VPRN 2 with address 192.168.1.1/32 to be used as source address for the ping command to verify the connectivity between CE-1 and P-5 over the IPSec tunnel.
The following base router configuration on CE-1 includes a static route with next hop 172.16.1.254, which is the VRRP backup address.
# on CE-1
configure
router Base
interface "int-CE-1-S-2"
address 172.16.1.100/24
port 1/1/1:1000
exit
interface "system"
address 172.31.2.1/32
exit
autonomous-system 64496
static-route-entry 0.0.0.0/0
next-hop 172.16.1.254 # VRRP backup address
no shutdown
exit
exit
IPSec is configured as follows:
configure
ipsec
ike-transform 1 create
exit
ike-policy 1 create
ike-version 2
dpd # dead peer detection (on peer side; not on MC-IPSec chassis)
ike-transform 1
exit
ipsec-transform 1 create
exit
Tunnel group 1 is configured as follows:
configure
isa
tunnel-group 1 isa-scale-mode tunnel-limit-2k create
primary 1/2
no shutdown
exit
The public IES service is configured as follows:
configure
service
ies 1 name "IES-1" customer 1 create
interface "int-IPsec-Public-1" create
address 10.10.10.254/24
tos-marking-state untrusted
sap tunnel-1.public:1 create
exit
exit
no shutdown
exit
The private VPRN service on CE-1 is configured as follows. Instead of configuring delivery-service 1 for the IPSec tunnel, it is possible to configure delivery-service-name "IES-1".
configure
service
vprn 2 name "VPRN-2" customer 1 create
ipsec
security-policy 1 create
entry 10 create
local-ip 192.168.1.1/32
remote-ip 192.168.1.5/32
exit
exit
exit
interface int-loopback-1 create
address 192.168.1.1/32
loopback
exit
interface int-IPsec-private-1 tunnel create
sap tunnel-1.private:1 create
ipsec-tunnel "tunnel-1" create
security-policy 1
local-gateway-address 10.10.10.1 peer 10.10.20.1 delivery-service 1
dynamic-keying
ike-policy 1
pre-shared-key "pass"
transform 1
exit
no shutdown
exit
exit
exit
static-route-entry 192.168.1.5/32
ipsec-tunnel "tunnel-1"
no shutdown
exit
exit
no shutdown
Configure S-2
On S-2, a local VPLS service 3 simulates a Layer 2 switch between CE-1, SeGW-3, and SeGW-4:
# on S-2
configure
service
vpls 3 name "VPLS-3" customer 1 create
sap 1/1/c1/1:1 create
description "to SAP in IES 1 on SeGW-3"
exit
sap 1/1/c1/2:1000 create
description "to router interface on CE-1"
exit
sap 1/1/c1/3:1 create
description "to SAP in IES 1 on SeGW-4"
exit
no shutdown
exit
Configure P-5
P-5 simulates the core network router, connecting to SeGW-3 and SeGW-4. The configuration on P-5 includes the following:
-
a loopback interface with address 192.168.1.5/32 in VPRN 2 is the destination address of the ping traffic from CE-1.
-
an MP-BGP session for the VPN-IPv4 address family between P-5, SeGW-3, and SeGW-4.
-
GRE spoke SDPs to connect to SeGW-3 and SeGW-4.
On P-5, the following router interfaces are configured in the base router. OSPF is used as IGP.
# on P-5
configure
router Base
interface "int-P-5-SeGW-3"
address 192.168.35.2/30
port 1/1/c1/2:1000
exit
interface "int-P-5-SeGW-4"
address 192.168.45.2/30
port 1/1/c1/1:1000
exit
interface "system"
address 192.0.2.5/32
exit
ospf 0
area 0.0.0.0
interface system
exit
interface "int-P-5-SeGW-3"
exit
interface "int-P-5-SeGW-4"
exit
exit
no shutdown
exit
On P-5, the following GRE SDPs are configured toward SeGW-3 and SeGW-4:
configure
service
sdp 53 create
description "GRE SDP toward SeGW-3"
signaling off
far-end 192.0.2.3
no shutdown
exit
sdp 54 create
description "GRE SDP toward SeGW-4"
signaling off
far-end 192.0.2.4
no shutdown
exit
VPRN 2 is configured on P-5, as follows:
configure
service
vprn 2 name "VPRN-2" customer 1 create
interface "int-loopback-1" create
address 192.168.1.5/32
loopback
exit
bgp-ipvpn
mpls
route-distinguisher 64496:2
vrf-target target:64496:2
no shutdown
exit
exit
spoke-sdp 53:2 create
exit
spoke-sdp 54:2 create
exit
no shutdown
exit
The BGP configuration on P-5 is as follows:
configure
router Base
autonomous-system 64496
bgp
group "MPBGP"
family vpn-ipv4
type internal
neighbor 192.0.2.3
exit
neighbor 192.0.2.4
exit
exit
no shutdown
exit
Configure IPSec tunnel on SeGW-3
The configuration on SeGW-3 is described in four consecutive sections. In this first section, the following is configured:
-
the tunnel group, which must be in multi-active mode before MC-IPSec can be enabled.
-
an interface "int-Redundant-1", which is a spoke-SDP terminated interface used for shunting.
-
GRE SDP 34 toward SeGW-4 and GRE SDP 35 toward P-5.
-
IPSec tunnel "tunnel-1" is the tunnel to CE-1; both SeGW-3 and SeGW-4 use the same local gateway address: 10.10.20.1.
The following configures tunnel group 1 on SeGW-3:
# on SeGW-3
configure
isa
tunnel-group 1 isa-scale-mode tunnel-limit-2k create
ipsec-responder-only
multi-active
mda 1/2
no shutdown
exit
On SeGW-3, the following router interfaces are configured in the base router. A static route is configured toward CE-1. OSPF is the IGP used between SeGW-3, SeGW-4, and P-5.
configure
router Base
interface "int-SeGW-3-P-5"
address 192.168.35.1/30
port 1/1/1:1000
no shutdown
exit
interface "int-SeGW-3-SeGW-4"
address 192.168.34.1/30
port 1/1/3:1000
no shutdown
exit
interface "system"
address 192.0.2.3/32
bfd 100 receive 100 multiplier 3
no shutdown
exit
static-route-entry 10.10.10.0/24
next-hop 172.16.1.100
no shutdown
exit
exit
ospf 0
area 0.0.0.0
interface "system"
no shutdown
exit
interface "int-SeGW-3-P-5"
no shutdown
exit
interface "int-SeGW-3-SeGW-4"
no shutdown
exit
exit
no shutdown
exit
The IPSec settings are as follows:
configure
ipsec
ike-transform 1 create
isakmp-lifetime 172800
exit
ike-policy 1 create
ike-version 2
ipsec-lifetime 7200
ike-transform 1
exit
ipsec-transform 1 create
exit
exit
The GRE SDPs are configured as follows:
configure
service
sdp 34 create
description "GRE SDP toward SeGW-4"
signaling off
far-end 192.0.2.4
keep-alive
shutdown
exit
no shutdown
exit
sdp 35 create
description "GRE SDP toward P-5"
signaling off
far-end 192.0.2.5
keep-alive
shutdown
exit
no shutdown
exit
The public IES service is configured as follows. The VRRP configuration will be added in a later step.
configure
service
ies 1 name "IES-1" customer 1 create
interface "int-SeGW-3-S-2" create
address 172.16.1.252/24
sap 1/1/2:1 create
description "SAP to switch S-2"
exit
exit
interface "int-IPsec-Public-1" create
address 10.10.20.254/24
tos-marking-state untrusted
sap tunnel-1.public:1 create
exit
static-tunnel-redundant-next-hop 192.168.34.2
exit
no shutdown
exit
The private VPRN service is configured as follows:
configure
service
vprn 2 name "VPRN-2" customer 1 create
ipsec
security-policy 1 create
entry 10 create
local-ip 192.168.1.5/32
remote-ip 192.168.1.1/32
exit
exit
exit
interface "int-IPsec-Private-1" tunnel create
sap tunnel-1.private:1 create
ipsec-tunnel "tunnel-1" create
security-policy 1
local-gateway-address 10.10.20.1 peer 10.10.10.1 delivery-service 1
dynamic-keying
ike-policy 1
pre-shared-key "pass"
transform 1
exit
no shutdown
exit
exit
static-tunnel-redundant-next-hop 192.168.20.2
exit
interface "int-Redundant-1" create
description "interface used for shunting"
address 192.168.20.1/30
spoke-sdp 34:20 create
ingress
vc-label 2049
exit
egress
vc-label 2048
exit
no shutdown
exit
exit
static-route-entry 192.168.1.1/32
ipsec-tunnel "tunnel-1"
no shutdown
exit
exit
bgp-ipvpn
mpls
route-distinguisher 64496:2
vrf-target target:64496:2
no shutdown
exit
exit
spoke-sdp 34:2 create
description "SDP to SeGW-4"
exit
spoke-sdp 35:2 create
description "SDP to P-5"
exit
no shutdown
exit
Enable MC-IPSec for tunnel group 1 on SeGW-3
In this section, the following steps are described:
-
Create a multi-chassis peer using the system address of SeGW-4.
-
Enable MCS for IPSec and tunnel group 1.
-
Enable MC-IPSec for the tunnel group with a configured priority 200.
-
Bind a central BFD session to MC-IPSec from the system interface.
Create multi-chassis peer 192.0.2.4 and enable MCS and MC-IPSec for tunnel group 1:
# on SeGW-3
configure
redundancy
multi-chassis
peer 192.0.2.4 create
sync
ipsec
tunnel-group 1 sync-tag "tag-1" create
no shutdown
exit
mc-ipsec
bfd-enable
tunnel-group 1 create
peer-group 1
priority 200
no shutdown
exit
exit
no shutdown
exit
exit
BFD is enabled in the preceding configuration. On the system interface, the following BFD settings are configured:
configure
router Base
interface "system"
address 192.0.2.3/32
bfd 100 receive 100 multiplier 3
no shutdown
exit
Configure MC-IPSec-aware routing on SeGW-3
In this step, a route policy is defined and applied to VPRN 2.
Route policy "IPsec-to-MPBGP" exports static route 192.168.1.1/32 in VPRN 2 to P-5. This policy sets the local preference of the prefix 192.168.1.1/32 according to the MC-IPSec state:
-
for the ipsec-master-with-peer state: local preference 200
-
for the ipsec-non-master state: local preference 100
-
for the ipsec-master-without-peer state: local preference 200
The state ipsec-master-without-peer can be used to attract traffic to the designated primary chassis in case of "dual master" (meaning two chassis lose the MIMP connection in the base routing instance). In this example, SeGW-3 has local preference 200 and SeGW-4 has local preference 100 for ipsec-master-without-peer.
The route policy is configured as follows:
# on SeGW-3:
configure
router Base
policy-options
begin
prefix-list "CE-1-Internal"
prefix 192.168.1.1/32 exact
exit
community "vprn2"
members "target:64496:2"
exit
policy-statement "IPsec-to-MPBGP"
entry 10
from
prefix-list "CE-1-Internal"
state ipsec-master-with-peer
exit
action accept
community add "vprn2"
local-preference 200
exit
exit
entry 20
from
prefix-list "CE-1-Internal"
state ipsec-non-master
exit
action accept
community add "vprn2"
local-preference 100
exit
exit
entry 30
from
prefix-list "CE-1-Internal"
state ipsec-master-without-peer
exit
action accept
community add "vprn2"
local-preference 200
exit
exit
default-action accept
community add "vprn2"
exit
exit
commit
The BGP configuration on SeGW-3 is as follows:
configure
router Base
autonomous-system 64496
bgp
group "MPBGP"
family vpn-ipv4
type internal
neighbor 192.0.2.4
exit
neighbor 192.0.2.5
exit
exit
no shutdown
exit
The route policy is applied as vrf-export in VPRN 2:
configure
service
vprn "VPRN-2"
bgp-ipvpn
mpls
vrf-export "IPsec-to-MPBGP"
exit
exit
exit
Configure MC-IPSec-aware VRRP on SeGW-3
In this section, a VRRP policy is defined that uses the mc-ipsec-non-forwarding priority event to lower the in-use VRRP priority upon MC-IPSec switchover, which ensures VRRP and MC-IPSec have the same primary chassis. The VRRP instance needs to be in preempt mode.
This VRRP policy is only configured on the designated VRRP primary chassis SeGW-3, not on the standby chassis. The VRRP policy is applied to the interface "int-SeGW3-S-2" of IES 1.
VRRP policy 1 is configured as follows:
# on SeGW-3:
configure
vrrp
policy 1
priority-event
mc-ipsec-non-forwarding 1
priority 50 explicit
exit
exit
exit
The VRRP policy is applied in VRRP instance 10 in the IES service:
configure
service
ies "IES-1"
interface "int-SeGW-3-S-2"
address 172.16.1.252/24
vrrp 10
backup 172.16.1.254
priority 200
policy 1
ping-reply
exit
---snip---
Configure SeGW-4
The configuration on the standby chassis SeGW-4 is similar, but with different priorities and without the VRRP policy.
The tunnel group is configured in multi-active mode:
# on SeGW-4
configure
isa
tunnel-group 1 create
ipsec-responder-only
multi-active
mda 1/2
no shutdown
exit
The MCS and MC-IPSec configuration is as follows:
configure
redundancy
multi-chassis
peer 192.0.2.3 create
sync
ipsec
tunnel-group 1 sync-tag "tag-1" create
no shutdown
exit
mc-ipsec
bfd-enable
tunnel-group 1 create
peer-group 1
priority 150
no shutdown
exit
exit
no shutdown
exit
exit
The base router configuration on SeGW-4 includes the following router interfaces and a static route to CE-1. OSPF is used as IGP between SeGW-3, SeGW-4, and P-5.
configure
router Base
interface "int-SeGW-4-P-5"
address 192.168.45.1/30
port 1/1/2:1000
no shutdown
exit
interface "int-SeGW-4-SeGW-3"
address 192.168.34.2/30
port 1/1/3:1000
no shutdown
exit
interface "system"
address 192.0.2.4/32
bfd 100 receive 100 multiplier 3
no shutdown
exit
static-route-entry 10.10.10.0/24
next-hop 172.16.1.100
no shutdown
exit
exit
ospf 0
area 0.0.0.0
interface "system"
no shutdown
exit
interface "int-SeGW-4-SeGW-3"
no shutdown
exit
interface "int-SeGW-4-P-5"
no shutdown
exit
exit
no shutdown
exit
The IPSec configuration is as follows:
configure
ipsec
ike-transform 1 create
isakmp-lifetime 172800
exit
ike-policy 1 create
ike-version 2
ipsec-lifetime 7200
ike-transform 1
exit
ipsec-transform 1 create
exit
The following route policy is configured on SeGW-4, The local preference is lower for the ipsec-master-without-peer state.
configure
router Base
policy-options
begin
prefix-list "CE-1-Internal"
prefix 192.168.1.1/32 exact
exit
community "vprn2"
members "target:64496:2"
exit
policy-statement "IPsec-to-MPBGP"
entry 10
from
prefix-list "CE-1-Internal"
state ipsec-master-with-peer
exit
action accept
community add "vprn2"
local-preference 200
exit
exit
entry 20
from
prefix-list "CE-1-Internal"
state ipsec-non-master
exit
action accept
community add "vprn2"
local-preference 100
exit
exit
entry 30
from
prefix-list "CE-1-Internal"
state ipsec-master-without-peer
exit
action accept
community add "vprn2"
local-preference 100 # lower preference on standby SeGW
exit
exit
default-action accept
community add "vprn2"
exit
exit
commit
The BGP configuration on SeGW-4 is as follows:
configure
router Base
autonomous-system 64496
bgp
group "MPBGP"
family vpn-ipv4
type internal
neighbor 192.0.2.3
exit
neighbor 192.0.2.5
exit
exit
no shutdown
exit
The following GRE SDPs are configured:
configure
service
sdp 43 create
description "GRE SDP toward SeGW-3"
signaling off
far-end 192.0.2.3
keep-alive
shutdown
exit
no shutdown
exit
sdp 45 create
description "GRE SDP toward P-5"
signaling off
far-end 192.0.2.5
keep-alive
shutdown
exit
no shutdown
exit
The public IES service is configured as follows:
configure
service
ies 1 name "IES-1" customer 1 create
interface "int-SeGW-4-S-2" create
address 172.16.1.253/24
vrrp 10
backup 172.16.1.254
ping-reply
exit
sap 1/1/1:1 create
description "SAP toward switch S-2"
exit
exit
interface "int-IPsec-Public-1" create
address 10.10.20.254/24
tos-marking-state untrusted
sap tunnel-1.public:1 create
exit
static-tunnel-redundant-next-hop 192.168.34.1
exit
no shutdown
exit
The private VPRN service is configured as follows:
configure
service
vprn 2 name "VPRN-2" customer 1 create
ipsec
security-policy 1 create
entry 10 create
local-ip 192.168.1.5/32
remote-ip 192.168.1.1/32
exit
exit
exit
interface "int-IPsec-Private-1" tunnel create
sap tunnel-1.private:1 create
ipsec-tunnel "tunnel-1" create
security-policy 1
local-gateway-address 10.10.20.1 peer 10.10.10.1 delivery-service 1
dynamic-keying
ike-policy 1
pre-shared-key "pass"
transform 1
exit
no shutdown
exit
exit
static-tunnel-redundant-next-hop 192.168.20.1
exit
interface "int-Redundant-1" create
description "interface used for shunting"
address 192.168.20.2/30
spoke-sdp 43:20 create
ingress
vc-label 2048
exit
egress
vc-label 2049
exit
no shutdown
exit
exit
static-route-entry 192.168.1.1/32
ipsec-tunnel "tunnel-1"
no shutdown
exit
exit
bgp-ipvpn
mpls
route-distinguisher 64496:2
vrf-export "IPsec-to-MPBGP"
vrf-target target:64496:2
no shutdown
exit
exit
spoke-sdp 43:2 create
description "SDP to SeGW-3"
exit
spoke-sdp 45:2 create
description "SDP to P-5"
exit
no shutdown
exit
Verification
The following will be verified in this section:
- the MC-IPSec status and VRRP status on SeGW-3 and SeGW-4
- the status of the IPSec tunnel on CE-1
- the status of the IPSec tunnel on the SeGWs
Verify the MC-IPSec status on SeGW-3 and SeGW-4
The following is verified:
-
SeGW-3 is the primary chassis and SeGW-4 is the standby for tunnel group 1 because SeGW-3 has the higher priority 200.
-
SeGW-3 is the primary node for VRRP instance 10 and SeGW-4 is the backup.
SeGW-3 is the primary chassis in tunnel group 1 with priority 200:
*A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:37:51
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up master
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
==============================================================================
SeGW-4 is the standby chassis in tunnel group 1 with priority 150:
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up standby
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
SeGW-3 is the primary node for VRRP instance 10:
*A:SeGW-3# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-3-S-2 10 No Up Master 200 1
IPv4 Up 1 200 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
SeGW-4 is backup for VRRP instance 10:
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Backup 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
Verify the IPSec tunnel on CE-1
The following is verified in this section:
- the connectivity between CE-1 and P-5
- the IPSec tunnel information
A ping command is launched from the loopback interface in VPRN 2 on CE-1 to the loopback interface in VPRN 2 on P-5:
*A:CE-1# ping router 2 192.168.1.5
PING 192.168.1.5 56 data bytes
64 bytes from 192.168.1.5: icmp_seq=1 ttl=63 time=3.97ms.
64 bytes from 192.168.1.5: icmp_seq=2 ttl=63 time=7.50ms.
64 bytes from 192.168.1.5: icmp_seq=3 ttl=63 time=2.84ms.
64 bytes from 192.168.1.5: icmp_seq=4 ttl=63 time=2.61ms.
64 bytes from 192.168.1.5: icmp_seq=5 ttl=63 time=2.67ms.
---- 192.168.1.5 PING Statistics ----
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min = 2.61ms, avg = 3.92ms, max = 7.50ms, stddev = 1.86ms
The following command shows the IPSec tunnel information.
*A:CE-1# show ipsec tunnel
===============================================================================
IPsec Tunnels
===============================================================================
TunnelName LocalAddress SvcId Admn Keying
SapId RemoteAddress DlvrySvcId Oper Sec
Plcy
-------------------------------------------------------------------------------
tunnel-1 10.10.10.1 2 Up Dynamic
tunnel-1.private:1 10.10.20.1 1 Up 1
-------------------------------------------------------------------------------
IPsec Tunnels: 1
===============================================================================
Verify the IPSec tunnel on the SeGWs
In this section, the following is verified:
-
the MCS database is in-sync, so the tunnel status is up on both chassis.
-
P-5 receives two VPN-IPv4 routes for prefix 192.168.1.1/32: the route from SeGW-3 has local preference 200; the route from SeGW-4 has local preference 100.
On both SeGWs, the IPSec tunnel with local address 10.10.20.1 and remote address 10.10.10.1 is up:
*A:SeGW-3# show ipsec tunnel
===============================================================================
IPsec Tunnels
===============================================================================
TunnelName LocalAddress SvcId Admn Keying
SapId RemoteAddress DlvrySvcId Oper Sec
Plcy
-------------------------------------------------------------------------------
tunnel-1 10.10.20.1 2 Up Dynamic
tunnel-1.private:1 10.10.10.1 1 Up 1
-------------------------------------------------------------------------------
IPsec Tunnels: 1
===============================================================================
*A:SeGW-4# show ipsec tunnel
===============================================================================
IPsec Tunnels
===============================================================================
TunnelName LocalAddress SvcId Admn Keying
SapId RemoteAddress DlvrySvcId Oper Sec
Plcy
-------------------------------------------------------------------------------
tunnel-1 10.10.20.1 2 Up Dynamic
tunnel-1.private:1 10.10.10.1 1 Up 1
-------------------------------------------------------------------------------
IPsec Tunnels: 1
===============================================================================
MCS is in sync on both SeGWs:
*A:SeGW-3# show redundancy multi-chassis sync
===============================================================================
Multi-chassis Peer Table
===============================================================================
Peer
-------------------------------------------------------------------------------
Peer IP Address : 192.0.2.4
Description : (Not Specified)
Authentication : Disabled
Source IP Address : 192.0.2.3
Admin State : Enabled
Warm standby : No
Remote warm standby : No
Sub-mgmt options :
DHCP lease threshold : Inactive
Local / Remote : -- / --
-------------------------------------------------------------------------------
Sync-status
-------------------------------------------------------------------------------
Client Applications : IPsec
Sync Admin State : Up
Sync Oper State : Up
Sync Oper Flags :
DB Sync State : inSync
Num Entries : 2
Lcl Deleted Entries : 0
Alarm Entries : 0
OMCR Standby Entries : 0
OMCR Alarm Entries : 0
Rem Num Entries : 2
Rem Lcl Deleted Entries : 0
Rem Alarm Entries : 0
Rem OMCR Standby Entries: 0
Rem OMCR Alarm Entries : 0
===============================================================================
===============================================================================
*A:SeGW-4# show redundancy multi-chassis sync
===============================================================================
Multi-chassis Peer Table
===============================================================================
Peer
-------------------------------------------------------------------------------
Peer IP Address : 192.0.2.3
Description : (Not Specified)
Authentication : Disabled
Source IP Address : 192.0.2.4
Admin State : Enabled
Warm standby : No
Remote warm standby : No
Sub-mgmt options :
DHCP lease threshold : Inactive
Local / Remote : -- / --
-------------------------------------------------------------------------------
Sync-status
-------------------------------------------------------------------------------
Client Applications : IPsec
Sync Admin State : Up
Sync Oper State : Up
Sync Oper Flags :
DB Sync State : inSync
Num Entries : 2
Lcl Deleted Entries : 0
Alarm Entries : 0
OMCR Standby Entries : 0
OMCR Alarm Entries : 0
Rem Num Entries : 2
Rem Lcl Deleted Entries : 0
Rem Alarm Entries : 0
Rem OMCR Standby Entries: 0
Rem OMCR Alarm Entries : 0
===============================================================================
===============================================================================
The following command shows that P-5 received two VPN-IPv4 routes for prefix 192.168.1.1/32: one from SeGW-3 with local preference 200 and one from SeGW-4 with local preference 100:
*A:P-5# show router bgp routes vpn-ipv4
===============================================================================
BGP Router ID:192.0.2.5 AS:64496 Local AS:64496
===============================================================================
Legend -
Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid
l - leaked, x - stale, > - best, b - backup, p - purge
Origin codes : i - IGP, e - EGP, ? - incomplete
===============================================================================
BGP VPN-IPv4 Routes
===============================================================================
Flag Network LocalPref MED
Nexthop (Router) Path-Id IGP Cost
As-Path Label
-------------------------------------------------------------------------------
u*>i 64496:2:192.168.1.1/32 200 None
192.0.2.3 None 10
No As-Path 524287
*i 64496:2:192.168.1.1/32 100 None
192.0.2.4 None 10
No As-Path 524287
u*>i 64496:2:192.168.20.0/30 100 None
192.0.2.3 None 10
No As-Path 524287
*>i 64496:2:192.168.20.0/30 100 None
192.0.2.4 None 10
No As-Path 524287
u*>i 64496:2:192.168.20.1/32 100 0
192.0.2.3 None 10
No As-Path 524287
u*>i 64496:2:192.168.20.2/32 100 0
192.0.2.4 None 10
No As-Path 524287
-------------------------------------------------------------------------------
Routes : 6
===============================================================================
MC-IPSec failover scenarios
Two MC-IPSec failover scenarios are described in this section:
- MC-IPSec failover when MS-ISA is disabled
- MC-IPSec failover when the primary chassis SeGW-3 reboots
Failover when MS-ISA is disabled
Initially, SeGW-3 is the primary chassis and SeGW-4 is the standby:
*A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:37:51
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up master
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
*A:SeGW-3# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-3-S-2 10 No Up Master 200 1
IPv4 Up 1 200 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up standby
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Backup 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
The following command disables the MS-ISA on the primary chassis SeGW-3, which will trigger an MC-IPSec failover.
configure
card 1
mda 2
shutdown
With MS-ISA disabled, the MC-IPSec state of tunnel group 1 on SeGW-3 becomes notEligible, which means that the tunnel group is down, see the 7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Guide for details description of MIMP states.:
*A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:37:51
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up notEligible
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
SeGW-3 is backup for VRRP instance 10 with in-use priority 50, as per the VRRP policy 1:
*A:SeGW-3# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-3-S-2 10 No Up Backup 200 1
IPv4 Up 1 50 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
SeGW-4 is now the primary chassis in tunnel group 1. This is triggered by MC-IPSec failover, as per the mc-ipsec-non-forwarding event in VRRP policy 1.
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up master
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
SeGW-4 is primary for VRRP instance 10;
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Master 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
The situation is restored by enabling MS-ISA on SeGW-3:
configure
card 1
mda 2
no shutdown
MC-IPSec failover when primary chassis reboots
The following tools command on SeGW-3 triggers an MC-IPSec switchover:
tools perform redundancy multi-chassis mc-ipsec force-switchover tunnel-group 1
A:SeGW-3# tools perform redundancy multi-chassis mc-ipsec force-switchover tunnel-group 1
WARNING! Forcing a mastership switchover may significantly impact traffic. Are you sure (y/n)? y
SeGW-3 is the primary chassis for tunnel group 1:
A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:37:51
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up master
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
SeGW-3 is primary for VRRP instance 10:
A:SeGW-3# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-3-S-2 10 No Up Master 200 1
IPv4 Up 1 200 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
SeGW-4 is the standby chassis for tunnel group 1:
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up standby
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
The VRRP state on SeGW-4 is backup:
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Backup 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
The following command reboots the primary chassis SeGW-3:
admin reboot now
While SeGW-3 reboots, the IPSec state of SeGW-4 becomes eligible:
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up eligible
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
The VRRP state on SeGW-4 is primary (master):
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Master 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
When SeGW-3 comes up, the IPSec state of tunnel group 1 is discovery, which means that the system has not established the MIMP session with its peer yet.
A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/10/2023 12:17:46
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up discovery
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
After a while, the preceding show command is repeated and the IPSec state for tunnel 1 on SeGW-3 is standby:
A:SeGW-3# show redundancy multi-chassis mc-ipsec peer 192.0.2.4
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.4
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:46:03
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 200 Up standby
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
The VRRP state on SeGW-3 is backup:
A:SeGW-3# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-3-S-2 10 No Up Backup 200 1
IPv4 Up 1 50 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
SeGW-4 is the primary chassis in MC-IPSec tunnel group 1:
*A:SeGW-4# show redundancy multi-chassis mc-ipsec peer 192.0.2.3
===============================================================================
Multi-Chassis MC-IPsec
===============================================================================
Peer Name : (Not Specified)
Peer Addr : 192.0.2.3
Keep Alive Intvl: 1.0 secs Hold on Nbr Fail : 3
Discovery Intvl : 300 secs Discovery Boot Intvl : 300 secs
BFD : Enable
Last update : 02/13/2023 09:38:21
======================================================================
Multi-Chassis IPsec Multi Active Tunnel-Group Table
======================================================================
ID Peer Group Priority Admin State Mastership
----------------------------------------------------------------------
1 1 150 Up master
----------------------------------------------------------------------
Multi Active Tunnel Group Entries found: 1
======================================================================
===============================================================================
SeGW-4 is the primary node for VRRP instance 10:
*A:SeGW-4# show router vrrp instance
===============================================================================
VRRP Instances
===============================================================================
Interface Name VR Id Own Adm State Base Pri Msg Int
IP Opr Pol Id InUse Pri Inh Int
-------------------------------------------------------------------------------
int-SeGW-4-S-2 10 No Up Master 100 1
IPv4 Up n/a 100 No
Backup Addr: 172.16.1.254
-------------------------------------------------------------------------------
Instances : 1
===============================================================================
Configuration guidelines
The following is a list of guidelines for configuring MC-IPSec:
-
To avoid high CPU load and issues in some complex cases, the following are suggestions for configuring the IKEv2 lifetime:
-
Both IKE_SA and CHILD_SA lifetime on MC-IPSec chassis (SeGW-3 and SeGW-4) should be around three times larger than on the IPSec peer (CE-1).
-
With the first rule, the lifetime of the side with smaller lifetime (IPSec peer CE-1) should not be too small (these being the default values):
-
IKE_SA: >= 86400 seconds
-
CHILD_SA: >= 3600 seconds
-
-
With the first rule, on the side with smaller lifetime (IPSec peer CE-1), the IKE_SA lifetime must be at least 3 times larger than CHILD_SA lifetime.
-
-
The IKE protocol is the control plane of IPSec, so IKE packets must be treated as high QoS priority in the end-to-end path of the public service. On the public interface, a SAP ingress QoS policy must be configured to ensure that IKE packets get high QoS priority.
-
Configure ipsec-responder-only under tunnel-group for static LAN-to-LAN tunnels.
-
Enable dead peer detection (DPD) on the IPSec peer side (CE-1); disable DPD (default) on the MC-IPSec chassis side.
-
The direct and redundant physical link between MC-IPSec chassis must be configured with sufficient bandwidth for MCS and shunting traffic, and proper QoS configuration to make sure the MIMP and MCS packets are treated as high priority traffic.
-
The system time must be same on both MC-IPSec chassis.
-
Make sure the protection status is nominal on both chassis before provoking a controlled switchover. The protection status can be displayed with the show redundancy multi-chassis mc-ipsec peer <addr> command.
-
Wait at least five minutes between two consecutive switchovers if possible, to prevent a second switchover happening before the standby is ready to become the primary chassis.
Conclusion
MC-IPSec provides a stateful multi-chassis IPSec redundancy solution. This is very important in a carrier grade network, especially in applications such as mobile backhaul where high value mobile services run over IPSec tunnels.