System management
The 7705 SAR-Hm series of routers supports system management parameters as covered in the following topics:
Security
For general information about system security support, see the following topics in the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide, "Security":
-
Authentication, authorization, and accounting
-
Authentication
-
Local authentication
-
RADIUS authentication
-
TACACS+ authentication
-
-
Authorization
-
Local authorization
-
RADIUS authorization
-
TACACS+ authorization
-
-
Security controls
-
-
RADIUS VSAs
-
TACACS+ services and VSAs
-
Control and management traffic protection
-
TTL security
-
Management Access Filter
-
-
Other security features
-
SSH
-
SSH PKI authentication
-
MAC client and server list
-
KEX client and server list
-
Regenerate the SSH key without disabling SSH
-
-
Exponential login backoff
-
User lockout
-
CLI login scripts
-
File access controls
-
802.1x network access control
-
TCP enhanced authentication option
-
- Configuring security with CLI
For descriptions of security commands, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Classic CLI Command Reference Guide and the 7450 ESS, 7750 SR, 7950 XRS, and VSR Clear, Monitor, Show, and Tools CLI Command Reference Guide.
SNMP
For general information about SNMP support, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide, "SNMP".
Event logs
For general information about event log support, see the following topics in the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide, "Event and accounting logs":
-
Logging overview
-
Log destinations
-
Console
-
Session
-
CLI logs
-
Memory logs
-
Log and accounting files
- Log file encryption
-
SNMP trap group
-
Syslog
-
-
Event logs
-
Configuration notes
-
Configuring logging with CLI
Public key infrastructure
For general information about public key support, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide, "Public key infrastructure".
In-band management over LTE
The 7705 SAR-Hm series of routers supports the following modes of operation over a cellular network:
-
static cellular system IPv4 mode
-
static cellular interface IPv4 mode or IPv6 mode
-
dynamic cellular interface IPv4 mode or IPv6 mode
The way in which the node is managed depends on which mode of operation is in use. See Services over the cellular PDN interface for more information about the modes of operation.
When a cellular port on the node is operating in static cellular system IP mode, the system IP address is identical to the cellular IP address assigned during the initial PDN attachment process. To manage the node in this mode, the NSP NFM-P or other network management platform reaches the node without using the system IP address directly over the cellular network. This is the only mode that does not require a pre-established in-band management service to manage the node.
When a cellular port on the node is operating in static cellular interface IP mode or dynamic cellular interface IP mode, the NSP NFM-P or other network management platform can only reach the node through an in-band management VPRN service. For these modes of operation, the system IP address used to manage the node is private and differs from the cellular port IP address assigned when connecting to the cellular network. The system IP address must be advertised from the 7705 SAR-Hm series node to the head-end node by the in-band management VPRN service. Routing in the private IP/MPLS network past the head-end node must allow management traffic to reach the head-end node which will then send the management traffic over the VPRN to the node being managed.
The NSP NFM-P automatically configures the required in-band management VPRN service during the ADP-Hm process; see ADP-Hm for more information.
On the 7705 SAR-Hm series nodes, there are two methods for enabling in-band management over a VPRN service:
-
performing a Global Routing Table (GRT) lookup and VPRN-to-GRT route leaking
-
using port cross-connect
GRT lookup and VPRN-to-GRT route leaking
GRT lookup and VPRN-to-GRT route leaking shows the GRT lookup and VPRN-to-GRT route leaking option for in-band management over a VPRN on the 7705 SAR-Hm.
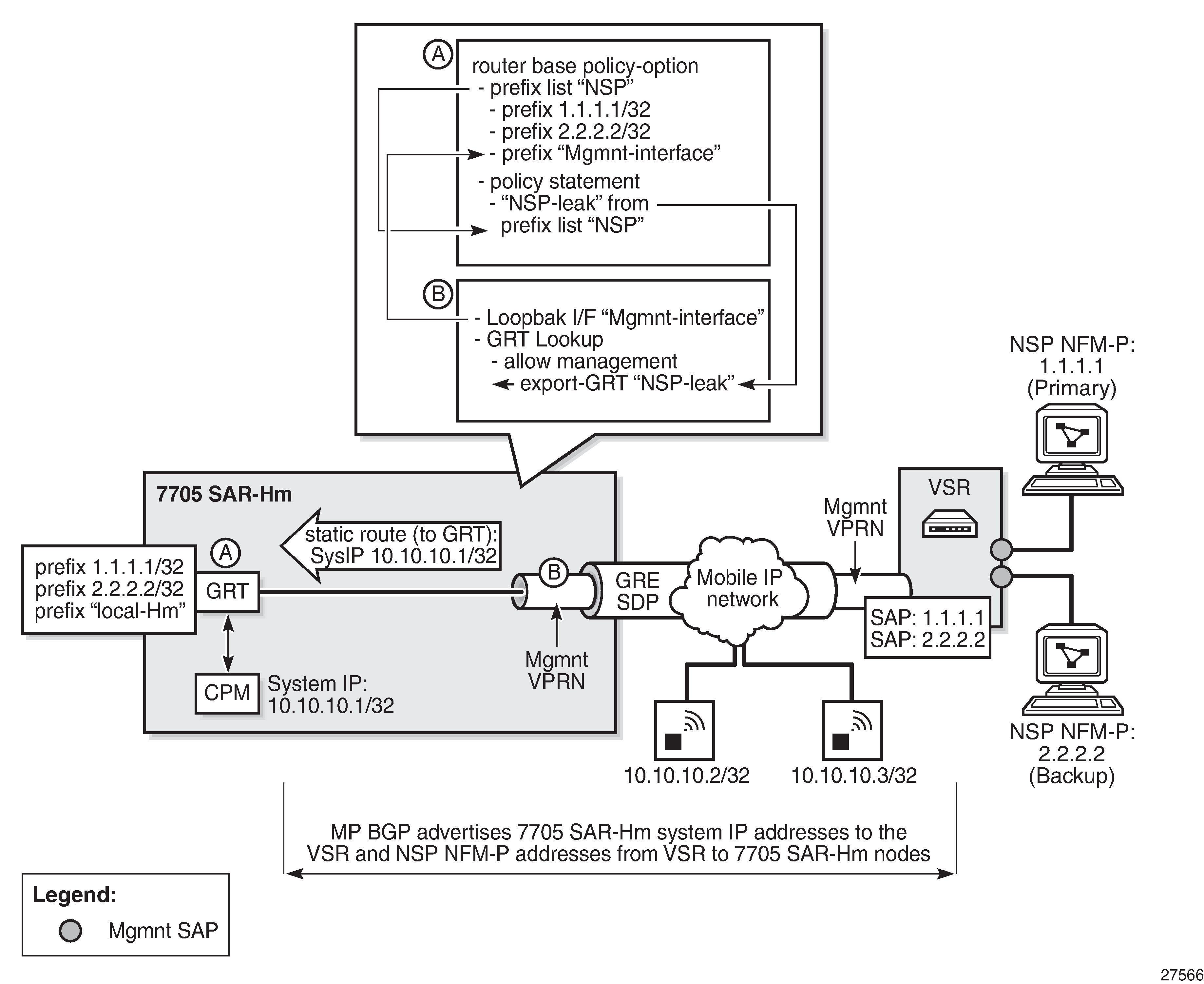
In-band management using the GRT lookup and VPRN-to-GRT route leaking option is enabled by configuring the following elements:
-
A base router policy statement that includes a prefix list used to leak VPRN reachable addresses to the GRT. This prefix list includes the NSP NFM-P addresses and the management loopback interface that allows the CPM to respond to management queries or commands from the NSP NFM-P.
-
A management loopback interface configured under the VPRN to allow the CPM to respond to management queries from the NSP NFM-P.
-
A static route from the VPRN to the GRT for the system IP address of the node
-
Enable a GRT lookup from the VPRN to the GRT so that management traffic received over the VPRN from the NSP NFM-P to the 7705 SAR-Hm series node can reach the CPM. This uses the grt-lookup, enable-grt, and allow-local-management CLI commands in the config>service>vprn context. For descriptions of these commands, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Classic CLI Command Reference Guide.
-
A VPRN-to-GRT route leak that populates the GRT routing table with addresses that are reachable by the VPRN, using the export-grt command. For a description of this command, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Classic CLI Command Reference Guide. The reachable addresses include those for the NSP NFM-P and the local management loopback interface that allows responses from the CPM to return to the corresponding VPRN.
The following CLI output shows a configuration example of in-band management using GRT lookup and VPRN-to-GRT route leaking, based on GRT lookup and VPRN-to-GRT route leaking.
#--------------------------------------------------
echo "Policy Configuration"
#--------------------------------------------------
policy-options
begin
prefix-list "NSP"
prefix 1.1.1.1/24 exact
prefix 2.2.2.2/24 exact
prefix 192.168.255.0/32 exact
exit
policy-statement "NSP-leak"
entry 10
from
prefix-list "NSP"
exit
action accept
exit
exit
exit
commit
exit
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
customer 1 name "1" create
description "Default customer"
exit
vprn 1 name "1" customer 1 create
interface "NSP" create
exit
exit
vprn 1 name "1" customer 1 create
route-distinguisher 65650:1
auto-bind-tunnel
resolution-filter
gre
exit
resolution filter
exit
vrf-target target:65650:1
interface "Mgmnt-interface" create
address 192.168.255.0/32
loopback
exit
static-route-entry 10.10.10.1/32
grt
no shutdown
exit
exit
grt-lookup
enable-grt
allow-local-management
exit
export-grt "NSP-leak"
exit
no shutdown
exit
exit
Port cross-connect (PXC)
For information about PXC, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Interface Configuration Guide, "Port Cross-connect".
In-band management using a VPRN service and PXC shows an example of the operation of in-band management using a VPRN and PXC.
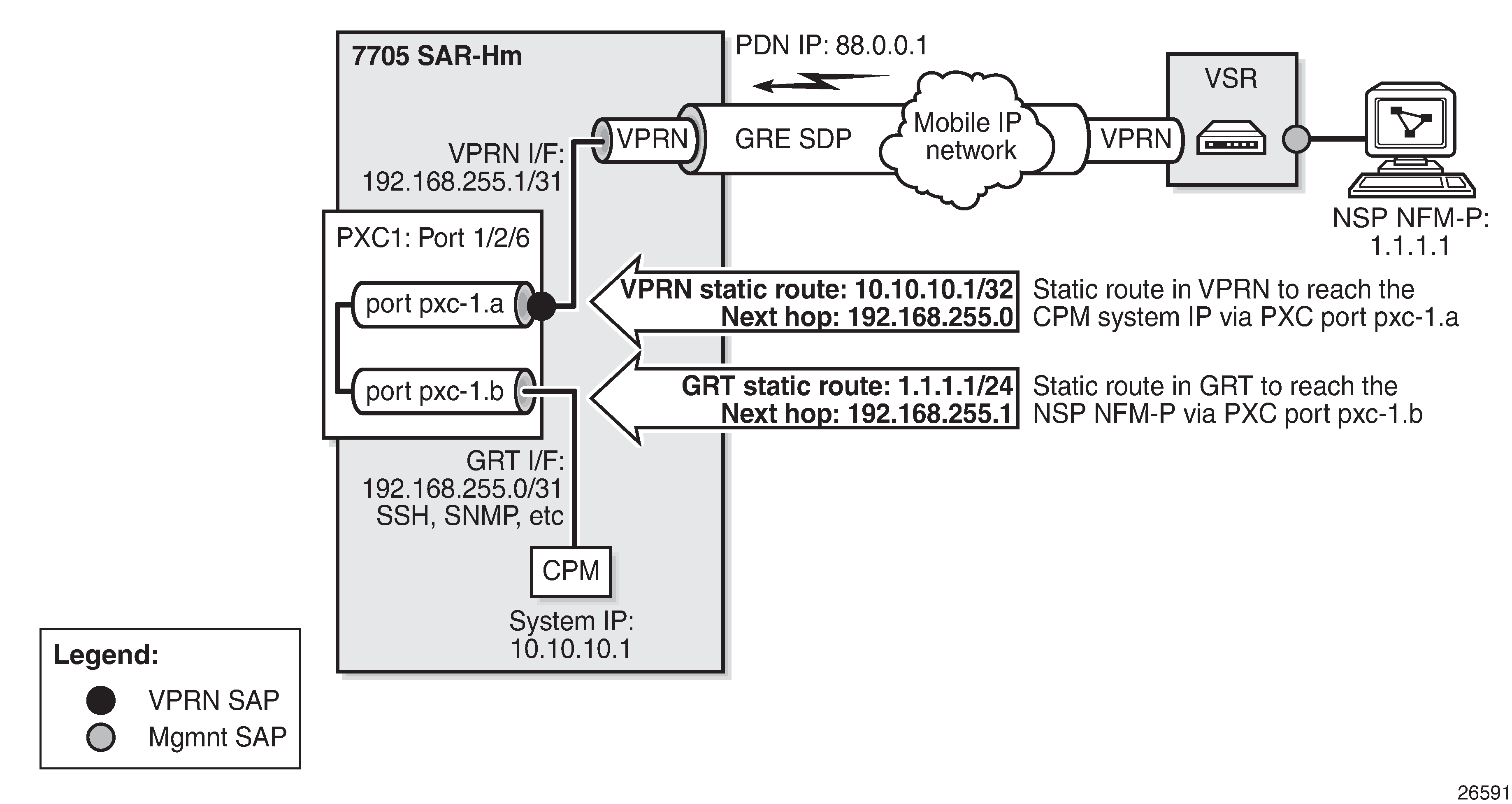
The following CLI example shows the configuration of the PXC based on the example shown in In-band management using a VPRN service and PXC.
- Example:
-
A:DUT>config>port 1/2/6 shutdownA:DUT>config>port-xcA:DUT>config>port-xc# pxc 1 createA:DUT>config>port-xc>pxc# port 1/2/6A:DUT>config>port-xc>pxc# no shutdownA:DUT>config>port-xc>pxc# exit allA:DUT>>configureA:DUT>>config# port pxc-1.a no shutdownA:DUT>>config# port pxc-1.b no shutdownA:DUT>>config# port 1/2/6 no shutdown
To ensure management traffic from the CPM can reach the NSP NFM-P over the VPRN, an interface in the Global Routing Table (GRT) is configured on one of the PXC ports. In the example shown in In-band management using a VPRN service and PXC, the GRT PXC port is port pxc-1.b. This port is looped internally together with PXC port pxc-1.a, the SAP of the in-band management VPRN. A router interface is required on port pxc-1.b:1 (VLAN 1) and used to route management traffic from the CPM toward the in-band management VPRN. A static route is configured in the GRT for the NSP NFM-P address, 1.1.1.1, with a next hop of the VPRN SAP, or port pxc-1.a:1. The following CLI output shows configuration examples in the GRT.
*A:DUT>config>service>vprn# info
----------------------------------------------
interface "pxc"
address 192.168.255.0/31
port pxc-1.b:1
no shutdown
exit
...
static-route-entry 1.1.1.1/24
next-hop 192.168.255.1
no shutdown
exit
exit
...
----------------------------------------------
*A:DUT>config>router#
A SAP interface on the other PXC port is required by the in-band management VPRN to route management traffic toward the CPM. A static route is configured in the VPRN for the CPM system IP address 10.10.10.1, with a next hop of the GRT interface port pxc-1.b:1. The following CLI output shows configuration examples for the VPRN.
*A:ALU-1>config>service# info
----------------------------------------------
...
vprn 1 customer 1 create
autonomous-system 65200
route-distinguisher 65200:1
auto-bind-tunnel
resolution-filter
gre
exit
exit
vrf-target target:65200:1
interface "pxc" create
address 192.168.255.1/31
sap pxc-1.a:1 create
exit
exit
static-route-entry 10.10.10.1/32 next-hop 192.168.255.0
no shutdown
exit
...